Evaluating Electricity Theft Detectors in Smart Grid Networks. Group 5:
|
|
|
- Giles Jenkins
- 5 years ago
- Views:
Transcription
1 Evaluating Electricity Theft Detectors in Smart Grid Networks Group 5: Ji, Xinyu Rivera, Asier
2 Agenda Introduction Background Electricity Theft Detectors and Attacks Results Discussion Conclusion 2
3 Introduction Bypass the Meter, so that, it doesn t count the consumed electricity. Detected under human inspection. 3
4 Background Observation (Electricity Consumption) X Sensor (SmartMeter) Y Classifier (Algorithm) Average attack: Set Y to low value => Really cheap electricity => Easy to detect. Sophisticated attack: Set Y to reasonable value => Cheaper electricity => Difficult to detect. Adversarial Classification: evaluate the effectiveness of the classifier against undetected attacks. Adversarial Learning: avoid the attacker to provide false data to the learning algorithm. 4
5 Adversarial classification Assumptions: A random process generates observations x X with probability distribution P 0 Use a maximum level of false negatives, α, that can be affordable Each classifier requires a threshold (Ƭ) to decide when raise the alert Attack vectors: 1. For each classifier, find the maximum value for the Ƭ among the P 0 distribution that fulfils α 2. Run all the classifiers set with the Ƭ selected in step 1, select the results that would produce the worst undetected attacks (more cost for the company) 3. Select the less costly (for the attacker) among the classifiers selected in step 2 5
6 Adversarial learning Contamination attacks: The classifiers uses a dataset to detect anomalies The attacker can inject false values to poison the dataset After some time, the data set is modified to fulfil the attackers requirements Contamination attack Y = Classifier would find purple as an anomaly Classifier would find purple as normal 6
7 Electricity-Theft Detectors and Attacks 1. Average Detector 2. ARMA-GLR 3. Nonparametric Statics (EWMA and CUSUM) 4. Unsupervised Learning (LOF) 7
8 Average Detector തY = 1 σ N i=1 N Y i In the paper they select the threshold in the following way: Given a training dataset, say T days in the most recent past, we can compute T daily averages, D i (i = 1,...,T) τ = min i (D i ) If തY <τ, where τ is a variable threshold. sending τ as Y i all the day Formulas from ECI Telecom. Fighting Electricity Theft with Advanced Metering Infrastructure (March 2011) 8
9 ARMA-GLR (Auto-Regressive Moving Average) ARMA probability distribution p0: If Y k > Y The attacker creates the probability distribution (P γ ) based on: Formulas from Forecast package for R, 9
10 EWMA (Exponentially-weighted Moving Average) EWMA i = λy i + (1 λ) EWMA i 1 If EWMA i < τ, where τ is a configurable parameter. λ is a weighting factor and 0 < λ 1 Yi is one of the time series measurements When EWMA i 1 When EWMA i 1 = τ, send Y i = τ. > τ, send Y i = MAX(0, τ (1 λ)ewma i 1 λ ) Formulas from EWMA Control Charts, 10
11 CUSUM (Cumulative Sum Control Chart) S i = MAX(0, S i 1 + (μ Y i b)) μ is the expected value of the time-series, (i = 1,...,N) b is a slack constant defined so that E[ μ Y i b] < 0 under normal operation if S i > τ Calculate M = τ+nb N and send Y i = μ M Formulas from Non-Parametric Methods in Change-Point Problems. Kluwer Academic Publishers by Brodsky, B., Darkhovsky, B 11
12 EXTRA: XMR chart (individuals and moving range chart) EWMA and CUSUM identify minor changes in small regions XMR chart identifies large changes over the time, it determines whether the process is stable and predictable or not It calculates various thresholds and classifies the anomalies depending on how the process overpasses those thresholds Images adapted from Fraud detection in registered electricity time series by Josif V. Spiric, Miroslav B. Docic and Slobodan S. Stankovic 12
13 LOF (Local Outlier Factor) 1. Create a vector containing all measurements of a day to be tested in order, V test = {Y 1,..., Y n } where N is the number of measurements per day. 2. For all days in a training dataset, create vectors in the same way, V i = {x i1, x in } (i = 1,...,T). 3. Create a set containing V test and all V is, and apply LOF to this set. 4. If LOF test < τ where LOF test is a score corresponding to V test, conclude V test is normal and exit. Select the value with the minimum consumption among the ones that their LOF score is less than τ. Reduce that value without raising the alarm and send it. Fomulas from Lof: Identifying density-based local outliers by Breunig, M., Kriegel, H.-P., Ng, R.T., Sander, J. 13
14 EXTRA: COF (Connectivity-based Outlier Factor) It is a variation of LOF, created because of the excessive complexity (N 2 ) LOF creates a neighbourhood based on the main given instance COF creates the neighbourhood in an aggregative way from the main given instance Image adapted from Anomaly Detection: A Survey by Varun Chandola, Arindam Banerjee and Vipin Kumar 14
15 Results In the paper, they use real meter-reading data measured by an electric utility company during 6 months. The meter reading consisted of 108 customers with a mix of residential and commercial customers and recorded every 15 minutes. 15
16 Adversarial Evaluation: Cost of Undetected Attacks Image adapted from Evaluating Electricity Theft Detectors in Smart Grid Networks by Daisuke Mashima and Alvaro A. Cárdenas 16
17 Monetary Loss Caused by Different Customers Average customers High consumption Customers Image adapted from Evaluating Electricity Theft Detectors in Smart Grid Networks by Daisuke Mashima and Alvaro A. Cárdenas 17
18 Adversarial Learning: Detecting Contaminated Datasets Image adapted from Evaluating Electricity Theft Detectors in Smart Grid Networks by Daisuke Mashima and Alvaro A. Cárdenas 18
19 Adversarial learning: Types Of Contamination Image adapted from Evaluating Electricity Theft Detectors in Smart Grid Networks by Daisuke Mashima and Alvaro A. Cárdenas 19
20 Discussion Cross-Correlation among customers Attackers should exhibit different trends compared to similar honest customers LOF to identify outliers Auto-Correlation in ARMA-GLR The residuals of generated attacks have high auto-correlation Durbin-Watson statistics then can detect attacks against ARMA-GLR Energy Efficiency Customers can add green-energy technology to the system, such as, solar panels Company should know about this information to set the classifiers properly Not general classifiers Depends on consumers lifestyle (changes from countries, areas, etc) 20
21 Conclusion These algorithms will perform much better under average cases where the attacker does not know the algorithm or time intervals we use for anomaly detection For companies, they need to combine all the information to consider their network and accurate the electricity-theft reports The proposed anomaly detector will only output indicators of an attack 21
Evaluating Electricity Theft Detectors in Smart Grid Networks
 Evaluating Electricity Theft Detectors in Smart Grid Networks Daisuke Mashima 1 and Alvaro A. Cárdenas 2 1 Georgia Institute of Technology mashima@cc.gatech.edu 2 Fujitsu Laboratories of America alvaro.cardenas-mora@us.fujitsu.com
Evaluating Electricity Theft Detectors in Smart Grid Networks Daisuke Mashima 1 and Alvaro A. Cárdenas 2 1 Georgia Institute of Technology mashima@cc.gatech.edu 2 Fujitsu Laboratories of America alvaro.cardenas-mora@us.fujitsu.com
Detection of Unauthorized Electricity Consumption using Machine Learning
 Detection of Unauthorized Electricity Consumption using Machine Learning Bo Tang, Ph.D. Department of Electrical and Computer Engineering Mississippi State University Outline Advanced Metering Infrastructure
Detection of Unauthorized Electricity Consumption using Machine Learning Bo Tang, Ph.D. Department of Electrical and Computer Engineering Mississippi State University Outline Advanced Metering Infrastructure
Journal of Chemical and Pharmaceutical Research, 2014, 6(5): Research Article
 Available online www.jocpr.com Journal of Chemical and Pharmaceutical Research, 2014, 6(5):266-270 Research Article ISSN : 0975-7384 CODEN(USA) : JCPRC5 Anomaly detection of cigarette sales using ARIMA
Available online www.jocpr.com Journal of Chemical and Pharmaceutical Research, 2014, 6(5):266-270 Research Article ISSN : 0975-7384 CODEN(USA) : JCPRC5 Anomaly detection of cigarette sales using ARIMA
CS570 Data Mining. Anomaly Detection. Li Xiong. Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber.
