Large Deviations for Channels with Memory
|
|
|
- Dwayne Caldwell
- 5 years ago
- Views:
Transcription
1 Large Deviations for Channels with Memory Santhosh Kumar Jean-Francois Chamberland Henry Pfister Electrical and Computer Engineering Texas A&M University September 30, / 1
2 Digital Landscape Delay Tolerance and Rate Requirement Context Packetized system supporting delay-sensitive traffic Point-to-point communication with partial feedback 2/ 1
3 Overview Main Objective Analytic framework for delay sensitive systems Rigorous treatment of channels with memory Highlights Focus on delay sensitive systems Random linear codes Large deviations Potential Applications Optimal Code Rate Interface Selection 3/ 1
4 Preview of Result Main Result Large deviation principles on the delay and service rate for channels with memory 4/ 1
5 Preview of Result Main Result Large deviation principles on the delay and service rate for channels with memory Why Large deviations? 4/ 1
6 Preview of Result Main Result Large deviation principles on the delay and service rate for channels with memory Why Large deviations? Represents softer constraints on large buffers 4/ 1
7 Preview of Result Main Result Large deviation principles on the delay and service rate for channels with memory Why Large deviations? Represents softer constraints on large buffers Cumbersome to evaluate explicit probabilities 4/ 1
8 Preview of Result Main Result Large deviation principles on the delay and service rate for channels with memory Why Large deviations? Represents softer constraints on large buffers Cumbersome to evaluate explicit probabilities Provides foundation for other concepts like effective capacity 4/ 1
9 Channel Abstraction - Finite State Bit Erasure Channel At each instant channel can be in one of k states Channel transitions over time form a first-order Markov process In state i, transmitted bit is erased with probability ε i Transition matrix p 11 p 1k..... p k1 p kk Evolution at bit level 1 b 2 b 3 b 1 ε 1 ε 1 1 ε 2 ε 2 1 ε 3 ε 3 b e b e b e 5/ 1
10 Coding Scheme Code Length N Information Bits K Parity Bits N K Code Generation Generate a binary random parity check matrix H of size (N K) N Codebook is null space of H Code Properties Decoding failure probability (under ML) with e erasures P f (N K, e) = e 1 1 (1 2 i (N K)) i=0 6/ 1
11 Distribution of Erasures induced by Channel 7/ 1
12 Distribution of Erasures induced by Channel Interested in conditional probabilities of type ψ = Pr(e Erasures, C N+1 = j C }{{} 1 = i ) }{{} Channel exit state Channel beginning state 7/ 1
13 Distribution of Erasures induced by Channel Interested in conditional probabilities of type ψ = Pr(e Erasures, C N+1 = j C }{{} 1 = i ) }{{} Channel exit state Channel beginning state / 1
14 Distribution of Erasures induced by Channel Interested in conditional probabilities of type ψ = Pr(e Erasures, C N+1 = j C }{{} 1 = i ) }{{} Channel exit state Channel beginning state 3 2 e 3 1 e 7/ 1
15 Distribution of Erasures induced by Channel Interested in conditional probabilities of type ψ = Pr(e Erasures, C N+1 = j C }{{} 1 = i ) }{{} Channel exit state Channel beginning state 3 2 e 3 1 e (1 ε 3 ) p 32 ε 2 p 23 (1 ε 3 ) p 31 ε 1 7/ 1
16 Distribution of Erasures induced by Channel Interested in conditional probabilities of type ψ = Pr(e Erasures, C N+1 = j C }{{} 1 = i ) }{{} Channel exit state Channel beginning state 3 2 e 3 1 e (1 ε 3 ) p 32 ε 2 p 23 (1 ε 3 ) p 31 ε 1 7/ 1
17 Distribution of Erasures induced by Channel Interested in conditional probabilities of type ψ = Pr(e Erasures, C N+1 = j C }{{} 1 = i ) }{{} Channel exit state Channel beginning state 3 2 e 3 1 e (1 ε 3 ) p 32 ε 2 p 23 (1 ε 3 ) p 31 ε 1 7/ 1
18 Distribution of Erasures induced by Channel Interested in conditional probabilities of type ψ = Pr(e Erasures, C N+1 = j C }{{} 1 = i ) }{{} Channel exit state Channel beginning state 3 2 e 3 1 e (1 ε 3 ) p 32 ε 2 p 23 (1 ε 3 ) p 31 ε 1 ψ is the coefficient of x e in [P N x ] ij, where p 11 (1 ε 1 + ε 1 x) p 1k (1 ε 1 + ε 1 x) P x =..... p k1 (1 ε k + ε k x) p kk (1 ε k + ε k x) 7/ 1
19 Packetized Model & Acknowledgments Acknowledgements of successful transmissions are available When transmission fails, data segments are re-transmitted 8/ 1
20 Hidden Markovian System 9/ 1
21 Hidden Markovian System System is Hidden Markov 9/ 1
22 Hidden Markovian System System is Hidden Markov Append Channel State 9/ 1
23 Hidden Markovian System System is Hidden Markov Append Channel State Adding Channel State to Queue Length (C sn+1, q s ) 1, 0 1, 1 1, 2 1, 3 1, 4 2, 0 2, 1 2, 2 2, 3 2, 4 3, 0 3, 1 3, 2 3, 3 3, 4 9/ 1
24 Hidden Markovian System System is Hidden Markov Append Channel State Adding Channel State to Queue Length (C sn+1, q s ) 1, 0 1, 1 1, 2 1, 3 1, 4 2, 0 2, 1 2, 2 2, 3 2, 4 3, 0 3, 1 3, 2 3, 3 3, 4 The aggregate system is Markovian 9/ 1
25 Hidden Markovian System - System Evolution Level Transitions µ 11 µ 21 µ 12 µ 22 µ 32 µ 23 µ 33 κ 21 κ 32 1, l 2, l 3, l κ 12 κ 23 System Evolution Governed by Matrices: M (Success) and K (Failure) M = K = µ 11 µ 12 µ 13 µ 21 µ 22 µ 23 µ 31 µ 32 µ 33 κ 11 κ 12 κ 13 κ 21 κ 22 κ 23 κ 31 κ 32 κ 33 10/ 1
26 Delay & Service Rate - I D 1 = 0 D 2 = 0 D 3 = 0 D 4 = 1 D 5 = 0 D 6 = 0 D 7 = 1 T 1 = 4 T 2 = 3 Delay T q is the time for delivery of data segment q Average Time: Y m = T T m m Service Rate D s (0 or 1) indicates the success of transmission s Average Service Rate: Z n = D D n n 11/ 1
27 Delay & Service Rate - II Delay τ - delay requirement Minimizing Pr(Y m > τ) is a service guarantee on delay Service Rate γ - service requirement Minimizing Pr(Z n < γ) is a service guarantee on rate Basis for the large deviation principles Look at the asymptotic decay rates (as m, n ) of Pr(Y m > τ) and Pr(Z n < γ) For large buffers large deviations characterization is appropriate 12/ 1
28 Large Deviations - A Brief Overview From WLLN, Pr ( X1 + +X n n ) > δ 0, when δ > E(X ) Large deviations theory characterizes the exponential decay rate with which Pr 0 I (δ) = lim }{{} 1 ( ) X1 + + X n log Pr > δ n n n Rate function When {X i } are iid, Cramér s Theorem characterizes the large deviations principle (LDP) When {X i } are weakly dependent, invoke Gärtner-Ellis Theorem 13/ 1
29 Two Deviations Theorem Y m satisfies a large deviations principle with rate function I del ( ) where I del (x) = sup{λx log ρ((i Ke λ ) 1 Me λ )} λ R Theorem Z n satisfies a large deviations principle with rate function I ser ( ) where I ser (x) = sup{λx log ρ(k + Me λ )} λ R ρ( ) is the spectral radius of a Matrix 14/ 1
30 Relation between the deviations Set equivalence {T T m > n} = {D D n < m} Relation xi del (1/x) = I ser (x) This implies the means (in the asymptotic sense) of {D s } and {T q } have an inverse relation 15/ 1
