Privacy-Preserving Point-to-Point Transportation Traffic Measurement through Bit Array Masking in Intelligent Cyber-Physical Road Systems
|
|
|
- Arline Nicholson
- 5 years ago
- Views:
Transcription
1 Privacy-Preerving Point-to-Point Tranportation Traffic Meaureent through Bit Array Making in Intelligent Cyber-Phyical Road Syte Yian Zhou Qingjun Xiao Zhen Mo Shigang Chen Yafeng Yin Departent of Coputer & Inforation Science & Engineering Departent of Civil and Coatal Engineering Univerity of Florida, Gaineville, FL 36, USA Abtract Traffic eaureent i a critical function in tranportation engineering. We conider privacy-preerving point-to-point traffic eaureent in thi paper. We eaure the nuber of vehicle traveling fro one geographical location to another by taking advantage of capabilitie provided by the intelligent cyber-phyical road yte that enable autoatic collection of traffic data. The challenge i to allow the collection of aggregate point-to-point data while preerving the privacy of individual vehicle. We propoe a novel eaureent chee which utilize bit array to collect data and adopt axiu likelihood etiation MLE) to obtain the eaureent reult. Both atheatical proof and iulation deontrate the practicality and calability of our chee. Keyword-tranportation traffic eaureent, privacy, cyber-phyical yte, axiu likelihood etiation I. INTRODUCTION Traffic eaureent i a critical function in tranportation engineering []. There are two categorie of traffic tatitic, point tatitic and point-to-point tatitic. Point tatitic tell the nuber of vehicle travering a pecific point location). Variou prediction odel have been propoed to etiate the [], [3]. Point-to-point tatitic decribe the nuber of vehicle traveling between two point. They are eential input to a variety of tudie including etiation of traffic link flow ditribution a part of invetent plan, calculation of road expoure rate a part of afety analyi, and characterization of turning oveent at interection for ignal tiing deterination. While pointto-point tatitic ay be inferred fro point data [4], little work ha been done on direct eaureent of point-topoint traffic particularly when driver location privacy i of concern. Thi paper conider the iportant proble of privacypreerving point-to-point tranportation traffic eaureent. The et of vehicle traveling fro one geographical location to another i odeled a a traffic flow, whoe ize i the nuber of vehicle in the et. To enable autoatic collection of traffic data, we take advantage of intelligent cyber-phyical road yte CPRS), which integrate the latet technologie in wirele counication and on-board coputer proceing to iprove afety and efficiency of tranportation yte [5] [6]. For exaple, IntelliDrive [7] fro USDOT [8] enviion a nationwide yte where vehicle counicate with roadide equipent RSE) in real tie via dedicated hort range counication. In CPRS, vehicle ay report their ID to RSE when they pa by, and that inforation can be ued by the authority to eaure traffic flow. However, if a vehicle keep tranitting it unique identifier to RSE, that inforation will enable other to track it entire oving hitory. A ore and ore people are concerned about their location privacy, the degree of privacy that a chee preerve will directly affect it applicability. To addre the iue of privacy, there are any iue that we need to conider: Firt of all, we need a criteria to tell what i good privacy and what i not. In thi paper, we capture the eence of privacy in traffic flow eaureent, and quantify it a a probability that a potential tracker cannot identify any trace of any vehicle. Secondly, given that criteria, how can we preerve the optial privacy? Apparently, the better the privacy preervation i, the ore applicable the eaureent chee will be. Furtherore, to protect the privacy of vehicle, only randoized and deidentified inforation i collected. We propoe a novel chee for privacy-preerving traffic flow eaureent. The new chee utilize bit array to encode tranportation traffic data ent fro vehicle to RSE, and adopt the axiu likelihood etiation MLE) to obtain the eaureent reult. The eaureent accuracy a well a privacy preerved by our propoed chee are analyzed through both atheatical proof and iulation, which deontrate the applicability of our chee. The ret of the paper i organized a follow: Section II give the yte and threat odel, the proble tateent, and the perforance etric that we conider. Section III dicue oe traightforward olution and their liitation, followed by Section IV which preent our novel olution and it perforance analyi. Section V how the iulation reult. Section VI uarize the related work. Finally, Section VII draw the concluion. A. Syte Model II. PRELIMINARIES We conider an intelligent cyber-phyical road yte involving three group of entitie: vehicle, roadide
2 equipent RSE), and a central erver. Each vehicle ha a unique ID, e.g., it VIN, or other nuber choen peranently or teporarily. Each RSE alo ha a unique ID. Both vehicle and RSE are equipped with coputing and counication capabilitie, e.g., on-board coputer chip and counication odule. Vehicle counicate with RSE in real tie via dedicated hort range counication DSRC) [8]. RSE are connected to the central erver through wired or wirele ean. They collect inforation fro vehicle and tranfer it to the central erver for further proceing at the end of each eaureent period. B. Proble Stateent We define a traffic flow between one RSE-equipped location and another RSE-equipped location a the et of vehicle traveling between the two location during a eaureent period. The traffic flow ize i the nuber of vehicle in the et. The proble i to eaure the ize of traffic flow in a road yte between all pair of location where RSE are intalled while protecting vehicle privacy. To achieve the privacy-preerving end, we need a olution in which a vehicle never tranit any unique identifier. Ideally, the inforation tranitted by the vehicle to the RSE look totally rando, out of which neither the identity nor the trajectory of any vehicle can be pried with high probability. We aue that a pecial MAC protocol i ued to upport privacy preervation uch that the MAC addre of a vehicle i not fixed. Vehicle ay pick an MAC addre randoly fro a large pace for one-tie ue. C. Threat Model We aue a ei-honet odel for the RSE. On the one hand, all RSE are fro trutworthy authoritie, which can be enforced by authentication baed on PKI. Each vehicle i pre-intalled with the public key of the truted third partie. Each RSE ut have a public-key certificate fro the. It broadcat the certificate in each query that it end out. When receiving a query, the vehicle verifie the certificate, and then ue the RSE public key to authenticate it. On the other hand, the authoritie ay exploit the inforation collected by RSE to track individual vehicle when they need to do o. For intance, if a vehicle tranit any unique identifier upon each query, that identifier can be exploited for tracking purpoe. Note that there are alo other way to track a vehicle, for exaple, tailgating the vehicle, or etting caera near RSE to take photo and uing iage proceing to recognize it. Thee ethod are beyond the cope of thi paper. In thi paper, we focu on preventing tracking caued by the traffic flow eaureent chee itelf. D. Perforance Metric In thi paper, we ue three perforance etric to evaluate a traffic flow eaureent chee: eaureent accuracy, coputation overhead, and preerved privacy. ) Meaureent Accuracy: Let n c be the true ize of a traffic flow between a pair of location and ˆn c be the correponding eaured reult. We pecify the eaureent accuracy through a paraeter β which atifie the following requireent: the probability for n c to fall into the interval [ˆn c β), ˆn c + β)] ut be at leat α, where α i a pre-deterined paraeter in the range of [, ]. Given α, a aller value of β ean better eaureent reult. For exaple, when α = 95%, a olution with β =.5 i better than a olution with β =. becaue the forer enure the eaured traffic flow ize ha a probability of 95% to be within ±5% of the true value, while the latter only enure the eaured reult to be within ±% of the true value. ) Coputation Overhead: We conider the coputation overhead for vehicle, RSE, and the central erver. For vehicle, we eaure the coputation overhead for each vehicle per RSE en route. For RSE, we eaure the coputation overhead for each RSE per paing vehicle. For the central erver, we eaure the coputation overhead to copute the traffic flow ize of per pair of RSE. 3) Preerved Privacy: We capture the eence of privacy preervation in point-to-point tranportation traffic eaureent, which i allowing the tracker only a liited chance to identify any partial or full trajectory of any vehicle. Accordingly, we quantify the privacy of a chee through a paraeter p which atifie the following requireent: the probability for any trace of any vehicle not to be identified ut be at leat p, where a trace of a vehicle i a pair of RSE it ha paed by. A larger value of p ean better privacy. Intuitively, a chee with p =.5 i better than one with p =. in ter of privacy becaue the latter give the tracker a better chance to link trace of a vehicle to obtain it trajectory ince it allow the trace to be identified with a higher probability, i.e., p. III. STRAIGHTFORWARD APPROACHES AND THEIR LIMITATIONS To eaure the traffic flow ize between all pair of RSE in the road yte, a traightforward approach i aking vehicle report their ID to all RSE that they pa by. RSE collect the ID fro the paing vehicle. At the end of each eaureent period, all RSE end their collected ID et to the central erver, which then eaure the traffic flow ize between each pair of RSE by iply coparing the two correponding ID et: if a vehicle ID appear in both ID et, then the vehicle ut have paed both RSE. Thu, the nuber of ID that appear in both ID et equal the true traffic flow ize between the two correponding RSE. However, thi iple approach lead to eriou privacy breaching a it reveal vehicle identitie along the way. A natural follow-up thinking i aking vehicle report their encrypted ID EID) to the RSE en route. The central erver will copute traffic flow ize baed on
