Truthful Spectrum Auction Design for Secondary Networks
|
|
|
- Bennett Barrett
- 5 years ago
- Views:
Transcription
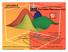
1 Truthful Spectrum Aucton Desgn for Secondary Networks Yuefe Zhu, Baochun L Department of Electrcal and Computer Engneerng Unversty of Toronto Zongpeng L Department of Computer Scence Unversty of Calgary Abstract Opportunstc wreless channel access by nonlcensed users has emerged as a promsng soluton for addressng the bandwdth scarcty challenge. Auctons represent a natural mechansm for allocatng the spectrum, generatng an economc ncentve for the lcensed user to relnqush channels. A severe lmtaton of exstng spectrum aucton desgns les n the oversmplfyng assumpton that every non-lcensed user s a snglenode or sngle-lnk secondary user. Whle such an assumpton makes the aucton desgn easer, t does not capture practcal scenaros where users have multhop routng deman. For the frst tme n the lterature, we propose to model non-lcensed users as secondary networks (SNs), each of whch comprses of a multhop network wth end-to-end routng deman. We am to desgn truthful auctons for allocatng channels to SNs n a coordnated fashon that maxmzes socal welfare of the system. We use smple examples to show that such auctons among SNs dffer drastcally from smple auctons among sngle-hop users, and prevous solutons suffer severely from local, per-hop decson makng. We frst desgn a smple, heurstc aucton that takes nter-sn nterference nto consderaton, and s truthful. We then desgn a randomzed aucton based on prmal-dual lnear optmzaton, wth a proven performance guarantee for approachng optmal socal welfare. A key technque n our soluton s to decompose a lnear program (LP) soluton for channel assgnment nto a set of nteger program (IP) solutons, then applyng a par of talored prmal and dual LPs for computng probabltes of choosng each IP soluton. We prove the truthfulness and performance bound of our soluton, and verfy ts effectveness through smulaton studes. I. INTRODUCTION Recent years have wtnessed substantal growth n wreless technology and applcatons, whch rely crucally on the avalablty of bandwdth spectrum. Tradtonal spectrum allocaton s statc, and s prone to neffcent spectrum utlzaton n both temporal and spatal domans: large spectrum chunks reman dlng whle new users are unable to access them. Such an observaton has prompted research nterest n desgnng a secondary spectrum market, where new users can access a lcensed channel when not n use by ts owner, wth approprate remuneraton transferred to the latter. In a secondary spectrum market, a spectrum owner or prmary user (PU) leases ts dle spectrum chunks (channels) to secondary users (SUs) through auctons [], [2]. SUs submt b for channels, and pay the PU a prce to access a channel f ther b are successful. A natural goal of spectrum aucton desgn s truthfulness, under whch an SU s best strategy s to bd ts true valuaton of a channel, wth no ncentve to le. A truthful aucton smplfes decson makng at SUs, and lays a foundaton for good decson makng at the PU. Another mportant goal n spectrum aucton desgn s socal welfare maxmzaton,.e., maxmzng the aggregated happness of everyone n the system. Such an aucton ten to allocate channels to SUs who value them the most. A unque feature of spectrum aucton desgn s the need of approprate consderaton for wreless nterference and spatal reuse of channels. A channel can be allocated to multple SUs provded that they are far apart, wth no mutual nterference. Optmal channel assgnment for socal welfare maxmzaton s equvalent to the graph colourng problem, and s NP-hard [3], even assumng truthful b are gven for free. Exstng works on spectrum auctons mostly focus on resolvng such a challenge (e.g., [4], [5]) whle assumng the smplest model of a SU: a sngle node, or a sngle lnk, smlar to a sngle hop transmsson n cellular networks [2], [4], [5]. SN 3 SN3 2 SN2 Fg. : A secondary spectrum market wth 3 SNs and 2 channels. After extensve research durng the past fve years, aucton desgn for sngle-hop users, each requestng a sngle channel, has been relatvely well understood. However, a practcal SU may very well comprse of multple nodes formng a multhop network, whch we refer to as a secondary network (SN). These nclude scenaros such as users wth multhop access to base statons, or users wth ther own moble ad hoc networks. SNs requre coordnated end-to-end channel assgnment, and n general beneft from mult-channel dversty along ts path. The SN model subsumes the SU model as the smplest specal case. Fg. depcts three co-located SNs, SN, SN2 and SN3, whch have nterference wth one another, because ther network regons overlap. The prmary network (PN) has two channels, Ch and Ch2, whch have been allocated to SN and SN2, respectvely. Now SN3 wshes to route along a two-hop path 2 3. Under exstng sngle-channel
2 auctons for SUs, SN3 cannot obtan a channel, because each channel nterferes wth ether SN or SN2. However, a soluton exsts by relaxng the one channel per user assumpton, and assgnng Ch to lnk 2 and Ch2 to the lnk 2 3. In general, takng multchannel, multhop transmssons by SNs nto consderaton can apparently mprove channel utlzaton and socal welfare. Note here that the model n whch an SN b for multple channels s napplcable, because due to the unawareness of other SNs nformaton, an SN cannot know the number of channels to bd for, to form a feasble path. Desgnng truthful auctons for SNs s an nterestng problem, but by no means an easy one. We note that t s hard for an SN to decde by tself an optmal or good path to bd for. Such decson makng requres global nformaton on other SNs as well, and s naturally best made by the auctoneer,.e., the PN. Consequently, a bd from an SN ncludes just a prce t wshes to pay, wth two nodes t wshes to connect usng a path. Furthermore, SNs now nterfere wth each other n a more complex manner. Not only that they transmt along multhop paths, but each path can be assgned wth dstnct channels at dfferent lnks. The PN, after recevng b, nee to make judcous jont routng and channel assgnment decsons. In ths work, we frst desgn a smple heurstc aucton for spectrum allocaton to SNs, whch guarantees both truthfulness and nterference-free channel allocaton, provdng wnnng SNs wth end-to-end multhop paths, wth a channel assgned to each hop. The heurstc aucton enables mult-channel assgnment along a path, thereby reducng the possblty that a path s blocked due to nterference. To acheve truthfulness, we employ a greedy, monotonc allocaton rule and desgn an accompanyng payment scheme, by referrng to Myerson s characterzaton of truthful auctons [6]. The heurstc aucton provdes no hard guarantee on socal welfare. We next desgn a randomzed aucton, whch s truthful n expectaton, and s provably approxmate optmal n socal welfare. We note that absolute optmal socal welfare s mpossble, snce the jont routng-channel assgnment problem s already NP-hard wth truthful b gven for free. We relax an nteger program (IP) formulaton to the socal welfare maxmzaton problem nto a lnear program (LP), and prove an upper-bound on the ntegralty gap. We then employ the decomposton technque due to Lav and Swamy [7] to decompose an LP soluton nto a set of feasble IP solutons (allocatons). A par of prmal-dual LPs are formulated, for computng a probablty dstrbuton over the allocaton set. Based on the set and the probabltes, an approxmaton algorthm s fnally desgned, for computng a feasble soluton to the orgnal IP wth a provable performance guarantee. Such a soluton assgns channels to paths constructed for wnnng SNs. We then apply the classc VCG [8] [] payment scheme, to conclude the desgn of a truthful aucton that approxmately maxmzes socal welfare for spectrum allocaton to SNs. The remander of the paper s organzed as follows. We dscuss related work n Sec. II, and present prelmnares n Sec. III. A heurstc truthful aucton s desgned n Sec. IV. In Sec. V, we propose and analyze a randomzed aucton wth performance bound. Smulaton studes are presented n Sec. VI. Sec. VII concludes the paper. II. RELATED WORK Auctons serve as an effcent mechansm for dstrbutng scarce resources to competng partcpants n a market. To smplfy the strategcal behavour of agents and hence encourage partcpaton, truthfulness s desred. A celebrated work s the VCG mechansm due to Vckrey [], Clarke [8], and Groves [9]. However, the VCG mechansm s only sutable when optmal solutons are computatonally feasble, and s not drectly applcable for secondary spectrum auctons, because nterference-free channel allocaton s NP-Hard. Allocatng spectrum usng auctons has receved consderable research attenton recently. Early solutons nclude auctons that allocate power [] and allocate a channel to each wnnng user [2]. These auctons are unfortunately not truthful. VERITAS [] s the frst truthful spectrum aucton based on the monotonc allocaton rule. Zhou and Zheng propose TRUST [3], whch s a double aucton wth multple sellers (lcensed users). Ja et al. [4] desgn a spectrum aucton mechansm that not only encourages truthful behavour but also computes approxmately maxmum revenue, whch s an alternatve goal to maxmum socal welfare. For spectrum auctons that take nterference among secondary users nto consderaton, Wu et al. [2] develop a semdefnte programmng based mechansm, whch s truthful and resstant to bdder colluson. Gopnathan [5] et al. propose auctons that ncorporate farness consderatons nto channel allocaton. Ther goal s to maxmze socal welfare, whle ensurng a noton of farness among bdders when the aucton s repeatedly held. A truthful and scalable spectrum aucton enablng both sharng and exclusve access s proposed by Kash et al. [4]. Ths aucton handles heterogeneous agent types wth dfferent transmsson powers and spectrum nee. We note that, all the works mentoned above focus on sngle-hop users bddng for a sngle channel only. Our work essentally generalzes the problem to mult-hop users, who may enjoy mult-channel paths. III. PRELIMINARIES In ths secton, we frst ntroduce some background n truthful aucton desgn n Sec. III-A, then descrbe our system model n Sec. III-B. A. Truthful Aucton Desgn Aucton theory s a branch of economcs that studes how people act n an aucton and analyzes the propertes of aucton markets. We frst ntroduce some basc and most related concepts, defntons and theorems from aucton desgn. An aucton allocates tems or goo (channels n our case) to compettve agents wth b and prvate valuatons. We adopt w as nonnegatve valuatons of each agent, whch s often prvate nformaton known only to the agent tself. Besdes determnng an allocaton, an aucton also computes
3 payments/charges for wnnng bdders. We denote by p() and b the payment and bd of agent, respectvely. Then the utlty of s a functon of all the b: { w p() f agent wth bd b gets an tem u (b, b ) = otherwse where b s the vector of all the b except b. We frst adopt some conventonal assumptons n economcs here. We assume that each agent s selfsh and ratonal. A selfsh agent s one that acts strategcally to maxmze ts utlty. An agent s sad to be ratonal n that t always prefers the outcome that brngs tself a larger utlty. Hence, an agent may le about ts valuaton, and bd b w f dong so yel a hgher utlty. Truthfulness s a desrable property of an aucton, where reportng true valuaton n the bd s optmal for each agent, regardless of other agents b. If agents have ncentves to le, other agents are forced to strategcally respond to these les, makng the aucton and ts analyss complex. A key advantage of a truthful aucton s that t smplfes agent strateges. Formally, an aucton s truthful f for any agent wth any b w, any b, we have u (w, b ) u (b, b ) () An aucton s randomzed f ts allocaton decson makng nvolves flppng a (based) con. The payment and utlty of an agent are then random varables. A randomzed aucton s truthful n expectaton f () hol n expectaton. Besdes, we also prefer an aucton to be ndvdually ratonal, n whch agents pay no more than ther gan (valuatons). As dscussed, the classc VCG mechansm for truthful aucton desgn requres the optmal allocaton to be effcently computable, and s not practcal for spectrum auctons, snce optmal channel allocaton s NP-hard. If we am to desgn a talored, heurstc truthful aucton, then we may rely on the characterzaton of truthful auctons by Myerson [6]. Theorem. Let P (b ) be the probablty of agent wth bd b wnnng an aucton. An aucton s truthful f and only f the followngs hold for a fxed b : P (b ) s monotoncally non-decreasng n b ; Agent bddng b s charged b P (b ) b P (b)db. Gven Theorem, we see that once the allocaton rule P( ) = {P (b )} N s fxed (N s the set of bdders), the payment rule s also fxed. For the case where the aucton s determnstc, there are two equvalent ways to nterpret Theorem : () there exsts a mnmum bd b, such that wll wn only f agent b at least b,.e., the monotoncty of P (b ) mples that, there s some crtcal bd b, such that P (b ) s for all b > b and for all b < b ; () the payment charged to agent for a fxed b should be ndependent of b (formally, p (b ) = b b db = b b ). B. System Model We assume there s a set of SNs, N. Each SN has deployed a set of nodes n a geographcal regon, and has a demand for multhop transmsson from a source to a destnaton. A PN TABLE I: Lst of notatons w valuaton of agent b bd of agent b bd of all agents except b φ() vrtual bd of agent p() payment of agent u a node n SN luv lnk from u to v fuv flow rate on lnk luv O(w) objectve functon of IP (5) S(w) objectve functon of the LPR I s() the set of SNs that nterfere wth SN along ts path x(c, luv) bnary var: whether channel c s allocated to lnk luv G (E, V ) connectvty graph of SN wth lnk set E, node set V H(E H, V H ) conflct graph of lnks of all the SNs wth edge set E H and vertex set V H has a set of channels, C, avalable for auctonng n the regon. We refer to SNs as agents and the PN as the auctoneer. Each node wthn an SN s equpped wth a rado that s capable of swtchng between dfferent channels. SNs do not collaborate wth each other, and nodes from dfferent SNs are not requred to forward traffc for each other. We assume nodes from each SN form a connected graph G (E, V ), whch also contans node locatons. We use node and lnk for the connectvty graphs and vertex and edge for the conflct graph ntroduced later. To better formulate the jont routng-channel assgnment problem, we ncorporate the concept of network flows. Let u be a node n SN and s, d be the source and the destnaton n SN. We use luv to denote the lnk from node u to node v belongng to SN, and fuv to denote the amount of flow on lnk luv. Later we connect d back to s wth a vrtual feedback lnk l, for a compact formulaton of the jont optmzaton IP. We defne a conflct graph H(E H, V H ), whose vertces correspond to lnks from all the connectvty graphs. We use (luv, lpq) j to denote an edge n E H, ndcatng that lnk luv and lnk lpq j nterfere f allocated a common channel. Before the aucton starts, each SN submts to the auctoneer a compound bd, defned as B = (G (E, V ), s, d, b ). Then the conflct graph can be centrally obtaned by the auctoneer. We denote by w the prvate valuaton of SN for a feasble path between s and d, and p() ts payment. b, w and p() all represent monetary amounts. Note that we assume agents only have ncentves to le about ther valuatons. We denote by R T (u ) and R I (u ) the transmsson range and nterference range of node u, respectvely. We assume that R I (u ) R T (u ) = and R T (u ) R max for any node u where. Snce no nter-sn collaboraton s assumed, lnks from dfferent SNs do not partcpate n jont MAC schedulng, and cannot be assgned the same channel f they nterfere. As a result, two lnks luv and lpq j nterfere f a node n {u, v} s wthn the nterference range of a node n {p, q}, and cannot be assgned the same channel f j. Formally, let a bnary varable x(c, luv) {, } denote whether channel c C s assgned to lnk luv for user. If for channel c C, x(c, luv) = x(c, lpq), j then (luv, lpq) j / E H. Hence, for the jont routng-channel assgnment problem we have the Channel Interference Constrants: x(c, l uv) + x(c, l j pq), (l uv, l j pq) E H, c C (2) We also need Flow Conservaton Constrants,.e., at any
4 node n V, the total ncomng and outgong flows equal (recall the vrtual feedback lnk): fuv = fvu, v V (3) u V u V Assumng each channel has the same unt capacty, we have the Capacty Constrants: x(c, luv) (4) uv u V \{d }f c C whch also ensures that a lnk can be assgned a sngle channel only. An agent nee an end-to-end path between ts source and destnaton. Ths correspon to a network flow of rate. Note that the lnk flow on the feedback lnk f equals the end-toend flow for SN. We formulate the jont routng-channel assgnment problem for SNs nto an IP: subject to maxmze O(w) = N w f (5) x(c, luv) + x(c, lpq) j, fuv = fvu, u V u V uv u V \{d }f x(c, luv), c C f uv, x(c, l uv) {, }. (l uv, l j pq) E H, c C v V v V where O(w) denotes the objectve functon of the IP. Solvng ths IP to optmal s an NP-hard problem. Therefore we frst ntroduce a heurstc aucton n Sec. IV, whch s based on the technque of monotonc allocaton and crtcal b, and s smple and truthful. However, t does not provde any bound on the socal welfare generated. A more sophstcated, randomzed aucton wth a proven bound s studed next, where the LP relaxaton of IP (5) s solved as a frst step. IV. A HEURISTIC TRUTHFUL AUCTION In ths secton, we desgn an aucton wth a greedy style allocaton and a payment scheme to ensure truthfulness. The aucton conssts of two phases: Algorthm determnes the channel assgnment and wnnng bdders, and Algorthm 2 computes the payments for wnnng agents. A. Channel Allocaton As dscussed n Sec. III, the key to desgnng a truthful aucton s to have a non-decreasng allocaton rule. Prces can then be calculated by the crtcal b to make the aucton truthful. A greedy allocaton s adopted n Algorthm. Assume channels are ndexed by, 2,... C. For a smple heurstc aucton, we frst compute the shortest path for each agent as ts end-to-end path. Let I s () be the set of SNs that nterfere wth along the path. We defne the vrtual bd of SN as φ() = b (6) I s () The ratonale behnd scalng the bd by I s () s to take s nterference wth other agents nto consderaton, for heurstcally maxmzng socal welfare. Then we greedly assgn mnmum ndexed avalable channels along the paths to each lnk, accordng to a non-ncreasng order of vrtual b φ(). Algorthm A greedy truthful aucton channel allocaton.. Input: Set of channels C, all the compound b B = (G (E, V ), s, d, b ), conflct graph H(E H, V H ) 2. for all N do 3. I s () ; 4. Compute the shortest path P from s to d ; 5. for all N do 6. for all luv along path P do 7. x(c, luv) c C; 8. f (luv, lpq) j E H then 9. I s () I s () {};. φ() b I ; s(). Wn() TRUE; 2. for N n non-ncreasng order of φ() do 3. for all luv along path P do 4. Let Tuv C; 5. for all c Tuv do 6. f x(c, lpq) j = wth (luv, lpq) j E H, p, q then 7. Tuv Tuv\{c}; 8. f Tuv = then 9. Wn() FALSE; 2. f Wn() = TRUE then for all luv along path P do Choose the mnmum ndexed channel c m n Tuv; 23. x(c m, luv) ; Fg. 2 shows an example to llustrate the channel assgnment procedure. There are four SNs, a, b, c and d, where φ(a) > φ(b) > φ(c) > φ(d). Two channels are avalable for allocaton. In the fgure, two ntersectng lnks also nterfere wth each other. If two lnks from two dfferent SNs ntersect, they cannot be allocated wth the same channel. The algorthm frst assgns Channel to SN a. As a result, t cannot assgn Channel to the frst lnk of SN b, whch receves Channel 2 nstead, as shown n Fg. 2b, leavng SN c wthout a channel t s mpossble to assgn ether channel to c s frst lnk. However, SN d wns, and receves a channel assgnment along ts path wthout ntroducng nterference to a or b. We now prove that the greedy aucton s monotone. Lemma. Algorthm s monotone. That s, the probablty of bdder wth bd b wnnng the aucton s non-decreasng n b, and crtcal b for wnnng agents exst. Proof: Bddng hgher can only ncrease an agent s vrtual bd, and therefore ncrease ts rank n Algorthm. Hence, the probablty of assgnng a channel to the agent s nondecreasng. Besdes, Algorthm s determnstc, so a crtcal bd b exsts for a wnnng bdder, such that agent always wns f t b b b.
5 d a c b d a c 2 b d a (a) Assgn channels to SN a (b) Assgn channels to SN b (c) Assgn channels to SN d Fg. 2: Procedure of channel assgnment. Dots and squares represent source and destnaton nodes respectvely. c 2 2 b B. Payment Calculaton Algorthm 2 computes payments for the wnnng agents. The payment scheme desgn s where we ensure the truthfulness of an aucton. Algorthm 2 ams to fnd a crtcal bdder wth crtcal bd b for a wnnng agent, such that s guaranteed to wn as long as s vrtual bd φ() φ (). Here φ () = b I s() s the crtcal vrtual bd for. If b s ndependent from b, then chargng agent b wll ensure that the aucton s truthful, whch we wll argue formally later. We now explan how Algorthm 2 works. It frst clears a wnnng agent s bd, and hence ts vrtual bd, to. Then we run Algorthm based on (, b ). In Algorthm, an agent loses only f a lnk along ts shortest path s unable to receve any channel. If we are unable to accommodate agent, there must exst at least one lnk along ts shortest path whose neghbourng lnks (neghbourng vertces n the conflct graph) have used all the channels. From all the agents that block lnks of agent, we fnd out an agent j wth the mnmum vrtual bd, set t as s crtcal bdder, and compute s payment. We clam that φ() φ(j), because otherwse agent would not be a wnnng agent among agents n I s () {}. Agent s payment can be computed as follows: p() = φ () I s () = φ(j) I s () (7) For the example n Fg. 2, we frst set SN a s bd to, and run Algorthm based on the new bd vector. After assgnng channels to agent c, we fnd that there are no avalable channels for the second lnk of agent a. Hence, agent c becomes the crtcal bdder of agent a, whch lea to a s payment p(a) = φ(c) I s (a). The rule apples to the other two wnnng agents b and d as well, where p(b) = φ(c) I s (b) and p(d) =. We next show that the aucton s ndvdually ratonal and truthful. Lemma 2. The aucton shown n Algorthms and 2 s ndvdually ratonal. Proof: Assume agent wns by bddng b, and let j be the crtcal bdder of. Then we have φ() φ(j), so p() = φ(j) I s () φ() I s () = b. Theorem 2. The aucton n Algorthms and 2 s truthful. Proof: Fx, b. Let w and w be agent s bd when beng truthful and not, respectvely. We need to show that for agent wth valuaton w, the utlty of bddng w s no less than the utlty of bddng w. We analyze the aucton case by Algorthm 2 A greedy truthful aucton payment calculaton.. Input: Set of channels C, all the compound b B = (G (E, V ), s, d, b ), conflct graph H(E H, V H ), all the routng paths P and channel assgnment from Algorthm. 2. for N n non-ncreasng order of φ() do 3. p() ; 4. f Wn() = then 5. Set b ; 6. Run Algorthm on (b, b ); 7. f Wn() = FALSE then 8. Let φ () + ; 9. for all luv along path P do. Let Tuv C;. for all c Tuv do 2. f x(c, lpq) j = wth (luv, lpq) j E H then 3. Tuv Tuv\{c}; 4. f T uv = then 5. A {j (luv, lpq) j E H, p, q; Wn(j) = TRUE}; 6. φ () mn(φ (), mn j A φ(j)); 7. p() φ () I s () ; case. Let { f agent wth bd b receves a channel; r(b ) = f agent wth bd b doesn t receve a channel. Frst, assume that w < w. Accordng to Lemma, t s mpossble for agent to have r(w ) = and r(w ) =. If r(w ) = and r(w ) =, there s no ncentve to le. If r(w ) = and r(w ) =, because the aucton s ndvdually ratonal, also has no ncentve to le. If r(w ) = and r(w ) =, then by observng that the crtcal bdder does not change, the utlty for agent remans the same. Next, assume that w > w. Agan t s mpossble for agent to have r(w ) = and r(w ) =. If r(w ) = and r(w ) =, the crtcal bdder does not change, so the utlty remans the same. If r(w ) = and r(w ) =, then has no ncentve to le. If r(w ) = and r(w ) =, then at least one lnk s unable to receve a channel (blocked), when agent b w. From all the agents that block lnks of, we fnd out the wnnng agent j wth mnmum vrtual bd. If b w > w and get assgned a channel, agent j would be the crtcal agent of. Then agent s payment would be p() = φ(j) I s () w, whch mples a nonpostve utlty of. Ths heurstc aucton, amng at achevng a monotonc
