Persistent Spread Measurement for Big Network Data Based on Register Intersection
|
|
|
- Elwin Daniels
- 5 years ago
- Views:
Transcription
1 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection YOU ZHOU, Univerity of Florida YIAN ZHOU, Google Inc. and Univerity of Florida MIN CHEN, Google Inc. and Univerity of Florida SHIGANG CHEN, Univerity of Florida Peritent pread eaureent i to count the nuber of ditinct eleent that perit in each network flow for predefined tie period. It ha any practical application, including detecting long-ter tealthy network activitie in the background of noral-uer activitie, uch a tealthy DDoS attack, tealthy network can, or faked network trend, which cannot be detected by traditional flow cardinality eaureent. With big network data, one challenge i to eaure the peritent pread of a aive nuber of flow without incurring too uch eory overhead a uch eaureent ay be perfored at the line peed by network proceor with fat but all on-chip eory. We propoe a highly copact Virtual Interection HyperLogLog VI-HLL architecture for thi purpoe. It achieve far better eory efficiency than the bet prior work of V-Bitap, and in the eantie dratically extend the eaureent range. Theoretical analyi and extenive experient deontrate that VI-HLL provide good eaureent accuracy even in very tight eory pace of le than bit per flow. 4 CCS Concept: Network Network eaureent; Network onitoring; Denial-of-ervice attack; Network anageent; Additional Key Word and Phrae: Peritent Spread Meaureent; Big Network Data; Network Traffic Meaureent; Network Security ACM Reference forat: You Zhou, Yian Zhou, Min Chen, and Shigang Chen. 27. Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection. Proc. ACM Mea. Anal. Coput. Syt.,, Article 4 June 27, 29 page. DOI: INTRODUCTION Maive and ditributed data are increaingly prevalent in odern network a high-peed router forward packet at hundred of gigabit or even terabit per econd. Big data alo happen at the network edge. For a few exaple, Google handle over 4, earch querie every econd [], and illion tweet are produced per day [2]. Traffic eaureent and claification at uch high peed and with uch aive volue poe ignificant challenge [3 4]. Exact eaureent of big network data i often infeaible due Thi work i upported in part by the National Science Foundation under grant STC-6248 and a grant fro Florida Center for Cyberecurity. Correponding author: Yian Zhouyianzhou@google.co. Author addree: Y. Zhou and S. Chen, Departent of Coputer and Inforation Science and Engineering, Univerity of Florida; Y. Zhou and M. Chen, Google, Mountain View. Periion to ake digital or hard copie of all or part of thi work for peronal or claroo ue i granted without fee provided that copie are not ade or ditributed for profit or coercial advantage and that copie bear thi notice and the full citation on the firt page. Copyright for coponent of thi work owned by other than ACM ut be honored. Abtracting with credit i peritted. To copy otherwie, or republih, to pot on erver or to reditribute to lit, require prior pecific periion and/or a fee. Requet periion fro periion@ac.org. 27 ACM /27/6-ART4 $. DOI:
2 4:2 Y. Zhou et al. Multi-period Analyi Traffic Sketche S S S S Raw Traffic Data Tie One Period One Period One Period Fig.. Multi-period analyi of data ketche. to exceively high eory requireent and coputation/counication overhead, wherea approxiate etiation with probabilitic guarantee i a viable option. Flow cardinality etiation [ 2] i a fundaental proble in network traffic eaureent. It etiate the nuber of ditinct eleent in every flow during pre-defined eaureent period. Each flow i uniquely identified by one or ultiple field in the packet header, called flow label, which can be flexibly defined baed on application need. A exaple, the flow under eaureent ay be per-ource flow with flow label being the ource addre, per-detination flow, TCP flow, WWW flow, or application-pecific flow. The eleent under eaureent can be detination addree, ource addree, port, value in other header field, or even keyword that appear in packet payload. For exaple, for each per-ource flow, if detination addree are treated a eleent, then a flow cardinality i the nuber of ditinct detination addree that the flow ource ha contacted, which can be ued for can detection. Exiting reearch on flow cardinality etiation ainly focue on analying traffic ketche fro one eaureent period, which i the uary of the raw traffic data in that tie period. Since online torage can only hold liited inforation, the ketche are uually offloaded to a erver after each eaureent period for long-ter torage and offline query. Thi paper tudie an under-invetigated proble of analyzing ketche acro ultiple period a hown in Figure. In particular, we are intereted in eauring the peritent pread of each flow, which i defined a the nuber of ditinct eleent that how up in a network flow during a certain nuber of conecutive eaureent period. Practical Iportance: Peritent pread eaureent ha any practical application. Traditional uper-preader detection i to identify the elephant flow whoe cardinalitie are abnorally large, and can be applied to onitoring network anoalie. For intance, canner ay be identified if they end probe to too any detination addree, i.e., the cardinalitie of per-ource flow are large. But there are practical cenario where flow cardinality alone i inadequate a tealthy canner ay intentionally reduce it probing rate to reduce it flow cardinality in order to evade detection. Even with a reduced probing rate, after ufficient tie, the canner can till dicover yte with vulnerability to exploit. In thi cae, eauring peritent pread can help identify uch tealthy canner. A a canner probe different detination addree over tie, it peritent pread i zero or low; if a canner deliberately
3 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection 4:3 Internet Attacker Server End-Uer Noral Connection Stealthy DDoS Fig. 2. Stealthy DDoS attack. repeated any of the ae detination, it would ignificantly low down the already all canning rate. Therefore, odet flow cardinality but uually low peritent pread help ignal a low-rate canner that wander in the detination addre pace. In the econd exaple, DDoS attack ay be identified if unuually any client end requet to a erver, i.e., the cardinality of a per-detination flow i too high. However, a illutrated in Figure 2, with a aller nuber of available attacking achine, a tealthy DDoS attack doe not attept to overwhel the target erver with exceive requet, but to degrade it perforance [2]. If the nuber of attacking achine i iilar to the nuber of legitiate uer, we will not oberve unuual flow cardinalitie. Again, eauring peritent flow cardinality ay help. According to the tudy [22] of real-world network trace fro CAIDA [23], the continuou interaction between legitiate uer and their target erver i norally horter than twenty inute. For attacker, ince their goal i to degrade the perforance of the target erver over a long period, thee hotile achine will end requet peritently to the target erver, reulting in a ignificant peritent cardinality over tie that i higher than uual. Peritent pread eaureent alo ha application at the network edge e.g., web earch and ocial edia. Take Google trend a an exaple. If Google treat all client IP that query a keyword a a flow, the cardinality of the flow ugget the popularity of the keyword being earched. However, a ignificant nuber of colluding achine with different IP addree can periodically query the ae keyword, and ake thee keyword popular in Google trend a they wih. Since noral uer typically do not query the ae keyword periodically for a long tie, peritent pread eaureent can help detect uch long-ter earch pattern, where a large et of IP keep querying the ae keyword over ultiple period. Beide detecting faked popularity, our work ay erve a a generalized priitive tool for detecting hidden activitie that anifet only over long tie. Prior Art and Challenge: Mot previou work focue on traffic ketche of one eaureent period. To deal with a large nuber of flow, a erie of ketche were developed to reduce aive raw data to a uary of per-flow cardinalitie during online eaureent. Thee olution include PCSA [6], Multi-Reolution Bitap [], LogLog [7], and HyperLogLog HLL [8]. The principle i to allocate a eparate data tructure, containing a certain nuber of bitap, regiter or other eleentary data tructure, to each flow for recording it eleent. Over the pat decade, a ajor reearch thrut i to reduce the ketche eory footprint. But it ha been a difficult undertaking with low progre. For
4 4:4 Y. Zhou et al. intance, per-flow eory requireent for cardinality eaureent wa reduced fro thouand of bit to hundred of bit by HLL [8], which enure a large eaureent range with good accuracy. However, a the Internet enter the big-data era, hundred of bit per flow can till be too uch when there are too any flow. An exaple i odern high-peed router, which forward packet fro incoing port to outgoing port via witching fabric at the extraordinary peed. To utain high throughput, online odule for packet cheduling, acce control, quality of ervice and traffic eaureent are often ipleented on network proceor, bypaing ain eory and CPU alot entirely. The on-die eory uch a SRAM in a network proceor i fat but all, and ay have to be hared by ultiple function. Therefore, it i highly deirable to ipleent thee function a copact a poible. A thi paper focue on peritent cardinality eaureent, we want to puh it eory uage to an unprecedented low level, in order to ave pace for other function on the ae chip. In another exaple, uppoe a web-earch analyt want to profile, for each keyword phrae, quetion or entence, the nuber of ditinct uer that have earched the keyword. Thi inforation i ueful in online ocial/econoical/opinion trend tudie or optiizing earch perforance [24]. A we have dicued earlier, peritent pread eaureent can be ued to detect faked popularity. However, ince the nuber of flow one flow per keyword, phrae, quetion or entence can be in any billion, it preent a challenge in coputational reource, and eory in particular. Intead of uing an expenive and powerful erver, if we can dratically reduce the reource requireent, we ay be able to run uch analyi on a cheap coodity coputer, which i a welcoe reult when high-end achine are not readily available. To u up, there are practical cenario with great diparity between eory deand and availability, which require online cardinality eaureent to be ipleented a copact a poible. Moreover, the deign of a eaureent function hould alo enure reaonable accuracy with a large eaureent range that upport elephant flow with very high peritent cardinalitie. To the bet of our knowledge, little reearch work on peritent pread eaureent exit in literature. Chen et al. [] propoe a continuou variant of Flajolet-Martin ketche adapted fro [6], which however cannot give accurate reult when the available eory pace i tight [22]. Xiao et al. [22] deign a bit haring architecture called ulti-virtual bitap, which tore a flow inforation in a virtual bitap during each eaureent period and analyze the bitap fro ultiple period to find peritent cardinality. The ajor drawback i that the eaureent range of bitap i very all and no ore than a few thouand for a typical ipleentation. Our Contribution: The objective of our reearch i to iprove the eory efficiency and enlarge the range of peritent pread eaureent, while keeping good accuracy. Our ain contribution are uarized below. Firt, we deign a highly efficient peritent pread etiator called Interection HLL I-HLL that work over ultiple eaureent period. Every flow i allocated a eparate HLL ketch of regiter to record it cardinality in a eaureent period. We apply regiter interection over the erie of HLL ketche produced for a flow during a given nuber of eaureent period. We then eploy axiu likelihood etiation to develop the forula of the I-HLL etiator that copute an etiate of the flow peritent pread. We forally analyze the accuracy of the etiation, and how I-HLL ha a large etiation range. Second, to further iprove eory efficiency, we introduce regiter haring on top of I-HLL and propoe a highly copact Virtual Interection HLL VI-HLL architecture to eaure the peritent pread of a large nuber of flow iultaneouly. Siilar to [2], each flow i allocated a virtual HLL ketch of ultiple regiter, and the virtual HLL ketche of all flow hare a coon pool of phyical regiter. But unlike [2] that eaure flow cardinality in one period, our VI-HLL deal with peritent
