Lecture 5. ALOHAnet. ALOHA protocols. Client. Client. Hub. Client
|
|
|
- David Terry
- 5 years ago
- Views:
Transcription
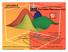
1 Lecture 5 ALOHA protocols ALOHAnet Aloha was a poneerng computer networkng system developed at the Unversty of Hawa n 97 s. The dea was to use rado to create a computer network lnkng the far-flung campuses of the Unversty. The orgnal verson of ALOHA used two dstnct frequences n a hub/star confguraton, wth the hub machne broadcastng packets to everyone on the downlnk channel, and the varous clent machnes sendng data to the hub on the uplnk channel. Clent Hub Clent Clent Data receved was mmedately re-sent, allowng clents to determne whether or not ther data had been receved properly. Any machne notcng corrupted data would wat a short tme and then re-send the packet
2 Infnte user populaton Users wll generate packets accordng to Posson process The aggregate packet arrval rate generated by the users s λ Pure Aloha If staton has a packet t wll mmedately try to transmt t Staton A Packet length s T Staton B t t + T t + T t + 3T 2 The packet generated by staton B colldes f any staton generates a packet on the tme nterval t <t<t +2T
3 Pure Aloha Packets arrve to the system wth ntensty λ Packets collde wth probablty p In case of collson, the packet wll be retransmtted after random back-off tme Aggregate of new packets and faled packets returnng to the transmtter buffer s stll a Posson process wth ntensty g = ( p) λ = λ λ 2 ( ) λ = λ+ λ g = p λ λ 2 μ λ = pλ Pure Aloha Packets arrval process s Posson wth ntensty g packets per second. Transmsson tme of the packet s T Probablty that k packets arrve n tme wndow Δt k gδt( gδt) Pr { k arrvals n Δ t} = e k! Probablty that there s no collson s equal to the probablty that no other packets arrve durng the tme nterval t : < t t + 2T 2 Pr{ no collson} = Pr{ arrvals n 2T} = e g T Normalzed load, average number of arrvals n tme T G=gT Throughput per tme T S = Ge 2G
4 Slotted Aloha If staton has a packet t wll mmedately n the begnnng of the next slot Departures Tme slot T Successful transmsson Collson Collson Successful transmsson Arrvals ~ ~ Busy perod B Idle perod I Cycle Slotted Aloha ~ The pdf for the length of the dle perod I s gven by Pr I = = Pr Some packets arrve durng the frst dle slot { } { } { } = Pr No arrval durng the frst slot = Pr Expected length of the dle perod G e { I = k} = Pr{ No arrvals durng k- frs slots and some arrvals at slot k} k ( ) e e = k {} { } ( ) I = E I = kpr I = k = k e e = e k= k=
5 Slotted Aloha The pdf for the length of the busy perod s gven by Pr B = = Pr No arrval durng the fst busy slot = e gt Pr { } { } { B = k} = Pr{ No arrval durng the fst k- busy slots and some arrvals at slot k} k ( e ) ( e ) = Expected length of the busy perod k B= E{ B } = kpr{ B = k} = k( e ) ( e ) = e k= k= G Slotted Aloha ~ Let U denote the number of useful slots durng the busy perod. That s, the number of slots durng whch there were no collsons. The probablty that a slot n busy perod s successful s Pr{ Busy slot s useful} = Pr{Number of arrvals = Number of arrvals>} Pr{ Number of arrvals=, Number of arrvals >} = Pr{ Number of arrvals>} Pr{ Number of arrvals =} Ge = = Pr Number of arrvals> e { } Expected number of useful slots s G U = Pr{ Busy slot s useful} B= G e
6 Throughput G U S = = e = Ge B+ I + e e Slotted Aloha Slotted Aloha.4.35 Pure ALOHA Slotted ALOHA.3.25 S G
7 Rado channel Consder a rado transmsson system n whch large number of transmtters are sendng packets to a base staton. P 625P α = 4 5 km km P Transmt power tx P,,2, 2 5 = Ptx = α < Receved power r α Power capture phenomena: The receved sgnal-tonterference rato (SIR) from one of the colldng packets s large enough so that t can be decoded successfully Rado channel Packet s receved correctly f the Sgnal-to-Interference Rato (SIR) s larger β P α tx r SIR = > β P α tx r j j Assume that capture occurs only f up to two packets collde and the SIR of the other packet s greater than β: { β } { β } { β } Pcapture = Pr P2 P + Pr P P2 = 2Pr P2 P 2 α α Pcapture 2Pr r β r2 = β
8 Rado channel Probablty of successful transmsson { } = { } + P { } Pr success Pr arrvals n T Pr arrval n T = + e PcaptureGe = e + β 2 α Ge capture Throughput per tme nterval T: 2 α S= GPr{ Success } = G e + β Ge 2 α = Ge + β G Rado channel α=3.5 β= db β=5 db β= db Slotted ALOHA.5 S G
9 Fnte user populaton M users share the channel An user can be n two states Thnkng The user has no packets n the transmsson buffer. The user generates a packet n a gven slot wth probablty σ Once a packet s generated, ts transmsson s attempted mmedately Backlogged If the packet transmsson was unsuccessful, the user enters the backlogged state In a gven slot a backlogged user tres to retransmt wth probablty ν Ths could be nterpreted as defnng geometrcally dstrbuted backoff tme n case of collson Slotted Aloha Fnte number of users Slots are numbered sequentally k=,, Let N(k) denote the number of backlogged users at the begnnng of slot k. N(k) defnes the state of the system The acton of an user depends on the current state of the system, but not on the past states. Hence, the system can be modeled as a Markov chan
10 Slotted Aloha Fnte number of users In steady state, the state probabltes converge to π j = lmk Pr { Nk ( ) = j} and the state transton probabltes converge to p = lm Pr Nk ( ) = jnk ( ) = j M k π = = { } The probabltes fulfll π= πp π = ( π π π ) P = p j M R. Rom and M. Sd, Multple Access Protocols, Sprnger-Verlag, Slotted Aloha Fnte number of users Let us defne j B j N j M j T j N j (, ) = Pr { backlogged users attempt transmsson = } = ν ( ν) (, ) = Pr { thnkng users attempt transmsson = } = σ ( σ) Transton from state to j<- s not possble, snce only one packet can be transmtted n a slot. Hence p j = for j=,,,-2 Transton from stat to tself, p can happen n two ways No new packet s generated No new packet n generated by a thnkng user and the transmsson of the backlogged users result n collson p = B(, ) T(, ) + B( k, T ) (, ) k= j M j
11 Slotted Aloha Fnte number of users Transton from state to j=+, can happen f one new packet s generated and there s collson p+ = B( k, T ) (, ) k= Transton from state to j>+ happens f j- thnkng users generated packet causng collson. The behavor of the backlogged users does not matter n ths case. p = T( j, ), j > + j The transton from state to state j=- occurs f no thnkng users generate packet and there s no collson p ( T ) B = (, ) (, ) Slotted Aloha Fnte number of users Fnally, we get j< M υ( υ) ( σ) j = M M υ( υ) ( σ) + ( M ) ρ( σ) ( υ) j = pj = M ( M ) ρ( σ) ( ( υ) ) j = + M j M j ρ ( σ) j > + j Now, the state probabltes can be solved from π= πp M π = =
12 Slotted Aloha Fnte number of users Probablty of successful transmsson when the number of backlogged users s Psuc () = T(, ) Psuc () = T(,) B(,) + T(,) B(,) M ( ) ( ) M = M σ σ ( υ) + ( σ) υ( υ) Total throughput M S E{ P () } P () π = = In a specal case where ν=σ, we get clearly suc suc = G lmm G = Ge M M M G S = E{ Psuc () } = Mσ ( σ) = G, G = Mσ M M Slotted Aloha Fnte number of users The throughput defnes the departure rate In state there are M- thnkng users generatng packets wth the rate (M-)σ. In stable system the nput and output rates must be equal. Thus we must requre that S = E{ ( M ) σ} = ( M N) σ where N s the average number of backlogged users N N = π =
13 Slotted Aloha Fnte number of users Let b denote the rate packets jon the backlog Snce packets depart from the system at rate S then a fracton of (S-b)/S of the packets are newer backlogged and suffer a delay of tme slot. The fracton of b/s of the packets that are backlogged wll frst have to wat n the backlog for w=n/b (b=nw) slots and thus see an overall delay of N/b+ slots. Hence the average delay n the system s ˆ S b b N D = + + S S b Recall that. S = ( M N) σ S Hence N = M σ and S M + b ˆ S b b M D σ = + = + S S b S σ Slotted Aloha Fnte number of users In a specal case where ν=σ, we get M ˆ ( σ ) D = + M σ ( σ) When M, also D so n the nfnte populaton case, the Aloha protocol becomes unstable When σ, we have D M. Ths mples that although most packets get through wth delay, some packets stll collde and see very large delays. On average the packet delay becomes equal to M
14 Slotted Aloha Fnte number of users The curve s parameterzed wth respect to σ Delay ncreases monotoncally as a functon of σ Throughput ncreases up to a pont after whch t starts to decrease agan Slotted Aloha Capture phenomenon If Mν<< and <<σ<, then capture phenomena s manfested Throughput Mσ S M + ( M ) σ ncreases as a functon of σ! Delay M D M + σ decrease as a functon of σ! R. Rom and M. Sd, Multple Access Protocols, Sprnger-Verlag, 989 The system eventually becomes backlogged, but the probablty that a backlogged user transmts s small. Hence, t s very lkely that a new packet gets transmtted rght away. One user captures the channel for a whle untl there s collson agan