 CS570 Data Mining Anomaly Detection Li Xiong Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber April 3, 2011 1 Anomaly Detection Anomaly is a pattern in the data that does not conform
CS570 Data Mining Anomaly Detection Li Xiong Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber April 3, 2011 1 Anomaly Detection Anomaly is a pattern in the data that does not conform
Anomaly Detection via Over-sampling Principal Component Analysis
 Anomaly Detection via Over-sampling Principal Component Analysis Yi-Ren Yeh, Zheng-Yi Lee, and Yuh-Jye Lee Abstract Outlier detection is an important issue in data mining and has been studied in different
Anomaly Detection via Over-sampling Principal Component Analysis Yi-Ren Yeh, Zheng-Yi Lee, and Yuh-Jye Lee Abstract Outlier detection is an important issue in data mining and has been studied in different
SHORT TERM LOAD FORECASTING
 Indian Institute of Technology Kanpur (IITK) and Indian Energy Exchange (IEX) are delighted to announce Training Program on "Power Procurement Strategy and Power Exchanges" 28-30 July, 2014 SHORT TERM
Indian Institute of Technology Kanpur (IITK) and Indian Energy Exchange (IEX) are delighted to announce Training Program on "Power Procurement Strategy and Power Exchanges" 28-30 July, 2014 SHORT TERM
Anomaly Detection. Jing Gao. SUNY Buffalo
 Anomaly Detection Jing Gao SUNY Buffalo 1 Anomaly Detection Anomalies the set of objects are considerably dissimilar from the remainder of the data occur relatively infrequently when they do occur, their
Anomaly Detection Jing Gao SUNY Buffalo 1 Anomaly Detection Anomalies the set of objects are considerably dissimilar from the remainder of the data occur relatively infrequently when they do occur, their
Data Mining Based Anomaly Detection In PMU Measurements And Event Detection
 Data Mining Based Anomaly Detection In PMU Measurements And Event Detection P. Banerjee, S. Pandey, M. Zhou, A. Srivastava, Y. Wu Smart Grid Demonstration and Research Investigation Lab (SGDRIL) Energy
Data Mining Based Anomaly Detection In PMU Measurements And Event Detection P. Banerjee, S. Pandey, M. Zhou, A. Srivastava, Y. Wu Smart Grid Demonstration and Research Investigation Lab (SGDRIL) Energy
False Data Injection Attacks Against Nonlinear State Estimation in Smart Power Grids
 1 False Data Injection Attacks Against Nonlinear State Estimation in Smart Power rids Md. Ashfaqur Rahman and Hamed Mohsenian-Rad Department of Electrical and Computer Engineering, Texas Tech University,
1 False Data Injection Attacks Against Nonlinear State Estimation in Smart Power rids Md. Ashfaqur Rahman and Hamed Mohsenian-Rad Department of Electrical and Computer Engineering, Texas Tech University,
An Overview of Outlier Detection Techniques and Applications
 Machine Learning Rhein-Neckar Meetup An Overview of Outlier Detection Techniques and Applications Ying Gu connygy@gmail.com 28.02.2016 Anomaly/Outlier Detection What are anomalies/outliers? The set of
Machine Learning Rhein-Neckar Meetup An Overview of Outlier Detection Techniques and Applications Ying Gu connygy@gmail.com 28.02.2016 Anomaly/Outlier Detection What are anomalies/outliers? The set of
Università di Pisa A.A Data Mining II June 13th, < {A} {B,F} {E} {A,B} {A,C,D} {F} {B,E} {C,D} > t=0 t=1 t=2 t=3 t=4 t=5 t=6 t=7
 Università di Pisa A.A. 2016-2017 Data Mining II June 13th, 2017 Exercise 1 - Sequential patterns (6 points) a) (3 points) Given the following input sequence < {A} {B,F} {E} {A,B} {A,C,D} {F} {B,E} {C,D}
Università di Pisa A.A. 2016-2017 Data Mining II June 13th, 2017 Exercise 1 - Sequential patterns (6 points) a) (3 points) Given the following input sequence < {A} {B,F} {E} {A,B} {A,C,D} {F} {B,E} {C,D}
Unsupervised Learning Methods
 Structural Health Monitoring Using Statistical Pattern Recognition Unsupervised Learning Methods Keith Worden and Graeme Manson Presented by Keith Worden The Structural Health Monitoring Process 1. Operational
Structural Health Monitoring Using Statistical Pattern Recognition Unsupervised Learning Methods Keith Worden and Graeme Manson Presented by Keith Worden The Structural Health Monitoring Process 1. Operational
Chart types and when to use them
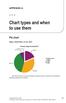 APPENDIX A Chart types and when to use them Pie chart Figure illustration of pie chart 2.3 % 4.5 % Browser Usage for April 2012 18.3 % 38.3 % Internet Explorer Firefox Chrome Safari Opera 35.8 % Pie chart
APPENDIX A Chart types and when to use them Pie chart Figure illustration of pie chart 2.3 % 4.5 % Browser Usage for April 2012 18.3 % 38.3 % Internet Explorer Firefox Chrome Safari Opera 35.8 % Pie chart
Justin Appleby CS 229 Machine Learning Project Report 12/15/17 Kevin Chalhoub Building Electricity Load Forecasting
 Justin Appleby CS 229 Machine Learning Project Report 12/15/17 Kevin Chalhoub Building Electricity Load Forecasting with ARIMA and Sequential Linear Regression Abstract Load forecasting is an essential
Justin Appleby CS 229 Machine Learning Project Report 12/15/17 Kevin Chalhoub Building Electricity Load Forecasting with ARIMA and Sequential Linear Regression Abstract Load forecasting is an essential
Multi-Plant Photovoltaic Energy Forecasting Challenge: Second place solution
 Multi-Plant Photovoltaic Energy Forecasting Challenge: Second place solution Clément Gautrais 1, Yann Dauxais 1, and Maël Guilleme 2 1 University of Rennes 1/Inria Rennes clement.gautrais@irisa.fr 2 Energiency/University
Multi-Plant Photovoltaic Energy Forecasting Challenge: Second place solution Clément Gautrais 1, Yann Dauxais 1, and Maël Guilleme 2 1 University of Rennes 1/Inria Rennes clement.gautrais@irisa.fr 2 Energiency/University
Department of Computer Science, University of Pittsburgh. Brigham and Women's Hospital and Harvard Medical School
 Siqi Liu 1, Adam Wright 2, and Milos Hauskrecht 1 1 Department of Computer Science, University of Pittsburgh 2 Brigham and Women's Hospital and Harvard Medical School Introduction Method Experiments and
Siqi Liu 1, Adam Wright 2, and Milos Hauskrecht 1 1 Department of Computer Science, University of Pittsburgh 2 Brigham and Women's Hospital and Harvard Medical School Introduction Method Experiments and
GLAD: Group Anomaly Detection in Social Media Analysis
 GLAD: Group Anomaly Detection in Social Media Analysis Poster #: 1150 Rose Yu, Xinran He and Yan Liu University of Southern California Group Anomaly Detection Anomalous phenomenon in social media data
