Machine Learning Approaches to Network Anomaly Detection
|
|
|
- Emma Bates
- 5 years ago
- Views:
Transcription
1 Machine Learning Approaches to Network Anomaly Detection Tarem Ahmed, Boris Oreshkin and Mark Coates USENIX SysML, Cambridge, MA April 1, 27 Research supported by Canadian National Science and Engineering Research Council (NSERC) through the Agile All- Photonics Research Network (AAPN) and MITACS projects
2 Introduction Network data are voluminous high-dimensional high-rate What is a network anomaly? rare event short-lived ML-based network anomaly detection methods more general than model-based signature-based
3 Our Methodology Show applicability of ML approaches to network anomaly detection Two example algorithms: One-Class Neighbor Machine (OCNM) [Muñoz 6] Kernel-based Online Anomaly Detection (KOAD) [Ahmed 7] Two example datasets: Transports Quebec Abilene Log of frequency Hash of srcip t=214 t=216 t=218
4 One-Class Neighbor Machine (OCNM) Region of normality should correspond to a Minimum Volume Set (MVS) OCNM for estimating MVS proposed in [Muñoz 6], Anomalous Normal Requires choice of sparsity measure, g. Example: k-th nearest-neighbour distance Sorts list of g, identifies fraction µ inside MVS 2-D Isomap of CHIN-LOSA backbone flow, srcip
5 Kernel-based Online Anomaly Detection (KOAD): Introduction Sequence of multivariate measurements: {x t } t=1:t Choose feature space with associated kernel: where ( x, x ) = ( x ), ( x ) k ϕ ϕ i j i j ϕ: x n ϕ x ( ) H Then feature vectors corresponding to normal traffic measurements should cluster
6 Kernel-based Online Anomaly Detection (KOAD): Dictionary Should be possible to describe region of normality in feature space using sparse dictionary, D { } j j= 1 = x M Feature vector is said to be approximately linearly independent on if [Engel 4]: m t 1 ϕ x t ( ) δ = min a φ( x ) φ( x ) > ν t j j t a j= 1 { ϕ ( x )} j j= 1 2 M (1) Dictionary approximation Threshold
7 Kernel-based Online Anomaly Detection (KOAD): Algorithm At timestep t with arriving input vector x t : δ t Evaluate according to (1), compare with and where δ ν1 ν 2 ν1 < ν 2 If, infer x t far from normality: Red1 t If t 1, raise Orange, resolve l timesteps later, after usefulness test δ < ν If, infer x t close to normality: Green t > ν 2 δ > ν 1 Delete obsolete elements, use exponential forgetting For details of KOAD see [Ahmed 7]
8 Dataset 1: Transports Quebec Cameras monitored
9 Sample Images (normal) Camera 1 Camera 2 Camera 3 Camera 4 Camera 5 Camera 6
10 Sample Images (anomalous) Camera 1 Camera 2 Camera 3 Camera 4 Camera 5 Camera 6
11 Feature Extraction: Discrete Wavelet Transform -5 α i (n), db Timestep At each timestep, at each camera, get 6-D wavelet feature vector
12 Transports Quebec Results α i, db Change of camera position Camera 1 Camera 6 Traffic jam α i, db Traffic jams OCNM distance 1-2 OCNM distance 1-1 KOAD δ KOAD δ Timestep Timestep Use n = 3 out of c = 6 voting at central monitoring unit
13 Transports Quebec ROC KOAD: Gaussian kernel, with varying standard deviation for the kernel function OCNM: identify 5%- 5% of outliers P D KOAD OCNM P FA
14 Dataset 2: Abilene Data collection 11 core routers, 121 backbone flows 4 main pkt header fields collected: (srcip, dstip, srcport, dstport) Data processing Abilene Weathermap Construct histogram of headers Calculate header entropies for each backbone flow, at each timestep Variations in entropies (distributions) reveal many anomalies [Lakhina 25] Log of frequency Hash of srcip t=214 t=216 t=218
15 Abilene Results δ.3 KOAD.1 Magnitude of residual Euclidean distance PCA, 1 components OCNM, 5% outliers KOAD PCA OCNM Timestep
16 Conclusions and Future Work Preliminary results indicate potential of ML approaches Parameters set using supervised learning Computations must be distributed Online: complexity must be independent of time
17 Acknowledgements, References Acknowledgements: Thanks to Sergio Restrepo for processing Transports Quebec data and to Anukool Lakhina for providing Abilene dataset. References: [Ahmed 7] T. Ahmed, M. Coates, and A. Lakhina, Multivariate online anomaly detection using kernel recursive least squares, in Proc. IEEE Infocom, Anchorage, AK, May 27, to appear. [Engel 4] Y. Engel, S. Mannor, and R. Meir, The kernel recursive least squares algorithm, IEEE Trans. Signal Proc., vol. 52, no. 8, pp , Aug. 24. [Lakhina 5] A. Lakhina, M. Crovella and C. Diot, Mining anomalies using traffic feature distributions, in Proc. ACM SIGCOMM, Philadelphia, PA, Aug. 25. [Muñoz 6] A. Muñoz and J. Moguerza, Estimation of high-density regions using one-class neighbor machines, IEEE Trans. Pattern Analysis and Machine Intelligence, vol. 28, num 3, pp , Mar. 26.