31 Scaling for Commonality 12 bits N = 5, K = 3 N = 6, K = 4 Normalized Delay Ỹ m = NT 1+ +NT m/k m 1 K I del( K N τ) Normalized Service Rate Z n = KD 1+ +KD n/n n 1 N I ser ( N K γ) 16/ 1
32 GSM Example System Parameters Speech frame length 228 bits Physical layer 1 bit in 40µs Delay Tolerance 40ms Requires 228 bits in 1000 channel uses Choose τ = 1000/228 for the example 17/ 1
33 Numerical Analysis System Parameters Channel Gilbert-Elliott Channel Erasure Probabilities ε 1 = 1, ε 2 = 0 Channel Memory 0.9 Code length N=114 Channel Diagram e Average erasure rate is 20% K is the parameter to be optimized 18/ 1
34 Numerical Analysis ( K N τ) 1 K I del τ = τ = τ = τ = ( 1 N N Iser K γ) γ = γ = γ = γ = Information Bits (K) Information Bits (K) Optimal Code Rate Depends heavily on the underlying traffic Very conservative as the service requirements are lowered The perspective of delay and service rate are related 19/ 1
35 Concluding Remarks Main Contributions Provided a methodology for designing delay sensitive systems Rigorously modeled channels with memory Possible Extensions Channel Estimation Analyze variable block lengths 20/ 1
Joint Iterative Decoding of LDPC Codes and Channels with Memory
 Joint Iterative Decoding of LDPC Codes and Channels with Memory Henry D. Pfister and Paul H. Siegel University of California, San Diego 3 rd Int l Symposium on Turbo Codes September 1, 2003 Outline Channels
Joint Iterative Decoding of LDPC Codes and Channels with Memory Henry D. Pfister and Paul H. Siegel University of California, San Diego 3 rd Int l Symposium on Turbo Codes September 1, 2003 Outline Channels
AN increasing number of multimedia applications require. Streaming Codes with Partial Recovery over Channels with Burst and Isolated Erasures
 1 Streaming Codes with Partial Recovery over Channels with Burst and Isolated Erasures Ahmed Badr, Student Member, IEEE, Ashish Khisti, Member, IEEE, Wai-Tian Tan, Member IEEE and John Apostolopoulos,
1 Streaming Codes with Partial Recovery over Channels with Burst and Isolated Erasures Ahmed Badr, Student Member, IEEE, Ashish Khisti, Member, IEEE, Wai-Tian Tan, Member IEEE and John Apostolopoulos,
Queueing Theory I Summary! Little s Law! Queueing System Notation! Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K "
 Queueing Theory I Summary Little s Law Queueing System Notation Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K " Little s Law a(t): the process that counts the number of arrivals
Queueing Theory I Summary Little s Law Queueing System Notation Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K " Little s Law a(t): the process that counts the number of arrivals
Introduction to Markov Chains, Queuing Theory, and Network Performance
 Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
Feedback Capacity of a Class of Symmetric Finite-State Markov Channels
 Feedback Capacity of a Class of Symmetric Finite-State Markov Channels Nevroz Şen, Fady Alajaji and Serdar Yüksel Department of Mathematics and Statistics Queen s University Kingston, ON K7L 3N6, Canada
Feedback Capacity of a Class of Symmetric Finite-State Markov Channels Nevroz Şen, Fady Alajaji and Serdar Yüksel Department of Mathematics and Statistics Queen s University Kingston, ON K7L 3N6, Canada
Capacity of a channel Shannon s second theorem. Information Theory 1/33
 Capacity of a channel Shannon s second theorem Information Theory 1/33 Outline 1. Memoryless channels, examples ; 2. Capacity ; 3. Symmetric channels ; 4. Channel Coding ; 5. Shannon s second theorem,
Capacity of a channel Shannon s second theorem Information Theory 1/33 Outline 1. Memoryless channels, examples ; 2. Capacity ; 3. Symmetric channels ; 4. Channel Coding ; 5. Shannon s second theorem,
Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by Self-similar Traffic
 Èíôîðìàöèîííûå ïðîöåññû, Òîì 5, 1, 2005, ñòð. 4046. c 2004 D'Apice, Manzo. INFORMATION THEORY AND INFORMATION PROCESSING Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by
Èíôîðìàöèîííûå ïðîöåññû, Òîì 5, 1, 2005, ñòð. 4046. c 2004 D'Apice, Manzo. INFORMATION THEORY AND INFORMATION PROCESSING Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by
Recent Results on Input-Constrained Erasure Channels
 Recent Results on Input-Constrained Erasure Channels A Case Study for Markov Approximation July, 2017@NUS Memoryless Channels Memoryless Channels Channel transitions are characterized by time-invariant
Recent Results on Input-Constrained Erasure Channels A Case Study for Markov Approximation July, 2017@NUS Memoryless Channels Memoryless Channels Channel transitions are characterized by time-invariant
Networked Control System Protocols Modeling & Analysis using Stochastic Impulsive Systems
 Networked Control System Protocols Modeling & Analysis using Stochastic Impulsive Systems João P. Hespanha Center for Control Dynamical Systems and Computation Talk outline Examples feedback over shared
Networked Control System Protocols Modeling & Analysis using Stochastic Impulsive Systems João P. Hespanha Center for Control Dynamical Systems and Computation Talk outline Examples feedback over shared
Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching
 Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching Cheng-Shang Chang, Jay Cheng, Tien-Ke Huang, Xuan-Chao Huang, Duan-Shin Lee, and Chao-Yi Chen Institute of Communications Engineering
Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching Cheng-Shang Chang, Jay Cheng, Tien-Ke Huang, Xuan-Chao Huang, Duan-Shin Lee, and Chao-Yi Chen Institute of Communications Engineering
MARKOV PROCESSES. Valerio Di Valerio
 MARKOV PROCESSES Valerio Di Valerio Stochastic Process Definition: a stochastic process is a collection of random variables {X(t)} indexed by time t T Each X(t) X is a random variable that satisfy some
MARKOV PROCESSES Valerio Di Valerio Stochastic Process Definition: a stochastic process is a collection of random variables {X(t)} indexed by time t T Each X(t) X is a random variable that satisfy some
NICTA Short Course. Network Analysis. Vijay Sivaraman. Day 1 Queueing Systems and Markov Chains. Network Analysis, 2008s2 1-1
 NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
Lower Bounds on the Graphical Complexity of Finite-Length LDPC Codes
 Lower Bounds on the Graphical Complexity of Finite-Length LDPC Codes Igal Sason Department of Electrical Engineering Technion - Israel Institute of Technology Haifa 32000, Israel 2009 IEEE International
Lower Bounds on the Graphical Complexity of Finite-Length LDPC Codes Igal Sason Department of Electrical Engineering Technion - Israel Institute of Technology Haifa 32000, Israel 2009 IEEE International