GLAD: Group Anomaly Detection in Social Media Analysis Poster #: 1150 Rose Yu, Xinran He and Yan Liu University of Southern California Group Anomaly Detection Anomalous phenomenon in social media data
A Framework for Adaptive Anomaly Detection Based on Support Vector Data Description
 A Framework for Adaptive Anomaly Detection Based on Support Vector Data Description Min Yang, HuanGuo Zhang, JianMing Fu, and Fei Yan School of Computer, State Key Laboratory of Software Engineering, Wuhan
A Framework for Adaptive Anomaly Detection Based on Support Vector Data Description Min Yang, HuanGuo Zhang, JianMing Fu, and Fei Yan School of Computer, State Key Laboratory of Software Engineering, Wuhan
Anomaly (outlier) detection. Huiping Cao, Anomaly 1
 Anomaly (outlier) detection Huiping Cao, Anomaly 1 Outline General concepts What are outliers Types of outliers Causes of anomalies Challenges of outlier detection Outlier detection approaches Huiping
Anomaly (outlier) detection Huiping Cao, Anomaly 1 Outline General concepts What are outliers Types of outliers Causes of anomalies Challenges of outlier detection Outlier detection approaches Huiping
Introduction to Time Series (I)
 Introduction to Time Series (I) ZHANG RONG Department of Social Networking Operations Social Networking Group Tencent Company November 20, 2017 ZHANG RONG Introduction to Time Series (I) 1/69 Outline 1
Introduction to Time Series (I) ZHANG RONG Department of Social Networking Operations Social Networking Group Tencent Company November 20, 2017 ZHANG RONG Introduction to Time Series (I) 1/69 Outline 1
Real-time Sentiment-Based Anomaly Detection in Twitter Data Streams
 Real-time Sentiment-Based Anomaly Detection in Twitter Data Streams Khantil Patel, Orland Hoeber, and Howard J. Hamilton Department of Computer Science University of Regina, Canada patel26k@uregina.ca,
Real-time Sentiment-Based Anomaly Detection in Twitter Data Streams Khantil Patel, Orland Hoeber, and Howard J. Hamilton Department of Computer Science University of Regina, Canada patel26k@uregina.ca,
Multi-criteria Anomaly Detection using Pareto Depth Analysis
 Multi-criteria Anomaly Detection using Pareto Depth Analysis Ko-Jen Hsiao, Kevin S. Xu, Jeff Calder, and Alfred O. Hero III University of Michigan, Ann Arbor, MI, USA 489 {coolmark,xukevin,jcalder,hero}@umich.edu
Multi-criteria Anomaly Detection using Pareto Depth Analysis Ko-Jen Hsiao, Kevin S. Xu, Jeff Calder, and Alfred O. Hero III University of Michigan, Ann Arbor, MI, USA 489 {coolmark,xukevin,jcalder,hero}@umich.edu
About Nnergix +2, More than 2,5 GW forecasted. Forecasting in 5 countries. 4 predictive technologies. More than power facilities
 About Nnergix +2,5 5 4 +20.000 More than 2,5 GW forecasted Forecasting in 5 countries 4 predictive technologies More than 20.000 power facilities Nnergix s Timeline 2012 First Solar Photovoltaic energy
About Nnergix +2,5 5 4 +20.000 More than 2,5 GW forecasted Forecasting in 5 countries 4 predictive technologies More than 20.000 power facilities Nnergix s Timeline 2012 First Solar Photovoltaic energy
Anomaly Detection via Online Oversampling Principal Component Analysis
 Anomaly Detection via Online Oversampling Principal Component Analysis R.Sundara Nagaraj 1, C.Anitha 2 and Mrs.K.K.Kavitha 3 1 PG Scholar (M.Phil-CS), Selvamm Art Science College (Autonomous), Namakkal,
Anomaly Detection via Online Oversampling Principal Component Analysis R.Sundara Nagaraj 1, C.Anitha 2 and Mrs.K.K.Kavitha 3 1 PG Scholar (M.Phil-CS), Selvamm Art Science College (Autonomous), Namakkal,
Electrical Energy Modeling In Y2E2 Building Based On Distributed Sensors Information
 Electrical Energy Modeling In Y2E2 Building Based On Distributed Sensors Information Mahmoud Saadat Saman Ghili Introduction Close to 40% of the primary energy consumption in the U.S. comes from commercial
Electrical Energy Modeling In Y2E2 Building Based On Distributed Sensors Information Mahmoud Saadat Saman Ghili Introduction Close to 40% of the primary energy consumption in the U.S. comes from commercial
Available online at ScienceDirect. Procedia Engineering 119 (2015 ) 13 18
 Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 119 (2015 ) 13 18 13th Computer Control for Water Industry Conference, CCWI 2015 Real-time burst detection in water distribution
Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 119 (2015 ) 13 18 13th Computer Control for Water Industry Conference, CCWI 2015 Real-time burst detection in water distribution
Unsupervised Anomaly Detection for High Dimensional Data
 Unsupervised Anomaly Detection for High Dimensional Data Department of Mathematics, Rowan University. July 19th, 2013 International Workshop in Sequential Methodologies (IWSM-2013) Outline of Talk Motivation
Unsupervised Anomaly Detection for High Dimensional Data Department of Mathematics, Rowan University. July 19th, 2013 International Workshop in Sequential Methodologies (IWSM-2013) Outline of Talk Motivation
Quantifying Cyber Security for Networked Control Systems
 Quantifying Cyber Security for Networked Control Systems Henrik Sandberg ACCESS Linnaeus Centre, KTH Royal Institute of Technology Joint work with: André Teixeira, György Dán, Karl H. Johansson (KTH) Kin
Quantifying Cyber Security for Networked Control Systems Henrik Sandberg ACCESS Linnaeus Centre, KTH Royal Institute of Technology Joint work with: André Teixeira, György Dán, Karl H. Johansson (KTH) Kin
Detection and Estimation Final Project Report: Modeling and the K-Sigma Algorithm for Radiation Detection
 Detection and Estimation Final Project Report: Modeling and the K-Sigma Algorithm for Radiation Detection Sijie Xiong, 151004243 Department of Electrical and Computer Engineering Rutgers, the State University
Detection and Estimation Final Project Report: Modeling and the K-Sigma Algorithm for Radiation Detection Sijie Xiong, 151004243 Department of Electrical and Computer Engineering Rutgers, the State University
CS4445 Data Mining and Knowledge Discovery in Databases. B Term 2014 Solutions Exam 2 - December 15, 2014
 CS4445 Data Mining and Knowledge Discovery in Databases. B Term 2014 Solutions Exam 2 - December 15, 2014 Prof. Carolina Ruiz Department of Computer Science Worcester Polytechnic Institute NAME: Prof.
