Maximum Likelihood Sequence Detection
|
|
|
- Valerie Rose
- 5 years ago
- Views:
Transcription
1 1 The Channel Delay Spread Channel Model Matched Filter as Receiver Front End... 4 Detection Terms Maximum Lielihood Detection of a Single Symbol Maximum Lielihood Detection of a Signal Vector ML Detection with Intersymbol Interference Sequence Detection Marov Chains Marov Chain Signal Generator The Viterbi Algorithm Error Probability Calculation Error Event Symbol Error Probability Upper Bound of Detection Error Lower Bound of Detection Error Upper and Lower Bounds of Detection Error... 18
2 1 The Channel If electromagnetic energy carrying a modulated signal, propagates along more than one path connecting the transmitter to the receiver, this is called multipath propagation. Multipath propagation occurs when for example radio waves are reflected, scattered or refracted by e.g. buildings, cars or hills. 1.1 Delay Spread Signal components traveling along different paths suffer from different attenuations and delays, which combine at the receiver to produce a distorted version of the transmitted signal. To characterize the various delays incurred by the signal traveling through the channel the delay spread is introduced as the largest of the delays. The delay spread causes the two effects of time dispersion and frequency selective fading. In a time dispersion channel a signal bandwidth much larger than the inverse of the delay spread the various paths are distinguishable as they produce copies of the transmitted signal with different delays and attenuations. For narrower bandwidths however, the received signal copies tend to overlap. This generates a form of linear distortion nown as intersymbol interference (ISI). If the bandwidth is large, different frequencies of the signal typically suffer from different attenuations along different paths. This is called frequency selective fading which is not a tpic in this paper. 1. Channel Model Any further only passband PAM modulation and its degenerate case of baseband PAM are considered, since FSK is generally not used in situations where ISI is an important phenomenon. PAM is preferred in this situation because FSK is a nonlinear modulation technique and is therefore difficult to equalize properly. In general a channel can be modeled as a linear time-invariant filter with impulse response b(t) and additive noise N(t), as shown in Figure 1-1. Figure 1-1 Advanced Signal Processing WT 004 Page of 18
3 Since the input to this transmit filter is discrete-time, and the output is sampled by the sampler, we can replace the transmit filter, channel and receive filter plus the sampler with an equivalent discrete-time filter. With U = U( T) = [ N( t)* f( t )] t = T (1) and p = p( T) = [ g( t)* b( t)* f( t )] t = t. () The discrete-time equivalent channel model for PAM (as in Figure 1-1) is then shown in Figure 1-. A passband PAM system with transmit filter g(t) and receive filter f(t)can be modeled as a completely discrete-time system if the continuous-time subsystems are considered as part of the channel. The equivalent discrete-time channel has impulse response p and transfer function P(z). jωt π π π Pe ( ) = G j ω m BE j ω m F j ω m m= T T T (3) The equivalent noise Z = ZT ( ) has independent real and imaginary parts each with variance given by σ. The power spectrum of the noise is given by N ( ( π ω )) T 0 ( ω S T Z e ) = T m= F j + m where T equals the symbol rate. Figure 1- (4) Figure 1-3 Advanced Signal Processing WT 004 Page 3 of 18
4 1.3 Matched Filter as Receiver Front End The first part of the receiver the receive filter and the sampler are typically built of a matched filter that is sampled at symbol rate. The discrete-time equivalent channel model utilizing a sampled matched filter may be depicted as in Figure 1-4. Figure 1-4 Of fundamental importance to the channel model is the autocorrelation function for a given baseband receive pulse shape h(t) * h( ) = ( ) ( ) ρ h t h t T dt. (5) j T The Fourier transform of (5) autocorrelation S ( e ω ) is called folded spectrum: h jωt 1 ( ( π ρ ω )) (6) jωt Sh( e ) = h( ) e = H j + m T = T m= The folded spectrum is real valued, nonnegative and in general not symmetric. Now the discrete time channel that includes the matched filter is easily obtained using the discrete-time model for PAM systems. The receive filter from the discrete PAM model is replaced by the sampled matched * filter F( jω) = H ( jω). The impulse response of the baseband channel ρ h( ), the pulse j T autocorrelation function and the transfer function are equal to the folded spectrum S ( e ω ). Further, the equivalent discrete-time noise process 0 Z has power spectrum jωt jωt S ( e ) = N S ( e ). (7) Z h At this point the calculation of probability density functions of the received estimates P is laborious because the noise in this model is not white and therefore the random variables P are not independent. Therefore the colorization from the matched filter has to be compensated. This can be achieved by spectral factorization of S z = M z M z. (8) ( ) ( ) (1/ ) h γ Then Sh( z) = H ( z) Hap( z) can be decomposed to a imal phase filter and an allpass filter where H ( z) γ M( z) =. So adding the inverse imal phase filter to the matched filter compensates the transfer function to constant attenuation of all frequencies as in Figure 1-5. h Figure 1-5 Advanced Signal Processing WT 004 Page 4 of 18
5 0 Therefore a new channel model is obtained where ( ) N SN z = is the variance of the now K Gaussian noise process N and U is the received symbol distorted by ISI. Figure 1-6 Detection The general approach to deriving optimal receivers is to model the relationship between the transmitted and received signals by joint probability distributions. Based on a noisy observation (the received signal plus noise), we wish to estimate or detect the input signal. The term estimation is used when the transmitted signal is a continuous-valued random variable and the term detection when the transmitted signal is discrete-valued (even if the received signal is continuous-valued). So the first case refers to analog and the second to digital communication systems. In this section the following model will be used. Figure -1 The deteristic portion of the channel is called signal generation and the random component the noise generation. The input X is a discrete-time and discrete-valued random process and has only a finite number of possible values..1 Terms Alphabet A: the set of symbols those are available for transmission. A = {-1,+1,-j,+j} Symbol a, A : -th symbol from the alphabet. a 1 =-1 Size of the alphabet M: number of symbols in the alphabet. M = 4 Sample space of the Alphabet Ω A Symbol of the sample space â Advanced Signal Processing WT 004 Page 5 of 18
6 . Maximum Lielihood Detection of a Single Symbol In order to decide about the received data symbol, nowledge about the noise generator is needed. The noise generator is completely specified by the discrete distribution of Y conditioned in the nowledge of the data symbol pya ( y â ). The maximum lielihood (ML) detector chooses âε Ω A to maximize the lielihood pya ( y â ), where y is the observation of Y. The ML detection is a special case of maximum a-posteriori probability detection for the simplifying assumption that all the possible inputs p ( â) are equally liely. p AY ( â y) p ( y â) p ( â) A = YA A py ( y) (9) Example: Suppose that we have additive discrete noise N, so that Y = A+N. Assume A and N are independent and tae on values zero and one according to the flip of two fair coins. There are three possible observations, y = 0, 1, or. The lielihoods pya ( y â ) for the observation y=0 are: pya (0 0) = 0.5 p (0 1) = 0 YA So if the observation is y=0, the ML detector selects â = 0. If the observation is y=1, then the lielihoods are equal pya (1 0) = pya (1 1) = 0.5 and therefore the ML detector selects either zero or one. If the observation is y =, the ML detector selects â = 1. The probability of error Pr[ error] = Pr[ â a] is a measure of the quality of the detector. Example: From the previous example Y=A+N taes on values in {0, 1, } with probabilities {0.5, 0.5, 0.5}, respectively. If the observation is y = 0 or y = the ML detector does not mae errors. If the observation is y = 1, however, the detector is unsure and chooses for example at random. Then the detector will be wrong half the time. Since p Y (1) = 0.5, the total probability of error is Pr[ error ] = 0.5. Advanced Signal Processing WT 004 Page 6 of 18
7 .3 Maximum Lielihood Detection of a Signal Vector Since the goal in this paper is the detection of a sequence of symbols it is convenient to extend the ML detection of a single symbol to a vector of symbols. Here the signal generator accepts an input X and maps it into a vector signal S with dimension M. The observation is a vector Y with the same dimension as the signal. The noise generator f ( ) is specified by the conditional distribution of the observation given the signal YS y s. A common characteristic of the noise generator is independent noise components M f ( y s YS ) = f ( y s ) (10). Y S = 1 The ML detector chooses the signal vector ŝ from all the possibilities in order to maximize the conditional probability ˆ ( y s ), which is given directly from the noise generator. f YS For additive Gaussian noise with variance σ and independent noise components f ( y sˆ) = f ( y sˆ sˆ) = f ( y s ˆ) (11). YS NS N Figure - Hence the ML detector selects ŝ to maximize 1 1 f ( y ˆ ) exp ˆ s = N M / M ( π) σ σ y s (1) where M is the dimension of the vectors and f N is the PDF of the Noise. Maximizing this is equivalent to imizing y s ˆ, the Euclidian distance between the received vector y and the signal vector ŝ. Advanced Signal Processing WT 004 Page 7 of 18
