Exploiting Transformations of the Galois Configuration to Improve Guess-and-Determine Attacks on NFSRs
|
|
|
- Anne Rose
- 5 years ago
- Views:
Transcription
1 Exploiting Tranformation of the Galoi Configuration to Improve Gue-and-Determine Attack on NFSR Gefei Li, Yuval Yarom, and Damith C. Ranainghe Univerity of Adelaide, Adelaide, South Autralia, Autralia Abtract. Gue-and-determine attack are baed on gueing a ubet of internal tate bit and ubequently uing thee guee together with the cipher output function to determine the value of the remaining tate. Thee attack have been uccefully employed to break NFSRbaed tream cipher. The complexity of a gue-and-determine attack i directly related to the number of tate bit ued in the output function. Conequently, an opportunity exit for efficient cryptanalyi of NFSRbaed tream cipher if NFSR ued can be tranformed to derive an equivalent tream cipher with a implified output function. In thi paper, we preent a new technique for tranforming NFSR. We how how we can ue thi technique to tranform NFSR to equivalent NFSR with implified output function. We explain how uch tranformation can ait in cryptanalyi of NFSR-baed cipher and demontrate the application of the technique to uccefully cryptanalye the lightweight cipher Sprout. Our attack on Sprout ha a time complexity of , which i time better than any publihed non-tmd attack, and require only 64 bit of plaintext-ciphertext pair. Keyword: Gue-and-determine, NFSR, Sprout Introduction Stream cipher generate a equence of peudorandom bit called a keytream which i combined with plaintext to produce a tream of ciphertext. Stream cipher are attractive becaue, generally, they can achieve high throughput and their implicity make them uitable for reource contrained device uch a wirele enor and Radio Frequency Identification tag. A typical tream cipher for achievement of fat encryption of meage contain feedback function and an output function [28]. Linear feedback hift regiter (LFSR) are often ued in the deign of tream cipher becaue LFSR are imple and eay to implement in hardware. However, they are inecure againt everal attack uch a fat correlation attack [24], and algebraic attack [, 25]. Nonlinear feedback hift regiter (NFSR) are introduced a a protection againt thee attack.
2 2 There are two way to implement NFSR. An n-bit NFSR in the Fibonacci configuration (Figure ), ha one feedback function which update the mot ignificant bit (bit n ) of the regiter. The value of other bit are determined by hifting. That i, bit i i hifted to the bit i (i = n,..., ). Feedback function n- n-2 n-3... Output Fig. : The Fibonacci configuration of NFSR In the Galoi configuration of NFSR (Figure 2), each bit i updated uing it own feedback function. Therefore, there are up to n feedback function. fn- n- fn-2 n-2... f Output Fig. 2: The Galoi configuration of NFSR Dubrova [] ha formulated a tranformation of the Fibonacci configuration to the Galoi configuration for NFSR with the aim of increaing the computation peed. She later outlined a method for deriving the correponding initial tate to generate identical output keytream [2]. Dubrova [4] further elaborate tranformation for NFSR. In [, 4], Dubrova identifie everal criteria that hould be atified in order to maintain an equivalent output keytream equence before and after the tranformation of the tream cipher. Dubrova [4] note the potential for exploiting NFSR tranformation for cryptanalyi, however no uch ue i propoed and to the bet of our knowledge thi concept ha, o far, not been ued for cryptanalyi. The baic idea of gue-and-determine attack (GD attack) i to gue a part of the internal tate of the cipher, and ue the gueed tate to determine the value of other unknown tate. The attack wa firt introduced by Knuden et al. [2] and by Bleichenbacher and Patel [9] and wa later named gue-
3 3 and-determine [5, 9]. Since then, the gue-and-determine attack ha been ued to target everal tream cipher [, 7, 27, 29, 3]. We propoe an improved gue-and-determine attack againt NFSR-baed tream cipher. The attack require everal round to gue and determine internal tate bit involved in the output function of the tream cipher. At each round, one bit of the keytream equence i ued to determine one bit of the internal tate. Meanwhile, the output function ued in other clock feedback function of the tream cipher are ued to create Boolean function ytem. More information collected from the keytream equence i able to reduce the complexity of the attack and alo increae the number of round we need. Conequently, to reduce the cardinality of the dependence et of the output function of tream cipher, the technique of tranformation on NFSR are adopted in thi attack. However, previou work on tranformation on NFSR contain everal criteria on tranformation. We develop the theorem on tranformation on NFSR a well. In FSE 25, Armknecht and Mikhalev [3] propoed a lightweight tream cipher called Sprout. The main inpiration of the deign i to reit the timememory-data (TMD) tradeoff attack [4, 6 8, 8], and break the rule of thumb that the ize of internal tate hould be at leat twice the ize of key. To achieve thee goal, the key bit are treated a implied internal tate and are included in the feedback function. Thi bring the total number of expreed and implied internal tate bit to twice the ize of key. While only mall part of key bit involved in the feedback function of Sprout. In cryptanalytic perpective, by gueing a mall ize of the key bit, the attacker are able to recover the whole expreed internal tate. Lallemand and Naya-Plaencia [22] apply a rebound attack [26] with a time complexity of , which i 2 time fater than a brute force attack. (The attack require the equivalent of trie of a brute force attack, compared with 2 8 required for the full brute force attack.) Thi attack, a well a other attack on Sprout, are ummaried in Table. Table : Summary of attack on Sprout Type of attack Data Time Memory Rebound attack [22] TMD tradeoff attack[6] terabyte Ditinguihing attack[5] 2 75 O(n) Gue-and-determine attack (thi paper) O(n) The main contribution of thi paper i howing how to exploit NFSR tranformation for cryptanalyi, in particular for reducing the time complexity of gue-and-determine attack. Firtly, we generalie the work of Dubrova [4] by relaxing the limitation on NFSR tranformation. We prove that our tranformation reult in equivalent NFSR, producing the ame output equence. We then how how to ue thee tranformation to reduce the complexity of the
4 4 NFSR output function, and with it the complexity of a gue-and-determine attack againt the NFSR. Finally, we apply the tranformation to the NFSR ued in the Sprout cipher and implement a gue-and-determine attack on the tranformed cipher. Our attack ha a complexity of , which i time better than the bet known non-tmd attack [22]. The paper i organied a follow: Section 2 provide background on NFSR and their tranformation and introduce the notation ued in thi paper. Section 3 preent our new tranformation of NFSR and prove that they preerve the output equence. Section 4 how how to ue the tranformation to improve gue-and-determine attack againt NFSR-baed cipher. In Section 5 we apply the technique to the Sprout cipher. 2 Preliminarie 2. Boolean function We firt introduce ome definition and notation we ue throughout the paper. Thee are, motly, baed on the notation of Dubrova []. Let GF (2) be the binary field with denoting the addition operation and juxtapoition denoting the field multiplication. For an arbitrary n, GF n (2) i the n-dimenional vector pace over GF (2). A Boolean function i a function f : GF n (2) GF (2). We ometime ue f(x) to replace the explicit notation f(x,..., x n ) when the number of variable i clear from the context. A product term of the variable x,..., x n i a term of the form x I = i I x i for ome I {,..., n }. Any Boolean function can be written a the um of product term of it input variable a format called the algebraic normal form (ANF). More formally, f(x,..., x n ) = c I x I I {,...,n } where c I {, } i called the coefficient of the product term x I. The dependence et of a Boolean function f i the et of thoe input variable that affect the function value. That i, i dep(f) iff there exit x,..., x i, x i+,..., x n uch that f(x,..., x i,, x i+,..., x n ) f(x,..., x i,, x i+,..., x n ) We note that for a product term we alway have dep(x I ) = I. Product term for which the cardinality of the dependence et i one, uch a x or x 5, are called linear product term. Product term with a larger cardinality of the dependence et, for example x x 2, are non-linear product term. The affine product term x = i neither linear nor non-linear. We do not ue the affine product term in thi work. For a Boolean function f(x,..., x n ) we define the poitive and negative m-hift of f, denoted by f +m and f m, a the function obtained from f by increaing and decreaing the indice of the input variable by m. That i, f +m (x,..., x n ) = f(x m,..., x n, x,..., x m ) f m (x,..., x n ) = f(x n m,..., x n, x,..., x n m )
5 5 2.2 Feedback Shift Regiter A hift regiter i a torage element coniting of n bit, known a the tate of the regiter. We ue the notation t i for the value of bit i of the tate at time t, and collectively denote the whole tate at time t by t = ( t,..., t n ). At each round, each of the tate bit receive the value of the next bit, i.e. t i = t i+ for i < n. At time t the regiter get an input which i entered into t n. The output of the regiter at time t i the value t. In a imple form of a feedback hift regiter, the input i calculated uing a Boolean feedback function f n of the tate. That i, t n = f n ( t ) = f n ( t,..., t n ). Thi form of feedback hift regiter i uually called the Fibonacci configuration. A more generalied form, known a the Galoi configuration, ha feedback function feeding into each bit. More formally, t i = f i( t ). A feedback function of the type f i ( t ) = t i+ g i( t ) uch that i + dep(g i ) i called ingular. Note that index arithmetic i done modulo-n, i.e. t n i the ame a t and n dep(g i ) iff dep(g i ). Further generaliation of feedback hift regiter include combining external input with the feedback function or uing a Boolean output function z( t ) to generate the output at time t. Two feedback hift regiter are conidered equivalent if they produce the ame output equence when given the ame input equence. In a linear feedback hift regiter (LFSR) the feedback function and the output function are all linear. Otherwie the regiter i a non-linear feedback hift regiter (NFSR). 2.3 Tranformation of NFSR Several work have looked at converion between Galoi and Fibonacci NFSR. Dubrova [] look at converting Fibonacci NFSR to the Galoi configuration with the aim of improving the performance by reducing the depth of the logical circuit ued for implementing the feedback function. Dubrova notice that under certain condition, an NFSR can be converted to an equivalent NFSR by hifting product term between the feedback function of the bit of the NFSR. More pecifically, the hift are poible if the NFSR are uniform. That i, they are plit around a terminal bit τ, uch that all of the non-trivial feedback function update bit above the terminal bit and take their input from tate bit below the terminal bit. Dubrova [2] how how to update the initial tate of the NFSR to enure that the output equence i the ame after the hift of product term when uing a trivial output function z(t) = t. Dubrova [4] pecifie a et of contraint for hifting product term between feedback function. The contraint are the ame a thoe we preent in Section 3.. Thee contraint are more relaxed than the requirement of uing uniform NFSR.