6 allocaton rule and fndng out a crtcal bdder for each wnnng agent, s drectly based on Theorem. V. A TRUTHFUL AUCTION FOR APPROXIMATELY MAXIMIZING SOCIAL WELFARE The greedy aucton just presented n Sec. IV, whle smple and truthful, attempts to maxmze socal welfare n a heurstc manner, wthout provdng any guarantee. In ths secton, we set out to desgn a more sophstcated, randomzed, lnear programmng based truthful aucton wth proven boun on approxmate socal welfare maxmzaton. We frst obtan the lnear programmng relaxaton (LPR) of IP (5), and solve the LPR optmally. We can turn the optmal LPR soluton, scaled down by, to a convex combnaton of nteger solutons, through a prmal-dual lnear program. Here s the upper bound of the ntegralty gap of IP (5) and the LPR. Vewng ths convex combnaton as specfyng a probablty dstrbuton over the nteger solutons, we arrve at a randomzed, truthful n expectaton aucton wth the VCG payment scheme. We prove that t approxmately maxmzes socal welfare. A. Decomposng the Fractonal Soluton Optmally and effcently solvng IP (5) s nfeasble, so we resort to an approxmaton approach. Frst, we obtan an LPR by allowng the nteger varables fuv, x(c, luv) to take fractonal values n [, ]. We use S(w) to denote the objectve functon of the LPR. Let f ( ) be the optmal flow vector from solvng the LPR, whch also contans agents wnnng/losng nformaton. Assume the ntegralty gap between IP (5) and ts LPR s at most, and there s a -approxmaton algorthm that verfes ths gap,.e., t acheves at least S(w), for any set of w. We employ the technque due to Lav and Swamy [7]. We utlze the -approxmaton algorthm and compute n polynomal tme a convex decomposton of f ( ) nto nteger solutons n polynomal sze. That s, we wll have ρ(l) values f ( ) such that = l I ρ(l)f (l), where {f (l)} l I s the set of all nteger solutons, I s ts ndex set and ρ(l), l I ρ(l) =. Now we can vew ths decomposton as specfyng a probablty dstrbuton over the nteger solutons. A soluton f (l) s selected wth probablty equal to ρ(l). If we set prces n such a way that the expected prces are VCG prces scaled down by, that wll make our randomzed aucton truthful n expectaton. Furthermore, the expected socal welfare s exactly the value of the LPR scaled by. We next provde detals on the decomposton and then prove the upper bound on the ntegralty gap. Let f ( ) be an optmal soluton to the LPR contanng all the f values. We use Z(F) = {f (l)} l I to denote the set of all nteger solutons to the LPR, where F denotes the feasble regon of the LPR, I s an ndex set of the nteger solutons. The crux of the method s to decde ρ(l) values such that f ( ) = l I ρ(l)f (l), where ρ(l), l I ρ(l) =. Now one can vew ths convex combnaton as specfyng a probablty dstrbuton over the nteger solutons, where a soluton f (l) s selected wth probablty equal to ρ(l). We solve the LP below to obtan the convex decomposton: subject to l I mnmze l I ρ(l)f (l) = f ( ) ρ(l) l I The dual of LP (8) s: subject to maxmze ρ(l) (8) N ρ(l) l I N η f(l) + λ N λ η unconstraned η f ( ) + λ (9) l I N To obtan the decomposton, an algorthm that approxmately computes the maxmum socal welfare s needed. We adapt a jont traffc routng and channel assgnment soluton framework due to Alcherry et al. [5] nto our settng, wth the objectve functon beng the weghted sum of throughput (socal welfare n our problem) and wth the number of rados at each node beng. Gven that ths algorthm may result n fractonal flows, we ntroduce the followng modfcaton: for an SN whose flow s fractonal, among SNs n {} I s () that also have fractonal flows, fnd out the SN wth maxmum w f, set ts flow to and others to. We denote ths modfed algorthm as A. We show later that Algorthm A verfes the upper bound of the ntegralty gap between (5) and the LPR. The prmal LP (8) has an exponental number of varables, whch wll take exponental tme to solve wth the smplex or nteror pont method [6]. Hence we resort to ts dual (9), whch has an exponental number of constrants. If we have a separaton oracle, we can apply the ellpsod method to solve the dual (9) and hence (8) n polynomal tme [6]. We show a separaton oracle for the dual later, so we can effcently solve ths par of prmal-dual LPs. One can vew η as a valuaton. A potental problem s that the η values could be negatve, whereas A s only for non-negatve valuatons. However, one can nstead use A wth the non-negatve valuatons η (+) gven by η (+) = max(η, ), and ths yel a separaton oracle [7]. Clam. Let η = {η } N be any weght vector. η (+) = max(η, ). Gven any nteger soluton f Z(F), one can obtan f (l) Z(F) such that N η f (l) = N η(+) f. Proof: We frst explot the packng property. That s, f a Z(F) and a 2 a s ntegral then a 2 Z(F). Now
7 we set f (l) = f f η and otherwse. Clearly, N η f (l) = N η(+) f. Snce f (l) f s ntegral, by the packng property f (l) Z(F). Now we are ready to show the followng lemma: Lemma 3. If the optmal soluton to (8) s ρ, then we have l I ρ (l) =. Proof: We show that the optmal value of (9) s, and hence the lemma follows by strong LP dualty. If we smply set λ =, η = for all N, t provdes a feasble soluton wth value. We then prove that the optmal value s at most by way of contradcton. Let (η ( ), λ ( ) ) denote the optmal soluton to (9). Suppose N η( ) f ( ) + λ ( ) >. Usng Algorthm A and Clam, we can compute a socal welfare maxmzng feasble soluton f (l), such that η ( ) f(l) S(η( )(+) ) N = N N η ( )(+) f ( ) η ( ) f ( ). () Now we have N η( ) f (l)+λ( ) N η( ) f ( ) + λ ( ) >, whch contradcts the frst set of nequaltes of (9), thereby contradctng the feasblty of (η ( ), λ ( ) ). The above lemma shows that wthout beng more restrctve, the nequalty N η f ( ) + λ can be added to the dual (9). We wll run the ellpsod method to solve ths dual LP. The frst set of nequaltes of (9) wll be the volated nequaltes returned by the separaton oracle durng the executon of the ellpsod method. The separaton oracle s, at a pont (η, λ), f N η f ( ) + λ >, then we can use Algorthm A and Clam to fnd an f (l) for whch the constrants of (9) s volated; otherwse, we use the half space N η f ( ) + λ to cut the current ellpsod. Snce the ellpsod method s guaranteed to take at most a polynomal number of steps, t wll return a set of solutons {f (l)} l I that s polynomal n sze. Then we can plug back these solutons to (8), leadng to a lnear program wth a polynomal number of varables and constrants, whch we can solve to recover ρ(l) s that sum to. B. Studyng the Integralty Gap Now we nvestgate the ntegralty gap of the IP (5) and the LPR. In the LPR, fractonal channel allocaton s drectly related to lnk flows, whch can be vewed as the fracton of tme a specfc lnk s actve. Smlarly, we can turn the constrant (2) nto the followng Lnk Schedulng Constrant [5]: fuv + fpq j. () l j pq:(l j pq,l uv ) E H where we assume there s only one channel, for ease of exposton. We wll argue later that the upper bound of the ntegralty gap between IP (5) and the LPR does not change when consderng multple channels. 2R max R max Fg. 3: The crcumstance formed by nterference regons of one lnk 2R max 2R max Fg. 4: The crcumstance formed by nterference regons of two lnks. We frst ntroduce the followng lemma for a sngle lnk, based on geometrc arguments: Lemma 4. For any channel c C, x(c, luv) + x(c, lpq) j α( ) (2) l j pq:(l j pq,l uv ) E H where α( ) s a constant that depen only on. Proof: For a gven lnk luv, we need to fnd the maxmum number of lnks that nterferes wth luv yet does not nterfere wth one another. For smplcty, we prove the followng for = 2; proofs for other values of can be derved smlarly. The worst case happens when R T (u ) = R T (v ) = R max and d(u, v ) = R max. We use U(u, v ) to denote the regon formed by the unon of two crcles wth radus 2R max and centre u and v, respectvely. Then the problem becomes placng a max number of ponts on the crcumference of U(u, v ) that are at least 2R max apart. The crcumference s composed of two major arcs wth length 4π 3, shown n Fg. 3. Among these lnks, every ndependent set s of sze at most 8. Hence n ths case α( ) = 9. We then nvestgate the ntegralty gap based on the worst case analyss of multhop transmssons. Lemma 5. For any channel c C and an SN wth a path that has L hops, there are at most g(l, ) nterference free SNs among I s () f all of them are assgned channel c, where g(l, ) s a functon that only depen on L and. Proof: Consderng the = 2 case as well, for an end-toend path, the worst case happens when the path s formed as a straght lne, and all the nterference-free lnks along the path belong to dfferent SNs. Addng one lnk nto a path ncreases the length of crcumstance by 4 arcsn 4, whch s due to the bold arcs shown n Fg. 4, where a two-hop path s formed. Then for an SN wth path length L, we have { L + 7 L s odd g(l, 2) = (3) L + 6 L s even We can loosen ths bound to L + 7, for all L. Smlar lnear functons of L can be derved wth other values of. Theorem 3. Assume that a SN s path s at most L max -hops. Then the ntegralty gap between the IP (5) and the LPR s at most = g(l max, ) +. Proof: For an SN and a sngle channel c, we know from Lemma 5 that there are at most g(l, ) nterference free SNs among I s (), ensurng every hop obeys (2). In the worst
8 case, the ntegral soluton pcks only one SN from at most g(l, ) + SNs. Snce ths s true for any SN and g(l, ) s an ncreasng functon of L, the lemma follows for a sngle channel case. If there are C channels, for an SN, we can magne that the maxmum ndependent set of a lnk s duplcated nto C copes, so that the ntegral soluton wll pck SNs from less than ( C )g(l, )L+( C )L+ = ( C )(g(l, )+ )L SNs. Snce the ntegral soluton pcks at least ( C )L+ SNs (pcks, and C SNs per lnk along s path), the ntegralty gap s at most ( C )(g(l max, ) + )L max + ( C )L max + ( C )(g(l max, ) + )L max ( C )L max g(l max, ) + (4) Snce Algorthm A modfes a fractonal flow to among I s (), t apparently verfes. C. A Randomzed Approxmaton Aucton We now present the desgn of our randomzed aucton, n Algorthm 3. It frst solves the LPR to obtan the optmal f ( ). Then a decomposton technque descrbed prevously s employed to compute a feasble set of allocatons and a probablty dstrbuton. Next, a soluton s chosen accordng to ts assocated probablty. Snce the ellpsod method and A both run n polynomal tme, our aucton s computatonally effcent. For each bdder that wns and acheves throughput f (l) wth probablty ρ(l), the payment s calculated as follows: p() = ( b f ( ) j y(j) b j f ( ) ) (5) j j where y s obtaned by recomputng the LPR wth b =. Algorthm 3 A truthful-n-expectaton aucton. Input: Set of channels C, all the compound b B = (G (E, V ), s, d, b ), conflct graph H(E H, V H ). 2. Solve the LPR, obtan optmal soluton f ( ) ; 3. Use the ellpsod method and Algorthm A on (9) wth f ( ), obtan a polynomally szed set of {f (l)}; 4. Solve (8) wth f ( ) and {f (l)}, fndng the ρ(l) values; 5. Pck some soluton f (l) wth probablty ρ(l); 6. Let p(), N ; 7. for all such that f (l) = do 8. Compute S(b =, b ) wth the LPR. Let y be the soluton; 9. p() ( j b jy(j) j b jf ( ) ); f ( ) Theorem 4. The aucton shown n Algorthm 3 s truthful n expectaton. Proof: Fx, b. Let w and w be agent s bd when beng truthful and not truthful, respectvely. Let a and a be the solutons to the LPR for b (w, b ) and (w, b ), respectvely. The expected utlty of when bddng truthfully s E[u (w )] = a() [w a() ( b j y(j) b j a(j))] j j = (w a() + j b j a(j) j b j y(j)) (6) Snce for every bdder, a s optmal for (w, w ). Assumng other bdders bd truthfully yel E[u (w )] (w a () + b j a (j) b j y(j)) j j = E[u (w )] (7) We now arrve at the followng theorem: Theorem 5. The aucton shown n Algorthm 3 acheves a -approxmate maxmum socal welfare n expectaton. VI. SIMULATION RESULTS Our auctons were evaluated through smulatons. We frst focus on the heurstc aucton. For each SN, we randomly and unformly dstrbute some nodes n a regon. Two nodes are connected f ther Eucldean dstance s at most.5. The largest connected component s used as the connected graph for the correspondng SN. All b are taken from a unform dstrbuton n the range of [4, ]. Snce the aucton has already been proven to be truthful and the optmal socal welfare s hard to obtan, we evaluate ts performance n terms of aucton effcency, whch s defned as N ϑ = w f N w (8) We then vary the number of channels n the smulatons to study the performance of the aucton, where all data are averaged over experments. We observe that, n general, as the number of channels ncreases, the aucton effcency ncreases as well, whch verfes the ntuton that the more channels, the hgher probablty for a bdder to wn. Frst we change the number of bdders (SNs), whle fxng = 4 and the number of nodes for each SN at 3. From Fg. 5a, we can see that our aucton n general effectvely explots the ncreasng number of channels avalable. Even n the extremely nterferng case where there are SNs n the regon, the effcency ncreases approxmately lnearly wth the number of channels. Fg. 5b (wth 5 bdders and 3 nodes for each SN) and Fg. 5c (wth 5 bdders and = 4) also show the performance of our aucton n terms of the severty of nterference, by changng and the sze of SNs. We can see that the change of s does not hurt the performance too much. However, large szes of SNs may ncrease nterference sgnfcantly, thereby decreasng the aucton effcency, where the connected graph for an SN wth 5 nodes dstrbuted can contan more than 5 nodes.