BIRTH DEATH PROCESSES AND QUEUEING SYSTEMS
 BIRTH DEATH PROCESSES AND QUEUEING SYSTEMS Andrea Bobbio Anno Accademico 999-2000 Queueing Systems 2 Notation for Queueing Systems /λ mean time between arrivals S = /µ ρ = λ/µ N mean service time traffic
BIRTH DEATH PROCESSES AND QUEUEING SYSTEMS Andrea Bobbio Anno Accademico 999-2000 Queueing Systems 2 Notation for Queueing Systems /λ mean time between arrivals S = /µ ρ = λ/µ N mean service time traffic
Intro Refresher Reversibility Open networks Closed networks Multiclass networks Other networks. Queuing Networks. Florence Perronnin
 Queuing Networks Florence Perronnin Polytech Grenoble - UGA March 23, 27 F. Perronnin (UGA) Queuing Networks March 23, 27 / 46 Outline Introduction to Queuing Networks 2 Refresher: M/M/ queue 3 Reversibility
Queuing Networks Florence Perronnin Polytech Grenoble - UGA March 23, 27 F. Perronnin (UGA) Queuing Networks March 23, 27 / 46 Outline Introduction to Queuing Networks 2 Refresher: M/M/ queue 3 Reversibility
Solutions to COMP9334 Week 8 Sample Problems
 Solutions to COMP9334 Week 8 Sample Problems Problem 1: Customers arrive at a grocery store s checkout counter according to a Poisson process with rate 1 per minute. Each customer carries a number of items
Solutions to COMP9334 Week 8 Sample Problems Problem 1: Customers arrive at a grocery store s checkout counter according to a Poisson process with rate 1 per minute. Each customer carries a number of items
Solution Set for Homework #1
 CS 683 Spring 07 Learning, Games, and Electronic Markets Solution Set for Homework #1 1. Suppose x and y are real numbers and x > y. Prove that e x > ex e y x y > e y. Solution: Let f(s = e s. By the mean
CS 683 Spring 07 Learning, Games, and Electronic Markets Solution Set for Homework #1 1. Suppose x and y are real numbers and x > y. Prove that e x > ex e y x y > e y. Solution: Let f(s = e s. By the mean
Guess & Check Codes for Deletions, Insertions, and Synchronization
 Guess & Check Codes for Deletions, Insertions, and Synchronization Serge Kas Hanna, Salim El Rouayheb ECE Department, Rutgers University sergekhanna@rutgersedu, salimelrouayheb@rutgersedu arxiv:759569v3
Guess & Check Codes for Deletions, Insertions, and Synchronization Serge Kas Hanna, Salim El Rouayheb ECE Department, Rutgers University sergekhanna@rutgersedu, salimelrouayheb@rutgersedu arxiv:759569v3
The impact of varying channel capacity on the quality of advanced data services in PCS networks
 The impact of varying channel capacity on the quality of advanced data services in PCS networks Markus Fiedler Dept. of Telecommunications and Signal Processing, University of Karlskrona/Ronneby, S-371
The impact of varying channel capacity on the quality of advanced data services in PCS networks Markus Fiedler Dept. of Telecommunications and Signal Processing, University of Karlskrona/Ronneby, S-371
Lecture 6 I. CHANNEL CODING. X n (m) P Y X
 6- Introduction to Information Theory Lecture 6 Lecturer: Haim Permuter Scribe: Yoav Eisenberg and Yakov Miron I. CHANNEL CODING We consider the following channel coding problem: m = {,2,..,2 nr} Encoder
6- Introduction to Information Theory Lecture 6 Lecturer: Haim Permuter Scribe: Yoav Eisenberg and Yakov Miron I. CHANNEL CODING We consider the following channel coding problem: m = {,2,..,2 nr} Encoder
Some Aspects of Finite State Channel related to Hidden Markov Process
 Some Aspects of Finite State Channel related to Hidden Markov Process Kingo Kobayashi National Institute of Information and Communications Tecnology(NICT), 4-2-1, Nukui-Kitamachi, Koganei, Tokyo, 184-8795,
Some Aspects of Finite State Channel related to Hidden Markov Process Kingo Kobayashi National Institute of Information and Communications Tecnology(NICT), 4-2-1, Nukui-Kitamachi, Koganei, Tokyo, 184-8795,
Lecture 4 Noisy Channel Coding
 Lecture 4 Noisy Channel Coding I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw October 9, 2015 1 / 56 I-Hsiang Wang IT Lecture 4 The Channel Coding Problem
Lecture 4 Noisy Channel Coding I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw October 9, 2015 1 / 56 I-Hsiang Wang IT Lecture 4 The Channel Coding Problem
Lecture 8: Shannon s Noise Models
 Error Correcting Codes: Combinatorics, Algorithms and Applications (Fall 2007) Lecture 8: Shannon s Noise Models September 14, 2007 Lecturer: Atri Rudra Scribe: Sandipan Kundu& Atri Rudra Till now we have
Error Correcting Codes: Combinatorics, Algorithms and Applications (Fall 2007) Lecture 8: Shannon s Noise Models September 14, 2007 Lecturer: Atri Rudra Scribe: Sandipan Kundu& Atri Rudra Till now we have
Design of IP networks with Quality of Service
 Course of Multimedia Internet (Sub-course Reti Internet Multimediali ), AA 2010-2011 Prof. Pag. 1 Design of IP networks with Quality of Service 1 Course of Multimedia Internet (Sub-course Reti Internet
Course of Multimedia Internet (Sub-course Reti Internet Multimediali ), AA 2010-2011 Prof. Pag. 1 Design of IP networks with Quality of Service 1 Course of Multimedia Internet (Sub-course Reti Internet
Modeling and Simulation NETW 707
 Modeling and Simulation NETW 707 Lecture 6 ARQ Modeling: Modeling Error/Flow Control Course Instructor: Dr.-Ing. Maggie Mashaly maggie.ezzat@guc.edu.eg C3.220 1 Data Link Layer Data Link Layer provides
Modeling and Simulation NETW 707 Lecture 6 ARQ Modeling: Modeling Error/Flow Control Course Instructor: Dr.-Ing. Maggie Mashaly maggie.ezzat@guc.edu.eg C3.220 1 Data Link Layer Data Link Layer provides
Introduction to Convolutional Codes, Part 1
 Introduction to Convolutional Codes, Part 1 Frans M.J. Willems, Eindhoven University of Technology September 29, 2009 Elias, Father of Coding Theory Textbook Encoder Encoder Properties Systematic Codes
Introduction to Convolutional Codes, Part 1 Frans M.J. Willems, Eindhoven University of Technology September 29, 2009 Elias, Father of Coding Theory Textbook Encoder Encoder Properties Systematic Codes
Lecture 14 February 28
 EE/Stats 376A: Information Theory Winter 07 Lecture 4 February 8 Lecturer: David Tse Scribe: Sagnik M, Vivek B 4 Outline Gaussian channel and capacity Information measures for continuous random variables
EE/Stats 376A: Information Theory Winter 07 Lecture 4 February 8 Lecturer: David Tse Scribe: Sagnik M, Vivek B 4 Outline Gaussian channel and capacity Information measures for continuous random variables
Turbo Compression. Andrej Rikovsky, Advisor: Pavol Hanus
 Turbo Compression Andrej Rikovsky, Advisor: Pavol Hanus Abstract Turbo codes which performs very close to channel capacity in channel coding can be also used to obtain very efficient source coding schemes.
