Cryptanalysis of RAKAPOSHI Stream Cipher
|
|
|
- Geraldine Cole
- 5 years ago
- Views:
Transcription
1 Crypanalysis of RAKAPOSHI Sream Cipher Lin Ding, Jie Guan Zhengzhou Informaion Science and Technology Insiue, China Absrac. RAKAPOSHI is a hardware oriened sream cipher designed by Carlos Cid e al. in 9. The sream cipher is based on Dynamic Linear Feedback Shif Regisers, wih a simple and poenially scalable design, and is paricularly suiable for hardware applicaions wih resriced resources. The RAKAPOSHI sream cipher offers 8-bi securiy. In his paper, we poin ou some weaknesses in he cipher. Firsly, i shows ha here are weak (key, IV) pairs in RAKAPOSHI sream cipher. Secondly, for weak (key, IV) pairs of RAKAPOSHI, hey are vulnerable o linear disinguishing aack and algebraic aack. Finally, we propose a real ime relaed key chosen IV aack on RAKAPOSHI. The aack on RAKAPOSHI recovers he bi secre key of wih a compuaional complexiy of, requiring 47 relaed keys, chosen IVs and keysream bis. The success probabiliy of his aack is.999, which is quie close o. The experimenal resuls corroborae our asserion. Keywords: Crypanalysis; linear disinguishing aack; algebraic aack; relaed key chosen IV aack; RAKAPOSHI; sream cipher. Inroducion Sream ciphers are symmeric encrypion algorihms based on he concep of pseudorandom keysream generaor. Alhough i seems raher difficul o consruc a very fas and secure sream cipher, some effors o achieve his have recenly been deployed. The NESSIE proec [] launched in 999 by he European Union did no succeed in selecing a secure enough sream cipher. In 5, he European proec ECRYPT decided o launch a compeiion o idenify new sream ciphers ha migh be suiable for widespread adopion. This proec is called estream [] and received 35 submissions. Those candidaes are divided ino sofware oriened and hardware oriened sream ciphers. Hardware oriened sream ciphers should be suiable for deploymen on passive RFID ags or low-cos devices such as migh be used in sensor neworks. Such devices are excepionally consrained in compuing poenial because of he number of logic gaes available or he amoun of power ha migh realisically be available. In 9, Carlos Cid e al. [3] proposed a new hardware-oriened sream cipher called RAKAPOSHI, which aims o complemen he curren estream porfolio of hardware-oriened sream ciphers. The RAKAPOSHI sream cipher offers 8-bi securiy. The designers claimed ha he cipher design and The paper had been submied and is under review now. The paper was done independenly of wo similar works, i.e., [8] and [9].
2 securiy evaluaion incorporaes lessons learned during he several years of exensive analysis in he estream process, and hus RAKAPOSHI is less likely o be suscepible o more recen aacks, such as iniializaion aacks. RAKAPOSHI is based on Dynamic Linear Feedback Shif Regisers (DLFSR), wih a simple and poenially scalable design, and is paricularly suiable for hardware applicaions wih resriced resources. A Dynamic Linear Feedback Shif Regiser scheme is a general consrucion consising usually of wo regisers: he firs subregiser A, is clocked regularly and updaed using a fixed mapping. Subregiser B, is updaed using a linear mapping, which varies wih ime and depends of he sae in regiser A. The design can be seem as a generalizaion of consrucions found in early designs, including he sop-and-go generaor [4], LILI [5], dynamic feedback polynomial swich [6], and K [7]. In fac, he RAKAPOSHI sream cipher is in fac a successor of he K sream cipher, bu aiming a low-cos hardware implemenaions. In his paper, we poin ou some weaknesses in he cipher. Firsly, he resul shows ha here are weak (key, IV) pairs in RAKAPOSHI sream cipher. Secondly, for weak (key, IV) pairs of RAKAPOSHI, hey are vulnerable o linear disinguishing aack and algebraic aack. Finally, we proposed a real ime relaed key chosen IV aack on RAKAPOSHI. The ime complexiy of our relaed key chosen IV aack on RAKAPOSHI is abou 34, requiring 39 relaed keys on average. The resuls show ha here exis some weaknesses in he cipher. See also [8] and [9] for wo works ha were done independenly of our resuls. This paper is organized as follows. In Secion, we briefly describe RAKAPOSHI sream cipher. We discuss he exisence of weak (key, IV) pairs, and presen linear disinguishing aack and algebraic aack agains he weak (key, IV) pairs of RAKAPOSHI in Secion 3. Secion 4 proposes a real ime relaed key chosen IV aack on RAKAPOSHI. The Secion 5 concludes his paper. 9 Brief Descripion of RAKAPOSHI The RAKAPOSHI sream cipher consiss of hree main building blocks, namely a 8-bi Non-Linear Feedback Shif Regiser (denoed as regiser A), a 9-bi Linear Feedback Shif Regiser (denoed as 8 regiser B), and a non-linear filer funcion over GF. I uses wo bis from he sae of he NLFSR o selec and dynamically modify he linear feedback funcion of he LFSR. The keysream is produced by combining he oupu of boh regisers wih he oupu of he non-linear filer funcion. An overview of he differen blocks used in he sream cipher can be found in Fig..
3 Figure. The srucure of RAKAPOSHI sream cipher We denoe by A ( a, a,, a ) he conens of he LFSR a ime. Similarly, he conen of he 7 NFSR is denoed by B ( b, b,, b ) a ime. a 4 c a 89 7 Non-Linear Feedback Shif Regiser A. The regiser A is a 8-bi NLSFR, defined using he following recurrence relaion. a g( a, a, a, a, a, a, a, a, a, a ) a a a a a a a a a a a a a a a a a a a a a a a a Linear Feedback Shif Regiser B. The regiser B is a 9-bi dynamic LFSR. Regiser A is used o selec and dynamically modify he feedback funcion of LFSR B using wo bis from he sae of regiser A, and as a resul, Regiser B, which can use four differen linear recursive funcions, presens an irregular updaing mechanism. Le and c be he 4 nd and 9 h bis of regiser A a ime, respecively (ha is, c and c ). Then LFSR B a ime is defined by he following recurrence relaion. b f( c, c, b, b, b, b, b, b, b, b, b, b, b, b, b, b ) b b b b b b b c c b c c b c c b c c b c b 55 c b 58 b Where c c represens he negaion of. i i c i Non-Linear Filer. The 8-o- non-linear filer funcion is he same funcion used as he non-affine componen of he AES S-Box. This funcion is a balanced Boolean funcion, wih polynomial represenaion (ANF) of degree 7. In he RAKAPOSHI sream cipher, he inpu bis for his funcion are exraced from boh regisers A and B, as s v( a, a, b, b, b, b, b, b ) The explici polynomial expression of he funcion v() is given in he Appendix A.
