KCV Kalyanarama Sesha Sayee and Anurag Kumar
|
|
|
- Sibyl Smith
- 6 years ago
- Views:
Transcription
1 Adaptive Algorithms for Admission of Elastic Sessions in the Internet KCV Kalyanarama Sesha Sayee and Anurag Kumar Abstract In the Internet, the majority of the traffic consists of elastic transfers. Users of elastic applications are generally not sensitive to the end-to-end delay of each packet, but to the time necessary to transfer an entire file, which depends on the number of such flows sharing the network bandwidth. In this paper we propose algorithms for blocking of new flows during overload conditions as a means to achieve a transfer throughput target. We study bandwidth sharing of elastic flows at a bottleneck link. We propose two control techniques, namely, Occupancy Limit (OLC) and Connection Limit (CLC) to implement admission control. We make the observation that by appropriate choice of parameters these controls yield the same performance. We then select OLC to implement admission control as it has implementation advantage over CLC. We propose some estimation based self-tuning algorithms for adaptively determining the connection blocking probabilities. Simulations are used to demonstrate the efficacy of these control algorithms. I. INTRODUCTION The bulk of the traffic in the Internet is due to the transfer of files between computers; such file transfers are generated by application protocols such as ftp and http. Such transfers are elastic in the sense that sources can adapt to the time varying available bandwidth in the network. For an elastic flow, quality of service is manifested essentially by the time it takes to complete the document transfer. This time depends both on the way bandwidth is shared and on the random fluctuations in the number of flows in progress as flows begin and end. Though there are no intrinsic temporal characteristics associated with elastic applications, it is widely accepted that elastic flows do not provide any utility once their resource share falls below some minimum acceptable value. This situation results in lot of ineffective traffic using the network. World wide web users often interpret bad throughputs as lost connections and hence terminate them thereby wasting the resources used in the partial transfer of the document. Also, the reduced bandwidth share increases delays experienced by packets at the gateways resulting in application timeout, and packet retransmissions. This adds to the ineffective traffic carried by the network. To ensure quality of service in case of traffic overload it appears necessary additionally to employ admission control ([3], [4], [8], and []) with flow blocking appearing as a more acceptable quality degradation than diminishing throughput. Instead of accepting a fresh connection in the presence of overload conditions, thus reducing the throughput of ongoing connections, it is better to reject new connections. In the rest of the paper we consider a bottleneck link shared by elastic traffic and then study various ways of implementing admission Department of Electrical Communication Engineering, Indian Institute of Science, Bangalore-56002, India. sayee, anurag@ece.iisc.ernet.in control to achieve a target performance. server server Internet II. OUTLINE OF PAPER ISP s leased line Local ISP ISP s controller Fig.. A model for a small Internet service provider (ISP) client client In Section III we introduce the notation to be used in this paper. In Section IV we describe the basic model that we propose to study and discuss ideal bandwidth sharing and its Processor Sharing model. Then we introduce a performance measure for bandwidth sharing known as Average Bandwidth Share. In Section V we look at the choice of blocking new sessions and then study how blocking affects the aforementioned performance measure. Toward this we propose two control strategies, namely, Occupancy Limit (OLC) and Connection Limit (CLC). Finally, in section VI, we come up with a few adaptive algorithms that implement the OLC strategy. Section VII provides some concluding remarks and then we briefly touch upon the users tendency of retrying their rejected connection requests and give a pointer to some work done by the authors on this problem. III. NOTATION The following notation will be used in the rest of the paper. ffl = the arrival rate of transfers ffl N (t) = number of ongoing transfers as a function of time ffl X k = service requirement of k th transfer (data units), assumed to be i.i.d. r.vs with X denoting the general r.v., with mean E(X) ffl W k = transfer completion (sojourn) time of the k th transfer ffl C = bottleneck link capacity ffl = the link utilization = E(X) C IV. THE MODEL AND A PERFORMANCE MEASURE The clients generate file transfer requests (see Fig. ). After the requests reach the server, we can view the files to be queued at the server, waiting as they are gradually transferred to the clients. Assuming a very high speed Internet backbone, we can see that the ISP s leased line forms the bottleneck link. Then effectively files get queued at the bottleneck link. With ideal bandwidth sharing, when there are n
2 files, each file transfers its packets at th of the link rate. The n network link carries the superposition of these rate controlled flows from each file transfer. Thus, considering a fluid model, we can model the file transfer processes, with ideal bandwidth sharing, by a processor sharing (PS) queue model. The PS model assumes ideal bandwidth sharing, and does not explicitly model the crude manner in which TCP attempts to adaptively share the link bandwidth. However ([2]), for small delay-bandwidth product, the processor sharing model captures the TCP performance quite well. As delay-bandwidth product increases the quality of the processor sharing model approximation becomes poor. The PS model needs to be modified to capture large delay-bandwidth products [5], [6], [7] and [3]. For large round trip times(rtt) the modifications proposed in ([]) can be used to model N (t). Since the instantaneous bandwidth available to a connection depends on the number of active flows, and because of random arrivals and departures, the instantaneous throughput experienced by a user is time varying in a random manner. Formally, per session throughput T W is defined as the mean throughput that an individual session gets, i.e., T W = P n lim n! Xk n k= Wk. Though this measure is simple to define, is not analytically tractable. For the rest of this paper we use a throughput measure known as average bandwidth share [] which has the advantage of being simple for analysis. If we let ff denote the average bandwidth share, then for a unit capacity server this measure is given by R t 0 N(u) I fn(u) gdu ff = lim t! R t 0 I fn(u) gdu ; () where the denominator converges to and is included in the expression to compensate for the fraction of time when the server is free, i.e., the fraction of time when there is no customer (and hence no throughput). Assuming that there is a steady state, let ß(n) denote the probability that there are n sessions in the system in steady state. Then we have ff = P ß(n) n=. Assuming ideal bandwidth sharing the steady n state distribution of N (t) is the same as that of M/M/ PS queue with arrival rate, service rate μ and utilization factor = E(X), the steady state probability measure exists for C <, and is given by It is easily seen that, ff() = ß(n) =( ) n X ß(n) n n= = ln ; (2) where we used the notation ff() to explicitly bring out the dependence of the average bandwidth share on. V. AVERAGE BANDWIDTH SHARE WITH BLOCKING Let admission control be used to limit the number of flows in progress to max. Then, the distribution of number of customers N (t) is given by truncating and renormalizing the above geometric distribution. In particular for any load, the probability a new request is blocked is given by PrfN (t) = max g = max ( ) max+. This follows from the insensitivity of M/G/ PS model to the customer file size distribution. Thus for a given blocking probability 0 <fi<,wehave η max fi ln ( fi) max = ln (3) load, β = 0. β = 0.2 β = 0.3 β = 0.4 β = Fig. 2. Maximum number of allowable transfers max vs. load. For a given blocking probability fi, the average bandwidth share can be found. In the average bandwidth share formula we considered () the denominator converges to the load allowed into the queue which is ( fi). If we let ff CLC (; fi) denote the average bandwidth share with a blocking(connection Limit, CLC) probability of fi, then ff CLC (; fi) = X max k ( ) ( fi) k max+ k= ( fi) = ln (4) ( fi) ( fi) Now, we make the important observation from (2) and (4) that ff CLC (; fi) = ff(( fi)) (5) Before we explain the significance of this observation, we first make a few comments on the plots shown in Fig. (2) and Fig. (3) that help us understand some of the available design choices. The plot in Fig. (2) shows how the maximum number of sessions max varies with the offered load,, for various blocking probabilities. The other plot shown in Fig. (3) shows the average bandwidth share, ff CLC (; fi), as a function of the offered load for different blocking probabilities. Comments: From the Figures 2 and 3 we can make the following observations. ffl From Fig. 3 we can observe that for a given traffic load, bandwidth share increases with target blocking probability fi.