6 6 Lin [23] examine the equivalence between the Galoi and the Fibonacci configuration of NFSR demontrating that Galoi NFSR of a pecific contruction can be converted into equivalent Fibonacci NFSR. The contruction require that the feedback function only take input from lower bit than the bit they update. That i, t+ i = t i+ g i( t ), uch that dep(g i ) {,..., i }. For thee NFSR, Lin [23] iteratively replace occurrence of t i in the feedback function with the expanded form t i = t i+ g i( t,..., t i ). Each uch replacement effectively hift the non-trivial part of the feedback function of bit i, creating an equivalent NFSR in which the feedback function of bit i i trivial, i.e. t+ i = t i. The reulting NFSR at the end of the proce ha only one non-trivial feedback function and i, therefore, a Fibonacci NFSR. 3 A Generalied NFSR Tranformation In thi ection we preent a generaliation of the tranformation uggeted in previou work. For implicity, we look at tranformation that hift a ingle product term one bit down the NFSR. Equivalent tranformation that hift the product term up one bit can be contructed in a imilar manner. We note that by repeatedly hifting multiple product term we can achieve the hift uggeted in the prior work. 3. The Baic Shift We have an n-bit NFSR N, with feedback function f i (x) = x i+ g i (x) and an output function z(x). We want to hift a product term p = x I, for ome I {,..., n }, from the feedback function f α to f α. Intuitively, what we want i to create an equivalent NFSR N with feedback function f i (x) = x i+ ḡ i (x) and an output function z(x) uch that the main difference between N and N i that f α (x) = f α (x) p(x) and f α (x) = f α p (x). In the general cae, we expect to need to have more difference between N and N to achieve equivalence. However, a a warmup, we firt look at a retricted cenario, in which N doe not require any further change. The contraint we have are:. α + I. 2. f i (x) = x i for all i I. 3. α dep(g i ) for any i α. 4. α dep(z). A mentioned above, thee contraint are the ame a the contraint of Dubrova [4]. The main difference between the etting we preent here and the etting of Dubrova i that we only hift the product term to a neighbouring bit, hence we require multiple hift to achieve the reult of Dubrova. Lin [23] define Galoi NFSR a thoe having thi pecific contruction. Thi i a ubet of the Galoi configuration a the term i ued in Dubrova [] and in thi paper.
7 7 We now define a hift tate tranform that we will ue for howing that N and N are equivalent. Definition. Let p = x I be a product term, and α < n. The hift tate tranform T p,α : GF n (2) GF n (2) i defined a follow: T p,α (,..., n ) = (,..., α, α p (,..., n ), α+,..., n ) Lemma. Let t and t denote the tate of N and N, repectively, at time t. If t = T p,α ( t ) then t+ = T p,α ( t+ ). Proof. We firt note that due to Contraint 2 if i I, t+ i = t i+. Hence, we have p( t ) = p ( t+ ). We alo note that from Contraint we have α + dep(p), which implie α dep(p ). Becaue the only difference between t and t i in bit α we have p ( t ) = p ( t ) and alo, by Contraint 3, we have g i ( t ) = g i ( t ). We now look at the bit of tate t+. For i α, i α we have ḡ i = g i. Conequently For tate bit α. For bit α we have: Thu t+ i = t i+ ḡ i ( t ) = t i+ g i ( t ) = t+ i t+ α = f α ( t ) = f α ( t ) p ( t ) = t α g α ( t ) p ( t ) = t α p ( t ) g α ( t ) p ( t ) = t α g α ( t ) = t α g α ( t ) = t+ α t+ α = f α ( t ) = f α ( t ) p( t ) = f α ( t ) p( t ) = f α ( t ) p ( t+ ) = f α ( t ) p ( t+ ) t+ = ( t+,..., t+ n ) = ( t+,..., t+ α, t+ α p ( t+ ), t+ α+,..., t+ n ) = T p,α ( t+ ) Theorem. If = T p,α ( ) then for all t, t = T p,α ( t ). Proof. Follow from Lemma by induction on t.
8 8 Theorem 2. N and N are equivalent. Proof. By definition, z, the output function of N i the ame a the output function of N. We need to how that for any initial tate of N we can find an initial tate of N uch that the output equence of the two NFSR are the ame. Let be the initial tate of N. We how that if N i initialied to T p,α ( ) then the output equence are the ame. By Theorem we know that for any t, t = T p,α ( t ). Hence, for any t, and for any i α, t i = t i. From Contraint 4 we know that z(t ) doe not depend on the value of t α. Hence, z( t ) = z( t ) = z( t ). We note that the operation we ue in the tranform are all reverible, hence a imilar contruction can be ued to hift p in the revere direction, i.e. from f α to f α+ 3.2 Relaxing the Contraint In Section 3. we pecified everal contraint on the hifted product term and ued thoe to etablih an invariant, baed on the hift tate tranform of Definition. In thi ection we want to relax ome of the contraint, namely Contraint 3 and 4, while preerving the invariant. The idea i imple: if we aume that the invariant hold we can modify the feedback and output function of N to account for the modified tate value t α. That i, the feedback function we ue i uch that f(x) = f(tp,α(x)), and becaue T p,α = Tp,α, we have f(x) = f(t p,α (x)). The following theorem applie thi idea more formally. Theorem 3. Let N be an n-bit NFSR, with feedback function f i (x) = x i+ g i (x), and an output function z(x). Let p = x I be a product term uch that Contraint and 2 above hold. If N i an n-bit NFSR, with feedback function f i (x) and an output function z(x) defined a follow: x α g α (T p,α (x)) p (x) i = α f i (x) = f α (T p,α (x)) p(x) i = α f i (T p,α (x)) Otherwie z(x) = z(t p,α (x)) then N and N are equivalent. Proof. We firt how that the invariant hold, i.e. that if t t+ = T p,α ( t+ ). For i α, i α we have: = T p,α ( t ) then t+ i = f i ( t ) = f i (T p,α ( t )) = f i ( t ) = t+ i
9 9 For tate bit α we have: t+ α = f α ( t ) = t α g α (T p,α ( t )) p ( t ) = t α p ( t ) g α (T p,α ( t )) p ( t ) = t α g α (T p,α ( t )) = t α g α ( t ) = t+ α Finally, for tate bit α: t+ α = f α ( t ) = f α (T p,α ( t )) p( t ) = f α ( t ) p( t ) = f α ( t ) p ( t+ ) = f α ( t ) p ( t+ ) Thu, t+ = ( t+,..., t+ n ) = ( t+,..., t+ α, t+ α p ( t+ ), t+ α+,..., t+ n ) = T p,α ( t+ ) By induction on t we how that if = T p,α ( ) than for all t t = T p,α ( t ) hence we have z( t ) = z(t p,α ( t )) = z( t ) and the output equence of N and N are identical. 3.3 Generalied Tranformation We now want to remove Contraint 2. When we remove the contraint, we can no longer claim that hifting the product term only introduce a one round delay. That i, we no longer have p( t ) = p ( t+ ). Conequently, to preerve the invariant we need to update f α. The fix, baically, revere the feedback function of the input of p. Thi fix i formalied in Theorem 4. Theorem 4. Let N be an n-bit NFSR, with feedback function f i (x) = x i+ g i (x), and an output function z(x). Let p = x I be a product term uch that α + I. If N i an n-bit NFSR, with feedback function fi (x) and an output function z(x) defined a follow: x α g α (T p,α (x)) p (x) i = α f i (x) = f α (T p,α (x)) p ( f (x),..., f α (x),, f α+ (x),..., f n (x)) i = α f i (T p,α (x)) Otherwie z(x) = z(t p,α (x)) then N and N are equivalent. Proof. We note that the only difference from Theorem 3 i the definition of f α, which only affect tate bit α. For thi bit we now have: t+ α = f α ( t ) = f α (T p,α ( t )) p ( f ( t ),..., f α ( t ),, f α+ ( t ),..., f n ( t )) = f α ( t ) p ( t+,..., t+ α,, t+ α+,..., t+ n )
10 Output and becaue α dep(p ), we have t+ α = f α ( t ) p ( t+ ) = t+ α p ( t+ ). The ret of the proof i the ame a the proof of Theorem Dicuion We can compare our work to previouly uggeted tranformation baed on two different criteria: the allowed combination of input and output of the product term that can be hifted and the other contraint on the hift. On the firt criterion, we ee that the work of Dubrova [] and it extenion [2] are limited to only move product term that have input below τ and output above τ. The pace of poible hift i depicted in Figure 3. The diagram diplay the poible input in the X axi and poible output in the Y axi, with a rectangular area correponding to thee hift. Input... τ... n- fn-... Dubrova [2] fτ fτ-... Lin [24] Our work and Dubrova [5] f Fig. 3: The condition to apply different method of tranformation on NFSR In Lin [23] the feedback function of bit i depend only on tate bit below i. Thi et of combination i a uperet of the poible combination in Dubrova []. Thi et cover all the area above the main diagonal in Figure 3. Dubrova [4] and our work increae the poible combination. Both work can hift product term from bit α a long a the product term do not depend on bit α +. The reaon we cannot hift product term from bit α if they depend on bit α + i that uch hift are not generally invertible. A Dubrova [4] note, uch product term are not common in cryptography becaue the ue of non-invertible function may reult in a lo of entropy [2].
11 On the econd criterion, we have already mentioned that Dubrova [4] impoe the ame contraint a our Theorem 2. Thee contraint alo apply implicitly to uniform NFSR [, 2]. A dicued above, when all of the contraint are impoed, the only change required for equivalence are in the feedback function of the bit the product term i hifted from and the bit the product term i hifted to. By adjuting the initial tate, we can guarantee equivalence of the output equence. The tranformation of Lin [23] doe not impoe our Contraint 3. Conequently, it reult in change in feedback function that depend on the original output of the hifted product term. The order of applying the tranformation implie our Contraint 2 and the implied ue of the output function z(x) = x implie our Contraint 4. Thu, our work i the firt to apply NFSR tranformation without Contraint 2 and 4. Another contraint implicit in all prior work i that they all hift product term that exit in the ANF of the feedback function. Our tranformation doe not impoe thi contraint. Naturally, hifting a product term from a feedback function it doe not exit in will add the product term to that feedback function, increaing it complexity. However, a we how below the complexity of the feedback function ha little implication on the gue-and-determine attack we ue. 4 Tranforming NFSR to Improve Gue-and-Determine Attack Dubrova [4] peculate that NFSR tranformation may be ueful for cryptanalyi, however, thi peculation i not ubtantiated and exploring thi i left for future work. In thi ection we how an example of how tranforming an NFSR can facilitate gue-and-determine attack. We firt introduce gue-anddetermine attack, with focu on attack in the context of NFSR-baed tream cipher and how how to apply the attack to a toy NFSR. We then explain how reducing the complexity of the output function facilitate gue-and-determine attack, and how how tranforming the toy NFSR can be reduce the complexity of the output function and with it the complexity of the attack. 4. The Gue-and-Determine Attack A gue-and-determine attack i a type of known plaintext attack that ha been uccefully employed againt tream cipher [9, 5, 7, 9, 2, 29, 3]. In a known plaintext attack model the adverary ha acce to both the plaintext and it encrypted ciphertext and, conequently, the adverary can recover the ecret keytream ued for encrypting the known plaintext to the known ciphertext. The central idea of a gue-and-determine attack i to part of the internal tate of a cipher and ubequently ue the known keytream bit to determine the remaining tate.