8 .4 ML Detection with Intersymbol Interference Consider a situation where the input to the signal generator is a single data symbol A, and the signal generator is a linear time-invariant filter with impulse response h,0 M, assumed to be finite in extent. This filter represents the dispersion of the data symbol in time. A single isolated discrete-time impulse δ amplitude modulated by an isolated data symbol A is transmitted. The noise is independent additive and Gaussian generated. The observation Y is only considered within the range 0 M, since there are no signal components outside. Thus the observation may be written in vector notation as Y= ha + N. If the single data symbol A from alphabet Ω A, the ML detector selects âε Ω A to imize the Euclidian distance between the vectors âh and observation y. Thus the ML detector computes y hâ = y y, h â+ h â (13) and chooses â for which this is the imum. Since y does not depend on the decision, the ML detector equivalently selects â to maximize The term Figure -3 yh, â h â. (14) [ ] 0 yh, = yh m m = y * h (15) = m may be computed using a correlator or a matched filter as depicted in Figure -4. Example: Figure -4 Suppose that a symbol A from the alphabet { 0,1} system with impulse response h = δ + 0.5δ 1. Ω = is transmitted through the LTI A In this case M=1 and -5. h =1.5, so the ML detector can be implemented lie in Figure Advanced Signal Processing WT 004 Page 8 of 18
9 In practice, however, this solution would be unacceptable due to its excessive complexity. In fact, for a message of K M-ary symbols, M K matched filters might be necessary, with about M K comparisons to be performed to select their largest sampled output..5 Sequence Detection To overcome the problems of the last section A. Viterbi of UCLA in 1967 proposed an algorithm for digital communication problems that can be formulated as suitable Marov chains. This algorithm selects the most liely symbol sequence in a number of computations and memory size that grow only linearly with respect to the message length K..5.1 Marov Chains A discrete-time Marov process { Ψ } is a random process that satisfies p Figure -5 (,,...) p( ) Ψ Ψ Ψ = Ψ Ψ. (16) In words, the future sample { Ψ + 1} is independent of past samples Ψ 1, Ψ,... if the present sample is nown. A Marov chain is called homogenous if the conditional probability p ( Ψ Ψ 1) is not a function of. A homogenous Marov chain is therefore a ind of stationary or time invariance. A Marov chain can be visualized by a state transition diagram as shown in Figure -6. Figure -6 Advanced Signal Processing WT 004 Page 9 of 18
10 Another valuable visualization is called the Trellis diagram, first suggested by D. Forney. Figure -7 Figure -7 shows the possible progression of states over time. Each small circle is called a node of the trellis, and corresponds to the Marov chain being a particular state at a particular time. Each arc is called a branch, and corresponds to a particular state transition at a particular time. The branches may be labeled lie the state transitions of the transition diagram. A collection of branches from the beginning to the teral node is called a path..5. Marov Chain Signal Generator Let Ψ be a sequence of a homogenous Marov chain. The sample space of each state Ψ is finite. For the signal generator of interest, the signal samples are a function of the Marov chain state transitions S = g( ψ, ψ + 1) where g(,) a memory less function as in Figure -8. The ML detector has to detect the sequence of states given an observation sequence Y, which is S passed through a noise generator with independent noise components. If h is a finite impulse response, than the inter symbol interference model that was previously developed in (see Figure -3) is an example of a shift-register process, where the observation function is M g( ψ, ψ + ) = ha. (17) 1 i 1 i= 0 The state of the Marov chain is [ X, X,..., X ] Ψ = (18) 1 M Figure -8 where M is the length of the shift-register. Advanced Signal Processing WT 004 Page 10 of 18
11 Example: Consider a discrete-time channel with impulse response h = δ + 0.5δ 1. Using the notation from the shift-register process this is depicted in Figure -9 (a). If the input symbols are independent identically distributed (i.i.d.), the observation Y is a noisy observation of the Marov chain with state diagram (b). Assug binary inputs A, there are only two states in (b) corresponding the two possible previous values for A -1. The arcs are labeled with the input/output (A,S ) of the signal generator. The Trellis diagram loos as follows: Figure -9 Figure The Viterbi Algorithm Every possible path in a trellis has a one-to-one correspondence with an input sequence X,0 K. The goal of a detector, based in the observation S corrupted by noise, is to decide the sequence of inputs. Deciding the sequence of inputs is equivalent to deciding the path through the trellis diagram. Recall that there is a signal s associated with each branch and each stage of the trellis. For each stage there is also an observation y. After observing y, we can assign to each branch of the trellis a numerical value called the branch metric that is low if y is close to s and high otherwise. For the Gaussian case the correct branch metric is branch metric = y s (19) Then for each path through the trellis, the path metric, which is the sum of the branch metrics, is calculated. The preferred path is the one with the lowest path metric. This is nothing else than imizing the Euclidian distance y s ˆ between the received vector y and the decision ŝ, as in section.3. Unfortunately the number of paths through the trellis grows exponentially with the message length K and therefore the computation time and memory usage, too. Advanced Signal Processing WT 004 Page 11 of 18
12 The Viterbi algorithm is a clever way of reducing this exponential growth to linear. Consider one node of the trellis an all paths through the trellis that pass through this node. There are a large number of paths through this node, but all these paths follow just one of four routs routes through this node AB, AD, BC or BD as in Figure -11. Figure -11 The path metric of a path through this node is the sum of the partial path metrics of the portion of the path on the right side of the node and on the left side of the node. Among all the partial paths to the left of the node, the detector pics the one with the smallest partial path metric, which is called the survivor path for that node. If any other partial path would be chosen the overall path metric would be grater than the one with the survivor path, and therefore would not be the smallest path. So every other partial path but the survivor path to the left may be thrown away. The Viterbi algorithm finds the path with the imum path metric by sequentially moving through the trellis and at each node retaining only the survivor paths. At each stage of the trellis it cannot be detered at which node the optimal path passes through, so one survivor Figure -1 path for each and every node must be retained. In a case where there are only two incog branches to a given node at time lie in Figure -1, the two possibilities for the survivor path to the node at time are consisting of the survivor paths at time -1 plus the branches to time. To decide the survivor the partial path metrics for each of those two paths are detered by sumg the partial path metric of the survivor at time -1 and the branch metric. The survivor path at that node is chosen as the path with the smaller partial path metric. Example: The trellis shown below is mared with branch metrics corresponding to the observation sequence {0., 0.6, 0.9, 0.1} of a discrete-time channel with impulse response h = δ + 0.5δ 1 and additive Gaussian noise as in the previous example. The possible state transitions are the following. Figure -13 Advanced Signal Processing WT 004 Page 1 of 18
13 The branches are labeled with their corresponding branch metrics y s. Also the survivor paths for each node and the partial path metrics of each surviving path are shown in Figure -14. Figure -14 A symbol by symbol ML detector would have decided, that the transmitted bits were {0, 1, 1, 0} whereas the ML sequence detector decides for {0, 1, 0, 0} taing into account nowledge of the ISI. The computational complexity of the Viterbi algorithm is the same at each time increment, and hence the total complexity is proportional to the length of K. Yet there is a practical problem remaining. The algorithm does not detere the optimal path until the teral code of the trellis. Since in digital communication systems state sequences may be very long this may result in a very long delay and a very big memory consumption which is generally not affordable. Occasionally all the survivor paths at some time coincide up to some time -d, then the partial paths have merged at depth d, and a decision can be made to all the inputs or states up to time -d. Unfortunately this depends on good fortune and therefore the algorithm is slightly modified to force a decision at time for all transitions prior to time -d, for some truncation depth d. Usually all the partial path metrics of the N partial paths at time are compared and the smallest path is piced. This path represents all the inputs or states until time -d and the node corresponding to this path is chosen to be the input or state at time -d for further computation. If d is chosen to be large enough, this modification will have negligible impact on the probability of detecting the correct sequence. Advanced Signal Processing WT 004 Page 13 of 18