CS4445 Data Mining and Knowledge Discovery in Databases. B Term 2014 Solutions Exam 2 - December 15, 2014 Prof. Carolina Ruiz Department of Computer Science Worcester Polytechnic Institute NAME: Prof.
Surprise Detection in Multivariate Astronomical Data Kirk Borne George Mason University
 Surprise Detection in Multivariate Astronomical Data Kirk Borne George Mason University kborne@gmu.edu, http://classweb.gmu.edu/kborne/ Outline What is Surprise Detection? Example Application: The LSST
Surprise Detection in Multivariate Astronomical Data Kirk Borne George Mason University kborne@gmu.edu, http://classweb.gmu.edu/kborne/ Outline What is Surprise Detection? Example Application: The LSST
Cyber Attacks, Detection and Protection in Smart Grid State Estimation
 1 Cyber Attacks, Detection and Protection in Smart Grid State Estimation Yi Zhou, Student Member, IEEE Zhixin Miao, Senior Member, IEEE Abstract This paper reviews the types of cyber attacks in state estimation
1 Cyber Attacks, Detection and Protection in Smart Grid State Estimation Yi Zhou, Student Member, IEEE Zhixin Miao, Senior Member, IEEE Abstract This paper reviews the types of cyber attacks in state estimation
Identification of False Data Injection Attacks with Considering the Impact of Wind Generation and Topology Reconfigurations
 1 Identification of False Data ion Attacks with Considering the Impact of Wind Generation and Topology Reconfigurations Mostafa Mohammadpourfard, Student Member, IEEE, Ashkan Sami, Member, IEEE, and Yang
1 Identification of False Data ion Attacks with Considering the Impact of Wind Generation and Topology Reconfigurations Mostafa Mohammadpourfard, Student Member, IEEE, Ashkan Sami, Member, IEEE, and Yang
Data and prognosis for renewable energy
 The Hong Kong Polytechnic University Department of Electrical Engineering Project code: FYP_27 Data and prognosis for renewable energy by Choi Man Hin 14072258D Final Report Bachelor of Engineering (Honours)
The Hong Kong Polytechnic University Department of Electrical Engineering Project code: FYP_27 Data and prognosis for renewable energy by Choi Man Hin 14072258D Final Report Bachelor of Engineering (Honours)
Description of the case study
 Description of the case study During the night and early morning of the 14 th of July 011 the significant cloud layer expanding in the West of the country and slowly moving East produced precipitation
Description of the case study During the night and early morning of the 14 th of July 011 the significant cloud layer expanding in the West of the country and slowly moving East produced precipitation
Predicting Solar Irradiance and Inverter power for PV sites
 Area of Expertise: Industry: Name of Client: Predicting Solar Irradiance and Inverter power for PV sites Data Analytics Solar Project End Date: January 2019 Project Timeline: 1. Optimisation Scope InnovateUK
Area of Expertise: Industry: Name of Client: Predicting Solar Irradiance and Inverter power for PV sites Data Analytics Solar Project End Date: January 2019 Project Timeline: 1. Optimisation Scope InnovateUK
ASSIGNMENT - 1 M.Sc. DEGREE EXAMINATION, MAY 2019 Second Year STATISTICS. Statistical Quality Control MAXIMUM : 30 MARKS ANSWER ALL QUESTIONS
 ASSIGNMENT - 1 Statistical Quality Control (DMSTT21) Q1) a) Explain the role and importance of statistical quality control in industry. b) Explain control charts for variables. Write the LCL, UCL for X,
ASSIGNMENT - 1 Statistical Quality Control (DMSTT21) Q1) a) Explain the role and importance of statistical quality control in industry. b) Explain control charts for variables. Write the LCL, UCL for X,
Forecasting demand in the National Electricity Market. October 2017
 Forecasting demand in the National Electricity Market October 2017 Agenda Trends in the National Electricity Market A review of AEMO s forecasting methods Long short-term memory (LSTM) neural networks
Forecasting demand in the National Electricity Market October 2017 Agenda Trends in the National Electricity Market A review of AEMO s forecasting methods Long short-term memory (LSTM) neural networks
Anomaly Detection in Logged Sensor Data. Master s thesis in Complex Adaptive Systems JOHAN FLORBÄCK
 Anomaly Detection in Logged Sensor Data Master s thesis in Complex Adaptive Systems JOHAN FLORBÄCK Department of Applied Mechanics CHALMERS UNIVERSITY OF TECHNOLOGY Göteborg, Sweden 2015 MASTER S THESIS
Anomaly Detection in Logged Sensor Data Master s thesis in Complex Adaptive Systems JOHAN FLORBÄCK Department of Applied Mechanics CHALMERS UNIVERSITY OF TECHNOLOGY Göteborg, Sweden 2015 MASTER S THESIS
Machine Learning Linear Classification. Prof. Matteo Matteucci
 Machine Learning Linear Classification Prof. Matteo Matteucci Recall from the first lecture 2 X R p Regression Y R Continuous Output X R p Y {Ω 0, Ω 1,, Ω K } Classification Discrete Output X R p Y (X)
Machine Learning Linear Classification Prof. Matteo Matteucci Recall from the first lecture 2 X R p Regression Y R Continuous Output X R p Y {Ω 0, Ω 1,, Ω K } Classification Discrete Output X R p Y (X)
Support Measure Data Description for Group Anomaly Detection
 Support Measure Data Description for Group Anomaly Detection 1 Jorge Guevara Díaz, 2 Stephane Canu, 1 Roberto Hirata Jr. 1 IME-USP, Brazil. 2 LITIS-INSA, France. November 03, 2015. Outline 1 Who am I?
Support Measure Data Description for Group Anomaly Detection 1 Jorge Guevara Díaz, 2 Stephane Canu, 1 Roberto Hirata Jr. 1 IME-USP, Brazil. 2 LITIS-INSA, France. November 03, 2015. Outline 1 Who am I?