Mining Anomalies Using Traffic Feature Distributions
 Boston University OpenBU Computer Science http://open.bu.edu CAS: Computer Science: Technical Reports 25--5 Mining Anomalies Using Traffic Feature Distributions Lakhina, Anukool Boston University Computer
Boston University OpenBU Computer Science http://open.bu.edu CAS: Computer Science: Technical Reports 25--5 Mining Anomalies Using Traffic Feature Distributions Lakhina, Anukool Boston University Computer
Decomposable Principal Component Analysis
 Decomposable Principal Component Analysis 1 Ami Wiesel and Alfred O. Hero III Department of Electrical Engineering and Computer Science University of Michigan, Ann Arbor, MI 48109, USA E-mails: {amiw,hero}@umich.edu
Decomposable Principal Component Analysis 1 Ami Wiesel and Alfred O. Hero III Department of Electrical Engineering and Computer Science University of Michigan, Ann Arbor, MI 48109, USA E-mails: {amiw,hero}@umich.edu
Anomaly Extraction in Backbone Networks using Association Rules
 1 Anomaly Extraction in Backbone Networks using Association Rules Daniela Brauckhoff, Xenofontas Dimitropoulos, Arno Wagner, and Kave Salamatian TIK-Report 309 ftp://ftp.tik.ee.ethz.ch/pub/publications/tik-report-309.pdf
1 Anomaly Extraction in Backbone Networks using Association Rules Daniela Brauckhoff, Xenofontas Dimitropoulos, Arno Wagner, and Kave Salamatian TIK-Report 309 ftp://ftp.tik.ee.ethz.ch/pub/publications/tik-report-309.pdf
References for online kernel methods
 References for online kernel methods W. Liu, J. Principe, S. Haykin Kernel Adaptive Filtering: A Comprehensive Introduction. Wiley, 2010. W. Liu, P. Pokharel, J. Principe. The kernel least mean square
References for online kernel methods W. Liu, J. Principe, S. Haykin Kernel Adaptive Filtering: A Comprehensive Introduction. Wiley, 2010. W. Liu, P. Pokharel, J. Principe. The kernel least mean square
SENATUS: An Approach to Joint Traffic Anomaly Detection and Root Cause Analysis
 SENATUS: An Approach to Joint Traffic Anomaly Detection and Root ause Analysis Atef Abdelkefi, Yuming Jiang, Sachin Sharma 2 NTNU - Norwegian University of Science and Technology, Norway. 2 NE Laboratories
SENATUS: An Approach to Joint Traffic Anomaly Detection and Root ause Analysis Atef Abdelkefi, Yuming Jiang, Sachin Sharma 2 NTNU - Norwegian University of Science and Technology, Norway. 2 NE Laboratories
Diagnosing Network-Wide Traffic Anomalies
 Diagnosing Network-Wide Traffic Anomalies Anukool Lakhina, Mark Crovella, and Christophe Diot Λ February 9, 4 BUCS-TR-4-8 and RR4-ATL-666 Abstract Anomalies are unusual and significant changes in a network
Diagnosing Network-Wide Traffic Anomalies Anukool Lakhina, Mark Crovella, and Christophe Diot Λ February 9, 4 BUCS-TR-4-8 and RR4-ATL-666 Abstract Anomalies are unusual and significant changes in a network
SPECTRAL ANOMALY DETECTION USING GRAPH-BASED FILTERING FOR WIRELESS SENSOR NETWORKS. Hilmi E. Egilmez and Antonio Ortega
 SPECTRAL ANOMALY DETECTION USING GRAPH-BASED FILTERING FOR WIRELESS SENSOR NETWORKS Hilmi E. Egilmez and Antonio Ortega Signal and Image Processing Institute, University of Southern California hegilmez@usc.edu,
SPECTRAL ANOMALY DETECTION USING GRAPH-BASED FILTERING FOR WIRELESS SENSOR NETWORKS Hilmi E. Egilmez and Antonio Ortega Signal and Image Processing Institute, University of Southern California hegilmez@usc.edu,
Anomaly (outlier) detection. Huiping Cao, Anomaly 1
 Anomaly (outlier) detection Huiping Cao, Anomaly 1 Outline General concepts What are outliers Types of outliers Causes of anomalies Challenges of outlier detection Outlier detection approaches Huiping
Anomaly (outlier) detection Huiping Cao, Anomaly 1 Outline General concepts What are outliers Types of outliers Causes of anomalies Challenges of outlier detection Outlier detection approaches Huiping
On the Generalization of the Mahalanobis Distance
 On the Generalization of the Mahalanobis Distance Gabriel Martos 1, Alberto Muñoz 1, and Javier González 2 1 University Carlos III, Department of Statistics, Madrid, Spain 2 J. Bernoulli Institute for
On the Generalization of the Mahalanobis Distance Gabriel Martos 1, Alberto Muñoz 1, and Javier González 2 1 University Carlos III, Department of Statistics, Madrid, Spain 2 J. Bernoulli Institute for
Available online at ScienceDirect. Procedia Computer Science 96 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 96 (2016 ) 139 146 20th International Conference on Knowledge Based and Intelligent Information and Engineering Systems
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 96 (2016 ) 139 146 20th International Conference on Knowledge Based and Intelligent Information and Engineering Systems
A Comparative Study of Two Network-based Anomaly Detection Methods
 A Comparative Study of Two Network-based Anomaly Detection Methods Kaustubh Nyalkalkar, Sushant Sinha, Michael Bailey and Farnam Jahanian Electrical Engineering and Computer Science, University of Michigan,
A Comparative Study of Two Network-based Anomaly Detection Methods Kaustubh Nyalkalkar, Sushant Sinha, Michael Bailey and Farnam Jahanian Electrical Engineering and Computer Science, University of Michigan,
Quantum machine learning for quantum anomaly detection CQT AND SUTD, SINGAPORE ARXIV:
 Quantum machine learning for quantum anomaly detection NANA LIU CQT AND SUTD, SINGAPORE ARXIV:1710.07405 TUESDAY 7 TH NOVEMBER 2017 QTML 2017, VERONA Types of anomaly detection algorithms Classification-based
Quantum machine learning for quantum anomaly detection NANA LIU CQT AND SUTD, SINGAPORE ARXIV:1710.07405 TUESDAY 7 TH NOVEMBER 2017 QTML 2017, VERONA Types of anomaly detection algorithms Classification-based
EXAMINING OUTLIER DETECTION PERFORMANCE FOR PRINCIPAL COMPONENTS ANALYSIS METHOD AND ITS ROBUSTIFICATION METHODS
 International Journal of Advances in Engineering & Technology, May 23. EXAMINING OUTLIER DETECTION PERFORMANCE FOR PRINCIPAL COMPONENTS ANALYSIS METHOD AND ITS ROBUSTIFICATION METHODS Nada Badr, Noureldien
International Journal of Advances in Engineering & Technology, May 23. EXAMINING OUTLIER DETECTION PERFORMANCE FOR PRINCIPAL COMPONENTS ANALYSIS METHOD AND ITS ROBUSTIFICATION METHODS Nada Badr, Noureldien
Bregman Divergences. Barnabás Póczos. RLAI Tea Talk UofA, Edmonton. Aug 5, 2008
 Bregman Divergences Barnabás Póczos RLAI Tea Talk UofA, Edmonton Aug 5, 2008 Contents Bregman Divergences Bregman Matrix Divergences Relation to Exponential Family Applications Definition Properties Generalization
Bregman Divergences Barnabás Póczos RLAI Tea Talk UofA, Edmonton Aug 5, 2008 Contents Bregman Divergences Bregman Matrix Divergences Relation to Exponential Family Applications Definition Properties Generalization
Clustering and Model Integration under the Wasserstein Metric. Jia Li Department of Statistics Penn State University
 Clustering and Model Integration under the Wasserstein Metric Jia Li Department of Statistics Penn State University Clustering Data represented by vectors or pairwise distances. Methods Top- down approaches
Clustering and Model Integration under the Wasserstein Metric Jia Li Department of Statistics Penn State University Clustering Data represented by vectors or pairwise distances. Methods Top- down approaches
CS570 Data Mining. Anomaly Detection. Li Xiong. Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber.