5 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection 4: cardinality over ultiple period. VI-HLL achieve far better eory efficiency and uch larger range than the bet exiting work V-Bitap [22] on peritent cardinality eaureent. Finally, not only do we atheatically analyze the etiation accuracy of VI-HLL, but alo perfor extenive experient to copare it with V-Bitap. The experiental reult deontrate the uperior perforance of VI-HLL. Interetingly, it etiation accuracy iprove when the nuber of eaureent period increae. The ret of thi paper i organized a follow. Section 2 forulate the peritent pread eaureent proble. Section 3 dicue the preliinarie. Section 4 propoe our I-HLL etiator. Section preent the enhanced VI-HLL architecture. Section 6 evaluate the perforance by iulation. Section 7 draw the concluion. 2 PROBLEM STATEMENT Conider the packet trea arriving at a router or firewall inide a high-peed network or the application record produced by a erver e.g., web earch at the network edge. We odel both type of network data a a equence of flow label, eleent pair in our abtraction. Baed on the flow label, the equence of pair are claified into different flow. For the packet trea a exaple, if we want to eaure the nuber of ditinct ource that have contacted each detination, we abtract every packet a a pair of detination addre and ource addre, which can both be extracted fro the packet header. All pair i.e., packet with the ae detination addre i.e., flow label contitute a flow. In the exaple of web earch, each earch record i abtracted a a pair of keyword and ource addre fro which the earch requet i received. All pair with the ae keyword are treated a a flow. We are intereted in eauring eleent that keep howing up over tie in each flow. The iue i how to quantitatively define the peritency of keep howing up over tie. Conider the traditional definition of flow cardinality or pread eaureent [ 8], which i to find the nuber of ditinct eleent in each flow during a certain tie frae [,T]. Thi definition doe not capture the property of peritency. We illutrate it through an exaple of eauring the nuber of ditinct ource that have contacted each detination, where all packet to the ae detination for a per-detination flow. Suppoe one illion different ource contacted a detination during a day. The cardinality of thi per-detination flow i one illion. But if all the ource contacted the detination in the firt inute and no contact wa ade for the ret of the day, we cannot ay thee ource kept contacting the detination for the day. The peritent pread i zero in thi cae. To forulating peritency, one way i to divide the day into eaureent period of inute each. If we find that ource out of the illion were preent in each period, they were the peritent eleent that we want to eaure. The reaining eleent that howed up only in the firt period were not peritent. So the peritent pread i. Generally, we pecify peritency by dividing tie into eaureent period and eaure thoe eleent that are preent peritently in a pre-et nuber t of conecutive period under conideration. We give a ore foral definition a follow: Conider an arbitrary flow and t conecutive eaureent period. Let S j be the et of ditinct eleent in the flow oberved during the jth eaureent period, j t. Let S be the ubet of coon eleent oberved in all t period, i.e., S = S S 2... S t. The proble of peritent pread eaureent i to find the ize of S, denoted a n = S, which i called the peritent pread of the flow. The eleent in S are called peritent eleent. The eleent in S j S, j t, are called tranient eleent. The propoed architecture for etiating the flow peritent pread i intended to be generic, while it paraeter hould be et by yte adin baed on their application need. In particular, the length of each period and the nuber t of period ued are application-dependent. A an analogy, a yte adin will configure the threhold for can detection i.e., the triggering nuber of different detination
6 4:6 Y. Zhou et al. Peritent Spread Period= econd Nuber of Period Peritent Spread Period= inute Nuber of Period Fig. 3. Peritent pread of a packet flow to detination , with repect to different period length in the two plot and different nuber t of period on the horizontal axi. 2 4 Peritent Spread 3 29 Period= econd Nuber of Period Peritent Spread Period= inute Nuber of Period Fig. 4. Peritent pread of a packet flow to detination , with repect to different period length in the two plot and different nuber t of period on the horizontal axi. that a ource contact over a period to be ore than the eaured nuber of ot noral ource, which ay vary fro network to network. Siilarly, the paraeter of peritent pread eaureent hould alo be et baed on application-pecific and yte-pecific noral traffic tatitic. Conider the exaple in the introduction on detecting tealthy DDoS attack by eauring peritent pread of per-detination erver flow. If we et the eaureent period to be a day, we ay find ignificant peritent pread for erver in noral traffic, becaue legitiate uer ay regularly acce their eail, web and other ervice on a daily bai. If we et the eaureent period to be a few econd, we ay till find ignificant peritent pread in noral traffic becaue any ingle connection to a ervice ay lat for any conecutive period. However, if we chooe a period length in-between and ue a ufficient nuber of period, it becoe unlikely for any noral uer to exhibit the ae peritency in acceing the erver a the attacking hot [22]. The above analyi i confired by our experient uing a real network traffic trace fro CAIDA, containing 39,46 per-detination flow in an hour. We vary the length of eaureent period and the nuber t of period when eauring the peritent pread of the flow. The eaureent reult for two
7 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection 4:7 Nuber of Flow t = Nuber of Flow t = e2 e3 e3 e4 Flow Cardinality e2 e3 e3 e4 Peritent Spread Nuber of Flow t = 3 Nuber of Flow t = e2 e3 e3 e4 Peritent Spread 7 7 e2 e3 e3 e4 Peritent Spread Fig.. Flow ditribution with repect to peritent pread under different t value. randoly-elected large flow are hown in Fig. 3-4, and the tatitic of all flow are hown in Fig.. Conider the flow in Fig. 3. Both plot how that it peritent pread drop quickly when we increae the nuber of period. However, in the left plot where the period i hort econd, if the nuber t of period ued i too all e.g., 2 or 3, the peritent pread of thi noral traffic can be ignificant. For exaple, when t = 2, the peritent pread i 668, which i 36% of the pread when t =, i.e., the nuber of active ource in one period. Siilar obervation can be ade in Fig. 4. On the other hand, a we increae the period length to inute in the right plot, when t = 2, the peritent pread i jut 3.8% of the pread when t =. Be aware that a period of inute ha any ore packet thu eleent than a period of econd; therefore, the relative percentage 36% v.. 3.8% i a better indicator for the ipact of period length on peritent pread. By chooing a period length of inute and letting t = 6, we oberve jut 3 peritent eleent ource in the flow during an hour. In contrat, when the period length i econd and t = 6, we oberve 98 peritent eleent in an hour. Fig. preent the flow ditribution with repect to the pread or cardinality value when t =,2,3 and 6 in the four plot, repectively. We put flow in bin with pread range of [, ],, ],, ],... The length of each period i inute. The figure how that ot flow in thi noral traffic trace have all pread. When we increae the nuber of period, the nuber of flow in bin of large pread decreae quickly, uggeting that the peritent pread of thoe flow are reduced to all value. Thi property help in anoaly detection: When we ee the peritent pread of a per-detination flow uddenly jup
8 4:8 Y. Zhou et al. fro a uually all value to a large one, it ignal a poible DDoS attack a we explain earlier in the introduction. The objective of thi paper i to deign a peritent pread etiation architecture that conit of an online coponent and an offline coponent, where the forer record all eleent fro all flow in real tie uing highly-copact data tructure which keep only ketche of the raw traffic data and are offloaded to a erver after each eaureent period, and the latter perfor peritent pread etiation baed on the ketche fro ultiple period. We will evaluate the perforance of our deign baed on the following two etric. Meory overhead: The diparity in eory deand and upply for practical traffic eaureent cenario explained in the introduction otivate u to ake the online coponent of peritent pread eaureent a copact a poible. Etiation accuracy: Let ˆn be the etiation reult of the actual peritent pread n of a flow. The etiation accuracy i evaluated baed on the relative bia, Biaˆn n, and the relative tandard error, StdErrˆn n, which are defined below. Bia ˆn n = E ˆn StdErr ˆn n =, n Var ˆn = n Varˆn n. Clearly, aller value of relative bia and relative tandard error ean ore accurate eaureent reult. Given a certain available eory pace, we want to ake peritent-pread etiation a accurate a poible. We ake two auption, which are needed by our tatitical analyi. The firt auption i that there are a large nuber of flow in each period and the nuber of ditinct eleent/peritent eleent in any flow i negligibly all when coparing with the total nuber of ditinct eleent/peritent eleent in all flow. The econd auption i that tranient eleent can be approxiately treated a being independent aong different period. The ae auption are needed in [22], which provide network traffic analyi to upport the auption. The obervation i that when the length of each period i ufficiently long, ot tranient eleent will tay in one period becaue ot uer connection do not take that long. For exaple, when the period i et to 7 inute with a gap of 3 inute between conecutive period, traffic analyi in [22] how that le than % of all HTTP connection overlap with ore than one period. The percentage will be lower if the period i et longer. 3 PRELIMINARIES In thi ection, we firt introduce the HyperLogLog HLL algorith [8], and then preent a traightforward regiter-union approach for peritent pread etiation baed on HLL, which further otivate a ore accurate regiter-interection approach. 3. HyperLogLog HLL Algorith The HLL algorith ha ade ipact on IT indutry [9]. It i deigned to etiate the nuber of ditinct eleent in a ingle trea flow during a ingle eaureent period. HLL enure a large etiation range and a good etiation accuracy. An incoing trea i odeled a a ulti-et S, whoe eleent are in the doain D. An HLL ketch M of regiter are allocated to tore the cardinality inforation. Without lo of generality, let = 2 b,b N. The ith regiter in M i denoted by M[i], i [,. The ize
