An efficient certificateless two-party authenticated key agreement protocol
|
|
|
- Dwight Gerald Marsh
- 5 years ago
- Views:
Transcription
1 An effcent certfcatele two-party authentcated key agreement protocol Debao He ahadeo Padhye Janhua hen chool of Mathematc and tattc Wuhan Unverty Wuhan hna Motlal Nehru NAtonal Inttute of Technology Allahabad Inda Emal: Abtract: Due to avodng the key ecrow problem n the dentty-baed cryptoytem certfcatele publc key cryptoytem (PK) ha receved a gnfcant attenton A an mportant part of the PK the certfcatele authentcated key agreement (AKA) protocol alo receved conderable attenton Mot AKA protocol are bult from blnear mappng on ellptc curve whch need cotly operaton To mprove the performance everal parng-free AKA protocol have been propoed In th paper we propoe a new parng-free AKA protocol ompared wth the related protocol our protocol ha better performance We alo how our protocol provably ecure n a very trong ecurty model e the extended anett- Krawczyk (ek) model Key word: ertfcatele cryptography; Authentcated key agreement; Provable ecurty; Blnear parng; Ellptc curve lafcaton ode: T7 94A60 Introducton To realze nformaton ecurty the publc key cryptography ha been wdely ued n network communcaton In the tradtonal publc key cryptography (PK) there a need for certfcate to aurance to the uer about the relatonhp between a publc key and the dentty of the holder of the correpondng prvate key o there come the problem of certfcate management ncludng revocaton torage dtrbuton etc [] To olve the above problem hamr ntroduced the concept of dentty-baed cryptography (ID-PK) [] In ID-PK ettng a uer publc key can be derved from h dentty (eg h name or emal addre) and h ecret key generated by the Key Generaton enter ( KG) Then there come the key ecrow problem e the PKG know all the uer ecret key In 003 Al-Ryam et al [3] propoed the certfcatele publc key cryptography (PK) to olve the key ecrow problem nce then the PK receved a gnfcant attenton
2 After Al-Ryam et al work [3] numerou certfcatele authentcated key agreement (AKA) protocol ung blnear mappng on ellptc curve have been propoed eg [4 0] However the relatve computaton cot of a parng approxmately twenty tme hgher than that of the calar multplcaton over ellptc curve group [] Therefore AKA protocol wthout blnear parng would be more appealng n term of effcency Recently everal AKA protocol wthout parng have been propoed n [-5] Yang et al [4] ponted out that nether Geng et al protocol [4] nor Hou et al protocol [3] ecure He et al [5] alo propoed a AKA protocol wthout parng However He et al protocol vulnerable to the type adverary [6] Although the latet AKA protocol [6] more effcent than other protocol [-5] t provably ecure under the mbr model [7] whch a very weak model Yang et al have hown that ther cheme provably ecure n a very trong model-the extended anett-krawczyk (ek) model [8] However the uer n Yang et al protocol need nne ellptc curve calar multplcaton to fnh the key agreement Moreover the uer ha to verfy the valdty of publc key Th not only ncreae the burden of the uer but alo revere the thought of PK In th paper we wll propoe a new parng-free AKA protocol whch provably ecure n the ek model Bede our protocol ha better performance than the related protocol The remander of th paper organzed a follow ecton decrbe ome prelmnare In ecton 3 we propoe our AKA protocol The ecurty analy of the propoed protocol preented n ecton 4 In ecton 5 performance analy preented Fnally n ecton 6 we conclude the paper Prelmnare Notaton In th ubecton we frt ntroduce ome notaton a follow whch are ued n th paper p n : two large prme number; F p : a fnte feld; E/ F p : an ellptc curve defned on F p ; G : the cyclc addtve group compoed of the pont on E / F p ;
3 P : a generator of G ; H () : a ecure one-way hah functon where H :{0} G Zn ; H () : a ecure one-way hah functon where H :{0} {0} G G G G G Zp ; ID : the dentty of uer ; ( x P pub ): the KG prvate/publc key par where Ppub = xp; ( x P ): the uer ecret value/publc key par where P = x P; ( r R ): a random pont generated by KG where R = r P; ( R ) : the uer partal prvate key where = r + hxmod n h = H ( ) ID R ; ( t T ): the uer ephemeral prvate/publc key par where T = t P; Background of ellptc curve group et the ymbol E/ F p denote an ellptc curve E over a prme fnte feld F p defned by an equaton y = x 3 + ax + b p and wth the dcrmnant a b F () 3 Δ= 4a + 7b 0 () The pont on E / F p together wth an extra pont O called the pont at nfnty form a group G = {( x y): x y F E( x y) = 0} { O} (3) p G a cyclc addtve group n the pont addton + defned a follow: et PQ G l be the lne contanng P and Q (tangent lne to E/ F p f P = Q ) and R the thrd pont of nterecton of l wth E / F p et l be the lne connectng R and O Then P + Q the pont uch that l nterect E/ F p at R and O calar multplcaton over E/ F p can be computed a follow: tp = P + P + + P( t tme) (4) et the order of G be n The followng problem are commonly ued n the ecurty analy of many cryptographc protocol 3
4 omputatonal Dffe-Hellman (DH) problem: Gven a generator P of G and ( ap bp ) for unknown ab R Zn the tak of DH problem to compute abp For convenence we defne the functon cdh a cdh ( ap bp )= abp Deconal Dffe-Hellman (DDH) problem: Gven a generator P of G and ( ap bp cp ) for unknown abc R Zn the tak of DDH problem to decde whether the equaton abp = cp hold Gap Dffe-Hellman (GDH) problem: Gven a generator P of G ( ap bp ) for unknown ab and an oracle O ddhp the tak of GDH problem R Zn to compute abp where O ddhp a decon oracle that on nput ( ap bp cp ) anwer f cdh( ap bp) = cp ; anwer 0 otherwe The GDH aumpton tate that the probablty of any polynomal-tme algorthm to olve the GDH problem neglgble AKA protocol A AKA protocol cont of x polynomal-tme algorthm [ 8]: etup Partal - Prvate - Key - Extract et ecret Value et - Prvate - Key et Publc Key and Key Agreement Thee algorthm are defned a follow etup : Th algorthm take ecurty parameter k a nput and return the ytem parameter param and mater key Partal - Prvate - Key - Extract : Th algorthm take param mater key a uer' dentty ID a nput and return a partal prvate key et ecret Value : Th algorthm take param and a uer' dentty ID a nput and generate a ecret value et - Prvate - Key : Th algorthm take param a uer' partal prvate key and h ecret value a nput and output the full prvate key et Publc Key : Th algorthm take param and a uer' ecret value a nput and generate a publc key for the uer Key Agreement : Th a probabltc polynomal-tme nteractve algorthm whch nvolve two entte A and B f the protocol doe not fal A and B wll obtan a ecret eon key 4
5 3 ecurty model for AKA protocol In AKA cheme there are two type of adverare wth dfferent capablte [9 4] The type adverary A act a a dhonet uer whle the type adverary A act a a malcou key generaton center (KG) A doe not know the mater key but A can replace the publc key of any entty wth a value of h choce A know the mater key but he cannot replace any uer' publc key et repreent the th eon whch run at party wth ntended partner party A eon enter an accepted tate when t compute a t eon key K Two eon and are called matchng f they have the ame eon dentty ppold et al [9] tranformed orgnal ek model [8] from the tradtonal PKI-baed ettng to the PK ettng The ek model n the PK ettng defned by the followng game between a challenger and an adverary A { A A } The game run n two phae Durng the frt phae the adverary A allowed to ue the followng quere n any order: reate() : On recevng uch a query generate the publc/prvate key par for partcpant wth dentty ID RevealMaterKey : gve the mater ecret key to A RevealeonKey( ): If the eon ha not been accepted return to A Otherwe reveal the accepted eon key to A to A RevealPartalPrvateKey() : return partcpant partal prvate key RevealecretValue() : return partcpant ecret value to A ReplacePublcKey( pk ): replace partcpant publc key wth the value choe by A RevealEphemeralKey( ): return partcpant ephemeral prvate key to A end( m) : The adverary end the meage m to the eon and get a repone accordng to the protocol pecfcaton 5
6 Once the adverary A decde that the frt phae over t tart the econd phae by choong a freh eon and ung a Tet( ) query where the freh eon and tet query are defned later The type adverary A could get any uer ecret value nce he can replace the publc key of any entty wth a value of h choce The type adverary A could get any uer partal prvate key nce he ha acce to the mater key Then everal cae do not ext n ppold et al model [9] To get better performance we defne the defnton of frehne for AKA cheme agant two type of adverary a follow Defnton (Frehne for AKA cheme agant Type Adverary) et ntance be a completed eon whch executed by an honet party wth another honet party We defne to be freh f none of the followng three condton hold: The adverary A reveal the eon key of or of t matchng eon (f the latter ext) t engaged n the eon matchng to and A ether reveal both of partal prvate key and ephemeral prvate key t or both of partal prvate key and ephemeral prvate key No eon matchng to ext and A ether reveal both of partal prvate key and ephemeral prvate key or partal prvate key Defnton (Frehne for AKA cheme agant Type Adverary) et ntance be a completed eon whch executed by an honet party wth another honet party We defne to be freh f none of the followng three condton hold: The adverary A reveal the eon key of or of t matchng eon (f the latter ext) t engaged n the eon matchng to and A ether reveal both of ecret value and ephemeral prvate key or t both of ecret value and ephemeral prvate key 6
7 No eon matchng to ext and A ether reveal both of ecret value and ephemeral prvate key or partal prvate key Tet( ): At ome pont A may chooe one of the oracle ay to ak a ngle Tet query Th oracle mut be freh To anwer the query the oracle flp a far con b {0} and return the eon key held by f b = 0 or a random ample from the dtrbuton of the eon key f b = At the end of the game A mut output a gue bt b A wn f and only f b = b A advantage to wn the above game denoted by Adv ( k) defned a: Adv ( k) Pr[ b A = = b] where k a ecurty parameter Defnton 3 A AKA cheme ad to be ecure f: t () In the preence of a bengn adverary on and both oracle alway agree on the ame eon key and th key dtrbuted unformly at random () For any adverary A { A A } AdvA ( k) neglgble 3 Our protocol In th ecton we wll propoe a new AKA protocol baed on prevou work [9 4 6] Our protocol cont of x polynomal-tme algorthm They are decrbed a follow etup : Th algorthm take a ecurty parameter k a an nput return ytem parameter and a mater key Gven k KG doe the followng tep ) KG chooe a k -bt prme p and determne the tuple { F E/ F G P } a defned n ecton p p A ) KG chooe the mater prvate key x Z n and compute the mater publc key Ppub = xp 3) KG chooe two cryptographc ecure hah functon :{0} H G Zn and H :{0} {0} G G G G G G Zn 4) KG publhe param = { Fp E / Fp G P Ppub H H } a ytem parameter and keep the mater key x ecretly 7
8 Partal - Prvate - Key - Extract : Th algorthm take mater key a uer dentfer ytem parameter a nput and return the uer ID-baed prvate key KG work a follow ) KG chooe a random number h ( ) = H ID R r Z compute R = r P and ) KG compute = r + hxmod n and ue ( R ) to the uer through ecret channel and et et ecret Value : The uer pck randomly x a h ecret value et - Prvate - Key : The uer wth dentty a t prvate key n n x Z compute P = x P ID take the par k = ( x ) et Publc Key : The uer wth dentty ID take pk = ( P) a t publc key Key Agreement : Aume that an entty A wth dentty ID A ha prvate key k = ( x ) and publc key pk = ( P ) and an entty B wth dentty B A A A A ID ha prvate key k = ( x ) and publc key pk = ( P ) want to B B B etablh a eon key they can do a hown n Fg a follow ) A chooe a random number end M = { ID R T } to B A A A t A n A Z and compute T A = t A P then A B B ) After recevng M B chooe a random number t B Z and n compute TB = tb P then B end M = { IDB RB TB} to A Then both A and B can compute the hared ecret a follow: A compute K = ( t + )( T + R + H ( ID R ) P ) (5) AB A A B B B B pub and B compute K = ( t + x )( T + P ) (6) AB A A B B K = t T (7) 3 AB A B K = ( t + )( T + R + H ( ID R ) P ) (8) BA B B A A A A pub K = ( t + x )( T + P ) (9) BA B B A A 8