14 3 Error Probability Calculation The sequence error probability is the probability that the path chosen through the trellis does not correspond to the actual state sequence, or in other words the probability that one or more states are in error. As the length of the message K increases this probability usually approaches unity. Fortunately the concern is normally with the probability of a single symbol or bit error, or the probability of a sequence error for a relatively short sequence. This implies that it would be better to optimize for single symbol error, but there are two reasons not to do this. First, it is much more complicated to implement and in fact the best nown algorithms for bitby-bit decision have exponential complexity in K. Secondly, the performance of the ML sequence detector is almost identical at high SNR to the detector that imizes the bit or symbol error probability. 3.1 Error Event It turns out useful to introduce the concept of an error event for the purpose of detering the symbol error probability. Let { Ψ } be the actual state sequence and { Ψˆ } be selected by the Viterbi algorithm. Each error event starts when the actual path and the selected path start to diverge and ends when Figure 3-1 they remerge. The length of an error event is the number of incorrect nodes in the path. So the error event in Figure 3-1 (a) has a length of one and in (b) a length of two. An error event yields in one ore more detection errors, which are incorrect symbols or bits as a result from taing an incorrect path through the trellis. The distance of the error event to the actual path is calculated in the following way. Assume an actual state sequence, and label each branch in the trellis with its squared distance form the corresponding branch of the actual state sequence as in Figure 3-. The actual state sequence will have branch metrics that are zero, and normally all the branches off the actual path sill have a non-zero branch metric. The path metric of each path through the trellis is now the square of the Euclidian distance of that path from the correct all-zero path. Using the branch metric = y s the distance can easily be obtained to be 1.5 for (a) and 3.5 for (b) in Figure 3-. Figure 3- Advanced Signal Processing WT 004 Page 14 of 18
15 3. Symbol Error Probability Now let E denote the set of all error events starting at time i. Each element e of E is characterized by both a correct path Ψ and an incorrect path ˆΨ that diverge and remerge sometime later. Pr[e] is assumed stationary that is Pr [e] is independent of i, the starting time of the error event. The approximation is accurate if the trellis is long relative to the length of the significant error events. Each error event causes one or more detection errors, where a detection error at time means that X at stage of the trellis is incorrect. For the ISI example, each X is a symbol A, so a detection error is the same as a symbol error. Function (0) characterizes the sample times corresponding to detection errors in error event e. 1; if e has a detection error in position m (from the start i) c m = (0) 0; otherwise The probability of a particular error event e starting at time i and causing a detection error at time is c ( e) Pr[ e] i. Of cause, if one error event occurs no other can occur. Therefore the error Events in E are disjoint so i i (1). i= E E i= Pr[detection error at time ] = Pr[ ec ] ( e) = Pr[ e] c ( e) The definition of the total number of detection errors i m () i= m= 0 we () = c () e = c () e yields Pr[detection error] = Pr[ ewe ] ( ). (3) E Hence, the probability of a detection error is equal to the expected number of detection errors in all error events starting at any fixed time i. The probability of the error event Pr[e] is depends on the probabilities of both the correct and incorrect paths Ψ and ˆΨ that mae up e, Pr[ e] = Pr[ Ψ] Pr Ψˆ Ψ. (4) Since it is usually difficult to extract expressions for Pr Ψˆ Ψ, only bounds are derived. Advanced Signal Processing WT 004 Page 15 of 18
16 3..1 Upper Bound of Detection Error Suppose that Ψ is the actual trajectory, corresponding to signals s in Figure 3-3 (a). The region corresponding to the detection of ˆΨ is shown in (b). The probability of the noise carrying the observation in this region is very difficult to calculate, but it is easy to find an upper bound by using a larger decision region as in (c) which ignores the possibility of any trajectory other than Ψ and ˆΨ. For the additive white Gaussian noise model, the probability of region in (c) is Pr ˆ ( ( ˆ Ψ Ψ Q d Ψ, Ψ) / σ ) (5) with Q(.) is defined as 1 α / Qx ( ) = Pr[ X> x] = 1 FX ( x) = e dα π (6) x If Q(x) is defined lie that for a Gaussian random variable X N ( µ, σ ) it becomes x µ Pr[ X > x] = Q σ. (7) Here d( ΨΨ ˆ, ) is the Euclidean distance between transmitted signal ŝ and s corresponding to the state trajectories ˆΨ and Ψ. Hence the probability of a detection error can be written as Pr[detection error] we ( ) Pr[ Ψ] Q( d( Ψˆ, Ψ) / σ ) (8) E If only the set B of error events with imal distance d are considered Pr[detection error] we ( ) Pr[ Ψ ] Q( d / σ ) + other terms (9) E the other terms become insignificant at high SNR. This probability approaches RQ( d / σ ) (30) where R= w()pr[ e Ψ]. (31) B Figure 3-3 Advanced Signal Processing WT 004 Page 16 of 18
17 Example: Here the error event e1 with w(e1)=1 and the distance 1.5 is considered as depicted in Figure 3-4. This is the imum distance. For a trellis with two states there are eight error events where each of them has also w(e)=1. Figure 3-4 So R= w( e) Pr[ Ψ] becomes R = 1Pr[ Ψ]. If all of these error events are equally B liely then R = 1*1/8 = 1 and B B ( σ ) Pr[detection error] Q 1.5 / + other terms. E Figure Lower Bound of Detection Error To obtain the lower bound the decision region of (d) can be used. This is the decision region where any error event conditioned on the actual state sequence Ψ is shown. The probability of any error event is clearly lower bounded by calculating the smaller decision region shown in (c). Figure 3-6 Since we () 1for all error events e the probability of a detection error can be written as Pr[detection error] Pr[ e] = Pr[an error event]. (3) E For one particular path through the trellis let d ( ) Ψ denote the distance of the imum distance error event. Let d be the imum distance error event over all possible actual state sequences Ψ. Then d ( Ψ) d. To mae the bound strongest, obviously the closest error event to Ψ has to be chosen, which is one of those at distance d ( Ψ ). Than the probability of any error event becomes Pr[an error event Ψ] Qd ( ( Ψ ) / σ ). (33) Advanced Signal Processing WT 004 Page 17 of 18
18 Consequently the probability of a detection error can be written as Pr[detection error Ψ] Qd ( ( Ψ ) / σ ). (34) And using the total probability this is Pr[detection error] Pr[ Ψ] Qd ( ( Ψ) / σ ). (35) Ψ It is save to omit some terms here because all terms are positive. So consider only those state sequences Ψ for which d ( Ψ ) = d. Pr[detection error] Pr[ Ψ] Qd ( ( Ψ) / σ ) (36) Ψε A Here A is the set of actual paths Ψ that have the imum distance error event, and d is that imum distance. Define the probability that a randomly chosen Ψ has an error event starting at any fixed time with distance d as P = Pr[ Ψ]. (37) Ψε A Than the lower bound can be expressed as Pr[detection error] PQ( d ( Ψ ) / σ ). (38) 3..3 Upper and Lower Bounds of Detection Error Combining upper an lower bounds, PQ( d / σ ) Pr[detection error] RQ( d ( Ψ ) / σ ) (39), where the upper bound is approximate since some terms were thrown away. To conclude, at high SNR Pr[detection error] CQ( d / σ ) for some constant C between P and R. (40) Example: From the previous example note that P=R=1. Hence Pr[detection error] Q( 1.5 / σ ). Here each detection error causes exactly one bit error, so Pr[detection error] = Pr[bit error]. Hence, with this sequence detector approximately the same probability of error is obtained as for an isolated pulse and a matched filter receiver. In general a single detection error may cause more than one bit error. Suppose each input of the Marov chain X is detered by n source bits (hence the alphabet has size n ). Then each detection error causes at least one and at most n bit errors. 1 Pr[detection error] Pr[bit error] Pr[detection error] (41) n The typical assumption is pessimistic: Pr[detection error] Pr[bit error] (4) Advanced Signal Processing WT 004 Page 18 of 18
BASICS OF DETECTION AND ESTIMATION THEORY
 BASICS OF DETECTION AND ESTIMATION THEORY 83050E/158 In this chapter we discuss how the transmitted symbols are detected optimally from a noisy received signal (observation). Based on these results, optimal
BASICS OF DETECTION AND ESTIMATION THEORY 83050E/158 In this chapter we discuss how the transmitted symbols are detected optimally from a noisy received signal (observation). Based on these results, optimal
Data Detection for Controlled ISI. h(nt) = 1 for n=0,1 and zero otherwise.
 Data Detection for Controlled ISI *Symbol by symbol suboptimum detection For the duobinary signal pulse h(nt) = 1 for n=0,1 and zero otherwise. The samples at the output of the receiving filter(demodulator)
Data Detection for Controlled ISI *Symbol by symbol suboptimum detection For the duobinary signal pulse h(nt) = 1 for n=0,1 and zero otherwise. The samples at the output of the receiving filter(demodulator)
RADIO SYSTEMS ETIN15. Lecture no: Equalization. Ove Edfors, Department of Electrical and Information Technology
 RADIO SYSTEMS ETIN15 Lecture no: 8 Equalization Ove Edfors, Department of Electrical and Information Technology Ove.Edfors@eit.lth.se Contents Inter-symbol interference Linear equalizers Decision-feedback
RADIO SYSTEMS ETIN15 Lecture no: 8 Equalization Ove Edfors, Department of Electrical and Information Technology Ove.Edfors@eit.lth.se Contents Inter-symbol interference Linear equalizers Decision-feedback
Direct-Sequence Spread-Spectrum
 Chapter 3 Direct-Sequence Spread-Spectrum In this chapter we consider direct-sequence spread-spectrum systems. Unlike frequency-hopping, a direct-sequence signal occupies the entire bandwidth continuously.
Chapter 3 Direct-Sequence Spread-Spectrum In this chapter we consider direct-sequence spread-spectrum systems. Unlike frequency-hopping, a direct-sequence signal occupies the entire bandwidth continuously.
