A Provably Secure Scheme for Remote User Authentication
|
|
|
- Oliver Carson
- 5 years ago
- Views:
Transcription
1 A Provably Secure Scheme for Remote Uer Authentication Fuw-Yi Yang 1, Su-Hui Chiu 2 1 Department of Computer Science and Information Engineering, Chaoyang Univerity of Technology Taichung County 41349, Taiwan, yangfy@cyut.edu.tw 2 Office of Accounting, Chaoyang Univerity of Technology Taichung County 41349, Taiwan, uhui@cyut.edu.tw Abtract Thi paper propoe a one-way uer authentication cheme. The propoed cheme ha everal advantage over previou cheme: 1. Thi cheme i provably ecure. 2. It atifie the forward ecrecy property. 3. It i ecure even under the colluion of uer. 1. INTRODUCTION A one-way uer authentication cheme enable an acce erver (receiver, ytem) to ditinguih between intruder and legitimate uer. By holding a paword table, the work in [1] propoed a remote paword authentication cheme with inecure communication. The paword table contain the account and paword of uer that have regitered in the ytem. A a uer enter the ytem, he mut key in the correct account number and paword. An authentication cheme that ue a paword table may not be uitable for non-repudiation application, ince both the ytem and uer know the paword tored in the paword table. The tored paword may alo be tolen by an intruder. The problem aociated with maintaining a paword table can be olved uing a mart card to tore the uer ecret data. The ytem tore each regitered uer authentication data in the mart card. The uer i authenticated by inpecting the data iued from the mart card. Thu, there i no paword table on the erver ide and the mart card olve the above mentioned problem. 1.1 Related work Thi ubection urvey ome authentication cheme that ue recently developed mart card. The ecurity weaknee in thee ytem are dicued. The cheme in [2] authenticate uer baed on the Chinee remainder theorem. The ytem generate authentication data (paword, algorithm, and other neceary parameter) and tore thee data in a mart card. Thi ytem can therefore authenticate uer without uing a paword table. Subequent to the cheme preented in [2], many imilar authentication cheme were developed. The cheme in [3] authenticate remote uer by applying imple geometric propertie on the Euclidean plane. The central authority aign a unique line to each regitered uer. A mart card i iued to the uer in a ecure way. Thi card contain ome ueful information including two ditinct point on the line. The line i deigned uch that the uer can calculate the third point on the line uing hi paword. With three ditinct point on the line, the uer i able to recontruct the line whenever he want to login to the erver. The ability to recontruct the predetermined line how that he i a genuine uer. Another cheme alo ue the geometric property propoed in [4]. A uer i authenticated baed on the n-dimenional circle property. Some cheme take advantage of public key cryptography to authenticate uer. The cheme preented in [5-6] authenticate uer baed on the famou ElGamal public key cryptoytem [7]. The cheme in [8] further extended the cheme in [5] to provide the forward ecrecy property, which mean that the uer paword are ecure even if the ytem ecret key i compromied. Uing only colliion-reitant hah function, the cheme in [9-10] are additional authentication method. Since thee two cheme do not require modular exponential operation, they are more efficient than cheme baed on the public key cryptoytem. However, the authentication cheme urveyed above are not provably ecure. Thee cheme lack formalized ecurity treatment. Therefore, the weaknee of ome cheme are uncovered oon after thee cheme are propoed. The work in [11] propoe an imperonation attack on the cheme in [2]. The cheme in [12] demontrate a method to recontruct the line hared with the ytem, and thu launche a replay attack on the cheme in [3]. Similarly, by recontructing the preet circle, the cheme in [13] preent an imperonation attack on the cheme in [4]. The cheme in [6], [8], and [14-16] apply a imple algebraic property to mount the homomorphim attack on the cheme in [5]. Similarly, the cheme in [6] i vulnerable to the ame attack illutrate for the cheme in [8] and [16]. The cheme in [17] propoe a gueing attack for the cheme in [9] and a parallel eion
2 attack on the cheme in [10]. Depite thee ecurity weaknee, the uer in cheme [2], [5-6], and [8] have no freedom to chooe their paword. The central authority aign paword. Having no right to chooe a paword could be inappropriate in ome circumtance, e.g., non-repudiation application. 1.2 Contribution The propoed cheme enable uer to chooe their private key on their own volition and keep it ecret. Guaranteeing ecurity, a formal proof i given to verify that the propoed cheme i ecure againt adaptively choen meage attack [18]. In thi attack model, it i aumed that the adverary ha acce to a login oracle, which generate login meage (login requet). The adverary i allowed to collect login meage by aking the login oracle a he wihe, except for the meage that the adverary i forging. Thi level of ecurity i ufficient to prevent the ytem from being attacked by the colluion of mart card holder. The mart card require only one modular exponentiation for off-line computation. The on-line computation involve one modular multiplication and one hah operation. The cot i quite efficient compared with the cheme in [5-6] and [8]. Thee cheme require two off-line modular exponentiation and one on-line modular exponentiation to iue a login requet. 1.3 Organization Section 2 decribe the notation and detail of the propoed cheme. Section 3 dicue the communicational bandwidth and computational complexity. Section 4 prove that the propoed cheme i ecure under the adaptively choen meage attack model. Section 5 conclude the paper. 2. THE PROPOSED SCHEME Aume that p i a large prime uch that (p - 1) i diviible by another large prime q. g i an element of order q in the multiplicative group of integer modulo p, i.e., g Z * p. G denote the ubgroup generated by g. h(.) i a colliion freene hah function that map arbitrary bit tring to the multiplicative group of integer modulo q, i.e., h(.): {0, 1} * Z * q. a b denote the concatenation of tring a and b. The ymbol a R G denote that a i randomly elected from the et G. a denote the bit length of a. The propoed cheme conit of three entitie: a Central Authority (CA), acce erver, and uer. For each authorized uer, the CA tore ome piece of ecret data in a mart card and end the mart card to the uer through a ecure channel. The mart card may contain the uer identity, the certificate iued from the CA, expiration date, uer ecret key, and other ueful information. Whenever a uer want to login to the acce erver, he inert hi mart card into an input device. The mart card will contruct a login meage and end it to the acce erver. After paing the authenticating procedure, the uer i uccefully logged-in to the acce erver. Each acce erver tore reource and provide ome acce ervice. Although the acce erver i reponible for uer authentication, it doe not hold any ecret uer information. There are four phae in the implementation, i.e., Initialization phae, Regitration phae, Login phae, and Authentication phae. The detail for each phae are decribed a follow. Initialization phae: Aume that CA ha a ecret key x R Z q and the correponding public key i y = g x mod p. CA publihe p, q, g, h(.) and y. Regitration phae: Aume that uer u want to regiter at the acce ytem. The CA and uer u execute cooperatively the following tep to complete the regitration phae. 1. Uer u chooe an integer x u R Z q a hi ecret key and the correponding public key i ID u = g x u mod p. He then tore the ecret number x u in a ecret place and regiter hi/her uer name and ID u in the CA. 2. The CA chooe an integer k R Z q and k compute r = g mod p. If r = 0 mod q repeat thi tep again. 3. The CA compute from the linear congruence equation, = h(r, ID u ) k + r x mod q. The tuple (ID u, r, ) i eentially a certificate iued by the CA. Any one can verify the validity of an ID u by checking g h( r, ID ) = r u r y mod p. 4. The certificate, expiration date and other neceary data are tored in the mart card. Thi card enable uer u to contruct a login meage for entering the acce erver. Login phae: Uer u mut inert hi mart card into a terminal and contruct a login meage according to the following tep, whenever he want to enter the acce erver at time T. 1. Uer u chooe an integer k R Z q, and compute the quantitie r = g k mod p, H = h(r, T, ID u, r, ), = (k H + x u r ) mod q. If r = 0 mod q, repeat thi tep again. Namely, the pair (r, ) i a ignature for uer u on the timetamp T and certificate (ID u, r, ).