4 Iniializaion Process. The RAKAPOSHI sream cipher suppors key size of 8 bis and IV size of 9 bis. Before he generaion of he cipher keysream, he cipher is iniialized wih he secre key and a seleced IV. The iniializaion process of RAKAPOSHI is done as follows. Firsly, he secre key K ( k,, k7) and IV ( iv,, iv9) are loaded ino he NLFSR and DLFSR, respecively, as follows. ( a,, a7 ) ( k,, k7 ) ( b,, b9) ( iv,, iv9 ) Secondly, he cipher hen clocks imes wih he oupu of he filer funcion back ino he cipher sae. This process is divided ino wo sages: v() (i.e., s ) being fed In he firs sage of he iniializaion, he cipher runs for 3 cycles, wih he oupu of he non-linear filer funcion v() being fed back ino he regiser B. In he second sage of he iniializaion, he cipher runs for furher 8 cycles, wih he oupu of he non-linear filer funcion v() being fed back ino he regiser A. A he end of he iniializaion, he cipher inernal sae is S ( A, B ), and i is ready o produce he firs keysream bi z. Keysream Generaion. The cipher oupus one keysream bi a each cycle. Given he cipher sae S ( A, B ) a ime, he cipher operaes as follows: The keysream bi z is compued as z a c, c A are used o updae he regiser B. Regisers A and B are updaed o obain A b s and B and is oupu., respecively. 3 Weak (key, IV) Pairs of RAKAPOSHI 3. The Exisence of he Weak (key, IV) Pairs RAKAPOSHI uses a dynamic linear feedback shif regiser o ensure good crypographic properies. However, here is an lock-up sae for he regiser A Tha is, if he iniializaion process leaves A in he all ones sae, hen i will remain permanenly in ha sae, and regiser B will become a simple linear feedback shif regiser, which is he only acive block of he cipher. As well known, keysream sequences generaed by a single LFSR and a non-linear filer funcion are vulnerable o disinguishing aack and algebraic aack. Consequenly, if he key and IV pair resuls in his lock-up sae for he regiser A, we define he key and IV pair as a weak (key, IV) pair. Now we reveal he exisence of he weak (key, IV) pairs in RAKAPOSHI sream cipher. For a weak (key, IV) pair, he sae A is he all one sae (,,,). Then our following purpose is o obain an available S from known algorihm o compue he weak (key, IV) pairs. S in reverse. According o he srucure of RAKAPOSHI, we presen an Finding Weak (key, IV) pairs Algorihm for RAKAPOSHI
5 . Se A be he all one sae (,,,), and selec B. From = 447 o = 3 do (.a) Compue c and c a 4 a 89 (.b) Compue s v( a67, a 7, b3, b53, b77, b8, b 3, b 8). (.c) Compue 9 c c b c b c b b. randomly. b b b b b b b b c c b c c b c c b (.d) Compue a a a a a a a a a a a a a a a 55 a7a8 a8a55 a6a45a6 a6a a6 s 3. From = 39 o = do (3.a) Compu c and c. e a 4 a 89 (3.b) Compue s v( a67, a 7, b, b, b, b, b, b (3.c) Compue b b b 9 b 4 b37 b4 b49 b5 b93 c c 7 c c b c c b 34 c c b c b c b b s (3.d) Compue a a a a a a a a a a a a a a a a a a a a a a a a a Oupu he iniial sae S ( A, B ). According he algorihm above, i is easy o see ha for each value of B )., here exiss a unique weak 9 (key, IV) pair. Since B can be randomly seleced in his algorihm, here are cerainly weak (key, IV) pairs in RAKAPOSHI sream cipher. One example is illusraed in Table. Table. Weak (key, IV) pair of RAKAPOSHI Key IV A B x894ef5d4b47934d5b58e5b8fa x4f9fe37b7c5a87f59ede8975ef6d6634eada64eaf3 xffffffffffffffffffffffffffffffff x7a7bd7c eba7c56fb69adfc865f4aada 3. Linear Disinguishing Aack and Algebraic Aack on Weak (key, IV) Pairs In disinguishing aacks, one aemps o disinguish he keysream sequence from a purely random sequence. For weak (key, IV) pairs of RAKAPOSHI, we ried o consruc linear disinguishers, by considering linear approximaions of funcions used in he sream cipher. For each weak (key, IV) pair of RAKAPOSHI, he inernal saes of he regiser A are all ones afer he iniializaion process, he recurrence relaion of LFSR B will remain permanenly as follows. b b b b b b b b b b b Now, he number of erms in he recurrence funcion of LFSR B is. We can consruc a linear disinguisher using keysream bis as follows.
