On the numerical solution of large-scale sparse discrete-time Riccati equations CSC/ Chemnitz Scientific Computing Preprints
|
|
|
- Baldric Heath
- 5 years ago
- Views:
Transcription
1 Peter Benner Heike Faßbender On the numerical solution of large-scale sparse discrete-time Riccati equations CSC/09-11 Chemnitz Scientific Computing Preprints
2 Impressum: Chemnitz Scientific Computing Preprints ISSN ( : Preprintreihe des Chemnitzer SFB393) Herausgeber: Professuren für Numerische und Angewandte Mathematik an der Fakultät für Mathematik der Technischen Universität Chemnitz Postanschrift: TU Chemnitz, Fakultät für Mathematik Chemnitz Sitz: Reichenhainer Str. 41, Chemnitz
3 Chemnitz Scientific Computing Preprints Peter Benner Heike Faßbender On the numerical solution of large-scale sparse discrete-time Riccati equations CSC/09-11 CSC/09-11 ISSN December 2009
4 Contents 1 Introduction 1 2 Newton s method for discrete-time algebraic Riccati equations 5 3 Smith s Method and ADI Iteration Smith s method ADI Iteration Numerical Examples 23 5 Conclusions 28 Author s addresses: Peter Benner TU Chemnitz Fakultät für Mathematik D Chemnitz benner@mathematik.tu-chemnitz.de Heike Faßbender TU Braunschweig Carl-Friedrich-Gauß-Fakultät Institut Computational Mathematics AG Numerik Braunschweig h.fassbender@tu-bs.de
5 Abstract The numerical solution of Stein (aka discrete Lyapunov) equations is the primary step in Newton s method for the solution of discrete-time algebraic Riccati equations (DARE). Here we present a low-rank Smith method as well as a low-rank alternating-direction-implicit-iteration to compute lowrank approximations to solutions of Stein equations arising in this context. Numerical results are given to verify the efficiency and accuracy of the proposed algorithms. Keywords. Riccati equation, discrete-time control, sparse matrices, Newton s method, Smith iteration, ADI iteration, low rank factor. AMS subject classifications (MSC2010). 65F30, 15A24, 93C20, 93C05. 1 Introduction After full (time and spatial) discretization, the solution of optimal control problems for parabolic partial differential equations (PDEs) leads to generalized largescale, sparse discrete time algebraic Riccati equation (DARE) 0 = R(X) = CQC T + AXA T EXE T (1) (AXB T + CS T )(R + BXB T ) 1 (BXA T + SC T ), where A and E R n n are large and sparse, B R m n, C R n p, Q R p p, R R m m, S R m p, and Q and R are symmetric. We also assume E to be invertible throughout. In the last decades, much research has addressed the construction of numerically robust algorithms for the solution of (1). However, these methods generally have at least a memory complexity O(n 2 ) and a computational complexity O(n 3 ), regardless whether or not the system matrix A is sparse or otherwise structured. Therefore, the majority of numerical algorithms is restricted to systems of moderate order. Of course, the upper limit for this order depends on the problem to be solved as well as the particular computing environment and may vary between a few hundreds and a few thousands. However, a significant number of applications lead to systems of larger order. Large systems arise from the semi-discretization of (possibly linearized) PDEs by means of finite differences or finite elements, see e.g. [4, 36, 40], and many more. Consider, e.g., the problem Minimize J (u) = y(t) T Qy(t) + u(t) T Ru(t) + 2y(t) T Su(t)dt
6 subject to the PDE constraint x(ζ, t) = (k(ζ) )x + c(ζ) x + r(ζ)x + b(ζ)u in Ω [0, T ], t x(ζ, t) = 0 on Ω, x(ζ, 0) = x 0 (ζ) on Ω, y(t) = c(ζ)x(ζ, t)dζ, Ω 0 Ω 0 Ω. Discretizing the PDE constraint using a finite-difference scheme or a finite element approach leads to a constraint in form of an ordinary differential equation Mẋ(t) = Kx(t) + F u, y(t) = Cx(t), where M and K are large, sparse square matrices, M is positive definite and K is negative definite. Employing further a time discretization a difference equation of the form Ex k+1 = Ax k + Bu k is obtained. In case the semi-implicit Euler method with stepsize t is used, one obtains (M tk)x k+1 = Mx k + tf u k, (2) that is A = M, E = M tk and B = tf. Alternatively, a Crank-Nicholsontype discretization can be used. Here, we will use the average of a forward Euler and a semi-implicit Euler step in time. That is, we average the equations Mx k+1 = (M + tk)x k + tf u k, Mx k+1 = Mx k + tkx k+1 + tf u k, and obtain (M t 2 K)x k+1 = (M + t 2 K)x k + tf u k, y k = Cx k. The discretized optimal control problem now reads Minimize J (u) = 1 2 yk T Qy k + u T k Ru k + 2yk T Su k k=0 subject to Ex k+1 = Ax k + Bu k, y k = Cx k, 2
7 where E = M t t K, A = M + K, B = tf. 2 2 Under generic control-theoretic conditions, the optimal solution of this minimization problem is given by the feedback control u k = (R + B T X d B) 1 (B T X d A + S T C)x k, k = 0, 1,..., where X d is the stabilizing solution of the DARE (1); see, e.g., [21, 39, 44, 52] and many other textbooks on control theory. DAREs also arise in other applications such as H -control, factorization problems for rational matrix functions, Kalman filtering. An overview of some of these applications is given in [39, Chapter 5]. A detailed discussion of the solution theory for the case E = I (which is equivalent to the case E nonsingular) is given in [39], whereas the case of singular E is treated in [44]. Solutions of the optimal control problem without solving the corresponding Riccati equation are given in [7, 16, 35, 43, 44], including the singular E case. It should be noted, though, that DARE-free solutions of the linear-quadratic discrete-time optimal control problem require the full n-dimensional deflating subspace of the corresponding (generalized) symplectic pencil. For large-scale problems, this is prohibitive as even if the sparsity structure of the problemdefining matrices could be employed, the subspace itself would require memory of size 2n 2. Mostly, systems originating from the application mentioned above possess two interesting properties. First, their order n is large (say, n > 1000), but the dimensions of the input and output spaces are relatively small (m, q n, often m, q 10). For example, the order of a system arising from a parabolic PDE is about the number of grid points or mesh nodes used for the semi-discretization w.r.t. the spatial coordinates, which is relatively large. In contrast, m and q are often quite small and independent of the fineness of the discretization. Second, the system matrix A is structured. Often, A is a sparse matrix or it is implicitly represented as a product of sparse matrices and inverses of sparse matrices. In general, this structure allows the numerically inexpensive realization of matrixvector products and the efficient solution of systems of linear equations with A. In the sequel we will use the abbreviation K(X) := (AXB T + CS T )(R + BXB T ) 1, (3) to simplify the notation and we will make the following assumptions: 3
8 1. E is nonsingular. 2. R = R] T > [ Q S S T R 4. A stabilizing solution X d of (1) exists, that is, a solution X d exists such that the eigenvalues of (A K(X d )B) λe lie in the open unit circle: (σ(a K(X d )B, E) D 1 (0)). It is unique, and furthermore, R + BX d B T > 0. (4) For sufficient conditions for 4. to hold, see, e.g., [39, Theorem ]. In principle, by inverting E, (1) can be reduced to the case E = I. However, this introduces unnecessary rounding errors and, if E is ill-conditioned, even numerical instability. Therefore, inverting E is avoided here. Considering E is important, as in the PDE control problems E I, and as E is large and sparse, its inverse in general would be large and dense, so that the large, sparse generalized DARE would be transformed into a large, dense one for which there do not exist any suitable numerical methods yet. The solution of DAREs has been an extremely active area of research, see, e.g., [21, 44, 52] for an overview. The usual solution methods for DAREs such as the Schur vector method [46], symplectic SR methods [12, 23], the matrix sign function [7, 15, 26, 51], the matrix disk function [7, 15, 39, 55] or the doubling method [52, 42] do not make (full) use of the sparse structure of A, E and require in general O(n 3 ) flops and workspace of size O(n 2 ) even for sparse problems, and are therefore not suitable here. The numerical solution of several types of large-scale matrix equations with sparse coefficient matrices arising in control theory has been the target of numerous papers in the last decade. Significant progress has been made in particular for continuous Lyapunov and algebraic Riccati equations, e.g., [8, 13, 53, 41, 49, 33]. For an overview and further references, see [9]. It is the aim of this paper to extend some of these results to DAREs. We will follow in particular the approach taken in [13]. That is, we will make use of the fact that R(X) = 0 defines a system of nonlinear equations and can hence be solved by an appropriate Newton method as proposed in [32, 3]. Newton s method is reviewed in Section 2. The main computational cost in the algorithm stems from the numerical solution of the Stein equation. Section 3 proposes low rank Smith and ADI iterations for its solution based on [13, 17, 41, 49]. Both methods compute an approximate lowrank Cholesky factor of the desired solution. Numerical experiments are reported in Section 4. 4
9 2 Newton s method for discrete-time algebraic Riccati equations The function R(X) in (1) is a rational matrix function, R(X) = 0 defines a system of nonlinear equations. Inspired by Kleinman s formulation of a Newton method for continuous-time algebraic Riccati equations [37], Hewer [32] proposed a Newton method for solving DAREs. The algorithm was extended to the generalized equation as given in (1) by Arnold and Laub [3]. A discussion of its convergence properties can be found in [39, 44]. Newton s method for the numerical solution of DAREs can be formulated as given in Algorithm 1. Algorithm 1 Newton s Method for the DARE Input: The coefficient matrices A, B, C, E, Q, R, S of the DARE (1), and a starting guess X 0, so that σ(a K(X 0 )B, E) D 1 (0) and R + BX 0 B T > 0. Output: An approximate solution X k+1 of the DARE (1) and an estimate N k for the error matrix X X k+1, where X is the stabilizing solution of R(X) = 0. for k = 0, 1, 2,... do 1. K k K(X k ). 2. A k A K k B. 3. R k R(X k ). 4. Solve for N k in the Stein equation A k N k A T k EN k E T = R k. 5. X k+1 X k + N k. end for We have the following convergence result for Algorithm 1 [32, 39, 44]. Theorem 2.1 If the assumptions (4) hold, and X 0 is stabilizing, then for the iterates produced by Algorithm 1 we have: a) All iterates X k are stabilizing, i.e., σ(a K(X k )B, E) D 1 (0) for all k N 0. b) X d... X k+1 X k... X 1. c) lim k X k = X d. 5
10 d) There exists a constant γ > 0 such that X k+1 X d γ X k X d 2, k 1, i.e., the X k converge globally quadratic to X d. The formulation of Algorithm 1 is analogous to the standard formulation of Newton s method as given, e.g., in [22, Algorithm 5.1.1] for the solution of nonlinear equations. Because of its robustness in the presence of rounding errors, in dense matrix computations one prefers to calculate the Newton step explicitly as in Algorithm 1 using the Stein equation A k N k A T k EN k E T = R k (5) rather than to use the mathematically equivalent formulation of the Newton step [3, 32, 39, 44], A k X k+1 A T k EX k+1 E T = CQC T + CS T K T k + K k SC T K k RK T k =: C(X k ) = C k, (6) which determines X k+1 directly. The coefficient matrices of the two Stein equations are the same, but the right-hand-sides are different; see Algorithm 2. Algorithm 2 Newton-Hewer Method for the DARE Input: The coefficient matrices A, B, C, E, Q, R, S of the DARE (1), and a starting guess X 0, so that σ(a K(X 0 )B, E) D 1 (0) and R + BX 0 B T > 0. Output: An approximate solution X k+1 of the DARE (1). for k = 0, 1, 2,... do 1. K k K(X k ). 2. A k A K k B. 3. C k C(X k ). 4. Solve for X k+1 in the Stein equation end for A k X k+1 A T k EX k+1 E T = C k. The problem for the successful application of the Newton method is to find a stabilizing initial guess X 0. There exist stabilization procedures for discrete-time linear systems (see, e.g., [2, 38, 52]). But these may give large initial errors X d X 0. The procedure suggested in [38] is even unfeasable for numerical computations as it is based on explicitly summing up A k BB T (A T ) k for k up to n, thereby often causing overflow already for small values of n. Suitable initialization procedures are suggested in [10, 11] which work quite well in practice, but 6