3 Average Bandwidth Share, σ CLC (, β) β max = 0.2 β = 0 β = 0. β = 0.4 β = * load, * β = 0 β = 0.2 Fig. 3. Average bandwidth share(ff CLC (; fi)) versus load() for various blocking probabilities. ffl In Fig. 2 we can see that for a fixed fi maximum number of sessions permitted increases with increasing traffic load. ffl When the offered load decreases from 2 to, where 2 >, we see from the curves that we have two options.. One option is to keep the blocking unchanged. Using CLC, this would require us to adjust max downwards (see Fig. 2) so that at the smaller load,, the blocking probability remains the same as with 2. It is then clear from the curves in Fig. 3 that ff will increase as we move along the constant fi curve. 2. On the other hand, users probably would not like to be blocked but would require a minimum throughput. In that case there would be a maximum acceptable fi max that would define the maximum acceptable operating load. For instance, if a desired throughput of (See Fig. 3) was being provided at ß 0:9, at some acceptable blocking of 0.2, and if the load drops to ß 0:72, the same throughput can be provided at a lower blocking, which in this case is zero. That is, if ( ;fi ) and ( 2 ;fi 2 ) can provide a desired throughput ff then ( fi )= 2 ( fi 2 ). This observation says that to achieve a desired ff it is sufficient to control the carried load value to a certain threshold Λ. This observation has the implementation advantage that, it may be processing wise less expensive to measure the carried load, rather than count the number of active connections. This can be seen from how TCP flows are identified in a. A TCP flow is identified by the 4-tuple source and destination IP addresses, and source and destination port numbers. When a handles a fewer TCP flows(for example, an edge connecting end users to an ISP), then it may be processing wise affordable to count active flows by classifying TCP packets by the 4-tuple. If the handles a larger number of flows(for example, a core ) then it is expensive to do the same. Having seen that either of the two control policies can be implemented as the other, for the rest of this paper we concentrate on OLC. In OLC we block the excess traffic once the server occupancy exceeds Λ. Suppose we know that the offered traffic load is (> Λ ), then we need to block a fraction fi = Λ of the offered load. So it is clear to see that fi is well determined by and Λ. Since we allow all customers when the load served by the queue is less than Λ, the concise representation for the desired acceptance probability is ff Λ = fi Λ = min Λ ; : VI. ESTIMATING THE OFFERED LOAD, In the previous section we have seen that to be able to implement Occupancy Limit (OLC) we need to know the offered load at the bottleneck link. In this section we study a linear model to estimate the offered load. For the scenario depicted in Fig. () with blocking new sessions, the offered load and the controlled load at the bottleneck link are as shown in the Fig. (4). The rectangle bars shown in the same figure represent unsent fragments of the files in the server. offered load λ - α α rejected requests controlled load Fig. 4. Figure shows the relation between the offered, controlled and rejected traffic at the bottleneck link To measure link occupancy, time is divided into fixed length intervals of length fi, and the measurements are made over these intervals. The time interval [(n )fi;nfi) will be identified as the nth measurement interval or slot. In any given interval the link occupancy is defined as the fraction of time the link is busy. For example, if c n is the aggregate data carried on the link in the nth measurement interval, then the link occupancy is cn. fic These occupancy measurements are used to compute the offered load estimate which in turn are used in the OLC algorithm to compute the control value. At the end of each of these successive intervals, an adjustment to the control level may be made and a new measurement is begun. We assume that during each measurement interval, the load presented to the link and the control level are fixed. Let the control level in the k th interval, k, the fraction of the offered load accepted into the queue, be denoted by ff k, and the load carried by the link in the k th interval be denoted by y k. We write the measurement in the k th interval as y k = ff k + w k ; < (6) where w k is the measurement noise. For further analysis we would like this noise to have zero mean. Obviously, the larger the fi is the better this approximation will be, but less frequently we will get the chance to adjust the control level. In order to determine suitable values for fi, we studied the random variable w k+ in detail. In this connection we can compute the first two moments of the measurement noise using the regen-
4 erative central limit theorem(theorem 23, Chapter 2, [0]). E(w k+ ) ß 0; 8k E(wk+ 2 ) ß ff k E(X 2 ) fic 2 ; 8k (7) Letting ^ n denote the offered load estimate, we use two algorithms (VI) and (VI) to estimate in the model (6) assuming that the data fy ;:::;y n g, fff 0 ;:::;ff n g and the initial load estimate ^ 0 are given. Least Squares Estimate(infinite memory version): ^ n = P n Pk=0 y k+ffk n k=0 ff2 k P n k=n W y k+ffk P n ; n Least Squares Estimate(finite memory version): ^ n = ; n k=n W ff2 k Once the offered load estimate is known then we can choose the control value as ff n = min Λ ^ n ; ; n. In other words, at each instant k we make an estimate of, and then we choose the control as if the estimate were the true parameter [9]. If ^ n converges to the true parameter, then Λ ; lim k! ff k =min = ff Λ, and such an adaptive control law is known as self-tuning. The following theorem guarantees that least squares estimate for the offered load converges to the true value and hence the control converges to the true control value. Theorem VI.: Let fw k ; F k g be a martingale difference sequence and suppose that sup n E(wk+ 2 jf k)» a:s:. Let fff k g be a process adapted to ff k g, i.e., ff k is F k -measurable for each k, where F k = fffff l ;w l ;l» kg. Then lim ^ n = a.s. and so lim ff k =min Λ ; holds a.s. Proof: For details see the theorem.2.7 of [9]. In the exponential forgetting algorithm, the offered load estimate in any measurement interval is computed as the sum of estimate in the previous time interval plus the estimate calculated from the most recent data. In this algorithm, the constant a, 0 <a<, is called the weighing factor or forgetting factor. By properly choosing a we can emphasize (or deemphasize) the influence of most recent data upon the estimate ^ n+. Exponential Forgetting Estimate: ^ n+ = ( a)^ n + a yn+ ffn The following theorem can be stated with respect to the exponential forgetting algorithm. Theorem VI.2: Let F 0 = ff(ff 0 ) and, for k, F k = ff(y s ;ff s ;s» k). Assume E(w k+ jf k )=0. Then. E^ n!. 2. The rate of convergence of the algorithm is geometric with the convergence ratio of a. 3. The mean square estimation error E( ^ n ) 2 converges to Λ a EX 2. 2 a fic 2 Proof: For details see [2]. To see the effectiveness of these adaptive control algorithms we simulated the M/M/ PS model. In the simulation runs the customer file request distribution is taken to be exponential with mean E(X) = 0 KBytes, which is a commonly used value for average file size in Internet. The bottleneck link capacity is taken to be 2 Mbps, which is a typical value for access link speeds in India. The length of the measurement intervals are choosen such that mean square estimation error of the offered load (7) is of some fixed value. In all the simulation results the offered load estimation error is fixed at 0 4. These results are shown in figures (5), (6), (7) and (8). For the simulation result shown in Fig. (5) offered load is estimated using least squares by incorporating the entire past and a large value of 480s for fi is chosen. In Fig. 6 most recent data is used to estimate the offered load. That is least squares with a window length equal to is used. In general, over such long time scales statistics of the arrival process may change and we would like to respond to such changes to maintain QoS. For that, for the simulation shown in Fig. (7), we used small update times fi =60sand then use a number of such previous measurements to estimate the offered load. Here a window length of 8 is used to estimate the offered load. By this choice of small update times we frequently update the control value estimates and at the same time are able to incorporate sufficient past information to improve accuracy of the offered load and control estimates. For the plot shown in fig. (8) exponential forgetting estimate is used. In all the simulation results shown, offered load and the target carried load are set at and respectively. Hence the desired control ff Λ = min( 0:6 ; ) = 0:75. 0:8 In Fig. (5) the control level responds immediately and converges to 5 where as in Figs. (6) and (7) the control oscillates around ff Λ =0:75. This can be explained as follows: for the plot shown in Fig. (5) the entire past information is used to estimate the control level and as more and more information is used the accuracy of the control estimate improves. For the plot shown in Fig. (6), only the most recent data is used to estimate the control level and this explains for the oscillatory behavior. The same explanation can be used to explain the oscillatory behavior shown in the Fig. (7) Offered Load = Target Load = Update Time = 480s Fig. 5. Infinite memory version of least squares: figure shows the control level and the controlled Load versus time; fi = 480s, E(X) = 0KBytes, =, Λ =.