3 2. Uer u end login meage L = {r,, T, ID u, r, } to erver. Authentication phae: The login requet L contain two ignature: the certificate (ID u, r, ) and the ignature ((T, ID u, r, ), r, ). CA contructed the firt ignature, which certifie that the ID u (uer u) i an authorized uer. Uer ID u ign on the meage (T, ID u, r, ), i.e., generate the econd ignature, when he want to acce the erver. Therefore, the authentication phae conit of two procedure to check whether thee ignature are valid. The erver perform the following tep to conclude the authentication proce. Aume that the login meage L arrived at time T'. 1. Server check whether (T' - T) i le than the legal tranmiion time. If not, reject the requet. 2. Server reject uer requet if the equation g h( r, ID ) = u r r y mod p doe not hold, i.e., verify the certificate (ID u, r, ). 3. Server compute hah value, H = h(r, T, ID u, r, ). 4. Accept the uer ID u a legal if the verifying equation g = r H IDu r mod p hold, otherwie deny the login requet. Note that if uing timetamp i not ufficient to defeat replay attack, then a traditional identification cheme with three move i required. In thi paper, we aumed that timetamp i appropriate. 3. PERFORMANCE AND CORRECTNESS To implify the computational cot etimation, we count only the modular exponentiation operation, which i the mot expenive computation among the cryptographic computation. Thi etimation i baed on the efficient imultaneou multiple exponentiation technique [19]. During the login phae, the propoed cheme require only one modular exponentiation, while the cheme in [5-6] and [8] require 2.17 modular exponentiation. Since the computation in thi phae are performed by the mart card, aving i valuable. The computational cot for the mart card can be further divided into on-line cot and off-line cot. The off-line cot mean that ome computation can be calculated during the idle time or computed by a powerful computer. The on-line computation for the propoed cheme are one hah operation and one modular multiplication compared with thoe required by the cheme in [5-6] and [8] which require one modular exponentiation and one hah operation. Note that a modular exponentiation require 1.5 q = 240 modular multiplication on average, if the generator, i.e. g, ha an order of q and q i 160 bit. The propoed cheme demand 2.5 modular exponentiation for authentication, while the cheme in [5-6] and [8] require 1.17 modular exponentiation. Our cheme require 3 p + 2 q + T for the login meage ize, wherea the cheme in [5-6] and [8] require 3 p + T. For a practical cryptoytem [20], i.e., p = 1024 bit and q = 160 bit, the communicational cot of our cheme i about 10% larger than that for the other ytem. Theorem 1 give the correctne of the propoed cheme. Theorem 3 and 5 in the next ection preent the oundne of the propoed cheme. Theorem 1. The authentication phae correctly determine whether a login meage i valid or not. Proof: In the authentication phae, checking the timetamp in tep 1 enure that the login meage i not a replay attack. In tep 2, the equation g h( r, ID ) = u r r y mod p prove that ID u ha been authorized by the CA to enter the acce erver. The equation g = r H ID u r mod p in tep 4 confirm that the login meage L i really contructed by the uer ID u. Thu, the authentication phae correctly check the login meage L. 4. ANALYSIS OF SECURITY The original ElGamal ignature cheme in [7] i well known to be exitentially forgeable. By replacing the earliet igning equation = k -1 (m - x r) mod (p - 1) with = k -1 (h(m, r) - x r) mod (p - 1), where r = g k * mod p and k, x R Z p 1, the modified cheme had been proven ecure againt the adaptively choen meage attack [21-22] under the random oracle model [23]. Conidering the limited computation capability of the mart card, the propoed cheme ue = (h(m, r)k + x r) mod q a the igning equation which ha the advantage of aving an invere computation. Baed on the work in [21-22], thi variant of the ElGamal ignature cheme (henceforth called V ignature cheme) can be proven ecure againt the adaptively choen meage attack in a rather brief way, ince the modulu i a prime q. Lemma 2. (The forking lemma) Let A denote an adverary, which i a Probabilitic Polynomial Time Turing machine given only the public data (g, y) a input. Replaying thi machine with the ame random tape and a different hah oracle,
4 with non-negligible probability, will generate two valid ignature (m, r, h(m, r), ) and (m, r, h 1 (m, r), 1 ) uch that h(m, r) h 1 (m, r), if A can find a valid ignature (m, r, h(m, r), ) with non-negligible probability [21-22]. Theorem 3. The dicrete logarithm problem can be olved in polynomial time, if the V ignature cheme i exitentially forgeable with non-negligible probability. Proof: Aume that (m, r, h(m, r), ) and (m, r, h 1 (m, r), 1 ) are two valid ignature by replaying the adverary A (the forking lemma). From thee two ignature, the following verification equation hold true. g = r h(m, r) y r = r h(m, r) g x r mod p (1) g 1 = r h 1 (m, r) y r = r h 1 (m, r) g x r mod p (2) Solving x in (1) and (2), we obtain the following expreion for the dicrete logarithm of y y, i.e., x = log g. x = [ h 1 (m, r) 1 h(m, r)] / [r h 1 (m, r) r h(m, r)] mod q (3) Becaue the dicrete logarithm of y i olvable with a non-negligible probability by replaying A, the dicrete logarithm of a random number z R G can alo be olved with a non-negligible probability. We how the detail a follow. Let u, v R Z q. Giving A the public data (g u, z g v ) a input, with non-negligible probability, A output x uch that (g u ) x = z g v. Thu, the dicrete logarithm of the random number z i calculated z uing the equation log g = u x - v. The reult contradict the intractability of the dicrete logarithm problem. Therefore, the V ignature cheme i exitential forgeable with negligible probability. Lemma 4. Knowing none of the igner ecret data, a imulator can imulate the igner of the V ignature cheme uch that the imulated ignature and the genuine ignature contructed by the igner are tatitical inditinguihable. Proof: The imulator chooe a R Z q, b R Z and calculate r = g a y b mod p, = - a r / b mod q, e = -r / b mod q. The quadruple (m, r, h(m, r), ) i an effective ignature of a meage m, if e = h(m, r). Let P(u) denote the probability ditribution of r choen by the imulator and P(i) denote the probability ditribution of r computed by the igner. Clearly, P(u) and P(i) are both uniformly ditributed over Z * p. A imilar dicuion applie to the repone. Therefore, in pite of the ignature being imulated by a imulator or truly igned by the igner, all of them are tatitical * q inditinguihable. Theorem 5. The dicrete logarithm problem can be olved in polynomial time, if the V ignature cheme i exitentially forgeable with non-negligible probability under the adaptively choen meage attack. Proof: In cae of an adaptively choen meage attack, the attacker adaptively chooe meage and ak the igning oracle to ign them. Hence, the attacker obtain a et of genuine ignature. Auming that the attacker could generate a new valid ignature from thee ignature, upplying the attacker with imulated ignature, he could alo generate a new valid ignature, becaue the attacker cannot ditinguih the imulated ignature from the genuine ignature. Thu, colluion between the attacker and the imulator could compute the dicrete logarithm of a random number z R G, by Lemma 4. Thi concluion contradict the hardne of olving the dicrete logarithm problem. Thu, the V ignature cheme i exitentially forgeable with negligible probability under the adaptively choen meage attack. Theorem 6. The propoed new cheme i ecure againt the adaptively choen meage attack. Proof: The requet meage L = {r,, T, ID u, r, } contain two ignature: 1. (ID u, r, ) and 2. ((T, ID u, r, ), r, ). The firt ignature guarantee that the uer ID u i legitimate and authorized by the CA. The econd ignature prove that the requet meage {r,, T, ID u, r, } i really preented by the uer ID u. Taking (T, ID u, r, ) a meage, L repreent a ignature iued by the uer ID u. Needle to ay, the requet meage L i not malleable even under the adaptively choen meage attack, by Theorem CONCLUSION The propoed cheme doe not merely mend the weaknee of the cheme mentioned in Section 1. The new cheme ha everal advantage over the cheme in [1-6] and [8-10]: 1. The propoed cheme i provably ecure. 2. The propoed cheme poee the property of non-repudiation. 3. The mart card require only one on-line modular multiplication and hah operation to contruct a login requet. 4. The new cheme ha the property of forward ecrecy. Among the previou cheme, only the cheme in [8] ha thi property. 5. A a reult of Theorem 6, no login meage can be counterfeited, even under the colluion of mart card holder. The acce ytem, which ha large number uer, i thu ecure. Thi advantage might be the mot important. REFERENCES
