Local Outlier Detection with Interpretation
|
|
|
- Howard Caldwell
- 5 years ago
- Views:
Transcription
1 Local Outlier Detection with Interpretation Xuan Hong Dang, Barbora Micenková, Ira Assent, and Raymond T. Ng 2 Aarhus University, Denmark, {dang,barbora,ira}@cs.au.dk 2 University of British Columbia, Canada, rng@cs.ubc.ca Abstract. Outlier detection aims at searching for a small set of objects that are inconsistent or considerably deviating from other objects in a dataset. Existing research focuses on outlier identification while omitting the equally important problem of outlier interpretation. This paper presents a novel method named LODI to address both problems at the same time. In LODI, we develop an approach that explores the quadratic entropy to adaptively select a set of neighboring instances, and a learning method to seek an optimal subspace in which an outlier is maximally separated from its neighbors. We show that this learning task can be optimally solved via the matrix eigen-decomposition and its solution contains all essential information to reveal which features in the original data space are the most important to interpret the exceptional properties of outliers. We demonstrate the appealing performance of LODI via a number of synthetic and real world datasets and compare its outlier detection rates against state-of-the-art algorithms. Introduction Data mining aims at searching for novel and actionable knowledge from data. Mining techniques can generally be divided into four main categories: clustering, classification, frequent pattern mining and anomalies detection. Unlike the first three main tasks whose objective is to find patterns that characterize for majority data, the fourth one aims at finding patterns that only represent the minority data. Such kind of patterns usually do not fit well to the mechanisms that have generated the data and are often referred to as outliers, anomalies or surprising patterns. Mining that sort of rare patterns therefore poses novel issues and challenges. Yet, they are of interest and particularly important in a number of real world applications ranging from bioinformatics [27], direct marketing [8], to various types of fraud detection [4]. Outlying patterns may be divided into two types: global and local outliers. A global outlier is an object which has a significantly large distance to its k-th nearest neighbor (usually greater than a global threshold) whereas a local outlier has a distance to its k-th neighbor that is large relatively to the average distance of its neighbors to their own k-th nearest neighbors [6]. Although it is also possible to create a ranking of global outliers (and select the top outliers), it is noted in [6, 3] that the notion of local outliers remains more general than that of global outliers and, usually, a global outlier is also a local one but not vice versa, making the methods to discover local outliers typically more computationally Part of this work has been supported by the Danish Council for Independent Research - Technology and Production Sciences (FTP), grant -8972
2 2 expensive. In this study, our objective is to focus on mining and interpreting local outliers. Although there is a large number of techniques for discovering global and local anomalous patterns [28, 25], most attempts focus solely on the aspect of outlier identification, ignoring the equally important problem of outlier interpretation. For many application domains, especially those with data described by a large number of features, the description/intepretation of outliers is essential. As such, an outlier should be explained clearly and compactly, like a subset of features, that shows its exceptionality. This knowledge obviously assists the user to evaluate the validity of the uncovered outliers. More importantly, it offers him/her a facility to gain insights into why an outlier is exceptionally different from other regular objects. To our best knowledge, the study developed in [3] is the only attempt that directly addresses this issue, yet for global outliers but not for the more challenging patterns of local outliers (shortly reviewed in Section 2). In this work, we introduce a novel approach that achieves both objectives of local outlier detection and interpretation at the same time. We propose a technique relying on the information theoretic measure of entropy to select an appropriate set of neighboring objects of an outlier candidate. Unlike most existing methods which often select the k closest objects as neighbors, our proposed technique goes further by requiring strong interconnections (or high entropy) amongst all neighboring members. This helps to remove irrelevant objects that can be nearby outliers or the objects coming from other distributions, and thus ensures all remaining objects to be truly normal inliers generated by the same distribution (illustrated via examples later). This characteristic is crucial since the statistical properties of the neighborhood play an essential role in our explanation of the outlierness. We then develop a method, whose solution firmly relies on the matrix eigen-decomposition, to learn an optimal one-dimensional subspace in which an outlier is most distinguishable from its neighboring set. The basic idea behind this approach is to consider the local outlier detection problem as a binary classification and thus ensure that a single dimension is sufficient to discriminate an outlier from its vicinity. The induced dimension is in essence a linear combination of the original features and thus contains all intrinsic information to reveal which original features are the most important to explain outliers. A visualization associated with the outlier interpretation is provided for intuitive understanding. Our explanation form not only shows the relevant features but also ranks objects according to their outlierness. 2 Related Work Studies in outlier detection can generally be divided into two categories stemming from: (i) statistics and (ii) data mining. In the statistical approach, most methods assume that the observed data are governed by some statistical process to which a standard probability distribution (e.g., Binomial, Gaussian, Poisson etc.) with appropriate parameters can be fitted to. An object is identified as an outlier based on how unlikely it could have been generated by that distribution [2]. Data mining techniques, on the other hand, attempt to avoid model assumptions; relying on the concepts of distance and density, as stated earlier.
3 3 For most distance-based methods [2, 26], two parameters called distance d and data fraction p are required. Following that, an outlier has at least fraction p of all instances farther than d from it [2]. As both d and p are parameters defined over the entire data, methods based on distance can only find global outliers. Techniques relying on density, in contrast, attempt to seek local outliers, whose outlying degrees ( local outlier factor LOF) are defined w.r.t. their neighborhoods rather than the entire dataset [3, 6]. There are several recent studies that attempt to find outliers in spaces with reduced dimensionality. Some of them consider every single dimension [] or every combination of two dimensions [7] as the reduced dimensional subspaces, others [9, ] go further in refining the number of relevant subspaces. While the work in [9] makes assumptions that outliers can only exist in subspaces with non-uniform distributions, the method developed in [] assumes that outliers only appear in subspaces showing high dependencies amongst their related dimensions. These studies, exploring either subspace projections [9, ] or subspace samplings [8,, 7], appear to be appropriate for the purpose of outlier interpretation. Nonetheless, as the outlier score of an object is aggregated from multiple spaces, it remains unclear which subspace should be selected to interpret its outlierness property. In addition, the number of explored subspaces for every object should be large in order to obtain good outlier ranking results. These techniques are hence closer to outlier ensembles [24] rather than outlier interpretation. The recent SOD method [4] pursues a slightly different approach in which it seeks an axis-parallel hyperplane (w.r.t. an object) as one spanned by the attributes with the highest data variances. The anomaly degree of the object is thus computed in the space orthogonal to this hyperplane. This technique also adopts an approach based on the shared neighbors between two objects to measure their similarity, which alleviates the almost equi-distance effect among all instances in a high dimensional space and thus can achieve better selection for neighboring sets. SOD was demonstrated to be effective in uncovering outliers that deviate from the most variance attributes yet it seems somewhat limited in searching outliers having extreme values in such directions. A similar approach is adopted in [6] where the subspace can be arbitrarily oriented (not only axis-parallel) and a form of outlier characterization based on vector directions have been proposed. ABOD [5] pursues a different approach where variance of angles among objects is taken into account to compute outlierness, making the method suitable for high dimensional data. In terms of outlier detection, we provide experimental comparisons with state-of-the-art algorithms in Section 4. 3 Our Approach In this work, we consider X = {x, x 2,..., x N } a dataset of N instances and each x i X is represented as a vector in a D-dimensional space. Each dimension represents a feature f to f D. We aim for an algorithm that can rank the objects in X w.r.t. their outlier degrees with the most outlying objects on the top. Having been queried for M outliers in X, the algorithm returns the top M outliers and for a threshold λ (, ) (to be clear in Section 3.3), each outlier x i is associated with a small set of features {f (xi),..., f (xi) }, d D explaining d
4 4 why the object is exceptional. The value of d may vary across different outliers. In addition, f (x i),..., f (x i) d are also weighted according to the degree to which they contribute to discriminate x i as an outlier. 3. Neighboring Set Selection Compared to global anomalous patterns, mining local outliers is generally harder and more challenging since it has to further deal with the problem of locally different densities in the data distribution. An outlier is considered anomalous if its density value is significantly different from the average density computed from the neighboring objects. The anomalous property of an outlier is thus decided by the local density distribution rather than the global knowledge derived from the entire distribution. For most existing studies [3, 4], the set of k nearest neighboring objects (knns) is used. Nonetheless, this approach has not been thoroughly investigated and may be misleading for outlier explanation. The difficulty comes from the fact that identifying a proper value of k is not only a non-trivial task [2, 3] but such a set of k closest neighbors might also contain nearby outliers or inliers from several distributions, which both strongly affect the statistical properties of the neighboring set. To give an illustration, we borrow a very popular data set from subspace clustering [22, 7] which includes four clusters in a 3-dimensional space with 2 outliers randomly added as shown in Figure (a). Each cluster is only visible in 2-dimensional subspace [7] and each outlier is considered anomalous w.r.t. its closest cluster. Now taking the outlier o as an example, regardless of how small k is selected, other nearby outliers such as o 2, o 3 or o 4 are included in its neighbors since they are amongst the closest objects (see Figure (a)). On the other hand, increasing k to include more inliers from the upper distribution can alleviate the effect of these outliers on the o s anomalous property. Unfortunately, such a large setting also comprises instances from the lower right distribution as shown in Figure (b). To cope with these issues, our objective is to ensure that all o s neighbors are truly inliers coming from a single closest distribution and thus o can be considered as its local outlier. Our proposed approach to handle this issue stems from the well-studied concept of entropy in information theory. The technique is adaptive by not fixing the number of neighboring inliers k. Instead, we only use k as a lower bound to ensure that the number of final nearby inliers is no less than k. In information theory, entropy is used to measure the uncertainty (or disorder) of a stochastic event. Following the definition by Shannon, the entropy of that event is defined by H(X) = p(x) log p(x)dx, of which X is the stochastic event or more specifically, a continuous random variable, and p(x) is its corresponding probability distribution. If the entropy of X is large, its purity is low, or equivalently, X s uncertainty is high. Therefore, it is natural to exploit entropy for our task of selecting neighboring inliers. Intuitively, for the entropy computed with respect to this set, we would expect its value to be small in order to infer that objects within the set are all similar (i.e., high purity) and thus there is a high possibility that they are being generated from the same statistical mechanism or distribution. Nonetheless, computing entropy in Shannon s definition is not an easy task since it requires p(x) to be known. We thus utilize
5 f (a) f f.5 o 3 o 2 o.5 o 4 f (b) - f f.5 - o 3 o o 4 o.5 Information potential 365 st large gap (c) 2nd large gap Index of nearby instances.5 f (d) f f.5 o Fig.. Neighbors selection: object under consideration is o and circle points are its nearest neighbors (figures are best visualized in colors). a more general form, the Renyi entropy [23], which enables a straightforward computation. Mathematically, given α as an order, Renyi entropy is defined as: H Rα (X) = α log p(x) α dx, for α >, α. () in which Shannon entropy is a special case when α is approaching (i.e., lim α H Rα (X) = H(X) [23]). However, in order to ensure the practical computation and impose no assumption regarding the probability distribution p(x), we select α = 2, yielding the quadratic form of entropy, and use the nonparametric Parzen window technique to estimate p(x). More specifically, let us denote R(o) = {x, x 2,..., x s } as the initial set of nearest neighboring instances closest to an outlier candidate o. Following the Parzen window technique, we approximate p(x) w.r.t. this set via the sum of kernels placed at each {x i } s i= and it follows that: p(x) = s G(x x i, σ 2 ) (2) s i= } { x xi 2 2σ 2 where G(x x i, σ 2 ) = (2πσ) D/2 exp is the Gaussian in the D- dimensional space used as the kernel function. In combination with setting α = 2, this leads to a direct computation of the local quadratic Renyi entropy as follows: ( ) s QE(R(o)) = ln G(x x i, σ 2 ) s G(x x j, σ 2 ) s s = ln s 2 s i i= j= s G(x i x j, 2σ 2 ) (3) j Notice that, unlike Shannon entropy, the above computation removes burden of the computation of the numerical integration due to the advantages of the quadratic form and the convolution property of two Gaussian functions. Essentially, the sum within the logarithm operation can be interpreted as the local information potential. Each term in the summation satisfies the positivity and increases as the distance between x i and x j decreases, very much analogous to the potential energy between two physical particles. As such, our objective of minimizing the entropy is equivalent to maximizing the information potential within the neighboring set. The higher the information potential of the set is, the more similar the elements within the set are. Having the way to capture the local quadratic entropy, an appropriate set of nearest neighbors can be selected adaptively as follows. We begin by setting the number of initial nearest neighbors to s (in our experiments, a setting of