9 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection 4:9 ALGORITHM : HLL Sketch for a trea S Initialize a regiter array M of ize = 2 b with all zero; for e S do x := he; p := x x 2...x b ; q := x b+ x b+2... ; M[p] := axm[p],ρq; end return M at the end of a eaureent period. of regiter i et baed on the axiu range of the cardinalitie to be etiated. Specifically, a regiter with bit can eaure cardinalitie up to Algorith uarize how to generate an HLL ketch for trea S. Firt, we initialize all M[i] to zero, i [,. Let h : [D] [,] {,} L be a uitable hah function that ap an eleent in doain D uniforly at rando to the binary range of L bit long. Let ρq be the poition of the leftot for a binary tring q {,} L, i.e., it equal one plu the length of leading zero in q. For exaple, if q =..., then ρq = 4. For an incoing eleent e in trea S, let x be the binary repreentation of hah value he, where p i the leading b bit in x, and q i the reaining bit. Then the eleent e i apped to M[p], and M[p] i updated by M[p] := axm[p],ρq. 2 In other word, the trea S i plit into ubtrea, each of which i encoded in a regiter baed on the firt b bit of hahed value he. Each regiter i et to the axiu value of ρq aong all eleent e in the correponding ubtrea. If no eleent i encoded by a regiter, the regiter reain zero. At the end of a period, HLL etiate the nuber of ditinct eleent encoded by it ketch M = {M[], M[],..., M[ ]} through noralized haronic ean [8]: ˆn S = α 2 2 M[i], 3 where α i the bia correction contant that i 2+u du α = log u Pre-coputed value of α ay be ued in practice: α 6 =.673, α 32 =.697, α 64 =.79, and α =.723/+.79/ for 28. According to [8], the etiation tandard error i ˆnS StdErr = O. n S It ha been hown that etiation by 3 i everely biaed when the cardinality i aller than 2.. Hence, when the etiated cardinality fro 3 i aller than 2., we treat M a a bitap of bit, with each regiter M[i] converted to one bit, whoe value i one when M[i] > or zero otherwie. The etiation forula for all cardinality i where V i the fraction of bit in the bitap whoe value reain zero. i= ˆn S = lnv, 6
10 4: Y. Zhou et al. 3.2 HLL-Baed Peritent Spread Etiation The HLL ketche can be adopted for peritent pread etiation. To ake technical dicuion ore concrete, we conider per-detination flow paing a router and eaure the nuber of ditinct ource addree in each flow. For an arbitrary flow, we allocate an HLL ketch M of regiter to record the flow ource addree in each period. Denote the HLL ketch of the jth period by M j. At the beginning of the jth period, all regiter of HLL ketch M j are initialized to zero. When the router receive a packet, it extract the flow label i.e., detination addre dt fro the packet header, and record the eleent i.e., ource addre rc in M j by Algorith. By the end of the period, the router ha recorded the et S j of eleent in M j. It offload M j to a erver for long-ter torage and offline query. After t conecutive period, we have a equence of HLL ketche M, M 2,..., M t. The proble i how to ue thee HLL ketche to etiate the peritent pread n = S = S S 2... S t, which i the nuber of ditinct eleent that are preent peritently through the t period. We propoe two approache, regiter union and regiter interection, to olve thi proble Regiter-Union Approach. According to the incluion-excluion rule, the cardinality of an arbitrary et interection, including n, can be expreed a u/difference of the cardinalitie of et union. The cardinality of any et union can be etiated uing the HLL etiator 3 after perforing regiter-wie union on the correponding ketche. For exaple, the cardinality of et interection S S 2 i S S 2 = S + S 2 S S 2. 7 Naely, S S 2 i repreented a the u/difference of three cardinalitie, S, S 2 and S S 2, where S and S 2 can be etiated fro M and M 2 uing the HLL etiator, repectively. Moreover, given the ketche M and M 2 for S and S 2, the HLL ketch for the et union S S 2 i iply regiter-wie union M = M M2, where operator i defined to be M [i] = axm [i],m 2 [i], i <. After that, S S 2 can be etiated by applying the HLL etiator on M. Generalizing the above analyi to interection over ore than two period i.e., t > 2 i traightforward. Depite it atheatical iplicity, regiter-union etiate i very inaccurate ince it doe not fully explore the correlation aong the t HLL ketche. Let n be the cardinality of et union S S 2... S t, n be the cardinality of et interection S, and ˆn be it etiate uing the regiter-union approach. According to [, 8], the etiation tandard error of n i ˆn n StdErr n = O. 8 n The etiation accuracy depend on n n, and StdErr ˆn n increae a n n becoe larger. When t i et large, n ay becoe large due to addition of ore tranient eleent, wherea n ay tay ore or le the ae if the et of peritent eleent doe not change uch, which drive up n n and thu inaccuracy in etiation. The accuracy lo a t grow can prohibit a network adin fro configuring a large value for t Regiter-Interection Approach. By contrat, the regiter-interection approach calculate the interection of HLL ketche, M = M M 2... M t, where operator on two arbitrary HLL ketche i defined a M j M j2 [i] = inm j [i],m j2 [i], i <. Therefore, the value of the ith regiter in the interection ketch M i the inial value of all correponding regiter in the t original HLL ketche, M [i] = in j [,t]{ Mj [i] }, i <. 9
11 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection 4: Let M be the iaginary HLL ketch M that record the true interection et S. We derive the relationhip between M and M. A tated earlier, each flow eleent peudo-randoly pick a regiter in M j by the hah function h, and update the choen regiter accordingly. Moreover, in different period, a peritent eleent e in S alway trie to update the ae regiter M j [p] uing the ae value ρq a uggeted by 2. Therefore, the ae ketch M contructed with the peritent eleent fro S i ebedded in M j, j t, which can be conidered a M T j, where T j i the ketch contructed with the tranient eleent, S j = S j S, in the jth period. T j change fro period to period a tranient eleent vary over tie. Hence, we have M = M M 2... M t = M T M T 2... M T t = M T T 2... T t. The value of the ith regiter in M i, for i <, M [i] = ax{m [i],in{t [i],t 2 [i],...,t t [i]}}. If we ue M to approxiate M, the HLL etiator will produce a reult with poitive bia becaue it ay happen that tranient eleent et the ith regiter in all t period higher than M [i], cauing overetiation of the peritent pread, although the probability for thi to happen decreae a the nuber t of period increae. We will addre thi overetiation iue by axiu likelihood etiation. 4 INTERSECTION HLL ESTIMATOR In thi ection, we preent an Interection HLL I-HLL etiator baed on regiter interection M and axiu likelihood etiation MLE to eaure the peritent cardinality of any flow. 4. The Interection Regiter Value We firt analyze the probabilitic ditribution for an arbitrary regiter in the I-HLL ketch M, which will be ued to contruct an MLE etiator. Suppoe we eaure a flow over t period, and obtain a equence of HLL ketche, M, M 2,..., M t, which record eleent et, S, S 2,..., S t, repectively. Let n j be the cardinality of S j. The nuber of eleent in the tranient ubet S j i n j = n j n. We know M j = M T j, i.e., the HLL ketch M j of the jth period i the cobination of M for the peritent eleent and T j for the tranient eleent. In other word, M j [i] = axm [i],t j [i], i <. Applying it to 9, we can expre the interection ketch M a M [i] = in {ax M [i], T j [i] } j [,t] = ax M { [i], in Tj [i] } 2. j [,t] Suppoe the value of the ith regiter in M i k, i.e., M [i] = k, k. There are two cae: I. The peritent eleent in S et the value of regiter M [i] to be k, and the tranient eleent in at{ leat one period et the value of M [i] no larger than k. Naely, M [i] = k and T[i] = Tj [i] } k. in j [,t] II. The peritent eleent in S et the value of regiter M [i] aller than k. Of the t HLL ketche of tranient{ eleent, the iniu value in thi regiter i exactly k. Naely, M [i] < k and T[i] = in Tj [i] } = k. j [,t]
12 4:2 Y. Zhou et al. To calculate the probability for M [i] = k, we hould firt analyze the probabilitic ditribution for M [i] and T[i] to carry a particular value. Let n [i] be the total nuber of peritent eleent recorded in the ith regiter of the ketch M, and n j [i] be the nuber of tranient eleent in the ith regiter of the ketch T j, j [,t]. Since each peritent eleent in S randoly elect a regiter in M, it ha a probability of to ap into M [i]. Hence n [i] approxiately follow a binoial ditribution, n [i] Binon,, and the probability for M [i] to record ν peritent eleent i Pn n [i] = ν = ν ν n ν. 3 According to the HLL algorith, the rando variable M [i] i the axiu value of ν rando variable that are independently and geoetrically ditributed according to PY > k = 2 k,k,ν >. Thu, the cuulative ditribution function of M [i] under the condition n [i] = ν,ν > i PM [i] k n [i] = ν, ν > = ν. Since = and PM [i] k n [i] = ν, ν = =, the above 2 k conditional cuulative ditribution function i alo atified if ν =. Cobining thee two cae, we have PM [i] k n [i] = ν = 2 k ν, ν, k. 4 Therefore, baed on 3 and 4, the cuulative ditribution function F M [i]k of M [i] i F M [i]k = PM [i] k = PM [i] k n [i] = ν Pn [i] = ν n ν= n = ν n ν= ν n ν ν. 2 k In ot ituation, the peritent pread n i at leat 2 and / i aller than or equal to. 2. Hence, Poion ditribution can be ued to approxiate the binoial ditribution for efficient calculation, Binon,/ Poiλ = n. Thereby, we have F M [i]k n ν= λ ν e λ ν! 2 k ν = e λ n ν= e λ e λ 2 k = e λ 2 k = e n 2 k. λ 2 k ν ν! 6 Siilarly, we calculate the cuulative ditribution function F Tj[i]k n j F Tj[i]k = ν= n j ν e n j 2 k = e n j n ν n j ν ν 2 k 2 k. 7
13 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection 4:3 A we aue that tranient eleent in different period are approxiately independent, the cuulative ditribution function F T[i] k of T[i] i F T[i] k = PT[i] k = PT[i] > k = P in { T j [i] } t > k PT j [,t] j [i] > k j= j= j= t = PTj [i] k t = FTj[i]k. 8 Therefore, the probability P i for the firt cae that M [i] = k i { P i = PM F M [i]k F T[i] k k =, [i] = k PT[i] k = [ FM [i]k F M [i]k ] F T[i] k k. The probability P i for the econd cae that M [i] = k i P i = PM [i] < k PT[i] = k = { k =, F M [i]k [F T[i] k F T[i] k ] k. To u up, the probability for M [i] = k i PM [i] = k = P i +P i = { F M [i]k F T[i] k k =, F M [i]k F T[i] k F M [i]k F T[i] k k. 9 Let a generation function G n,n 2,...,n t,n,k repreent the expreion F M [i]k F T[i] k. Cobining 6, 7 and 8, then we have G n,n 2,...,n t,n,k = F M [i]k F T[i] k t e n 2 k e n j n 2 k. j= 2 Note that the n,n 2,...,n t can be etiated uing the HLL algorith on HLL ketche M, M 2,..., M t, repectively. Thu, they can be treated a contant in the generation function G, o we can iplify G n,n 2,...,n t,n,k to G n,k. We poition a the ubcript of function G becaue the nuber of regiter in each period i deterined by the available eory and i typically a fixed value. Therefore, the probability that the ith regiter in the interection ketch M ha the value k i { G n,k k =, PM [i] = k = G n,k G n 2,k k. In practice, a regiter can only carry a value in a pecific range due to the liited eory ize e.g., bit per regiter. Let H be the threhold, which i the axiu value upper bound that a regiter capacity can record. For intance, if the ize of a regiter i bit, it recording range i fro to 2 = 32 excluive, and the threhold H i 3. Let h be the ize of a regiter, then H = 2 h.