5 [1] L. Lamport, Paword authentication with inecure communication, Communication of ACM, Vol. 24, pp , [2] C. C. Chang and T. C. Wu, Remote paword authentication with mart card, IEE Proceeding-E, Vol. 138, No. 3, pp , [3] T. C. Wu, Remote login authentication cheme baed on a geometric approach, Computer Communication, Vol. 18, No. 12, pp , [4] S. J. Wang, Yet another log-in authentication uing n-dimenional contruction baed on circle property, IEEE Tranaction on Conumer Electronic, Vol. 49, No. 2, pp , [5] M. S. Hwang and L. H. Li, A new remote uer authentication cheme uing mart card, IEEE Tranaction on Conumer Electronic, Vol. 46, No. 1, pp , [6] J. J. Shen, C. W. Lin, and M. S. Hwang, A modified remote uer authentication cheme uing mart card, IEEE Tranaction on Conumer Electronic, Vol. 49, No. 2, pp , [7] T. ElGamal, A public key cryptoytem and a ignature cheme baed on dicrete logarithm, IEEE Tran. Inform. Theory, IT-31, (4), pp , [8] A. K. Awathi and S. Lal, A remote uer authentication cheme uing mart card with forward ecrecy, IEEE Tranaction on Conumer Electronic, Vol. 49, No. 4, pp , [9] H. M. Sun, An efficient remote uer authentication cheme uing mart card, IEEE Tranaction on Conumer Electronic, Vol. 46, No. 4, pp , [10] H. Y. Chien, J. K. Jan, and Y. M. Teng, An efficient and practical olution to remote authentication: Smart Card, Computer and Security, Vol. 21, No. 4, pp , [11] C. C. Chang and C. S. Laih, Correpondence--Remote paword authentication with mart card, IEE Proceeding-E, Vol. 139, No. 4, pp. 372, [12] M. S. Hwang, Cryptanalyi of a remote login authentication cheme, Computer Communication, Vol. 22, No. 8, pp , [13] F. Y. Yang and J. K. Jan, Cryptanalyi of Log-in Authentication Baed on Circle Property, IEEE Tranaction on Conumer Electronic, Vol. 50, Iue 2, to appear, [14] C. K. Chan and L. M. Cheng, Cryptanalyi of a remote uer authentication cheme uing mart card, IEEE Tranaction on Conumer Electronic, Vol. 46, No. 4, pp , [15] C. C. Chang and K. F. Hwang, Some forgery attack on a remote uer authentication cheme uing mart card, Informatic, Vol. 14, No. 3, pp , [16] K. C. Leung, L. M. Cheng, A. S. Fong, and C. K. Chan, Cryptanalyi of a modified remote uer authentication cheme uing mart card, IEEE Tranaction on Conumer Electronic, Vol. 49, No. 4, pp , [17] C. L. Hu, Security of two remote uer authentication cheme uing mart card, IEEE Tranaction on Conumer Electronic, Vol. 49, No. 4, pp , [18] S. Goldwaer, S. Micali, and R. Rivet, A digital ignature cheme ecure againt adaptive choen-meage attack, SIAM journal of computing, Vol. 17, No. 2, pp ,1988. [19] A. Meneze, P. van Oorchot, and S. Vantone, Handbook of Applied Cryptography, CRC Pre, pp , [20] A. Lentra and E. Verheul, Selecting cryptographic key ize, The Third International Workhop on Practice and Theory in Public Key Cryptography (PKC2000), LNCS 1751, pp , [21] D. Pointcheval and J. Stern, Security proof for ignature cheme, Advance in Cryptology-EUROCRYPT 96, LNCS 1070, pp , [22] D. Pointcheval and J. Stern, Security argument for digital ignature and blind ignature, Journal of Cryptology, Vol. 13, N0. 3, pp , [23] M. Bellare and P. Rogaway, Random oracle are practical: a paradigm for deigning efficient protocol, Proc. of the 1t ACM Conference on Computer and Communication Security CCS 93, ACM pre, pp , 1993.
Topic 6. Digital Signatures and Identity Based Encryption
 Topic 6. Digital Signature and Identity Baed Encryption. Security of Public-key Cryptography 2. Example of Public-key Algorithm: Diffie- Hellman Key Exchange Scheme 3. RSA Encryption and Digital Signature
Topic 6. Digital Signature and Identity Baed Encryption. Security of Public-key Cryptography 2. Example of Public-key Algorithm: Diffie- Hellman Key Exchange Scheme 3. RSA Encryption and Digital Signature
Identity-based Hierarchical Designated Decryption *
 JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 26, 243-259 (200) Identity-baed Hierarchical Deignated Decryption * SHU-HUI CHANG, CHUAN-MING LI 2 AND TZONELIH HWANG 3 Center of General Education Southern
JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 26, 243-259 (200) Identity-baed Hierarchical Deignated Decryption * SHU-HUI CHANG, CHUAN-MING LI 2 AND TZONELIH HWANG 3 Center of General Education Southern
Lecture 8: Period Finding: Simon s Problem over Z N
 Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
Clustering Methods without Given Number of Clusters
 Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Codes Correcting Two Deletions
 1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
Lecture 9: Shor s Algorithm
 Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Evolutionary Algorithms Based Fixed Order Robust Controller Design and Robustness Performance Analysis
 Proceeding of 01 4th International Conference on Machine Learning and Computing IPCSIT vol. 5 (01) (01) IACSIT Pre, Singapore Evolutionary Algorithm Baed Fixed Order Robut Controller Deign and Robutne
Proceeding of 01 4th International Conference on Machine Learning and Computing IPCSIT vol. 5 (01) (01) IACSIT Pre, Singapore Evolutionary Algorithm Baed Fixed Order Robut Controller Deign and Robutne
7.2 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 281
 72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
Memory Erasability Amplification
 Memory Eraability Amplification Jan Camenich 1, Robert R. Enderlein 1,2, and Ueli Maurer 2 1 IBM Reearch Zurich, Switzerland 2 Department of Computer Science, ETH Zürich, Switzerland Abtract. Eraable memory
Memory Eraability Amplification Jan Camenich 1, Robert R. Enderlein 1,2, and Ueli Maurer 2 1 IBM Reearch Zurich, Switzerland 2 Department of Computer Science, ETH Zürich, Switzerland Abtract. Eraable memory
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS
 CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
Shannon s Theory. Objectives
 Shannon Theory Debdeep Mukhopadhyay IIT Kharagpur Objective Undertand the definition of Perfect Secrecy Prove that a given crypto-ytem i perfectly ecured One Time Pad Entropy and it computation Ideal Cipher
Shannon Theory Debdeep Mukhopadhyay IIT Kharagpur Objective Undertand the definition of Perfect Secrecy Prove that a given crypto-ytem i perfectly ecured One Time Pad Entropy and it computation Ideal Cipher
A Study on Simulating Convolutional Codes and Turbo Codes
 A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
A BATCH-ARRIVAL QUEUE WITH MULTIPLE SERVERS AND FUZZY PARAMETERS: PARAMETRIC PROGRAMMING APPROACH