9 and K = t T (0) 3 BA B A Thu the agreed eon key for A and B can be computed a: k = H ID ID T T K K K 3 ( A B A B AB AB AB) = H ID ID T T K K K 3 ( A B A B BA BA BA) () B Fg Key agreement of our protocol nce TA = ta P PA = xa P P ( ) A = RA + H IDA RA Ppub TB = tb P P = x P and P= R + H ( ) ID R P then we have B B B B B pub K = ( t + )( T + R + H ( ID R ) P ) AB A A B B B B pub = ( t + )( t + ) P= ( t + )( t + ) P A A B B B B A A = ( t + )( T + R + H ( ID R ) P ) = K B B A A A A pub BA () and K = ( t + x )( T + P ) AB A A B B = ( t + x )( t + x ) P = ( t + x )( t + x ) P A A B B B B A A = ( t + x )( T + P ) = K B B A A BA 3 3 AB A B B A BA (3) K = t t P= t t P= K (4) Thu the correctne of the protocol proved 4 ecurty Analy In th ecton we wll how our cheme provably ecure n ek model We treat H and H a two random oracle [9] For the ecurty the followng lemma and theorem are provded emma If two oracle are matchng both of them wll be accepted and wll get the ame eon key whch dtrbuted unformly at random n the eon key ample pace 9
10 Proof From the correcton analy of our protocol n ecton 3 we know f two oracle are matchng then both of them are accepted and have the ame eon key The eon key are dtrbuted unformly nce t A and t B are elected unformly durng the executon emma Aumng that the GDH problem ntractable the advantage of a type adverary agant our protocol neglgble Proof uppoe that there a type adverary A who can wn the game defned n ubecton 3 wth a non-neglgble advantage Adv ( k) A n polynomal-tme t Then we wll how how to ue the ablty of A to contruct an algorthm to olve the GDH problem et n 0 be the maxmum number of eon that any one party may have Aume that the adverary A actvate at mot n dtnctve honet parte Aume that the adverary A actvate at mot n dtnctve hah quere Aume alo that Adv ( k) A non-neglgble Before the game tart tre to gue the tet eon and the trategy that the adverary A wll adopt randomly elect two ndexe I J { n} : I J whch repreent the I th and the J th dtnct honet party that the adverary ntally chooe Alo chooe { n0} and determne the Tet eon IJ whch correct wth probablty larger than nn et T J I be the matchng eon of IJ 0 nce H and H are modeled a random oracle after the adverary ue the tet query t ha only three poble way to dtnguh the teted eon key from a random trng: AE : Forgng attack: Aume that IJ the tet eon At ome pont n t run the adverary A quere H on the value 3 ( I J I J IJ IJ IJ ) ID ID T T K K K n the tet eon owned by I communcatng wth J learly n th cae A compute the value K IJ K IJ and K 3 IJ telf AE : Gueng attack: A correctly guee the eon key AE 3: Key-replcaton attack: The adverary A force a nonmatchng eon to have the ame eon key wth the tet eon In th cae 0
11 the adverary A can mply learn the eon key by queryng the nonmatchng eon nce H a random oracle the probablty of gueng the output of H k O (/ ) whch neglgble The nput to the key dervaton functon H nclude all nformaton that can unquely dentfy the matchng eon nce two non-matchng eon can not have the ame dentte and the ame ephemeral publc key and H modeled a a random oracle the ucce probablty of Key-replcaton attack alo neglgble Thu Gueng attack and Key-replcaton attack can be ruled out and the ret of the proof manly devoted to the analy of Forgng attack A the attack that the adverary A mount Forgng attack A can not get an advantage n wnnng the game agant the protocol unle t quere the H oracle on the eon key The ret of th ecton manly devoted to the analy of the Forgng attack To relate the advantage of the adverary A agant our protocol to the GDH aumpton we ue a clacal reducton approach In the followng a challenger ntereted to ue the adverary A to turn A advantage n dtnguhng the teted eon key from a random trng nto an advantage n olvng the GDH problem The followng two ub-cae hould be condered AE : No honet party own a matchng eon to the Tet eon AE : The Tet eon ha a matchng eon owned by another honet party The analy of AE : nce A trong type adverary then he can get any uer ecret key x value through ReplacePublcKey query Accordng to Defnton ha the followng two choce for A trategy: AE : At ome pont the partal prvate key of party I ha been revealed by the adverary A Accordng to Defnton A not permtted to reveal the ephemeral prvate key of the Tet eon AE : The partal prvate key of party I ha never been revealed by the adverary A Accordng to Defnton A may reveal the ephemeral prvate key of the Tet eon AE :
12 GDH et Adv ( k) be the advantage that the challenger get n olvng the GDH problem gven the ecurty parameter k Gven a GDH problem ntance(u = upv = vp O ddhp ) and tak to compute cdh( U V ) = uvp where O ddhp a decon oracle that on nput ( ap bp cp ) anwer f cdh( ap bp) = cp ; anwer 0 otherwe frt chooe P 0 G at random et P 0 a the ytem publc key P pub elect the ytem parameter param = { F E / F G P P H H } and end param to A Then p p pub mulate the game outlned n ecton 3 a follow reate() : mantan an ntally empty lt contng of tuple of the form ( ID R x P ) If = J chooe two random number h x Z compute R = U hp 0 P = xp et H ( ID R) h and tore n ( ID R x P ) and ( ID R h ) n and H eparately Otherwe chooe three random number h x Zn compute R = P hp pub P = xp et H ( ) ID R h and tore ( ID R x P) and ( ID R h ) n and H eparately H ( ) ID R : mantan an ntally empty lt H whch contan tuple of the form ( ID R h ) If ( ID R ) on the lt H return h Otherwe chooe a random number h tore ( ID R h ) n H and return h H ( ID ID T T Z Z Z k ): mantan an ntally empty lt 3 H wth entre of the form ( ID ID T T Z Z Z3 k) If the tuple n the lt H repond wth k Otherwe repond to thee quere n the followng way: If ID = IDJ look the lt for entry ( ID ID T T ) If fnd the entry he compute Z = Z t ( T + R + H ( ID R )) ( R + H ( ID R)) Then check whether Z correct by checkng whether the oracle O ddhp output when the tuple ( R ( ) + H ID R Ppub T Z)
13 nputted alo check whether Z are equal by checkng f the equaton Z = ( t + x)( T + P) = tt hold eparately If Z Z and Z 3 are correct tore the tuple ( 3 ID ID T T Z Z Z k) nto H where the value k come from Otherwe chooe a random number tore the tuple ( ID ID T T Z Z Z3 k) nto H k {0} k and Otherwe look up the lt for entry ( ID ID T T ) If fnd the entry he tore the tuple ( ID ID T T Z Z Z3 k ) nto H where the value k come from Otherwe chooe a random number k {0} k and tore the tuple ( ID ID T T Z Z Z3 k) nto H RevealPartalPrvateKey() : anwer A quere a follow If ID = IDJ then top the mulaton Otherwe look up the lt E and return the correpondng partal prvate key to the adverary A RevealecretValue() : look up the table for entry ( ID ) If fnd the entry he return x Otherwe carre out the query reate() and return the correpondng x ReplacePublcKey( pk ): Upon recevng the query look up the table for entry ( ID ) If fnd the entry he replace x and P wth x and P eparately where pk = ( P ) and P = xp Otherwe carre out reate() and replace x and P wth x and P eparately RevealEphemeralKey( ): anwer A quere a follow If = I J then top the mulaton Otherwe return the tored ephemeral prvate key to A RevealMaterKey : top the mulaton RevealeonKey( ): anwer A quere a follow 3
14 T If = I J or = J I then top the mulaton Otherwe f return the eon key k to A end( m) t : mantan an ntally empty lt wth entre of the form ( ID ID T T k) and anwer A quere a follow t If = I J then return T = V to A Otherwe f ID = ID J he generate a random t Z n compute Z = Z t ( T + R + H ( ID R )) ( R + H ( ID R)) Then check whether Z correct by checkng whether the oracle O ddhp output when the tuple ( R ( ) + H ID R Ppub T Z ) nputted alo check whether Z are equal by checkng whether the equaton Z = ( t + x)( T + P) = tt hold eparately If Z Z are correct tore the tuple ( ID ID T T k) nto where the value k come from H Otherwe chooe a random number k {0} k and tore the tuple ( ID ID T T k) nto Otherwe reple accordng to the pecfcaton of the protocol Tet( ): anwer A quere a follow t If I J then top the mulaton Otherwe generate a random number ξ {0} k and return t to A A the adverary A mount the forgng attack f A ucceed t mut have quered oracle H on the form Z = ( t + )( T + R + H ( ID R ) P ) = ( t + )( T + U) I I J J J J pub I I J Z = ( ti + xi)( TJ + PJ) = tt I J where T I = V the outgong meage of Tet eon by the mulator and T J the ncomng meage from the adverary A To olve cdh( U V ) for all entre n H randomly chooe one entry wth the probablty n and compute Z = Z t ( T + R + H ( ID R )) ( R + H ( ID R )) J I I I I I J J J = t ( R + H ( ID R )) = cdh( U V) I J J J (6) 4
15 The advantage of olvng GDH problem wth the advantage Adv ( k) Adv ( k) GDH A (7) nnn 0 GDH Then Adv ( k) non-neglgble nce we aume that Adv ( k) A nonneglgble Th contradct the GDH aumpton AE : GDH et Adv ( k) be the advantage that the challenger get n olvng the GDH problem gven the ecurty parameter k Gven a GDH problem ntance(u = upv = vp O ddhp ) and tak to compute cdh( U V ) = uvp where O ddhp a decon oracle that on nput ( ap bp cp ) anwer f cdh( ap bp) = cp ; anwer 0 otherwe frt chooe P 0 G at random et P 0 a the ytem publc key P pub elect the ytem parameter param = { F E / F G P P H H } and end param to A Then p p pub mulate the game outlned n ecton 3 a follow Then mulate the game outlned n ecton 3 Durng the game mulate A H ( ) ID R RevealMaterKey RevealecretValue( ) ReplacePublcKey( pk ) RevealeonKey( ) and Tet( ) quere a that of AE mulate other oracle a follow reate() : mulate the oracle n the ame way a that of AE except for = I If = I chooe two random number h x Z n compute R = V hp 0 P = xp et H ( ) ID R h and tore ( ID R x P) and ( ID R h ) n and H eparately H ( ID ID T T Z Z Z h ): mulate the oracle n the ame way a 3 that of AE except for the form ( ID ID T T Z Z Z 3 ) and ( J I J I 3 I J I J ID ID T T Z Z Z ) repond to thee quere n the followng way: If ( ID ID T T Z Z Z3 h) or ( ID ID T T Z Z Z3 h) n I J I J H repond wth the tored value h J I J I Otherwe look up the table for entry ( ID ID T T ) If there no uch entry chooe a random number h {0} k and 5
16 tore the new entry ( ID ID T T Z Z Z3 h) n H Otherwe compute Z = Z t ( T + R + H( ID R )) t ( R + H( ID R )) Then check whether Z correct by checkng whether the oracle O ddhp output when the tuple ( R + H ( ID R ) P R + H ( ID R ) P Z ) pub pub nputted alo check whether Z are equal by checkng f the equaton Z = ( t + x)( T + P) = tt hold eparately If Z Z and Z 3 are correct tore the tuple ( 3 ID ID T T Z Z Z k) nto H where the value k come from Otherwe chooe a random number k {0} k and tore the tuple ( ID ID T T Z Z Z3 k) nto H RevealPartalPrvateKey() : anwer A quere a follow If = I or = J top the mulaton Otherwe look up the lt and return the correpondng partal prvate key D to the adverary A A RevealEphemeralKey( ): return the tored ephemeral prvate key to end( m) : mulate the oracle n the ame way a that of AE except for the followng quere: If = I J chooe t Z n and return T = t P to A If = I and = J (the cae that = J and = I could be deal wth mlarly) chooe t Z n and return T = t P to A look up the lt for entry ( ID ID T T ) (If H reponder eon wll look up for ( ID ID T T )) If there no uch entry chooe a random number k {0} k and tore the new entry ( ID ID T T k ) n Otherwe compute Z = Z t ( T + R + H ( ID R )) t ( R + H ( ID R )) Then check whether Z correct by checkng whether the oracle O ddhp 6