3 the EID et collected by RSE. To prevent the tracker fro uing fixed EID to identify vehicle, each vehicle ha any EID encrypted by different key. However, the EID of a vehicle ut atify the following property: they will produce the ae reult after a certain procedure of coputation, allowing the central erver to find out they repreent the ae vehicle. In thi chee, although vehicle true identitie are hidden, trace of each vehicle are till revealed and can be linked to obtain it full trajectory. An alternative approach i having the RSE broadcat their ID RID). Each vehicle will record the RID of all RSE it ha paed by, and tranit the to every RSE that it pae in the future. RSE collect thoe RID fro paing vehicle, and end the to the central erver at the end of each eaureent period. To copute the ize of a traffic flow between two RSE, R x and R y, the central erver iply goe through the RID et collected by R y R x ), and count the nuber of tie that R x R y ) appear in thi et. Thi i the ize of the directional traffic flow fro R x R y ) to R y R x ). The undirectional traffic flow between R x and R y i the u of both directional flow ize. Clearly, thi approach alo reveal a vehicle trajectory in the for of a lit of RID ent to each RSE that it pae. IV. PRIVACY PRESERVING POINT-TO-POINT TRANSPORTATION TRAFFIC MEASUREMENT In thi ection, we preent our novel chee for privacy preerving point-to-point tranportation traffic eaureent. There are two phae for each eaureent period: online coding and offline decoding. Online coding i an interaction between vehicle and RSE, where neceary inforation for traffic flow eaureent are ecurely collected. Later in the offline decoding phae, the central erver will ue thoe inforation to copute traffic flow ize. In the following, we firt illutrate the two eaureent phae, and then evaluate our chee with repect to the three perforance etric decribed in Section II-D. A. Online Coding Phae In our chee, each RSE R x aintain a counter n x, which keep track of the total nuber of vehicle paing by during the current eaureent period. R x alo aintain a bit array B x with a fixed length > ) to ak vehicle identitie. At the beginning of each eaureent period, n x and all the bit in B x are et to zero. In addition, each vehicle v ha a logical bit array LB v, which conit of < < ) bit randoly elected fro B x. The indice of thee bit B x are Hv K v X[]),..., Hv K v X[ ]), where i the bitwie XOR, H...) i a hah function whoe range i [, ), X i an integer array of randoly choen The identity of a vehicle ay be revealed by a photograph triggered by the vehicle ruhing a red light or by a police car topping the vehicle. When the identify i cobined by the trajectory tranitted by the vehicle, the entire traveling path of the driver will be revealed. contant whoe purpoe i to arbitrarily alter the hah reult, and K v i the private key of v whoe purpoe i to protect the privacy of it logical bit array. The online coding phae i quite iple. RSE broadcat querie in pre-et interval e.g., once a econd), enuring that each paing vehicle receive at leat one query and eanwhile giving enough tie for the vehicle to reply. Colliion can be reolved through well-etablihed CSMA or TDMA protocol, which are not the focu of thi paper. Every query that an RSE end out include the RSE RID and it public-key certificate. Suppoe a vehicle, whoe ID i v, receive a query fro an RSE, whoe ID i R x. The vehicle firt verifie the certificate, and then ue the RSE public key to authenticate the RSE. After verifying that R x i fro the trutworthy authority, the vehicle v will randoly elect a bit fro it logical bit array LB v by coputing an index b = Hv K v X[HR x ) od ]). The vehicle v then end the reulting index b to the RSE R x. Upon receiving the index b, R x will firt increae it counter n x by, and then et the bth in B x to : B x [Hv K v X[HR x ) od ])] =. ) B. Offline Decoding Phae At the end of each eaureent period, all RSE will end their counter and bit array to the central erver, which then perfor the offline eaureent. We eploy the axiu likelihood etiation MLE) [9] to eaure the ize of traffic flow baed on the counter and bit array. Suppoe the et of vehicle that pa RSE R x R y ) i denoted a S x S y ) with cardinality S x = n x S y = n y ). Clearly, the et of vehicle that pa both RSE R x and R y i S x S y. Denote it cardinality a n c, which i the value that we want to eaure. Furtherore, denote by S the ubet of vehicle in S x S y that happen to et the ae bit in B x and B y, where B x and B y are the bit array at R x and R y, repectively. Let n o be the cardinality of S, i.e., n o = S. Clearly, S S x S y and n o n c. For any vehicle, it ha the ae probability to et any bit in it -bit logical bit array. A a reult, the probability for an arbitrary vehicle v fro S x S y to elect the ae bit in both B x and B y i =. Therefore, the nuber of uch vehicle, n o, i binoially ditributed according to Bn c, ). Accordingly, the probability for n o = z z n c ) i nc P n o = z) = z ) )z )nc z. ) Given the counter n x and n y, and bit array B x and B y, we eaure n c a follow: Firt, take a bitwie AND of B x and B y, and denote the reulting bit array a B c. Naely, B c [i] = B x [i] B y [i], i [, ]. 3) Calculate the nuber of in B c and denote it a U c. For an arbitrary bit b in B c, it i if and only if the following
4 two condition are atified: Firt, it i not choen by any vehicle in S. If b i choen by a vehicle v S, we know that bit b in B x and B y are both et to hence bit b in B c i alo ). Since each vehicle in S x S y ha probability to et bit b to, the probability for the vehicle not to chooe bit b i. There are n o vehicle in S. Therefore, the probability for bit b not choen by any vehicle in S i q = )no. 4) Second, it i either not choen by any vehicle in S x S or not choen by any vehicle in S y S. Otherwie, bit b in both B x and B y will be et to hence bit b in B c i alo ). Siilar to the previou analyi, we can obtain that the probability for bit b not choen by any vehicle in S x S i )nx no, and the probability for bit b not choen by any vehicle in S y S i )ny no. Therefore, the probability for the econd condition to be atified i q = )nx no ) )ny no ) = )nx no + )ny no )nx+ny no. 5) Cobining the above analyi, the conditional probability for bit b in B c to reain given n o = z i q q, naely, qn c n o = z) = )nx + )ny )nx+ny z. 6) Given qn c n o = z) and the ditribution of n o, the overall probability qn c ) for bit b in B c to reain i qn c ) = = n c z= n c qn c n o = z) P n o = z) qn c n o = z) z= ) nc z )z )nc z = )nx + )ny )nx+ny + ) ) ) nc. 7) Since each bit in B c ha a probability qn c ) to be, and the oberved nuber of bit in B c i U c, the likelihood function for thi obervation to occur i: L = qn c )) Uc qn c )) Uc. 8) We follow the tandard proce of MLE to find the optial value of n c that axiize the likelihood function in 8): ˆn c = arg ax n c {L} 9) To find ˆn c, we take logarith on both ide of 8): ln L = U c ln qn c ) + U c ) ln qn c )). ) Take the firt order derivative of ), we have: d ln L Uc = dn c qn c ) U ) c q n c ), ) qn c ) where q n c ) can be coputed fro 7) a follow: q n c ) = dqn c) dn c = )nx+ny + ) ) ) nc ln + ) ) ). ) To copute ˆn c, we et the right ide of ) to : Uc qn c ) U ) c q n c ) =. 3) qn c ) Oberve fro ) that q n c ) cannot be when > and >. Therefore, we have: U c qn c ) U c =. 4) qn c ) Subtituting 7) to 4), we obtain the MLE etiator ˆn c of the deired traffic flow ize n c a follow: ˆn c = ln + )nx )ny Uc ) n x + n y ) ln ) ) ln C. Meaureent Accuracy + ) ) 5) In the previou ubection, we give the MLE etiator ˆn c of the traffic flow ize n c. Now we analyze it eaureent accuracy. According to the tandard theory of MLE [], when the value of, n x, and n y are large enough, the eaured traffic flow ize approxiately follow the noral ditribution below: ˆn c Nor n c, ), 6) Iˆn c ) where Iˆn c ) i the fiher inforation of L, defined a: [ d ] ln L Iˆn c ) = E. 7) dn c According to ), we copute the econd-order derivative of ln L in the following: d ln L dn = U c q n c ) c q U c) q ) n c ) n c ) qn c )) q n c ) Uc + qn c ) U ) c q n c ) ln C, 8) qn c )
5 where C = + ) ) and q n c ) i given in ). For an arbitrary bit b in B c, it ha probability qn c ) to reain. U c i the nuber of in B c. Therefore, U c follow a binoial ditribution B, qn c )). Accordingly, EU c ) = qn c ). 9) Subtituting 8) and 9) to copute 7), we have q n c ) Iˆn c ) = + ) q n c ) q n c ) qn c ) qn c ) q n c )) = qn c ) qn c )), ) According to 6), the variance of ˆn c i V arˆn c ) = Iˆn c ) = qn c) qn c )) q n c )). ) Therefore, the confidence interval of our eaureent i qn c ) qn c )) ˆn c ± Z α q n c )), ) where α i the confidence level paraeter and Z α i the α percentile for the tandard Gauian ditribution []. D. Privacy Guarantee Next, we evaluate the preerved privacy of our eaureent chee. Note that in our chee, the only inforation that a vehicle v ever tranit to an RSE en route i an index of a bit b randoly elected fro it - bit logical bit array, LB v. Fro the tracker point of view, it can only identify the trace of a vehicle paing by two RSE R x and R y through the obervation of the bit that are et to in both B x and B y ; thee bit will be in B c. Therefore, the preerved privacy of our chee i actually a conditional probability which tell to what degree an oberved in B c doe not repreent a coon vehicle paing by both R x and R y. We derive thi conditional probability in the following. Firtly, conider the probability for the tracker to oberve an arbitrary bit, b, to be et to in both B x and B y event A), P A). Obviouly, the probability P A) equal inu qn c ) given our analyi in Section IV-B: P A) = )nx )ny + )nx+ny + ) ) ) nc 3) Secondly, conider the conditional probability for uch a bit, b, to not repreent a coon vehicle paing both R x and R y event E), P E A). Thi i the privacy p that we want to derive. Note that event E happen if and only if bit b in B x i et only by vehicle paing only RSE R x i.e., in et S x S y ), and bit b in B y i et only by vehicle paing only RSE R y i.e., in et S y S x ). Denote thee two event a E x and E y, repectively. There are n x n y ) vehicle paing R x R y ), and n c vehicle aong the pa both R x and R y. Since each vehicle ha a probability to et bit b to, the probability for E x E y ) to happen i: P E x ) = )nx nc ) )nc, 4) P E y ) = )ny nc ) )nc. 5) Cobining the above analyi, we have the forula for the preerved privacy of our chee a follow: p = P E A) = P E x) P E y ) P A) = P A) )nc )nx ) )nc )ny ), 6) where P A) i given in 3). Oberve that there are paraeter, and, that deterine the value of P E A). Aong the, only appear in the denoinator P A), and it influence P E A) through varying the value of P A). influence both the denoinator and the nuerator. In the following, we conider the influence of and on P E A) by firt exaining the influence of on P A) hence that on P E A)) under variou value of, and then analyzing how deterine the value of P E A) given value for. ) Influence of on P A): To exaine how effect P A), we take partial derivative of 3) with repect to P A) = )nx+ny n c ) Cnc. 7) P A) Clearly, <. Therefore, with the increent of, the value of P A) decreae, and in turn, the value of P E A) increae. In other word, the preerved privacy will be better with a larger value of. The nuerical reult are hown in the firt two plot of Figure where n x = n y = n = 5,, n c = 5,, and =, 5,, correponding to three curve in each plot. Clearly, a increae, the probability P A) decreae. Another obervation fro the nuerical reult give that when > 5, the difference in probability P A) under different becoe quite all. For intance, when [5n, n], the difference in P A) when and = i aller than.5 ee the two lower curve in the econd plot of Figure ). When n >, that difference becoe negligible. Therefore, when we analyze the effect of on P E A) in the following ubection, and et up the paraeter for our iulation, we only conider the cae when =, 5,, with etablihed undertanding that larger value of will only ake negligible difference.