 Mathematical and Computational Application Vol. 11 No. pp. 181-191 006. Aociation for Scientific Reearch A BATCH-ARRIVA QEE WITH MTIPE SERVERS AND FZZY PARAMETERS: PARAMETRIC PROGRAMMING APPROACH Jau-Chuan
Mathematical and Computational Application Vol. 11 No. pp. 181-191 006. Aociation for Scientific Reearch A BATCH-ARRIVA QEE WITH MTIPE SERVERS AND FZZY PARAMETERS: PARAMETRIC PROGRAMMING APPROACH Jau-Chuan
Social Studies 201 Notes for November 14, 2003
 1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
Hybrid Projective Dislocated Synchronization of Liu Chaotic System Based on Parameters Identification
 www.ccenet.org/ma Modern Applied Science Vol. 6, No. ; February Hybrid Projective Dilocated Synchronization of Liu Chaotic Sytem Baed on Parameter Identification Yanfei Chen College of Science, Guilin
www.ccenet.org/ma Modern Applied Science Vol. 6, No. ; February Hybrid Projective Dilocated Synchronization of Liu Chaotic Sytem Baed on Parameter Identification Yanfei Chen College of Science, Guilin
Optimizing Cost-sensitive Trust-negotiation Protocols
 Optimizing Cot-enitive Trut-negotiation Protocol Weifeng Chen, Lori Clarke, Jim Kuroe, Don Towley Department of Computer Science Univerity of Maachuett, Amhert {chenwf, clarke, kuroe, towley}@c.uma.edu
Optimizing Cot-enitive Trut-negotiation Protocol Weifeng Chen, Lori Clarke, Jim Kuroe, Don Towley Department of Computer Science Univerity of Maachuett, Amhert {chenwf, clarke, kuroe, towley}@c.uma.edu
Lecture 21. The Lovasz splitting-off lemma Topics in Combinatorial Optimization April 29th, 2004
 18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
Gain and Phase Margins Based Delay Dependent Stability Analysis of Two- Area LFC System with Communication Delays
 Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
A Simplified Methodology for the Synthesis of Adaptive Flight Control Systems
 A Simplified Methodology for the Synthei of Adaptive Flight Control Sytem J.ROUSHANIAN, F.NADJAFI Department of Mechanical Engineering KNT Univerity of Technology 3Mirdamad St. Tehran IRAN Abtract- A implified
A Simplified Methodology for the Synthei of Adaptive Flight Control Sytem J.ROUSHANIAN, F.NADJAFI Department of Mechanical Engineering KNT Univerity of Technology 3Mirdamad St. Tehran IRAN Abtract- A implified
Optimal Coordination of Samples in Business Surveys
 Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
CHAPTER 4 DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL
 98 CHAPTER DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL INTRODUCTION The deign of ytem uing tate pace model for the deign i called a modern control deign and it i
98 CHAPTER DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL INTRODUCTION The deign of ytem uing tate pace model for the deign i called a modern control deign and it i
Design By Emulation (Indirect Method)
 Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
Bogoliubov Transformation in Classical Mechanics
 Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Simple Observer Based Synchronization of Lorenz System with Parametric Uncertainty
 IOSR Journal of Electrical and Electronic Engineering (IOSR-JEEE) ISSN: 78-676Volume, Iue 6 (Nov. - Dec. 0), PP 4-0 Simple Oberver Baed Synchronization of Lorenz Sytem with Parametric Uncertainty Manih
IOSR Journal of Electrical and Electronic Engineering (IOSR-JEEE) ISSN: 78-676Volume, Iue 6 (Nov. - Dec. 0), PP 4-0 Simple Oberver Baed Synchronization of Lorenz Sytem with Parametric Uncertainty Manih
Fast explicit formulae for genus 2 hyperelliptic curves using projective coordinates
 Fat explicit formulae for genu hyperelliptic curve uing projective coordinate Thoma Wollinger Ecrypt embedded ecurity GmbH twollinger@ecryptde Abtract Thi contribution propoe a modification of method of
Fat explicit formulae for genu hyperelliptic curve uing projective coordinate Thoma Wollinger Ecrypt embedded ecurity GmbH twollinger@ecryptde Abtract Thi contribution propoe a modification of method of
Chapter 2 Sampling and Quantization. In order to investigate sampling and quantization, the difference between analog
 Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS. Volker Ziegler Technische Universität Graz, Austria
 GLASNIK MATEMATIČKI Vol. 1(61)(006), 9 30 ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS Volker Ziegler Techniche Univerität Graz, Autria Abtract. We conider the parameterized Thue
GLASNIK MATEMATIČKI Vol. 1(61)(006), 9 30 ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS Volker Ziegler Techniche Univerität Graz, Autria Abtract. We conider the parameterized Thue
Hardware Implementation of Canonic Signed Digit Recoding
 IOSR Journal of VLSI and Signal Proceing (IOSR-JVSP) Volume 6, Iue 2, Ver. I (Mar. -Apr. 2016), PP 11-15 e-issn: 2319 4200, p-issn No. : 2319 4197 www.iorjournal.org Hardware Implementation of Canonic
IOSR Journal of VLSI and Signal Proceing (IOSR-JVSP) Volume 6, Iue 2, Ver. I (Mar. -Apr. 2016), PP 11-15 e-issn: 2319 4200, p-issn No. : 2319 4197 www.iorjournal.org Hardware Implementation of Canonic
Preemptive scheduling on a small number of hierarchical machines
 Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
One Class of Splitting Iterative Schemes
 One Cla of Splitting Iterative Scheme v Ciegi and V. Pakalnytė Vilniu Gedimina Technical Univerity Saulėtekio al. 11, 2054, Vilniu, Lithuania rc@fm.vtu.lt Abtract. Thi paper deal with the tability analyi
One Cla of Splitting Iterative Scheme v Ciegi and V. Pakalnytė Vilniu Gedimina Technical Univerity Saulėtekio al. 11, 2054, Vilniu, Lithuania rc@fm.vtu.lt Abtract. Thi paper deal with the tability analyi
Introduction to Laplace Transform Techniques in Circuit Analysis
 Unit 6 Introduction to Laplace Tranform Technique in Circuit Analyi In thi unit we conider the application of Laplace Tranform to circuit analyi. A relevant dicuion of the one-ided Laplace tranform i found
Unit 6 Introduction to Laplace Tranform Technique in Circuit Analyi In thi unit we conider the application of Laplace Tranform to circuit analyi. A relevant dicuion of the one-ided Laplace tranform i found
The Hassenpflug Matrix Tensor Notation
 The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
Microblog Hot Spot Mining Based on PAM Probabilistic Topic Model
 MATEC Web of Conference 22, 01062 ( 2015) DOI: 10.1051/ matecconf/ 2015220106 2 C Owned by the author, publihed by EDP Science, 2015 Microblog Hot Spot Mining Baed on PAM Probabilitic Topic Model Yaxin
MATEC Web of Conference 22, 01062 ( 2015) DOI: 10.1051/ matecconf/ 2015220106 2 C Owned by the author, publihed by EDP Science, 2015 Microblog Hot Spot Mining Baed on PAM Probabilitic Topic Model Yaxin
REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS. Logic and Applications 2015 (LAP 2015) September 21-25, 2015, Dubrovnik, Croatia
 REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS SMILE MARKOVSKI Faculty of Computer Science and Engineering, S Ciryl and Methodiu Univerity in Skopje, MACEDONIA mile.markovki@gmail.com Logic
REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS SMILE MARKOVSKI Faculty of Computer Science and Engineering, S Ciryl and Methodiu Univerity in Skopje, MACEDONIA mile.markovki@gmail.com Logic
A Constraint Propagation Algorithm for Determining the Stability Margin. The paper addresses the stability margin assessment for linear systems
 A Contraint Propagation Algorithm for Determining the Stability Margin of Linear Parameter Circuit and Sytem Lubomir Kolev and Simona Filipova-Petrakieva Abtract The paper addree the tability margin aement
A Contraint Propagation Algorithm for Determining the Stability Margin of Linear Parameter Circuit and Sytem Lubomir Kolev and Simona Filipova-Petrakieva Abtract The paper addree the tability margin aement