17 output when the tuple ( R + H ( ID R ) P R + H ( ID R ) P Z ) pub pub nputted alo check whether Z are equal by checkng f the equaton Z = ( t + x)( T + P) = tt hold eparately If all of the equaton are equal tore ( ID ID T T h) nto where h come from H Otherwe chooe a random number k and tore ( ID ID T T k ) nto A the adverary A mount the forgng attack f A ucceed t mut have quered oracle H on the form Z = ( t + )( T + R + H ( ID R ) P ) = ( t + )( T + U) Z = ( t + x )( T + P ) I I J J J J pub I I J I I J J and Z3 = tt I J where T I = t I P the outgong meage of Tet eon by the mulator A To olve cdh( U V ) for all entre n H randomly chooe one entry wth the probablty n and compute Z = Z ti( TJ + RJ + H( IDJ RJ)) tj( RI + H( IDI RI)) (8) = ( R + H ( ID R )) = U = cdh( U V) I J J J I We can conclude that Adv ( k) Adv ( k) GBDH A (9) nnn 0 GBDH Then Adv ( k) non-neglgble nce we aume that Adv ( k) A non-neglgble Th contradct the GDH aumpton The analy of AE : In th cae the Tet eon ha a matchng eon owned by IJ another honet party J Accordng to Defnton the adverary A ha four way to mount the attack AE The adverary A make ephemeral key query to both the Tet eon and the matchng eon of the Tet eon (The adverary doe not reveal ther correpondng partal prvate key) In th cae the proof dentcal to that of AE To ave pace we omt the detal AE The adverary A make quere to the partal prvate key of the owner of Tet eon and t peer' ephemeral prvate key In th cae the proof dentcal to that of AE To ave pace we omt the detal 7
18 AE 3 The adverary A make quere to the ephemeral prvate key of the owner of Tet eon and t peer' partal prvate key In th cae the proof dentcal to that of AE To ave pace we omt the detal AE 4 The adverary A learn the partal prvate key of both the owner of Tet eon and t peer (The adverary doe not reveal ther correpondng ephemeral prvate key) anwer H ( ) ID R ReplacePublcKey( pk ) RevealecretValue() RevealMaterKey RevealeonKey( t ) and Tet( t ) a he doe n the above cae He alo anwer other quere a follow reate() : mantan an ntally empty lt contng of tuple of the form ( ID R x P ) chooe three random number h x Z n compute R = P hp pub P = xp et H ( ) ID R h and tore ( ID R x P) and ( ID R h ) n and H eparately H ( ID ID T T Z Z Z k ): mantan an ntally empty lt 3 H wth entre of the form ( ID ID T T Z Z Z3 k) If the tuple n the lt H repond wth k Otherwe repond to thee quere n the followng way: look the lt for entry ( ID ID T T ) If fnd the entry he compute and Z = Z ( T + R + H ( ID R )) T (0) Z = Z () Z = Z x ( T + P ) x T () Then check whether Z correct by checkng whether the oracle O output when the tuple ( T T Z ) nputted where = 3 If ddhp Z Z are correct tore the tuple ( 3 ID ID T T Z Z Z k) nto H where the value k come from Otherwe chooe a random number k {0} k and tore the tuple ( ID ID T T Z Z Z3 k) nto H 8
19 Otherwe chooe a random number k {0} k and tore the tuple ( ID ID T T Z Z Z3 k) nto H RevealPartalPrvateKey() : look up the lt and return the correpondng partal prvate key to the adverary A RevealEphemeralKey( ): anwer A quere a follow T If = or = then top the mulaton I J J I Otherwe return the tored ephemeral prvate key to A end( m) : mantan an ntally empty lt wth entre of the form ( ID ID T T k) and anwer A quere a follow T If = I J return T = U to A T Otherwe f = I J return T = V to A Otherwe reple accordng to the pecfcaton of the protocol A the attack that adverary A mount the forgng attack f A ucceed t mut have quered oracle H on the form Z = ( t + )( T + R + H ( ID R ) P ) Z = ( t + x )( T + P ) and Z I I J J J J pub = tt where T I 3 I J I I J J = U the outgong meage of Tet eon by the mulator and T J = V the ncomng meage from the adverary A To olve cdh( U V ) for all entre n H randomly chooe one entry wth the probablty n and return Z 3 a the oluton to cdh( U V ) The advantage of olvng GDH problem wth the advantage Adv ( k) Adv ( k) GDH A () nnn 0 GDH Then Adv ( k) non-neglgble nce we aume that Adv ( k) A nonneglgble Th contradct the GDH aumpton We could conclude that the advantage of a type adverary agant our protocol neglgble f the GDH problem ntractable emma Aumng that the GDH problem ntractable the advantage of a type adverary agant our protocol neglgble 9
20 Proof uppoe that there a type adverary A who can wn the game defned n ubecton 3 wth a non-neglgble advantage Adv ( k) A n polynomal-tme t Then we wll how how to ue the ablty of A to contruct an algorthm to olve the GDH problem et n 0 be the maxmum number of eon that any one party may have Aume that the adverary A actvate at mot n dtnctve honet parte Aume that the adverary A actvate at mot n dtnctve hah quere Aume alo that Adv ( k) A non-neglgble Before the game tart tre to gue the tet eon and the trategy that the adverary A wll adopt randomly elect two ndexe I J { n} : I J whch repreent the I th and the J th dtnct honet party that the adverary ntally chooe Alo chooe { n0} and determne the Tet eon IJ whch correct wth probablty larger than nn et T J I be the matchng eon of IJ 0 nce H and H are modeled a random oracle after the adverary ue the tet query t ha only three poble way to dtnguh the teted eon key from a random trng: AE : Forgng attack: Aume that the tet eon At ome pont n t run the adverary A quere H on the 3 value ( ID ID T T K K K ) n the tet eon owned by I I J I J IJ IJ IJ IJ communcatng wth J learly n th cae A compute the value K IJ K IJ and K 3 IJ telf AE : Gueng attack: A correctly guee the eon key AE 3: Key-replcaton attack: The adverary A force a nonmatchng eon to have the ame eon key wth the tet eon In th cae the adverary A can mply learn the eon key by queryng the nonmatchng eon Through the ame analy we know the ucce probablty of Keyreplcaton attack and Gueng attack alo neglgble Thu Gueng attack and Key-replcaton attack can be ruled out A the attack that the adverary 0
21 A mount Forgng attack A can not get an advantage n wnnng the game agant the protocol unle t quere the H oracle on the eon key In the followng a challenger ntereted to ue the adverary A to turn A advantage n dtnguhng the teted eon key from a random trng nto an advantage n olvng the GDH problem The followng two ubcae hould be condered AE : No honet party own a matchng eon to the Tet eon AE : The Tet eon ha a matchng eon owned by another honet party The analy of AE : nce A trong type adverary then he can get any uer partal prvate key nce he a malcou KG Accordng to Defnton ha the followng two choce for A trategy: AE : At ome pont the ecret value of party I ha been revealed by the adverary A Accordng to Defnton A not permtted to reveal the ephemeral prvate key of the Tet eon AE : The ecret value of party I ha never been revealed by the adverary A Accordng to Defnton A may reveal the ephemeral prvate key of the Tet eon AE : GDH et Adv ( k) be the advantage that the challenger get n olvng the GDH problem gven the ecurty parameter k Gven a GDH problem ntance (U = upv = vp O ddhp ) and tak to compute cdh( U V ) = uvp where O ddhp a decon oracle that on nput ( ap bp cp ) anwer f cdh( ap bp) = cp ; anwer 0 otherwe frt chooe a random number x Z n et xp a the ytem publc key P pub elect the ytem parameter param = { F E / F G P P H H } and end param to A Then p p pub mulate the game outlned n ecton 3 a follow reate() : mantan an ntally empty lt contng of tuple of the form ( ID R x P) If = J chooe two random number r Z n compute R = rp h ( ) = H ID R = r + hx P = U and tore ( ID R P)n Otherwe chooe two random number r x Z n
22 compute R = rp h ( ) = H ID R = r + hx P = xp and tore ( ID R x P) n H ( ) ID R : mantan an ntally empty lt H whch contan tuple of the form ( ID R h ) If ( ID R ) on the lt H return h Otherwe chooe a random number h tore ( ID R h ) n H and return h H ( ID ID T T Z Z Z k ): mantan an ntally empty lt 3 H wth entre of the form ( ID ID T T Z Z Z3 k) If the tuple n the lt H repond wth k Otherwe repond to thee quere n the followng way: If ID = IDJ look the lt for entry ( ID ID T T ) If fnd the entry he compute Z = Z t ( T + P ) x P Then check whether Z correct by checkng whether the oracle O output when the tuple ( PT Z ) nputted ddhp alo check whether Z are equal by checkng whether the equaton Z = ( t + )( T + R + H( ID R)) and Z3 = tt hold eparately If Z Z are correct tore the tuple ( 3 ID ID T T Z Z Z k) nto H where the value k come from Otherwe Otherwe chooe a random number tore the tuple ( ID ID T T Z Z Z3 k) nto H k {0} k and look the lt for entry ( ID ID T T ) If fnd the entry he tore the tuple ( ID ID T T Z Z Z3 k ) nto H where the value k come from Otherwe chooe a random number k {0} k and tore the tuple ( ID ID T T Z Z Z3 k) nto H RevealPartalPrvateKey() : look up the lt correpondng partal prvate key to the adverary A E and return the
23 RevealecretValue() : anwer A quere a follow If ID = IDJ then top the mulaton Otherwe look up the table for entry ( ID ) and return x RevealEphemeralKey( ): anwer A quere a follow t If = then top the mulaton I J Otherwe return the tored ephemeral prvate key to A RevealMaterKey : return the mater key x to A RevealeonKey( ): anwer A quere a follow t T If = or = then top the mulaton I J Otherwe f return the eon key k to A end( ) m : mantan an ntally empty lt form ( ID ID T T k) and anwer A quere a follow If = I J then return T I J = V to A wth entre of the Otherwe f ID = ID J he generate a random t Z n compute Z = Z t ( T + P ) x P Then check whether Z correct by checkng whether the oracle O output when the tuple ( PT Z ) ddhp nputted alo check whether Z are equal by checkng whether the equaton Z = ( t + )( T + R + H ( ID R)) = tt hold eparately If Z Z are correct tore the tuple ( ID ID T T k ) nto where the value k come from H Otherwe chooe a random number k {0} k and tore the tuple ( ID ID T T k) nto Otherwe reple accordng to the pecfcaton of the protocol Tet( ): anwer A quere a follow t t If then top the mulaton I J Otherwe generate a random number ξ {0} k and return t to A 3
24 A the adverary A mount the forgng attack f A ucceed t mut have quered oracle H on the form Z = ( t + )( T + R + H( ID R ) P ) Z = ( ti + xi)( TJ + U) = tt I J where TI Tet eon by the mulator and I I J J J J pub = V the outgong meage of T J the ncomng meage from the adverary A To olve GDHUV ( ) for all entre n H randomly chooe one entry wth the probablty n and compute Z = Z x ( T + U)) Z (3) I J 3 It eay to verfy that the equaton Z = cdh( U V ) hold The advantage of olvng GDH problem wth the advantage Adv ( k) Adv ( k) GDH A (4) nnn 0 GDH Then Adv ( k) non-neglgble nce we aume that Adv ( k) A nonneglgble Th contradct the GDH aumpton AE : anwer H ( ID R ) RevealPartalPrvateKey( ) t RevealEphemeralKey( ) RevealMaterKey RevealeonKey( t ) and Tet( ) a he doe n AE 33 of emma 3 He alo anwer other quere t a follow reate() : mulate the oracle n the ame way a that of AE except for = I If = I chooe two random number r Z n compute R = rp h ( ) = H ID R = r + hx P = V and tore ( ID R P)n Otherwe chooe two random number r x Z n compute R = rp h ( ) = H ID R = r + hx P = xp and tore ( ID R x P) n H ( ID ID T T Z Z Z h ): mulate the oracle n the ame way a 3 that of AE except for the form ( ID ID T T Z Z Z 3) and ( J I J I 3 I J I J ID ID T T Z Z Z ) repond to thee quere n the followng way: 4
25 If ( ID ID T T Z Z Z3 h) or ( ID ID T T Z Z Z3 h) n I J I J H repond wth the tored value h J I J I Otherwe look up the table for entry ( ID ID T T ) If there no uch entry chooe a random number h {0} k and tore the new entry ( ID ID T T Z Z Z3 h) n H Otherwe compute Z = Z t ( T + P ) t P Then check whether Z correct by checkng whether the oracle ( O ddhp output when the tuple P P Z ) nputted alo check whether Z are equal by checkng f the equaton Z = ( t + )( T + R + H ( ID R ) P ) and Z 3 pub = tt hold eparately If Z Z are correct tore the tuple ( ID ID T T Z Z Z3 k) nto H where the value k come from Otherwe chooe a random number tore the tuple ( ID ID T T Z Z Z3 k) nto H k {0} k and RevealecretValue() : : mulate the oracle n the ame way a that of AE except for = I If = I top the mulaton end( m) : mulate the oracle n the ame way a that of AE except for the followng quere: If = I J chooe t Z n and return T = t P to A If = I and = J (the cae that = J and = I could be deal wth mlarly) chooe t Z n and return T = t P to A look up the lt for entry ( ID ID T T ) (If H reponder eon wll look up for ( ID ID T T )) If there no uch entry chooe a random number k {0} k and tore the new entry ( ID ID T T k ) n Otherwe compute Z = Z t ( T + P ) t P Then check whether Z correct by checkng whether the oracle O output when the tuple ( P P Z ) ddhp nputted alo check whether Z are equal by checkng f 5