12 2 When applied to NFSR-baed tream cipher, the attack firt guee the value of tate bit in the dependence et of the output function. It then eliminate guee that are inconitent with the (known) output bit. Thi gue and elimination tep can be viewed a gueing ome tate bit and uing the output function to determine the value of other. If there are remaining guee, the attack ue the NFSR feedback function to propagate the previouly gueed bit and repeat with a gue of the next round. If there are no remaining guee at a round, the attack backtrack to the previou round and trie another gue. If, at ome tage, all of the tate bit are gueed, the attack run the NFSR for everal round to enure it i conitent with the known output tream. Thi general attack methodology i illutrated in algorithm. Input : An n-bit keytream equence, the output function and feedback function of the cipher Output: Internal tate Initialie the ytem of Boolean function baed on the output function and feedback function; i ; while Sytem of boolean function i not recovered do Gue value of unknown variable in the dependent et of the output function in the i-th round; Ue the i-th bit of the keytream to determine variable() in the dependence et of the output function; if the ytem of Boolean function i olved then return the information from the i-th round to determine the value of key bit end ele if the Boolean function ytem i conitent then i i + ; Move to the next round; end ele Reject the wrong gue, and move to the next gue; if all guee are exhauted and there i no correct gue then i i Move to the previou round; end end end Algorithm : Gue-and-Determine Attack Generally, a the attack progree, information from ome of the previouly gueed bit will propagate to tate bit in the dependence et of the output function, reducing the number of bit to be gueed in future round. For example, if the output function depend on x i and x i+2, and auming trivial feedback
13 function for tate bit i and i+, a gue of t i+2 would propagate in two round to t+2 i, hence there would be no need to gue the latter. When the output function i non-linear, the amount of reduction in the number of bit to gue may depend on the value of previouly gueed bit. For example, if the ANF of the output function contain the product term x i x j, and at round t the adverary ha a gue for t i, the gueed value will determine whether t j need to be gueed. If t i =, the product term evaluate to irrepective of the value of t j. There i, therefore, no need to gue the latter. If, however, t i =, the value of the product term depend on t j, which need to be gueed. Similarly, when the a feedback function i not linear, it may ometime be poible to ue it to propagate guee even if not all of it input are known Attack Example A an illutrative example we now conider a toy 6-bit NFSR N with the following feedback function: f 5 (x) = x x x 2 x x 2 f 4 (x) = x 5 f 3 (x) = x 4 f 2 (x) = x 3 f (x) = x 2 f (x) = x which ha a period of 63 [3]. The output function we ue i z(x) = x x x 2 x 3 x 4 x 5 A brute force attack on the cipher ha to gue each poible combination of the initial tate of the cipher, reulting in a earch pace of ize 2 6. To perform a gue-and-determine attack on N, we gue the initial tate of bit to 4, i.e.,..., 4. Uing the output function and the firt output bit, we can now determine the value of 5 and recover the initial tate with an attack complexity of 2 5. Figure 4 illutrate thi attack. 4.3 Improving the Gue-and-Determine Attack When we examine the gue-and-determine attack above, we can ee that we ue one bit of information from the output equence. By uing thi bit we can reduce the attack complexity by one bit. To do better we will need to ue more bit from the output equence, and for that we need to be able to gue le than five bit in the firt round and till be able to ue the firt output bit to determine part of the tate.
14 4 bit round t d g g g g g 2 nd d Gueed in thi round Unknown Determined by output function Determined by feedback function From previou round Fig. 4: The gue-and-determine attack on NFSR N One way to achieve thi i to rely on the non-linearity of the output function. For the pecific example of N, we note that if we gue 2 =, there i no need to gue 3. We can ue,, 2, 4 and the output bit to determine 5. Not gueing 3 mean that we cannot propagate it value the econd round, hence we will not have the value 2, but we will have the value of all of the other tate bit. If 3 =, we can ue the next output bit to determine the value of 2 and complete the attack. Otherwie, we note that =, hence 2 5 doe not depend on 2 and we can move to the next round. In the next round we till mi the value of the lat bit 2, which we can determine from the output bit. Thee cenario are illutrated in Figure 5. In ummary, in half of the cae, when we gue 2 =, we need to gue 5 bit and in the other half, when 2 = we only need to gue 4 bit. Thi give a total of 24 cae to earch and the attack complexity i Reducing the Complexity of the Output Function Another way of reducing the number of tate bit we need to gue in each round i to reduce the cardinality of the dependence et of the output function. To be able to ue the output function to determine tate bit value, we need to gue the value of all but one of the input of the output function. Reducing the cardinality of the output function reduce the number of bit we need to gue each round and ha the potential of increaing the number of output bit we can ue. The main contribution of thi paper i howing how tranforming the NFSR can reduce the attack complexity by reducing the cardinality of the dependence et of the output function. Suppoe that the output function can be expreed a z(x) = x a x a+i z (x), uch that a dep(z ), a + i dep(z ) and i >. We want to eliminate x a from the output function. We note that if we hift the product term p = x a+ from f a+i to f a+i, we get a new output function z(x) = z(t xa+,a+i(x)) = x a (x a+i x a ) z (x) = x a+i z (x). Note that becaue a + i dep(z ), the tranform doe not modify z. While thi approach reduce the cardinality of the output function, it may complicate the feedback function. In particular, for the cae of Fibonacci NF-
15 5 bit bit round t d u g g t d u g g 2 nd d g 2 nd u d u (A) Gueed in thi round Unknown 3 rd 2 d g (B) Determined by output function Determined by feedback function From previou round Fig. 5: Improved attack on NFSR N. (A) when 2 = and 3 =. (B) when 2 = and 3 =
16 6 SR, uch a tranformation introduce two non-trivial feedback function at f a+i and f a+i that reduce the amount of tate propagation we can ue. Hence, tranforming the NFSR preent a balancing act between the complexity of the feedback function and the cardinality of the dependence et of the output function. Depending on the tructure of the original NFSR, we can ue two heuritic to reduce the effect of the tranformation on the tructure of the feedback function. Auming a Fibonacci NFSR, when a + i i cloe to n, we ue multiple hift to hift x n i from f n to f a+i. uch a hift will only reult in one non-trivial feedback function at f a+i. Furthermore, if we have a < b < a + i, uch that z(x) = x a x b x a+i x b+i z (x) () and a, b, a + i, b + i dep(z ), hifting x n i from f n to f a+i would eliminate both x a and x b from the output function, while only introducing one non-trivial feedback function at f a+i. 4.5 Attacking a Tranformed NFSR Oberving N we note that there i a combination of four product term in the output function which atifie the criteria outlined in Equation. Therefore, we hift the product term x 2 from the bit 5 to the bit 4, and then to the bit 3 to produce the following equivalent Galoi NFSR N 2 : f 5 (x) = x x x x 2 f 4 (x) = x 5 f 3 (x) = x 4 x f 2 (x) = x 3 f (x) = x 2 f (x) = x with a tranformed output function we ue i z(x) = x 2 x 3 x 4 x 5 Now we perform the gue-and-determine attack on N 2. In the firt round we gue bit 2, 3 and 4 and ue the output function to determine 5. We now propagate the known tate we know the value of, 2 and 4. However, becaue the feedback function f 3 i not trivial we do not know 3, o we gue it, and can ue the econd output bit to determine 5. We now have guee for 3 and 4 combining thee with 3 = f 3 ( ) = 4 allow u to determine. If 2 =, we can ue with 5 = f 5 ( ) = 2 = = to determine. Thi recover the complete initial tate. Thi cae i diplayed in Figure 6 (A).
17 7 If 2 = (Figure 6 (B)), we can reduce f 5 ( ) = 2 = =. Becaue i determined via f 3, it i independent of 5. Hence there i a 5% chance that the ytem i inconitent, with 5. When the ytem i conitent, we propagate the data we have to 2, gue 2 3 and determine 2 5 and we have the complete tate. bit bit round t d g g u u t d g g u u 2 nd d g d d 2 nd u d d g u 3 rd 2 d d g (A) (B) Gueed in thi round Unknown Determined by output function Determined by feedback function From previou round Fig. 6: Gue-and-determine attack on NFSR N 2. (A) 2 =, (B) 2 = To um up, we gue four bit for the firt two round. In 3/4 of the cae we can completely determine the internal tate. For the other /4 we need an additional gue. Hence, the attack complexity i = 2 = Admittedly, thi i a very mall improvement over the attack on the original NFSR. However, thi i a toy example. A we hall now ee, for larger NFSR the improvement can be much more ignificant.
18 8 5 A Gue-and-Determine Attack on the Sprout Stream Cipher So far we have demontrated that NFSR tranformation can improve gueand-determine attack only in a very limited cenario. We now how that the technique alo work for real cipher. In thi ection we decribe an attack on the Sprout cipher [3]. We tart with a decription of the cipher, proceed with a decription of a tranformation that reduce the cardinality of the output function and implement a gue-anddetermine attack on the cipher. 5. Decription of Sprout Stream Cipher k k... k79 Round key function * kt g Counter f NFSR LFSR Output Zt Fig. 7: Sprout cipher Sprout [3] i a Grain-family tream cipher, which i inpired by Grain-28a [2]. It internal tate conit of a 4-bit LFSR l, a 4-bit Fibonacci NFSR n and a 7-bit counter c. The counter elect key bit that are fed together with counter bit c t 4 to the feedback function of the NFSR. Sprout ue an 8 bit key and a 7 bit initialiation vector (IV). To decribe the cipher We adopt a notation imilar to that of Lallemand and Naya-Plaencia [22]: t: clock-cycle number.