5 5 Offered Load = Target Load = Update Time = 480s 5 control led load Fig. 6. Figure shows the control level and the controlled Load versus time; fi = 480s, E(X) = 0KBytes, =, Λ =, Window Length, W = Time Fig. 8. Exponential Forgetting Estimate: figure shows the control level and the controlled load verses time; a =0:6, fi =60s, E(X) = 0KBytes, = 0:8, Λ = 0: Offered Load = Target Load = Update Time = 60s user decides to abandon the request. This retrial behavior on users part brings to fore some issues which are hard to model and do the relevant performance analysis, partly due to unpredictable user patience levels. For example, in the presence of user retrial behavior, unlike in the model (6), the offered load, carried load, control and retrial probability are related through a non-linear relationship. An attempt has been made to study these issues in [2]. Very soon we plan to publish this work Fig. 7. Figure shows the control level and the controlled load verses time; fi =60s, E(X) = 0KBytes, = 0:8, Λ = 0:6, Window Length, W =8. VII. CONCLUSIONS We considered blocking new elastic flows on a bottleneck link to achieve a bandwidth performance objective. We proposed two control strategies, namely, CLC and OLC, and then used simple system control approaches to study a few well known adaptive control algorithms to implement OLC. Generally most of the time bottleneck links operate under overload conditions. In this paper we have not discussed control strategies that work in overload conditions. An interesting aspect to admission control comes from users retrial behavior. Generally when a user requesting the download of a file or web page is rejected the user will not abandon the request but will retry after some time hoping that this time the request will get through. If the request is again rejected it may decide either to retry after some time or may withdraw its request forever which generally depends on the user patience level. This retrial process goes on until either the request gets through, or the REFERENCES [] J. W. Roberts and L. Massoulie, Arguments in Favour of Admission for TCP Flows, International Teletraffic Conference 6, Edinburgh, 999 [2] A. A. Kherani and Anurag Kumar and Pinaki Chanda, An Approximate Calculation of Max-Min Fair Throughputs for Non-Persistent Elastic Sessions, Internet Performance Symposium, IEEE Globecom, 200 [3] Anurag Kumar and Malati Hegde and S.V.R. Anand and B.N. Bindu and Dinesh Thirumurthy and A.A. Kherani, Nonintrusive TCP Connection Admission for Bandwidth Management of an Internet Access Link, IEEE Communications Magazine, May 2000 [4] J. W. Roberts and L. Massoulie, Bandwidth Sharing and Admission for Elastic Traffic, ITC Specialist Seminar, Yokohama, October 998 [5] Tian Bu and Don Towsley, Fixed Point Approximations for TCP Behaviour in an AQM Network, Proceedings of ACM SIGMETRICS 200 [6] M. Vojnovic and J.-Y. Le Boudec and C. Boutremans, Global Fairness of Additive Increase and Multiplicative Decrease with Heterogenous Round Trip Times, Proc. IEEE Infocom 2000, 2000 [7] Thomas Bonald and Laurent Massoulie, Impact of Fairness on Internet Performance, Sigmetrics, 200 [8] J. W. Roberts and L. Massoulie, Bandwidth Sharing: Objectives and Algorithms, IEEE Tran. on Networking, 0(3), pp , June 2002 [9] P. R. Kumar and Pravin Varaiya, Stochastic Systems: Estimation, Identification, and Adaptive, Prentice Hall, 986 [0] Ronald W. Wolff, Stochastic Modelling and The Theory of Queues, Prentice Hall, 989 [] A. A. Kherani and Anurag Kumar, Stochastic Models for Throughput Analysis of Randomly Arriving Elastic Flows in the Internet, IEEE Infocom, 2002 [2] KCV Kalyanarama Sesha Sayee, Adaptive Algorithms for Admission of Elastic Sessions in the Internet, MS.c (Engg) Thesis, Indian Institute of Science, 200, Bangalore [3] Pinaki Shankar Chanda, Models for Traffic Engineering of Packet Networks with Non-Persistent Elastic Flows, ME Thesis, Indian Institute of Scince, 200, Bangalore
Dynamic resource sharing
 J. Virtamo 38.34 Teletraffic Theory / Dynamic resource sharing and balanced fairness Dynamic resource sharing In previous lectures we have studied different notions of fair resource sharing. Our focus
J. Virtamo 38.34 Teletraffic Theory / Dynamic resource sharing and balanced fairness Dynamic resource sharing In previous lectures we have studied different notions of fair resource sharing. Our focus
Queueing Theory I Summary! Little s Law! Queueing System Notation! Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K "
 Queueing Theory I Summary Little s Law Queueing System Notation Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K " Little s Law a(t): the process that counts the number of arrivals
Queueing Theory I Summary Little s Law Queueing System Notation Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K " Little s Law a(t): the process that counts the number of arrivals
Congestion In Large Balanced Fair Links
 Congestion In Large Balanced Fair Links Thomas Bonald (Telecom Paris-Tech), Jean-Paul Haddad (Ernst and Young) and Ravi R. Mazumdar (Waterloo) ITC 2011, San Francisco Introduction File transfers compose
Congestion In Large Balanced Fair Links Thomas Bonald (Telecom Paris-Tech), Jean-Paul Haddad (Ernst and Young) and Ravi R. Mazumdar (Waterloo) ITC 2011, San Francisco Introduction File transfers compose
Capacity management for packet-switched networks with heterogeneous sources. Linda de Jonge. Master Thesis July 29, 2009.
 Capacity management for packet-switched networks with heterogeneous sources Linda de Jonge Master Thesis July 29, 2009 Supervisors Dr. Frank Roijers Prof. dr. ir. Sem Borst Dr. Andreas Löpker Industrial
Capacity management for packet-switched networks with heterogeneous sources Linda de Jonge Master Thesis July 29, 2009 Supervisors Dr. Frank Roijers Prof. dr. ir. Sem Borst Dr. Andreas Löpker Industrial
Classical Queueing Models.
 Sergey Zeltyn January 2005 STAT 99. Service Engineering. The Wharton School. University of Pennsylvania. Based on: Classical Queueing Models. Mandelbaum A. Service Engineering course, Technion. http://iew3.technion.ac.il/serveng2005w
Sergey Zeltyn January 2005 STAT 99. Service Engineering. The Wharton School. University of Pennsylvania. Based on: Classical Queueing Models. Mandelbaum A. Service Engineering course, Technion. http://iew3.technion.ac.il/serveng2005w
Analysis of Scalable TCP in the presence of Markovian Losses
 Analysis of Scalable TCP in the presence of Markovian Losses E Altman K E Avrachenkov A A Kherani BJ Prabhu INRIA Sophia Antipolis 06902 Sophia Antipolis, France Email:altman,kavratchenkov,alam,bprabhu}@sophiainriafr
Analysis of Scalable TCP in the presence of Markovian Losses E Altman K E Avrachenkov A A Kherani BJ Prabhu INRIA Sophia Antipolis 06902 Sophia Antipolis, France Email:altman,kavratchenkov,alam,bprabhu}@sophiainriafr
High speed access links. High speed access links. a(t) process (aggregate traffic into buffer)
 Long Range Dependence in Network Traffic and the Closed Loop Behaviour of Buffers Under Adaptive Window Control Arzad A. Kherani and Anurag Kumar Dept. of Electrical Communication Engg. Indian Institute
Long Range Dependence in Network Traffic and the Closed Loop Behaviour of Buffers Under Adaptive Window Control Arzad A. Kherani and Anurag Kumar Dept. of Electrical Communication Engg. Indian Institute
Computer Networks More general queuing systems
 Computer Networks More general queuing systems Saad Mneimneh Computer Science Hunter College of CUNY New York M/G/ Introduction We now consider a queuing system where the customer service times have a
Computer Networks More general queuing systems Saad Mneimneh Computer Science Hunter College of CUNY New York M/G/ Introduction We now consider a queuing system where the customer service times have a
Fair Scheduling in Input-Queued Switches under Inadmissible Traffic
 Fair Scheduling in Input-Queued Switches under Inadmissible Traffic Neha Kumar, Rong Pan, Devavrat Shah Departments of EE & CS Stanford University {nehak, rong, devavrat@stanford.edu Abstract In recent
Fair Scheduling in Input-Queued Switches under Inadmissible Traffic Neha Kumar, Rong Pan, Devavrat Shah Departments of EE & CS Stanford University {nehak, rong, devavrat@stanford.edu Abstract In recent
Figure 10.1: Recording when the event E occurs
 10 Poisson Processes Let T R be an interval. A family of random variables {X(t) ; t T} is called a continuous time stochastic process. We often consider T = [0, 1] and T = [0, ). As X(t) is a random variable
10 Poisson Processes Let T R be an interval. A family of random variables {X(t) ; t T} is called a continuous time stochastic process. We often consider T = [0, 1] and T = [0, ). As X(t) is a random variable
Performance Analysis of Priority Queueing Schemes in Internet Routers
 Conference on Information Sciences and Systems, The Johns Hopkins University, March 8, Performance Analysis of Priority Queueing Schemes in Internet Routers Ashvin Lakshmikantha Coordinated Science Lab
Conference on Information Sciences and Systems, The Johns Hopkins University, March 8, Performance Analysis of Priority Queueing Schemes in Internet Routers Ashvin Lakshmikantha Coordinated Science Lab
Stochastic Network Calculus
 Stochastic Network Calculus Assessing the Performance of the Future Internet Markus Fidler joint work with Amr Rizk Institute of Communications Technology Leibniz Universität Hannover April 22, 2010 c
Stochastic Network Calculus Assessing the Performance of the Future Internet Markus Fidler joint work with Amr Rizk Institute of Communications Technology Leibniz Universität Hannover April 22, 2010 c
Queueing Theory and Simulation. Introduction
 Queueing Theory and Simulation Based on the slides of Dr. Dharma P. Agrawal, University of Cincinnati and Dr. Hiroyuki Ohsaki Graduate School of Information Science & Technology, Osaka University, Japan
Queueing Theory and Simulation Based on the slides of Dr. Dharma P. Agrawal, University of Cincinnati and Dr. Hiroyuki Ohsaki Graduate School of Information Science & Technology, Osaka University, Japan
ECE 3511: Communications Networks Theory and Analysis. Fall Quarter Instructor: Prof. A. Bruce McDonald. Lecture Topic
 ECE 3511: Communications Networks Theory and Analysis Fall Quarter 2002 Instructor: Prof. A. Bruce McDonald Lecture Topic Introductory Analysis of M/G/1 Queueing Systems Module Number One Steady-State