Turbo Compression Andrej Rikovsky, Advisor: Pavol Hanus Abstract Turbo codes which performs very close to channel capacity in channel coding can be also used to obtain very efficient source coding schemes.
Capacity-Achieving Ensembles for the Binary Erasure Channel With Bounded Complexity
 Capacity-Achieving Ensembles for the Binary Erasure Channel With Bounded Complexity Henry D. Pfister, Member, Igal Sason, Member, and Rüdiger Urbanke Abstract We present two sequences of ensembles of non-systematic
Capacity-Achieving Ensembles for the Binary Erasure Channel With Bounded Complexity Henry D. Pfister, Member, Igal Sason, Member, and Rüdiger Urbanke Abstract We present two sequences of ensembles of non-systematic
Chapter 5. Elementary Performance Analysis
 Chapter 5 Elementary Performance Analysis 1 5.0 2 5.1 Ref: Mischa Schwartz Telecommunication Networks Addison-Wesley publishing company 1988 3 4 p t T m T P(k)= 5 6 5.2 : arrived rate : service rate 7
Chapter 5 Elementary Performance Analysis 1 5.0 2 5.1 Ref: Mischa Schwartz Telecommunication Networks Addison-Wesley publishing company 1988 3 4 p t T m T P(k)= 5 6 5.2 : arrived rate : service rate 7
Chapter 1 Elements of Information Theory for Networked Control Systems
 Chapter 1 Elements of Information Theory for Networked Control Systems Massimo Franceschetti and Paolo Minero 1.1 Introduction Next generation cyber-physical systems [35] will integrate computing, communication,
Chapter 1 Elements of Information Theory for Networked Control Systems Massimo Franceschetti and Paolo Minero 1.1 Introduction Next generation cyber-physical systems [35] will integrate computing, communication,
Wireless Internet Exercises
 Wireless Internet Exercises Prof. Alessandro Redondi 2018-05-28 1 WLAN 1.1 Exercise 1 A Wi-Fi network has the following features: Physical layer transmission rate: 54 Mbps MAC layer header: 28 bytes MAC
Wireless Internet Exercises Prof. Alessandro Redondi 2018-05-28 1 WLAN 1.1 Exercise 1 A Wi-Fi network has the following features: Physical layer transmission rate: 54 Mbps MAC layer header: 28 bytes MAC
Dispersion of the Gilbert-Elliott Channel
 Dispersion of the Gilbert-Elliott Channel Yury Polyanskiy Email: ypolyans@princeton.edu H. Vincent Poor Email: poor@princeton.edu Sergio Verdú Email: verdu@princeton.edu Abstract Channel dispersion plays
Dispersion of the Gilbert-Elliott Channel Yury Polyanskiy Email: ypolyans@princeton.edu H. Vincent Poor Email: poor@princeton.edu Sergio Verdú Email: verdu@princeton.edu Abstract Channel dispersion plays
MARKOV CHAINS A finite state Markov chain is a sequence of discrete cv s from a finite alphabet where is a pmf on and for
 MARKOV CHAINS A finite state Markov chain is a sequence S 0,S 1,... of discrete cv s from a finite alphabet S where q 0 (s) is a pmf on S 0 and for n 1, Q(s s ) = Pr(S n =s S n 1 =s ) = Pr(S n =s S n 1
MARKOV CHAINS A finite state Markov chain is a sequence S 0,S 1,... of discrete cv s from a finite alphabet S where q 0 (s) is a pmf on S 0 and for n 1, Q(s s ) = Pr(S n =s S n 1 =s ) = Pr(S n =s S n 1
Stochastic process. X, a series of random variables indexed by t
 Stochastic process X, a series of random variables indexed by t X={X(t), t 0} is a continuous time stochastic process X={X(t), t=0,1, } is a discrete time stochastic process X(t) is the state at time t,
Stochastic process X, a series of random variables indexed by t X={X(t), t 0} is a continuous time stochastic process X={X(t), t=0,1, } is a discrete time stochastic process X(t) is the state at time t,
Approximate Queueing Model for Multi-rate Multi-user MIMO systems.
 An Approximate Queueing Model for Multi-rate Multi-user MIMO systems Boris Bellalta,Vanesa Daza, Miquel Oliver Abstract A queueing model for Multi-rate Multi-user MIMO systems is presented. The model is
An Approximate Queueing Model for Multi-rate Multi-user MIMO systems Boris Bellalta,Vanesa Daza, Miquel Oliver Abstract A queueing model for Multi-rate Multi-user MIMO systems is presented. The model is
Fundamental Limits of Invisible Flow Fingerprinting
 Fundamental Limits of Invisible Flow Fingerprinting Ramin Soltani, Dennis Goeckel, Don Towsley, and Amir Houmansadr Electrical and Computer Engineering Department, University of Massachusetts, Amherst,
Fundamental Limits of Invisible Flow Fingerprinting Ramin Soltani, Dennis Goeckel, Don Towsley, and Amir Houmansadr Electrical and Computer Engineering Department, University of Massachusetts, Amherst,
Capacity Region of the Permutation Channel
 Capacity Region of the Permutation Channel John MacLaren Walsh and Steven Weber Abstract We discuss the capacity region of a degraded broadcast channel (DBC) formed from a channel that randomly permutes
Capacity Region of the Permutation Channel John MacLaren Walsh and Steven Weber Abstract We discuss the capacity region of a degraded broadcast channel (DBC) formed from a channel that randomly permutes
Fundamental rate delay tradeoffs in multipath routed and network coded networks
 Fundamental rate delay tradeoffs in multipath routed and network coded networks John Walsh and Steven Weber Drexel University, Dept of ECE Philadelphia, PA 94 {jwalsh,sweber}@ecedrexeledu IP networks subject
Fundamental rate delay tradeoffs in multipath routed and network coded networks John Walsh and Steven Weber Drexel University, Dept of ECE Philadelphia, PA 94 {jwalsh,sweber}@ecedrexeledu IP networks subject
Asymptotic Statistics-III. Changliang Zou
 Asymptotic Statistics-III Changliang Zou The multivariate central limit theorem Theorem (Multivariate CLT for iid case) Let X i be iid random p-vectors with mean µ and and covariance matrix Σ. Then n (
Asymptotic Statistics-III Changliang Zou The multivariate central limit theorem Theorem (Multivariate CLT for iid case) Let X i be iid random p-vectors with mean µ and and covariance matrix Σ. Then n (
Homework 1 - SOLUTION
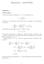 Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
Relaying Information Streams
 Relaying Information Streams Anant Sahai UC Berkeley EECS sahai@eecs.berkeley.edu Originally given: Oct 2, 2002 This was a talk only. I was never able to rigorously formalize the back-of-the-envelope reasoning
Relaying Information Streams Anant Sahai UC Berkeley EECS sahai@eecs.berkeley.edu Originally given: Oct 2, 2002 This was a talk only. I was never able to rigorously formalize the back-of-the-envelope reasoning
ITCT Lecture IV.3: Markov Processes and Sources with Memory
 ITCT Lecture IV.3: Markov Processes and Sources with Memory 4. Markov Processes Thus far, we have been occupied with memoryless sources and channels. We must now turn our attention to sources with memory.