6 Probability PA) = = 5 5 f = / n Probability PA) = = 5 5 f = / n Privacy, p = PE A) =. = 5 5 f = / n Figure. n x = n y = n = 5,, n c = 5, ; Firt Plot: probability P A) when varie fro.n to n, controlled by different =, 5, ; Second Plot: a zoo-in of the firt plot when varie fro 5n to n; Third Plot: probability P E A) when varie fro.n to n, controlled by different =, 5,. ) Influence of on P E A): To exaine the effect of on P E A), we take the partial derivative of 6) with repect to and obtain the following P E A) P E) = P A) P A) P E) P A) 8) where P E) = P E x ) P E y ). P E x ) and P E y ) are given in 4) and 5), repectively. Therefore, the partial derivative of P E) with repect to i [ n c )nc n c + n x ) )nc+nx n c + n y ) + n )nc+ny x + n y ) ] )nx+ny P E) = 3 9) In addition, fro 3), we can copute the derivative of P A) with repect to : P A) = [ n x )nx n y )ny + )nx+ny C nc n x + n y ) ) + ln C )] 3) P E) P A) Both and are negative, eaning that both P E) and P A) decreae with the increent of. Intuitively, increaing give each vehicle a aller chance to et an arbitrary bit, b. Hence, P E) and P A) alo drop. The effect that ha on P E A) are twofold: on the one hand, the increent of decreae the denoinator P A), which pull the privacy up; on the other hand, the increent of decreae the nuerator P E), which drag the privacy down. The cobination of thee two effect give that the partial derivative of P E A) with repect to can be poitive, negative, or, according to 8). Alo, given, we can chooe an optial to achieve the bet degree of privacy. The optial i obtained by etting the right ide of 8) to. The third plot of Figure how the nuerical reult for the preerved privacy under different when n x = n y = n = 5,, n c = 5,, and =, 5,. Clearly, along each curve controlled by ), there i an optial value of that give the optial privacy, p. For intance, = 3.8n give the optial privacy p =.766 when =. Another obervation i, when i large 5 or ), there alway exit a ooth interval of near it extree point that can achieve coparable privacy a the optial. For exaple, when =, the value of within the interval [3.8n, 3.n] achieve privacy that i within 5% of the optial privacy.766. Thi ooth interval for privacy allow u to adjut the value of to achieve better eaureent reult while preerving coparable privacy. E. Coputation Overhead In our chee, when a vehicle v pae an RSE R x, the vehicle v only need to copute two hahe to obtain an index of a rando bit in it logical array LB v, and the RSE R x only need to et bit in it bit array B x, a decribed in Section IV-A. Therefore, the coputation overhead for the vehicle per RSE a well a the RSE per vehicle are both O). A for the central erver, in order to copute a traffic flow ize between a pair of location, it only need to do a bitwie AND over two -bit bit array, count the nuber of in the reulting bit array, and ue 5) to copute the MLE etiator. Therefore, the coputation overhead for the central erver i alo O). V. SIMULATION In thi ection, we evaluate the perforance of our eaureent chee through iulation. The iulation are perfored under five yte paraeter, n x, n y, n c,, and. For a pair of RSE, R x and R y, n x n y ) i the nuber of vehicle paing by R x R y ). There are n c vehicle paing both R x and R y, which ean the true traffic flow ize i n c. i the nuber of bit that each vehicle chooe in it logical bit array, and i the nuber of bit in the bit array of each RSE. In the iulation, we chooe the five paraeter a follow: n x = n y = n = 5,,,, or 5,, and n c varie fro %n to 5%n, with tep ize of.%n; =, 5,, and
7 .5 x 4 = x 4.5 x x 4.5 x 4 = x 4 Figure. Meaureent accuracy controlled by, n x = n y = n = 5,, n c = [.n,.5n]. The x-axi how true traffic flow ize, and the y-axi how the correponding eaured traffic flow ize. Firt Plot: = ; Second Plot: ; Third Plot: =. 5 x 4 = x 4 5 x x 4 5 x 4 = x 4 Figure 3. Meaureent accuracy controlled by, n x = n y = n =,, n c = [.n,.5n]. The x-axi how true traffic flow ize, and the y-axi how the correponding eaured traffic flow ize. Firt Plot: = ; Second Plot: ; Third Plot: =..5 x 5 = x 5.5 x x 5.5 x 5 = x 5 Figure 4. Meaureent accuracy controlled by, n x = n y = n = 5,, n c = [.n,.5n]. The x-axi how true traffic flow ize, and the y-axi how the correponding eaured traffic flow ize. Firt Plot: = ; Second Plot: ; Third Plot: =. Table I VALUES FOR TO ACHIEVE OPTIMAL p UNDER DIFFERENT. 5 optial.7n.7n 3.8n optial p i choen to achieve the optial privacy p, a deterined in Section IV-D. Table I lit the value for to achieve optial p under different value of. Figure, 3, and 4 how our iulation reult when n = 5,,,, and 5,, repectively. For each figure, there are three plot, correponding to the reult of three et of iulation controlled by paraeter, where =, 5, and. Each plot how the eaured traffic flow ize ˆn c y-axi) with repect to different true traffic flow ize n c x-axi) under a given etting of n,, and, where i choen a decribed in Table I o that the optial privacy i achieved. We alo draw the equality line y = x in each plot for reference. Clearly, the cloer a point i to the equality line, the ore accurate the eaureent reult. Fro the figure, one can ee that given other paraeter, our MLE etiator produce alot perfect reult when = the firt plot in Figure, 3, and 4). When becoe larger, the variant for our etiator alo becoe larger, producing ore point not cloe to the equality line the third plot in Figure, 3, and 4). Recall that a larger value of bring better privacy Table I). For exaple, the optial privacy i.766 when =, better than the optial
8 privacy of.758 when =. Thi iplie a tradeoff between the preerved privacy and eaureent accuracy. Fro Section IV-D, we know when i large, there alway exit a ooth interval of near it extree point that can achieve coparable privacy a the optial. In reality, one can chooe a relatively large value for e.g., 5 or ), and adjut the value of to achieve better eaureent reult while till preerving coparable privacy a the optial. Finally, the reult are ore accurate with larger value of n, which i a natural phenoenon given that the eaureent reult i obtained through an MLE etiator. VI. RELATED WORK A. Tranportation Traffic Meaureent In the area of tranportation traffic eaureent, variou prediction odel have been propoed to eaure point traffic tatitic, uing data recorded by autoatic traffic recorder ATR) intalled at road ection. For exaple, the ultiple linear regreion odel in [], and the artificial neural network in [3], etc. Thoe olution, though elegant, are not appropriate for point-to-point tranportation traffic eaureent. While oe point-to-point tatitic ay be inferred fro point data [4], we prefer a ore accurate direct-eaureent approach that hould alo addre the privacy concern. Although Google recently announced to provide real-tie traffic data ervice in Google ap [], their approach cannot aure vehicle privacy ince it ue GPS and Wi-Fi in phone to track location [3]. B. Network Traffic Meaureent Another branch of reearch that relate to but i alo ignificantly different fro) our i network traffic eaureent, where reearcher have propoed variou ethod for traffic flow eaureent. Though having the ae nae, their proble i different fro our: to eaure the network traffic between two network router. The olution can be uarized into two categorie. One i indirect etiation baed on link load, and network routing, by eploying tatitical technique [4] [5]. Thee ethod cannot achieve high accuracy ince their etiation are baed on the unknown traffic volue. The other i direct eaureent by different counting ethod [6] [7]. In particular, Li et al. [7] develop a bitap-baed counting ethod for traffic flow eaureent, which i ot related to our work. However, all thee olution are not appropriate for our proble, ince they eaure traffic in network environent where the privacy of packet i not a concern, o counting can be done directly baed on the packet ID. In our proble, the privacy of vehicle i the ajor concern. Therefore, the olution ut incorporate randoization and de-identification technique to protect vehicle privacy, and do counting baed on inforation that look totally rando. VII. CONCLUSION In thi paper, we focu on the proble of privacypreerving point-to-point tranportation traffic onitoring in intelligent cyber-phyical road yte. We foralize point-to-point traffic a traffic flow, and quantify privacy a a probability. We propoe a novel chee which allow the collection of aggregate traffic flow data while preerving the optial privacy of individual vehicle. The propoed chee utilize bit array to collect data and adopt axiu likelihood etiation MLE) to obtain the eaureent reult. The feaibility and calability of our chee are hown by both atheatical proof and iulation. VIII. ACKNOWLEDGMENT Thi work i upported in part by the National Science Foundation under grant CPS and by a grant fro the Center for Multiodal Solution for Congetion Mitigation ponored by the US Departent of Tranportation. REFERENCES [] USDOT, Traffic Monitoring Guide, [] D. Mohaad, K. C. Sinha, T. Kuczek, and C. F. Scholer, Annual Average Daily Traffic Prediction Model for County Road, Journal of the Tranportation Reearch Board, vol. 67/998, pp , 998. [3] W. La and J. Xu, Etiation of AADT fro Short Period Count in Hong Kong A Coparion Between Neural Network Method and Regreion Analyi, Journal of Advanced Tranportation,. [4] Y. Lou and Y. Yin, A Decopoition Schee for Etiating Dynaic Origin-detination Flow on Actuation-controlled Signalized Arterial, Tranportation Reearch Part C, vol. 8,. [5] J. Erikon, H. Balakrihnan, and S. Madden, Cabernet: Vehicular Content Delivery Uing WiFi, Proc. of MOBICOM, 8. [6] U. Lee, J. Lee, J. Park, and M. Gerla, FleaNet: A Virtual Market Place on Vehicular Network, IEEE Tran. on Vehicular Technology,. [7] [Online]. Available: [8] [Online]. Available: [9] G. Caella and R. L. Berger, Statitical Inference, nd edition, Duxbury Pre,. [] W. Newey and D. McFadden, Large Saple Etiation and Hypothei Teting, Dan. Handbook of Econoetric, vol. 4, pp. 45, 994. [] W. Bryc, The noral ditribution: characterization with application, Springer-Verlag, 995. [] Google ap tie-in-traffic feature. [Online]. Available: [3] T. Jeke, Floating Car Data fro Sartphone: What Google and Waze Know About You and How Hacker Can Control Traffic, Proc. of the BlackHat Europe, 3. [4] Y. Zhang, M. Roughan, C. Lund, and D. Donoho, An inforation-theoretic approach to traffic atrix etiation, Proc. of SIGCOMM, 3. [5] Y. Zhang, M. Roughan, N. Duffield, and A. Greenberg, Fat accurate coputation of large-cale IP traffic atrice fro link load, Proc. of SIGMETRICS, 3. [6] J. Cao, A. Chen, and T. Bu, A Quai-Likelihood Approach for Accurate Traffic Matrix Etiation in a High Speed Network, Proc. of INFOCOM, 8. [7] T. Li, S. Chen, and Y. Qiao, Origin-Detination Flow Meaureent in High-Speed Network, Proc. of INFOCOM,.