ECE 3511: Communications Networks Theory and Analysis Fall Quarter 2002 Instructor: Prof. A. Bruce McDonald Lecture Topic Introductory Analysis of M/G/1 Queueing Systems Module Number One Steady-State
M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS
 M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS MOHAMMED HAWA AND DAVID W. PETR Information and Telecommunications Technology Center University of Kansas, Lawrence, Kansas, 66045 email: {hawa, dwp}@ittc.ku.edu
M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS MOHAMMED HAWA AND DAVID W. PETR Information and Telecommunications Technology Center University of Kansas, Lawrence, Kansas, 66045 email: {hawa, dwp}@ittc.ku.edu
requests/sec. The total channel load is requests/sec. Using slot as the time unit, the total channel load is 50 ( ) = 1
 Prof. X. Shen E&CE 70 : Examples #2 Problem Consider the following Aloha systems. (a) A group of N users share a 56 kbps pure Aloha channel. Each user generates at a Passion rate of one 000-bit packet
Prof. X. Shen E&CE 70 : Examples #2 Problem Consider the following Aloha systems. (a) A group of N users share a 56 kbps pure Aloha channel. Each user generates at a Passion rate of one 000-bit packet
A STAFFING ALGORITHM FOR CALL CENTERS WITH SKILL-BASED ROUTING: SUPPLEMENTARY MATERIAL
 A STAFFING ALGORITHM FOR CALL CENTERS WITH SKILL-BASED ROUTING: SUPPLEMENTARY MATERIAL by Rodney B. Wallace IBM and The George Washington University rodney.wallace@us.ibm.com Ward Whitt Columbia University
A STAFFING ALGORITHM FOR CALL CENTERS WITH SKILL-BASED ROUTING: SUPPLEMENTARY MATERIAL by Rodney B. Wallace IBM and The George Washington University rodney.wallace@us.ibm.com Ward Whitt Columbia University
A New Technique for Link Utilization Estimation
 A New Technique for Link Utilization Estimation in Packet Data Networks using SNMP Variables S. Amarnath and Anurag Kumar* Dept. of Electrical Communication Engineering Indian Institute of Science, Bangalore
A New Technique for Link Utilization Estimation in Packet Data Networks using SNMP Variables S. Amarnath and Anurag Kumar* Dept. of Electrical Communication Engineering Indian Institute of Science, Bangalore
Session-Based Queueing Systems
 Session-Based Queueing Systems Modelling, Simulation, and Approximation Jeroen Horters Supervisor VU: Sandjai Bhulai Executive Summary Companies often offer services that require multiple steps on the
Session-Based Queueing Systems Modelling, Simulation, and Approximation Jeroen Horters Supervisor VU: Sandjai Bhulai Executive Summary Companies often offer services that require multiple steps on the
Lecture 7: Simulation of Markov Processes. Pasi Lassila Department of Communications and Networking
 Lecture 7: Simulation of Markov Processes Pasi Lassila Department of Communications and Networking Contents Markov processes theory recap Elementary queuing models for data networks Simulation of Markov
Lecture 7: Simulation of Markov Processes Pasi Lassila Department of Communications and Networking Contents Markov processes theory recap Elementary queuing models for data networks Simulation of Markov
COMP9334 Capacity Planning for Computer Systems and Networks
 COMP9334 Capacity Planning for Computer Systems and Networks Week 2: Operational Analysis and Workload Characterisation COMP9334 1 Last lecture Modelling of computer systems using Queueing Networks Open
COMP9334 Capacity Planning for Computer Systems and Networks Week 2: Operational Analysis and Workload Characterisation COMP9334 1 Last lecture Modelling of computer systems using Queueing Networks Open
NICTA Short Course. Network Analysis. Vijay Sivaraman. Day 1 Queueing Systems and Markov Chains. Network Analysis, 2008s2 1-1
 NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
Network Traffic Characteristic
 Network Traffic Characteristic Hojun Lee hlee02@purros.poly.edu 5/24/2002 EL938-Project 1 Outline Motivation What is self-similarity? Behavior of Ethernet traffic Behavior of WAN traffic Behavior of WWW
Network Traffic Characteristic Hojun Lee hlee02@purros.poly.edu 5/24/2002 EL938-Project 1 Outline Motivation What is self-similarity? Behavior of Ethernet traffic Behavior of WAN traffic Behavior of WWW
A Retrial Queueing model with FDL at OBS core node
 A Retrial Queueing model with FDL at OBS core node Chuong Dang Thanh a, Duc Pham Trung a, Thang Doan Van b a Faculty of Information Technology, College of Sciences, Hue University, Hue, Viet Nam. E-mail:
A Retrial Queueing model with FDL at OBS core node Chuong Dang Thanh a, Duc Pham Trung a, Thang Doan Van b a Faculty of Information Technology, College of Sciences, Hue University, Hue, Viet Nam. E-mail:
TCP over Cognitive Radio Channels
 1/43 TCP over Cognitive Radio Channels Sudheer Poojary Department of ECE, Indian Institute of Science, Bangalore IEEE-IISc I-YES seminar 19 May 2016 2/43 Acknowledgments The work presented here was done
1/43 TCP over Cognitive Radio Channels Sudheer Poojary Department of ECE, Indian Institute of Science, Bangalore IEEE-IISc I-YES seminar 19 May 2016 2/43 Acknowledgments The work presented here was done
Bounded Delay for Weighted Round Robin with Burst Crediting
 Bounded Delay for Weighted Round Robin with Burst Crediting Sponsor: Sprint Kert Mezger David W. Petr Technical Report TISL-0230-08 Telecommunications and Information Sciences Laboratory Department of
Bounded Delay for Weighted Round Robin with Burst Crediting Sponsor: Sprint Kert Mezger David W. Petr Technical Report TISL-0230-08 Telecommunications and Information Sciences Laboratory Department of
Combining Opportunistic and Size-Based Scheduling in Wireless Systems
 Combining Opportunistic and Size-Based Scheduling in Wireless Systems Pasi Lassila TKK Helsinki University of Technology P.O.Box 3, FI-15 TKK, Finland Pasi.Lassila@tkk.fi Samuli Aalto TKK Helsinki University
Combining Opportunistic and Size-Based Scheduling in Wireless Systems Pasi Lassila TKK Helsinki University of Technology P.O.Box 3, FI-15 TKK, Finland Pasi.Lassila@tkk.fi Samuli Aalto TKK Helsinki University
Performance Evaluation of Queuing Systems
 Performance Evaluation of Queuing Systems Introduction to Queuing Systems System Performance Measures & Little s Law Equilibrium Solution of Birth-Death Processes Analysis of Single-Station Queuing Systems
Performance Evaluation of Queuing Systems Introduction to Queuing Systems System Performance Measures & Little s Law Equilibrium Solution of Birth-Death Processes Analysis of Single-Station Queuing Systems
A flow-based model for Internet backbone traffic
 A flow-based model for Internet backbone traffic Chadi Barakat, Patrick Thiran Gianluca Iannaccone, Christophe iot Philippe Owezarski ICA - SC - EPFL Sprint Labs LAAS-CNRS {Chadi.Barakat,Patrick.Thiran}@epfl.ch
A flow-based model for Internet backbone traffic Chadi Barakat, Patrick Thiran Gianluca Iannaccone, Christophe iot Philippe Owezarski ICA - SC - EPFL Sprint Labs LAAS-CNRS {Chadi.Barakat,Patrick.Thiran}@epfl.ch
Reliable Data Transport: Sliding Windows
 Reliable Data Transport: Sliding Windows 6.02 Fall 2013 Lecture 23 Exclusive! A Brief History of the Internet guest lecture by Prof. Hari Balakrishnan Wenesday December 4, 2013, usual 6.02 lecture time
Reliable Data Transport: Sliding Windows 6.02 Fall 2013 Lecture 23 Exclusive! A Brief History of the Internet guest lecture by Prof. Hari Balakrishnan Wenesday December 4, 2013, usual 6.02 lecture time
Modeling Approximations for an IEEE WLAN under Poisson MAC-Level Arrivals
 Modeling Approximations for an IEEE 802.11 WLAN under Poisson MAC-Level Arrivals Ioannis Koukoutsidis 1 and Vasilios A. Siris 1,2 1 FORTH-ICS, P.O. Box 1385, 71110 Heraklion, Crete, Greece 2 Computer Science
Modeling Approximations for an IEEE 802.11 WLAN under Poisson MAC-Level Arrivals Ioannis Koukoutsidis 1 and Vasilios A. Siris 1,2 1 FORTH-ICS, P.O. Box 1385, 71110 Heraklion, Crete, Greece 2 Computer Science
BIRTH DEATH PROCESSES AND QUEUEING SYSTEMS
 BIRTH DEATH PROCESSES AND QUEUEING SYSTEMS Andrea Bobbio Anno Accademico 999-2000 Queueing Systems 2 Notation for Queueing Systems /λ mean time between arrivals S = /µ ρ = λ/µ N mean service time traffic
BIRTH DEATH PROCESSES AND QUEUEING SYSTEMS Andrea Bobbio Anno Accademico 999-2000 Queueing Systems 2 Notation for Queueing Systems /λ mean time between arrivals S = /µ ρ = λ/µ N mean service time traffic
CPSC 531: System Modeling and Simulation. Carey Williamson Department of Computer Science University of Calgary Fall 2017
 CPSC 531: System Modeling and Simulation Carey Williamson Department of Computer Science University of Calgary Fall 2017 Motivating Quote for Queueing Models Good things come to those who wait - poet/writer
CPSC 531: System Modeling and Simulation Carey Williamson Department of Computer Science University of Calgary Fall 2017 Motivating Quote for Queueing Models Good things come to those who wait - poet/writer
Introduction to Markov Chains, Queuing Theory, and Network Performance
 Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
Capturing Network Traffic Dynamics Small Scales. Rolf Riedi
 Capturing Network Traffic Dynamics Small Scales Rolf Riedi Dept of Statistics Stochastic Systems and Modelling in Networking and Finance Part II Dependable Adaptive Systems and Mathematical Modeling Kaiserslautern,
Capturing Network Traffic Dynamics Small Scales Rolf Riedi Dept of Statistics Stochastic Systems and Modelling in Networking and Finance Part II Dependable Adaptive Systems and Mathematical Modeling Kaiserslautern,
384Y Project June 5, Stability of Congestion Control Algorithms Using Control Theory with an application to XCP
 384Y Project June 5, 00 Stability of Congestion Control Algorithms Using Control Theory with an application to XCP . Introduction During recent years, a lot of work has been done towards the theoretical
384Y Project June 5, 00 Stability of Congestion Control Algorithms Using Control Theory with an application to XCP . Introduction During recent years, a lot of work has been done towards the theoretical
Modeling and Stability of PERT
 Modeling Stability of PET Yueping Zhang yueping@cs.tamu.edu I. SYSTEM MODEL Our modeling of PET is composed of three parts: window adjustment ED emulation queuing behavior. We start with the window dynamics.