26 the equaton Z = ( t + )( T + R + H( ID R ) Ppub) = tt hold eparately If all of the equaton are equal tore ( ID ID T T h) nto where h come from H Otherwe chooe a random number k and tore ( ID ID T T k ) nto A the adverary A mount the forgng attack f A ucceed t mut have quered oracle H on the form Z = ( t + )( T + R + H( ID R ) P ) Z = ( ti + xi)( TJ + U) = tt I J where PI I I J J J J pub = U PJ = V and T J the ncomng meage from the adverary A To olve GDHUV ( ) for all entre n H randomly chooe one entry wth the probablty wth followng tep: compute n and proceed Z = Z t ( T + U) t V = cdh( U V) (5) I J J The advantage of olvng GDH problem wth the advantage Adv ( k) Adv ( k) GDH A nnn 0 GDH Then Adv ( k) non-neglgble nce we aume that Adv ( k) A nonneglgble Th contradct the GDH aumpton The analy of AE : In th cae the Tet eon ha a matchng eon owned by IJ another honet party J Accordng to Defnton the adverary A ha four way to mount the attack AE The adverary A make ephemeral key query to both the Tet eon and the matchng eon of the Tet eon (The adverary doe not reveal ther correpondng partal prvate key) In th cae the proof dentcal to that of AE To ave pace we omt the detal AE The adverary A make quere to the partal prvate key of the owner of Tet eon and t peer' ephemeral prvate key In th cae the proof dentcal to that of AE To ave pace we omt the detal AE 3 The adverary A make quere to the ephemeral prvate key of the owner of Tet eon and t peer' partal prvate key In th cae the proof dentcal to that of AE To ave pace we omt the detal 6
27 AE 4 The adverary A learn the partal prvate key of both the owner of Tet eon and t peer (The adverary doe not reveal ther correpondng ephemeral prvate key) In th cae the proof dentcal to that of AE 4 of the above lemma To ave pace we omt the detal We could conclude that the advantage of a type adverary agant our protocol neglgble f the GDH problem ntractable From the above three lemma we can get the followng theorem Theorem Our protocol a ecure AKA protocol n the ek model under the GDH aumpton 5 omparon wth prevou protocol et mbr and ek denote the modfed Bellare-Rogaway model [7] and the extended anett Krawczyk (ek) model [8] eparately For the convenence of evaluatng the computatonal cot we defne ome notaton a follow T mul T add T nv : The tme of executng a calar multplcaton operaton of pont : The tme of executng an addton operaton of pont : The tme of executng a modular nvaon operaton T h : The tme of executng a one-way hah functon We wll compare the effcency of our protocol wth fve AKA protocol wthout parng e Geng et al protocol [] Hou et al protocol [3] Yang et al protocol[4] and He et al protocol[56] Table how the comparon between parng-free AKA protocol n term of effcency ecurty model and underlyng hardne aumpton nce the calar multplcaton operaton of pont more complcated than the addton operaton of pont modular nvaon operaton and the hah functon operaton then our protocol ha better performance than Geng et al protocol [] Hou et al protocol [3] and He et al protocol[5] Moreover Geng et al protocol [] Hou et al protocol [3] and He et al protocol[5] are not ecure agant type adverary Then our protocol ha advantage n both the performance and the ecurty over Geng et al protocol [] Hou et al protocol [3] and He et al protocol [5] It well known that the ek model much uperor to the mbr model Then Yang et al protocol [5] and our protocol ha advantage n ecurty to He et al protocol [6] At the ame tme 7
28 our protocol alo ha better performance than He et al protocol [6] Yang et al propoed the frt parng-free AKA protocol whch provably ecure n the ek model However n Yang et al protocol the uer ha to verfy the valdty of publc key Th doe not only ncreae the burden of the uer but alo revere the thought of PK From Table we know our protocol ha much better performance than Yang et al protocol [5] We conclude that our protocol more utable for practcal applcaton Table : omparon among dfferent protocol omputatonal ecurty Aumpton Meage cot model exchange Geng et al protocol [] Hou et al protocol [3] Yang et al protocol [4] He et al protocol[5] 7T + T mbr GDH mul h 6T + T mbr GDH mul h 9T + T ek GDH mul 5T + 3T mul + T + T nv h add h mbr GDH 3 He et al protocol[6] 5T + 4T mul + T h add mbr GDH Our protocol 5T + 3T mul + T h add ek GDH 6 oncluon The certfcatele publc key cryptography recevng gnfcant attenton becaue t a new paradgm that mplfe the publc key cryptography Recently everal parng-free AKA have been propoed In th paper we propoed a more effcent AKA protocol wthout parng and proved t ecurty n the ek model under the GDH aumpton The propoed protocol ha the bet performance among the related protocol Acknowledgement The author thank Prof Ervn Y Rodn and the anonymou revewer for ther valuable comment Th reearch wa upported by the Fundamental Reearch 8
29 Fund for the entral Unverte and the pecalzed Reearch Fund for the Doctoral Program of Hgher Educaton of hna (Grant No ) Reference [] KY ho JH Park DH ee A new provably ecure certfcatele hort gnature cheme omputer and Mathematc wth Applcaton 6(7)(0) [] A hamr Identty-baed cryptoytem and gnature protocol Proc RYPTO984 N vol pp47 53 [3] Al-Ryam KG Pateron ertfcatele publc key cryptography Proceedng of AIARYPT 003 N 894 prnger-verlag 003 pp [4] Z hao Effcent authentcated key agreement protocol ung elf-certfed publc key from parng Wuhan Unverty Journal of Natural cence 0() (005) [5] Wang Z ao X Dong ertfcatele authentcated key agreement baed on the MTI/O protocol Journal of Informaton and omputatonal cence 3 (006) [6] T Mandt Tan ertfcatele authentcated two-party key agreement protocol n: Proceedng of the AIAN 006 N vol 4435 prnger-verlag 008 pp [7] Y h J Two-party authentcated key agreement n certfcatele publc key cryptography Wuhan Unverty Journal of Natural cence () (007) 7 74 [8] wanon ecurty n key agreement: Two-party certfcatele protocol Mater The Unverty of Waterloo 008 [9] G ppold Boyd J Neto trongly ecure certfcatele key agreement In Parng pp [0] Zhang F Zhang Q Wua J Domngo-Ferrer mulatable certfcatele two-party authentcated key agreement protocol Informaton cence 80 (00) [] hen Z heng and NP mart Identty-baed key agreement protocol from parng Internatonal Journal Informaton ecurty 6 (007) 3 4 [] M Geng and F Zhang Provably ecure certfcatele two-party authentcated key agreement protocol wthout parng In Internatonal onference on omputatonal Intellgence and ecurty 009 pp 08- [3] M Hou and Q Xu A two-party certfcatele authentcated key agreement protocol wthout parng In nd IEEE Internatonal onference on omputer cence and Informaton Technology 009 pp 4-46 [4] G Yang Tan trongly ecure certfcatele key exchange wthout parng 6th AM ympoum on Informaton omputer and ommuncaton ecurty 0 pp 7-79 [5] D He J hen J Hu A parng-free certfcatele authentcated key agreement protocol Internatonal Journal of ommuncaton ytem (In pre) DOI: 000/dac65 0 [6] D He Y hen J hen R Zhang W Han A new two-round certfcatele authentcated key agreement protocol wthout blnear parng Mathematcal and omputer Modellng (0) do:006/mcm
30 [7] M Bellare P Rogaway Entty authentcaton and key dtrbuton In: Proceedng of the RYPTO 993 N vol 773 prnger-verlag; 993 p 3 49 [8] B amaccha K auter A Mtyagn tronger ecurty of authentcated key exchange In: Proceedng of the Provecton 007 N vol 4784 prnger-verlag; 007 p 6 [9] M Bellare and P Rogaway Random oracle are practcal: A paradgm for degnng effcent protocol n Proc t AM onf omput ommun ecurty 993 pp
Cryptanalysis of pairing-free certificateless authenticated key agreement protocol
 Cryptanalyss of parng-free certfcateless authentcated key agreement protocol Zhan Zhu Chna Shp Development Desgn Center CSDDC Wuhan Chna Emal: zhuzhan0@gmal.com bstract: Recently He et al. [D. He J. Chen
Cryptanalyss of parng-free certfcateless authentcated key agreement protocol Zhan Zhu Chna Shp Development Desgn Center CSDDC Wuhan Chna Emal: zhuzhan0@gmal.com bstract: Recently He et al. [D. He J. Chen
Improvements on Waring s Problem
 Improvement on Warng Problem L An-Png Bejng, PR Chna apl@nacom Abtract By a new recurve algorthm for the auxlary equaton, n th paper, we wll gve ome mprovement for Warng problem Keyword: Warng Problem,
Improvement on Warng Problem L An-Png Bejng, PR Chna apl@nacom Abtract By a new recurve algorthm for the auxlary equaton, n th paper, we wll gve ome mprovement for Warng problem Keyword: Warng Problem,
Additional File 1 - Detailed explanation of the expression level CPD
 Addtonal Fle - Detaled explanaton of the expreon level CPD A mentoned n the man text, the man CPD for the uterng model cont of two ndvdual factor: P( level gen P( level gen P ( level gen 2 (.).. CPD factor
Addtonal Fle - Detaled explanaton of the expreon level CPD A mentoned n the man text, the man CPD for the uterng model cont of two ndvdual factor: P( level gen P( level gen P ( level gen 2 (.).. CPD factor
Specification -- Assumptions of the Simple Classical Linear Regression Model (CLRM) 1. Introduction
 ECONOMICS 35* -- NOTE ECON 35* -- NOTE Specfcaton -- Aumpton of the Smple Clacal Lnear Regreon Model (CLRM). Introducton CLRM tand for the Clacal Lnear Regreon Model. The CLRM alo known a the tandard lnear
ECONOMICS 35* -- NOTE ECON 35* -- NOTE Specfcaton -- Aumpton of the Smple Clacal Lnear Regreon Model (CLRM). Introducton CLRM tand for the Clacal Lnear Regreon Model. The CLRM alo known a the tandard lnear
Comments on a secure dynamic ID-based remote user authentication scheme for multiserver environment using smart cards
 Comments on a secure dynamc ID-based remote user authentcaton scheme for multserver envronment usng smart cards Debao He chool of Mathematcs tatstcs Wuhan nversty Wuhan People s Republc of Chna Emal: hedebao@63com
Comments on a secure dynamc ID-based remote user authentcaton scheme for multserver envronment usng smart cards Debao He chool of Mathematcs tatstcs Wuhan nversty Wuhan People s Republc of Chna Emal: hedebao@63com
Harmonic oscillator approximation
 armonc ocllator approxmaton armonc ocllator approxmaton Euaton to be olved We are fndng a mnmum of the functon under the retrcton where W P, P,..., P, Q, Q,..., Q P, P,..., P, Q, Q,..., Q lnwgner functon
armonc ocllator approxmaton armonc ocllator approxmaton Euaton to be olved We are fndng a mnmum of the functon under the retrcton where W P, P,..., P, Q, Q,..., Q P, P,..., P, Q, Q,..., Q lnwgner functon
Efficient and Secure ECC-based Electronic Cash Payment Applications for Internet Consumers
 Int'l onf. Internet omputng and Internet of hng IOMP'17 25 Effcent and ecure E-baed Electronc ah Payment Applcaton for Internet onumer Woe-Junn aur 1 Lo-ao eh 2 and ong-ng Juang 3 1 omputer enter Natonal
Int'l onf. Internet omputng and Internet of hng IOMP'17 25 Effcent and ecure E-baed Electronc ah Payment Applcaton for Internet onumer Woe-Junn aur 1 Lo-ao eh 2 and ong-ng Juang 3 1 omputer enter Natonal
a new crytoytem baed on the dea of Shmuley and roved t rovably ecure baed on ntractablty of factorng [Mc88] After that n 999 El Bham, Dan Boneh and Om
![a new crytoytem baed on the dea of Shmuley and roved t rovably ecure baed on ntractablty of factorng [Mc88] After that n 999 El Bham, Dan Boneh and Om a new crytoytem baed on the dea of Shmuley and roved t rovably ecure baed on ntractablty of factorng [Mc88] After that n 999 El Bham, Dan Boneh and Om](/thumbs/87/96774651.jpg) Weak Comote Dffe-Hellman not Weaker than Factorng Koohar Azman, azman@ceharfedu Javad Mohajer mohajer@harfedu Mahmoud Salmazadeh alma@harfedu Electronc Reearch Centre, Sharf Unverty of Technology Deartment
Weak Comote Dffe-Hellman not Weaker than Factorng Koohar Azman, azman@ceharfedu Javad Mohajer mohajer@harfedu Mahmoud Salmazadeh alma@harfedu Electronc Reearch Centre, Sharf Unverty of Technology Deartment
An Improved Remote User Authentication Scheme with Elliptic Curve Cryptography and Smart Card without using Bilinear Pairings
 SRameh etal / Internatonal Journal of Engneerng and Technology (IJET) n Improved Remote er uthentcaton Scheme wth Ellptc Curve Cryptography and Smart Card wthout ung Blnear Parng SRameh #1, DrVMural Bhakaran
SRameh etal / Internatonal Journal of Engneerng and Technology (IJET) n Improved Remote er uthentcaton Scheme wth Ellptc Curve Cryptography and Smart Card wthout ung Blnear Parng SRameh #1, DrVMural Bhakaran