15 Slotted Aloha Capture phenomenon Example packet trace M= σ=.7 ν=. Backlogged state, no transmsson Collson Successful transmsson from backlogged state Successful transmsson from thnkng state Due to hgh transmsson probablty, all users eventually become backlogged Capture Collson Backlogged user has low transmt probablty, but when t fnally transmts and becomes thnkng, she can capture the channel for long tme due to hgh σ (In)Stablty Stablty condton, for the nfnte number of users case: S=Ge -G G => G e In practce the assumpton that the aggregate rate of new packets and backlogged packets s Posson does not hold. Consder the case, n whch the traffc source s generatng packets wth arrval rate λ The arrval rate s only an average rate. The actual arrvals wll fluctuate around ths mean. If the tme average of the mean rate exceeds e - the throughput starts to degrease and the number of backlogged users growng wthout bound. Ths wll happen wth probablty! That s, the ALOHA protocol s nstable
16 (In)Stablty.45 Tme average over 5 slots Arrval rate exceed e - and thus the queues start to grow wthout bound Tme average G Throughput (S) λ Tme wndow Offered Traffc (G) G = λt Arrval process Backlogged users Stablzng Aloha { } a = Pr new packets arrve at slot = a λ = a = { } b( n) = Pr backlogged users transmt at slot n backlogged users Number of backlogged users at slot k when Nk ( ) = b( ) a [ ] + () [ ] wth probablty wth probablty b( ) a b a Nk ( + ) = + wth probablty b( ) a + j, j 2 wth probablty aj 6
17 Stablzng Aloha Expected change n system state durng one tme slot { } ( ) () () ( ) ( ) ( ) ( ) () ( ) j j= 2 E N k+ N k N k = = b a + b a + b a + + j a () () = λ b a b a System s stable f E N ( k+ ) N ( k) N ( k) = = λ b a b a { } ( ) ( ) () () λ < b a + b a Stablzng Aloha Assume that we somehow know how many packets are backlogged and choose the retransmsson probablty based on the state n n b ( n) = υ( n) υ( n) The maxmum arrval rate under whch the system s stable s gven by { ( ) ( ) } λ = lmsup n b n a + b n a n The stablty lmt yelds λ < e log a a + a
18 Defne Stablzng Aloha ( ) ( ) ( ) ( ) n ( ) ( ) Sn υ = b n a + b n a = υ n a + nυ n υ n a Maxmzng the above wth respect to ν yelds * a a ν ( n) = na a The maxmum throughput for gven n s thus n * * n Sn ( υ ) = a a n a The maxmum arrval rate must correspond to the system throughput a ln a + * * a λ < lmn Sn υ = e 35 ( ) n Stablzng Aloha For Posson arrval of packets, we have a ( ) λ λ = e! a = λ a Hence the stablty condton becomes a ln a + a λ < e = e And the probablty for backlogged user to transmt becomes a λ ν ( ) = = for small λ a n n λ n a * a n
19 Stablzng Aloha The mert of ALOHA s beng very smple protocol Its major drawback s that s nstable Stablzaton of the protocol requres knowledge on the system state n whch requres Coordnaton between the transmtters Or Some form of feedback mechansm to be appled ν k + = f ( vk, Feedback of slot k) Stablzng Aloha In practce, the number of retransmsson attempts s lmted. If the maxmum number of transmsson attempts s reach the packet s rejected. In ths manner the system can be stablzed, but the we have to cope wth occasonal packet drop. For smplcty, let us consder the case n whch σ=ν. The probablty of successful transmsson s M M G Psuc = E{ Psuc () } = Mσ ( σ) = G = S M Maxmum number of transmsson attempts s r. Probablty that packet s rejected s R. If retransmsson r attempts are ndependent R= ( S ) + Offered traffc G = RMσ
20 Reverse engneerng ALOHA Strategc games One shot random access game Stategc games Game theory s a form of nteractve decson theory that provdes a rgorous mathematcal formulaton for how decson-makers behave when they nteract. Players n a strategc game choose ther actons smultaneously and ndependently wthout knowng the selectons done by others nor past outcomes of the game. Defnton: A strategc game s the tuple G = N, { A, N},{ u, N} where N denotes the set of players For every N, A s the set of actons avalable to player. For every N, u : x A j R j N s the utlty functon of player showng hs preference over the set of acton profles A
21 Stategc games If the set of actons for every player s fnte, then the game s fnte An acton profle a=(a ) N s an outcome. That s, t defnes the actons taken by the players. An acton profle a A s preferred over acton profle b A only f u (a) u (b) Let Δ(A ) denote the set of all probablty dstrbutons σ on A (σ s the probablty that acton a s selected) There are two types of strateges avalable for the users Pure strategy: Player chooses an acton a A wth probablty. Mxed strategy: Player chooses an acton a A wth probablty σ (a ) Stategc games Defnton: The mxed strategy profle σ* n a strategc game wth s a mxed strategy Nash equlbrum f, for each player and every mxed strategy σ of player, the expected payoff to player of (σ *, σ* - ) s at least as large as the expected payoff to player of (σ, σ* - ). That s, σ = arg max σ, σ ( ) u A ( ) * * σ Δ Furthermore, the mxed strategy Nash equlbrum s sad to be fully mxed f σ non-degenerate. That s for all σ (a )
22 One shot random access game Each player can choose from two actons: a =: Transmt a =: Stay dle The utltes are gven by a = u( a) = a = N c a > Cost nduced by unsuccessful transmsson N One shot random access game Accordng to Inealtekn and Wcker (25), the one shot random access game wtn n players has 2 n - Nash equlbrum ponts: n pure strateges n whch only one node transmts There s one fully mxed nash equlbrum (FMNE) wth c n a = c + Stay dle σ ( a) = c n a = c + Transmt The rest are combnatons of pure and mxed strateges where some of the players choose to stay dle all the tme and the remanng n users use mxed strategy
23 One shot random access game The throughput of the FMNE s gven by c c n Sn ( ) = n c + c + Throughput s maxmzed f n * n c = n n The optmal throughput s gven by * lm n S ( n) e = whch corresponds to the maxmum channel utlzaton of the slotted ALOHA Reverse engneerng ALOHA Furthermore, when n the number of players choosng to transmt converge to Posson dstrbuton For gven c, the throughput S converges to c c S = lm n S( n) = ln + c + c The throughput of slotted aloha n case of nfnte user populaton s S = Ge c The throughput becomes the same f = e. That s, + c e c = e
24 Reverse engneerng ALOHA Convergence of the channel throughput Inaltekn, H.; Wcker, S., "A one-shot random access game for wreless networks, Wreless Networks, Communcatons and Moble Computng, 25 Internatonal Conference on, vol.2, no., pp vol.2, 3-6 June Applcatons of ALOHA ALOHA s utlzed n applcatons where carrer sensng s dffcult or not possble. E.g. In Frequency Dvson Duplexng (FDD), systems transmsson and recevng takes place smultaneously on dfferent frequency bands In under water acoustc communcatons, the propagaton delays are very long (long tme would be needed for carrer sensng n order to detect ongong transmssons)
Queueing Networks II Network Performance
 Queueng Networks II Network Performance Davd Tpper Assocate Professor Graduate Telecommuncatons and Networkng Program Unversty of Pttsburgh Sldes 6 Networks of Queues Many communcaton systems must be modeled
Queueng Networks II Network Performance Davd Tpper Assocate Professor Graduate Telecommuncatons and Networkng Program Unversty of Pttsburgh Sldes 6 Networks of Queues Many communcaton systems must be modeled
Analysis of Discrete Time Queues (Section 4.6)
 Analyss of Dscrete Tme Queues (Secton 4.6) Copyrght 2002, Sanjay K. Bose Tme axs dvded nto slots slot slot boundares Arrvals can only occur at slot boundares Servce to a job can only start at a slot boundary
Analyss of Dscrete Tme Queues (Secton 4.6) Copyrght 2002, Sanjay K. Bose Tme axs dvded nto slots slot slot boundares Arrvals can only occur at slot boundares Servce to a job can only start at a slot boundary
6. Stochastic processes (2)
 Contents Markov processes Brth-death processes Lect6.ppt S-38.45 - Introducton to Teletraffc Theory Sprng 5 Markov process Consder a contnuous-tme and dscrete-state stochastc process X(t) wth state space
Contents Markov processes Brth-death processes Lect6.ppt S-38.45 - Introducton to Teletraffc Theory Sprng 5 Markov process Consder a contnuous-tme and dscrete-state stochastc process X(t) wth state space
6. Stochastic processes (2)
 6. Stochastc processes () Lect6.ppt S-38.45 - Introducton to Teletraffc Theory Sprng 5 6. Stochastc processes () Contents Markov processes Brth-death processes 6. Stochastc processes () Markov process
6. Stochastc processes () Lect6.ppt S-38.45 - Introducton to Teletraffc Theory Sprng 5 6. Stochastc processes () Contents Markov processes Brth-death processes 6. Stochastc processes () Markov process
ECE559VV Project Report
 ECE559VV Project Report (Supplementary Notes Loc Xuan Bu I. MAX SUM-RATE SCHEDULING: THE UPLINK CASE We have seen (n the presentaton that, for downlnk (broadcast channels, the strategy maxmzng the sum-rate
ECE559VV Project Report (Supplementary Notes Loc Xuan Bu I. MAX SUM-RATE SCHEDULING: THE UPLINK CASE We have seen (n the presentaton that, for downlnk (broadcast channels, the strategy maxmzng the sum-rate
TCOM 501: Networking Theory & Fundamentals. Lecture 7 February 25, 2003 Prof. Yannis A. Korilis
 TCOM 501: Networkng Theory & Fundamentals Lecture 7 February 25, 2003 Prof. Yanns A. Korls 1 7-2 Topcs Open Jackson Networks Network Flows State-Dependent Servce Rates Networks of Transmsson Lnes Klenrock
TCOM 501: Networkng Theory & Fundamentals Lecture 7 February 25, 2003 Prof. Yanns A. Korls 1 7-2 Topcs Open Jackson Networks Network Flows State-Dependent Servce Rates Networks of Transmsson Lnes Klenrock
Equilibrium Analysis of the M/G/1 Queue
 Eulbrum nalyss of the M/G/ Queue Copyrght, Sanay K. ose. Mean nalyss usng Resdual Lfe rguments Secton 3.. nalyss usng an Imbedded Marov Chan pproach Secton 3. 3. Method of Supplementary Varables done later!