9 Effcency Bdders 2 Bdders.2 5 Bdders Bdders Number of Channels (a) Aucton effcency wth dfferent numbers of bdders enrolled. Effcency = = 2.2 = 3 = Number of Channels (b) Aucton effcency under dfferent nterference stuatons. Fg. 5: Performance evaluaton of the heurstc aucton. Effcency Nodes.2 3 Nodes 5 Nodes Number of Channels (c) Aucton effcency wth dfferent szes of networks. We then compare the performance of our aucton wth two other approaches. One s a greedy aucton that only assgns one channel to an SN, n whch the same channel cannot be assgned to SNs who nterfere wth one another. The other one s smply a mult-tem aucton that greedly assgns channels to lnks n each SN, wthout global vson of formng an end-toend path. We fx = 4, the number of potental nodes for each SN s 45, and the number of bdders s 5. We can see from Fg. 6 that our aucton and the sngle-channel aucton perform much better than the mult-tem aucton. Another observaton s that the effcency of our aucton ncreases faster than the sngle-channel one as the number of channels ncreases. Ths justfes the use of multchannel assgnment for each SN. Effcency Multchannel Enabled Sngle Channel Mult Item Number of Channels Fg. 6: Comparson of three dfferent aucton settngs. Number of SNs Amount of Flows Fg. 7: A hstogram of fractonal solutons of the LPR. Fg. 7 shows the dstrbuton of the fractonal soluton to the LPR for one smulaton nstance (wth 5 bdders, 3 nodes for each SN, one channel and = 4), where the sum of all flows equals The agents wth relatvely large non-zero flows n the soluton are shown n Table II. We can see that there s only one agent guaranteed to wn and most of them almost always lose (the amount of flows s approxmately ). In the worst case, our randomzed aucton wll select agents wth flow amount,.85,.54, and one of agents wth flow amount.5, and another agent wth fractonal flow. Note that two agents wth flow amount larger than.5 must not nterfere wth each other. Hence, n ths experment, algorthm A can actually acheve of the soluton to the LPR, hence rasng.3 the socal welfare wth our randomzed aucton. TABLE II: Agents wth non-zero fractonal flows Agent Flow VII. CONCLUSION Secondary spectrum auctons are emergng as a promsng approach to effcently dstrbutng and sharng scarce wreless spectrum. For the frst tme n the lterature, we propose the concept of a secondary network, relaxng the over-smplfyng assumpton on secondary users n exstng research. We desgned two auctons for spectrum allocaton among SNs. The frst s a smple, greedy style determnstc aucton that heurstcally maxmzes socal welfare. The heurstc aucton s truthful due to ts monotone allocaton rule. The second s a randomzed, lnear optmzaton based aucton that s not only truthful (n expectaton), but also provdes proven guarantees on socal welfare. In future work, we plan to further mprove the performance guarantee of the randomzed aucton, by provng a tghter bound on socal welfare approxmaton. REFERENCES [] X. Zhou, S. Gandh, S. Sur, and H. Zheng, ebay n the Sky: Strategy- Proof Wrelss Spectrum Auctons, n Proc. ACM MobCom, August 25. [2] Y. Wu, B. Wang, K. J. R. Lu, and T. C. Clancy, A Scalable Colluson-Resstant Mult-Wnner Cogntve Spectrum Aucton Game, IEEE Trans. Comm., vol. 57, no. 2, pp , 29. [3] M. Garey and D. Johnson, Computers and Intractablty: A Gude to the Theory of NP-Completeness. W.H. Freeman and Company, 99. [4] I. Kash, R. Murty, and D. C. Parkes, Enablng Spectrum Sharng n Secondary Market Auctons, n Proc. NetEcon, June 2. [5] A. Gopnathan, Z. L, and C. Wu, Strategyproof Auctons for Balancng Socal Welfare and Farness n Secondary Spectrum Markets, n Proc. IEEE INFOCOM, Aprl 2, pp [6] R. Myerson, Optmal Aucton Desgn, Mathematcs of Operatons Research, vol. 6, no., pp , 98. [7] R. Lav and C. Swamy, Truthful and Near-Optmal Mechansm Desgn va Lnear Programmng, n Proc. IEEE FOCS, October 25. [8] E. H. Clarke, Multpart Prcng of Publc Goo, Publc Choce, vol., pp. 7 33, 97. [9] T. Groves, Incentves n Teams, Econometrca: Journal of the Econometrc Socety, pp , 973. [] W. Vckrey, Counterspeculaton, Auctons, and Compettve Sealed Tenders, Journal of Fnance, pp. 8 37, 96. [] J. Huang, R. A. Berry, and M. L. Hong, Aucton Mechansms for Dstrbuted Spectrum Sharng, n Proc. Allerton, September 24. [2] M. M. Buddhkot and K. Ryan, Spectrum Management n Coordnated Dynamc Spectrum Access Based Cellular Networks, n Proc. IEEE DySPAN, November 25, pp [3] X. Zhou and H. Zheng, TRUST: A General Framework for Truthful Double Spectrum Auctons, n Proc. IEEE INFOCOM 29, Aprl 29. [4] J. Ja, Q. Zhang, Q. Zhang, and M. Lu, Revenue Generaton for Truthful Spectrum Aucton n Dynamc Spectrum Access, n Proc. ACM MobHoc, May 29, pp [5] M. Alcherry, R. Bhata, and L. L, Jont Channel Assgnment and Routng for Throughput Optmzaton n Mult-rado Wreless Mesh Networks, n Proc. ACM MobCom, August 25, pp [6] G. B. Dantzg and M. N. Thapa, Lnear Programmng 2: Theory and Extensons. Sprnger, 23.
Vickrey Auction VCG Combinatorial Auctions. Mechanism Design. Algorithms and Data Structures. Winter 2016
 Mechansm Desgn Algorthms and Data Structures Wnter 2016 1 / 39 Vckrey Aucton Vckrey-Clarke-Groves Mechansms Sngle-Mnded Combnatoral Auctons 2 / 39 Mechansm Desgn (wth Money) Set A of outcomes to choose
Mechansm Desgn Algorthms and Data Structures Wnter 2016 1 / 39 Vckrey Aucton Vckrey-Clarke-Groves Mechansms Sngle-Mnded Combnatoral Auctons 2 / 39 Mechansm Desgn (wth Money) Set A of outcomes to choose
Assortment Optimization under MNL
 Assortment Optmzaton under MNL Haotan Song Aprl 30, 2017 1 Introducton The assortment optmzaton problem ams to fnd the revenue-maxmzng assortment of products to offer when the prces of products are fxed.
Assortment Optmzaton under MNL Haotan Song Aprl 30, 2017 1 Introducton The assortment optmzaton problem ams to fnd the revenue-maxmzng assortment of products to offer when the prces of products are fxed.
Resource Allocation with a Budget Constraint for Computing Independent Tasks in the Cloud
 Resource Allocaton wth a Budget Constrant for Computng Independent Tasks n the Cloud Wemng Sh and Bo Hong School of Electrcal and Computer Engneerng Georga Insttute of Technology, USA 2nd IEEE Internatonal
Resource Allocaton wth a Budget Constrant for Computng Independent Tasks n the Cloud Wemng Sh and Bo Hong School of Electrcal and Computer Engneerng Georga Insttute of Technology, USA 2nd IEEE Internatonal
Problem Set 9 Solutions
 Desgn and Analyss of Algorthms May 4, 2015 Massachusetts Insttute of Technology 6.046J/18.410J Profs. Erk Demane, Srn Devadas, and Nancy Lynch Problem Set 9 Solutons Problem Set 9 Solutons Ths problem
Desgn and Analyss of Algorthms May 4, 2015 Massachusetts Insttute of Technology 6.046J/18.410J Profs. Erk Demane, Srn Devadas, and Nancy Lynch Problem Set 9 Solutons Problem Set 9 Solutons Ths problem
princeton univ. F 17 cos 521: Advanced Algorithm Design Lecture 7: LP Duality Lecturer: Matt Weinberg
 prnceton unv. F 17 cos 521: Advanced Algorthm Desgn Lecture 7: LP Dualty Lecturer: Matt Wenberg Scrbe: LP Dualty s an extremely useful tool for analyzng structural propertes of lnear programs. Whle there
prnceton unv. F 17 cos 521: Advanced Algorthm Desgn Lecture 7: LP Dualty Lecturer: Matt Wenberg Scrbe: LP Dualty s an extremely useful tool for analyzng structural propertes of lnear programs. Whle there
College of Computer & Information Science Fall 2009 Northeastern University 20 October 2009
 College of Computer & Informaton Scence Fall 2009 Northeastern Unversty 20 October 2009 CS7880: Algorthmc Power Tools Scrbe: Jan Wen and Laura Poplawsk Lecture Outlne: Prmal-dual schema Network Desgn:
College of Computer & Informaton Scence Fall 2009 Northeastern Unversty 20 October 2009 CS7880: Algorthmc Power Tools Scrbe: Jan Wen and Laura Poplawsk Lecture Outlne: Prmal-dual schema Network Desgn:
COS 521: Advanced Algorithms Game Theory and Linear Programming
 COS 521: Advanced Algorthms Game Theory and Lnear Programmng Moses Charkar February 27, 2013 In these notes, we ntroduce some basc concepts n game theory and lnear programmng (LP). We show a connecton
COS 521: Advanced Algorthms Game Theory and Lnear Programmng Moses Charkar February 27, 2013 In these notes, we ntroduce some basc concepts n game theory and lnear programmng (LP). We show a connecton
On the Multicriteria Integer Network Flow Problem
 BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 5, No 2 Sofa 2005 On the Multcrtera Integer Network Flow Problem Vassl Vasslev, Marana Nkolova, Maryana Vassleva Insttute of
BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 5, No 2 Sofa 2005 On the Multcrtera Integer Network Flow Problem Vassl Vasslev, Marana Nkolova, Maryana Vassleva Insttute of
The Minimum Universal Cost Flow in an Infeasible Flow Network
 Journal of Scences, Islamc Republc of Iran 17(2): 175-180 (2006) Unversty of Tehran, ISSN 1016-1104 http://jscencesutacr The Mnmum Unversal Cost Flow n an Infeasble Flow Network H Saleh Fathabad * M Bagheran
Journal of Scences, Islamc Republc of Iran 17(2): 175-180 (2006) Unversty of Tehran, ISSN 1016-1104 http://jscencesutacr The Mnmum Unversal Cost Flow n an Infeasble Flow Network H Saleh Fathabad * M Bagheran
ECE559VV Project Report
 ECE559VV Project Report (Supplementary Notes Loc Xuan Bu I. MAX SUM-RATE SCHEDULING: THE UPLINK CASE We have seen (n the presentaton that, for downlnk (broadcast channels, the strategy maxmzng the sum-rate
ECE559VV Project Report (Supplementary Notes Loc Xuan Bu I. MAX SUM-RATE SCHEDULING: THE UPLINK CASE We have seen (n the presentaton that, for downlnk (broadcast channels, the strategy maxmzng the sum-rate
2E Pattern Recognition Solutions to Introduction to Pattern Recognition, Chapter 2: Bayesian pattern classification
 E395 - Pattern Recognton Solutons to Introducton to Pattern Recognton, Chapter : Bayesan pattern classfcaton Preface Ths document s a soluton manual for selected exercses from Introducton to Pattern Recognton
E395 - Pattern Recognton Solutons to Introducton to Pattern Recognton, Chapter : Bayesan pattern classfcaton Preface Ths document s a soluton manual for selected exercses from Introducton to Pattern Recognton
Kernel Methods and SVMs Extension
 Kernel Methods and SVMs Extenson The purpose of ths document s to revew materal covered n Machne Learnng 1 Supervsed Learnng regardng support vector machnes (SVMs). Ths document also provdes a general
Kernel Methods and SVMs Extenson The purpose of ths document s to revew materal covered n Machne Learnng 1 Supervsed Learnng regardng support vector machnes (SVMs). Ths document also provdes a general
U.C. Berkeley CS294: Beyond Worst-Case Analysis Luca Trevisan September 5, 2017
 U.C. Berkeley CS94: Beyond Worst-Case Analyss Handout 4s Luca Trevsan September 5, 07 Summary of Lecture 4 In whch we ntroduce semdefnte programmng and apply t to Max Cut. Semdefnte Programmng Recall that
U.C. Berkeley CS94: Beyond Worst-Case Analyss Handout 4s Luca Trevsan September 5, 07 Summary of Lecture 4 In whch we ntroduce semdefnte programmng and apply t to Max Cut. Semdefnte Programmng Recall that
Real-Time Systems. Multiprocessor scheduling. Multiprocessor scheduling. Multiprocessor scheduling
 Real-Tme Systems Multprocessor schedulng Specfcaton Implementaton Verfcaton Multprocessor schedulng -- -- Global schedulng How are tasks assgned to processors? Statc assgnment The processor(s) used for
Real-Tme Systems Multprocessor schedulng Specfcaton Implementaton Verfcaton Multprocessor schedulng -- -- Global schedulng How are tasks assgned to processors? Statc assgnment The processor(s) used for