Point-to-Point Traffic Volume Measurement through Variable-Length Bit Array Masking in Vehicular Cyber-Physical Systems
 25 IEEE 35th International Conference on Ditributed Computing Sytem Point-to-Point Traffic Volume Meaurement through Variable-Length Bit Array Making in Vehicular Cyber-Phyical Sytem Yian Zhou Shigang
25 IEEE 35th International Conference on Ditributed Computing Sytem Point-to-Point Traffic Volume Meaurement through Variable-Length Bit Array Making in Vehicular Cyber-Phyical Sytem Yian Zhou Shigang
Scale Efficiency in DEA and DEA-R with Weight Restrictions
 Available online at http://ijdea.rbiau.ac.ir Int. J. Data Envelopent Analyi (ISSN 2345-458X) Vol.2, No.2, Year 2014 Article ID IJDEA-00226, 5 page Reearch Article International Journal of Data Envelopent
Available online at http://ijdea.rbiau.ac.ir Int. J. Data Envelopent Analyi (ISSN 2345-458X) Vol.2, No.2, Year 2014 Article ID IJDEA-00226, 5 page Reearch Article International Journal of Data Envelopent
IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 64, NO. 12, DECEMBER
 IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 64, NO. 12, DECEMBER 2015 5619 Privacy-Preerving Multi-Point Traffic Volume Meaurement Through Vehicle-to-Infratructure Communication Yian Zhou, Member,
IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 64, NO. 12, DECEMBER 2015 5619 Privacy-Preerving Multi-Point Traffic Volume Meaurement Through Vehicle-to-Infratructure Communication Yian Zhou, Member,
Image Denoising Based on Non-Local Low-Rank Dictionary Learning
 Advanced cience and Technology Letter Vol.11 (AT 16) pp.85-89 http://dx.doi.org/1.1457/atl.16. Iage Denoiing Baed on Non-Local Low-Rank Dictionary Learning Zhang Bo 1 1 Electronic and Inforation Engineering
Advanced cience and Technology Letter Vol.11 (AT 16) pp.85-89 http://dx.doi.org/1.1457/atl.16. Iage Denoiing Baed on Non-Local Low-Rank Dictionary Learning Zhang Bo 1 1 Electronic and Inforation Engineering
The Extended Balanced Truncation Algorithm
 International Journal of Coputing and Optiization Vol. 3, 2016, no. 1, 71-82 HIKARI Ltd, www.-hikari.co http://dx.doi.org/10.12988/ijco.2016.635 The Extended Balanced Truncation Algorith Cong Huu Nguyen
International Journal of Coputing and Optiization Vol. 3, 2016, no. 1, 71-82 HIKARI Ltd, www.-hikari.co http://dx.doi.org/10.12988/ijco.2016.635 The Extended Balanced Truncation Algorith Cong Huu Nguyen
Persistent Spread Measurement for Big Network Data Based on Register Intersection
 Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection YOU ZHOU, Univerity of Florida YIAN ZHOU, Google Inc. and Univerity of Florida MIN CHEN, Google Inc. and Univerity of Florida
Peritent Spread Meaureent for Big Network Data Baed on Regiter Interection YOU ZHOU, Univerity of Florida YIAN ZHOU, Google Inc. and Univerity of Florida MIN CHEN, Google Inc. and Univerity of Florida
DIFFERENTIAL EQUATIONS
 Matheatic Reviion Guide Introduction to Differential Equation Page of Author: Mark Kudlowki MK HOME TUITION Matheatic Reviion Guide Level: A-Level Year DIFFERENTIAL EQUATIONS Verion : Date: 3-4-3 Matheatic
Matheatic Reviion Guide Introduction to Differential Equation Page of Author: Mark Kudlowki MK HOME TUITION Matheatic Reviion Guide Level: A-Level Year DIFFERENTIAL EQUATIONS Verion : Date: 3-4-3 Matheatic
Ranking DEA Efficient Units with the Most Compromising Common Weights
 The Sixth International Sypoiu on Operation Reearch and It Application ISORA 06 Xiniang, China, Augut 8 12, 2006 Copyright 2006 ORSC & APORC pp. 219 234 Ranking DEA Efficient Unit with the Mot Coproiing
The Sixth International Sypoiu on Operation Reearch and It Application ISORA 06 Xiniang, China, Augut 8 12, 2006 Copyright 2006 ORSC & APORC pp. 219 234 Ranking DEA Efficient Unit with the Mot Coproiing
Topic 7 Fuzzy expert systems: Fuzzy inference
 Topic 7 Fuzzy expert yte: Fuzzy inference adani fuzzy inference ugeno fuzzy inference Cae tudy uary Fuzzy inference The ot coonly ued fuzzy inference technique i the o-called adani ethod. In 975, Profeor
Topic 7 Fuzzy expert yte: Fuzzy inference adani fuzzy inference ugeno fuzzy inference Cae tudy uary Fuzzy inference The ot coonly ued fuzzy inference technique i the o-called adani ethod. In 975, Profeor
Persistent Traffic Measurement Through Vehicle-to-Infrastructure Communications
 217 IEEE 37th International Conference on Distributed Coputing Systes Persistent Traffic Measureent Through Vehicle-to-Infrastructure Counications He Huang, Yu-E Sun, Shigang Chen, Hongli Xu, Yian Zhou
217 IEEE 37th International Conference on Distributed Coputing Systes Persistent Traffic Measureent Through Vehicle-to-Infrastructure Counications He Huang, Yu-E Sun, Shigang Chen, Hongli Xu, Yian Zhou
Conservation of Energy
 Add Iportant Conervation of Energy Page: 340 Note/Cue Here NGSS Standard: HS-PS3- Conervation of Energy MA Curriculu Fraework (006):.,.,.3 AP Phyic Learning Objective: 3.E.., 3.E.., 3.E..3, 3.E..4, 4.C..,
Add Iportant Conervation of Energy Page: 340 Note/Cue Here NGSS Standard: HS-PS3- Conervation of Energy MA Curriculu Fraework (006):.,.,.3 AP Phyic Learning Objective: 3.E.., 3.E.., 3.E..3, 3.E..4, 4.C..,
Bayesian Reliability Estimation of Inverted Exponential Distribution under Progressive Type-II Censored Data
 J. Stat. Appl. Pro. 3, No. 3, 317-333 (2014) 317 Journal of Statitic Application & Probability An International Journal http://dx.doi.org/10.12785/jap/030303 Bayeian Reliability Etiation of Inverted Exponential
J. Stat. Appl. Pro. 3, No. 3, 317-333 (2014) 317 Journal of Statitic Application & Probability An International Journal http://dx.doi.org/10.12785/jap/030303 Bayeian Reliability Etiation of Inverted Exponential
24P 2, where W (measuring tape weight per meter) = 0.32 N m
 Ue of a 1W Laer to Verify the Speed of Light David M Verillion PHYS 375 North Carolina Agricultural and Technical State Univerity February 3, 2018 Abtract The lab wa et up to verify the accepted value
Ue of a 1W Laer to Verify the Speed of Light David M Verillion PHYS 375 North Carolina Agricultural and Technical State Univerity February 3, 2018 Abtract The lab wa et up to verify the accepted value
THE BICYCLE RACE ALBERT SCHUELLER
 THE BICYCLE RACE ALBERT SCHUELLER. INTRODUCTION We will conider the ituation of a cyclit paing a refrehent tation in a bicycle race and the relative poition of the cyclit and her chaing upport car. The
THE BICYCLE RACE ALBERT SCHUELLER. INTRODUCTION We will conider the ituation of a cyclit paing a refrehent tation in a bicycle race and the relative poition of the cyclit and her chaing upport car. The
On the Use of High-Order Moment Matching to Approximate the Generalized-K Distribution by a Gamma Distribution
 On the Ue of High-Order Moent Matching to Approxiate the Generalized- Ditribution by a Gaa Ditribution Saad Al-Ahadi Departent of Syte & Coputer Engineering Carleton Univerity Ottawa Canada aahadi@ce.carleton.ca
On the Ue of High-Order Moent Matching to Approxiate the Generalized- Ditribution by a Gaa Ditribution Saad Al-Ahadi Departent of Syte & Coputer Engineering Carleton Univerity Ottawa Canada aahadi@ce.carleton.ca
Lecture 2 Phys 798S Spring 2016 Steven Anlage. The heart and soul of superconductivity is the Meissner Effect. This feature uniquely distinguishes
 ecture Phy 798S Spring 6 Steven Anlage The heart and oul of uperconductivity i the Meiner Effect. Thi feature uniquely ditinguihe uperconductivity fro any other tate of atter. Here we dicu oe iple phenoenological
ecture Phy 798S Spring 6 Steven Anlage The heart and oul of uperconductivity i the Meiner Effect. Thi feature uniquely ditinguihe uperconductivity fro any other tate of atter. Here we dicu oe iple phenoenological
MODE SHAPE EXPANSION FROM DATA-BASED SYSTEM IDENTIFICATION PROCEDURES
 Mecánica Coputacional Vol XXV, pp. 1593-1602 Alberto Cardona, Norberto Nigro, Victorio Sonzogni, Mario Storti. (Ed.) Santa Fe, Argentina, Noviebre 2006 MODE SHAPE EXPANSION FROM DATA-BASED SYSTEM IDENTIFICATION