19 9 l t i the ith tate of the LFSR at clock t. n t i the ith tate of the NFSR at clock t. k = (k, k,..., k 79 ) the key bit. IV = (IV, IV,..., IV 69 ) initialiation vector. k t t round key bit generated at clock t. z t keytream bit generated at clock t. c t the value of the counter at clock t. The LFSR ue the following feedback function: l t+ 39 = l t l t 5 l t 5 l t 2 l t 25 l t 34 The NFSR ue the following feedback function: n t+ 39 =k t l t c t n t n t 3 n t 9 n t 35 n t 39 n t 2n t 25 n t 3n t 5 n t 7n t 8 n t 4n t 2 n t 6n t 8 n t 22n t 24 n t 26n t 32 n t 33n t 36n t 37n t 38 n t n t n t 2 n t 27n t 3n t 3 where k t i defined a: { kt k = t t 79 (k t mod 8 )(l4 t l2 t l37 t n t 9 n t 2 n t 29) t 8 The output function i: z t = n t 4l t 6 l t 8l t l t 32l t 7 l t 9l t 23 n t 4n t 38l t 32 l t 3 n t n t 6 n t 5 n t 7 n t 23 n t 28 n t 34 When the cipher tart, the NFSR and the LFSR are initialied from the IV uing the following formula: n i = IV i, i 39, li = IV i+4, i 29, and li =, 3 i 38, l39 =. The cipher then execute 32 initialiation round, in which rather than producing output, z t i fed back into the feedback function of the LFSR and the NFSR to update internal tate. 5.2 Tranformation of Sprout Cipher We oberve that the four linear product term n 7, n 23, n 28, n 34 of the output function meet the requirement of Equation, with a = 7, b = 23 and i =. We, therefore apply the tranformation uggeted above by hifting p = x n i = x 29 from f 39 to f 27. We note that x 29 i not in the ANF of the feedback function. Conequently, moving it from the feedback function will add the product term, making the function lightly more complex. Furthermore, for each hift we execute, we might have to update the feedback function a decribed in Theorem 4. The reulting
20 2 feedback function i: n t+ 39 =k t l t c t n t n t 3 n t 7 n t 8 n t 9 n t 24 n t 28 n t 29 n t 35 n t 39 n t 2n t 25 n t 3n t 5 n t 7n t 8 n t 4n t 2 n t 6n t 8 n t 22n t 24 n t 26(n t 32 n t 2) (n t 33 n t 22)(n t 36 n t 25)(n t 37 n t 26)(n t 38 n t 27) n t n t n t 2 n t 27(n t 3 n t 9)(n t 3 n t 2) n t+ 27 =n t 28 n t 7 We alo note that kt depend on ome internal tate that i modified by the tranform hence we need to update it to: { kt k = t t 79 (k t mod 8 )(l4 t l2 t l37 t n t 9 n t 8 n t 2 n t 29) t 8 Finally, the output function depend on n 38. Conequently, while the tranformation remove n 7 and n 23 from the output function, it alo add a dependency on n 27. Thu the cardinality of the output function i only reduced by. The new output function i: z t = n t 4l t 6 l t 8l t l t 32l t 7 l t 9l t 23 n t 4l t 32(n t 38 n t 27) l t 3 n t n t 6 n t 5 n t 28 n t 34 For initialiation, we apply the hift tate tranformation of Definition to initialie the 4-bit NFSR of the tranformed Sprout by: (IV, IV,..., IV 27, IV 28 IV 6, IV 29 IV 7,..., IV 39 IV 28 ) 5.3 Implementation of Gue-and-Determine Attack on the Sprout In each of the firt 8 round, we ue one keytream bit to determine one bit in the internal tate. In the firt round, we gue 5 bit (8 from the LFSR and 7 from the NFSR), and determine one bit by the output function (ee Figure 8. For implicity, we do not preent the tatu of the LFSR in the diagram. In the econd round, we again gue 5 bit and determine one (Figure 9). Additionally, becaue we know both n 27 and n 28 we can ue the feedback function of n 27 to determine n 7 = n 6. From the third round forward, the tate propagation provide u with ome guee to the dependence et of the output function. Conequently, we only need to gue 9 bit (4 LFSR and 5 NFSR) in the third round. (Figure.) The number of bit we gue keep decreaing we only need to gue 8, 6, 6, 5 and 3 bit for the fourth, fifth, ixth, eventh and eighth round, repectively. Thee are hown in Figure 5. During thee round, we continue to ue the feedback function of n 27 to determine n 7. For the ninth round we know all but four of the input of the output function, o we need to gue three to determine the fourth. We gue two additional tate bit in the NFSR (ee Figure 6) to increae the number of NFSR bit we know.
21 2 473 g g 478 d g g g g g 484 Determined by output function Unknown Gueed in thi round Fig. 8: The t round of gue-and-determine attack on Sprout d g g g 479 d g g g g Determined by output function Determined by feedback function Unknown Gueed in thi round From previou round Fig. 9: The 2nd round of gue-and-determine attack on Sprout d g g g d g g Determined by output function Determined by feedback function Unknown Gueed in thi round From previou round Fig. : The 3rd round of gue-and-determine attack on Sprout d g g d g g Determined by output function Determined by feedback function Unknown Gueed in thi round From previou round Fig. : The 4th round of gue-and-determine attack on Sprout d g g d g Determined by output function Determined by feedback function Unknown Gueed in thi round From previou round Fig. 2: The 5th round of gue-and-determine attack on Sprout d g g d g Determined by output function Determined by feedback function Unknown Gueed in thi round From previou round Fig. 3: The 6th round of gue-and-determine attack on Sprout
22 d g g d Determined by output function Determined by feedback function Unknown Gueed in thi round From previou round Fig. 4: The 7th round of gue-and-determine attack on Sprout d g g d Determined by output function Determined by feedback function Unknown Gueed in thi round From previou round Fig. 5: The 8th round of gue-and-determine attack on Sprout At thi tage mot of the tate ha been gueed and we can tart exploiting the non-linear term of the output function to determine ome more bit and to reject inconitent tate. (See Section 4.3.) If we are able to determine all of the tate bit, we are done. Otherwie we need to gue an additional bit and repeat the attempt to complete the tate d g g d g g Determined by output function Determined by feedback function Unknown Gueed in thi round From previou round Additional guee Fig. 6: The 9th round of gue-and-determine attack on Sprout Once the internal tate i recovered we follow the technique of Lallemand and Naya-Plaencia [22] to recover the key. Each round there i a 5% probability of having a key bit in the feedback function. Hence, by running the cipher for 6 round we expect to have 6 of the key bit affecting at leat one of thee
23 23 6 round. We need to run the cipher for four more round for the key bit to affect the output function. Hence after 64 round we can expect to recover 6 key bit. We can then brute force the remaining 2 bit. To etimate the complexity of the attack, we ran,, intance of the lat 3 round and counted the number of guee in each. More pecifically, for each of the,, intance we choe a random key, a random IV and a random gue of 59 bit gueed in for firt ix round of the attack. We then count the number of guee we make for round 7 to 9. The average number of guee we make i = For the firt ix round we need to gue a total of 59 bit. Hence, the attack complexity i = Thi compare favourably with the attack of Lallemand and Naya-Plaencia [22] and Banik [5] which require and 2 75 guee, repectively. The attack i ignificantly lower than the TMD attack of Egin and Kara [6], however, our attack ha modet memory requirement wherea their attack require over 77 terabyte of memory. 6 Concluion In thi paper we how that tranformation of NFSR from the Fibonacci configuration to the Galoi configuration can ait cryptanalyi. To demontrate thi, we generalie and extend pat work on NFSR tranformation. We dicu the condition under which uch tranformation can facilitate cryptanalytic attack and demontrate the ue of the technique to cryptanalye the Sprout cipher. Our gue-and-determine attack i fater than all previouly publihed non-tmd attack on Sprout. Our technique eentially hift complexity from the output function to the feedback function of the NFSR. While we are able to demontrate improvement in cryptanalyi, further work i required for better undertanding the trade-off in NFSR tranformation. Such undertanding i alo likely to help in deigning more ecure NFSR.
24 Bibliography [] Mohamed Ahmed Abdelraheem, Julia Borghoff, Erik Zenner, and Mathieu David. Cryptanalyi of the light-weight cipher A2U2. In Proceeding of the 3th IMA International Conference on Cryptography and Coding (IMACC), page , Oxford, UK, December 2. [2] Martin Ågren, Martin Hell, Thoma Johanon, and Willi Meier. Grain- 28a: a new verion of Grain-28 with optional authentication. International Journal of Wirele and Mobile Computing, 5():48 59, December 2. [3] Frederik Armknecht and Vaily Mikhalev. On lightweight tream cipher with horter internal tate. In Proceeding of the 22nd International Workhop on Fat Software Encryption (FSE), page 45 47, Itanbul, Turkey, mar 25. [4] S. H. Babbage. Improved exhautive earch attack on tream cipher. In European Convention on Security and Detection, page 6 66, Brighton, UK, May 995. [5] Subhadeep Banik. Some reult on Sprout. Cryptology eprint Archive Report 25/327, April 25. [6] Elad Barkan, Eli Biham, and Adi Shamir. Rigorou bound on cryptanalytic time/memory tradeoff. In Advance in Cryptology Crypto 26, page 2, Santa Barbara, CA, US, aug 26. [7] Alex Biryukov and Adi Shamir. Cryptanalytic time/memory/data tradeoff for tream cipher. In Advance in Cryptology ASIACRYPT 2, page 3, Kyoto, Japan, December 2. [8] Alex Biryukov, Adi Shamir, and David Wagner. Real time cryptanalyi of A5/ on a PC. In Fat Software Encryption, page 8, New York, NY, US, April 2. [9] Daniel Bleichenbacher and Sarvar Patel. SOBER cryptanalyi. In Fat Software Encryption, page 35 36, Rome, Italy, March 999. [] Nicola T. Courtoi and Willi Meier. Algebraic attack on tream cipher with linear feedback. In Advance in Cryptology EUROCRYPT 23, page , Waraw, Poland, May 23. [] Elena Dubrova. A tranformation from the Fibonacci to the Galoi NLFSR. IEEE Tranaction on Information Theory, 55(): , November 29. [2] Elena Dubrova. Finding matching initial tate for equivalent NLFSR in the Fibonacci and the Galoi configuration. IEEE Tranaction on Information Theory, 56(6): , June 2. [3] Elena Dubrova. A lit of maximum period NLFSR. Cryptology eprint Archive Report 22/66, March 22. [4] Elena Dubrova. An equivalence-preerving tranformation of hift regiter. In Sequence and Their Application, page 87 99, Melbourne, VIC, Autralia, November 24.