 CS570 Data Mining Anomaly Detection Li Xiong Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber April 3, 2011 1 Anomaly Detection Anomaly is a pattern in the data that does not conform
CS570 Data Mining Anomaly Detection Li Xiong Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber April 3, 2011 1 Anomaly Detection Anomaly is a pattern in the data that does not conform
Recovery of Low-Rank Plus Compressed Sparse Matrices with Application to Unveiling Traffic Anomalies
 July 12, 212 Recovery of Low-Rank Plus Compressed Sparse Matrices with Application to Unveiling Traffic Anomalies Morteza Mardani Dept. of ECE, University of Minnesota, Minneapolis, MN 55455 Acknowledgments:
July 12, 212 Recovery of Low-Rank Plus Compressed Sparse Matrices with Application to Unveiling Traffic Anomalies Morteza Mardani Dept. of ECE, University of Minnesota, Minneapolis, MN 55455 Acknowledgments:
Roberto Perdisci^+, Guofei Gu^, Wenke Lee^ presented by Roberto Perdisci. ^Georgia Institute of Technology, Atlanta, GA, USA
 U s i n g a n E n s e m b l e o f O n e - C l a s s S V M C l a s s i f i e r s t o H a r d e n P a y l o a d - B a s e d A n o m a l y D e t e c t i o n S y s t e m s Roberto Perdisci^+, Guofei Gu^, Wenke
U s i n g a n E n s e m b l e o f O n e - C l a s s S V M C l a s s i f i e r s t o H a r d e n P a y l o a d - B a s e d A n o m a l y D e t e c t i o n S y s t e m s Roberto Perdisci^+, Guofei Gu^, Wenke
Detection and Classification of Anomalies in Network Traffic Using Generalized Entropies and OC-SVM with Mahalanobis Kernel
 OPEN ACCESS Conference Proceedings Paper Entropy www.sciforum.net/conference/ecea-1 Detection and Classification of Anomalies in Network Traffic Using Generalized Entropies and OC-SVM with Mahalanobis
OPEN ACCESS Conference Proceedings Paper Entropy www.sciforum.net/conference/ecea-1 Detection and Classification of Anomalies in Network Traffic Using Generalized Entropies and OC-SVM with Mahalanobis
Mixture Models and EM
 Mixture Models and EM Goal: Introduction to probabilistic mixture models and the expectationmaximization (EM) algorithm. Motivation: simultaneous fitting of multiple model instances unsupervised clustering
Mixture Models and EM Goal: Introduction to probabilistic mixture models and the expectationmaximization (EM) algorithm. Motivation: simultaneous fitting of multiple model instances unsupervised clustering
A Modified Incremental Principal Component Analysis for On-Line Learning of Feature Space and Classifier
 A Modified Incremental Principal Component Analysis for On-Line Learning of Feature Space and Classifier Seiichi Ozawa 1, Shaoning Pang 2, and Nikola Kasabov 2 1 Graduate School of Science and Technology,
A Modified Incremental Principal Component Analysis for On-Line Learning of Feature Space and Classifier Seiichi Ozawa 1, Shaoning Pang 2, and Nikola Kasabov 2 1 Graduate School of Science and Technology,
A Framework for Adaptive Anomaly Detection Based on Support Vector Data Description
 A Framework for Adaptive Anomaly Detection Based on Support Vector Data Description Min Yang, HuanGuo Zhang, JianMing Fu, and Fei Yan School of Computer, State Key Laboratory of Software Engineering, Wuhan
A Framework for Adaptive Anomaly Detection Based on Support Vector Data Description Min Yang, HuanGuo Zhang, JianMing Fu, and Fei Yan School of Computer, State Key Laboratory of Software Engineering, Wuhan
Anomaly Detection. Jing Gao. SUNY Buffalo
 Anomaly Detection Jing Gao SUNY Buffalo 1 Anomaly Detection Anomalies the set of objects are considerably dissimilar from the remainder of the data occur relatively infrequently when they do occur, their
Anomaly Detection Jing Gao SUNY Buffalo 1 Anomaly Detection Anomalies the set of objects are considerably dissimilar from the remainder of the data occur relatively infrequently when they do occur, their
Streaming multiscale anomaly detection
 Streaming multiscale anomaly detection DATA-ENS Paris and ThalesAlenia Space B Ravi Kiran, Université Lille 3, CRISTaL Joint work with Mathieu Andreux beedotkiran@gmail.com June 20, 2017 (CRISTaL) Streaming
Streaming multiscale anomaly detection DATA-ENS Paris and ThalesAlenia Space B Ravi Kiran, Université Lille 3, CRISTaL Joint work with Mathieu Andreux beedotkiran@gmail.com June 20, 2017 (CRISTaL) Streaming
Anomaly detection and. in time series
 Anomaly detection and sequential statistics in time series Alex Shyr CS 294 Practical Machine Learning 11/12/2009 (many slides from XuanLong Nguyen and Charles Sutton) Two topics Anomaly detection Sequential
Anomaly detection and sequential statistics in time series Alex Shyr CS 294 Practical Machine Learning 11/12/2009 (many slides from XuanLong Nguyen and Charles Sutton) Two topics Anomaly detection Sequential
A Modified Incremental Principal Component Analysis for On-line Learning of Feature Space and Classifier
 A Modified Incremental Principal Component Analysis for On-line Learning of Feature Space and Classifier Seiichi Ozawa, Shaoning Pang, and Nikola Kasabov Graduate School of Science and Technology, Kobe
A Modified Incremental Principal Component Analysis for On-line Learning of Feature Space and Classifier Seiichi Ozawa, Shaoning Pang, and Nikola Kasabov Graduate School of Science and Technology, Kobe
An Overview of Outlier Detection Techniques and Applications
 Machine Learning Rhein-Neckar Meetup An Overview of Outlier Detection Techniques and Applications Ying Gu connygy@gmail.com 28.02.2016 Anomaly/Outlier Detection What are anomalies/outliers? The set of
Machine Learning Rhein-Neckar Meetup An Overview of Outlier Detection Techniques and Applications Ying Gu connygy@gmail.com 28.02.2016 Anomaly/Outlier Detection What are anomalies/outliers? The set of
A Robust Anomaly Detection Technique Using Combined Statistical Methods
 A Robust Anomaly Detection Technique Using Combined Statistical Methods Joseph Ndong, Kavé Salamatian To cite this version: Joseph Ndong, Kavé Salamatian. A Robust Anomaly Detection Technique Using Combined
A Robust Anomaly Detection Technique Using Combined Statistical Methods Joseph Ndong, Kavé Salamatian To cite this version: Joseph Ndong, Kavé Salamatian. A Robust Anomaly Detection Technique Using Combined
Adding rigor to the comparison of anomaly detector outputs
 Adding rigor to the comparison of anomaly detector outputs Romain Fontugne, National Institute of Informatics / SOKENDAI, Tokyo Pierre Borgnat, Physics Lab, CNRS, ENS Lyon Patrice Abry, Physics Lab, CNRS,
Adding rigor to the comparison of anomaly detector outputs Romain Fontugne, National Institute of Informatics / SOKENDAI, Tokyo Pierre Borgnat, Physics Lab, CNRS, ENS Lyon Patrice Abry, Physics Lab, CNRS,
Unsupervised Anomaly Detection for High Dimensional Data
 Unsupervised Anomaly Detection for High Dimensional Data Department of Mathematics, Rowan University. July 19th, 2013 International Workshop in Sequential Methodologies (IWSM-2013) Outline of Talk Motivation
Unsupervised Anomaly Detection for High Dimensional Data Department of Mathematics, Rowan University. July 19th, 2013 International Workshop in Sequential Methodologies (IWSM-2013) Outline of Talk Motivation
Iterative Laplacian Score for Feature Selection
