IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH A High-speed, Low-Resource ASR Back-end Based on Custom Arithmetic
|
|
|
- Candace Riley
- 5 years ago
- Views:
Transcription
1 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH A High-speed, Low-Resource ASR Back-end Based on Custom Arithmetic Xiao Li, Jonathan Malkin, Jeff Bilmes Abstract With the skyrocketing popularity of mobile devices, new processing methods tailored to a specific application have become necessary for low-resource systems. This work presents a high-speed, low-resource speech recognition system using custom arithmetic units, where all system variables are represented by integer indices and all arithmetic operations are replaced by hardware-based table lookups. To this end, several reordering and rescaling techniques, including two accumulation structures for Gaussian evaluation and a novel method for the normalization of Viterbi search scores, are proposed to ensure low entropy for all variables. Furthermore, a discriminatively inspired distortion measure is investigated for scalar quantization of forward probabilities to maximize the recognition rate. Finally, heuristic algorithms are explored to optimize system-wide resource allocation. Our best bit-width allocation scheme only requires 59kB of ROMs to hold the lookup tables, and its recognition performance with various vocabulary sizes in both clean and noisy conditions is nearly as good as that of a system using a 32- bit floating-point unit. Simulations on various architectures show that on most modern processor designs, we can expect a cyclecount speedup of at least 3 times over systems with floating-point units. Additionally, the memory bandwidth is reduced by over 70% and the offline storage for model parameters is reduced by 80%. Index Terms Speech recognition, custom arithmetic, high speed, low resource, quantization, normalization, bit-width allocation, discriminative distortion measure, forward probability normalization and scaling, alpha recursion I. INTRODUCTION THE burgeoning development of mobile devices has brought about a great need for a more friendly and convenient user interface. Automatic speech recognition (ASR) has unquestionable utility when used in environments without a keyboard, or where hands are unavailable. To take full advantage of the envisioned smart home of the future, in which most appliances are online and connected, we will want a fully-functioning ASR system on a highly portable device, such as a watch, necklace, or pendant. However, unlike desktop applications with ample memory and a perpetual power supply, portable devices suffer from limited computational and memory resources and strict power consumption constraints. Most state-of-the-art ASR systems running on desktops use continuous-density HMMs (CHMM with floating-point arithmetic. These systems are computationally expensive, posing potential problems for real-time processing and battery life. The development of a high-speed, low-resource ASR system, therefore, becomes crucial to the prevalence of speech technologies on mobile devices. This work was funded by National Science Foundation under Grant Award The authors are with the Department of Electrical Engineering, University of Washington. s: {lixiao, sm, bilmes}@ee.washington.edu In the literature, there are many techniques to speed up computation at the algorithmic level, among which quantization with table lookups has been extensively used. First, observation vectors or sub-vectors can be quantized and their state or Gaussian mixture component likelihoods can be obtained efficiently via pre-computed tables. A discrete-density HMM, for example, applies vector quantization (VQ) to the observations and approximates the state likelihood computation by lookup operations. As a further improvement, a discrete mixture HMM assumes discrete distributions at the scalar or subvector level of a mixture model, and applies scalar quantization or sub-vector quantization to the observations [1], [2]. Even in a CHMM, the computational load can be greatly reduced by restricting the precise likelihood computation to the most relevant Gaussians using VQ [3], [4]. Second, quantization techniques also contribute to a compact representation of model parameters, which not only saves memory but also reduces computational cost [5] [9]. The problem can also be approached from the hardware side. A floating-point unit is power-hungry, and requires a rather large chip area when implemented. Software implementation of floating-point arithmetic takes less power and chip area, but has significantly higher latencies [10]. Additionally, speech recognizers usually do not use the precision of a floating-point representation efficiently. Fixed-point arithmetic offers only a partial solution. Operations can be much faster using a fixed-point implementation [11] [13]. But this method often cuts the available dynamic range without having its representation precision fully utilized. Additionally, some operations can still take numerous processor cycles to complete. Fixed-point ALUs, therefore, are often combined with rescaling and table lookup techniques for better performance. With 32-bit computing having reached the embedded market and after years of finding ways to make general purpose chips more powerful, the use of custom logic might seem a rather curious choice [14]. Many signal processing applications produce system variables (system inputs, outputs and all intermediate values) with very low entropy. It would be beneficial to record these computation results so that they may be reused many times in the future, thereby amortizing the cost of computation. [15] uses cache-like structures they call memo-tables to store the outputs of particular instruction types. It performs a table lookup in parallel with conventional computation which is halted if the lookup succeeds. The paper argues that the cycle time of a memo-table lookup is comparable to that of a cache lookup. Generally speaking, quantization on a lower-entropy variable, using a fixed number of bits, has a smaller expected quantization distortion. Motivated by empirically observed low
2 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH entropy of the variables within several speech recognition systems, we present a novel custom arithmetic architecture based on high-speed lookup tables (LUTs). Therein, each system variable is quantized to low precision and each arithmetic operation is pre-computed for each of its input and output codewords vectors. The goal is appealing, considering the high speed and low power consumption of a hardware-based lookup compared to that of a complicated arithmetic function. On the other hand, the obective also looks daunting, since an ASR system might have dozens of variables and operations, leading to a prohibitive amount of storage for tables. Therefore, to implement an ASR system using custom arithmetic units, the first and foremost assumption is that the value distributions of such a system have entropy low enough for low-precision quantization. Second, the quantization of a specific variable should ideally be consistent with minimizing the degradation in recognition performance. Finally, a bit-width allocation algorithm must be provided to optimize the resource performance. While in [16] and [17] we proposed a general design methodology for custom arithmetic and reported preliminary results for system development, this paper approaches the problem systematically, discusses the solutions in great detail and presents new evaluation results with different vocabulary sizes and in different noisy conditions. We choose to apply custom arithmetic to the back-end but not to the front-end for several reasons. The back-end accounts for most of the computational load of an ASR system, but it has fewer variables than the front-end since many of its operations are repetitive. By contrast, the front-end has relatively low computational cost but a large variety of variables and operations which would quickly complicate the lookup table design. In addition, the fixed-point arithmetic for feature extraction has been well studied and can be implemented by DSPs very efficiently [18]. Therefore, we envision a chip using a combination of both standard fixed-point arithmetic for the front-end, and custom arithmetic for the back-end. The rest of the paper is organized as follows. Section II discusses the general mechanism of custom arithmetic. Section III and Section IV present our computation reordering technique for Gaussian evaluation and our normalization method for Viterbi search respectively. Section V formulates a discriminatively inspired distortion measure for quantizing forward probabilities. Section VI investigates several heuristics for bit-width allocation. Section VII describes our system organization, and Section VIII reports our word error rate (WER) and cycle time experiments and results, followed by concluding remarks. II. GENERAL DESIGN METHODOLOGY In this section we present an ASR system driven by custom arithmetic, where all floating-point calculations are precomputed. In addition, we address several potential issues associated with custom arithmetic design for an ASR system. A. General Arithmetic Mechanism A high-level programming language allows complex expressions involving multiple operands. We split all such complex expressions into sequences of two-operand operations by introducing intermediate variables. We can then express any operation on scalar variables V i and V, with the result saved as V h, by a function, V h = F k (V i, V ), where i,, h {1..L}. The function F k ( ), k {1..K}, can be an arbitrary arithmetic operation or sequence of operations, e.g. V h = (V i V ) 2. The first step of custom arithmetic design is to create a codebook for each scalar variable. The codewords are the quantized values of that variable, and the indices of those codewords are consecutive integers. For a variable with value V l = x, the closest codeword in the codebook is denoted as Q Vl (x), and its associated index is denoted as I Vl (x). Second, a table T Fk is created to store all allowable values for the function F k ( ), as defined by the input and output codebooks. Each address in the table is determined by the indices of the input operand codewords and the output is the index of the result s codeword. Equationally, for z = F k (x, y), we have I Vh (z) = T Fk (I Vi (x), I V (y)). If the output and the two inputs have bit-widths of n 0, n 1, and n 2, respectively, then the table requires a total storage of n 0 2 n1+n2 bits. The final step in designing this custom arithmetic system is to replace all floating-point values with the corresponding integer indices and approximate all two-operand arithmetic operations with table lookups. Note that the output index is used as the input of the next table lookup, so that all data flow and storage are represented in integer form, and all complex operations become a series of simple table accesses. The physical device realization of the LUTs is beyond the scope of this work. The implementation of custom arithmetic units can be simplified using reconfigurable logic [19], [20], although at the expense of increased power consumption. B. Design Issues for ASR In spite of the attractiveness of custom arithmetic, such a system becomes unrealistic if the table size gets too large. This poses several challenges to the custom arithmetic design for an ASR system: 1) How to modify the decoding algorithm to ensure low entropy for all system variables. 2) What are quantization methods consistent with recognition rate maximization. 3) How to allocate bit-widths among system variables to optimize resource performance. As stated in the introduction, the foremost assumption of a custom arithmetic based system is the low entropy of all system variables. Most variables in a state-of-the-art ASR backend, as will be seen in Section VIII, can be quantized to low precision without loss of recognition accuracy. However there do exist several variables with high entropy, which must be tackled by algorithmic level modification. In the Mahalanobis distance calculation of Gaussian evaluation, for example, the distance is accumulated along the dimension of the features, resulting in a relatively spread-out distribution covering all partial accumulations. Additionally, the forward probability α in decoding possesses a potentially more fatal problem the forward pass computes over an arbitrarily long utterance in real applications, making α s value distribution unknown to the quantizer at the codebook design stage. Consequently,
3 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH the designed codebook may not cover all values that may occur at decode time, leading to poor recognition performance. Although certain normalization techniques have been proposed in the literature, they can not essentially solve the problem for custom arithmetic design. Potential solutions to this first issue will be discussed in Section III and Section IV. The second issue is in fact a quantization problem. Since the bit-width of each variable directly influences the table size, we want each variable to be scalar quantized to as low precision as possible without degradation in recognition rate. The distortion measure should ideally be consistent with minimizing recognition degradation. In this work, we are particularly interested in further compressing the forward probability α, which has the highest entropy even after rescaling, as will be shown in Section VIII. Section V presents a discriminatively inspired distortion measure to quantize this variable. Finally, the last issue is a search problem for optimally allocating memory resources among tables. Since the search space could be quite large for an ASR system, we investigate several heuristics in Section VI to find the best search scheme within the existing computational capacity. III. COMPUTATION REORDERING FOR GAUSSIAN LIKELIHOOD EVALUATION Gaussian evaluation can dominate the operational load by taking up to 96% of the total computation for a typical small vocabulary application [3], and 30% to 70% of the total computation for LVCSR tasks [4]. However, the nature of Gaussian evaluation makes this task particularly suited to our custom arithmetic, as will be seen in this section. As a side note, the required memory footprint for these calculations can also be reduced through the use of lookup tables, providing an added benefit. A. Problem Formulation Log arithmetic is widely used in practical ASR systems to achieve numerical values with a very wide dynamic range. In this paper, a variable with a bar denotes its log value. For example, x = log x. Also, denotes log addition where x ȳ = log(e x + eȳ) 1. To this end, the log state likelihood b (t) of the t th observation vector (x 1 (t), x 2 (t),..., x D (t)), given a certain state q t =, can be expressed as b (t) = i M ( w i + c i 1 2 D (x k (t) µ i,k ) 2 ), (1) k=1 σ 2 i,k where M is the subset of diagonal Gaussians belonging to state ; the variables µ i,k and σ i,k are the mean and