Codes Correcting Two Deletions
 1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
A Constraint Propagation Algorithm for Determining the Stability Margin. The paper addresses the stability margin assessment for linear systems
 A Contraint Propagation Algorithm for Determining the Stability Margin of Linear Parameter Circuit and Sytem Lubomir Kolev and Simona Filipova-Petrakieva Abtract The paper addree the tability margin aement
A Contraint Propagation Algorithm for Determining the Stability Margin of Linear Parameter Circuit and Sytem Lubomir Kolev and Simona Filipova-Petrakieva Abtract The paper addree the tability margin aement
Fast explicit formulae for genus 2 hyperelliptic curves using projective coordinates
 Fat explicit formulae for genu hyperelliptic curve uing projective coordinate Thoma Wollinger Ecrypt embedded ecurity GmbH twollinger@ecryptde Abtract Thi contribution propoe a modification of method of
Fat explicit formulae for genu hyperelliptic curve uing projective coordinate Thoma Wollinger Ecrypt embedded ecurity GmbH twollinger@ecryptde Abtract Thi contribution propoe a modification of method of
Jul 4, 2005 turbo_code_primer Revision 0.0. Turbo Code Primer
 Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
7.2 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 281
 72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
Preemptive scheduling on a small number of hierarchical machines
 Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
CHAPTER 4 DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL
 98 CHAPTER DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL INTRODUCTION The deign of ytem uing tate pace model for the deign i called a modern control deign and it i
98 CHAPTER DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL INTRODUCTION The deign of ytem uing tate pace model for the deign i called a modern control deign and it i
Problem Set 8 Solutions
 Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Lecture 21. The Lovasz splitting-off lemma Topics in Combinatorial Optimization April 29th, 2004
 18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
Evolutionary Algorithms Based Fixed Order Robust Controller Design and Robustness Performance Analysis
 Proceeding of 01 4th International Conference on Machine Learning and Computing IPCSIT vol. 5 (01) (01) IACSIT Pre, Singapore Evolutionary Algorithm Baed Fixed Order Robut Controller Deign and Robutne
Proceeding of 01 4th International Conference on Machine Learning and Computing IPCSIT vol. 5 (01) (01) IACSIT Pre, Singapore Evolutionary Algorithm Baed Fixed Order Robut Controller Deign and Robutne
Bogoliubov Transformation in Classical Mechanics
 Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Clustering Methods without Given Number of Clusters
 Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
A Simplified Methodology for the Synthesis of Adaptive Flight Control Systems
 A Simplified Methodology for the Synthei of Adaptive Flight Control Sytem J.ROUSHANIAN, F.NADJAFI Department of Mechanical Engineering KNT Univerity of Technology 3Mirdamad St. Tehran IRAN Abtract- A implified
A Simplified Methodology for the Synthei of Adaptive Flight Control Sytem J.ROUSHANIAN, F.NADJAFI Department of Mechanical Engineering KNT Univerity of Technology 3Mirdamad St. Tehran IRAN Abtract- A implified
A Provably Secure Scheme for Remote User Authentication
 A Provably Secure Scheme for Remote Uer Authentication Fuw-Yi Yang 1, Su-Hui Chiu 2 1 Department of Computer Science and Information Engineering, Chaoyang Univerity of Technology Taichung County 41349,
A Provably Secure Scheme for Remote Uer Authentication Fuw-Yi Yang 1, Su-Hui Chiu 2 1 Department of Computer Science and Information Engineering, Chaoyang Univerity of Technology Taichung County 41349,
Social Studies 201 Notes for November 14, 2003
 1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
White Rose Research Online URL for this paper: Version: Accepted Version
 Thi i a repoitory copy of Identification of nonlinear ytem with non-peritent excitation uing an iterative forward orthogonal leat quare regreion algorithm. White Roe Reearch Online URL for thi paper: http://eprint.whiteroe.ac.uk/107314/
Thi i a repoitory copy of Identification of nonlinear ytem with non-peritent excitation uing an iterative forward orthogonal leat quare regreion algorithm. White Roe Reearch Online URL for thi paper: http://eprint.whiteroe.ac.uk/107314/
Digital Control System
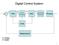 Digital Control Sytem - A D D A Micro ADC DAC Proceor Correction Element Proce Clock Meaurement A: Analog D: Digital Continuou Controller and Digital Control Rt - c Plant yt Continuou Controller Digital
Digital Control Sytem - A D D A Micro ADC DAC Proceor Correction Element Proce Clock Meaurement A: Analog D: Digital Continuou Controller and Digital Control Rt - c Plant yt Continuou Controller Digital
Social Studies 201 Notes for March 18, 2005
 1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
Lecture 9: Shor s Algorithm
 Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Lecture 10 Filtering: Applied Concepts
 Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
Convex Hulls of Curves Sam Burton
 Convex Hull of Curve Sam Burton 1 Introduction Thi paper will primarily be concerned with determining the face of convex hull of curve of the form C = {(t, t a, t b ) t [ 1, 1]}, a < b N in R 3. We hall
Convex Hull of Curve Sam Burton 1 Introduction Thi paper will primarily be concerned with determining the face of convex hull of curve of the form C = {(t, t a, t b ) t [ 1, 1]}, a < b N in R 3. We hall
Nonlinear Single-Particle Dynamics in High Energy Accelerators
 Nonlinear Single-Particle Dynamic in High Energy Accelerator Part 6: Canonical Perturbation Theory Nonlinear Single-Particle Dynamic in High Energy Accelerator Thi coure conit of eight lecture: 1. Introduction
Nonlinear Single-Particle Dynamic in High Energy Accelerator Part 6: Canonical Perturbation Theory Nonlinear Single-Particle Dynamic in High Energy Accelerator Thi coure conit of eight lecture: 1. Introduction
NCAAPMT Calculus Challenge Challenge #3 Due: October 26, 2011
 NCAAPMT Calculu Challenge 011 01 Challenge #3 Due: October 6, 011 A Model of Traffic Flow Everyone ha at ome time been on a multi-lane highway and encountered road contruction that required the traffic
NCAAPMT Calculu Challenge 011 01 Challenge #3 Due: October 6, 011 A Model of Traffic Flow Everyone ha at ome time been on a multi-lane highway and encountered road contruction that required the traffic
Topic 6. Digital Signatures and Identity Based Encryption
 Topic 6. Digital Signature and Identity Baed Encryption. Security of Public-key Cryptography 2. Example of Public-key Algorithm: Diffie- Hellman Key Exchange Scheme 3. RSA Encryption and Digital Signature
Topic 6. Digital Signature and Identity Baed Encryption. Security of Public-key Cryptography 2. Example of Public-key Algorithm: Diffie- Hellman Key Exchange Scheme 3. RSA Encryption and Digital Signature
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS
 CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
Lecture 8: Period Finding: Simon s Problem over Z N
 Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
IEOR 3106: Fall 2013, Professor Whitt Topics for Discussion: Tuesday, November 19 Alternating Renewal Processes and The Renewal Equation
 IEOR 316: Fall 213, Profeor Whitt Topic for Dicuion: Tueday, November 19 Alternating Renewal Procee and The Renewal Equation 1 Alternating Renewal Procee An alternating renewal proce alternate between
IEOR 316: Fall 213, Profeor Whitt Topic for Dicuion: Tueday, November 19 Alternating Renewal Procee and The Renewal Equation 1 Alternating Renewal Procee An alternating renewal proce alternate between
Optimal Coordination of Samples in Business Surveys
 Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Avoiding Forbidden Submatrices by Row Deletions
 Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Unavoidable Cycles in Polynomial-Based Time-Invariant LDPC Convolutional Codes
 European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
UNIT 15 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS
 UNIT 1 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS Structure 1.1 Introduction Objective 1.2 Redundancy 1.3 Reliability of k-out-of-n Sytem 1.4 Reliability of Standby Sytem 1. Summary 1.6 Solution/Anwer
UNIT 1 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS Structure 1.1 Introduction Objective 1.2 Redundancy 1.3 Reliability of k-out-of-n Sytem 1.4 Reliability of Standby Sytem 1. Summary 1.6 Solution/Anwer
SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lectures 41-48)
 Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Singular perturbation theory
 Singular perturbation theory Marc R. Rouel June 21, 2004 1 Introduction When we apply the teady-tate approximation (SSA) in chemical kinetic, we typically argue that ome of the intermediate are highly
Singular perturbation theory Marc R. Rouel June 21, 2004 1 Introduction When we apply the teady-tate approximation (SSA) in chemical kinetic, we typically argue that ome of the intermediate are highly
A Strategy for Constructing Fast Round Functions with Practical Security Against Differential and Linear Cryptanalysis
 A Strategy for Contructing Fat Round Function with Practical Security Againt Differential and Linear Cryptanalyi Maayuki Kanda, Youichi Takahima 2, Tutomu Matumoto 3, Kazumaro Aoki,andKazuoOhta NTT Information