6 6 s = 2k often gives good results), and aim to find an optimal subset of no less than k instances with maximum local information potential. Obviously, a naive way to find such an optimal set may require computing all s ( s ) i=k i possible combinations, which is prohibitively expensive. We thus make use of an heuristic approach to select such a subset. Specifically, removing an object from the neighboring set will lead to a decrement in the total information potential. Those instances resulting in the most decrement are important ones whereas those causing least decrement tend to be irrelevant for the neighboring set. With the latter objects, their potential energy is minor as they loosely interact with the rest of neighboring objects and thus excluding them makes the neighboring set less uncertain or more pure. These objects in fact can be either other outliers or part of nearby distributions. Our method thus ranks the total information potential left in the increasing order and removes objects behind the first significant gap as long as the number of remaining instances is no less than k. A significant gap is defined to have a value larger than the average gap. For illustration, we plot in Figure (c) the total information potential left (ordered increasingly) after excluding each of nearest neighboring objects represented in Figure (b). One may observe that there are two remarkably large gaps in the plot (noted by the red vertical lines in Figure (c)), which indeed reflect the nature of local distribution surrounding outlier o. In particular, the first large gap signifies the information decrement in removing instances from the lower right distribution whereas the second one corresponds to the removal of nearby outliers. By excluding these irrelevant objects from the set of o s neighboring instances, the remaining ones are true inliers coming from the same and closest distribution shown as blue points in Figure (d). 3.2 Anomaly Degree Computation Given a way to compute the neighboring (or reference ) set above, we develop a method to calculate the anomaly degree for each object in the dataset X. Essentially, directly computing that measure in the original multidimensional data space is often less reliable since many features may not be relevant for the task of identifying local outliers. We thus exploit an approach of a local dimensionality reduction. For the remaining discussion, let us denote o as an outlier candidate under consideration, R(o) as its neighboring inliers found by the entropy-based technique presented in the previous section and R as the matrix form of R(o). Each neighboring inlier x i R(o) corresponds to a column in R and together with o, they are all vectors in the R D space. Essentially, we view the local outlier detection as a binary classification problem in the sense that the outlier candidate o should be distinguished from its neighbors R(o). By dimensionality reduction, this objective is equivalent to the objective of learning an optimal subspace such that o is maximally separated from every object in R(o). More specifically, o needs to be strongly deviating from R(o) while at the same time R(o) shows high density or low variance in that induced subspace. Following this approach, we denote the optimal -dimensional subspace as w and in order to achieve our goal, data variance is obviously an
7 7 important statistical measure to explore. Toward this goal, we define the first variance of all neighboring objects projected onto w as follows: V ar(r(o)) = w T ( R Ree T /N o ) ( R Ree T /N o ) T w = w T AA T w (4) where A = ( R Ree T /N o ), No is the number of neighboring instances in R(o) and e is the vector with all entries equal to. Another important statistic in our approach is the distance between o and every object in R(o). This resembles an average proximity in a hierarchical clustering technique[9] where all pairwise data distances are taken into account. Compared to the two extremes of using minimum or maximum distance, this measure often shows better stability. We hence formulate their variance in the projected dimension w as the following quantity: D (o,r(o)) = w T ( (o xi )(o x i ) T ) w = w T BB T w, (5) where x i R(o) and B is defined as the matrix whose each column corresponds to a vector (o x i ). Intuitively, in order to achieve the goal of optimally distinguishing o from its neighboring reference inliers, we want to learn a direction for w such that the variance of R(o) projected onto it is minimized whereas the variance between o and R(o) also projected on that direction is maximized. One possible way to do that is to form an objective function resembling Rayleigh s quotient which maximizes the ratio between D (o,r(o)) and R(o) as follows: arg maxj(w) = D (o,r(o)) w V ar(r(o)) = wt BB T w w T AA T w. (6) It is obvious that setting the derivative of J(w) w.r.t. w equal to results in (w T BB T w)aa T w = (w T AA T w)bb T w, which is in essence equivalent to solving the following generalized eigensystem: J(w)AA T w = BB T w. (7) Dealing with this objective function, notice that AA T, though symmetric, may not be full rank (i.e., singular) because the number of neighboring instances can be smaller than the number of original features. This matrix is thus not directly invertible. Moreover, the size of AA T can be large and quadratically proportional to the feature number which makes its eigendecomposition computationally expensive. To alleviate this problem, we propose to only approximate A via its singular value decomposition and thus w can be computed using the pseudo inversion of AA T. Specifically, since A in general is a rectangular matrix, it can be decomposed into three matrices A = UΣV T of which U and V are matrices whose columns are A s left and right singular eigenvectors and Σ is the diagonal matrix of its singular values. In essence, as our objective is to compute matrix inversion, we remove singular values which are very close to and approximate A by its set of leading singular values and vectors. More concretely, we estimate A = l u lσ l vl T such that the sum over keeping singular values σ l s explains for 95% (as demonstrated in our experimental studies) of the total values in the
8 8 diagonal matrix Σ. Additionally, we compute U via the eigendecomposition of A T A which has a lower dimensionality. Particularly, we can see that: A T A = VΣ 2 V T. (8) Then, taking the square of both sides and pre-multiplying with Σ V T and post-multiplying with VΣ, we obtain: Σ V T A T (AA T )AVΣ = Σ 2 U T (AA T )U = Σ 2. (9) This implies that columns in U are the eigenvectors of AA T and they can be computed via the eigenvectors of the smaller matrix A T A, i.e., U = AVΣ. Thus, the final pseudo inversion (AA T ) can be simply approximated by UΣ 2 U T. Plugging this value into our objective function in Eq.(7), it is straightforward to see that the optimal direction for w is the first eigenvector of the matrix UΣ 2 U T BB T of which J(w) achieves the maximum value as the largest eigenvalue of this matrix. Given the optimal direction w uncovered by the technique developed above, the statistical distance between o and R(o) can be calculated in terms of the standard deviation as follows: (w T o w T x i i N AD(o) = max o ) T (w T o w T x i i N o ), V ar(r(o)) V ar(r(o)) () where the second term in the max operation is added to ensure that the projection of o is not too close to the center of the projected neighboring instances (calculated in the first term). Notice that unlike most techniques that find multiple subspaces and have to deal with the problem of dimensionality bias [2], our approach naturally avoids this issue since it learns a -dimensional subspace and thus directly enables a comparison across objects. Therefore, with the objective of generating an outlier ranking over all objects, the relative difference between the statistical distance of an object o defined above and that of its neighboring objects is used to define its local anomalous degree: LAD(o) = AD(o) ( AD(xi )/N o ). () For this relative outlier measure, it is easy to see that if o is a regular object embedded in a cluster, its local anomaly degree is close to whereas if it is a true outlier, the value will be greater than. 3.3 Outlier Interpretation In interpreting the anomaly degree of an outlier, it is possible to rely on the correlation between the projected data in w and those in each of the original dimensions (i.e., R s rows). Features with highest absolute values can be used to interpret the anomaly degree of o since values of o and its referenced objects on these features are correlated to those projected onto w. Nonetheless, this approach requires computing correlations with respect to all original features. A better and more direct approach is to exploit the optimal direction w directly.
9 9 Recall that the projection of R(o) over w is equivalent to the local linear combination of the original features. Consequently, coefficients within the eigenvector w are truly the weights of the original features. The feature corresponding to the largest absolute coefficient is the most important in determining o as an outlier. Analogously, the second important feature is the one corresponding to the second w s largest absolute component and so on. In this way, we are not only able to figure out which original features are crucial in distinguishing o but also show how important they are via the weights of the corresponding components in w. Generally, we can provide the user with a parameter λ, whose values are between (, ), to control the number of features used to interpret the anomaly degree. We select {f i } d i= as the set of features that correspond to the top d largest absolute coefficients in w and s.t. d i= w i λ D j= w j. The degree of importance of each respective f i can be further computed as the ratio w i / D j= w j. An object o therefore can be interpreted as an outlier in the d-subspace {f,..., f d } with the corresponding feature importance degrees. An illustration is given in Figure where w is plotted as the green line whose coefficients in the rightmost subgraph are (., 4.63, 5.2) (or in terms of importance degrees (.3,.46,.5)) which obviously reveals {f 2, f 3 } being two important features to explain o as an outlier. Note that the corresponding values of w (green lines) in Figures (a) and (b) are respectively (6.2, 5.7,.59) and (2.9, 4.72, 2.), which tend to select {f, f 2 } and {f, f 2, f 3 } as the subspaces for o due to the influence of nearby irrelevant instances. The advantage of our entropy-based neighbor selection is thus demonstrated here where only the direction of w in Figures (d) is in parallel to the relevant subspace {f 2, f 3 } (compared to the slant lines of w shown in Figures (a) and (b)). 3.4 Algorithm Complexity We name our algorithm LODI which stands for Local Outlier Detection with Interpretation and its computation complexity is analyzed as follows. LODI requires the calculation of the neighboring set as well as the local quadratic Renyi entropy. Both these steps take O(DN log N) with the implementation of the k d tree data structure. The size of the matrix A T A is s s and thus its eigen-decomposition is O(Ds log s) using the Lanczos method [8]. Similarly, computing the eigen-decomposition of UΣ 2 U T BB T amounts to O(D 2 log D). We compute these steps for all instances to render the outlier ranking list so these computations take O(DN(s log s + D log D)). The overall complexity is thus at most O(DN(log N + s log s + D log D)). 4 Experimental Results In this section, we provide experimental results on both synthetic and real-world datasets. We compare LODI against the following algorithms: LOF (densitybased technique) [3], ABOD (angle-based) [5] and SOD (axis-parallel subspaces) [4]. The last two algorithms are adapted from the ELKI package 3 with some small changes in their output formats. Unless specified differently, we use 3
10 (a) (b) (c) Fig. 2. Feature visualization over 5 top ranking outliers found in Syn, Syn2 and Syn3 datasets (x- and y-axis are respectively the features index and importance degree). k = 2 as the lower bound for the number of knns used in LODI. We also vary the number of neighbors, like minp ts in LOF or reference points in SOD, between and 4 and report the best results. With SOD, we further set α =.8 as recommended by the authors [4]. 4. Synthetic Data Data Description We generate three synthetic datasets Syn, Syn2 and Syn3, each consists of 5K data instances generated from normal distributions. For each dimension ith of a normal distribution, the center µ i is randomly selected from {, 2, 3, 4, 5} while variance σ i is taken from either of two (considerably different) values and. Such a setting aims to ensure that if the dimension ith of a distribution takes the large variance, its corresponding generated data will spread out in almost entire data space and thus an outlier close to this distribution can be hard to uncover in the ith dimension due to the strongly overlapping values projected onto this dimension. We set the percentage of the large variance to 4%, 6% and 8%, respectively, to generate Syn, Syn2 and Syn3. For each dataset, we vary %, 2%, 5% and % of the whole data as the number of randomly generated outliers within the range of the data space and also vary the dimensionality of each dataset from 5 to 5. Outlier Explanation In Figure 2, we provide a feature visualization of the 5 top-ranked outliers returned by our LODI algorithm on the three datasets. For each graph in the figure, the x-axis shows the index of features while the y-axis shows their degree of importance. For the purpose of visualization, we plot the results where three datasets are generated with 5% outlier percentage and in 5 dimensions. The results for higher dimensionalities and other outlier percentages are very similar to those plotted here and thus were omitted to save space (yet, they are summarized in Table and will be soon discussed). As observed from these graphs, the number of relevant features used to explain the anomalous property of each outlier is varied considerably across the three datasets. In Syn (Figure 2(a)), each identified outlier can be interpreted in a large number of dimensions since the percentage of the large variance used to generate this dataset is small, only 4%. When increasing the percentage to 6% in Syn2 and to 8% in Syn3 (Figures 2(b-c)), the number of relevant features reduces accordingly. In Syn3 dataset, generally only 3 features are needed to interpret its outliers.