Mecánica Coputacional Vol XXV, pp. 1593-1602 Alberto Cardona, Norberto Nigro, Victorio Sonzogni, Mario Storti. (Ed.) Santa Fe, Argentina, Noviebre 2006 MODE SHAPE EXPANSION FROM DATA-BASED SYSTEM IDENTIFICATION
ADAPTIVE CONTROL DESIGN FOR A SYNCHRONOUS GENERATOR
 ADAPTIVE CONTROL DESIGN FOR A SYNCHRONOUS GENERATOR SAEED ABAZARI MOHSEN HEIDARI NAVID REZA ABJADI Key word: Adaptive control Lyapunov tability Tranient tability Mechanical power. The operating point of
ADAPTIVE CONTROL DESIGN FOR A SYNCHRONOUS GENERATOR SAEED ABAZARI MOHSEN HEIDARI NAVID REZA ABJADI Key word: Adaptive control Lyapunov tability Tranient tability Mechanical power. The operating point of
LEARNING DISCRIMINATIVE BASIS COEFFICIENTS FOR EIGENSPACE MLLR UNSUPERVISED ADAPTATION. Yajie Miao, Florian Metze, Alex Waibel
 LEARNING DISCRIMINATIVE BASIS COEFFICIENTS FOR EIGENSPACE MLLR UNSUPERVISED ADAPTATION Yajie Miao, Florian Metze, Alex Waibel Language Technologie Intitute, Carnegie Mellon Univerity, Pittburgh, PA, USA
LEARNING DISCRIMINATIVE BASIS COEFFICIENTS FOR EIGENSPACE MLLR UNSUPERVISED ADAPTATION Yajie Miao, Florian Metze, Alex Waibel Language Technologie Intitute, Carnegie Mellon Univerity, Pittburgh, PA, USA
Research Article An Extension of Cross Redundancy of Interval Scale Outputs and Inputs in DEA
 Hindawi Publihing Corporation pplied Matheatic Volue 2013, rticle ID 658635, 7 page http://dx.doi.org/10.1155/2013/658635 Reearch rticle n Extenion of Cro Redundancy of Interval Scale Output and Input
Hindawi Publihing Corporation pplied Matheatic Volue 2013, rticle ID 658635, 7 page http://dx.doi.org/10.1155/2013/658635 Reearch rticle n Extenion of Cro Redundancy of Interval Scale Output and Input
15 N 5 N. Chapter 4 Forces and Newton s Laws of Motion. The net force on an object is the vector sum of all forces acting on that object.
 Chapter 4 orce and ewton Law of Motion Goal for Chapter 4 to undertand what i force to tudy and apply ewton irt Law to tudy and apply the concept of a and acceleration a coponent of ewton Second Law to
Chapter 4 orce and ewton Law of Motion Goal for Chapter 4 to undertand what i force to tudy and apply ewton irt Law to tudy and apply the concept of a and acceleration a coponent of ewton Second Law to
Relevance Estimation of Cooperative Awareness Messages in VANETs
 Relevance Etiation of Cooperative Awarene Meage in VANET Jakob Breu Reearch and Developent Dailer AG Böblingen, Gerany Eail: jakobbreu@dailerco Michael Menth Departent of Coputer Science Univerity of Tübingen
Relevance Etiation of Cooperative Awarene Meage in VANET Jakob Breu Reearch and Developent Dailer AG Böblingen, Gerany Eail: jakobbreu@dailerco Michael Menth Departent of Coputer Science Univerity of Tübingen
2FSK-LFM Compound Signal Parameter Estimation Based on Joint FRFT-ML Method
 International Conerence on et eaureent Coputational ethod (C 5 FS-F Copound Signal Paraeter Etiation Baed on Joint FF- ethod Zhaoyang Qiu Bin ang School o Electronic Engineering Univerity o Electronic
International Conerence on et eaureent Coputational ethod (C 5 FS-F Copound Signal Paraeter Etiation Baed on Joint FF- ethod Zhaoyang Qiu Bin ang School o Electronic Engineering Univerity o Electronic
4 Conservation of Momentum
 hapter 4 oneration of oentu 4 oneration of oentu A coon itake inoling coneration of oentu crop up in the cae of totally inelatic colliion of two object, the kind of colliion in which the two colliding
hapter 4 oneration of oentu 4 oneration of oentu A coon itake inoling coneration of oentu crop up in the cae of totally inelatic colliion of two object, the kind of colliion in which the two colliding
An Exact Solution for the Deflection of a Clamped Rectangular Plate under Uniform Load
 Applied Matheatical Science, Vol. 1, 007, no. 3, 19-137 An Exact Solution for the Deflection of a Claped Rectangular Plate under Unifor Load C.E. İrak and İ. Gerdeeli Itanbul Technical Univerity Faculty
Applied Matheatical Science, Vol. 1, 007, no. 3, 19-137 An Exact Solution for the Deflection of a Claped Rectangular Plate under Unifor Load C.E. İrak and İ. Gerdeeli Itanbul Technical Univerity Faculty
The Features For Dark Matter And Dark Flow Found.
 The Feature For Dark Matter And Dark Flow Found. Author: Dan Vier, Alere, the Netherland Date: January 04 Abtract. Fly-By- and GPS-atellite reveal an earth-dark atter-halo i affecting the orbit-velocitie
The Feature For Dark Matter And Dark Flow Found. Author: Dan Vier, Alere, the Netherland Date: January 04 Abtract. Fly-By- and GPS-atellite reveal an earth-dark atter-halo i affecting the orbit-velocitie
Lecture 2 DATA ENVELOPMENT ANALYSIS - II
 Lecture DATA ENVELOPMENT ANALYSIS - II Learning objective To eplain Data Envelopent Anali for ultiple input and ultiple output cae in the for of linear prograing .5 DEA: Multiple input, ultiple output
Lecture DATA ENVELOPMENT ANALYSIS - II Learning objective To eplain Data Envelopent Anali for ultiple input and ultiple output cae in the for of linear prograing .5 DEA: Multiple input, ultiple output
Chemistry I Unit 3 Review Guide: Energy and Electrons
 Cheitry I Unit 3 Review Guide: Energy and Electron Practice Quetion and Proble 1. Energy i the capacity to do work. With reference to thi definition, decribe how you would deontrate that each of the following
Cheitry I Unit 3 Review Guide: Energy and Electron Practice Quetion and Proble 1. Energy i the capacity to do work. With reference to thi definition, decribe how you would deontrate that each of the following
A New Model and Calculation of Available Transfer Capability With Wind Generation *
 The Eighth International Sypoiu on Operation Reearch and It Application (ISORA 09) Zhangjiajie, China, Septeber 0, 009 Copyright 009 ORSC & APORC, pp. 70 79 A New Model and Calculation of Available Tranfer
The Eighth International Sypoiu on Operation Reearch and It Application (ISORA 09) Zhangjiajie, China, Septeber 0, 009 Copyright 009 ORSC & APORC, pp. 70 79 A New Model and Calculation of Available Tranfer
Investment decision for supply chain resilience based on Evolutionary Game theory
 Invetent deciion for upply chain reilience baed on Evolutionary Gae theory Xiaowei Ji(jixw@hut.edu.cn), Haijun Wang Manageent School Huazhong Univerity of Science and Technology Wuhan, Hubei, 4374, China
Invetent deciion for upply chain reilience baed on Evolutionary Gae theory Xiaowei Ji(jixw@hut.edu.cn), Haijun Wang Manageent School Huazhong Univerity of Science and Technology Wuhan, Hubei, 4374, China
Cryptography and Security Final Exam
 Cryptography and Security Final Exa Solution Serge Vaudenay 17.1.2017 duration: 3h no docuent allowed, except one 2-ided heet of handwritten note a pocket calculator i allowed counication device are not
Cryptography and Security Final Exa Solution Serge Vaudenay 17.1.2017 duration: 3h no docuent allowed, except one 2-ided heet of handwritten note a pocket calculator i allowed counication device are not
Convergence of a Fixed-Point Minimum Error Entropy Algorithm
 Entropy 05, 7, 5549-5560; doi:0.3390/e7085549 Article OPE ACCESS entropy ISS 099-4300 www.dpi.co/journal/entropy Convergence of a Fixed-Point Miniu Error Entropy Algorith Yu Zhang, Badong Chen, *, Xi Liu,
Entropy 05, 7, 5549-5560; doi:0.3390/e7085549 Article OPE ACCESS entropy ISS 099-4300 www.dpi.co/journal/entropy Convergence of a Fixed-Point Miniu Error Entropy Algorith Yu Zhang, Badong Chen, *, Xi Liu,
Lecture 21. The Lovasz splitting-off lemma Topics in Combinatorial Optimization April 29th, 2004
 18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
Hybrid technique based on chirp effect and phase shifts for spectral Talbot effect in sampled fiber Bragg gratings (FBGs)
 Optica Applicata, Vol. XLI, No. 1, 011 Hybrid technique baed on chirp effect and phae hift for pectral Talbot effect in apled fiber Bragg grating (FBG) GUO DENG *, WEI PAN Center for Inforation Photonic
Optica Applicata, Vol. XLI, No. 1, 011 Hybrid technique baed on chirp effect and phae hift for pectral Talbot effect in apled fiber Bragg grating (FBG) GUO DENG *, WEI PAN Center for Inforation Photonic