11 cannot exploit sparsity of the problem and are therefore not suitable for largescale problems. An iterative procedure for stabilizing large-scale discrete-time systems is suggested in [25] and can be used for our purposes. Despite the ultimate rapid convergence indicated by Theorem 2.1 d), the iteration may initially converge slowly. This can be due to a large initial error X d X 0 or a disastrously large first Newton step resulting in a large error X d X 1. In both cases, it is possible that many iterations are required to find the region of rapid convergence. An ill-conditioned Stein equation makes it difficult to compute an accurate Newton step. An inaccurately computed Newton step can cause the usual convergence theory to break down in practice. Sometimes rounding errors or a poor choice of X 0 cause Newton s method to converge to a nonstabilizing solution. Fortunately, in PDE control as considered here, we often have σ(e, A) D 1 (0), so that X 0 = 0 is an appropriate starting guess. The computational cost for Algorithms 1 and 2 mainly depends upon the cost for the numerical solution of the Stein equation (5), (6), resp.. This can be done using the Bartels Stewart algorithm [5, 6] or an extension to the case E I [27, 28, 48]. The Bartels-Stewart algorithm is the standard direct method for the solution of Stein equations of small to moderate size. This method requires the computation of a Schur decomposition, and thus is not appropriate for large scale problems. The cost for the solution of the Stein equation is 73n 3 flops. See [52] for a discussion of an efficient implementation. In [52], the following idea based on [31, 56] how to solve stable nonnegative Stein equations AXA H X = C (7) where C C n n is positive semidefinite and A C n n is stable, is also discussed: The unique solution X is positive semidefinite and hence allows for a Cholesky factorization X = LL H. Let U be the unitary matrix that reduces A to upper Schur form T = UAU H, such that we have (U H T U)(LL H )(U H T H U) LL H = BB H where BB H = C and B C n m, m n. Or, equivalently, T (UL)(L H U H )T H (UL)(L H U H ) = (UB)(B H U H ). Using the RQ factorizations of UB and UL we obtain T ZZ H T H ZZ H = RR H, where Z and R are triangular matrices. This equation can be solved efficiently in Z, the Cholesky factor of the solution of the original equation (7), see [52] for details. The memory space needed for the data is 2n 2, while the computational cost is about cn 3 flops, where c is of the order of unity. Although this method 7
12 is not suitable in the context of large sparse DAREs, we will make use of the idea of computing only a (Cholesky) factor of the desired solution. Other iterative schemes for solving the Stein equation (5), (6), resp., have been developed. Most of these were first formulated for the continuous-time case. Examples are the Smith method [54], the sign-function method [51], and the alternating direction implicit (ADI) iteration method [57]. Unfortunately, all of these methods compute the solution in dense form and hence require O(n 2 ) storage. In case the solution to the Stein equation has low numerical rank (i.e., the eigenvalues decay rapidly) one can take advantage of this low rank structure to obtain approximate solutions in low rank factored form [14]. If the effective rank is r n, then the storage is reduced from O(n 2 ) to O(nr). This approach will be discussed in detail in Section 3. 3 Smith s Method and ADI Iteration In this section, iterative methods for solving the equivalent Stein equations A k Y A T k EY E T = R k (8) and with A k Y A T k EY E T = C k (9) A k = A K k B, K k = K(X k ), R k = R(X k ), C k = C(X k ) will be discussed. In particular, it will be assumed that the solution Y has numerically low rank. This is usually the case if the DARE stems from a discretized PDE control problem as illustrated in Figure 1, where the eigenvalues of the solution of the DARE corresponding to the discrete heat equation example from the SLICOT Model Reduction Benchmark Collection [19] are shown, see also Example 4.2. Here, the numerical rank of X is 31 as compared to n = 200. The symmetric Stein equation S ASA T = V, (10) where A and V are given n n matrices and V is symmetric, has a unique solution S (necessarily symmetric) provided zw 1 for every pair of eigenvalues z, w of A, see [39, pp ]. In particular, this is the case when all eigenvalues of A lie in the open unit disk. Then the unique solution is given by S = A j V A T j (11) j=0 8
13 Figure 1: Decay of the eigenvalues of the DARE solution corresponding to the discrete heat equation example from [19] with n = 200, m = p = 1. (the series converges because z 0 < 1 for every z 0 σ(a)). Moreover, if all eigenvalues of A are in the open unit disk, then we have for the unique solution S of (10) S 0 if V 0. From this we have, that for given matrices A k, E R n n the Stein equations (8) and (9) have a unique solution if and only if λ r λ s 1 for any λ r, λ s σ(a k, E). Hence, as the Stein equation (8) (or (9), respectively) arises in the Newton iteration, Theorem 2.1a) guarantees here the existence of a unique symmetric solution of the Stein equation. 3.1 Smith s method The Smith iteration [54] is derived from the symmetric Stein equation (10) and its representation (11) S 0 = 0, S j+1 = V + AS j A T. If all eigenvalues of A lie in the open unit disk, this iteration converges and the iterates can be written as j 1 S j = A i V A T i, j = 1, 2,.... i=0 9
14 Its rate of convergence is quite slow, in general. The accelerated version [54] the so-called squared Smith method is based on the recursion Its iterates can be written as S 0 = V, S j+1 = S j + A 2j S j A T 2j. (12) 2 j S j = A i 1 V A T (i 1). i=1 Despite the quadratic convergence rate, one should be reluctant to apply the squared method to large, sparse equations. The matrices A 2j, which have to be squared explicitly in each step of the iteration, are dense even if A is sparse. We will discuss how to use the standard Smith iteration efficiently for solving the Stein equations (8) and (9) in the context of large, sparse equations. The idea behind this is based on a low-rank version of (12) as proposed, e.g., in [14]. The Smith iteration for (8) is given by while for (9) it is given by EY j+1 E T = A k Y j A T k + R k, (13) EY j+1 E T = A k Y j A T k + C k. (14) The last term on the right hand side of (14) can be expressed as As [ Q S S T R C k = CQC T CS T Kk T K k SC T + K k RKk T [ ] [ ] Q S T C T = [C K k ]. S R K T k ] 0, we can obtain a (Cholesky) factorization [ Q S T [C K k ] S R [ = [C K k ] = [ ] [ C T K T k ] L 0 SL T W CL 0 K k SL T K k W ] [ L T L 1 S T ] [ C T 0 W T ] [ L T C T L 1 S T Kk T 0 W T K T k K T k ] ] = UU T (15) with Q = LL T, and W W T = R SL 1 L T S T. The latter expression is positive semidefinite due to Assumption 3. on page 4. Therefore, UU T 0. When the 10
15 iteration (14) is started with Y 0 = 0, then Y 1 = E 1 UU T E T and all subsequent iterates j 1 Y j = (E 1 A k ) i E 1 UU T E T (A T k E T ) i, j = 1, 2,... i=0 are symmetric positive semidefinite and converge to a positive semidefinite matrix Y. Based on the assumption that the spectrum of the positive semidefinite matrix Y decays to zero very rapidly, we can expect that Y can be written using a factorization ZZ T for some Z R n r, r n. Now, if we assume that Y j = Z j Zj T for rank(z j ) = r j n, Z j R n r j and observe that rank(uu T + A k Y j A T k ) m + p + r j n, we see that we can solve (14) for a low-rank representation of the (Cholesky) factor of Y j. In particular, we have [ (Z (EZ j+1 )(Zj+1E T T ) = (A k Z j )(Zj T A T k ) + UU T T [A k Z j U] j A T k ) ] U T Hence, = MM T. (16) EZ j+1 = [A k Z j U] yields one possible representation of the solution Y j+1. Thus, the Smith algorithm can be reformulated in terms of the (Cholesky) factor Z j of Y j. There is no need to compute Y j at each iteration; only Z j is needed. Incorporating this Smith iteration into Algorithm 2 we obtain Algorithm 3. Remark 3.1 For Z 0 = 0 it is straightforward to see that Z j = E 1 [ (A k E 1 ) j 1 U (A k E 1 ) j 2 U... (A k E 1 )U U ]. If Z j R n r j, then M in (16) is in R n (rj+p+m) and, as E R n n, Z j+1 R n (rj+p+m). The dimension of Z j+1 will increase by p + m in each iteration step. Hence, if p + m is large and/or the convergence is slow, the number of columns of Z j+1 will easily reach unmanageable levels of memory requirements. But if Z j+1 is of low rank r j+1, then we can approximate it as follows. The rank-revealing LQ decomposition [20, 29] of M yields [ ] L11 0 ΠM = V, L Ω 11 R r j+1 r j+1, L 21 R (n r j+1) r j+1, L 21 where L 11 is lower triangular, V R n (n+rj) is orthogonal, Π is a permutation, and Ω 0 can be regarded as negligible. If we partition V in the form [ ] V1 V =, V 1 R rj+1 n, V 2 11
16 Algorithm 3 Newton-Hewer-Smith Method for the DARE Input: The coefficient matrices A, B, C, E, Q, R, S of the DARE (1), and a starting guess X 0 in terms of its (Cholesky) factor T 0, so that σ(a K(X 0 )B, E) D 1 (0) and R + BX 0 B T > 0. Output: An approximate solution X k+1 of the DARE (1) in terms of its (Cholesky) factor T k+1. Compute the Cholesky factorization [ Q S S T R ] = LL T. for k = 0, 1, 2,... do 1. K k K(X k ) (making use of the fact that X k = T k T T k ). 2. A k A K k B. 3. U [C K k ]L. 4. Z 0 0. for j = 0, 1, 2,... do 5. Solve for Z j+1 in EZ j+1 = [A k Z j U]. end for 6. T k+1 Z j+1 end for and set Ω = 0, we obtain the full-rank approximation M = Π T [ L11 L 21 In any unitary invariant norm, we have Now we approximate Hence ] V 1 = Π LV 1, L R n r j+1. M M = Ω. (EZ j+1 )(Z T j+1e T ) M M T = Π T L LT Π. EZ j+1 Π T L yields one possible approximate low-rank representation of the solution Y j+1 of (14) such that Z j+1 R n r j+1. Alternatively, as suggested for the Smith iteration in [30], a thin singular value decomposition [29] of M can be employed, M = UΣV T, where, with l = r j + p + m, V R l l, V T V = I, U R n l has orthonormal columns and Σ = diag(σ 1,..., σ l ) R l l, σ 1 σ 2... σ l. Partition this decomposition as [ ] Σ1 [V ] T M = [U 1 U 2 ] 1 V2 T, Σ 2 12
17 where Σ 1 R r j+1 r j+1, V 1 R l r j+1, U 1 R n r j+1. In case Σ 2 is negligible, we can approximate M by M = U 1 Σ 1 V1 T. By the Schmidt-Eckart-Young-Mirsky-theorem we have Now we approximate M M = σ rj Hence (EZ j+1 )(Z T j+1e T ) M M T = U 1 Σ 1 V T 1 V 1 Σ 1 U T 1 = U 1 Σ 2 1U T 1. EZ j+1 U 1 Σ 1 yields another possible approximate low-rank representation of the solution Y j+1 of (14) such that Z j+1 R n r j+1. Therefore, instead of computing the solution Y of (9) directly, we only compute an approximation to its low rank factor Z with Y = ZZ T. In order to make use of this representation of the solution we have to modify Algorithm 3 by replacing Step 7. appropriately, see Algorithm 4. That is, we simply ignore the trailing part of L which is less than or equal to some given tolerance. While going from the jth to the (j + 1)st step, the number of columns of Z j+1 generally does not increase. Indeed an increase will only occur if the rank of Z j+1 is larger than that of Z j. In any case, there can be at most n additional columns added at any step which is the same as in the unmodified version. Let us assume that X k = T k Tk T to compute the (Cholesky) factorization of with T k R n s k. In order to obtain Zj+1 one has [ Q S S T R ] R (p+m) (p+m), this requires O((p + m) 3 /3) flops [29] but only needs to be computed once before the iteration is started; evaluate K k, this involves five matrix-matrix products of matrices of size m n and n s k, m s k and s k m (for R + (BT k )(T T k BT ), re-using BT k and exploiting symmetry), s k n and n n, m s k and s k n (for (BT k )(T T k A), re-using BT k from the previous computation), and m p and p n (for SC T, which should be precomputed), and a linear solve with a system matrix of size m m and a right hand side of size m n which requires O(2m 3 /3) flops [29] plus forward and backward substitution; compute U, this involves one matrix-matrix product of matrices of size n (p + m) and (p + m) (p + m); compute A k Z j = AZ j K k (BZ j ) for j = 0, 1,..., this involves three matrixmatrix products of matrices of size n n and n r j, m n and n r j, and n m and m r j in each iteration step; 13
18 Algorithm 4 Low Rank Newton-Hewer-Smith Method for the DARE Input: The coefficient matrices A, B, C, E, Q, R, S of the DARE (1), and a starting guess X 0 in terms of its (Cholesky) factor T 0, so that σ(a K(X 0 )B, E) D 1 (0) and R + BX 0 B T > 0. Output: An approximate solution X k+1 of the DARE (1) in terms of its low rank (Cholesky) factor T k+1. Compute the Cholesky factorization [ Q S S T R ] = LL T. for k = 0, 1, 2,... do 1. K k K(X k ) (making use of the fact that X k = T k Tk T ). 2. A k A K k B. 3. C k C(X k ). 4. U [C K k ]L. 5. Z 0 0. for j = 0, 1, 2,... do [ L Compute the RRLQ factorization Π[A k Z j U] = [ ] L 21 Ω V1, V 1 R r j+1 n L 11 R r j+1 r j+1, V = [ ] 7. L L11. L 12 V 2 8. Solve for Z j+1 in EZ j+1 = Π L. end for 9. T k+1 Z j+1 end for ] V, 14
