Shannon s Theory. Objectives
|
|
|
- Osborne Carter
- 6 years ago
- Views:
Transcription
1 Shannon Theory Debdeep Mukhopadhyay IIT Kharagpur Objective Undertand the definition of Perfect Secrecy Prove that a given crypto-ytem i perfectly ecured One Time Pad Entropy and it computation Ideal Cipher Equivocation of Key
2 Unconditional Security Concern the ecurity of cryptoytem when the adverary ha unbounded computational power, that i ha infinite reource. Cipher-text only Attack: Attack the cipher uing the cipher text only. When i a cipher i unconditionally ecured? A priori and A poteriori Probabilitie The plain-text ha a probability ditribution p P (x): A priori probability of a plain text The key alo ha a probability ditribution p K (K): A priori probability of the key. The cipher text i generated by applying the encryption function. Thu y=e K (x) i the cipher text. Note, that the plain text and the key are independent ditribution.
3 Attacker want to compute a poteriori probability of plain text The probability ditribution on P and K, induce a probability ditribution on C, the cipher text. For a key K, C K (x)={e K (x): x Є P} Doe the cipher text leak information about the plain text? Given, the cipher text y, we hall compute the a poteriori probability of the plain text, ie. p P (x y) and ee whether it matche with that of the a priori probability of the plain text. Example a K a b b K K 3 K K 3 K K 3 K 3 4 K P={a,b}; p P (a)=/4, p P (b)=3/4 K={K,K }, p K (K )=/, p K (K )= p K (K 3 )=/4 C={,,3,4}. What the a poteriori probabilitie of the plain text, given the cipher text from C? 3
4 b a Example K K K 3 K K 3 K P={a,b}; p P (a)=/4, p P (b)=3/4 K={K,K }, p K (K )=/, p K (K )= p K (K 3 )=/4 3 4 p C ()=p P (a)p K (K ) =(/4).(/)=/8 p C (3)=p P (a)p K (K 3 ) +p P (b) p K (K ) =(/4)(/4)+(3/4)(/4)=/ 6+3/6=/4 Likewie I can compute the other probabilitie b a Example K K K 3 K K 3 K P={a,b}; p P (a)=/4, p P (b)=3/4 K={K,K }, p K (K )=/, p K (K )= p K (K 3 )=/4 3 4 p P (a )=;p P (b )=0 p P (a )=? The can come when the plain text wa a and the key wa K or when the plain text wa b and the key wa K Given, we need to compute the probability that it came from a. I it that of chooing K? No. 4
5 b a Example K K K 3 K K 3 K P={a,b}; p P (a)=/4, p P (b)=3/4 K={K,K }, p K (K )=/, p K (K )= p K (K 3 )=/4 3 4 Given, we need to compute the probability that it came from a. The can appear with a probability: by having a a the PT and K a the key: (/4)(/4)=/6 by having b a the PT and K a the key: (3/4)(/)=6/6 p P (a )=(/6)/(7/6)=/7 Generalization of the Example p P ( x y) = p () x p ( K) P { Ky : C( K)} Kx : = d ( y) K K p ( K) p ( d ( y)) K P K 5
6 Perfect Secrecy A Cryptoytem ha perfect ecrecy if p P (x y)=p P (x) for all x Є P, y Є C. That i the a poteriori probability that the plaintext i x, given that the cipher text y i oberved, i identical to the a priori probability that the plaintext i x. Shift Cipher ha perfect ecrecy Suppoe the 6 key in the Shift Cipher are ued with equal probability /6. Then for any plain text ditribution, the Shift Cipher ha perfect ecrecy. Note that P=K=C=Z 6 and for 0 K 5 Encryption function: y=e K (x)=(x+k)mod 6 6
7 Perfect Secrecy p P ( x y) = pp( x) pc( y x) p ( y) p ( y) = p ( K) p ( d ( y)) C K P K K Z 6 = pp ( y K) = 6 6 K Z 6 p ( y x) = P ( y x mod 6) C K = 6 Hence Proved C Theorem Suppoe (P,C,K,E,D) be a cryptoytem, where K = C = P. The cryptoytem offer perfect ecrecy if and only if every key i ued with probability / K, and for every xєp and every y ЄC, there i a unique key, uch that y=e K (x). Perfect Secrecy (equivalent): p C (y x)=p C (y) Thu if Perfect Secret, a cheme ha to follow the above equation. 7
8 Cryptographic Propertie p C (y x)>0 Thi mean that for every cipher text, there i a key, K, t. y=e K (x) Thu K C. In our cae, K = C Thu, there i no cipher text, y, for which there are two key which take them to the ame plaintext. There i exactly one key, uch that y=e K (x) One-time Pad e= h=00 i=00 k=0 l=00 r= = t= Encryption: Plaintext Key = Ciphertext h e i l h i t l e r Plaintext: Key: Ciphertext: r l h t h r 8
9 One-time Pad Suppoe a wrong key i ued to decrypt: r l h t h r Ciphertext: key : Plaintext : k i l l h i t l e r e= h=00 i=00 k=0 l=00 r= = t= One-time Pad And thi i the correct key: r l h t h r Ciphertext: Key : Plaintext : h e l i k e i k e e= h=00 i=00 k=0 l=00 r= = t= 9
10 Unconditionally ecured cheme For a given ciphertext of ame ize a the plaintext, there i a equi-probable key that produce it. Thu the cheme i unconditionally ecured. Practical Problem Large quantitie of random key are neceary. Increae the problem of key ditribution. Thu we will continue to earch for cipher where one key can be ued to encrypt a large tring of data and till provide computational ecurity. Like DES (Data Encryption Standard) 0
11 One-time Pad Summary Provably ecure, when ued correctly Cipher-text provide no information about plaintext All plaintext are equally likely Pad mut be random, ued only once Pad i known only by ender and receiver Pad i ame ize a meage No aurance of meage integrity Why not ditribute meage the ame way a the pad? Entropy Reviited P={a,b}; p P (a)=/4, p P (b)=3/4 K={K,K,K 3 }, p K (K )=/, p K (K )= p K (K 3 )=/4 What i H(P)? H(P)=(/4)log (4)+(3/4)log (4/3) 0.8 H(K).5 H(C).85
12 Huffman Encoding Conider S: a dicrete ource of ymbol The meage from S: {,,,k} Can we encode thee meage uch that their average length i a hort a poible, and hopefully equal to H(S)? Huffman Code provide an optimal olution to thi problem. Informal Decription The meage et X ha a probability ditribution. Arrange them in acending order: p(x) p(x) p(x3) p(xj) Initially the code of each element are empty. Chooe the two element with minimum probabilitie Merge them into a new letter, ay x with probability a the um of x and x. Encode the maller letter 0 and the larger. When only one element remain, the code of each letter can be contructed by reading the equence backward.