and decompose in cycles of length two
 Permutaton of Proceedng of the Natona Conference On Undergraduate Reearch (NCUR) 006 Domncan Unverty of Caforna San Rafae, Caforna Apr - 4, 007 that are gven by bnoma and decompoe n cyce of ength two Yeena
Permutaton of Proceedng of the Natona Conference On Undergraduate Reearch (NCUR) 006 Domncan Unverty of Caforna San Rafae, Caforna Apr - 4, 007 that are gven by bnoma and decompoe n cyce of ength two Yeena
Scattering of two identical particles in the center-of. of-mass frame. (b)
 Lecture # November 5 Scatterng of two dentcal partcle Relatvtc Quantum Mechanc: The Klen-Gordon equaton Interpretaton of the Klen-Gordon equaton The Drac equaton Drac repreentaton for the matrce α and
Lecture # November 5 Scatterng of two dentcal partcle Relatvtc Quantum Mechanc: The Klen-Gordon equaton Interpretaton of the Klen-Gordon equaton The Drac equaton Drac repreentaton for the matrce α and
Method Of Fundamental Solutions For Modeling Electromagnetic Wave Scattering Problems
 Internatonal Workhop on MehFree Method 003 1 Method Of Fundamental Soluton For Modelng lectromagnetc Wave Scatterng Problem Der-Lang Young (1) and Jhh-We Ruan (1) Abtract: In th paper we attempt to contruct
Internatonal Workhop on MehFree Method 003 1 Method Of Fundamental Soluton For Modelng lectromagnetc Wave Scatterng Problem Der-Lang Young (1) and Jhh-We Ruan (1) Abtract: In th paper we attempt to contruct
Improvements on Waring s Problem
 Imrovement on Warng Problem L An-Png Bejng 85, PR Chna al@nacom Abtract By a new recurve algorthm for the auxlary equaton, n th aer, we wll gve ome mrovement for Warng roblem Keyword: Warng Problem, Hardy-Lttlewood
Imrovement on Warng Problem L An-Png Bejng 85, PR Chna al@nacom Abtract By a new recurve algorthm for the auxlary equaton, n th aer, we wll gve ome mrovement for Warng roblem Keyword: Warng Problem, Hardy-Lttlewood
Start Point and Trajectory Analysis for the Minimal Time System Design Algorithm
 Start Pont and Trajectory Analy for the Mnmal Tme Sytem Degn Algorthm ALEXANDER ZEMLIAK, PEDRO MIRANDA Department of Phyc and Mathematc Puebla Autonomou Unverty Av San Claudo /n, Puebla, 757 MEXICO Abtract:
Start Pont and Trajectory Analy for the Mnmal Tme Sytem Degn Algorthm ALEXANDER ZEMLIAK, PEDRO MIRANDA Department of Phyc and Mathematc Puebla Autonomou Unverty Av San Claudo /n, Puebla, 757 MEXICO Abtract:
MULTIPLE REGRESSION ANALYSIS For the Case of Two Regressors
 MULTIPLE REGRESSION ANALYSIS For the Cae of Two Regreor In the followng note, leat-quare etmaton developed for multple regreon problem wth two eplanator varable, here called regreor (uch a n the Fat Food
MULTIPLE REGRESSION ANALYSIS For the Cae of Two Regreor In the followng note, leat-quare etmaton developed for multple regreon problem wth two eplanator varable, here called regreor (uch a n the Fat Food
Team. Outline. Statistics and Art: Sampling, Response Error, Mixed Models, Missing Data, and Inference
 Team Stattc and Art: Samplng, Repone Error, Mxed Model, Mng Data, and nference Ed Stanek Unverty of Maachuett- Amhert, USA 9/5/8 9/5/8 Outlne. Example: Doe-repone Model n Toxcology. ow to Predct Realzed
Team Stattc and Art: Samplng, Repone Error, Mxed Model, Mng Data, and nference Ed Stanek Unverty of Maachuett- Amhert, USA 9/5/8 9/5/8 Outlne. Example: Doe-repone Model n Toxcology. ow to Predct Realzed
Root Locus Techniques
 Root Locu Technque ELEC 32 Cloed-Loop Control The control nput u t ynthezed baed on the a pror knowledge of the ytem plant, the reference nput r t, and the error gnal, e t The control ytem meaure the output,
Root Locu Technque ELEC 32 Cloed-Loop Control The control nput u t ynthezed baed on the a pror knowledge of the ytem plant, the reference nput r t, and the error gnal, e t The control ytem meaure the output,
Chapter 6 The Effect of the GPS Systematic Errors on Deformation Parameters
 Chapter 6 The Effect of the GPS Sytematc Error on Deformaton Parameter 6.. General Beutler et al., (988) dd the frt comprehenve tudy on the GPS ytematc error. Baed on a geometrc approach and aumng a unform
Chapter 6 The Effect of the GPS Sytematc Error on Deformaton Parameter 6.. General Beutler et al., (988) dd the frt comprehenve tudy on the GPS ytematc error. Baed on a geometrc approach and aumng a unform
On the SO 2 Problem in Thermal Power Plants. 2.Two-steps chemical absorption modeling
 Internatonal Journal of Engneerng Reearch ISSN:39-689)(onlne),347-53(prnt) Volume No4, Iue No, pp : 557-56 Oct 5 On the SO Problem n Thermal Power Plant Two-tep chemcal aborpton modelng hr Boyadjev, P
Internatonal Journal of Engneerng Reearch ISSN:39-689)(onlne),347-53(prnt) Volume No4, Iue No, pp : 557-56 Oct 5 On the SO Problem n Thermal Power Plant Two-tep chemcal aborpton modelng hr Boyadjev, P
Small signal analysis
 Small gnal analy. ntroducton Let u conder the crcut hown n Fg., where the nonlnear retor decrbed by the equaton g v havng graphcal repreentaton hown n Fg.. ( G (t G v(t v Fg. Fg. a D current ource wherea
Small gnal analy. ntroducton Let u conder the crcut hown n Fg., where the nonlnear retor decrbed by the equaton g v havng graphcal repreentaton hown n Fg.. ( G (t G v(t v Fg. Fg. a D current ource wherea
Confidence intervals for the difference and the ratio of Lognormal means with bounded parameters
 Songklanakarn J. Sc. Technol. 37 () 3-40 Mar.-Apr. 05 http://www.jt.pu.ac.th Orgnal Artcle Confdence nterval for the dfference and the rato of Lognormal mean wth bounded parameter Sa-aat Nwtpong* Department
Songklanakarn J. Sc. Technol. 37 () 3-40 Mar.-Apr. 05 http://www.jt.pu.ac.th Orgnal Artcle Confdence nterval for the dfference and the rato of Lognormal mean wth bounded parameter Sa-aat Nwtpong* Department
Chapter 11. Supplemental Text Material. The method of steepest ascent can be derived as follows. Suppose that we have fit a firstorder
 S-. The Method of Steepet cent Chapter. Supplemental Text Materal The method of teepet acent can be derved a follow. Suppoe that we have ft a frtorder model y = β + β x and we wh to ue th model to determne
S-. The Method of Steepet cent Chapter. Supplemental Text Materal The method of teepet acent can be derved a follow. Suppoe that we have ft a frtorder model y = β + β x and we wh to ue th model to determne
A Model of Bilinear-Pairings Based Designated-Verifier Proxy Signatue Scheme*
 A Model of Blnear-Parngs Based Desgnated-Verfer Proxy Sgnatue Scheme Fengyng L,, Qngshu Xue, Jpng Zhang, Zhenfu Cao Department of Educaton Informaton Technology, East Chna Normal Unversty, 0006, Shangha,
A Model of Blnear-Parngs Based Desgnated-Verfer Proxy Sgnatue Scheme Fengyng L,, Qngshu Xue, Jpng Zhang, Zhenfu Cao Department of Educaton Informaton Technology, East Chna Normal Unversty, 0006, Shangha,
The Order Relation and Trace Inequalities for. Hermitian Operators
 Internatonal Mathematcal Forum, Vol 3, 08, no, 507-57 HIKARI Ltd, wwwm-hkarcom https://doorg/0988/mf088055 The Order Relaton and Trace Inequaltes for Hermtan Operators Y Huang School of Informaton Scence
Internatonal Mathematcal Forum, Vol 3, 08, no, 507-57 HIKARI Ltd, wwwm-hkarcom https://doorg/0988/mf088055 The Order Relaton and Trace Inequaltes for Hermtan Operators Y Huang School of Informaton Scence
ENTROPY BOUNDS USING ARITHMETIC- GEOMETRIC-HARMONIC MEAN INEQUALITY. Guru Nanak Dev University Amritsar, , INDIA
 Internatonal Journal of Pure and Appled Mathematc Volume 89 No. 5 2013, 719-730 ISSN: 1311-8080 prnted veron; ISSN: 1314-3395 on-lne veron url: http://.jpam.eu do: http://dx.do.org/10.12732/jpam.v895.8
Internatonal Journal of Pure and Appled Mathematc Volume 89 No. 5 2013, 719-730 ISSN: 1311-8080 prnted veron; ISSN: 1314-3395 on-lne veron url: http://.jpam.eu do: http://dx.do.org/10.12732/jpam.v895.8
Provable Security Signatures
 Provable Securty Sgnatures UCL - Louvan-la-Neuve Wednesday, July 10th, 2002 LIENS-CNRS Ecole normale supéreure Summary Introducton Sgnature FD PSS Forkng Lemma Generc Model Concluson Provable Securty -
Provable Securty Sgnatures UCL - Louvan-la-Neuve Wednesday, July 10th, 2002 LIENS-CNRS Ecole normale supéreure Summary Introducton Sgnature FD PSS Forkng Lemma Generc Model Concluson Provable Securty -
Hash functions : MAC / HMAC
 Hash functons : MAC / HMAC Outlne Message Authentcaton Codes Keyed hash famly Uncondtonally Secure MACs Ref: D Stnson: Cryprography Theory and Practce (3 rd ed), Chap 4. Unversal hash famly Notatons: X
Hash functons : MAC / HMAC Outlne Message Authentcaton Codes Keyed hash famly Uncondtonally Secure MACs Ref: D Stnson: Cryprography Theory and Practce (3 rd ed), Chap 4. Unversal hash famly Notatons: X
Variable Structure Control ~ Basics
 Varable Structure Control ~ Bac Harry G. Kwatny Department of Mechancal Engneerng & Mechanc Drexel Unverty Outlne A prelmnary example VS ytem, ldng mode, reachng Bac of dcontnuou ytem Example: underea
Varable Structure Control ~ Bac Harry G. Kwatny Department of Mechancal Engneerng & Mechanc Drexel Unverty Outlne A prelmnary example VS ytem, ldng mode, reachng Bac of dcontnuou ytem Example: underea
Separation Axioms of Fuzzy Bitopological Spaces
 IJCSNS Internatonal Journal of Computer Scence and Network Securty VOL3 No October 3 Separaton Axom of Fuzzy Btopologcal Space Hong Wang College of Scence Southwet Unverty of Scence and Technology Manyang
IJCSNS Internatonal Journal of Computer Scence and Network Securty VOL3 No October 3 Separaton Axom of Fuzzy Btopologcal Space Hong Wang College of Scence Southwet Unverty of Scence and Technology Manyang
NUMERICAL DIFFERENTIATION
 NUMERICAL DIFFERENTIATION 1 Introducton Dfferentaton s a method to compute the rate at whch a dependent output y changes wth respect to the change n the ndependent nput x. Ths rate of change s called the
NUMERICAL DIFFERENTIATION 1 Introducton Dfferentaton s a method to compute the rate at whch a dependent output y changes wth respect to the change n the ndependent nput x. Ths rate of change s called the
Speeding up Computation of Scalar Multiplication in Elliptic Curve Cryptosystem
 H.K. Pathak et. al. / (IJCSE) Internatonal Journal on Computer Scence and Engneerng Speedng up Computaton of Scalar Multplcaton n Ellptc Curve Cryptosystem H. K. Pathak Manju Sangh S.o.S n Computer scence
H.K. Pathak et. al. / (IJCSE) Internatonal Journal on Computer Scence and Engneerng Speedng up Computaton of Scalar Multplcaton n Ellptc Curve Cryptosystem H. K. Pathak Manju Sangh S.o.S n Computer scence
On the U-WPF Acts over Monoids
 Journal of cence, Ilamc Republc of Iran 8(4): 33-38 (007) Unverty of Tehran, IN 06-04 http://jcence.ut.ac.r On the U-WPF ct over Monod. Golchn * and H. Mohammadzadeh Department of Mathematc, Unverty of
Journal of cence, Ilamc Republc of Iran 8(4): 33-38 (007) Unverty of Tehran, IN 06-04 http://jcence.ut.ac.r On the U-WPF ct over Monod. Golchn * and H. Mohammadzadeh Department of Mathematc, Unverty of
6.842 Randomness and Computation February 18, Lecture 4
 6.842 Randomness and Computaton February 18, 2014 Lecture 4 Lecturer: Rontt Rubnfeld Scrbe: Amartya Shankha Bswas Topcs 2-Pont Samplng Interactve Proofs Publc cons vs Prvate cons 1 Two Pont Samplng 1.1
6.842 Randomness and Computaton February 18, 2014 Lecture 4 Lecturer: Rontt Rubnfeld Scrbe: Amartya Shankha Bswas Topcs 2-Pont Samplng Interactve Proofs Publc cons vs Prvate cons 1 Two Pont Samplng 1.1
728. Mechanical and electrical elements in reduction of vibrations
 78. Mechancal and electrcal element n reducton of vbraton Katarzyna BIAŁAS The Slean Unverty of Technology, Faculty of Mechancal Engneerng Inttute of Engneerng Procee Automaton and Integrated Manufacturng
78. Mechancal and electrcal element n reducton of vbraton Katarzyna BIAŁAS The Slean Unverty of Technology, Faculty of Mechancal Engneerng Inttute of Engneerng Procee Automaton and Integrated Manufacturng
Introduction to Interfacial Segregation. Xiaozhe Zhang 10/02/2015
 Introducton to Interfacal Segregaton Xaozhe Zhang 10/02/2015 Interfacal egregaton Segregaton n materal refer to the enrchment of a materal conttuent at a free urface or an nternal nterface of a materal.