19 compute the rank-revealing LQ decomposition of M = [A k Z j U], this requires 4n(m + p + r j )r j+1 2(n + m + p + r j )rj r3 j+1 flops (see, e.g., [29, Section 5.4.1]) noting that Q need not be accumulated; solve EZ j+1 = Π L for Z j+1 for j = 0, 1,..., this involves a (sparse) linear solve with a system matrix of size n n and a right hand side of size n r j+1. Please note, that the (sparse) LU decomposition of E needs to be computed only once, the rest of the computations are solely forward and backward solves. In the case of a DARE coming from a discretized PDE control problem, E will often be positive definite so that a (sparse) Cholesky decomposition can be employed and the factorization cost can be halved. Hence, the overall flop count for the computation of Z j+1 depends mainly on the choice of the solver for the linear systems in the outer loop as well as on the cost of the rank-revealing LQ decomposition in the inner loop and the pre-computable (Cholesky) factorizations. The iteration (13) does not allow a factored representation of the solution Y j+1 as R k might be indefinite. But (in contrast to the continuous-time case) R k can be split explicitly into its positive and negative semidefinite part P k and N k, resp., with P k = CQC T + AX k A T, R k = P k N k N k = EX k E T + (AX k B T + CS T )(R + BX k B T ) 1 (BX k A T + SC T ). Splitting the iterates into their positive and negative semidefinite parts Yj P, resp., Y N j we have Y j = Y P j Y N j E(Yj+1 P Yj+1)E N T = A k (Yj P Yj N )A T k + (P k N k ), that is, we can iterate on the positive and negative semidefinite parts separately and EYj+1E P = A k Yj P A T k + P k, (17) EYj+1E N = A k Yj N A T k + N k. (18) Now, with Q = LL T and X k = T k T T k, T k R n s k, we have [ L P k = CQC T + AX k A T = CLL T C T + AT k Tk T A T = [CL AT k ] T C T Tk T AT ]. 15
20 Writing Y P j = Z P j (Z P j ) T we obtain EZj+1(Z P j+1) P T E T = [ ] A k Zj P CL AT k (Z P j ) T A T k L T C T T T k AT. Hence, EZ P j+1 = [ A k Z P j CL AT k ] is one possible representation of the (Cholesky) factor Z P j+1 of the positive semidefinite part Y P j+1 of Y j+1. If Z P j R n rp j, then EZ P j+1 R n (rp j +p+s k) and, as E R n n, Z P j+1 R n (rp j +p+s k). The dimension of Z P j+1 would increase in each iteration step. But if Z P j+1 is of low rank r P j+1, then we can approximate it using a rank-revealing LQ factorization as before. Moreover, with X k = T k T T k and R + BX kb T = S k S T k we have N k = EX k E T + (AX k B T + CS T )(R + BX k B T ) 1 (BX k A T + SC T ) = EX k E T + (AX k B T + CS T )S T k = [ ET k (AX k B T + CS T )S T k S 1 From this, we obtain EYj+1E N = [ A k Zj N ET k ] (AX k B T + CS T )S T k (BX ka T + SC T ) ] [ Tk T ET S 1 k (BX ka T + SC T ) k ]. (Z N j ) T A T k T T k ET S 1 k (BX ka T + SC T ). Hence, with Y N j = Z N j (Z N j ) T EZj+1 N = [ ] A k Zj N ET k (AX k B T + CS T )S T k is one possible representation of a factor Z N j+1 of the negative semidefinite part Y N j+1 of Y j+1. If Z N j R n rn j, then EZ N j+1 R n (rn j +m+s k) and, as E R n n, Z N j+1 R n (rn j +m+s k). The dimension of Z N j+1 would increase in each iteration step. But if Z N j+1 is of low rank r N j+1, then we can approximate it using a rankrevealing LQ factorization as before. From Zj+1 P and Zj+1, N one can determine Y j+1 = Zj+1(Z P j+1) P T Zj+1(Z N j+1) N T. The overall flop count for this computation of Y j+1 is higher than the one for the iteration (14). As for (14), K k and A k have to be set up. In case this is (BX ka T + SC T ) is computed as ] by-product when R (p+m) (p+m), done in a reasonable way, S 1 k setting up K k. Instead of the (Cholesky) factorization of here only the factorization of Q = LL T [ Q S S T R R p p is needed. While before, A k Z j 16
21 was computed, we now need A k Z P j, A k Z N j, AT k and ET k. Moreover, two instead of one rank-revealing QL factorizations have to be computed and two linear systems with the system matrix E have to be solved (this can be done using one factorization of E). As the solution Y j+1 is constructed from two different iterations, one should use some kind of defect correction in order to increase the accuracy of the solution and to generate the (Cholesky) factor of Y j+1. The first idea that might come to mind is to use the following result from [45]. Theorem 3.2 Let X be an Hermitian solution of 0 = R(X), and let X be an Hermitian approximation to X. Let V = X X. If R = R + B XB T and I + V B T R 1 B are nonsingular, then V satisfies the equation 0 = R( X) EV E T + ÃV ÃT (ÃV BT ) T ( R + BV B T ) 1 (ÃV BT ) where à T = B T R 1 CS T + (I B T R 1 B X)A T. Unfortunately, the resulting algorithm can not be used here, as in each iteration step, one has to solve (1). Using the approach discussed above, this would lead to a solution in terms of (Cholesky) factors of the positive and the negative semidefinite part of the solution and not to a (Cholesky) factor of the solution itself. A different option might be to make use of the following observation which allows us to solve the DARE in each iteration step so that the desired (Cholesky) factor of the solution itself is computed. A formidable computation [39, p.312] shows that the DARE (1) can be rewritten as with EY E T ĂY ĂT = Q + (CS T K(Y )R)R 1 (CS T K(Y )R) T (19) Ă = A K(Y )B Q = CQC T CS T R 1 SC T = C ( Q S T R 1 S ) C T and K(Y ) as in (3) as a symmetric Stein equation. As Q S T R] 1 S is the Schur complement of R in the positive semidefinite matrix [34], Q is symmetric positive semidefinite. Now, denote the solution of (1) obtained by the [ Q S S T R 17
22 Smith iteration (17) (18) by Y. Fix the right hand side of (19) by evaluating K(Y ) = K, EY E T ĂY ĂT = Q + (CS T K R)R 1 (CS T K R) T. (20) We will use this as a defect correction and update our approximate solution Y by Y which is the solution of E Y E T = Ă Y ĂT + Q + (CS T K R)R 1 (CS T K R) T. (21) This may be done by the Smith iteration (14) where we substitute A k by Ă and C k by C k = Q + (CS T K R)R 1 (CS T K R) T. A disadvantage of the Smith iteration is that its convergence is linear and the rate is bounded by ρ k = max{ λ, λ σ(a k, E)}. As ρ k can be close to 1, this may be very slow. The ADI iteration discussed next offers an alternative. 3.2 ADI Iteration The alternating direction implicit (ADI) iteration was first introduced [47] to solve linear systems arising from the discretization of elliptic boundary value problems. In general, the ADI iteration is used to solve linear systems of the form My = b, where M is symmetric positive definite and can be split into the sum of two positive definite matrices M = M 1 + M 2 for which the following iteration is efficient: y 0 = 0, (M 1 + µ j I)y j 1/2 = b (M 2 µ j I)y j 1, (M 2 + η j I)y j = b (M 1 η j I)y j 1/2, for j = 1, 2, 3,.... The ADI shift parameters µ j and η j are determined from spectral bounds on M 1 and M 2 to improve the convergence rate. In [17], the ADI iteration is applied to the equation X ÂX B = Ĉ, Â Rs s, B R t t, Ĉ Rs t. (22) Let X 0 be an initial approximate solution of this equation. Then the ADI iteration generates new iterates X M+N as follows M := M + 1; X M+N (I µ M B) = ( Â µ M I)X M+N 1 B + Ĉ, (23) N := N + 1; (I η N Â)X M+N = ÂX M+N 1( B η N I) + Ĉ, (24) 18
23 where one starts with M = N = 0. Either (23) or (24) can be used to determine X M+N from X M+N 1. When (23) and (24) are used in a strictly alternating fashion, the ADI method obtained is analogous to the classical ADI iteration for Sylvester s equation discussed by Wachspress [57]. In [17], strict alternation between the formulas (23) and (24) is not required as, e.g., the structures and sizes of the matrices  and B may make the computation of X M+N in one of the equations, say (23) faster than by the other one. In this case the computational effort to solve (22) may be reduced by applying (23) more often than (24), even if such an approach would result in slightly lower convergence than strict alternation. The convergence of the iteration (23) (24) for different ratios M/N is analyzed in [17] as well as the choice of the iteration parameters. There is still the problem of storing the usually dense n n matrix X M+N. This storage can be avoided by observing that, for the problems under consideration, the spectrum of the positive semidefinite matrix X M+N = Z M+N ZM+N T often decays to zero rapidly. Here Z M+N can be considered as a Cholesky factor of X M+N. We T expect that X M+N can be approximated accurately by a factorization Z Z for some Z R n r with r n. Here, we will restrict our discussion to a strict alternation between the two equations. With  = E 1 A k, B = A T k E T, and Ĉ = E 1 R k E T, (22) is equivalent to (8) and we obtain from (23) X i 1 (I µ i A T k E T ) = (E 1 A k µ i I)X i 1 A T k E T + E 1 R k E T, 2 while (24) yields (I η i E 1 A k )X i = E 1 A k X i 1 (A T k E T η i I) + E 1 R k E T. 2 In order to get rid of the inverses of E, one can manipulate both equations in an obvious way to reach EX i 1 (E T µ i A T k ) = (A k µ i E)X i 1 A T k + R k, (25) 2 (E η i A k )X i E T = A k X i 1 (A T k η i E T ) + R k. 2 Similarly, with  = E 1 A k, B = A T k E T, and Ĉ = E 1 C k E T, (22) is equivalent to (9) and we obtain EX i 1 (E T µ i A T k ) = (A k µ i E)X i 1 A T k + EĈET, (26) 2 (E η i A k )X i E T = A k X i 1 (A T k η i E T ) + EĈET. 2 While R k in (25) may be indefinite, E T ĈE in (26) is positive semidefinite, see (15). 19
24 In order to derive a formulation in terms of (Cholesky) factors, let us rewrite the iteration (26) in a single equation. In particular, we have Hence, with X i 1 2 X i 1 (I µ i A T k E T ) = (E 1 A k µ i I)X i 1 A T k E T + Ĉ, 2 (I η i E 1 A k )X i = E 1 A k X i 1 (A T k E T η i I) + Ĉ. 2 = (E 1 A k µ i I)X i 1 A T k E T (I µ i A T k E T ) 1 + Ĉ(I µ ia T k E T ) 1, we have X i = ) (I η i E 1 A k ) (E 1 1 A k X i 1 (A T k E T η i I) + Ĉ 2 = (I η i E 1 A k ) 1 ( E 1 A k (E 1 A k µ i I)X i 1 A T k E T (I µ i A T k E T ) 1 (A T k E T η i I) ) + E 1 A k Ĉ(I µ i A T k E T ) 1 (A T k E T η i I) + Ĉ. As we have (I µ i A T k E T ) 1 (A T k E T η i I) = (A T k E T η i I)(I µ i A T k E T ) 1 X i = (I η i E 1 A k ) (E 1 1 A k (E 1 A k µ i I)X i 1 A T k E T (A T k E T η i I) ) + E 1 A k Ĉ(A T k E T η i I) + Ĉ(I µ ia T k E T ) (I µ i A T k E T ) 1. Obviously, in order to obtain a symmetric X i we have to restrict the choice of µ i and η i such that η i = µ i, ( X i = (I µ i E 1 A k ) 1 E 1 A k (E 1 A k µ i I)X i 1 (A T k E T µ i I)A T k E T ) + E 1 A k Ĉ(A T k E T µ i I) + Ĉ(I µ ia T k E T ) (I µ i E 1 A k ) T. Observe that E 1 A k Ĉ(A T k E T µ i I) + Ĉ(I µ ia T k E T ) = E 1 A k ĈA T k E T µ i E 1 A k Ĉ + Ĉ µ iĉat k E T = E 1 A k ĈA T k E T + (I µ i E 1 A k )Ĉ(I µ ia T k E T ) µ i 2 E 1 A k ĈA T k E T = (1 µ i 2 )E 1 A k ĈA T k E T + (I µ i E 1 A k )Ĉ(I µ ia T k E T ). 20
25 Algorithm 5 ADI-Newton s Method for the DARE Input: The coefficient matrices A, B, C, E, Q, R, S of the DARE (1), and a starting guess X 0, so that σ(a K(X 0 )B, E) D 1 (0) and R + BX 0 B T > 0. Output: An approximate solution X k+1 of the DARE (1). for k = 0, 1, 2,... do 1. K k K(X k ). 2. A k A K k B. 3. C k C(X k ). 4. Y 0 0. for j = 1, 2,... do 5. Choose shift µ j 6. Y j E 1 C k E T. 7. H (1 µ j 2 )E 1 A k Y j A T k E T. 8. H H + E 1 A k (E 1 A k µ j I)Y j 1 (A T k E T µ j I)A T k E T. 9. Y j Y j + (I µ j E 1 A k ) 1 H(I µ j E 1 A k ) T. end for 10. X k Y j. end for Hence, we obtain the single equation X i = Ĉ + (I µ ie 1 A k ) 1 ((1 µ i 2 )E 1 A k ĈA T k E T + (27) E 1 A k (E 1 A k µ i I)X i 1 (A T k E T µ i I)A T k E T ) (I µ i E 1 A k ) T. If X i 1 is positive semidefinite, then so is X i. As (A T k E T µ i I)A T k E T (I µ i E 1 A k ) T = (A T k E T µ i I)(E T A T k µ i I) 1, the spectral radius ρ ADI = ρ ( l j=1 (A 1 k E µ ii) 1 (E 1 A k µ i I) determines the rate of convergence, where l is the number of iteration steps and shifts used. The minimization of ρ ADI with respect to the shift parameters µ i is given by (λ µ min max 1 ) (λ µ l ) µ 1,...,µ l λ σ(e 1 A k ) ( 1 µ λ 1) ( 1 µ λ l). (28) In [17] the choice of shifts for the more general ADI iteration (23), (24) applied to (22) is discussed. Although here we are considering a special case of that ) 21