An Inequality for Nonnegative Matrices and the Inverse Eigenvalue Problem
 An Inequality for Nonnegative Matrice and the Invere Eigenvalue Problem Robert Ream Program in Mathematical Science The Univerity of Texa at Dalla Box 83688, Richardon, Texa 7583-688 Abtract We preent
An Inequality for Nonnegative Matrice and the Invere Eigenvalue Problem Robert Ream Program in Mathematical Science The Univerity of Texa at Dalla Box 83688, Richardon, Texa 7583-688 Abtract We preent
Lqr Based Load Frequency Control By Introducing Demand Response
 Lqr Baed Load Frequency Control By Introducing Demand Repone P.Venkateh Department of Electrical and Electronic Engineering, V.R iddhartha Engineering College, Vijayawada, AP, 520007, India K.rikanth Department
Lqr Baed Load Frequency Control By Introducing Demand Repone P.Venkateh Department of Electrical and Electronic Engineering, V.R iddhartha Engineering College, Vijayawada, AP, 520007, India K.rikanth Department
Beyond Cut-Set Bounds - The Approximate Capacity of D2D Networks
 Beyond Cut-Set Bound - The Approximate Capacity of DD Network Avik Sengupta Hume Center for National Security and Technology Department of Electrical and Computer Engineering Virginia Tech, Blackburg,
Beyond Cut-Set Bound - The Approximate Capacity of DD Network Avik Sengupta Hume Center for National Security and Technology Department of Electrical and Computer Engineering Virginia Tech, Blackburg,
White Rose Research Online URL for this paper: Version: Accepted Version
 Thi i a repoitory copy of Identification of nonlinear ytem with non-peritent excitation uing an iterative forward orthogonal leat quare regreion algorithm. White Roe Reearch Online URL for thi paper: http://eprint.whiteroe.ac.uk/107314/
Thi i a repoitory copy of Identification of nonlinear ytem with non-peritent excitation uing an iterative forward orthogonal leat quare regreion algorithm. White Roe Reearch Online URL for thi paper: http://eprint.whiteroe.ac.uk/107314/
Multicast Network Coding and Field Sizes
 Multicat Network Coding and Field Size Qifu (Tyler) Sun, Xunrui Yin, Zongpeng Li, and Keping Long Intitute of Advanced Networking Technology and New Service, Univerity of Science and Technology Beijing,
Multicat Network Coding and Field Size Qifu (Tyler) Sun, Xunrui Yin, Zongpeng Li, and Keping Long Intitute of Advanced Networking Technology and New Service, Univerity of Science and Technology Beijing,
Unavoidable Cycles in Polynomial-Based Time-Invariant LDPC Convolutional Codes
 European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS
 ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS VOLKER ZIEGLER Abtract We conider the parameterized Thue equation X X 3 Y (ab + (a + bx Y abxy 3 + a b Y = ±1, where a, b 1 Z uch that
ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS VOLKER ZIEGLER Abtract We conider the parameterized Thue equation X X 3 Y (ab + (a + bx Y abxy 3 + a b Y = ±1, where a, b 1 Z uch that
Problem Set 8 Solutions
 Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD
 SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
Jan Purczyński, Kamila Bednarz-Okrzyńska Estimation of the shape parameter of GED distribution for a small sample size
 Jan Purczyńki, Kamila Bednarz-Okrzyńka Etimation of the hape parameter of GED ditribution for a mall ample ize Folia Oeconomica Stetinenia 4()/, 35-46 04 Folia Oeconomica Stetinenia DOI: 0.478/foli-04-003
Jan Purczyńki, Kamila Bednarz-Okrzyńka Etimation of the hape parameter of GED ditribution for a mall ample ize Folia Oeconomica Stetinenia 4()/, 35-46 04 Folia Oeconomica Stetinenia DOI: 0.478/foli-04-003
[Saxena, 2(9): September, 2013] ISSN: Impact Factor: INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY
![[Saxena, 2(9): September, 2013] ISSN: Impact Factor: INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY [Saxena, 2(9): September, 2013] ISSN: Impact Factor: INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY](/thumbs/90/102186320.jpg) [Saena, (9): September, 0] ISSN: 77-9655 Impact Factor:.85 IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY Contant Stre Accelerated Life Teting Uing Rayleigh Geometric Proce
[Saena, (9): September, 0] ISSN: 77-9655 Impact Factor:.85 IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY Contant Stre Accelerated Life Teting Uing Rayleigh Geometric Proce
5.5 Application of Frequency Response: Signal Filters
 44 Dynamic Sytem Second order lowpa filter having tranfer function H()=H ()H () u H () H () y Firt order lowpa filter Figure 5.5: Contruction of a econd order low-pa filter by combining two firt order
44 Dynamic Sytem Second order lowpa filter having tranfer function H()=H ()H () u H () H () y Firt order lowpa filter Figure 5.5: Contruction of a econd order low-pa filter by combining two firt order
Lecture 7: Testing Distributions
 CSE 5: Sublinear (and Streaming) Algorithm Spring 014 Lecture 7: Teting Ditribution April 1, 014 Lecturer: Paul Beame Scribe: Paul Beame 1 Teting Uniformity of Ditribution We return today to property teting
CSE 5: Sublinear (and Streaming) Algorithm Spring 014 Lecture 7: Teting Ditribution April 1, 014 Lecturer: Paul Beame Scribe: Paul Beame 1 Teting Uniformity of Ditribution We return today to property teting
On the Big Gap Between p and q in DSA
 On the Big Gap Between p and in DSA Zhengjun Cao Department of Mathematics, Shanghai University, Shanghai, China, 200444. caozhj@shu.edu.cn Abstract We introduce a message attack against DSA and show that
On the Big Gap Between p and in DSA Zhengjun Cao Department of Mathematics, Shanghai University, Shanghai, China, 200444. caozhj@shu.edu.cn Abstract We introduce a message attack against DSA and show that
Cryptography and Security Final Exam
 Cryptography and Security Final Exa Solution Serge Vaudenay 17.1.2017 duration: 3h no docuent allowed, except one 2-ided heet of handwritten note a pocket calculator i allowed counication device are not
Cryptography and Security Final Exa Solution Serge Vaudenay 17.1.2017 duration: 3h no docuent allowed, except one 2-ided heet of handwritten note a pocket calculator i allowed counication device are not
On the Isomorphism of Fractional Factorial Designs 1
 journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
By Xiaoquan Wen and Matthew Stephens University of Michigan and University of Chicago
 Submitted to the Annal of Applied Statitic SUPPLEMENTARY APPENDIX TO BAYESIAN METHODS FOR GENETIC ASSOCIATION ANALYSIS WITH HETEROGENEOUS SUBGROUPS: FROM META-ANALYSES TO GENE-ENVIRONMENT INTERACTIONS
Submitted to the Annal of Applied Statitic SUPPLEMENTARY APPENDIX TO BAYESIAN METHODS FOR GENETIC ASSOCIATION ANALYSIS WITH HETEROGENEOUS SUBGROUPS: FROM META-ANALYSES TO GENE-ENVIRONMENT INTERACTIONS
1. The F-test for Equality of Two Variances
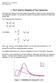 . The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
. The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
FUNDAMENTALS OF POWER SYSTEMS
 1 FUNDAMENTALS OF POWER SYSTEMS 1 Chapter FUNDAMENTALS OF POWER SYSTEMS INTRODUCTION The three baic element of electrical engineering are reitor, inductor and capacitor. The reitor conume ohmic or diipative
1 FUNDAMENTALS OF POWER SYSTEMS 1 Chapter FUNDAMENTALS OF POWER SYSTEMS INTRODUCTION The three baic element of electrical engineering are reitor, inductor and capacitor. The reitor conume ohmic or diipative
Control Systems Analysis and Design by the Root-Locus Method
 6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
Fermi Distribution Function. n(e) T = 0 T > 0 E F
 LECTURE 3 Maxwell{Boltzmann, Fermi, and Boe Statitic Suppoe we have a ga of N identical point particle in a box ofvolume V. When we ay \ga", we mean that the particle are not interacting with one another.