13 Example X={a,b,c,d,e} p(a)=.05, p(b)=.0, p(c)=., p(d)=.3, p(e)=.6 a Illutration of the encoding b c d e c x a b f(x) d e 0 0 3
14 Some more reult on Entropy X and Y are random variable. H(X,Y) H(X)+H(Y) When X and Y are independent: H(X,Y)=H(X)+H(Y) Conditional Entropy: H(X Y)=-Σp(x y)log p(x y) H(X,Y)=H(Y)+H(X Y) H(X Y) H(X) When X and Y are independent: H(X Y)=H(X) Theorem Let (P,C,K,D,E) be an encryption algorithm. Then H(K C)=H(K)+H(P)-H(C) Proof: H(P,K)=H(C,K) [why?] or, H(P)+H(K) = H(K C)+H(C) or, H(K C)=H(K)+H(P)-H(C) Equivocation (ambiguity) of key given the ciphertext 4
15 Perfect v Ideal Cipher H(P)=H(C), then we have H(K C)=H(K) That i the uncertainty of the key given the cryptogram i the ame a that of the key without the cryptogram. Such kind of cipher are called ideal cipher For perfect cipher, we had H(P)=H(P C) or, equivalently H(C)=H(C P) Perfect v Ideal Cipher For perfect cipher, the key ize i infinite if the meage ize i infinite. however if a horter key ize i ued then the cipher can be attacked by omeone with infinite computational power. Thu, H(K C) give u thi idea of ecurity (or, inecurity) 5
16 Unicity and Brute Force Attack Q: How to protect data againt a brute force attacker with infinite computation power? Shannon defined unicity ditance (we hall call it unicity), a the leat amount of plaintext which can be deciphered uniquely from the correponding ciphertext: given unbounded reource by the attacker. Often meaured in unit of byte, letter, ymbol. An Important Point A common miconception: any cipher can be attacked by exhautively trying all poible key : Thu DES which ha a 56 bit key can alo be broken by brute force. But if the cipher i ued within it unicity then even DES i theoretically ecured, like the One Time Pad (OTP). 6
17 Spuriou Key Thu, H(K C) i the amount of uncertainty that remain of the key after the cipher text i revealed. We know, it i called the key equivocation Attacker to gue the key from the ciphertext hall gue the key and decrypt the cipher. He check whether the plaintext obtained i meaningful Englih. If not, he rule out the key. But due to the redundancy of language more than one key will pa thi tet. Thoe key, apart from the correct key, are called puriou. Entropy of Plain Text H L : meaure of the amount of information per letter of meaningful tring of plaintext. A random tring of plaintext formed uing Englih letter ha an entropy of log But Englih letter have a probability ditribution. 7
18 Frequency of Englih letter A firt order entropy of the Englih text i H(P) 4.76 In general Succeive letter have correlation, which reduce the entropy. Define P L to be the random variable that ha a probability ditribution of n-gram of plaintext Define H L a the entropy of a natural language L: H L = lim n H( Pn ) n 8
19 Fraction of exce letter Redundancy R L HL = log P For Englih Language, H L.5. Conidering H L =.5, and P =6, R L Englih Language i 75% redundant. Entropy of the language Entropy of the random language A lower Bound of equivocation of key P n : r.v repreenting n-gram plaintext C n : r.v repreenting n-gram ciphertext H(K C n )=H(K)+H(P n )-H(C n ) H(P n ) nh L (auming large n) =n(-r L )log P H(C n ) nlog C If P = C, H(K C n ) H(K)-nR L log P 9
20 Poible Key Define, K(y)={poible key given that y i the ciphertext} that i K(y) i the et of thoe key for which y i the ciphertext for meaningful plaintext When y i the ciphertext, number of key i K(y) Out of them, only one i correct. Ret are puriou. So, number of puriou key= K(y) - Expected number of puriou key Expected number of puriou key=average number of puriou key over all poible ciphertext i denoted by n. = p( y)( K( y) ) n n y C =( py ( ) Ky ( ) ) n y C 0
21 Computing the upper bound of equivocation of key n HKC ( ) = pyhk ( ) ( y) n y C n y C n y C pyhky ( ) ( ( )) py ( )log ( Ky ( ) ) log ( py ( ) Ky ( ) ) = log ( + ) n y C n Lower Bound of puriou key Combining the previou reult: HK ( ) nrllog P log ( n+ ) log ( n+ ) HK ( ) nrllog P If the key are choen equi-probably: H(K)=log K. Hence, we have: n K nrl P
22 Unicity Ditance Thu increaing n, reduce the number of puriou key. Unicity Ditance i the number of ciphertext, n 0 for which the number of puriou key i reduced to zero. n n = 0 log K R log P L Thi calculation may not be accurate for large value of n Unicity Ditance for Subtitution Cipher P =6 K =6! 4 x 0 6, R L =0.75 n 0 =5 (approx) Given a ciphertext tring of length 5, it i poible to predict the correct key uniquely Thu key ize alone doe not guarantee ecurity, if brute force i poible to an attacker with infinite computational power.
23 Aignment Let n be a poitive integer. A Latin quare of order n i an nxn array L with integer,,,n uch that every integer occur exactly once in each row and column. An example for n=3 i: Aignment Given any Latin quare of order n, we can define a related cryptoytem, e i (j)=l(i,j), where i,j n. Prove from the computation of probabilitie that the Latin quare cryptoytem achieve perfect ecrecy. Deadline for ubmiion: Pleae ubmit hand written proof. 3
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
 Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. # 01 Lecture No. # 08 Shannon s Theory (Contd.)
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. # 01 Lecture No. # 08 Shannon s Theory (Contd.)
