Discrete Principal Component Analysis
|
|
|
- Lionel Kelley
- 6 years ago
- Views:
Transcription
1 Discrete Principal Component Analysis Wray Buntine 1 and Ales Jaulin 2 1 Complex Systems Computation Group (CoSCo), Helsini Institute for Information Technology (HIIT) P.O. Box 9800, FIN HUT, Finland. Wray.Buntine@hiit.fi 2 Department of Knowledge Technologies Jozef Stefan Institute Jamova 39, 1000 Ljubljana, Slovenia jaulin@gmail.com Abstract. This article presents a unified theory for analysis of components in discrete data, and compares the methods with techniques such as independent component analysis (ICA), non-negative matrix factorisation (NMF) and latent Dirichlet allocation (LDA). The main families of algorithms discussed are mean field, Gibbs sampling, and Rao-Blacwellised Gibbs sampling. Applications are presented for voting records from the United States Senate for 2003, and the use of components in subsequent classification. 1 Introduction Principal component analysis (PCA), latent semantic indexing (LSI), and independent component analysis (ICA, see [19]) are ey methods in the statistical engineering toolbox. They have a long history, are used in many different ways, and under different names. They were primarily developed in the engineering community where the notion of a filter is common, and maximum lielihood methods less so. They are usually applied to measurements and real valued data, and used for feature extraction or data summarization. Relatively recently the statistical computing community has become aware of seemingly similar approaches for discrete data that appears under many names: grade of membership (GOM) [31], probabilistic latent semantic indexing (PLSI) [17], non-negative matrix factorisation (NMF) [23], genotype inference using admixtures [29], latent Dirichlet allocation (LDA) [5], multinomial PCA (MPCA) [6], multiple aspect modelling [26], and Gamma-Poisson models (GaP) [9]. We refer to these methods jointly as Discrete PCA (DPCA), and this article provides a unifying model for them. Note also, that it is possible these methods existed in reduced form in other statistical fields perhaps decades earlier. These methods are applied in the social sciences, demographics and medical informatics, genotype inference, text and image analysis, and information Draft paper for the PASCAL Bohinj worshop. Cite as HIIT Technical Report, July 2005.
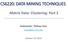
2 retrieval. By far the largest body of applied wor in this area (using citation indexes) is in genotype inference due to the Structure program [29]. A growing body of wor is in text classification and topic modelling (see [16, 8]), and language modelling in information retrieval (see [1, 7, 9]). Here we present in Section 3 a unified theory for analysis of components in discrete data, and compare the methods with related techniques. The main families of algorithms discussed are mean field, Gibbs sampling, and Rao-Blacwellised Gibbs sampling in Section 5. Applications are presented in Section 6 for voting records from the United States Senate for 2003, and the use of components in subsequent classification. 2 Views of DPCA One interpretation of the DPCA methods is that they are a way of approximating large sparse discrete matrices. Suppose we have a 500, 000 documents made up of 1, 500, 000 different words. A document such as a page out of Dr. Zeuss s The Cat in The Hat, is first given as a sequence of words. So, as fast as I could, I went after my net. And I said, With my net I can bet them I bet, I bet, with my net, I can get those Things yet! It can be put in the bag of words representation, where word order is lost, as a list of words and their counts in bracets: so (1) as (2) fast (1) I (7) could (1) went (1) after (1) my (3) net (3) and (1) said (1) with (2) can (2) bet (3) them (1) get (1) those (1) things (1) yet (1). This sparse vector can be represented as a vector in full word space with 1, 499, 981 zeroes and the counts above maing the non-zero entries in the appropriate places. Given a matrix made up of rows of such vectors of non-negative integers dominated by zeros, it is called here a large sparse discrete matrix. Bag of words is a basic representation in information retrieval [2]. The alternative is sequence of words. In DPCA, either representation can be used and the models act the same, up to any word order effects introduced by incremental algorithms. This detail is made precise in subsequent sections. In this section, we argue from various perspectives that large sparse discrete data is not well suited to standard PCA, which is implicitly Gaussian, or ICA methods, which are justified using continuous data. 2.1 DPCA as Approximation In the PCA method, one sees to approximate a large matrix by a product of smaller matrices, by eliminating the lower-order eigenvectors, the least contributing components in the least squares sense. This is represented in Figure 1. If there are I documents, J words and K components, then the matrix on the
3 words components words documents documents (a) (b) Fig. 1. The Matrix View: matrix product (b) approximates sparse discrete matrix (a) left has I J entries and the two matrices on the right have (I + J) K entries. This represents a simplification when K I, J. We can view DPCA methods as seeing the same goal in the case where the matrices are sparse and discrete. When applying PCA to large sparse discrete matrices, interpretation becomes difficult. Negative values appear in the component matrices, so they cannot be interpreted as typical documents in any usual sense. This applies to many other inds of sparse discrete data: low intensity images (such as astronomical images) and verb-noun data used in language models introduced by [27], for instance. DPCA, then, places constraints on the approximating matrices in Figure 1(b) so that they are also non-negative. Also, there are fundamentally two different inds of large sample approximating distributions that dominate discrete statistics: the Poisson and the Gaussian. For instance, a large sample binomial is approximated as a Poisson when the probability is small and as a Gaussian otherwise [30]. Thus in image analysis based on analogue to digital converters, where data is counts, Gaussian errors can sometimes be assumed, but the Poisson should be used if counts are small. DPCA then avoids Gaussian modelling of the data. 2.2 Independent Components Independent component analysis (ICA) was also developed as an alternative to PCA. Hyvänen and Oja [20] argue that PCA methods merely decorrelate data, finding uncorrelated components. ICA then was developed as a way of representing multivariate data with truly independent components. The basic formulation is that a K-dimensional data vector w is a linear function of K independent components represented as a K-dimensional hidden vector l, w = Θl for square matrix Θ. For some univariate density function g(), the independent components are distributed as p(l) = g(l ). This implies p(w Θ) = g ((Θw) ) 1 det(θ) The Fast ICA algorithm [20] can be interpreted as a maximum lielihood approach based on this probability formula. In the sparse discrete case, however,
4 this formulation breas down for the simple reason that w is mostly zeros: the equation can only hold if l and Θ are discrete as well and thus the gradientbased algorithms for ICA cannot be justified. To get around this in practice, when applying ICA to documents [4], word counts are sometimes first turned into TF-IDF scores [2]. To arrive at a formulation more suited to discrete data, we can relax the equality in ICA (i.e., w = Θl) to be an expectation: Exp p(w l) (w) = Θl. We still have independent components, but a more general relationship then exists with the data. Correspondence between ICA and DPCA has been reported in [7, 9]. Note with this expectation relationship, the dimension of l can now be less than the dimension of w, and thus Θ would be a rectangular matrix. For p(w Θ) in the so-called exponential family distributions [15], the expected value of w is referred to as the dual parameter, and it is usually the parameter we now best. For the Bernoulli with probability p, the dual parameter is p, for the Poisson with rate λ, the dual parameter is λ, and for the Gaussian with mean µ, the dual parameter is the mean. Our formulation, then, can be also be interpreted as letting w be exponential family with dual parameter given by (Θl). Our formulation then generalises PCA in the same way that linear models [25] generalises linear regression 3. Note, an alternative has also been presented [13] where w has an exponential family distribution with natural parameters given by (Θl). For the Bernoulli with probability p, the natural parameter is log p/(1 p), for the Poisson with rate λ, the natural parameter is log λ and for the Gaussian with mean µ, the natural parameter is the mean. This formulation generalises PCA in the same way that generalised linear models [25] generalises linear regression. 3 The Basic Model A good introduction to these models from a number of viewpoints is by [5, 9, 7]. Here we present a general model and show its relationship to previous wor. The notation of words, bags and documents will be used throughout, even though other inds of data representations also apply. In machine learning terminology, a word is a feature, a bag is a data vector, and a document is a sample. Notice that the bag collects the words in the document and loses their ordering. The bag is represented as a data vector w. It is now J-dimensional, and the hidden vector l called the components is K-dimensional, where K < J. The term component is used here instead of, for instance, topic. The parameter matrix Θ is J K. 3.1 Bags or Sequences of Words? For a document d represented as a sequence of words, if w = bag(d) is its bagged form, the bag of words, represented as a vector of counts, then for any model M 3 Though it is an artifact of statistical methods in general that linear models are best defined as generalised linear models with a linear lin function.
5 that consistently handles both inds of data p(w M) = ( w j )! j w p(d M). (1) j! Note that some lielihood based methods such as maximum lielihood, some Bayesian methods, and some other fitting methods (for instance, a cross validation technique) use the lielihood as a functional. They tae values or derivatives but otherwise do not further interact with the lielihood. The combinatoric first term on the right hand side of Equation (1) can be dropped here safely because it does not affect the fitting of the parameters for M. Thus for these methods, it is irrelevant whether the data is treated as a bag or as a sequence. This is a general property of multinomial data. Some advanced fitting methods such as Gibbs sampling do not treat the lielihood as a functional. They introduce hidden variables that changes the lielihood, and they may update parts of a document in turn. For these, ordering affects can be incurred by bagging a document, since updates for different parts of the data will now be done in a different order. But the combinatoric first data dependent term in Equation (1) will still be ignored and the algorithms are effectively the same up to the ordering affects. Thus, while we consider bag of words in this article, all the theory equally applies to the sequence of words representation. Implementation can easily address both cases with little change to the algorithms, just to the data handling routines. 3.2 General DPCA The general formulation introduced in Section 2.2 is an unsupervised version of a linear model, and it applies to the bag of words w (the sequence of words version replaces w with d) as w PD D (Θl, α 1 ) such that Exp p(w l) (w) = Θl (2) l PD C (α 2 ), where PD D (, ) is a discrete vector valued probability distribution, PD C ( ) is a continuous vector valued probability density function that may introduce constraints on the domain of l such as non-negativity. The hyper-parameter vectors α 1 and α 2 might also be in use. In the simplest case these two distributions are a product of univariate distributions, so we might have l PD c (α ) for each as in Section 2.2. Various cases of DPCA can now be represented in terms of this format, as given in Table 1. The discrete distribution is the multivariate form of a binomial where an index j {0, 1,..., J 1} is selected according to a J-dimensional probability vector. A multinomial with total count L is the bagged version of L discretes. In the table, non-spec indicates that this aspect of the model was left unspecified. Note that NMF used a cost function formulation, and thus avoided defining lielihood models. PLSI used a weighted lielihood formulation that treated hidden variables without defining a distribution for them.