Decision-Point Signal to Noise Ratio (SNR)
 Decision-Point Signal to Noise Ratio (SNR) Receiver Decision ^ SNR E E e y z Matched Filter Bound error signal at input to decision device Performance upper-bound on ISI channels Achieved on memoryless
Decision-Point Signal to Noise Ratio (SNR) Receiver Decision ^ SNR E E e y z Matched Filter Bound error signal at input to decision device Performance upper-bound on ISI channels Achieved on memoryless
Signal Processing for Digital Data Storage (11)
 Outline Signal Processing for Digital Data Storage (11) Assist.Prof. Piya Kovintavewat, Ph.D. Data Storage Technology Research Unit Nahon Pathom Rajabhat University Partial-Response Maximum-Lielihood (PRML)
Outline Signal Processing for Digital Data Storage (11) Assist.Prof. Piya Kovintavewat, Ph.D. Data Storage Technology Research Unit Nahon Pathom Rajabhat University Partial-Response Maximum-Lielihood (PRML)
Signal Design for Band-Limited Channels
 Wireless Information Transmission System Lab. Signal Design for Band-Limited Channels Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal
Wireless Information Transmission System Lab. Signal Design for Band-Limited Channels Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal
Digital Band-pass Modulation PROF. MICHAEL TSAI 2011/11/10
 Digital Band-pass Modulation PROF. MICHAEL TSAI 211/11/1 Band-pass Signal Representation a t g t General form: 2πf c t + φ t g t = a t cos 2πf c t + φ t Envelope Phase Envelope is always non-negative,
Digital Band-pass Modulation PROF. MICHAEL TSAI 211/11/1 Band-pass Signal Representation a t g t General form: 2πf c t + φ t g t = a t cos 2πf c t + φ t Envelope Phase Envelope is always non-negative,
Chapter 7: Channel coding:convolutional codes
 Chapter 7: : Convolutional codes University of Limoges meghdadi@ensil.unilim.fr Reference : Digital communications by John Proakis; Wireless communication by Andreas Goldsmith Encoder representation Communication
Chapter 7: : Convolutional codes University of Limoges meghdadi@ensil.unilim.fr Reference : Digital communications by John Proakis; Wireless communication by Andreas Goldsmith Encoder representation Communication
that efficiently utilizes the total available channel bandwidth W.
 Signal Design for Band-Limited Channels Wireless Information Transmission System Lab. Institute of Communications Engineering g National Sun Yat-sen University Introduction We consider the problem of signal
Signal Design for Band-Limited Channels Wireless Information Transmission System Lab. Institute of Communications Engineering g National Sun Yat-sen University Introduction We consider the problem of signal
Introduction to Convolutional Codes, Part 1
 Introduction to Convolutional Codes, Part 1 Frans M.J. Willems, Eindhoven University of Technology September 29, 2009 Elias, Father of Coding Theory Textbook Encoder Encoder Properties Systematic Codes
Introduction to Convolutional Codes, Part 1 Frans M.J. Willems, Eindhoven University of Technology September 29, 2009 Elias, Father of Coding Theory Textbook Encoder Encoder Properties Systematic Codes
EE5713 : Advanced Digital Communications
 EE5713 : Advanced Digital Communications Week 12, 13: Inter Symbol Interference (ISI) Nyquist Criteria for ISI Pulse Shaping and Raised-Cosine Filter Eye Pattern Equalization (On Board) 20-May-15 Muhammad
EE5713 : Advanced Digital Communications Week 12, 13: Inter Symbol Interference (ISI) Nyquist Criteria for ISI Pulse Shaping and Raised-Cosine Filter Eye Pattern Equalization (On Board) 20-May-15 Muhammad
LECTURE 16 AND 17. Digital signaling on frequency selective fading channels. Notes Prepared by: Abhishek Sood
 ECE559:WIRELESS COMMUNICATION TECHNOLOGIES LECTURE 16 AND 17 Digital signaling on frequency selective fading channels 1 OUTLINE Notes Prepared by: Abhishek Sood In section 2 we discuss the receiver design
ECE559:WIRELESS COMMUNICATION TECHNOLOGIES LECTURE 16 AND 17 Digital signaling on frequency selective fading channels 1 OUTLINE Notes Prepared by: Abhishek Sood In section 2 we discuss the receiver design
Copyright license. Exchanging Information with the Stars. The goal. Some challenges
 Copyright license Exchanging Information with the Stars David G Messerschmitt Department of Electrical Engineering and Computer Sciences University of California at Berkeley messer@eecs.berkeley.edu Talk
Copyright license Exchanging Information with the Stars David G Messerschmitt Department of Electrical Engineering and Computer Sciences University of California at Berkeley messer@eecs.berkeley.edu Talk
Square Root Raised Cosine Filter
 Wireless Information Transmission System Lab. Square Root Raised Cosine Filter Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal design
Wireless Information Transmission System Lab. Square Root Raised Cosine Filter Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal design
Estimation of the Capacity of Multipath Infrared Channels
 Estimation of the Capacity of Multipath Infrared Channels Jeffrey B. Carruthers Department of Electrical and Computer Engineering Boston University jbc@bu.edu Sachin Padma Department of Electrical and
Estimation of the Capacity of Multipath Infrared Channels Jeffrey B. Carruthers Department of Electrical and Computer Engineering Boston University jbc@bu.edu Sachin Padma Department of Electrical and
The Viterbi Algorithm EECS 869: Error Control Coding Fall 2009
 1 Bacground Material 1.1 Organization of the Trellis The Viterbi Algorithm EECS 869: Error Control Coding Fall 2009 The Viterbi algorithm (VA) processes the (noisy) output sequence from a state machine
1 Bacground Material 1.1 Organization of the Trellis The Viterbi Algorithm EECS 869: Error Control Coding Fall 2009 The Viterbi algorithm (VA) processes the (noisy) output sequence from a state machine
Principles of Communications
 Principles of Communications Chapter V: Representation and Transmission of Baseband Digital Signal Yongchao Wang Email: ychwang@mail.xidian.edu.cn Xidian University State Key Lab. on ISN November 18, 2012
Principles of Communications Chapter V: Representation and Transmission of Baseband Digital Signal Yongchao Wang Email: ychwang@mail.xidian.edu.cn Xidian University State Key Lab. on ISN November 18, 2012
Digital Baseband Systems. Reference: Digital Communications John G. Proakis
 Digital Baseband Systems Reference: Digital Communications John G. Proais Baseband Pulse Transmission Baseband digital signals - signals whose spectrum extend down to or near zero frequency. Model of the
Digital Baseband Systems Reference: Digital Communications John G. Proais Baseband Pulse Transmission Baseband digital signals - signals whose spectrum extend down to or near zero frequency. Model of the
Es e j4φ +4N n. 16 KE s /N 0. σ 2ˆφ4 1 γ s. p(φ e )= exp 1 ( 2πσ φ b cos N 2 φ e 0
 Problem 6.15 : he received signal-plus-noise vector at the output of the matched filter may be represented as (see (5-2-63) for example) : r n = E s e j(θn φ) + N n where θ n =0,π/2,π,3π/2 for QPSK, and
Problem 6.15 : he received signal-plus-noise vector at the output of the matched filter may be represented as (see (5-2-63) for example) : r n = E s e j(θn φ) + N n where θ n =0,π/2,π,3π/2 for QPSK, and
UCSD ECE153 Handout #40 Prof. Young-Han Kim Thursday, May 29, Homework Set #8 Due: Thursday, June 5, 2011
 UCSD ECE53 Handout #40 Prof. Young-Han Kim Thursday, May 9, 04 Homework Set #8 Due: Thursday, June 5, 0. Discrete-time Wiener process. Let Z n, n 0 be a discrete time white Gaussian noise (WGN) process,
UCSD ECE53 Handout #40 Prof. Young-Han Kim Thursday, May 9, 04 Homework Set #8 Due: Thursday, June 5, 0. Discrete-time Wiener process. Let Z n, n 0 be a discrete time white Gaussian noise (WGN) process,
Lecture 2. Fading Channel
 1 Lecture 2. Fading Channel Characteristics of Fading Channels Modeling of Fading Channels Discrete-time Input/Output Model 2 Radio Propagation in Free Space Speed: c = 299,792,458 m/s Isotropic Received
1 Lecture 2. Fading Channel Characteristics of Fading Channels Modeling of Fading Channels Discrete-time Input/Output Model 2 Radio Propagation in Free Space Speed: c = 299,792,458 m/s Isotropic Received
Performance evaluation for ML sequence detection in ISI channels with Gauss Markov Noise
 arxiv:0065036v [csit] 25 Jun 200 Performance evaluation for ML sequence detection in ISI channels with Gauss Marov Noise Naveen Kumar, Aditya Ramamoorthy and Murti Salapaa Dept of Electrical and Computer
arxiv:0065036v [csit] 25 Jun 200 Performance evaluation for ML sequence detection in ISI channels with Gauss Marov Noise Naveen Kumar, Aditya Ramamoorthy and Murti Salapaa Dept of Electrical and Computer
This examination consists of 11 pages. Please check that you have a complete copy. Time: 2.5 hrs INSTRUCTIONS
 THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 6 December 2006 This examination consists of
THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 6 December 2006 This examination consists of
This examination consists of 10 pages. Please check that you have a complete copy. Time: 2.5 hrs INSTRUCTIONS
 THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 08 December 2009 This examination consists of
THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 08 December 2009 This examination consists of
a) Find the compact (i.e. smallest) basis set required to ensure sufficient statistics.