11 Truepositive rate.8 D5 D3 D5 Outlier % LODI SOD LODI SOD LODI SOD % 3.2± ± ± ± ± ±3.95 2% 3.2± ± ±.4 6.3±2.56.3± ±4.5 5% 3.5±.8 8.6± ±.8 6.2± ± ±4.3 % 3.4± ± ± ±3.5.8± ±4.8 Table. Average dimensionality of the subspaces selected for outlier explanation in LODI and SOD in Syn3 dataset (values after ± are standard deviations). Truepositiverate LODI auc=.993 LODI auc=.99 LODI auc=.956 ABOD auc=.96 ABOD auc= ABOD auc= LOF auc=.96.4 LOF auc=.828 LOF auc=.758 SOD auc=.98 SOD auc=.95 SOD auc= LODIw/o auc=.984 LODIw/o auc=.935 LODIw/o auc= (a) Syn (b) Syn2 (c) Syn3 Fig. 3. Outlier detection rate of all algorithms on three synthetic datasets (D=5). These results have been anticipated and quite intuitive since once the number of dimensions with large variance increases, the dimensionality of the subspaces in which an outlier can be found and explained will be narrowed down. This is due to the wide overlapping of outliers and regular objects projected onto these (large variance) dimensions. For comparison against other techniques, we select the SOD algorithm. Recall that SOD is not directly designed for outlier interpretation, yet its uncovered axis-parallel subspaces might be used to select outliers relevant features. For these experiments, we select Syn3 dataset and vary the outlier percentage from % to %, and the data dimensionality from 5 to 5 features. Table reports the average subspace s dimensionality of LODI and SOD computed from their top ranking outliers. The first column shows the outlier percentages while D5, D3 and D5 denote the data dimensionality. We set λ =.8 (see Section 3.3) for LODI and α =.8 for SOD to ensure their good performance. As one can observe, LODI tends to select subspaces with dimensionality close to the true one whereas the dimensionality of the axis-parallel subspaces in SOD is often higher. For example, at D5, LODI uses around 3 original features to explain each outlier, which is quite consistent with the percentage of 8% of the large variance while it is approximately 8 features for SOD. It can further be observed that the number of relevant features uncovered by SOD also greatly varies, which is indicated by the high standard deviation. Additionally, it tends to increase as the percentage of outliers increases. In contrast, our method performs better and the relevant subspace dimensionality is less sensitive to the variation of the outlier percentages as well as to the number of original features. Outlier Detection For comparison of outlier detection rates, we further include the angle-based ABOD and the density-based LOF techniques. The receiver operating characteristic (ROC) is used to evaluate the performance of all algorithms. It was observed that all methods performed quite competitively in the low dimensionality yet their performances were more divergent on higher dimensional data. We hence report in Figure 3 the outlier detection rates of all Truepositiverate.8
12 2.9.9 True positiverate k=5 auc=.933 k=2 auc= k=25 auc=.994 k=3 auc= k=35 auc=. k=4 auc= k=5 auc=.938 k=2 auc=.959 k=25 auc=.982 k=3 auc=. k=35 auc=. k=4 auc= (a) Varying %outlier and dimensionality (b) Varying lower threshold k (D=3) (c) Varying lower threshold k (D=5) Fig. 4. Performance of LODI on Syn3 dataset with varying % outliers and threshold k Truepositiverate True positiverate %svals=.85 auc=.93 %svals=.9 auc=.97 %svals=.95 auc=.965 %svals=.99 auc= (a) Varying percentage of svalues (D=3) True positiverate %svals=.85 auc=.99 %svals=.9 auc=.94 %svals=.95 auc=.959 %svals=.99 auc= (b) Varying percentage of svalues (D=5) Fig. 5. Performance of LODI on Syn3 dataset with varying % singular values. methods in D5, setting for all 3 datasets. As observed from these graphs, the outlier detection performance of all algorithms is likely to be decreased as the the large variance percentage used to generate the data increases. However, while the detection rates decrease vastly for other methods, our technique LODI remains stable from Syn to Syn2 dataset, and only slightly reduces in Syn3. Nonetheless, its area under the ROC (AUC) is still around 96% for this dataset. Amongst other techniques, the AUCs of LOF are the lowest. This could be explained through its density-based approach which often makes LOF s performance deteriorated in high dimensional data. The performances of both ABOD and SOD are quite competitive yet their ROC curves are still lower than that of LODI for all three examined datasets. In Figure 3, we also report the performance of LODI not using the entropy-based approach in knns selection (denoted as LODIw/o). Instead, k is varied from to 4 and the best result is reported. As seen in Figure 3, the AUC of LODIw/o in all cases are smaller than that of LODI, which highlights the significance of the entropy-based approach for knns selection. However, compared to other techniques, LODIw/o s outlier detection rate is still better, demonstrating the appealing approach of computing outlier degrees in subspaces learnt from the objective function developed in Eq.(6). Parameters Sensitivity To provide more insights into the performance of our LODI technique, we further test its detection rates with various parameter settings. In Figure 4(a), we plot its AUC performance on the Syn3 dataset when the data dimensionality increases from D5 to D5 and the outlier percentage varies from % to %. The lower threshold k for the neighboring set remains at 2. One may see that LODI s performance slightly deteriorates as the number of outliers generated in the dataset increases. This happens since once the number of outliers increases, there are higher chances for them to be included in other instances neighboring sets. Recall that LODI has alleviated this issue by excluding those with low information potential via the use of quadratic entropy.
13 (a) (b) (c) fea6 fea3 fea row_cid fea fea2 saturatoin exgreen hue fea8 fea7 fea25 fea27 fea fea row_cid fea fea2 fea9 fea8 fea fea fea6 exgreen hue fea5 saturatoin fea6 fea23 fea fea row_cid fea fea8 fea2 fea9 fea3 hue saturatoin exgreen 5 5 fea3 fea8 fea2 fea24 fea23 fea6 fea8 5 fea3 fea32 fea fea8 fea7 fea3 fea9 fea fea fea4 fea2 fea2 saturatoin hue exgreen exred fea3 fea29 fea fea23 fea8 fea fea fea3 fea fea fea fea9 fea2 fea6 fea8 exgreen hue exred 5 5 fea3 5 fea2 saturatoin fea9 fea8 fea6 Fig. 6. Feature visualization over 5 top outliers found in: Ionosphere data (a), Image segmentation data (b) and Vowel data (c) (relevant features are shown with labels). fea32 fea29 fea24 fea28 And in order to gain insights into this matter, we further test the case when the lower threshold for the neighboring set is varied. Figures 4(b-c) show the algorithm s ROC curves when k is changed from 5 to 4 for two cases of D3 and D5. As expected, once k increases, LODI has more capability in excluding irrelevant instances from the neighboring sets and its overall performance increases. As visualized from Figures 4(a-b), a general setting of k around 2 or 25 often leads to competitive results. We finally provide the impact of the total number of singular values used in our matrix approximation. In Figure 5, our algorithm s ROC curves are plotted as the percentage of keeping singular values is varied from 85%, 9%, 95% to 99%. We use Syn3 dataset for these experiments with the data dimensionality at 3 and 5. It is clearly seen that LODI performs better for higher percentages of singular values and in order to keep it at high performance, this parameter should be set around 9% or 95%. 4.2 Real world Data In this section, we provide the experimental results of all algorithms on three real-world datasets selected from the UCI repository []. The first dataset is the image segmentation data which includes 2 3 instances of outdoor images {brickface, sky, foliage, cement, window, path, grass} classified into 7 classes. Each instance is a 3 3 region described by 9 attributes. However, we remove three features 5,7 and 9 from this data as they are known to be repetitive with the attributes 4,6 and 8 []. The second dataset is the vowel data consisting of 99 instances and is described by variables (low pass filtered signals), of which the last one is the class label corresponding to different English vowels {hid, hid, hed, had, hyd, had, hod, hod, hud, hud, hed}. The third dataset is the ionosphere data containing 35 instances and being described by 32 features (electromagnetic signals). Instead of randomly generating artificial outliers and adding them to these datasets, it is more natural to directly downsample several classes and treat them as hidden outliers (as suggested in [9, ]). Specifically, we keep instances from two randomly selected classes of segmentation data as regular objects and downsample five remaining classes, each to 2 instances to represent hidden outliers. Likewise with the vowel dataset, we keep one class of regular objects and randomly sample instances from the remaining classes to represent outliers. With the 2-class ionosphere data, we select instances from
14 4 Truepositiverate.8.6 Truepositiverate LODI auc=.94 LODI auc=.972 LODI auc=.892 ABOD auc=.92 ABOD auc= ABOD auc= LOF auc=.884 LOF auc=.864 LOF auc= SOD auc=.9 SOD auc=.936 SOD auc= (a) Segmentation (b) Vowel (c) Ionosphere Fig. 7. Performance of all algorithms on three UCI real datasets. the second class as outliers since its number of objects is much lower than that of the first class. Unlike the synthetic data where we can manage the data distributions and report the average subspace sizes for all outliers, it is harder to perform such analysis for the real-world datasets since different outliers may have relevant subspaces of different sizes. However, in an attempt to interpret the results of LODI, we plot in Figures 6(a-c) the original features important degrees of 5 top-ranking outliers respectively selected from the ionosphere, image segmentation and vowel datasets. Figure 6(a) reveals that, for each outlier, there are only few features having high importance degrees and they can be selected as the subspace to interpret the abnormal property of the outlier. However, as this dataset has a large number of outliers, the subspaces do not have many features in common. It is thus more interesting to observe the feature visualization for the two other datasets. Looking at the the 5 top outliers of the image segmentation dataset in Figure 6(b), one can see that out of 5 original features, only a few are suitable to interpret the outliers. For example, the space spanned by {row icd, exgreen, saturatioin, hue} attributes is suitable to interpret the exceptional property of the first 3 outliers while the space spanned by {exred, exgreen, saturatioin, hue} is appropriate to explain the last 2 outliers. Taking a closer look, we find out that these two types of outliers are indeed exceptional with respect to the 2 main distributions which correspond to the outdoor imaging instances of 2 classes (number 3rd and 6th) in the segmentation data. In the last dataset, vowel, shown in 6(c), few prominent features stand out for outlier interpretation, yet the features vary across different outliers (using λ =.8). Nevertheless, a common and interesting point is that the first attribute always has the highest value across all outliers, indicating it is the most important feature. Recall that for this dataset, we keep instances from only a single vowel (by random selection it is hyd ) as normal objects while randomly downsample one from each of the remaining vowels as hidden outliers. This might also justify the diversity of the other prominent features across the 5 outliers shown here. We now compare the performance of LODI and the other algorithms through their outlier detection rates. In Figure 7, we report the ROC curves of all algorithms over the three datasets. As observed, LODI shows the best detection performance compared to all three techniques. In the segmentation data, LOF is less successful with its AUC value around 88% though we have tried to optimize its parameter minp ts. The detection rates of ABOD and SOD are quite Truepositiverate