26 situation, the proposed choice of the shifts can not be carried over directly, as the shifts µ M and η N in (23) and (24) are not related to each other, while we require µ j = η j in order to obtain a symmetric solution from a symmetric starting guess. The choice of the shift parameters µ i is related to a rational approximation problem. The conventional approach to the computation of these parameters in other ADI settings is to cover the spectrum by a domain Ω C and to solve the minmax problem with respect to Ω instead of the spectrum. This approximation theory based approach generally requires the knowledge of certain bounds of the spectrum. Heuristic approaches have also been proposed. See, e.g., [18, 49] and the references therein. In Section 4 we propose to use a quite simple, numerically inexpensive, heuristic algorithm which replaces the spectrum by some approximations to the largest and the smallest eigenvalues in the spectrum σ(e 1 A k ). Assume that the largest l and the smallest j eigenvalues have been approximated, S = { λ 1,..., λ l, λ n j+1,..., λ n }. Then the minmax problem is replaced by (λ µ min max 1 ) (λ µ l ) µ 1,...,µ l λ S ( 1 µ λ 1) ( 1 µ λ l). (29) Next a heuristic optimization method is employed in order to compute suitable shifts. For an efficient solution of large-scale DAREs, the solution of (28) will require further studies in the future. Using (15) we can write Ĉ = ( E 1 U ) ( U T E T ) = MM T, M R n (p+m). Finally, with µ i 1, X i = Z i Z T i, Z i R n r j and 1 µi 2 (I µ i E 1 A k ) 1 E 1 A k M = M, (I µ i E 1 A k ) 1 E 1 A k (E 1 A k µ i I)Z i 1 = M, we have 1 µi 2 (E µ i A k ) 1 A k M = M R n (p+m), (E µ i A k ) 1 A k E 1 (A k µ i E)Z i 1 = M R n r j 1. With this we can write (27) in terms of a factorization X i = Z i Z T i = MM T + M M T + M M T = [ M M M] M T M T M T. Hence, Z i = [ M ] M M R n (2(p+m)+r j) 22
27 is one possible representation of the (Cholesky) factor of the solution X i. The dimension of Z j would increase by 2(p + m) in each iteration step. But if Z j is of low rank r j, then we can approximate it using a rank-revealing LQ factorization as before. The derivation of the algorithm is straightforward, hence we omit its statement. 4 Numerical Examples All numerical tests were done in Matlab R2009a on a Pentium M notebook with 512 MB main memory. The iterations were stopped in all algorithms as soon as Z j+1 Z T j+1 Z j Z T j F / Z j+1 Z T j+1 F and T k+1 T T k+1 T kt T k F / T k+1 T T k+1 F were less than a given tolerance. The examples considered are optimal control problems of the following form: min J (u), J (u) = 1 2 yk T Qy k + u T k Ru k + 2yk T Su k k=0 subject to a fully discretized parabolic PDE constraint Ex k+1 = Ax k + Bu k, (30) y k = Cx k. (31) In all examples we have m = p = 1 and choose R = 1, Q = 1, S = 0. In order to compare the computed solutions to an exact one, the Matlab routine dare was used to produce the exact solution X exact. In our examples we used only one shift for the ADI iteration. problem (28) is replaced by The minmax min µ max λ S λ µ (32) µ, where S is either the set of all eigenvalues computed by eig or eigenvalue approximations computed by eigs. Assume that the largest l and the smallest j eigenvalues have been approximated so that S = { λ 1,..., λ l, λ n j+1,..., λ n }. Next, fminsearch is employed as a heuristic optimization method in order to compute a suitable shift which we simply call µ in the following. The standard setting for all examples presented is l = 8, j = 2. Moreover, eigs was called with OPTS.tol = 10 2 as more accuracy in this computation does not increase the accuracy of the computed solution or convergence rate of the algorithm. Note that an optimization with respect to the full spectral set did in no case improve 1 λ 23
28 the convergence of the overall algorithms, i.e., the computed l + j Ritz values were sufficient to obtain a suitable shift. Thus, we only report results based on S being composed of the computed l + j Ritz values. When further developing the algorithms proposed in this paper, a multi-shift selection strategy needs to be developed. A first candidate for this would be Penzl s heuristic [49] that often yields good results in the ADI iteration for continuous Lyapunov equations. Example 4.1 The data of this example come from the autonomous linear-quadratic optimal control problem of one dimensional heat flow and is taken from [1, Example 4.2]. The model equations are x(t, η) t = 2 α x(t, η) + b(η)u(t) η2 η (0, 1); t > 0 x(t, 0) = 0 = x(t, 1) t > 0 x(0, η) = x 0 (η) η (0, 1) y(x) = 1 0 c(η)x(t, η)dη, x > 0, where α > 0 and x 0, b, c L 2 (0, 1). Using a standard linear finite element (FE) discretization in space, one obtains an ordinary differential equation M N ẋ(t) = K N x(t) + F u(t), y(t) = Cx(t), where M N = 1 6N , K N = αn F = b N and C = c T N, M N, K N R N N. The vectors b N and c N are obtained from the L 2 inner products of indicator functions for subsets of (0, 1) with the FE basis functions {φ N i } N 1 (b N ) j = 1 0 i=1 : β(s)φ N i (s)ds, and (c N ) j = 1 where the functions β, γ L 2 (0, 1) are given by { 1, s [0.1, 0.5], β(s) = γ(s) = 0, otherwise. 0, γ(s)φ N i (s)ds, j = 1,..., N 1, (Note: β, γ are parameter-dependent in [1] and may differ here we chose them equal for simplicity.) Employing the semi-implicit Euler method with stepsize t yields the difference equation (M tk)x k+1 = Mx k + tf u k, 24
29 that is, A = M, E = M tk, and B = tf in (30). In the computational experiments reported in Tables 1 2, we set α = 0.05 (default in [1]). fminsearch was started with different starting guesses µ 0. The resulting shift is given as µ. Different n, tol and h have been considered. Here only the results for n = 1000, h = 0.1 and h = 0.01 as well as tol = 10 8 and tol = are presented. Here and in the following, ρ(a, E) denotes the spectral radius of A λe, i.e., ρ(a, E) = max λ σ(a,e) { λ }. No matter how the parameters were chosen, all methods needed 4 Newton steps. The number of Smith iteration steps was usually quite high, about twice as many as needed for the unshifted ADI iteration. Obviously, neither the Smith iteration nor the unshifted ADI iteration yield feasible methods for solving the DARE with Newton s method in this example. On the other hand, using our fairly simple heuristic for choosing a single shift, the ADI iteration with shift converges up to 100 times faster than the ADI iteration without a shift. The number of iterations needed varied from Newton step to Newton step, being larger at first. Changing n while keeping the rest of the parameters fixed, does not change the number of iterations needed for convergence or the accuracy achieved. t = 0.1, ρ(a, E) X dare Z smith Z adi Z adi µ = no shift Newton steps Smith/ADI steps R(X) X dare X F / X F rank(zz T ) t = 0.01, ρ(a, E) X dare Z smith Z adi Z adi µ = no shift Newton steps Smith/ADI steps R(X) X dare X F / X F rank(zz T ) Table 1: Example 1, tol = 10 8, n = 1000, µ 0 = 1. Example 4.2 Here, we use again a discretized control problem for the heat equation, this time taken from the SLICOT Model Reduction Benchmark Collection [19]. (The eigenvalues of the DARE solution are shown in Figure 1.) In contrast to Example 4.1, this time a finite differences discretization is used, 25
30 t = 0.1 X dare Z smith Z adi Z adi µ = no shift Newton steps Smith/ADI steps R(X) X dare X F / X F rank(zz T ) t = 0.01 X dare Z smith Z adi Z adi µ = no shift Newton steps Smith/ADI steps R(X) X dare X F / X F rank(zz T ) Table 2: Example 1, tol = 10 12, n = 1000, µ 0 = 0. where the spatial domain is discretized into segments of length h = 1 N+1. Suppose for example that one wants to heat in a point of the rod located at 1/3 of the length and wants to record the temperature at 2/3 of the length. We obtain the semi-discretized system: ẋ(t) = Kx(t) + F u(t), x(0) = 0, y(t) = Cx(t), where K = α h R N N, F = e (N+1)/3 R N, C = e 2N/3 R N, and x(t) R N is the solution evaluated at each x value in the discretization for t. Here, e k denotes the kth unit vector. Now if we want to completely discretize the system, for example using Crank-Nicholson we obtain: Ex k+1 = Ax k + Bu k, x 0 = 0 y k = Cx k where E = I N tk, A = I 2 N + t K, B = tf, and t is the time step. 2 26
31 The data provided in the benchmark collection [19] yields matrices K, F and C with N = 200, m = p = 1. As ρ(a, E) , the iteration for the Stein equation converges quite slowly, for the results see Table 3. When using the Smith iteration on this example, the iterations converged after 3 Newton iteration, while in each iteration step the Smith iteration took 1343 steps. The rank of X exact is 31, the rank of the computed low-rank factorization factor Z is 39, the rank of ZZ T is 25. When looking at the singular values of X exact and ZZ T, one can see that this is a numerical accuracy problem, the first about 25 singular values are of the order of 10 8 to 10 14, while the rest is even smaller. Without the low-rank reduction of Z j in every step, the factor Z j would increase to the size R , while due to the low-rank reduction, the factor Z j is at most of size R The ADI iteration converged much quicker than the Smith iteration, moreover the use of a shift allowed the computation of a more accurate solution. In order to obtain a better convergence behavior for the Stein equation, we use the same data, but set K = 0.5 K. This reduces ρ(a, E) to As can be seen from Table 3, the iteration for the Stein equation converges much faster for all algorithms considered. Here, our heuristic to choose the shift does not work very well, the computed shift is close to 0 which is almost the same as using no shift. Using a smaller tol does give more accurate results, but no significant chance in the number of iterations needed. Example 4.3 For the final example, we set up with v = [1, 1, 0,..., ] T R 10 and B = C = [v,..., v] R 100 A = I, K = tridiag(d, T, D) R , with D = diag( 121,..., 121) R and T = = tridiag( 126.5, 484, 115.5) R The K matrix is constructed using the Matlab function fdm2d matrix from Lyapack [50]. We include this fairly small example, as it shows that the number of Newton steps also may depend on the algorithm used for the inner iteration to solve the Stein equations. This number is slightly larger for the Smith iteration than for the ADI iteration with shift. 27
32 original K, ρ(a, E) X dare Z smith Z adi Z adi µ = no shift Newton steps Smith/ADI steps R(X) X dare X F / X F rank(x)/rank(zz T ) K = 0.5K, ρ(a, E) X dare Z smith Z adi Z adi µ = no shift Newton steps Smith/ADI steps R(X) X dare X F / X F rank(x)/rank(zz T ) Table 3: Example 2, n = 200, tol = 10 8, µ 0 = 0. X dare Z smith Z adi µ = Newton steps 10 8 Smith/ADI steps R(X) X dare X F / X F rank(x)/rank(zz T ) Table 4: Example 3, tol = 10 12, n = 100, t = 0.01, µ 0 = 1. 5 Conclusions This paper addresses the numerical solution of large, sparse DAREs based on the Newton method. Its primary step involves the solution of large, sparse, stable Stein equations. We have presented two iterative methods which deliver low-rank approximations to the desired solution, a Smith and an ADI iteration. The ADI iteration can be accelerated significantly by introducing suitable shift parameters. We presented a simple heuristic algorithm for determining a set of ADI parameters. Finally, the algorithms are used to numerically solve an optimal control problem for parabolic PDEs. Future work will include a detailed study of the problem of choosing the ADI parameters as well as the adaptation of the precision to which the Stein equation is solved to that of the Newton recursion as in [24] done for continuous-time 28
On the numerical solution of large-scale sparse discrete-time Riccati equations
 Advances in Computational Mathematics manuscript No (will be inserted by the editor) On the numerical solution of large-scale sparse discrete-time Riccati equations Peter Benner Heike Faßbender Received:
Advances in Computational Mathematics manuscript No (will be inserted by the editor) On the numerical solution of large-scale sparse discrete-time Riccati equations Peter Benner Heike Faßbender Received:
Chemnitz Scientific Computing Preprints
 Peter Benner Heike Faßbender On the numerical solution of large-scale sparse discrete-time Riccati equations CSC/09-11 Chemnitz Scientific Computing Preprints ISSN 1864-0087 Chemnitz Scientific Computing
Peter Benner Heike Faßbender On the numerical solution of large-scale sparse discrete-time Riccati equations CSC/09-11 Chemnitz Scientific Computing Preprints ISSN 1864-0087 Chemnitz Scientific Computing
S N. hochdimensionaler Lyapunov- und Sylvestergleichungen. Peter Benner. Mathematik in Industrie und Technik Fakultät für Mathematik TU Chemnitz
 Ansätze zur numerischen Lösung hochdimensionaler Lyapunov- und Sylvestergleichungen Peter Benner Mathematik in Industrie und Technik Fakultät für Mathematik TU Chemnitz S N SIMULATION www.tu-chemnitz.de/~benner
Ansätze zur numerischen Lösung hochdimensionaler Lyapunov- und Sylvestergleichungen Peter Benner Mathematik in Industrie und Technik Fakultät für Mathematik TU Chemnitz S N SIMULATION www.tu-chemnitz.de/~benner
The Newton-ADI Method for Large-Scale Algebraic Riccati Equations. Peter Benner.