6 D z z z z 4 z 49 z 5 z 93 z 36 z 58 z 76 z 9 : 4 37 Simulaneiy, he 8-o- non-linear filer funcion v() can be simplified as follows since he firs wo inpu bis are se o ones. s v a a b ( 67, 7, 3 b53 b77 b8 b 3 b 8,,,,, ) v(,, b, b, b, b, b, b ) v() The bes affine approximaion of he nonlinear filer v() has bias.4 designers [3]. However, he bes affine approximaion of he nonlinear filer v() has bias. Using he Pilling-up Lemma [], he bias of he linear disinguisher is esimaed as as claimed in sec.5.3 by he So, if he keysream sequence is generaed by RAKAPOSHI wih a weak (key, IV) pair, he linear 6.6 disinguisher D holds wih he probabiliy bias. As a resul, o disinguish he RAKAPOSHI wih a weak (key, IV) pair, i requires / keysream bis. As claimed in sec.5.3 by he designers, RAKAPOSHI sream cipher is secure agains disinguishing aacks. However, for weak (key, IV) pairs of RAKAPOSHI, i is vulnerable o linear disinguishing aacks. A weak Key-IV can be disinguished means ha he regiser A iniial sae of he weak Key-IV is he all ones sae. Consequenly, he nex ask is o recover he regiser B iniial sae. Algebraic aacks agains sream ciphers were originally proposed in 3 by Courois and Meier []. The aack is a powerful crypanalyic echnique agains some LFSR-based sream ciphers. For he RAKAPOSHI sream cipher wih a weak (key, IV) pair, he keysream oupu 7 by means of a Boolean funcion over GF given by z a b s a b v( a, a, b, b, b, b, b, b ) b v This funcion has degree 5 and algebraic immuniy 3 (which is he same of he funcion v ( ) ). For each weak (key, IV) pair of RAKAPOSHI, he inernal saes of he regiser A are all ones afer he iniializaion process. Here we use he XL mehod [] o esimae he ime complexiy of solving he above algebraic equaion sysem, and obain ha is ime complexiy is abou i i 3 z is compued The algebraic aack requires approximaely.7 keysream bis. The ime complexiy of his aack is much smaller han he ime complexiy of a brue force aack. Therefore for weak (key, IV) pairs of RAKAPOSHI, i is weak agains algebraic aack. 4 Relaed Key Chosen IV Aack on RAKAPOSHI In his secion, we will propose a relaed key chosen IV aack on RAKAPOSHI sream cipher. The aack on RAKAPOSHI is done by assuming four condiions as shown in Table. The relaion of ( K, IV ) and
7 ( K, IV ) is as follows. K ( k,, k7 ) K ( k,, k7, k ). IV ( iv,, iv ) IV ( iv,, iv,) 9 9 Where {,}, is a binary consan. Table. Condiions used in he aack on RAKAPOSHI K ( k,, k7), IV ( iv,, iv9) K ( k,, k7, kd), IV ( iv,, iv9,) Condiion a 7 9 k 7 iv9 b a 7 b 9 g( A ) f S s k g( A ) k f S s g( A ) f S s g( A ) f S s g A 39 g( A ) 3 g A 3 s s 3 3 f S s f( S ) 3 3 f( S ) 3 g A f S 38 g( A ) 39 g( A ) s f S 38 f S s 38 s s ( s s ) g A 447 s f( S ) 447 g A s f( S ) 449 g A f( S ) g A 447 s f( S ) 447 s ( s s ) Le Z and Z be keysream sequences generaed from ( K, IV ) and ( K, IV ). According o able, we can ge Proper y as follows. Propery. The sysem S a) g( A ) k ; b) f S s. S holds when he following wo condiions are simulaneously saisfied. Recall he iniializaion of RAKAPOSHI sream cipher. I consiss of wo sages, which differ from each oher in he feedback of s. According o able and Propery, we can ge Propery as follows. Propery. If he sysem S S holds, he sysem S condiions are simulaneously saisfied. z i c) s3 ; d) s. I is easy o see ha if he sysem S z for i. i 449 i i S holds for i when he following wo S holds, here exiss a clear relaion beween Z and Z, i.e., Le Z[ m] ( z,, z m ) be he m-bi keysream sequence saring from he second keyseam bi generaed by ( K, IV ) and Z[ m] ( z,, z m ) be m-bi keysream sequence saring from he firs keyseam bi generaed
8 by relaed ( K, IV ) pair. We define h e even Z[ m] Z[ m] (i.e., zi z for i m ) by and is c comple men by. We denoe he even ha he condiions a) and b) are simulaneously saisfied by L and c is co mplemen by L. Since he condiions c) and d) are obained in differen clocks, and hen are assumed o be independen o faciliae calculaion of probabiliy. Hence, when he even L occurs, he even occurs wih probabiliy Pr( L) Pr( c d) Pr( c) Pr( d). c However, when he even L occurs, afer 447 clocks of ieraion, he differenials of inernal saes will be fairly even and unpredicable, he even occurs wih probabiliy m. Tha is, c Pr( L ) In order o recover he some key bis effecively, choose iv 7 iv iv 34 iv 36 iv 55 and iv 58. Thus, he equaion f( S ) s can be simplified as follows. m i we should fix some IV bis. Here, we f ( S ) s iv iv4 iv37 iv4 iv49 iv5 iv93 c iv iv iv iv iv iv iv iv k iv iv s s iv iv iv iv iv iv iv k iv iv s () Where v( a, a b 3 b 53 b 77 b 8 b 3 b 8 v k 67 k7, iv3, iv53, iv77 iv 8 s,,,,,, ) (,, 67 7, iv, iv ). When iv iv Recall he non-linear filer funcion v(). Three funcions can be obained as follows. iv77 iv8 iv8 and iv3, s v( k, k, iv, iv, iv, iv, iv, iv 8 ) () When iv3 iv53 iv77 iv3 iv8 and iv8, s v( k, k, iv, iv, iv, iv, iv, iv ) k (3) When iv77 iv8 iv3 iv8 and iv3 iv53, s vk ( 67, k7, iv3, iv53, iv77, iv8, iv3, iv ) 8 k7 (4) Now, we will inroduce a mehod o recover one key bi wih h chosen IVs, named Algorihm. Algorihm. Under fixed and unknown K and K, choose h IVs where iv7 iv iv34 iv36 iv 55, iv58, ( iv,, ivh )are all h -bi values and he remaining bis are fixed o e ( {,}).. Unil no more chosen IV remain, repea he followings. Generae he keysream sequences Z[ m] ( z,, z ) using ( K, IV ); Generae he keysream sequences Z[ m] ( z,, z m ) using ( K, IV ); m Check Z[ m] Z [ m]. If he wo keysream sequences pass he check, oupu g( A ) k. Oherwise ry oher chosen IVs. 3. If no chosen IVs passes he check, hen oupu g( A ) k. Wih a decision rule of Algorihm, wo ypes of errors denoed as ype I and ype II exis, see Figure.. Le and denoe he probabiliies of ype I and II errors, respecively. Thus,. Hence, m Pr ( ) h and Pr ( ) h we can obain he equaion g( A ) k wih a success probabiliy