Pricing and Resource Allocation Game Theoretic Models
 Prcng and Resource Allocaton Game Theoretc Models Zhy Huang Changbn Lu Q Zhang Computer and Informaton Scence December 8, 2009 Z. Huang, C. Lu, and Q. Zhang (CIS) Game Theoretc Models December 8, 2009
Prcng and Resource Allocaton Game Theoretc Models Zhy Huang Changbn Lu Q Zhang Computer and Informaton Scence December 8, 2009 Z. Huang, C. Lu, and Q. Zhang (CIS) Game Theoretc Models December 8, 2009
Computing Correlated Equilibria in Multi-Player Games
 Computng Correlated Equlbra n Mult-Player Games Chrstos H. Papadmtrou Presented by Zhanxang Huang December 7th, 2005 1 The Author Dr. Chrstos H. Papadmtrou CS professor at UC Berkley (taught at Harvard,
Computng Correlated Equlbra n Mult-Player Games Chrstos H. Papadmtrou Presented by Zhanxang Huang December 7th, 2005 1 The Author Dr. Chrstos H. Papadmtrou CS professor at UC Berkley (taught at Harvard,
Edge Isoperimetric Inequalities
 November 7, 2005 Ross M. Rchardson Edge Isopermetrc Inequaltes 1 Four Questons Recall that n the last lecture we looked at the problem of sopermetrc nequaltes n the hypercube, Q n. Our noton of boundary
November 7, 2005 Ross M. Rchardson Edge Isopermetrc Inequaltes 1 Four Questons Recall that n the last lecture we looked at the problem of sopermetrc nequaltes n the hypercube, Q n. Our noton of boundary
Winter 2008 CS567 Stochastic Linear/Integer Programming Guest Lecturer: Xu, Huan
 Wnter 2008 CS567 Stochastc Lnear/Integer Programmng Guest Lecturer: Xu, Huan Class 2: More Modelng Examples 1 Capacty Expanson Capacty expanson models optmal choces of the tmng and levels of nvestments
Wnter 2008 CS567 Stochastc Lnear/Integer Programmng Guest Lecturer: Xu, Huan Class 2: More Modelng Examples 1 Capacty Expanson Capacty expanson models optmal choces of the tmng and levels of nvestments
NP-Completeness : Proofs
 NP-Completeness : Proofs Proof Methods A method to show a decson problem Π NP-complete s as follows. (1) Show Π NP. (2) Choose an NP-complete problem Π. (3) Show Π Π. A method to show an optmzaton problem
NP-Completeness : Proofs Proof Methods A method to show a decson problem Π NP-complete s as follows. (1) Show Π NP. (2) Choose an NP-complete problem Π. (3) Show Π Π. A method to show an optmzaton problem
CS : Algorithms and Uncertainty Lecture 17 Date: October 26, 2016
 CS 29-128: Algorthms and Uncertanty Lecture 17 Date: October 26, 2016 Instructor: Nkhl Bansal Scrbe: Mchael Denns 1 Introducton In ths lecture we wll be lookng nto the secretary problem, and an nterestng
CS 29-128: Algorthms and Uncertanty Lecture 17 Date: October 26, 2016 Instructor: Nkhl Bansal Scrbe: Mchael Denns 1 Introducton In ths lecture we wll be lookng nto the secretary problem, and an nterestng
Simultaneous Optimization of Berth Allocation, Quay Crane Assignment and Quay Crane Scheduling Problems in Container Terminals
 Smultaneous Optmzaton of Berth Allocaton, Quay Crane Assgnment and Quay Crane Schedulng Problems n Contaner Termnals Necat Aras, Yavuz Türkoğulları, Z. Caner Taşkın, Kuban Altınel Abstract In ths work,
Smultaneous Optmzaton of Berth Allocaton, Quay Crane Assgnment and Quay Crane Schedulng Problems n Contaner Termnals Necat Aras, Yavuz Türkoğulları, Z. Caner Taşkın, Kuban Altınel Abstract In ths work,
Stanford University CS359G: Graph Partitioning and Expanders Handout 4 Luca Trevisan January 13, 2011
 Stanford Unversty CS359G: Graph Parttonng and Expanders Handout 4 Luca Trevsan January 3, 0 Lecture 4 In whch we prove the dffcult drecton of Cheeger s nequalty. As n the past lectures, consder an undrected
Stanford Unversty CS359G: Graph Parttonng and Expanders Handout 4 Luca Trevsan January 3, 0 Lecture 4 In whch we prove the dffcult drecton of Cheeger s nequalty. As n the past lectures, consder an undrected
Solutions to exam in SF1811 Optimization, Jan 14, 2015
 Solutons to exam n SF8 Optmzaton, Jan 4, 25 3 3 O------O -4 \ / \ / The network: \/ where all lnks go from left to rght. /\ / \ / \ 6 O------O -5 2 4.(a) Let x = ( x 3, x 4, x 23, x 24 ) T, where the varable
Solutons to exam n SF8 Optmzaton, Jan 4, 25 3 3 O------O -4 \ / \ / The network: \/ where all lnks go from left to rght. /\ / \ / \ 6 O------O -5 2 4.(a) Let x = ( x 3, x 4, x 23, x 24 ) T, where the varable
Structure and Drive Paul A. Jensen Copyright July 20, 2003
 Structure and Drve Paul A. Jensen Copyrght July 20, 2003 A system s made up of several operatons wth flow passng between them. The structure of the system descrbes the flow paths from nputs to outputs.
Structure and Drve Paul A. Jensen Copyrght July 20, 2003 A system s made up of several operatons wth flow passng between them. The structure of the system descrbes the flow paths from nputs to outputs.
Annexes. EC.1. Cycle-base move illustration. EC.2. Problem Instances
 ec Annexes Ths Annex frst llustrates a cycle-based move n the dynamc-block generaton tabu search. It then dsplays the characterstcs of the nstance sets, followed by detaled results of the parametercalbraton
ec Annexes Ths Annex frst llustrates a cycle-based move n the dynamc-block generaton tabu search. It then dsplays the characterstcs of the nstance sets, followed by detaled results of the parametercalbraton
Economics 101. Lecture 4 - Equilibrium and Efficiency
 Economcs 0 Lecture 4 - Equlbrum and Effcency Intro As dscussed n the prevous lecture, we wll now move from an envronment where we looed at consumers mang decsons n solaton to analyzng economes full of
Economcs 0 Lecture 4 - Equlbrum and Effcency Intro As dscussed n the prevous lecture, we wll now move from an envronment where we looed at consumers mang decsons n solaton to analyzng economes full of
Calculation of time complexity (3%)
 Problem 1. (30%) Calculaton of tme complexty (3%) Gven n ctes, usng exhaust search to see every result takes O(n!). Calculaton of tme needed to solve the problem (2%) 40 ctes:40! dfferent tours 40 add
Problem 1. (30%) Calculaton of tme complexty (3%) Gven n ctes, usng exhaust search to see every result takes O(n!). Calculaton of tme needed to solve the problem (2%) 40 ctes:40! dfferent tours 40 add
An Interactive Optimisation Tool for Allocation Problems
 An Interactve Optmsaton ool for Allocaton Problems Fredr Bonäs, Joam Westerlund and apo Westerlund Process Desgn Laboratory, Faculty of echnology, Åbo Aadem Unversty, uru 20500, Fnland hs paper presents
An Interactve Optmsaton ool for Allocaton Problems Fredr Bonäs, Joam Westerlund and apo Westerlund Process Desgn Laboratory, Faculty of echnology, Åbo Aadem Unversty, uru 20500, Fnland hs paper presents
Solutions HW #2. minimize. Ax = b. Give the dual problem, and make the implicit equality constraints explicit. Solution.
 Solutons HW #2 Dual of general LP. Fnd the dual functon of the LP mnmze subject to c T x Gx h Ax = b. Gve the dual problem, and make the mplct equalty constrants explct. Soluton. 1. The Lagrangan s L(x,
Solutons HW #2 Dual of general LP. Fnd the dual functon of the LP mnmze subject to c T x Gx h Ax = b. Gve the dual problem, and make the mplct equalty constrants explct. Soluton. 1. The Lagrangan s L(x,
An Admission Control Algorithm in Cloud Computing Systems
 An Admsson Control Algorthm n Cloud Computng Systems Authors: Frank Yeong-Sung Ln Department of Informaton Management Natonal Tawan Unversty Tape, Tawan, R.O.C. ysln@m.ntu.edu.tw Yngje Lan Management Scence
An Admsson Control Algorthm n Cloud Computng Systems Authors: Frank Yeong-Sung Ln Department of Informaton Management Natonal Tawan Unversty Tape, Tawan, R.O.C. ysln@m.ntu.edu.tw Yngje Lan Management Scence
Notes on Frequency Estimation in Data Streams
 Notes on Frequency Estmaton n Data Streams In (one of) the data streamng model(s), the data s a sequence of arrvals a 1, a 2,..., a m of the form a j = (, v) where s the dentty of the tem and belongs to
Notes on Frequency Estmaton n Data Streams In (one of) the data streamng model(s), the data s a sequence of arrvals a 1, a 2,..., a m of the form a j = (, v) where s the dentty of the tem and belongs to
Module 9. Lecture 6. Duality in Assignment Problems
 Module 9 1 Lecture 6 Dualty n Assgnment Problems In ths lecture we attempt to answer few other mportant questons posed n earler lecture for (AP) and see how some of them can be explaned through the concept
Module 9 1 Lecture 6 Dualty n Assgnment Problems In ths lecture we attempt to answer few other mportant questons posed n earler lecture for (AP) and see how some of them can be explaned through the concept
3.1 Expectation of Functions of Several Random Variables. )' be a k-dimensional discrete or continuous random vector, with joint PMF p (, E X E X1 E X
 Statstcs 1: Probablty Theory II 37 3 EPECTATION OF SEVERAL RANDOM VARIABLES As n Probablty Theory I, the nterest n most stuatons les not on the actual dstrbuton of a random vector, but rather on a number
Statstcs 1: Probablty Theory II 37 3 EPECTATION OF SEVERAL RANDOM VARIABLES As n Probablty Theory I, the nterest n most stuatons les not on the actual dstrbuton of a random vector, but rather on a number
The Second Anti-Mathima on Game Theory
 The Second Ant-Mathma on Game Theory Ath. Kehagas December 1 2006 1 Introducton In ths note we wll examne the noton of game equlbrum for three types of games 1. 2-player 2-acton zero-sum games 2. 2-player
The Second Ant-Mathma on Game Theory Ath. Kehagas December 1 2006 1 Introducton In ths note we wll examne the noton of game equlbrum for three types of games 1. 2-player 2-acton zero-sum games 2. 2-player
Queueing Networks II Network Performance
 Queueng Networks II Network Performance Davd Tpper Assocate Professor Graduate Telecommuncatons and Networkng Program Unversty of Pttsburgh Sldes 6 Networks of Queues Many communcaton systems must be modeled
Queueng Networks II Network Performance Davd Tpper Assocate Professor Graduate Telecommuncatons and Networkng Program Unversty of Pttsburgh Sldes 6 Networks of Queues Many communcaton systems must be modeled
Lecture Notes on Linear Regression
 Lecture Notes on Lnear Regresson Feng L fl@sdueducn Shandong Unversty, Chna Lnear Regresson Problem In regresson problem, we am at predct a contnuous target value gven an nput feature vector We assume
Lecture Notes on Lnear Regresson Feng L fl@sdueducn Shandong Unversty, Chna Lnear Regresson Problem In regresson problem, we am at predct a contnuous target value gven an nput feature vector We assume
Lecture 14: Bandits with Budget Constraints
 IEOR 8100-001: Learnng and Optmzaton for Sequental Decson Makng 03/07/16 Lecture 14: andts wth udget Constrants Instructor: Shpra Agrawal Scrbed by: Zhpeng Lu 1 Problem defnton In the regular Mult-armed
IEOR 8100-001: Learnng and Optmzaton for Sequental Decson Makng 03/07/16 Lecture 14: andts wth udget Constrants Instructor: Shpra Agrawal Scrbed by: Zhpeng Lu 1 Problem defnton In the regular Mult-armed
Chapter 5. Solution of System of Linear Equations. Module No. 6. Solution of Inconsistent and Ill Conditioned Systems
 Numercal Analyss by Dr. Anta Pal Assstant Professor Department of Mathematcs Natonal Insttute of Technology Durgapur Durgapur-713209 emal: anta.bue@gmal.com 1 . Chapter 5 Soluton of System of Lnear Equatons
Numercal Analyss by Dr. Anta Pal Assstant Professor Department of Mathematcs Natonal Insttute of Technology Durgapur Durgapur-713209 emal: anta.bue@gmal.com 1 . Chapter 5 Soluton of System of Lnear Equatons
For now, let us focus on a specific model of neurons. These are simplified from reality but can achieve remarkable results.