Modeling Stability of PET Yueping Zhang yueping@cs.tamu.edu I. SYSTEM MODEL Our modeling of PET is composed of three parts: window adjustment ED emulation queuing behavior. We start with the window dynamics.
Homework 1 - SOLUTION
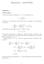 Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
Computer Networks Fairness
 Computer Networks Fairness Saad Mneimneh Computer Science Hunter College of CUNY New York Life is not fair, but we can at least theorize 1 Introduction So far, we analyzed a number of systems in terms
Computer Networks Fairness Saad Mneimneh Computer Science Hunter College of CUNY New York Life is not fair, but we can at least theorize 1 Introduction So far, we analyzed a number of systems in terms
A Study on Performance Analysis of Queuing System with Multiple Heterogeneous Servers
 UNIVERSITY OF OKLAHOMA GENERAL EXAM REPORT A Study on Performance Analysis of Queuing System with Multiple Heterogeneous Servers Prepared by HUSNU SANER NARMAN husnu@ou.edu based on the papers 1) F. S.
UNIVERSITY OF OKLAHOMA GENERAL EXAM REPORT A Study on Performance Analysis of Queuing System with Multiple Heterogeneous Servers Prepared by HUSNU SANER NARMAN husnu@ou.edu based on the papers 1) F. S.
CHAPTER 4. Networks of queues. 1. Open networks Suppose that we have a network of queues as given in Figure 4.1. Arrivals
 CHAPTER 4 Networks of queues. Open networks Suppose that we have a network of queues as given in Figure 4.. Arrivals Figure 4.. An open network can occur from outside of the network to any subset of nodes.
CHAPTER 4 Networks of queues. Open networks Suppose that we have a network of queues as given in Figure 4.. Arrivals Figure 4.. An open network can occur from outside of the network to any subset of nodes.
Wireless Internet Exercises
 Wireless Internet Exercises Prof. Alessandro Redondi 2018-05-28 1 WLAN 1.1 Exercise 1 A Wi-Fi network has the following features: Physical layer transmission rate: 54 Mbps MAC layer header: 28 bytes MAC
Wireless Internet Exercises Prof. Alessandro Redondi 2018-05-28 1 WLAN 1.1 Exercise 1 A Wi-Fi network has the following features: Physical layer transmission rate: 54 Mbps MAC layer header: 28 bytes MAC
Chapter 2 Queueing Theory and Simulation
 Chapter 2 Queueing Theory and Simulation Based on the slides of Dr. Dharma P. Agrawal, University of Cincinnati and Dr. Hiroyuki Ohsaki Graduate School of Information Science & Technology, Osaka University,
Chapter 2 Queueing Theory and Simulation Based on the slides of Dr. Dharma P. Agrawal, University of Cincinnati and Dr. Hiroyuki Ohsaki Graduate School of Information Science & Technology, Osaka University,
Discrete-event simulations
 Discrete-event simulations Lecturer: Dmitri A. Moltchanov E-mail: moltchan@cs.tut.fi http://www.cs.tut.fi/kurssit/elt-53606/ OUTLINE: Why do we need simulations? Step-by-step simulations; Classifications;
Discrete-event simulations Lecturer: Dmitri A. Moltchanov E-mail: moltchan@cs.tut.fi http://www.cs.tut.fi/kurssit/elt-53606/ OUTLINE: Why do we need simulations? Step-by-step simulations; Classifications;
A discrete-time priority queue with train arrivals
 A discrete-time priority queue with train arrivals Joris Walraevens, Sabine Wittevrongel and Herwig Bruneel SMACS Research Group Department of Telecommunications and Information Processing (IR07) Ghent
A discrete-time priority queue with train arrivals Joris Walraevens, Sabine Wittevrongel and Herwig Bruneel SMACS Research Group Department of Telecommunications and Information Processing (IR07) Ghent
Evaluation of Effective Bandwidth Schemes for Self-Similar Traffic
 Proceedings of the 3th ITC Specialist Seminar on IP Measurement, Modeling and Management, Monterey, CA, September 2000, pp. 2--2-0 Evaluation of Effective Bandwidth Schemes for Self-Similar Traffic Stefan
Proceedings of the 3th ITC Specialist Seminar on IP Measurement, Modeling and Management, Monterey, CA, September 2000, pp. 2--2-0 Evaluation of Effective Bandwidth Schemes for Self-Similar Traffic Stefan
UC Irvine UC Irvine Previously Published Works
 UC Irvine UC Irvine Previously Published Works Title Throughput in processor-sharing queues Permalink https://escholarship.org/uc/item/98599m4 Journal IEEE Transactions on Automatic Control, 52(2) ISSN
UC Irvine UC Irvine Previously Published Works Title Throughput in processor-sharing queues Permalink https://escholarship.org/uc/item/98599m4 Journal IEEE Transactions on Automatic Control, 52(2) ISSN
A POMDP Framework for Cognitive MAC Based on Primary Feedback Exploitation
 A POMDP Framework for Cognitive MAC Based on Primary Feedback Exploitation Karim G. Seddik and Amr A. El-Sherif 2 Electronics and Communications Engineering Department, American University in Cairo, New
A POMDP Framework for Cognitive MAC Based on Primary Feedback Exploitation Karim G. Seddik and Amr A. El-Sherif 2 Electronics and Communications Engineering Department, American University in Cairo, New
A Starvation-free Algorithm For Achieving 100% Throughput in an Input- Queued Switch
 A Starvation-free Algorithm For Achieving 00% Throughput in an Input- Queued Switch Abstract Adisak ekkittikul ick ckeown Department of Electrical Engineering Stanford University Stanford CA 9405-400 Tel
A Starvation-free Algorithm For Achieving 00% Throughput in an Input- Queued Switch Abstract Adisak ekkittikul ick ckeown Department of Electrical Engineering Stanford University Stanford CA 9405-400 Tel
A novel algorithm for dynamic admission control of elastic flows
 A novel algorithm for dynamic admission control of elastic flows Franco Blanchini, Daniele Casagrande and Pier Luca Montessoro Abstract The task of assigning part of the forwarding capability of a router
A novel algorithm for dynamic admission control of elastic flows Franco Blanchini, Daniele Casagrande and Pier Luca Montessoro Abstract The task of assigning part of the forwarding capability of a router
Load Balancing in Distributed Service System: A Survey
 Load Balancing in Distributed Service System: A Survey Xingyu Zhou The Ohio State University zhou.2055@osu.edu November 21, 2016 Xingyu Zhou (OSU) Load Balancing November 21, 2016 1 / 29 Introduction and
Load Balancing in Distributed Service System: A Survey Xingyu Zhou The Ohio State University zhou.2055@osu.edu November 21, 2016 Xingyu Zhou (OSU) Load Balancing November 21, 2016 1 / 29 Introduction and
class class ff ff (t) packet loss packet loss (t) - - RED controlled queue Figure : Illustration of a Differentiad Services framework. RED has been an
 Modeling RED with Two Traffic Classes P. Kuusela and J. T. Virtamo Laboratory of Telecommunications Technology Helsinki University of Technology P. O. Box 3000, FIN-005 HUT, Finland Email: fpirkko.kuusela,
Modeling RED with Two Traffic Classes P. Kuusela and J. T. Virtamo Laboratory of Telecommunications Technology Helsinki University of Technology P. O. Box 3000, FIN-005 HUT, Finland Email: fpirkko.kuusela,
MASSACHUSETTS INSTITUTE OF TECHNOLOGY Department of Electrical Engineering and Computer Science
 MASSACHUSETTS INSTITUTE OF TECHNOLOGY Department of Electrical Engineering and Computer Science 6.262 Discrete Stochastic Processes Midterm Quiz April 6, 2010 There are 5 questions, each with several parts.