variance scalars of a Gaussian respectively; w i is the log value of the i th component responsibility (or mixture weight) and c i is a constant, both of which can be computed offline. As mentioned earlier, many operations in Gaussian evaluation are repetitive: to evaluate the observation probabilities for an utterance with T frames in a system with M different Gaussian components, the operation of the form (x k (t) µ i,k ) 2 /σi,k 2 will be performed T M D times, 1 Log addition in our system was implemented in a more efficient way. which easily could indicate millions of floating-point multiplications. Similarly, the more expensive log addition may be performed thousands of times. Substituting in simple LUTs can provide substantial benefit. A crucial problem inherent to Gaussian likelihood evaluation is that there are two iterative operations suggested by D (1). One is e i (t) = d i,k (t), where d i,k (t) = (x k (t) k=1 µ i,k ) 2 /σ 2 i,k, and the other is b (t) associated with the log addition. The accumulations associated with these operations may produce high-entropy variables, making codebook design difficult. For example, in the above calculation, consider the distribution of the partial accumulation at different points in the summation calculation. Using a temporary value to store the result of the partial accumulation, we initially have tmp = d i,1 (t) + d i,2 (t). If we assume that the d i,k (t) values are identically distributed, then tmp at this point will have a dynamic range of twice that of d i,k (t). At the next step, tmp = tmp + d i,3 (t), tmp will have a dynamic range of three times that of d i,k (t), and so forth. Before moving on, there is a subtle but important distinction to make between the entropy and the dynamic range of a random variable. These two concepts are related in accumulation. If all input values to be summed are identically distributed, an accumulation will see many partial accumulative values at each portion of its dynamic range. The resulting distribution will have probability for values in the dynamic ranges of all partial accumulations, and so the larger dynamic range will imply high entropy. B. Computation Reordering Strategies There are two natural strategies for performing quantized accumulation: a linear accumulation and a binary tree. Each corresponds to a data-flow diagram and consequently to a precedence order for the operations. They are natural in that they closely parallel common data structures used for dealing with an array of values, and in fact represent the extremes of a large set of possibilities. Linear accumulation is a straightforward accumulative algorithm, where the next value of a variable equals the current value plus an additional value as depicted on the left in Figure 1. In the case of e i (t), the accumulator needs to be initialized to zero. e i (t) = e i (t) + d i,k (t) is then consecutively performed for k = 1..D. An alternative to linear accumulation is to use a binary tree as depicted on the right in Figure 1, where the original inputs are combined separately and the outputs are again combined separately. There are different ways of implementing these two schemes with LUTs. First, a separate table could be used for each circle, where each table would be customized to its particular distribution of input and output values. This would lead to small tables since each table would be customized for the typical dynamic range of its operands, but D 1 distinct tables would be needed. At the other extreme, a single table could be used for all circles but it must account for enough values to adequately
4 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH result result Fig. 1. Linear accumulation vs. tree-structure accumulation. Squares refer to operands; circles refer to arithmetic operators to be implemented by table lookup. Note that a separate LUT could be used for each circle, one large LUT could be used for all circles, or some subset of circles could share from a set of LUTs. IV. NORMALIZATION OF VITERBI SEARCH Viterbi search is another heavy load for an ASR engine. A key goal of this work is for custom arithmetic to be applicable to Viterbi search as well. A. Problem Formulation In decoding, the forward probability α (t) = P (O 1:t, q t = ) is calculated as ᾱ (t) = [ i (ᾱ i (t 1) + ā i )] + b (t) (2) represent the value range produced by the operation. Therefore, the table itself might be very large since the distributions of its inputs and output would have much higher entropy. Using a single table, however, may work well in cases such as b (t) = ( ), where the log addition operator does not dramatically change the value range between inputs and output at each iteration. Similarly, if an operation is iterated only a small number of times, a single table may also be sufficient. Between these two extremes, fewer than D 1 tables can account for all D 1 circles. There is a tradeoff between the number of tables and table size a smaller number of tables requires larger but shared codebooks. One solution in the tree case is to use a separate table for each tree level, leading to log D tables. The potential advantage here is that each tree level can expect to see input operands with a similar dynamic range and output operand distributions with lower entropy. As a result, the total table size may be minimized. This work compares three strategies in computing e i (t). First, we implemented the linear case using one shared operator (LUT). Second, we tried two different tree accumulation patterns, both with log D operators as mentioned above. The two tree strategies differ only at the top level. As shown on the left in Figure 2, the first case adds adacent elements of the vector {d i,k (t)} D k=1, but at the next tree level half the inputs consist of combined static features and the other half consist of combined deltas. The second case, depicted on the right in Figure 2, instead combines the d i,k (t) of each feature with its corresponding delta. This idea is based on the empirical observation that the dynamic range of d i,k (t) is similar between the static features after mean subtraction and variance normalization, and similar also between the deltas. This will cause the outputs of the top level to be more homogeneous, leading to better quantization and representation. When dealing with an incomplete tree (D is not a power of 2), some values are allowed to pass over levels and are added to lower levels of the tree, as shown on the right in Figure 1. MFCCs Single deltas c 0 c 1 c K-1 c K δ 0 δ 1 δ K-1 δ K Mixed MFCCs and S ingle delta s c 0 δ 0 c i-1 δ i-1 c i δ i c K δ K Fig. 2. Adding adacent elements vs. re-ordering elements to add MFCCs and corresponding deltas; only the first level of the accumulation is shown, with the array elements corresponding to the boxes of Fig. 1. or, using the Viterbi approximation to exact inference, φ (t) = [max( φ i (t 1) + ā i )] + b (t) (3) i with the final score approximated as log P (O 1:T ) max[ φ (T ) + ā N ]. Here we let states 1 and N denote the beginning and ending non-emitting states respectively. As can be seen in Equation (2) and Equation (3), neither ᾱ nor φ has a bounded dynamic range. Specifically, as T increases these log Viterbi scores will decrease, causing severe problems in codebook design. Since the utterance length in real applications is unknown at the system design stage, the ᾱ (or φ) values at decode time might not lie in the dynamic range of those values used for quantization at codebook design time. Essentially, the distribution over ᾱ has high entropy since the values decrease unboundedly with T. While we could assume some upper bound on T and quantize with ᾱ distributed accordingly, this would yield an exponentially larger and wasteful codebook with many values seldom used by short utterances. Therefore, we need a normalized version of the forward probability, where inference is still valid but the dynamic range is restricted regardless of utterance length. B. Within-word Normalization In this subsection we modify the notation by adding a subscript k to distinguish between values associated with different word models W k, k = 1..K. Also, Q k denotes the set of states in word W k. In the literature, α,k (t) = P (q t = O 1:t, W k ) has commonly served as a normalized forward probability to solve the underflow problem that occurs in the Baum-Welch algorithm using fixed-precision floating-point representation [21], [22]. This is equivalent to rescaling α,k (t) by P (O 1:t W k ), producing a quantity with a representable numerical range. The recursion then becomes α,k(t) = P (O 1:t 1 W k ) α P (O 1:t W k ) i,k(t 1)a i,k b,k (t) (4) i Q k = 1 α R k (t) i,k(t 1)a i,k b,k (t), (5) i Q k where R k (t) = P (O t O 1:t 1, W k ) is computed as R k (t) = [ α i,k(t 1)a i,k ]b,k (t). (6) Q k i Q k
5 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH However, computing α,k (T ) = P (q T = O 1:T, W k ) alone is insufficient to obtain the final likelihood score P (O 1:T W k ) needed in decoding. Obtaining this score requires log R k (t) to be stored during the forward pass and be summed up over t at the end, again giving an ever growing dynamic range. C. Cross-word Normalization The essential problem with within-word normalization is that the scaling factor is different for different word models at each frame. The final α scores, therefore, are not comparable to each other. One standard approach [21] to circumvent this problem is to use the same scaling factor at each frame for all word models. Formally, we introduce α,k (t) with a recursion α,k(t) = 1 S(t) [ α i,k(t 1)a i,k ]b,k (t). (7) i Q k where S(t) = k Q k [ i Q k α i,k i,k]b,k (t) max k, Qk [ i Q k α i,k i,k]b,k (t). (8) This scaling factor in α s recursion is independent of W k, and it naturally obtains the score for W k at the end of the corresponding forward pass: ˆk = argmax k,k(t )a N,k. (9) Q k α There are potential difficulties, however, with implementing this recursion. As can be seen in Equations (7) and (8), computing the scaling factor involves significant additional operations. When implemented with custom arithmetic, there is the additional problem that the total table size might still be large since extra LUTs are needed for the scaling operation. D. Time-invariant Normalization Under modest assumptions, we show that the dynamic range of φ is bounded by linear functions of time. Equation (3) suggests that max min φ (t) max φ (t) min φ i (t 1) max i i φi (t 1) min i i ā i + max b (t) ā i + min b (t). (10) Equation (10) can be written recursively for all frames and summed up on both sides, leading to max φ (t) t max i min φ (t) t min i ā i + ā i + t s=1 t s=1 max b (s) min b (s). (11) Assuming max b (t) is a mean ergodic process, namely t max b (s) = E[max b (t)], and similarly for the min 1 t s=1 case, we have r l t φ (t) r h t (12) where r h = max i ā i + E[max b (t)] and r l = min ā i + i E[min b (t)]. Motivated by Equation (12), we propose a normalized forward probability η (t) = φ (t)e rt, where r is a positive constant. The final Viterbi score consequently becomes max[ η (T ) + ā N ] log P (O 1:T ) + rt (13) First, Equation (13) is a valid scoring criterion because the offset rt stays the same for all word candidates and hence has no impact on the final decision. This allows us to choose the r that best normalizes the forward probability. Second, dynamic programming still applies to the inference: η (t) = max[ η i (t 1) + ā i ] + b (t) + r. (14) i As shown in Section VII, this normalization does not require extra table lookup operations. Finally, the dynamic range of the normalized log forward probability η is controlled by r, since by Equation (12) (r l + r)t η (t) (r h + r)t. (15) To choose r, we compute the scores of all utterances from the training set evaluated on their own generative word models, and let r = E [log P (O 1:T correct model)/t ], in an attempt to normalize to zero the correct model s log likelihood score with zero word error. It still might be true that when evaluating utterances on the test set with respect to a wrong word model, or if the right model happens to currently be in error, the score decreases as T increases. When this happens, however, it will be for those words with lower partial likelihoods, and are (hopefully) in error. The scheme may act as pruning away unpromising partial hypotheses by encoding their likelihoods with a very few number of bits. V. DISCRIMINATIVELY INSPIRED DISTORTION MEASURE Lacking an analytically well-defined distortion measure to maximize recognition rate, conventional discrete-density HMM based ASR systems often use Euclidean or Mahalanobis distance for VQ [21]. Here, we present a new metric customized to minimize the degradation in recognition accuracy. As will be shown in Section VIII, the forward probability requires the highest bit-width among all system variables. We are therefore particularly interested in further compressing this variable. Forward probabilities are in fact ust likelihoods. The correct answer will typically have a high likelihood, whereas very wrong answers will typically have low likelihoods and are likely to be pruned away. A standard data-driven quantization scheme, however, tends to allocate more bits to a value range based only on its probability mass. Since low likelihoods are more probable (there is only one correct answer and many wrong ones), more bits will be allocated to these low scores at quantization time, thereby giving them excessively high resolution. Therefore, we propose a discriminatively inspired distortion measure to penalize low-valued forward probabilities. We