 Neural Networks : Dervaton compled by Alvn Wan from Professor Jtendra Malk s lecture Ths type of computaton s called deep learnng and s the most popular method for many problems, such as computer vson
Neural Networks : Dervaton compled by Alvn Wan from Professor Jtendra Malk s lecture Ths type of computaton s called deep learnng and s the most popular method for many problems, such as computer vson
A Distributed Spectrum Sharing Algorithm in Cognitive Radio Networks
 A Dstrbuted Spectrum Sharng Algorthm n Cogntve Rado Networks We Sun, Tong Lu, Yanmn Zhu, Bo L Shangha Jao Tong Unversty Hong Kong Unversty of Scence and Technology Emal: {sunwt,lutong2569164,yzhu}@sjtu.edu.cn,
A Dstrbuted Spectrum Sharng Algorthm n Cogntve Rado Networks We Sun, Tong Lu, Yanmn Zhu, Bo L Shangha Jao Tong Unversty Hong Kong Unversty of Scence and Technology Emal: {sunwt,lutong2569164,yzhu}@sjtu.edu.cn,
Lecture Randomized Load Balancing strategies and their analysis. Probability concepts include, counting, the union bound, and Chernoff bounds.
 U.C. Berkeley CS273: Parallel and Dstrbuted Theory Lecture 1 Professor Satsh Rao August 26, 2010 Lecturer: Satsh Rao Last revsed September 2, 2010 Lecture 1 1 Course Outlne We wll cover a samplng of the
U.C. Berkeley CS273: Parallel and Dstrbuted Theory Lecture 1 Professor Satsh Rao August 26, 2010 Lecturer: Satsh Rao Last revsed September 2, 2010 Lecture 1 1 Course Outlne We wll cover a samplng of the
MMA and GCMMA two methods for nonlinear optimization
 MMA and GCMMA two methods for nonlnear optmzaton Krster Svanberg Optmzaton and Systems Theory, KTH, Stockholm, Sweden. krlle@math.kth.se Ths note descrbes the algorthms used n the author s 2007 mplementatons
MMA and GCMMA two methods for nonlnear optmzaton Krster Svanberg Optmzaton and Systems Theory, KTH, Stockholm, Sweden. krlle@math.kth.se Ths note descrbes the algorthms used n the author s 2007 mplementatons
Pricing Network Services by Jun Shu, Pravin Varaiya
 Prcng Network Servces by Jun Shu, Pravn Varaya Presented by Hayden So September 25, 2003 Introducton: Two Network Problems Engneerng: A game theoretcal sound congeston control mechansm that s ncentve compatble
Prcng Network Servces by Jun Shu, Pravn Varaya Presented by Hayden So September 25, 2003 Introducton: Two Network Problems Engneerng: A game theoretcal sound congeston control mechansm that s ncentve compatble
Appendix B: Resampling Algorithms
 407 Appendx B: Resamplng Algorthms A common problem of all partcle flters s the degeneracy of weghts, whch conssts of the unbounded ncrease of the varance of the mportance weghts ω [ ] of the partcles
407 Appendx B: Resamplng Algorthms A common problem of all partcle flters s the degeneracy of weghts, whch conssts of the unbounded ncrease of the varance of the mportance weghts ω [ ] of the partcles
Interactive Bi-Level Multi-Objective Integer. Non-linear Programming Problem
 Appled Mathematcal Scences Vol 5 0 no 65 3 33 Interactve B-Level Mult-Objectve Integer Non-lnear Programmng Problem O E Emam Department of Informaton Systems aculty of Computer Scence and nformaton Helwan
Appled Mathematcal Scences Vol 5 0 no 65 3 33 Interactve B-Level Mult-Objectve Integer Non-lnear Programmng Problem O E Emam Department of Informaton Systems aculty of Computer Scence and nformaton Helwan
4 Analysis of Variance (ANOVA) 5 ANOVA. 5.1 Introduction. 5.2 Fixed Effects ANOVA
 4 Analyss of Varance (ANOVA) 5 ANOVA 51 Introducton ANOVA ANOVA s a way to estmate and test the means of multple populatons We wll start wth one-way ANOVA If the populatons ncluded n the study are selected
4 Analyss of Varance (ANOVA) 5 ANOVA 51 Introducton ANOVA ANOVA s a way to estmate and test the means of multple populatons We wll start wth one-way ANOVA If the populatons ncluded n the study are selected
Lecture 20: Lift and Project, SDP Duality. Today we will study the Lift and Project method. Then we will prove the SDP duality theorem.
 prnceton u. sp 02 cos 598B: algorthms and complexty Lecture 20: Lft and Project, SDP Dualty Lecturer: Sanjeev Arora Scrbe:Yury Makarychev Today we wll study the Lft and Project method. Then we wll prove
prnceton u. sp 02 cos 598B: algorthms and complexty Lecture 20: Lft and Project, SDP Dualty Lecturer: Sanjeev Arora Scrbe:Yury Makarychev Today we wll study the Lft and Project method. Then we wll prove
U.C. Berkeley CS294: Spectral Methods and Expanders Handout 8 Luca Trevisan February 17, 2016
 U.C. Berkeley CS94: Spectral Methods and Expanders Handout 8 Luca Trevsan February 7, 06 Lecture 8: Spectral Algorthms Wrap-up In whch we talk about even more generalzatons of Cheeger s nequaltes, and
U.C. Berkeley CS94: Spectral Methods and Expanders Handout 8 Luca Trevsan February 7, 06 Lecture 8: Spectral Algorthms Wrap-up In whch we talk about even more generalzatons of Cheeger s nequaltes, and
FUZZY GOAL PROGRAMMING VS ORDINARY FUZZY PROGRAMMING APPROACH FOR MULTI OBJECTIVE PROGRAMMING PROBLEM
 Internatonal Conference on Ceramcs, Bkaner, Inda Internatonal Journal of Modern Physcs: Conference Seres Vol. 22 (2013) 757 761 World Scentfc Publshng Company DOI: 10.1142/S2010194513010982 FUZZY GOAL
Internatonal Conference on Ceramcs, Bkaner, Inda Internatonal Journal of Modern Physcs: Conference Seres Vol. 22 (2013) 757 761 World Scentfc Publshng Company DOI: 10.1142/S2010194513010982 FUZZY GOAL
Min Cut, Fast Cut, Polynomial Identities
 Randomzed Algorthms, Summer 016 Mn Cut, Fast Cut, Polynomal Identtes Instructor: Thomas Kesselhem and Kurt Mehlhorn 1 Mn Cuts n Graphs Lecture (5 pages) Throughout ths secton, G = (V, E) s a mult-graph.
Randomzed Algorthms, Summer 016 Mn Cut, Fast Cut, Polynomal Identtes Instructor: Thomas Kesselhem and Kurt Mehlhorn 1 Mn Cuts n Graphs Lecture (5 pages) Throughout ths secton, G = (V, E) s a mult-graph.
Maximizing the number of nonnegative subsets
 Maxmzng the number of nonnegatve subsets Noga Alon Hao Huang December 1, 213 Abstract Gven a set of n real numbers, f the sum of elements of every subset of sze larger than k s negatve, what s the maxmum
Maxmzng the number of nonnegatve subsets Noga Alon Hao Huang December 1, 213 Abstract Gven a set of n real numbers, f the sum of elements of every subset of sze larger than k s negatve, what s the maxmum
Generalized Linear Methods
 Generalzed Lnear Methods 1 Introducton In the Ensemble Methods the general dea s that usng a combnaton of several weak learner one could make a better learner. More formally, assume that we have a set
Generalzed Lnear Methods 1 Introducton In the Ensemble Methods the general dea s that usng a combnaton of several weak learner one could make a better learner. More formally, assume that we have a set
DUE: WEDS FEB 21ST 2018
 HOMEWORK # 1: FINITE DIFFERENCES IN ONE DIMENSION DUE: WEDS FEB 21ST 2018 1. Theory Beam bendng s a classcal engneerng analyss. The tradtonal soluton technque makes smplfyng assumptons such as a constant
HOMEWORK # 1: FINITE DIFFERENCES IN ONE DIMENSION DUE: WEDS FEB 21ST 2018 1. Theory Beam bendng s a classcal engneerng analyss. The tradtonal soluton technque makes smplfyng assumptons such as a constant
Single-Facility Scheduling over Long Time Horizons by Logic-based Benders Decomposition
 Sngle-Faclty Schedulng over Long Tme Horzons by Logc-based Benders Decomposton Elvn Coban and J. N. Hooker Tepper School of Busness, Carnege Mellon Unversty ecoban@andrew.cmu.edu, john@hooker.tepper.cmu.edu
Sngle-Faclty Schedulng over Long Tme Horzons by Logc-based Benders Decomposton Elvn Coban and J. N. Hooker Tepper School of Busness, Carnege Mellon Unversty ecoban@andrew.cmu.edu, john@hooker.tepper.cmu.edu
Module 3 LOSSY IMAGE COMPRESSION SYSTEMS. Version 2 ECE IIT, Kharagpur
 Module 3 LOSSY IMAGE COMPRESSION SYSTEMS Verson ECE IIT, Kharagpur Lesson 6 Theory of Quantzaton Verson ECE IIT, Kharagpur Instructonal Objectves At the end of ths lesson, the students should be able to:
Module 3 LOSSY IMAGE COMPRESSION SYSTEMS Verson ECE IIT, Kharagpur Lesson 6 Theory of Quantzaton Verson ECE IIT, Kharagpur Instructonal Objectves At the end of ths lesson, the students should be able to:
Lecture 10 Support Vector Machines II
 Lecture 10 Support Vector Machnes II 22 February 2016 Taylor B. Arnold Yale Statstcs STAT 365/665 1/28 Notes: Problem 3 s posted and due ths upcomng Frday There was an early bug n the fake-test data; fxed
Lecture 10 Support Vector Machnes II 22 February 2016 Taylor B. Arnold Yale Statstcs STAT 365/665 1/28 Notes: Problem 3 s posted and due ths upcomng Frday There was an early bug n the fake-test data; fxed
Case A. P k = Ni ( 2L i k 1 ) + (# big cells) 10d 2 P k.