ITCT Lecture IV.3: Markov Processes and Sources with Memory 4. Markov Processes Thus far, we have been occupied with memoryless sources and channels. We must now turn our attention to sources with memory.
ELEC546 Review of Information Theory
 ELEC546 Review of Information Theory Vincent Lau 1/1/004 1 Review of Information Theory Entropy: Measure of uncertainty of a random variable X. The entropy of X, H(X), is given by: If X is a discrete random
ELEC546 Review of Information Theory Vincent Lau 1/1/004 1 Review of Information Theory Entropy: Measure of uncertainty of a random variable X. The entropy of X, H(X), is given by: If X is a discrete random
Capacity of the Discrete Memoryless Energy Harvesting Channel with Side Information
 204 IEEE International Symposium on Information Theory Capacity of the Discrete Memoryless Energy Harvesting Channel with Side Information Omur Ozel, Kaya Tutuncuoglu 2, Sennur Ulukus, and Aylin Yener
204 IEEE International Symposium on Information Theory Capacity of the Discrete Memoryless Energy Harvesting Channel with Side Information Omur Ozel, Kaya Tutuncuoglu 2, Sennur Ulukus, and Aylin Yener
Diversity-Multiplexing Tradeoff in MIMO Channels with Partial CSIT. ECE 559 Presentation Hoa Pham Dec 3, 2007
 Diversity-Multiplexing Tradeoff in MIMO Channels with Partial CSIT ECE 559 Presentation Hoa Pham Dec 3, 2007 Introduction MIMO systems provide two types of gains Diversity Gain: each path from a transmitter
Diversity-Multiplexing Tradeoff in MIMO Channels with Partial CSIT ECE 559 Presentation Hoa Pham Dec 3, 2007 Introduction MIMO systems provide two types of gains Diversity Gain: each path from a transmitter
Tail Inequalities Randomized Algorithms. Sariel Har-Peled. December 20, 2002
 Tail Inequalities 497 - Randomized Algorithms Sariel Har-Peled December 0, 00 Wir mssen wissen, wir werden wissen (We must know, we shall know) David Hilbert 1 Tail Inequalities 1.1 The Chernoff Bound
Tail Inequalities 497 - Randomized Algorithms Sariel Har-Peled December 0, 00 Wir mssen wissen, wir werden wissen (We must know, we shall know) David Hilbert 1 Tail Inequalities 1.1 The Chernoff Bound
Positive Harris Recurrence and Diffusion Scale Analysis of a Push Pull Queueing Network. Haifa Statistics Seminar May 5, 2008
 Positive Harris Recurrence and Diffusion Scale Analysis of a Push Pull Queueing Network Yoni Nazarathy Gideon Weiss Haifa Statistics Seminar May 5, 2008 1 Outline 1 Preview of Results 2 Introduction Queueing
Positive Harris Recurrence and Diffusion Scale Analysis of a Push Pull Queueing Network Yoni Nazarathy Gideon Weiss Haifa Statistics Seminar May 5, 2008 1 Outline 1 Preview of Results 2 Introduction Queueing
Anytime Capacity of the AWGN+Erasure Channel with Feedback. Qing Xu. B.S. (Beijing University) 1997 M.S. (University of California at Berkeley) 2000
 Anytime Capacity of the AWGN+Erasure Channel with Feedback by Qing Xu B.S. (Beijing University) 1997 M.S. (University of California at Berkeley) 2000 A dissertation submitted in partial satisfaction of
Anytime Capacity of the AWGN+Erasure Channel with Feedback by Qing Xu B.S. (Beijing University) 1997 M.S. (University of California at Berkeley) 2000 A dissertation submitted in partial satisfaction of
Queueing Theory II. Summary. ! M/M/1 Output process. ! Networks of Queue! Method of Stages. ! General Distributions
 Queueing Theory II Summary! M/M/1 Output process! Networks of Queue! Method of Stages " Erlang Distribution " Hyperexponential Distribution! General Distributions " Embedded Markov Chains M/M/1 Output
Queueing Theory II Summary! M/M/1 Output process! Networks of Queue! Method of Stages " Erlang Distribution " Hyperexponential Distribution! General Distributions " Embedded Markov Chains M/M/1 Output
CDA5530: Performance Models of Computers and Networks. Chapter 4: Elementary Queuing Theory
 CDA5530: Performance Models of Computers and Networks Chapter 4: Elementary Queuing Theory Definition Queuing system: a buffer (waiting room), service facility (one or more servers) a scheduling policy
CDA5530: Performance Models of Computers and Networks Chapter 4: Elementary Queuing Theory Definition Queuing system: a buffer (waiting room), service facility (one or more servers) a scheduling policy
Compressed Sensing and Linear Codes over Real Numbers
 Compressed Sensing and Linear Codes over Real Numbers Henry D. Pfister (joint with Fan Zhang) Texas A&M University College Station Information Theory and Applications Workshop UC San Diego January 31st,
Compressed Sensing and Linear Codes over Real Numbers Henry D. Pfister (joint with Fan Zhang) Texas A&M University College Station Information Theory and Applications Workshop UC San Diego January 31st,
6 Solving Queueing Models
 6 Solving Queueing Models 6.1 Introduction In this note we look at the solution of systems of queues, starting with simple isolated queues. The benefits of using predefined, easily classified queues will
6 Solving Queueing Models 6.1 Introduction In this note we look at the solution of systems of queues, starting with simple isolated queues. The benefits of using predefined, easily classified queues will
Message Delivery Probability of Two-Hop Relay with Erasure Coding in MANETs
 01 7th International ICST Conference on Communications and Networking in China (CHINACOM) Message Delivery Probability of Two-Hop Relay with Erasure Coding in MANETs Jiajia Liu Tohoku University Sendai,
01 7th International ICST Conference on Communications and Networking in China (CHINACOM) Message Delivery Probability of Two-Hop Relay with Erasure Coding in MANETs Jiajia Liu Tohoku University Sendai,
Stochastic Optimization for Undergraduate Computer Science Students
 Stochastic Optimization for Undergraduate Computer Science Students Professor Joongheon Kim School of Computer Science and Engineering, Chung-Ang University, Seoul, Republic of Korea 1 Reference 2 Outline
Stochastic Optimization for Undergraduate Computer Science Students Professor Joongheon Kim School of Computer Science and Engineering, Chung-Ang University, Seoul, Republic of Korea 1 Reference 2 Outline
Communications Theory and Engineering
 Communications Theory and Engineering Master's Degree in Electronic Engineering Sapienza University of Rome A.A. 2018-2019 AEP Asymptotic Equipartition Property AEP In information theory, the analog of
Communications Theory and Engineering Master's Degree in Electronic Engineering Sapienza University of Rome A.A. 2018-2019 AEP Asymptotic Equipartition Property AEP In information theory, the analog of
Error Detection and Correction: Hamming Code; Reed-Muller Code
 Error Detection and Correction: Hamming Code; Reed-Muller Code Greg Plaxton Theory in Programming Practice, Spring 2005 Department of Computer Science University of Texas at Austin Hamming Code: Motivation
Error Detection and Correction: Hamming Code; Reed-Muller Code Greg Plaxton Theory in Programming Practice, Spring 2005 Department of Computer Science University of Texas at Austin Hamming Code: Motivation
Resource Allocation for Video Streaming in Wireless Environment
 Resource Allocation for Video Streaming in Wireless Environment Shahrokh Valaee and Jean-Charles Gregoire Abstract This paper focuses on the development of a new resource allocation scheme for video streaming
Resource Allocation for Video Streaming in Wireless Environment Shahrokh Valaee and Jean-Charles Gregoire Abstract This paper focuses on the development of a new resource allocation scheme for video streaming
ECEN 655: Advanced Channel Coding