6 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH define the distortion between a sample η (t) = x and its quantized value Q(x) as D(x, Q(x)) = (x Q(x))2, (16) f(x) where f(x) is strictly positive. In choosing f(x), it is desired that as x increases, the distance between x and Q(x) will increase, which will cause more bits to be allocated for higher likelihood scores. f(x) = s x is such a function, where s > max x controls the degree of discrimination with smaller s implying higher discrimination. In this work, s was determined empirically from training data. VI. OPTIMIZATION OF BIT-WIDTH ALLOCATION So far, we have discussed table construction, but have not addressed how to determine the size of each table. The goal is to come up with a system-wide optimization algorithm to allocate resources among all variables. We aim to find the bitwidth allocation scheme which minimizes the cost of resources while maintaining baseline recognition performance. The algorithms will be presented for a system with L variables {V i } L i=1. We now define the following: fp The bit-width of an unquantized floating-point value. Typically, fp = 32; bw i the bit-width of V i. bw i can take any integer value below fp. When bw i = fp, V i is unquantized; bw = (bw1, bw 2,..., bw L ) a bit-width allocation scheme; bw i an increment of 1 bit for variable V i, where bw+ bw i = (bw 1,..., bw i + 1,..., bw L ); wer( bw) the word error rate (WER) evaluated at bw; cost( bw) total cost of resources evaluated at bw. Note that the cost function can be arbitrarily defined depending on the specific goals of the allocation. In this paper, we use the total storage of the tables as the cost. Additionally, we define the gradient δ as the ratio of the decrease in WER to the increase in cost evaluated in a certain axis direction, for example, δ i ( bw) = wer( bw) wer( bw + bw i + bw ) cost( bw + bw i + bw ) cost( bw) (17) reflects the rate of improvement along the oint direction of bw i and bw. For a single-dimensional increment, we set = 0: δ i ( bw) = δ i0. We define a baseline WER BWER wer( bw) bw=(fp,fp,...,fp) + ɛ, with ɛ a tolerance for increased error due to quantization. Our goal can be interpreted as bw = bw:wer( argmin bw) BWER = cost( bw) (18) This search space is highly discrete and, due to the effects of quantization noise, only approximately smooth. An exhaustive search for bw, evaluating wer( bw) and cost( bw) at every possible bw, is clearly exponential in L. Even constraining the bitwidth of each variable to a restricted range of possible values gives a very large search space. In the following subsections, we present two heuristics that work well experimentally. The basic idea is that we start with a low-cost bw with low enough a WER that gradients are not meaningless (they provide no information if bit-widths are too low) and greedily increase the bit-widths of one or a small group of variables until we find an acceptable solution. This is similar to the method used in [23] to optimize floating-point bit-widths. A. Single-Variable Quantization Finding a reasonable starting point is an important part of these algorithms. In general, it is expected that the noise introduced into the system by quantizing an additional variable will produce a result that is not better than without the extra variable quantized. For that reason, we take the starting point to be the minimum number of bits needed to quantize a single variable to produce baseline WER results. We call that result m i, the minimum bit-width of variable V i. We determine an upper bound M i by inspection. Specific methods for quantizing individual variables have been introduced in the previous sections. Once we determine the boundaries for each single variable, we have constrained our search to the hypercube bounded by m i bw i M i, i = 1..L. We then start each of the following algorithms at bwinit = (bw 1 = m 1, bw 2 = m 2,..., bw L = m L ). In all cases, it is assumed that wer( bw init ) > BWER since the algorithms are designed to stop when they find a bw with a WER as low as the target rate. B. Single-Dimensional Increment This algorithm allows only single-dimensional increments. It uses the gradient δ i ( bw) as a measure of improvement. The algorithm is described as follows, 1. Evaluate the gradients δ i ( bw), i = 1..L, for the current bw according to Equation (17), where L tests are needed to obtain the WERs. If δ i ( bw) < 0 i, return bw = bw; 2. Choose the direction k = argmax δ i ( bw), and set i:bw i+1 M k bw = bw + bw k ; 3. If wer( bw) BWER, return bw = bw; otherwise repeat steps 1 and 2. For speech recognition, online evaluation for a test takes a significant amount of time. As this takes place during the design stage, this is not a problem. Note that there might exist the case that no improvement exists along each of the L directions, but that one does exist with oint increments along multiple dimensions. With this algorithm, the search can easily become stuck in a local optimum. C. Multi-Dimensional Increment To avoid local optimum, the bit-widths of multiple variables could be increased in parallel. Considering the computational complexity, we only allow ( ) one- or two-dimensional increments, leading to L + possible candidates. We could L 2 extend this to include triplet increments, but it would take an
7 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH intolerably long time to finish. Only steps 1 and 2 differ from the above algorithm, becoming: 1. Evaluate the gradients δ i ( bw) and δ i ( bw), i = 1..L, ( = 1..L on current bw L where L + tests are 2 needed to obtain the WERs. Return bw = bw if all these gradients are negative; 2. Choose the direction k or a pair of directions {k, l} where δ k ( bw) or δ kl ( bw) is the maximum among all the single-dimensional and pair-wise increments. Increase the bit-width of V k or those of {V k, V l } by one if no one exceeds its upper bound. This algorithm is superior to the first one in the sense that it explores many more candidate points in the search space. It considers only one additional direction and may still fall into a local optimum, but is less likely to do so than in the previous case. The downside is that this algorithm takes substantially longer to complete. VII. SYSTEM ORGANIZATION A. Baseline System Configuration The database used for system evaluation is NYNEX Phone- Book [24], a phonetically-rich speech database designed for isolated-word recognition tasks. It consists of isolated-word utterances recorded via telephone channels with an 8,000 Hz sampling rate. Each sample is encoded into 8 bits according to µ-law. We set aside utterances for training, 6598 for development and 7191 for evaluation. 2 The development set is comprised of 8 different subsets, each with a different 75- word vocabulary. For a comprehensive testing, the evaluation set is divided in four ways: a) 8 subsets each with a 75-word vocabulary; b) 4 subsets each with a 150-word vocabulary; c) 2 subsets each with a 300-word vocabulary and d) one set with a 600-word vocabulary. Besides the experiments in clean conditions, artificial white Gaussian noise is added to the evaluation set generating utterances with SNRs of 30dB, 20dB and 10dB. The acoustic features are the standard MFCCs plus the log energy and their deltas, yielding 26-dimensional vectors. Each vector has mean subtraction and variance normalization applied to both static and dynamic features in an attempt to make the system robust to noise. The acoustic models are a set of phone-based CHMMs. This enables a customizable vocabulary, a desirable goal for an embedded device. Our system has 42 phone models, each composed of 4 emitting states except for the silence model which has 1 emitting state. The state probability distribution is a mixture of 12 diagonal Gaussians. The front-end and the back-end are two main components of the recognizer, where the back-end has been discussed in 2 Specifically, the training set consisted of subsets aa, ab, ah, ai, am, an, aq, at, au, ax, ba, bb, bh, bi, bm, bn, bq, bt, bu, bx, ca, cb, ch, ci, cm, cn, cq, ct, cu, cx, da, db, dh, di, dm, dn, dq, dt, du, dx, ea and eb. The development set included subsets ad, ar, bd, br, cd, cr, dd and dr. Finally, the evaluation set was comprised of subsets ao, ay, bo, by, co, cc, do, dy. ) previous sections. Our front-end consists of active speech detection and feature extraction. It expands each µ-law encoded sample into linear 16-bit PCM, and then creates a frame every 10ms (80 samples), each with a length of 25ms (200 samples). The speech detector used is one of the simplest; it detects speech when the energy level of the speech signal rises above a certain threshold. This design uses minimal extra resources while still accurately detecting speech when noise conditions are stationary. Feature extraction is triggered immediately when active speech is detected. It follows a standard procedure described in [25], We then add the first order dynamic features followed by mean subtraction and variance normalization. The feature vectors obtained are fed into the back-end, where the pattern matching takes place. Since we propose applying our custom arithmetic to the back-end but not to the front-end, an interface is necessary. At the interface, the floating-point value of a feature element is converted into its integer index in the associated codebook by a binary search. This is in fact the only place in the system where a software codebook search is needed, and is the biggest overhead introduced by custom arithmetic. This overhead is taken into account in our CPU time simulations. B. Codebook and Table Definition Based on the analysis in the previous sections, we defined 13 variables to be quantized which are listed in Table I. The variable x is the output feature element of the frontend, m, v, c, w and a are the acoustic model parameters precomputed, and s, d, e, p, q, b and η are other intermediate variables in the back-end system. TABLE I SYSTEM VARIABLES AND THEIR CORRESPONDING EXPRESSIONS symbol in Equation (1) symbol in Equation (1) x x k (t) s (x k (t) µ i,k ) 2 m µ i,k d d i,k (t) v σi,k 2 e e i (t) c c i p c i 1 2 e i(t) w w i q b w i c i 1 2 e i(t) b (t) a ā i, η η (t); η (t) + ā i There are 8 functions and hence 8 potential LUTs associated with these variables: F 1 ( ) : s = (x m) 2 F 5 ( ) : q = w + p F 2 ( ) : d = s/v F 6 ( ) : b = b q F 3 ( ) : e = e + d F 7 ( ) : η = η + a F 4 ( ) : p = c e/2 F 8 ( ) : η = η + b + r F 1 ( ) and F 2 ( ) involve floating-point multiplication and division respectively, and these operations would be performed millions of times for an ordinary isolated word recognition task. F 6 ( ) would be executed thousands of times with even more expensive log computation. We expect the simple hardware-based lookup operations will dramatically save cycles as well as power on these functions. Note that the comparison operations implicit in Equation (14) are easily implemented, since they can be achieved using low bit-width integer comparisons operations, so no extra tables are required.
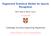
8 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH VIII. EXPERIMENTS AND RESULTS Before reporting our experiments and results, we would like to clarify two points. First, the recognition program used in all our simulations does not utilize purely algorithmic methodology such as Gaussian selection, beam pruning or algorithmic-level vector quantization techniques; incorporating these procedures may indeed affect (and likely improve) our speedup factors. But in this work we concentrate solely on architectural customization and enhancement. Second, we must acknowledge that an alternative architectural strategy is to utilize a hybrid system consisting of a mix between floating- and fixed-point arithmetic operations. Our contention, however, is that when the greatest possible power savings must be obtained, custom designed arithmetic operations (as we employ in this work) will yield the best tradeoff between ASR accuracy and power consumption reduction. This section first reports the results of system development. The LBG [26] algorithm was used in all single variable quantization experiments. These experiments were performed on the 8 development subsets mentioned in the previous section. The WERs reported were an average over these subsets. We also tried 150-, 300- and 600-word vocabulary cases on the development set and observed similar trends. Based on the single-variable quantization experiments, we applied our search algorithms for resource allocation, where the WERs were again evaluated on the development set. Next we evaluated the recognition accuracy of the best allocation scheme in both clean and noisy conditions on our evaluation set. Finally, we estimated its memory usage and simulated its speed performance. Figure 3 summarizes the results in terms of WER vs. bit-width of each codebook. Tree-structure 1 denotes the method where adacent pairs in the vector are added at all levels to form the next-level codebook, whereas in tree-structure 2, MFCCs are added to their corresponding deltas at the first level. It can be seen that in order to achieve the baseline recognition rate, linear accumulation needs 7 bits and tree-structure schemes need 6 bits for each codebook. The total table size, however, is a different story since the tree-structure schemes require 5 separate LUTs. To compute the total table size, we only consider the two functions in which e is involved. 3 Assuming n d = 5, n c = 5 and n p = 6 according to Table II, 6 kbytes of LUTs are needed to realize the operations involving e using linear accumulation, whereas the required space goes up to almost 10 kbytes for the tree-structure schemes to achieve the same goal. It is worth noting that the feature dimension is fixed at 26 and is relatively low, and the addition operation only changes the dynamic range of the output at a linear scale. This yields only a mild increase in the entropy of e, thereby making the linear accumulation an effective approach. Nevertheless, the tree structure may show advantages for other types of operations such as a long sequence of multiplications. % WER linear quantization tree-structure I tree-structure II A. System development In the single-variable quantization experiments, we quantize each variable individually, leaving all other variables at full precision. The baseline WER of the development set is 2.07%. Table II shows the minimum bit-width to which a variable can be quantized without any increase in WER on the development set. Here we report all system variables except for the accumulated Mahalanobis distance e and the forward probability η which will be discussed separately later. Note that we let q and b share the same codebook because their value ranges have much overlap. TABLE II MINIMUM BIT-WIDTH TO WHICH EACH VARIABLE CAN BE INDIVIDUALLY QUANTIZED WITHOUT INCREASE IN WER variable m v w a x s d c p b (q) min bit Section III presented two approaches to quantize variable e. In our case, the operation e = e + d is repeated 26 times to get the final value of e. Using linear accumulation, it involves only two variables e and d and only one table e = e + d. Alternatively, we can use tree-structure accumulation with multiple variables and log 26 = 5 different tables each of relatively small size. For simplicity, the variables in each level of the tree structure are quantized with the same bit-width. Fig BIT-WIDTH OF EACH CODEBOOK Single-variable quantization for accumulative variable e Section IV proposed a time-invariant normalization to the forward probability to reduce its entropy without affecting recognition decision. To show the advantage of the normalization on quantization, we extracted forward probability samples with and without normalization on the same subset of training data, and generated codebooks based on the Euclidean distance distortion measure for each case. We additionally applied quantization of the normalized forward probabilities using our discriminatively inspired distortion measure. As shown in Figure 4, the normalized Viterbi search obviously outperforms the unnormalized case by saving 1 bit while keeping the baseline recognition rate (thus nearly halving the total table size). In fact, we believe the benefits of normalization would be more pronounced on a task with longer utterances, such as connected-digit or continuous speech recognition. In addition, 3 With e, d, c and p quantized to n e, n d, n c and n p bits respectively, all related tables total n e2 n d+n e + n p2 nc+ne bits.