Eulbrum nalyss of the M/G/ Queue Copyrght, Sanay K. ose. Mean nalyss usng Resdual Lfe rguments Secton 3.. nalyss usng an Imbedded Marov Chan pproach Secton 3. 3. Method of Supplementary Varables done later!
Error Probability for M Signals
 Chapter 3 rror Probablty for M Sgnals In ths chapter we dscuss the error probablty n decdng whch of M sgnals was transmtted over an arbtrary channel. We assume the sgnals are represented by a set of orthonormal
Chapter 3 rror Probablty for M Sgnals In ths chapter we dscuss the error probablty n decdng whch of M sgnals was transmtted over an arbtrary channel. We assume the sgnals are represented by a set of orthonormal
Introduction to Continuous-Time Markov Chains and Queueing Theory
 Introducton to Contnuous-Tme Markov Chans and Queueng Theory From DTMC to CTMC p p 1 p 12 1 2 k-1 k p k-1,k p k-1,k k+1 p 1 p 21 p k,k-1 p k,k-1 DTMC 1. Transtons at dscrete tme steps n=,1,2, 2. Past doesn
Introducton to Contnuous-Tme Markov Chans and Queueng Theory From DTMC to CTMC p p 1 p 12 1 2 k-1 k p k-1,k p k-1,k k+1 p 1 p 21 p k,k-1 p k,k-1 DTMC 1. Transtons at dscrete tme steps n=,1,2, 2. Past doesn
Resource Allocation with a Budget Constraint for Computing Independent Tasks in the Cloud
 Resource Allocaton wth a Budget Constrant for Computng Independent Tasks n the Cloud Wemng Sh and Bo Hong School of Electrcal and Computer Engneerng Georga Insttute of Technology, USA 2nd IEEE Internatonal
Resource Allocaton wth a Budget Constrant for Computng Independent Tasks n the Cloud Wemng Sh and Bo Hong School of Electrcal and Computer Engneerng Georga Insttute of Technology, USA 2nd IEEE Internatonal
Problem Set 9 - Solutions Due: April 27, 2005
 Problem Set - Solutons Due: Aprl 27, 2005. (a) Frst note that spam messages, nvtatons and other e-mal are all ndependent Posson processes, at rates pλ, qλ, and ( p q)λ. The event of the tme T at whch you
Problem Set - Solutons Due: Aprl 27, 2005. (a) Frst note that spam messages, nvtatons and other e-mal are all ndependent Posson processes, at rates pλ, qλ, and ( p q)λ. The event of the tme T at whch you
Queuing system theory
 Elements of queung system: Queung system theory Every queung system conssts of three elements: An arrval process: s characterzed by the dstrbuton of tme between the arrval of successve customers, the mean
Elements of queung system: Queung system theory Every queung system conssts of three elements: An arrval process: s characterzed by the dstrbuton of tme between the arrval of successve customers, the mean
COMPARISON OF SOME RELIABILITY CHARACTERISTICS BETWEEN REDUNDANT SYSTEMS REQUIRING SUPPORTING UNITS FOR THEIR OPERATIONS
 Avalable onlne at http://sck.org J. Math. Comput. Sc. 3 (3), No., 6-3 ISSN: 97-537 COMPARISON OF SOME RELIABILITY CHARACTERISTICS BETWEEN REDUNDANT SYSTEMS REQUIRING SUPPORTING UNITS FOR THEIR OPERATIONS
Avalable onlne at http://sck.org J. Math. Comput. Sc. 3 (3), No., 6-3 ISSN: 97-537 COMPARISON OF SOME RELIABILITY CHARACTERISTICS BETWEEN REDUNDANT SYSTEMS REQUIRING SUPPORTING UNITS FOR THEIR OPERATIONS
CS 798: Homework Assignment 2 (Probability)
 0 Sample space Assgned: September 30, 2009 In the IEEE 802 protocol, the congeston wndow (CW) parameter s used as follows: ntally, a termnal wats for a random tme perod (called backoff) chosen n the range
0 Sample space Assgned: September 30, 2009 In the IEEE 802 protocol, the congeston wndow (CW) parameter s used as follows: ntally, a termnal wats for a random tme perod (called backoff) chosen n the range
2E Pattern Recognition Solutions to Introduction to Pattern Recognition, Chapter 2: Bayesian pattern classification
 E395 - Pattern Recognton Solutons to Introducton to Pattern Recognton, Chapter : Bayesan pattern classfcaton Preface Ths document s a soluton manual for selected exercses from Introducton to Pattern Recognton
E395 - Pattern Recognton Solutons to Introducton to Pattern Recognton, Chapter : Bayesan pattern classfcaton Preface Ths document s a soluton manual for selected exercses from Introducton to Pattern Recognton
Chapter 7 Channel Capacity and Coding
 Wreless Informaton Transmsson System Lab. Chapter 7 Channel Capacty and Codng Insttute of Communcatons Engneerng atonal Sun Yat-sen Unversty Contents 7. Channel models and channel capacty 7.. Channel models
Wreless Informaton Transmsson System Lab. Chapter 7 Channel Capacty and Codng Insttute of Communcatons Engneerng atonal Sun Yat-sen Unversty Contents 7. Channel models and channel capacty 7.. Channel models
Cognitive Access Algorithms For Multiple Access Channels
 203 IEEE 4th Workshop on Sgnal Processng Advances n Wreless Communcatons SPAWC) Cogntve Access Algorthms For Multple Access Channels Ychuan Hu and Alejandro Rbero, Department of Electrcal and Systems Engneerng,
203 IEEE 4th Workshop on Sgnal Processng Advances n Wreless Communcatons SPAWC) Cogntve Access Algorthms For Multple Access Channels Ychuan Hu and Alejandro Rbero, Department of Electrcal and Systems Engneerng,
The optimal delay of the second test is therefore approximately 210 hours earlier than =2.