15 5 competitive and achieve 9% AUC which yet is still lower than LODI s 94%. Moreover, LODI is also likely to uncover all true outliers earlier than the other techniques. As observed in Figure 7, its false positive rate is only at 24% when all outliers are found compared to that of 43% for SOD or 6% for LOF. With the vowel dataset, we observe a similar behavior. Nevertheless, in the ionosphere where the number of outliers is considerably larger, none of the algorithms can discover all outliers before their false positive rate reaches %. However, it is seen that while both SOD and ABOD can uncover at most 7% of true outliers when the false positive rate is at 2%, LODI retrieves 86% at the same level. Its overall area under the curve is 89% which is clearly better than the other algorithms. 5 Conclusion In this work, we developed the LODI algorithm to address outlier identification and explanation at the same time. In achieving this twin-objective, our method makes use of an approach firmly rooted from information theory to select appropriate sets of neighboring objects. We developed an objective function to learn subspaces in which outliers are most separable from their nearby inliers. We showed that the optimization problem can be solved via the matrix eigen-decomposition of which relevant features can be obtained to understand exceptional properties of outliers. Our thorough evaluation on both synthetic and real-world datasets demonstrated the appealing performance of LODI and its interpretation form over outliers is intuitive and meaningful. Nonetheless, LODI has some limitations. First, its computation is rather expensive (quadratic in the dimensionality), making LODI less suitable for very large and high dimensional datasets. In dealing with this issue, approaches based on features sampling [?] seem to be potential yet they also lead to some information lost. The challenge is thus to compromise the trade-off between these two criteria. Second, LODI made an assumption that an outlier can be linearly separated from inliers. This assumption may not be practical if the distribution of inliers exhibits some nonconvex shapes. Though several learning techniques based on nonlinear dimensionality reduction can be applied to uncover such outliers [5], this, however, still leaves open to the difficult question of what can be an appropriate form to interpret these nonlinear outliers. We consider these challenges as open issues for our future work. References. A. Asuncion and D. Newman. UCI machine learning repository, V. Barnett and T. Lewis. Outliers in statistical data. John Wiley & Sons Ltd., 3rd edition edition, M. M. Breunig, H. P. Kriegel, R. T. Ng, and J. Sander. LOF: Identifying densitybased local outliers. In SIGMOD, V. Chandola, A. Banerjee, and V. Kumar. Anomaly detection: A survey. ACM Computing Surveys, 4(3), X. H. Dang, B. Micenková, I. Assent, and R. T. Ng. Outlier detection with space transformation and spectral analysis. In SDM, 23.
16 6 6. T. de Vries, S. Chawla, and M. E. Houle. Finding local anomalies in very high dimensional space. In ICDM, pages 28 37, A. Foss, O. R. Zaïane, and S. Zilles. Unsupervised class separation of multivariate data through cumulative variance-based ranking. In ICDM, G. Golub and C. Loan. Matrix Computations. The Johns Hopkins University Press, 3rd edition, J. Han, M. Kamber, and J. Pei. Data Mining: Concepts and Techniques, 3rd. Morgan Kaufmann Publishers Inc, 22.. Z. He, S. Deng, and X. Xu. A unified subspace outlier ensemble framework for outlier detection. In WAIM, 25.. F. Keller, E. Müller, and K. Böhm. Hics: High contrast subspaces for density-based outlier ranking. In ICDE, E. M. Knorr and R. T. Ng. Algorithms for mining distance-based outliers in large datasets. In VLDB, E. M. Knorr and R. T. Ng. Finding intensional knowledge of distance-based outliers. The VLDB Journal, 8:2 222, H. Kriegel, P. Kröger, E. Schubert, and A. Zimek. Outlier detection in axis-parallel subspaces of high dimensional data. In PAKDD, H. Kriegel, M. Schubert, and A. Zimek. Angle-based outlier detection in highdimensional data. In SIGKDD, H.-P. Kriegel, P. Kröger, E. Schubert, and A. Zimek. Outlier detection in arbitrarily oriented subspaces. In ICDM, pages , H.-P. Kriegel, P. Kröger, and A. Zimek. Clustering high-dimensional data: A survey on subspace clustering, pattern-based clustering, and correlation clustering. TKDD, 3(), A. Lazarevic and V. Kumar. Feature bagging for outlier detection. In SIGKDD, pages 57 66, E. Müller, M. Schiffer, and T. Seidl. Statistical selection of relevant subspace projections for outlier ranking. In ICDE, pages , V. Nguyen, V. Gopalkrishnan, and I. Assent. An unbiased distance-based outlier detection approach for high-dimensional data. In DASFAA, S. Papadimitriou, H. Kitagawa, P. B. Gibbons, and C. Faloutsos. Loci: Fast outlier detection using the local correlation integral. In ICDE, pages , L. Parsons, E. Haque, and H. Liu. Subspace clustering for high dimensional data: a review. SIGKDD Explorations, 6():9 5, A. Renyi. On measures of entropy and information. Proc. Fourth Berkeley Symp. Math., Statistics, and Probability, pages , E. Schubert, R. Wojdanowski, A. Zimek, and H.-P. Kriegel. On evaluation of outlier rankings and outlier scores. In SDM, E. Schubert, A. Zimek, and H.-P. Kriegel. Local outlier detection reconsidered: a generalized view on locality with applications to spatial, video, and network outlier detection. Data Mining and Knowledge Discovery, pages 48, Y. Tao, X. Xiao, and S. Zhou. Mining distance-based outliers from large databases in any metric space. In SIGKDD, R. Tibshirani and T. Hastie. Outlier sums for differential gene expression analysis. Biostatistics, 8():2 8, A. Zimek, E. Schubert, and H.-P. Kriegel. A survey on unsupervised outlier detection in high-dimensional numerical data. Statistical Analysis and Data Mining, 5(5): , 22.
Local Outlier Detection with Interpretation
 Local Outlier Detection with Interpretation Xuan Hong Dang, Barbora Micenková, Ira Assent, and Raymond T. Ng 2 Aarhus University, Denmark, {dang,barbora,ira}@cs.au.dk 2 University of British Columbia,
Local Outlier Detection with Interpretation Xuan Hong Dang, Barbora Micenková, Ira Assent, and Raymond T. Ng 2 Aarhus University, Denmark, {dang,barbora,ira}@cs.au.dk 2 University of British Columbia,
Anomaly Detection via Online Oversampling Principal Component Analysis
 Anomaly Detection via Online Oversampling Principal Component Analysis R.Sundara Nagaraj 1, C.Anitha 2 and Mrs.K.K.Kavitha 3 1 PG Scholar (M.Phil-CS), Selvamm Art Science College (Autonomous), Namakkal,
Anomaly Detection via Online Oversampling Principal Component Analysis R.Sundara Nagaraj 1, C.Anitha 2 and Mrs.K.K.Kavitha 3 1 PG Scholar (M.Phil-CS), Selvamm Art Science College (Autonomous), Namakkal,
Anomaly Detection via Over-sampling Principal Component Analysis
 Anomaly Detection via Over-sampling Principal Component Analysis Yi-Ren Yeh, Zheng-Yi Lee, and Yuh-Jye Lee Abstract Outlier detection is an important issue in data mining and has been studied in different
Anomaly Detection via Over-sampling Principal Component Analysis Yi-Ren Yeh, Zheng-Yi Lee, and Yuh-Jye Lee Abstract Outlier detection is an important issue in data mining and has been studied in different
P leiades: Subspace Clustering and Evaluation
 P leiades: Subspace Clustering and Evaluation Ira Assent, Emmanuel Müller, Ralph Krieger, Timm Jansen, and Thomas Seidl Data management and exploration group, RWTH Aachen University, Germany {assent,mueller,krieger,jansen,seidl}@cs.rwth-aachen.de
P leiades: Subspace Clustering and Evaluation Ira Assent, Emmanuel Müller, Ralph Krieger, Timm Jansen, and Thomas Seidl Data management and exploration group, RWTH Aachen University, Germany {assent,mueller,krieger,jansen,seidl}@cs.rwth-aachen.de
Outlier Detection from Network Data with Subnetwork Interpretation
 Outlier Detection from Network Data with Subnetwork Interpretation Xuan-Hong Dang, Arlei Silva, Ambuj Singh University of California Santa Barbara {xdang,arlei,ambuj}@cs.ucsb.edu Ananthram Swami Army Research
Outlier Detection from Network Data with Subnetwork Interpretation Xuan-Hong Dang, Arlei Silva, Ambuj Singh University of California Santa Barbara {xdang,arlei,ambuj}@cs.ucsb.edu Ananthram Swami Army Research
Machine Learning (Spring 2012) Principal Component Analysis
 1-71 Machine Learning (Spring 1) Principal Component Analysis Yang Xu This note is partly based on Chapter 1.1 in Chris Bishop s book on PRML and the lecture slides on PCA written by Carlos Guestrin in
1-71 Machine Learning (Spring 1) Principal Component Analysis Yang Xu This note is partly based on Chapter 1.1 in Chris Bishop s book on PRML and the lecture slides on PCA written by Carlos Guestrin in
Discriminative Direction for Kernel Classifiers
 Discriminative Direction for Kernel Classifiers Polina Golland Artificial Intelligence Lab Massachusetts Institute of Technology Cambridge, MA 02139 polina@ai.mit.edu Abstract In many scientific and engineering
Discriminative Direction for Kernel Classifiers Polina Golland Artificial Intelligence Lab Massachusetts Institute of Technology Cambridge, MA 02139 polina@ai.mit.edu Abstract In many scientific and engineering
Outlier Detection in High-Dimensional Data
 Tutorial Arthur Zimek 1,2, Erich Schubert 2, Hans-Peter Kriegel 2 1 University of Alberta Edmonton, AB, Canada 2 Ludwig-Maximilians-Universität München Munich, Germany PAKDD 2013, Gold Coast, Australia
Tutorial Arthur Zimek 1,2, Erich Schubert 2, Hans-Peter Kriegel 2 1 University of Alberta Edmonton, AB, Canada 2 Ludwig-Maximilians-Universität München Munich, Germany PAKDD 2013, Gold Coast, Australia
In order to compare the proteins of the phylogenomic matrix, we needed a similarity
 Similarity Matrix Generation In order to compare the proteins of the phylogenomic matrix, we needed a similarity measure. Hamming distances between phylogenetic profiles require the use of thresholds for