1-D SEDIMENT NUMERICAL MODEL AND ITS APPLICATION. Weimin Wu 1 and Guolu Yang 2
 U-CHINA WORKHOP ON ADVANCED COMPUTATIONAL MODELLING IN HYDROCIENCE & ENGINEERING epteber 9-, Oxford, Miiippi, UA -D EDIMENT NUMERICAL MODEL AND IT APPLICATION Weiin Wu and Guolu Yang ABTRACT A one dienional
U-CHINA WORKHOP ON ADVANCED COMPUTATIONAL MODELLING IN HYDROCIENCE & ENGINEERING epteber 9-, Oxford, Miiippi, UA -D EDIMENT NUMERICAL MODEL AND IT APPLICATION Weiin Wu and Guolu Yang ABTRACT A one dienional
SIMM Method Based on Acceleration Extraction for Nonlinear Maneuvering Target Tracking
 Journal of Electrical Engineering & Technology Vol. 7, o. 2, pp. 255~263, 202 255 http://dx.doi.org/0.5370/jeet.202.7.2.255 SIMM Method Baed on Acceleration Extraction for onlinear Maneuvering Target Tracking
Journal of Electrical Engineering & Technology Vol. 7, o. 2, pp. 255~263, 202 255 http://dx.doi.org/0.5370/jeet.202.7.2.255 SIMM Method Baed on Acceleration Extraction for onlinear Maneuvering Target Tracking
AN EASY INTRODUCTION TO THE CIRCLE METHOD
 AN EASY INTRODUCTION TO THE CIRCLE METHOD EVAN WARNER Thi talk will try to ketch out oe of the ajor idea involved in the Hardy- Littlewood circle ethod in the context of Waring proble.. Setup Firt, let
AN EASY INTRODUCTION TO THE CIRCLE METHOD EVAN WARNER Thi talk will try to ketch out oe of the ajor idea involved in the Hardy- Littlewood circle ethod in the context of Waring proble.. Setup Firt, let
Gain and Phase Margins Based Delay Dependent Stability Analysis of Two- Area LFC System with Communication Delays
 Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Social Studies 201 Notes for November 14, 2003
 1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
PPP AND UNIT ROOTS: LEARNING ACROSS REGIMES
 PPP AND UNIT ROOTS: LEARNING ACROSS REGIMES GERALD P. DYWER, MARK FISHER, THOMAS J. FLAVIN, AND JAMES R. LOTHIAN Preliinary and incoplete Abtract. Taking a Bayeian approach, we focu on the inforation content
PPP AND UNIT ROOTS: LEARNING ACROSS REGIMES GERALD P. DYWER, MARK FISHER, THOMAS J. FLAVIN, AND JAMES R. LOTHIAN Preliinary and incoplete Abtract. Taking a Bayeian approach, we focu on the inforation content
Performance Analysis of Sub-Rating for Handoff Calls in HCN
 I. J. Counication, Network and Syte Science, 29, 1, 1-89 Publihed Online February 29 in SciRe (http://www.scirp.org/journal/ijcn/). Perforance Analyi of Sub-Rating for Handoff Call in HCN Xiaolong WU 1,
I. J. Counication, Network and Syte Science, 29, 1, 1-89 Publihed Online February 29 in SciRe (http://www.scirp.org/journal/ijcn/). Perforance Analyi of Sub-Rating for Handoff Call in HCN Xiaolong WU 1,
Fair scheduling in cellular systems in the presence of noncooperative mobiles
 1 Fair cheduling in cellular yte in the preence of noncooperative obile Veeraruna Kavitha +, Eitan Altan R. El-Azouzi + and Rajeh Sundarean Maetro group, INRIA, 2004 Route de Luciole, Sophia Antipoli,
1 Fair cheduling in cellular yte in the preence of noncooperative obile Veeraruna Kavitha +, Eitan Altan R. El-Azouzi + and Rajeh Sundarean Maetro group, INRIA, 2004 Route de Luciole, Sophia Antipoli,
Clustering Methods without Given Number of Clusters
 Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Practice Problem Solutions. Identify the Goal The acceleration of the object Variables and Constants Known Implied Unknown m = 4.
 Chapter 5 Newton Law Practice Proble Solution Student Textbook page 163 1. Frae the Proble - Draw a free body diagra of the proble. - The downward force of gravity i balanced by the upward noral force.
Chapter 5 Newton Law Practice Proble Solution Student Textbook page 163 1. Frae the Proble - Draw a free body diagra of the proble. - The downward force of gravity i balanced by the upward noral force.
_10_EE394J_2_Spring12_Inertia_Calculation.doc. Procedure for Estimating Grid Inertia H from Frequency Droop Measurements
 Procedure or Etiating Grid Inertia ro Frequency Droop Meaureent While the exion or inertia and requency droop are well known, it i prudent to rederive the here. Treating all the grid generator a one large
Procedure or Etiating Grid Inertia ro Frequency Droop Meaureent While the exion or inertia and requency droop are well known, it i prudent to rederive the here. Treating all the grid generator a one large
Related Rates section 3.9
 Related Rate ection 3.9 Iportant Note: In olving the related rate proble, the rate of change of a quantity i given and the rate of change of another quantity i aked for. You need to find a relationhip
Related Rate ection 3.9 Iportant Note: In olving the related rate proble, the rate of change of a quantity i given and the rate of change of another quantity i aked for. You need to find a relationhip
13.2 Fully Polynomial Randomized Approximation Scheme for Permanent of Random 0-1 Matrices
 CS71 Randoness & Coputation Spring 018 Instructor: Alistair Sinclair Lecture 13: February 7 Disclaier: These notes have not been subjected to the usual scrutiny accorded to foral publications. They ay
CS71 Randoness & Coputation Spring 018 Instructor: Alistair Sinclair Lecture 13: February 7 Disclaier: These notes have not been subjected to the usual scrutiny accorded to foral publications. They ay
Periodic Table of Physical Elements
 Periodic Table of Phyical Eleent Periodic Table of Phyical Eleent Author:Zhiqiang Zhang fro Dalian, China Eail: dlxinzhigao@6.co ABSTRACT Thi i one of y original work in phyic to preent periodic table
Periodic Table of Phyical Eleent Periodic Table of Phyical Eleent Author:Zhiqiang Zhang fro Dalian, China Eail: dlxinzhigao@6.co ABSTRACT Thi i one of y original work in phyic to preent periodic table
V2V-Based Vehicle Risk Assessment and Control for Lane-Keeping and Collision Avoidance
 VV-Baed Vehicle Rik Aeent and Control for Lane-Keeping and Colliion Avoidance Haze M. Fahy Electronic Departent Geran Univerity in Cairo haze.fahyy9@gail.co Haan Motafa Electronic and Electrical Counication
VV-Baed Vehicle Rik Aeent and Control for Lane-Keeping and Colliion Avoidance Haze M. Fahy Electronic Departent Geran Univerity in Cairo haze.fahyy9@gail.co Haan Motafa Electronic and Electrical Counication
Improving Efficiency Scores of Inefficient Units. with Restricted Primary Resources
 Applied Matheatical Science, Vol. 3, 2009, no. 52, 2595-2602 Iproving Efficienc Score of Inefficient Unit with Retricted Priar Reource Farhad Hoeinzadeh Lotfi * Departent of Matheatic, Science and Reearch
Applied Matheatical Science, Vol. 3, 2009, no. 52, 2595-2602 Iproving Efficienc Score of Inefficient Unit with Retricted Priar Reource Farhad Hoeinzadeh Lotfi * Departent of Matheatic, Science and Reearch
Moisture transport in concrete during wetting/drying cycles
 Cheitry and Material Reearch Vol.5 03 Special Iue for International Congre on Material & Structural Stability Rabat Morocco 7-30 Noveber 03 Moiture tranport in concrete during wetting/drying cycle A. Taher
Cheitry and Material Reearch Vol.5 03 Special Iue for International Congre on Material & Structural Stability Rabat Morocco 7-30 Noveber 03 Moiture tranport in concrete during wetting/drying cycle A. Taher
Problem Set 8 Solutions
 Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Suggested Answers To Exercises. estimates variability in a sampling distribution of random means. About 68% of means fall
 Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Social Studies 201 Notes for March 18, 2005
 1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
CHAPTER 6. Estimation
 CHAPTER 6 Etimation Definition. Statitical inference i the procedure by which we reach a concluion about a population on the bai of information contained in a ample drawn from that population. Definition.
CHAPTER 6 Etimation Definition. Statitical inference i the procedure by which we reach a concluion about a population on the bai of information contained in a ample drawn from that population. Definition.