9 of Pr if he equaion probabiliy of Pr( ) holds, and obain he equaion g( A ) k wih a success g( A ) k if he equaion g( A ) k does no hold. Thus, he success probabiliy of his algorihm is bounded below bypr Pr. In our paper, we use p Pr Pr as he success probabiliy of our a ack. The acual value of success probabiliy is in fac more, making our aack ma rginally sronger. L: g( A ) k L g A k c : Figure. Two ypes of errors in he decision rule of Algorihm The number of chosen IVs used In Algorihm i s h. For each chosen IV, he algorihm needs o execue he h h encrypion process of RAKAPOSHI wo imes. Thus, he compuaional complexiy of Algorihm is. h h I requires ( m m) (m) keysream bis. In our relaed key aacks on RAKAPOSHI, we use m relaed keys, which are shows as follows. For m, K ( k,, k ) K ( k,, k, k ), K ( k,, k, k ) IV ( iv,, iv ) IV ( iv,, iv,) 9 9 Noe ha K K. Now, we will inroduce a mehod o recover more key bis using hese relaed keys, named Algorihm. For m, do he followings. Algorihm. Under he relaed keys K and K, run Algorihm. If Algorihm oupus g( A ) k, goo sep. Oherwise, goo sep 3.. Under he relaed keys K and K, do he followings. Se iv3 iv53 iv77 iv8 iv 8 and iv 3, and hen run Algorihm. Recover he key bi k4 of K using he equaion () and (). Se iv3 iv53 iv iv iv 8 and iv 8, and hen run Algorihm. Recover he key bi k67 of K 77 3 using he equaion () and (3). Se iv77 iv8 iv3 iv8 and iv 3 iv 53, and hen run Algorihm. Recover he key bi k 7 of using he equaion () and (4). 3. Under he relaed keys K and K, do he followings. Se iv3 iv53 iv77 iv8 iv8 and iv 3, and hen run Algorihm. Recover he key bi k4 of K usin g he equaion () and (). Se iv3 iv53 iv77 iv3 iv8 and iv 8, and hen run Algorihm. Recover he key bi k67 of K K
10 using he equaion () and (3). Se iv77 iv8 iv3 iv8 and iv 3 iv 53, and hen run Algorihm. Recover he key bi k 7 of using he equaion () and (4). Using he Algorihm, we can recover he following key bis. k,, k m k,, k m k,, k m 4mod8 4 mod8 67 mod8 67 mod8 7 mod8 7 mod8 Furhermore, we also can obain m non-linear funcions wih some key bis. In Algorihm, for m, we should run Algorihm four imes under relaed keys. Hence, Algorihm requires h 4 h In order h h3 chosen IVs and (m) 4 (m ) keysre am bis. The compuaional complexiy of h h3 Algorihm is 4. The success probabiliy of Algorihm is bounded below by p success probabiliy of Algorihm is bounded below by p. K, since he o ge a high success probabiliy for recovering he 8-bi secre key, m and h should be properly seleced. When we se m 3, hen he aacker can recover 69 key bis ( k,, k, k 4,, k 63, k 67,, k 89, k 7 ). We also can obain 3 non-linear funcions wih key bis ( k,, k4, k64, k65, k66 ). In fac, we can simplify hese non-linear funcions using he recovered 69 key bi s. Thus, he key bi (,, ) can be recovered easily, wih a compuaional complexiy of a mos. Finally, he remaining 37 key 3m s k, k4, k64, k 65 k66 ( k,, k ) should be exhausive searched. Thus, considering Algorihm, h e compuaional complexiy bis u h of our relaed key chosen IV aack on RAKAPOSHI is abo, requiring h chosen IVs and h3 (m ) keysream bis. Table 3 shows he complexiies of our aack on RAKAPOSHI for parameers h. Noe ha in our relaed key aacks on RAKAPOSHI, we use m 47 relaed keys in Algorihm. Table 3. Our resuls on RAKAPOSHI for parameers h h Compuaional Keysream bis Chosen IVs complexiy required Success probabiliy Here, we cho ose h 6. Thus, we can recover he 8-bi secre key of RAKAPOSHI wih a compuaional complexiy of 37, requiring 47 relaed keys, chosen IVs and keysream bis. The success probabiliy of our aack on RAKAPOSHI is.999, which is quie close o. We also validae our resul by simulaing Algorihm and solving he 3 non-linear funcions. The resul shows ha we can recover he 9 (=69+) key bis wihin.8 minues on average. By simulaing RAKAPOSHI sream cipher, he remaining 37 can be recove red wihin 3.4 hours on average. The simulaion was implemened on AMD Ahlon(m) 64 X Dual Core Processor 44+, CPU.3GHz, 768 Gb RAM, OS Windows XP Pro SP3. These experimenal resuls corroborae our asserion. 5 Conclusions
11 RAKAPOSHI is a hardware-oriened sream cipher designed by Carlos Cid e al. in 9. The RAKAPOSHI sream cipher offers 8-bi securiy. Unil now, no aack on he cipher has been published. In his paper, we poin ou some weaknesses in he cipher. Firsly, he resul shows ha here are weak (key, IV) pairs in RAKAPOSHI sream cipher. Secondly, for weak (key, IV) pairs of RAKAPOSHI, hey are vulnerable o linear disinguishing aack and algebraic aack. Finally, we proposed a real ime relaed key chosen IV aack on RAKAPOSHI. The ime complexiy of our relaed key chosen IV aack on RAKAPOSHI is 34 abou, requiring 39 relaed keys on average. The resuls show ha here exis some weaknesses in he cipher. We hope our resuls can be helpful in evaluaing he securiy of RAKAPOSHI sream ciphers agains relaed key aacks, and we look forward o furher work in evaluaing RAKAPOSHI sream ciphers agains oher kinds of crypanalyic aacks. Acknowledgemens 9 This work is suppored in par by he Naional Naural Science Foundaion of China (No. 649, 674, 67488). References [] NESSIE. New European Schemes for Signaures, Inegriy, and Encrypion. Available a hp:// Accessed Augus 8, 3 [] ECRYPT. estream: ECRYPT Sream Cipher Proec, IST Available a hp:// Accessed Sepember 9, 5 [3] Carlos Cid, Shinsaku Kiyomoo, and Jun Kurihara. The RAKAPOSHI Sream Cipher. Informaion and Communicaions Securiy, LNCS 597[C] [4] T. Beh and F.C. Piper. The sop-and-go-generaor. In Proceedings of EUROCRYPT 984, number 9 in LNCS, pages Springer-Verlag, 985. [5] L.R. Simpson, E. Dawson, J. Golic, and W. Millan. LILI Keysream Generaor. In Seleced Areas in Crypography, number in LNCS, pages Springer-Verlag,. [6] D. Horan and R. Guinee. A Novel Keysream Generaor using Pseudo Random Binary Sequences for Crypographic Applicaions. In Irish Signals and Sysems Conference 6, pages IEEE, 6. [7] S. Kiyomoo, T. Tanaka, and K. Sakurai. K: A Sream Cipher Algorihm Using Dynamic Feedback Conrol. In Proceedings of SECRYPT 7, pages 4 3, 8. [8] T. Isobe, T. Ohigashi, and M. Morii, Slide crypanalysis of lighweigh sream cipher rakaposhi, in Advances in Informaion and Compuer Securiy, G. Hanaoka and T. Yamauchi, eds., vol. 763 of Lecure Noes in Compuer Science, Springer Berlin Heidelberg,, pp
12 [9] Mohammad Ali Orumiehchiha, Josef Pieprzyk, Elham Shakour and Ron Seinfeld. Securiy Evaluaion of Rakaposhi Sream Cipher. Crypology eprin Archive Repor /656, hp://eprin.iacr.org/. [] M. Masui. Linear Crypanalysis Mehod for DES Cipher. In Proceedings of EUROCRYPT 993, number 765 in LNCS, pages Springer-Verlag, 993. [] N. Courois and W. Meier. Algebraic Aacks on Sream Ciphers wih Linear Feedback. In E. Biham, edior, Advances in Crypology EUROCRYPT 3, volume 656 of LNCS, pages Springer Verlag, 3. [] C. Diem, The XL-Algorihm and a Conecure from Commuaive Algebra, In Pil Joong Lee, edior, Advances in Crypology-ASIACRYPT4, LNCS 339, pp , 4.