 Digital Modulation and Coding Tutorial-1 1. Consider the signal set shown below in Fig.1 a) Find the compact (i.e. smallest) basis set required to ensure sufficient statistics. b) What is the minimum Euclidean
Digital Modulation and Coding Tutorial-1 1. Consider the signal set shown below in Fig.1 a) Find the compact (i.e. smallest) basis set required to ensure sufficient statistics. b) What is the minimum Euclidean
3. ESTIMATION OF SIGNALS USING A LEAST SQUARES TECHNIQUE
 3. ESTIMATION OF SIGNALS USING A LEAST SQUARES TECHNIQUE 3.0 INTRODUCTION The purpose of this chapter is to introduce estimators shortly. More elaborated courses on System Identification, which are given
3. ESTIMATION OF SIGNALS USING A LEAST SQUARES TECHNIQUE 3.0 INTRODUCTION The purpose of this chapter is to introduce estimators shortly. More elaborated courses on System Identification, which are given
Chapter [4] "Operations on a Single Random Variable"
![Chapter [4] Operations on a Single Random Variable Chapter [4] Operations on a Single Random Variable](/thumbs/93/112549011.jpg) Chapter [4] "Operations on a Single Random Variable" 4.1 Introduction In our study of random variables we use the probability density function or the cumulative distribution function to provide a complete
Chapter [4] "Operations on a Single Random Variable" 4.1 Introduction In our study of random variables we use the probability density function or the cumulative distribution function to provide a complete
Revision of Lecture 4
 Revision of Lecture 4 We have completed studying digital sources from information theory viewpoint We have learnt all fundamental principles for source coding, provided by information theory Practical
Revision of Lecture 4 We have completed studying digital sources from information theory viewpoint We have learnt all fundamental principles for source coding, provided by information theory Practical
Physical Layer and Coding
 Physical Layer and Coding Muriel Médard Professor EECS Overview A variety of physical media: copper, free space, optical fiber Unified way of addressing signals at the input and the output of these media:
Physical Layer and Coding Muriel Médard Professor EECS Overview A variety of physical media: copper, free space, optical fiber Unified way of addressing signals at the input and the output of these media:
SOLUTIONS TO ECE 6603 ASSIGNMENT NO. 6
 SOLUTIONS TO ECE 6603 ASSIGNMENT NO. 6 PROBLEM 6.. Consider a real-valued channel of the form r = a h + a h + n, which is a special case of the MIMO channel considered in class but with only two inputs.
SOLUTIONS TO ECE 6603 ASSIGNMENT NO. 6 PROBLEM 6.. Consider a real-valued channel of the form r = a h + a h + n, which is a special case of the MIMO channel considered in class but with only two inputs.
Lecture 7: Wireless Channels and Diversity Advanced Digital Communications (EQ2410) 1
 Wireless : Wireless Advanced Digital Communications (EQ2410) 1 Thursday, Feb. 11, 2016 10:00-12:00, B24 1 Textbook: U. Madhow, Fundamentals of Digital Communications, 2008 1 / 15 Wireless Lecture 1-6 Equalization
Wireless : Wireless Advanced Digital Communications (EQ2410) 1 Thursday, Feb. 11, 2016 10:00-12:00, B24 1 Textbook: U. Madhow, Fundamentals of Digital Communications, 2008 1 / 15 Wireless Lecture 1-6 Equalization
Massachusetts Institute of Technology
 Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.011: Introduction to Communication, Control and Signal Processing QUIZ, April 1, 010 QUESTION BOOKLET Your
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.011: Introduction to Communication, Control and Signal Processing QUIZ, April 1, 010 QUESTION BOOKLET Your
Principles of Communications Lecture 8: Baseband Communication Systems. Chih-Wei Liu 劉志尉 National Chiao Tung University
 Principles of Communications Lecture 8: Baseband Communication Systems Chih-Wei Liu 劉志尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.tw Outlines Introduction Line codes Effects of filtering Pulse
Principles of Communications Lecture 8: Baseband Communication Systems Chih-Wei Liu 劉志尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.tw Outlines Introduction Line codes Effects of filtering Pulse
Communication Theory Summary of Important Definitions and Results
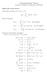 Signal and system theory Convolution of signals x(t) h(t) = y(t): Fourier Transform: Communication Theory Summary of Important Definitions and Results X(ω) = X(ω) = y(t) = X(ω) = j x(t) e jωt dt, 0 Properties
Signal and system theory Convolution of signals x(t) h(t) = y(t): Fourier Transform: Communication Theory Summary of Important Definitions and Results X(ω) = X(ω) = y(t) = X(ω) = j x(t) e jωt dt, 0 Properties
MAXIMUM LIKELIHOOD SEQUENCE ESTIMATION FROM THE LATTICE VIEWPOINT. By Mow Wai Ho
 MAXIMUM LIKELIHOOD SEQUENCE ESTIMATION FROM THE LATTICE VIEWPOINT By Mow Wai Ho A thesis submitted in partial fulfillment of the requirements for the Degree of Master of Philosophy Department of Information
MAXIMUM LIKELIHOOD SEQUENCE ESTIMATION FROM THE LATTICE VIEWPOINT By Mow Wai Ho A thesis submitted in partial fulfillment of the requirements for the Degree of Master of Philosophy Department of Information
A FEASIBILITY STUDY OF PARTICLE FILTERS FOR MOBILE STATION RECEIVERS. Michael Lunglmayr, Martin Krueger, Mario Huemer
 A FEASIBILITY STUDY OF PARTICLE FILTERS FOR MOBILE STATION RECEIVERS Michael Lunglmayr, Martin Krueger, Mario Huemer Michael Lunglmayr and Martin Krueger are with Infineon Technologies AG, Munich email:
A FEASIBILITY STUDY OF PARTICLE FILTERS FOR MOBILE STATION RECEIVERS Michael Lunglmayr, Martin Krueger, Mario Huemer Michael Lunglmayr and Martin Krueger are with Infineon Technologies AG, Munich email:
Lecture 12. Block Diagram
 Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Digital Communications
 Digital Communications Chapter 9 Digital Communications Through Band-Limited Channels Po-Ning Chen, Professor Institute of Communications Engineering National Chiao-Tung University, Taiwan Digital Communications:
Digital Communications Chapter 9 Digital Communications Through Band-Limited Channels Po-Ning Chen, Professor Institute of Communications Engineering National Chiao-Tung University, Taiwan Digital Communications:
Analysis of Finite Wordlength Effects
 Analysis of Finite Wordlength Effects Ideally, the system parameters along with the signal variables have infinite precision taing any value between and In practice, they can tae only discrete values within
Analysis of Finite Wordlength Effects Ideally, the system parameters along with the signal variables have infinite precision taing any value between and In practice, they can tae only discrete values within
Exercise 1. = P(y a 1)P(a 1 )
 Chapter 7 Channel Capacity Exercise 1 A source produces independent, equally probable symbols from an alphabet {a 1, a 2 } at a rate of one symbol every 3 seconds. These symbols are transmitted over a
Chapter 7 Channel Capacity Exercise 1 A source produces independent, equally probable symbols from an alphabet {a 1, a 2 } at a rate of one symbol every 3 seconds. These symbols are transmitted over a
On the exact bit error probability for Viterbi decoding of convolutional codes
 On the exact bit error probability for Viterbi decoding of convolutional codes Irina E. Bocharova, Florian Hug, Rolf Johannesson, and Boris D. Kudryashov Dept. of Information Systems Dept. of Electrical
On the exact bit error probability for Viterbi decoding of convolutional codes Irina E. Bocharova, Florian Hug, Rolf Johannesson, and Boris D. Kudryashov Dept. of Information Systems Dept. of Electrical
Error Correction and Trellis Coding
 Advanced Signal Processing Winter Term 2001/2002 Digital Subscriber Lines (xdsl): Broadband Communication over Twisted Wire Pairs Error Correction and Trellis Coding Thomas Brandtner brandt@sbox.tugraz.at
Advanced Signal Processing Winter Term 2001/2002 Digital Subscriber Lines (xdsl): Broadband Communication over Twisted Wire Pairs Error Correction and Trellis Coding Thomas Brandtner brandt@sbox.tugraz.at
Soft-Output Trellis Waveform Coding
 Soft-Output Trellis Waveform Coding Tariq Haddad and Abbas Yongaçoḡlu School of Information Technology and Engineering, University of Ottawa Ottawa, Ontario, K1N 6N5, Canada Fax: +1 (613) 562 5175 thaddad@site.uottawa.ca
Soft-Output Trellis Waveform Coding Tariq Haddad and Abbas Yongaçoḡlu School of Information Technology and Engineering, University of Ottawa Ottawa, Ontario, K1N 6N5, Canada Fax: +1 (613) 562 5175 thaddad@site.uottawa.ca
ADAPTIVE FILTER ALGORITHMS. Prepared by Deepa.T, Asst.Prof. /TCE
 ADAPTIVE FILTER ALGORITHMS Prepared by Deepa.T, Asst.Prof. /TCE Equalization Techniques Fig.3 Classification of equalizers Equalizer Techniques Linear transversal equalizer (LTE, made up of tapped delay
ADAPTIVE FILTER ALGORITHMS Prepared by Deepa.T, Asst.Prof. /TCE Equalization Techniques Fig.3 Classification of equalizers Equalizer Techniques Linear transversal equalizer (LTE, made up of tapped delay
CS6956: Wireless and Mobile Networks Lecture Notes: 2/4/2015
 CS6956: Wireless and Mobile Networks Lecture Notes: 2/4/2015 [Most of the material for this lecture has been taken from the Wireless Communications & Networks book by Stallings (2 nd edition).] Effective
CS6956: Wireless and Mobile Networks Lecture Notes: 2/4/2015 [Most of the material for this lecture has been taken from the Wireless Communications & Networks book by Stallings (2 nd edition).] Effective
ITCT Lecture IV.3: Markov Processes and Sources with Memory
 ITCT Lecture IV.3: Markov Processes and Sources with Memory 4. Markov Processes Thus far, we have been occupied with memoryless sources and channels. We must now turn our attention to sources with memory.