 Iterative Laplacian Score for Feature Selection Linling Zhu, Linsong Miao, and Daoqiang Zhang College of Computer Science and echnology, Nanjing University of Aeronautics and Astronautics, Nanjing 2006,
Iterative Laplacian Score for Feature Selection Linling Zhu, Linsong Miao, and Daoqiang Zhang College of Computer Science and echnology, Nanjing University of Aeronautics and Astronautics, Nanjing 2006,
Geometric entropy minimization
 Geometric entropy minimization Alfred Hero University of Michigan Ann Arbor www.eecs.umich.edu/~hero 1 Outline Motivation: entropy and entropy minimization Random geometric graphs and the BHH theorem Application:
Geometric entropy minimization Alfred Hero University of Michigan Ann Arbor www.eecs.umich.edu/~hero 1 Outline Motivation: entropy and entropy minimization Random geometric graphs and the BHH theorem Application:
A Data-driven Approach for Remaining Useful Life Prediction of Critical Components
 GT S3 : Sûreté, Surveillance, Supervision Meeting GdR Modélisation, Analyse et Conduite des Systèmes Dynamiques (MACS) January 28 th, 2014 A Data-driven Approach for Remaining Useful Life Prediction of
GT S3 : Sûreté, Surveillance, Supervision Meeting GdR Modélisation, Analyse et Conduite des Systèmes Dynamiques (MACS) January 28 th, 2014 A Data-driven Approach for Remaining Useful Life Prediction of
Entropic graphs for high dimensional data analysis. A Hero, Newton08
 Entropic graphs for high dimensional data analysis Alfred Hero University of Michigan Ann Arbor wwweecsumichedu/~hero 1 Outline Motivation: statistical high dimensional data analysis Random geometric graphs
Entropic graphs for high dimensional data analysis Alfred Hero University of Michigan Ann Arbor wwweecsumichedu/~hero 1 Outline Motivation: statistical high dimensional data analysis Random geometric graphs
Face Recognition Using Laplacianfaces He et al. (IEEE Trans PAMI, 2005) presented by Hassan A. Kingravi
 Face Recognition Using Laplacianfaces He et al. (IEEE Trans PAMI, 2005) presented by Hassan A. Kingravi Overview Introduction Linear Methods for Dimensionality Reduction Nonlinear Methods and Manifold
Face Recognition Using Laplacianfaces He et al. (IEEE Trans PAMI, 2005) presented by Hassan A. Kingravi Overview Introduction Linear Methods for Dimensionality Reduction Nonlinear Methods and Manifold
Learning Eigenfunctions: Links with Spectral Clustering and Kernel PCA
 Learning Eigenfunctions: Links with Spectral Clustering and Kernel PCA Yoshua Bengio Pascal Vincent Jean-François Paiement University of Montreal April 2, Snowbird Learning 2003 Learning Modal Structures
Learning Eigenfunctions: Links with Spectral Clustering and Kernel PCA Yoshua Bengio Pascal Vincent Jean-François Paiement University of Montreal April 2, Snowbird Learning 2003 Learning Modal Structures
ADMIRE: Anomaly Detection Method Using Entropy-based PCA with Three-step Sketches
 ADMIRE: Anomaly Detection Method Using Entropy-based PCA with Three-step Sketches Yoshiki Kanda a, Romain Fontugne b, Kensuke Fukuda b,c, Toshiharu Sugawara a a Graduate School of Fundamental Science and
ADMIRE: Anomaly Detection Method Using Entropy-based PCA with Three-step Sketches Yoshiki Kanda a, Romain Fontugne b, Kensuke Fukuda b,c, Toshiharu Sugawara a a Graduate School of Fundamental Science and
An Automatic and Dynamic Parameter Tuning of a Statistic-based Anomaly Detection Algorithm
 An Automatic and Dynamic Parameter Tuning of a Statistic-based Anomaly Detection Algorithm Yosuke Himura The University of Tokyo him@hongo.wide.ad.jp Kensuke Fukuda National Institute of Informatics /
An Automatic and Dynamic Parameter Tuning of a Statistic-based Anomaly Detection Algorithm Yosuke Himura The University of Tokyo him@hongo.wide.ad.jp Kensuke Fukuda National Institute of Informatics /
MINIMUM EXPECTED RISK PROBABILITY ESTIMATES FOR NONPARAMETRIC NEIGHBORHOOD CLASSIFIERS. Maya Gupta, Luca Cazzanti, and Santosh Srivastava
 MINIMUM EXPECTED RISK PROBABILITY ESTIMATES FOR NONPARAMETRIC NEIGHBORHOOD CLASSIFIERS Maya Gupta, Luca Cazzanti, and Santosh Srivastava University of Washington Dept. of Electrical Engineering Seattle,
MINIMUM EXPECTED RISK PROBABILITY ESTIMATES FOR NONPARAMETRIC NEIGHBORHOOD CLASSIFIERS Maya Gupta, Luca Cazzanti, and Santosh Srivastava University of Washington Dept. of Electrical Engineering Seattle,
Sparse Gaussian Markov Random Field Mixtures for Anomaly Detection
 Sparse Gaussian Markov Random Field Mixtures for Anomaly Detection Tsuyoshi Idé ( Ide-san ), Ankush Khandelwal*, Jayant Kalagnanam IBM Research, T. J. Watson Research Center (*Currently with University
Sparse Gaussian Markov Random Field Mixtures for Anomaly Detection Tsuyoshi Idé ( Ide-san ), Ankush Khandelwal*, Jayant Kalagnanam IBM Research, T. J. Watson Research Center (*Currently with University
Final Exam, Machine Learning, Spring 2009
 Name: Andrew ID: Final Exam, 10701 Machine Learning, Spring 2009 - The exam is open-book, open-notes, no electronics other than calculators. - The maximum possible score on this exam is 100. You have 3
Name: Andrew ID: Final Exam, 10701 Machine Learning, Spring 2009 - The exam is open-book, open-notes, no electronics other than calculators. - The maximum possible score on this exam is 100. You have 3
Anomaly Detection via Over-sampling Principal Component Analysis
 Anomaly Detection via Over-sampling Principal Component Analysis Yi-Ren Yeh, Zheng-Yi Lee, and Yuh-Jye Lee Abstract Outlier detection is an important issue in data mining and has been studied in different
Anomaly Detection via Over-sampling Principal Component Analysis Yi-Ren Yeh, Zheng-Yi Lee, and Yuh-Jye Lee Abstract Outlier detection is an important issue in data mining and has been studied in different
Multiple Similarities Based Kernel Subspace Learning for Image Classification
 Multiple Similarities Based Kernel Subspace Learning for Image Classification Wang Yan, Qingshan Liu, Hanqing Lu, and Songde Ma National Laboratory of Pattern Recognition, Institute of Automation, Chinese
Multiple Similarities Based Kernel Subspace Learning for Image Classification Wang Yan, Qingshan Liu, Hanqing Lu, and Songde Ma National Laboratory of Pattern Recognition, Institute of Automation, Chinese
EEL 851: Biometrics. An Overview of Statistical Pattern Recognition EEL 851 1
 EEL 851: Biometrics An Overview of Statistical Pattern Recognition EEL 851 1 Outline Introduction Pattern Feature Noise Example Problem Analysis Segmentation Feature Extraction Classification Design Cycle
EEL 851: Biometrics An Overview of Statistical Pattern Recognition EEL 851 1 Outline Introduction Pattern Feature Noise Example Problem Analysis Segmentation Feature Extraction Classification Design Cycle
Multi-criteria Anomaly Detection using Pareto Depth Analysis
 Multi-criteria Anomaly Detection using Pareto Depth Analysis Ko-Jen Hsiao, Kevin S. Xu, Jeff Calder, and Alfred O. Hero III University of Michigan, Ann Arbor, MI, USA 489 {coolmark,xukevin,jcalder,hero}@umich.edu
Multi-criteria Anomaly Detection using Pareto Depth Analysis Ko-Jen Hsiao, Kevin S. Xu, Jeff Calder, and Alfred O. Hero III University of Michigan, Ann Arbor, MI, USA 489 {coolmark,xukevin,jcalder,hero}@umich.edu
Laplacian Eigenmaps for Dimensionality Reduction and Data Representation