 THE IEC 61508 FORMULAS 223 The optmal delay of the second test s therefore approxmately 210 hours earler than =2. 8.4 The IEC 61508 Formulas IEC 61508-6 provdes approxmaton formulas for the PF for smple
THE IEC 61508 FORMULAS 223 The optmal delay of the second test s therefore approxmately 210 hours earler than =2. 8.4 The IEC 61508 Formulas IEC 61508-6 provdes approxmaton formulas for the PF for smple
P R. Lecture 4. Theory and Applications of Pattern Recognition. Dept. of Electrical and Computer Engineering /
 Theory and Applcatons of Pattern Recognton 003, Rob Polkar, Rowan Unversty, Glassboro, NJ Lecture 4 Bayes Classfcaton Rule Dept. of Electrcal and Computer Engneerng 0909.40.0 / 0909.504.04 Theory & Applcatons
Theory and Applcatons of Pattern Recognton 003, Rob Polkar, Rowan Unversty, Glassboro, NJ Lecture 4 Bayes Classfcaton Rule Dept. of Electrcal and Computer Engneerng 0909.40.0 / 0909.504.04 Theory & Applcatons
Externalities in wireless communication: A public goods solution approach to power allocation. by Shrutivandana Sharma
 Externaltes n wreless communcaton: A publc goods soluton approach to power allocaton by Shrutvandana Sharma SI 786 Tuesday, Feb 2, 2006 Outlne Externaltes: Introducton Plannng wth externaltes Power allocaton:
Externaltes n wreless communcaton: A publc goods soluton approach to power allocaton by Shrutvandana Sharma SI 786 Tuesday, Feb 2, 2006 Outlne Externaltes: Introducton Plannng wth externaltes Power allocaton:
An Upper Bound on SINR Threshold for Call Admission Control in Multiple-Class CDMA Systems with Imperfect Power-Control
 An Upper Bound on SINR Threshold for Call Admsson Control n Multple-Class CDMA Systems wth Imperfect ower-control Mahmoud El-Sayes MacDonald, Dettwler and Assocates td. (MDA) Toronto, Canada melsayes@hotmal.com
An Upper Bound on SINR Threshold for Call Admsson Control n Multple-Class CDMA Systems wth Imperfect ower-control Mahmoud El-Sayes MacDonald, Dettwler and Assocates td. (MDA) Toronto, Canada melsayes@hotmal.com
Suggested solutions for the exam in SF2863 Systems Engineering. June 12,
 Suggested solutons for the exam n SF2863 Systems Engneerng. June 12, 2012 14.00 19.00 Examner: Per Enqvst, phone: 790 62 98 1. We can thnk of the farm as a Jackson network. The strawberry feld s modelled
Suggested solutons for the exam n SF2863 Systems Engneerng. June 12, 2012 14.00 19.00 Examner: Per Enqvst, phone: 790 62 98 1. We can thnk of the farm as a Jackson network. The strawberry feld s modelled
Lecture 4: November 17, Part 1 Single Buffer Management
 Lecturer: Ad Rosén Algorthms for the anagement of Networs Fall 2003-2004 Lecture 4: November 7, 2003 Scrbe: Guy Grebla Part Sngle Buffer anagement In the prevous lecture we taled about the Combned Input
Lecturer: Ad Rosén Algorthms for the anagement of Networs Fall 2003-2004 Lecture 4: November 7, 2003 Scrbe: Guy Grebla Part Sngle Buffer anagement In the prevous lecture we taled about the Combned Input
Composite Hypotheses testing
 Composte ypotheses testng In many hypothess testng problems there are many possble dstrbutons that can occur under each of the hypotheses. The output of the source s a set of parameters (ponts n a parameter
Composte ypotheses testng In many hypothess testng problems there are many possble dstrbutons that can occur under each of the hypotheses. The output of the source s a set of parameters (ponts n a parameter
Chapter 7 Channel Capacity and Coding
 Chapter 7 Channel Capacty and Codng Contents 7. Channel models and channel capacty 7.. Channel models Bnary symmetrc channel Dscrete memoryless channels Dscrete-nput, contnuous-output channel Waveform
Chapter 7 Channel Capacty and Codng Contents 7. Channel models and channel capacty 7.. Channel models Bnary symmetrc channel Dscrete memoryless channels Dscrete-nput, contnuous-output channel Waveform
Participation Incentives on a Wireless Random Access Erasure Collision Channel
 Partcpaton Incentves on a Wreless Random Access Erasure Collson Channel [Short talk] ABSTRACT Vasls Gkatzels Drexel Unversty Department of Computer Scence Phladelpha, PA gkatz@drexel.edu Random medum access
Partcpaton Incentves on a Wreless Random Access Erasure Collson Channel [Short talk] ABSTRACT Vasls Gkatzels Drexel Unversty Department of Computer Scence Phladelpha, PA gkatz@drexel.edu Random medum access
Pricing Network Services by Jun Shu, Pravin Varaiya
 Prcng Network Servces by Jun Shu, Pravn Varaya Presented by Hayden So September 25, 2003 Introducton: Two Network Problems Engneerng: A game theoretcal sound congeston control mechansm that s ncentve compatble
Prcng Network Servces by Jun Shu, Pravn Varaya Presented by Hayden So September 25, 2003 Introducton: Two Network Problems Engneerng: A game theoretcal sound congeston control mechansm that s ncentve compatble
Communication with AWGN Interference
 Communcaton wth AWG Interference m {m } {p(m } Modulator s {s } r=s+n Recever ˆm AWG n m s a dscrete random varable(rv whch takes m wth probablty p(m. Modulator maps each m nto a waveform sgnal s m=m
Communcaton wth AWG Interference m {m } {p(m } Modulator s {s } r=s+n Recever ˆm AWG n m s a dscrete random varable(rv whch takes m wth probablty p(m. Modulator maps each m nto a waveform sgnal s m=m
Tornado and Luby Transform Codes. Ashish Khisti Presentation October 22, 2003
 Tornado and Luby Transform Codes Ashsh Khst 6.454 Presentaton October 22, 2003 Background: Erasure Channel Elas[956] studed the Erasure Channel β x x β β x 2 m x 2 k? Capacty of Noseless Erasure Channel
Tornado and Luby Transform Codes Ashsh Khst 6.454 Presentaton October 22, 2003 Background: Erasure Channel Elas[956] studed the Erasure Channel β x x β β x 2 m x 2 k? Capacty of Noseless Erasure Channel
Applied Stochastic Processes
 STAT455/855 Fall 23 Appled Stochastc Processes Fnal Exam, Bref Solutons 1. (15 marks) (a) (7 marks) The dstrbuton of Y s gven by ( ) ( ) y 2 1 5 P (Y y) for y 2, 3,... The above follows because each of
STAT455/855 Fall 23 Appled Stochastc Processes Fnal Exam, Bref Solutons 1. (15 marks) (a) (7 marks) The dstrbuton of Y s gven by ( ) ( ) y 2 1 5 P (Y y) for y 2, 3,... The above follows because each of
Concepts for Wireless Ad Hoc
 Bandwdth and Avalable Bandwdth oncepts for Wreless Ad Hoc Networks Marco A. Alzate Unversdad Dstrtal, Bogotá Néstor M. Peña Unversdad de los Andes, Bogotá Mguel A. abrador Unversty of South Florda, Tampa
Bandwdth and Avalable Bandwdth oncepts for Wreless Ad Hoc Networks Marco A. Alzate Unversdad Dstrtal, Bogotá Néstor M. Peña Unversdad de los Andes, Bogotá Mguel A. abrador Unversty of South Florda, Tampa
Maximum Likelihood Estimation of Binary Dependent Variables Models: Probit and Logit. 1. General Formulation of Binary Dependent Variables Models
 ECO 452 -- OE 4: Probt and Logt Models ECO 452 -- OE 4 Maxmum Lkelhood Estmaton of Bnary Dependent Varables Models: Probt and Logt hs note demonstrates how to formulate bnary dependent varables models
ECO 452 -- OE 4: Probt and Logt Models ECO 452 -- OE 4 Maxmum Lkelhood Estmaton of Bnary Dependent Varables Models: Probt and Logt hs note demonstrates how to formulate bnary dependent varables models
Lectures - Week 4 Matrix norms, Conditioning, Vector Spaces, Linear Independence, Spanning sets and Basis, Null space and Range of a Matrix
 Lectures - Week 4 Matrx norms, Condtonng, Vector Spaces, Lnear Independence, Spannng sets and Bass, Null space and Range of a Matrx Matrx Norms Now we turn to assocatng a number to each matrx. We could
Lectures - Week 4 Matrx norms, Condtonng, Vector Spaces, Lnear Independence, Spannng sets and Bass, Null space and Range of a Matrx Matrx Norms Now we turn to assocatng a number to each matrx. We could
Secret Communication using Artificial Noise
 Secret Communcaton usng Artfcal Nose Roht Neg, Satashu Goel C Department, Carnege Mellon Unversty, PA 151, USA {neg,satashug}@ece.cmu.edu Abstract The problem of secret communcaton between two nodes over
Secret Communcaton usng Artfcal Nose Roht Neg, Satashu Goel C Department, Carnege Mellon Unversty, PA 151, USA {neg,satashug}@ece.cmu.edu Abstract The problem of secret communcaton between two nodes over
Fixed Point Analysis of Single Cell IEEE e WLANs: Uniqueness, Multistability and Throughput Differentiation
 Fxed Pont Analyss of Sngle Cell IEEE 82.e WLANs: Unqueness, Multstablty and Throughput Dfferentaton Venkatesh Ramayan ECE Department Indan Insttute of Scence Bangalore, Inda rvenkat@ece.sc.ernet.n Anurag
Fxed Pont Analyss of Sngle Cell IEEE 82.e WLANs: Unqueness, Multstablty and Throughput Dfferentaton Venkatesh Ramayan ECE Department Indan Insttute of Scence Bangalore, Inda rvenkat@ece.sc.ernet.n Anurag
CIE4801 Transportation and spatial modelling Trip distribution
 CIE4801 ransportaton and spatal modellng rp dstrbuton Rob van Nes, ransport & Plannng 17/4/13 Delft Unversty of echnology Challenge the future Content What s t about hree methods Wth specal attenton for
CIE4801 ransportaton and spatal modellng rp dstrbuton Rob van Nes, ransport & Plannng 17/4/13 Delft Unversty of echnology Challenge the future Content What s t about hree methods Wth specal attenton for
Lossy Compression. Compromise accuracy of reconstruction for increased compression.