The Changing Landscape of Land Administration
 The Changing Landscape of Land Administration B r e n t J o n e s P E, PLS E s r i World s Largest Media Company No Journalists No Content Producers No Photographers World s Largest Hospitality Company
The Changing Landscape of Land Administration B r e n t J o n e s P E, PLS E s r i World s Largest Media Company No Journalists No Content Producers No Photographers World s Largest Hospitality Company
Learning an Optimal Policy for Police Resource Allocation on Freeways
 Brian Jackson Taylor Howell Ola Shorinwa Abstract Anomaly detection is well studied and has applications in surveillance, driver assistance, and navigation. In this project, we develop an anomaly detection
Brian Jackson Taylor Howell Ola Shorinwa Abstract Anomaly detection is well studied and has applications in surveillance, driver assistance, and navigation. In this project, we develop an anomaly detection
Stat 500 Midterm 2 8 November 2007 page 0 of 4
 Stat 500 Midterm 2 8 November 2007 page 0 of 4 Please put your name on the back of your answer book. Do NOT put it on the front. Thanks. DO NOT START until I tell you to. You are welcome to read this front
Stat 500 Midterm 2 8 November 2007 page 0 of 4 Please put your name on the back of your answer book. Do NOT put it on the front. Thanks. DO NOT START until I tell you to. You are welcome to read this front
Improving Biosurveillance System Performance. Ronald D. Fricker, Jr. Virginia Tech July 7, 2015
 Improving Biosurveillance System Performance Ronald D. Fricker, Jr. Virginia Tech July 7, 2015 What is Biosurveillance? The term biosurveillance means the process of active datagathering of biosphere data
Improving Biosurveillance System Performance Ronald D. Fricker, Jr. Virginia Tech July 7, 2015 What is Biosurveillance? The term biosurveillance means the process of active datagathering of biosphere data
Prompt Network Anomaly Detection using SSA-Based Change-Point Detection. Hao Chen 3/7/2014
 Prompt Network Anomaly Detection using SSA-Based Change-Point Detection Hao Chen 3/7/2014 Network Anomaly Detection Network Intrusion Detection (NID) Signature-based detection Detect known attacks Use
Prompt Network Anomaly Detection using SSA-Based Change-Point Detection Hao Chen 3/7/2014 Network Anomaly Detection Network Intrusion Detection (NID) Signature-based detection Detect known attacks Use
AWERProcedia Information Technology & Computer Science
 AWERProcedia Information Technology & Computer Science Vol 04 (2013) 851-856 3 rd World Conference on Innovation and Computer Sciences 2013 Mathematical model of the control system of objects of electro
AWERProcedia Information Technology & Computer Science Vol 04 (2013) 851-856 3 rd World Conference on Innovation and Computer Sciences 2013 Mathematical model of the control system of objects of electro
b) Explain about charts for attributes and explain their uses. 4) a) Distinguish the difference between CUSUM charts and Shewartz control charts.
 ASSIGNMENT - 1, DEC - 2016. PAPER- I : STATISTICAL QUALITY CONTROL (DMSTT 21) 1) a) Explain about Midrange control chart and median control chart. b) Explain about average run length for X chart. 2) a)
ASSIGNMENT - 1, DEC - 2016. PAPER- I : STATISTICAL QUALITY CONTROL (DMSTT 21) 1) a) Explain about Midrange control chart and median control chart. b) Explain about average run length for X chart. 2) a)
Weather Normalization: Model Selection and Validation EFG Workshop, Baltimore Prasenjit Shil
 Weather Normalization: Model Selection and Validation 05.07.15 EFG Workshop, Baltimore Prasenjit Shil Ameren at a Glance Ameren Missouri, Ameren Illinois and Ameren Transmission Company 2.4 million electric
Weather Normalization: Model Selection and Validation 05.07.15 EFG Workshop, Baltimore Prasenjit Shil Ameren at a Glance Ameren Missouri, Ameren Illinois and Ameren Transmission Company 2.4 million electric
Predictive Modeling: Classification. KSE 521 Topic 6 Mun Yi
 Predictive Modeling: Classification Topic 6 Mun Yi Agenda Models and Induction Entropy and Information Gain Tree-Based Classifier Probability Estimation 2 Introduction Key concept of BI: Predictive modeling
Predictive Modeling: Classification Topic 6 Mun Yi Agenda Models and Induction Entropy and Information Gain Tree-Based Classifier Probability Estimation 2 Introduction Key concept of BI: Predictive modeling
Detecting Non-Technical Energy Losses through Structural Periodic Patterns in AMI data
 2016 IEEE International Conference on Big Data (Big Data) Detecting Non-Technical Energy Losses through Structural Periodic Patterns in AMI data Viktor Botev, Magnus Almgren, Vincenzo Gulisano, Olaf Landsiedel,
2016 IEEE International Conference on Big Data (Big Data) Detecting Non-Technical Energy Losses through Structural Periodic Patterns in AMI data Viktor Botev, Magnus Almgren, Vincenzo Gulisano, Olaf Landsiedel,
Structured Denoising Autoencoder for Fault Detection and Analysis
 JMLR: Workshop and Conference Proceedings 39:96 111, 2014 ACML 2014 Structured Denoising Autoencoder for Fault Detection and Analysis Takaaki Tagawa Yukihiro Tadokoro TOYOTA CENTRAL R&D LABS., INC., Japan
JMLR: Workshop and Conference Proceedings 39:96 111, 2014 ACML 2014 Structured Denoising Autoencoder for Fault Detection and Analysis Takaaki Tagawa Yukihiro Tadokoro TOYOTA CENTRAL R&D LABS., INC., Japan
Doing Right By Massive Data: How To Bring Probability Modeling To The Analysis Of Huge Datasets Without Taking Over The Datacenter
 Doing Right By Massive Data: How To Bring Probability Modeling To The Analysis Of Huge Datasets Without Taking Over The Datacenter Alexander W Blocker Pavlos Protopapas Xiao-Li Meng 9 February, 2010 Outline
Doing Right By Massive Data: How To Bring Probability Modeling To The Analysis Of Huge Datasets Without Taking Over The Datacenter Alexander W Blocker Pavlos Protopapas Xiao-Li Meng 9 February, 2010 Outline
Hierarchical Anomaly Detection in Load Testing with StormRunner Load
 White Paper Application Development, Test & Delivery Hierarchical Anomaly Detection in Load Testing with StormRunner Load A fresh approach to cloud-based website load testing is proving more effective
White Paper Application Development, Test & Delivery Hierarchical Anomaly Detection in Load Testing with StormRunner Load A fresh approach to cloud-based website load testing is proving more effective
Aalborg Universitet. CLIMA proceedings of the 12th REHVA World Congress Heiselberg, Per Kvols. Publication date: 2016
 Aalborg Universitet CLIMA 2016 - proceedings of the 12th REHVA World Congress Heiselberg, Per Kvols Publication date: 2016 Document Version Final published version Link to publication from Aalborg University
Aalborg Universitet CLIMA 2016 - proceedings of the 12th REHVA World Congress Heiselberg, Per Kvols Publication date: 2016 Document Version Final published version Link to publication from Aalborg University
Predicting New Search-Query Cluster Volume