 The Newton-ADI Method for Large-Scale Algebraic Riccati Equations Mathematik in Industrie und Technik Fakultät für Mathematik Peter Benner benner@mathematik.tu-chemnitz.de Sonderforschungsbereich 393 S
The Newton-ADI Method for Large-Scale Algebraic Riccati Equations Mathematik in Industrie und Technik Fakultät für Mathematik Peter Benner benner@mathematik.tu-chemnitz.de Sonderforschungsbereich 393 S
Efficient Implementation of Large Scale Lyapunov and Riccati Equation Solvers
 Efficient Implementation of Large Scale Lyapunov and Riccati Equation Solvers Jens Saak joint work with Peter Benner (MiIT) Professur Mathematik in Industrie und Technik (MiIT) Fakultät für Mathematik
Efficient Implementation of Large Scale Lyapunov and Riccati Equation Solvers Jens Saak joint work with Peter Benner (MiIT) Professur Mathematik in Industrie und Technik (MiIT) Fakultät für Mathematik
BALANCING-RELATED MODEL REDUCTION FOR DATA-SPARSE SYSTEMS
 BALANCING-RELATED Peter Benner Professur Mathematik in Industrie und Technik Fakultät für Mathematik Technische Universität Chemnitz Computational Methods with Applications Harrachov, 19 25 August 2007
BALANCING-RELATED Peter Benner Professur Mathematik in Industrie und Technik Fakultät für Mathematik Technische Universität Chemnitz Computational Methods with Applications Harrachov, 19 25 August 2007
A Newton-Galerkin-ADI Method for Large-Scale Algebraic Riccati Equations
 A Newton-Galerkin-ADI Method for Large-Scale Algebraic Riccati Equations Peter Benner Max-Planck-Institute for Dynamics of Complex Technical Systems Computational Methods in Systems and Control Theory
A Newton-Galerkin-ADI Method for Large-Scale Algebraic Riccati Equations Peter Benner Max-Planck-Institute for Dynamics of Complex Technical Systems Computational Methods in Systems and Control Theory
Numerical Methods I Non-Square and Sparse Linear Systems
 Numerical Methods I Non-Square and Sparse Linear Systems Aleksandar Donev Courant Institute, NYU 1 donev@courant.nyu.edu 1 MATH-GA 2011.003 / CSCI-GA 2945.003, Fall 2014 September 25th, 2014 A. Donev (Courant
Numerical Methods I Non-Square and Sparse Linear Systems Aleksandar Donev Courant Institute, NYU 1 donev@courant.nyu.edu 1 MATH-GA 2011.003 / CSCI-GA 2945.003, Fall 2014 September 25th, 2014 A. Donev (Courant
Structured Krylov Subspace Methods for Eigenproblems with Spectral Symmetries
 Structured Krylov Subspace Methods for Eigenproblems with Spectral Symmetries Fakultät für Mathematik TU Chemnitz, Germany Peter Benner benner@mathematik.tu-chemnitz.de joint work with Heike Faßbender
Structured Krylov Subspace Methods for Eigenproblems with Spectral Symmetries Fakultät für Mathematik TU Chemnitz, Germany Peter Benner benner@mathematik.tu-chemnitz.de joint work with Heike Faßbender
Synopsis of Numerical Linear Algebra
 Synopsis of Numerical Linear Algebra Eric de Sturler Department of Mathematics, Virginia Tech sturler@vt.edu http://www.math.vt.edu/people/sturler Iterative Methods for Linear Systems: Basics to Research
Synopsis of Numerical Linear Algebra Eric de Sturler Department of Mathematics, Virginia Tech sturler@vt.edu http://www.math.vt.edu/people/sturler Iterative Methods for Linear Systems: Basics to Research
Least Squares. Tom Lyche. October 26, Centre of Mathematics for Applications, Department of Informatics, University of Oslo
 Least Squares Tom Lyche Centre of Mathematics for Applications, Department of Informatics, University of Oslo October 26, 2010 Linear system Linear system Ax = b, A C m,n, b C m, x C n. under-determined
Least Squares Tom Lyche Centre of Mathematics for Applications, Department of Informatics, University of Oslo October 26, 2010 Linear system Linear system Ax = b, A C m,n, b C m, x C n. under-determined
Model Reduction for Dynamical Systems
 Otto-von-Guericke Universität Magdeburg Faculty of Mathematics Summer term 2015 Model Reduction for Dynamical Systems Lecture 8 Peter Benner Lihong Feng Max Planck Institute for Dynamics of Complex Technical
Otto-von-Guericke Universität Magdeburg Faculty of Mathematics Summer term 2015 Model Reduction for Dynamical Systems Lecture 8 Peter Benner Lihong Feng Max Planck Institute for Dynamics of Complex Technical
Perturbation theory for eigenvalues of Hermitian pencils. Christian Mehl Institut für Mathematik TU Berlin, Germany. 9th Elgersburg Workshop
 Perturbation theory for eigenvalues of Hermitian pencils Christian Mehl Institut für Mathematik TU Berlin, Germany 9th Elgersburg Workshop Elgersburg, March 3, 2014 joint work with Shreemayee Bora, Michael
Perturbation theory for eigenvalues of Hermitian pencils Christian Mehl Institut für Mathematik TU Berlin, Germany 9th Elgersburg Workshop Elgersburg, March 3, 2014 joint work with Shreemayee Bora, Michael
ECE133A Applied Numerical Computing Additional Lecture Notes
 Winter Quarter 2018 ECE133A Applied Numerical Computing Additional Lecture Notes L. Vandenberghe ii Contents 1 LU factorization 1 1.1 Definition................................. 1 1.2 Nonsingular sets
Winter Quarter 2018 ECE133A Applied Numerical Computing Additional Lecture Notes L. Vandenberghe ii Contents 1 LU factorization 1 1.1 Definition................................. 1 1.2 Nonsingular sets
Index. for generalized eigenvalue problem, butterfly form, 211
 Index ad hoc shifts, 165 aggressive early deflation, 205 207 algebraic multiplicity, 35 algebraic Riccati equation, 100 Arnoldi process, 372 block, 418 Hamiltonian skew symmetric, 420 implicitly restarted,
Index ad hoc shifts, 165 aggressive early deflation, 205 207 algebraic multiplicity, 35 algebraic Riccati equation, 100 Arnoldi process, 372 block, 418 Hamiltonian skew symmetric, 420 implicitly restarted,
On the -Sylvester Equation AX ± X B = C
 Department of Applied Mathematics National Chiao Tung University, Taiwan A joint work with E. K.-W. Chu and W.-W. Lin Oct., 20, 2008 Outline 1 Introduction 2 -Sylvester Equation 3 Numerical Examples 4
Department of Applied Mathematics National Chiao Tung University, Taiwan A joint work with E. K.-W. Chu and W.-W. Lin Oct., 20, 2008 Outline 1 Introduction 2 -Sylvester Equation 3 Numerical Examples 4
Optimization problems on the rank and inertia of the Hermitian matrix expression A BX (BX) with applications
 Optimization problems on the rank and inertia of the Hermitian matrix expression A BX (BX) with applications Yongge Tian China Economics and Management Academy, Central University of Finance and Economics,
Optimization problems on the rank and inertia of the Hermitian matrix expression A BX (BX) with applications Yongge Tian China Economics and Management Academy, Central University of Finance and Economics,
Scientific Computing with Case Studies SIAM Press, Lecture Notes for Unit VII Sparse Matrix
 Scientific Computing with Case Studies SIAM Press, 2009 http://www.cs.umd.edu/users/oleary/sccswebpage Lecture Notes for Unit VII Sparse Matrix Computations Part 1: Direct Methods Dianne P. O Leary c 2008
Scientific Computing with Case Studies SIAM Press, 2009 http://www.cs.umd.edu/users/oleary/sccswebpage Lecture Notes for Unit VII Sparse Matrix Computations Part 1: Direct Methods Dianne P. O Leary c 2008
Matrix Algorithms. Volume II: Eigensystems. G. W. Stewart H1HJ1L. University of Maryland College Park, Maryland
 Matrix Algorithms Volume II: Eigensystems G. W. Stewart University of Maryland College Park, Maryland H1HJ1L Society for Industrial and Applied Mathematics Philadelphia CONTENTS Algorithms Preface xv xvii
Matrix Algorithms Volume II: Eigensystems G. W. Stewart University of Maryland College Park, Maryland H1HJ1L Society for Industrial and Applied Mathematics Philadelphia CONTENTS Algorithms Preface xv xvii
Numerical Methods - Numerical Linear Algebra
 Numerical Methods - Numerical Linear Algebra Y. K. Goh Universiti Tunku Abdul Rahman 2013 Y. K. Goh (UTAR) Numerical Methods - Numerical Linear Algebra I 2013 1 / 62 Outline 1 Motivation 2 Solving Linear
Numerical Methods - Numerical Linear Algebra Y. K. Goh Universiti Tunku Abdul Rahman 2013 Y. K. Goh (UTAR) Numerical Methods - Numerical Linear Algebra I 2013 1 / 62 Outline 1 Motivation 2 Solving Linear
Preliminary/Qualifying Exam in Numerical Analysis (Math 502a) Spring 2012
 Instructions Preliminary/Qualifying Exam in Numerical Analysis (Math 502a) Spring 2012 The exam consists of four problems, each having multiple parts. You should attempt to solve all four problems. 1.
Instructions Preliminary/Qualifying Exam in Numerical Analysis (Math 502a) Spring 2012 The exam consists of four problems, each having multiple parts. You should attempt to solve all four problems. 1.