Lecture 8 - Cryptography and Information Theory
 Lecture 8 - Cryptography and Information Theory Jan Bouda FI MU April 22, 2010 Jan Bouda (FI MU) Lecture 8 - Cryptography and Information Theory April 22, 2010 1 / 25 Part I Cryptosystem Jan Bouda (FI
Lecture 8 - Cryptography and Information Theory Jan Bouda FI MU April 22, 2010 Jan Bouda (FI MU) Lecture 8 - Cryptography and Information Theory April 22, 2010 1 / 25 Part I Cryptosystem Jan Bouda (FI
Cryptography - Session 2
 Cryptography - Session 2 O. Geil, Aalborg University November 18, 2010 Random variables Discrete random variable X: 1. Probability distribution on finite set X. 2. For x X write Pr(x) = Pr(X = x). X and
Cryptography - Session 2 O. Geil, Aalborg University November 18, 2010 Random variables Discrete random variable X: 1. Probability distribution on finite set X. 2. For x X write Pr(x) = Pr(X = x). X and
Topics. Probability Theory. Perfect Secrecy. Information Theory
 Topics Probability Theory Perfect Secrecy Information Theory Some Terms (P,C,K,E,D) Computational Security Computational effort required to break cryptosystem Provable Security Relative to another, difficult
Topics Probability Theory Perfect Secrecy Information Theory Some Terms (P,C,K,E,D) Computational Security Computational effort required to break cryptosystem Provable Security Relative to another, difficult
Quantitative Information Leakage. Lecture 9
 Quantitative Information Leakage Lecture 9 1 The baic model: Sytem = Information-Theoretic channel Secret Information Obervable 1 o1... Sytem... m on Input Output 2 Toward a quantitative notion of leakage
Quantitative Information Leakage Lecture 9 1 The baic model: Sytem = Information-Theoretic channel Secret Information Obervable 1 o1... Sytem... m on Input Output 2 Toward a quantitative notion of leakage
Lecture 7: Testing Distributions
 CSE 5: Sublinear (and Streaming) Algorithm Spring 014 Lecture 7: Teting Ditribution April 1, 014 Lecturer: Paul Beame Scribe: Paul Beame 1 Teting Uniformity of Ditribution We return today to property teting
CSE 5: Sublinear (and Streaming) Algorithm Spring 014 Lecture 7: Teting Ditribution April 1, 014 Lecturer: Paul Beame Scribe: Paul Beame 1 Teting Uniformity of Ditribution We return today to property teting
Lecture 9: Shor s Algorithm
 Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Social Studies 201 Notes for March 18, 2005
 1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
Problem Set 8 Solutions
 Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Cryptography. Lecture 2: Perfect Secrecy and its Limitations. Gil Segev
 Cryptography Lecture 2: Perfect Secrecy and its Limitations Gil Segev Last Week Symmetric-key encryption (KeyGen, Enc, Dec) Historical ciphers that are completely broken The basic principles of modern
Cryptography Lecture 2: Perfect Secrecy and its Limitations Gil Segev Last Week Symmetric-key encryption (KeyGen, Enc, Dec) Historical ciphers that are completely broken The basic principles of modern
EME : extending EME to handle arbitrary-length messages with associated data
 EME : extending EME to handle arbitrary-length meage with aociated data (Preliminary Report) Shai Halevi May 27, 2004 Abtract Thi work decribe a mode of operation, EME, that turn a regular block cipher
EME : extending EME to handle arbitrary-length meage with aociated data (Preliminary Report) Shai Halevi May 27, 2004 Abtract Thi work decribe a mode of operation, EME, that turn a regular block cipher
A Provably Secure Scheme for Remote User Authentication
 A Provably Secure Scheme for Remote Uer Authentication Fuw-Yi Yang 1, Su-Hui Chiu 2 1 Department of Computer Science and Information Engineering, Chaoyang Univerity of Technology Taichung County 41349,
A Provably Secure Scheme for Remote Uer Authentication Fuw-Yi Yang 1, Su-Hui Chiu 2 1 Department of Computer Science and Information Engineering, Chaoyang Univerity of Technology Taichung County 41349,
Codes Correcting Two Deletions
 1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
Outline. Computer Science 418. Number of Keys in the Sum. More on Perfect Secrecy, One-Time Pad, Entropy. Mike Jacobson. Week 3
 Outline Computer Science 48 More on Perfect Secrecy, One-Time Pad, Mike Jacobson Department of Computer Science University of Calgary Week 3 2 3 Mike Jacobson (University of Calgary) Computer Science 48
Outline Computer Science 48 More on Perfect Secrecy, One-Time Pad, Mike Jacobson Department of Computer Science University of Calgary Week 3 2 3 Mike Jacobson (University of Calgary) Computer Science 48
THE UNIVERSITY OF CALGARY FACULTY OF SCIENCE DEPARTMENT OF COMPUTER SCIENCE DEPARTMENT OF MATHEMATICS & STATISTICS MIDTERM EXAMINATION 1 FALL 2018
 THE UNIVERSITY OF CALGARY FACULTY OF SCIENCE DEPARTMENT OF COMPUTER SCIENCE DEPARTMENT OF MATHEMATICS & STATISTICS MIDTERM EXAMINATION 1 FALL 2018 CPSC 418/MATH 318 L01 October 17, 2018 Time: 50 minutes
THE UNIVERSITY OF CALGARY FACULTY OF SCIENCE DEPARTMENT OF COMPUTER SCIENCE DEPARTMENT OF MATHEMATICS & STATISTICS MIDTERM EXAMINATION 1 FALL 2018 CPSC 418/MATH 318 L01 October 17, 2018 Time: 50 minutes
Week 3 Statistics for bioinformatics and escience
 Week 3 Statitic for bioinformatic and escience Line Skotte 28. november 2008 2.9.3-4) In thi eercie we conider microrna data from Human and Moue. The data et repreent 685 independent realiation of the
Week 3 Statitic for bioinformatic and escience Line Skotte 28. november 2008 2.9.3-4) In thi eercie we conider microrna data from Human and Moue. The data et repreent 685 independent realiation of the
Chapter 2 Sampling and Quantization. In order to investigate sampling and quantization, the difference between analog
 Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Social Studies 201 Notes for November 14, 2003
 1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
3F1: Signals and Systems INFORMATION THEORY Examples Paper Solutions
 Engineering Tripos Part IIA THIRD YEAR 3F: Signals and Systems INFORMATION THEORY Examples Paper Solutions. Let the joint probability mass function of two binary random variables X and Y be given in the
Engineering Tripos Part IIA THIRD YEAR 3F: Signals and Systems INFORMATION THEORY Examples Paper Solutions. Let the joint probability mass function of two binary random variables X and Y be given in the
c n b n 0. c k 0 x b n < 1 b k b n = 0. } of integers between 0 and b 1 such that x = b k. b k c k c k
 1. Exitence Let x (0, 1). Define c k inductively. Suppoe c 1,..., c k 1 are already defined. We let c k be the leat integer uch that x k An eay proof by induction give that and for all k. Therefore c n