LECTURE 3 Maxwell{Boltzmann, Fermi, and Boe Statitic Suppoe we have a ga of N identical point particle in a box ofvolume V. When we ay \ga", we mean that the particle are not interacting with one another.
ON TESTING THE DIVISIBILITY OF LACUNARY POLYNOMIALS BY CYCLOTOMIC POLYNOMIALS Michael Filaseta* and Andrzej Schinzel 1. Introduction and the Main Theo
 ON TESTING THE DIVISIBILITY OF LACUNARY POLYNOMIALS BY CYCLOTOMIC POLYNOMIALS Michael Filaeta* and Andrzej Schinzel 1. Introduction and the Main Theorem Thi note decribe an algorithm for determining whether
ON TESTING THE DIVISIBILITY OF LACUNARY POLYNOMIALS BY CYCLOTOMIC POLYNOMIALS Michael Filaeta* and Andrzej Schinzel 1. Introduction and the Main Theorem Thi note decribe an algorithm for determining whether
ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION. Xiaoqun Wang
 Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
EME : extending EME to handle arbitrary-length messages with associated data
 EME : extending EME to handle arbitrary-length meage with aociated data (Preliminary Report) Shai Halevi May 27, 2004 Abtract Thi work decribe a mode of operation, EME, that turn a regular block cipher
EME : extending EME to handle arbitrary-length meage with aociated data (Preliminary Report) Shai Halevi May 27, 2004 Abtract Thi work decribe a mode of operation, EME, that turn a regular block cipher
The machines in the exercise work as follows:
 Tik-79.148 Spring 2001 Introduction to Theoretical Computer Science Tutorial 9 Solution to Demontration Exercie 4. Contructing a complex Turing machine can be very laboriou. With the help of machine chema
Tik-79.148 Spring 2001 Introduction to Theoretical Computer Science Tutorial 9 Solution to Demontration Exercie 4. Contructing a complex Turing machine can be very laboriou. With the help of machine chema
Statistics and Data Analysis
 Simulation of Propenity Scoring Method Dee H. Wu, Ph.D, David M. Thompon, Ph.D., David Bard, Ph.D. Univerity of Oklahoma Health Science Center, Oklahoma City, OK ABSTRACT In certain clinical trial or obervational
Simulation of Propenity Scoring Method Dee H. Wu, Ph.D, David M. Thompon, Ph.D., David Bard, Ph.D. Univerity of Oklahoma Health Science Center, Oklahoma City, OK ABSTRACT In certain clinical trial or obervational
Chapter 4. The Laplace Transform Method
 Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
Jul 4, 2005 turbo_code_primer Revision 0.0. Turbo Code Primer
 Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Flag-transitive non-symmetric 2-designs with (r, λ) = 1 and alternating socle
 Flag-tranitive non-ymmetric -deign with (r, λ = 1 and alternating ocle Shenglin Zhou, Yajie Wang School of Mathematic South China Univerity of Technology Guangzhou, Guangdong 510640, P. R. China lzhou@cut.edu.cn
Flag-tranitive non-ymmetric -deign with (r, λ = 1 and alternating ocle Shenglin Zhou, Yajie Wang School of Mathematic South China Univerity of Technology Guangzhou, Guangdong 510640, P. R. China lzhou@cut.edu.cn
Theoretical Computer Science. Optimal algorithms for online scheduling with bounded rearrangement at the end
 Theoretical Computer Science 4 (0) 669 678 Content lit available at SciVere ScienceDirect Theoretical Computer Science journal homepage: www.elevier.com/locate/tc Optimal algorithm for online cheduling
Theoretical Computer Science 4 (0) 669 678 Content lit available at SciVere ScienceDirect Theoretical Computer Science journal homepage: www.elevier.com/locate/tc Optimal algorithm for online cheduling
Lecture 17: Analytic Functions and Integrals (See Chapter 14 in Boas)
 Lecture 7: Analytic Function and Integral (See Chapter 4 in Boa) Thi i a good point to take a brief detour and expand on our previou dicuion of complex variable and complex function of complex variable.
Lecture 7: Analytic Function and Integral (See Chapter 4 in Boa) Thi i a good point to take a brief detour and expand on our previou dicuion of complex variable and complex function of complex variable.
SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lectures 41-48)
 Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Control of Delayed Integrating Processes Using Two Feedback Controllers R MS Approach
 Proceeding of the 7th WSEAS International Conference on SYSTEM SCIENCE and SIMULATION in ENGINEERING (ICOSSSE '8) Control of Delayed Integrating Procee Uing Two Feedback Controller R MS Approach LIBOR
Proceeding of the 7th WSEAS International Conference on SYSTEM SCIENCE and SIMULATION in ENGINEERING (ICOSSSE '8) Control of Delayed Integrating Procee Uing Two Feedback Controller R MS Approach LIBOR
Acceptance sampling uses sampling procedure to determine whether to
 DOI: 0.545/mji.203.20 Bayeian Repetitive Deferred Sampling Plan Indexed Through Relative Slope K.K. Sureh, S. Umamahewari and K. Pradeepa Veerakumari Department of Statitic, Bharathiar Univerity, Coimbatore,
DOI: 0.545/mji.203.20 Bayeian Repetitive Deferred Sampling Plan Indexed Through Relative Slope K.K. Sureh, S. Umamahewari and K. Pradeepa Veerakumari Department of Statitic, Bharathiar Univerity, Coimbatore,
arxiv: v1 [math.mg] 25 Aug 2011
![arxiv: v1 [math.mg] 25 Aug 2011 arxiv: v1 [math.mg] 25 Aug 2011](/thumbs/72/67862976.jpg) ABSORBING ANGLES, STEINER MINIMAL TREES, AND ANTIPODALITY HORST MARTINI, KONRAD J. SWANEPOEL, AND P. OLOFF DE WET arxiv:08.5046v [math.mg] 25 Aug 20 Abtract. We give a new proof that a tar {op i : i =,...,
ABSORBING ANGLES, STEINER MINIMAL TREES, AND ANTIPODALITY HORST MARTINI, KONRAD J. SWANEPOEL, AND P. OLOFF DE WET arxiv:08.5046v [math.mg] 25 Aug 20 Abtract. We give a new proof that a tar {op i : i =,...,
LOW ORDER MIMO CONTROLLER DESIGN FOR AN ENGINE DISTURBANCE REJECTION PROBLEM. P.Dickinson, A.T.Shenton
 LOW ORDER MIMO CONTROLLER DESIGN FOR AN ENGINE DISTURBANCE REJECTION PROBLEM P.Dickinon, A.T.Shenton Department of Engineering, The Univerity of Liverpool, Liverpool L69 3GH, UK Abtract: Thi paper compare
LOW ORDER MIMO CONTROLLER DESIGN FOR AN ENGINE DISTURBANCE REJECTION PROBLEM P.Dickinon, A.T.Shenton Department of Engineering, The Univerity of Liverpool, Liverpool L69 3GH, UK Abtract: Thi paper compare
A FUNCTIONAL BAYESIAN METHOD FOR THE SOLUTION OF INVERSE PROBLEMS WITH SPATIO-TEMPORAL PARAMETERS AUTHORS: CORRESPONDENCE: ABSTRACT