Stabilization and Acceleration of Algebraic Multigrid Method
 Stabilization and Acceleration of Algebraic Multigrid Method Recursive Projection Algorithm A. Jemcov J.P. Maruszewski Fluent Inc. October 24, 2006 Outline 1 Need for Algorithm Stabilization and Acceleration
Stabilization and Acceleration of Algebraic Multigrid Method Recursive Projection Algorithm A. Jemcov J.P. Maruszewski Fluent Inc. October 24, 2006 Outline 1 Need for Algorithm Stabilization and Acceleration
12. Cholesky factorization
 L. Vandenberghe ECE133A (Winter 2018) 12. Cholesky factorization positive definite matrices examples Cholesky factorization complex positive definite matrices kernel methods 12-1 Definitions a symmetric
L. Vandenberghe ECE133A (Winter 2018) 12. Cholesky factorization positive definite matrices examples Cholesky factorization complex positive definite matrices kernel methods 12-1 Definitions a symmetric
AMS526: Numerical Analysis I (Numerical Linear Algebra)
 AMS526: Numerical Analysis I (Numerical Linear Algebra) Lecture 3: Positive-Definite Systems; Cholesky Factorization Xiangmin Jiao Stony Brook University Xiangmin Jiao Numerical Analysis I 1 / 11 Symmetric
AMS526: Numerical Analysis I (Numerical Linear Algebra) Lecture 3: Positive-Definite Systems; Cholesky Factorization Xiangmin Jiao Stony Brook University Xiangmin Jiao Numerical Analysis I 1 / 11 Symmetric
Parallel Model Reduction of Large Linear Descriptor Systems via Balanced Truncation
 Parallel Model Reduction of Large Linear Descriptor Systems via Balanced Truncation Peter Benner 1, Enrique S. Quintana-Ortí 2, Gregorio Quintana-Ortí 2 1 Fakultät für Mathematik Technische Universität
Parallel Model Reduction of Large Linear Descriptor Systems via Balanced Truncation Peter Benner 1, Enrique S. Quintana-Ortí 2, Gregorio Quintana-Ortí 2 1 Fakultät für Mathematik Technische Universität
Orthogonalization and least squares methods
 Chapter 3 Orthogonalization and least squares methods 31 QR-factorization (QR-decomposition) 311 Householder transformation Definition 311 A complex m n-matrix R = [r ij is called an upper (lower) triangular
Chapter 3 Orthogonalization and least squares methods 31 QR-factorization (QR-decomposition) 311 Householder transformation Definition 311 A complex m n-matrix R = [r ij is called an upper (lower) triangular
Iterative Solution of a Matrix Riccati Equation Arising in Stochastic Control
 Iterative Solution of a Matrix Riccati Equation Arising in Stochastic Control Chun-Hua Guo Dedicated to Peter Lancaster on the occasion of his 70th birthday We consider iterative methods for finding the
Iterative Solution of a Matrix Riccati Equation Arising in Stochastic Control Chun-Hua Guo Dedicated to Peter Lancaster on the occasion of his 70th birthday We consider iterative methods for finding the
Scientific Computing WS 2018/2019. Lecture 9. Jürgen Fuhrmann Lecture 9 Slide 1
 Scientific Computing WS 2018/2019 Lecture 9 Jürgen Fuhrmann juergen.fuhrmann@wias-berlin.de Lecture 9 Slide 1 Lecture 9 Slide 2 Simple iteration with preconditioning Idea: Aû = b iterative scheme û = û
Scientific Computing WS 2018/2019 Lecture 9 Jürgen Fuhrmann juergen.fuhrmann@wias-berlin.de Lecture 9 Slide 1 Lecture 9 Slide 2 Simple iteration with preconditioning Idea: Aû = b iterative scheme û = û
Numerical Methods in Matrix Computations
 Ake Bjorck Numerical Methods in Matrix Computations Springer Contents 1 Direct Methods for Linear Systems 1 1.1 Elements of Matrix Theory 1 1.1.1 Matrix Algebra 2 1.1.2 Vector Spaces 6 1.1.3 Submatrices
Ake Bjorck Numerical Methods in Matrix Computations Springer Contents 1 Direct Methods for Linear Systems 1 1.1 Elements of Matrix Theory 1 1.1.1 Matrix Algebra 2 1.1.2 Vector Spaces 6 1.1.3 Submatrices
SOLUTION OF ALGEBRAIC RICCATI EQUATIONS ARISING IN CONTROL OF PARTIAL DIFFERENTIAL EQUATIONS
 SOLUTION OF ALGEBRAIC RICCATI EQUATIONS ARISING IN CONTROL OF PARTIAL DIFFERENTIAL EQUATIONS Kirsten Morris Department of Applied Mathematics University of Waterloo Waterloo, CANADA N2L 3G1 kmorris@uwaterloo.ca
SOLUTION OF ALGEBRAIC RICCATI EQUATIONS ARISING IN CONTROL OF PARTIAL DIFFERENTIAL EQUATIONS Kirsten Morris Department of Applied Mathematics University of Waterloo Waterloo, CANADA N2L 3G1 kmorris@uwaterloo.ca
AMS526: Numerical Analysis I (Numerical Linear Algebra for Computational and Data Sciences)
 AMS526: Numerical Analysis I (Numerical Linear Algebra for Computational and Data Sciences) Lecture 19: Computing the SVD; Sparse Linear Systems Xiangmin Jiao Stony Brook University Xiangmin Jiao Numerical
AMS526: Numerical Analysis I (Numerical Linear Algebra for Computational and Data Sciences) Lecture 19: Computing the SVD; Sparse Linear Systems Xiangmin Jiao Stony Brook University Xiangmin Jiao Numerical
On Linear-Quadratic Control Theory of Implicit Difference Equations
 On Linear-Quadratic Control Theory of Implicit Difference Equations Daniel Bankmann Technische Universität Berlin 10. Elgersburg Workshop 2016 February 9, 2016 D. Bankmann (TU Berlin) Control of IDEs February
On Linear-Quadratic Control Theory of Implicit Difference Equations Daniel Bankmann Technische Universität Berlin 10. Elgersburg Workshop 2016 February 9, 2016 D. Bankmann (TU Berlin) Control of IDEs February
Lecture notes: Applied linear algebra Part 1. Version 2
 Lecture notes: Applied linear algebra Part 1. Version 2 Michael Karow Berlin University of Technology karow@math.tu-berlin.de October 2, 2008 1 Notation, basic notions and facts 1.1 Subspaces, range and
Lecture notes: Applied linear algebra Part 1. Version 2 Michael Karow Berlin University of Technology karow@math.tu-berlin.de October 2, 2008 1 Notation, basic notions and facts 1.1 Subspaces, range and
Sparsity-Preserving Difference of Positive Semidefinite Matrix Representation of Indefinite Matrices
 Sparsity-Preserving Difference of Positive Semidefinite Matrix Representation of Indefinite Matrices Jaehyun Park June 1 2016 Abstract We consider the problem of writing an arbitrary symmetric matrix as
Sparsity-Preserving Difference of Positive Semidefinite Matrix Representation of Indefinite Matrices Jaehyun Park June 1 2016 Abstract We consider the problem of writing an arbitrary symmetric matrix as
A POD Projection Method for Large-Scale Algebraic Riccati Equations
 A POD Projection Method for Large-Scale Algebraic Riccati Equations Boris Kramer Department of Mathematics Virginia Tech Blacksburg, VA 24061-0123 Email: bokr@vt.edu John R. Singler Department of Mathematics
A POD Projection Method for Large-Scale Algebraic Riccati Equations Boris Kramer Department of Mathematics Virginia Tech Blacksburg, VA 24061-0123 Email: bokr@vt.edu John R. Singler Department of Mathematics
MODEL REDUCTION BY A CROSS-GRAMIAN APPROACH FOR DATA-SPARSE SYSTEMS
 MODEL REDUCTION BY A CROSS-GRAMIAN APPROACH FOR DATA-SPARSE SYSTEMS Ulrike Baur joint work with Peter Benner Mathematics in Industry and Technology Faculty of Mathematics Chemnitz University of Technology
MODEL REDUCTION BY A CROSS-GRAMIAN APPROACH FOR DATA-SPARSE SYSTEMS Ulrike Baur joint work with Peter Benner Mathematics in Industry and Technology Faculty of Mathematics Chemnitz University of Technology
Passivity Preserving Model Reduction for Large-Scale Systems. Peter Benner.
 Passivity Preserving Model Reduction for Large-Scale Systems Peter Benner Mathematik in Industrie und Technik Fakultät für Mathematik Sonderforschungsbereich 393 S N benner@mathematik.tu-chemnitz.de SIMULATION
Passivity Preserving Model Reduction for Large-Scale Systems Peter Benner Mathematik in Industrie und Technik Fakultät für Mathematik Sonderforschungsbereich 393 S N benner@mathematik.tu-chemnitz.de SIMULATION
Theorem Let X be a symmetric solution of DR(X) = 0. Let X b be a symmetric approximation to Xand set V := X? X. b If R b = R + B T XB b and I + V B R
 Initializing Newton's method for discrete-time algebraic Riccati equations using the buttery SZ algorithm Heike Fabender Zentrum fur Technomathematik Fachbereich - Mathematik und Informatik Universitat
Initializing Newton's method for discrete-time algebraic Riccati equations using the buttery SZ algorithm Heike Fabender Zentrum fur Technomathematik Fachbereich - Mathematik und Informatik Universitat
Structure preserving Krylov-subspace methods for Lyapunov equations
 Structure preserving Krylov-subspace methods for Lyapunov equations Matthias Bollhöfer, André Eppler Institute Computational Mathematics TU Braunschweig MoRePas Workshop, Münster September 17, 2009 System
Structure preserving Krylov-subspace methods for Lyapunov equations Matthias Bollhöfer, André Eppler Institute Computational Mathematics TU Braunschweig MoRePas Workshop, Münster September 17, 2009 System
Factorized Solution of Sylvester Equations with Applications in Control
 Factorized Solution of Sylvester Equations with Applications in Control Peter Benner Abstract Sylvester equations play a central role in many areas of applied mathematics and in particular in systems and
Factorized Solution of Sylvester Equations with Applications in Control Peter Benner Abstract Sylvester equations play a central role in many areas of applied mathematics and in particular in systems and
Numerical Linear Algebra
 Numerical Linear Algebra Decompositions, numerical aspects Gerard Sleijpen and Martin van Gijzen September 27, 2017 1 Delft University of Technology Program Lecture 2 LU-decomposition Basic algorithm Cost
Numerical Linear Algebra Decompositions, numerical aspects Gerard Sleijpen and Martin van Gijzen September 27, 2017 1 Delft University of Technology Program Lecture 2 LU-decomposition Basic algorithm Cost
Program Lecture 2. Numerical Linear Algebra. Gaussian elimination (2) Gaussian elimination. Decompositions, numerical aspects
 Numerical Linear Algebra Decompositions, numerical aspects Program Lecture 2 LU-decomposition Basic algorithm Cost Stability Pivoting Cholesky decomposition Sparse matrices and reorderings Gerard Sleijpen
Numerical Linear Algebra Decompositions, numerical aspects Program Lecture 2 LU-decomposition Basic algorithm Cost Stability Pivoting Cholesky decomposition Sparse matrices and reorderings Gerard Sleijpen
Iterative Methods for Solving A x = b
 Iterative Methods for Solving A x = b A good (free) online source for iterative methods for solving A x = b is given in the description of a set of iterative solvers called templates found at netlib: http
Iterative Methods for Solving A x = b A good (free) online source for iterative methods for solving A x = b is given in the description of a set of iterative solvers called templates found at netlib: http
CLASSICAL ITERATIVE METHODS
 CLASSICAL ITERATIVE METHODS LONG CHEN In this notes we discuss classic iterative methods on solving the linear operator equation (1) Au = f, posed on a finite dimensional Hilbert space V = R N equipped
CLASSICAL ITERATIVE METHODS LONG CHEN In this notes we discuss classic iterative methods on solving the linear operator equation (1) Au = f, posed on a finite dimensional Hilbert space V = R N equipped
Numerical solution of large-scale Lyapunov equations, Riccati equations, and linear-quadratic optimal control problems
 NUMERICAL LINEAR ALGEBRA WITH APPLICATIONS Numer. Linear Algebra Appl. 2008; 15:755 777 Published online in Wiley InterScience (www.interscience.wiley.com)..622 Numerical solution of large-scale Lyapunov
NUMERICAL LINEAR ALGEBRA WITH APPLICATIONS Numer. Linear Algebra Appl. 2008; 15:755 777 Published online in Wiley InterScience (www.interscience.wiley.com)..622 Numerical solution of large-scale Lyapunov
Exploiting off-diagonal rank structures in the solution of linear matrix equations
 Stefano Massei Exploiting off-diagonal rank structures in the solution of linear matrix equations Based on joint works with D. Kressner (EPFL), M. Mazza (IPP of Munich), D. Palitta (IDCTS of Magdeburg)
Stefano Massei Exploiting off-diagonal rank structures in the solution of linear matrix equations Based on joint works with D. Kressner (EPFL), M. Mazza (IPP of Munich), D. Palitta (IDCTS of Magdeburg)
6. Iterative Methods for Linear Systems. The stepwise approach to the solution...
 6 Iterative Methods for Linear Systems The stepwise approach to the solution Miriam Mehl: 6 Iterative Methods for Linear Systems The stepwise approach to the solution, January 18, 2013 1 61 Large Sparse
6 Iterative Methods for Linear Systems The stepwise approach to the solution Miriam Mehl: 6 Iterative Methods for Linear Systems The stepwise approach to the solution, January 18, 2013 1 61 Large Sparse
Gramian-Based Model Reduction for Data-Sparse Systems CSC/ Chemnitz Scientific Computing Preprints
 Ulrike Baur Peter Benner Gramian-Based Model Reduction for Data-Sparse Systems CSC/07-01 Chemnitz Scientific Computing Preprints Impressum: Chemnitz Scientific Computing Preprints ISSN 1864-0087 (1995
Ulrike Baur Peter Benner Gramian-Based Model Reduction for Data-Sparse Systems CSC/07-01 Chemnitz Scientific Computing Preprints Impressum: Chemnitz Scientific Computing Preprints ISSN 1864-0087 (1995
Arnoldi Methods in SLEPc
 Scalable Library for Eigenvalue Problem Computations SLEPc Technical Report STR-4 Available at http://slepc.upv.es Arnoldi Methods in SLEPc V. Hernández J. E. Román A. Tomás V. Vidal Last update: October,
Scalable Library for Eigenvalue Problem Computations SLEPc Technical Report STR-4 Available at http://slepc.upv.es Arnoldi Methods in SLEPc V. Hernández J. E. Román A. Tomás V. Vidal Last update: October,
Last Time. Social Network Graphs Betweenness. Graph Laplacian. Girvan-Newman Algorithm. Spectral Bisection
 Eigenvalue Problems Last Time Social Network Graphs Betweenness Girvan-Newman Algorithm Graph Laplacian Spectral Bisection λ 2, w 2 Today Small deviation into eigenvalue problems Formulation Standard eigenvalue
Eigenvalue Problems Last Time Social Network Graphs Betweenness Girvan-Newman Algorithm Graph Laplacian Spectral Bisection λ 2, w 2 Today Small deviation into eigenvalue problems Formulation Standard eigenvalue
EIGENVALUE PROBLEMS. EIGENVALUE PROBLEMS p. 1/4
 EIGENVALUE PROBLEMS EIGENVALUE PROBLEMS p. 1/4 EIGENVALUE PROBLEMS p. 2/4 Eigenvalues and eigenvectors Let A C n n. Suppose Ax = λx, x 0, then x is a (right) eigenvector of A, corresponding to the eigenvalue
EIGENVALUE PROBLEMS EIGENVALUE PROBLEMS p. 1/4 EIGENVALUE PROBLEMS p. 2/4 Eigenvalues and eigenvectors Let A C n n. Suppose Ax = λx, x 0, then x is a (right) eigenvector of A, corresponding to the eigenvalue
Iterative methods for Linear System
 Iterative methods for Linear System JASS 2009 Student: Rishi Patil Advisor: Prof. Thomas Huckle Outline Basics: Matrices and their properties Eigenvalues, Condition Number Iterative Methods Direct and
Iterative methods for Linear System JASS 2009 Student: Rishi Patil Advisor: Prof. Thomas Huckle Outline Basics: Matrices and their properties Eigenvalues, Condition Number Iterative Methods Direct and
Numerical Methods. Elena loli Piccolomini. Civil Engeneering. piccolom. Metodi Numerici M p. 1/??