1. Exitence Let x (0, 1). Define c k inductively. Suppoe c 1,..., c k 1 are already defined. We let c k be the leat integer uch that x k An eay proof by induction give that and for all k. Therefore c n
UNIT 15 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS
 UNIT 1 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS Structure 1.1 Introduction Objective 1.2 Redundancy 1.3 Reliability of k-out-of-n Sytem 1.4 Reliability of Standby Sytem 1. Summary 1.6 Solution/Anwer
UNIT 1 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS Structure 1.1 Introduction Objective 1.2 Redundancy 1.3 Reliability of k-out-of-n Sytem 1.4 Reliability of Standby Sytem 1. Summary 1.6 Solution/Anwer
11.2 Stability. A gain element is an active device. One potential problem with every active circuit is its stability
 5/7/2007 11_2 tability 1/2 112 tability eading Aignment: pp 542-548 A gain element i an active device One potential problem with every active circuit i it tability HO: TABIITY Jim tile The Univ of Kana
5/7/2007 11_2 tability 1/2 112 tability eading Aignment: pp 542-548 A gain element i an active device One potential problem with every active circuit i it tability HO: TABIITY Jim tile The Univ of Kana
List coloring hypergraphs
 Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
μ + = σ = D 4 σ = D 3 σ = σ = All units in parts (a) and (b) are in V. (1) x chart: Center = μ = 0.75 UCL =
 Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Topic 6. Digital Signatures and Identity Based Encryption
 Topic 6. Digital Signature and Identity Baed Encryption. Security of Public-key Cryptography 2. Example of Public-key Algorithm: Diffie- Hellman Key Exchange Scheme 3. RSA Encryption and Digital Signature
Topic 6. Digital Signature and Identity Baed Encryption. Security of Public-key Cryptography 2. Example of Public-key Algorithm: Diffie- Hellman Key Exchange Scheme 3. RSA Encryption and Digital Signature
Clustering Methods without Given Number of Clusters
 Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Shannon s Theory of Secrecy Systems
 Shannon s Theory of Secrecy Systems See: C. E. Shannon, Communication Theory of Secrecy Systems, Bell Systems Technical Journal, Vol. 28, pp. 656 715, 1948. c Eli Biham - March 1, 2011 59 Shannon s Theory
Shannon s Theory of Secrecy Systems See: C. E. Shannon, Communication Theory of Secrecy Systems, Bell Systems Technical Journal, Vol. 28, pp. 656 715, 1948. c Eli Biham - March 1, 2011 59 Shannon s Theory
EC381/MN308 Probability and Some Statistics. Lecture 7 - Outline. Chapter Cumulative Distribution Function (CDF) Continuous Random Variables
 EC38/MN38 Probability and Some Statitic Yanni Pachalidi yannip@bu.edu, http://ionia.bu.edu/ Lecture 7 - Outline. Continuou Random Variable Dept. of Manufacturing Engineering Dept. of Electrical and Computer
EC38/MN38 Probability and Some Statitic Yanni Pachalidi yannip@bu.edu, http://ionia.bu.edu/ Lecture 7 - Outline. Continuou Random Variable Dept. of Manufacturing Engineering Dept. of Electrical and Computer
Computer Science A Cryptography and Data Security. Claude Crépeau
 Computer Science 308-547A Cryptography and Data Security Claude Crépeau These notes are, largely, transcriptions by Anton Stiglic of class notes from the former course Cryptography and Data Security (308-647A)
Computer Science 308-547A Cryptography and Data Security Claude Crépeau These notes are, largely, transcriptions by Anton Stiglic of class notes from the former course Cryptography and Data Security (308-647A)
Shift Cipher. For 0 i 25, the ith plaintext character is. E.g. k = 3
 Shift Cipher For 0 i 25, the ith plaintext character is shifted by some value 0 k 25 (mod 26). E.g. k = 3 a b c d e f g h i j k l m n o p q r s t u v w x y z D E F G H I J K L M N O P Q R S T U V W X Y
Shift Cipher For 0 i 25, the ith plaintext character is shifted by some value 0 k 25 (mod 26). E.g. k = 3 a b c d e f g h i j k l m n o p q r s t u v w x y z D E F G H I J K L M N O P Q R S T U V W X Y
Linear Motion, Speed & Velocity
 Add Important Linear Motion, Speed & Velocity Page: 136 Linear Motion, Speed & Velocity NGSS Standard: N/A MA Curriculum Framework (006): 1.1, 1. AP Phyic 1 Learning Objective: 3.A.1.1, 3.A.1.3 Knowledge/Undertanding
Add Important Linear Motion, Speed & Velocity Page: 136 Linear Motion, Speed & Velocity NGSS Standard: N/A MA Curriculum Framework (006): 1.1, 1. AP Phyic 1 Learning Objective: 3.A.1.1, 3.A.1.3 Knowledge/Undertanding
Cryptographic Engineering
 Cryptographic Engineering Clément PERNET M2 Cyber Security, UFR-IM 2 AG, Univ. Grenoble-Alpes ENSIMAG, Grenoble INP Outline Unconditional security of symmetric cryptosystem Probabilities and information
Cryptographic Engineering Clément PERNET M2 Cyber Security, UFR-IM 2 AG, Univ. Grenoble-Alpes ENSIMAG, Grenoble INP Outline Unconditional security of symmetric cryptosystem Probabilities and information
March 18, 2014 Academic Year 2013/14
 POLITONG - SHANGHAI BASIC AUTOMATIC CONTROL Exam grade March 8, 4 Academic Year 3/4 NAME (Pinyin/Italian)... STUDENT ID Ue only thee page (including the back) for anwer. Do not ue additional heet. Ue of
POLITONG - SHANGHAI BASIC AUTOMATIC CONTROL Exam grade March 8, 4 Academic Year 3/4 NAME (Pinyin/Italian)... STUDENT ID Ue only thee page (including the back) for anwer. Do not ue additional heet. Ue of
Identity-based Hierarchical Designated Decryption *
 JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 26, 243-259 (200) Identity-baed Hierarchical Deignated Decryption * SHU-HUI CHANG, CHUAN-MING LI 2 AND TZONELIH HWANG 3 Center of General Education Southern
JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 26, 243-259 (200) Identity-baed Hierarchical Deignated Decryption * SHU-HUI CHANG, CHUAN-MING LI 2 AND TZONELIH HWANG 3 Center of General Education Southern
Preemptive scheduling on a small number of hierarchical machines
 Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Jul 4, 2005 turbo_code_primer Revision 0.0. Turbo Code Primer
 Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
7.2 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 281
 72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
A Study on Simulating Convolutional Codes and Turbo Codes
 A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
Avoiding Forbidden Submatrices by Row Deletions
 Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Outline. CPSC 418/MATH 318 Introduction to Cryptography. Information Theory. Partial Information. Perfect Secrecy, One-Time Pad