6 Table 1. DPCA Example Models Name Bagged PD D PD C Constraints NMF [23] yes non-spec non-spec l 0 PLSI [17] no discrete non-spec l 0, l = 1 LDA [5] no discrete Dirichlet l 0, l = 1 MPCA [6] yes multinomial Dirichlet l 0, l = 1 GaP [9] yes Poisson gamma l 0 The formulation of Equation (2) is also called an admixture in the statistical literature [29]. Let θ be the -th row of Θ. The parameters for the distribution of w are formed by maing a weighted sum of the parameters represented by the K vectors θ. This is in contrast with a mixture model [15] which is formed by maing a weighted sum of the probability distributions PD D (θ, α 1 ). 3.3 The Gamma-Poisson Model The general Gamma-Poisson form of DPCA, introduced as GaP [9] is now considered in more detail: Document data is supplied in the form of word counts. The word count for each word type is w j. Let L be the total count, so L = j w j. The document also has hidden component variables l that indicate the amount of the component in the document. In the general case, the l are independent and gamma distributed l Gamma(α, β ) for = 1,..., K. The β affects scaling of the components 4, while α changes the shape of the distribution. Initially the K-dimensional hyper-parameter vectors α and β will be treated as constants, and their estimation will be considered later. There is a general model matrix Θ of size J K with entries θ j, that controls the partition of features amongst each component. This is normalised along rows ( j.θ j, = 1). The data is now Poisson distributed, for each j w j Poisson ((Θl) j ). The hidden or latent variables here are the vector l. The model parameters are the gamma hyper-parameters β and α, and the matrix Θ. The full lielihood for each document then becomes: β α lα 1 e β l ( l θ j, ) wj e ( l θ j,) Γ (α ) w j j! 4 Note conventions for the gamma vary. Sometimes a parameter 1/β is used. Our convention is revealed in Equation (3). (3)
7 To obtain a full posterior for the problem, these terms are multiplied across all documents, and a Dirichlet prior for Θ added in. 3.4 The Dirichlet-Multinomial Model The Dirichlet-multinomial form of DPCA was introduced as MPCA. In this case, the normalised hidden variables m are used, and the total word count L is not modelled. m Dirichlet K (α), w Multinomial(Θm, L) The full lielihood for each document then becomes: ( ) ( ) Cw L Γ m α wj 1 α l θ j, (4) Γ (α ) j where C L w is L choose w. LDA has the multinomial replaced by a discrete, and thus the choose term drops, as per Section 3.1. PLSI is related to LDA but lacs a prior distribution on m. It does not model these hidden variables using probability theory, but instead using a weighted lielihood method [17]. 4 Aspects of the Model Before starting analysis and presenting algorithms, this section discusses some useful aspects of the DPCA model family. 4.1 Correspondence While it was argued in Section 3.4 that LDA and MPCA are essentially the same model, up to ordering effects 5 it is also the case that these methods have a close relationship to GaP. Consider the Gamma-Poisson model. A set of Poisson variables can always be converted into a total Poisson and a multinomial over the set [30]. The set of Poisson distributions on w j then is equivalent to: ( ) ( ) 1 L Poisson l, w Multinomial l Θl, L. Moreover, if the β hyper-parameter is a constant vector, then m = l / l is distributed as a Dirichlet, Dirichlet K (α), and l is distributed independently as a gamma Γ ( α, β). The second distribution above can then be represented as w Multinomial (Θm, L). Note also, that marginalising out l convolves a Poisson and a gamma distribution to produce a Poisson-Gamma distribution for L [3]. Thus, we have proven the following. 5 Note that the algorithm for MPCA borrowed the techniques of LDA directly.
8 Lemma 1. Given a Gamma-Poisson model of Section 3.3 where the β hyperparameter is a constant vector with all entries the same, β, the model is equivalent to a Dirichlet-multinomial model of Section 3.4 where m = l / l, and in addition ( ) L Poisson-Gamma α, β, 1 The implication is that if α is treated as nown, and not estimated from the data, then L is aposteriori independent of m and Θ. In this context, when the β hyper-parameter is a constant vector, LDA, MPCA and GaP are equivalent models ignoring representational issues. If α is estimated from the data in GaP, then the presence of the data L will influence α, and thus the other estimates such as of Θ. In this case, LDA and MPCA will no longer be effectively equivalent to GaP. Note, Canny recommends fixing α and estimating β from the data [9]. To complete the set of correspondences, note that in Section 5.1 it is proven that NMF corresponds to a maximum lielihood version of GaP, and thus it also corresponds to a maximum lielihood version of LDA, MPCA, and PLSI. To relationship is made by normalising the matrices that result. 4.2 A Multivariate Version Another variation of the methods is to allow grouping of the count data. Words can be grouped into separate variable sets. These groups might be title words, body words, and topics in web page analysis or nouns, verbs and adjectives in text analysis. The groups can be treated with separate discrete distributions, as below. The J possible word types in a document are partitioned into G groups B 1,..., B G. The total word counts for each group g is denoted L g = j B g w j. If the vector w is split up into G vectors w g = {w j : j B g }, and the matrix Θ is now normalised by group in each row, so j B g θ j, = 1, then a multivariate version of MPCA is created so that for each group g, ({ } ) Multinomial m θ j, : j B g, L g. w g Fitting and modelling methods for this variation are related to LDA or MPCA, and will not be considered in more detail here. This has the advantage that different inds of words have their own multinomial and the distribution of different inds is ignored. This version is demonstrated subsequently on US Senate voting records, where each multinomial is now a single vote. 4.3 Component Assignments for Words In standard mixture models, each document in a collection is assigned to one (hidden) component. In the DPCA family of models, each word in each document is assigned to one (hidden) component. To see this, we introduce another hidden vector which represents the component assignments for different words.
9 As in Section 3.1, this can be done using a bag of components or a sequence of components representation, and no effective change occurs in the basic models, or in the algorithms so derived. What this does is expand out the term Θl into parts, treating it as if it is the result of marginalising out some hidden variable. Here we just treat the two cases of Gamma-Poisson and Dirichlet-multinomial. We introduce a K-dimensional discrete hidden vector c whose total count is L, the same as the word count. This records the component for each word in a bag of components representation. Thus c gives the number of words in the document appearing in the -th component. Its posterior mean maes an excellent diagnostic and interpretable result. A document from the sports news might have 50 football words, 10 German words, 20 sports fan words and 20 general vocabulary words. So an estimate or expected value for v, is thus used to give the amount of a component in a document, and forms the basis of any posterior analysis and hand inspection of the results. With the new hidden vector, the distributions underlying the Gamma-Poisson model become: l Gamma(α, β ) (5) c Poisson (l ) w j = v j, where v j, Multinomial (θ, c ). The joint lielihood thus becomes, after some rearrangement β α Note that l can be marginalised out, yielding lc +α 1 e (β +1)l θ v j, j, Γ (α ) v j,!. (6) j, Γ (c + α ) Γ (α ) β α (β + 1) c +α j, θ v j, j, v j,! (7) and the posterior mean of l given c is (c + α )/(1 + β ). Thus each c Poisson-Gamma(α, β, 1). For the Dirichlet-multinomial model, a similar reconstruction applies: m Dirichlet K (α) (8) c Multinomial (m, L) w j = v j, where v j, Multinomial (θ, c ). The joint lielihood thus becomes, after some rearrangement ( ) L! Γ α m c +α 1 Γ (α ) j, θ v j, j, v j,!. (9)
10 Again, m can be marginalised out yielding L! Γ ( α ) Γ (L + Γ (c + α ) θ v j, j, α ) Γ (α ) v j,!. (10) j, Note, in both the Gamma-Poisson and Dirichlet-multinomial models each count w j is the sum of counts in the individual components, w j = v j,. The sparse matrix v j, of size J K is thus a hidden variable, with row totals w j given in the data and column totals c. 4.4 Historical Notes The first clear enunciation of the large-scale model in its Poisson form comes from [23], and in its multinomial form from [17] and [29]. The first clear expression of the problem as a hidden variable problem is given by [29], although no doubt earlier versions appear in statistical journals under other names, and perhaps in reduced dimensions (e.g., K = 3). The application of Gibbs is due to [29], and of the mean field method is due to [5], the newer fast Gibbs version to [16]. The mean field method was a significant introduction because of its speed. The relationship between LDA and PLSI and that NMF was a Poisson version of LDA was first pointed out by [6]. The connections to ICA come from [7] and [9]. The general Gamma-Poisson formulation, perhaps the final generalisation to this line of wor, is in [9]. 5 Algorithms Neither of the lielihoods yield to standard EM analysis. For instance, in the lielihood Equation (6) and (9), the hidden variables l/m and v/c are coupled, which is not compatible with the standard EM theory. Most authors point out that EM-lie analysis applies and use EM terminology, and indeed this is the basis of the mean field approach for this problem. For the exponential family, mean field algorithms correspond to an extension of the EM algorithm [6]. EM and maximum lielihood algorithms can be used if one is willing to include the hidden variables in the optimization criterion, as done for instance with the K-means algorithm. Algorithms for this problem follow some general approaches in the statistical computing community: Straight maximum lielihood such as by [23], sometimes expressed as a Kullbac-Leibler divergence, annealed maximum lielihood by [17], best viewed in terms of its clustering precursor such as by [18], Gibbs sampling on v, l/m and Θ in turn using a full probability distribution by [29], or Gibbs sampling on v alone (or equivalently, component assignments for words in the sequence of words representation) after marginalising out l/m and Θ by [16],
11 mean field methods by [5], and expectation propagation (lie so-called cavity methods) by [26]. The maximum lielihood algorithms are not considered here. Their use is always discouraged when a large number of hidden variables exist, and they are mostly simplifications of the algorithms here,. Expectation propagation does not scale, thus it is not considered subsequently either. While other algorithms typically require O(L) or O(K) hidden variables stored per document, expectation propagation requires O(KL). To complete the specification of the problem, a prior is needed for Θ. A Dirichlet prior can be used for each -th component of Θ with J prior parameters γ j, so θ Dirichlet J (γ). 5.1 Mean Field The mean field method was first applied to the sequential variant of the Dirichletmultinomial version of the problem by [5]. In the mean field approach, generally a factored posterior approximation q() is developed for the hidden variables l (or m) and v, and it wors well if it taes the same functional form as the prior probabilities for the hidden variables. The functional form of the approximation can be derived by inspection of the recursive functional forms (see [6] Equation (4)): q(l) 1 Z l exp ( E q(v) {log p (l, v, w Θ, α, β, K)} ) (11) q(v) 1 Z v exp ( E q(l) {log p (l, v, w Θ, α, β, K)} ), where the Z l and Z r are normalising constants. An important computation used during convergence in this approach is a lower bound on the individual document log probabilities, log p (w Θ, α, β, K). This comes naturally out of the mean field algorithm (see [6] Equation (6)). Using the approximation q() defined by the above distributions, the bound is given by Exp q() (log p (l, v, w Θ, α, β, K)) + I(q()). (12) The mean field algorithm applies to the Gamma-Poisson version and the Dirichletmultinomial version. Gamma-Poisson model: So for the Gamma-Poisson case introduce approximation parameters a, b and n j, (normalised as n j, = 1), and then use posterior approximations matching the corresponding model in Equations (5): l Gamma(a, b ) {v j, : = 1,..., K} Multinomial({n j, : = 1,..., K}, w j )
12 for each document. Matching the lielihood these two form with Equation (6), according to the rules of Equations (11), yields the re-write rules for these new parameters: n j, = 1 ( ) θ j, exp log l, (13) Z j a = α + j w j n j,, where b = 1 + β, log l Exp l a.b (log l ) = Ψ 0 (a ) log b, Z j ( ) θ j, exp log l. Here, Ψ 0 () is the digamma function. These equations form the first step of each major cycle, and are performed on each document. The second step is to re-estimate the original model parameters Θ using the posterior approximation by maximising the expectation according to q(l, v) of the log of the full posterior probability Exp q() (log p (l, v, w, Θ, α, β, K)). This incorporates Equation (6) for each document, and a Dirichlet prior term for Θ. Denote the intermediate variables n for the i-th document by adding a (i) subscript, as n j,,(i), and liewise for w j,(i). All these log probability formulas yield linear terms in θ j,, thus one gets θ j, i w j,(i) n j,,(i) + γ j. (14) The lower bound on the log probability of Equation (12), after some simplification and use of the rewrites of Equation (13), becomes 1 log j w j! + ( (α a ) log l log Γ (α )b a ) Γ (a )β α + w j log Z j. (15) j The mean field algorithm for Gamma-Poisson version is given in Figure 2. Dirichlet-multinomial model: For the Dirichlet-multinomial case, the mean field algorithm taes a related form. The approximate posterior is given by: m Dirichlet(a) {v j, : = 1,..., K} multinomial({n j, : = 1,..., K}, w j ) This yields the same style update equations as Equations (13) except that β = 1 n j, = 1 ( ) θ j, exp log m Z j, (16) a = α + j w j n j,,
13 1. Initialise a for each document. The uniform initialisation would be a = ( α + L ) /K. Note n is not stored. 2. Do for each document: (a) Using Equations (13), recompute n and update a in place. (b) Concurrently, compute the log-probability bound of Equation (15), and add to a running total. (c) Concurrently, maintain the sufficient statistics for Θ, the total i w j,(i)n j,,(i) for each j, over documents. (d) Store a for the next cycle and discard n. 3. Update Θ using Equation (14), normalising appropriately. 4. Report the total log-probability bound, and repeat, starting at Step 2. Fig. 2. Mean Field Algorithm for Gamma-Poisson where ( log m Exp m a(log m ) = Ψ 0 (a ) Ψ 0 Z j ( ) θ j, exp log m. a ), Equation (14) is also the same. The lower bound on the individual document log probabilities, log p (w Θ, α, K) now taes the form ( log Cw L Γ ( α ) ) Γ ( a + ) ( (α a ) log m log Γ (α ) ) + Γ (a ) j w j log Z j. (17) The mean field algorithm for Dirichlet-multinomial version is related to that in Figure 2. Equations (16) replace Equations (13), Equation (17) replaces Equation (15), and the initialisation for a should be 0.5, a Jeffreys prior. Complexity: Because Step 2(a) only uses words appearing in a document, the full Step 2 is O(SK) in time complexity where S is the number of words in the full collection. Step 3 is O(JK) in time complexity. Space complexity is O(IK) to store the intermediate parameters a for each document, and the O(2JK) to store Θ and its statistics. In implementation, Step 2 for each document is often quite slow, and thus both a and the document word data can be stored on dis and streamed, thus the main memory complexity is O(2JK). Correspondence with NMF A precursor to the GaP model is non-negative matrix factorisation (NMF) [24], which is based on the matrix approximation paradigm using Kullbac-Leibler divergence. The algorithm itself, converted to the notation used here, is as follows l,(i) l,(i) j θ j, j θ j, w j,(i) θ j,l,(i) θ j, θ j, i l,(i) i l,(i) w j,(i) θ j,l,(i)