MASSACHUSETTS INSTITUTE OF TECHNOLOGY Department of Electrical Engineering and Computer Science 6.262 Discrete Stochastic Processes Midterm Quiz April 6, 2010 There are 5 questions, each with several parts.
Introduction to queuing theory
 Introduction to queuing theory Claude Rigault ENST claude.rigault@enst.fr Introduction to Queuing theory 1 Outline The problem The number of clients in a system The client process Delay processes Loss
Introduction to queuing theory Claude Rigault ENST claude.rigault@enst.fr Introduction to Queuing theory 1 Outline The problem The number of clients in a system The client process Delay processes Loss
A Simple Model for the Window Size Evolution of TCP Coupled with MAC and PHY Layers
 A Simple Model for the Window Size Evolution of TCP Coupled with and PHY Layers George Papageorgiou, John S. Baras Institute for Systems Research, University of Maryland, College Par, MD 20742 Email: gpapag,
A Simple Model for the Window Size Evolution of TCP Coupled with and PHY Layers George Papageorgiou, John S. Baras Institute for Systems Research, University of Maryland, College Par, MD 20742 Email: gpapag,
Solutions to COMP9334 Week 8 Sample Problems
 Solutions to COMP9334 Week 8 Sample Problems Problem 1: Customers arrive at a grocery store s checkout counter according to a Poisson process with rate 1 per minute. Each customer carries a number of items
Solutions to COMP9334 Week 8 Sample Problems Problem 1: Customers arrive at a grocery store s checkout counter according to a Poisson process with rate 1 per minute. Each customer carries a number of items
Analysis on Packet Resequencing for Reliable Network Protocols
 1 Analysis on Packet Resequencing for Reliable Network Protocols Ye Xia David Tse Department of Electrical Engineering and Computer Science University of California, Berkeley Abstract Protocols such as
1 Analysis on Packet Resequencing for Reliable Network Protocols Ye Xia David Tse Department of Electrical Engineering and Computer Science University of California, Berkeley Abstract Protocols such as
The impact of varying channel capacity on the quality of advanced data services in PCS networks
 The impact of varying channel capacity on the quality of advanced data services in PCS networks Markus Fiedler Dept. of Telecommunications and Signal Processing, University of Karlskrona/Ronneby, S-371
The impact of varying channel capacity on the quality of advanced data services in PCS networks Markus Fiedler Dept. of Telecommunications and Signal Processing, University of Karlskrona/Ronneby, S-371
Performance analysis of IEEE WLANs with saturated and unsaturated sources
 Performance analysis of IEEE 82.11 WLANs with saturated and unsaturated sources Suong H. Nguyen, Hai L. Vu, Lachlan L. H. Andrew Centre for Advanced Internet Architectures, Technical Report 11811A Swinburne
Performance analysis of IEEE 82.11 WLANs with saturated and unsaturated sources Suong H. Nguyen, Hai L. Vu, Lachlan L. H. Andrew Centre for Advanced Internet Architectures, Technical Report 11811A Swinburne
Giuseppe Bianchi, Ilenia Tinnirello
 Capacity of WLAN Networs Summary Ł Ł Ł Ł Arbitrary networ capacity [Gupta & Kumar The Capacity of Wireless Networs ] Ł! Ł "! Receiver Model Ł Ł # Ł $%&% Ł $% '( * &%* r (1+ r Ł + 1 / n 1 / n log n Area
Capacity of WLAN Networs Summary Ł Ł Ł Ł Arbitrary networ capacity [Gupta & Kumar The Capacity of Wireless Networs ] Ł! Ł "! Receiver Model Ł Ł # Ł $%&% Ł $% '( * &%* r (1+ r Ł + 1 / n 1 / n log n Area
Information in Aloha Networks
 Achieving Proportional Fairness using Local Information in Aloha Networks Koushik Kar, Saswati Sarkar, Leandros Tassiulas Abstract We address the problem of attaining proportionally fair rates using Aloha
Achieving Proportional Fairness using Local Information in Aloha Networks Koushik Kar, Saswati Sarkar, Leandros Tassiulas Abstract We address the problem of attaining proportionally fair rates using Aloha
Dynamic Call Center Routing Policies Using Call Waiting and Agent Idle Times Online Supplement
 Submitted to imanufacturing & Service Operations Management manuscript MSOM-11-370.R3 Dynamic Call Center Routing Policies Using Call Waiting and Agent Idle Times Online Supplement (Authors names blinded
Submitted to imanufacturing & Service Operations Management manuscript MSOM-11-370.R3 Dynamic Call Center Routing Policies Using Call Waiting and Agent Idle Times Online Supplement (Authors names blinded
Analysis of Software Artifacts
 Analysis of Software Artifacts System Performance I Shu-Ngai Yeung (with edits by Jeannette Wing) Department of Statistics Carnegie Mellon University Pittsburgh, PA 15213 2001 by Carnegie Mellon University
Analysis of Software Artifacts System Performance I Shu-Ngai Yeung (with edits by Jeannette Wing) Department of Statistics Carnegie Mellon University Pittsburgh, PA 15213 2001 by Carnegie Mellon University
Markovian Model of Internetworking Flow Control
 Информационные процессы, Том 2, 2, 2002, стр. 149 154. c 2002 Bogoiavlenskaia. KALASHNIKOV MEMORIAL SEMINAR Markovian Model of Internetworking Flow Control O. Bogoiavlenskaia Petrozavodsk State University
Информационные процессы, Том 2, 2, 2002, стр. 149 154. c 2002 Bogoiavlenskaia. KALASHNIKOV MEMORIAL SEMINAR Markovian Model of Internetworking Flow Control O. Bogoiavlenskaia Petrozavodsk State University
Size-based Adaptive Bandwidth Allocation:
 Size-based Adaptive Bandwidth Allocation: Optimizing the Average QoS for Elastic Flows Shanchieh Yang (scyang@ece.utexas.edu), Gustavo de Veciana (gustavo@ece.utexas.edu) Department of Electrical and Computer
Size-based Adaptive Bandwidth Allocation: Optimizing the Average QoS for Elastic Flows Shanchieh Yang (scyang@ece.utexas.edu), Gustavo de Veciana (gustavo@ece.utexas.edu) Department of Electrical and Computer
Competitive Management of Non-Preemptive Queues with Multiple Values
 Competitive Management of Non-Preemptive Queues with Multiple Values Nir Andelman and Yishay Mansour School of Computer Science, Tel-Aviv University, Tel-Aviv, Israel Abstract. We consider the online problem
Competitive Management of Non-Preemptive Queues with Multiple Values Nir Andelman and Yishay Mansour School of Computer Science, Tel-Aviv University, Tel-Aviv, Israel Abstract. We consider the online problem
Fairness comparison of FAST TCP and TCP Vegas
 Fairness comparison of FAST TCP and TCP Vegas Lachlan L. H. Andrew, Liansheng Tan, Tony Cui, and Moshe Zukerman ARC Special Research Centre for Ultra-Broadband Information Networks (CUBIN), an affiliated
Fairness comparison of FAST TCP and TCP Vegas Lachlan L. H. Andrew, Liansheng Tan, Tony Cui, and Moshe Zukerman ARC Special Research Centre for Ultra-Broadband Information Networks (CUBIN), an affiliated
Stabilizing Customer Abandonment in Many-Server Queues with Time-Varying Arrivals
 OPERATIONS RESEARCH Vol. 6, No. 6, November December 212, pp. 1551 1564 ISSN 3-364X (print) ISSN 1526-5463 (online) http://dx.doi.org/1.1287/opre.112.114 212 INFORMS Stabilizing Customer Abandonment in
OPERATIONS RESEARCH Vol. 6, No. 6, November December 212, pp. 1551 1564 ISSN 3-364X (print) ISSN 1526-5463 (online) http://dx.doi.org/1.1287/opre.112.114 212 INFORMS Stabilizing Customer Abandonment in
CDA5530: Performance Models of Computers and Networks. Chapter 4: Elementary Queuing Theory
 CDA5530: Performance Models of Computers and Networks Chapter 4: Elementary Queuing Theory Definition Queuing system: a buffer (waiting room), service facility (one or more servers) a scheduling policy
CDA5530: Performance Models of Computers and Networks Chapter 4: Elementary Queuing Theory Definition Queuing system: a buffer (waiting room), service facility (one or more servers) a scheduling policy
Singular perturbation analysis of an additive increase multiplicative decrease control algorithm under time-varying buffering delays.