Similarity Matrix Generation In order to compare the proteins of the phylogenomic matrix, we needed a similarity measure. Hamming distances between phylogenetic profiles require the use of thresholds for
A Modified Incremental Principal Component Analysis for On-line Learning of Feature Space and Classifier
 A Modified Incremental Principal Component Analysis for On-line Learning of Feature Space and Classifier Seiichi Ozawa, Shaoning Pang, and Nikola Kasabov Graduate School of Science and Technology, Kobe
A Modified Incremental Principal Component Analysis for On-line Learning of Feature Space and Classifier Seiichi Ozawa, Shaoning Pang, and Nikola Kasabov Graduate School of Science and Technology, Kobe
Linear Spectral Hashing
 Linear Spectral Hashing Zalán Bodó and Lehel Csató Babeş Bolyai University - Faculty of Mathematics and Computer Science Kogălniceanu 1., 484 Cluj-Napoca - Romania Abstract. assigns binary hash keys to
Linear Spectral Hashing Zalán Bodó and Lehel Csató Babeş Bolyai University - Faculty of Mathematics and Computer Science Kogălniceanu 1., 484 Cluj-Napoca - Romania Abstract. assigns binary hash keys to
L11: Pattern recognition principles
 L11: Pattern recognition principles Bayesian decision theory Statistical classifiers Dimensionality reduction Clustering This lecture is partly based on [Huang, Acero and Hon, 2001, ch. 4] Introduction
L11: Pattern recognition principles Bayesian decision theory Statistical classifiers Dimensionality reduction Clustering This lecture is partly based on [Huang, Acero and Hon, 2001, ch. 4] Introduction
Linear Dimensionality Reduction
 Outline Hong Chang Institute of Computing Technology, Chinese Academy of Sciences Machine Learning Methods (Fall 2012) Outline Outline I 1 Introduction 2 Principal Component Analysis 3 Factor Analysis
Outline Hong Chang Institute of Computing Technology, Chinese Academy of Sciences Machine Learning Methods (Fall 2012) Outline Outline I 1 Introduction 2 Principal Component Analysis 3 Factor Analysis
Anomaly Detection. Jing Gao. SUNY Buffalo
 Anomaly Detection Jing Gao SUNY Buffalo 1 Anomaly Detection Anomalies the set of objects are considerably dissimilar from the remainder of the data occur relatively infrequently when they do occur, their
Anomaly Detection Jing Gao SUNY Buffalo 1 Anomaly Detection Anomalies the set of objects are considerably dissimilar from the remainder of the data occur relatively infrequently when they do occur, their
Discovering Contexts and Contextual Outliers Using Random Walks in Graphs
 Discovering Contexts and Contextual Outliers Using Random Walks in Graphs Xiang Wang Ian Davidson Abstract Introduction. Motivation The identifying of contextual outliers allows the discovery of anomalous
Discovering Contexts and Contextual Outliers Using Random Walks in Graphs Xiang Wang Ian Davidson Abstract Introduction. Motivation The identifying of contextual outliers allows the discovery of anomalous
A Modified Incremental Principal Component Analysis for On-Line Learning of Feature Space and Classifier
 A Modified Incremental Principal Component Analysis for On-Line Learning of Feature Space and Classifier Seiichi Ozawa 1, Shaoning Pang 2, and Nikola Kasabov 2 1 Graduate School of Science and Technology,
A Modified Incremental Principal Component Analysis for On-Line Learning of Feature Space and Classifier Seiichi Ozawa 1, Shaoning Pang 2, and Nikola Kasabov 2 1 Graduate School of Science and Technology,
15 Singular Value Decomposition
 15 Singular Value Decomposition For any high-dimensional data analysis, one s first thought should often be: can I use an SVD? The singular value decomposition is an invaluable analysis tool for dealing
15 Singular Value Decomposition For any high-dimensional data analysis, one s first thought should often be: can I use an SVD? The singular value decomposition is an invaluable analysis tool for dealing
Machine learning for pervasive systems Classification in high-dimensional spaces
 Machine learning for pervasive systems Classification in high-dimensional spaces Department of Communications and Networking Aalto University, School of Electrical Engineering stephan.sigg@aalto.fi Version
Machine learning for pervasive systems Classification in high-dimensional spaces Department of Communications and Networking Aalto University, School of Electrical Engineering stephan.sigg@aalto.fi Version
Problem # Max points possible Actual score Total 120
 FINAL EXAMINATION - MATH 2121, FALL 2017. Name: ID#: Email: Lecture & Tutorial: Problem # Max points possible Actual score 1 15 2 15 3 10 4 15 5 15 6 15 7 10 8 10 9 15 Total 120 You have 180 minutes to
FINAL EXAMINATION - MATH 2121, FALL 2017. Name: ID#: Email: Lecture & Tutorial: Problem # Max points possible Actual score 1 15 2 15 3 10 4 15 5 15 6 15 7 10 8 10 9 15 Total 120 You have 180 minutes to
Structure in Data. A major objective in data analysis is to identify interesting features or structure in the data.
 Structure in Data A major objective in data analysis is to identify interesting features or structure in the data. The graphical methods are very useful in discovering structure. There are basically two
Structure in Data A major objective in data analysis is to identify interesting features or structure in the data. The graphical methods are very useful in discovering structure. There are basically two
Classification Methods II: Linear and Quadratic Discrimminant Analysis
 Classification Methods II: Linear and Quadratic Discrimminant Analysis Rebecca C. Steorts, Duke University STA 325, Chapter 4 ISL Agenda Linear Discrimminant Analysis (LDA) Classification Recall that linear
Classification Methods II: Linear and Quadratic Discrimminant Analysis Rebecca C. Steorts, Duke University STA 325, Chapter 4 ISL Agenda Linear Discrimminant Analysis (LDA) Classification Recall that linear
Density-Based Clustering
 Density-Based Clustering idea: Clusters are dense regions in feature space F. density: objects volume ε here: volume: ε-neighborhood for object o w.r.t. distance measure dist(x,y) dense region: ε-neighborhood
Density-Based Clustering idea: Clusters are dense regions in feature space F. density: objects volume ε here: volume: ε-neighborhood for object o w.r.t. distance measure dist(x,y) dense region: ε-neighborhood
CS570 Data Mining. Anomaly Detection. Li Xiong. Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber.
 CS570 Data Mining Anomaly Detection Li Xiong Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber April 3, 2011 1 Anomaly Detection Anomaly is a pattern in the data that does not conform
CS570 Data Mining Anomaly Detection Li Xiong Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber April 3, 2011 1 Anomaly Detection Anomaly is a pattern in the data that does not conform
Machine Learning. B. Unsupervised Learning B.2 Dimensionality Reduction. Lars Schmidt-Thieme, Nicolas Schilling
 Machine Learning B. Unsupervised Learning B.2 Dimensionality Reduction Lars Schmidt-Thieme, Nicolas Schilling Information Systems and Machine Learning Lab (ISMLL) Institute for Computer Science University
Machine Learning B. Unsupervised Learning B.2 Dimensionality Reduction Lars Schmidt-Thieme, Nicolas Schilling Information Systems and Machine Learning Lab (ISMLL) Institute for Computer Science University
Unbiased Multivariate Correlation Analysis
 Unbiased Multivariate Correlation Analysis Yisen Wang,, Simone Romano, Vinh Nguyen, James Bailey, Xingjun Ma, Shu-Tao Xia Dept. of Computer Science and Technology, Tsinghua University, China Dept. of Computing
Unbiased Multivariate Correlation Analysis Yisen Wang,, Simone Romano, Vinh Nguyen, James Bailey, Xingjun Ma, Shu-Tao Xia Dept. of Computer Science and Technology, Tsinghua University, China Dept. of Computing
5. Discriminant analysis
 5. Discriminant analysis We continue from Bayes s rule presented in Section 3 on p. 85 (5.1) where c i is a class, x isap-dimensional vector (data case) and we use class conditional probability (density
5. Discriminant analysis We continue from Bayes s rule presented in Section 3 on p. 85 (5.1) where c i is a class, x isap-dimensional vector (data case) and we use class conditional probability (density
Flexible and Adaptive Subspace Search for Outlier Analysis
 Flexible and Adaptive Subspace Search for Outlier Analysis Fabian Keller Emmanuel Müller Andreas Wixler Klemens Böhm Karlsruhe Institute of Technology (KIT), Germany {fabian.keller, emmanuel.mueller, klemens.boehm}@kit.edu
Flexible and Adaptive Subspace Search for Outlier Analysis Fabian Keller Emmanuel Müller Andreas Wixler Klemens Böhm Karlsruhe Institute of Technology (KIT), Germany {fabian.keller, emmanuel.mueller, klemens.boehm}@kit.edu
14 Singular Value Decomposition
 14 Singular Value Decomposition For any high-dimensional data analysis, one s first thought should often be: can I use an SVD? The singular value decomposition is an invaluable analysis tool for dealing
14 Singular Value Decomposition For any high-dimensional data analysis, one s first thought should often be: can I use an SVD? The singular value decomposition is an invaluable analysis tool for dealing
Machine Learning (BSMC-GA 4439) Wenke Liu
 Machine Learning (BSMC-GA 4439) Wenke Liu 02-01-2018 Biomedical data are usually high-dimensional Number of samples (n) is relatively small whereas number of features (p) can be large Sometimes p>>n Problems
Machine Learning (BSMC-GA 4439) Wenke Liu 02-01-2018 Biomedical data are usually high-dimensional Number of samples (n) is relatively small whereas number of features (p) can be large Sometimes p>>n Problems
Lecture 6: Methods for high-dimensional problems
 Lecture 6: Methods for high-dimensional problems Hector Corrada Bravo and Rafael A. Irizarry March, 2010 In this Section we will discuss methods where data lies on high-dimensional spaces. In particular,
Lecture 6: Methods for high-dimensional problems Hector Corrada Bravo and Rafael A. Irizarry March, 2010 In this Section we will discuss methods where data lies on high-dimensional spaces. In particular,
Lecture 4 Discriminant Analysis, k-nearest Neighbors
 Lecture 4 Discriminant Analysis, k-nearest Neighbors Fredrik Lindsten Division of Systems and Control Department of Information Technology Uppsala University. Email: fredrik.lindsten@it.uu.se fredrik.lindsten@it.uu.se
Lecture 4 Discriminant Analysis, k-nearest Neighbors Fredrik Lindsten Division of Systems and Control Department of Information Technology Uppsala University. Email: fredrik.lindsten@it.uu.se fredrik.lindsten@it.uu.se
Rare Event Discovery And Event Change Point In Biological Data Stream
 Rare Event Discovery And Event Change Point In Biological Data Stream T. Jagadeeswari 1 M.Tech(CSE) MISTE, B. Mahalakshmi 2 M.Tech(CSE)MISTE, N. Anusha 3 M.Tech(CSE) Department of Computer Science and
Rare Event Discovery And Event Change Point In Biological Data Stream T. Jagadeeswari 1 M.Tech(CSE) MISTE, B. Mahalakshmi 2 M.Tech(CSE)MISTE, N. Anusha 3 M.Tech(CSE) Department of Computer Science and
Focus was on solving matrix inversion problems Now we look at other properties of matrices Useful when A represents a transformations.