14 Notice that the solution is indeterminate up to a factor ψ. Multiple l,(i) by ψ and divide θ j, by ψ and the solution still holds. Thus, without loss of generality, let θ j, be normalised on j, so that j θ j, = 1. Lemma 2. Tae a solution to the NMF equations, and divide θ j, by a factor ψ = j θ j,, and multiply l,(i) by the same factor. This is equivalent to a solution for the following rewrite rules l,(i) l,(i) j θ j, w j,(i) θ j,l,(i) where θ j, is ept normalised on j. θ j, θ j, i l,(i) w j,(i) θ j,l,(i) Proof. First prove the forward direction. Tae the scaled solution to NMF. The NMF equation for l,(i) is equivalent to the equation for l,(i) in the lemma. Tae the NMF equation for θ j, and separately normalise both sides. The i l,(i) term drops out and one is left with the equation for θ j, in the lemma. Now prove the bacward direction. It is sufficient to show that the NMF equations hold for the solution to the rewrite rules in the lemma, since θ j, is already normalised. The NMF equation for l,(i) clearly holds. Assuming the rewrite rules in the lemma hold, then θ j, = = θ j, i l w j,(i),(i) j θ j, i l,(i) θ j,l,(i) w j,(i) θ j, i l w j,(i),(i) i l,(i) j θ j, θ j, i l,(i) = i l,(i) θ j,l,(i) θ j,l,(i) w j,(i) θ j,l,(i) w j,(i) θ j,l,(i) (reorder sum) (apply first rewrite rule) Thus the second equation for NMF holds. The importance of this lemma is in realising that the introduced set of equations are the maximum lielihood version of the mean-field algorithm for the Gamma- Poisson model. That is, NMF where Θ is returned normalised is a maximum w.r.t. Θ and l for the Gamma-Poisson lielihood p(w Θ, l, α = 0, β = 0, K). This can be seen by inspection of the equations at the beginning of this section. Note, including a hidden variable such as l in the lielihood is not correct maximum lielihood, and for clustering yields the K-means algorithm. 5.2 Gibbs Sampling There are two styles of Gibbs sampling that apply.
15 Direct Gibbs sampling: The basic Prichard s style Gibbs sampling wors off Equation (6) or Equation (9) together with a Dirichlet prior for rows of Θ. The hidden variables can easily seen to be conditionally distributed in these equations according to standard probability distributions, in a manner allowing direct application of Gibbs sampling methods. The direct Gibbs algorithm for both versions is given in Figure 3. This Gibbs scheme then re-estimates each 1. For each document, retrieve the last c from store, then (a) Sample the hidden component variables: i. In the Gamma-Poisson case, l Gamma(c +α, 1+β ) independently. ii. In the Dirichlet-multinomial case, l Dirichlet({c + α : }). (b) For each word j in the document with positive count w j, the component counts vector, from Equation (5) and Equation (8), {v j, : = 1,..., K} Multinomial ({ l θ j, l θ j, } ) :, w j. Alternatively, if the sequence-of-components version is to be used, the component for each word can be sampled in turn using the corresponding Bernoulli distribution. (c) Concurrently, record the log-probability i. In the Gamma-Poisson case, p (w l, Θ, α, β, K). ii. In the Dirichlet-multinomial case, p (w m, L, Θ, α, β, K). These represent a reasonable estimate of the lielihood p (w Θ, α, β, K). (d) Concurrently, maintain the sufficient statistics for Θ, the total i w j,(i)n j,,(i) for each j, over documents. (e) Store c for the next cycle and discard v. 2. Using a Dirichlet prior for rows of Θ, and having accumulated all the counts v for each document in sufficient statistics for Θ, then its posterior has rows that are Dirichlet. Sample. 3. Report the total log-probability, and report. Fig. 3. One Major Cycle of Gibbs Algorithm for DPCA of the variables in turn. In implementation, this turns out to correspond to the mean field algorithms, excepting that sampling is done instead of maximisation or expectation. Rao-Blacwellised Gibbs sampling: The Griffiths-Steyvers style Gibbs sampling is a Rao-Blacwellisation (see [11]) of direct Gibbs sampling. It taes the lielihood versions of Equations (7) and (10) multiplied up for each document together with a prior on Θ, and marginalises out Θ. As before, denote the hidden variables v for the i-th document by adding an (i) subscript, as v j,,(i). Then the Gamma-Poisson posterior for documents i 1,..., I, with Θ and l marginalised,
16 and constants dropped becomes: i Γ (c,(i) + α ) (1 + β ) c,(i)+α j, 1 v j,,(i)! j Γ ( γ j + i v ) j,,(i) ( Γ j γ j + (18) i,(i)) c A similar formula applies in the Dirichlet-multinomial version: Γ (c,(i) + α ) i j 1 v j,,(i)! j Γ ( γ j + i v ) j,,(i) ( Γ j γ j + (19) i,(i)) c If sequence of components formulation is used, instead of bag of components, as discussed in Section 3.1, then the v j,,(i)! terms are dropped. Now bag of components sampling would require a sampling scheme for each set {v j,,(i) : 1,..., K}. No such scheme appears to exist, other than doing sequence of components sampling, thus we do that. In one step, change the counts {v j,,(i) : 1,..., K} by one (one is increased and one is decreased) eeping the total w j constant. For instance, if a word has index j and is originally in component 1 but re-sampled to 2, then decrease v j,1,(i) by one and increase v j,2,(i) by one. Do this for every word in the document, thus it is done L times for the document per major sampling cycle. This Rao-Blacwellised Gibbs algorithm for the Gamma-Poisson and Dirichletmultinomial versions, both using sequence of components sampling, is given in Figure 3. Implementation notes: Because Griffiths-Steyvers scheme is a Rao-Blacwellisation of the direct Gibbs sampling, it implies that both l and Θ are effectively reestimated with each sampling step, instead of once after the full pass over documents. This is most effective during early stages, and explains the superiority of the method observed in practice. Moreover, it means only one storage slot for Θ is needed (to store the sufficient statistics), whereas in direct Gibbs two slots are needed (current value plus the sufficient statistics). This represents a major savings in memory. Finally, l and Θ can be sampled at any stage of this process (because their sufficient statistics mae up the totals appearing in the formula), thus Gibbs estimates for them can be made as well during the MCMC process. 5.3 Other Aspects for Estimation and Use A number of other algorithms are needed to put these models into regular use. Component hyper-parameters: The treatment so far has assumed the parameters α and β are given. It is more usual to estimate these parameters with the rest of the estimation tass as done by [5, 9]. This is feasible because the parameters are shared across all the data, unlie the component vectors themselves.
17 1. Maintain the sufficient statistics for Θ, given by v i j,,(i) for each j and, and the individual component assignment for each word in each document. 2. For each document i, retrieve the component assignments for each word then (a) Recompute statistics for l (i) given by c,(i) = v j j,,(i) for each from the individual component assignment for each word. (b) For each word in the document: i. Re-sample the component assignment for the word according to Equation (18) or (19) with the v j,,(i)! terms dropped. If v j,,(i) is the word counts without this word, and c,(i) the corresponding component totals, then this simplifies dramatically (e.g., Γ (x + 1)/Γ (x) = x). A. For the Gamma-Poisson, sample the component proportionally to c,(i) + α γ j + i v j,,(i) 1 + β j γj + i c,(i) B. For the Dirichlet-multinomial, sample the component proportionally to (c,(i) + α ) γj + i v j,,(i) j γj + i c,(i) ii. Concurrently, record the log-probability p (w c, Θ, α, β, K). It represents a reasonable estimate of the lielihood p (w Θ, α, β, K). iii. Concurrently, update the statistics for l/m and Θ. Fig. 4. One Major Cycle of Rao-Blacwellised Gibbs Algorithm for DPCA Estimating the number of components K: A simple scheme exists within importance sampling in Gibbs to estimate the evidence term for a DPCA model, proposed by [7], first proposed in the general sampling context by [10]. One would lie to find the value of K with the highest posterior probability (or, for instance, cross validation score). In popular terms, this could be used to find the right number of components, though in practice and theory such a thing might not exist. Use on new data: A typical use of the model requires performing inference related to a particular document. Suppose, for instance, one wished to estimate how well a snippet of text, a query, matches a document. Our document s components are summarised by the hidden variables m (or l). If the new query is represented by q, then p(q m, Θ, K) is the matching quantity one would lie ideally. Since m is unnown, we must average over it. Various methods have been proposed [26, 7]. Alternative components: Hierarchical components have been suggested [7] as a way of organising an otherwise large flat component space. For instance, the Wiipedia with over half a million documents can easily support the discovery of several hundred components. Dirichlet processes have been developed as an alternative to the K-dimensional component priors in the Dirichlet-
18 multinomial/discrete model [32], although in implementation the effect is to use K-dimensional Dirichlets for a large K and delete low performing components. 6 Applications This section briefly discusses a two applications of the methods. 6.1 Voting Data One type of political science data are the roll calls. There were 459 roll calls in the US Senate in the year For each of those, the vote of every senator was recorded in three ways: Yea, Nay and Not Voting. The outcome of the roll call can be positive (e.g., Bill Passed, Nomination Confirmed) corresponding to Yea, or negative (e.g., Resolution Rejected, Veto Sustained). Hence, the outcome of the vote can be interpreted as the 101st senator, by associating positive outcomes with Yea and negative outcomes with Nay. Application of the Method We can now map the roll call data to the DPCA framewor. For each senator X we form two words, where w X,y implies that X voted Yea, and w X,n implies that X voted Nay. Each roll call can be interpreted as a document containing a single occurrence of some of the available words. The pair of words w X,y, w X,n s then treated as a binomial, so the multivariate formulation of Section 4.2 is used. Priors for Θ were Jeffreys priors, α was (0.1,0.1,...,0.1), and regular Gibbs sampling was used. Special-purpose models are normally used for interpreting roll call data in political science, and they often postulate a model of rational decision maing. Each senator is modelled as a position or an ideal point in a continuous spatial model of preferences [12]. For example, the first dimension often delineates the liberal-conservative preference, and the second region or social issues preference. The proximities between ideal points explain the positive correlations between the senators votes. The ideal points for each senator can be obtained either by optimization, for instance, with the optimal classification algorithm [28], or through Bayesian modelling [12]. Unlie the spatial models, the DPCA interprets the correlations between votes through membership of the senators in similar blocs. Blocs correspond to hidden component variables. Of course, we can spea only of the probability that a particular senator is a member of a particular bloc. The corresponding probability vector is normalized and thus assures that a senator is always a member of one bloc on the average. The outcome of the vote is also a member of several blocs, and we can interpret the membership as a measure of how influential a particular bloc is. Visualization We can analyze two aspects of the DPCA model as applied to the roll call data: we can examine the membership of senators in blocs, and we can
19 examine the actions of blocs for individual issues. The approach to visualization is very similar, as we are visualizing a set of probability vectors. We can use the gray scale to mirror the probabilities ranging from 0 (white) to 1 (blac). As yet, we have not mentioned the choice of K - the number of blocs. Although the number of blocs can be a nuisance variable, such a model is distinctly more difficult to show than one for a fixed K. We obtain the following negative logarithms to the base 2 of the model s lielihood for K = 4, 5, 6, 7, 10: , , , , We see that K = 5 is overwhelmingly selected over all others, with K = 4 being far worse. This means that with our model, we best describe the roll call votes with the existence of five blocs. Fewer blocs do not capture the nuances as well, while more blocs would not yield reliable probability estimates given such an amount of data. Still, those models are too valid to some extent. It is just that for a single visualization we pic the best individual one of them. We will now illustrate the membership of senators in blocs. Each senator is represented with a vertical bar of 5 squares that indicate his or her membership in blocs. We have arranged the senators from left to right using the binary PCA approach of [14]. This ordering attempts to sort senators from the most extreme to the most moderate and to the most extreme again. Figure 5 shows the Democrat senators and Figure 6 the Republicans Boxer (D CA) Harin (D IA) Sarbanes (D MD) Levin (D MI) Leahy (D VT) Reed (D RI) Lautenberg (D NJ) Clinton (D NY) Durbin (D IL) Kennedy (D MA) Miulsi (D MD) Corzine (D NJ) Stabenow (D MI) Kerry (D MA) Schumer (D NY) Edwards (D NC) Murray (D WA) Graham (D FL) Aaa (D HI) Rocefeller (D WV) Cantwell (D WA) Dodd (D CT) Reid (D NV) Byrd (D WV) Daschle (D SD) Kohl (D WI) Lieberman (D CT) Johnson (D SD) Feingold (D WI) Inouye (D HI) Dayton (D MN) Bingaman (D NM) Wyden (D OR) Dorgan (D ND) Feinstein (D CA) Nelson (D FL) Biden (D DE) Hollings (D SC) Conrad (D ND) Pryor (D AR) Jeffords (I VT) Bayh (D IN) Carper (D DE) Lincoln (D AR) Landrieu (D LA) Baucus (D MT) Breaux (D LA) Nelson (D NE) Outcome Miller (D GA) Democrats Fig. 5. Component membership for Democrats We can observe that component 5 is the Democrat majority. It is the strongest overall component, yet quite uninfluential about the outcome. Component 4 is are the moderate Democrats, and they seem distinctly more influential than the Democrats of the majority. Component 3 is a small group of Republican moderates. Component 2 is the Republican majority, the most influential bloc. Component 5 is the Republican minority, not very influential. Component 5 tends to be slightly more extreme than component 4 on the average, but the two components clearly cannot be unambiguously sorted.