 THE CELLULAR METHOD In ths lecture, we ntroduce the cellular method as an approach to ncdence geometry theorems lke the Szemeréd-Trotter theorem. The method was ntroduced n the paper Combnatoral complexty
THE CELLULAR METHOD In ths lecture, we ntroduce the cellular method as an approach to ncdence geometry theorems lke the Szemeréd-Trotter theorem. The method was ntroduced n the paper Combnatoral complexty
Spectral Graph Theory and its Applications September 16, Lecture 5
 Spectral Graph Theory and ts Applcatons September 16, 2004 Lecturer: Danel A. Spelman Lecture 5 5.1 Introducton In ths lecture, we wll prove the followng theorem: Theorem 5.1.1. Let G be a planar graph
Spectral Graph Theory and ts Applcatons September 16, 2004 Lecturer: Danel A. Spelman Lecture 5 5.1 Introducton In ths lecture, we wll prove the followng theorem: Theorem 5.1.1. Let G be a planar graph
HMMT February 2016 February 20, 2016
 HMMT February 016 February 0, 016 Combnatorcs 1. For postve ntegers n, let S n be the set of ntegers x such that n dstnct lnes, no three concurrent, can dvde a plane nto x regons (for example, S = {3,
HMMT February 016 February 0, 016 Combnatorcs 1. For postve ntegers n, let S n be the set of ntegers x such that n dstnct lnes, no three concurrent, can dvde a plane nto x regons (for example, S = {3,
P R. Lecture 4. Theory and Applications of Pattern Recognition. Dept. of Electrical and Computer Engineering /
 Theory and Applcatons of Pattern Recognton 003, Rob Polkar, Rowan Unversty, Glassboro, NJ Lecture 4 Bayes Classfcaton Rule Dept. of Electrcal and Computer Engneerng 0909.40.0 / 0909.504.04 Theory & Applcatons
Theory and Applcatons of Pattern Recognton 003, Rob Polkar, Rowan Unversty, Glassboro, NJ Lecture 4 Bayes Classfcaton Rule Dept. of Electrcal and Computer Engneerng 0909.40.0 / 0909.504.04 Theory & Applcatons
Linear Approximation with Regularization and Moving Least Squares
 Lnear Approxmaton wth Regularzaton and Movng Least Squares Igor Grešovn May 007 Revson 4.6 (Revson : March 004). 5 4 3 0.5 3 3.5 4 Contents: Lnear Fttng...4. Weghted Least Squares n Functon Approxmaton...
Lnear Approxmaton wth Regularzaton and Movng Least Squares Igor Grešovn May 007 Revson 4.6 (Revson : March 004). 5 4 3 0.5 3 3.5 4 Contents: Lnear Fttng...4. Weghted Least Squares n Functon Approxmaton...
CIE4801 Transportation and spatial modelling Trip distribution
 CIE4801 ransportaton and spatal modellng rp dstrbuton Rob van Nes, ransport & Plannng 17/4/13 Delft Unversty of echnology Challenge the future Content What s t about hree methods Wth specal attenton for
CIE4801 ransportaton and spatal modellng rp dstrbuton Rob van Nes, ransport & Plannng 17/4/13 Delft Unversty of echnology Challenge the future Content What s t about hree methods Wth specal attenton for
Finding Dense Subgraphs in G(n, 1/2)
 Fndng Dense Subgraphs n Gn, 1/ Atsh Das Sarma 1, Amt Deshpande, and Rav Kannan 1 Georga Insttute of Technology,atsh@cc.gatech.edu Mcrosoft Research-Bangalore,amtdesh,annan@mcrosoft.com Abstract. Fndng
Fndng Dense Subgraphs n Gn, 1/ Atsh Das Sarma 1, Amt Deshpande, and Rav Kannan 1 Georga Insttute of Technology,atsh@cc.gatech.edu Mcrosoft Research-Bangalore,amtdesh,annan@mcrosoft.com Abstract. Fndng
Technical Note: Capacity Constraints Across Nests in Assortment Optimization Under the Nested Logit Model
 Techncal Note: Capacty Constrants Across Nests n Assortment Optmzaton Under the Nested Logt Model Jacob B. Feldman, Huseyn Topaloglu School of Operatons Research and Informaton Engneerng, Cornell Unversty,
Techncal Note: Capacty Constrants Across Nests n Assortment Optmzaton Under the Nested Logt Model Jacob B. Feldman, Huseyn Topaloglu School of Operatons Research and Informaton Engneerng, Cornell Unversty,
COMPARISON OF SOME RELIABILITY CHARACTERISTICS BETWEEN REDUNDANT SYSTEMS REQUIRING SUPPORTING UNITS FOR THEIR OPERATIONS
 Avalable onlne at http://sck.org J. Math. Comput. Sc. 3 (3), No., 6-3 ISSN: 97-537 COMPARISON OF SOME RELIABILITY CHARACTERISTICS BETWEEN REDUNDANT SYSTEMS REQUIRING SUPPORTING UNITS FOR THEIR OPERATIONS
Avalable onlne at http://sck.org J. Math. Comput. Sc. 3 (3), No., 6-3 ISSN: 97-537 COMPARISON OF SOME RELIABILITY CHARACTERISTICS BETWEEN REDUNDANT SYSTEMS REQUIRING SUPPORTING UNITS FOR THEIR OPERATIONS
Section 8.3 Polar Form of Complex Numbers
 80 Chapter 8 Secton 8 Polar Form of Complex Numbers From prevous classes, you may have encountered magnary numbers the square roots of negatve numbers and, more generally, complex numbers whch are the
80 Chapter 8 Secton 8 Polar Form of Complex Numbers From prevous classes, you may have encountered magnary numbers the square roots of negatve numbers and, more generally, complex numbers whch are the
A 2D Bounded Linear Program (H,c) 2D Linear Programming
 A 2D Bounded Lnear Program (H,c) h 3 v h 8 h 5 c h 4 h h 6 h 7 h 2 2D Lnear Programmng C s a polygonal regon, the ntersecton of n halfplanes. (H, c) s nfeasble, as C s empty. Feasble regon C s unbounded
A 2D Bounded Lnear Program (H,c) h 3 v h 8 h 5 c h 4 h h 6 h 7 h 2 2D Lnear Programmng C s a polygonal regon, the ntersecton of n halfplanes. (H, c) s nfeasble, as C s empty. Feasble regon C s unbounded
(1 ) (1 ) 0 (1 ) (1 ) 0
 Appendx A Appendx A contans proofs for resubmsson "Contractng Informaton Securty n the Presence of Double oral Hazard" Proof of Lemma 1: Assume that, to the contrary, BS efforts are achevable under a blateral
Appendx A Appendx A contans proofs for resubmsson "Contractng Informaton Securty n the Presence of Double oral Hazard" Proof of Lemma 1: Assume that, to the contrary, BS efforts are achevable under a blateral
TAHES: Truthful Double Auction for Heterogeneous Spectrums
 The 31st Annual IEEE Internatonal Conference on Computer Communcatons: Mn-Conference TAHES: Truthful Double Aucton for Heterogeneous Spectrums Xaojun Feng, Yanjao Chen, Jn Zhang, Qan Zhang, and Bo L Department
The 31st Annual IEEE Internatonal Conference on Computer Communcatons: Mn-Conference TAHES: Truthful Double Aucton for Heterogeneous Spectrums Xaojun Feng, Yanjao Chen, Jn Zhang, Qan Zhang, and Bo L Department
Amiri s Supply Chain Model. System Engineering b Department of Mathematics and Statistics c Odette School of Business
 Amr s Supply Chan Model by S. Ashtab a,, R.J. Caron b E. Selvarajah c a Department of Industral Manufacturng System Engneerng b Department of Mathematcs Statstcs c Odette School of Busness Unversty of
Amr s Supply Chan Model by S. Ashtab a,, R.J. Caron b E. Selvarajah c a Department of Industral Manufacturng System Engneerng b Department of Mathematcs Statstcs c Odette School of Busness Unversty of
Smooth Games, Price of Anarchy and Composability of Auctions - a Quick Tutorial
 Smooth Games, Prce of Anarchy and Composablty of Auctons - a Quck Tutoral Abhshek Snha Laboratory for Informaton and Decson Systems, Massachusetts Insttute of Technology, Cambrdge, MA 02139 Emal: snhaa@mt.edu
Smooth Games, Prce of Anarchy and Composablty of Auctons - a Quck Tutoral Abhshek Snha Laboratory for Informaton and Decson Systems, Massachusetts Insttute of Technology, Cambrdge, MA 02139 Emal: snhaa@mt.edu
A FAST HEURISTIC FOR TASKS ASSIGNMENT IN MANYCORE SYSTEMS WITH VOLTAGE-FREQUENCY ISLANDS
 Shervn Haamn A FAST HEURISTIC FOR TASKS ASSIGNMENT IN MANYCORE SYSTEMS WITH VOLTAGE-FREQUENCY ISLANDS INTRODUCTION Increasng computatons n applcatons has led to faster processng. o Use more cores n a chp
Shervn Haamn A FAST HEURISTIC FOR TASKS ASSIGNMENT IN MANYCORE SYSTEMS WITH VOLTAGE-FREQUENCY ISLANDS INTRODUCTION Increasng computatons n applcatons has led to faster processng. o Use more cores n a chp
An Upper Bound on SINR Threshold for Call Admission Control in Multiple-Class CDMA Systems with Imperfect Power-Control
 An Upper Bound on SINR Threshold for Call Admsson Control n Multple-Class CDMA Systems wth Imperfect ower-control Mahmoud El-Sayes MacDonald, Dettwler and Assocates td. (MDA) Toronto, Canada melsayes@hotmal.com
An Upper Bound on SINR Threshold for Call Admsson Control n Multple-Class CDMA Systems wth Imperfect ower-control Mahmoud El-Sayes MacDonald, Dettwler and Assocates td. (MDA) Toronto, Canada melsayes@hotmal.com
Analysis of Queuing Delay in Multimedia Gateway Call Routing
 Analyss of Queung Delay n Multmeda ateway Call Routng Qwe Huang UTtarcom Inc, 33 Wood Ave. outh Iseln, NJ 08830, U..A Errol Lloyd Computer Informaton cences Department, Unv. of Delaware, Newark, DE 976,
Analyss of Queung Delay n Multmeda ateway Call Routng Qwe Huang UTtarcom Inc, 33 Wood Ave. outh Iseln, NJ 08830, U..A Errol Lloyd Computer Informaton cences Department, Unv. of Delaware, Newark, DE 976,
APPENDIX A Some Linear Algebra
 APPENDIX A Some Lnear Algebra The collecton of m, n matrces A.1 Matrces a 1,1,..., a 1,n A = a m,1,..., a m,n wth real elements a,j s denoted by R m,n. If n = 1 then A s called a column vector. Smlarly,
APPENDIX A Some Lnear Algebra The collecton of m, n matrces A.1 Matrces a 1,1,..., a 1,n A = a m,1,..., a m,n wth real elements a,j s denoted by R m,n. If n = 1 then A s called a column vector. Smlarly,
CS286r Assign One. Answer Key
 CS286r Assgn One Answer Key 1 Game theory 1.1 1.1.1 Let off-equlbrum strateges also be that people contnue to play n Nash equlbrum. Devatng from any Nash equlbrum s a weakly domnated strategy. That s,
CS286r Assgn One Answer Key 1 Game theory 1.1 1.1.1 Let off-equlbrum strateges also be that people contnue to play n Nash equlbrum. Devatng from any Nash equlbrum s a weakly domnated strategy. That s,
Formulas for the Determinant
 page 224 224 CHAPTER 3 Determnants e t te t e 2t 38 A = e t 2te t e 2t e t te t 2e 2t 39 If 123 A = 345, 456 compute the matrx product A adj(a) What can you conclude about det(a)? For Problems 40 43, use
page 224 224 CHAPTER 3 Determnants e t te t e 2t 38 A = e t 2te t e 2t e t te t 2e 2t 39 If 123 A = 345, 456 compute the matrx product A adj(a) What can you conclude about det(a)? For Problems 40 43, use
Lecture 4: November 17, Part 1 Single Buffer Management
 Lecturer: Ad Rosén Algorthms for the anagement of Networs Fall 2003-2004 Lecture 4: November 7, 2003 Scrbe: Guy Grebla Part Sngle Buffer anagement In the prevous lecture we taled about the Combned Input
Lecturer: Ad Rosén Algorthms for the anagement of Networs Fall 2003-2004 Lecture 4: November 7, 2003 Scrbe: Guy Grebla Part Sngle Buffer anagement In the prevous lecture we taled about the Combned Input
Welfare Properties of General Equilibrium. What can be said about optimality properties of resource allocation implied by general equilibrium?