A Strategy for Contructing Fat Round Function with Practical Security Againt Differential and Linear Cryptanalyi Maayuki Kanda, Youichi Takahima 2, Tutomu Matumoto 3, Kazumaro Aoki,andKazuoOhta NTT Information
An estimation approach for autotuning of event-based PI control systems
 Acta de la XXXIX Jornada de Automática, Badajoz, 5-7 de Septiembre de 08 An etimation approach for autotuning of event-baed PI control ytem Joé Sánchez Moreno, María Guinaldo Loada, Sebatián Dormido Departamento
Acta de la XXXIX Jornada de Automática, Badajoz, 5-7 de Septiembre de 08 An etimation approach for autotuning of event-baed PI control ytem Joé Sánchez Moreno, María Guinaldo Loada, Sebatián Dormido Departamento
Gain and Phase Margins Based Delay Dependent Stability Analysis of Two- Area LFC System with Communication Delays
 Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Shannon s Theory. Objectives
 Shannon Theory Debdeep Mukhopadhyay IIT Kharagpur Objective Undertand the definition of Perfect Secrecy Prove that a given crypto-ytem i perfectly ecured One Time Pad Entropy and it computation Ideal Cipher
Shannon Theory Debdeep Mukhopadhyay IIT Kharagpur Objective Undertand the definition of Perfect Secrecy Prove that a given crypto-ytem i perfectly ecured One Time Pad Entropy and it computation Ideal Cipher
into a discrete time function. Recall that the table of Laplace/z-transforms is constructed by (i) selecting to get
 Lecture 25 Introduction to Some Matlab c2d Code in Relation to Sampled Sytem here are many way to convert a continuou time function, { h( t) ; t [0, )} into a dicrete time function { h ( k) ; k {0,,, }}
Lecture 25 Introduction to Some Matlab c2d Code in Relation to Sampled Sytem here are many way to convert a continuou time function, { h( t) ; t [0, )} into a dicrete time function { h ( k) ; k {0,,, }}
On the Isomorphism of Fractional Factorial Designs 1
 journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
CONTROL SYSTEMS, ROBOTICS AND AUTOMATION Vol. VIII Decoupling Control - M. Fikar
 DECOUPLING CONTROL M. Fikar Department of Proce Control, Faculty of Chemical and Food Technology, Slovak Univerity of Technology in Bratilava, Radlinkého 9, SK-812 37 Bratilava, Slovakia Keyword: Decoupling:
DECOUPLING CONTROL M. Fikar Department of Proce Control, Faculty of Chemical and Food Technology, Slovak Univerity of Technology in Bratilava, Radlinkého 9, SK-812 37 Bratilava, Slovakia Keyword: Decoupling:
Chapter 4. The Laplace Transform Method
 Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
Chapter 2 Sampling and Quantization. In order to investigate sampling and quantization, the difference between analog
 Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Multicolor Sunflowers
 Multicolor Sunflower Dhruv Mubayi Lujia Wang October 19, 2017 Abtract A unflower i a collection of ditinct et uch that the interection of any two of them i the ame a the common interection C of all of
Multicolor Sunflower Dhruv Mubayi Lujia Wang October 19, 2017 Abtract A unflower i a collection of ditinct et uch that the interection of any two of them i the ame a the common interection C of all of
Sampling and the Discrete Fourier Transform
 Sampling and the Dicrete Fourier Tranform Sampling Method Sampling i mot commonly done with two device, the ample-and-hold (S/H) and the analog-to-digital-converter (ADC) The S/H acquire a CT ignal at
Sampling and the Dicrete Fourier Tranform Sampling Method Sampling i mot commonly done with two device, the ample-and-hold (S/H) and the analog-to-digital-converter (ADC) The S/H acquire a CT ignal at
A Study on Simulating Convolutional Codes and Turbo Codes
 A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
Advanced D-Partitioning Analysis and its Comparison with the Kharitonov s Theorem Assessment
 Journal of Multidiciplinary Engineering Science and Technology (JMEST) ISSN: 59- Vol. Iue, January - 5 Advanced D-Partitioning Analyi and it Comparion with the haritonov Theorem Aement amen M. Yanev Profeor,
Journal of Multidiciplinary Engineering Science and Technology (JMEST) ISSN: 59- Vol. Iue, January - 5 Advanced D-Partitioning Analyi and it Comparion with the haritonov Theorem Aement amen M. Yanev Profeor,
Control of Delayed Integrating Processes Using Two Feedback Controllers R MS Approach
 Proceeding of the 7th WSEAS International Conference on SYSTEM SCIENCE and SIMULATION in ENGINEERING (ICOSSSE '8) Control of Delayed Integrating Procee Uing Two Feedback Controller R MS Approach LIBOR
Proceeding of the 7th WSEAS International Conference on SYSTEM SCIENCE and SIMULATION in ENGINEERING (ICOSSSE '8) Control of Delayed Integrating Procee Uing Two Feedback Controller R MS Approach LIBOR
DIFFERENTIAL EQUATIONS
 DIFFERENTIAL EQUATIONS Laplace Tranform Paul Dawkin Table of Content Preface... Laplace Tranform... Introduction... The Definition... 5 Laplace Tranform... 9 Invere Laplace Tranform... Step Function...4
DIFFERENTIAL EQUATIONS Laplace Tranform Paul Dawkin Table of Content Preface... Laplace Tranform... Introduction... The Definition... 5 Laplace Tranform... 9 Invere Laplace Tranform... Step Function...4
3.1 The Revised Simplex Algorithm. 3 Computational considerations. Thus, we work with the following tableau. Basic observations = CARRY. ... m.
 3 Computational conideration In what follow, we analyze the complexity of the Simplex algorithm more in detail For thi purpoe, we focu on the update proce in each iteration of thi procedure Clearly, ince,
3 Computational conideration In what follow, we analyze the complexity of the Simplex algorithm more in detail For thi purpoe, we focu on the update proce in each iteration of thi procedure Clearly, ince,
PIPELINED DIVISION OF SIGNED NUMBERS WITH THE USE OF RESIDUE ARITHMETIC FOR SMALL NUMBER RANGE WITH THE PROGRAMMABLE GATE ARRAY
 POZNAN UNIVE RSITY OF TE CHNOLOGY ACADE MIC JOURNALS No 76 Electrical Engineering 03 Robert SMYK* Zenon ULMAN* Maciej CZYŻAK* PIPELINED DIVISION OF SIGNED NUMBERS WITH THE USE OF RESIDUE ARITHMETIC FOR
POZNAN UNIVE RSITY OF TE CHNOLOGY ACADE MIC JOURNALS No 76 Electrical Engineering 03 Robert SMYK* Zenon ULMAN* Maciej CZYŻAK* PIPELINED DIVISION OF SIGNED NUMBERS WITH THE USE OF RESIDUE ARITHMETIC FOR
Efficient Methods of Doppler Processing for Coexisting Land and Weather Clutter
 Efficient Method of Doppler Proceing for Coexiting Land and Weather Clutter Ça gatay Candan and A Özgür Yılmaz Middle Eat Technical Univerity METU) Ankara, Turkey ccandan@metuedutr, aoyilmaz@metuedutr
Efficient Method of Doppler Proceing for Coexiting Land and Weather Clutter Ça gatay Candan and A Özgür Yılmaz Middle Eat Technical Univerity METU) Ankara, Turkey ccandan@metuedutr, aoyilmaz@metuedutr
Alternate Dispersion Measures in Replicated Factorial Experiments
 Alternate Diperion Meaure in Replicated Factorial Experiment Neal A. Mackertich The Raytheon Company, Sudbury MA 02421 Jame C. Benneyan Northeatern Univerity, Boton MA 02115 Peter D. Krau The Raytheon
Alternate Diperion Meaure in Replicated Factorial Experiment Neal A. Mackertich The Raytheon Company, Sudbury MA 02421 Jame C. Benneyan Northeatern Univerity, Boton MA 02115 Peter D. Krau The Raytheon
Compact finite-difference approximations for anisotropic image smoothing and painting
 CWP-593 Compact finite-difference approximation for aniotropic image moothing and painting Dave Hale Center for Wave Phenomena, Colorado School of Mine, Golden CO 80401, USA ABSTRACT Finite-difference
CWP-593 Compact finite-difference approximation for aniotropic image moothing and painting Dave Hale Center for Wave Phenomena, Colorado School of Mine, Golden CO 80401, USA ABSTRACT Finite-difference
Hybrid Projective Dislocated Synchronization of Liu Chaotic System Based on Parameters Identification
 www.ccenet.org/ma Modern Applied Science Vol. 6, No. ; February Hybrid Projective Dilocated Synchronization of Liu Chaotic Sytem Baed on Parameter Identification Yanfei Chen College of Science, Guilin
www.ccenet.org/ma Modern Applied Science Vol. 6, No. ; February Hybrid Projective Dilocated Synchronization of Liu Chaotic Sytem Baed on Parameter Identification Yanfei Chen College of Science, Guilin
REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS. Logic and Applications 2015 (LAP 2015) September 21-25, 2015, Dubrovnik, Croatia
 REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS SMILE MARKOVSKI Faculty of Computer Science and Engineering, S Ciryl and Methodiu Univerity in Skopje, MACEDONIA mile.markovki@gmail.com Logic
REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS SMILE MARKOVSKI Faculty of Computer Science and Engineering, S Ciryl and Methodiu Univerity in Skopje, MACEDONIA mile.markovki@gmail.com Logic
Dimensional Analysis A Tool for Guiding Mathematical Calculations
 Dimenional Analyi A Tool for Guiding Mathematical Calculation Dougla A. Kerr Iue 1 February 6, 2010 ABSTRACT AND INTRODUCTION In converting quantitie from one unit to another, we may know the applicable
Dimenional Analyi A Tool for Guiding Mathematical Calculation Dougla A. Kerr Iue 1 February 6, 2010 ABSTRACT AND INTRODUCTION In converting quantitie from one unit to another, we may know the applicable
A SIMPLE NASH-MOSER IMPLICIT FUNCTION THEOREM IN WEIGHTED BANACH SPACES. Sanghyun Cho
 A SIMPLE NASH-MOSER IMPLICIT FUNCTION THEOREM IN WEIGHTED BANACH SPACES Sanghyun Cho Abtract. We prove a implified verion of the Nah-Moer implicit function theorem in weighted Banach pace. We relax the