20 Chafee (R RI) Snowe (R ME) Collins (R ME) Outcome McCain (R AZ) Specter (R PA) Campbell (R CO) Gregg (R NH) Smith (R OR) DeWine (R OH) Murowsi (R AK) Voinovich (R OH) Hutchison (R TX) Coleman (R MN) Fitzgerald (R IL) Ensign (R NV) Stevens (R AK) Warner (R VA) Lugar (R IN) Sununu (R NH) Graham (R SC) Hagel (R NE) Brownbac (R KS) Shelby (R AL) Roberts (R KS) Domenici (R NM) Bond (R MO) Talent (R MO) Grassley (R IA) Dole (R NC) Santorum (R PA) Hatch (R UT) Bennett (R UT) Lott (R MS) Allen (R VA) Chambliss (R GA) Burns (R MT) Frist (R TN) Inhofe (R OK) Cochran (R MS) Allard (R CO) Alexander (R TN) McConnell (R KY) Sessions (R AL) Bunning (R KY) Cornyn (R TX) Crapo (R ID) Kyl (R AZ) Craig (R ID) Enzi (R WY) Nicles (R OK) Thomas (R WY) Republicans Fig. 6. Component membership for Republicans 7 Classification Experiments We tested the use of MPCA in its role as a feature construction tool, a common use for PCA and ICA, and as a classification tool. For this, we used the 20 newsgroups collection described previously as well as the Reuters collection 6. We employed the SVM light V5.0 [22] classifier with default settings. For classification, we added the class as a distinct multinomial (cf. Section 4.2) for the training data and left it empty for the test data, and then predicted the class value. Note that for performance and accuracy, SVM is the clear winner: as the state of the art optimized discrimination-based system this is to be expected. It is interesting to see how MPCA compares. Each component can be seen as generating a number of words in each document. This number of component-generated words plays the same role in classification as does the number of lexemes in the document in ordinary classification. In both cases, we employed the TF-IDF transformed word and componentgenerated word counts as feature values. Since SVM wors with sparse data matrices, we assumed that a component is not present in a document if the number of words that would a component have generated is less than The components alone do not yield a classification performance that would be competitive with SVM, as the label has no distinguished role in the fitting. However, we may add these component-words in the default bag of words, hoping that the conjunctions of words inherent to each component will help improve the classification performance. For the Reuters collection, we used the ModApte split. For each of the 6 most frequent categories, we performed binary classification. Further results are disclosed in Table 2 7. No major change was observed by adding 50 components to the original set of words. By performing classification on components alone, the results were inferior, even with a large number of components. In fact, with The Reuters-21578, Distribution 1.0 test collection is available from David D. Lewis professional home page, currently: lewis 7 The numbers are percentages, and P/R indicates precision/recall.
21 components, the results were worse than with 200 components, probably because of over-fitting. Therefore, regardless of the number of components, the SVM performance with words cannot be reproduced by component-generated words in this collection. Classifying newsgroup articles into 20 categories proved more suc- Table 2. SVM Classification Results SVM SVM+MPCA CAT ACC. P/R ACC. P/R earn / /97.1 acq / /82.2 moneyfx / /55.9 grain / /74.5 crude / /70.9 trade / /69.8 MPCA (50 comp.) MPCA (200 comp.) CAT ACC. P/R ACC. P/R earn / /94.8 acq / /68.2 moneyfx / /54.7 grain / /53.0 crude / /52.4 trade / /56.0 cessful. We employed two replications of 5-fold cross validation, and we achieved the classification accuracy of 90.7% with 50 additional MPCA components, and 87.1% with SVM alone. Comparing the two confusion matrices, the most frequent mistaes caused by SVM+MPCA beyond those of SVM alone were predicting tal.politics.misc as sci.crypt (26 errors) and tal.religion.misc predicted as sci.electron (25 errors). On the other hand, the components helped better identify alt.atheism and tal.politics.misc, which were misclassified as tal.religion.misc (259 fewer errors) earlier. Also, tal.politics.misc and tal.religion.misc were not misclassified as tal.politics.gun (98 fewer errors). These 50 components were not very successful alone, resulting in 18.5% classification accuracy. By increasing the number of components to 100 and 300, the classification accuracy gradually increases to 25.0% and 34.3%. Therefore, many components are needed for general-purpose classification. From these experiments, we can conclude that components may help with tightly coupled categories that require conjunctions of words (20 newsgroups), but not with the eyword-identifiable categories (Reuters). Judging from the ideas in [21], the components help in two cases: a) when the co-appearance of two words is more informative than sum of informativeness of individual appearance
22 of either word, and b) when the appearance of one word implies the appearance of another word, which does not always appear in the document. 8 Conclusion In this article, we have presented a unifying framewor for various approaches to discrete component analysis, presenting them as a model closely related to ICA. We have shown the relationships between existing approaches here such as NMF, PLSI, LDA, MPCA and GaP, and presented the different algorithms available for two general cases, Gamma-Poisson and Dirichlet-multinomial. For instance NMF corresponds to a maximum lielihood solution for LDA. These methods share many similarities with both PCA and ICA, and are thus useful in a range of feature engineering tass in machine learning and pattern recognition. Acnowledgments The first author s wor was supported by the Academy of Finland under the PROSE Project, by Finnish Technology Development Center (TEKES) under the Search-Ina-Box Project, and by the EU 6th Framewor Programme in the IST Priority under the ALVIS project. The results and experiments reported are only made possible by the extensive document processing environment and set of test collections at the COSCO group, and particularly the information retrieval software Ydin of Sami Perttu. The second author wishes to than his advisor Ivan Brato. The Mpca software used in the experiments was co-developed by a number of authors, reported at the code website 8. References [1] L. Azzopardi, M. Girolami, and K. van Risjbergen. Investigating the relationship between language model perplexity and IR precision-recall measures. In SIGIR 03: Proceedings of the 26th annual international ACM SIGIR conference on Research and development in informaion retrieval, pages , [2] R. Baeza-Yates and B. Ribeiro-Neto. Modern Information Retrieval. Addison Wesley, [3] J.M. Bernardo and A.F.M. Smith. Bayesian Theory. John Wiley, Chichester, [4] E. Bingham, A. Kabán, and M. Girolami. Topic identification in dynamical text by complexity pursuit. Neural Process. Lett., 17(1):69 83, [5] D.M. Blei, A.Y. Ng, and M.I. Jordan. Latent Dirichlet allocation. Journal of Machine Learning Research, 3: , [6] W. Buntine. Variational extensions to EM and multinomial PCA. In ECML 2002, [7] W. Buntine and A. Jaulin. Applying discrete PCA in data analysis. In UAI-2004, Banff, Canada,
A Brief Primer on Ideal Point Estimates
 Joshua D. Clinton Princeton University clinton@princeton.edu January 28, 2008 Really took off with growth of game theory and EITM. Claim: ideal points = player preferences. Widely used in American, Comparative
Joshua D. Clinton Princeton University clinton@princeton.edu January 28, 2008 Really took off with growth of game theory and EITM. Claim: ideal points = player preferences. Widely used in American, Comparative
Variational Extensions to EM and Multinomial PCA
 T. Elomaa et al. (Eds.): ECML, LNAI 2430, pp. 23 34, 2002. c Springer-Verlag Berlin Heidelberg 2002. Variational Extensions to EM and Multinomial PCA Wray Buntine Helsini Inst. of Information Technology
T. Elomaa et al. (Eds.): ECML, LNAI 2430, pp. 23 34, 2002. c Springer-Verlag Berlin Heidelberg 2002. Variational Extensions to EM and Multinomial PCA Wray Buntine Helsini Inst. of Information Technology
Nursing Facilities' Life Safety Standard Survey Results Quarterly Reference Tables
 Nursing Facilities' Life Safety Standard Survey Results Quarterly Reference Tables Table of Contents Table 1: Summary of Life Safety Survey Results by State Table 2: Ten Most Frequently Cited Life Safety
Nursing Facilities' Life Safety Standard Survey Results Quarterly Reference Tables Table of Contents Table 1: Summary of Life Safety Survey Results by State Table 2: Ten Most Frequently Cited Life Safety
Applying Discrete PCA in Data Analysis
 UAI 2004 BUNTINE & JAKULIN 59 Applying Discrete PCA in Data Analysis Wray Buntine Complex Systems Computation Group, Helsini Institute for Information Technology P.O. Box 9800, FIN-02015 HUT, Finland.
UAI 2004 BUNTINE & JAKULIN 59 Applying Discrete PCA in Data Analysis Wray Buntine Complex Systems Computation Group, Helsini Institute for Information Technology P.O. Box 9800, FIN-02015 HUT, Finland.
Lecture 26 Section 8.4. Mon, Oct 13, 2008
 Lecture 26 Section 8.4 Hampden-Sydney College Mon, Oct 13, 2008 Outline 1 2 3 4 Exercise 8.12, page 528. Suppose that 60% of all students at a large university access course information using the Internet.