9 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH the discriminative distortion measure works slightly better than the normal one. % WER Fig unnormalized normailized discriminative normalized BIT-WIDTH OF FORWARD PROBABILITY Single-variable quantization for forward probability We therefore chose linear accumulation in quantizing e and normalized Viterbi search using our distortion measure in quantizing the forward probability. Together with other variable quantization results, codebooks with different resolution were generated for all system variables, to which an optimization search was applied to find the best bit-width allocation scheme. The results of running both allocation algorithms appear in Table III. Recall that the baseline WER of the development set is 2.07%. TABLE III COMPARISON OF TWO BIT-WIDTH OPTIMIZATION ALGORITHMS WER Table (kb) # Tests 1-D 3.09% D 2.53% The 1-D (single-dimensional increment) algorithm tested a total of 52 configurations before it reached a local optimum. It managed to find a fairly small ROM size but the WER was not very satisfactory. The 2-D (two-dimensional increment) algorithm found a much better WER than 1-D, even if its total table size was larger. The final bit-width allocation scheme of the last algorithm is shown in Table IV, where the first row indicates the variable and the second row shows the corresponding bit-width. As TABLE IV THE OPTIMAL BIT-WIDTH ALLOCATION SCHEME V m v w x s d e c p b a η BW shown in the table, all the variables can be compressed to less than 10 bits, which substantially reduces the memory band-width. This scheme takes only 59 kbytes of memory for table storage, an amount affordable for most modern chips. It is also interesting to see that the responsibility w, transition probability a, mean scalar m, variance scalar v and constant c can each be quantized to less than 8 bits, leading to an 80% reduction of model parameter storage as opposed to 32- bit floating-point representation. In addition, the feature scalar x and the state likelihood b can be quantized to 7 and 5 bits respectively, resulting in an additional saving in online memory usage. For some computer architectures, 8- or 16-bit is the bitwidth that can be most effectively used. For example, the design of a lookup instruction would be easier if its operands are uniformly 8 bits (those smaller can be filled with zeros at the beginning). For this reason, we additionally conducted an optimization experiment with the constraint that all variables were quantized to no more than 8 bits. Note that to minimize the table size, variables with fewer than 8 bits were not expanded to 8 bits. The resulting bit-width allocation scheme uses 68.5 kb to achieve a WER of 3.22%. We would also like to mention that for custom chips and reconfigurable logic chips, 8- or 16-bit is not always necessary since buses and registers can have smaller bit-widths. B. Final system evaluation We tested the recognition performance of the scheme in Table IV on our evaluation set for all 75-, 150-, 300- and 600-word vocabulary cases as defined in Section VII. The experiments were done in both clean and noisy conditions. We did not apply any noise-robustness techniques except for mean subtraction and variance normalization to the MFCC and delta features. As shown in Table V, for recognition in relatively clean conditions (clean and SNR=30dB cases), the system using custom arithmetic units has slight degradation in recognition rate compared to the baseline system using a floating point unit. The maximum degradation, an absolute 1.7% increase in WER, happens in the 600-word and 30dB case. This is graceful considering the potential speedup that custom arithmetic brings, which is discussed in the next subsection. It is interesting to see that in more noisy conditions (SNR=20dB and SNR=10dB cases), custom arithmetic does not deteriorate the recognition performance any more, but on the contrary, slightly enhances it. One explanation is that the quantization noise introduced may, to some extent, compensate for the more continuous additive noise in the speech; so quantization then acts as a regularizer the decision boundaries are probably slightly less susceptible to minor perturbations when variables are so coarsely quantized in the custom arithmetic case. TABLE V %WERS ON EVAL SET USING THE SCHEME IN TABLE IV vocab. 75-word 150-word 300-word 600-word fp. custom fp. custom fp. custom fp. custom clean db db db C. CPU Time Simulation We utilized SimpleScalar [27], an architecture-level execution-driven simulator, for CPU time simulation. All
10 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH tables were pre-calculated by SimpleScalar at runtime. We extended the instruction set and modified the assembler to support our new lookup instructions. The simulation was targeted for a variety of architectures. Without a detailed manufacturer-supplied simulator, an indepth analysis of any specific architecture is impossible, but by using a range of simulated architectures we can still discover meaningful trends in performance. The first is the SimpleScalar default configuration, roughly akin to a third generation Alpha, an out-of-order superscalar processor. The second represents a more modern desktop machine; cache sizes and latencies have been updated from the defaults, several years old, to reflect more current values. Our third configuration attempts to represent a typical high-end DSP chip. Since most DSP chips are Very Long Instruction Word (VLIW) architectures, a feature not replicable with SimpleScalar, we chose instead to force in-order execution with high parallelism as a very rough approximation of VLIW. Finally, we simulated a very simple processor with a single pipeline and no cache. This last case is similar to what could be expected of a lowpower processor designed to run on an extremely portable device, the expected target platform for custom arithmetic. In each case, we allowed multiple tables to be accessed in parallel, although a specific table could be used by only one instruction at a time. SPEEDUP Fig CYCLES PER LOOKUP SimpleScalar Default Modern Desktop High-end DSP Simple Processor Speedup (in cycles) versus cycles per lookup We simulated each of the target machines for a range of table lookup speeds. This is independent of WER since, assuming the table is not too large, the precision of the output of a lookup has little to do with the speed of the lookup. Figure 5 shows the speedup obtained versus the number of cycles required for each lookup. The speedup ranges from ust under 2.5 to nearly 4 when lookups take only 1 cycle, and falls off as they become more expensive. If the ROM tables are small enough to fit on the processor chip, which is the case using the 59kB results from Table IV, a 1-cycle lookup is quite realistic for a state-of-the-art system. To be more explicit, we assume that the ROMs will be on-die and implemented using either reconfigurable logic or a custom die for embedded applications. Although this may seem to require a large chip area, there is substantial savings in the on-chip cache size resulting from the reduction in the bit-widths of all variables. As shown in the figure, using a single pipeline and no cache (simple processor), meaning essentially a cache miss every time, does reduce the speedup but still provides a significant gain in speed. Much benefit actually comes from replacing sequences of instructions with a single lookup, as the dynamic instruction count falls nearly as much as execution time. Note that because we did not try to implement a low-power frontend, a feature that would be necessary for a final realization of this system, we used pre-calculated MFCCs in floating-point values and included the time for MFCC quantization when calculating speedups. IX. SUMMARY AND CONCLUSION This paper presented a methodology for the design of highspeed, low-resource systems using custom arithmetic units. We focused our attention on the scalar quantization of system variables with high entropy, involving reordering and rescaling of the decoding algorithms and a discriminatively inspired distortion measure. We also demonstrated several resource allocation search heuristics suitable for finding acceptable points in an otherwise intractable search space. Our findings were then applied to a CHMM based ASR system, where a fully-functioning ASR back-end was achieved by LUTs without floating-point arithmetic units. The 59kB of tables is small enough that it can be added to any chip with an access time of 1 cycle. When implementing this design on a modern processor, we show that the expected speedup is at least 3, and possibly larger. Furthermore, the memory required for parameter storage and online computation can be greatly reduced. In addition, we are looking forward to hardware support for our custom arithmetic; the amount of savings in cycles and power also depends on the physical realization of the LUTs and the ISA designed to support lookup operations. ACKNOWLEDGMENTS We would like to thank Carl Ebeling for useful advice. REFERENCES [1] S. Takahashi, K. Aikawa, and S. Sagayama, Discrete mixture HMM, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, 1997, vol. 2, pp [2] V. Digalakis, S. Tsakalidis, C. Harizakis, and L. Neumeyer, Efficient speech recognition using subvector quantization and discrete-mixture HMMs, Computer Speech and Language, vol. 14, pp , [3] E. Bocchieri, Vector quantization for the efficient computation of continuous density likelihoods, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, 1993, vol. 2, pp [4] M. J. F. Gales, K. M. Knill, and S. J. Young, State based Gaussian selection in large vocabulary continuous speech recognition using HMMs, IEEE Trans. on Speech and Audio Processing, vol. 7, [5] M. Ravishankar, R. Bisiani, and E. Thayer, Sub-vector clustering to improve memory and speed performance of acoustic likelihood computation, in Proc. Eurospeech 97, 1997, pp [6] M. Vasilache, Speech recognition using hmms with quantized parameters, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, [7] E. Bocchieri and B. K. Mak, Subspace distribution clustering hidden Markov model, IEEE Trans. on Speech and Audio Processing, vol. 9, no. 3, pp , [8] K. Filali, X. Li, and J. Bilmes, Data-driven vector clustering for low-memory footprint asr, in Proc. Int. Conf. on Spoken Language Processing, 2002.
11 IEEE TRANSACTIONS ON SPEECH AND AUDIO PROCESSING, VOL. XX, NO. Y, MONTH [9] K. Filali, X. Li, and J. Bilmes, Algorithms for data-driven asr parameter quantization, (accepted) Computer, Speech and Language. [10] C. Iordache and P. T. P. Tang, An overview of floating-point support and math library on the intel xscale architecture, in 16th IEEE Symposium on Computer Arithmetic, June [11] Y. Gong and U. H. Kao, Implementing a high accuracy speakerindependent continuous speech recognizer on a fixed DSP, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, 2000, pp [12] E. Cornu, N. Destrez, A. Dufaux, H. Sheikhzadeh, and R. Brennan, An ultra low power, ultra miniature voice command system based on hidden markov models, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, 2002, vol. 4, pp [13] I. Varga and et. al., ASR in mobile phones An industrial approach, IEEE Trans. on Speech and Audio Processing, vol. 10, no. 8, pp , [14] B. Mathew, A. Davis, and Z. Fang, A low-power accelerator for the SPHINX 3 speech recognition system, in Proc. Intl. Conf. on Compilers, Architectures and Synthesis for Embedded Systems, [15] D. Citron, D. Feitelson, and L. Rudolph, Accelerating multi-media processing by implementing memoing in multiplication and division units, in Proc. Intl. Conf. on Architectural Support for Programming Languages and Operating Systems, 1998, pp [16] X. Li, J. Malkin, and J. Bilmes, Codebook design for ASR systems using custom arithmetic units, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, May [17] J. Malkin, X. Li, and J. Bilmes, Custom arithmetic for high-speed, low-resource ASR systems, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, May [18] B. Delaney, N. Jayant, M. Hans, T. Simunic, and A. Acquaviva, A lowpower, fixed-point, front-end feature extraction for a distributed speech recognition system, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, 2002, vol. 1, pp [19] S. J. Melnikoff, P. B. James-Roxby, S. F. Quigley, and M. J. Russel, Reconfigurable computing for speech recognition: Preliminary findings, in Proc. Intl. Conf. on Field Programmable Logic and Applications, 2000, pp [20] S. Hauck, T. W. Fry, M. M. Hosler, and J. P. Kao, The chimaera reconfigurable functional unit, IEEE Trans. on VLSI Systems, vol. 12, no. 2, pp , February [21] K-F. Lee, Automatic speech recognition: the development of the SPHINX system, Kluwer Academic Publishers, [22] J. R. Deller, J. H. Hansen, and J. G. Proakis, Discrete-time processing of Speech Signals, Wiley, [23] F. Fang, T. Chen, and R. A. Rutenbar, Floating-point bit-width optimization for low-power signal processing applications, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, 2002, pp [24] J. F. Pitrelli, C. Fong, and H. C. Leung, PhoneBook: A phoneticallyrich isolated-word telephone-speech database, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, [25] S. Young, G. Evermann, D. Kershaw, G. Moore, J. Odell, D. Ollason, V. Valtchev, and P. Woodland, The HTK Book (for HTK Version 3.1), Microsoft Corporation and Cambridge University Engineering Dept, [26] Y. Linde, A. Buzo, and R. M. Gray, An algorithm for vector quantizer, IEEE Trans. on Communication, vol. 28, pp , [27] D. Burger, T. M. Austin, and S. Bennett, Evaluating future microprocessors: The simplescalar tool set, Tech. Rep. CS-TR , Dept. of Computer Science, Univ. of Wisconsin-Madison, [28] P. Beyerlein and M. Ullrich, Hamming distance approximation for a fast log-likelihood computation for mixture densities, in Proc. Eur. Conf. Speech Communication Technology, 1995, vol. 2, pp [29] J. R. Bellegarda and D. Nahamoo, Tied mixture continuous parameter modeling for speech recognition, IEEE Trans. on Acoustics, Speech and Signal Processing, vol. 38, pp , [30] J. A. Bilmes, Buried Markov models for speech recognition, in Proc. Int. Conf. on Acousitics, Speech and Signal Processing, research fellowship. Xiao Li received the B.S.E.E degree from Tsinghua University, Beiing, China, in 2001 and the M.S.E.E. degree from the University of Washington, Seattle, in She is currently pursuing the Ph.D. degree in electrical engineering at the University of Washington, working on learning and adaptation in voice driven human-computer interaction. Her research interests include statistical learning, acoustic and speech processing and low-resource speech recognition for embedded systems. She is a 2005 recipient of Microsoft Jon Malkin received the B.S. degree in electrical engineering and computer science from Yale Universitty and the M.S. degree in electrical engineering from the University of Washington in 2002 and 2005, respectively. He is continuing at the University of Washington in pursuing the Ph.D. degree, focusing on vocal parameters and human factors for voice-based human-computer interaction. His research interests include pattern recognition, low-resource computation for realtime systems, speech and audio processing and recognition and human-computer interaction. Jeff A. Bilmes is an Assistant Professor (Associate, September 05) in the Department of Electrical Engineering at the University of Washington, Seattle (adunct in Linguistics and also in Computer Science and Engineering). He cofounded the Signal, Speech, and Language Interpretation Laboratory at the University. He received a master s degree from MIT, and a Ph.D. in Computer Science at the University of California, Berkeley. Jeff has done much research on both structure learning of and fast probabilistic inference in dynamic Graphical models. His main research lies in statistical graphical models, speech, language and time series, human-computer interaction, machine learning, and high-performance computing. He was a general co-chair for IEEE Automatic Speech Recognition and Understanding 2003, is a member of IEEE, ACM, and ACL, is a 2001 CRA Digital-Government Research Fellow, and is a 2001 recipient of the NSF CAREER award.