THE NEW HEURISTIC GUESS AND DETERMINE ATTACK ON SNOW 2.0 STREAM CIPHER
 THE NEW HEURISTIC GUESS AND DETERMINE ATTACK ON SNOW 0 STREAM CIPHER Mohammad Sadegh Nemai Nia 1, Ali Payandeh 1, Faculy of Informaion, Telecommunicaion and Securiy Technologies, Malek-e- Ashar Universiy
THE NEW HEURISTIC GUESS AND DETERMINE ATTACK ON SNOW 0 STREAM CIPHER Mohammad Sadegh Nemai Nia 1, Ali Payandeh 1, Faculy of Informaion, Telecommunicaion and Securiy Technologies, Malek-e- Ashar Universiy
Li An-Ping. Beijing , P.R.China
 A NEW TYPE OF CIPHER: DICING_CSB Li An-Ping Beijing 100085, P.R.China apli0001@sina.com Absrac: In his paper, we will propose a new ype of cipher named DICING_CSB, which come from our previous a synchronous
A NEW TYPE OF CIPHER: DICING_CSB Li An-Ping Beijing 100085, P.R.China apli0001@sina.com Absrac: In his paper, we will propose a new ype of cipher named DICING_CSB, which come from our previous a synchronous
Algebraic Attacks on Summation Generators
 Algebraic Aacks on Summaion Generaors Dong Hoon Lee, Jaeheon Kim, Jin Hong, Jae Woo Han, and Dukjae Moon Naional Securiy Research Insiue 161 Gajeong-dong, Yuseong-gu, Daejeon, 305-350, Korea {dlee,jaeheon,jinhong,jwhan,djmoon}@eri.re.kr
Algebraic Aacks on Summaion Generaors Dong Hoon Lee, Jaeheon Kim, Jin Hong, Jae Woo Han, and Dukjae Moon Naional Securiy Research Insiue 161 Gajeong-dong, Yuseong-gu, Daejeon, 305-350, Korea {dlee,jaeheon,jinhong,jwhan,djmoon}@eri.re.kr
Vehicle Arrival Models : Headway
 Chaper 12 Vehicle Arrival Models : Headway 12.1 Inroducion Modelling arrival of vehicle a secion of road is an imporan sep in raffic flow modelling. I has imporan applicaion in raffic flow simulaion where
Chaper 12 Vehicle Arrival Models : Headway 12.1 Inroducion Modelling arrival of vehicle a secion of road is an imporan sep in raffic flow modelling. I has imporan applicaion in raffic flow simulaion where
An introduction to the theory of SDDP algorithm
 An inroducion o he heory of SDDP algorihm V. Leclère (ENPC) Augus 1, 2014 V. Leclère Inroducion o SDDP Augus 1, 2014 1 / 21 Inroducion Large scale sochasic problem are hard o solve. Two ways of aacking
An inroducion o he heory of SDDP algorihm V. Leclère (ENPC) Augus 1, 2014 V. Leclère Inroducion o SDDP Augus 1, 2014 1 / 21 Inroducion Large scale sochasic problem are hard o solve. Two ways of aacking
STATE-SPACE MODELLING. A mass balance across the tank gives:
 B. Lennox and N.F. Thornhill, 9, Sae Space Modelling, IChemE Process Managemen and Conrol Subjec Group Newsleer STE-SPACE MODELLING Inroducion: Over he pas decade or so here has been an ever increasing
B. Lennox and N.F. Thornhill, 9, Sae Space Modelling, IChemE Process Managemen and Conrol Subjec Group Newsleer STE-SPACE MODELLING Inroducion: Over he pas decade or so here has been an ever increasing
Final Spring 2007
 .615 Final Spring 7 Overview The purpose of he final exam is o calculae he MHD β limi in a high-bea oroidal okamak agains he dangerous n = 1 exernal ballooning-kink mode. Effecively, his corresponds o
.615 Final Spring 7 Overview The purpose of he final exam is o calculae he MHD β limi in a high-bea oroidal okamak agains he dangerous n = 1 exernal ballooning-kink mode. Effecively, his corresponds o
Chapter 2. First Order Scalar Equations
 Chaper. Firs Order Scalar Equaions We sar our sudy of differenial equaions in he same way he pioneers in his field did. We show paricular echniques o solve paricular ypes of firs order differenial equaions.
Chaper. Firs Order Scalar Equaions We sar our sudy of differenial equaions in he same way he pioneers in his field did. We show paricular echniques o solve paricular ypes of firs order differenial equaions.