Lecture 26 Section 8.4 Hampden-Sydney College Mon, Oct 13, 2008 Outline 1 2 3 4 Exercise 8.12, page 528. Suppose that 60% of all students at a large university access course information using the Internet.
Document and Topic Models: plsa and LDA
 Document and Topic Models: plsa and LDA Andrew Levandoski and Jonathan Lobo CS 3750 Advanced Topics in Machine Learning 2 October 2018 Outline Topic Models plsa LSA Model Fitting via EM phits: link analysis
Document and Topic Models: plsa and LDA Andrew Levandoski and Jonathan Lobo CS 3750 Advanced Topics in Machine Learning 2 October 2018 Outline Topic Models plsa LSA Model Fitting via EM phits: link analysis
Learning the Semantic Correlation: An Alternative Way to Gain from Unlabeled Text
 Learning the Semantic Correlation: An Alternative Way to Gain from Unlabeled Text Yi Zhang Machine Learning Department Carnegie Mellon University yizhang1@cs.cmu.edu Jeff Schneider The Robotics Institute
Learning the Semantic Correlation: An Alternative Way to Gain from Unlabeled Text Yi Zhang Machine Learning Department Carnegie Mellon University yizhang1@cs.cmu.edu Jeff Schneider The Robotics Institute
PROBABILISTIC LATENT SEMANTIC ANALYSIS
 PROBABILISTIC LATENT SEMANTIC ANALYSIS Lingjia Deng Revised from slides of Shuguang Wang Outline Review of previous notes PCA/SVD HITS Latent Semantic Analysis Probabilistic Latent Semantic Analysis Applications
PROBABILISTIC LATENT SEMANTIC ANALYSIS Lingjia Deng Revised from slides of Shuguang Wang Outline Review of previous notes PCA/SVD HITS Latent Semantic Analysis Probabilistic Latent Semantic Analysis Applications
Sample Statistics 5021 First Midterm Examination with solutions
 THE UNIVERSITY OF MINNESOTA Statistics 5021 February 12, 2003 Sample First Midterm Examination (with solutions) 1. Baseball pitcher Nolan Ryan played in 20 games or more in the 24 seasons from 1968 through
THE UNIVERSITY OF MINNESOTA Statistics 5021 February 12, 2003 Sample First Midterm Examination (with solutions) 1. Baseball pitcher Nolan Ryan played in 20 games or more in the 24 seasons from 1968 through
Your Galactic Address
 How Big is the Universe? Usually you think of your address as only three or four lines long: your name, street, city, and state. But to address a letter to a friend in a distant galaxy, you have to specify
How Big is the Universe? Usually you think of your address as only three or four lines long: your name, street, city, and state. But to address a letter to a friend in a distant galaxy, you have to specify
Analyzing Severe Weather Data
 Chapter Weather Patterns and Severe Storms Investigation A Analyzing Severe Weather Data Introduction Tornadoes are violent windstorms associated with severe thunderstorms. Meteorologists carefully monitor
Chapter Weather Patterns and Severe Storms Investigation A Analyzing Severe Weather Data Introduction Tornadoes are violent windstorms associated with severe thunderstorms. Meteorologists carefully monitor
Fast Inference and Learning for Modeling Documents with a Deep Boltzmann Machine
 Fast Inference and Learning for Modeling Documents with a Deep Boltzmann Machine Nitish Srivastava nitish@cs.toronto.edu Ruslan Salahutdinov rsalahu@cs.toronto.edu Geoffrey Hinton hinton@cs.toronto.edu
Fast Inference and Learning for Modeling Documents with a Deep Boltzmann Machine Nitish Srivastava nitish@cs.toronto.edu Ruslan Salahutdinov rsalahu@cs.toronto.edu Geoffrey Hinton hinton@cs.toronto.edu
Study Notes on the Latent Dirichlet Allocation
 Study Notes on the Latent Dirichlet Allocation Xugang Ye 1. Model Framework A word is an element of dictionary {1,,}. A document is represented by a sequence of words: =(,, ), {1,,}. A corpus is a collection
Study Notes on the Latent Dirichlet Allocation Xugang Ye 1. Model Framework A word is an element of dictionary {1,,}. A document is represented by a sequence of words: =(,, ), {1,,}. A corpus is a collection
Use your text to define the following term. Use the terms to label the figure below. Define the following term.
 Mapping Our World Section. and Longitude Skim Section of your text. Write three questions that come to mind from reading the headings and the illustration captions.. Responses may include questions about
Mapping Our World Section. and Longitude Skim Section of your text. Write three questions that come to mind from reading the headings and the illustration captions.. Responses may include questions about
Gaussian Mixture Model
 Case Study : Document Retrieval MAP EM, Latent Dirichlet Allocation, Gibbs Sampling Machine Learning/Statistics for Big Data CSE599C/STAT59, University of Washington Emily Fox 0 Emily Fox February 5 th,
Case Study : Document Retrieval MAP EM, Latent Dirichlet Allocation, Gibbs Sampling Machine Learning/Statistics for Big Data CSE599C/STAT59, University of Washington Emily Fox 0 Emily Fox February 5 th,
Information retrieval LSI, plsi and LDA. Jian-Yun Nie
 Information retrieval LSI, plsi and LDA Jian-Yun Nie Basics: Eigenvector, Eigenvalue Ref: http://en.wikipedia.org/wiki/eigenvector For a square matrix A: Ax = λx where x is a vector (eigenvector), and
Information retrieval LSI, plsi and LDA Jian-Yun Nie Basics: Eigenvector, Eigenvalue Ref: http://en.wikipedia.org/wiki/eigenvector For a square matrix A: Ax = λx where x is a vector (eigenvector), and
Forecasting the 2012 Presidential Election from History and the Polls
 Forecasting the 2012 Presidential Election from History and the Polls Drew Linzer Assistant Professor Emory University Department of Political Science Visiting Assistant Professor, 2012-13 Stanford University
Forecasting the 2012 Presidential Election from History and the Polls Drew Linzer Assistant Professor Emory University Department of Political Science Visiting Assistant Professor, 2012-13 Stanford University
DISTRIBUTIONAL SEMANTICS
 COMP90042 LECTURE 4 DISTRIBUTIONAL SEMANTICS LEXICAL DATABASES - PROBLEMS Manually constructed Expensive Human annotation can be biased and noisy Language is dynamic New words: slangs, terminology, etc.
COMP90042 LECTURE 4 DISTRIBUTIONAL SEMANTICS LEXICAL DATABASES - PROBLEMS Manually constructed Expensive Human annotation can be biased and noisy Language is dynamic New words: slangs, terminology, etc.
Understanding Comments Submitted to FCC on Net Neutrality. Kevin (Junhui) Mao, Jing Xia, Dennis (Woncheol) Jeong December 12, 2014
 Understanding Comments Submitted to FCC on Net Neutrality Kevin (Junhui) Mao, Jing Xia, Dennis (Woncheol) Jeong December 12, 2014 Abstract We aim to understand and summarize themes in the 1.65 million
Understanding Comments Submitted to FCC on Net Neutrality Kevin (Junhui) Mao, Jing Xia, Dennis (Woncheol) Jeong December 12, 2014 Abstract We aim to understand and summarize themes in the 1.65 million
Notes on Latent Semantic Analysis
 Notes on Latent Semantic Analysis Costas Boulis 1 Introduction One of the most fundamental problems of information retrieval (IR) is to find all documents (and nothing but those) that are semantically
Notes on Latent Semantic Analysis Costas Boulis 1 Introduction One of the most fundamental problems of information retrieval (IR) is to find all documents (and nothing but those) that are semantically
112th U.S. Senate ACEC Scorecard
 112th U.S. Senate ACEC Scorecard HR 658 FAA Funding Alaska Alabama Arkansas Arizona California Colorado Connecticut S1 Lisa Murkowski R 100% Y Y Y Y Y Y Y Y Y S2 Mark Begich D 89% Y Y Y Y N Y Y Y Y S1
112th U.S. Senate ACEC Scorecard HR 658 FAA Funding Alaska Alabama Arkansas Arizona California Colorado Connecticut S1 Lisa Murkowski R 100% Y Y Y Y Y Y Y Y Y S2 Mark Begich D 89% Y Y Y Y N Y Y Y Y S1
Estimating Dynamic Games of Electoral Competition to Evaluate Term Limits in U.S. Gubernatorial Elections: Online Appendix
 Estimating Dynamic Games of Electoral Competition to Evaluate Term Limits in U.S. Gubernatorial Elections: Online ppendix Holger Sieg University of Pennsylvania and NBER Chamna Yoon Baruch College I. States
Estimating Dynamic Games of Electoral Competition to Evaluate Term Limits in U.S. Gubernatorial Elections: Online ppendix Holger Sieg University of Pennsylvania and NBER Chamna Yoon Baruch College I. States
Latent variable models for discrete data
 Latent variable models for discrete data Jianfei Chen Department of Computer Science and Technology Tsinghua University, Beijing 100084 chris.jianfei.chen@gmail.com Janurary 13, 2014 Murphy, Kevin P. Machine
Latent variable models for discrete data Jianfei Chen Department of Computer Science and Technology Tsinghua University, Beijing 100084 chris.jianfei.chen@gmail.com Janurary 13, 2014 Murphy, Kevin P. Machine
Modeling User Rating Profiles For Collaborative Filtering
 Modeling User Rating Profiles For Collaborative Filtering Benjamin Marlin Department of Computer Science University of Toronto Toronto, ON, M5S 3H5, CANADA marlin@cs.toronto.edu Abstract In this paper
Modeling User Rating Profiles For Collaborative Filtering Benjamin Marlin Department of Computer Science University of Toronto Toronto, ON, M5S 3H5, CANADA marlin@cs.toronto.edu Abstract In this paper
An Introduction to Expectation-Maximization
 An Introduction to Expectation-Maximization Dahua Lin Abstract This notes reviews the basics about the Expectation-Maximization EM) algorithm, a popular approach to perform model estimation of the generative
An Introduction to Expectation-Maximization Dahua Lin Abstract This notes reviews the basics about the Expectation-Maximization EM) algorithm, a popular approach to perform model estimation of the generative
Replicated Softmax: an Undirected Topic Model. Stephen Turner
 Replicated Softmax: an Undirected Topic Model Stephen Turner 1. Introduction 2. Replicated Softmax: A Generative Model of Word Counts 3. Evaluating Replicated Softmax as a Generative Model 4. Experimental
Replicated Softmax: an Undirected Topic Model Stephen Turner 1. Introduction 2. Replicated Softmax: A Generative Model of Word Counts 3. Evaluating Replicated Softmax as a Generative Model 4. Experimental
2006 Supplemental Tax Information for JennisonDryden and Strategic Partners Funds
 2006 Supplemental Information for JennisonDryden and Strategic Partners s We have compiled the following information to help you prepare your 2006 federal and state tax returns: Percentage of income from
2006 Supplemental Information for JennisonDryden and Strategic Partners s We have compiled the following information to help you prepare your 2006 federal and state tax returns: Percentage of income from
Latent Dirichlet Allocation (LDA)
 Latent Dirichlet Allocation (LDA) D. Blei, A. Ng, and M. Jordan. Journal of Machine Learning Research, 3:993-1022, January 2003. Following slides borrowed ant then heavily modified from: Jonathan Huang
Latent Dirichlet Allocation (LDA) D. Blei, A. Ng, and M. Jordan. Journal of Machine Learning Research, 3:993-1022, January 2003. Following slides borrowed ant then heavily modified from: Jonathan Huang