 ECEN 655: Advanced Channel Coding Course Introduction Henry D. Pfister Department of Electrical and Computer Engineering Texas A&M University ECEN 655: Advanced Channel Coding 1 / 19 Outline 1 History
ECEN 655: Advanced Channel Coding Course Introduction Henry D. Pfister Department of Electrical and Computer Engineering Texas A&M University ECEN 655: Advanced Channel Coding 1 / 19 Outline 1 History
Capacity Bounds on Timing Channels with Bounded Service Times
 Capacity Bounds on Timing Channels with Bounded Service Times S. Sellke, C.-C. Wang, N. B. Shroff, and S. Bagchi School of Electrical and Computer Engineering Purdue University, West Lafayette, IN 47907
Capacity Bounds on Timing Channels with Bounded Service Times S. Sellke, C.-C. Wang, N. B. Shroff, and S. Bagchi School of Electrical and Computer Engineering Purdue University, West Lafayette, IN 47907
This examination consists of 11 pages. Please check that you have a complete copy. Time: 2.5 hrs INSTRUCTIONS
 THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 6 December 2006 This examination consists of
THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 6 December 2006 This examination consists of
SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land
 SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land Ingmar Land, SIPCom8-1: Information Theory and Coding (2005 Spring) p.1 Overview Basic Concepts of Channel Coding Block Codes I:
SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land Ingmar Land, SIPCom8-1: Information Theory and Coding (2005 Spring) p.1 Overview Basic Concepts of Channel Coding Block Codes I:
Chapter 4. Data Transmission and Channel Capacity. Po-Ning Chen, Professor. Department of Communications Engineering. National Chiao Tung University
 Chapter 4 Data Transmission and Channel Capacity Po-Ning Chen, Professor Department of Communications Engineering National Chiao Tung University Hsin Chu, Taiwan 30050, R.O.C. Principle of Data Transmission
Chapter 4 Data Transmission and Channel Capacity Po-Ning Chen, Professor Department of Communications Engineering National Chiao Tung University Hsin Chu, Taiwan 30050, R.O.C. Principle of Data Transmission
Linear Model Predictive Control for Queueing Networks in Manufacturing and Road Traffic
 Linear Model Predictive Control for ueueing Networks in Manufacturing and Road Traffic Yoni Nazarathy Swinburne University of Technology, Melbourne. Joint work with: Erjen Lefeber (manufacturing), Hai
Linear Model Predictive Control for ueueing Networks in Manufacturing and Road Traffic Yoni Nazarathy Swinburne University of Technology, Melbourne. Joint work with: Erjen Lefeber (manufacturing), Hai
Waiting-Time Distribution of a Discrete-time Multiserver Queue with Correlated. Arrivals and Deterministic Service Times: D-MAP/D/k System
 Waiting-Time Distribution of a Discrete-time Multiserver Queue with Correlated Arrivals and Deterministic Service Times: D-MAP/D/k System Mohan L. Chaudhry a, *, Bong K. Yoon b, Kyung C. Chae b a Department
Waiting-Time Distribution of a Discrete-time Multiserver Queue with Correlated Arrivals and Deterministic Service Times: D-MAP/D/k System Mohan L. Chaudhry a, *, Bong K. Yoon b, Kyung C. Chae b a Department
Multiaccess Communication
 Information Networks p. 1 Multiaccess Communication Satellite systems, radio networks (WLAN), Ethernet segment The received signal is the sum of attenuated transmitted signals from a set of other nodes,
Information Networks p. 1 Multiaccess Communication Satellite systems, radio networks (WLAN), Ethernet segment The received signal is the sum of attenuated transmitted signals from a set of other nodes,
Information and Entropy
 Information and Entropy Shannon s Separation Principle Source Coding Principles Entropy Variable Length Codes Huffman Codes Joint Sources Arithmetic Codes Adaptive Codes Thomas Wiegand: Digital Image Communication
Information and Entropy Shannon s Separation Principle Source Coding Principles Entropy Variable Length Codes Huffman Codes Joint Sources Arithmetic Codes Adaptive Codes Thomas Wiegand: Digital Image Communication
Lecture 4: Proof of Shannon s theorem and an explicit code
 CSE 533: Error-Correcting Codes (Autumn 006 Lecture 4: Proof of Shannon s theorem and an explicit code October 11, 006 Lecturer: Venkatesan Guruswami Scribe: Atri Rudra 1 Overview Last lecture we stated
CSE 533: Error-Correcting Codes (Autumn 006 Lecture 4: Proof of Shannon s theorem and an explicit code October 11, 006 Lecturer: Venkatesan Guruswami Scribe: Atri Rudra 1 Overview Last lecture we stated
Lecture 4 : Introduction to Low-density Parity-check Codes
 Lecture 4 : Introduction to Low-density Parity-check Codes LDPC codes are a class of linear block codes with implementable decoders, which provide near-capacity performance. History: 1. LDPC codes were
Lecture 4 : Introduction to Low-density Parity-check Codes LDPC codes are a class of linear block codes with implementable decoders, which provide near-capacity performance. History: 1. LDPC codes were
LIMITS FOR QUEUES AS THE WAITING ROOM GROWS. Bell Communications Research AT&T Bell Laboratories Red Bank, NJ Murray Hill, NJ 07974
 LIMITS FOR QUEUES AS THE WAITING ROOM GROWS by Daniel P. Heyman Ward Whitt Bell Communications Research AT&T Bell Laboratories Red Bank, NJ 07701 Murray Hill, NJ 07974 May 11, 1988 ABSTRACT We study the
LIMITS FOR QUEUES AS THE WAITING ROOM GROWS by Daniel P. Heyman Ward Whitt Bell Communications Research AT&T Bell Laboratories Red Bank, NJ 07701 Murray Hill, NJ 07974 May 11, 1988 ABSTRACT We study the
Stochastic Network Calculus
 Stochastic Network Calculus Assessing the Performance of the Future Internet Markus Fidler joint work with Amr Rizk Institute of Communications Technology Leibniz Universität Hannover April 22, 2010 c
Stochastic Network Calculus Assessing the Performance of the Future Internet Markus Fidler joint work with Amr Rizk Institute of Communications Technology Leibniz Universität Hannover April 22, 2010 c
On ARQ for Packet Erasure Channels with Bernoulli Arrivals
 On ARQ for Packet Erasure Channels with Bernoulli Arrivals Dinkar Vasudevan, Vijay G. Subramanian and Douglas J. Leith Hamilton Institute, National University of Ireland, Maynooth Abstract We study packet
On ARQ for Packet Erasure Channels with Bernoulli Arrivals Dinkar Vasudevan, Vijay G. Subramanian and Douglas J. Leith Hamilton Institute, National University of Ireland, Maynooth Abstract We study packet
Information Theory. Lecture 10. Network Information Theory (CT15); a focus on channel capacity results
 Information Theory Lecture 10 Network Information Theory (CT15); a focus on channel capacity results The (two-user) multiple access channel (15.3) The (two-user) broadcast channel (15.6) The relay channel
Information Theory Lecture 10 Network Information Theory (CT15); a focus on channel capacity results The (two-user) multiple access channel (15.3) The (two-user) broadcast channel (15.6) The relay channel
requests/sec. The total channel load is requests/sec. Using slot as the time unit, the total channel load is 50 ( ) = 1
 Prof. X. Shen E&CE 70 : Examples #2 Problem Consider the following Aloha systems. (a) A group of N users share a 56 kbps pure Aloha channel. Each user generates at a Passion rate of one 000-bit packet
Prof. X. Shen E&CE 70 : Examples #2 Problem Consider the following Aloha systems. (a) A group of N users share a 56 kbps pure Aloha channel. Each user generates at a Passion rate of one 000-bit packet
Lecture 3: Channel Capacity
 Lecture 3: Channel Capacity 1 Definitions Channel capacity is a measure of maximum information per channel usage one can get through a channel. This one of the fundamental concepts in information theory.