 Introduction and Data Representation Mikhail Belkin & Partha Niyogi Department of Electrical Engieering University of Minnesota Mar 21, 2017 1/22 Outline Introduction 1 Introduction 2 3 4 Connections to
Introduction and Data Representation Mikhail Belkin & Partha Niyogi Department of Electrical Engieering University of Minnesota Mar 21, 2017 1/22 Outline Introduction 1 Introduction 2 3 4 Connections to
Non-parametric Methods
 Non-parametric Methods Machine Learning Alireza Ghane Non-Parametric Methods Alireza Ghane / Torsten Möller 1 Outline Machine Learning: What, Why, and How? Curve Fitting: (e.g.) Regression and Model Selection
Non-parametric Methods Machine Learning Alireza Ghane Non-Parametric Methods Alireza Ghane / Torsten Möller 1 Outline Machine Learning: What, Why, and How? Curve Fitting: (e.g.) Regression and Model Selection
P-Channels: Robust Multivariate M-Estimation of Large Datasets
 P-Channels: Robust Multivariate M-Estimation of Large Datasets Michael Felsberg Linköping University Computer Vision Laboratory mfe@isy.liu.se Gösta Granlund Linköping University Computer Vision Laboratory
P-Channels: Robust Multivariate M-Estimation of Large Datasets Michael Felsberg Linköping University Computer Vision Laboratory mfe@isy.liu.se Gösta Granlund Linköping University Computer Vision Laboratory
Chart types and when to use them
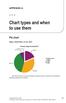 APPENDIX A Chart types and when to use them Pie chart Figure illustration of pie chart 2.3 % 4.5 % Browser Usage for April 2012 18.3 % 38.3 % Internet Explorer Firefox Chrome Safari Opera 35.8 % Pie chart
APPENDIX A Chart types and when to use them Pie chart Figure illustration of pie chart 2.3 % 4.5 % Browser Usage for April 2012 18.3 % 38.3 % Internet Explorer Firefox Chrome Safari Opera 35.8 % Pie chart
CPSC 340: Machine Learning and Data Mining. Linear Least Squares Fall 2016
 CPSC 340: Machine Learning and Data Mining Linear Least Squares Fall 2016 Assignment 2 is due Friday: Admin You should already be started! 1 late day to hand it in on Wednesday, 2 for Friday, 3 for next
CPSC 340: Machine Learning and Data Mining Linear Least Squares Fall 2016 Assignment 2 is due Friday: Admin You should already be started! 1 late day to hand it in on Wednesday, 2 for Friday, 3 for next
Value Function Approximation through Sparse Bayesian Modeling
 Value Function Approximation through Sparse Bayesian Modeling Nikolaos Tziortziotis and Konstantinos Blekas Department of Computer Science, University of Ioannina, P.O. Box 1186, 45110 Ioannina, Greece,
Value Function Approximation through Sparse Bayesian Modeling Nikolaos Tziortziotis and Konstantinos Blekas Department of Computer Science, University of Ioannina, P.O. Box 1186, 45110 Ioannina, Greece,
Using Generalized Quantile Sets and FDR
 Nonparametric Assessment of Contamination in Multivariate Data Using Generalized Quantile Sets and FDR Clayton Scott and Eric Kolaczyk January 19, 2010 Abstract Large, multivariate datasets from high-throughput
Nonparametric Assessment of Contamination in Multivariate Data Using Generalized Quantile Sets and FDR Clayton Scott and Eric Kolaczyk January 19, 2010 Abstract Large, multivariate datasets from high-throughput
Machine Learning. Nonparametric Methods. Space of ML Problems. Todo. Histograms. Instance-Based Learning (aka non-parametric methods)
 Machine Learning InstanceBased Learning (aka nonparametric methods) Supervised Learning Unsupervised Learning Reinforcement Learning Parametric Non parametric CSE 446 Machine Learning Daniel Weld March
Machine Learning InstanceBased Learning (aka nonparametric methods) Supervised Learning Unsupervised Learning Reinforcement Learning Parametric Non parametric CSE 446 Machine Learning Daniel Weld March
Linear Models for Regression. Sargur Srihari
 Linear Models for Regression Sargur srihari@cedar.buffalo.edu 1 Topics in Linear Regression What is regression? Polynomial Curve Fitting with Scalar input Linear Basis Function Models Maximum Likelihood
Linear Models for Regression Sargur srihari@cedar.buffalo.edu 1 Topics in Linear Regression What is regression? Polynomial Curve Fitting with Scalar input Linear Basis Function Models Maximum Likelihood
Impact of Packet Sampling on Portscan Detection
 Impact of Packet Sampling on Portscan Detection Jianning Mai, Student Member, IEEE, Ashwin Sridharan, Member, IEEE, Chen-Nee Chuah, Member, IEEE, Hui Zang, Senior Member, IEEE, and Tao Ye, Member, IEEE
Impact of Packet Sampling on Portscan Detection Jianning Mai, Student Member, IEEE, Ashwin Sridharan, Member, IEEE, Chen-Nee Chuah, Member, IEEE, Hui Zang, Senior Member, IEEE, and Tao Ye, Member, IEEE
Using Image Moment Invariants to Distinguish Classes of Geographical Shapes
 Using Image Moment Invariants to Distinguish Classes of Geographical Shapes J. F. Conley, I. J. Turton, M. N. Gahegan Pennsylvania State University Department of Geography 30 Walker Building University
Using Image Moment Invariants to Distinguish Classes of Geographical Shapes J. F. Conley, I. J. Turton, M. N. Gahegan Pennsylvania State University Department of Geography 30 Walker Building University
Change Detection in Multivariate Data
 Change Detection in Multivariate Data Likelihood and Detectability Loss Giacomo Boracchi July, 8 th, 2016 giacomo.boracchi@polimi.it TJ Watson, IBM NY Examples of CD Problems: Anomaly Detection Examples
Change Detection in Multivariate Data Likelihood and Detectability Loss Giacomo Boracchi July, 8 th, 2016 giacomo.boracchi@polimi.it TJ Watson, IBM NY Examples of CD Problems: Anomaly Detection Examples
CPSC 340: Machine Learning and Data Mining. Sparse Matrix Factorization Fall 2018
 CPSC 340: Machine Learning and Data Mining Sparse Matrix Factorization Fall 2018 Last Time: PCA with Orthogonal/Sequential Basis When k = 1, PCA has a scaling problem. When k > 1, have scaling, rotation,
CPSC 340: Machine Learning and Data Mining Sparse Matrix Factorization Fall 2018 Last Time: PCA with Orthogonal/Sequential Basis When k = 1, PCA has a scaling problem. When k > 1, have scaling, rotation,
BasisDetect : A Model-based Network Event Detection Framework
 BasisDetect : A Model-based Network Event Detection Framework Brian Eriksson UW-Madison bceriksson@wisc.edu Nick Duffield AT&T Research duffield@research.att.com Paul Barford UW-Madison and Nemean Networks
BasisDetect : A Model-based Network Event Detection Framework Brian Eriksson UW-Madison bceriksson@wisc.edu Nick Duffield AT&T Research duffield@research.att.com Paul Barford UW-Madison and Nemean Networks
Statistical Learning. Dong Liu. Dept. EEIS, USTC
 Statistical Learning Dong Liu Dept. EEIS, USTC Chapter 6. Unsupervised and Semi-Supervised Learning 1. Unsupervised learning 2. k-means 3. Gaussian mixture model 4. Other approaches to clustering 5. Principle
Statistical Learning Dong Liu Dept. EEIS, USTC Chapter 6. Unsupervised and Semi-Supervised Learning 1. Unsupervised learning 2. k-means 3. Gaussian mixture model 4. Other approaches to clustering 5. Principle
REAL-TIME TIME-FREQUENCY BASED BLIND SOURCE SEPARATION. Scott Rickard, Radu Balan, Justinian Rosca. Siemens Corporate Research Princeton, NJ 08540
 REAL-TIME TIME-FREQUENCY BASED BLIND SOURCE SEPARATION Scott Rickard, Radu Balan, Justinian Rosca Siemens Corporate Research Princeton, NJ 84 fscott.rickard,radu.balan,justinian.roscag@scr.siemens.com