Appendix 5 Summary of State Trademark Registration Provisions (as of July 2016)
 Appendix 5 Summary of State Trademark Registration Provisions (as of July 2016) App. 5-1 Registration Renewal Assignments Dates Term # of of 1st # of Use # of Form Serv. Key & State (Years) Fee Spec. Use
Appendix 5 Summary of State Trademark Registration Provisions (as of July 2016) App. 5-1 Registration Renewal Assignments Dates Term # of of 1st # of Use # of Form Serv. Key & State (Years) Fee Spec. Use
Class business PS is due Wed. Lecture 20 (QPM 2016) Multivariate Regression November 14, / 44
 Multivariate Regression Prof. Jacob M. Montgomery Quantitative Political Methodology (L32 363) November 14, 2016 Lecture 20 (QPM 2016) Multivariate Regression November 14, 2016 1 / 44 Class business PS
Multivariate Regression Prof. Jacob M. Montgomery Quantitative Political Methodology (L32 363) November 14, 2016 Lecture 20 (QPM 2016) Multivariate Regression November 14, 2016 1 / 44 Class business PS
Latent Variable Models and EM algorithm
 Latent Variable Models and EM algorithm SC4/SM4 Data Mining and Machine Learning, Hilary Term 2017 Dino Sejdinovic 3.1 Clustering and Mixture Modelling K-means and hierarchical clustering are non-probabilistic
Latent Variable Models and EM algorithm SC4/SM4 Data Mining and Machine Learning, Hilary Term 2017 Dino Sejdinovic 3.1 Clustering and Mixture Modelling K-means and hierarchical clustering are non-probabilistic
Topic Modelling and Latent Dirichlet Allocation
 Topic Modelling and Latent Dirichlet Allocation Stephen Clark (with thanks to Mark Gales for some of the slides) Lent 2013 Machine Learning for Language Processing: Lecture 7 MPhil in Advanced Computer
Topic Modelling and Latent Dirichlet Allocation Stephen Clark (with thanks to Mark Gales for some of the slides) Lent 2013 Machine Learning for Language Processing: Lecture 7 MPhil in Advanced Computer
Lecture 13 : Variational Inference: Mean Field Approximation
 10-708: Probabilistic Graphical Models 10-708, Spring 2017 Lecture 13 : Variational Inference: Mean Field Approximation Lecturer: Willie Neiswanger Scribes: Xupeng Tong, Minxing Liu 1 Problem Setup 1.1
10-708: Probabilistic Graphical Models 10-708, Spring 2017 Lecture 13 : Variational Inference: Mean Field Approximation Lecturer: Willie Neiswanger Scribes: Xupeng Tong, Minxing Liu 1 Problem Setup 1.1
Introduction to Mathematical Statistics and Its Applications Richard J. Larsen Morris L. Marx Fifth Edition
 Introduction to Mathematical Statistics and Its Applications Richard J. Larsen Morris L. Marx Fifth Edition Pearson Education Limited Edinburgh Gate Harlow Essex CM20 2JE England and Associated Companies
Introduction to Mathematical Statistics and Its Applications Richard J. Larsen Morris L. Marx Fifth Edition Pearson Education Limited Edinburgh Gate Harlow Essex CM20 2JE England and Associated Companies
Kernel Density Topic Models: Visual Topics Without Visual Words
 Kernel Density Topic Models: Visual Topics Without Visual Words Konstantinos Rematas K.U. Leuven ESAT-iMinds krematas@esat.kuleuven.be Mario Fritz Max Planck Institute for Informatics mfrtiz@mpi-inf.mpg.de
Kernel Density Topic Models: Visual Topics Without Visual Words Konstantinos Rematas K.U. Leuven ESAT-iMinds krematas@esat.kuleuven.be Mario Fritz Max Planck Institute for Informatics mfrtiz@mpi-inf.mpg.de
Machine Learning Lecture Notes
 Machine Learning Lecture Notes Predrag Radivojac January 25, 205 Basic Principles of Parameter Estimation In probabilistic modeling, we are typically presented with a set of observations and the objective
Machine Learning Lecture Notes Predrag Radivojac January 25, 205 Basic Principles of Parameter Estimation In probabilistic modeling, we are typically presented with a set of observations and the objective
Bayesian Data Fusion with Gaussian Process Priors : An Application to Protein Fold Recognition
 Bayesian Data Fusion with Gaussian Process Priors : An Application to Protein Fold Recognition Mar Girolami 1 Department of Computing Science University of Glasgow girolami@dcs.gla.ac.u 1 Introduction
Bayesian Data Fusion with Gaussian Process Priors : An Application to Protein Fold Recognition Mar Girolami 1 Department of Computing Science University of Glasgow girolami@dcs.gla.ac.u 1 Introduction
Annual Performance Report: State Assessment Data
 Annual Performance Report: 2005-2006 State Assessment Data Summary Prepared by: Martha Thurlow, Jason Altman, Damien Cormier, and Ross Moen National Center on Educational Outcomes (NCEO) April, 2008 The
Annual Performance Report: 2005-2006 State Assessment Data Summary Prepared by: Martha Thurlow, Jason Altman, Damien Cormier, and Ross Moen National Center on Educational Outcomes (NCEO) April, 2008 The
Topic Modeling: Beyond Bag-of-Words
 University of Cambridge hmw26@cam.ac.uk June 26, 2006 Generative Probabilistic Models of Text Used in text compression, predictive text entry, information retrieval Estimate probability of a word in a
University of Cambridge hmw26@cam.ac.uk June 26, 2006 Generative Probabilistic Models of Text Used in text compression, predictive text entry, information retrieval Estimate probability of a word in a
Multiway Analysis of Bridge Structural Types in the National Bridge Inventory (NBI) A Tensor Decomposition Approach
 Multiway Analysis of Bridge Structural Types in the National Bridge Inventory (NBI) A Tensor Decomposition Approach By Offei A. Adarkwa Nii Attoh-Okine (Ph.D) (IEEE Big Data Conference -10/27/2014) 1 Presentation
Multiway Analysis of Bridge Structural Types in the National Bridge Inventory (NBI) A Tensor Decomposition Approach By Offei A. Adarkwa Nii Attoh-Okine (Ph.D) (IEEE Big Data Conference -10/27/2014) 1 Presentation
Statistical Mechanics of Money, Income, and Wealth
 Statistical Mechanics of Money, Income, and Wealth Victor M. Yakovenko Adrian A. Dragulescu and A. Christian Silva Department of Physics, University of Maryland, College Park, USA http://www2.physics.umd.edu/~yakovenk/econophysics.html
Statistical Mechanics of Money, Income, and Wealth Victor M. Yakovenko Adrian A. Dragulescu and A. Christian Silva Department of Physics, University of Maryland, College Park, USA http://www2.physics.umd.edu/~yakovenk/econophysics.html
Latent Dirichlet Allocation Introduction/Overview
 Latent Dirichlet Allocation Introduction/Overview David Meyer 03.10.2016 David Meyer http://www.1-4-5.net/~dmm/ml/lda_intro.pdf 03.10.2016 Agenda What is Topic Modeling? Parametric vs. Non-Parametric Models
Latent Dirichlet Allocation Introduction/Overview David Meyer 03.10.2016 David Meyer http://www.1-4-5.net/~dmm/ml/lda_intro.pdf 03.10.2016 Agenda What is Topic Modeling? Parametric vs. Non-Parametric Models
Latent Dirichlet Allocation
 Outlines Advanced Artificial Intelligence October 1, 2009 Outlines Part I: Theoretical Background Part II: Application and Results 1 Motive Previous Research Exchangeability 2 Notation and Terminology
Outlines Advanced Artificial Intelligence October 1, 2009 Outlines Part I: Theoretical Background Part II: Application and Results 1 Motive Previous Research Exchangeability 2 Notation and Terminology
Pattern Recognition and Machine Learning
 Christopher M. Bishop Pattern Recognition and Machine Learning ÖSpri inger Contents Preface Mathematical notation Contents vii xi xiii 1 Introduction 1 1.1 Example: Polynomial Curve Fitting 4 1.2 Probability
Christopher M. Bishop Pattern Recognition and Machine Learning ÖSpri inger Contents Preface Mathematical notation Contents vii xi xiii 1 Introduction 1 1.1 Example: Polynomial Curve Fitting 4 1.2 Probability
Language Information Processing, Advanced. Topic Models
 Language Information Processing, Advanced Topic Models mcuturi@i.kyoto-u.ac.jp Kyoto University - LIP, Adv. - 2011 1 Today s talk Continue exploring the representation of text as histogram of words. Objective:
Language Information Processing, Advanced Topic Models mcuturi@i.kyoto-u.ac.jp Kyoto University - LIP, Adv. - 2011 1 Today s talk Continue exploring the representation of text as histogram of words. Objective:
Algorithm-Independent Learning Issues
 Algorithm-Independent Learning Issues Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr CS 551, Spring 2007 c 2007, Selim Aksoy Introduction We have seen many learning
Algorithm-Independent Learning Issues Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr CS 551, Spring 2007 c 2007, Selim Aksoy Introduction We have seen many learning
Evolution Strategies for Optimizing Rectangular Cartograms
 Evolution Strategies for Optimizing Rectangular Cartograms Kevin Buchin 1, Bettina Speckmann 1, and Sander Verdonschot 2 1 TU Eindhoven, 2 Carleton University September 20, 2012 Sander Verdonschot (Carleton
Evolution Strategies for Optimizing Rectangular Cartograms Kevin Buchin 1, Bettina Speckmann 1, and Sander Verdonschot 2 1 TU Eindhoven, 2 Carleton University September 20, 2012 Sander Verdonschot (Carleton
Topic Models and Applications to Short Documents
 Topic Models and Applications to Short Documents Dieu-Thu Le Email: dieuthu.le@unitn.it Trento University April 6, 2011 1 / 43 Outline Introduction Latent Dirichlet Allocation Gibbs Sampling Short Text
Topic Models and Applications to Short Documents Dieu-Thu Le Email: dieuthu.le@unitn.it Trento University April 6, 2011 1 / 43 Outline Introduction Latent Dirichlet Allocation Gibbs Sampling Short Text
Modeling the Score Distributions of Relevant and Non-relevant Documents
 Modeling the Score Distributions of Relevant and Non-relevant Documents Evangelos Kanoulas, Virgil Pavlu, Keshi Dai, and Javed A. Aslam College of Computer and Information Science Northeastern University,
Modeling the Score Distributions of Relevant and Non-relevant Documents Evangelos Kanoulas, Virgil Pavlu, Keshi Dai, and Javed A. Aslam College of Computer and Information Science Northeastern University,
Crouching Dirichlet, Hidden Markov Model: Unsupervised POS Tagging with Context Local Tag Generation
 Crouching Dirichlet, Hidden Markov Model: Unsupervised POS Tagging with Context Local Tag Generation Taesun Moon Katrin Erk and Jason Baldridge Department of Linguistics University of Texas at Austin 1
Crouching Dirichlet, Hidden Markov Model: Unsupervised POS Tagging with Context Local Tag Generation Taesun Moon Katrin Erk and Jason Baldridge Department of Linguistics University of Texas at Austin 1
arxiv: v3 [cs.lg] 18 Mar 2013
![arxiv: v3 [cs.lg] 18 Mar 2013 arxiv: v3 [cs.lg] 18 Mar 2013](/thumbs/72/67390553.jpg) Hierarchical Data Representation Model - Multi-layer NMF arxiv:1301.6316v3 [cs.lg] 18 Mar 2013 Hyun Ah Song Department of Electrical Engineering KAIST Daejeon, 305-701 hyunahsong@kaist.ac.kr Abstract Soo-Young
Hierarchical Data Representation Model - Multi-layer NMF arxiv:1301.6316v3 [cs.lg] 18 Mar 2013 Hyun Ah Song Department of Electrical Engineering KAIST Daejeon, 305-701 hyunahsong@kaist.ac.kr Abstract Soo-Young