A SIMPLE NASH-MOSER IMPLICIT FUNCTION THEOREM IN WEIGHTED BANACH SPACES Sanghyun Cho Abtract. We prove a implified verion of the Nah-Moer implicit function theorem in weighted Banach pace. We relax the
DYNAMIC MODELS FOR CONTROLLER DESIGN
 DYNAMIC MODELS FOR CONTROLLER DESIGN M.T. Tham (996,999) Dept. of Chemical and Proce Engineering Newcatle upon Tyne, NE 7RU, UK.. INTRODUCTION The problem of deigning a good control ytem i baically that
DYNAMIC MODELS FOR CONTROLLER DESIGN M.T. Tham (996,999) Dept. of Chemical and Proce Engineering Newcatle upon Tyne, NE 7RU, UK.. INTRODUCTION The problem of deigning a good control ytem i baically that
arxiv: v2 [nucl-th] 3 May 2018
![arxiv: v2 [nucl-th] 3 May 2018 arxiv: v2 [nucl-th] 3 May 2018](/thumbs/89/101162462.jpg) DAMTP-207-44 An Alpha Particle Model for Carbon-2 J. I. Rawlinon arxiv:72.05658v2 [nucl-th] 3 May 208 Department of Applied Mathematic and Theoretical Phyic, Univerity of Cambridge, Wilberforce Road, Cambridge
DAMTP-207-44 An Alpha Particle Model for Carbon-2 J. I. Rawlinon arxiv:72.05658v2 [nucl-th] 3 May 208 Department of Applied Mathematic and Theoretical Phyic, Univerity of Cambridge, Wilberforce Road, Cambridge
The machines in the exercise work as follows:
 Tik-79.148 Spring 2001 Introduction to Theoretical Computer Science Tutorial 9 Solution to Demontration Exercie 4. Contructing a complex Turing machine can be very laboriou. With the help of machine chema
Tik-79.148 Spring 2001 Introduction to Theoretical Computer Science Tutorial 9 Solution to Demontration Exercie 4. Contructing a complex Turing machine can be very laboriou. With the help of machine chema
CHEAP CONTROL PERFORMANCE LIMITATIONS OF INPUT CONSTRAINED LINEAR SYSTEMS
 Copyright 22 IFAC 5th Triennial World Congre, Barcelona, Spain CHEAP CONTROL PERFORMANCE LIMITATIONS OF INPUT CONSTRAINED LINEAR SYSTEMS Tritan Pérez Graham C. Goodwin Maria M. Serón Department of Electrical
Copyright 22 IFAC 5th Triennial World Congre, Barcelona, Spain CHEAP CONTROL PERFORMANCE LIMITATIONS OF INPUT CONSTRAINED LINEAR SYSTEMS Tritan Pérez Graham C. Goodwin Maria M. Serón Department of Electrical
Z a>2 s 1n = X L - m. X L = m + Z a>2 s 1n X L = The decision rule for this one-tail test is
 M09_BERE8380_12_OM_C09.QD 2/21/11 3:44 PM Page 1 9.6 The Power of a Tet 9.6 The Power of a Tet 1 Section 9.1 defined Type I and Type II error and their aociated rik. Recall that a repreent the probability
M09_BERE8380_12_OM_C09.QD 2/21/11 3:44 PM Page 1 9.6 The Power of a Tet 9.6 The Power of a Tet 1 Section 9.1 defined Type I and Type II error and their aociated rik. Recall that a repreent the probability
ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS
 ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS VOLKER ZIEGLER Abtract We conider the parameterized Thue equation X X 3 Y (ab + (a + bx Y abxy 3 + a b Y = ±1, where a, b 1 Z uch that
ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS VOLKER ZIEGLER Abtract We conider the parameterized Thue equation X X 3 Y (ab + (a + bx Y abxy 3 + a b Y = ±1, where a, b 1 Z uch that
The Laplace Transform (Intro)
 4 The Laplace Tranform (Intro) The Laplace tranform i a mathematical tool baed on integration that ha a number of application It particular, it can implify the olving of many differential equation We will
4 The Laplace Tranform (Intro) The Laplace tranform i a mathematical tool baed on integration that ha a number of application It particular, it can implify the olving of many differential equation We will
TRIPLE SOLUTIONS FOR THE ONE-DIMENSIONAL
 GLASNIK MATEMATIČKI Vol. 38583, 73 84 TRIPLE SOLUTIONS FOR THE ONE-DIMENSIONAL p-laplacian Haihen Lü, Donal O Regan and Ravi P. Agarwal Academy of Mathematic and Sytem Science, Beijing, China, National
GLASNIK MATEMATIČKI Vol. 38583, 73 84 TRIPLE SOLUTIONS FOR THE ONE-DIMENSIONAL p-laplacian Haihen Lü, Donal O Regan and Ravi P. Agarwal Academy of Mathematic and Sytem Science, Beijing, China, National
S_LOOP: SINGLE-LOOP FEEDBACK CONTROL SYSTEM ANALYSIS
 S_LOOP: SINGLE-LOOP FEEDBACK CONTROL SYSTEM ANALYSIS by Michelle Gretzinger, Daniel Zyngier and Thoma Marlin INTRODUCTION One of the challenge to the engineer learning proce control i relating theoretical
S_LOOP: SINGLE-LOOP FEEDBACK CONTROL SYSTEM ANALYSIS by Michelle Gretzinger, Daniel Zyngier and Thoma Marlin INTRODUCTION One of the challenge to the engineer learning proce control i relating theoretical
On Multi-source Networks: Enumeration, Rate Region Computation, and Hierarchy
 On Multi-ource Network: Enumeration, Rate Region Computation, and Hierarchy Congduan Li, Student Member, IEEE, Steven Weber, Senior Member, IEEE, and John MacLaren Walh, Member, IEEE arxiv:5070578v [cit]
On Multi-ource Network: Enumeration, Rate Region Computation, and Hierarchy Congduan Li, Student Member, IEEE, Steven Weber, Senior Member, IEEE, and John MacLaren Walh, Member, IEEE arxiv:5070578v [cit]
In presenting the dissertation as a partial fulfillment of the requirements for an advanced degree from the Georgia Institute of Technology, I agree
 In preenting the diertation a a partial fulfillment of the requirement for an advanced degree from the Georgia Intitute of Technology, I agree that the Library of the Intitute hall make it available for
In preenting the diertation a a partial fulfillment of the requirement for an advanced degree from the Georgia Intitute of Technology, I agree that the Library of the Intitute hall make it available for
Control Systems Analysis and Design by the Root-Locus Method
 6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
LDPC Convolutional Codes Based on Permutation Polynomials over Integer Rings
 LDPC Convolutional Code Baed on Permutation Polynomial over Integer Ring Marco B. S. Tavare and Gerhard P. Fettwei Vodafone Chair Mobile Communication Sytem, Dreden Univerity of Technology, 01062 Dreden,
LDPC Convolutional Code Baed on Permutation Polynomial over Integer Ring Marco B. S. Tavare and Gerhard P. Fettwei Vodafone Chair Mobile Communication Sytem, Dreden Univerity of Technology, 01062 Dreden,
Symmetric Determinantal Representation of Formulas and Weakly Skew Circuits
 Contemporary Mathematic Symmetric Determinantal Repreentation of Formula and Weakly Skew Circuit Bruno Grenet, Erich L. Kaltofen, Pacal Koiran, and Natacha Portier Abtract. We deploy algebraic complexity
Contemporary Mathematic Symmetric Determinantal Repreentation of Formula and Weakly Skew Circuit Bruno Grenet, Erich L. Kaltofen, Pacal Koiran, and Natacha Portier Abtract. We deploy algebraic complexity
Extending MFM Function Ontology for Representing Separation and Conversion in Process Plant
 Downloaded from orbit.dtu.dk on: Oct 05, 2018 Extending MFM Function Ontology for Repreenting Separation and Converion in Proce Plant Zhang, Xinxin; Lind, Morten; Jørgenen, Sten Bay; Wu, Jing; Karnati,
Downloaded from orbit.dtu.dk on: Oct 05, 2018 Extending MFM Function Ontology for Repreenting Separation and Converion in Proce Plant Zhang, Xinxin; Lind, Morten; Jørgenen, Sten Bay; Wu, Jing; Karnati,
LINEAR ALGEBRA METHOD IN COMBINATORICS. Theorem 1.1 (Oddtown theorem). In a town of n citizens, no more than n clubs can be formed under the rules
 LINEAR ALGEBRA METHOD IN COMBINATORICS 1 Warming-up example Theorem 11 (Oddtown theorem) In a town of n citizen, no more tha club can be formed under the rule each club have an odd number of member each
LINEAR ALGEBRA METHOD IN COMBINATORICS 1 Warming-up example Theorem 11 (Oddtown theorem) In a town of n citizen, no more tha club can be formed under the rule each club have an odd number of member each
Factor Analysis with Poisson Output
 Factor Analyi with Poion Output Gopal Santhanam Byron Yu Krihna V. Shenoy, Department of Electrical Engineering, Neurocience Program Stanford Univerity Stanford, CA 94305, USA {gopal,byronyu,henoy}@tanford.edu
Factor Analyi with Poion Output Gopal Santhanam Byron Yu Krihna V. Shenoy, Department of Electrical Engineering, Neurocience Program Stanford Univerity Stanford, CA 94305, USA {gopal,byronyu,henoy}@tanford.edu
Online Appendix for Managerial Attention and Worker Performance by Marina Halac and Andrea Prat
 Online Appendix for Managerial Attention and Worker Performance by Marina Halac and Andrea Prat Thi Online Appendix contain the proof of our reult for the undicounted limit dicued in Section 2 of the paper,
Online Appendix for Managerial Attention and Worker Performance by Marina Halac and Andrea Prat Thi Online Appendix contain the proof of our reult for the undicounted limit dicued in Section 2 of the paper,
Advanced Digital Signal Processing. Stationary/nonstationary signals. Time-Frequency Analysis... Some nonstationary signals. Time-Frequency Analysis
 Advanced Digital ignal Proceing Prof. Nizamettin AYDIN naydin@yildiz.edu.tr Time-Frequency Analyi http://www.yildiz.edu.tr/~naydin 2 tationary/nontationary ignal Time-Frequency Analyi Fourier Tranform
Advanced Digital ignal Proceing Prof. Nizamettin AYDIN naydin@yildiz.edu.tr Time-Frequency Analyi http://www.yildiz.edu.tr/~naydin 2 tationary/nontationary ignal Time-Frequency Analyi Fourier Tranform
EE Control Systems LECTURE 14
 Updated: Tueday, March 3, 999 EE 434 - Control Sytem LECTURE 4 Copyright FL Lewi 999 All right reerved ROOT LOCUS DESIGN TECHNIQUE Suppoe the cloed-loop tranfer function depend on a deign parameter k We
Updated: Tueday, March 3, 999 EE 434 - Control Sytem LECTURE 4 Copyright FL Lewi 999 All right reerved ROOT LOCUS DESIGN TECHNIQUE Suppoe the cloed-loop tranfer function depend on a deign parameter k We