Lecture 3: Channel Capacity 1 Definitions Channel capacity is a measure of maximum information per channel usage one can get through a channel. This one of the fundamental concepts in information theory.
Distributed Data Storage with Minimum Storage Regenerating Codes - Exact and Functional Repair are Asymptotically Equally Efficient
 Distributed Data Storage with Minimum Storage Regenerating Codes - Exact and Functional Repair are Asymptotically Equally Efficient Viveck R Cadambe, Syed A Jafar, Hamed Maleki Electrical Engineering and
Distributed Data Storage with Minimum Storage Regenerating Codes - Exact and Functional Repair are Asymptotically Equally Efficient Viveck R Cadambe, Syed A Jafar, Hamed Maleki Electrical Engineering and
An engineering approximation for the mean waiting time in the M/H 2 b /s queue
 An engineering approximation for the mean waiting time in the M/H b /s queue Francisco Barceló Universidad Politécnica de Catalunya c/ Jordi Girona, -3, Barcelona 08034 Email : barcelo@entel.upc.es Abstract
An engineering approximation for the mean waiting time in the M/H b /s queue Francisco Barceló Universidad Politécnica de Catalunya c/ Jordi Girona, -3, Barcelona 08034 Email : barcelo@entel.upc.es Abstract
Estimation of the long Memory parameter using an Infinite Source Poisson model applied to transmission rate measurements
 of the long Memory parameter using an Infinite Source Poisson model applied to transmission rate measurements François Roueff Ecole Nat. Sup. des Télécommunications 46 rue Barrault, 75634 Paris cedex 13,
of the long Memory parameter using an Infinite Source Poisson model applied to transmission rate measurements François Roueff Ecole Nat. Sup. des Télécommunications 46 rue Barrault, 75634 Paris cedex 13,
Congestion Control. Need to understand: What is congestion? How do we prevent or manage it?
 Congestion Control Phenomenon: when too much traffic enters into system, performance degrades excessive traffic can cause congestion Problem: regulate traffic influx such that congestion does not occur
Congestion Control Phenomenon: when too much traffic enters into system, performance degrades excessive traffic can cause congestion Problem: regulate traffic influx such that congestion does not occur
Control Over Noisy Channels
 IEEE RANSACIONS ON AUOMAIC CONROL, VOL??, NO??, MONH?? 004 Control Over Noisy Channels Sekhar atikonda, Member, IEEE, and Sanjoy Mitter, Fellow, IEEE, Abstract Communication is an important component of
IEEE RANSACIONS ON AUOMAIC CONROL, VOL??, NO??, MONH?? 004 Control Over Noisy Channels Sekhar atikonda, Member, IEEE, and Sanjoy Mitter, Fellow, IEEE, Abstract Communication is an important component of
On Achievable Rates and Complexity of LDPC Codes over Parallel Channels: Bounds and Applications
 On Achievable Rates and Complexity of LDPC Codes over Parallel Channels: Bounds and Applications Igal Sason, Member and Gil Wiechman, Graduate Student Member Abstract A variety of communication scenarios
On Achievable Rates and Complexity of LDPC Codes over Parallel Channels: Bounds and Applications Igal Sason, Member and Gil Wiechman, Graduate Student Member Abstract A variety of communication scenarios
Operational Laws Raj Jain
 Operational Laws 33-1 Overview What is an Operational Law? 1. Utilization Law 2. Forced Flow Law 3. Little s Law 4. General Response Time Law 5. Interactive Response Time Law 6. Bottleneck Analysis 33-2
Operational Laws 33-1 Overview What is an Operational Law? 1. Utilization Law 2. Forced Flow Law 3. Little s Law 4. General Response Time Law 5. Interactive Response Time Law 6. Bottleneck Analysis 33-2
M.Sc. (MATHEMATICS WITH APPLICATIONS IN COMPUTER SCIENCE) M.Sc. (MACS)
 No. of Printed Pages : 6 MMT-008 M.Sc. (MATHEMATICS WITH APPLICATIONS IN COMPUTER SCIENCE) M.Sc. (MACS) Term-End Examination 0064 December, 202 MMT-008 : PROBABILITY AND STATISTICS Time : 3 hours Maximum
No. of Printed Pages : 6 MMT-008 M.Sc. (MATHEMATICS WITH APPLICATIONS IN COMPUTER SCIENCE) M.Sc. (MACS) Term-End Examination 0064 December, 202 MMT-008 : PROBABILITY AND STATISTICS Time : 3 hours Maximum
Survey of Source Modeling Techniques for ATM Networks
 Survey of Source Modeling Techniques for ATM Networks Sponsor: Sprint Yong-Qing Lu David W. Petr Victor S. Frost Technical Report TISL-10230-1 Telecommunications and Information Sciences Laboratory Department
Survey of Source Modeling Techniques for ATM Networks Sponsor: Sprint Yong-Qing Lu David W. Petr Victor S. Frost Technical Report TISL-10230-1 Telecommunications and Information Sciences Laboratory Department
Information Sources. Professor A. Manikas. Imperial College London. EE303 - Communication Systems An Overview of Fundamentals
 Information Sources Professor A. Manikas Imperial College London EE303 - Communication Systems An Overview of Fundamentals Prof. A. Manikas (Imperial College) EE303: Information Sources 24 Oct. 2011 1
Information Sources Professor A. Manikas Imperial College London EE303 - Communication Systems An Overview of Fundamentals Prof. A. Manikas (Imperial College) EE303: Information Sources 24 Oct. 2011 1
Distributed Source Coding Using LDPC Codes
 Distributed Source Coding Using LDPC Codes Telecommunications Laboratory Alex Balatsoukas-Stimming Technical University of Crete May 29, 2010 Telecommunications Laboratory (TUC) Distributed Source Coding
Distributed Source Coding Using LDPC Codes Telecommunications Laboratory Alex Balatsoukas-Stimming Technical University of Crete May 29, 2010 Telecommunications Laboratory (TUC) Distributed Source Coding
16.36 Communication Systems Engineering
 MIT OpenCourseWare http://ocw.mit.edu 16.36 Communication Systems Engineering Spring 2009 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. 16.36: Communication
MIT OpenCourseWare http://ocw.mit.edu 16.36 Communication Systems Engineering Spring 2009 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. 16.36: Communication
Lecture 4. Capacity of Fading Channels