Final Exam, Machine Learning, Spring 2009
 Name: Andrew ID: Final Exam, 10701 Machine Learning, Spring 2009 - The exam is open-book, open-notes, no electronics other than calculators. - The maximum possible score on this exam is 100. You have 3
Name: Andrew ID: Final Exam, 10701 Machine Learning, Spring 2009 - The exam is open-book, open-notes, no electronics other than calculators. - The maximum possible score on this exam is 100. You have 3
CS145: INTRODUCTION TO DATA MINING
 CS145: INTRODUCTION TO DATA MINING Text Data: Topic Model Instructor: Yizhou Sun yzsun@cs.ucla.edu December 4, 2017 Methods to be Learnt Vector Data Set Data Sequence Data Text Data Classification Clustering
CS145: INTRODUCTION TO DATA MINING Text Data: Topic Model Instructor: Yizhou Sun yzsun@cs.ucla.edu December 4, 2017 Methods to be Learnt Vector Data Set Data Sequence Data Text Data Classification Clustering
Probabilistic Latent Semantic Analysis
 Probabilistic Latent Semantic Analysis Dan Oneaţă 1 Introduction Probabilistic Latent Semantic Analysis (plsa) is a technique from the category of topic models. Its main goal is to model cooccurrence information
Probabilistic Latent Semantic Analysis Dan Oneaţă 1 Introduction Probabilistic Latent Semantic Analysis (plsa) is a technique from the category of topic models. Its main goal is to model cooccurrence information
Latent Dirichlet Allocation (LDA)
 Latent Dirichlet Allocation (LDA) A review of topic modeling and customer interactions application 3/11/2015 1 Agenda Agenda Items 1 What is topic modeling? Intro Text Mining & Pre-Processing Natural Language
Latent Dirichlet Allocation (LDA) A review of topic modeling and customer interactions application 3/11/2015 1 Agenda Agenda Items 1 What is topic modeling? Intro Text Mining & Pre-Processing Natural Language
CS6220: DATA MINING TECHNIQUES
 CS6220: DATA MINING TECHNIQUES Matrix Data: Clustering: Part 2 Instructor: Yizhou Sun yzsun@ccs.neu.edu October 19, 2014 Methods to Learn Matrix Data Set Data Sequence Data Time Series Graph & Network
CS6220: DATA MINING TECHNIQUES Matrix Data: Clustering: Part 2 Instructor: Yizhou Sun yzsun@ccs.neu.edu October 19, 2014 Methods to Learn Matrix Data Set Data Sequence Data Time Series Graph & Network
A Generalization of Principal Component Analysis to the Exponential Family
 A Generalization of Principal Component Analysis to the Exponential Family Michael Collins Sanjoy Dasgupta Robert E. Schapire AT&T Labs Research 8 Park Avenue, Florham Park, NJ 7932 mcollins, dasgupta,
A Generalization of Principal Component Analysis to the Exponential Family Michael Collins Sanjoy Dasgupta Robert E. Schapire AT&T Labs Research 8 Park Avenue, Florham Park, NJ 7932 mcollins, dasgupta,
Recent Advances in Bayesian Inference Techniques
 Recent Advances in Bayesian Inference Techniques Christopher M. Bishop Microsoft Research, Cambridge, U.K. research.microsoft.com/~cmbishop SIAM Conference on Data Mining, April 2004 Abstract Bayesian
Recent Advances in Bayesian Inference Techniques Christopher M. Bishop Microsoft Research, Cambridge, U.K. research.microsoft.com/~cmbishop SIAM Conference on Data Mining, April 2004 Abstract Bayesian
Estimating Likelihoods for Topic Models
 Estimating Likelihoods for Topic Models Wray Buntine NICTA and Australian National University Locked Bag 8001, Canberra, 2601, ACT Australia wray.buntine@nicta.com.au Abstract. Topic models are a discrete
Estimating Likelihoods for Topic Models Wray Buntine NICTA and Australian National University Locked Bag 8001, Canberra, 2601, ACT Australia wray.buntine@nicta.com.au Abstract. Topic models are a discrete
Gaussian Models
 Gaussian Models ddebarr@uw.edu 2016-04-28 Agenda Introduction Gaussian Discriminant Analysis Inference Linear Gaussian Systems The Wishart Distribution Inferring Parameters Introduction Gaussian Density
Gaussian Models ddebarr@uw.edu 2016-04-28 Agenda Introduction Gaussian Discriminant Analysis Inference Linear Gaussian Systems The Wishart Distribution Inferring Parameters Introduction Gaussian Density
Bayesian Approach 2. CSC412 Probabilistic Learning & Reasoning
 CSC412 Probabilistic Learning & Reasoning Lecture 12: Bayesian Parameter Estimation February 27, 2006 Sam Roweis Bayesian Approach 2 The Bayesian programme (after Rev. Thomas Bayes) treats all unnown quantities
CSC412 Probabilistic Learning & Reasoning Lecture 12: Bayesian Parameter Estimation February 27, 2006 Sam Roweis Bayesian Approach 2 The Bayesian programme (after Rev. Thomas Bayes) treats all unnown quantities
DEPARTMENT OF COMPUTER SCIENCE Autumn Semester MACHINE LEARNING AND ADAPTIVE INTELLIGENCE
 Data Provided: None DEPARTMENT OF COMPUTER SCIENCE Autumn Semester 203 204 MACHINE LEARNING AND ADAPTIVE INTELLIGENCE 2 hours Answer THREE of the four questions. All questions carry equal weight. Figures
Data Provided: None DEPARTMENT OF COMPUTER SCIENCE Autumn Semester 203 204 MACHINE LEARNING AND ADAPTIVE INTELLIGENCE 2 hours Answer THREE of the four questions. All questions carry equal weight. Figures
PATTERN CLASSIFICATION
 PATTERN CLASSIFICATION Second Edition Richard O. Duda Peter E. Hart David G. Stork A Wiley-lnterscience Publication JOHN WILEY & SONS, INC. New York Chichester Weinheim Brisbane Singapore Toronto CONTENTS
PATTERN CLASSIFICATION Second Edition Richard O. Duda Peter E. Hart David G. Stork A Wiley-lnterscience Publication JOHN WILEY & SONS, INC. New York Chichester Weinheim Brisbane Singapore Toronto CONTENTS
Topic Models. Brandon Malone. February 20, Latent Dirichlet Allocation Success Stories Wrap-up
 Much of this material is adapted from Blei 2003. Many of the images were taken from the Internet February 20, 2014 Suppose we have a large number of books. Each is about several unknown topics. How can
Much of this material is adapted from Blei 2003. Many of the images were taken from the Internet February 20, 2014 Suppose we have a large number of books. Each is about several unknown topics. How can
Stat 542: Item Response Theory Modeling Using The Extended Rank Likelihood
 Stat 542: Item Response Theory Modeling Using The Extended Rank Likelihood Jonathan Gruhl March 18, 2010 1 Introduction Researchers commonly apply item response theory (IRT) models to binary and ordinal
Stat 542: Item Response Theory Modeling Using The Extended Rank Likelihood Jonathan Gruhl March 18, 2010 1 Introduction Researchers commonly apply item response theory (IRT) models to binary and ordinal
Bayesian Inference: Principles and Practice 3. Sparse Bayesian Models and the Relevance Vector Machine
 Bayesian Inference: Principles and Practice 3. Sparse Bayesian Models and the Relevance Vector Machine Mike Tipping Gaussian prior Marginal prior: single α Independent α Cambridge, UK Lecture 3: Overview
Bayesian Inference: Principles and Practice 3. Sparse Bayesian Models and the Relevance Vector Machine Mike Tipping Gaussian prior Marginal prior: single α Independent α Cambridge, UK Lecture 3: Overview
A Unified Posterior Regularized Topic Model with Maximum Margin for Learning-to-Rank
 A Unified Posterior Regularized Topic Model with Maximum Margin for Learning-to-Rank Shoaib Jameel Shoaib Jameel 1, Wai Lam 2, Steven Schockaert 1, and Lidong Bing 3 1 School of Computer Science and Informatics,
A Unified Posterior Regularized Topic Model with Maximum Margin for Learning-to-Rank Shoaib Jameel Shoaib Jameel 1, Wai Lam 2, Steven Schockaert 1, and Lidong Bing 3 1 School of Computer Science and Informatics,
UNIVERSITY of PENNSYLVANIA CIS 520: Machine Learning Final, Fall 2013
 UNIVERSITY of PENNSYLVANIA CIS 520: Machine Learning Final, Fall 2013 Exam policy: This exam allows two one-page, two-sided cheat sheets; No other materials. Time: 2 hours. Be sure to write your name and
UNIVERSITY of PENNSYLVANIA CIS 520: Machine Learning Final, Fall 2013 Exam policy: This exam allows two one-page, two-sided cheat sheets; No other materials. Time: 2 hours. Be sure to write your name and
Advanced Machine Learning & Perception
 Advanced Machine Learning & Perception Instructor: Tony Jebara Topic 6 Standard Kernels Unusual Input Spaces for Kernels String Kernels Probabilistic Kernels Fisher Kernels Probability Product Kernels
Advanced Machine Learning & Perception Instructor: Tony Jebara Topic 6 Standard Kernels Unusual Input Spaces for Kernels String Kernels Probabilistic Kernels Fisher Kernels Probability Product Kernels
Augmented Statistical Models for Speech Recognition
 Augmented Statistical Models for Speech Recognition Mark Gales & Martin Layton 31 August 2005 Trajectory Models For Speech Processing Workshop Overview Dependency Modelling in Speech Recognition: latent
Augmented Statistical Models for Speech Recognition Mark Gales & Martin Layton 31 August 2005 Trajectory Models For Speech Processing Workshop Overview Dependency Modelling in Speech Recognition: latent
Parametric Test. Multiple Linear Regression Spatial Application I: State Homicide Rates Equations taken from Zar, 1984.
 Multiple Linear Regression Spatial Application I: State Homicide Rates Equations taken from Zar, 984. y ˆ = a + b x + b 2 x 2K + b n x n where n is the number of variables Example: In an earlier bivariate
Multiple Linear Regression Spatial Application I: State Homicide Rates Equations taken from Zar, 984. y ˆ = a + b x + b 2 x 2K + b n x n where n is the number of variables Example: In an earlier bivariate
2 Inference for Multinomial Distribution
 Markov Chain Monte Carlo Methods Part III: Statistical Concepts By K.B.Athreya, Mohan Delampady and T.Krishnan 1 Introduction In parts I and II of this series it was shown how Markov chain Monte Carlo
Markov Chain Monte Carlo Methods Part III: Statistical Concepts By K.B.Athreya, Mohan Delampady and T.Krishnan 1 Introduction In parts I and II of this series it was shown how Markov chain Monte Carlo
CS534 Machine Learning - Spring Final Exam
 CS534 Machine Learning - Spring 2013 Final Exam Name: You have 110 minutes. There are 6 questions (8 pages including cover page). If you get stuck on one question, move on to others and come back to the
CS534 Machine Learning - Spring 2013 Final Exam Name: You have 110 minutes. There are 6 questions (8 pages including cover page). If you get stuck on one question, move on to others and come back to the
Prediction of Citations for Academic Papers
 000 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050
000 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050
Factor Analysis (10/2/13)
 STA561: Probabilistic machine learning Factor Analysis (10/2/13) Lecturer: Barbara Engelhardt Scribes: Li Zhu, Fan Li, Ni Guan Factor Analysis Factor analysis is related to the mixture models we have studied.
STA561: Probabilistic machine learning Factor Analysis (10/2/13) Lecturer: Barbara Engelhardt Scribes: Li Zhu, Fan Li, Ni Guan Factor Analysis Factor analysis is related to the mixture models we have studied.