 Outline CPSC 418/MATH 318 Introduction to Cryptography, One-Time Pad Renate Scheidler Department of Mathematics & Statistics Department of Computer Science University of Calgary Based in part on slides
Outline CPSC 418/MATH 318 Introduction to Cryptography, One-Time Pad Renate Scheidler Department of Mathematics & Statistics Department of Computer Science University of Calgary Based in part on slides
SOME RESULTS ON INFINITE POWER TOWERS
 NNTDM 16 2010) 3, 18-24 SOME RESULTS ON INFINITE POWER TOWERS Mladen Vailev - Miana 5, V. Hugo Str., Sofia 1124, Bulgaria E-mail:miana@abv.bg Abtract To my friend Kratyu Gumnerov In the paper the infinite
NNTDM 16 2010) 3, 18-24 SOME RESULTS ON INFINITE POWER TOWERS Mladen Vailev - Miana 5, V. Hugo Str., Sofia 1124, Bulgaria E-mail:miana@abv.bg Abtract To my friend Kratyu Gumnerov In the paper the infinite
The machines in the exercise work as follows:
 Tik-79.148 Spring 2001 Introduction to Theoretical Computer Science Tutorial 9 Solution to Demontration Exercie 4. Contructing a complex Turing machine can be very laboriou. With the help of machine chema
Tik-79.148 Spring 2001 Introduction to Theoretical Computer Science Tutorial 9 Solution to Demontration Exercie 4. Contructing a complex Turing machine can be very laboriou. With the help of machine chema
An Inequality for Nonnegative Matrices and the Inverse Eigenvalue Problem
 An Inequality for Nonnegative Matrice and the Invere Eigenvalue Problem Robert Ream Program in Mathematical Science The Univerity of Texa at Dalla Box 83688, Richardon, Texa 7583-688 Abtract We preent
An Inequality for Nonnegative Matrice and the Invere Eigenvalue Problem Robert Ream Program in Mathematical Science The Univerity of Texa at Dalla Box 83688, Richardon, Texa 7583-688 Abtract We preent
MATEMATIK Datum: Tid: eftermiddag. A.Heintz Telefonvakt: Anders Martinsson Tel.:
 MATEMATIK Datum: 20-08-25 Tid: eftermiddag GU, Chalmer Hjälpmedel: inga A.Heintz Telefonvakt: Ander Martinon Tel.: 073-07926. Löningar till tenta i ODE och matematik modellering, MMG5, MVE6. Define what
MATEMATIK Datum: 20-08-25 Tid: eftermiddag GU, Chalmer Hjälpmedel: inga A.Heintz Telefonvakt: Ander Martinon Tel.: 073-07926. Löningar till tenta i ODE och matematik modellering, MMG5, MVE6. Define what
Introduction to Laplace Transform Techniques in Circuit Analysis
 Unit 6 Introduction to Laplace Tranform Technique in Circuit Analyi In thi unit we conider the application of Laplace Tranform to circuit analyi. A relevant dicuion of the one-ided Laplace tranform i found
Unit 6 Introduction to Laplace Tranform Technique in Circuit Analyi In thi unit we conider the application of Laplace Tranform to circuit analyi. A relevant dicuion of the one-ided Laplace tranform i found
Improving the Efficiency of a Digital Filtering Scheme for Diabatic Initialization
 1976 MONTHLY WEATHER REVIEW VOLUME 15 Improving the Efficiency of a Digital Filtering Scheme for Diabatic Initialization PETER LYNCH Met Éireann, Dublin, Ireland DOMINIQUE GIARD CNRM/GMAP, Météo-France,
1976 MONTHLY WEATHER REVIEW VOLUME 15 Improving the Efficiency of a Digital Filtering Scheme for Diabatic Initialization PETER LYNCH Met Éireann, Dublin, Ireland DOMINIQUE GIARD CNRM/GMAP, Météo-France,
Assignment for Mathematics for Economists Fall 2016
 Due date: Mon. Nov. 1. Reading: CSZ, Ch. 5, Ch. 8.1 Aignment for Mathematic for Economit Fall 016 We now turn to finihing our coverage of concavity/convexity. There are two part: Jenen inequality for concave/convex
Due date: Mon. Nov. 1. Reading: CSZ, Ch. 5, Ch. 8.1 Aignment for Mathematic for Economit Fall 016 We now turn to finihing our coverage of concavity/convexity. There are two part: Jenen inequality for concave/convex
SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lectures 41-48)
 Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Bogoliubov Transformation in Classical Mechanics
 Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Chapter 5 Consistency, Zero Stability, and the Dahlquist Equivalence Theorem
 Chapter 5 Conitency, Zero Stability, and the Dahlquit Equivalence Theorem In Chapter 2 we dicued convergence of numerical method and gave an experimental method for finding the rate of convergence (aka,
Chapter 5 Conitency, Zero Stability, and the Dahlquit Equivalence Theorem In Chapter 2 we dicued convergence of numerical method and gave an experimental method for finding the rate of convergence (aka,
Convex Hulls of Curves Sam Burton
 Convex Hull of Curve Sam Burton 1 Introduction Thi paper will primarily be concerned with determining the face of convex hull of curve of the form C = {(t, t a, t b ) t [ 1, 1]}, a < b N in R 3. We hall
Convex Hull of Curve Sam Burton 1 Introduction Thi paper will primarily be concerned with determining the face of convex hull of curve of the form C = {(t, t a, t b ) t [ 1, 1]}, a < b N in R 3. We hall
On the Isomorphism of Fractional Factorial Designs 1
 journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
Suggested Answers To Exercises. estimates variability in a sampling distribution of random means. About 68% of means fall
 Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Online supplementary information
 Electronic Supplementary Material (ESI) for Soft Matter. Thi journal i The Royal Society of Chemitry 15 Online upplementary information Governing Equation For the vicou flow, we aume that the liquid thickne
Electronic Supplementary Material (ESI) for Soft Matter. Thi journal i The Royal Society of Chemitry 15 Online upplementary information Governing Equation For the vicou flow, we aume that the liquid thickne
REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS. Logic and Applications 2015 (LAP 2015) September 21-25, 2015, Dubrovnik, Croatia
 REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS SMILE MARKOVSKI Faculty of Computer Science and Engineering, S Ciryl and Methodiu Univerity in Skopje, MACEDONIA mile.markovki@gmail.com Logic
REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS SMILE MARKOVSKI Faculty of Computer Science and Engineering, S Ciryl and Methodiu Univerity in Skopje, MACEDONIA mile.markovki@gmail.com Logic
Physics 741 Graduate Quantum Mechanics 1 Solutions to Final Exam, Fall 2014
 Phyic 7 Graduate Quantum Mechanic Solution to inal Eam all 0 Each quetion i worth 5 point with point for each part marked eparately Some poibly ueful formula appear at the end of the tet In four dimenion
Phyic 7 Graduate Quantum Mechanic Solution to inal Eam all 0 Each quetion i worth 5 point with point for each part marked eparately Some poibly ueful formula appear at the end of the tet In four dimenion