 A FUNCTIONAL BAYESIAN METHOD FOR THE SOLUTION OF INVERSE PROBLEMS WITH SPATIO-TEMPORAL PARAMETERS AUTHORS: Zenon Medina-Cetina International Centre for Geohazard / Norwegian Geotechnical Intitute Roger
A FUNCTIONAL BAYESIAN METHOD FOR THE SOLUTION OF INVERSE PROBLEMS WITH SPATIO-TEMPORAL PARAMETERS AUTHORS: Zenon Medina-Cetina International Centre for Geohazard / Norwegian Geotechnical Intitute Roger
arxiv: v1 [math.ac] 30 Nov 2012
![arxiv: v1 [math.ac] 30 Nov 2012 arxiv: v1 [math.ac] 30 Nov 2012](/thumbs/89/99380025.jpg) ON MODULAR INVARIANTS OF A VECTOR AND A COVECTOR YIN CHEN arxiv:73v [mathac 3 Nov Abtract Let S L (F q be the pecial linear group over a finite field F q, V be the -dimenional natural repreentation of
ON MODULAR INVARIANTS OF A VECTOR AND A COVECTOR YIN CHEN arxiv:73v [mathac 3 Nov Abtract Let S L (F q be the pecial linear group over a finite field F q, V be the -dimenional natural repreentation of
Computers and Mathematics with Applications. Sharp algebraic periodicity conditions for linear higher order
 Computer and Mathematic with Application 64 (2012) 2262 2274 Content lit available at SciVere ScienceDirect Computer and Mathematic with Application journal homepage: wwweleviercom/locate/camwa Sharp algebraic
Computer and Mathematic with Application 64 (2012) 2262 2274 Content lit available at SciVere ScienceDirect Computer and Mathematic with Application journal homepage: wwweleviercom/locate/camwa Sharp algebraic
S_LOOP: SINGLE-LOOP FEEDBACK CONTROL SYSTEM ANALYSIS
 S_LOOP: SINGLE-LOOP FEEDBACK CONTROL SYSTEM ANALYSIS by Michelle Gretzinger, Daniel Zyngier and Thoma Marlin INTRODUCTION One of the challenge to the engineer learning proce control i relating theoretical
S_LOOP: SINGLE-LOOP FEEDBACK CONTROL SYSTEM ANALYSIS by Michelle Gretzinger, Daniel Zyngier and Thoma Marlin INTRODUCTION One of the challenge to the engineer learning proce control i relating theoretical
MATEMATIK Datum: Tid: eftermiddag. A.Heintz Telefonvakt: Anders Martinsson Tel.:
 MATEMATIK Datum: 20-08-25 Tid: eftermiddag GU, Chalmer Hjälpmedel: inga A.Heintz Telefonvakt: Ander Martinon Tel.: 073-07926. Löningar till tenta i ODE och matematik modellering, MMG5, MVE6. Define what
MATEMATIK Datum: 20-08-25 Tid: eftermiddag GU, Chalmer Hjälpmedel: inga A.Heintz Telefonvakt: Ander Martinon Tel.: 073-07926. Löningar till tenta i ODE och matematik modellering, MMG5, MVE6. Define what
Security Proofs for Signature Schemes. Ecole Normale Superieure. 45, rue d'ulm Paris Cedex 05
 Security Proofs for Signature Schemes David Pointcheval David.Pointcheval@ens.fr Jacques Stern Jacques.Stern@ens.fr Ecole Normale Superieure Laboratoire d'informatique 45, rue d'ulm 75230 Paris Cedex 05
Security Proofs for Signature Schemes David Pointcheval David.Pointcheval@ens.fr Jacques Stern Jacques.Stern@ens.fr Ecole Normale Superieure Laboratoire d'informatique 45, rue d'ulm 75230 Paris Cedex 05
CDMA Signature Sequences with Low Peak-to-Average-Power Ratio via Alternating Projection
 CDMA Signature Sequence with Low Peak-to-Average-Power Ratio via Alternating Projection Joel A Tropp Int for Comp Engr and Sci (ICES) The Univerity of Texa at Autin 1 Univerity Station C0200 Autin, TX
CDMA Signature Sequence with Low Peak-to-Average-Power Ratio via Alternating Projection Joel A Tropp Int for Comp Engr and Sci (ICES) The Univerity of Texa at Autin 1 Univerity Station C0200 Autin, TX
Online Parallel Scheduling of Non-uniform Tasks: Trading Failures for Energy
 Online Parallel Scheduling of Non-uniform Tak: Trading Failure for Energy Antonio Fernández Anta a, Chryi Georgiou b, Dariuz R. Kowalki c, Elli Zavou a,d,1 a Intitute IMDEA Network b Univerity of Cypru
Online Parallel Scheduling of Non-uniform Tak: Trading Failure for Energy Antonio Fernández Anta a, Chryi Georgiou b, Dariuz R. Kowalki c, Elli Zavou a,d,1 a Intitute IMDEA Network b Univerity of Cypru
Physics 741 Graduate Quantum Mechanics 1 Solutions to Final Exam, Fall 2014
 Phyic 7 Graduate Quantum Mechanic Solution to inal Eam all 0 Each quetion i worth 5 point with point for each part marked eparately Some poibly ueful formula appear at the end of the tet In four dimenion
Phyic 7 Graduate Quantum Mechanic Solution to inal Eam all 0 Each quetion i worth 5 point with point for each part marked eparately Some poibly ueful formula appear at the end of the tet In four dimenion
Exploiting Transformations of the Galois Configuration to Improve Guess-and-Determine Attacks on NFSRs
 Exploiting Tranformation of the Galoi Configuration to Improve Gue-and-Determine Attack on NFSR Gefei Li, Yuval Yarom, and Damith C. Ranainghe Univerity of Adelaide, Adelaide, South Autralia, Autralia
Exploiting Tranformation of the Galoi Configuration to Improve Gue-and-Determine Attack on NFSR Gefei Li, Yuval Yarom, and Damith C. Ranainghe Univerity of Adelaide, Adelaide, South Autralia, Autralia
List coloring hypergraphs
 Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
IEOR 3106: Fall 2013, Professor Whitt Topics for Discussion: Tuesday, November 19 Alternating Renewal Processes and The Renewal Equation
 IEOR 316: Fall 213, Profeor Whitt Topic for Dicuion: Tueday, November 19 Alternating Renewal Procee and The Renewal Equation 1 Alternating Renewal Procee An alternating renewal proce alternate between
IEOR 316: Fall 213, Profeor Whitt Topic for Dicuion: Tueday, November 19 Alternating Renewal Procee and The Renewal Equation 1 Alternating Renewal Procee An alternating renewal proce alternate between
Digital Control System
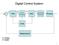 Digital Control Sytem - A D D A Micro ADC DAC Proceor Correction Element Proce Clock Meaurement A: Analog D: Digital Continuou Controller and Digital Control Rt - c Plant yt Continuou Controller Digital
Digital Control Sytem - A D D A Micro ADC DAC Proceor Correction Element Proce Clock Meaurement A: Analog D: Digital Continuou Controller and Digital Control Rt - c Plant yt Continuou Controller Digital
Chapter 4: Applications of Fourier Representations. Chih-Wei Liu
 Chapter 4: Application of Fourier Repreentation Chih-Wei Liu Outline Introduction Fourier ranform of Periodic Signal Convolution/Multiplication with Non-Periodic Signal Fourier ranform of Dicrete-ime Signal
Chapter 4: Application of Fourier Repreentation Chih-Wei Liu Outline Introduction Fourier ranform of Periodic Signal Convolution/Multiplication with Non-Periodic Signal Fourier ranform of Dicrete-ime Signal