A High-speed, Low-Resource ASR Back-end Based on Custom Arithmetic
 A High-speed, Low-Resource ASR Back-end Based on Custom Arithmetic Xiao Li, Jonathan Malkin, Jeff Bilmes {lixiao,sm,bilmes}@ee.washington.edu Dept of EE, University of Washington Seattle WA, 98195-2500
A High-speed, Low-Resource ASR Back-end Based on Custom Arithmetic Xiao Li, Jonathan Malkin, Jeff Bilmes {lixiao,sm,bilmes}@ee.washington.edu Dept of EE, University of Washington Seattle WA, 98195-2500
FEATURE PRUNING IN LIKELIHOOD EVALUATION OF HMM-BASED SPEECH RECOGNITION. Xiao Li and Jeff Bilmes
 FEATURE PRUNING IN LIKELIHOOD EVALUATION OF HMM-BASED SPEECH RECOGNITION Xiao Li and Jeff Bilmes Department of Electrical Engineering University. of Washington, Seattle {lixiao, bilmes}@ee.washington.edu
FEATURE PRUNING IN LIKELIHOOD EVALUATION OF HMM-BASED SPEECH RECOGNITION Xiao Li and Jeff Bilmes Department of Electrical Engineering University. of Washington, Seattle {lixiao, bilmes}@ee.washington.edu
Experiments with a Gaussian Merging-Splitting Algorithm for HMM Training for Speech Recognition
 Experiments with a Gaussian Merging-Splitting Algorithm for HMM Training for Speech Recognition ABSTRACT It is well known that the expectation-maximization (EM) algorithm, commonly used to estimate hidden
Experiments with a Gaussian Merging-Splitting Algorithm for HMM Training for Speech Recognition ABSTRACT It is well known that the expectation-maximization (EM) algorithm, commonly used to estimate hidden
The Noisy Channel Model. CS 294-5: Statistical Natural Language Processing. Speech Recognition Architecture. Digitizing Speech
 CS 294-5: Statistical Natural Language Processing The Noisy Channel Model Speech Recognition II Lecture 21: 11/29/05 Search through space of all possible sentences. Pick the one that is most probable given
CS 294-5: Statistical Natural Language Processing The Noisy Channel Model Speech Recognition II Lecture 21: 11/29/05 Search through space of all possible sentences. Pick the one that is most probable given
The Noisy Channel Model. Statistical NLP Spring Mel Freq. Cepstral Coefficients. Frame Extraction ... Lecture 10: Acoustic Models
 Statistical NLP Spring 2009 The Noisy Channel Model Lecture 10: Acoustic Models Dan Klein UC Berkeley Search through space of all possible sentences. Pick the one that is most probable given the waveform.
Statistical NLP Spring 2009 The Noisy Channel Model Lecture 10: Acoustic Models Dan Klein UC Berkeley Search through space of all possible sentences. Pick the one that is most probable given the waveform.
Statistical NLP Spring The Noisy Channel Model
 Statistical NLP Spring 2009 Lecture 10: Acoustic Models Dan Klein UC Berkeley The Noisy Channel Model Search through space of all possible sentences. Pick the one that is most probable given the waveform.
Statistical NLP Spring 2009 Lecture 10: Acoustic Models Dan Klein UC Berkeley The Noisy Channel Model Search through space of all possible sentences. Pick the one that is most probable given the waveform.
The Noisy Channel Model. Statistical NLP Spring Mel Freq. Cepstral Coefficients. Frame Extraction ... Lecture 9: Acoustic Models
 Statistical NLP Spring 2010 The Noisy Channel Model Lecture 9: Acoustic Models Dan Klein UC Berkeley Acoustic model: HMMs over word positions with mixtures of Gaussians as emissions Language model: Distributions
Statistical NLP Spring 2010 The Noisy Channel Model Lecture 9: Acoustic Models Dan Klein UC Berkeley Acoustic model: HMMs over word positions with mixtures of Gaussians as emissions Language model: Distributions
Vector Quantization. Institut Mines-Telecom. Marco Cagnazzo, MN910 Advanced Compression
 Institut Mines-Telecom Vector Quantization Marco Cagnazzo, cagnazzo@telecom-paristech.fr MN910 Advanced Compression 2/66 19.01.18 Institut Mines-Telecom Vector Quantization Outline Gain-shape VQ 3/66 19.01.18
Institut Mines-Telecom Vector Quantization Marco Cagnazzo, cagnazzo@telecom-paristech.fr MN910 Advanced Compression 2/66 19.01.18 Institut Mines-Telecom Vector Quantization Outline Gain-shape VQ 3/66 19.01.18
Necessary Corrections in Intransitive Likelihood-Ratio Classifiers
 Necessary Corrections in Intransitive Likelihood-Ratio Classifiers Gang Ji and Jeff Bilmes SSLI-Lab, Department of Electrical Engineering University of Washington Seattle, WA 9895-500 {gang,bilmes}@ee.washington.edu
Necessary Corrections in Intransitive Likelihood-Ratio Classifiers Gang Ji and Jeff Bilmes SSLI-Lab, Department of Electrical Engineering University of Washington Seattle, WA 9895-500 {gang,bilmes}@ee.washington.edu
Scalar and Vector Quantization. National Chiao Tung University Chun-Jen Tsai 11/06/2014
 Scalar and Vector Quantization National Chiao Tung University Chun-Jen Tsai 11/06/014 Basic Concept of Quantization Quantization is the process of representing a large, possibly infinite, set of values
Scalar and Vector Quantization National Chiao Tung University Chun-Jen Tsai 11/06/014 Basic Concept of Quantization Quantization is the process of representing a large, possibly infinite, set of values
Lecture 12. Block Diagram
 Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Outline of Today s Lecture
 University of Washington Department of Electrical Engineering Computer Speech Processing EE516 Winter 2005 Jeff A. Bilmes Lecture 12 Slides Feb 23 rd, 2005 Outline of Today s
University of Washington Department of Electrical Engineering Computer Speech Processing EE516 Winter 2005 Jeff A. Bilmes Lecture 12 Slides Feb 23 rd, 2005 Outline of Today s
Maximum Likelihood and Maximum A Posteriori Adaptation for Distributed Speaker Recognition Systems
 Maximum Likelihood and Maximum A Posteriori Adaptation for Distributed Speaker Recognition Systems Chin-Hung Sit 1, Man-Wai Mak 1, and Sun-Yuan Kung 2 1 Center for Multimedia Signal Processing Dept. of
Maximum Likelihood and Maximum A Posteriori Adaptation for Distributed Speaker Recognition Systems Chin-Hung Sit 1, Man-Wai Mak 1, and Sun-Yuan Kung 2 1 Center for Multimedia Signal Processing Dept. of
Statistical NLP Spring Digitizing Speech
 Statistical NLP Spring 2008 Lecture 10: Acoustic Models Dan Klein UC Berkeley Digitizing Speech 1 Frame Extraction A frame (25 ms wide) extracted every 10 ms 25 ms 10ms... a 1 a 2 a 3 Figure from Simon
Statistical NLP Spring 2008 Lecture 10: Acoustic Models Dan Klein UC Berkeley Digitizing Speech 1 Frame Extraction A frame (25 ms wide) extracted every 10 ms 25 ms 10ms... a 1 a 2 a 3 Figure from Simon
Digitizing Speech. Statistical NLP Spring Frame Extraction. Gaussian Emissions. Vector Quantization. HMMs for Continuous Observations? ...
 Statistical NLP Spring 2008 Digitizing Speech Lecture 10: Acoustic Models Dan Klein UC Berkeley Frame Extraction A frame (25 ms wide extracted every 10 ms 25 ms 10ms... a 1 a 2 a 3 Figure from Simon Arnfield
Statistical NLP Spring 2008 Digitizing Speech Lecture 10: Acoustic Models Dan Klein UC Berkeley Frame Extraction A frame (25 ms wide extracted every 10 ms 25 ms 10ms... a 1 a 2 a 3 Figure from Simon Arnfield
Speech and Language Processing. Chapter 9 of SLP Automatic Speech Recognition (II)
 Speech and Language Processing Chapter 9 of SLP Automatic Speech Recognition (II) Outline for ASR ASR Architecture The Noisy Channel Model Five easy pieces of an ASR system 1) Language Model 2) Lexicon/Pronunciation
Speech and Language Processing Chapter 9 of SLP Automatic Speech Recognition (II) Outline for ASR ASR Architecture The Noisy Channel Model Five easy pieces of an ASR system 1) Language Model 2) Lexicon/Pronunciation
Hidden Markov Modelling
 Hidden Markov Modelling Introduction Problem formulation Forward-Backward algorithm Viterbi search Baum-Welch parameter estimation Other considerations Multiple observation sequences Phone-based models
Hidden Markov Modelling Introduction Problem formulation Forward-Backward algorithm Viterbi search Baum-Welch parameter estimation Other considerations Multiple observation sequences Phone-based models
Fast speaker diarization based on binary keys. Xavier Anguera and Jean François Bonastre
 Fast speaker diarization based on binary keys Xavier Anguera and Jean François Bonastre Outline Introduction Speaker diarization Binary speaker modeling Binary speaker diarization system Experiments Conclusions
Fast speaker diarization based on binary keys Xavier Anguera and Jean François Bonastre Outline Introduction Speaker diarization Binary speaker modeling Binary speaker diarization system Experiments Conclusions
Augmented Statistical Models for Speech Recognition
 Augmented Statistical Models for Speech Recognition Mark Gales & Martin Layton 31 August 2005 Trajectory Models For Speech Processing Workshop Overview Dependency Modelling in Speech Recognition: latent
Augmented Statistical Models for Speech Recognition Mark Gales & Martin Layton 31 August 2005 Trajectory Models For Speech Processing Workshop Overview Dependency Modelling in Speech Recognition: latent
Noise Robust Isolated Words Recognition Problem Solving Based on Simultaneous Perturbation Stochastic Approximation Algorithm
 EngOpt 2008 - International Conference on Engineering Optimization Rio de Janeiro, Brazil, 0-05 June 2008. Noise Robust Isolated Words Recognition Problem Solving Based on Simultaneous Perturbation Stochastic
EngOpt 2008 - International Conference on Engineering Optimization Rio de Janeiro, Brazil, 0-05 June 2008. Noise Robust Isolated Words Recognition Problem Solving Based on Simultaneous Perturbation Stochastic
Jorge Silva and Shrikanth Narayanan, Senior Member, IEEE. 1 is the probability measure induced by the probability density function
 890 IEEE TRANSACTIONS ON AUDIO, SPEECH, AND LANGUAGE PROCESSING, VOL. 14, NO. 3, MAY 2006 Average Divergence Distance as a Statistical Discrimination Measure for Hidden Markov Models Jorge Silva and Shrikanth
890 IEEE TRANSACTIONS ON AUDIO, SPEECH, AND LANGUAGE PROCESSING, VOL. 14, NO. 3, MAY 2006 Average Divergence Distance as a Statistical Discrimination Measure for Hidden Markov Models Jorge Silva and Shrikanth
On the Influence of the Delta Coefficients in a HMM-based Speech Recognition System
 On the Influence of the Delta Coefficients in a HMM-based Speech Recognition System Fabrice Lefèvre, Claude Montacié and Marie-José Caraty Laboratoire d'informatique de Paris VI 4, place Jussieu 755 PARIS
On the Influence of the Delta Coefficients in a HMM-based Speech Recognition System Fabrice Lefèvre, Claude Montacié and Marie-José Caraty Laboratoire d'informatique de Paris VI 4, place Jussieu 755 PARIS
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi
 Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
10. Hidden Markov Models (HMM) for Speech Processing. (some slides taken from Glass and Zue course)
 10. Hidden Markov Models (HMM) for Speech Processing (some slides taken from Glass and Zue course) Definition of an HMM The HMM are powerful statistical methods to characterize the observed samples of
10. Hidden Markov Models (HMM) for Speech Processing (some slides taken from Glass and Zue course) Definition of an HMM The HMM are powerful statistical methods to characterize the observed samples of
HIDDEN MARKOV MODELS IN SPEECH RECOGNITION
 HIDDEN MARKOV MODELS IN SPEECH RECOGNITION Wayne Ward Carnegie Mellon University Pittsburgh, PA 1 Acknowledgements Much of this talk is derived from the paper "An Introduction to Hidden Markov Models",
HIDDEN MARKOV MODELS IN SPEECH RECOGNITION Wayne Ward Carnegie Mellon University Pittsburgh, PA 1 Acknowledgements Much of this talk is derived from the paper "An Introduction to Hidden Markov Models",
STA 414/2104: Machine Learning
 STA 414/2104: Machine Learning Russ Salakhutdinov Department of Computer Science! Department of Statistics! rsalakhu@cs.toronto.edu! http://www.cs.toronto.edu/~rsalakhu/ Lecture 9 Sequential Data So far
STA 414/2104: Machine Learning Russ Salakhutdinov Department of Computer Science! Department of Statistics! rsalakhu@cs.toronto.edu! http://www.cs.toronto.edu/~rsalakhu/ Lecture 9 Sequential Data So far
Analysis of methods for speech signals quantization
 INFOTEH-JAHORINA Vol. 14, March 2015. Analysis of methods for speech signals quantization Stefan Stojkov Mihajlo Pupin Institute, University of Belgrade Belgrade, Serbia e-mail: stefan.stojkov@pupin.rs
INFOTEH-JAHORINA Vol. 14, March 2015. Analysis of methods for speech signals quantization Stefan Stojkov Mihajlo Pupin Institute, University of Belgrade Belgrade, Serbia e-mail: stefan.stojkov@pupin.rs
CSCI Final Project Report A Parallel Implementation of Viterbi s Decoding Algorithm
 CSCI 1760 - Final Project Report A Parallel Implementation of Viterbi s Decoding Algorithm Shay Mozes Brown University shay@cs.brown.edu Abstract. This report describes parallel Java implementations of
CSCI 1760 - Final Project Report A Parallel Implementation of Viterbi s Decoding Algorithm Shay Mozes Brown University shay@cs.brown.edu Abstract. This report describes parallel Java implementations of
Proc. of NCC 2010, Chennai, India
 Proc. of NCC 2010, Chennai, India Trajectory and surface modeling of LSF for low rate speech coding M. Deepak and Preeti Rao Department of Electrical Engineering Indian Institute of Technology, Bombay
Proc. of NCC 2010, Chennai, India Trajectory and surface modeling of LSF for low rate speech coding M. Deepak and Preeti Rao Department of Electrical Engineering Indian Institute of Technology, Bombay
TinySR. Peter Schmidt-Nielsen. August 27, 2014