REAL-TIME TIME-FREQUENCY BASED BLIND SOURCE SEPARATION Scott Rickard, Radu Balan, Justinian Rosca Siemens Corporate Research Princeton, NJ 84 fscott.rickard,radu.balan,justinian.roscag@scr.siemens.com
Introduction to Machine Learning. PCA and Spectral Clustering. Introduction to Machine Learning, Slides: Eran Halperin
 1 Introduction to Machine Learning PCA and Spectral Clustering Introduction to Machine Learning, 2013-14 Slides: Eran Halperin Singular Value Decomposition (SVD) The singular value decomposition (SVD)
1 Introduction to Machine Learning PCA and Spectral Clustering Introduction to Machine Learning, 2013-14 Slides: Eran Halperin Singular Value Decomposition (SVD) The singular value decomposition (SVD)
Curve Fitting Re-visited, Bishop1.2.5
 Curve Fitting Re-visited, Bishop1.2.5 Maximum Likelihood Bishop 1.2.5 Model Likelihood differentiation p(t x, w, β) = Maximum Likelihood N N ( t n y(x n, w), β 1). (1.61) n=1 As we did in the case of the
Curve Fitting Re-visited, Bishop1.2.5 Maximum Likelihood Bishop 1.2.5 Model Likelihood differentiation p(t x, w, β) = Maximum Likelihood N N ( t n y(x n, w), β 1). (1.61) n=1 As we did in the case of the
Unsupervised Data Discretization of Mixed Data Types
 Unsupervised Data Discretization of Mixed Data Types Jee Vang Outline Introduction Background Objective Experimental Design Results Future Work 1 Introduction Many algorithms in data mining, machine learning,
Unsupervised Data Discretization of Mixed Data Types Jee Vang Outline Introduction Background Objective Experimental Design Results Future Work 1 Introduction Many algorithms in data mining, machine learning,
A NEW ONE-CLASS SVM FOR ANOMALY DETECTION. Yuting Chen Jing Qian Venkatesh Saligrama. Boston University Boston, MA, 02215
 A NEW ONE-CLASS SVM FOR ANOMALY DETECTION Yuting Chen Jing Qian Venkatesh Saligrama Boston University Boston, MA, 225 ABSTRACT Given n i.i.d. samples from some unknown nominal density f, the task of anomaly
A NEW ONE-CLASS SVM FOR ANOMALY DETECTION Yuting Chen Jing Qian Venkatesh Saligrama Boston University Boston, MA, 225 ABSTRACT Given n i.i.d. samples from some unknown nominal density f, the task of anomaly
Censor, Sketch, and Validate for Learning from Large-Scale Data
 Censor, Sketch, and Validate for Learning from Large-Scale Data Georgios B. Giannakis Acknowledgments: D. Berberidis, F. Sheikholeslami, P. Traganitis; and Prof. G. Mateos NSF 1343860, 1442686, 1514056,
Censor, Sketch, and Validate for Learning from Large-Scale Data Georgios B. Giannakis Acknowledgments: D. Berberidis, F. Sheikholeslami, P. Traganitis; and Prof. G. Mateos NSF 1343860, 1442686, 1514056,
Support Measure Data Description for Group Anomaly Detection
 Support Measure Data Description for Group Anomaly Detection 1 Jorge Guevara Díaz, 2 Stephane Canu, 1 Roberto Hirata Jr. 1 IME-USP, Brazil. 2 LITIS-INSA, France. November 03, 2015. Outline 1 Who am I?
Support Measure Data Description for Group Anomaly Detection 1 Jorge Guevara Díaz, 2 Stephane Canu, 1 Roberto Hirata Jr. 1 IME-USP, Brazil. 2 LITIS-INSA, France. November 03, 2015. Outline 1 Who am I?
Internet Traffic Mid-Term Forecasting: a Pragmatic Approach using Statistical Analysis Tools
 Internet Traffic Mid-Term Forecasting: a Pragmatic Approach using Statistical Analysis Tools Rachel Babiarz Jean-Sebastien Bedo France Telecom R&D Division, Innovation Economics Laboratory, 38-40 rue du
Internet Traffic Mid-Term Forecasting: a Pragmatic Approach using Statistical Analysis Tools Rachel Babiarz Jean-Sebastien Bedo France Telecom R&D Division, Innovation Economics Laboratory, 38-40 rue du
Principles of Pattern Recognition. C. A. Murthy Machine Intelligence Unit Indian Statistical Institute Kolkata
 Principles of Pattern Recognition C. A. Murthy Machine Intelligence Unit Indian Statistical Institute Kolkata e-mail: murthy@isical.ac.in Pattern Recognition Measurement Space > Feature Space >Decision
Principles of Pattern Recognition C. A. Murthy Machine Intelligence Unit Indian Statistical Institute Kolkata e-mail: murthy@isical.ac.in Pattern Recognition Measurement Space > Feature Space >Decision
Surprise Detection in Science Data Streams Kirk Borne Dept of Computational & Data Sciences George Mason University
 Surprise Detection in Science Data Streams Kirk Borne Dept of Computational & Data Sciences George Mason University kborne@gmu.edu, http://classweb.gmu.edu/kborne/ Outline Astroinformatics Example Application:
Surprise Detection in Science Data Streams Kirk Borne Dept of Computational & Data Sciences George Mason University kborne@gmu.edu, http://classweb.gmu.edu/kborne/ Outline Astroinformatics Example Application:
Detection of Unauthorized Electricity Consumption using Machine Learning
 Detection of Unauthorized Electricity Consumption using Machine Learning Bo Tang, Ph.D. Department of Electrical and Computer Engineering Mississippi State University Outline Advanced Metering Infrastructure
Detection of Unauthorized Electricity Consumption using Machine Learning Bo Tang, Ph.D. Department of Electrical and Computer Engineering Mississippi State University Outline Advanced Metering Infrastructure
Independent Component Analysis and Unsupervised Learning. Jen-Tzung Chien
 Independent Component Analysis and Unsupervised Learning Jen-Tzung Chien TABLE OF CONTENTS 1. Independent Component Analysis 2. Case Study I: Speech Recognition Independent voices Nonparametric likelihood
Independent Component Analysis and Unsupervised Learning Jen-Tzung Chien TABLE OF CONTENTS 1. Independent Component Analysis 2. Case Study I: Speech Recognition Independent voices Nonparametric likelihood
Part I. Linear regression & LASSO. Linear Regression. Linear Regression. Week 10 Based in part on slides from textbook, slides of Susan Holmes
 Week 10 Based in part on slides from textbook, slides of Susan Holmes Part I Linear regression & December 5, 2012 1 / 1 2 / 1 We ve talked mostly about classification, where the outcome categorical. If
Week 10 Based in part on slides from textbook, slides of Susan Holmes Part I Linear regression & December 5, 2012 1 / 1 2 / 1 We ve talked mostly about classification, where the outcome categorical. If
PATTERN RECOGNITION AND MACHINE LEARNING CHAPTER 2: PROBABILITY DISTRIBUTIONS
 PATTERN RECOGNITION AND MACHINE LEARNING CHAPTER 2: PROBABILITY DISTRIBUTIONS Parametric Distributions Basic building blocks: Need to determine given Representation: or? Recall Curve Fitting Binary Variables
PATTERN RECOGNITION AND MACHINE LEARNING CHAPTER 2: PROBABILITY DISTRIBUTIONS Parametric Distributions Basic building blocks: Need to determine given Representation: or? Recall Curve Fitting Binary Variables
ECE521: Inference Algorithms and Machine Learning University of Toronto. Assignment 1: k-nn and Linear Regression
 ECE521: Inference Algorithms and Machine Learning University of Toronto Assignment 1: k-nn and Linear Regression TA: Use Piazza for Q&A Due date: Feb 7 midnight, 2017 Electronic submission to: ece521ta@gmailcom
ECE521: Inference Algorithms and Machine Learning University of Toronto Assignment 1: k-nn and Linear Regression TA: Use Piazza for Q&A Due date: Feb 7 midnight, 2017 Electronic submission to: ece521ta@gmailcom
STEADY-STATE MEAN SQUARE PERFORMANCE OF A SPARSIFIED KERNEL LEAST MEAN SQUARE ALGORITHM.