Introducton to Interfacal Segregaton Xaozhe Zhang 10/02/2015 Interfacal egregaton Segregaton n materal refer to the enrchment of a materal conttuent at a free urface or an nternal nterface of a materal.
Calculation of time complexity (3%)
 Problem 1. (30%) Calculaton of tme complexty (3%) Gven n ctes, usng exhaust search to see every result takes O(n!). Calculaton of tme needed to solve the problem (2%) 40 ctes:40! dfferent tours 40 add
Problem 1. (30%) Calculaton of tme complexty (3%) Gven n ctes, usng exhaust search to see every result takes O(n!). Calculaton of tme needed to solve the problem (2%) 40 ctes:40! dfferent tours 40 add
Lecture 10 Support Vector Machines II
 Lecture 10 Support Vector Machnes II 22 February 2016 Taylor B. Arnold Yale Statstcs STAT 365/665 1/28 Notes: Problem 3 s posted and due ths upcomng Frday There was an early bug n the fake-test data; fxed
Lecture 10 Support Vector Machnes II 22 February 2016 Taylor B. Arnold Yale Statstcs STAT 365/665 1/28 Notes: Problem 3 s posted and due ths upcomng Frday There was an early bug n the fake-test data; fxed
A Result on a Cyclic Polynomials
 Gen. Math. Note, Vol. 6, No., Feruary 05, pp. 59-65 ISSN 9-78 Copyrght ICSRS Pulcaton, 05.-cr.org Avalale free onlne at http:.geman.n A Reult on a Cyclc Polynomal S.A. Wahd Department of Mathematc & Stattc
Gen. Math. Note, Vol. 6, No., Feruary 05, pp. 59-65 ISSN 9-78 Copyrght ICSRS Pulcaton, 05.-cr.org Avalale free onlne at http:.geman.n A Reult on a Cyclc Polynomal S.A. Wahd Department of Mathematc & Stattc
Problem Set 9 Solutions
 Desgn and Analyss of Algorthms May 4, 2015 Massachusetts Insttute of Technology 6.046J/18.410J Profs. Erk Demane, Srn Devadas, and Nancy Lynch Problem Set 9 Solutons Problem Set 9 Solutons Ths problem
Desgn and Analyss of Algorthms May 4, 2015 Massachusetts Insttute of Technology 6.046J/18.410J Profs. Erk Demane, Srn Devadas, and Nancy Lynch Problem Set 9 Solutons Problem Set 9 Solutons Ths problem
Cryptanalysis of Threshold Proxy Signature Schemes 1)
 MM Research Preprnts, 226 233 MMRC, AMSS, Academa Snca No. 23, December 24 Cryptanalyss of Threshold Proxy Sgnature Schemes 1) Zuo-Wen Tan and Zhuo-Jun Lu Key Laboratory of Mathematcs Mechanzaton Insttute
MM Research Preprnts, 226 233 MMRC, AMSS, Academa Snca No. 23, December 24 Cryptanalyss of Threshold Proxy Sgnature Schemes 1) Zuo-Wen Tan and Zhuo-Jun Lu Key Laboratory of Mathematcs Mechanzaton Insttute
REDUCTION MODULO p. We will prove the reduction modulo p theorem in the general form as given by exercise 4.12, p. 143, of [1].
![REDUCTION MODULO p. We will prove the reduction modulo p theorem in the general form as given by exercise 4.12, p. 143, of [1]. REDUCTION MODULO p. We will prove the reduction modulo p theorem in the general form as given by exercise 4.12, p. 143, of [1].](/thumbs/73/68500980.jpg) REDUCTION MODULO p. IAN KIMING We wll prove the reducton modulo p theorem n the general form as gven by exercse 4.12, p. 143, of [1]. We consder an ellptc curve E defned over Q and gven by a Weerstraß
REDUCTION MODULO p. IAN KIMING We wll prove the reducton modulo p theorem n the general form as gven by exercse 4.12, p. 143, of [1]. We consder an ellptc curve E defned over Q and gven by a Weerstraß
Two Approaches to Proving. Goldbach s Conjecture
 Two Approache to Provng Goldbach Conecture By Bernard Farley Adved By Charle Parry May 3 rd 5 A Bref Introducton to Goldbach Conecture In 74 Goldbach made h mot famou contrbuton n mathematc wth the conecture
Two Approache to Provng Goldbach Conecture By Bernard Farley Adved By Charle Parry May 3 rd 5 A Bref Introducton to Goldbach Conecture In 74 Goldbach made h mot famou contrbuton n mathematc wth the conecture
APPENDIX A Some Linear Algebra
 APPENDIX A Some Lnear Algebra The collecton of m, n matrces A.1 Matrces a 1,1,..., a 1,n A = a m,1,..., a m,n wth real elements a,j s denoted by R m,n. If n = 1 then A s called a column vector. Smlarly,
APPENDIX A Some Lnear Algebra The collecton of m, n matrces A.1 Matrces a 1,1,..., a 1,n A = a m,1,..., a m,n wth real elements a,j s denoted by R m,n. If n = 1 then A s called a column vector. Smlarly,
Information Acquisition in Global Games of Regime Change (Online Appendix)
 Informaton Acquton n Global Game of Regme Change (Onlne Appendx) Mchal Szkup and Iabel Trevno Augut 4, 05 Introducton Th appendx contan the proof of all the ntermedate reult that have been omtted from
Informaton Acquton n Global Game of Regme Change (Onlne Appendx) Mchal Szkup and Iabel Trevno Augut 4, 05 Introducton Th appendx contan the proof of all the ntermedate reult that have been omtted from
Notes on Frequency Estimation in Data Streams
 Notes on Frequency Estmaton n Data Streams In (one of) the data streamng model(s), the data s a sequence of arrvals a 1, a 2,..., a m of the form a j = (, v) where s the dentty of the tem and belongs to
Notes on Frequency Estmaton n Data Streams In (one of) the data streamng model(s), the data s a sequence of arrvals a 1, a 2,..., a m of the form a j = (, v) where s the dentty of the tem and belongs to
Synchronization Protocols. Task Allocation Bin-Packing Heuristics: First-Fit Subtasks assigned in arbitrary order To allocate a new subtask T i,j
 End-to-End Schedulng Framework 1. Tak allocaton: bnd tak to proceor 2. Synchronzaton protocol: enforce precedence contrant 3. Subdeadlne agnment 4. Schedulablty analy Tak Allocaton Bn-Packng eurtc: Frt-Ft
End-to-End Schedulng Framework 1. Tak allocaton: bnd tak to proceor 2. Synchronzaton protocol: enforce precedence contrant 3. Subdeadlne agnment 4. Schedulablty analy Tak Allocaton Bn-Packng eurtc: Frt-Ft
Verification of Selected Precision Parameters of the Trimble S8 DR Plus Robotic Total Station
 81 Verfcaton of Selected Precon Parameter of the Trmble S8 DR Plu Robotc Total Staton Sokol, Š., Bajtala, M. and Ježko, J. Slovak Unverty of Technology, Faculty of Cvl Engneerng, Radlnkého 11, 81368 Bratlava,
81 Verfcaton of Selected Precon Parameter of the Trmble S8 DR Plu Robotc Total Staton Sokol, Š., Bajtala, M. and Ježko, J. Slovak Unverty of Technology, Faculty of Cvl Engneerng, Radlnkého 11, 81368 Bratlava,
Problem #1. Known: All required parameters. Schematic: Find: Depth of freezing as function of time. Strategy:
 BEE 3500 013 Prelm Soluton Problem #1 Known: All requred parameter. Schematc: Fnd: Depth of freezng a functon of tme. Strategy: In thee mplfed analy for freezng tme, a wa done n cla for a lab geometry,
BEE 3500 013 Prelm Soluton Problem #1 Known: All requred parameter. Schematc: Fnd: Depth of freezng a functon of tme. Strategy: In thee mplfed analy for freezng tme, a wa done n cla for a lab geometry,
Security Vulnerability in Identity-Based Public Key Cryptosystems from Pairings
 Internatonal Journal of Informaton and Educaton Technology Vol No 4 August 0 Securty Vulnerablty n Identty-Based ublc Key Cryptosystems from arngs Jyh-aw Yeh Abstract Many dentty-based lc key cryptosystems
Internatonal Journal of Informaton and Educaton Technology Vol No 4 August 0 Securty Vulnerablty n Identty-Based ublc Key Cryptosystems from arngs Jyh-aw Yeh Abstract Many dentty-based lc key cryptosystems
A Provably Secure Scheme for Remote User Authentication
 A Provably Secure Scheme for Remote Uer Authentication Fuw-Yi Yang 1, Su-Hui Chiu 2 1 Department of Computer Science and Information Engineering, Chaoyang Univerity of Technology Taichung County 41349,
A Provably Secure Scheme for Remote Uer Authentication Fuw-Yi Yang 1, Su-Hui Chiu 2 1 Department of Computer Science and Information Engineering, Chaoyang Univerity of Technology Taichung County 41349,
Transfer Functions. Convenient representation of a linear, dynamic model. A transfer function (TF) relates one input and one output: ( ) system
 Transfer Functons Convenent representaton of a lnear, dynamc model. A transfer functon (TF) relates one nput and one output: x t X s y t system Y s The followng termnology s used: x y nput output forcng
Transfer Functons Convenent representaton of a lnear, dynamc model. A transfer functon (TF) relates one nput and one output: x t X s y t system Y s The followng termnology s used: x y nput output forcng
A Study of Quantum Strategies for Newcomb s Paradox
 Bune, 00, : 4-50 do:0.436/b.00.004 Publhed Onlne March 00 (http://www.scrp.org/journal/b A Study of Quantum Stratege for ewcomb Paradox Taah Mhara Department of Informaton Scence and Art, Toyo Unverty,
Bune, 00, : 4-50 do:0.436/b.00.004 Publhed Onlne March 00 (http://www.scrp.org/journal/b A Study of Quantum Stratege for ewcomb Paradox Taah Mhara Department of Informaton Scence and Art, Toyo Unverty,
More metrics on cartesian products
 More metrcs on cartesan products If (X, d ) are metrc spaces for 1 n, then n Secton II4 of the lecture notes we defned three metrcs on X whose underlyng topologes are the product topology The purpose of
More metrcs on cartesan products If (X, d ) are metrc spaces for 1 n, then n Secton II4 of the lecture notes we defned three metrcs on X whose underlyng topologes are the product topology The purpose of
A New Virtual Indexing Method for Measuring Host Connection Degrees
 A New Vrtual Indexng Method for Meaurng ot Connecton Degree Pnghu Wang, Xaohong Guan,, Webo Gong 3, and Don Towley 4 SKLMS Lab and MOE KLINNS Lab, X an Jaotong Unverty, X an, Chna Department of Automaton
A New Vrtual Indexng Method for Meaurng ot Connecton Degree Pnghu Wang, Xaohong Guan,, Webo Gong 3, and Don Towley 4 SKLMS Lab and MOE KLINNS Lab, X an Jaotong Unverty, X an, Chna Department of Automaton
Two-Layered Model of Blood Flow through Composite Stenosed Artery
 Avalable at http://pvamu.edu/aam Appl. Appl. Math. ISSN: 93-9466 Vol. 4, Iue (December 9), pp. 343 354 (Prevouly, Vol. 4, No.) Applcaton Appled Mathematc: An Internatonal Journal (AAM) Two-ayered Model
Avalable at http://pvamu.edu/aam Appl. Appl. Math. ISSN: 93-9466 Vol. 4, Iue (December 9), pp. 343 354 (Prevouly, Vol. 4, No.) Applcaton Appled Mathematc: An Internatonal Journal (AAM) Two-ayered Model
Preemptive scheduling. Disadvantages of preemptions WCET. Preemption indirect costs 19/10/2018. Cache related preemption delay
 19/1/18 Preemptve cedulng Mot o wor on cedulng a been ocued on ully preemptve ytem, becaue tey allow ger reponvene: Preemptve Non Preemptve Dadvantage o preempton However, eac preempton a a cot: ontext
19/1/18 Preemptve cedulng Mot o wor on cedulng a been ocued on ully preemptve ytem, becaue tey allow ger reponvene: Preemptve Non Preemptve Dadvantage o preempton However, eac preempton a a cot: ontext
This appendix presents the derivations and proofs omitted from the main text.