 TinySR Peter Schmidt-Nielsen August 27, 2014 Abstract TinySR is a light weight real-time small vocabulary speech recognizer written entirely in portable C. The library fits in a single file (plus header),
TinySR Peter Schmidt-Nielsen August 27, 2014 Abstract TinySR is a light weight real-time small vocabulary speech recognizer written entirely in portable C. The library fits in a single file (plus header),
Detection-Based Speech Recognition with Sparse Point Process Models
 Detection-Based Speech Recognition with Sparse Point Process Models Aren Jansen Partha Niyogi Human Language Technology Center of Excellence Departments of Computer Science and Statistics ICASSP 2010 Dallas,
Detection-Based Speech Recognition with Sparse Point Process Models Aren Jansen Partha Niyogi Human Language Technology Center of Excellence Departments of Computer Science and Statistics ICASSP 2010 Dallas,
C.M. Liu Perceptual Signal Processing Lab College of Computer Science National Chiao-Tung University
 Quantization C.M. Liu Perceptual Signal Processing Lab College of Computer Science National Chiao-Tung University http://www.csie.nctu.edu.tw/~cmliu/courses/compression/ Office: EC538 (03)5731877 cmliu@cs.nctu.edu.tw
Quantization C.M. Liu Perceptual Signal Processing Lab College of Computer Science National Chiao-Tung University http://www.csie.nctu.edu.tw/~cmliu/courses/compression/ Office: EC538 (03)5731877 cmliu@cs.nctu.edu.tw
STA 4273H: Statistical Machine Learning
 STA 4273H: Statistical Machine Learning Russ Salakhutdinov Department of Statistics! rsalakhu@utstat.toronto.edu! http://www.utstat.utoronto.ca/~rsalakhu/ Sidney Smith Hall, Room 6002 Lecture 11 Project
STA 4273H: Statistical Machine Learning Russ Salakhutdinov Department of Statistics! rsalakhu@utstat.toronto.edu! http://www.utstat.utoronto.ca/~rsalakhu/ Sidney Smith Hall, Room 6002 Lecture 11 Project
CS 136a Lecture 7 Speech Recognition Architecture: Training models with the Forward backward algorithm
 + September13, 2016 Professor Meteer CS 136a Lecture 7 Speech Recognition Architecture: Training models with the Forward backward algorithm Thanks to Dan Jurafsky for these slides + ASR components n Feature
+ September13, 2016 Professor Meteer CS 136a Lecture 7 Speech Recognition Architecture: Training models with the Forward backward algorithm Thanks to Dan Jurafsky for these slides + ASR components n Feature
On Compression Encrypted Data part 2. Prof. Ja-Ling Wu The Graduate Institute of Networking and Multimedia National Taiwan University
 On Compression Encrypted Data part 2 Prof. Ja-Ling Wu The Graduate Institute of Networking and Multimedia National Taiwan University 1 Brief Summary of Information-theoretic Prescription At a functional
On Compression Encrypted Data part 2 Prof. Ja-Ling Wu The Graduate Institute of Networking and Multimedia National Taiwan University 1 Brief Summary of Information-theoretic Prescription At a functional
ISOLATED WORD RECOGNITION FOR ENGLISH LANGUAGE USING LPC,VQ AND HMM
 ISOLATED WORD RECOGNITION FOR ENGLISH LANGUAGE USING LPC,VQ AND HMM Mayukh Bhaowal and Kunal Chawla (Students)Indian Institute of Information Technology, Allahabad, India Abstract: Key words: Speech recognition
ISOLATED WORD RECOGNITION FOR ENGLISH LANGUAGE USING LPC,VQ AND HMM Mayukh Bhaowal and Kunal Chawla (Students)Indian Institute of Information Technology, Allahabad, India Abstract: Key words: Speech recognition
NCU EE -- DSP VLSI Design. Tsung-Han Tsai 1
 NCU EE -- DSP VLSI Design. Tsung-Han Tsai 1 Multi-processor vs. Multi-computer architecture µp vs. DSP RISC vs. DSP RISC Reduced-instruction-set Register-to-register operation Higher throughput by using
NCU EE -- DSP VLSI Design. Tsung-Han Tsai 1 Multi-processor vs. Multi-computer architecture µp vs. DSP RISC vs. DSP RISC Reduced-instruction-set Register-to-register operation Higher throughput by using
Codes for Partially Stuck-at Memory Cells
 1 Codes for Partially Stuck-at Memory Cells Antonia Wachter-Zeh and Eitan Yaakobi Department of Computer Science Technion Israel Institute of Technology, Haifa, Israel Email: {antonia, yaakobi@cs.technion.ac.il
1 Codes for Partially Stuck-at Memory Cells Antonia Wachter-Zeh and Eitan Yaakobi Department of Computer Science Technion Israel Institute of Technology, Haifa, Israel Email: {antonia, yaakobi@cs.technion.ac.il
Vector Quantization Encoder Decoder Original Form image Minimize distortion Table Channel Image Vectors Look-up (X, X i ) X may be a block of l
 Vector Quantization Encoder Decoder Original Image Form image Vectors X Minimize distortion k k Table X^ k Channel d(x, X^ Look-up i ) X may be a block of l m image or X=( r, g, b ), or a block of DCT
Vector Quantization Encoder Decoder Original Image Form image Vectors X Minimize distortion k k Table X^ k Channel d(x, X^ Look-up i ) X may be a block of l m image or X=( r, g, b ), or a block of DCT
4. Quantization and Data Compression. ECE 302 Spring 2012 Purdue University, School of ECE Prof. Ilya Pollak
 4. Quantization and Data Compression ECE 32 Spring 22 Purdue University, School of ECE Prof. What is data compression? Reducing the file size without compromising the quality of the data stored in the
4. Quantization and Data Compression ECE 32 Spring 22 Purdue University, School of ECE Prof. What is data compression? Reducing the file size without compromising the quality of the data stored in the
On Optimal Coding of Hidden Markov Sources
 2014 Data Compression Conference On Optimal Coding of Hidden Markov Sources Mehdi Salehifar, Emrah Akyol, Kumar Viswanatha, and Kenneth Rose Department of Electrical and Computer Engineering University
2014 Data Compression Conference On Optimal Coding of Hidden Markov Sources Mehdi Salehifar, Emrah Akyol, Kumar Viswanatha, and Kenneth Rose Department of Electrical and Computer Engineering University
A matrix over a field F is a rectangular array of elements from F. The symbol
 Chapter MATRICES Matrix arithmetic A matrix over a field F is a rectangular array of elements from F The symbol M m n (F ) denotes the collection of all m n matrices over F Matrices will usually be denoted
Chapter MATRICES Matrix arithmetic A matrix over a field F is a rectangular array of elements from F The symbol M m n (F ) denotes the collection of all m n matrices over F Matrices will usually be denoted
THE TRANSLATION PLANES OF ORDER 49 AND THEIR AUTOMORPHISM GROUPS
 MATHEMATICS OF COMPUTATION Volume 67, Number 223, July 1998, Pages 1207 1224 S 0025-5718(98)00961-2 THE TRANSLATION PLANES OF ORDER 49 AND THEIR AUTOMORPHISM GROUPS C. CHARNES AND U. DEMPWOLFF Abstract.
MATHEMATICS OF COMPUTATION Volume 67, Number 223, July 1998, Pages 1207 1224 S 0025-5718(98)00961-2 THE TRANSLATION PLANES OF ORDER 49 AND THEIR AUTOMORPHISM GROUPS C. CHARNES AND U. DEMPWOLFF Abstract.
Information redundancy
 Information redundancy Information redundancy add information to date to tolerate faults error detecting codes error correcting codes data applications communication memory p. 2 - Design of Fault Tolerant
Information redundancy Information redundancy add information to date to tolerate faults error detecting codes error correcting codes data applications communication memory p. 2 - Design of Fault Tolerant
ON SCALABLE CODING OF HIDDEN MARKOV SOURCES. Mehdi Salehifar, Tejaswi Nanjundaswamy, and Kenneth Rose
 ON SCALABLE CODING OF HIDDEN MARKOV SOURCES Mehdi Salehifar, Tejaswi Nanjundaswamy, and Kenneth Rose Department of Electrical and Computer Engineering University of California, Santa Barbara, CA, 93106
ON SCALABLE CODING OF HIDDEN MARKOV SOURCES Mehdi Salehifar, Tejaswi Nanjundaswamy, and Kenneth Rose Department of Electrical and Computer Engineering University of California, Santa Barbara, CA, 93106
Upper Bound Kullback-Leibler Divergence for Hidden Markov Models with Application as Discrimination Measure for Speech Recognition
 Upper Bound Kullback-Leibler Divergence for Hidden Markov Models with Application as Discrimination Measure for Speech Recognition Jorge Silva and Shrikanth Narayanan Speech Analysis and Interpretation
Upper Bound Kullback-Leibler Divergence for Hidden Markov Models with Application as Discrimination Measure for Speech Recognition Jorge Silva and Shrikanth Narayanan Speech Analysis and Interpretation
Automatic Differentiation Equipped Variable Elimination for Sensitivity Analysis on Probabilistic Inference Queries
 Automatic Differentiation Equipped Variable Elimination for Sensitivity Analysis on Probabilistic Inference Queries Anonymous Author(s) Affiliation Address email Abstract 1 2 3 4 5 6 7 8 9 10 11 12 Probabilistic
Automatic Differentiation Equipped Variable Elimination for Sensitivity Analysis on Probabilistic Inference Queries Anonymous Author(s) Affiliation Address email Abstract 1 2 3 4 5 6 7 8 9 10 11 12 Probabilistic
EE368B Image and Video Compression
 EE368B Image and Video Compression Homework Set #2 due Friday, October 20, 2000, 9 a.m. Introduction The Lloyd-Max quantizer is a scalar quantizer which can be seen as a special case of a vector quantizer
EE368B Image and Video Compression Homework Set #2 due Friday, October 20, 2000, 9 a.m. Introduction The Lloyd-Max quantizer is a scalar quantizer which can be seen as a special case of a vector quantizer
on a per-coecient basis in large images is computationally expensive. Further, the algorithm in [CR95] needs to be rerun, every time a new rate of com
![on a per-coecient basis in large images is computationally expensive. Further, the algorithm in [CR95] needs to be rerun, every time a new rate of com on a per-coecient basis in large images is computationally expensive. Further, the algorithm in [CR95] needs to be rerun, every time a new rate of com](/thumbs/83/87515090.jpg) Extending RD-OPT with Global Thresholding for JPEG Optimization Viresh Ratnakar University of Wisconsin-Madison Computer Sciences Department Madison, WI 53706 Phone: (608) 262-6627 Email: ratnakar@cs.wisc.edu
Extending RD-OPT with Global Thresholding for JPEG Optimization Viresh Ratnakar University of Wisconsin-Madison Computer Sciences Department Madison, WI 53706 Phone: (608) 262-6627 Email: ratnakar@cs.wisc.edu
Multimedia Communications. Scalar Quantization
 Multimedia Communications Scalar Quantization Scalar Quantization In many lossy compression applications we want to represent source outputs using a small number of code words. Process of representing
Multimedia Communications Scalar Quantization Scalar Quantization In many lossy compression applications we want to represent source outputs using a small number of code words. Process of representing
A Reservoir Sampling Algorithm with Adaptive Estimation of Conditional Expectation
 A Reservoir Sampling Algorithm with Adaptive Estimation of Conditional Expectation Vu Malbasa and Slobodan Vucetic Abstract Resource-constrained data mining introduces many constraints when learning from
A Reservoir Sampling Algorithm with Adaptive Estimation of Conditional Expectation Vu Malbasa and Slobodan Vucetic Abstract Resource-constrained data mining introduces many constraints when learning from
HARMONIC VECTOR QUANTIZATION
 HARMONIC VECTOR QUANTIZATION Volodya Grancharov, Sigurdur Sverrisson, Erik Norvell, Tomas Toftgård, Jonas Svedberg, and Harald Pobloth SMN, Ericsson Research, Ericsson AB 64 8, Stockholm, Sweden ABSTRACT
HARMONIC VECTOR QUANTIZATION Volodya Grancharov, Sigurdur Sverrisson, Erik Norvell, Tomas Toftgård, Jonas Svedberg, and Harald Pobloth SMN, Ericsson Research, Ericsson AB 64 8, Stockholm, Sweden ABSTRACT
Chapter 9 Fundamental Limits in Information Theory
 Chapter 9 Fundamental Limits in Information Theory Information Theory is the fundamental theory behind information manipulation, including data compression and data transmission. 9.1 Introduction o For
Chapter 9 Fundamental Limits in Information Theory Information Theory is the fundamental theory behind information manipulation, including data compression and data transmission. 9.1 Introduction o For
ELEMENTARY LINEAR ALGEBRA
 ELEMENTARY LINEAR ALGEBRA K R MATTHEWS DEPARTMENT OF MATHEMATICS UNIVERSITY OF QUEENSLAND First Printing, 99 Chapter LINEAR EQUATIONS Introduction to linear equations A linear equation in n unknowns x,
ELEMENTARY LINEAR ALGEBRA K R MATTHEWS DEPARTMENT OF MATHEMATICS UNIVERSITY OF QUEENSLAND First Printing, 99 Chapter LINEAR EQUATIONS Introduction to linear equations A linear equation in n unknowns x,
Multivariate Gaussian Random Number Generator Targeting Specific Resource Utilization in an FPGA
 Multivariate Gaussian Random Number Generator Targeting Specific Resource Utilization in an FPGA Chalermpol Saiprasert, Christos-Savvas Bouganis and George A. Constantinides Department of Electrical &
Multivariate Gaussian Random Number Generator Targeting Specific Resource Utilization in an FPGA Chalermpol Saiprasert, Christos-Savvas Bouganis and George A. Constantinides Department of Electrical &
SPEECH ANALYSIS AND SYNTHESIS
 16 Chapter 2 SPEECH ANALYSIS AND SYNTHESIS 2.1 INTRODUCTION: Speech signal analysis is used to characterize the spectral information of an input speech signal. Speech signal analysis [52-53] techniques
16 Chapter 2 SPEECH ANALYSIS AND SYNTHESIS 2.1 INTRODUCTION: Speech signal analysis is used to characterize the spectral information of an input speech signal. Speech signal analysis [52-53] techniques
a 11 x 1 + a 12 x a 1n x n = b 1 a 21 x 1 + a 22 x a 2n x n = b 2.