Physics 2212 G Quiz #2 Solutions Spring 2018
 Phyic 2212 G Quiz #2 Solution Spring 2018 I. (16 point) A hollow inulating phere ha uniform volume charge denity ρ, inner radiu R, and outer radiu 3R. Find the magnitude of the electric field at a ditance
Phyic 2212 G Quiz #2 Solution Spring 2018 I. (16 point) A hollow inulating phere ha uniform volume charge denity ρ, inner radiu R, and outer radiu 3R. Find the magnitude of the electric field at a ditance
Electronic Theses and Dissertations
 Eat Tenneee State Univerity Digital Common @ Eat Tenneee State Univerity Electronic Thee and Diertation Student Work 5-208 Vector Partition Jennifer French Eat Tenneee State Univerity Follow thi and additional
Eat Tenneee State Univerity Digital Common @ Eat Tenneee State Univerity Electronic Thee and Diertation Student Work 5-208 Vector Partition Jennifer French Eat Tenneee State Univerity Follow thi and additional
SECTION x2 x > 0, t > 0, (8.19a)
 SECTION 8.5 433 8.5 Application of aplace Tranform to Partial Differential Equation In Section 8.2 and 8.3 we illutrated the effective ue of aplace tranform in olving ordinary differential equation. The
SECTION 8.5 433 8.5 Application of aplace Tranform to Partial Differential Equation In Section 8.2 and 8.3 we illutrated the effective ue of aplace tranform in olving ordinary differential equation. The
CS 170: Midterm Exam II University of California at Berkeley Department of Electrical Engineering and Computer Sciences Computer Science Division
 1 1 April 000 Demmel / Shewchuk CS 170: Midterm Exam II Univerity of California at Berkeley Department of Electrical Engineering and Computer Science Computer Science Diviion hi i a cloed book, cloed calculator,
1 1 April 000 Demmel / Shewchuk CS 170: Midterm Exam II Univerity of California at Berkeley Department of Electrical Engineering and Computer Science Computer Science Diviion hi i a cloed book, cloed calculator,
arxiv: v1 [math.mg] 25 Aug 2011
![arxiv: v1 [math.mg] 25 Aug 2011 arxiv: v1 [math.mg] 25 Aug 2011](/thumbs/72/67862976.jpg) ABSORBING ANGLES, STEINER MINIMAL TREES, AND ANTIPODALITY HORST MARTINI, KONRAD J. SWANEPOEL, AND P. OLOFF DE WET arxiv:08.5046v [math.mg] 25 Aug 20 Abtract. We give a new proof that a tar {op i : i =,...,
ABSORBING ANGLES, STEINER MINIMAL TREES, AND ANTIPODALITY HORST MARTINI, KONRAD J. SWANEPOEL, AND P. OLOFF DE WET arxiv:08.5046v [math.mg] 25 Aug 20 Abtract. We give a new proof that a tar {op i : i =,...,
William Stallings Copyright 2010
 A PPENDIX F M EASURES OF S ECRECY AND S ECURITY William Stallings Copyright 2010 F.1 PERFECT SECRECY...2! F.2 INFORMATION AND ENTROPY...8! Information...8! Entropy...10! Properties of the Entropy Function...12!
A PPENDIX F M EASURES OF S ECRECY AND S ECURITY William Stallings Copyright 2010 F.1 PERFECT SECRECY...2! F.2 INFORMATION AND ENTROPY...8! Information...8! Entropy...10! Properties of the Entropy Function...12!
Primitive Digraphs with the Largest Scrambling Index
 Primitive Digraph with the Larget Scrambling Index Mahmud Akelbek, Steve Kirkl 1 Department of Mathematic Statitic, Univerity of Regina, Regina, Sakatchewan, Canada S4S 0A Abtract The crambling index of
Primitive Digraph with the Larget Scrambling Index Mahmud Akelbek, Steve Kirkl 1 Department of Mathematic Statitic, Univerity of Regina, Regina, Sakatchewan, Canada S4S 0A Abtract The crambling index of
Exploiting Transformations of the Galois Configuration to Improve Guess-and-Determine Attacks on NFSRs
 Exploiting Tranformation of the Galoi Configuration to Improve Gue-and-Determine Attack on NFSR Gefei Li, Yuval Yarom, and Damith C. Ranainghe Univerity of Adelaide, Adelaide, South Autralia, Autralia
Exploiting Tranformation of the Galoi Configuration to Improve Gue-and-Determine Attack on NFSR Gefei Li, Yuval Yarom, and Damith C. Ranainghe Univerity of Adelaide, Adelaide, South Autralia, Autralia
Lecture 8: Period Finding: Simon s Problem over Z N
 Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS
 www.arpapre.com/volume/vol29iue1/ijrras_29_1_01.pdf RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS Sevcan Demir Atalay 1,* & Özge Elmataş Gültekin
www.arpapre.com/volume/vol29iue1/ijrras_29_1_01.pdf RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS Sevcan Demir Atalay 1,* & Özge Elmataş Gültekin
III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SUBSTANCES
 III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SBSTANCES. Work purpoe The analyi of the behaviour of a ferroelectric ubtance placed in an eternal electric field; the dependence of the electrical polariation
III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SBSTANCES. Work purpoe The analyi of the behaviour of a ferroelectric ubtance placed in an eternal electric field; the dependence of the electrical polariation
Halliday/Resnick/Walker 7e Chapter 6
 HRW 7e Chapter 6 Page of Halliday/Renick/Walker 7e Chapter 6 3. We do not conider the poibility that the bureau might tip, and treat thi a a purely horizontal motion problem (with the peron puh F in the
HRW 7e Chapter 6 Page of Halliday/Renick/Walker 7e Chapter 6 3. We do not conider the poibility that the bureau might tip, and treat thi a a purely horizontal motion problem (with the peron puh F in the
Dimensional Analysis A Tool for Guiding Mathematical Calculations
 Dimenional Analyi A Tool for Guiding Mathematical Calculation Dougla A. Kerr Iue 1 February 6, 2010 ABSTRACT AND INTRODUCTION In converting quantitie from one unit to another, we may know the applicable
Dimenional Analyi A Tool for Guiding Mathematical Calculation Dougla A. Kerr Iue 1 February 6, 2010 ABSTRACT AND INTRODUCTION In converting quantitie from one unit to another, we may know the applicable
Cryptography CS 555. Topic 2: Evolution of Classical Cryptography CS555. Topic 2 1
 Cryptography CS 555 Topic 2: Evolution of Classical Cryptography Topic 2 1 Lecture Outline Basics of probability Vigenere cipher. Attacks on Vigenere: Kasisky Test and Index of Coincidence Cipher machines:
Cryptography CS 555 Topic 2: Evolution of Classical Cryptography Topic 2 1 Lecture Outline Basics of probability Vigenere cipher. Attacks on Vigenere: Kasisky Test and Index of Coincidence Cipher machines:
Chapter 4. The Laplace Transform Method
 Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS
 CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
SOLUTIONS TO ALGEBRAIC GEOMETRY AND ARITHMETIC CURVES BY QING LIU. I will collect my solutions to some of the exercises in this book in this document.