Random Walk with Anti-Correlated Steps
 Random Walk wih Ani-Correlaed Seps John Noga Dirk Wagner 2 Absrac We conjecure he expeced value of random walks wih ani-correlaed seps o be exacly. We suppor his conjecure wih 2 plausibiliy argumens and
Random Walk wih Ani-Correlaed Seps John Noga Dirk Wagner 2 Absrac We conjecure he expeced value of random walks wih ani-correlaed seps o be exacly. We suppor his conjecure wih 2 plausibiliy argumens and
Lecture 20: Riccati Equations and Least Squares Feedback Control
 34-5 LINEAR SYSTEMS Lecure : Riccai Equaions and Leas Squares Feedback Conrol 5.6.4 Sae Feedback via Riccai Equaions A recursive approach in generaing he marix-valued funcion W ( ) equaion for i for he
34-5 LINEAR SYSTEMS Lecure : Riccai Equaions and Leas Squares Feedback Conrol 5.6.4 Sae Feedback via Riccai Equaions A recursive approach in generaing he marix-valued funcion W ( ) equaion for i for he
Simulation-Solving Dynamic Models ABE 5646 Week 2, Spring 2010
 Simulaion-Solving Dynamic Models ABE 5646 Week 2, Spring 2010 Week Descripion Reading Maerial 2 Compuer Simulaion of Dynamic Models Finie Difference, coninuous saes, discree ime Simple Mehods Euler Trapezoid
Simulaion-Solving Dynamic Models ABE 5646 Week 2, Spring 2010 Week Descripion Reading Maerial 2 Compuer Simulaion of Dynamic Models Finie Difference, coninuous saes, discree ime Simple Mehods Euler Trapezoid
Christos Papadimitriou & Luca Trevisan November 22, 2016
 U.C. Bereley CS170: Algorihms Handou LN-11-22 Chrisos Papadimiriou & Luca Trevisan November 22, 2016 Sreaming algorihms In his lecure and he nex one we sudy memory-efficien algorihms ha process a sream
U.C. Bereley CS170: Algorihms Handou LN-11-22 Chrisos Papadimiriou & Luca Trevisan November 22, 2016 Sreaming algorihms In his lecure and he nex one we sudy memory-efficien algorihms ha process a sream
Spring Ammar Abu-Hudrouss Islamic University Gaza
 Chaper 7 Reed-Solomon Code Spring 9 Ammar Abu-Hudrouss Islamic Universiy Gaza ١ Inroducion A Reed Solomon code is a special case of a BCH code in which he lengh of he code is one less han he size of he
Chaper 7 Reed-Solomon Code Spring 9 Ammar Abu-Hudrouss Islamic Universiy Gaza ١ Inroducion A Reed Solomon code is a special case of a BCH code in which he lengh of he code is one less han he size of he
More Digital Logic. t p output. Low-to-high and high-to-low transitions could have different t p. V in (t)
 EECS 4 Spring 23 Lecure 2 EECS 4 Spring 23 Lecure 2 More igial Logic Gae delay and signal propagaion Clocked circui elemens (flip-flop) Wriing a word o memory Simplifying digial circuis: Karnaugh maps
EECS 4 Spring 23 Lecure 2 EECS 4 Spring 23 Lecure 2 More igial Logic Gae delay and signal propagaion Clocked circui elemens (flip-flop) Wriing a word o memory Simplifying digial circuis: Karnaugh maps
Learning Objectives: Practice designing and simulating digital circuits including flip flops Experience state machine design procedure
 Lab 4: Synchronous Sae Machine Design Summary: Design and implemen synchronous sae machine circuis and es hem wih simulaions in Cadence Viruoso. Learning Objecives: Pracice designing and simulaing digial
Lab 4: Synchronous Sae Machine Design Summary: Design and implemen synchronous sae machine circuis and es hem wih simulaions in Cadence Viruoso. Learning Objecives: Pracice designing and simulaing digial
Modal identification of structures from roving input data by means of maximum likelihood estimation of the state space model
 Modal idenificaion of srucures from roving inpu daa by means of maximum likelihood esimaion of he sae space model J. Cara, J. Juan, E. Alarcón Absrac The usual way o perform a forced vibraion es is o fix
Modal idenificaion of srucures from roving inpu daa by means of maximum likelihood esimaion of he sae space model J. Cara, J. Juan, E. Alarcón Absrac The usual way o perform a forced vibraion es is o fix
Cryptanalysis of Reduced NORX initially discussed at ASK 2016
 Crypanalysis of Reduced NORX iniiy discussed a ASK 2016 Nasour Bagheri (SRTTU, Iran), Tao Huang (NTU, Singaopre), Keing Jia (Tsinghua Univ., Sae Key Lab, China), Florian Mendel (TUGraz, Ausria), Yu Sasaki
Crypanalysis of Reduced NORX iniiy discussed a ASK 2016 Nasour Bagheri (SRTTU, Iran), Tao Huang (NTU, Singaopre), Keing Jia (Tsinghua Univ., Sae Key Lab, China), Florian Mendel (TUGraz, Ausria), Yu Sasaki
Physical Limitations of Logic Gates Week 10a
 Physical Limiaions of Logic Gaes Week 10a In a compuer we ll have circuis of logic gaes o perform specific funcions Compuer Daapah: Boolean algebraic funcions using binary variables Symbolic represenaion
Physical Limiaions of Logic Gaes Week 10a In a compuer we ll have circuis of logic gaes o perform specific funcions Compuer Daapah: Boolean algebraic funcions using binary variables Symbolic represenaion
Georey E. Hinton. University oftoronto. Technical Report CRG-TR February 22, Abstract
 Parameer Esimaion for Linear Dynamical Sysems Zoubin Ghahramani Georey E. Hinon Deparmen of Compuer Science Universiy oftorono 6 King's College Road Torono, Canada M5S A4 Email: zoubin@cs.orono.edu Technical
Parameer Esimaion for Linear Dynamical Sysems Zoubin Ghahramani Georey E. Hinon Deparmen of Compuer Science Universiy oftorono 6 King's College Road Torono, Canada M5S A4 Email: zoubin@cs.orono.edu Technical
An recursive analytical technique to estimate time dependent physical parameters in the presence of noise processes
 WHAT IS A KALMAN FILTER An recursive analyical echnique o esimae ime dependen physical parameers in he presence of noise processes Example of a ime and frequency applicaion: Offse beween wo clocks PREDICTORS,
WHAT IS A KALMAN FILTER An recursive analyical echnique o esimae ime dependen physical parameers in he presence of noise processes Example of a ime and frequency applicaion: Offse beween wo clocks PREDICTORS,
Stability and Bifurcation in a Neural Network Model with Two Delays