 Chapter 1 LINEAR EQUATIONS 11 Introduction to linear equations A linear equation in n unknowns x 1, x,, x n is an equation of the form a 1 x 1 + a x + + a n x n = b, where a 1, a,, a n, b are given real
Chapter 1 LINEAR EQUATIONS 11 Introduction to linear equations A linear equation in n unknowns x 1, x,, x n is an equation of the form a 1 x 1 + a x + + a n x n = b, where a 1, a,, a n, b are given real
Improved Bayesian Compression
 Improved Bayesian Compression Marco Federici University of Amsterdam marco.federici@student.uva.nl Karen Ullrich University of Amsterdam karen.ullrich@uva.nl Max Welling University of Amsterdam Canadian
Improved Bayesian Compression Marco Federici University of Amsterdam marco.federici@student.uva.nl Karen Ullrich University of Amsterdam karen.ullrich@uva.nl Max Welling University of Amsterdam Canadian
Multimedia Systems Giorgio Leonardi A.A Lecture 4 -> 6 : Quantization
 Multimedia Systems Giorgio Leonardi A.A.2014-2015 Lecture 4 -> 6 : Quantization Overview Course page (D.I.R.): https://disit.dir.unipmn.it/course/view.php?id=639 Consulting: Office hours by appointment:
Multimedia Systems Giorgio Leonardi A.A.2014-2015 Lecture 4 -> 6 : Quantization Overview Course page (D.I.R.): https://disit.dir.unipmn.it/course/view.php?id=639 Consulting: Office hours by appointment:
University of Cambridge. MPhil in Computer Speech Text & Internet Technology. Module: Speech Processing II. Lecture 2: Hidden Markov Models I
 University of Cambridge MPhil in Computer Speech Text & Internet Technology Module: Speech Processing II Lecture 2: Hidden Markov Models I o o o o o 1 2 3 4 T 1 b 2 () a 12 2 a 3 a 4 5 34 a 23 b () b ()
University of Cambridge MPhil in Computer Speech Text & Internet Technology Module: Speech Processing II Lecture 2: Hidden Markov Models I o o o o o 1 2 3 4 T 1 b 2 () a 12 2 a 3 a 4 5 34 a 23 b () b ()
Soft-Output Trellis Waveform Coding
 Soft-Output Trellis Waveform Coding Tariq Haddad and Abbas Yongaçoḡlu School of Information Technology and Engineering, University of Ottawa Ottawa, Ontario, K1N 6N5, Canada Fax: +1 (613) 562 5175 thaddad@site.uottawa.ca
Soft-Output Trellis Waveform Coding Tariq Haddad and Abbas Yongaçoḡlu School of Information Technology and Engineering, University of Ottawa Ottawa, Ontario, K1N 6N5, Canada Fax: +1 (613) 562 5175 thaddad@site.uottawa.ca
Let s now begin to formalize our analysis of sequential machines Powerful methods for designing machines for System control Pattern recognition Etc.
 Finite State Machines Introduction Let s now begin to formalize our analysis of sequential machines Powerful methods for designing machines for System control Pattern recognition Etc. Such devices form
Finite State Machines Introduction Let s now begin to formalize our analysis of sequential machines Powerful methods for designing machines for System control Pattern recognition Etc. Such devices form
Temporal Modeling and Basic Speech Recognition
 UNIVERSITY ILLINOIS @ URBANA-CHAMPAIGN OF CS 498PS Audio Computing Lab Temporal Modeling and Basic Speech Recognition Paris Smaragdis paris@illinois.edu paris.cs.illinois.edu Today s lecture Recognizing
UNIVERSITY ILLINOIS @ URBANA-CHAMPAIGN OF CS 498PS Audio Computing Lab Temporal Modeling and Basic Speech Recognition Paris Smaragdis paris@illinois.edu paris.cs.illinois.edu Today s lecture Recognizing
Direct-Sequence Spread-Spectrum
 Chapter 3 Direct-Sequence Spread-Spectrum In this chapter we consider direct-sequence spread-spectrum systems. Unlike frequency-hopping, a direct-sequence signal occupies the entire bandwidth continuously.
Chapter 3 Direct-Sequence Spread-Spectrum In this chapter we consider direct-sequence spread-spectrum systems. Unlike frequency-hopping, a direct-sequence signal occupies the entire bandwidth continuously.
The Optimality of Beamforming: A Unified View
 The Optimality of Beamforming: A Unified View Sudhir Srinivasa and Syed Ali Jafar Electrical Engineering and Computer Science University of California Irvine, Irvine, CA 92697-2625 Email: sudhirs@uciedu,
The Optimality of Beamforming: A Unified View Sudhir Srinivasa and Syed Ali Jafar Electrical Engineering and Computer Science University of California Irvine, Irvine, CA 92697-2625 Email: sudhirs@uciedu,
A New OCR System Similar to ASR System
 A ew OCR System Similar to ASR System Abstract Optical character recognition (OCR) system is created using the concepts of automatic speech recognition where the hidden Markov Model is widely used. Results
A ew OCR System Similar to ASR System Abstract Optical character recognition (OCR) system is created using the concepts of automatic speech recognition where the hidden Markov Model is widely used. Results
INF2270 Spring Philipp Häfliger. Lecture 8: Superscalar CPUs, Course Summary/Repetition (1/2)
 INF2270 Spring 2010 Philipp Häfliger Summary/Repetition (1/2) content From Scalar to Superscalar Lecture Summary and Brief Repetition Binary numbers Boolean Algebra Combinational Logic Circuits Encoder/Decoder
INF2270 Spring 2010 Philipp Häfliger Summary/Repetition (1/2) content From Scalar to Superscalar Lecture Summary and Brief Repetition Binary numbers Boolean Algebra Combinational Logic Circuits Encoder/Decoder
Pulse-Code Modulation (PCM) :
 PCM & DPCM & DM 1 Pulse-Code Modulation (PCM) : In PCM each sample of the signal is quantized to one of the amplitude levels, where B is the number of bits used to represent each sample. The rate from
PCM & DPCM & DM 1 Pulse-Code Modulation (PCM) : In PCM each sample of the signal is quantized to one of the amplitude levels, where B is the number of bits used to represent each sample. The rate from
Multi-level Gaussian selection for accurate low-resource ASR systems
 Multi-level Gaussian selection for accurate low-resource ASR systems Leïla Zouari, Gérard Chollet GET-ENST/CNRS-LTCI 46 rue Barrault, 75634 Paris cedex 13, France Abstract For Automatic Speech Recognition
Multi-level Gaussian selection for accurate low-resource ASR systems Leïla Zouari, Gérard Chollet GET-ENST/CNRS-LTCI 46 rue Barrault, 75634 Paris cedex 13, France Abstract For Automatic Speech Recognition
A Gentle Tutorial of the EM Algorithm and its Application to Parameter Estimation for Gaussian Mixture and Hidden Markov Models
 A Gentle Tutorial of the EM Algorithm and its Application to Parameter Estimation for Gaussian Mixture and Hidden Markov Models Jeff A. Bilmes (bilmes@cs.berkeley.edu) International Computer Science Institute
A Gentle Tutorial of the EM Algorithm and its Application to Parameter Estimation for Gaussian Mixture and Hidden Markov Models Jeff A. Bilmes (bilmes@cs.berkeley.edu) International Computer Science Institute
A TWO-LAYER NON-NEGATIVE MATRIX FACTORIZATION MODEL FOR VOCABULARY DISCOVERY. MengSun,HugoVanhamme
 A TWO-LAYER NON-NEGATIVE MATRIX FACTORIZATION MODEL FOR VOCABULARY DISCOVERY MengSun,HugoVanhamme Department of Electrical Engineering-ESAT, Katholieke Universiteit Leuven, Kasteelpark Arenberg 10, Bus
A TWO-LAYER NON-NEGATIVE MATRIX FACTORIZATION MODEL FOR VOCABULARY DISCOVERY MengSun,HugoVanhamme Department of Electrical Engineering-ESAT, Katholieke Universiteit Leuven, Kasteelpark Arenberg 10, Bus
A Nonuniform Quantization Scheme for High Speed SAR ADC Architecture
 A Nonuniform Quantization Scheme for High Speed SAR ADC Architecture Youngchun Kim Electrical and Computer Engineering The University of Texas Wenjuan Guo Intel Corporation Ahmed H Tewfik Electrical and
A Nonuniform Quantization Scheme for High Speed SAR ADC Architecture Youngchun Kim Electrical and Computer Engineering The University of Texas Wenjuan Guo Intel Corporation Ahmed H Tewfik Electrical and
Optimal Multiple Description and Multiresolution Scalar Quantizer Design
 Optimal ultiple Description and ultiresolution Scalar Quantizer Design ichelle Effros California Institute of Technology Abstract I present new algorithms for fixed-rate multiple description and multiresolution
Optimal ultiple Description and ultiresolution Scalar Quantizer Design ichelle Effros California Institute of Technology Abstract I present new algorithms for fixed-rate multiple description and multiresolution
THIS paper is aimed at designing efficient decoding algorithms
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 45, NO. 7, NOVEMBER 1999 2333 Sort-and-Match Algorithm for Soft-Decision Decoding Ilya Dumer, Member, IEEE Abstract Let a q-ary linear (n; k)-code C be used
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 45, NO. 7, NOVEMBER 1999 2333 Sort-and-Match Algorithm for Soft-Decision Decoding Ilya Dumer, Member, IEEE Abstract Let a q-ary linear (n; k)-code C be used
Selective Use Of Multiple Entropy Models In Audio Coding
 Selective Use Of Multiple Entropy Models In Audio Coding Sanjeev Mehrotra, Wei-ge Chen Microsoft Corporation One Microsoft Way, Redmond, WA 98052 {sanjeevm,wchen}@microsoft.com Abstract The use of multiple
Selective Use Of Multiple Entropy Models In Audio Coding Sanjeev Mehrotra, Wei-ge Chen Microsoft Corporation One Microsoft Way, Redmond, WA 98052 {sanjeevm,wchen}@microsoft.com Abstract The use of multiple
Robust Sound Event Detection in Continuous Audio Environments
 Robust Sound Event Detection in Continuous Audio Environments Haomin Zhang 1, Ian McLoughlin 2,1, Yan Song 1 1 National Engineering Laboratory of Speech and Language Information Processing The University
Robust Sound Event Detection in Continuous Audio Environments Haomin Zhang 1, Ian McLoughlin 2,1, Yan Song 1 1 National Engineering Laboratory of Speech and Language Information Processing The University
New Minimal Weight Representations for Left-to-Right Window Methods
 New Minimal Weight Representations for Left-to-Right Window Methods James A. Muir 1 and Douglas R. Stinson 2 1 Department of Combinatorics and Optimization 2 School of Computer Science University of Waterloo
New Minimal Weight Representations for Left-to-Right Window Methods James A. Muir 1 and Douglas R. Stinson 2 1 Department of Combinatorics and Optimization 2 School of Computer Science University of Waterloo
Chapter 1 Computer Arithmetic
 Numerical Analysis (Math 9372) 2017-2016 Chapter 1 Computer Arithmetic 1.1 Introduction Numerical analysis is a way to solve mathematical problems by special procedures which use arithmetic operations
Numerical Analysis (Math 9372) 2017-2016 Chapter 1 Computer Arithmetic 1.1 Introduction Numerical analysis is a way to solve mathematical problems by special procedures which use arithmetic operations