 APPLIED WELFARE ECONOMICS AND POLICY ANALYSIS Welfare Propertes of General Equlbrum What can be sad about optmalty propertes of resource allocaton mpled by general equlbrum? Any crteron used to compare
APPLIED WELFARE ECONOMICS AND POLICY ANALYSIS Welfare Propertes of General Equlbrum What can be sad about optmalty propertes of resource allocaton mpled by general equlbrum? Any crteron used to compare
Chapter - 2. Distribution System Power Flow Analysis
 Chapter - 2 Dstrbuton System Power Flow Analyss CHAPTER - 2 Radal Dstrbuton System Load Flow 2.1 Introducton Load flow s an mportant tool [66] for analyzng electrcal power system network performance. Load
Chapter - 2 Dstrbuton System Power Flow Analyss CHAPTER - 2 Radal Dstrbuton System Load Flow 2.1 Introducton Load flow s an mportant tool [66] for analyzng electrcal power system network performance. Load
Combining Constraint Programming and Integer Programming
 Combnng Constrant Programmng and Integer Programmng GLOBAL CONSTRAINT OPTIMIZATION COMPONENT Specal Purpose Algorthm mn c T x +(x- 0 ) x( + ()) =1 x( - ()) =1 FILTERING ALGORITHM COST-BASED FILTERING ALGORITHM
Combnng Constrant Programmng and Integer Programmng GLOBAL CONSTRAINT OPTIMIZATION COMPONENT Specal Purpose Algorthm mn c T x +(x- 0 ) x( + ()) =1 x( - ()) =1 FILTERING ALGORITHM COST-BASED FILTERING ALGORITHM
Lecture 4: Universal Hash Functions/Streaming Cont d
 CSE 5: Desgn and Analyss of Algorthms I Sprng 06 Lecture 4: Unversal Hash Functons/Streamng Cont d Lecturer: Shayan Oves Gharan Aprl 6th Scrbe: Jacob Schreber Dsclamer: These notes have not been subjected
CSE 5: Desgn and Analyss of Algorthms I Sprng 06 Lecture 4: Unversal Hash Functons/Streamng Cont d Lecturer: Shayan Oves Gharan Aprl 6th Scrbe: Jacob Schreber Dsclamer: These notes have not been subjected
Assortment Optimization under the Paired Combinatorial Logit Model
 Assortment Optmzaton under the Pared Combnatoral Logt Model Heng Zhang, Paat Rusmevchentong Marshall School of Busness, Unversty of Southern Calforna, Los Angeles, CA 90089 hengz@usc.edu, rusmevc@marshall.usc.edu
Assortment Optmzaton under the Pared Combnatoral Logt Model Heng Zhang, Paat Rusmevchentong Marshall School of Busness, Unversty of Southern Calforna, Los Angeles, CA 90089 hengz@usc.edu, rusmevc@marshall.usc.edu
Communication Complexity 16:198: February Lecture 4. x ij y ij
 Communcaton Complexty 16:198:671 09 February 2010 Lecture 4 Lecturer: Troy Lee Scrbe: Rajat Mttal 1 Homework problem : Trbes We wll solve the thrd queston n the homework. The goal s to show that the nondetermnstc
Communcaton Complexty 16:198:671 09 February 2010 Lecture 4 Lecturer: Troy Lee Scrbe: Rajat Mttal 1 Homework problem : Trbes We wll solve the thrd queston n the homework. The goal s to show that the nondetermnstc
The Order Relation and Trace Inequalities for. Hermitian Operators
 Internatonal Mathematcal Forum, Vol 3, 08, no, 507-57 HIKARI Ltd, wwwm-hkarcom https://doorg/0988/mf088055 The Order Relaton and Trace Inequaltes for Hermtan Operators Y Huang School of Informaton Scence
Internatonal Mathematcal Forum, Vol 3, 08, no, 507-57 HIKARI Ltd, wwwm-hkarcom https://doorg/0988/mf088055 The Order Relaton and Trace Inequaltes for Hermtan Operators Y Huang School of Informaton Scence
An Integrated OR/CP Method for Planning and Scheduling
 An Integrated OR/CP Method for Plannng and Schedulng John Hooer Carnege Mellon Unversty IT Unversty of Copenhagen June 2005 The Problem Allocate tass to facltes. Schedule tass assgned to each faclty. Subect
An Integrated OR/CP Method for Plannng and Schedulng John Hooer Carnege Mellon Unversty IT Unversty of Copenhagen June 2005 The Problem Allocate tass to facltes. Schedule tass assgned to each faclty. Subect
Revenue in Resource Allocation Games and Applications
 Revenue n Resource Allocaton Games and Applcatons by Thanh Ten Nguyen Ths thess/dssertaton document has been electroncally approved by the followng ndvduals: Tardos,Eva (Charperson) Kozen,Dexter Campbell
Revenue n Resource Allocaton Games and Applcatons by Thanh Ten Nguyen Ths thess/dssertaton document has been electroncally approved by the followng ndvduals: Tardos,Eva (Charperson) Kozen,Dexter Campbell
Module 17: Mechanism Design & Optimal Auctions
 Module 7: Mechansm Desgn & Optmal Auctons Informaton Economcs (Ec 55) George Georgads Examples: Auctons Blateral trade Producton and dstrbuton n socety General Setup N agents Each agent has prvate nformaton
Module 7: Mechansm Desgn & Optmal Auctons Informaton Economcs (Ec 55) George Georgads Examples: Auctons Blateral trade Producton and dstrbuton n socety General Setup N agents Each agent has prvate nformaton
Tornado and Luby Transform Codes. Ashish Khisti Presentation October 22, 2003
 Tornado and Luby Transform Codes Ashsh Khst 6.454 Presentaton October 22, 2003 Background: Erasure Channel Elas[956] studed the Erasure Channel β x x β β x 2 m x 2 k? Capacty of Noseless Erasure Channel
Tornado and Luby Transform Codes Ashsh Khst 6.454 Presentaton October 22, 2003 Background: Erasure Channel Elas[956] studed the Erasure Channel β x x β β x 2 m x 2 k? Capacty of Noseless Erasure Channel
Introduction to Algorithms
 Introducton to Algorthms 6.046J/8.40J Lecture 7 Prof. Potr Indyk Data Structures Role of data structures: Encapsulate data Support certan operatons (e.g., INSERT, DELETE, SEARCH) Our focus: effcency of
Introducton to Algorthms 6.046J/8.40J Lecture 7 Prof. Potr Indyk Data Structures Role of data structures: Encapsulate data Support certan operatons (e.g., INSERT, DELETE, SEARCH) Our focus: effcency of
Perfect Competition and the Nash Bargaining Solution
 Perfect Competton and the Nash Barganng Soluton Renhard John Department of Economcs Unversty of Bonn Adenauerallee 24-42 53113 Bonn, Germany emal: rohn@un-bonn.de May 2005 Abstract For a lnear exchange
Perfect Competton and the Nash Barganng Soluton Renhard John Department of Economcs Unversty of Bonn Adenauerallee 24-42 53113 Bonn, Germany emal: rohn@un-bonn.de May 2005 Abstract For a lnear exchange
Lecture 2: Gram-Schmidt Vectors and the LLL Algorithm
 NYU, Fall 2016 Lattces Mn Course Lecture 2: Gram-Schmdt Vectors and the LLL Algorthm Lecturer: Noah Stephens-Davdowtz 2.1 The Shortest Vector Problem In our last lecture, we consdered short solutons to
NYU, Fall 2016 Lattces Mn Course Lecture 2: Gram-Schmdt Vectors and the LLL Algorthm Lecturer: Noah Stephens-Davdowtz 2.1 The Shortest Vector Problem In our last lecture, we consdered short solutons to
Externalities in wireless communication: A public goods solution approach to power allocation. by Shrutivandana Sharma
 Externaltes n wreless communcaton: A publc goods soluton approach to power allocaton by Shrutvandana Sharma SI 786 Tuesday, Feb 2, 2006 Outlne Externaltes: Introducton Plannng wth externaltes Power allocaton:
Externaltes n wreless communcaton: A publc goods soluton approach to power allocaton by Shrutvandana Sharma SI 786 Tuesday, Feb 2, 2006 Outlne Externaltes: Introducton Plannng wth externaltes Power allocaton:
Revenue Maximization in a Spectrum Auction for Dynamic Spectrum Access
 Revenue Maxmzaton n a Spectrum Aucton for Dynamc Spectrum Access Al Kakhbod, Ashutosh Nayyar and Demosthens Teneketzs Department of Electrcal Engneerng and Computer Scence Unversty of Mchgan, Ann Arbor,
Revenue Maxmzaton n a Spectrum Aucton for Dynamc Spectrum Access Al Kakhbod, Ashutosh Nayyar and Demosthens Teneketzs Department of Electrcal Engneerng and Computer Scence Unversty of Mchgan, Ann Arbor,
More metrics on cartesian products
 More metrcs on cartesan products If (X, d ) are metrc spaces for 1 n, then n Secton II4 of the lecture notes we defned three metrcs on X whose underlyng topologes are the product topology The purpose of
More metrcs on cartesan products If (X, d ) are metrc spaces for 1 n, then n Secton II4 of the lecture notes we defned three metrcs on X whose underlyng topologes are the product topology The purpose of
find (x): given element x, return the canonical element of the set containing x;
 COS 43 Sprng, 009 Dsjont Set Unon Problem: Mantan a collecton of dsjont sets. Two operatons: fnd the set contanng a gven element; unte two sets nto one (destructvely). Approach: Canoncal element method:
COS 43 Sprng, 009 Dsjont Set Unon Problem: Mantan a collecton of dsjont sets. Two operatons: fnd the set contanng a gven element; unte two sets nto one (destructvely). Approach: Canoncal element method:
(a) Policy A Queue Bid price Charged price Action None None Deliver Deliver Utility
 Socally-Optmal Onlne Spectrum Auctons for Secondary Wreless Communcaton Hongxng L, Chuan Wu and Zongpeng L Coordnated Scence Laboratory, Unversty of Illnos at Urbana-Champagn, Emal: hxlhku@gmal.com Department
Socally-Optmal Onlne Spectrum Auctons for Secondary Wreless Communcaton Hongxng L, Chuan Wu and Zongpeng L Coordnated Scence Laboratory, Unversty of Illnos at Urbana-Champagn, Emal: hxlhku@gmal.com Department
Lecture 12: Discrete Laplacian
 Lecture 12: Dscrete Laplacan Scrbe: Tanye Lu Our goal s to come up wth a dscrete verson of Laplacan operator for trangulated surfaces, so that we can use t n practce to solve related problems We are mostly
Lecture 12: Dscrete Laplacan Scrbe: Tanye Lu Our goal s to come up wth a dscrete verson of Laplacan operator for trangulated surfaces, so that we can use t n practce to solve related problems We are mostly
EEL 6266 Power System Operation and Control. Chapter 3 Economic Dispatch Using Dynamic Programming
 EEL 6266 Power System Operaton and Control Chapter 3 Economc Dspatch Usng Dynamc Programmng Pecewse Lnear Cost Functons Common practce many utltes prefer to represent ther generator cost functons as sngle-
EEL 6266 Power System Operaton and Control Chapter 3 Economc Dspatch Usng Dynamc Programmng Pecewse Lnear Cost Functons Common practce many utltes prefer to represent ther generator cost functons as sngle-
= z 20 z n. (k 20) + 4 z k = 4
 Problem Set #7 solutons 7.2.. (a Fnd the coeffcent of z k n (z + z 5 + z 6 + z 7 + 5, k 20. We use the known seres expanson ( n+l ( z l l z n below: (z + z 5 + z 6 + z 7 + 5 (z 5 ( + z + z 2 + z + 5 5
Problem Set #7 solutons 7.2.. (a Fnd the coeffcent of z k n (z + z 5 + z 6 + z 7 + 5, k 20. We use the known seres expanson ( n+l ( z l l z n below: (z + z 5 + z 6 + z 7 + 5 (z 5 ( + z + z 2 + z + 5 5