14 4:4 Y. Zhou et al. Conidering the liited regiter ize, we need to odify probability for M H. Aue the regiter i aigned to H when it value i out of bound. Hence, we have H PM [i] = H = PM [i] = k k= = G n,h. Therefore, the probability ditribution function for M [i] to carry a value k in 2 becoe G n,k k =, G n,k G n,k < k < H, PM [i] = k = G n,k k = H, k > H I-HLL Etiator We provide the I-HLL etiator for peritent pread n baed on MLE. To etablih the likelihood function, we firt eaure the nuber of regiter aong the regiter in M that carry the value k, which i denoted by N k. The reaon why we ue N k intead of k a the oberving factor i that the oberving pace ize of N k i equal to H, which i far le than k oberving pace ize. The probability for oberving N k regiter in M carrying the value k i PM [i] = k N k, auing thee regiter are approxiately independent. Hence, the cobined probability for oberving N, N,..., N H under the condition that there are n eleent in the peritent et i H PN,N,...,N H n = α PM [i] = k N k, 24 where α i a contant that equal! N!N!...N H!. The likelihood function for oberving N, N,..., N H with repect to n i Ln N,N,...,N H = α k= H PM [i] = k N k. 2 Taking the logarith on both ize of the likelihood function, we obtain the log baed likelihood function a follow: lnl = lnα+ k= H N k lnpm [i] = k. 26 Taking the partial derivative on log baed likelihood function with repect to n, we obtain lnl n = n lnα+ = H k= H k= k= N k lnpm [i] = k N k lnpm [i] = k n = H k= N k n PM [i] = k. PM [i] = k 27
15 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection 4: The derivative of PM [i] = k with repect to n for an arbitrary value k [,H] i given a follow, PM [i] = k n G n,k k =, n = n G n,k G n,k < k < H, 28 n G n,k k = H, where the partial derivative of G n,k over n i n G n,k n 2 k e 2 k + t j= n j n t e 2 k j= e n j n 2 k. 29 The calculation of n G n,k i given in the Appendix A. The axiu likelihood etiation i to find an etiated peritent pread ˆn that axiize the log likelihood function lnl. Therefore, we obtain an etiator for n : ˆn { } { = arg ax lnl = n n n lnl = }. 3 A a uary, we define a unified function f t to give a foral I-HLL etiator ˆn to eaure the peritent pread n over an arbitrary nuber t of tie period, which i equivalent to 3. Definition 4.. [I-HLL Peritent Spread Etiator] For t 2, a unified function to etiate the peritent pread of a flow i ˆn = f t,m,{m j } j [,t], 3 where i the nuber of regiter in each HLL ketch, M j i the HLL ketch in the jth period j [,t], and M i the interection HLL ketch that equal M M 2 M t. 4.3 Accuracy Analyi We analyze the relative bia and relative tandard error of I-HLL etiator. We denote the value of the ith regiter of M by a rando variable X i, thereby P Xi k = PM [i] = k. Then the expected value and variance of lnp X i k n are µ = E lnp Xi k n σ 2 = Var lnp Xi k n = H k= = H lnp Xi k PXi n k, k= lnp Xi k n 2 PXi k µ 2. Moreover, the new likelihood function for preerving X = k, X = k,, X = k can be written a Ln k,k 2,,k = P Xi k. 33 Note that the above likelihood function i only the original likelihood function ultiplied by a contant value α. Hence, we can till ue the notation L without confuion. Taking the logarith of the likelihood function and the derivative with repect to n, we have E lnl 2 n = E i= i= 32 lnp Xi k i n 2. 34
16 4:6 Y. Zhou et al. Since X,X,,X are roughly independent, auing ψ 2 = n σ 2, then we have E lnl 2 n lnp Xi k i 2 E + n = E i= i,j [, i j E lnp Xi k i n E lnp Xj k j n lnp Xi k i 2 + E lnp Xi k i lnp Xj k j E n n n = σ 2 +µ 2 + µ 2 = µ 2 +σ 2 = µ 2 + ψ n 2, where µ = and ψ 2 i 2 ψ 2 = n 2 G 3 n n,+ 2 G 2 n,h 3 2 2H G n,h + H n G 2 n,k 2G n,k k= 3 2 2k G n,k G n.,k The calculation of µ and ψ 2 can be found in the Appendix B. Hence, the fiher inforation [2] i Iˆn = E lnl n 2 = ψ n 2. According to the ayptotic propertie of axiu likelihood etiation, our etiator i ayptotically unbiaed, and it achieve the Craer-Rao lower bound: Therefore, the relative tandard error i and the ǫ confidence interval for n i VIRTUAL I-HLL ARCHITECTURE. Motivation ˆn d Noraln, Iˆn = Noraln, n 2. 3 ψ2 StdErr ˆn n ψ, 36 ˆn n ±Z ǫ ψ In the deign of our I-HLL etiator, all flow are allocated with eparated and equal-ized HLL ketche to record their eleent in each eaureent period, which bet fit when the flow cardinality i uniforly ditributed. However, any tudie oberve a coon fact that the ditribution of flow cardinalitie i extreely unbalanced in real network, and all percentage of large flow account for a ajority of the Internet traffic alo known a the heavy-tailed ditribution. Without lo of generality, we ue the real network trace captured by the ain gateway of our univerity a an exaple. The ditribution of per-ource flow and per-detination flow are illutrated in Figure 6a and Figure 6b, repectively. Clearly, the vat ajority of flow have all cardinalitie, while only a all nuber of flow have large cardinalitie. The ae trend i oberved in the traffic trace fro CAIDA [23]. Under thi coon obervation of unbalanced ditribution in network traffic data, aintaining one HLL ketch for each flow i not applicable due to the liited ize of on-chip SRAM. The reaon i that, when we don t know which flow are elephant flow in advance, the ize of all HLL ketche for I-HLL etiator hould be configured according to the larget flow cardinalitie in order to achieve reaonably accurate eaureent. Therefore, we have to allocate all HLL ketche with the ae ize that are large enough to accoodate the elephant flow. Hence, for the ajority of flow with all cardinalitie, the high-order bit in their regiter are actually under-utilized a any or even ot of the reain zero,
17 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection 4: Nuber of Flow Nuber of Flow e3 e4 e e6 Flow Cardinality a Per-ource flow e3 e4 e e6 Flow Cardinality b Per-detination flow Fig. 6. Flow cardinality ditribution for different flow which caue a ignificant wate of eory. To reduce the eory wate caued by the uneven flow cardinality ditribution, regiter haring hould be enabled aong the flow to utilize thee unued bit..2 Regiter Sharing and Virtual HLL Sketch Our idea i to enable regiter haring aong HLL ketche of all flow. An exaple i illutrated in Figure 7, where each cell repreent a regiter. The HLL ketche of all flow are no longer eparated. Intead, they hare regiter fro a coon regiter pool, called phyical regiter array A. Each flow peudo-randoly pick a nuber of regiter fro the phyical regiter array A to for it logical data tructure called virtual HLL ketch. Since virtual HLL ketche of all flow hare the ae regiter pool A, elephant flow can borrow eory fro all flow to utilize the unued pace. Virtual HLL Sketch Virtual HLL Sketch 2 Virtual HLL Sketch 3 Size Phyical Regiter array Size Fig. 7. Regiter haring and virtual HLL ketch. Fro above, we deign a novel peritent pread etiation architecture baed on virtual HLL ketche on top of regiter haring, called Virtual Interection HyperLogLog etiator VI-HLL, where each flow i allocated with a virtual HLL ketch of ultiple regiter in each eaureent period. Suppoe the total eory ize of A i M bit, and the ize of each regiter i h bit. So the nuber of regiter in A i = M h. Each virtual HLL ketch i configured a unified ize that i large enough to accoodate all flow. For each flow dt, we randoly elect regiter fro A to for it virtual HLL ketch A dt. The
18 4:8 Y. Zhou et al. Table. Notation A a phyical array of regiter A j a phyical regiter array of period j nuber of regiter in phyical regiter array A dt virtual HLL ketch of flow dt nuber of regiter ued by virtual HLL ketch H i dt hah function that ap the ith regiter of A dt to A n nuber of peritent eleent of flow dt ˆn an etiation of n n nuber of peritent eleent in A dt ˆn an etiation of n n u nuber of peritent eleent in A ˆn u an etiation of n u ith regiter in A dt, denoted by A dt [i], can be elected fro A a follow, A dt [i] = A[H i dt], i <, 38 where H i i a hah function whoe range i [,. The hah function H i can be ipleented uing one ater hah function H, H i dt = Hdt R[i], i <, 39 where H i a hah function whoe range i [,, i the XOR operator, and R i an array of rando eed. In the next ubection, we will introduce our VI-HLL architecture to etiate the peritent pread iultaneouly for ultiple flow. The architecture include two coponent; one for recording flow eleent in A, and the other for etiating the peritent pread for an arbitrary flow dt. The frequently ued notation are uarized in Table for quick reference..3 Record Flow Eleent in A In each tie period, a regiter array A of regiter i ued to record eleent inforation of all flow. At the beginning of each period, all regiter of A are initialized to zero. In technical dicuion below, we again conider per-detination flow through a router that eaure the ditinct nuber of ource addree in each flow. When a packet arrive, the router extract it flow label dt and treat the ource addre rc a an eleent of flow dt. The router record the eleent in the flow virtual HLL ketch A dt. To do o, it firt perfor a hah Hrc, whoe binary repreentation i denoted a x. Let p i the leading b b = log 2 bit in x, and q i the reaining bit: p = x x 2...x b, q = x b+ x b Uing the value of p, the router ap the eleent rc of flow dt peudorandoly to a regiter of it virtual HLL ketch A dt [p], and update the value A dt [p] if it current value i aller than ρq, A dt [p] = ax A dt [p],ρq. 4
19 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection 4:9 ALGORITHM 2: Online recording odule for one tie period Initialize a regiter array A of ize with all zero; for package rc, dt do x := Hrc; p := x x 2...x b ; q := x b+ x b+2... ; i := Hdt R[p]; A[i] = ax A[i],ρq ; end return A at the end of the eaureent period Applying 38 and 39, we have A[Hdt R[p]] = ax A[Hdt R[p]],ρq. 4 The online recording odule for one tie period i uarized in Algorith 2. At the end of each eaureent period, the phyical regiter array A will be offloaded fro on-chip SRAM to ain eory of a erver for long-ter torage and offline query. Aue that we have eaured t conecutive tie period, thereby we have t phyical regiter array, which are denoted by A,A 2,...,A t..4 VI-HLL Etiator We decribe our VI-HLL etiator, which ue the equence of phyical regiter array A,A 2,...,A t, to etiate the peritent pread for an arbitrary flow. Conider a flow dt under query, we recontruct it virtual HLL ketch M fro an arbitrary phyical regiter array A, where the ith regiter in virtual HLL ketch ha been apped to the regiter A[H i dt] in A, M[i] = A dt [i] = A[H i dt], i <. So M = A dt [],A dt [],...,A dt [ ] = A[H dt],a[h 2 dt],...,a[h dt]. Since we have t phyical regiter array A,A 2,...,A t, we can recontruct t virtual HLL ketche, denoted a M,M 2,...,M t. Then we have the virtual interection HLL ketch M : M = M M 2 M t. An intuitive ethod i that we can apply our previou I-HLL etiator on M,M 2,...,M t and M in Definition 4., to filter the tranient eleent and etiate the cardinality of peritent eleent in the virtual HLL ketch. However, thi intuitive ethod will caue overetiating proble for the peritent pread n of flow dt. Thi i becaue the virtual HLL ketch of flow dt not only record the peritent eleent belonging to flow dt, but alo contain the peritent eleent coing fro other flow due to the echani of regiter haring. Specifically, if oe of regiter hared with other flow happen to be et by oe peritent eleent of thee flow, then thee regiter will be updated in all virtual HLL ketche M,M 2,...,M t in all t period uch that they are recorded in M. Therefore, the peritent eleent introduced by regiter haring, called noie, caue the overetiation proble when etiating the peritent pread of the flow dt with I-HLL etiator. Our VI-HLL etiator i to reove the noie that coe fro other flow, and give unbiaed peritent pread etiation. Let n be the nuber of peritent eleent of flow dt, n be the nuber of peritent eleent recorded in virtual interection HLL ketch M of flow dt, and n u be the nuber of peritent eleent in phyical interection regiter array A = A A 2 A t. Due to regiter haring, we know that n i the peritent pread n of flow dt plu the noie peritent pread introduced by other flow. Let Y be a rando variable for the nuber of noie peritent pread recorded by the virtual
20 4:2 Y. Zhou et al. ALGORITHM 3: VI-HLL peritent pread etiator for flow dt Input:,, {M j} j [,t] and {A j} j [,t]. Step : Obtain the virtual interection HLL ketch of flow dt: M M M 2 M t. Etiate n in M by Definition 4.: ˆn := f t,m,{m j} j [,t] ; Step 2: Obtain the interection HLL ketch of all flow: A A A 2 A t. Etiate n u in A by Definition 4.: ˆn u := f t,a,{a j} j [,t] ; Step 3: Reove noie and obtain etiation of n by 4: ˆn ˆn u ; ˆn := return the etiated peritent pread ˆn. interection HLL ketch M, then we have Y = n n. 42 To recover n fro virtual HLL ketche of flow dt, we reove uch noie a follow. The total nuber of peritent eleent coing fro other flow i n u n. Fro the view of the flow dt, thee eleent are noie. A we aue that there are any flow and n n u, each noie eleent fro other flow ha approxiately the ae probability to ap into M. Thi probability i equal to due to the rando election of regiter by the virtual HLL ketch fro A regiter. Hence, Y follow a binoial ditribution, Y Binon n,. The expected nuber of noie eleent apped to M i EY = n u n. Therefore, we have En n = EY = n u n. 43 By the law of large nuber in probability theory, if the nuber of i large, the relative variance Var n n En n approache to zero. In thi cae, the expected value En n can be approxiated by an intance value, n n. Hence, we have n n n u n n n n u. 44 Baed on Definition 4., we can obtain accurate etiation ˆn and ˆn u over M and A, repectively. ˆn = f t,m,{m j } j [,t], ˆn u = f t,a,{a j } j [,t]. Therefore, we obtain the etiate for peritent pread n : ˆn = ˆn ˆn u. 4 The VI-HLL etiator for flow dt i uarized in Algorith 3.. Accuracy Analyi We now analyze the relative bia and relative tandard error of our VI-HLL etiator. According to analyi of I-HLL etiator in Section 4.3, we have the following theore.