 Inernaional Mahemaical Forum, Vol. 6, 11, no. 35, 175-1731 Sabiliy and Bifurcaion in a Neural Nework Model wih Two Delays GuangPing Hu and XiaoLing Li School of Mahemaics and Physics, Nanjing Universiy
Inernaional Mahemaical Forum, Vol. 6, 11, no. 35, 175-1731 Sabiliy and Bifurcaion in a Neural Nework Model wih Two Delays GuangPing Hu and XiaoLing Li School of Mahemaics and Physics, Nanjing Universiy
LAPLACE TRANSFORM AND TRANSFER FUNCTION
 CHBE320 LECTURE V LAPLACE TRANSFORM AND TRANSFER FUNCTION Professor Dae Ryook Yang Spring 2018 Dep. of Chemical and Biological Engineering 5-1 Road Map of he Lecure V Laplace Transform and Transfer funcions
CHBE320 LECTURE V LAPLACE TRANSFORM AND TRANSFER FUNCTION Professor Dae Ryook Yang Spring 2018 Dep. of Chemical and Biological Engineering 5-1 Road Map of he Lecure V Laplace Transform and Transfer funcions
Linear Cryptanalysis
 Linear Crypanalysis T-79.550 Crypology Lecure 5 February 6, 008 Kaisa Nyberg Linear Crypanalysis /36 SPN A Small Example Linear Crypanalysis /36 Linear Approximaion of S-boxes Linear Crypanalysis 3/36
Linear Crypanalysis T-79.550 Crypology Lecure 5 February 6, 008 Kaisa Nyberg Linear Crypanalysis /36 SPN A Small Example Linear Crypanalysis /36 Linear Approximaion of S-boxes Linear Crypanalysis 3/36
Section 3.5 Nonhomogeneous Equations; Method of Undetermined Coefficients
 Secion 3.5 Nonhomogeneous Equaions; Mehod of Undeermined Coefficiens Key Terms/Ideas: Linear Differenial operaor Nonlinear operaor Second order homogeneous DE Second order nonhomogeneous DE Soluion o homogeneous
Secion 3.5 Nonhomogeneous Equaions; Mehod of Undeermined Coefficiens Key Terms/Ideas: Linear Differenial operaor Nonlinear operaor Second order homogeneous DE Second order nonhomogeneous DE Soluion o homogeneous
Ensamble methods: Boosting
 Lecure 21 Ensamble mehods: Boosing Milos Hauskrech milos@cs.pi.edu 5329 Senno Square Schedule Final exam: April 18: 1:00-2:15pm, in-class Term projecs April 23 & April 25: a 1:00-2:30pm in CS seminar room
Lecure 21 Ensamble mehods: Boosing Milos Hauskrech milos@cs.pi.edu 5329 Senno Square Schedule Final exam: April 18: 1:00-2:15pm, in-class Term projecs April 23 & April 25: a 1:00-2:30pm in CS seminar room
Notes on Kalman Filtering
 Noes on Kalman Filering Brian Borchers and Rick Aser November 7, Inroducion Daa Assimilaion is he problem of merging model predicions wih acual measuremens of a sysem o produce an opimal esimae of he curren
Noes on Kalman Filering Brian Borchers and Rick Aser November 7, Inroducion Daa Assimilaion is he problem of merging model predicions wih acual measuremens of a sysem o produce an opimal esimae of he curren
ADDITIONAL PROBLEMS (a) Find the Fourier transform of the half-cosine pulse shown in Fig. 2.40(a). Additional Problems 91
 ddiional Problems 9 n inverse relaionship exiss beween he ime-domain and freuency-domain descripions of a signal. Whenever an operaion is performed on he waveform of a signal in he ime domain, a corresponding
ddiional Problems 9 n inverse relaionship exiss beween he ime-domain and freuency-domain descripions of a signal. Whenever an operaion is performed on he waveform of a signal in he ime domain, a corresponding
Finding Near-Optimum Message Scheduling Settings for SHA-256 Variants Using Genetic Algorithms
 Finding Near-Opimum essage Scheduling Seings for SHA-256 Varians Using Geneic Algorihms CHU-HSING LIN, CHEN-YU LEE 2, KRISHNA. KAVI 3, DENG-JYI CHEN 2, YI-SHIUNG YEH 2 Deparmen of Compuer Science Tunghai
Finding Near-Opimum essage Scheduling Seings for SHA-256 Varians Using Geneic Algorihms CHU-HSING LIN, CHEN-YU LEE 2, KRISHNA. KAVI 3, DENG-JYI CHEN 2, YI-SHIUNG YEH 2 Deparmen of Compuer Science Tunghai
EXPLICIT TIME INTEGRATORS FOR NONLINEAR DYNAMICS DERIVED FROM THE MIDPOINT RULE
 Version April 30, 2004.Submied o CTU Repors. EXPLICIT TIME INTEGRATORS FOR NONLINEAR DYNAMICS DERIVED FROM THE MIDPOINT RULE Per Krysl Universiy of California, San Diego La Jolla, California 92093-0085,
Version April 30, 2004.Submied o CTU Repors. EXPLICIT TIME INTEGRATORS FOR NONLINEAR DYNAMICS DERIVED FROM THE MIDPOINT RULE Per Krysl Universiy of California, San Diego La Jolla, California 92093-0085,
Ensamble methods: Bagging and Boosting
 Lecure 21 Ensamble mehods: Bagging and Boosing Milos Hauskrech milos@cs.pi.edu 5329 Senno Square Ensemble mehods Mixure of expers Muliple base models (classifiers, regressors), each covers a differen par
Lecure 21 Ensamble mehods: Bagging and Boosing Milos Hauskrech milos@cs.pi.edu 5329 Senno Square Ensemble mehods Mixure of expers Muliple base models (classifiers, regressors), each covers a differen par
Physics 235 Chapter 2. Chapter 2 Newtonian Mechanics Single Particle
 Chaper 2 Newonian Mechanics Single Paricle In his Chaper we will review wha Newon s laws of mechanics ell us abou he moion of a single paricle. Newon s laws are only valid in suiable reference frames,
Chaper 2 Newonian Mechanics Single Paricle In his Chaper we will review wha Newon s laws of mechanics ell us abou he moion of a single paricle. Newon s laws are only valid in suiable reference frames,
Recursive Least-Squares Fixed-Interval Smoother Using Covariance Information based on Innovation Approach in Linear Continuous Stochastic Systems
 8 Froniers in Signal Processing, Vol. 1, No. 1, July 217 hps://dx.doi.org/1.2266/fsp.217.112 Recursive Leas-Squares Fixed-Inerval Smooher Using Covariance Informaion based on Innovaion Approach in Linear
8 Froniers in Signal Processing, Vol. 1, No. 1, July 217 hps://dx.doi.org/1.2266/fsp.217.112 Recursive Leas-Squares Fixed-Inerval Smooher Using Covariance Informaion based on Innovaion Approach in Linear
RC, RL and RLC circuits
 Name Dae Time o Complee h m Parner Course/ Secion / Grade RC, RL and RLC circuis Inroducion In his experimen we will invesigae he behavior of circuis conaining combinaions of resisors, capaciors, and inducors.