Suggested Answers To Exercises. estimates variability in a sampling distribution of random means. About 68% of means fall
 Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Proactive Serving Decreases User Delay Exponentially: The Light-tailed Service Time Case
 Proactive Serving Decreae Uer Delay Exponentially: The Light-tailed Service Time Cae Shaoquan Zhang, Longbo Huang, Minghua Chen, and Xin Liu Abtract In online ervice ytem, the delay experienced by uer
Proactive Serving Decreae Uer Delay Exponentially: The Light-tailed Service Time Cae Shaoquan Zhang, Longbo Huang, Minghua Chen, and Xin Liu Abtract In online ervice ytem, the delay experienced by uer
Electronic Theses and Dissertations
 Eat Tenneee State Univerity Digital Common @ Eat Tenneee State Univerity Electronic Thee and Diertation Student Work 5-208 Vector Partition Jennifer French Eat Tenneee State Univerity Follow thi and additional
Eat Tenneee State Univerity Digital Common @ Eat Tenneee State Univerity Electronic Thee and Diertation Student Work 5-208 Vector Partition Jennifer French Eat Tenneee State Univerity Follow thi and additional
Social Studies 201 Notes for March 18, 2005
 1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
Convex Hulls of Curves Sam Burton
 Convex Hull of Curve Sam Burton 1 Introduction Thi paper will primarily be concerned with determining the face of convex hull of curve of the form C = {(t, t a, t b ) t [ 1, 1]}, a < b N in R 3. We hall
Convex Hull of Curve Sam Burton 1 Introduction Thi paper will primarily be concerned with determining the face of convex hull of curve of the form C = {(t, t a, t b ) t [ 1, 1]}, a < b N in R 3. We hall
New Variant of ElGamal Signature Scheme
 Int. J. Contemp. Math. Sciences, Vol. 5, 2010, no. 34, 1653-1662 New Variant of ElGamal Signature Scheme Omar Khadir Department of Mathematics Faculty of Science and Technology University of Hassan II-Mohammedia,
Int. J. Contemp. Math. Sciences, Vol. 5, 2010, no. 34, 1653-1662 New Variant of ElGamal Signature Scheme Omar Khadir Department of Mathematics Faculty of Science and Technology University of Hassan II-Mohammedia,
SOME RESULTS ON INFINITE POWER TOWERS
 NNTDM 16 2010) 3, 18-24 SOME RESULTS ON INFINITE POWER TOWERS Mladen Vailev - Miana 5, V. Hugo Str., Sofia 1124, Bulgaria E-mail:miana@abv.bg Abtract To my friend Kratyu Gumnerov In the paper the infinite
NNTDM 16 2010) 3, 18-24 SOME RESULTS ON INFINITE POWER TOWERS Mladen Vailev - Miana 5, V. Hugo Str., Sofia 1124, Bulgaria E-mail:miana@abv.bg Abtract To my friend Kratyu Gumnerov In the paper the infinite
Avoiding Forbidden Submatrices by Row Deletions
 Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Reliability Analysis of Embedded System with Different Modes of Failure Emphasizing Reboot Delay
 International Journal of Applied Science and Engineering 3., 4: 449-47 Reliability Analyi of Embedded Sytem with Different Mode of Failure Emphaizing Reboot Delay Deepak Kumar* and S. B. Singh Department
International Journal of Applied Science and Engineering 3., 4: 449-47 Reliability Analyi of Embedded Sytem with Different Mode of Failure Emphaizing Reboot Delay Deepak Kumar* and S. B. Singh Department
Stochastic Optimization with Inequality Constraints Using Simultaneous Perturbations and Penalty Functions
 Stochatic Optimization with Inequality Contraint Uing Simultaneou Perturbation and Penalty Function I-Jeng Wang* and Jame C. Spall** The John Hopkin Univerity Applied Phyic Laboratory 11100 John Hopkin
Stochatic Optimization with Inequality Contraint Uing Simultaneou Perturbation and Penalty Function I-Jeng Wang* and Jame C. Spall** The John Hopkin Univerity Applied Phyic Laboratory 11100 John Hopkin
Lecture 16 Chiu Yuen Koo Nikolai Yakovenko. 1 Digital Signature Schemes. CMSC 858K Advanced Topics in Cryptography March 18, 2004
 CMSC 858K Advanced Topics in Cryptography March 18, 2004 Lecturer: Jonathan Katz Lecture 16 Scribe(s): Chiu Yuen Koo Nikolai Yakovenko Jeffrey Blank 1 Digital Signature Schemes In this lecture, we introduce
CMSC 858K Advanced Topics in Cryptography March 18, 2004 Lecturer: Jonathan Katz Lecture 16 Scribe(s): Chiu Yuen Koo Nikolai Yakovenko Jeffrey Blank 1 Digital Signature Schemes In this lecture, we introduce
Multi Constrained Optimization model of Supply Chain Based on Intelligent Algorithm Han Juan School of Management Shanghai University
 5th nternational Conference on Advanced Material and Computer cience (CAMC 206) Multi Contrained Optimization model of upply Chain Baed on ntelligent Algorithm Han Juan chool of Management hanghai Univerity
5th nternational Conference on Advanced Material and Computer cience (CAMC 206) Multi Contrained Optimization model of upply Chain Baed on ntelligent Algorithm Han Juan chool of Management hanghai Univerity
Sampling and the Discrete Fourier Transform
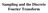 Sampling and the Dicrete Fourier Tranform Sampling Method Sampling i mot commonly done with two device, the ample-and-hold (S/H) and the analog-to-digital-converter (ADC) The S/H acquire a CT ignal at
Sampling and the Dicrete Fourier Tranform Sampling Method Sampling i mot commonly done with two device, the ample-and-hold (S/H) and the analog-to-digital-converter (ADC) The S/H acquire a CT ignal at
Analysis of Step Response, Impulse and Ramp Response in the Continuous Stirred Tank Reactor System
 ISSN: 454-50 Volume 0 - Iue 05 May 07 PP. 7-78 Analyi of Step Repone, Impule and Ramp Repone in the ontinuou Stirred Tank Reactor Sytem * Zohreh Khohraftar, Pirouz Derakhhi, (Department of hemitry, Science
ISSN: 454-50 Volume 0 - Iue 05 May 07 PP. 7-78 Analyi of Step Repone, Impule and Ramp Repone in the ontinuou Stirred Tank Reactor Sytem * Zohreh Khohraftar, Pirouz Derakhhi, (Department of hemitry, Science
Finding the location of switched capacitor banks in distribution systems based on wavelet transform
 UPEC00 3t Aug - 3rd Sept 00 Finding the location of witched capacitor bank in ditribution ytem baed on wavelet tranform Bahram nohad Shahid Chamran Univerity in Ahvaz bahramnohad@yahoo.com Mehrdad keramatzadeh
UPEC00 3t Aug - 3rd Sept 00 Finding the location of witched capacitor bank in ditribution ytem baed on wavelet tranform Bahram nohad Shahid Chamran Univerity in Ahvaz bahramnohad@yahoo.com Mehrdad keramatzadeh