21 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection 4:2 Theore.. Let n be the nuber of peritent eleent that are apped to the virtual HLL ketch. Suppoe the nuber of regiter i large enough. Then, where ψ i a variance related to and n. Eˆn n Varˆn n 2 StdErr ˆn n ψ 2 ψ 46.. Relative Bia. According to 42, we know that n = n +Y, and Y follow a binoial ditribution of Binon u n,. Cobing Theore., under the condition of Y = l, l [,n u n ], we have and By 47 and 48, we can calculate Eˆn = Eˆn Y = l n = n +l, 47 n PY = l = u n l n u n l= Eˆn Y = l PY = l n u n l= n +l n u n l n u n l. 48 l l n u n l = n +EY = n + n u n. 49 The value of ˆn u i etiated baed on the phyical regiter array A. Therefore, Eˆn u n u. Fro the definition in and etiation forula 4, the relative bia of ˆn i Bia ˆn n = E ˆn Eˆn = n n + n u n n Hence, the VI-HLL etiator ˆn i approxiately unbiaed for n. n Eˆn u n ˆn u n =...2 Relative Standard Error. Next we derive the relative tandard error of ˆn. Under the condition of Y = l, by Theore., we have Siilarly, we have Varˆn Y = l n +l 2 ψ 2 Varˆn u n u 2 ψ 2, 2
The Extended Balanced Truncation Algorithm
 International Journal of Coputing and Optiization Vol. 3, 2016, no. 1, 71-82 HIKARI Ltd, www.-hikari.co http://dx.doi.org/10.12988/ijco.2016.635 The Extended Balanced Truncation Algorith Cong Huu Nguyen
International Journal of Coputing and Optiization Vol. 3, 2016, no. 1, 71-82 HIKARI Ltd, www.-hikari.co http://dx.doi.org/10.12988/ijco.2016.635 The Extended Balanced Truncation Algorith Cong Huu Nguyen
Privacy-Preserving Point-to-Point Transportation Traffic Measurement through Bit Array Masking in Intelligent Cyber-Physical Road Systems
 Privacy-Preerving Point-to-Point Tranportation Traffic Meaureent through Bit Array Making in Intelligent Cyber-Phyical Road Syte Yian Zhou Qingjun Xiao Zhen Mo Shigang Chen Yafeng Yin Departent of Coputer
Privacy-Preerving Point-to-Point Tranportation Traffic Meaureent through Bit Array Making in Intelligent Cyber-Phyical Road Syte Yian Zhou Qingjun Xiao Zhen Mo Shigang Chen Yafeng Yin Departent of Coputer
Image Denoising Based on Non-Local Low-Rank Dictionary Learning
 Advanced cience and Technology Letter Vol.11 (AT 16) pp.85-89 http://dx.doi.org/1.1457/atl.16. Iage Denoiing Baed on Non-Local Low-Rank Dictionary Learning Zhang Bo 1 1 Electronic and Inforation Engineering
Advanced cience and Technology Letter Vol.11 (AT 16) pp.85-89 http://dx.doi.org/1.1457/atl.16. Iage Denoiing Baed on Non-Local Low-Rank Dictionary Learning Zhang Bo 1 1 Electronic and Inforation Engineering
Topic 7 Fuzzy expert systems: Fuzzy inference
 Topic 7 Fuzzy expert yte: Fuzzy inference adani fuzzy inference ugeno fuzzy inference Cae tudy uary Fuzzy inference The ot coonly ued fuzzy inference technique i the o-called adani ethod. In 975, Profeor
Topic 7 Fuzzy expert yte: Fuzzy inference adani fuzzy inference ugeno fuzzy inference Cae tudy uary Fuzzy inference The ot coonly ued fuzzy inference technique i the o-called adani ethod. In 975, Profeor
Fit a Spread Estimator in Small Memory
 Fit a Spread Etimator in Small Memory MyungKeun Yoon Tao Li Shigang Chen Jih-Kwon Peir Department of Computer & Information Science & Engineering Univerity of Florida, Gaineville, FL 36, USA Email: {myoon,
Fit a Spread Etimator in Small Memory MyungKeun Yoon Tao Li Shigang Chen Jih-Kwon Peir Department of Computer & Information Science & Engineering Univerity of Florida, Gaineville, FL 36, USA Email: {myoon,
THE BICYCLE RACE ALBERT SCHUELLER
 THE BICYCLE RACE ALBERT SCHUELLER. INTRODUCTION We will conider the ituation of a cyclit paing a refrehent tation in a bicycle race and the relative poition of the cyclit and her chaing upport car. The
THE BICYCLE RACE ALBERT SCHUELLER. INTRODUCTION We will conider the ituation of a cyclit paing a refrehent tation in a bicycle race and the relative poition of the cyclit and her chaing upport car. The
Ranking DEA Efficient Units with the Most Compromising Common Weights
 The Sixth International Sypoiu on Operation Reearch and It Application ISORA 06 Xiniang, China, Augut 8 12, 2006 Copyright 2006 ORSC & APORC pp. 219 234 Ranking DEA Efficient Unit with the Mot Coproiing
The Sixth International Sypoiu on Operation Reearch and It Application ISORA 06 Xiniang, China, Augut 8 12, 2006 Copyright 2006 ORSC & APORC pp. 219 234 Ranking DEA Efficient Unit with the Mot Coproiing
Scale Efficiency in DEA and DEA-R with Weight Restrictions
 Available online at http://ijdea.rbiau.ac.ir Int. J. Data Envelopent Analyi (ISSN 2345-458X) Vol.2, No.2, Year 2014 Article ID IJDEA-00226, 5 page Reearch Article International Journal of Data Envelopent
Available online at http://ijdea.rbiau.ac.ir Int. J. Data Envelopent Analyi (ISSN 2345-458X) Vol.2, No.2, Year 2014 Article ID IJDEA-00226, 5 page Reearch Article International Journal of Data Envelopent
Conservation of Energy
 Add Iportant Conervation of Energy Page: 340 Note/Cue Here NGSS Standard: HS-PS3- Conervation of Energy MA Curriculu Fraework (006):.,.,.3 AP Phyic Learning Objective: 3.E.., 3.E.., 3.E..3, 3.E..4, 4.C..,
Add Iportant Conervation of Energy Page: 340 Note/Cue Here NGSS Standard: HS-PS3- Conervation of Energy MA Curriculu Fraework (006):.,.,.3 AP Phyic Learning Objective: 3.E.., 3.E.., 3.E..3, 3.E..4, 4.C..,
Preemptive scheduling on a small number of hierarchical machines
 Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Research Article An Extension of Cross Redundancy of Interval Scale Outputs and Inputs in DEA
 Hindawi Publihing Corporation pplied Matheatic Volue 2013, rticle ID 658635, 7 page http://dx.doi.org/10.1155/2013/658635 Reearch rticle n Extenion of Cro Redundancy of Interval Scale Output and Input
Hindawi Publihing Corporation pplied Matheatic Volue 2013, rticle ID 658635, 7 page http://dx.doi.org/10.1155/2013/658635 Reearch rticle n Extenion of Cro Redundancy of Interval Scale Output and Input
24P 2, where W (measuring tape weight per meter) = 0.32 N m
 Ue of a 1W Laer to Verify the Speed of Light David M Verillion PHYS 375 North Carolina Agricultural and Technical State Univerity February 3, 2018 Abtract The lab wa et up to verify the accepted value
Ue of a 1W Laer to Verify the Speed of Light David M Verillion PHYS 375 North Carolina Agricultural and Technical State Univerity February 3, 2018 Abtract The lab wa et up to verify the accepted value
An Exact Solution for the Deflection of a Clamped Rectangular Plate under Uniform Load
 Applied Matheatical Science, Vol. 1, 007, no. 3, 19-137 An Exact Solution for the Deflection of a Claped Rectangular Plate under Unifor Load C.E. İrak and İ. Gerdeeli Itanbul Technical Univerity Faculty
Applied Matheatical Science, Vol. 1, 007, no. 3, 19-137 An Exact Solution for the Deflection of a Claped Rectangular Plate under Unifor Load C.E. İrak and İ. Gerdeeli Itanbul Technical Univerity Faculty
Utilizing Dynamic Properties of Sharing Bits and Registers to Estimate User Cardinalities over Time
 Utilizing Dynaic Propertie of Sharing it and egiter to Etiate Uer Cardinalitie over Tie arxiv:181109126v1 [cds] 22 Nov 2018 Pinghui Wang 1,2, Peng Jia 1, Xiangliang Zhang 3, Jing Tao 1,2,4, Xiaohong Guan
Utilizing Dynaic Propertie of Sharing it and egiter to Etiate Uer Cardinalitie over Tie arxiv:181109126v1 [cds] 22 Nov 2018 Pinghui Wang 1,2, Peng Jia 1, Xiangliang Zhang 3, Jing Tao 1,2,4, Xiaohong Guan
The Features For Dark Matter And Dark Flow Found.