 Previously Focus was on solving matrix inversion problems Now we look at other properties of matrices Useful when A represents a transformations y = Ax Or A simply represents data Notion of eigenvectors,
Previously Focus was on solving matrix inversion problems Now we look at other properties of matrices Useful when A represents a transformations y = Ax Or A simply represents data Notion of eigenvectors,
CSE 417T: Introduction to Machine Learning. Final Review. Henry Chai 12/4/18
 CSE 417T: Introduction to Machine Learning Final Review Henry Chai 12/4/18 Overfitting Overfitting is fitting the training data more than is warranted Fitting noise rather than signal 2 Estimating! "#$
CSE 417T: Introduction to Machine Learning Final Review Henry Chai 12/4/18 Overfitting Overfitting is fitting the training data more than is warranted Fitting noise rather than signal 2 Estimating! "#$
Unsupervised Learning with Permuted Data
 Unsupervised Learning with Permuted Data Sergey Kirshner skirshne@ics.uci.edu Sridevi Parise sparise@ics.uci.edu Padhraic Smyth smyth@ics.uci.edu School of Information and Computer Science, University
Unsupervised Learning with Permuted Data Sergey Kirshner skirshne@ics.uci.edu Sridevi Parise sparise@ics.uci.edu Padhraic Smyth smyth@ics.uci.edu School of Information and Computer Science, University
EEL 851: Biometrics. An Overview of Statistical Pattern Recognition EEL 851 1
 EEL 851: Biometrics An Overview of Statistical Pattern Recognition EEL 851 1 Outline Introduction Pattern Feature Noise Example Problem Analysis Segmentation Feature Extraction Classification Design Cycle
EEL 851: Biometrics An Overview of Statistical Pattern Recognition EEL 851 1 Outline Introduction Pattern Feature Noise Example Problem Analysis Segmentation Feature Extraction Classification Design Cycle
Data Mining. Linear & nonlinear classifiers. Hamid Beigy. Sharif University of Technology. Fall 1396
 Data Mining Linear & nonlinear classifiers Hamid Beigy Sharif University of Technology Fall 1396 Hamid Beigy (Sharif University of Technology) Data Mining Fall 1396 1 / 31 Table of contents 1 Introduction
Data Mining Linear & nonlinear classifiers Hamid Beigy Sharif University of Technology Fall 1396 Hamid Beigy (Sharif University of Technology) Data Mining Fall 1396 1 / 31 Table of contents 1 Introduction
CS 231A Section 1: Linear Algebra & Probability Review
 CS 231A Section 1: Linear Algebra & Probability Review 1 Topics Support Vector Machines Boosting Viola-Jones face detector Linear Algebra Review Notation Operations & Properties Matrix Calculus Probability
CS 231A Section 1: Linear Algebra & Probability Review 1 Topics Support Vector Machines Boosting Viola-Jones face detector Linear Algebra Review Notation Operations & Properties Matrix Calculus Probability
8.1 Concentration inequality for Gaussian random matrix (cont d)
 MGMT 69: Topics in High-dimensional Data Analysis Falll 26 Lecture 8: Spectral clustering and Laplacian matrices Lecturer: Jiaming Xu Scribe: Hyun-Ju Oh and Taotao He, October 4, 26 Outline Concentration
MGMT 69: Topics in High-dimensional Data Analysis Falll 26 Lecture 8: Spectral clustering and Laplacian matrices Lecturer: Jiaming Xu Scribe: Hyun-Ju Oh and Taotao He, October 4, 26 Outline Concentration
When Fisher meets Fukunaga-Koontz: A New Look at Linear Discriminants
 When Fisher meets Fukunaga-Koontz: A New Look at Linear Discriminants Sheng Zhang erence Sim School of Computing, National University of Singapore 3 Science Drive 2, Singapore 7543 {zhangshe, tsim}@comp.nus.edu.sg
When Fisher meets Fukunaga-Koontz: A New Look at Linear Discriminants Sheng Zhang erence Sim School of Computing, National University of Singapore 3 Science Drive 2, Singapore 7543 {zhangshe, tsim}@comp.nus.edu.sg
Classification and Pattern Recognition
 Classification and Pattern Recognition Léon Bottou NEC Labs America COS 424 2/23/2010 The machine learning mix and match Goals Representation Capacity Control Operational Considerations Computational Considerations
Classification and Pattern Recognition Léon Bottou NEC Labs America COS 424 2/23/2010 The machine learning mix and match Goals Representation Capacity Control Operational Considerations Computational Considerations
Data Mining. Dimensionality reduction. Hamid Beigy. Sharif University of Technology. Fall 1395
 Data Mining Dimensionality reduction Hamid Beigy Sharif University of Technology Fall 1395 Hamid Beigy (Sharif University of Technology) Data Mining Fall 1395 1 / 42 Outline 1 Introduction 2 Feature selection
Data Mining Dimensionality reduction Hamid Beigy Sharif University of Technology Fall 1395 Hamid Beigy (Sharif University of Technology) Data Mining Fall 1395 1 / 42 Outline 1 Introduction 2 Feature selection
Linear Models for Regression. Sargur Srihari
 Linear Models for Regression Sargur srihari@cedar.buffalo.edu 1 Topics in Linear Regression What is regression? Polynomial Curve Fitting with Scalar input Linear Basis Function Models Maximum Likelihood
Linear Models for Regression Sargur srihari@cedar.buffalo.edu 1 Topics in Linear Regression What is regression? Polynomial Curve Fitting with Scalar input Linear Basis Function Models Maximum Likelihood
Clustering. CSL465/603 - Fall 2016 Narayanan C Krishnan
 Clustering CSL465/603 - Fall 2016 Narayanan C Krishnan ckn@iitrpr.ac.in Supervised vs Unsupervised Learning Supervised learning Given x ", y " "%& ', learn a function f: X Y Categorical output classification
Clustering CSL465/603 - Fall 2016 Narayanan C Krishnan ckn@iitrpr.ac.in Supervised vs Unsupervised Learning Supervised learning Given x ", y " "%& ', learn a function f: X Y Categorical output classification
Data Mining Techniques
 Data Mining Techniques CS 6220 - Section 3 - Fall 2016 Lecture 12 Jan-Willem van de Meent (credit: Yijun Zhao, Percy Liang) DIMENSIONALITY REDUCTION Borrowing from: Percy Liang (Stanford) Linear Dimensionality
Data Mining Techniques CS 6220 - Section 3 - Fall 2016 Lecture 12 Jan-Willem van de Meent (credit: Yijun Zhao, Percy Liang) DIMENSIONALITY REDUCTION Borrowing from: Percy Liang (Stanford) Linear Dimensionality
COMS 4771 Introduction to Machine Learning. Nakul Verma
 COMS 4771 Introduction to Machine Learning Nakul Verma Announcements HW1 due next lecture Project details are available decide on the group and topic by Thursday Last time Generative vs. Discriminative
COMS 4771 Introduction to Machine Learning Nakul Verma Announcements HW1 due next lecture Project details are available decide on the group and topic by Thursday Last time Generative vs. Discriminative
Statistical Pattern Recognition
 Statistical Pattern Recognition Feature Extraction Hamid R. Rabiee Jafar Muhammadi, Alireza Ghasemi, Payam Siyari Spring 2014 http://ce.sharif.edu/courses/92-93/2/ce725-2/ Agenda Dimensionality Reduction
Statistical Pattern Recognition Feature Extraction Hamid R. Rabiee Jafar Muhammadi, Alireza Ghasemi, Payam Siyari Spring 2014 http://ce.sharif.edu/courses/92-93/2/ce725-2/ Agenda Dimensionality Reduction
Iterative Laplacian Score for Feature Selection
 Iterative Laplacian Score for Feature Selection Linling Zhu, Linsong Miao, and Daoqiang Zhang College of Computer Science and echnology, Nanjing University of Aeronautics and Astronautics, Nanjing 2006,
Iterative Laplacian Score for Feature Selection Linling Zhu, Linsong Miao, and Daoqiang Zhang College of Computer Science and echnology, Nanjing University of Aeronautics and Astronautics, Nanjing 2006,
Machine Learning for Software Engineering
 Machine Learning for Software Engineering Dimensionality Reduction Prof. Dr.-Ing. Norbert Siegmund Intelligent Software Systems 1 2 Exam Info Scheduled for Tuesday 25 th of July 11-13h (same time as the
Machine Learning for Software Engineering Dimensionality Reduction Prof. Dr.-Ing. Norbert Siegmund Intelligent Software Systems 1 2 Exam Info Scheduled for Tuesday 25 th of July 11-13h (same time as the
Dimensionality Reduction
 Dimensionality Reduction Le Song Machine Learning I CSE 674, Fall 23 Unsupervised learning Learning from raw (unlabeled, unannotated, etc) data, as opposed to supervised data where a classification of
Dimensionality Reduction Le Song Machine Learning I CSE 674, Fall 23 Unsupervised learning Learning from raw (unlabeled, unannotated, etc) data, as opposed to supervised data where a classification of
Reverse Nearest Neighbors in Unsupervised Distance-Based Outlier Detection. I.Priyanka 1. Research Scholar,Bharathiyar University. G.