Multi-faceted Learning for Web Taxonomies
 Pp. 52 60 in Second Workshop on Semantic Web Mining, edited by B. Berendt, A. Hotho and G. Stumme. KD-Net, 2002. Multi-faceted Learning for Web Taxonomies Wray Buntine and Henry Tirri Helsinki Inst. of
Pp. 52 60 in Second Workshop on Semantic Web Mining, edited by B. Berendt, A. Hotho and G. Stumme. KD-Net, 2002. Multi-faceted Learning for Web Taxonomies Wray Buntine and Henry Tirri Helsinki Inst. of
Bayesian Nonparametrics for Speech and Signal Processing
 Bayesian Nonparametrics for Speech and Signal Processing Michael I. Jordan University of California, Berkeley June 28, 2011 Acknowledgments: Emily Fox, Erik Sudderth, Yee Whye Teh, and Romain Thibaux Computer
Bayesian Nonparametrics for Speech and Signal Processing Michael I. Jordan University of California, Berkeley June 28, 2011 Acknowledgments: Emily Fox, Erik Sudderth, Yee Whye Teh, and Romain Thibaux Computer
A graph contains a set of nodes (vertices) connected by links (edges or arcs)
 BOLTZMANN MACHINES Generative Models Graphical Models A graph contains a set of nodes (vertices) connected by links (edges or arcs) In a probabilistic graphical model, each node represents a random variable,
BOLTZMANN MACHINES Generative Models Graphical Models A graph contains a set of nodes (vertices) connected by links (edges or arcs) In a probabilistic graphical model, each node represents a random variable,
13: Variational inference II
 10-708: Probabilistic Graphical Models, Spring 2015 13: Variational inference II Lecturer: Eric P. Xing Scribes: Ronghuo Zheng, Zhiting Hu, Yuntian Deng 1 Introduction We started to talk about variational
10-708: Probabilistic Graphical Models, Spring 2015 13: Variational inference II Lecturer: Eric P. Xing Scribes: Ronghuo Zheng, Zhiting Hu, Yuntian Deng 1 Introduction We started to talk about variational
Lecture 19, November 19, 2012
 Machine Learning 0-70/5-78, Fall 0 Latent Space Analysis SVD and Topic Models Eric Xing Lecture 9, November 9, 0 Reading: Tutorial on Topic Model @ ACL Eric Xing @ CMU, 006-0 We are inundated with data
Machine Learning 0-70/5-78, Fall 0 Latent Space Analysis SVD and Topic Models Eric Xing Lecture 9, November 9, 0 Reading: Tutorial on Topic Model @ ACL Eric Xing @ CMU, 006-0 We are inundated with data
Topic Models. Charles Elkan November 20, 2008
 Topic Models Charles Elan elan@cs.ucsd.edu November 20, 2008 Suppose that we have a collection of documents, and we want to find an organization for these, i.e. we want to do unsupervised learning. One
Topic Models Charles Elan elan@cs.ucsd.edu November 20, 2008 Suppose that we have a collection of documents, and we want to find an organization for these, i.e. we want to do unsupervised learning. One
Click Prediction and Preference Ranking of RSS Feeds
 Click Prediction and Preference Ranking of RSS Feeds 1 Introduction December 11, 2009 Steven Wu RSS (Really Simple Syndication) is a family of data formats used to publish frequently updated works. RSS
Click Prediction and Preference Ranking of RSS Feeds 1 Introduction December 11, 2009 Steven Wu RSS (Really Simple Syndication) is a family of data formats used to publish frequently updated works. RSS
19 : Bayesian Nonparametrics: The Indian Buffet Process. 1 Latent Variable Models and the Indian Buffet Process
 10-708: Probabilistic Graphical Models, Spring 2015 19 : Bayesian Nonparametrics: The Indian Buffet Process Lecturer: Avinava Dubey Scribes: Rishav Das, Adam Brodie, and Hemank Lamba 1 Latent Variable
10-708: Probabilistic Graphical Models, Spring 2015 19 : Bayesian Nonparametrics: The Indian Buffet Process Lecturer: Avinava Dubey Scribes: Rishav Das, Adam Brodie, and Hemank Lamba 1 Latent Variable
Collaborative topic models: motivations cont
 Collaborative topic models: motivations cont Two topics: machine learning social network analysis Two people: " boy Two articles: article A! girl article B Preferences: The boy likes A and B --- no problem.
Collaborative topic models: motivations cont Two topics: machine learning social network analysis Two people: " boy Two articles: article A! girl article B Preferences: The boy likes A and B --- no problem.
FERMENTATION BATCH PROCESS MONITORING BY STEP-BY-STEP ADAPTIVE MPCA. Ning He, Lei Xie, Shu-qing Wang, Jian-ming Zhang
 FERMENTATION BATCH PROCESS MONITORING BY STEP-BY-STEP ADAPTIVE MPCA Ning He Lei Xie Shu-qing Wang ian-ming Zhang National ey Laboratory of Industrial Control Technology Zhejiang University Hangzhou 3007
FERMENTATION BATCH PROCESS MONITORING BY STEP-BY-STEP ADAPTIVE MPCA Ning He Lei Xie Shu-qing Wang ian-ming Zhang National ey Laboratory of Industrial Control Technology Zhejiang University Hangzhou 3007
Text Mining for Economics and Finance Latent Dirichlet Allocation
 Text Mining for Economics and Finance Latent Dirichlet Allocation Stephen Hansen Text Mining Lecture 5 1 / 45 Introduction Recall we are interested in mixed-membership modeling, but that the plsi model
Text Mining for Economics and Finance Latent Dirichlet Allocation Stephen Hansen Text Mining Lecture 5 1 / 45 Introduction Recall we are interested in mixed-membership modeling, but that the plsi model
EXST 7015 Fall 2014 Lab 08: Polynomial Regression
 EXST 7015 Fall 2014 Lab 08: Polynomial Regression OBJECTIVES Polynomial regression is a statistical modeling technique to fit the curvilinear data that either shows a maximum or a minimum in the curve,
EXST 7015 Fall 2014 Lab 08: Polynomial Regression OBJECTIVES Polynomial regression is a statistical modeling technique to fit the curvilinear data that either shows a maximum or a minimum in the curve,
Bayesian Methods for Machine Learning
 Bayesian Methods for Machine Learning CS 584: Big Data Analytics Material adapted from Radford Neal s tutorial (http://ftp.cs.utoronto.ca/pub/radford/bayes-tut.pdf), Zoubin Ghahramni (http://hunch.net/~coms-4771/zoubin_ghahramani_bayesian_learning.pdf),
Bayesian Methods for Machine Learning CS 584: Big Data Analytics Material adapted from Radford Neal s tutorial (http://ftp.cs.utoronto.ca/pub/radford/bayes-tut.pdf), Zoubin Ghahramni (http://hunch.net/~coms-4771/zoubin_ghahramani_bayesian_learning.pdf),
STA 4273H: Statistical Machine Learning
 STA 4273H: Statistical Machine Learning Russ Salakhutdinov Department of Statistics! rsalakhu@utstat.toronto.edu! http://www.utstat.utoronto.ca/~rsalakhu/ Sidney Smith Hall, Room 6002 Lecture 11 Project
STA 4273H: Statistical Machine Learning Russ Salakhutdinov Department of Statistics! rsalakhu@utstat.toronto.edu! http://www.utstat.utoronto.ca/~rsalakhu/ Sidney Smith Hall, Room 6002 Lecture 11 Project
Two Useful Bounds for Variational Inference
 Two Useful Bounds for Variational Inference John Paisley Department of Computer Science Princeton University, Princeton, NJ jpaisley@princeton.edu Abstract We review and derive two lower bounds on the
Two Useful Bounds for Variational Inference John Paisley Department of Computer Science Princeton University, Princeton, NJ jpaisley@princeton.edu Abstract We review and derive two lower bounds on the
Chris Bishop s PRML Ch. 8: Graphical Models
 Chris Bishop s PRML Ch. 8: Graphical Models January 24, 2008 Introduction Visualize the structure of a probabilistic model Design and motivate new models Insights into the model s properties, in particular
Chris Bishop s PRML Ch. 8: Graphical Models January 24, 2008 Introduction Visualize the structure of a probabilistic model Design and motivate new models Insights into the model s properties, in particular
Sparse vectors recap. ANLP Lecture 22 Lexical Semantics with Dense Vectors. Before density, another approach to normalisation.
 ANLP Lecture 22 Lexical Semantics with Dense Vectors Henry S. Thompson Based on slides by Jurafsky & Martin, some via Dorota Glowacka 5 November 2018 Previous lectures: Sparse vectors recap How to represent
ANLP Lecture 22 Lexical Semantics with Dense Vectors Henry S. Thompson Based on slides by Jurafsky & Martin, some via Dorota Glowacka 5 November 2018 Previous lectures: Sparse vectors recap How to represent
ANLP Lecture 22 Lexical Semantics with Dense Vectors
 ANLP Lecture 22 Lexical Semantics with Dense Vectors Henry S. Thompson Based on slides by Jurafsky & Martin, some via Dorota Glowacka 5 November 2018 Henry S. Thompson ANLP Lecture 22 5 November 2018 Previous
ANLP Lecture 22 Lexical Semantics with Dense Vectors Henry S. Thompson Based on slides by Jurafsky & Martin, some via Dorota Glowacka 5 November 2018 Henry S. Thompson ANLP Lecture 22 5 November 2018 Previous
Pattern Recognition and Machine Learning. Learning and Evaluation of Pattern Recognition Processes
 Pattern Recognition and Machine Learning James L. Crowley ENSIMAG 3 - MMIS Fall Semester 2016 Lesson 1 5 October 2016 Learning and Evaluation of Pattern Recognition Processes Outline Notation...2 1. The
Pattern Recognition and Machine Learning James L. Crowley ENSIMAG 3 - MMIS Fall Semester 2016 Lesson 1 5 October 2016 Learning and Evaluation of Pattern Recognition Processes Outline Notation...2 1. The
Linear & nonlinear classifiers
 Linear & nonlinear classifiers Machine Learning Hamid Beigy Sharif University of Technology Fall 1394 Hamid Beigy (Sharif University of Technology) Linear & nonlinear classifiers Fall 1394 1 / 34 Table
Linear & nonlinear classifiers Machine Learning Hamid Beigy Sharif University of Technology Fall 1394 Hamid Beigy (Sharif University of Technology) Linear & nonlinear classifiers Fall 1394 1 / 34 Table
Manning & Schuetze, FSNLP, (c)
 page 554 554 15 Topics in Information Retrieval co-occurrence Latent Semantic Indexing Term 1 Term 2 Term 3 Term 4 Query user interface Document 1 user interface HCI interaction Document 2 HCI interaction
page 554 554 15 Topics in Information Retrieval co-occurrence Latent Semantic Indexing Term 1 Term 2 Term 3 Term 4 Query user interface Document 1 user interface HCI interaction Document 2 HCI interaction
Data Visualization (DSC 530/CIS )
 Data Visualization (DSC 530/CIS 602-01) Tables Dr. David Koop Visualization of Tables Items and attributes For now, attributes are not known to be positions Keys and values - key is an independent attribute
Data Visualization (DSC 530/CIS 602-01) Tables Dr. David Koop Visualization of Tables Items and attributes For now, attributes are not known to be positions Keys and values - key is an independent attribute
Content-based Recommendation
 Content-based Recommendation Suthee Chaidaroon June 13, 2016 Contents 1 Introduction 1 1.1 Matrix Factorization......................... 2 2 slda 2 2.1 Model................................. 3 3 flda 3
Content-based Recommendation Suthee Chaidaroon June 13, 2016 Contents 1 Introduction 1 1.1 Matrix Factorization......................... 2 2 slda 2 2.1 Model................................. 3 3 flda 3
Inference and estimation in probabilistic time series models
 1 Inference and estimation in probabilistic time series models David Barber, A Taylan Cemgil and Silvia Chiappa 11 Time series The term time series refers to data that can be represented as a sequence
1 Inference and estimation in probabilistic time series models David Barber, A Taylan Cemgil and Silvia Chiappa 11 Time series The term time series refers to data that can be represented as a sequence
Cluster Analysis. Part of the Michigan Prosperity Initiative
 Cluster Analysis Part of the Michigan Prosperity Initiative 6/17/2010 Land Policy Institute Contributors Dr. Soji Adelaja, Director Jason Ball, Visiting Academic Specialist Jonathon Baird, Research Assistant
Cluster Analysis Part of the Michigan Prosperity Initiative 6/17/2010 Land Policy Institute Contributors Dr. Soji Adelaja, Director Jason Ball, Visiting Academic Specialist Jonathon Baird, Research Assistant