 The Feature For Dark Matter And Dark Flow Found. Author: Dan Vier, Alere, the Netherland Date: January 04 Abtract. Fly-By- and GPS-atellite reveal an earth-dark atter-halo i affecting the orbit-velocitie
The Feature For Dark Matter And Dark Flow Found. Author: Dan Vier, Alere, the Netherland Date: January 04 Abtract. Fly-By- and GPS-atellite reveal an earth-dark atter-halo i affecting the orbit-velocitie
Chapter 2 Sampling and Quantization. In order to investigate sampling and quantization, the difference between analog
 Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Lecture 21. The Lovasz splitting-off lemma Topics in Combinatorial Optimization April 29th, 2004
 18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
Codes Correcting Two Deletions
 1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
MODE SHAPE EXPANSION FROM DATA-BASED SYSTEM IDENTIFICATION PROCEDURES
 Mecánica Coputacional Vol XXV, pp. 1593-1602 Alberto Cardona, Norberto Nigro, Victorio Sonzogni, Mario Storti. (Ed.) Santa Fe, Argentina, Noviebre 2006 MODE SHAPE EXPANSION FROM DATA-BASED SYSTEM IDENTIFICATION
Mecánica Coputacional Vol XXV, pp. 1593-1602 Alberto Cardona, Norberto Nigro, Victorio Sonzogni, Mario Storti. (Ed.) Santa Fe, Argentina, Noviebre 2006 MODE SHAPE EXPANSION FROM DATA-BASED SYSTEM IDENTIFICATION
Problem Set 8 Solutions
 Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Lecture 2 Phys 798S Spring 2016 Steven Anlage. The heart and soul of superconductivity is the Meissner Effect. This feature uniquely distinguishes
 ecture Phy 798S Spring 6 Steven Anlage The heart and oul of uperconductivity i the Meiner Effect. Thi feature uniquely ditinguihe uperconductivity fro any other tate of atter. Here we dicu oe iple phenoenological
ecture Phy 798S Spring 6 Steven Anlage The heart and oul of uperconductivity i the Meiner Effect. Thi feature uniquely ditinguihe uperconductivity fro any other tate of atter. Here we dicu oe iple phenoenological
Section J8b: FET Low Frequency Response
 ection J8b: FET ow Frequency epone In thi ection of our tudie, we re o to reiit the baic FET aplifier confiuration but with an additional twit The baic confiuration are the ae a we etiated ection J6 of
ection J8b: FET ow Frequency epone In thi ection of our tudie, we re o to reiit the baic FET aplifier confiuration but with an additional twit The baic confiuration are the ae a we etiated ection J6 of
Chemistry I Unit 3 Review Guide: Energy and Electrons
 Cheitry I Unit 3 Review Guide: Energy and Electron Practice Quetion and Proble 1. Energy i the capacity to do work. With reference to thi definition, decribe how you would deontrate that each of the following
Cheitry I Unit 3 Review Guide: Energy and Electron Practice Quetion and Proble 1. Energy i the capacity to do work. With reference to thi definition, decribe how you would deontrate that each of the following
Periodic Table of Physical Elements
 Periodic Table of Phyical Eleent Periodic Table of Phyical Eleent Author:Zhiqiang Zhang fro Dalian, China Eail: dlxinzhigao@6.co ABSTRACT Thi i one of y original work in phyic to preent periodic table
Periodic Table of Phyical Eleent Periodic Table of Phyical Eleent Author:Zhiqiang Zhang fro Dalian, China Eail: dlxinzhigao@6.co ABSTRACT Thi i one of y original work in phyic to preent periodic table
AN EASY INTRODUCTION TO THE CIRCLE METHOD
 AN EASY INTRODUCTION TO THE CIRCLE METHOD EVAN WARNER Thi talk will try to ketch out oe of the ajor idea involved in the Hardy- Littlewood circle ethod in the context of Waring proble.. Setup Firt, let
AN EASY INTRODUCTION TO THE CIRCLE METHOD EVAN WARNER Thi talk will try to ketch out oe of the ajor idea involved in the Hardy- Littlewood circle ethod in the context of Waring proble.. Setup Firt, let
Source slideplayer.com/fundamentals of Analytical Chemistry, F.J. Holler, S.R.Crouch. Chapter 6: Random Errors in Chemical Analysis
 Source lideplayer.com/fundamental of Analytical Chemitry, F.J. Holler, S.R.Crouch Chapter 6: Random Error in Chemical Analyi Random error are preent in every meaurement no matter how careful the experimenter.
Source lideplayer.com/fundamental of Analytical Chemitry, F.J. Holler, S.R.Crouch Chapter 6: Random Error in Chemical Analyi Random error are preent in every meaurement no matter how careful the experimenter.
ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION. Xiaoqun Wang
 Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
DIFFERENTIAL EQUATIONS
 Matheatic Reviion Guide Introduction to Differential Equation Page of Author: Mark Kudlowki MK HOME TUITION Matheatic Reviion Guide Level: A-Level Year DIFFERENTIAL EQUATIONS Verion : Date: 3-4-3 Matheatic
Matheatic Reviion Guide Introduction to Differential Equation Page of Author: Mark Kudlowki MK HOME TUITION Matheatic Reviion Guide Level: A-Level Year DIFFERENTIAL EQUATIONS Verion : Date: 3-4-3 Matheatic
On the Use of High-Order Moment Matching to Approximate the Generalized-K Distribution by a Gamma Distribution
 On the Ue of High-Order Moent Matching to Approxiate the Generalized- Ditribution by a Gaa Ditribution Saad Al-Ahadi Departent of Syte & Coputer Engineering Carleton Univerity Ottawa Canada aahadi@ce.carleton.ca
On the Ue of High-Order Moent Matching to Approxiate the Generalized- Ditribution by a Gaa Ditribution Saad Al-Ahadi Departent of Syte & Coputer Engineering Carleton Univerity Ottawa Canada aahadi@ce.carleton.ca
Bayesian Reliability Estimation of Inverted Exponential Distribution under Progressive Type-II Censored Data
 J. Stat. Appl. Pro. 3, No. 3, 317-333 (2014) 317 Journal of Statitic Application & Probability An International Journal http://dx.doi.org/10.12785/jap/030303 Bayeian Reliability Etiation of Inverted Exponential
J. Stat. Appl. Pro. 3, No. 3, 317-333 (2014) 317 Journal of Statitic Application & Probability An International Journal http://dx.doi.org/10.12785/jap/030303 Bayeian Reliability Etiation of Inverted Exponential
15 N 5 N. Chapter 4 Forces and Newton s Laws of Motion. The net force on an object is the vector sum of all forces acting on that object.
 Chapter 4 orce and ewton Law of Motion Goal for Chapter 4 to undertand what i force to tudy and apply ewton irt Law to tudy and apply the concept of a and acceleration a coponent of ewton Second Law to
Chapter 4 orce and ewton Law of Motion Goal for Chapter 4 to undertand what i force to tudy and apply ewton irt Law to tudy and apply the concept of a and acceleration a coponent of ewton Second Law to
Clustering Methods without Given Number of Clusters
 Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Bogoliubov Transformation in Classical Mechanics
 Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Lecture 2 DATA ENVELOPMENT ANALYSIS - II
 Lecture DATA ENVELOPMENT ANALYSIS - II Learning objective To eplain Data Envelopent Anali for ultiple input and ultiple output cae in the for of linear prograing .5 DEA: Multiple input, ultiple output
Lecture DATA ENVELOPMENT ANALYSIS - II Learning objective To eplain Data Envelopent Anali for ultiple input and ultiple output cae in the for of linear prograing .5 DEA: Multiple input, ultiple output
Improving Efficiency Scores of Inefficient Units. with Restricted Primary Resources
 Applied Matheatical Science, Vol. 3, 2009, no. 52, 2595-2602 Iproving Efficienc Score of Inefficient Unit with Retricted Priar Reource Farhad Hoeinzadeh Lotfi * Departent of Matheatic, Science and Reearch
Applied Matheatical Science, Vol. 3, 2009, no. 52, 2595-2602 Iproving Efficienc Score of Inefficient Unit with Retricted Priar Reource Farhad Hoeinzadeh Lotfi * Departent of Matheatic, Science and Reearch
Social Studies 201 Notes for November 14, 2003
 1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
List coloring hypergraphs
 Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
7.2 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 281
 72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
Alternate Dispersion Measures in Replicated Factorial Experiments
 Alternate Diperion Meaure in Replicated Factorial Experiment Neal A. Mackertich The Raytheon Company, Sudbury MA 02421 Jame C. Benneyan Northeatern Univerity, Boton MA 02115 Peter D. Krau The Raytheon
Alternate Diperion Meaure in Replicated Factorial Experiment Neal A. Mackertich The Raytheon Company, Sudbury MA 02421 Jame C. Benneyan Northeatern Univerity, Boton MA 02115 Peter D. Krau The Raytheon
Introduction to Laplace Transform Techniques in Circuit Analysis
 Unit 6 Introduction to Laplace Tranform Technique in Circuit Analyi In thi unit we conider the application of Laplace Tranform to circuit analyi. A relevant dicuion of the one-ided Laplace tranform i found
Unit 6 Introduction to Laplace Tranform Technique in Circuit Analyi In thi unit we conider the application of Laplace Tranform to circuit analyi. A relevant dicuion of the one-ided Laplace tranform i found
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD
 SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
1-D SEDIMENT NUMERICAL MODEL AND ITS APPLICATION. Weimin Wu 1 and Guolu Yang 2
 U-CHINA WORKHOP ON ADVANCED COMPUTATIONAL MODELLING IN HYDROCIENCE & ENGINEERING epteber 9-, Oxford, Miiippi, UA -D EDIMENT NUMERICAL MODEL AND IT APPLICATION Weiin Wu and Guolu Yang ABTRACT A one dienional
U-CHINA WORKHOP ON ADVANCED COMPUTATIONAL MODELLING IN HYDROCIENCE & ENGINEERING epteber 9-, Oxford, Miiippi, UA -D EDIMENT NUMERICAL MODEL AND IT APPLICATION Weiin Wu and Guolu Yang ABTRACT A one dienional
Optimal Coordination of Samples in Business Surveys
 Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Convergence of a Fixed-Point Minimum Error Entropy Algorithm
 Entropy 05, 7, 5549-5560; doi:0.3390/e7085549 Article OPE ACCESS entropy ISS 099-4300 www.dpi.co/journal/entropy Convergence of a Fixed-Point Miniu Error Entropy Algorith Yu Zhang, Badong Chen, *, Xi Liu,
Entropy 05, 7, 5549-5560; doi:0.3390/e7085549 Article OPE ACCESS entropy ISS 099-4300 www.dpi.co/journal/entropy Convergence of a Fixed-Point Miniu Error Entropy Algorith Yu Zhang, Badong Chen, *, Xi Liu,
Copyright 1967, by the author(s). All rights reserved.
 Copyright 1967, by the author(). All right reerved. Permiion to make digital or hard copie of all or part of thi work for peronal or claroom ue i granted without fee provided that copie are not made or
Copyright 1967, by the author(). All right reerved. Permiion to make digital or hard copie of all or part of thi work for peronal or claroom ue i granted without fee provided that copie are not made or
Cryptography and Security Final Exam
 Cryptography and Security Final Exa Solution Serge Vaudenay 17.1.2017 duration: 3h no docuent allowed, except one 2-ided heet of handwritten note a pocket calculator i allowed counication device are not
Cryptography and Security Final Exa Solution Serge Vaudenay 17.1.2017 duration: 3h no docuent allowed, except one 2-ided heet of handwritten note a pocket calculator i allowed counication device are not
Lecture 9: Shor s Algorithm
 Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Relevance Estimation of Cooperative Awareness Messages in VANETs
 Relevance Etiation of Cooperative Awarene Meage in VANET Jakob Breu Reearch and Developent Dailer AG Böblingen, Gerany Eail: jakobbreu@dailerco Michael Menth Departent of Coputer Science Univerity of Tübingen
Relevance Etiation of Cooperative Awarene Meage in VANET Jakob Breu Reearch and Developent Dailer AG Böblingen, Gerany Eail: jakobbreu@dailerco Michael Menth Departent of Coputer Science Univerity of Tübingen
ADAPTIVE CONTROL DESIGN FOR A SYNCHRONOUS GENERATOR
 ADAPTIVE CONTROL DESIGN FOR A SYNCHRONOUS GENERATOR SAEED ABAZARI MOHSEN HEIDARI NAVID REZA ABJADI Key word: Adaptive control Lyapunov tability Tranient tability Mechanical power. The operating point of
ADAPTIVE CONTROL DESIGN FOR A SYNCHRONOUS GENERATOR SAEED ABAZARI MOHSEN HEIDARI NAVID REZA ABJADI Key word: Adaptive control Lyapunov tability Tranient tability Mechanical power. The operating point of
μ + = σ = D 4 σ = D 3 σ = σ = All units in parts (a) and (b) are in V. (1) x chart: Center = μ = 0.75 UCL =
 Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Avoiding Forbidden Submatrices by Row Deletions
 Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Gain and Phase Margins Based Delay Dependent Stability Analysis of Two- Area LFC System with Communication Delays
 Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
LOAD AND RESISTANCE FACTOR DESIGN APPROACH FOR FATIGUE OF MARINE STRUCTURES
 8 th ACE pecialty Conference on Probabilitic Mechanic and tructural Reliability PMC2000-169 LOAD AND REITANCE FACTOR DEIGN APPROACH FOR FATIGUE OF MARINE TRUCTURE Abtract I.A. Aakkaf, G. ACE, and B.M.