 Lossy Compresson Compromse accuracy of reconstructon for ncreased compresson. The reconstructon s usually vsbly ndstngushable from the orgnal mage. Typcally, one can get up to 0:1 compresson wth almost
Lossy Compresson Compromse accuracy of reconstructon for ncreased compresson. The reconstructon s usually vsbly ndstngushable from the orgnal mage. Typcally, one can get up to 0:1 compresson wth almost
CS286r Assign One. Answer Key
 CS286r Assgn One Answer Key 1 Game theory 1.1 1.1.1 Let off-equlbrum strateges also be that people contnue to play n Nash equlbrum. Devatng from any Nash equlbrum s a weakly domnated strategy. That s,
CS286r Assgn One Answer Key 1 Game theory 1.1 1.1.1 Let off-equlbrum strateges also be that people contnue to play n Nash equlbrum. Devatng from any Nash equlbrum s a weakly domnated strategy. That s,
Distributed Optimal TXOP Control for Throughput Requirements in IEEE e Wireless LAN
 Dstrbuted Optmal TXOP Control for Throughput Requrements n IEEE 80.e Wreless LAN Ju Yong Lee, Ho Young Hwang, Jtae Shn, and Shahrokh Valaee KAIST Insttute for Informaton Technology Convergence, KAIST,
Dstrbuted Optmal TXOP Control for Throughput Requrements n IEEE 80.e Wreless LAN Ju Yong Lee, Ho Young Hwang, Jtae Shn, and Shahrokh Valaee KAIST Insttute for Informaton Technology Convergence, KAIST,
IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 59, NO. 5, JUNE
 IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 59, NO. 5, JUNE 2010 2511 Optmal Confguraton of 802.11e EDCA for Real-Tme and Data Traffc Pablo Serrano, Member, IEEE, Albert Banchs, Member, IEEE, Paul
IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 59, NO. 5, JUNE 2010 2511 Optmal Confguraton of 802.11e EDCA for Real-Tme and Data Traffc Pablo Serrano, Member, IEEE, Albert Banchs, Member, IEEE, Paul
Turing Machines (intro)
 CHAPTER 3 The Church-Turng Thess Contents Turng Machnes defntons, examples, Turng-recognzable and Turng-decdable languages Varants of Turng Machne Multtape Turng machnes, non-determnstc Turng Machnes,
CHAPTER 3 The Church-Turng Thess Contents Turng Machnes defntons, examples, Turng-recognzable and Turng-decdable languages Varants of Turng Machne Multtape Turng machnes, non-determnstc Turng Machnes,
Outline. Communication. Bellman Ford Algorithm. Bellman Ford Example. Bellman Ford Shortest Path [1]
![Outline. Communication. Bellman Ford Algorithm. Bellman Ford Example. Bellman Ford Shortest Path [1] Outline. Communication. Bellman Ford Algorithm. Bellman Ford Example. Bellman Ford Shortest Path [1]](/thumbs/81/84170417.jpg) DYNAMIC SHORTEST PATH SEARCH AND SYNCHRONIZED TASK SWITCHING Jay Wagenpfel, Adran Trachte 2 Outlne Shortest Communcaton Path Searchng Bellmann Ford algorthm Algorthm for dynamc case Modfcatons to our algorthm
DYNAMIC SHORTEST PATH SEARCH AND SYNCHRONIZED TASK SWITCHING Jay Wagenpfel, Adran Trachte 2 Outlne Shortest Communcaton Path Searchng Bellmann Ford algorthm Algorthm for dynamc case Modfcatons to our algorthm
Convergence of random processes
 DS-GA 12 Lecture notes 6 Fall 216 Convergence of random processes 1 Introducton In these notes we study convergence of dscrete random processes. Ths allows to characterze phenomena such as the law of large
DS-GA 12 Lecture notes 6 Fall 216 Convergence of random processes 1 Introducton In these notes we study convergence of dscrete random processes. Ths allows to characterze phenomena such as the law of large
(1 ) (1 ) 0 (1 ) (1 ) 0
 Appendx A Appendx A contans proofs for resubmsson "Contractng Informaton Securty n the Presence of Double oral Hazard" Proof of Lemma 1: Assume that, to the contrary, BS efforts are achevable under a blateral
Appendx A Appendx A contans proofs for resubmsson "Contractng Informaton Securty n the Presence of Double oral Hazard" Proof of Lemma 1: Assume that, to the contrary, BS efforts are achevable under a blateral
The Gaussian classifier. Nuno Vasconcelos ECE Department, UCSD
 he Gaussan classfer Nuno Vasconcelos ECE Department, UCSD Bayesan decson theory recall that we have state of the world X observatons g decson functon L[g,y] loss of predctng y wth g Bayes decson rule s
he Gaussan classfer Nuno Vasconcelos ECE Department, UCSD Bayesan decson theory recall that we have state of the world X observatons g decson functon L[g,y] loss of predctng y wth g Bayes decson rule s
The Second Anti-Mathima on Game Theory
 The Second Ant-Mathma on Game Theory Ath. Kehagas December 1 2006 1 Introducton In ths note we wll examne the noton of game equlbrum for three types of games 1. 2-player 2-acton zero-sum games 2. 2-player
The Second Ant-Mathma on Game Theory Ath. Kehagas December 1 2006 1 Introducton In ths note we wll examne the noton of game equlbrum for three types of games 1. 2-player 2-acton zero-sum games 2. 2-player
MAXIMIZING THE THROUGHPUT OF CDMA DATA COMMUNICATIONS THROUGH JOINT ADMISSION AND POWER CONTROL
 MAXIMIZI THE THROUHPUT OF CDMA DATA COMMUICATIOS THROUH JOIT ADMISSIO AD POWER COTROL Penna Orensten, Davd oodman and Zory Marantz Department of Electrcal and Computer Engneerng Polytechnc Unversty Brooklyn,
MAXIMIZI THE THROUHPUT OF CDMA DATA COMMUICATIOS THROUH JOIT ADMISSIO AD POWER COTROL Penna Orensten, Davd oodman and Zory Marantz Department of Electrcal and Computer Engneerng Polytechnc Unversty Brooklyn,
CS-433: Simulation and Modeling Modeling and Probability Review
 CS-433: Smulaton and Modelng Modelng and Probablty Revew Exercse 1. (Probablty of Smple Events) Exercse 1.1 The owner of a camera shop receves a shpment of fve cameras from a camera manufacturer. Unknown
CS-433: Smulaton and Modelng Modelng and Probablty Revew Exercse 1. (Probablty of Smple Events) Exercse 1.1 The owner of a camera shop receves a shpment of fve cameras from a camera manufacturer. Unknown
Tit-For-Tat Equilibria in Discounted Repeated Games with. Private Monitoring
 1 Tt-For-Tat Equlbra n Dscounted Repeated Games wth Prvate Montorng Htosh Matsushma 1 Department of Economcs, Unversty of Tokyo 2 Aprl 24, 2007 Abstract We nvestgate nfntely repeated games wth mperfect
1 Tt-For-Tat Equlbra n Dscounted Repeated Games wth Prvate Montorng Htosh Matsushma 1 Department of Economcs, Unversty of Tokyo 2 Aprl 24, 2007 Abstract We nvestgate nfntely repeated games wth mperfect
Online Appendix. t=1 (p t w)q t. Then the first order condition shows that
 Artcle forthcomng to ; manuscrpt no (Please, provde the manuscrpt number!) 1 Onlne Appendx Appendx E: Proofs Proof of Proposton 1 Frst we derve the equlbrum when the manufacturer does not vertcally ntegrate
Artcle forthcomng to ; manuscrpt no (Please, provde the manuscrpt number!) 1 Onlne Appendx Appendx E: Proofs Proof of Proposton 1 Frst we derve the equlbrum when the manufacturer does not vertcally ntegrate
Dynamic Programming. Lecture 13 (5/31/2017)
 Dynamc Programmng Lecture 13 (5/31/2017) - A Forest Thnnng Example - Projected yeld (m3/ha) at age 20 as functon of acton taken at age 10 Age 10 Begnnng Volume Resdual Ten-year Volume volume thnned volume
Dynamc Programmng Lecture 13 (5/31/2017) - A Forest Thnnng Example - Projected yeld (m3/ha) at age 20 as functon of acton taken at age 10 Age 10 Begnnng Volume Resdual Ten-year Volume volume thnned volume
Lecture 3: Shannon s Theorem
 CSE 533: Error-Correctng Codes (Autumn 006 Lecture 3: Shannon s Theorem October 9, 006 Lecturer: Venkatesan Guruswam Scrbe: Wdad Machmouch 1 Communcaton Model The communcaton model we are usng conssts
CSE 533: Error-Correctng Codes (Autumn 006 Lecture 3: Shannon s Theorem October 9, 006 Lecturer: Venkatesan Guruswam Scrbe: Wdad Machmouch 1 Communcaton Model The communcaton model we are usng conssts
EGR 544 Communication Theory
 EGR 544 Communcaton Theory. Informaton Sources Z. Alyazcoglu Electrcal and Computer Engneerng Department Cal Poly Pomona Introducton Informaton Source x n Informaton sources Analog sources Dscrete sources
EGR 544 Communcaton Theory. Informaton Sources Z. Alyazcoglu Electrcal and Computer Engneerng Department Cal Poly Pomona Introducton Informaton Source x n Informaton sources Analog sources Dscrete sources
DISCRETE TIME ATTACKER-DEFENDER GAME
 JP Journal of Appled Mathematcs Volume 5, Issue, 7, Pages 35-6 7 Ishaan Publshng House Ths paper s avalable onlne at http://www.phsc.com DISCRETE TIME ATTACKER-DEFENDER GAME Faculty of Socal and Economc
JP Journal of Appled Mathematcs Volume 5, Issue, 7, Pages 35-6 7 Ishaan Publshng House Ths paper s avalable onlne at http://www.phsc.com DISCRETE TIME ATTACKER-DEFENDER GAME Faculty of Socal and Economc
A Game-Theoretic Framework for Medium Access Control
 IEEE JOURNAL ON SELECTED AREAS OF COMMUNICATIONS, VOL. XX, NO. XX, DECEMBER 28 A Game-Theoretc Framework for Medum Access Control Tao Cu, Ljun Chen, Member, IEEE, and Steven H. Low, Fellow, IEEE Abstract
IEEE JOURNAL ON SELECTED AREAS OF COMMUNICATIONS, VOL. XX, NO. XX, DECEMBER 28 A Game-Theoretc Framework for Medum Access Control Tao Cu, Ljun Chen, Member, IEEE, and Steven H. Low, Fellow, IEEE Abstract
A Lower Bound on SINR Threshold for Call Admission Control in Multiple-Class CDMA Systems with Imperfect Power-Control
 A ower Bound on SIR Threshold for Call Admsson Control n Multple-Class CDMA Systems w Imperfect ower-control Mohamed H. Ahmed Faculty of Engneerng and Appled Scence Memoral Unversty of ewfoundland St.