ITCT Lecture IV.3: Markov Processes and Sources with Memory 4. Markov Processes Thus far, we have been occupied with memoryless sources and channels. We must now turn our attention to sources with memory.
Sample Problems for the 9th Quiz
 Sample Problems for the 9th Quiz. Draw the line coded signal waveform of the below line code for 0000. (a Unipolar nonreturn-to-zero (NRZ signaling (b Polar nonreturn-to-zero (NRZ signaling (c Unipolar
Sample Problems for the 9th Quiz. Draw the line coded signal waveform of the below line code for 0000. (a Unipolar nonreturn-to-zero (NRZ signaling (b Polar nonreturn-to-zero (NRZ signaling (c Unipolar
Handout 12: Error Probability Analysis of Binary Detection
 ENGG 230-B: Principles of Communication Systems 207 8 First Term Handout 2: Error Probability Analysis of Binary Detection Instructor: Wing-Kin Ma November 4, 207 Suggested Reading: Chapter 8 of Simon
ENGG 230-B: Principles of Communication Systems 207 8 First Term Handout 2: Error Probability Analysis of Binary Detection Instructor: Wing-Kin Ma November 4, 207 Suggested Reading: Chapter 8 of Simon
SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land
 SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land Ingmar Land, SIPCom8-1: Information Theory and Coding (2005 Spring) p.1 Overview Basic Concepts of Channel Coding Block Codes I:
SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land Ingmar Land, SIPCom8-1: Information Theory and Coding (2005 Spring) p.1 Overview Basic Concepts of Channel Coding Block Codes I:
ELECTRONICS & COMMUNICATIONS DIGITAL COMMUNICATIONS
 EC 32 (CR) Total No. of Questions :09] [Total No. of Pages : 02 III/IV B.Tech. DEGREE EXAMINATIONS, APRIL/MAY- 207 Second Semester ELECTRONICS & COMMUNICATIONS DIGITAL COMMUNICATIONS Time: Three Hours
EC 32 (CR) Total No. of Questions :09] [Total No. of Pages : 02 III/IV B.Tech. DEGREE EXAMINATIONS, APRIL/MAY- 207 Second Semester ELECTRONICS & COMMUNICATIONS DIGITAL COMMUNICATIONS Time: Three Hours
MMSE Decision Feedback Equalization of Pulse Position Modulated Signals
 SE Decision Feedback Equalization of Pulse Position odulated Signals AG Klein and CR Johnson, Jr School of Electrical and Computer Engineering Cornell University, Ithaca, NY 4853 email: agk5@cornelledu
SE Decision Feedback Equalization of Pulse Position odulated Signals AG Klein and CR Johnson, Jr School of Electrical and Computer Engineering Cornell University, Ithaca, NY 4853 email: agk5@cornelledu
Carrier frequency estimation. ELEC-E5410 Signal processing for communications
 Carrier frequency estimation ELEC-E54 Signal processing for communications Contents. Basic system assumptions. Data-aided DA: Maximum-lielihood ML estimation of carrier frequency 3. Data-aided: Practical
Carrier frequency estimation ELEC-E54 Signal processing for communications Contents. Basic system assumptions. Data-aided DA: Maximum-lielihood ML estimation of carrier frequency 3. Data-aided: Practical
EE 574 Detection and Estimation Theory Lecture Presentation 8
 Lecture Presentation 8 Aykut HOCANIN Dept. of Electrical and Electronic Engineering 1/14 Chapter 3: Representation of Random Processes 3.2 Deterministic Functions:Orthogonal Representations For a finite-energy
Lecture Presentation 8 Aykut HOCANIN Dept. of Electrical and Electronic Engineering 1/14 Chapter 3: Representation of Random Processes 3.2 Deterministic Functions:Orthogonal Representations For a finite-energy
ECE6604 PERSONAL & MOBILE COMMUNICATIONS. Week 3. Flat Fading Channels Envelope Distribution Autocorrelation of a Random Process
 1 ECE6604 PERSONAL & MOBILE COMMUNICATIONS Week 3 Flat Fading Channels Envelope Distribution Autocorrelation of a Random Process 2 Multipath-Fading Mechanism local scatterers mobile subscriber base station
1 ECE6604 PERSONAL & MOBILE COMMUNICATIONS Week 3 Flat Fading Channels Envelope Distribution Autocorrelation of a Random Process 2 Multipath-Fading Mechanism local scatterers mobile subscriber base station
Revision of Lecture 4
 Revision of Lecture 4 We have discussed all basic components of MODEM Pulse shaping Tx/Rx filter pair Modulator/demodulator Bits map symbols Discussions assume ideal channel, and for dispersive channel
Revision of Lecture 4 We have discussed all basic components of MODEM Pulse shaping Tx/Rx filter pair Modulator/demodulator Bits map symbols Discussions assume ideal channel, and for dispersive channel
EE4512 Analog and Digital Communications Chapter 4. Chapter 4 Receiver Design
 Chapter 4 Receiver Design Chapter 4 Receiver Design Probability of Bit Error Pages 124-149 149 Probability of Bit Error The low pass filtered and sampled PAM signal results in an expression for the probability
Chapter 4 Receiver Design Chapter 4 Receiver Design Probability of Bit Error Pages 124-149 149 Probability of Bit Error The low pass filtered and sampled PAM signal results in an expression for the probability
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi
 Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
P 1.5 X 4.5 / X 2 and (iii) The smallest value of n for
 DHANALAKSHMI COLLEGE OF ENEINEERING, CHENNAI DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING MA645 PROBABILITY AND RANDOM PROCESS UNIT I : RANDOM VARIABLES PART B (6 MARKS). A random variable X
DHANALAKSHMI COLLEGE OF ENEINEERING, CHENNAI DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING MA645 PROBABILITY AND RANDOM PROCESS UNIT I : RANDOM VARIABLES PART B (6 MARKS). A random variable X
Determining the Optimal Decision Delay Parameter for a Linear Equalizer
 International Journal of Automation and Computing 1 (2005) 20-24 Determining the Optimal Decision Delay Parameter for a Linear Equalizer Eng Siong Chng School of Computer Engineering, Nanyang Technological
International Journal of Automation and Computing 1 (2005) 20-24 Determining the Optimal Decision Delay Parameter for a Linear Equalizer Eng Siong Chng School of Computer Engineering, Nanyang Technological
GEORGIA INSTITUTE OF TECHNOLOGY SCHOOL OF ELECTRICAL AND COMPUTER ENGINEERING Final Examination - Fall 2015 EE 4601: Communication Systems
 GEORGIA INSTITUTE OF TECHNOLOGY SCHOOL OF ELECTRICAL AND COMPUTER ENGINEERING Final Examination - Fall 2015 EE 4601: Communication Systems Aids Allowed: 2 8 1/2 X11 crib sheets, calculator DATE: Tuesday
GEORGIA INSTITUTE OF TECHNOLOGY SCHOOL OF ELECTRICAL AND COMPUTER ENGINEERING Final Examination - Fall 2015 EE 4601: Communication Systems Aids Allowed: 2 8 1/2 X11 crib sheets, calculator DATE: Tuesday
ANALYSIS OF A PARTIAL DECORRELATOR IN A MULTI-CELL DS/CDMA SYSTEM
 ANAYSIS OF A PARTIA DECORREATOR IN A MUTI-CE DS/CDMA SYSTEM Mohammad Saquib ECE Department, SU Baton Rouge, A 70803-590 e-mail: saquib@winlab.rutgers.edu Roy Yates WINAB, Rutgers University Piscataway
ANAYSIS OF A PARTIA DECORREATOR IN A MUTI-CE DS/CDMA SYSTEM Mohammad Saquib ECE Department, SU Baton Rouge, A 70803-590 e-mail: saquib@winlab.rutgers.edu Roy Yates WINAB, Rutgers University Piscataway
Capacity Penalty due to Ideal Zero-Forcing Decision-Feedback Equalization
 Capacity Penalty due to Ideal Zero-Forcing Decision-Feedback Equalization John R. Barry, Edward A. Lee, and David. Messerschmitt John R. Barry, School of Electrical Engineering, eorgia Institute of Technology,
Capacity Penalty due to Ideal Zero-Forcing Decision-Feedback Equalization John R. Barry, Edward A. Lee, and David. Messerschmitt John R. Barry, School of Electrical Engineering, eorgia Institute of Technology,
Memo of J. G. Proakis and M Salehi, Digital Communications, 5th ed. New York: McGraw-Hill, Chenggao HAN
 Memo of J. G. Proakis and M Salehi, Digital Communications, 5th ed. New York: McGraw-Hill, 007 Chenggao HAN Contents 1 Introduction 1 1.1 Elements of a Digital Communication System.....................