 STEADY-STATE MEAN SQUARE PERFORMANCE OF A SPARSIFIED KERNEL LEAST MEAN SQUARE ALGORITHM Badong Chen 1, Zhengda Qin 1, Lei Sun 2 1 Institute of Artificial Intelligence and Robotics, Xi an Jiaotong University,
STEADY-STATE MEAN SQUARE PERFORMANCE OF A SPARSIFIED KERNEL LEAST MEAN SQUARE ALGORITHM Badong Chen 1, Zhengda Qin 1, Lei Sun 2 1 Institute of Artificial Intelligence and Robotics, Xi an Jiaotong University,
Stochastic Online Anomaly Analysis for Streaming Time Series
 Stochastic Online Anomaly Analysis for Streaming Time Series Zhao Xu 1, Kristian Kersting, Lorenzo von Ritter 1,3 1 NEC Labs Europe, Germany Technical University of Darmstadt, Germany 3 Technical University
Stochastic Online Anomaly Analysis for Streaming Time Series Zhao Xu 1, Kristian Kersting, Lorenzo von Ritter 1,3 1 NEC Labs Europe, Germany Technical University of Darmstadt, Germany 3 Technical University
WE consider principal component analysis (PCA)
 IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL. 57, NO. 11, NOVEMBER 2009 4369 Decomposable Principal Component Analysis Ami Wiesel, Member, IEEE, and Alfred O. Hero, Fellow, IEEE Abstract In this paper,
IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL. 57, NO. 11, NOVEMBER 2009 4369 Decomposable Principal Component Analysis Ami Wiesel, Member, IEEE, and Alfred O. Hero, Fellow, IEEE Abstract In this paper,
One-class Label Propagation Using Local Cone Based Similarity
 One-class Label Propagation Using Local Based Similarity Takumi Kobayashi and Nobuyuki Otsu Abstract In this paper, we propose a novel method of label propagation for one-class learning. For binary (positive/negative)
One-class Label Propagation Using Local Based Similarity Takumi Kobayashi and Nobuyuki Otsu Abstract In this paper, we propose a novel method of label propagation for one-class learning. For binary (positive/negative)
Modeling Residual-Geometric Flow Sampling
 Modeling Residual-Geometric Flow Sampling Xiaoming Wang Joint work with Xiaoyong Li and Dmitri Loguinov Amazon.com Inc., Seattle, WA April 13 th, 2011 1 Agenda Introduction Underlying model of residual
Modeling Residual-Geometric Flow Sampling Xiaoming Wang Joint work with Xiaoyong Li and Dmitri Loguinov Amazon.com Inc., Seattle, WA April 13 th, 2011 1 Agenda Introduction Underlying model of residual
Anomaly Detection in Large-Scale Data Stream Networks
 Preprint manuscript No. (will be inserted by the editor) Anomaly Detection in Large-Scale Data Stream Networks Duc-Son Pham Svetha Venkatesh Mihai Lazarescu Saha Budhaditya Received: date / Accepted: date
Preprint manuscript No. (will be inserted by the editor) Anomaly Detection in Large-Scale Data Stream Networks Duc-Son Pham Svetha Venkatesh Mihai Lazarescu Saha Budhaditya Received: date / Accepted: date
Research Article Comparative Features Extraction Techniques for Electrocardiogram Images Regression
 Research Journal of Applied Sciences, Engineering and Technology (): 6, 7 DOI:.96/rjaset..6 ISSN: -79; e-issn: -767 7 Maxwell Scientific Organization Corp. Submitted: September 8, 6 Accepted: November,
Research Journal of Applied Sciences, Engineering and Technology (): 6, 7 DOI:.96/rjaset..6 ISSN: -79; e-issn: -767 7 Maxwell Scientific Organization Corp. Submitted: September 8, 6 Accepted: November,
Rapid Object Recognition from Discriminative Regions of Interest
 Rapid Object Recognition from Discriminative Regions of Interest Gerald Fritz, Christin Seifert, Lucas Paletta JOANNEUM RESEARCH Institute of Digital Image Processing Wastiangasse 6, A-81 Graz, Austria
Rapid Object Recognition from Discriminative Regions of Interest Gerald Fritz, Christin Seifert, Lucas Paletta JOANNEUM RESEARCH Institute of Digital Image Processing Wastiangasse 6, A-81 Graz, Austria
Minimum message length estimation of mixtures of multivariate Gaussian and von Mises-Fisher distributions
 Minimum message length estimation of mixtures of multivariate Gaussian and von Mises-Fisher distributions Parthan Kasarapu & Lloyd Allison Monash University, Australia September 8, 25 Parthan Kasarapu
Minimum message length estimation of mixtures of multivariate Gaussian and von Mises-Fisher distributions Parthan Kasarapu & Lloyd Allison Monash University, Australia September 8, 25 Parthan Kasarapu
An online kernel-based clustering approach for value function approximation
 An online kernel-based clustering approach for value function approximation N. Tziortziotis and K. Blekas Department of Computer Science, University of Ioannina P.O.Box 1186, Ioannina 45110 - Greece {ntziorzi,kblekas}@cs.uoi.gr
An online kernel-based clustering approach for value function approximation N. Tziortziotis and K. Blekas Department of Computer Science, University of Ioannina P.O.Box 1186, Ioannina 45110 - Greece {ntziorzi,kblekas}@cs.uoi.gr
Statistical Machine Learning
 Statistical Machine Learning Christoph Lampert Spring Semester 2015/2016 // Lecture 12 1 / 36 Unsupervised Learning Dimensionality Reduction 2 / 36 Dimensionality Reduction Given: data X = {x 1,..., x
Statistical Machine Learning Christoph Lampert Spring Semester 2015/2016 // Lecture 12 1 / 36 Unsupervised Learning Dimensionality Reduction 2 / 36 Dimensionality Reduction Given: data X = {x 1,..., x
Machine Learning. CUNY Graduate Center, Spring Lectures 11-12: Unsupervised Learning 1. Professor Liang Huang.