 Predicting New Search-Query Cluster Volume Jacob Sisk, Cory Barr December 14, 2007 1 Problem Statement Search engines allow people to find information important to them, and search engine companies derive
Predicting New Search-Query Cluster Volume Jacob Sisk, Cory Barr December 14, 2007 1 Problem Statement Search engines allow people to find information important to them, and search engine companies derive
Distribution-Free Monitoring of Univariate Processes. Peihua Qiu 1 and Zhonghua Li 1,2. Abstract
 Distribution-Free Monitoring of Univariate Processes Peihua Qiu 1 and Zhonghua Li 1,2 1 School of Statistics, University of Minnesota, USA 2 LPMC and Department of Statistics, Nankai University, China
Distribution-Free Monitoring of Univariate Processes Peihua Qiu 1 and Zhonghua Li 1,2 1 School of Statistics, University of Minnesota, USA 2 LPMC and Department of Statistics, Nankai University, China
Prediction for night-time ventilation in Stanford s Y2E2 building
 Prediction for night-time ventilation in Stanford s Y2E2 building Balthazar Donon Stanford University December 16, 2016 Indoor ventilation I. Introduction In the United States, around 40% of the energy
Prediction for night-time ventilation in Stanford s Y2E2 building Balthazar Donon Stanford University December 16, 2016 Indoor ventilation I. Introduction In the United States, around 40% of the energy
EXAD: A System for Explainable Anomaly Detection on Big Data Traces
 EXAD: A System for Explainable Anomaly Detection on Big Data Traces Fei Song Inria, France fei.song@inria.fr Arnaud Stiegler arnaud.stiegler@polytechnique.edu Yanlei Diao University of Massachusetts Amherst
EXAD: A System for Explainable Anomaly Detection on Big Data Traces Fei Song Inria, France fei.song@inria.fr Arnaud Stiegler arnaud.stiegler@polytechnique.edu Yanlei Diao University of Massachusetts Amherst
Anomaly detection and. in time series
 Anomaly detection and sequential statistics in time series Alex Shyr CS 294 Practical Machine Learning 11/12/2009 (many slides from XuanLong Nguyen and Charles Sutton) Two topics Anomaly detection Sequential
Anomaly detection and sequential statistics in time series Alex Shyr CS 294 Practical Machine Learning 11/12/2009 (many slides from XuanLong Nguyen and Charles Sutton) Two topics Anomaly detection Sequential
Nonparametric forecasting of the French load curve
 An overview RTE & UPMC-ISUP ISNPS 214, Cadix June 15, 214 Table of contents 1 Introduction 2 MAVE modeling 3 IBR modeling 4 Sparse modeling Electrical context Generation must be strictly equal to consumption
An overview RTE & UPMC-ISUP ISNPS 214, Cadix June 15, 214 Table of contents 1 Introduction 2 MAVE modeling 3 IBR modeling 4 Sparse modeling Electrical context Generation must be strictly equal to consumption
Jeffrey D. Ullman Stanford University
 Jeffrey D. Ullman Stanford University 3 We are given a set of training examples, consisting of input-output pairs (x,y), where: 1. x is an item of the type we want to evaluate. 2. y is the value of some
Jeffrey D. Ullman Stanford University 3 We are given a set of training examples, consisting of input-output pairs (x,y), where: 1. x is an item of the type we want to evaluate. 2. y is the value of some
Artificial Neural Networks Examination, June 2005
 Artificial Neural Networks Examination, June 2005 Instructions There are SIXTY questions. (The pass mark is 30 out of 60). For each question, please select a maximum of ONE of the given answers (either
Artificial Neural Networks Examination, June 2005 Instructions There are SIXTY questions. (The pass mark is 30 out of 60). For each question, please select a maximum of ONE of the given answers (either
Roberto Perdisci^+, Guofei Gu^, Wenke Lee^ presented by Roberto Perdisci. ^Georgia Institute of Technology, Atlanta, GA, USA
 U s i n g a n E n s e m b l e o f O n e - C l a s s S V M C l a s s i f i e r s t o H a r d e n P a y l o a d - B a s e d A n o m a l y D e t e c t i o n S y s t e m s Roberto Perdisci^+, Guofei Gu^, Wenke
U s i n g a n E n s e m b l e o f O n e - C l a s s S V M C l a s s i f i e r s t o H a r d e n P a y l o a d - B a s e d A n o m a l y D e t e c t i o n S y s t e m s Roberto Perdisci^+, Guofei Gu^, Wenke
Application-Aware Anomaly Detection of Sensor Measurements in Cyber-Physical Systems
 sensors Article Application-Aware Anomaly Detection of Sensor Measurements in Cyber-Physical Systems Amin Ghafouri 1 ID, Aron Laszka 2 ID, and Xenofon Koutsoukos 1, * ID 1 Department of Electrical Engineering
sensors Article Application-Aware Anomaly Detection of Sensor Measurements in Cyber-Physical Systems Amin Ghafouri 1 ID, Aron Laszka 2 ID, and Xenofon Koutsoukos 1, * ID 1 Department of Electrical Engineering
Concept Drift. Albert Bifet. March 2012
 Concept Drift Albert Bifet March 2012 COMP423A/COMP523A Data Stream Mining Outline 1. Introduction 2. Stream Algorithmics 3. Concept drift 4. Evaluation 5. Classification 6. Ensemble Methods 7. Regression
Concept Drift Albert Bifet March 2012 COMP423A/COMP523A Data Stream Mining Outline 1. Introduction 2. Stream Algorithmics 3. Concept drift 4. Evaluation 5. Classification 6. Ensemble Methods 7. Regression
Analysis. Components of a Time Series
 Module 8: Time Series Analysis 8.2 Components of a Time Series, Detection of Change Points and Trends, Time Series Models Components of a Time Series There can be several things happening simultaneously
Module 8: Time Series Analysis 8.2 Components of a Time Series, Detection of Change Points and Trends, Time Series Models Components of a Time Series There can be several things happening simultaneously
Anomaly Detection for the CERN Large Hadron Collider injection magnets
 Anomaly Detection for the CERN Large Hadron Collider injection magnets Armin Halilovic KU Leuven - Department of Computer Science In cooperation with CERN 2018-07-27 0 Outline 1 Context 2 Data 3 Preprocessing
Anomaly Detection for the CERN Large Hadron Collider injection magnets Armin Halilovic KU Leuven - Department of Computer Science In cooperation with CERN 2018-07-27 0 Outline 1 Context 2 Data 3 Preprocessing
Quality Control & Statistical Process Control (SPC)
 Quality Control & Statistical Process Control (SPC) DR. RON FRICKER PROFESSOR & HEAD, DEPARTMENT OF STATISTICS DATAWORKS CONFERENCE, MARCH 22, 2018 Agenda Some Terminology & Background SPC Methods & Philosophy
Quality Control & Statistical Process Control (SPC) DR. RON FRICKER PROFESSOR & HEAD, DEPARTMENT OF STATISTICS DATAWORKS CONFERENCE, MARCH 22, 2018 Agenda Some Terminology & Background SPC Methods & Philosophy
Graph-Based Anomaly Detection with Soft Harmonic Functions
 Graph-Based Anomaly Detection with Soft Harmonic Functions Michal Valko Advisor: Milos Hauskrecht Computer Science Department, University of Pittsburgh, Computer Science Day 2011, March 18 th, 2011. Anomaly