Memo of J. G. Proakis and M Salehi, Digital Communications, 5th ed. New York: McGraw-Hill, 007 Chenggao HAN Contents 1 Introduction 1 1.1 Elements of a Digital Communication System.....................
s o (t) = S(f)H(f; t)e j2πft df,
 Sample Problems for Midterm. The sample problems for the fourth and fifth quizzes as well as Example on Slide 8-37 and Example on Slides 8-39 4) will also be a key part of the second midterm.. For a causal)
Sample Problems for Midterm. The sample problems for the fourth and fifth quizzes as well as Example on Slide 8-37 and Example on Slides 8-39 4) will also be a key part of the second midterm.. For a causal)
Digital Modulation 1
 Digital Modulation 1 Lecture Notes Ingmar Land and Bernard H. Fleury Navigation and Communications () Department of Electronic Systems Aalborg University, DK Version: February 5, 27 i Contents I Basic
Digital Modulation 1 Lecture Notes Ingmar Land and Bernard H. Fleury Navigation and Communications () Department of Electronic Systems Aalborg University, DK Version: February 5, 27 i Contents I Basic
12.4 Known Channel (Water-Filling Solution)
 ECEn 665: Antennas and Propagation for Wireless Communications 54 2.4 Known Channel (Water-Filling Solution) The channel scenarios we have looed at above represent special cases for which the capacity
ECEn 665: Antennas and Propagation for Wireless Communications 54 2.4 Known Channel (Water-Filling Solution) The channel scenarios we have looed at above represent special cases for which the capacity
Parameter Estimation
 1 / 44 Parameter Estimation Saravanan Vijayakumaran sarva@ee.iitb.ac.in Department of Electrical Engineering Indian Institute of Technology Bombay October 25, 2012 Motivation System Model used to Derive
1 / 44 Parameter Estimation Saravanan Vijayakumaran sarva@ee.iitb.ac.in Department of Electrical Engineering Indian Institute of Technology Bombay October 25, 2012 Motivation System Model used to Derive
SIGNAL SPACE CONCEPTS
 SIGNAL SPACE CONCEPTS TLT-5406/0 In this section we familiarize ourselves with the representation of discrete-time and continuous-time communication signals using the concepts of vector spaces. These concepts
SIGNAL SPACE CONCEPTS TLT-5406/0 In this section we familiarize ourselves with the representation of discrete-time and continuous-time communication signals using the concepts of vector spaces. These concepts
Communications and Signal Processing Spring 2017 MSE Exam
 Communications and Signal Processing Spring 2017 MSE Exam Please obtain your Test ID from the following table. You must write your Test ID and name on each of the pages of this exam. A page with missing
Communications and Signal Processing Spring 2017 MSE Exam Please obtain your Test ID from the following table. You must write your Test ID and name on each of the pages of this exam. A page with missing
EE4304 C-term 2007: Lecture 17 Supplemental Slides
 EE434 C-term 27: Lecture 17 Supplemental Slides D. Richard Brown III Worcester Polytechnic Institute, Department of Electrical and Computer Engineering February 5, 27 Geometric Representation: Optimal
EE434 C-term 27: Lecture 17 Supplemental Slides D. Richard Brown III Worcester Polytechnic Institute, Department of Electrical and Computer Engineering February 5, 27 Geometric Representation: Optimal
Digital Transmission Methods S
 Digital ransmission ethods S-7.5 Second Exercise Session Hypothesis esting Decision aking Gram-Schmidt method Detection.K.K. Communication Laboratory 5//6 Konstantinos.koufos@tkk.fi Exercise We assume
Digital ransmission ethods S-7.5 Second Exercise Session Hypothesis esting Decision aking Gram-Schmidt method Detection.K.K. Communication Laboratory 5//6 Konstantinos.koufos@tkk.fi Exercise We assume
MLSE in a single path channel. MLSE in a multipath channel. State model for a multipath channel. State model for a multipath channel
 MLSE in a single path channel MLSE - Maximum Lielihood Sequence Estimation T he op timal detector is the one w hich selects from all p ossib le transmitted b it sequences the one w ith hig hest p rob ab
MLSE in a single path channel MLSE - Maximum Lielihood Sequence Estimation T he op timal detector is the one w hich selects from all p ossib le transmitted b it sequences the one w ith hig hest p rob ab
ELEC546 Review of Information Theory
 ELEC546 Review of Information Theory Vincent Lau 1/1/004 1 Review of Information Theory Entropy: Measure of uncertainty of a random variable X. The entropy of X, H(X), is given by: If X is a discrete random
ELEC546 Review of Information Theory Vincent Lau 1/1/004 1 Review of Information Theory Entropy: Measure of uncertainty of a random variable X. The entropy of X, H(X), is given by: If X is a discrete random
Lecture 7. Union bound for reducing M-ary to binary hypothesis testing
 Lecture 7 Agenda for the lecture M-ary hypothesis testing and the MAP rule Union bound for reducing M-ary to binary hypothesis testing Introduction of the channel coding problem 7.1 M-ary hypothesis testing
Lecture 7 Agenda for the lecture M-ary hypothesis testing and the MAP rule Union bound for reducing M-ary to binary hypothesis testing Introduction of the channel coding problem 7.1 M-ary hypothesis testing
Intercarrier and Intersymbol Interference Analysis of OFDM Systems on Time-Varying channels
 Intercarrier and Intersymbol Interference Analysis of OFDM Systems on Time-Varying channels Van Duc Nguyen, Hans-Peter Kuchenbecker University of Hannover, Institut für Allgemeine Nachrichtentechnik Appelstr.
Intercarrier and Intersymbol Interference Analysis of OFDM Systems on Time-Varying channels Van Duc Nguyen, Hans-Peter Kuchenbecker University of Hannover, Institut für Allgemeine Nachrichtentechnik Appelstr.