 Journal of Analysis and Computation (JAC) (An International Peer Reviewed Journal), www.ijaconline.com, ISSN 0973-2861 International Conference on Emerging Trends in IOT & Machine Learning, 2018 Reverse
Journal of Analysis and Computation (JAC) (An International Peer Reviewed Journal), www.ijaconline.com, ISSN 0973-2861 International Conference on Emerging Trends in IOT & Machine Learning, 2018 Reverse
Correlation Preserving Unsupervised Discretization. Outline
 Correlation Preserving Unsupervised Discretization Jee Vang Outline Paper References What is discretization? Motivation Principal Component Analysis (PCA) Association Mining Correlation Preserving Discretization
Correlation Preserving Unsupervised Discretization Jee Vang Outline Paper References What is discretization? Motivation Principal Component Analysis (PCA) Association Mining Correlation Preserving Discretization
CS 231A Section 1: Linear Algebra & Probability Review. Kevin Tang
 CS 231A Section 1: Linear Algebra & Probability Review Kevin Tang Kevin Tang Section 1-1 9/30/2011 Topics Support Vector Machines Boosting Viola Jones face detector Linear Algebra Review Notation Operations
CS 231A Section 1: Linear Algebra & Probability Review Kevin Tang Kevin Tang Section 1-1 9/30/2011 Topics Support Vector Machines Boosting Viola Jones face detector Linear Algebra Review Notation Operations
Motivating the Covariance Matrix
 Motivating the Covariance Matrix Raúl Rojas Computer Science Department Freie Universität Berlin January 2009 Abstract This note reviews some interesting properties of the covariance matrix and its role
Motivating the Covariance Matrix Raúl Rojas Computer Science Department Freie Universität Berlin January 2009 Abstract This note reviews some interesting properties of the covariance matrix and its role
Kernel Density Topic Models: Visual Topics Without Visual Words
 Kernel Density Topic Models: Visual Topics Without Visual Words Konstantinos Rematas K.U. Leuven ESAT-iMinds krematas@esat.kuleuven.be Mario Fritz Max Planck Institute for Informatics mfrtiz@mpi-inf.mpg.de
Kernel Density Topic Models: Visual Topics Without Visual Words Konstantinos Rematas K.U. Leuven ESAT-iMinds krematas@esat.kuleuven.be Mario Fritz Max Planck Institute for Informatics mfrtiz@mpi-inf.mpg.de
Spectral Clustering. Zitao Liu
 Spectral Clustering Zitao Liu Agenda Brief Clustering Review Similarity Graph Graph Laplacian Spectral Clustering Algorithm Graph Cut Point of View Random Walk Point of View Perturbation Theory Point of
Spectral Clustering Zitao Liu Agenda Brief Clustering Review Similarity Graph Graph Laplacian Spectral Clustering Algorithm Graph Cut Point of View Random Walk Point of View Perturbation Theory Point of
The Laplacian PDF Distance: A Cost Function for Clustering in a Kernel Feature Space
 The Laplacian PDF Distance: A Cost Function for Clustering in a Kernel Feature Space Robert Jenssen, Deniz Erdogmus 2, Jose Principe 2, Torbjørn Eltoft Department of Physics, University of Tromsø, Norway
The Laplacian PDF Distance: A Cost Function for Clustering in a Kernel Feature Space Robert Jenssen, Deniz Erdogmus 2, Jose Principe 2, Torbjørn Eltoft Department of Physics, University of Tromsø, Norway
ECE521 week 3: 23/26 January 2017
 ECE521 week 3: 23/26 January 2017 Outline Probabilistic interpretation of linear regression - Maximum likelihood estimation (MLE) - Maximum a posteriori (MAP) estimation Bias-variance trade-off Linear
ECE521 week 3: 23/26 January 2017 Outline Probabilistic interpretation of linear regression - Maximum likelihood estimation (MLE) - Maximum a posteriori (MAP) estimation Bias-variance trade-off Linear
Comparison of Shannon, Renyi and Tsallis Entropy used in Decision Trees
 Comparison of Shannon, Renyi and Tsallis Entropy used in Decision Trees Tomasz Maszczyk and W lodzis law Duch Department of Informatics, Nicolaus Copernicus University Grudzi adzka 5, 87-100 Toruń, Poland
Comparison of Shannon, Renyi and Tsallis Entropy used in Decision Trees Tomasz Maszczyk and W lodzis law Duch Department of Informatics, Nicolaus Copernicus University Grudzi adzka 5, 87-100 Toruń, Poland
The local equivalence of two distances between clusterings: the Misclassification Error metric and the χ 2 distance
 The local equivalence of two distances between clusterings: the Misclassification Error metric and the χ 2 distance Marina Meilă University of Washington Department of Statistics Box 354322 Seattle, WA
The local equivalence of two distances between clusterings: the Misclassification Error metric and the χ 2 distance Marina Meilă University of Washington Department of Statistics Box 354322 Seattle, WA
SYSTEMATIC CONSTRUCTION OF ANOMALY DETECTION BENCHMARKS FROM REAL DATA. Outlier Detection And Description Workshop 2013
 SYSTEMATIC CONSTRUCTION OF ANOMALY DETECTION BENCHMARKS FROM REAL DATA Outlier Detection And Description Workshop 2013 Authors Andrew Emmott emmott@eecs.oregonstate.edu Thomas Dietterich tgd@eecs.oregonstate.edu
SYSTEMATIC CONSTRUCTION OF ANOMALY DETECTION BENCHMARKS FROM REAL DATA Outlier Detection And Description Workshop 2013 Authors Andrew Emmott emmott@eecs.oregonstate.edu Thomas Dietterich tgd@eecs.oregonstate.edu
Dimensionality Reduction
 Lecture 5 1 Outline 1. Overview a) What is? b) Why? 2. Principal Component Analysis (PCA) a) Objectives b) Explaining variability c) SVD 3. Related approaches a) ICA b) Autoencoders 2 Example 1: Sportsball
Lecture 5 1 Outline 1. Overview a) What is? b) Why? 2. Principal Component Analysis (PCA) a) Objectives b) Explaining variability c) SVD 3. Related approaches a) ICA b) Autoencoders 2 Example 1: Sportsball
Pattern Recognition 2
 Pattern Recognition 2 KNN,, Dr. Terence Sim School of Computing National University of Singapore Outline 1 2 3 4 5 Outline 1 2 3 4 5 The Bayes Classifier is theoretically optimum. That is, prob. of error
Pattern Recognition 2 KNN,, Dr. Terence Sim School of Computing National University of Singapore Outline 1 2 3 4 5 Outline 1 2 3 4 5 The Bayes Classifier is theoretically optimum. That is, prob. of error
USING SINGULAR VALUE DECOMPOSITION (SVD) AS A SOLUTION FOR SEARCH RESULT CLUSTERING
 POZNAN UNIVE RSIY OF E CHNOLOGY ACADE MIC JOURNALS No. 80 Electrical Engineering 2014 Hussam D. ABDULLA* Abdella S. ABDELRAHMAN* Vaclav SNASEL* USING SINGULAR VALUE DECOMPOSIION (SVD) AS A SOLUION FOR
POZNAN UNIVE RSIY OF E CHNOLOGY ACADE MIC JOURNALS No. 80 Electrical Engineering 2014 Hussam D. ABDULLA* Abdella S. ABDELRAHMAN* Vaclav SNASEL* USING SINGULAR VALUE DECOMPOSIION (SVD) AS A SOLUION FOR
ECE 661: Homework 10 Fall 2014
 ECE 661: Homework 10 Fall 2014 This homework consists of the following two parts: (1) Face recognition with PCA and LDA for dimensionality reduction and the nearest-neighborhood rule for classification;
ECE 661: Homework 10 Fall 2014 This homework consists of the following two parts: (1) Face recognition with PCA and LDA for dimensionality reduction and the nearest-neighborhood rule for classification;
Leverage Sparse Information in Predictive Modeling
 Leverage Sparse Information in Predictive Modeling Liang Xie Countrywide Home Loans, Countrywide Bank, FSB August 29, 2008 Abstract This paper examines an innovative method to leverage information from
Leverage Sparse Information in Predictive Modeling Liang Xie Countrywide Home Loans, Countrywide Bank, FSB August 29, 2008 Abstract This paper examines an innovative method to leverage information from
Linear Regression and Its Applications
 Linear Regression and Its Applications Predrag Radivojac October 13, 2014 Given a data set D = {(x i, y i )} n the objective is to learn the relationship between features and the target. We usually start
Linear Regression and Its Applications Predrag Radivojac October 13, 2014 Given a data set D = {(x i, y i )} n the objective is to learn the relationship between features and the target. We usually start
Midterm. Introduction to Machine Learning. CS 189 Spring Please do not open the exam before you are instructed to do so.
 CS 89 Spring 07 Introduction to Machine Learning Midterm Please do not open the exam before you are instructed to do so. The exam is closed book, closed notes except your one-page cheat sheet. Electronic
CS 89 Spring 07 Introduction to Machine Learning Midterm Please do not open the exam before you are instructed to do so. The exam is closed book, closed notes except your one-page cheat sheet. Electronic
Predictive analysis on Multivariate, Time Series datasets using Shapelets
 1 Predictive analysis on Multivariate, Time Series datasets using Shapelets Hemal Thakkar Department of Computer Science, Stanford University hemal@stanford.edu hemal.tt@gmail.com Abstract Multivariate,
1 Predictive analysis on Multivariate, Time Series datasets using Shapelets Hemal Thakkar Department of Computer Science, Stanford University hemal@stanford.edu hemal.tt@gmail.com Abstract Multivariate,
Data Preprocessing Tasks
 Data Tasks 1 2 3 Data Reduction 4 We re here. 1 Dimensionality Reduction Dimensionality reduction is a commonly used approach for generating fewer features. Typically used because too many features can
Data Tasks 1 2 3 Data Reduction 4 We re here. 1 Dimensionality Reduction Dimensionality reduction is a commonly used approach for generating fewer features. Typically used because too many features can
Randomized Algorithms
 Randomized Algorithms Saniv Kumar, Google Research, NY EECS-6898, Columbia University - Fall, 010 Saniv Kumar 9/13/010 EECS6898 Large Scale Machine Learning 1 Curse of Dimensionality Gaussian Mixture Models
Randomized Algorithms Saniv Kumar, Google Research, NY EECS-6898, Columbia University - Fall, 010 Saniv Kumar 9/13/010 EECS6898 Large Scale Machine Learning 1 Curse of Dimensionality Gaussian Mixture Models
Instance-based Learning CE-717: Machine Learning Sharif University of Technology. M. Soleymani Fall 2016
 Instance-based Learning CE-717: Machine Learning Sharif University of Technology M. Soleymani Fall 2016 Outline Non-parametric approach Unsupervised: Non-parametric density estimation Parzen Windows Kn-Nearest
Instance-based Learning CE-717: Machine Learning Sharif University of Technology M. Soleymani Fall 2016 Outline Non-parametric approach Unsupervised: Non-parametric density estimation Parzen Windows Kn-Nearest
Feature selection and classifier performance in computer-aided diagnosis: The effect of finite sample size
 Feature selection and classifier performance in computer-aided diagnosis: The effect of finite sample size Berkman Sahiner, a) Heang-Ping Chan, Nicholas Petrick, Robert F. Wagner, b) and Lubomir Hadjiiski
Feature selection and classifier performance in computer-aided diagnosis: The effect of finite sample size Berkman Sahiner, a) Heang-Ping Chan, Nicholas Petrick, Robert F. Wagner, b) and Lubomir Hadjiiski
Streaming multiscale anomaly detection
 Streaming multiscale anomaly detection DATA-ENS Paris and ThalesAlenia Space B Ravi Kiran, Université Lille 3, CRISTaL Joint work with Mathieu Andreux beedotkiran@gmail.com June 20, 2017 (CRISTaL) Streaming
Streaming multiscale anomaly detection DATA-ENS Paris and ThalesAlenia Space B Ravi Kiran, Université Lille 3, CRISTaL Joint work with Mathieu Andreux beedotkiran@gmail.com June 20, 2017 (CRISTaL) Streaming
Statistical Machine Learning
 Statistical Machine Learning Christoph Lampert Spring Semester 2015/2016 // Lecture 12 1 / 36 Unsupervised Learning Dimensionality Reduction 2 / 36 Dimensionality Reduction Given: data X = {x 1,..., x
Statistical Machine Learning Christoph Lampert Spring Semester 2015/2016 // Lecture 12 1 / 36 Unsupervised Learning Dimensionality Reduction 2 / 36 Dimensionality Reduction Given: data X = {x 1,..., x
A comparison of three class separability measures
 A comparison of three class separability measures L.S Mthembu & J.Greene Department of Electrical Engineering, University of Cape Town Rondebosch, 7001, South Africa. Abstract lsmthlin007@mail.uct.ac.za
A comparison of three class separability measures L.S Mthembu & J.Greene Department of Electrical Engineering, University of Cape Town Rondebosch, 7001, South Africa. Abstract lsmthlin007@mail.uct.ac.za
The University of Texas at Austin Department of Electrical and Computer Engineering. EE381V: Large Scale Learning Spring 2013.