A ower Bound on SIR Threshold for Call Admsson Control n Multple-Class CDMA Systems w Imperfect ower-control Mohamed H. Ahmed Faculty of Engneerng and Appled Scence Memoral Unversty of ewfoundland St.
Simulation and Random Number Generation
 Smulaton and Random Number Generaton Summary Dscrete Tme vs Dscrete Event Smulaton Random number generaton Generatng a random sequence Generatng random varates from a Unform dstrbuton Testng the qualty
Smulaton and Random Number Generaton Summary Dscrete Tme vs Dscrete Event Smulaton Random number generaton Generatng a random sequence Generatng random varates from a Unform dstrbuton Testng the qualty
CHAPTER 5 NUMERICAL EVALUATION OF DYNAMIC RESPONSE
 CHAPTER 5 NUMERICAL EVALUATION OF DYNAMIC RESPONSE Analytcal soluton s usually not possble when exctaton vares arbtrarly wth tme or f the system s nonlnear. Such problems can be solved by numercal tmesteppng
CHAPTER 5 NUMERICAL EVALUATION OF DYNAMIC RESPONSE Analytcal soluton s usually not possble when exctaton vares arbtrarly wth tme or f the system s nonlnear. Such problems can be solved by numercal tmesteppng
Order Optimal Delay for Opportunistic Scheduling in Multi-User Wireless Uplinks and Downlinks
 IEEE TRANSACTIONS ON NETWORKING, VOL. 16, NO. 5, PP. 1188-1199, OCT. 008 1 Order Optmal Delay for Opportunstc Schedulng n Mult-User Wreless Uplnks and Downlnks Mchael J. Neely Unversty of Southern Calforna
IEEE TRANSACTIONS ON NETWORKING, VOL. 16, NO. 5, PP. 1188-1199, OCT. 008 1 Order Optmal Delay for Opportunstc Schedulng n Mult-User Wreless Uplnks and Downlnks Mchael J. Neely Unversty of Southern Calforna
Week3, Chapter 4. Position and Displacement. Motion in Two Dimensions. Instantaneous Velocity. Average Velocity
 Week3, Chapter 4 Moton n Two Dmensons Lecture Quz A partcle confned to moton along the x axs moves wth constant acceleraton from x =.0 m to x = 8.0 m durng a 1-s tme nterval. The velocty of the partcle
Week3, Chapter 4 Moton n Two Dmensons Lecture Quz A partcle confned to moton along the x axs moves wth constant acceleraton from x =.0 m to x = 8.0 m durng a 1-s tme nterval. The velocty of the partcle
4 Analysis of Variance (ANOVA) 5 ANOVA. 5.1 Introduction. 5.2 Fixed Effects ANOVA
 4 Analyss of Varance (ANOVA) 5 ANOVA 51 Introducton ANOVA ANOVA s a way to estmate and test the means of multple populatons We wll start wth one-way ANOVA If the populatons ncluded n the study are selected
4 Analyss of Varance (ANOVA) 5 ANOVA 51 Introducton ANOVA ANOVA s a way to estmate and test the means of multple populatons We wll start wth one-way ANOVA If the populatons ncluded n the study are selected
Probability and Random Variable Primer
 B. Maddah ENMG 622 Smulaton 2/22/ Probablty and Random Varable Prmer Sample space and Events Suppose that an eperment wth an uncertan outcome s performed (e.g., rollng a de). Whle the outcome of the eperment
B. Maddah ENMG 622 Smulaton 2/22/ Probablty and Random Varable Prmer Sample space and Events Suppose that an eperment wth an uncertan outcome s performed (e.g., rollng a de). Whle the outcome of the eperment
Introduction to Algorithms
 Introducton to Algorthms 6.046J/8.40J Lecture 7 Prof. Potr Indyk Data Structures Role of data structures: Encapsulate data Support certan operatons (e.g., INSERT, DELETE, SEARCH) Our focus: effcency of
Introducton to Algorthms 6.046J/8.40J Lecture 7 Prof. Potr Indyk Data Structures Role of data structures: Encapsulate data Support certan operatons (e.g., INSERT, DELETE, SEARCH) Our focus: effcency of
TAIL BOUNDS FOR SUMS OF GEOMETRIC AND EXPONENTIAL VARIABLES
 TAIL BOUNDS FOR SUMS OF GEOMETRIC AND EXPONENTIAL VARIABLES SVANTE JANSON Abstract. We gve explct bounds for the tal probabltes for sums of ndependent geometrc or exponental varables, possbly wth dfferent
TAIL BOUNDS FOR SUMS OF GEOMETRIC AND EXPONENTIAL VARIABLES SVANTE JANSON Abstract. We gve explct bounds for the tal probabltes for sums of ndependent geometrc or exponental varables, possbly wth dfferent
Hopfield networks and Boltzmann machines. Geoffrey Hinton et al. Presented by Tambet Matiisen
 Hopfeld networks and Boltzmann machnes Geoffrey Hnton et al. Presented by Tambet Matsen 18.11.2014 Hopfeld network Bnary unts Symmetrcal connectons http://www.nnwj.de/hopfeld-net.html Energy functon The
Hopfeld networks and Boltzmann machnes Geoffrey Hnton et al. Presented by Tambet Matsen 18.11.2014 Hopfeld network Bnary unts Symmetrcal connectons http://www.nnwj.de/hopfeld-net.html Energy functon The
Notes on Frequency Estimation in Data Streams
 Notes on Frequency Estmaton n Data Streams In (one of) the data streamng model(s), the data s a sequence of arrvals a 1, a 2,..., a m of the form a j = (, v) where s the dentty of the tem and belongs to
Notes on Frequency Estmaton n Data Streams In (one of) the data streamng model(s), the data s a sequence of arrvals a 1, a 2,..., a m of the form a j = (, v) where s the dentty of the tem and belongs to
Continuous Time Markov Chain
 Contnuous Tme Markov Chan Hu Jn Department of Electroncs and Communcaton Engneerng Hanyang Unversty ERICA Campus Contents Contnuous tme Markov Chan (CTMC) Propertes of sojourn tme Relatons Transton probablty
Contnuous Tme Markov Chan Hu Jn Department of Electroncs and Communcaton Engneerng Hanyang Unversty ERICA Campus Contents Contnuous tme Markov Chan (CTMC) Propertes of sojourn tme Relatons Transton probablty
Equilibrium with Complete Markets. Instructor: Dmytro Hryshko
 Equlbrum wth Complete Markets Instructor: Dmytro Hryshko 1 / 33 Readngs Ljungqvst and Sargent. Recursve Macroeconomc Theory. MIT Press. Chapter 8. 2 / 33 Equlbrum n pure exchange, nfnte horzon economes,
Equlbrum wth Complete Markets Instructor: Dmytro Hryshko 1 / 33 Readngs Ljungqvst and Sargent. Recursve Macroeconomc Theory. MIT Press. Chapter 8. 2 / 33 Equlbrum n pure exchange, nfnte horzon economes,
Module 3 LOSSY IMAGE COMPRESSION SYSTEMS. Version 2 ECE IIT, Kharagpur
 Module 3 LOSSY IMAGE COMPRESSION SYSTEMS Verson ECE IIT, Kharagpur Lesson 6 Theory of Quantzaton Verson ECE IIT, Kharagpur Instructonal Objectves At the end of ths lesson, the students should be able to:
Module 3 LOSSY IMAGE COMPRESSION SYSTEMS Verson ECE IIT, Kharagpur Lesson 6 Theory of Quantzaton Verson ECE IIT, Kharagpur Instructonal Objectves At the end of ths lesson, the students should be able to:
Application of Queuing Theory to Waiting Time of Out-Patients in Hospitals.