 SOLUTIONS TO ALGEBRAIC GEOMETRY AND ARITHMETIC CURVES BY QING LIU CİHAN BAHRAN I will collect my olution to ome of the exercie in thi book in thi document. Section 2.1 1. Let A = k[[t ]] be the ring of
SOLUTIONS TO ALGEBRAIC GEOMETRY AND ARITHMETIC CURVES BY QING LIU CİHAN BAHRAN I will collect my olution to ome of the exercie in thi book in thi document. Section 2.1 1. Let A = k[[t ]] be the ring of
CPSC 467b: Cryptography and Computer Security
 CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 3 January 22, 2013 CPSC 467b, Lecture 3 1/35 Perfect secrecy Caesar cipher Loss of perfection Classical ciphers One-time pad Affine
CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 3 January 22, 2013 CPSC 467b, Lecture 3 1/35 Perfect secrecy Caesar cipher Loss of perfection Classical ciphers One-time pad Affine
A Strategy for Constructing Fast Round Functions with Practical Security Against Differential and Linear Cryptanalysis
 A Strategy for Contructing Fat Round Function with Practical Security Againt Differential and Linear Cryptanalyi Maayuki Kanda, Youichi Takahima 2, Tutomu Matumoto 3, Kazumaro Aoki,andKazuoOhta NTT Information
A Strategy for Contructing Fat Round Function with Practical Security Againt Differential and Linear Cryptanalyi Maayuki Kanda, Youichi Takahima 2, Tutomu Matumoto 3, Kazumaro Aoki,andKazuoOhta NTT Information
Lecture Note 3 Date:
 P.Lafourcade Lecture Note 3 Date: 28.09.2009 Security models 1st Semester 2007/2008 ROUAULT Boris GABIAM Amanda ARNEDO Pedro 1 Contents 1 Perfect Encryption 3 1.1 Notations....................................
P.Lafourcade Lecture Note 3 Date: 28.09.2009 Security models 1st Semester 2007/2008 ROUAULT Boris GABIAM Amanda ARNEDO Pedro 1 Contents 1 Perfect Encryption 3 1.1 Notations....................................
EE Control Systems LECTURE 14
 Updated: Tueday, March 3, 999 EE 434 - Control Sytem LECTURE 4 Copyright FL Lewi 999 All right reerved ROOT LOCUS DESIGN TECHNIQUE Suppoe the cloed-loop tranfer function depend on a deign parameter k We
Updated: Tueday, March 3, 999 EE 434 - Control Sytem LECTURE 4 Copyright FL Lewi 999 All right reerved ROOT LOCUS DESIGN TECHNIQUE Suppoe the cloed-loop tranfer function depend on a deign parameter k We
Adder Circuits Ivor Page 1
 Adder Circuit Adder Circuit Ivor Page 4. The Ripple Carr Adder The ripple carr adder i probabl the implet parallel binar adder. It i made up of k full-adder tage, where each full-adder can be convenientl
Adder Circuit Adder Circuit Ivor Page 4. The Ripple Carr Adder The ripple carr adder i probabl the implet parallel binar adder. It i made up of k full-adder tage, where each full-adder can be convenientl
Optimal Coordination of Samples in Business Surveys
 Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Solving Differential Equations by the Laplace Transform and by Numerical Methods
 36CH_PHCalter_TechMath_95099 3//007 :8 PM Page Solving Differential Equation by the Laplace Tranform and by Numerical Method OBJECTIVES When you have completed thi chapter, you hould be able to: Find the
36CH_PHCalter_TechMath_95099 3//007 :8 PM Page Solving Differential Equation by the Laplace Tranform and by Numerical Method OBJECTIVES When you have completed thi chapter, you hould be able to: Find the
Manprit Kaur and Arun Kumar
 CUBIC X-SPLINE INTERPOLATORY FUNCTIONS Manprit Kaur and Arun Kumar manpreet2410@gmail.com, arun04@rediffmail.com Department of Mathematic and Computer Science, R. D. Univerity, Jabalpur, INDIA. Abtract:
CUBIC X-SPLINE INTERPOLATORY FUNCTIONS Manprit Kaur and Arun Kumar manpreet2410@gmail.com, arun04@rediffmail.com Department of Mathematic and Computer Science, R. D. Univerity, Jabalpur, INDIA. Abtract:
Math Skills. Scientific Notation. Uncertainty in Measurements. Appendix A5 SKILLS HANDBOOK
 ppendix 5 Scientific Notation It i difficult to work with very large or very mall number when they are written in common decimal notation. Uually it i poible to accommodate uch number by changing the SI
ppendix 5 Scientific Notation It i difficult to work with very large or very mall number when they are written in common decimal notation. Uually it i poible to accommodate uch number by changing the SI
Online Appendix for Managerial Attention and Worker Performance by Marina Halac and Andrea Prat
 Online Appendix for Managerial Attention and Worker Performance by Marina Halac and Andrea Prat Thi Online Appendix contain the proof of our reult for the undicounted limit dicued in Section 2 of the paper,
Online Appendix for Managerial Attention and Worker Performance by Marina Halac and Andrea Prat Thi Online Appendix contain the proof of our reult for the undicounted limit dicued in Section 2 of the paper,
Z a>2 s 1n = X L - m. X L = m + Z a>2 s 1n X L = The decision rule for this one-tail test is
 M09_BERE8380_12_OM_C09.QD 2/21/11 3:44 PM Page 1 9.6 The Power of a Tet 9.6 The Power of a Tet 1 Section 9.1 defined Type I and Type II error and their aociated rik. Recall that a repreent the probability
M09_BERE8380_12_OM_C09.QD 2/21/11 3:44 PM Page 1 9.6 The Power of a Tet 9.6 The Power of a Tet 1 Section 9.1 defined Type I and Type II error and their aociated rik. Recall that a repreent the probability
Root Locus Diagram. Root loci: The portion of root locus when k assume positive values: that is 0
 Objective Root Locu Diagram Upon completion of thi chapter you will be able to: Plot the Root Locu for a given Tranfer Function by varying gain of the ytem, Analye the tability of the ytem from the root
Objective Root Locu Diagram Upon completion of thi chapter you will be able to: Plot the Root Locu for a given Tranfer Function by varying gain of the ytem, Analye the tability of the ytem from the root
If Y is normally Distributed, then and 2 Y Y 10. σ σ
 ull Hypothei Significance Teting V. APS 50 Lecture ote. B. Dudek. ot for General Ditribution. Cla Member Uage Only. Chi-Square and F-Ditribution, and Diperion Tet Recall from Chapter 4 material on: ( )