 The University of Texas at Austin Department of Electrical and Computer Engineering EE381V: Large Scale Learning Spring 2013 Assignment 1 Caramanis/Sanghavi Due: Thursday, Feb. 7, 2013. (Problems 1 and
The University of Texas at Austin Department of Electrical and Computer Engineering EE381V: Large Scale Learning Spring 2013 Assignment 1 Caramanis/Sanghavi Due: Thursday, Feb. 7, 2013. (Problems 1 and
Stephen Scott.
 1 / 35 (Adapted from Ethem Alpaydin and Tom Mitchell) sscott@cse.unl.edu In Homework 1, you are (supposedly) 1 Choosing a data set 2 Extracting a test set of size > 30 3 Building a tree on the training
1 / 35 (Adapted from Ethem Alpaydin and Tom Mitchell) sscott@cse.unl.edu In Homework 1, you are (supposedly) 1 Choosing a data set 2 Extracting a test set of size > 30 3 Building a tree on the training
Protein Complex Identification by Supervised Graph Clustering
 Protein Complex Identification by Supervised Graph Clustering Yanjun Qi 1, Fernanda Balem 2, Christos Faloutsos 1, Judith Klein- Seetharaman 1,2, Ziv Bar-Joseph 1 1 School of Computer Science, Carnegie
Protein Complex Identification by Supervised Graph Clustering Yanjun Qi 1, Fernanda Balem 2, Christos Faloutsos 1, Judith Klein- Seetharaman 1,2, Ziv Bar-Joseph 1 1 School of Computer Science, Carnegie
Projective Clustering by Histograms
 Projective Clustering by Histograms Eric Ka Ka Ng, Ada Wai-chee Fu and Raymond Chi-Wing Wong, Member, IEEE Abstract Recent research suggests that clustering for high dimensional data should involve searching
Projective Clustering by Histograms Eric Ka Ka Ng, Ada Wai-chee Fu and Raymond Chi-Wing Wong, Member, IEEE Abstract Recent research suggests that clustering for high dimensional data should involve searching
20 Unsupervised Learning and Principal Components Analysis (PCA)
 116 Jonathan Richard Shewchuk 20 Unsupervised Learning and Principal Components Analysis (PCA) UNSUPERVISED LEARNING We have sample points, but no labels! No classes, no y-values, nothing to predict. Goal:
116 Jonathan Richard Shewchuk 20 Unsupervised Learning and Principal Components Analysis (PCA) UNSUPERVISED LEARNING We have sample points, but no labels! No classes, no y-values, nothing to predict. Goal:
Wolf-Tilo Balke Silviu Homoceanu Institut für Informationssysteme Technische Universität Braunschweig
 Multimedia Databases Wolf-Tilo Balke Silviu Homoceanu Institut für Informationssysteme Technische Universität Braunschweig http://www.ifis.cs.tu-bs.de 14 Indexes for Multimedia Data 14 Indexes for Multimedia
Multimedia Databases Wolf-Tilo Balke Silviu Homoceanu Institut für Informationssysteme Technische Universität Braunschweig http://www.ifis.cs.tu-bs.de 14 Indexes for Multimedia Data 14 Indexes for Multimedia
Outlier Detection Using Rough Set Theory
 Outlier Detection Using Rough Set Theory Feng Jiang 1,2, Yuefei Sui 1, and Cungen Cao 1 1 Key Laboratory of Intelligent Information Processing, Institute of Computing Technology, Chinese Academy of Sciences,
Outlier Detection Using Rough Set Theory Feng Jiang 1,2, Yuefei Sui 1, and Cungen Cao 1 1 Key Laboratory of Intelligent Information Processing, Institute of Computing Technology, Chinese Academy of Sciences,
PCA, Kernel PCA, ICA
 PCA, Kernel PCA, ICA Learning Representations. Dimensionality Reduction. Maria-Florina Balcan 04/08/2015 Big & High-Dimensional Data High-Dimensions = Lot of Features Document classification Features per
PCA, Kernel PCA, ICA Learning Representations. Dimensionality Reduction. Maria-Florina Balcan 04/08/2015 Big & High-Dimensional Data High-Dimensions = Lot of Features Document classification Features per
Fantope Regularization in Metric Learning
 Fantope Regularization in Metric Learning CVPR 2014 Marc T. Law (LIP6, UPMC), Nicolas Thome (LIP6 - UPMC Sorbonne Universités), Matthieu Cord (LIP6 - UPMC Sorbonne Universités), Paris, France Introduction
Fantope Regularization in Metric Learning CVPR 2014 Marc T. Law (LIP6, UPMC), Nicolas Thome (LIP6 - UPMC Sorbonne Universités), Matthieu Cord (LIP6 - UPMC Sorbonne Universités), Paris, France Introduction
Linear Discrimination Functions
 Laurea Magistrale in Informatica Nicola Fanizzi Dipartimento di Informatica Università degli Studi di Bari November 4, 2009 Outline Linear models Gradient descent Perceptron Minimum square error approach
Laurea Magistrale in Informatica Nicola Fanizzi Dipartimento di Informatica Università degli Studi di Bari November 4, 2009 Outline Linear models Gradient descent Perceptron Minimum square error approach
Unsupervised learning: beyond simple clustering and PCA
 Unsupervised learning: beyond simple clustering and PCA Liza Rebrova Self organizing maps (SOM) Goal: approximate data points in R p by a low-dimensional manifold Unlike PCA, the manifold does not have
Unsupervised learning: beyond simple clustering and PCA Liza Rebrova Self organizing maps (SOM) Goal: approximate data points in R p by a low-dimensional manifold Unlike PCA, the manifold does not have
Self-Tuning Spectral Clustering
 Self-Tuning Spectral Clustering Lihi Zelnik-Manor Pietro Perona Department of Electrical Engineering Department of Electrical Engineering California Institute of Technology California Institute of Technology
Self-Tuning Spectral Clustering Lihi Zelnik-Manor Pietro Perona Department of Electrical Engineering Department of Electrical Engineering California Institute of Technology California Institute of Technology
PRINCIPAL COMPONENTS ANALYSIS
 121 CHAPTER 11 PRINCIPAL COMPONENTS ANALYSIS We now have the tools necessary to discuss one of the most important concepts in mathematical statistics: Principal Components Analysis (PCA). PCA involves
121 CHAPTER 11 PRINCIPAL COMPONENTS ANALYSIS We now have the tools necessary to discuss one of the most important concepts in mathematical statistics: Principal Components Analysis (PCA). PCA involves
Final Overview. Introduction to ML. Marek Petrik 4/25/2017
 Final Overview Introduction to ML Marek Petrik 4/25/2017 This Course: Introduction to Machine Learning Build a foundation for practice and research in ML Basic machine learning concepts: max likelihood,
Final Overview Introduction to ML Marek Petrik 4/25/2017 This Course: Introduction to Machine Learning Build a foundation for practice and research in ML Basic machine learning concepts: max likelihood,
9 Classification. 9.1 Linear Classifiers
 9 Classification This topic returns to prediction. Unlike linear regression where we were predicting a numeric value, in this case we are predicting a class: winner or loser, yes or no, rich or poor, positive
9 Classification This topic returns to prediction. Unlike linear regression where we were predicting a numeric value, in this case we are predicting a class: winner or loser, yes or no, rich or poor, positive
Lecture 2. Judging the Performance of Classifiers. Nitin R. Patel
 Lecture 2 Judging the Performance of Classifiers Nitin R. Patel 1 In this note we will examine the question of how to udge the usefulness of a classifier and how to compare different classifiers. Not only
Lecture 2 Judging the Performance of Classifiers Nitin R. Patel 1 In this note we will examine the question of how to udge the usefulness of a classifier and how to compare different classifiers. Not only
In the Name of God. Lectures 15&16: Radial Basis Function Networks
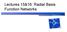 1 In the Name of God Lectures 15&16: Radial Basis Function Networks Some Historical Notes Learning is equivalent to finding a surface in a multidimensional space that provides a best fit to the training
1 In the Name of God Lectures 15&16: Radial Basis Function Networks Some Historical Notes Learning is equivalent to finding a surface in a multidimensional space that provides a best fit to the training
COMP 558 lecture 18 Nov. 15, 2010
 Least squares We have seen several least squares problems thus far, and we will see more in the upcoming lectures. For this reason it is good to have a more general picture of these problems and how to
Least squares We have seen several least squares problems thus far, and we will see more in the upcoming lectures. For this reason it is good to have a more general picture of these problems and how to
Non-Bayesian Classifiers Part II: Linear Discriminants and Support Vector Machines
 Non-Bayesian Classifiers Part II: Linear Discriminants and Support Vector Machines Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr CS 551, Fall 2018 CS 551, Fall
Non-Bayesian Classifiers Part II: Linear Discriminants and Support Vector Machines Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr CS 551, Fall 2018 CS 551, Fall
arxiv: v1 [math.na] 5 May 2011
![arxiv: v1 [math.na] 5 May 2011 arxiv: v1 [math.na] 5 May 2011](/thumbs/95/123583746.jpg) ITERATIVE METHODS FOR COMPUTING EIGENVALUES AND EIGENVECTORS MAYSUM PANJU arxiv:1105.1185v1 [math.na] 5 May 2011 Abstract. We examine some numerical iterative methods for computing the eigenvalues and
ITERATIVE METHODS FOR COMPUTING EIGENVALUES AND EIGENVECTORS MAYSUM PANJU arxiv:1105.1185v1 [math.na] 5 May 2011 Abstract. We examine some numerical iterative methods for computing the eigenvalues and
Preprocessing & dimensionality reduction
 Introduction to Data Mining Preprocessing & dimensionality reduction CPSC/AMTH 445a/545a Guy Wolf guy.wolf@yale.edu Yale University Fall 2016 CPSC 445 (Guy Wolf) Dimensionality reduction Yale - Fall 2016
Introduction to Data Mining Preprocessing & dimensionality reduction CPSC/AMTH 445a/545a Guy Wolf guy.wolf@yale.edu Yale University Fall 2016 CPSC 445 (Guy Wolf) Dimensionality reduction Yale - Fall 2016
Bayesian Decision Theory
 Bayesian Decision Theory Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr CS 551, Fall 2017 CS 551, Fall 2017 c 2017, Selim Aksoy (Bilkent University) 1 / 46 Bayesian
Bayesian Decision Theory Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr CS 551, Fall 2017 CS 551, Fall 2017 c 2017, Selim Aksoy (Bilkent University) 1 / 46 Bayesian
Discrete Mathematics and Probability Theory Fall 2015 Lecture 21
 CS 70 Discrete Mathematics and Probability Theory Fall 205 Lecture 2 Inference In this note we revisit the problem of inference: Given some data or observations from the world, what can we infer about
CS 70 Discrete Mathematics and Probability Theory Fall 205 Lecture 2 Inference In this note we revisit the problem of inference: Given some data or observations from the world, what can we infer about
18.9 SUPPORT VECTOR MACHINES
 744 Chapter 8. Learning from Examples is the fact that each regression problem will be easier to solve, because it involves only the examples with nonzero weight the examples whose kernels overlap the
744 Chapter 8. Learning from Examples is the fact that each regression problem will be easier to solve, because it involves only the examples with nonzero weight the examples whose kernels overlap the