 Singular perturbation analysis of an additive increase multiplicative decrease control algorithm under time-varying buffering delays. V. Guffens 1 and G. Bastin 2 Intelligent Systems and Networks Research
Singular perturbation analysis of an additive increase multiplicative decrease control algorithm under time-varying buffering delays. V. Guffens 1 and G. Bastin 2 Intelligent Systems and Networks Research
On the Tradeoff Between Blocking and Dropping Probabilities in CDMA Networks Supporting Elastic Services
 On the Tradeoff Between Blocking and Dropping Probabilities in CDMA Networks Supporting Elastic Services Gábor Fodor 1, Miklós Telek 2, and Leonardo Badia 3 1 Ericsson Research, SE-164 80 Stockholm, Sweden,
On the Tradeoff Between Blocking and Dropping Probabilities in CDMA Networks Supporting Elastic Services Gábor Fodor 1, Miklós Telek 2, and Leonardo Badia 3 1 Ericsson Research, SE-164 80 Stockholm, Sweden,
A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks
 A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks by Doo Il Choi, Charles Knessl and Charles Tier University of Illinois at Chicago 85 South
A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks by Doo Il Choi, Charles Knessl and Charles Tier University of Illinois at Chicago 85 South
Environment (E) IBP IBP IBP 2 N 2 N. server. System (S) Adapter (A) ACV
 The Adaptive Cross Validation Method - applied to polling schemes Anders Svensson and Johan M Karlsson Department of Communication Systems Lund Institute of Technology P. O. Box 118, 22100 Lund, Sweden
The Adaptive Cross Validation Method - applied to polling schemes Anders Svensson and Johan M Karlsson Department of Communication Systems Lund Institute of Technology P. O. Box 118, 22100 Lund, Sweden
Analysis of a Two-Phase Queueing System with Impatient Customers and Multiple Vacations
 The Tenth International Symposium on Operations Research and Its Applications (ISORA 211) Dunhuang, China, August 28 31, 211 Copyright 211 ORSC & APORC, pp. 292 298 Analysis of a Two-Phase Queueing System
The Tenth International Symposium on Operations Research and Its Applications (ISORA 211) Dunhuang, China, August 28 31, 211 Copyright 211 ORSC & APORC, pp. 292 298 Analysis of a Two-Phase Queueing System
Queues and Queueing Networks
 Queues and Queueing Networks Sanjay K. Bose Dept. of EEE, IITG Copyright 2015, Sanjay K. Bose 1 Introduction to Queueing Models and Queueing Analysis Copyright 2015, Sanjay K. Bose 2 Model of a Queue Arrivals
Queues and Queueing Networks Sanjay K. Bose Dept. of EEE, IITG Copyright 2015, Sanjay K. Bose 1 Introduction to Queueing Models and Queueing Analysis Copyright 2015, Sanjay K. Bose 2 Model of a Queue Arrivals
An M/M/1 Queue in Random Environment with Disasters
 An M/M/1 Queue in Random Environment with Disasters Noam Paz 1 and Uri Yechiali 1,2 1 Department of Statistics and Operations Research School of Mathematical Sciences Tel Aviv University, Tel Aviv 69978,
An M/M/1 Queue in Random Environment with Disasters Noam Paz 1 and Uri Yechiali 1,2 1 Department of Statistics and Operations Research School of Mathematical Sciences Tel Aviv University, Tel Aviv 69978,
Processor Sharing Flows in the Internet
 STANFORD HPNG TECHNICAL REPORT TR4-HPNG4 Processor Sharing Flows in the Internet Nandita Dukkipati, Nick McKeown Computer Systems Laboratory Stanford University Stanford, CA 9434-93, USA nanditad, nickm
STANFORD HPNG TECHNICAL REPORT TR4-HPNG4 Processor Sharing Flows in the Internet Nandita Dukkipati, Nick McKeown Computer Systems Laboratory Stanford University Stanford, CA 9434-93, USA nanditad, nickm
Approximate Queueing Model for Multi-rate Multi-user MIMO systems.
 An Approximate Queueing Model for Multi-rate Multi-user MIMO systems Boris Bellalta,Vanesa Daza, Miquel Oliver Abstract A queueing model for Multi-rate Multi-user MIMO systems is presented. The model is
An Approximate Queueing Model for Multi-rate Multi-user MIMO systems Boris Bellalta,Vanesa Daza, Miquel Oliver Abstract A queueing model for Multi-rate Multi-user MIMO systems is presented. The model is
1.225 Transportation Flow Systems Quiz (December 17, 2001; Duration: 3 hours)
 1.225 Transportation Flow Systems Quiz (December 17, 2001; Duration: 3 hours) Student Name: Alias: Instructions: 1. This exam is open-book 2. No cooperation is permitted 3. Please write down your name
1.225 Transportation Flow Systems Quiz (December 17, 2001; Duration: 3 hours) Student Name: Alias: Instructions: 1. This exam is open-book 2. No cooperation is permitted 3. Please write down your name
Non Markovian Queues (contd.)
 MODULE 7: RENEWAL PROCESSES 29 Lecture 5 Non Markovian Queues (contd) For the case where the service time is constant, V ar(b) = 0, then the P-K formula for M/D/ queue reduces to L s = ρ + ρ 2 2( ρ) where
MODULE 7: RENEWAL PROCESSES 29 Lecture 5 Non Markovian Queues (contd) For the case where the service time is constant, V ar(b) = 0, then the P-K formula for M/D/ queue reduces to L s = ρ + ρ 2 2( ρ) where
Exercises Stochastic Performance Modelling. Hamilton Institute, Summer 2010
 Exercises Stochastic Performance Modelling Hamilton Institute, Summer Instruction Exercise Let X be a non-negative random variable with E[X ]
Exercises Stochastic Performance Modelling Hamilton Institute, Summer Instruction Exercise Let X be a non-negative random variable with E[X ]
THE HEAVY-TRAFFIC BOTTLENECK PHENOMENON IN OPEN QUEUEING NETWORKS. S. Suresh and W. Whitt AT&T Bell Laboratories Murray Hill, New Jersey 07974
 THE HEAVY-TRAFFIC BOTTLENECK PHENOMENON IN OPEN QUEUEING NETWORKS by S. Suresh and W. Whitt AT&T Bell Laboratories Murray Hill, New Jersey 07974 ABSTRACT This note describes a simulation experiment involving
THE HEAVY-TRAFFIC BOTTLENECK PHENOMENON IN OPEN QUEUEING NETWORKS by S. Suresh and W. Whitt AT&T Bell Laboratories Murray Hill, New Jersey 07974 ABSTRACT This note describes a simulation experiment involving
Queuing Networks. - Outline of queuing networks. - Mean Value Analisys (MVA) for open and closed queuing networks
 Queuing Networks - Outline of queuing networks - Mean Value Analisys (MVA) for open and closed queuing networks 1 incoming requests Open queuing networks DISK CPU CD outgoing requests Closed queuing networks
Queuing Networks - Outline of queuing networks - Mean Value Analisys (MVA) for open and closed queuing networks 1 incoming requests Open queuing networks DISK CPU CD outgoing requests Closed queuing networks
Quality of Real-Time Streaming in Wireless Cellular Networks : Stochastic Modeling and Analysis
 Quality of Real-Time Streaming in Wireless Cellular Networs : Stochastic Modeling and Analysis B. Blaszczyszyn, M. Jovanovic and M. K. Karray Based on paper [1] WiOpt/WiVid Mai 16th, 2014 Outline Introduction
Quality of Real-Time Streaming in Wireless Cellular Networs : Stochastic Modeling and Analysis B. Blaszczyszyn, M. Jovanovic and M. K. Karray Based on paper [1] WiOpt/WiVid Mai 16th, 2014 Outline Introduction
Scheduling: Queues & Computation
 Scheduling: Queues Computation achieving baseline performance efficiently Devavrat Shah LIDS, MIT Outline Two models switched network and bandwidth sharing Scheduling: desirable performance queue-size