 Onlne Appendx A Appendx: Omtted Dervaton and Proof Th appendx preent the dervaton and proof omtted from the man text A Omtted dervaton n Secton Mot of the analy provded n the man text Here, we formally
Onlne Appendx A Appendx: Omtted Dervaton and Proof Th appendx preent the dervaton and proof omtted from the man text A Omtted dervaton n Secton Mot of the analy provded n the man text Here, we formally
G /G Advanced Cryptography 12/9/2009. Lecture 14
 G22.3220-001/G63.2180 Advanced Cryptography 12/9/2009 Lecturer: Yevgeny Dods Lecture 14 Scrbe: Arsteds Tentes In ths lecture we covered the Ideal/Real paradgm and the noton of UC securty. Moreover, we
G22.3220-001/G63.2180 Advanced Cryptography 12/9/2009 Lecturer: Yevgeny Dods Lecture 14 Scrbe: Arsteds Tentes In ths lecture we covered the Ideal/Real paradgm and the noton of UC securty. Moreover, we
Distributed Control for the Parallel DC Linked Modular Shunt Active Power Filters under Distorted Utility Voltage Condition
 Dtrbted Control for the Parallel DC Lnked Modlar Shnt Actve Power Flter nder Dtorted Utlty Voltage Condton Reearch Stdent: Adl Salman Spervor: Dr. Malabka Ba School of Electrcal and Electronc Engneerng
Dtrbted Control for the Parallel DC Lnked Modlar Shnt Actve Power Flter nder Dtorted Utlty Voltage Condton Reearch Stdent: Adl Salman Spervor: Dr. Malabka Ba School of Electrcal and Electronc Engneerng
Inner Product. Euclidean Space. Orthonormal Basis. Orthogonal
 Inner Product Defnton 1 () A Eucldean space s a fnte-dmensonal vector space over the reals R, wth an nner product,. Defnton 2 (Inner Product) An nner product, on a real vector space X s a symmetrc, blnear,
Inner Product Defnton 1 () A Eucldean space s a fnte-dmensonal vector space over the reals R, wth an nner product,. Defnton 2 (Inner Product) An nner product, on a real vector space X s a symmetrc, blnear,
Pythagorean triples. Leen Noordzij.
 Pythagorean trple. Leen Noordz Dr.l.noordz@leennoordz.nl www.leennoordz.me Content A Roadmap for generatng Pythagorean Trple.... Pythagorean Trple.... 3 Dcuon Concluon.... 5 A Roadmap for generatng Pythagorean
Pythagorean trple. Leen Noordz Dr.l.noordz@leennoordz.nl www.leennoordz.me Content A Roadmap for generatng Pythagorean Trple.... Pythagorean Trple.... 3 Dcuon Concluon.... 5 A Roadmap for generatng Pythagorean
RSA /2002/13(08) , ); , ) RSA RSA : RSA RSA [2] , [1,4]
![RSA /2002/13(08) , ); , ) RSA RSA : RSA RSA [2] , [1,4] RSA /2002/13(08) , ); , ) RSA RSA : RSA RSA [2] , [1,4]](/thumbs/88/115270966.jpg) 1000-9825/2002/13(081729-06 2002 Journal of Software Vol13, No8 RSA 1,2 1, 1 (, 200433; 2 (, 200070 E-mal: yfhu@fudaneducn http://wwwfudaneducn : RSA RSA :, ; RSA,,, RSA,, : ; RSA ; ;RSA; : TP309 : A RSA
1000-9825/2002/13(081729-06 2002 Journal of Software Vol13, No8 RSA 1,2 1, 1 (, 200433; 2 (, 200070 E-mal: yfhu@fudaneducn http://wwwfudaneducn : RSA RSA :, ; RSA,,, RSA,, : ; RSA ; ;RSA; : TP309 : A RSA
One-sided finite-difference approximations suitable for use with Richardson extrapolation
 Journal of Computatonal Physcs 219 (2006) 13 20 Short note One-sded fnte-dfference approxmatons sutable for use wth Rchardson extrapolaton Kumar Rahul, S.N. Bhattacharyya * Department of Mechancal Engneerng,
Journal of Computatonal Physcs 219 (2006) 13 20 Short note One-sded fnte-dfference approxmatons sutable for use wth Rchardson extrapolaton Kumar Rahul, S.N. Bhattacharyya * Department of Mechancal Engneerng,
Estimation of Finite Population Total under PPS Sampling in Presence of Extra Auxiliary Information
 Internatonal Journal of Stattc and Analy. ISSN 2248-9959 Volume 6, Number 1 (2016), pp. 9-16 Reearch Inda Publcaton http://www.rpublcaton.com Etmaton of Fnte Populaton Total under PPS Samplng n Preence
Internatonal Journal of Stattc and Analy. ISSN 2248-9959 Volume 6, Number 1 (2016), pp. 9-16 Reearch Inda Publcaton http://www.rpublcaton.com Etmaton of Fnte Populaton Total under PPS Samplng n Preence
Electrical Circuits II (ECE233b)
 Electrcal Crcut II (ECE33b) Applcaton of Laplace Tranform to Crcut Analy Anet Dounav The Unverty of Wetern Ontaro Faculty of Engneerng Scence Crcut Element Retance Tme Doman (t) v(t) R v(t) = R(t) Frequency
Electrcal Crcut II (ECE33b) Applcaton of Laplace Tranform to Crcut Analy Anet Dounav The Unverty of Wetern Ontaro Faculty of Engneerng Scence Crcut Element Retance Tme Doman (t) v(t) R v(t) = R(t) Frequency
Not at Steady State! Yes! Only if reactions occur! Yes! Ideal Gas, change in temperature or pressure. Yes! Class 15. Is the following possible?
 Chapter 5-6 (where we are gong) Ideal gae and lqud (today) Dente Partal preure Non-deal gae (next tme) Eqn. of tate Reduced preure and temperature Compreblty chart (z) Vapor-lqud ytem (Ch. 6) Vapor preure
Chapter 5-6 (where we are gong) Ideal gae and lqud (today) Dente Partal preure Non-deal gae (next tme) Eqn. of tate Reduced preure and temperature Compreblty chart (z) Vapor-lqud ytem (Ch. 6) Vapor preure
Errors for Linear Systems
 Errors for Lnear Systems When we solve a lnear system Ax b we often do not know A and b exactly, but have only approxmatons  and ˆb avalable. Then the best thng we can do s to solve ˆx ˆb exactly whch
Errors for Lnear Systems When we solve a lnear system Ax b we often do not know A and b exactly, but have only approxmatons  and ˆb avalable. Then the best thng we can do s to solve ˆx ˆb exactly whch
Quick Visit to Bernoulli Land
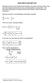 Although we have een the Bernoull equaton and een t derved before, th next note how t dervaton for an uncopreble & nvcd flow. The dervaton follow that of Kuethe &Chow ot cloely (I lke t better than Anderon).
Although we have een the Bernoull equaton and een t derved before, th next note how t dervaton for an uncopreble & nvcd flow. The dervaton follow that of Kuethe &Chow ot cloely (I lke t better than Anderon).
Weak McCoy Ore Extensions
 Internatonal Mathematcal Forum, Vol. 6, 2, no. 2, 75-86 Weak McCoy Ore Extenon R. Mohammad, A. Mouav and M. Zahr Department of Pure Mathematc, Faculty of Mathematcal Scence Tarbat Modare Unverty, P.O.
Internatonal Mathematcal Forum, Vol. 6, 2, no. 2, 75-86 Weak McCoy Ore Extenon R. Mohammad, A. Mouav and M. Zahr Department of Pure Mathematc, Faculty of Mathematcal Scence Tarbat Modare Unverty, P.O.
Maximizing the number of nonnegative subsets
 Maxmzng the number of nonnegatve subsets Noga Alon Hao Huang December 1, 213 Abstract Gven a set of n real numbers, f the sum of elements of every subset of sze larger than k s negatve, what s the maxmum
Maxmzng the number of nonnegatve subsets Noga Alon Hao Huang December 1, 213 Abstract Gven a set of n real numbers, f the sum of elements of every subset of sze larger than k s negatve, what s the maxmum
No! Yes! Only if reactions occur! Yes! Ideal Gas, change in temperature or pressure. Survey Results. Class 15. Is the following possible?
 Survey Reult Chapter 5-6 (where we are gong) % of Student 45% 40% 35% 30% 25% 20% 15% 10% 5% 0% Hour Spent on ChE 273 1-2 3-4 5-6 7-8 9-10 11+ Hour/Week 2008 2009 2010 2011 2012 2013 2014 2015 2017 F17
Survey Reult Chapter 5-6 (where we are gong) % of Student 45% 40% 35% 30% 25% 20% 15% 10% 5% 0% Hour Spent on ChE 273 1-2 3-4 5-6 7-8 9-10 11+ Hour/Week 2008 2009 2010 2011 2012 2013 2014 2015 2017 F17
APPROXIMATE FUZZY REASONING BASED ON INTERPOLATION IN THE VAGUE ENVIRONMENT OF THE FUZZY RULEBASE AS A PRACTICAL ALTERNATIVE OF THE CLASSICAL CRI
 Kovác, Sz., Kóczy, L.T.: Approxmate Fuzzy Reaonng Baed on Interpolaton n the Vague Envronment of the Fuzzy Rulebae a a Practcal Alternatve of the Clacal CRI, Proceedng of the 7 th Internatonal Fuzzy Sytem
Kovác, Sz., Kóczy, L.T.: Approxmate Fuzzy Reaonng Baed on Interpolaton n the Vague Envronment of the Fuzzy Rulebae a a Practcal Alternatve of the Clacal CRI, Proceedng of the 7 th Internatonal Fuzzy Sytem
PHYS 100 Worked Examples Week 05: Newton s 2 nd Law
 PHYS 00 Worked Eaple Week 05: ewton nd Law Poor Man Acceleroeter A drver hang an ar frehener fro ther rearvew rror wth a trng. When acceleratng onto the hghwa, the drver notce that the ar frehener ake
PHYS 00 Worked Eaple Week 05: ewton nd Law Poor Man Acceleroeter A drver hang an ar frehener fro ther rearvew rror wth a trng. When acceleratng onto the hghwa, the drver notce that the ar frehener ake
Solution Methods for Time-indexed MIP Models for Chemical Production Scheduling
 Ian Davd Lockhart Bogle and Mchael Farweather (Edtor), Proceedng of the 22nd European Sympoum on Computer Aded Proce Engneerng, 17-2 June 212, London. 212 Elever B.V. All rght reerved. Soluton Method for
Ian Davd Lockhart Bogle and Mchael Farweather (Edtor), Proceedng of the 22nd European Sympoum on Computer Aded Proce Engneerng, 17-2 June 212, London. 212 Elever B.V. All rght reerved. Soluton Method for
Computation of Higher Order Moments from Two Multinomial Overdispersion Likelihood Models
 Computaton of Hgher Order Moments from Two Multnomal Overdsperson Lkelhood Models BY J. T. NEWCOMER, N. K. NEERCHAL Department of Mathematcs and Statstcs, Unversty of Maryland, Baltmore County, Baltmore,
Computaton of Hgher Order Moments from Two Multnomal Overdsperson Lkelhood Models BY J. T. NEWCOMER, N. K. NEERCHAL Department of Mathematcs and Statstcs, Unversty of Maryland, Baltmore County, Baltmore,
Lecture 8: Time & Clocks. CDK: Sections TVS: Sections
 Lecture 8: Tme & Clocks CDK: Sectons 11.1 11.4 TVS: Sectons 6.1 6.2 Topcs Synchronzaton Logcal tme (Lamport) Vector clocks We assume there are benefts from havng dfferent systems n a network able to agree
Lecture 8: Tme & Clocks CDK: Sectons 11.1 11.4 TVS: Sectons 6.1 6.2 Topcs Synchronzaton Logcal tme (Lamport) Vector clocks We assume there are benefts from havng dfferent systems n a network able to agree
MAE140 - Linear Circuits - Winter 16 Final, March 16, 2016
 ME140 - Lnear rcuts - Wnter 16 Fnal, March 16, 2016 Instructons () The exam s open book. You may use your class notes and textbook. You may use a hand calculator wth no communcaton capabltes. () You have
ME140 - Lnear rcuts - Wnter 16 Fnal, March 16, 2016 Instructons () The exam s open book. You may use your class notes and textbook. You may use a hand calculator wth no communcaton capabltes. () You have
Augmented Broadcaster Identity-based Broadcast Encryption
 Augmented Broadcaster Identty-based Broadcast Encrypton Janhong Zhang Yuwe Xu Zhpeng Chen Insttuton of Image Processng and Pattern Recognton North Chna Unversty of Technology Bejng Chna 100144 ywxupaper@163com