 Metodi Numerici M p. 1/?? Numerical Methods Elena loli Piccolomini Civil Engeneering http://www.dm.unibo.it/ piccolom elena.loli@unibo.it Metodi Numerici M p. 2/?? Least Squares Data Fitting Measurement
Metodi Numerici M p. 1/?? Numerical Methods Elena loli Piccolomini Civil Engeneering http://www.dm.unibo.it/ piccolom elena.loli@unibo.it Metodi Numerici M p. 2/?? Least Squares Data Fitting Measurement
Algebra C Numerical Linear Algebra Sample Exam Problems
 Algebra C Numerical Linear Algebra Sample Exam Problems Notation. Denote by V a finite-dimensional Hilbert space with inner product (, ) and corresponding norm. The abbreviation SPD is used for symmetric
Algebra C Numerical Linear Algebra Sample Exam Problems Notation. Denote by V a finite-dimensional Hilbert space with inner product (, ) and corresponding norm. The abbreviation SPD is used for symmetric
AMS526: Numerical Analysis I (Numerical Linear Algebra)
 AMS526: Numerical Analysis I (Numerical Linear Algebra) Lecture 16: Reduction to Hessenberg and Tridiagonal Forms; Rayleigh Quotient Iteration Xiangmin Jiao Stony Brook University Xiangmin Jiao Numerical
AMS526: Numerical Analysis I (Numerical Linear Algebra) Lecture 16: Reduction to Hessenberg and Tridiagonal Forms; Rayleigh Quotient Iteration Xiangmin Jiao Stony Brook University Xiangmin Jiao Numerical
SOLVING SPARSE LINEAR SYSTEMS OF EQUATIONS. Chao Yang Computational Research Division Lawrence Berkeley National Laboratory Berkeley, CA, USA
 1 SOLVING SPARSE LINEAR SYSTEMS OF EQUATIONS Chao Yang Computational Research Division Lawrence Berkeley National Laboratory Berkeley, CA, USA 2 OUTLINE Sparse matrix storage format Basic factorization
1 SOLVING SPARSE LINEAR SYSTEMS OF EQUATIONS Chao Yang Computational Research Division Lawrence Berkeley National Laboratory Berkeley, CA, USA 2 OUTLINE Sparse matrix storage format Basic factorization
Krylov subspace projection methods
 I.1.(a) Krylov subspace projection methods Orthogonal projection technique : framework Let A be an n n complex matrix and K be an m-dimensional subspace of C n. An orthogonal projection technique seeks
I.1.(a) Krylov subspace projection methods Orthogonal projection technique : framework Let A be an n n complex matrix and K be an m-dimensional subspace of C n. An orthogonal projection technique seeks
On Spectral Factorization and Riccati Equations for Time-Varying Systems in Discrete Time
 On Spectral Factorization and Riccati Equations for Time-Varying Systems in Discrete Time Alle-Jan van der Veen and Michel Verhaegen Delft University of Technology Department of Electrical Engineering
On Spectral Factorization and Riccati Equations for Time-Varying Systems in Discrete Time Alle-Jan van der Veen and Michel Verhaegen Delft University of Technology Department of Electrical Engineering
Lecture 3: QR-Factorization
 Lecture 3: QR-Factorization This lecture introduces the Gram Schmidt orthonormalization process and the associated QR-factorization of matrices It also outlines some applications of this factorization
Lecture 3: QR-Factorization This lecture introduces the Gram Schmidt orthonormalization process and the associated QR-factorization of matrices It also outlines some applications of this factorization
AMS526: Numerical Analysis I (Numerical Linear Algebra) Lecture 23: GMRES and Other Krylov Subspace Methods; Preconditioning
 AMS526: Numerical Analysis I (Numerical Linear Algebra) Lecture 23: GMRES and Other Krylov Subspace Methods; Preconditioning Xiangmin Jiao SUNY Stony Brook Xiangmin Jiao Numerical Analysis I 1 / 18 Outline
AMS526: Numerical Analysis I (Numerical Linear Algebra) Lecture 23: GMRES and Other Krylov Subspace Methods; Preconditioning Xiangmin Jiao SUNY Stony Brook Xiangmin Jiao Numerical Analysis I 1 / 18 Outline
Bindel, Fall 2016 Matrix Computations (CS 6210) Notes for
 1 Iteration basics Notes for 2016-11-07 An iterative solver for Ax = b is produces a sequence of approximations x (k) x. We always stop after finitely many steps, based on some convergence criterion, e.g.
1 Iteration basics Notes for 2016-11-07 An iterative solver for Ax = b is produces a sequence of approximations x (k) x. We always stop after finitely many steps, based on some convergence criterion, e.g.
6.241 Dynamic Systems and Control
 6.241 Dynamic Systems and Control Lecture 24: H2 Synthesis Emilio Frazzoli Aeronautics and Astronautics Massachusetts Institute of Technology May 4, 2011 E. Frazzoli (MIT) Lecture 24: H 2 Synthesis May
6.241 Dynamic Systems and Control Lecture 24: H2 Synthesis Emilio Frazzoli Aeronautics and Astronautics Massachusetts Institute of Technology May 4, 2011 E. Frazzoli (MIT) Lecture 24: H 2 Synthesis May
Structured eigenvalue/eigenvector backward errors of matrix pencils arising in optimal control
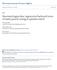 Electronic Journal of Linear Algebra Volume 34 Volume 34 08) Article 39 08 Structured eigenvalue/eigenvector backward errors of matrix pencils arising in optimal control Christian Mehl Technische Universitaet
Electronic Journal of Linear Algebra Volume 34 Volume 34 08) Article 39 08 Structured eigenvalue/eigenvector backward errors of matrix pencils arising in optimal control Christian Mehl Technische Universitaet
Definite versus Indefinite Linear Algebra. Christian Mehl Institut für Mathematik TU Berlin Germany. 10th SIAM Conference on Applied Linear Algebra
 Definite versus Indefinite Linear Algebra Christian Mehl Institut für Mathematik TU Berlin Germany 10th SIAM Conference on Applied Linear Algebra Monterey Bay Seaside, October 26-29, 2009 Indefinite Linear
Definite versus Indefinite Linear Algebra Christian Mehl Institut für Mathematik TU Berlin Germany 10th SIAM Conference on Applied Linear Algebra Monterey Bay Seaside, October 26-29, 2009 Indefinite Linear
EAD 115. Numerical Solution of Engineering and Scientific Problems. David M. Rocke Department of Applied Science
 EAD 115 Numerical Solution of Engineering and Scientific Problems David M. Rocke Department of Applied Science Taylor s Theorem Can often approximate a function by a polynomial The error in the approximation
EAD 115 Numerical Solution of Engineering and Scientific Problems David M. Rocke Department of Applied Science Taylor s Theorem Can often approximate a function by a polynomial The error in the approximation
H 2 optimal model reduction - Wilson s conditions for the cross-gramian
 H 2 optimal model reduction - Wilson s conditions for the cross-gramian Ha Binh Minh a, Carles Batlle b a School of Applied Mathematics and Informatics, Hanoi University of Science and Technology, Dai
H 2 optimal model reduction - Wilson s conditions for the cross-gramian Ha Binh Minh a, Carles Batlle b a School of Applied Mathematics and Informatics, Hanoi University of Science and Technology, Dai
CS 450 Numerical Analysis. Chapter 5: Nonlinear Equations
 Lecture slides based on the textbook Scientific Computing: An Introductory Survey by Michael T. Heath, copyright c 2018 by the Society for Industrial and Applied Mathematics. http://www.siam.org/books/cl80
Lecture slides based on the textbook Scientific Computing: An Introductory Survey by Michael T. Heath, copyright c 2018 by the Society for Industrial and Applied Mathematics. http://www.siam.org/books/cl80
OUTLINE ffl CFD: elliptic pde's! Ax = b ffl Basic iterative methods ffl Krylov subspace methods ffl Preconditioning techniques: Iterative methods ILU
 Preconditioning Techniques for Solving Large Sparse Linear Systems Arnold Reusken Institut für Geometrie und Praktische Mathematik RWTH-Aachen OUTLINE ffl CFD: elliptic pde's! Ax = b ffl Basic iterative
Preconditioning Techniques for Solving Large Sparse Linear Systems Arnold Reusken Institut für Geometrie und Praktische Mathematik RWTH-Aachen OUTLINE ffl CFD: elliptic pde's! Ax = b ffl Basic iterative
A Continuation Approach to a Quadratic Matrix Equation
 A Continuation Approach to a Quadratic Matrix Equation Nils Wagner nwagner@mecha.uni-stuttgart.de Institut A für Mechanik, Universität Stuttgart GAMM Workshop Applied and Numerical Linear Algebra September
A Continuation Approach to a Quadratic Matrix Equation Nils Wagner nwagner@mecha.uni-stuttgart.de Institut A für Mechanik, Universität Stuttgart GAMM Workshop Applied and Numerical Linear Algebra September
Modern Optimal Control
 Modern Optimal Control Matthew M. Peet Arizona State University Lecture 19: Stabilization via LMIs Optimization Optimization can be posed in functional form: min x F objective function : inequality constraints
Modern Optimal Control Matthew M. Peet Arizona State University Lecture 19: Stabilization via LMIs Optimization Optimization can be posed in functional form: min x F objective function : inequality constraints
Linear Algebra Massoud Malek
 CSUEB Linear Algebra Massoud Malek Inner Product and Normed Space In all that follows, the n n identity matrix is denoted by I n, the n n zero matrix by Z n, and the zero vector by θ n An inner product
CSUEB Linear Algebra Massoud Malek Inner Product and Normed Space In all that follows, the n n identity matrix is denoted by I n, the n n zero matrix by Z n, and the zero vector by θ n An inner product
Chapter 7 Iterative Techniques in Matrix Algebra
 Chapter 7 Iterative Techniques in Matrix Algebra Per-Olof Persson persson@berkeley.edu Department of Mathematics University of California, Berkeley Math 128B Numerical Analysis Vector Norms Definition
Chapter 7 Iterative Techniques in Matrix Algebra Per-Olof Persson persson@berkeley.edu Department of Mathematics University of California, Berkeley Math 128B Numerical Analysis Vector Norms Definition
Computational Methods. Eigenvalues and Singular Values
 Computational Methods Eigenvalues and Singular Values Manfred Huber 2010 1 Eigenvalues and Singular Values Eigenvalues and singular values describe important aspects of transformations and of data relations
Computational Methods Eigenvalues and Singular Values Manfred Huber 2010 1 Eigenvalues and Singular Values Eigenvalues and singular values describe important aspects of transformations and of data relations
j=1 x j p, if 1 p <, x i ξ : x i < ξ} 0 as p.