Graph-Based Anomaly Detection with Soft Harmonic Functions Michal Valko Advisor: Milos Hauskrecht Computer Science Department, University of Pittsburgh, Computer Science Day 2011, March 18 th, 2011. Anomaly
Improving Gas Demand Forecast During Extreme Cold Events
 Marquette University e-publications@marquette Master's Theses (2009 -) Dissertations, Theses, and Professional Projects Improving Gas Demand Forecast During Extreme Cold Events Babatunde Isaac Ishola Marquette
Marquette University e-publications@marquette Master's Theses (2009 -) Dissertations, Theses, and Professional Projects Improving Gas Demand Forecast During Extreme Cold Events Babatunde Isaac Ishola Marquette
Performance of Conventional X-bar Chart for Autocorrelated Data Using Smaller Sample Sizes
 , 23-25 October, 2013, San Francisco, USA Performance of Conventional X-bar Chart for Autocorrelated Data Using Smaller Sample Sizes D. R. Prajapati Abstract Control charts are used to determine whether
, 23-25 October, 2013, San Francisco, USA Performance of Conventional X-bar Chart for Autocorrelated Data Using Smaller Sample Sizes D. R. Prajapati Abstract Control charts are used to determine whether
Wireless Sensor Network Wormhole Detection using an Artificial Neural Network
 Int'l Conf. Wireless Networks ICWN'15 115 Wireless Sensor Network Wormhole Detection using an Artificial Neural Network Mohammad Nurul Afsar Shaon and Ken Ferens Department of Electrical and Computer Engineering
Int'l Conf. Wireless Networks ICWN'15 115 Wireless Sensor Network Wormhole Detection using an Artificial Neural Network Mohammad Nurul Afsar Shaon and Ken Ferens Department of Electrical and Computer Engineering
Real-Time Detection of Hybrid and Stealthy Cyber-Attacks in Smart Grid
 1 Real-Time Detection of Hybrid and Stealthy Cyber-Attacks in Smart Grid Mehmet Necip Kurt, Yasin Yılmaz, Member, IEEE, and Xiaodong Wang, Fellow, IEEE Abstract For a safe and reliable operation of the
1 Real-Time Detection of Hybrid and Stealthy Cyber-Attacks in Smart Grid Mehmet Necip Kurt, Yasin Yılmaz, Member, IEEE, and Xiaodong Wang, Fellow, IEEE Abstract For a safe and reliable operation of the
2.830J / 6.780J / ESD.63J Control of Manufacturing Processes (SMA 6303) Spring 2008
 MIT OpenCourseWare http://ocw.mit.edu 2.830J / 6.780J / ESD.63J Control of Processes (SMA 6303) Spring 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/term
MIT OpenCourseWare http://ocw.mit.edu 2.830J / 6.780J / ESD.63J Control of Processes (SMA 6303) Spring 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/term
Performance Evaluation
 Performance Evaluation David S. Rosenberg Bloomberg ML EDU October 26, 2017 David S. Rosenberg (Bloomberg ML EDU) October 26, 2017 1 / 36 Baseline Models David S. Rosenberg (Bloomberg ML EDU) October 26,
Performance Evaluation David S. Rosenberg Bloomberg ML EDU October 26, 2017 David S. Rosenberg (Bloomberg ML EDU) October 26, 2017 1 / 36 Baseline Models David S. Rosenberg (Bloomberg ML EDU) October 26,
Predicting Solar Flares by Converting GOES X-ray Data to Gramian Angular Fields (GAF) Images
 , July 4-6, 2018, London, U.K. Predicting Solar Flares by Converting GOES X-ray Data to Gramian Angular Fields (GAF) Images Tarek Nagem, Rami Qahwaji, Stanley Ipson, Amro Alasta Abstract: Predicting solar
, July 4-6, 2018, London, U.K. Predicting Solar Flares by Converting GOES X-ray Data to Gramian Angular Fields (GAF) Images Tarek Nagem, Rami Qahwaji, Stanley Ipson, Amro Alasta Abstract: Predicting solar
ECE 5424: Introduction to Machine Learning
 ECE 5424: Introduction to Machine Learning Topics: Ensemble Methods: Bagging, Boosting PAC Learning Readings: Murphy 16.4;; Hastie 16 Stefan Lee Virginia Tech Fighting the bias-variance tradeoff Simple
ECE 5424: Introduction to Machine Learning Topics: Ensemble Methods: Bagging, Boosting PAC Learning Readings: Murphy 16.4;; Hastie 16 Stefan Lee Virginia Tech Fighting the bias-variance tradeoff Simple
ECML PKDD Discovery Challenges 2017
 ECML PKDD Discovery Challenges 2017 Roberto Corizzo 1 and Dino Ienco 2 1 Department of Computer Science, University of Bari Aldo Moro, Bari, Italy roberto.corizzo@uniba.it 2 Irstea, UMR TETIS, Univ. Montpellier,
ECML PKDD Discovery Challenges 2017 Roberto Corizzo 1 and Dino Ienco 2 1 Department of Computer Science, University of Bari Aldo Moro, Bari, Italy roberto.corizzo@uniba.it 2 Irstea, UMR TETIS, Univ. Montpellier,
MS&E 226: Small Data
 MS&E 226: Small Data Lecture 9: Logistic regression (v2) Ramesh Johari ramesh.johari@stanford.edu 1 / 28 Regression methods for binary outcomes 2 / 28 Binary outcomes For the duration of this lecture suppose
MS&E 226: Small Data Lecture 9: Logistic regression (v2) Ramesh Johari ramesh.johari@stanford.edu 1 / 28 Regression methods for binary outcomes 2 / 28 Binary outcomes For the duration of this lecture suppose
Demand and Supply Integration:
 Demand and Supply Integration: The Key to World-Class Demand Forecasting Mark A. Moon FT Press Contents Preface xxi Chapter 1 Demand/Supply Integration 1 the Idea Behind DSI 2 How DSI Is Different from
Demand and Supply Integration: The Key to World-Class Demand Forecasting Mark A. Moon FT Press Contents Preface xxi Chapter 1 Demand/Supply Integration 1 the Idea Behind DSI 2 How DSI Is Different from
David John Gagne II, NCAR
 The Performance Impacts of Machine Learning Design Choices for Gridded Solar Irradiance Forecasting Features work from Evaluating Statistical Learning Configurations for Gridded Solar Irradiance Forecasting,
The Performance Impacts of Machine Learning Design Choices for Gridded Solar Irradiance Forecasting Features work from Evaluating Statistical Learning Configurations for Gridded Solar Irradiance Forecasting,
Figure 1. Time Series Plot of arrivals from Western Europe
 FORECASTING TOURIST ARRIVALS TO SRI LANKA FROM WESTERN EUROPE K. M. U. B. Konarasinghe 1 * 1 Institute of Mathematics & Management, Nugegoda, Sri Lanka INTRODUCTION Sri Lanka was re-emerging after defeating
FORECASTING TOURIST ARRIVALS TO SRI LANKA FROM WESTERN EUROPE K. M. U. B. Konarasinghe 1 * 1 Institute of Mathematics & Management, Nugegoda, Sri Lanka INTRODUCTION Sri Lanka was re-emerging after defeating
Gov 2002: 3. Randomization Inference
 Gov 2002: 3. Randomization Inference Matthew Blackwell September 10, 2015 Where are we? Where are we going? Last week: This week: What can we identify using randomization? Estimators were justified via
Gov 2002: 3. Randomization Inference Matthew Blackwell September 10, 2015 Where are we? Where are we going? Last week: This week: What can we identify using randomization? Estimators were justified via
2.830J / 6.780J / ESD.63J Control of Manufacturing Processes (SMA 6303) Spring 2008
 MIT OpenCourseWare http://ocw.mit.edu 2.830J / 6.780J / ESD.63J Control of Processes (SMA 6303) Spring 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms.
MIT OpenCourseWare http://ocw.mit.edu 2.830J / 6.780J / ESD.63J Control of Processes (SMA 6303) Spring 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms.