Principles of Communications
 Principles of Communications Weiyao Lin, PhD Shanghai Jiao Tong University Chapter 4: Analog-to-Digital Conversion Textbook: 7.1 7.4 2010/2011 Meixia Tao @ SJTU 1 Outline Analog signal Sampling Quantization
Principles of Communications Weiyao Lin, PhD Shanghai Jiao Tong University Chapter 4: Analog-to-Digital Conversion Textbook: 7.1 7.4 2010/2011 Meixia Tao @ SJTU 1 Outline Analog signal Sampling Quantization
Multiuser Detection. Summary for EECS Graduate Seminar in Communications. Benjamin Vigoda
 Multiuser Detection Summary for 6.975 EECS Graduate Seminar in Communications Benjamin Vigoda The multiuser detection problem applies when we are sending data on the uplink channel from a handset to a
Multiuser Detection Summary for 6.975 EECS Graduate Seminar in Communications Benjamin Vigoda The multiuser detection problem applies when we are sending data on the uplink channel from a handset to a
Solutions Communications Technology II WS 2010/2011
 Solutions Communications Technology II WS 010/011 Yidong Lang, Henning Schepker NW1, Room N350, Tel.: 041/18-6393 E-mail: lang/ schepker@ant.uni-bremen.de Universität Bremen, FB1 Institut für Telekommunikation
Solutions Communications Technology II WS 010/011 Yidong Lang, Henning Schepker NW1, Room N350, Tel.: 041/18-6393 E-mail: lang/ schepker@ant.uni-bremen.de Universität Bremen, FB1 Institut für Telekommunikation
Multi User Detection I
 January 12, 2005 Outline Overview Multiple Access Communication Motivation: What is MU Detection? Overview of DS/CDMA systems Concept and Codes used in CDMA CDMA Channels Models Synchronous and Asynchronous
January 12, 2005 Outline Overview Multiple Access Communication Motivation: What is MU Detection? Overview of DS/CDMA systems Concept and Codes used in CDMA CDMA Channels Models Synchronous and Asynchronous
A First Course in Digital Communications
 A First Course in Digital Communications Ha H. Nguyen and E. Shwedyk February 9 A First Course in Digital Communications 1/46 Introduction There are benefits to be gained when M-ary (M = 4 signaling methods
A First Course in Digital Communications Ha H. Nguyen and E. Shwedyk February 9 A First Course in Digital Communications 1/46 Introduction There are benefits to be gained when M-ary (M = 4 signaling methods
2016 Spring: The Final Exam of Digital Communications
 2016 Spring: The Final Exam of Digital Communications The total number of points is 131. 1. Image of Transmitter Transmitter L 1 θ v 1 As shown in the figure above, a car is receiving a signal from a remote
2016 Spring: The Final Exam of Digital Communications The total number of points is 131. 1. Image of Transmitter Transmitter L 1 θ v 1 As shown in the figure above, a car is receiving a signal from a remote
Ralf Koetter, Andrew C. Singer, and Michael Tüchler
 Ralf Koetter, Andrew C. Singer, and Michael Tüchler Capitalizing on the tremendous performance gains of turbo codes and the turbo decoding algorithm, turbo equalization is an iterative equalization and
Ralf Koetter, Andrew C. Singer, and Michael Tüchler Capitalizing on the tremendous performance gains of turbo codes and the turbo decoding algorithm, turbo equalization is an iterative equalization and
Digital Communications: A Discrete-Time Approach M. Rice. Errata. Page xiii, first paragraph, bare witness should be bear witness
 Digital Communications: A Discrete-Time Approach M. Rice Errata Foreword Page xiii, first paragraph, bare witness should be bear witness Page xxi, last paragraph, You know who you. should be You know who
Digital Communications: A Discrete-Time Approach M. Rice Errata Foreword Page xiii, first paragraph, bare witness should be bear witness Page xxi, last paragraph, You know who you. should be You know who
FROM ANALOGUE TO DIGITAL
 SIGNALS AND SYSTEMS: PAPER 3C1 HANDOUT 7. Dr David Corrigan 1. Electronic and Electrical Engineering Dept. corrigad@tcd.ie www.mee.tcd.ie/ corrigad FROM ANALOGUE TO DIGITAL To digitize signals it is necessary
SIGNALS AND SYSTEMS: PAPER 3C1 HANDOUT 7. Dr David Corrigan 1. Electronic and Electrical Engineering Dept. corrigad@tcd.ie www.mee.tcd.ie/ corrigad FROM ANALOGUE TO DIGITAL To digitize signals it is necessary
Example: Bipolar NRZ (non-return-to-zero) signaling
 Baseand Data Transmission Data are sent without using a carrier signal Example: Bipolar NRZ (non-return-to-zero signaling is represented y is represented y T A -A T : it duration is represented y BT. Passand
Baseand Data Transmission Data are sent without using a carrier signal Example: Bipolar NRZ (non-return-to-zero signaling is represented y is represented y T A -A T : it duration is represented y BT. Passand
Performance of MLSE-Based Receivers in Lightwave Systems with Nonlinear Dispersion and Amplified Spontaneous Emission Noise
 Performance of MLSE-Based Receivers in Lightwave Systems with Nonlinear Dispersion and Amplified Spontaneous Emission Noise Mario R. Hueda Diego E. Crivelli Hugo S. Carrer Digital Communications Research
Performance of MLSE-Based Receivers in Lightwave Systems with Nonlinear Dispersion and Amplified Spontaneous Emission Noise Mario R. Hueda Diego E. Crivelli Hugo S. Carrer Digital Communications Research
Module 1. Introduction to Digital Communications and Information Theory. Version 2 ECE IIT, Kharagpur
 Module ntroduction to Digital Communications and nformation Theory Lesson 3 nformation Theoretic Approach to Digital Communications After reading this lesson, you will learn about Scope of nformation Theory
Module ntroduction to Digital Communications and nformation Theory Lesson 3 nformation Theoretic Approach to Digital Communications After reading this lesson, you will learn about Scope of nformation Theory
Equalization. Contents. John Barry. October 5, 2015
 Equalization John Barry October 5, 205 School of Electrical and Computer Engineering Georgia Institute of Technology Atlanta, GA 30332-0250 barry@ece.gatech.edu Contents Motivation 2 2 Models and Metrics
Equalization John Barry October 5, 205 School of Electrical and Computer Engineering Georgia Institute of Technology Atlanta, GA 30332-0250 barry@ece.gatech.edu Contents Motivation 2 2 Models and Metrics
Optical Fiber Signal Degradation
 Optical Fiber Signal Degradation Effects Pulse Spreading Dispersion (Distortion) Causes the optical pulses to broaden as they travel along a fiber Overlap between neighboring pulses creates errors Resulting
Optical Fiber Signal Degradation Effects Pulse Spreading Dispersion (Distortion) Causes the optical pulses to broaden as they travel along a fiber Overlap between neighboring pulses creates errors Resulting
TSKS01 Digital Communication Lecture 1
 TSKS01 Digital Communication Lecture 1 Introduction, Repetition, and Noise Modeling Emil Björnson Department of Electrical Engineering (ISY) Division of Communication Systems Emil Björnson Course Director
TSKS01 Digital Communication Lecture 1 Introduction, Repetition, and Noise Modeling Emil Björnson Department of Electrical Engineering (ISY) Division of Communication Systems Emil Björnson Course Director
EE4601 Communication Systems
 EE4601 Communication Systems Week 13 Linear Zero Forcing Equalization 0 c 2012, Georgia Institute of Technology (lect13 1) Equalization The cascade of the transmit filter g(t), channel c(t), receiver filter
EE4601 Communication Systems Week 13 Linear Zero Forcing Equalization 0 c 2012, Georgia Institute of Technology (lect13 1) Equalization The cascade of the transmit filter g(t), channel c(t), receiver filter
An analysis of the computational complexity of sequential decoding of specific tree codes over Gaussian channels
 An analysis of the computational complexity of sequential decoding of specific tree codes over Gaussian channels B. Narayanaswamy, Rohit Negi and Pradeep Khosla Department of ECE Carnegie Mellon University
An analysis of the computational complexity of sequential decoding of specific tree codes over Gaussian channels B. Narayanaswamy, Rohit Negi and Pradeep Khosla Department of ECE Carnegie Mellon University
Channel Coding and Interleaving
 Lecture 6 Channel Coding and Interleaving 1 LORA: Future by Lund www.futurebylund.se The network will be free for those who want to try their products, services and solutions in a precommercial stage.
Lecture 6 Channel Coding and Interleaving 1 LORA: Future by Lund www.futurebylund.se The network will be free for those who want to try their products, services and solutions in a precommercial stage.
PCM Reference Chapter 12.1, Communication Systems, Carlson. PCM.1
 PCM Reference Chapter 1.1, Communication Systems, Carlson. PCM.1 Pulse-code modulation (PCM) Pulse modulations use discrete time samples of analog signals the transmission is composed of analog information
PCM Reference Chapter 1.1, Communication Systems, Carlson. PCM.1 Pulse-code modulation (PCM) Pulse modulations use discrete time samples of analog signals the transmission is composed of analog information
Lecture 27 Frequency Response 2
 Lecture 27 Frequency Response 2 Fundamentals of Digital Signal Processing Spring, 2012 Wei-Ta Chu 2012/6/12 1 Application of Ideal Filters Suppose we can generate a square wave with a fundamental period
Lecture 27 Frequency Response 2 Fundamentals of Digital Signal Processing Spring, 2012 Wei-Ta Chu 2012/6/12 1 Application of Ideal Filters Suppose we can generate a square wave with a fundamental period
Appendix D: Basics of convolutional codes
 Appendix D: Basics of convolutional codes Convolutional encoder: In convolutional code (B. P. Lathi, 2009; S. G. Wilson, 1996; E. Biglieri, 2005; T. Oberg, 2001), the block of n code bits generated by
Appendix D: Basics of convolutional codes Convolutional encoder: In convolutional code (B. P. Lathi, 2009; S. G. Wilson, 1996; E. Biglieri, 2005; T. Oberg, 2001), the block of n code bits generated by
Projects in Wireless Communication Lecture 1
 Projects in Wireless Communication Lecture 1 Fredrik Tufvesson/Fredrik Rusek Department of Electrical and Information Technology Lund University, Sweden Lund, Sept 2018 Outline Introduction to the course
Projects in Wireless Communication Lecture 1 Fredrik Tufvesson/Fredrik Rusek Department of Electrical and Information Technology Lund University, Sweden Lund, Sept 2018 Outline Introduction to the course
1 1 0, g Exercise 1. Generator polynomials of a convolutional code, given in binary form, are g
 Exercise Generator polynomials of a convolutional code, given in binary form, are g 0, g 2 0 ja g 3. a) Sketch the encoding circuit. b) Sketch the state diagram. c) Find the transfer function TD. d) What
Exercise Generator polynomials of a convolutional code, given in binary form, are g 0, g 2 0 ja g 3. a) Sketch the encoding circuit. b) Sketch the state diagram. c) Find the transfer function TD. d) What
Modulation & Coding for the Gaussian Channel
 Modulation & Coding for the Gaussian Channel Trivandrum School on Communication, Coding & Networking January 27 30, 2017 Lakshmi Prasad Natarajan Dept. of Electrical Engineering Indian Institute of Technology
Modulation & Coding for the Gaussian Channel Trivandrum School on Communication, Coding & Networking January 27 30, 2017 Lakshmi Prasad Natarajan Dept. of Electrical Engineering Indian Institute of Technology