 Applcaton of Queung Theory to Watng Tme of Out-Patents n Hosptals. R.A. Adeleke *, O.D. Ogunwale, and O.Y. Hald. Department of Mathematcal Scences, Unversty of Ado-Ekt, Ado-Ekt, Ekt State, Ngera. E-mal:
Applcaton of Queung Theory to Watng Tme of Out-Patents n Hosptals. R.A. Adeleke *, O.D. Ogunwale, and O.Y. Hald. Department of Mathematcal Scences, Unversty of Ado-Ekt, Ado-Ekt, Ekt State, Ngera. E-mal:
3.1 Expectation of Functions of Several Random Variables. )' be a k-dimensional discrete or continuous random vector, with joint PMF p (, E X E X1 E X
 Statstcs 1: Probablty Theory II 37 3 EPECTATION OF SEVERAL RANDOM VARIABLES As n Probablty Theory I, the nterest n most stuatons les not on the actual dstrbuton of a random vector, but rather on a number
Statstcs 1: Probablty Theory II 37 3 EPECTATION OF SEVERAL RANDOM VARIABLES As n Probablty Theory I, the nterest n most stuatons les not on the actual dstrbuton of a random vector, but rather on a number
CS : Algorithms and Uncertainty Lecture 17 Date: October 26, 2016
 CS 29-128: Algorthms and Uncertanty Lecture 17 Date: October 26, 2016 Instructor: Nkhl Bansal Scrbe: Mchael Denns 1 Introducton In ths lecture we wll be lookng nto the secretary problem, and an nterestng
CS 29-128: Algorthms and Uncertanty Lecture 17 Date: October 26, 2016 Instructor: Nkhl Bansal Scrbe: Mchael Denns 1 Introducton In ths lecture we wll be lookng nto the secretary problem, and an nterestng
Distributions /06. G.Serazzi 05/06 Dimensionamento degli Impianti Informatici distrib - 1
 Dstrbutons 8/03/06 /06 G.Serazz 05/06 Dmensonamento degl Impant Informatc dstrb - outlne densty, dstrbuton, moments unform dstrbuton Posson process, eponental dstrbuton Pareto functon densty and dstrbuton
Dstrbutons 8/03/06 /06 G.Serazz 05/06 Dmensonamento degl Impant Informatc dstrb - outlne densty, dstrbuton, moments unform dstrbuton Posson process, eponental dstrbuton Pareto functon densty and dstrbuton
Pricing and Resource Allocation Game Theoretic Models
 Prcng and Resource Allocaton Game Theoretc Models Zhy Huang Changbn Lu Q Zhang Computer and Informaton Scence December 8, 2009 Z. Huang, C. Lu, and Q. Zhang (CIS) Game Theoretc Models December 8, 2009
Prcng and Resource Allocaton Game Theoretc Models Zhy Huang Changbn Lu Q Zhang Computer and Informaton Scence December 8, 2009 Z. Huang, C. Lu, and Q. Zhang (CIS) Game Theoretc Models December 8, 2009
j) = 1 (note sigma notation) ii. Continuous random variable (e.g. Normal distribution) 1. density function: f ( x) 0 and f ( x) dx = 1
 Random varables Measure of central tendences and varablty (means and varances) Jont densty functons and ndependence Measures of assocaton (covarance and correlaton) Interestng result Condtonal dstrbutons
Random varables Measure of central tendences and varablty (means and varances) Jont densty functons and ndependence Measures of assocaton (covarance and correlaton) Interestng result Condtonal dstrbutons
Lecture 7: Boltzmann distribution & Thermodynamics of mixing
 Prof. Tbbtt Lecture 7 etworks & Gels Lecture 7: Boltzmann dstrbuton & Thermodynamcs of mxng 1 Suggested readng Prof. Mark W. Tbbtt ETH Zürch 13 März 018 Molecular Drvng Forces Dll and Bromberg: Chapters
Prof. Tbbtt Lecture 7 etworks & Gels Lecture 7: Boltzmann dstrbuton & Thermodynamcs of mxng 1 Suggested readng Prof. Mark W. Tbbtt ETH Zürch 13 März 018 Molecular Drvng Forces Dll and Bromberg: Chapters
Market structure and Innovation
 Market structure and Innovaton Ths presentaton s based on the paper Market structure and Innovaton authored by Glenn C. Loury, publshed n The Quarterly Journal of Economcs, Vol. 93, No.3 ( Aug 1979) I.
Market structure and Innovaton Ths presentaton s based on the paper Market structure and Innovaton authored by Glenn C. Loury, publshed n The Quarterly Journal of Economcs, Vol. 93, No.3 ( Aug 1979) I.
See Book Chapter 11 2 nd Edition (Chapter 10 1 st Edition)
 Count Data Models See Book Chapter 11 2 nd Edton (Chapter 10 1 st Edton) Count data consst of non-negatve nteger values Examples: number of drver route changes per week, the number of trp departure changes
Count Data Models See Book Chapter 11 2 nd Edton (Chapter 10 1 st Edton) Count data consst of non-negatve nteger values Examples: number of drver route changes per week, the number of trp departure changes
1 Derivation of Rate Equations from Single-Cell Conductance (Hodgkin-Huxley-like) Equations
 Physcs 171/271 -Davd Klenfeld - Fall 2005 (revsed Wnter 2011) 1 Dervaton of Rate Equatons from Sngle-Cell Conductance (Hodgkn-Huxley-lke) Equatons We consder a network of many neurons, each of whch obeys
Physcs 171/271 -Davd Klenfeld - Fall 2005 (revsed Wnter 2011) 1 Dervaton of Rate Equatons from Sngle-Cell Conductance (Hodgkn-Huxley-lke) Equatons We consder a network of many neurons, each of whch obeys
The Mixed Strategy Nash Equilibrium of the Television News Scheduling Game
 The Mxed Strategy Nash Equlbrum of the Televson News Schedulng Game Jean Gabszewcz Dder Laussel Mchel Le Breton July 007 Abstract We characterze the unque mxed-strategy equlbrum of an extenson of the "televson
The Mxed Strategy Nash Equlbrum of the Televson News Schedulng Game Jean Gabszewcz Dder Laussel Mchel Le Breton July 007 Abstract We characterze the unque mxed-strategy equlbrum of an extenson of the "televson
Analysis of Queuing Delay in Multimedia Gateway Call Routing
 Analyss of Queung Delay n Multmeda ateway Call Routng Qwe Huang UTtarcom Inc, 33 Wood Ave. outh Iseln, NJ 08830, U..A Errol Lloyd Computer Informaton cences Department, Unv. of Delaware, Newark, DE 976,
Analyss of Queung Delay n Multmeda ateway Call Routng Qwe Huang UTtarcom Inc, 33 Wood Ave. outh Iseln, NJ 08830, U..A Errol Lloyd Computer Informaton cences Department, Unv. of Delaware, Newark, DE 976,
Markov chains. Definition of a CTMC: [2, page 381] is a continuous time, discrete value random process such that for an infinitesimal
![Markov chains. Definition of a CTMC: [2, page 381] is a continuous time, discrete value random process such that for an infinitesimal Markov chains. Definition of a CTMC: [2, page 381] is a continuous time, discrete value random process such that for an infinitesimal](/thumbs/77/76061795.jpg) Markov chans M. Veeraraghavan; March 17, 2004 [Tp: Study the MC, QT, and Lttle s law lectures together: CTMC (MC lecture), M/M/1 queue (QT lecture), Lttle s law lecture (when dervng the mean response tme
Markov chans M. Veeraraghavan; March 17, 2004 [Tp: Study the MC, QT, and Lttle s law lectures together: CTMC (MC lecture), M/M/1 queue (QT lecture), Lttle s law lecture (when dervng the mean response tme
1960 IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS, VOL. 13, NO. 4, APRIL 2014
 1960 IEEE TRANSACTIONS ON WIRELESS COUNICATIONS, VOL. 13, NO. 4, APRIL 2014 Dynamc Chnese Restaurant Game: Theory and Applcaton to Cogntve Rado Networks Chunxao Jang, ember, IEEE, Yan Chen, ember, IEEE,
1960 IEEE TRANSACTIONS ON WIRELESS COUNICATIONS, VOL. 13, NO. 4, APRIL 2014 Dynamc Chnese Restaurant Game: Theory and Applcaton to Cogntve Rado Networks Chunxao Jang, ember, IEEE, Yan Chen, ember, IEEE,
Maximum Likelihood Estimation of Binary Dependent Variables Models: Probit and Logit. 1. General Formulation of Binary Dependent Variables Models
 ECO 452 -- OE 4: Probt and Logt Models ECO 452 -- OE 4 Mamum Lkelhood Estmaton of Bnary Dependent Varables Models: Probt and Logt hs note demonstrates how to formulate bnary dependent varables models for
ECO 452 -- OE 4: Probt and Logt Models ECO 452 -- OE 4 Mamum Lkelhood Estmaton of Bnary Dependent Varables Models: Probt and Logt hs note demonstrates how to formulate bnary dependent varables models for