2.7.2 Limits to Parallelism
 Chapter 2 Exercie 53 The 1990 will find a broader ue of multiproceor a the peed of individual proceor reache the limit of metal interconnection. The highet utainable clock rate for metal interconnection
Chapter 2 Exercie 53 The 1990 will find a broader ue of multiproceor a the peed of individual proceor reache the limit of metal interconnection. The highet utainable clock rate for metal interconnection
Asymptotics of ABC. Paul Fearnhead 1, Correspondence: Abstract
 Aymptotic of ABC Paul Fearnhead 1, 1 Department of Mathematic and Statitic, Lancater Univerity Correpondence: p.fearnhead@lancater.ac.uk arxiv:1706.07712v1 [tat.me] 23 Jun 2017 Abtract Thi document i due
Aymptotic of ABC Paul Fearnhead 1, 1 Department of Mathematic and Statitic, Lancater Univerity Correpondence: p.fearnhead@lancater.ac.uk arxiv:1706.07712v1 [tat.me] 23 Jun 2017 Abtract Thi document i due
New bounds for Morse clusters
 New bound for More cluter Tamá Vinkó Advanced Concept Team, European Space Agency, ESTEC Keplerlaan 1, 2201 AZ Noordwijk, The Netherland Tama.Vinko@ea.int and Arnold Neumaier Fakultät für Mathematik, Univerität
New bound for More cluter Tamá Vinkó Advanced Concept Team, European Space Agency, ESTEC Keplerlaan 1, 2201 AZ Noordwijk, The Netherland Tama.Vinko@ea.int and Arnold Neumaier Fakultät für Mathematik, Univerität
Cryptanalysis of the Light-Weight Cipher A2U2 First Draft version
 Cryptanalysis of the Light-Weight Cipher A2U2 First Draft version Mohamed Ahmed Abdelraheem, Julia Borghoff, Erik Zenner Technical University of Denmark, DK-2800 Kgs. Lyngby, Denmark {M.A.Abdelraheem,J.Borghoff,E.Zenner}@mat.dtu.dk
Cryptanalysis of the Light-Weight Cipher A2U2 First Draft version Mohamed Ahmed Abdelraheem, Julia Borghoff, Erik Zenner Technical University of Denmark, DK-2800 Kgs. Lyngby, Denmark {M.A.Abdelraheem,J.Borghoff,E.Zenner}@mat.dtu.dk
Stochastic Optimization with Inequality Constraints Using Simultaneous Perturbations and Penalty Functions
 Stochatic Optimization with Inequality Contraint Uing Simultaneou Perturbation and Penalty Function I-Jeng Wang* and Jame C. Spall** The John Hopkin Univerity Applied Phyic Laboratory 11100 John Hopkin
Stochatic Optimization with Inequality Contraint Uing Simultaneou Perturbation and Penalty Function I-Jeng Wang* and Jame C. Spall** The John Hopkin Univerity Applied Phyic Laboratory 11100 John Hopkin
List coloring hypergraphs
 Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
March 18, 2014 Academic Year 2013/14
 POLITONG - SHANGHAI BASIC AUTOMATIC CONTROL Exam grade March 8, 4 Academic Year 3/4 NAME (Pinyin/Italian)... STUDENT ID Ue only thee page (including the back) for anwer. Do not ue additional heet. Ue of
POLITONG - SHANGHAI BASIC AUTOMATIC CONTROL Exam grade March 8, 4 Academic Year 3/4 NAME (Pinyin/Italian)... STUDENT ID Ue only thee page (including the back) for anwer. Do not ue additional heet. Ue of
Calculation of the temperature of boundary layer beside wall with time-dependent heat transfer coefficient
 Ŕ periodica polytechnica Mechanical Engineering 54/1 21 15 2 doi: 1.3311/pp.me.21-1.3 web: http:// www.pp.bme.hu/ me c Periodica Polytechnica 21 RESERCH RTICLE Calculation of the temperature of boundary
Ŕ periodica polytechnica Mechanical Engineering 54/1 21 15 2 doi: 1.3311/pp.me.21-1.3 web: http:// www.pp.bme.hu/ me c Periodica Polytechnica 21 RESERCH RTICLE Calculation of the temperature of boundary
A TMDTO Attack Against Lizard
 A TMDTO Attack Against Lizard Subhamoy Maitra 1, Nishant Sinha 2, Akhilesh Siddhanti 3, Ravi Anand 4, Sugata Gangopadhyay 2 1 Indian Statistical Institute, Kolkata, subho@isical.ac.in 2 Indian Institute
A TMDTO Attack Against Lizard Subhamoy Maitra 1, Nishant Sinha 2, Akhilesh Siddhanti 3, Ravi Anand 4, Sugata Gangopadhyay 2 1 Indian Statistical Institute, Kolkata, subho@isical.ac.in 2 Indian Institute
ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS. Volker Ziegler Technische Universität Graz, Austria
 GLASNIK MATEMATIČKI Vol. 1(61)(006), 9 30 ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS Volker Ziegler Techniche Univerität Graz, Autria Abtract. We conider the parameterized Thue
GLASNIK MATEMATIČKI Vol. 1(61)(006), 9 30 ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS Volker Ziegler Techniche Univerität Graz, Autria Abtract. We conider the parameterized Thue
μ + = σ = D 4 σ = D 3 σ = σ = All units in parts (a) and (b) are in V. (1) x chart: Center = μ = 0.75 UCL =
 Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Proactive Serving Decreases User Delay Exponentially: The Light-tailed Service Time Case
 Proactive Serving Decreae Uer Delay Exponentially: The Light-tailed Service Time Cae Shaoquan Zhang, Longbo Huang, Minghua Chen, and Xin Liu Abtract In online ervice ytem, the delay experienced by uer
Proactive Serving Decreae Uer Delay Exponentially: The Light-tailed Service Time Cae Shaoquan Zhang, Longbo Huang, Minghua Chen, and Xin Liu Abtract In online ervice ytem, the delay experienced by uer
Standard Guide for Conducting Ruggedness Tests 1
 Deignation: E 69 89 (Reapproved 996) Standard Guide for Conducting Ruggedne Tet AMERICA SOCIETY FOR TESTIG AD MATERIALS 00 Barr Harbor Dr., Wet Conhohocken, PA 948 Reprinted from the Annual Book of ASTM
Deignation: E 69 89 (Reapproved 996) Standard Guide for Conducting Ruggedne Tet AMERICA SOCIETY FOR TESTIG AD MATERIALS 00 Barr Harbor Dr., Wet Conhohocken, PA 948 Reprinted from the Annual Book of ASTM
Convergence criteria and optimization techniques for beam moments
 Pure Appl. Opt. 7 (1998) 1221 1230. Printed in the UK PII: S0963-9659(98)90684-5 Convergence criteria and optimization technique for beam moment G Gbur and P S Carney Department of Phyic and Atronomy and
Pure Appl. Opt. 7 (1998) 1221 1230. Printed in the UK PII: S0963-9659(98)90684-5 Convergence criteria and optimization technique for beam moment G Gbur and P S Carney Department of Phyic and Atronomy and
Lecture 17: Analytic Functions and Integrals (See Chapter 14 in Boas)
 Lecture 7: Analytic Function and Integral (See Chapter 4 in Boa) Thi i a good point to take a brief detour and expand on our previou dicuion of complex variable and complex function of complex variable.
Lecture 7: Analytic Function and Integral (See Chapter 4 in Boa) Thi i a good point to take a brief detour and expand on our previou dicuion of complex variable and complex function of complex variable.
Simple Observer Based Synchronization of Lorenz System with Parametric Uncertainty
 IOSR Journal of Electrical and Electronic Engineering (IOSR-JEEE) ISSN: 78-676Volume, Iue 6 (Nov. - Dec. 0), PP 4-0 Simple Oberver Baed Synchronization of Lorenz Sytem with Parametric Uncertainty Manih
IOSR Journal of Electrical and Electronic Engineering (IOSR-JEEE) ISSN: 78-676Volume, Iue 6 (Nov. - Dec. 0), PP 4-0 Simple Oberver Baed Synchronization of Lorenz Sytem with Parametric Uncertainty Manih
A Simple Approach to Synthesizing Naïve Quantized Control for Reference Tracking
 A Simple Approach to Syntheizing Naïve Quantized Control for Reference Tracking SHIANG-HUA YU Department of Electrical Engineering National Sun Yat-Sen Univerity 70 Lien-Hai Road, Kaohiung 804 TAIAN Abtract:
A Simple Approach to Syntheizing Naïve Quantized Control for Reference Tracking SHIANG-HUA YU Department of Electrical Engineering National Sun Yat-Sen Univerity 70 Lien-Hai Road, Kaohiung 804 TAIAN Abtract:
EFFECT ON PERSISTENCE OF INTRA-SPECIFIC COMPETITION IN COMPETITION MODELS
 Electronic Journal of Differential Equation, Vol. 2007(2007, No. 25, pp. 0. ISSN: 072-669. URL: http://ejde.math.txtate.edu or http://ejde.math.unt.edu ftp ejde.math.txtate.edu (login: ftp EFFECT ON PERSISTENCE
Electronic Journal of Differential Equation, Vol. 2007(2007, No. 25, pp. 0. ISSN: 072-669. URL: http://ejde.math.txtate.edu or http://ejde.math.unt.edu ftp ejde.math.txtate.edu (login: ftp EFFECT ON PERSISTENCE
The Hassenpflug Matrix Tensor Notation
 The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION. Xiaoqun Wang
 Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SUBSTANCES
 III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SBSTANCES. Work purpoe The analyi of the behaviour of a ferroelectric ubtance placed in an eternal electric field; the dependence of the electrical polariation
III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SBSTANCES. Work purpoe The analyi of the behaviour of a ferroelectric ubtance placed in an eternal electric field; the dependence of the electrical polariation
EE 508 Lecture 16. Filter Transformations. Lowpass to Bandpass Lowpass to Highpass Lowpass to Band-reject
 EE 508 Lecture 6 Filter Tranformation Lowpa to Bandpa Lowpa to Highpa Lowpa to Band-reject Review from Lat Time Theorem: If the perimeter variation and contact reitance are neglected, the tandard deviation
EE 508 Lecture 6 Filter Tranformation Lowpa to Bandpa Lowpa to Highpa Lowpa to Band-reject Review from Lat Time Theorem: If the perimeter variation and contact reitance are neglected, the tandard deviation
Hardware Implementation of Canonic Signed Digit Recoding
 IOSR Journal of VLSI and Signal Proceing (IOSR-JVSP) Volume 6, Iue 2, Ver. I (Mar. -Apr. 2016), PP 11-15 e-issn: 2319 4200, p-issn No. : 2319 4197 www.iorjournal.org Hardware Implementation of Canonic
IOSR Journal of VLSI and Signal Proceing (IOSR-JVSP) Volume 6, Iue 2, Ver. I (Mar. -Apr. 2016), PP 11-15 e-issn: 2319 4200, p-issn No. : 2319 4197 www.iorjournal.org Hardware Implementation of Canonic