A First Digit Theorem for Square-Free Integer Powers
 Pure Matheatical Science, Vol. 3, 014, no. 3, 19-139 HIKARI Ltd, www.-hikari.co http://dx.doi.org/10.1988/p.014.4615 A Firt Digit Theore or Square-Free Integer Power Werner Hürliann Feldtrae 145, CH-8004
Pure Matheatical Science, Vol. 3, 014, no. 3, 19-139 HIKARI Ltd, www.-hikari.co http://dx.doi.org/10.1988/p.014.4615 A Firt Digit Theore or Square-Free Integer Power Werner Hürliann Feldtrae 145, CH-8004
Research Article Efficient Recursive Methods for Partial Fraction Expansion of General Rational Functions
 Journal of Applied atheatic Volue 24, Article ID 89536, 8 page http://dx.doi.org/.55/24/89536 Reearch Article Efficient Recurive ethod for Partial Fraction Expanion of General Rational Function Youneng
Journal of Applied atheatic Volue 24, Article ID 89536, 8 page http://dx.doi.org/.55/24/89536 Reearch Article Efficient Recurive ethod for Partial Fraction Expanion of General Rational Function Youneng
Model Fitting. CURM Background Material, Fall 2014 Dr. Doreen De Leon
 Model Fitting CURM Background Material, Fall 014 Dr. Doreen De Leon 1 Introduction Given a set of data points, we often want to fit a selected odel or type to the data (e.g., we suspect an exponential
Model Fitting CURM Background Material, Fall 014 Dr. Doreen De Leon 1 Introduction Given a set of data points, we often want to fit a selected odel or type to the data (e.g., we suspect an exponential
LOAD AND RESISTANCE FACTOR DESIGN APPROACH FOR FATIGUE OF MARINE STRUCTURES
 8 th ACE pecialty Conference on Probabilitic Mechanic and tructural Reliability PMC2000-169 LOAD AND REITANCE FACTOR DEIGN APPROACH FOR FATIGUE OF MARINE TRUCTURE Abtract I.A. Aakkaf, G. ACE, and B.M.
8 th ACE pecialty Conference on Probabilitic Mechanic and tructural Reliability PMC2000-169 LOAD AND REITANCE FACTOR DEIGN APPROACH FOR FATIGUE OF MARINE TRUCTURE Abtract I.A. Aakkaf, G. ACE, and B.M.
Bogoliubov Transformation in Classical Mechanics
 Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
μ + = σ = D 4 σ = D 3 σ = σ = All units in parts (a) and (b) are in V. (1) x chart: Center = μ = 0.75 UCL =
 Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Root Locus Diagram. Root loci: The portion of root locus when k assume positive values: that is 0
 Objective Root Locu Diagram Upon completion of thi chapter you will be able to: Plot the Root Locu for a given Tranfer Function by varying gain of the ytem, Analye the tability of the ytem from the root
Objective Root Locu Diagram Upon completion of thi chapter you will be able to: Plot the Root Locu for a given Tranfer Function by varying gain of the ytem, Analye the tability of the ytem from the root
The generalized Pareto sum
 HYDROLOGICAL PROCESSES Hydrol. Proce. 22, 288 294 28) Publihed online 28 Noveber 27 in Wiley InterScience www.intercience.wiley.co).662 The generalized Pareto u Saralee Nadarajah 1 *SauelKotz 2 1 School
HYDROLOGICAL PROCESSES Hydrol. Proce. 22, 288 294 28) Publihed online 28 Noveber 27 in Wiley InterScience www.intercience.wiley.co).662 The generalized Pareto u Saralee Nadarajah 1 *SauelKotz 2 1 School
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS
 CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
NCAAPMT Calculus Challenge Challenge #3 Due: October 26, 2011
 NCAAPMT Calculu Challenge 011 01 Challenge #3 Due: October 6, 011 A Model of Traffic Flow Everyone ha at ome time been on a multi-lane highway and encountered road contruction that required the traffic
NCAAPMT Calculu Challenge 011 01 Challenge #3 Due: October 6, 011 A Model of Traffic Flow Everyone ha at ome time been on a multi-lane highway and encountered road contruction that required the traffic
Preemptive scheduling on a small number of hierarchical machines
 Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
7.2 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 281
 72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
A Simplified Methodology for the Synthesis of Adaptive Flight Control Systems
 A Simplified Methodology for the Synthei of Adaptive Flight Control Sytem J.ROUSHANIAN, F.NADJAFI Department of Mechanical Engineering KNT Univerity of Technology 3Mirdamad St. Tehran IRAN Abtract- A implified
A Simplified Methodology for the Synthei of Adaptive Flight Control Sytem J.ROUSHANIAN, F.NADJAFI Department of Mechanical Engineering KNT Univerity of Technology 3Mirdamad St. Tehran IRAN Abtract- A implified
CHAPTER 13 FILTERS AND TUNED AMPLIFIERS
 HAPTE FILTES AND TUNED AMPLIFIES hapter Outline. Filter Traniion, Type and Specification. The Filter Tranfer Function. Butterworth and hebyhev Filter. Firt Order and Second Order Filter Function.5 The
HAPTE FILTES AND TUNED AMPLIFIES hapter Outline. Filter Traniion, Type and Specification. The Filter Tranfer Function. Butterworth and hebyhev Filter. Firt Order and Second Order Filter Function.5 The
1.3.3 Statistical (or precision) uncertainty Due to transient variations, spatial variations 100%
 1.1 Why eaure, and why tudy eaureent? 1. Introductory Exaple Exaple: Meauring your weight: The eaureent i not the thing. 1.3 Practical Source o Meaureent Uncertainty Exaple: Meauring T o roo. 1.3.1 Reading
1.1 Why eaure, and why tudy eaureent? 1. Introductory Exaple Exaple: Meauring your weight: The eaureent i not the thing. 1.3 Practical Source o Meaureent Uncertainty Exaple: Meauring T o roo. 1.3.1 Reading
Lecture 4 Topic 3: General linear models (GLMs), the fundamentals of the analysis of variance (ANOVA), and completely randomized designs (CRDs)
 Lecture 4 Topic 3: General linear model (GLM), the fundamental of the analyi of variance (ANOVA), and completely randomized deign (CRD) The general linear model One population: An obervation i explained
Lecture 4 Topic 3: General linear model (GLM), the fundamental of the analyi of variance (ANOVA), and completely randomized deign (CRD) The general linear model One population: An obervation i explained
Rigorous analysis of diffraction gratings of arbitrary profiles using virtual photonic crystals
 2192 J. Opt. Soc. A. A/ Vol. 23, No. 9/ Septeber 2006 W. Jiang and R. T. Chen Rigorou analyi of diffraction grating of arbitrary profile uing virtual photonic crytal Wei Jiang and Ray T. Chen Microelectronic
2192 J. Opt. Soc. A. A/ Vol. 23, No. 9/ Septeber 2006 W. Jiang and R. T. Chen Rigorou analyi of diffraction grating of arbitrary profile uing virtual photonic crytal Wei Jiang and Ray T. Chen Microelectronic
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD
 SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
IN SUPERVISING the correct operation of dynamic plants,
 1158 IEEE TRANSACTIONS ON CONTROL SYSTEMS TECHNOLOGY, VOL. 14, NO. 6, NOVEMBER 2006 Nonlinear Fault Detection and Iolation in a Three-Tank Heating Syte Raffaella Mattone and Aleandro De Luca, Senior Meber,
1158 IEEE TRANSACTIONS ON CONTROL SYSTEMS TECHNOLOGY, VOL. 14, NO. 6, NOVEMBER 2006 Nonlinear Fault Detection and Iolation in a Three-Tank Heating Syte Raffaella Mattone and Aleandro De Luca, Senior Meber,
Research Article Numerical and Analytical Study for Fourth-Order Integro-Differential Equations Using a Pseudospectral Method
 Matheatical Proble in Engineering Volue 213, Article ID 43473, 7 page http://d.doi.org/1.11/213/43473 Reearch Article Nuerical and Analytical Study for Fourth-Order Integro-Differential Equation Uing a
Matheatical Proble in Engineering Volue 213, Article ID 43473, 7 page http://d.doi.org/1.11/213/43473 Reearch Article Nuerical and Analytical Study for Fourth-Order Integro-Differential Equation Uing a
ANALOG REALIZATIONS OF FRACTIONAL-ORDER INTEGRATORS/DIFFERENTIATORS A Comparison
 AALOG REALIZATIOS OF FRACTIOAL-ORDER ITEGRATORS/DIFFERETIATORS A Coparion Guido DEESD, Technical Univerity of Bari, Via de Gaperi, nc, I-7, Taranto, Italy gaione@poliba.it Keyword: Abtract: on-integer-order
AALOG REALIZATIOS OF FRACTIOAL-ORDER ITEGRATORS/DIFFERETIATORS A Coparion Guido DEESD, Technical Univerity of Bari, Via de Gaperi, nc, I-7, Taranto, Italy gaione@poliba.it Keyword: Abtract: on-integer-order
Codes Correcting Two Deletions
 1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
Simple Observer Based Synchronization of Lorenz System with Parametric Uncertainty
 IOSR Journal of Electrical and Electronic Engineering (IOSR-JEEE) ISSN: 78-676Volume, Iue 6 (Nov. - Dec. 0), PP 4-0 Simple Oberver Baed Synchronization of Lorenz Sytem with Parametric Uncertainty Manih
IOSR Journal of Electrical and Electronic Engineering (IOSR-JEEE) ISSN: 78-676Volume, Iue 6 (Nov. - Dec. 0), PP 4-0 Simple Oberver Baed Synchronization of Lorenz Sytem with Parametric Uncertainty Manih
CONSOLIDATION ANALYSIS OF SOFT CLAY AT LARGE STRAIN
 Proceeding of Softoil 04, October, -3 rd 04 CONSOLIDATION ANALYSIS OF SOFT CLAY AT LARGE STRAIN Yakin, Y. A., Djayaputra, A. A. and Rahardjo, P. P. 3 ABSTRACT: Settleent of oft oil caued by external load
Proceeding of Softoil 04, October, -3 rd 04 CONSOLIDATION ANALYSIS OF SOFT CLAY AT LARGE STRAIN Yakin, Y. A., Djayaputra, A. A. and Rahardjo, P. P. 3 ABSTRACT: Settleent of oft oil caued by external load