SPEED SCALING FOR ENERGY AWARE PROCESSOR SCHEDULING: ALGORITHMS AND ANALYSIS
 SPEED SCALING FOR ENERGY AWARE PROCESSOR SCHEDULING: ALGORITHMS AND ANALYSIS by Daniel Cole B.S. in Computer Science and Engineering, The Ohio State University, 2003 Submitted to the Graduate Faculty of
SPEED SCALING FOR ENERGY AWARE PROCESSOR SCHEDULING: ALGORITHMS AND ANALYSIS by Daniel Cole B.S. in Computer Science and Engineering, The Ohio State University, 2003 Submitted to the Graduate Faculty of
Design and Implementation of Speech Recognition Systems
 Design and Implementation of Speech Recognition Systems Spring 2013 Class 7: Templates to HMMs 13 Feb 2013 1 Recap Thus far, we have looked at dynamic programming for string matching, And derived DTW from
Design and Implementation of Speech Recognition Systems Spring 2013 Class 7: Templates to HMMs 13 Feb 2013 1 Recap Thus far, we have looked at dynamic programming for string matching, And derived DTW from
Reduced-Area Constant-Coefficient and Multiple-Constant Multipliers for Xilinx FPGAs with 6-Input LUTs
 Article Reduced-Area Constant-Coefficient and Multiple-Constant Multipliers for Xilinx FPGAs with 6-Input LUTs E. George Walters III Department of Electrical and Computer Engineering, Penn State Erie,
Article Reduced-Area Constant-Coefficient and Multiple-Constant Multipliers for Xilinx FPGAs with 6-Input LUTs E. George Walters III Department of Electrical and Computer Engineering, Penn State Erie,
Recognition Performance from SAR Imagery Subject to System Resource Constraints
 Recognition Performance from SAR Imagery Subject to System Resource Constraints Michael D. DeVore Advisor: Joseph A. O SullivanO Washington University in St. Louis Electronic Systems and Signals Research
Recognition Performance from SAR Imagery Subject to System Resource Constraints Michael D. DeVore Advisor: Joseph A. O SullivanO Washington University in St. Louis Electronic Systems and Signals Research
Residue Number Systems Ivor Page 1
 Residue Number Systems 1 Residue Number Systems Ivor Page 1 7.1 Arithmetic in a modulus system The great speed of arithmetic in Residue Number Systems (RNS) comes from a simple theorem from number theory:
Residue Number Systems 1 Residue Number Systems Ivor Page 1 7.1 Arithmetic in a modulus system The great speed of arithmetic in Residue Number Systems (RNS) comes from a simple theorem from number theory:
Binary Multipliers. Reading: Study Chapter 3. The key trick of multiplication is memorizing a digit-to-digit table Everything else was just adding
 Binary Multipliers The key trick of multiplication is memorizing a digit-to-digit table Everything else was just adding 2 3 4 5 6 7 8 9 2 3 4 5 6 7 8 9 2 2 4 6 8 2 4 6 8 3 3 6 9 2 5 8 2 24 27 4 4 8 2 6
Binary Multipliers The key trick of multiplication is memorizing a digit-to-digit table Everything else was just adding 2 3 4 5 6 7 8 9 2 3 4 5 6 7 8 9 2 2 4 6 8 2 4 6 8 3 3 6 9 2 5 8 2 24 27 4 4 8 2 6
L11: Pattern recognition principles
 L11: Pattern recognition principles Bayesian decision theory Statistical classifiers Dimensionality reduction Clustering This lecture is partly based on [Huang, Acero and Hon, 2001, ch. 4] Introduction
L11: Pattern recognition principles Bayesian decision theory Statistical classifiers Dimensionality reduction Clustering This lecture is partly based on [Huang, Acero and Hon, 2001, ch. 4] Introduction
Lecture 3: ASR: HMMs, Forward, Viterbi
 Original slides by Dan Jurafsky CS 224S / LINGUIST 285 Spoken Language Processing Andrew Maas Stanford University Spring 2017 Lecture 3: ASR: HMMs, Forward, Viterbi Fun informative read on phonetics The
Original slides by Dan Jurafsky CS 224S / LINGUIST 285 Spoken Language Processing Andrew Maas Stanford University Spring 2017 Lecture 3: ASR: HMMs, Forward, Viterbi Fun informative read on phonetics The
Learning Recurrent Neural Networks with Hessian-Free Optimization: Supplementary Materials
 Learning Recurrent Neural Networks with Hessian-Free Optimization: Supplementary Materials Contents 1 Pseudo-code for the damped Gauss-Newton vector product 2 2 Details of the pathological synthetic problems
Learning Recurrent Neural Networks with Hessian-Free Optimization: Supplementary Materials Contents 1 Pseudo-code for the damped Gauss-Newton vector product 2 2 Details of the pathological synthetic problems
BASICS OF DETECTION AND ESTIMATION THEORY
 BASICS OF DETECTION AND ESTIMATION THEORY 83050E/158 In this chapter we discuss how the transmitted symbols are detected optimally from a noisy received signal (observation). Based on these results, optimal
BASICS OF DETECTION AND ESTIMATION THEORY 83050E/158 In this chapter we discuss how the transmitted symbols are detected optimally from a noisy received signal (observation). Based on these results, optimal
Lecture 3: Pattern Classification
 EE E6820: Speech & Audio Processing & Recognition Lecture 3: Pattern Classification 1 2 3 4 5 The problem of classification Linear and nonlinear classifiers Probabilistic classification Gaussians, mixtures
EE E6820: Speech & Audio Processing & Recognition Lecture 3: Pattern Classification 1 2 3 4 5 The problem of classification Linear and nonlinear classifiers Probabilistic classification Gaussians, mixtures
ww.padasalai.net
 t w w ADHITHYA TRB- TET COACHING CENTRE KANCHIPURAM SUNDER MATRIC SCHOOL - 9786851468 TEST - 2 COMPUTER SCIENC PG - TRB DATE : 17. 03. 2019 t et t et t t t t UNIT 1 COMPUTER SYSTEM ARCHITECTURE t t t t
t w w ADHITHYA TRB- TET COACHING CENTRE KANCHIPURAM SUNDER MATRIC SCHOOL - 9786851468 TEST - 2 COMPUTER SCIENC PG - TRB DATE : 17. 03. 2019 t et t et t t t t UNIT 1 COMPUTER SYSTEM ARCHITECTURE t t t t
Improving the Multi-Stack Decoding Algorithm in a Segment-based Speech Recognizer
 Improving the Multi-Stack Decoding Algorithm in a Segment-based Speech Recognizer Gábor Gosztolya, András Kocsor Research Group on Artificial Intelligence of the Hungarian Academy of Sciences and University
Improving the Multi-Stack Decoding Algorithm in a Segment-based Speech Recognizer Gábor Gosztolya, András Kocsor Research Group on Artificial Intelligence of the Hungarian Academy of Sciences and University
Multi-Robotic Systems
 CHAPTER 9 Multi-Robotic Systems The topic of multi-robotic systems is quite popular now. It is believed that such systems can have the following benefits: Improved performance ( winning by numbers ) Distributed
CHAPTER 9 Multi-Robotic Systems The topic of multi-robotic systems is quite popular now. It is believed that such systems can have the following benefits: Improved performance ( winning by numbers ) Distributed
Constructing Polar Codes Using Iterative Bit-Channel Upgrading. Arash Ghayoori. B.Sc., Isfahan University of Technology, 2011
 Constructing Polar Codes Using Iterative Bit-Channel Upgrading by Arash Ghayoori B.Sc., Isfahan University of Technology, 011 A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree
Constructing Polar Codes Using Iterative Bit-Channel Upgrading by Arash Ghayoori B.Sc., Isfahan University of Technology, 011 A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree
CS264: Beyond Worst-Case Analysis Lecture #11: LP Decoding
 CS264: Beyond Worst-Case Analysis Lecture #11: LP Decoding Tim Roughgarden October 29, 2014 1 Preamble This lecture covers our final subtopic within the exact and approximate recovery part of the course.
CS264: Beyond Worst-Case Analysis Lecture #11: LP Decoding Tim Roughgarden October 29, 2014 1 Preamble This lecture covers our final subtopic within the exact and approximate recovery part of the course.
page 1 Total ( )
 A B C D E F Costs budget of [Claimant / Defendant] dated [ ] Estimated page 1 Work done / to be done Pre-action Disbs ( ) Time ( ) Disbs ( ) Time ( ) Total ( ) 1 Issue /statements of case 0.00 0.00 CMC
A B C D E F Costs budget of [Claimant / Defendant] dated [ ] Estimated page 1 Work done / to be done Pre-action Disbs ( ) Time ( ) Disbs ( ) Time ( ) Total ( ) 1 Issue /statements of case 0.00 0.00 CMC
Exact Probability of Erasure and a Decoding Algorithm for Convolutional Codes on the Binary Erasure Channel
 Exact Probability of Erasure and a Decoding Algorithm for Convolutional Codes on the Binary Erasure Channel Brian M. Kurkoski, Paul H. Siegel, and Jack K. Wolf Department of Electrical and Computer Engineering
Exact Probability of Erasure and a Decoding Algorithm for Convolutional Codes on the Binary Erasure Channel Brian M. Kurkoski, Paul H. Siegel, and Jack K. Wolf Department of Electrical and Computer Engineering
Digital Systems Roberto Muscedere Images 2013 Pearson Education Inc. 1
 Digital Systems Digital systems have such a prominent role in everyday life The digital age The technology around us is ubiquitous, that is we don t even notice it anymore Digital systems are used in:
Digital Systems Digital systems have such a prominent role in everyday life The digital age The technology around us is ubiquitous, that is we don t even notice it anymore Digital systems are used in:
Computer Science 324 Computer Architecture Mount Holyoke College Fall Topic Notes: Digital Logic
 Computer Science 324 Computer Architecture Mount Holyoke College Fall 2007 Topic Notes: Digital Logic Our goal for the next few weeks is to paint a a reasonably complete picture of how we can go from transistor
Computer Science 324 Computer Architecture Mount Holyoke College Fall 2007 Topic Notes: Digital Logic Our goal for the next few weeks is to paint a a reasonably complete picture of how we can go from transistor
Word-length Optimization and Error Analysis of a Multivariate Gaussian Random Number Generator
 Word-length Optimization and Error Analysis of a Multivariate Gaussian Random Number Generator Chalermpol Saiprasert, Christos-Savvas Bouganis and George A. Constantinides Department of Electrical & Electronic
Word-length Optimization and Error Analysis of a Multivariate Gaussian Random Number Generator Chalermpol Saiprasert, Christos-Savvas Bouganis and George A. Constantinides Department of Electrical & Electronic
Optimal Power Control in Decentralized Gaussian Multiple Access Channels
 1 Optimal Power Control in Decentralized Gaussian Multiple Access Channels Kamal Singh Department of Electrical Engineering Indian Institute of Technology Bombay. arxiv:1711.08272v1 [eess.sp] 21 Nov 2017
1 Optimal Power Control in Decentralized Gaussian Multiple Access Channels Kamal Singh Department of Electrical Engineering Indian Institute of Technology Bombay. arxiv:1711.08272v1 [eess.sp] 21 Nov 2017