ull Hypothei Significance Teting V. APS 50 Lecture ote. B. Dudek. ot for General Ditribution. Cla Member Uage Only. Chi-Square and F-Ditribution, and Diperion Tet Recall from Chapter 4 material on: ( )
At the end of this lesson, the students should be able to understand:
 Intructional Objective: At the end of thi leon, the tudent hould be able to undertand: Baic failure mechanim of riveted joint. Concept of deign of a riveted joint. 1. Strength of riveted joint: Strength
Intructional Objective: At the end of thi leon, the tudent hould be able to undertand: Baic failure mechanim of riveted joint. Concept of deign of a riveted joint. 1. Strength of riveted joint: Strength
Linear System Fundamentals
 Linear Sytem Fundamental MEM 355 Performance Enhancement of Dynamical Sytem Harry G. Kwatny Department of Mechanical Engineering & Mechanic Drexel Univerity Content Sytem Repreentation Stability Concept
Linear Sytem Fundamental MEM 355 Performance Enhancement of Dynamical Sytem Harry G. Kwatny Department of Mechanical Engineering & Mechanic Drexel Univerity Content Sytem Repreentation Stability Concept
PERFECT SECRECY AND ADVERSARIAL INDISTINGUISHABILITY
 PERFECT SECRECY AND ADVERSARIAL INDISTINGUISHABILITY BURTON ROSENBERG UNIVERSITY OF MIAMI Contents 1. Perfect Secrecy 1 1.1. A Perfectly Secret Cipher 2 1.2. Odds Ratio and Bias 3 1.3. Conditions for Perfect
PERFECT SECRECY AND ADVERSARIAL INDISTINGUISHABILITY BURTON ROSENBERG UNIVERSITY OF MIAMI Contents 1. Perfect Secrecy 1 1.1. A Perfectly Secret Cipher 2 1.2. Odds Ratio and Bias 3 1.3. Conditions for Perfect
ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION. Xiaoqun Wang
 Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
Unbounded solutions of second order discrete BVPs on infinite intervals
 Available online at www.tjna.com J. Nonlinear Sci. Appl. 9 206), 357 369 Reearch Article Unbounded olution of econd order dicrete BVP on infinite interval Hairong Lian a,, Jingwu Li a, Ravi P Agarwal b
Available online at www.tjna.com J. Nonlinear Sci. Appl. 9 206), 357 369 Reearch Article Unbounded olution of econd order dicrete BVP on infinite interval Hairong Lian a,, Jingwu Li a, Ravi P Agarwal b
(b) Is the game below solvable by iterated strict dominance? Does it have a unique Nash equilibrium?
 14.1 Final Exam Anwer all quetion. You have 3 hour in which to complete the exam. 1. (60 Minute 40 Point) Anwer each of the following ubquetion briefly. Pleae how your calculation and provide rough explanation
14.1 Final Exam Anwer all quetion. You have 3 hour in which to complete the exam. 1. (60 Minute 40 Point) Anwer each of the following ubquetion briefly. Pleae how your calculation and provide rough explanation
Cumulative Review of Calculus
 Cumulative Review of Calculu. Uing the limit definition of the lope of a tangent, determine the lope of the tangent to each curve at the given point. a. f 5,, 5 f,, f, f 5,,,. The poition, in metre, of
Cumulative Review of Calculu. Uing the limit definition of the lope of a tangent, determine the lope of the tangent to each curve at the given point. a. f 5,, 5 f,, f, f 5,,,. The poition, in metre, of
Design spacecraft external surfaces to ensure 95 percent probability of no mission-critical failures from particle impact.
 PREFERRED RELIABILITY PAGE 1 OF 6 PRACTICES METEOROIDS & SPACE DEBRIS Practice: Deign pacecraft external urface to enure 95 percent probability of no miion-critical failure from particle impact. Benefit:
PREFERRED RELIABILITY PAGE 1 OF 6 PRACTICES METEOROIDS & SPACE DEBRIS Practice: Deign pacecraft external urface to enure 95 percent probability of no miion-critical failure from particle impact. Benefit:
Nonlinear Single-Particle Dynamics in High Energy Accelerators
 Nonlinear Single-Particle Dynamic in High Energy Accelerator Part 6: Canonical Perturbation Theory Nonlinear Single-Particle Dynamic in High Energy Accelerator Thi coure conit of eight lecture: 1. Introduction
Nonlinear Single-Particle Dynamic in High Energy Accelerator Part 6: Canonical Perturbation Theory Nonlinear Single-Particle Dynamic in High Energy Accelerator Thi coure conit of eight lecture: 1. Introduction
k-connectivity of uniform s-intersection graphs
 k-connectivity of uniform -interection graph Mindauga Blozneli, Katarzyna Rybarczyk Faculty of Mathematic and Informatic, Vilniu Univerity, 03225 Vilniu, Lithuania, E-MAIL: mindauga.blozneli@mif.vu.lt
k-connectivity of uniform -interection graph Mindauga Blozneli, Katarzyna Rybarczyk Faculty of Mathematic and Informatic, Vilniu Univerity, 03225 Vilniu, Lithuania, E-MAIL: mindauga.blozneli@mif.vu.lt
1. The F-test for Equality of Two Variances
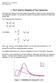 . The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
. The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
Lecture 21. The Lovasz splitting-off lemma Topics in Combinatorial Optimization April 29th, 2004
 18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
into a discrete time function. Recall that the table of Laplace/z-transforms is constructed by (i) selecting to get
 Lecture 25 Introduction to Some Matlab c2d Code in Relation to Sampled Sytem here are many way to convert a continuou time function, { h( t) ; t [0, )} into a dicrete time function { h ( k) ; k {0,,, }}
Lecture 25 Introduction to Some Matlab c2d Code in Relation to Sampled Sytem here are many way to convert a continuou time function, { h( t) ; t [0, )} into a dicrete time function { h ( k) ; k {0,,, }}
STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND
 OPERATIONS RESEARCH AND DECISIONS No. 4 203 DOI: 0.5277/ord30402 Marcin ANHOLCER STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND The generalized tranportation problem
OPERATIONS RESEARCH AND DECISIONS No. 4 203 DOI: 0.5277/ord30402 Marcin ANHOLCER STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND The generalized tranportation problem