8 th ACE pecialty Conference on Probabilitic Mechanic and tructural Reliability PMC2000-169 LOAD AND REITANCE FACTOR DEIGN APPROACH FOR FATIGUE OF MARINE TRUCTURE Abtract I.A. Aakkaf, G. ACE, and B.M.
2FSK-LFM Compound Signal Parameter Estimation Based on Joint FRFT-ML Method
 International Conerence on et eaureent Coputational ethod (C 5 FS-F Copound Signal Paraeter Etiation Baed on Joint FF- ethod Zhaoyang Qiu Bin ang School o Electronic Engineering Univerity o Electronic
International Conerence on et eaureent Coputational ethod (C 5 FS-F Copound Signal Paraeter Etiation Baed on Joint FF- ethod Zhaoyang Qiu Bin ang School o Electronic Engineering Univerity o Electronic
Performance Analysis of Sub-Rating for Handoff Calls in HCN
 I. J. Counication, Network and Syte Science, 29, 1, 1-89 Publihed Online February 29 in SciRe (http://www.scirp.org/journal/ijcn/). Perforance Analyi of Sub-Rating for Handoff Call in HCN Xiaolong WU 1,
I. J. Counication, Network and Syte Science, 29, 1, 1-89 Publihed Online February 29 in SciRe (http://www.scirp.org/journal/ijcn/). Perforance Analyi of Sub-Rating for Handoff Call in HCN Xiaolong WU 1,
LEARNING DISCRIMINATIVE BASIS COEFFICIENTS FOR EIGENSPACE MLLR UNSUPERVISED ADAPTATION. Yajie Miao, Florian Metze, Alex Waibel
 LEARNING DISCRIMINATIVE BASIS COEFFICIENTS FOR EIGENSPACE MLLR UNSUPERVISED ADAPTATION Yajie Miao, Florian Metze, Alex Waibel Language Technologie Intitute, Carnegie Mellon Univerity, Pittburgh, PA, USA
LEARNING DISCRIMINATIVE BASIS COEFFICIENTS FOR EIGENSPACE MLLR UNSUPERVISED ADAPTATION Yajie Miao, Florian Metze, Alex Waibel Language Technologie Intitute, Carnegie Mellon Univerity, Pittburgh, PA, USA
White Rose Research Online URL for this paper: Version: Accepted Version
 Thi i a repoitory copy of Identification of nonlinear ytem with non-peritent excitation uing an iterative forward orthogonal leat quare regreion algorithm. White Roe Reearch Online URL for thi paper: http://eprint.whiteroe.ac.uk/107314/
Thi i a repoitory copy of Identification of nonlinear ytem with non-peritent excitation uing an iterative forward orthogonal leat quare regreion algorithm. White Roe Reearch Online URL for thi paper: http://eprint.whiteroe.ac.uk/107314/
A BATCH-ARRIVAL QUEUE WITH MULTIPLE SERVERS AND FUZZY PARAMETERS: PARAMETRIC PROGRAMMING APPROACH
 Mathematical and Computational Application Vol. 11 No. pp. 181-191 006. Aociation for Scientific Reearch A BATCH-ARRIVA QEE WITH MTIPE SERVERS AND FZZY PARAMETERS: PARAMETRIC PROGRAMMING APPROACH Jau-Chuan
Mathematical and Computational Application Vol. 11 No. pp. 181-191 006. Aociation for Scientific Reearch A BATCH-ARRIVA QEE WITH MTIPE SERVERS AND FZZY PARAMETERS: PARAMETRIC PROGRAMMING APPROACH Jau-Chuan
Microblog Hot Spot Mining Based on PAM Probabilistic Topic Model
 MATEC Web of Conference 22, 01062 ( 2015) DOI: 10.1051/ matecconf/ 2015220106 2 C Owned by the author, publihed by EDP Science, 2015 Microblog Hot Spot Mining Baed on PAM Probabilitic Topic Model Yaxin
MATEC Web of Conference 22, 01062 ( 2015) DOI: 10.1051/ matecconf/ 2015220106 2 C Owned by the author, publihed by EDP Science, 2015 Microblog Hot Spot Mining Baed on PAM Probabilitic Topic Model Yaxin
Fair scheduling in cellular systems in the presence of noncooperative mobiles
 1 Fair cheduling in cellular yte in the preence of noncooperative obile Veeraruna Kavitha +, Eitan Altan R. El-Azouzi + and Rajeh Sundarean Maetro group, INRIA, 2004 Route de Luciole, Sophia Antipoli,
1 Fair cheduling in cellular yte in the preence of noncooperative obile Veeraruna Kavitha +, Eitan Altan R. El-Azouzi + and Rajeh Sundarean Maetro group, INRIA, 2004 Route de Luciole, Sophia Antipoli,
Optimizing Cost-sensitive Trust-negotiation Protocols
 Optimizing Cot-enitive Trut-negotiation Protocol Weifeng Chen, Lori Clarke, Jim Kuroe, Don Towley Department of Computer Science Univerity of Maachuett, Amhert {chenwf, clarke, kuroe, towley}@c.uma.edu
Optimizing Cot-enitive Trut-negotiation Protocol Weifeng Chen, Lori Clarke, Jim Kuroe, Don Towley Department of Computer Science Univerity of Maachuett, Amhert {chenwf, clarke, kuroe, towley}@c.uma.edu
Investment decision for supply chain resilience based on Evolutionary Game theory
 Invetent deciion for upply chain reilience baed on Evolutionary Gae theory Xiaowei Ji(jixw@hut.edu.cn), Haijun Wang Manageent School Huazhong Univerity of Science and Technology Wuhan, Hubei, 4374, China
Invetent deciion for upply chain reilience baed on Evolutionary Gae theory Xiaowei Ji(jixw@hut.edu.cn), Haijun Wang Manageent School Huazhong Univerity of Science and Technology Wuhan, Hubei, 4374, China
s s 1 s = m s 2 = 0; Δt = 1.75s; a =? mi hr
 Flipping Phyic Lecture Note: Introduction to Acceleration with Priu Brake Slaing Exaple Proble a Δv a Δv v f v i & a t f t i Acceleration: & flip the guy and ultiply! Acceleration, jut like Diplaceent
Flipping Phyic Lecture Note: Introduction to Acceleration with Priu Brake Slaing Exaple Proble a Δv a Δv v f v i & a t f t i Acceleration: & flip the guy and ultiply! Acceleration, jut like Diplaceent
Lecture 4 Topic 3: General linear models (GLMs), the fundamentals of the analysis of variance (ANOVA), and completely randomized designs (CRDs)
 Lecture 4 Topic 3: General linear model (GLM), the fundamental of the analyi of variance (ANOVA), and completely randomized deign (CRD) The general linear model One population: An obervation i explained
Lecture 4 Topic 3: General linear model (GLM), the fundamental of the analyi of variance (ANOVA), and completely randomized deign (CRD) The general linear model One population: An obervation i explained
Investigation of application of extractive distillation method in chloroform manufacture
 Invetigation of application of etractive ditillation ethod in chlorofor anufacture Proceeding of uropean Congre of Cheical ngineering (CC-6) Copenhagen, 16-20 Septeber 2007 Invetigation of application
Invetigation of application of etractive ditillation ethod in chlorofor anufacture Proceeding of uropean Congre of Cheical ngineering (CC-6) Copenhagen, 16-20 Septeber 2007 Invetigation of application
Proactive Serving Decreases User Delay Exponentially: The Light-tailed Service Time Case
 Proactive Serving Decreae Uer Delay Exponentially: The Light-tailed Service Time Cae Shaoquan Zhang, Longbo Huang, Minghua Chen, and Xin Liu Abtract In online ervice ytem, the delay experienced by uer
Proactive Serving Decreae Uer Delay Exponentially: The Light-tailed Service Time Cae Shaoquan Zhang, Longbo Huang, Minghua Chen, and Xin Liu Abtract In online ervice ytem, the delay experienced by uer
Social Studies 201 Notes for March 18, 2005
 1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
PHYSICS 211 MIDTERM II 12 May 2004
 PHYSIS IDTER II ay 004 Exa i cloed boo, cloed note. Ue only your forula heet. Write all wor and anwer in exa boolet. The bac of page will not be graded unle you o requet on the front of the page. Show
PHYSIS IDTER II ay 004 Exa i cloed boo, cloed note. Ue only your forula heet. Write all wor and anwer in exa boolet. The bac of page will not be graded unle you o requet on the front of the page. Show
Lecture 17: Frequency Response of Amplifiers
 ecture 7: Frequency epone of Aplifier Gu-Yeon Wei Diiion of Engineering and Applied Science Harard Unierity guyeon@eec.harard.edu Wei Oeriew eading S&S: Chapter 7 Ski ection ince otly decribed uing BJT
ecture 7: Frequency epone of Aplifier Gu-Yeon Wei Diiion of Engineering and Applied Science Harard Unierity guyeon@eec.harard.edu Wei Oeriew eading S&S: Chapter 7 Ski ection ince otly decribed uing BJT
Question 1 Equivalent Circuits
 MAE 40 inear ircuit Fall 2007 Final Intruction ) Thi exam i open book You may ue whatever written material you chooe, including your cla note and textbook You may ue a hand calculator with no communication
MAE 40 inear ircuit Fall 2007 Final Intruction ) Thi exam i open book You may ue whatever written material you chooe, including your cla note and textbook You may ue a hand calculator with no communication
HIGH-THROUGHPUT DUAL-MODE SINGLE/DOUBLE BINARY MAP PROCESSOR DESIGN FOR WIRELESS WAN
 HIGH-THROUGHPUT DUAL-MODE SINGLE/DOUBLE BINARY MAP PROCESSOR DESIGN FOR WIRELESS WAN Chun-Yu Chen Cheng-Hung Lin and An-Yeu (Andy) Wu Graduate Intitute of Electronic Engineering and Departent of Electrical
HIGH-THROUGHPUT DUAL-MODE SINGLE/DOUBLE BINARY MAP PROCESSOR DESIGN FOR WIRELESS WAN Chun-Yu Chen Cheng-Hung Lin and An-Yeu (Andy) Wu Graduate Intitute of Electronic Engineering and Departent of Electrical
Standard Guide for Conducting Ruggedness Tests 1
 Deignation: E 69 89 (Reapproved 996) Standard Guide for Conducting Ruggedne Tet AMERICA SOCIETY FOR TESTIG AD MATERIALS 00 Barr Harbor Dr., Wet Conhohocken, PA 948 Reprinted from the Annual Book of ASTM
Deignation: E 69 89 (Reapproved 996) Standard Guide for Conducting Ruggedne Tet AMERICA SOCIETY FOR TESTIG AD MATERIALS 00 Barr Harbor Dr., Wet Conhohocken, PA 948 Reprinted from the Annual Book of ASTM
Electronic Theses and Dissertations
 Eat Tenneee State Univerity Digital Common @ Eat Tenneee State Univerity Electronic Thee and Diertation Student Work 5-208 Vector Partition Jennifer French Eat Tenneee State Univerity Follow thi and additional
Eat Tenneee State Univerity Digital Common @ Eat Tenneee State Univerity Electronic Thee and Diertation Student Work 5-208 Vector Partition Jennifer French Eat Tenneee State Univerity Follow thi and additional
_10_EE394J_2_Spring12_Inertia_Calculation.doc. Procedure for Estimating Grid Inertia H from Frequency Droop Measurements
 Procedure or Etiating Grid Inertia ro Frequency Droop Meaureent While the exion or inertia and requency droop are well known, it i prudent to rederive the here. Treating all the grid generator a one large
Procedure or Etiating Grid Inertia ro Frequency Droop Meaureent While the exion or inertia and requency droop are well known, it i prudent to rederive the here. Treating all the grid generator a one large
Lecture 7: Testing Distributions
 CSE 5: Sublinear (and Streaming) Algorithm Spring 014 Lecture 7: Teting Ditribution April 1, 014 Lecturer: Paul Beame Scribe: Paul Beame 1 Teting Uniformity of Ditribution We return today to property teting
CSE 5: Sublinear (and Streaming) Algorithm Spring 014 Lecture 7: Teting Ditribution April 1, 014 Lecturer: Paul Beame Scribe: Paul Beame 1 Teting Uniformity of Ditribution We return today to property teting
2.7.2 Limits to Parallelism
 Chapter 2 Exercie 53 The 1990 will find a broader ue of multiproceor a the peed of individual proceor reache the limit of metal interconnection. The highet utainable clock rate for metal interconnection
Chapter 2 Exercie 53 The 1990 will find a broader ue of multiproceor a the peed of individual proceor reache the limit of metal interconnection. The highet utainable clock rate for metal interconnection
Dynamic Behaviour of Timber Footbridges
 Contança RIGUEIRO MSc PhD Student EST-IPCB contança@et.ipcb.pt Dynamic Behaviour of Timber Footbridge Graduated in Civil Engineering in Univ. of Coimbra (1992). MSc, Univ. of Coimbra (1997). João NEGRÃO
Contança RIGUEIRO MSc PhD Student EST-IPCB contança@et.ipcb.pt Dynamic Behaviour of Timber Footbridge Graduated in Civil Engineering in Univ. of Coimbra (1992). MSc, Univ. of Coimbra (1997). João NEGRÃO
1. The F-test for Equality of Two Variances
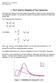 . The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
. The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
Comparing Means: t-tests for Two Independent Samples
 Comparing ean: t-tet for Two Independent Sample Independent-eaure Deign t-tet for Two Independent Sample Allow reearcher to evaluate the mean difference between two population uing data from two eparate
Comparing ean: t-tet for Two Independent Sample Independent-eaure Deign t-tet for Two Independent Sample Allow reearcher to evaluate the mean difference between two population uing data from two eparate
Control Systems Analysis and Design by the Root-Locus Method
 6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
Design spacecraft external surfaces to ensure 95 percent probability of no mission-critical failures from particle impact.