 1 Lecture 4. Capacity of Fading Channels Capacity of AWGN Channels Capacity of Fading Channels Ergodic Capacity Outage Capacity Shannon and Information Theory Claude Elwood Shannon (April 3, 1916 February
1 Lecture 4. Capacity of Fading Channels Capacity of AWGN Channels Capacity of Fading Channels Ergodic Capacity Outage Capacity Shannon and Information Theory Claude Elwood Shannon (April 3, 1916 February
Cyclic Redundancy Check Codes
 Cyclic Redundancy Check Codes Lectures No. 17 and 18 Dr. Aoife Moloney School of Electronics and Communications Dublin Institute of Technology Overview These lectures will look at the following: Cyclic
Cyclic Redundancy Check Codes Lectures No. 17 and 18 Dr. Aoife Moloney School of Electronics and Communications Dublin Institute of Technology Overview These lectures will look at the following: Cyclic
Performance Evaluation of Queuing Systems
 Performance Evaluation of Queuing Systems Introduction to Queuing Systems System Performance Measures & Little s Law Equilibrium Solution of Birth-Death Processes Analysis of Single-Station Queuing Systems
Performance Evaluation of Queuing Systems Introduction to Queuing Systems System Performance Measures & Little s Law Equilibrium Solution of Birth-Death Processes Analysis of Single-Station Queuing Systems
Symmetric Product Codes
 Symmetric Product Codes Henry D. Pfister 1, Santosh Emmadi 2, and Krishna Narayanan 2 1 Department of Electrical and Computer Engineering Duke University 2 Department of Electrical and Computer Engineering
Symmetric Product Codes Henry D. Pfister 1, Santosh Emmadi 2, and Krishna Narayanan 2 1 Department of Electrical and Computer Engineering Duke University 2 Department of Electrical and Computer Engineering
Layered Error-Correction Codes for Real-Time Streaming over Erasure Channels
 Layered Error-Correction Codes for Real-Time Streaming over Erasure Channels Ashish Khisti University of Toronto Joint Work: Ahmed Badr (Toronto), Wai-Tian Tan (Cisco), John Apostolopoulos (Cisco). Sequential
Layered Error-Correction Codes for Real-Time Streaming over Erasure Channels Ashish Khisti University of Toronto Joint Work: Ahmed Badr (Toronto), Wai-Tian Tan (Cisco), John Apostolopoulos (Cisco). Sequential
Chapter 3 Balance equations, birth-death processes, continuous Markov Chains
 Chapter 3 Balance equations, birth-death processes, continuous Markov Chains Ioannis Glaropoulos November 4, 2012 1 Exercise 3.2 Consider a birth-death process with 3 states, where the transition rate
Chapter 3 Balance equations, birth-death processes, continuous Markov Chains Ioannis Glaropoulos November 4, 2012 1 Exercise 3.2 Consider a birth-death process with 3 states, where the transition rate
On Asymptotic Strategies for GMD Decoding with Arbitrary Error-Erasure Tradeoff
 On Asymptotic Strategies for GMD Decoding with Arbitrary Error-Erasure Tradeoff Joschi Brauchle and Vladimir Sidorenko Institute for Communications Engineering, Technische Universität München Arcisstrasse
On Asymptotic Strategies for GMD Decoding with Arbitrary Error-Erasure Tradeoff Joschi Brauchle and Vladimir Sidorenko Institute for Communications Engineering, Technische Universität München Arcisstrasse
Technion - Computer Science Department - Technical Report CS On Centralized Smooth Scheduling
 On Centralized Smooth Scheduling Ami Litman January 25, 2005 Abstract Shiri Moran-Schein This paper studies evenly distributed sets of natural numbers and their applications to scheduling in a centralized
On Centralized Smooth Scheduling Ami Litman January 25, 2005 Abstract Shiri Moran-Schein This paper studies evenly distributed sets of natural numbers and their applications to scheduling in a centralized
Predictive Coding. Prediction Prediction in Images
 Prediction Prediction in Images Predictive Coding Principle of Differential Pulse Code Modulation (DPCM) DPCM and entropy-constrained scalar quantization DPCM and transmission errors Adaptive intra-interframe
Prediction Prediction in Images Predictive Coding Principle of Differential Pulse Code Modulation (DPCM) DPCM and entropy-constrained scalar quantization DPCM and transmission errors Adaptive intra-interframe
Predictive Coding. Prediction
 Predictive Coding Prediction Prediction in Images Principle of Differential Pulse Code Modulation (DPCM) DPCM and entropy-constrained scalar quantization DPCM and transmission errors Adaptive intra-interframe
Predictive Coding Prediction Prediction in Images Principle of Differential Pulse Code Modulation (DPCM) DPCM and entropy-constrained scalar quantization DPCM and transmission errors Adaptive intra-interframe
Introduction to queuing theory
 Introduction to queuing theory Claude Rigault ENST claude.rigault@enst.fr Introduction to Queuing theory 1 Outline The problem The number of clients in a system The client process Delay processes Loss
Introduction to queuing theory Claude Rigault ENST claude.rigault@enst.fr Introduction to Queuing theory 1 Outline The problem The number of clients in a system The client process Delay processes Loss
Optimal power-delay trade-offs in fading channels: small delay asymptotics
 Optimal power-delay trade-offs in fading channels: small delay asymptotics Randall A. Berry Dept. of EECS, Northwestern University 45 Sheridan Rd., Evanston IL 6008 Email: rberry@ece.northwestern.edu Abstract
Optimal power-delay trade-offs in fading channels: small delay asymptotics Randall A. Berry Dept. of EECS, Northwestern University 45 Sheridan Rd., Evanston IL 6008 Email: rberry@ece.northwestern.edu Abstract
BOUNDS ON THE MAP THRESHOLD OF ITERATIVE DECODING SYSTEMS WITH ERASURE NOISE. A Thesis CHIA-WEN WANG
 BOUNDS ON THE MAP THRESHOLD OF ITERATIVE DECODING SYSTEMS WITH ERASURE NOISE A Thesis by CHIA-WEN WANG Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the
BOUNDS ON THE MAP THRESHOLD OF ITERATIVE DECODING SYSTEMS WITH ERASURE NOISE A Thesis by CHIA-WEN WANG Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the