Optimal Coordination of Samples in Business Surveys
 Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
The Four Kinetic Regimes of Adsorption from Micellar Surfactant Solutions
 The Four Kinetic Regie of Adorption fro Micellar Surfactant Solution P.A. Kralchevky, K.. anov, N.. enkov, N.C. Chritov, K.P. Ananthapadanabhan,* and Alex Lip* Laboratory of Cheical Phyic and Engineering,
The Four Kinetic Regie of Adorption fro Micellar Surfactant Solution P.A. Kralchevky, K.. anov, N.. enkov, N.C. Chritov, K.P. Ananthapadanabhan,* and Alex Lip* Laboratory of Cheical Phyic and Engineering,
Comparing Means: t-tests for Two Independent Samples
 Comparing ean: t-tet for Two Independent Sample Independent-eaure Deign t-tet for Two Independent Sample Allow reearcher to evaluate the mean difference between two population uing data from two eparate
Comparing ean: t-tet for Two Independent Sample Independent-eaure Deign t-tet for Two Independent Sample Allow reearcher to evaluate the mean difference between two population uing data from two eparate
[Saxena, 2(9): September, 2013] ISSN: Impact Factor: INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY
![[Saxena, 2(9): September, 2013] ISSN: Impact Factor: INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY [Saxena, 2(9): September, 2013] ISSN: Impact Factor: INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY](/thumbs/90/102186320.jpg) [Saena, (9): September, 0] ISSN: 77-9655 Impact Factor:.85 IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY Contant Stre Accelerated Life Teting Uing Rayleigh Geometric Proce
[Saena, (9): September, 0] ISSN: 77-9655 Impact Factor:.85 IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY Contant Stre Accelerated Life Teting Uing Rayleigh Geometric Proce
By Xiaoquan Wen and Matthew Stephens University of Michigan and University of Chicago
 Submitted to the Annal of Applied Statitic SUPPLEMENTARY APPENDIX TO BAYESIAN METHODS FOR GENETIC ASSOCIATION ANALYSIS WITH HETEROGENEOUS SUBGROUPS: FROM META-ANALYSES TO GENE-ENVIRONMENT INTERACTIONS
Submitted to the Annal of Applied Statitic SUPPLEMENTARY APPENDIX TO BAYESIAN METHODS FOR GENETIC ASSOCIATION ANALYSIS WITH HETEROGENEOUS SUBGROUPS: FROM META-ANALYSES TO GENE-ENVIRONMENT INTERACTIONS
Copyright 1967, by the author(s). All rights reserved.
 Copyright 1967, by the author(). All right reerved. Permiion to make digital or hard copie of all or part of thi work for peronal or claroom ue i granted without fee provided that copie are not made or
Copyright 1967, by the author(). All right reerved. Permiion to make digital or hard copie of all or part of thi work for peronal or claroom ue i granted without fee provided that copie are not made or
Non-Parametric Non-Line-of-Sight Identification 1
 Non-Paraetric Non-Line-of-Sight Identification Sinan Gezici, Hisashi Kobayashi and H. Vincent Poor Departent of Electrical Engineering School of Engineering and Applied Science Princeton University, Princeton,
Non-Paraetric Non-Line-of-Sight Identification Sinan Gezici, Hisashi Kobayashi and H. Vincent Poor Departent of Electrical Engineering School of Engineering and Applied Science Princeton University, Princeton,
Investigation of application of extractive distillation method in chloroform manufacture
 Invetigation of application of etractive ditillation ethod in chlorofor anufacture Proceeding of uropean Congre of Cheical ngineering (CC-6) Copenhagen, 16-20 Septeber 2007 Invetigation of application
Invetigation of application of etractive ditillation ethod in chlorofor anufacture Proceeding of uropean Congre of Cheical ngineering (CC-6) Copenhagen, 16-20 Septeber 2007 Invetigation of application
Ensemble Based on Data Envelopment Analysis
 Enseble Based on Data Envelopent Analysis So Young Sohn & Hong Choi Departent of Coputer Science & Industrial Systes Engineering, Yonsei University, Seoul, Korea Tel) 82-2-223-404, Fax) 82-2- 364-7807
Enseble Based on Data Envelopent Analysis So Young Sohn & Hong Choi Departent of Coputer Science & Industrial Systes Engineering, Yonsei University, Seoul, Korea Tel) 82-2-223-404, Fax) 82-2- 364-7807
Section J8b: FET Low Frequency Response
 ection J8b: FET ow Frequency epone In thi ection of our tudie, we re o to reiit the baic FET aplifier confiuration but with an additional twit The baic confiuration are the ae a we etiated ection J6 of
ection J8b: FET ow Frequency epone In thi ection of our tudie, we re o to reiit the baic FET aplifier confiuration but with an additional twit The baic confiuration are the ae a we etiated ection J6 of
Hybrid Projective Dislocated Synchronization of Liu Chaotic System Based on Parameters Identification
 www.ccenet.org/ma Modern Applied Science Vol. 6, No. ; February Hybrid Projective Dilocated Synchronization of Liu Chaotic Sytem Baed on Parameter Identification Yanfei Chen College of Science, Guilin
www.ccenet.org/ma Modern Applied Science Vol. 6, No. ; February Hybrid Projective Dilocated Synchronization of Liu Chaotic Sytem Baed on Parameter Identification Yanfei Chen College of Science, Guilin
Research Article Reliability of Foundation Pile Based on Settlement and a Parameter Sensitivity Analysis
 Mathematical Problem in Engineering Volume 2016, Article ID 1659549, 7 page http://dxdoiorg/101155/2016/1659549 Reearch Article Reliability of Foundation Pile Baed on Settlement and a Parameter Senitivity
Mathematical Problem in Engineering Volume 2016, Article ID 1659549, 7 page http://dxdoiorg/101155/2016/1659549 Reearch Article Reliability of Foundation Pile Baed on Settlement and a Parameter Senitivity
Chapter 2 Sampling and Quantization. In order to investigate sampling and quantization, the difference between analog
 Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Lecture 10 Filtering: Applied Concepts
 Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
UNIT 15 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS
 UNIT 1 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS Structure 1.1 Introduction Objective 1.2 Redundancy 1.3 Reliability of k-out-of-n Sytem 1.4 Reliability of Standby Sytem 1. Summary 1.6 Solution/Anwer
UNIT 1 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS Structure 1.1 Introduction Objective 1.2 Redundancy 1.3 Reliability of k-out-of-n Sytem 1.4 Reliability of Standby Sytem 1. Summary 1.6 Solution/Anwer
Performance Analysis of a Three-Channel Control Architecture for Bilateral Teleoperation with Time Delay
 Extended Suary pp.1224 1230 Perforance Analyi of a Three-Channel Control Architecture for Bilateral Teleoperation with Tie Delay Ryogo Kubo Meber (Keio Univerity, kubo@u.d.keio.ac.jp) Noriko Iiyaa Student
Extended Suary pp.1224 1230 Perforance Analyi of a Three-Channel Control Architecture for Bilateral Teleoperation with Tie Delay Ryogo Kubo Meber (Keio Univerity, kubo@u.d.keio.ac.jp) Noriko Iiyaa Student
PHYSICS 211 MIDTERM II 12 May 2004
 PHYSIS IDTER II ay 004 Exa i cloed boo, cloed note. Ue only your forula heet. Write all wor and anwer in exa boolet. The bac of page will not be graded unle you o requet on the front of the page. Show
PHYSIS IDTER II ay 004 Exa i cloed boo, cloed note. Ue only your forula heet. Write all wor and anwer in exa boolet. The bac of page will not be graded unle you o requet on the front of the page. Show
Lecture 17: Frequency Response of Amplifiers
 ecture 7: Frequency epone of Aplifier Gu-Yeon Wei Diiion of Engineering and Applied Science Harard Unierity guyeon@eec.harard.edu Wei Oeriew eading S&S: Chapter 7 Ski ection ince otly decribed uing BJT
ecture 7: Frequency epone of Aplifier Gu-Yeon Wei Diiion of Engineering and Applied Science Harard Unierity guyeon@eec.harard.edu Wei Oeriew eading S&S: Chapter 7 Ski ection ince otly decribed uing BJT
Extending MFM Function Ontology for Representing Separation and Conversion in Process Plant
 Downloaded from orbit.dtu.dk on: Oct 05, 2018 Extending MFM Function Ontology for Repreenting Separation and Converion in Proce Plant Zhang, Xinxin; Lind, Morten; Jørgenen, Sten Bay; Wu, Jing; Karnati,
Downloaded from orbit.dtu.dk on: Oct 05, 2018 Extending MFM Function Ontology for Repreenting Separation and Converion in Proce Plant Zhang, Xinxin; Lind, Morten; Jørgenen, Sten Bay; Wu, Jing; Karnati,
Determination of the local contrast of interference fringe patterns using continuous wavelet transform
 Determination of the local contrat of interference fringe pattern uing continuou wavelet tranform Jong Kwang Hyok, Kim Chol Su Intitute of Optic, Department of Phyic, Kim Il Sung Univerity, Pyongyang,
Determination of the local contrat of interference fringe pattern uing continuou wavelet tranform Jong Kwang Hyok, Kim Chol Su Intitute of Optic, Department of Phyic, Kim Il Sung Univerity, Pyongyang,
1. The F-test for Equality of Two Variances
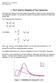 . The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
. The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