Scheduling: Queues Computation achieving baseline performance efficiently Devavrat Shah LIDS, MIT Outline Two models switched network and bandwidth sharing Scheduling: desirable performance queue-size
ON MAIN CHARACTERISTICS OF THE M/M/1/N QUEUE WITH SINGLE AND BATCH ARRIVALS AND THE QUEUE SIZE CONTROLLED BY AQM ALGORITHMS
 K Y B E R N E T I K A V O L U M E 4 7 ( 2 0 1 1 ), N U M B E R 6, P A G E S 9 3 0 9 4 3 ON MAIN CHARACTERISTICS OF THE M/M/1/N QUEUE WITH SINGLE AND BATCH ARRIVALS AND THE QUEUE SIZE CONTROLLED BY AQM
K Y B E R N E T I K A V O L U M E 4 7 ( 2 0 1 1 ), N U M B E R 6, P A G E S 9 3 0 9 4 3 ON MAIN CHARACTERISTICS OF THE M/M/1/N QUEUE WITH SINGLE AND BATCH ARRIVALS AND THE QUEUE SIZE CONTROLLED BY AQM
Performance analysis of IEEE WLANs with saturated and unsaturated sources
 1 Performance analysis of IEEE 8.11 WLANs with saturated and unsaturated sources Suong H. Nguyen, Student Member, IEEE, Hai L. Vu, Senior Member, IEEE, and Lachlan L. H. Andrew, Senior Member, IEEE Abstract
1 Performance analysis of IEEE 8.11 WLANs with saturated and unsaturated sources Suong H. Nguyen, Student Member, IEEE, Hai L. Vu, Senior Member, IEEE, and Lachlan L. H. Andrew, Senior Member, IEEE Abstract
One billion+ terminals in voice network alone
 Traffic Engineering Traffic Engineering One billion+ terminals in voice networ alone Plus data, video, fax, finance, etc. Imagine all users want service simultaneously its not even nearly possible (despite
Traffic Engineering Traffic Engineering One billion+ terminals in voice networ alone Plus data, video, fax, finance, etc. Imagine all users want service simultaneously its not even nearly possible (despite
The Performance Impact of Delay Announcements
 The Performance Impact of Delay Announcements Taking Account of Customer Response IEOR 4615, Service Engineering, Professor Whitt Supplement to Lecture 21, April 21, 2015 Review: The Purpose of Delay Announcements
The Performance Impact of Delay Announcements Taking Account of Customer Response IEOR 4615, Service Engineering, Professor Whitt Supplement to Lecture 21, April 21, 2015 Review: The Purpose of Delay Announcements
A POPULATION-MIX DRIVEN APPROXIMATION FOR QUEUEING NETWORKS WITH FINITE CAPACITY REGIONS
 A POPULATION-MIX DRIVEN APPROXIMATION FOR QUEUEING NETWORKS WITH FINITE CAPACITY REGIONS J. Anselmi 1, G. Casale 2, P. Cremonesi 1 1 Politecnico di Milano, Via Ponzio 34/5, I-20133 Milan, Italy 2 Neptuny
A POPULATION-MIX DRIVEN APPROXIMATION FOR QUEUEING NETWORKS WITH FINITE CAPACITY REGIONS J. Anselmi 1, G. Casale 2, P. Cremonesi 1 1 Politecnico di Milano, Via Ponzio 34/5, I-20133 Milan, Italy 2 Neptuny
1.225J J (ESD 205) Transportation Flow Systems
 1.225J J (ESD 25) Transportation Flow Systems Lecture 9 Simulation Models Prof. Ismail Chabini and Prof. Amedeo R. Odoni Lecture 9 Outline About this lecture: It is based on R16. Only material covered
1.225J J (ESD 25) Transportation Flow Systems Lecture 9 Simulation Models Prof. Ismail Chabini and Prof. Amedeo R. Odoni Lecture 9 Outline About this lecture: It is based on R16. Only material covered
Markov decision processes with threshold-based piecewise-linear optimal policies
 1/31 Markov decision processes with threshold-based piecewise-linear optimal policies T. Erseghe, A. Zanella, C. Codemo Dept. of Information Engineering, University of Padova, Italy Padova, June 2, 213
1/31 Markov decision processes with threshold-based piecewise-linear optimal policies T. Erseghe, A. Zanella, C. Codemo Dept. of Information Engineering, University of Padova, Italy Padova, June 2, 213
Análise e Modelagem de Desempenho de Sistemas de Computação
 Análise e Modelagem de Desempenho de Sistemas de Computação ``Performance Models Virgilio A. F. Almeida 1 o Semestre de 2009 Introdução: Semana #4 Computer Science Department Federal University of Minas
Análise e Modelagem de Desempenho de Sistemas de Computação ``Performance Models Virgilio A. F. Almeida 1 o Semestre de 2009 Introdução: Semana #4 Computer Science Department Federal University of Minas
Packet Loss Analysis of Load-Balancing Switch with ON/OFF Input Processes
 Packet Loss Analysis of Load-Balancing Switch with ON/OFF Input Processes Yury Audzevich, Levente Bodrog 2, Yoram Ofek, and Miklós Telek 2 Department of Information Engineering and Computer Science, University
Packet Loss Analysis of Load-Balancing Switch with ON/OFF Input Processes Yury Audzevich, Levente Bodrog 2, Yoram Ofek, and Miklós Telek 2 Department of Information Engineering and Computer Science, University
Dynamic Call Center Routing Policies Using Call Waiting and Agent Idle Times Online Supplement
 Dynamic Call Center Routing Policies Using Call Waiting and Agent Idle Times Online Supplement Wyean Chan DIRO, Université de Montréal, C.P. 6128, Succ. Centre-Ville, Montréal (Québec), H3C 3J7, CANADA,
Dynamic Call Center Routing Policies Using Call Waiting and Agent Idle Times Online Supplement Wyean Chan DIRO, Université de Montréal, C.P. 6128, Succ. Centre-Ville, Montréal (Québec), H3C 3J7, CANADA,
M/G/1/MLPS compared to M/G/1/PS
 Operations Research Letters 33 (25) 519 524 Operations Research Letters www.elsevier.com/locate/orl M/G/1/MLPS compared to M/G/1/PS Samuli Aalto a,, Urtzi Ayesta b, Eeva Nyberg-Oksanen a,1 a Networking
Operations Research Letters 33 (25) 519 524 Operations Research Letters www.elsevier.com/locate/orl M/G/1/MLPS compared to M/G/1/PS Samuli Aalto a,, Urtzi Ayesta b, Eeva Nyberg-Oksanen a,1 a Networking
Multiserver Queueing Model subject to Single Exponential Vacation
 Journal of Physics: Conference Series PAPER OPEN ACCESS Multiserver Queueing Model subject to Single Exponential Vacation To cite this article: K V Vijayashree B Janani 2018 J. Phys.: Conf. Ser. 1000 012129
Journal of Physics: Conference Series PAPER OPEN ACCESS Multiserver Queueing Model subject to Single Exponential Vacation To cite this article: K V Vijayashree B Janani 2018 J. Phys.: Conf. Ser. 1000 012129
Stationary remaining service time conditional on queue length
 Stationary remaining service time conditional on queue length Karl Sigman Uri Yechiali October 7, 2006 Abstract In Mandelbaum and Yechiali (1979) a simple formula is derived for the expected stationary
Stationary remaining service time conditional on queue length Karl Sigman Uri Yechiali October 7, 2006 Abstract In Mandelbaum and Yechiali (1979) a simple formula is derived for the expected stationary
On the static assignment to parallel servers
 On the static assignment to parallel servers Ger Koole Vrije Universiteit Faculty of Mathematics and Computer Science De Boelelaan 1081a, 1081 HV Amsterdam The Netherlands Email: koole@cs.vu.nl, Url: www.cs.vu.nl/
On the static assignment to parallel servers Ger Koole Vrije Universiteit Faculty of Mathematics and Computer Science De Boelelaan 1081a, 1081 HV Amsterdam The Netherlands Email: koole@cs.vu.nl, Url: www.cs.vu.nl/
TRANSMISSION STRATEGIES FOR SINGLE-DESTINATION WIRELESS NETWORKS
 The 20 Military Communications Conference - Track - Waveforms and Signal Processing TRANSMISSION STRATEGIES FOR SINGLE-DESTINATION WIRELESS NETWORKS Gam D. Nguyen, Jeffrey E. Wieselthier 2, Sastry Kompella,
The 20 Military Communications Conference - Track - Waveforms and Signal Processing TRANSMISSION STRATEGIES FOR SINGLE-DESTINATION WIRELESS NETWORKS Gam D. Nguyen, Jeffrey E. Wieselthier 2, Sastry Kompella,