Canonical transformations
 Canoncal transformatons November 23, 2014 Recall that we have defned a symplectc transformaton to be any lnear transformaton M A B leavng the symplectc form nvarant, Ω AB M A CM B DΩ CD Coordnate transformatons,
Canoncal transformatons November 23, 2014 Recall that we have defned a symplectc transformaton to be any lnear transformaton M A B leavng the symplectc form nvarant, Ω AB M A CM B DΩ CD Coordnate transformatons,
Cournot Equilibrium with N firms
 Recap Last class (September 8, Thursday) Examples of games wth contnuous acton sets Tragedy of the commons Duopoly models: ournot o class on Sept. 13 due to areer Far Today (September 15, Thursday) Duopoly
Recap Last class (September 8, Thursday) Examples of games wth contnuous acton sets Tragedy of the commons Duopoly models: ournot o class on Sept. 13 due to areer Far Today (September 15, Thursday) Duopoly
Prof. Dr. I. Nasser Phys 630, T Aug-15 One_dimensional_Ising_Model
 EXACT OE-DIMESIOAL ISIG MODEL The one-dmensonal Isng model conssts of a chan of spns, each spn nteractng only wth ts two nearest neghbors. The smple Isng problem n one dmenson can be solved drectly n several
EXACT OE-DIMESIOAL ISIG MODEL The one-dmensonal Isng model conssts of a chan of spns, each spn nteractng only wth ts two nearest neghbors. The smple Isng problem n one dmenson can be solved drectly n several
Game Theory. Lecture Notes By Y. Narahari. Department of Computer Science and Automation Indian Institute of Science Bangalore, India February 2008
 Game Theory Lecture Notes By Y. Narahar Department of Computer Scence and Automaton Indan Insttute of Scence Bangalore, Inda February 2008 Chapter 10: Two Person Zero Sum Games Note: Ths s a only a draft
Game Theory Lecture Notes By Y. Narahar Department of Computer Scence and Automaton Indan Insttute of Scence Bangalore, Inda February 2008 Chapter 10: Two Person Zero Sum Games Note: Ths s a only a draft
IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS, VOL. 16, NO. 12, DECEMBER
 IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS, VOL. 16, NO. 12, DECEMBER 2017 7687 Cogntve Herarchy Theory for Dstrbuted Resource Allocaton n the Internet of Thngs Nof Abuzanab, Wald Saad, Senor Member,
IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS, VOL. 16, NO. 12, DECEMBER 2017 7687 Cogntve Herarchy Theory for Dstrbuted Resource Allocaton n the Internet of Thngs Nof Abuzanab, Wald Saad, Senor Member,
Econ107 Applied Econometrics Topic 3: Classical Model (Studenmund, Chapter 4)
 I. Classcal Assumptons Econ7 Appled Econometrcs Topc 3: Classcal Model (Studenmund, Chapter 4) We have defned OLS and studed some algebrac propertes of OLS. In ths topc we wll study statstcal propertes
I. Classcal Assumptons Econ7 Appled Econometrcs Topc 3: Classcal Model (Studenmund, Chapter 4) We have defned OLS and studed some algebrac propertes of OLS. In ths topc we wll study statstcal propertes
Smooth Games, Price of Anarchy and Composability of Auctions - a Quick Tutorial
 Smooth Games, Prce of Anarchy and Composablty of Auctons - a Quck Tutoral Abhshek Snha Laboratory for Informaton and Decson Systems, Massachusetts Insttute of Technology, Cambrdge, MA 02139 Emal: snhaa@mt.edu
Smooth Games, Prce of Anarchy and Composablty of Auctons - a Quck Tutoral Abhshek Snha Laboratory for Informaton and Decson Systems, Massachusetts Insttute of Technology, Cambrdge, MA 02139 Emal: snhaa@mt.edu
A note on almost sure behavior of randomly weighted sums of φ-mixing random variables with φ-mixing weights
 ACTA ET COMMENTATIONES UNIVERSITATIS TARTUENSIS DE MATHEMATICA Volume 7, Number 2, December 203 Avalable onlne at http://acutm.math.ut.ee A note on almost sure behavor of randomly weghted sums of φ-mxng
ACTA ET COMMENTATIONES UNIVERSITATIS TARTUENSIS DE MATHEMATICA Volume 7, Number 2, December 203 Avalable onlne at http://acutm.math.ut.ee A note on almost sure behavor of randomly weghted sums of φ-mxng
Economics 101. Lecture 4 - Equilibrium and Efficiency
 Economcs 0 Lecture 4 - Equlbrum and Effcency Intro As dscussed n the prevous lecture, we wll now move from an envronment where we looed at consumers mang decsons n solaton to analyzng economes full of
Economcs 0 Lecture 4 - Equlbrum and Effcency Intro As dscussed n the prevous lecture, we wll now move from an envronment where we looed at consumers mang decsons n solaton to analyzng economes full of
Meenu Gupta, Man Singh & Deepak Gupta
 IJS, Vol., o. 3-4, (July-December 0, pp. 489-497 Serals Publcatons ISS: 097-754X THE STEADY-STATE SOLUTIOS OF ULTIPLE PARALLEL CHAELS I SERIES AD O-SERIAL ULTIPLE PARALLEL CHAELS BOTH WITH BALKIG & REEGIG
IJS, Vol., o. 3-4, (July-December 0, pp. 489-497 Serals Publcatons ISS: 097-754X THE STEADY-STATE SOLUTIOS OF ULTIPLE PARALLEL CHAELS I SERIES AD O-SERIAL ULTIPLE PARALLEL CHAELS BOTH WITH BALKIG & REEGIG
J. Parallel Distrib. Comput.
 J. Parallel Dstrb. Comput. 7 (20) 537 555 Contents lsts avalable at ScenceDrect J. Parallel Dstrb. Comput. ournal homepage: www.elsever.com/locate/pdc Game-theoretc statc load balancng for dstrbuted systems
J. Parallel Dstrb. Comput. 7 (20) 537 555 Contents lsts avalable at ScenceDrect J. Parallel Dstrb. Comput. ournal homepage: www.elsever.com/locate/pdc Game-theoretc statc load balancng for dstrbuted systems
Polynomial Regression Models
 LINEAR REGRESSION ANALYSIS MODULE XII Lecture - 6 Polynomal Regresson Models Dr. Shalabh Department of Mathematcs and Statstcs Indan Insttute of Technology Kanpur Test of sgnfcance To test the sgnfcance
LINEAR REGRESSION ANALYSIS MODULE XII Lecture - 6 Polynomal Regresson Models Dr. Shalabh Department of Mathematcs and Statstcs Indan Insttute of Technology Kanpur Test of sgnfcance To test the sgnfcance
Introduction to Vapor/Liquid Equilibrium, part 2. Raoult s Law:
 CE304, Sprng 2004 Lecture 4 Introducton to Vapor/Lqud Equlbrum, part 2 Raoult s Law: The smplest model that allows us do VLE calculatons s obtaned when we assume that the vapor phase s an deal gas, and
CE304, Sprng 2004 Lecture 4 Introducton to Vapor/Lqud Equlbrum, part 2 Raoult s Law: The smplest model that allows us do VLE calculatons s obtaned when we assume that the vapor phase s an deal gas, and
COMPLETE BUFFER SHARING IN ATM NETWORKS UNDER BURSTY ARRIVALS
 COMPLETE BUFFER SHARING WITH PUSHOUT THRESHOLDS IN ATM NETWORKS UNDER BURSTY ARRIVALS Ozgur Aras and Tugrul Dayar Abstract. Broadband Integrated Servces Dgtal Networks (B{ISDNs) are to support multple
COMPLETE BUFFER SHARING WITH PUSHOUT THRESHOLDS IN ATM NETWORKS UNDER BURSTY ARRIVALS Ozgur Aras and Tugrul Dayar Abstract. Broadband Integrated Servces Dgtal Networks (B{ISDNs) are to support multple
Lecture 10 Support Vector Machines II
 Lecture 10 Support Vector Machnes II 22 February 2016 Taylor B. Arnold Yale Statstcs STAT 365/665 1/28 Notes: Problem 3 s posted and due ths upcomng Frday There was an early bug n the fake-test data; fxed
Lecture 10 Support Vector Machnes II 22 February 2016 Taylor B. Arnold Yale Statstcs STAT 365/665 1/28 Notes: Problem 3 s posted and due ths upcomng Frday There was an early bug n the fake-test data; fxed
Asynchronous CSMA Policies in Multihop Wireless Networks with Primary Interference Constraints
 Asynchronous CSMA Polces n Multhop Wreless Networks wth Prmary Interference Constrants Peter Marbach, Atlla Erylmaz, and Asu Ozdaglar Abstract We analyze Asynchronous Carrer Sense Multple Access (CSMA)
Asynchronous CSMA Polces n Multhop Wreless Networks wth Prmary Interference Constrants Peter Marbach, Atlla Erylmaz, and Asu Ozdaglar Abstract We analyze Asynchronous Carrer Sense Multple Access (CSMA)