 Machine Learning CUNY Graduate Center, Spring 2013 Lectures 11-12: Unsupervised Learning 1 (Clustering: k-means, EM, mixture models) Professor Liang Huang huang@cs.qc.cuny.edu http://acl.cs.qc.edu/~lhuang/teaching/machine-learning
Machine Learning CUNY Graduate Center, Spring 2013 Lectures 11-12: Unsupervised Learning 1 (Clustering: k-means, EM, mixture models) Professor Liang Huang huang@cs.qc.cuny.edu http://acl.cs.qc.edu/~lhuang/teaching/machine-learning
Virtual Sensors and Large-Scale Gaussian Processes
 Virtual Sensors and Large-Scale Gaussian Processes Ashok N. Srivastava, Ph.D. Principal Investigator, IVHM Project Group Lead, Intelligent Data Understanding ashok.n.srivastava@nasa.gov Coauthors: Kamalika
Virtual Sensors and Large-Scale Gaussian Processes Ashok N. Srivastava, Ph.D. Principal Investigator, IVHM Project Group Lead, Intelligent Data Understanding ashok.n.srivastava@nasa.gov Coauthors: Kamalika
Instance-based Learning CE-717: Machine Learning Sharif University of Technology. M. Soleymani Fall 2016
 Instance-based Learning CE-717: Machine Learning Sharif University of Technology M. Soleymani Fall 2016 Outline Non-parametric approach Unsupervised: Non-parametric density estimation Parzen Windows Kn-Nearest
Instance-based Learning CE-717: Machine Learning Sharif University of Technology M. Soleymani Fall 2016 Outline Non-parametric approach Unsupervised: Non-parametric density estimation Parzen Windows Kn-Nearest
Household Energy Disaggregation based on Difference Hidden Markov Model
 1 Household Energy Disaggregation based on Difference Hidden Markov Model Ali Hemmatifar (ahemmati@stanford.edu) Manohar Mogadali (manoharm@stanford.edu) Abstract We aim to address the problem of energy
1 Household Energy Disaggregation based on Difference Hidden Markov Model Ali Hemmatifar (ahemmati@stanford.edu) Manohar Mogadali (manoharm@stanford.edu) Abstract We aim to address the problem of energy
Kaviti Sai Saurab. October 23,2014. IIT Kanpur. Kaviti Sai Saurab (UCLA) Quantum methods in ML October 23, / 8
 A review of Quantum Algorithms for Nearest-Neighbor Methods for Supervised and Unsupervised Learning Nathan Wiebe,Ashish Kapoor,Krysta M. Svore Jan.2014 Kaviti Sai Saurab IIT Kanpur October 23,2014 Kaviti
A review of Quantum Algorithms for Nearest-Neighbor Methods for Supervised and Unsupervised Learning Nathan Wiebe,Ashish Kapoor,Krysta M. Svore Jan.2014 Kaviti Sai Saurab IIT Kanpur October 23,2014 Kaviti
Automated Sensor Verification using Outlier Detection in the Internet of Things
 Automated Sensor Verification using Outlier Detection in the Internet of Things Nauman Javed and Tilman Wolf Department of Electrical and Computer Engineering University of Massachusetts, Amherst, MA,
Automated Sensor Verification using Outlier Detection in the Internet of Things Nauman Javed and Tilman Wolf Department of Electrical and Computer Engineering University of Massachusetts, Amherst, MA,
A signal processing approach to anomaly detection in networks. Kavé Salamatian Université de Savoie
 A signal processing approach to anomaly detection in networks Kavé Salamatian Université de Savoie Acknowledgements Coauthors Daniela Brauckhoff, Martin May, Nahur Fonseca, Mark Crovella, Nina Taft, Augustin
A signal processing approach to anomaly detection in networks Kavé Salamatian Université de Savoie Acknowledgements Coauthors Daniela Brauckhoff, Martin May, Nahur Fonseca, Mark Crovella, Nina Taft, Augustin
Sparsity and Morphological Diversity in Source Separation. Jérôme Bobin IRFU/SEDI-Service d Astrophysique CEA Saclay - France
 Sparsity and Morphological Diversity in Source Separation Jérôme Bobin IRFU/SEDI-Service d Astrophysique CEA Saclay - France Collaborators - Yassir Moudden - CEA Saclay, France - Jean-Luc Starck - CEA
Sparsity and Morphological Diversity in Source Separation Jérôme Bobin IRFU/SEDI-Service d Astrophysique CEA Saclay - France Collaborators - Yassir Moudden - CEA Saclay, France - Jean-Luc Starck - CEA
Preserving Privacy in Data Mining using Data Distortion Approach
 Preserving Privacy in Data Mining using Data Distortion Approach Mrs. Prachi Karandikar #, Prof. Sachin Deshpande * # M.E. Comp,VIT, Wadala, University of Mumbai * VIT Wadala,University of Mumbai 1. prachiv21@yahoo.co.in
Preserving Privacy in Data Mining using Data Distortion Approach Mrs. Prachi Karandikar #, Prof. Sachin Deshpande * # M.E. Comp,VIT, Wadala, University of Mumbai * VIT Wadala,University of Mumbai 1. prachiv21@yahoo.co.in
Randomized Algorithms
 Randomized Algorithms Saniv Kumar, Google Research, NY EECS-6898, Columbia University - Fall, 010 Saniv Kumar 9/13/010 EECS6898 Large Scale Machine Learning 1 Curse of Dimensionality Gaussian Mixture Models
Randomized Algorithms Saniv Kumar, Google Research, NY EECS-6898, Columbia University - Fall, 010 Saniv Kumar 9/13/010 EECS6898 Large Scale Machine Learning 1 Curse of Dimensionality Gaussian Mixture Models
Learning an Optimal Policy for Police Resource Allocation on Freeways
 Brian Jackson Taylor Howell Ola Shorinwa Abstract Anomaly detection is well studied and has applications in surveillance, driver assistance, and navigation. In this project, we develop an anomaly detection
Brian Jackson Taylor Howell Ola Shorinwa Abstract Anomaly detection is well studied and has applications in surveillance, driver assistance, and navigation. In this project, we develop an anomaly detection
Dynamic Probabilistic Models for Latent Feature Propagation in Social Networks
 Dynamic Probabilistic Models for Latent Feature Propagation in Social Networks Creighton Heaukulani and Zoubin Ghahramani University of Cambridge TU Denmark, June 2013 1 A Network Dynamic network data
Dynamic Probabilistic Models for Latent Feature Propagation in Social Networks Creighton Heaukulani and Zoubin Ghahramani University of Cambridge TU Denmark, June 2013 1 A Network Dynamic network data
OVERLAPPING ANIMAL SOUND CLASSIFICATION USING SPARSE REPRESENTATION
 OVERLAPPING ANIMAL SOUND CLASSIFICATION USING SPARSE REPRESENTATION Na Lin, Haixin Sun Xiamen University Key Laboratory of Underwater Acoustic Communication and Marine Information Technology, Ministry
OVERLAPPING ANIMAL SOUND CLASSIFICATION USING SPARSE REPRESENTATION Na Lin, Haixin Sun Xiamen University Key Laboratory of Underwater Acoustic Communication and Marine Information Technology, Ministry
Astroinformatics in the data-driven Astronomy
 Astroinformatics in the data-driven Astronomy Massimo Brescia 2017 ICT Workshop Astronomy vs Astroinformatics Most of the initial time has been spent to find a common language among communities How astronomers
Astroinformatics in the data-driven Astronomy Massimo Brescia 2017 ICT Workshop Astronomy vs Astroinformatics Most of the initial time has been spent to find a common language among communities How astronomers