Augmented Broadcaster Identty-based Broadcast Encrypton Janhong Zhang Yuwe Xu Zhpeng Chen Insttuton of Image Processng and Pattern Recognton North Chna Unversty of Technology Bejng Chna 100144 ywxupaper@163com
Design By Emulation (Indirect Method)
 Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
A METHOD TO REPRESENT THE SEMANTIC DESCRIPTION OF A WEB SERVICE BASED ON COMPLEXITY FUNCTIONS
 UPB Sc Bull, Sere A, Vol 77, I, 5 ISSN 3-77 A METHOD TO REPRESENT THE SEMANTIC DESCRIPTION OF A WEB SERVICE BASED ON COMPLEXITY FUNCTIONS Andre-Hora MOGOS, Adna Magda FLOREA Semantc web ervce repreent
UPB Sc Bull, Sere A, Vol 77, I, 5 ISSN 3-77 A METHOD TO REPRESENT THE SEMANTIC DESCRIPTION OF A WEB SERVICE BASED ON COMPLEXITY FUNCTIONS Andre-Hora MOGOS, Adna Magda FLOREA Semantc web ervce repreent
A A Non-Constructible Equilibrium 1
 A A Non-Contructbe Equbrum 1 The eampe depct a eparabe contet wth three payer and one prze of common vaue 1 (o v ( ) =1 c ( )). I contruct an equbrum (C, G, G) of the contet, n whch payer 1 bet-repone
A A Non-Contructbe Equbrum 1 The eampe depct a eparabe contet wth three payer and one prze of common vaue 1 (o v ( ) =1 c ( )). I contruct an equbrum (C, G, G) of the contet, n whch payer 1 bet-repone
Resonant FCS Predictive Control of Power Converter in Stationary Reference Frame
 Preprnt of the 9th World Congre The Internatonal Federaton of Automatc Control Cape Town, South Afrca. Augut -9, Reonant FCS Predctve Control of Power Converter n Statonary Reference Frame Lupng Wang K
Preprnt of the 9th World Congre The Internatonal Federaton of Automatc Control Cape Town, South Afrca. Augut -9, Reonant FCS Predctve Control of Power Converter n Statonary Reference Frame Lupng Wang K
College of Computer & Information Science Fall 2009 Northeastern University 20 October 2009
 College of Computer & Informaton Scence Fall 2009 Northeastern Unversty 20 October 2009 CS7880: Algorthmc Power Tools Scrbe: Jan Wen and Laura Poplawsk Lecture Outlne: Prmal-dual schema Network Desgn:
College of Computer & Informaton Scence Fall 2009 Northeastern Unversty 20 October 2009 CS7880: Algorthmc Power Tools Scrbe: Jan Wen and Laura Poplawsk Lecture Outlne: Prmal-dual schema Network Desgn:
Foundations of Arithmetic
 Foundatons of Arthmetc Notaton We shall denote the sum and product of numbers n the usual notaton as a 2 + a 2 + a 3 + + a = a, a 1 a 2 a 3 a = a The notaton a b means a dvdes b,.e. ac = b where c s an
Foundatons of Arthmetc Notaton We shall denote the sum and product of numbers n the usual notaton as a 2 + a 2 + a 3 + + a = a, a 1 a 2 a 3 a = a The notaton a b means a dvdes b,.e. ac = b where c s an
Basic Regular Expressions. Introduction. Introduction to Computability. Theory. Motivation. Lecture4: Regular Expressions
 Introducton to Computablty Theory Lecture: egular Expressons Prof Amos Israel Motvaton If one wants to descrbe a regular language, La, she can use the a DFA, Dor an NFA N, such L ( D = La that that Ths
Introducton to Computablty Theory Lecture: egular Expressons Prof Amos Israel Motvaton If one wants to descrbe a regular language, La, she can use the a DFA, Dor an NFA N, such L ( D = La that that Ths
Anonymous Identity-Based Broadcast Encryption with Revocation for File Sharing
 Anonymous Identty-Based Broadcast Encrypton wth Revocaton for Fle Sharng Janchang La, Y Mu, Fuchun Guo, Wlly Suslo, and Rongmao Chen Centre for Computer and Informaton Securty Research, School of Computng
Anonymous Identty-Based Broadcast Encrypton wth Revocaton for Fle Sharng Janchang La, Y Mu, Fuchun Guo, Wlly Suslo, and Rongmao Chen Centre for Computer and Informaton Securty Research, School of Computng
Problem Do any of the following determine homomorphisms from GL n (C) to GL n (C)?
 Homework 8 solutons. Problem 16.1. Whch of the followng defne homomomorphsms from C\{0} to C\{0}? Answer. a) f 1 : z z Yes, f 1 s a homomorphsm. We have that z s the complex conjugate of z. If z 1,z 2
Homework 8 solutons. Problem 16.1. Whch of the followng defne homomomorphsms from C\{0} to C\{0}? Answer. a) f 1 : z z Yes, f 1 s a homomorphsm. We have that z s the complex conjugate of z. If z 1,z 2
Password Based Key Exchange With Mutual Authentication
 Password Based Key Exchange Wth Mutual Authentcaton Shaoquan Jang and Guang Gong Department of Electrcal and Computer Engneerng Unversty of Waterloo Waterloo, Ontaro N2L 3G1, CANADA Emal:{angshq,ggong}@callope.uwaterloo.ca
Password Based Key Exchange Wth Mutual Authentcaton Shaoquan Jang and Guang Gong Department of Electrcal and Computer Engneerng Unversty of Waterloo Waterloo, Ontaro N2L 3G1, CANADA Emal:{angshq,ggong}@callope.uwaterloo.ca
MODELLING OF TRANSIENT HEAT TRANSPORT IN TWO-LAYERED CRYSTALLINE SOLID FILMS USING THE INTERVAL LATTICE BOLTZMANN METHOD
 Journal o Appled Mathematc and Computatonal Mechanc 7, 6(4), 57-65 www.amcm.pcz.pl p-issn 99-9965 DOI:.75/jamcm.7.4.6 e-issn 353-588 MODELLING OF TRANSIENT HEAT TRANSPORT IN TWO-LAYERED CRYSTALLINE SOLID
Journal o Appled Mathematc and Computatonal Mechanc 7, 6(4), 57-65 www.amcm.pcz.pl p-issn 99-9965 DOI:.75/jamcm.7.4.6 e-issn 353-588 MODELLING OF TRANSIENT HEAT TRANSPORT IN TWO-LAYERED CRYSTALLINE SOLID
The Study of Teaching-learning-based Optimization Algorithm
 Advanced Scence and Technology Letters Vol. (AST 06), pp.05- http://dx.do.org/0.57/astl.06. The Study of Teachng-learnng-based Optmzaton Algorthm u Sun, Yan fu, Lele Kong, Haolang Q,, Helongang Insttute
Advanced Scence and Technology Letters Vol. (AST 06), pp.05- http://dx.do.org/0.57/astl.06. The Study of Teachng-learnng-based Optmzaton Algorthm u Sun, Yan fu, Lele Kong, Haolang Q,, Helongang Insttute
BOUNDARY ELEMENT METHODS FOR VIBRATION PROBLEMS. Ashok D. Belegundu Professor of Mechanical Engineering Penn State University
 BOUNDARY ELEMENT METHODS FOR VIBRATION PROBLEMS by Aho D. Belegundu Profeor of Mechancal Engneerng Penn State Unverty ahobelegundu@yahoo.com ASEE Fello, Summer 3 Colleague at NASA Goddard: Danel S. Kaufman
BOUNDARY ELEMENT METHODS FOR VIBRATION PROBLEMS by Aho D. Belegundu Profeor of Mechancal Engneerng Penn State Unverty ahobelegundu@yahoo.com ASEE Fello, Summer 3 Colleague at NASA Goddard: Danel S. Kaufman
Statistical Properties of the OLS Coefficient Estimators. 1. Introduction
 ECOOMICS 35* -- OTE 4 ECO 35* -- OTE 4 Stattcal Properte of the OLS Coeffcent Etmator Introducton We derved n ote the OLS (Ordnary Leat Square etmator ˆβ j (j, of the regreon coeffcent βj (j, n the mple
ECOOMICS 35* -- OTE 4 ECO 35* -- OTE 4 Stattcal Properte of the OLS Coeffcent Etmator Introducton We derved n ote the OLS (Ordnary Leat Square etmator ˆβ j (j, of the regreon coeffcent βj (j, n the mple
arxiv: v1 [cs.gt] 15 Jan 2019
![arxiv: v1 [cs.gt] 15 Jan 2019 arxiv: v1 [cs.gt] 15 Jan 2019](/thumbs/88/114623985.jpg) Model and algorthm for tme-content rk-aware Markov game Wenje Huang, Pham Vet Ha and Wllam B. Hakell January 16, 2019 arxv:1901.04882v1 [c.gt] 15 Jan 2019 Abtract In th paper, we propoe a model for non-cooperatve
Model and algorthm for tme-content rk-aware Markov game Wenje Huang, Pham Vet Ha and Wllam B. Hakell January 16, 2019 arxv:1901.04882v1 [c.gt] 15 Jan 2019 Abtract In th paper, we propoe a model for non-cooperatve
The multivariate Gaussian probability density function for random vector X (X 1,,X ) T. diagonal term of, denoted
 Appendx Proof of heorem he multvarate Gauan probablty denty functon for random vector X (X,,X ) px exp / / x x mean and varance equal to the th dagonal term of, denoted he margnal dtrbuton of X Gauan wth
Appendx Proof of heorem he multvarate Gauan probablty denty functon for random vector X (X,,X ) px exp / / x x mean and varance equal to the th dagonal term of, denoted he margnal dtrbuton of X Gauan wth
STOCHASTIC BEHAVIOUR OF COMMUNICATION SUBSYSTEM OF COMMUNICATION SATELLITE
 IJS 4 () July Sharma & al ehavour of Subytem of ommuncaton Satellte SOHSI HVIOU O OMMUNIION SUSYSM O OMMUNIION SLLI SK Mttal eepankar Sharma & Neelam Sharma 3 S he author n th paper have dcued the tochatc
IJS 4 () July Sharma & al ehavour of Subytem of ommuncaton Satellte SOHSI HVIOU O OMMUNIION SUSYSM O OMMUNIION SLLI SK Mttal eepankar Sharma & Neelam Sharma 3 S he author n th paper have dcued the tochatc
8 Waves in Uniform Magnetized Media
 8 Wave n Unform Magnetzed Meda 81 Suceptblte The frt order current can be wrtten j = j = q d 3 p v f 1 ( r, p, t) = ɛ 0 χ E For Maxwellan dtrbuton Y n (λ) = f 0 (v, v ) = 1 πvth exp (v V ) v th 1 πv th
8 Wave n Unform Magnetzed Meda 81 Suceptblte The frt order current can be wrtten j = j = q d 3 p v f 1 ( r, p, t) = ɛ 0 χ E For Maxwellan dtrbuton Y n (λ) = f 0 (v, v ) = 1 πvth exp (v V ) v th 1 πv th
Formulas for the Determinant
 page 224 224 CHAPTER 3 Determnants e t te t e 2t 38 A = e t 2te t e 2t e t te t 2e 2t 39 If 123 A = 345, 456 compute the matrx product A adj(a) What can you conclude about det(a)? For Problems 40 43, use
page 224 224 CHAPTER 3 Determnants e t te t e 2t 38 A = e t 2te t e 2t e t te t 2e 2t 39 If 123 A = 345, 456 compute the matrx product A adj(a) What can you conclude about det(a)? For Problems 40 43, use
Module 5. Cables and Arches. Version 2 CE IIT, Kharagpur
 odule 5 Cable and Arche Veron CE IIT, Kharagpur Leon 33 Two-nged Arch Veron CE IIT, Kharagpur Intructonal Objectve: After readng th chapter the tudent wll be able to 1. Compute horzontal reacton n two-hnged
odule 5 Cable and Arche Veron CE IIT, Kharagpur Leon 33 Two-nged Arch Veron CE IIT, Kharagpur Intructonal Objectve: After readng th chapter the tudent wll be able to 1. Compute horzontal reacton n two-hnged
Chapter.4 MAGNETIC CIRCUIT OF A D.C. MACHINE
 Chapter.4 MAGNETIC CIRCUIT OF A D.C. MACHINE The dfferent part of the dc machne manetc crcut / pole are yoke, pole, ar ap, armature teeth and armature core. Therefore, the ampere-turn /pole to etablh the
Chapter.4 MAGNETIC CIRCUIT OF A D.C. MACHINE The dfferent part of the dc machne manetc crcut / pole are yoke, pole, ar ap, armature teeth and armature core. Therefore, the ampere-turn /pole to etablh the
Grover s Algorithm + Quantum Zeno Effect + Vaidman
 Grover s Algorthm + Quantum Zeno Effect + Vadman CS 294-2 Bomb 10/12/04 Fall 2004 Lecture 11 Grover s algorthm Recall that Grover s algorthm for searchng over a space of sze wors as follows: consder the
Grover s Algorthm + Quantum Zeno Effect + Vadman CS 294-2 Bomb 10/12/04 Fall 2004 Lecture 11 Grover s algorthm Recall that Grover s algorthm for searchng over a space of sze wors as follows: consder the