 LINEAR ALGEBRA Fall 203 The final exam Almost all of the problems solved Exercise Let (V, ) be a normed vector space. Prove x y x y for all x, y V. Everybody knows how to do this! Exercise 2 If V is a
LINEAR ALGEBRA Fall 203 The final exam Almost all of the problems solved Exercise Let (V, ) be a normed vector space. Prove x y x y for all x, y V. Everybody knows how to do this! Exercise 2 If V is a
ADI-preconditioned FGMRES for solving large generalized Lyapunov equations - A case study
 -preconditioned for large - A case study Matthias Bollhöfer, André Eppler TU Braunschweig Institute Computational Mathematics Syrene-MOR Workshop, TU Hamburg October 30, 2008 2 / 20 Outline 1 2 Overview
-preconditioned for large - A case study Matthias Bollhöfer, André Eppler TU Braunschweig Institute Computational Mathematics Syrene-MOR Workshop, TU Hamburg October 30, 2008 2 / 20 Outline 1 2 Overview
Eigenvalue Problems. Eigenvalue problems occur in many areas of science and engineering, such as structural analysis
 Eigenvalue Problems Eigenvalue problems occur in many areas of science and engineering, such as structural analysis Eigenvalues also important in analyzing numerical methods Theory and algorithms apply
Eigenvalue Problems Eigenvalue problems occur in many areas of science and engineering, such as structural analysis Eigenvalues also important in analyzing numerical methods Theory and algorithms apply
In order to solve the linear system KL M N when K is nonsymmetric, we can solve the equivalent system
 !"#$% "&!#' (%)!#" *# %)%(! #! %)!#" +, %"!"#$ %*&%! $#&*! *# %)%! -. -/ 0 -. 12 "**3! * $!#%+,!2!#% 44" #% ! # 4"!#" "%! "5"#!!#6 -. - #% " 7% "3#!#3! - + 87&2! * $!#% 44" ) 3( $! # % %#!!#%+ 9332!
!"#$% "&!#' (%)!#" *# %)%(! #! %)!#" +, %"!"#$ %*&%! $#&*! *# %)%! -. -/ 0 -. 12 "**3! * $!#%+,!2!#% 44" #% ! # 4"!#" "%! "5"#!!#6 -. - #% " 7% "3#!#3! - + 87&2! * $!#% 44" ) 3( $! # % %#!!#%+ 9332!
Model order reduction of large-scale dynamical systems with Jacobi-Davidson style eigensolvers
 MAX PLANCK INSTITUTE International Conference on Communications, Computing and Control Applications March 3-5, 2011, Hammamet, Tunisia. Model order reduction of large-scale dynamical systems with Jacobi-Davidson
MAX PLANCK INSTITUTE International Conference on Communications, Computing and Control Applications March 3-5, 2011, Hammamet, Tunisia. Model order reduction of large-scale dynamical systems with Jacobi-Davidson
Bindel, Fall 2016 Matrix Computations (CS 6210) Notes for
 1 Logistics Notes for 2016-08-29 General announcement: we are switching from weekly to bi-weekly homeworks (mostly because the course is much bigger than planned). If you want to do HW but are not formally
1 Logistics Notes for 2016-08-29 General announcement: we are switching from weekly to bi-weekly homeworks (mostly because the course is much bigger than planned). If you want to do HW but are not formally
STAT 309: MATHEMATICAL COMPUTATIONS I FALL 2018 LECTURE 9
 STAT 309: MATHEMATICAL COMPUTATIONS I FALL 2018 LECTURE 9 1. qr and complete orthogonal factorization poor man s svd can solve many problems on the svd list using either of these factorizations but they
STAT 309: MATHEMATICAL COMPUTATIONS I FALL 2018 LECTURE 9 1. qr and complete orthogonal factorization poor man s svd can solve many problems on the svd list using either of these factorizations but they
Iterative methods for Linear System of Equations. Joint Advanced Student School (JASS-2009)
 Iterative methods for Linear System of Equations Joint Advanced Student School (JASS-2009) Course #2: Numerical Simulation - from Models to Software Introduction In numerical simulation, Partial Differential
Iterative methods for Linear System of Equations Joint Advanced Student School (JASS-2009) Course #2: Numerical Simulation - from Models to Software Introduction In numerical simulation, Partial Differential
Lecture 11: CMSC 878R/AMSC698R. Iterative Methods An introduction. Outline. Inverse, LU decomposition, Cholesky, SVD, etc.
 Lecture 11: CMSC 878R/AMSC698R Iterative Methods An introduction Outline Direct Solution of Linear Systems Inverse, LU decomposition, Cholesky, SVD, etc. Iterative methods for linear systems Why? Matrix
Lecture 11: CMSC 878R/AMSC698R Iterative Methods An introduction Outline Direct Solution of Linear Systems Inverse, LU decomposition, Cholesky, SVD, etc. Iterative methods for linear systems Why? Matrix
Synopsis of Numerical Linear Algebra
 Synopsis of Numerical Linear Algebra Eric de Sturler Department of Mathematics, Virginia Tech sturler@vt.edu http://www.math.vt.edu/people/sturler Iterative Methods for Linear Systems: Basics to Research
Synopsis of Numerical Linear Algebra Eric de Sturler Department of Mathematics, Virginia Tech sturler@vt.edu http://www.math.vt.edu/people/sturler Iterative Methods for Linear Systems: Basics to Research
Scientific Computing: Solving Linear Systems
 Scientific Computing: Solving Linear Systems Aleksandar Donev Courant Institute, NYU 1 donev@courant.nyu.edu 1 Course MATH-GA.2043 or CSCI-GA.2112, Spring 2012 September 17th and 24th, 2015 A. Donev (Courant
Scientific Computing: Solving Linear Systems Aleksandar Donev Courant Institute, NYU 1 donev@courant.nyu.edu 1 Course MATH-GA.2043 or CSCI-GA.2112, Spring 2012 September 17th and 24th, 2015 A. Donev (Courant
Data Analysis and Manifold Learning Lecture 2: Properties of Symmetric Matrices and Examples
 Data Analysis and Manifold Learning Lecture 2: Properties of Symmetric Matrices and Examples Radu Horaud INRIA Grenoble Rhone-Alpes, France Radu.Horaud@inrialpes.fr http://perception.inrialpes.fr/ Outline
Data Analysis and Manifold Learning Lecture 2: Properties of Symmetric Matrices and Examples Radu Horaud INRIA Grenoble Rhone-Alpes, France Radu.Horaud@inrialpes.fr http://perception.inrialpes.fr/ Outline
Balanced Truncation 1
 Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.242, Fall 2004: MODEL REDUCTION Balanced Truncation This lecture introduces balanced truncation for LTI
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.242, Fall 2004: MODEL REDUCTION Balanced Truncation This lecture introduces balanced truncation for LTI
Chemnitz Scientific Computing Preprints
 Arnd Meyer The Koiter shell equation in a coordinate free description CSC/1-0 Chemnitz Scientific Computing Preprints ISSN 1864-0087 Chemnitz Scientific Computing Preprints Impressum: Chemnitz Scientific
Arnd Meyer The Koiter shell equation in a coordinate free description CSC/1-0 Chemnitz Scientific Computing Preprints ISSN 1864-0087 Chemnitz Scientific Computing Preprints Impressum: Chemnitz Scientific
MATH36001 Generalized Inverses and the SVD 2015
 MATH36001 Generalized Inverses and the SVD 201 1 Generalized Inverses of Matrices A matrix has an inverse only if it is square and nonsingular. However there are theoretical and practical applications
MATH36001 Generalized Inverses and the SVD 201 1 Generalized Inverses of Matrices A matrix has an inverse only if it is square and nonsingular. However there are theoretical and practical applications
Model Order Reduction of Continuous LTI Large Descriptor System Using LRCF-ADI and Square Root Balanced Truncation
 , July 1-3, 15, London, U.K. Model Order Reduction of Continuous LI Large Descriptor System Using LRCF-ADI and Square Root Balanced runcation Mehrab Hossain Likhon, Shamsil Arifeen, and Mohammad Sahadet
, July 1-3, 15, London, U.K. Model Order Reduction of Continuous LI Large Descriptor System Using LRCF-ADI and Square Root Balanced runcation Mehrab Hossain Likhon, Shamsil Arifeen, and Mohammad Sahadet
Balancing-Related Model Reduction for Large-Scale Systems
 Balancing-Related Model Reduction for Large-Scale Systems Peter Benner Professur Mathematik in Industrie und Technik Fakultät für Mathematik Technische Universität Chemnitz D-09107 Chemnitz benner@mathematik.tu-chemnitz.de
Balancing-Related Model Reduction for Large-Scale Systems Peter Benner Professur Mathematik in Industrie und Technik Fakultät für Mathematik Technische Universität Chemnitz D-09107 Chemnitz benner@mathematik.tu-chemnitz.de
Kasetsart University Workshop. Multigrid methods: An introduction
 Kasetsart University Workshop Multigrid methods: An introduction Dr. Anand Pardhanani Mathematics Department Earlham College Richmond, Indiana USA pardhan@earlham.edu A copy of these slides is available
Kasetsart University Workshop Multigrid methods: An introduction Dr. Anand Pardhanani Mathematics Department Earlham College Richmond, Indiana USA pardhan@earlham.edu A copy of these slides is available
Solving linear systems (6 lectures)
 Chapter 2 Solving linear systems (6 lectures) 2.1 Solving linear systems: LU factorization (1 lectures) Reference: [Trefethen, Bau III] Lecture 20, 21 How do you solve Ax = b? (2.1.1) In numerical linear
Chapter 2 Solving linear systems (6 lectures) 2.1 Solving linear systems: LU factorization (1 lectures) Reference: [Trefethen, Bau III] Lecture 20, 21 How do you solve Ax = b? (2.1.1) In numerical linear
In this article we discuss sparse matrix algorithms and parallel algorithms, Solving Large-Scale Control Problems
 F E A T U R E Solving Large-Scale Control Problems EYEWIRE Sparsity and parallel algorithms: two approaches to beat the curse of dimensionality. By Peter Benner In this article we discuss sparse matrix
F E A T U R E Solving Large-Scale Control Problems EYEWIRE Sparsity and parallel algorithms: two approaches to beat the curse of dimensionality. By Peter Benner In this article we discuss sparse matrix
Krylov Subspace Type Methods for Solving Projected Generalized Continuous-Time Lyapunov Equations
 Krylov Subspace Type Methods for Solving Proected Generalized Continuous-Time Lyapunov Equations YUIAN ZHOU YIQIN LIN Hunan University of Science and Engineering Institute of Computational Mathematics
Krylov Subspace Type Methods for Solving Proected Generalized Continuous-Time Lyapunov Equations YUIAN ZHOU YIQIN LIN Hunan University of Science and Engineering Institute of Computational Mathematics
MIT Final Exam Solutions, Spring 2017
 MIT 8.6 Final Exam Solutions, Spring 7 Problem : For some real matrix A, the following vectors form a basis for its column space and null space: C(A) = span,, N(A) = span,,. (a) What is the size m n of
MIT 8.6 Final Exam Solutions, Spring 7 Problem : For some real matrix A, the following vectors form a basis for its column space and null space: C(A) = span,, N(A) = span,,. (a) What is the size m n of
7.2 Steepest Descent and Preconditioning
 7.2 Steepest Descent and Preconditioning Descent methods are a broad class of iterative methods for finding solutions of the linear system Ax = b for symmetric positive definite matrix A R n n. Consider
7.2 Steepest Descent and Preconditioning Descent methods are a broad class of iterative methods for finding solutions of the linear system Ax = b for symmetric positive definite matrix A R n n. Consider
arxiv: v1 [math.na] 5 May 2011
![arxiv: v1 [math.na] 5 May 2011 arxiv: v1 [math.na] 5 May 2011](/thumbs/95/123583746.jpg) ITERATIVE METHODS FOR COMPUTING EIGENVALUES AND EIGENVECTORS MAYSUM PANJU arxiv:1105.1185v1 [math.na] 5 May 2011 Abstract. We examine some numerical iterative methods for computing the eigenvalues and
ITERATIVE METHODS FOR COMPUTING EIGENVALUES AND EIGENVECTORS MAYSUM PANJU arxiv:1105.1185v1 [math.na] 5 May 2011 Abstract. We examine some numerical iterative methods for computing the eigenvalues and
NORMS ON SPACE OF MATRICES
 NORMS ON SPACE OF MATRICES. Operator Norms on Space of linear maps Let A be an n n real matrix and x 0 be a vector in R n. We would like to use the Picard iteration method to solve for the following system
NORMS ON SPACE OF MATRICES. Operator Norms on Space of linear maps Let A be an n n real matrix and x 0 be a vector in R n. We would like to use the Picard iteration method to solve for the following system
The QR Decomposition
 The QR Decomposition We have seen one major decomposition of a matrix which is A = LU (and its variants) or more generally PA = LU for a permutation matrix P. This was valid for a square matrix and aided
The QR Decomposition We have seen one major decomposition of a matrix which is A = LU (and its variants) or more generally PA = LU for a permutation matrix P. This was valid for a square matrix and aided
Balanced Truncation Model Reduction of Large and Sparse Generalized Linear Systems
 Balanced Truncation Model Reduction of Large and Sparse Generalized Linear Systems Jos M. Badía 1, Peter Benner 2, Rafael Mayo 1, Enrique S. Quintana-Ortí 1, Gregorio Quintana-Ortí 1, A. Remón 1 1 Depto.
Balanced Truncation Model Reduction of Large and Sparse Generalized Linear Systems Jos M. Badía 1, Peter Benner 2, Rafael Mayo 1, Enrique S. Quintana-Ortí 1, Gregorio Quintana-Ortí 1, A. Remón 1 1 Depto.