Seasonal ARMA-based SPC charts for anomaly detection: Application to emergency department systems
 Seasonal ARMA-based SPC charts for anomaly detection: Application to emergency department systems Item Type Article Authors Kadri, Farid; Harrou, Fouzi; Chaabane, Sondès; Sun, Ying; Tahon, Christian Citation
Seasonal ARMA-based SPC charts for anomaly detection: Application to emergency department systems Item Type Article Authors Kadri, Farid; Harrou, Fouzi; Chaabane, Sondès; Sun, Ying; Tahon, Christian Citation
8. Classifier Ensembles for Changing Environments
 1 8. Classifier Ensembles for Changing Environments 8.1. Streaming data and changing environments. 8.2. Approach 1: Change detection. An ensemble method 8.2. Approach 2: Constant updates. Classifier ensembles
1 8. Classifier Ensembles for Changing Environments 8.1. Streaming data and changing environments. 8.2. Approach 1: Change detection. An ensemble method 8.2. Approach 2: Constant updates. Classifier ensembles
Automatic Singular Spectrum Analysis and Forecasting Michele Trovero, Michael Leonard, and Bruce Elsheimer SAS Institute Inc.
 ABSTRACT Automatic Singular Spectrum Analysis and Forecasting Michele Trovero, Michael Leonard, and Bruce Elsheimer SAS Institute Inc., Cary, NC, USA The singular spectrum analysis (SSA) method of time
ABSTRACT Automatic Singular Spectrum Analysis and Forecasting Michele Trovero, Michael Leonard, and Bruce Elsheimer SAS Institute Inc., Cary, NC, USA The singular spectrum analysis (SSA) method of time
Energy Consumption Anomaly Monitoring Model
 Energy Consumption Anomaly Monitoring Model Lin Chen 1, a, Xiangwei Luo 1, b, Jie Deng 1, c, Yu Jiang 1, d, Bo Wang 1, e, Yao Xiao 1, f 1Chongqing University of Posts and Telecommunications, Chongqing
Energy Consumption Anomaly Monitoring Model Lin Chen 1, a, Xiangwei Luo 1, b, Jie Deng 1, c, Yu Jiang 1, d, Bo Wang 1, e, Yao Xiao 1, f 1Chongqing University of Posts and Telecommunications, Chongqing
Robust and Rapid Adaption for Concept Drift in Software System Anomaly Detection
 Robust and Rapid Adaption for Concept Drift in Software System Anomaly Detection Minghua Ma, Shenglin Zhang, Dan Pei, Xin Huang, Hongwei Dai Department of Computer Science and Technology, Tsinghua University,
Robust and Rapid Adaption for Concept Drift in Software System Anomaly Detection Minghua Ma, Shenglin Zhang, Dan Pei, Xin Huang, Hongwei Dai Department of Computer Science and Technology, Tsinghua University,
Uncertainty. Jayakrishnan Unnikrishnan. CSL June PhD Defense ECE Department
 Decision-Making under Statistical Uncertainty Jayakrishnan Unnikrishnan PhD Defense ECE Department University of Illinois at Urbana-Champaign CSL 141 12 June 2010 Statistical Decision-Making Relevant in
Decision-Making under Statistical Uncertainty Jayakrishnan Unnikrishnan PhD Defense ECE Department University of Illinois at Urbana-Champaign CSL 141 12 June 2010 Statistical Decision-Making Relevant in
Development of System for Supporting Lock Position Adjustment Work for Electric Point Machine
 PAPER Development of System for Supporting Lock Position Adjustment Work for Electric Point Machine Nagateru IWASAWA Satoko RYUO Kunihiro KAWASAKI Akio HADA Telecommunications and Networking Laboratory,
PAPER Development of System for Supporting Lock Position Adjustment Work for Electric Point Machine Nagateru IWASAWA Satoko RYUO Kunihiro KAWASAKI Akio HADA Telecommunications and Networking Laboratory,
The Dayton Power and Light Company Load Profiling Methodology Revised 7/1/2017
 The Dayton Power and Light Company Load Profiling Methodology Revised 7/1/2017 Overview of Methodology Dayton Power and Light (DP&L) load profiles will be used to estimate hourly loads for customers without
The Dayton Power and Light Company Load Profiling Methodology Revised 7/1/2017 Overview of Methodology Dayton Power and Light (DP&L) load profiles will be used to estimate hourly loads for customers without
MULTIVARIATE PATTERN RECOGNITION FOR CHEMOMETRICS. Richard Brereton
 MULTIVARIATE PATTERN RECOGNITION FOR CHEMOMETRICS Richard Brereton r.g.brereton@bris.ac.uk Pattern Recognition Book Chemometrics for Pattern Recognition, Wiley, 2009 Pattern Recognition Pattern Recognition
MULTIVARIATE PATTERN RECOGNITION FOR CHEMOMETRICS Richard Brereton r.g.brereton@bris.ac.uk Pattern Recognition Book Chemometrics for Pattern Recognition, Wiley, 2009 Pattern Recognition Pattern Recognition
Introduction to Statistical Inference
 Structural Health Monitoring Using Statistical Pattern Recognition Introduction to Statistical Inference Presented by Charles R. Farrar, Ph.D., P.E. Outline Introduce statistical decision making for Structural
Structural Health Monitoring Using Statistical Pattern Recognition Introduction to Statistical Inference Presented by Charles R. Farrar, Ph.D., P.E. Outline Introduce statistical decision making for Structural
Evaluation. Andrea Passerini Machine Learning. Evaluation
 Andrea Passerini passerini@disi.unitn.it Machine Learning Basic concepts requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain
Andrea Passerini passerini@disi.unitn.it Machine Learning Basic concepts requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain
Lessons learned from the theory and practice of. change detection. Introduction. Content. Simulated data - One change (Signal and spectral densities)
 Lessons learned from the theory and practice of change detection Simulated data - One change (Signal and spectral densities) - Michèle Basseville - 4 6 8 4 6 8 IRISA / CNRS, Rennes, France michele.basseville@irisa.fr
Lessons learned from the theory and practice of change detection Simulated data - One change (Signal and spectral densities) - Michèle Basseville - 4 6 8 4 6 8 IRISA / CNRS, Rennes, France michele.basseville@irisa.fr
CHAPTER 6 CONCLUSION AND FUTURE SCOPE
 CHAPTER 6 CONCLUSION AND FUTURE SCOPE 146 CHAPTER 6 CONCLUSION AND FUTURE SCOPE 6.1 SUMMARY The first chapter of the thesis highlighted the need of accurate wind forecasting models in order to transform
CHAPTER 6 CONCLUSION AND FUTURE SCOPE 146 CHAPTER 6 CONCLUSION AND FUTURE SCOPE 6.1 SUMMARY The first chapter of the thesis highlighted the need of accurate wind forecasting models in order to transform
Correlative Monitoring for Detection of False Data Injection Attacks in Smart Grids
 Correlative Monitoring for Detection of False Data Injection Attacks in Smart Grids Michael G. Kallitsis, George Michailidis, Samir Tout Merit Network, Inc, University of Michigan, Ann Arbor, Michigan
Correlative Monitoring for Detection of False Data Injection Attacks in Smart Grids Michael G. Kallitsis, George Michailidis, Samir Tout Merit Network, Inc, University of Michigan, Ann Arbor, Michigan
Chapter-1 Introduction
 Modeling of rainfall variability and drought assessment in Sabarmati basin, Gujarat, India Chapter-1 Introduction 1.1 General Many researchers had studied variability of rainfall at spatial as well as
Modeling of rainfall variability and drought assessment in Sabarmati basin, Gujarat, India Chapter-1 Introduction 1.1 General Many researchers had studied variability of rainfall at spatial as well as