 PREFERRED RELIABILITY PAGE 1 OF 6 PRACTICES METEOROIDS & SPACE DEBRIS Practice: Deign pacecraft external urface to enure 95 percent probability of no miion-critical failure from particle impact. Benefit:
PREFERRED RELIABILITY PAGE 1 OF 6 PRACTICES METEOROIDS & SPACE DEBRIS Practice: Deign pacecraft external urface to enure 95 percent probability of no miion-critical failure from particle impact. Benefit:
Unavoidable Cycles in Polynomial-Based Time-Invariant LDPC Convolutional Codes
 European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
4.5 Evaporation and Diffusion Evaporation and Diffusion through Quiescent Air (page 286) bulk motion of air and j. y a,2, y j,2 or P a,2, P j,2
 4.5 Evaporation and Diffuion 4.5.4 Evaporation and Diffuion through Quiecent Air (page 86) z bul otion of air and j z diffuion of air (a) diffuion of containant (j) y a,, y j, or P a,, P j, z 1 volatile
4.5 Evaporation and Diffuion 4.5.4 Evaporation and Diffuion through Quiecent Air (page 86) z bul otion of air and j z diffuion of air (a) diffuion of containant (j) y a,, y j, or P a,, P j, z 1 volatile
A First Digit Theorem for Square-Free Integer Powers
 Pure Matheatical Science, Vol. 3, 014, no. 3, 19-139 HIKARI Ltd, www.-hikari.co http://dx.doi.org/10.1988/p.014.4615 A Firt Digit Theore or Square-Free Integer Power Werner Hürliann Feldtrae 145, CH-8004
Pure Matheatical Science, Vol. 3, 014, no. 3, 19-139 HIKARI Ltd, www.-hikari.co http://dx.doi.org/10.1988/p.014.4615 A Firt Digit Theore or Square-Free Integer Power Werner Hürliann Feldtrae 145, CH-8004
Suggested Answers To Exercises. estimates variability in a sampling distribution of random means. About 68% of means fall
 Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
CHAPTER 6. Estimation
 CHAPTER 6 Etimation Definition. Statitical inference i the procedure by which we reach a concluion about a population on the bai of information contained in a ample drawn from that population. Definition.
CHAPTER 6 Etimation Definition. Statitical inference i the procedure by which we reach a concluion about a population on the bai of information contained in a ample drawn from that population. Definition.
Theoretical Computer Science. Optimal algorithms for online scheduling with bounded rearrangement at the end
 Theoretical Computer Science 4 (0) 669 678 Content lit available at SciVere ScienceDirect Theoretical Computer Science journal homepage: www.elevier.com/locate/tc Optimal algorithm for online cheduling
Theoretical Computer Science 4 (0) 669 678 Content lit available at SciVere ScienceDirect Theoretical Computer Science journal homepage: www.elevier.com/locate/tc Optimal algorithm for online cheduling
Lecture 8: Period Finding: Simon s Problem over Z N
 Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
Chapter Landscape of an Optimization Problem. Local Search. Coping With NP-Hardness. Gradient Descent: Vertex Cover
 Coping With NP-Hardne Chapter 12 Local Search Q Suppoe I need to olve an NP-hard problem What hould I do? A Theory ay you're unlikely to find poly-time algorithm Mut acrifice one of three deired feature
Coping With NP-Hardne Chapter 12 Local Search Q Suppoe I need to olve an NP-hard problem What hould I do? A Theory ay you're unlikely to find poly-time algorithm Mut acrifice one of three deired feature
m 0 are described by two-component relativistic equations. Accordingly, the noncharged
 Generalized Relativitic Equation of Arbitrary Ma and Spin and Bai Set of Spinor Function for It Solution in Poition, Moentu and Four-Dienional Space Abtract I.I.Gueinov Departent of Phyic, Faculty of Art
Generalized Relativitic Equation of Arbitrary Ma and Spin and Bai Set of Spinor Function for It Solution in Poition, Moentu and Four-Dienional Space Abtract I.I.Gueinov Departent of Phyic, Faculty of Art
IN SUPERVISING the correct operation of dynamic plants,
 1158 IEEE TRANSACTIONS ON CONTROL SYSTEMS TECHNOLOGY, VOL. 14, NO. 6, NOVEMBER 2006 Nonlinear Fault Detection and Iolation in a Three-Tank Heating Syte Raffaella Mattone and Aleandro De Luca, Senior Meber,
1158 IEEE TRANSACTIONS ON CONTROL SYSTEMS TECHNOLOGY, VOL. 14, NO. 6, NOVEMBER 2006 Nonlinear Fault Detection and Iolation in a Three-Tank Heating Syte Raffaella Mattone and Aleandro De Luca, Senior Meber,
Lecture 10 Filtering: Applied Concepts
 Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
CHAPTER 13 FILTERS AND TUNED AMPLIFIERS
 HAPTE FILTES AND TUNED AMPLIFIES hapter Outline. Filter Traniion, Type and Specification. The Filter Tranfer Function. Butterworth and hebyhev Filter. Firt Order and Second Order Filter Function.5 The
HAPTE FILTES AND TUNED AMPLIFIES hapter Outline. Filter Traniion, Type and Specification. The Filter Tranfer Function. Butterworth and hebyhev Filter. Firt Order and Second Order Filter Function.5 The
Answer keys. EAS 1600 Lab 1 (Clicker) Math and Science Tune-up. Note: Students can receive partial credit for the graphs/dimensional analysis.
 Anwer key EAS 1600 Lab 1 (Clicker) Math and Science Tune-up Note: Student can receive partial credit for the graph/dienional analyi. For quetion 1-7, atch the correct forula (fro the lit A-I below) to
Anwer key EAS 1600 Lab 1 (Clicker) Math and Science Tune-up Note: Student can receive partial credit for the graph/dienional analyi. For quetion 1-7, atch the correct forula (fro the lit A-I below) to
SIMM Method Based on Acceleration Extraction for Nonlinear Maneuvering Target Tracking
 Journal of Electrical Engineering & Technology Vol. 7, o. 2, pp. 255~263, 202 255 http://dx.doi.org/0.5370/jeet.202.7.2.255 SIMM Method Baed on Acceleration Extraction for onlinear Maneuvering Target Tracking
Journal of Electrical Engineering & Technology Vol. 7, o. 2, pp. 255~263, 202 255 http://dx.doi.org/0.5370/jeet.202.7.2.255 SIMM Method Baed on Acceleration Extraction for onlinear Maneuvering Target Tracking
4 Conservation of Momentum
 hapter 4 oneration of oentu 4 oneration of oentu A coon itake inoling coneration of oentu crop up in the cae of totally inelatic colliion of two object, the kind of colliion in which the two colliding
hapter 4 oneration of oentu 4 oneration of oentu A coon itake inoling coneration of oentu crop up in the cae of totally inelatic colliion of two object, the kind of colliion in which the two colliding
SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lectures 41-48)
 Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
PHY 171 Practice Test 3 Solutions Fall 2013
 PHY 171 Practice et 3 Solution Fall 013 Q1: [4] In a rare eparatene, And a peculiar quietne, hing One and hing wo Lie at ret, relative to the ground And their wacky hairdo. If hing One freeze in Oxford,
PHY 171 Practice et 3 Solution Fall 013 Q1: [4] In a rare eparatene, And a peculiar quietne, hing One and hing wo Lie at ret, relative to the ground And their wacky hairdo. If hing One freeze in Oxford,
MAE140 Linear Circuits Fall 2012 Final, December 13th
 MAE40 Linear Circuit Fall 202 Final, December 3th Intruction. Thi exam i open book. You may ue whatever written material you chooe, including your cla note and textbook. You may ue a hand calculator with
MAE40 Linear Circuit Fall 202 Final, December 3th Intruction. Thi exam i open book. You may ue whatever written material you chooe, including your cla note and textbook. You may ue a hand calculator with
TP A.30 The effect of cue tip offset, cue weight, and cue speed on cue ball speed and spin
 technical proof TP A.30 The effect of cue tip offet, cue weight, and cue peed on cue all peed and pin technical proof upporting: The Illutrated Principle of Pool and Billiard http://illiard.colotate.edu
technical proof TP A.30 The effect of cue tip offet, cue weight, and cue peed on cue all peed and pin technical proof upporting: The Illutrated Principle of Pool and Billiard http://illiard.colotate.edu