Name Dae Time o Complee h m Parner Course/ Secion / Grade RC, RL and RLC circuis Inroducion In his experimen we will invesigae he behavior of circuis conaining combinaions of resisors, capaciors, and inducors.
Single-Pass-Based Heuristic Algorithms for Group Flexible Flow-shop Scheduling Problems
 Single-Pass-Based Heurisic Algorihms for Group Flexible Flow-shop Scheduling Problems PEI-YING HUANG, TZUNG-PEI HONG 2 and CHENG-YAN KAO, 3 Deparmen of Compuer Science and Informaion Engineering Naional
Single-Pass-Based Heurisic Algorihms for Group Flexible Flow-shop Scheduling Problems PEI-YING HUANG, TZUNG-PEI HONG 2 and CHENG-YAN KAO, 3 Deparmen of Compuer Science and Informaion Engineering Naional
Particle Swarm Optimization
 Paricle Swarm Opimizaion Speaker: Jeng-Shyang Pan Deparmen of Elecronic Engineering, Kaohsiung Universiy of Applied Science, Taiwan Email: jspan@cc.kuas.edu.w 7/26/2004 ppso 1 Wha is he Paricle Swarm Opimizaion
Paricle Swarm Opimizaion Speaker: Jeng-Shyang Pan Deparmen of Elecronic Engineering, Kaohsiung Universiy of Applied Science, Taiwan Email: jspan@cc.kuas.edu.w 7/26/2004 ppso 1 Wha is he Paricle Swarm Opimizaion
Kinematics and kinematic functions
 Kinemaics and kinemaic funcions Kinemaics deals wih he sudy of four funcions (called kinemaic funcions or KFs) ha mahemaically ransform join variables ino caresian variables and vice versa Direc Posiion
Kinemaics and kinemaic funcions Kinemaics deals wih he sudy of four funcions (called kinemaic funcions or KFs) ha mahemaically ransform join variables ino caresian variables and vice versa Direc Posiion
Chapter 7: Solving Trig Equations
 Haberman MTH Secion I: The Trigonomeric Funcions Chaper 7: Solving Trig Equaions Le s sar by solving a couple of equaions ha involve he sine funcion EXAMPLE a: Solve he equaion sin( ) The inverse funcions
Haberman MTH Secion I: The Trigonomeric Funcions Chaper 7: Solving Trig Equaions Le s sar by solving a couple of equaions ha involve he sine funcion EXAMPLE a: Solve he equaion sin( ) The inverse funcions
Some Basic Information about M-S-D Systems
 Some Basic Informaion abou M-S-D Sysems 1 Inroducion We wan o give some summary of he facs concerning unforced (homogeneous) and forced (non-homogeneous) models for linear oscillaors governed by second-order,
Some Basic Informaion abou M-S-D Sysems 1 Inroducion We wan o give some summary of he facs concerning unforced (homogeneous) and forced (non-homogeneous) models for linear oscillaors governed by second-order,
Inventory Analysis and Management. Multi-Period Stochastic Models: Optimality of (s, S) Policy for K-Convex Objective Functions
 Muli-Period Sochasic Models: Opimali of (s, S) Polic for -Convex Objecive Funcions Consider a seing similar o he N-sage newsvendor problem excep ha now here is a fixed re-ordering cos (> 0) for each (re-)order.
Muli-Period Sochasic Models: Opimali of (s, S) Polic for -Convex Objecive Funcions Consider a seing similar o he N-sage newsvendor problem excep ha now here is a fixed re-ordering cos (> 0) for each (re-)order.
Online Convex Optimization Example And Follow-The-Leader
 CSE599s, Spring 2014, Online Learning Lecure 2-04/03/2014 Online Convex Opimizaion Example And Follow-The-Leader Lecurer: Brendan McMahan Scribe: Sephen Joe Jonany 1 Review of Online Convex Opimizaion
CSE599s, Spring 2014, Online Learning Lecure 2-04/03/2014 Online Convex Opimizaion Example And Follow-The-Leader Lecurer: Brendan McMahan Scribe: Sephen Joe Jonany 1 Review of Online Convex Opimizaion
Application of a Stochastic-Fuzzy Approach to Modeling Optimal Discrete Time Dynamical Systems by Using Large Scale Data Processing
 Applicaion of a Sochasic-Fuzzy Approach o Modeling Opimal Discree Time Dynamical Sysems by Using Large Scale Daa Processing AA WALASZE-BABISZEWSA Deparmen of Compuer Engineering Opole Universiy of Technology
Applicaion of a Sochasic-Fuzzy Approach o Modeling Opimal Discree Time Dynamical Sysems by Using Large Scale Daa Processing AA WALASZE-BABISZEWSA Deparmen of Compuer Engineering Opole Universiy of Technology
A DELAY-DEPENDENT STABILITY CRITERIA FOR T-S FUZZY SYSTEM WITH TIME-DELAYS
 A DELAY-DEPENDENT STABILITY CRITERIA FOR T-S FUZZY SYSTEM WITH TIME-DELAYS Xinping Guan ;1 Fenglei Li Cailian Chen Insiue of Elecrical Engineering, Yanshan Universiy, Qinhuangdao, 066004, China. Deparmen
A DELAY-DEPENDENT STABILITY CRITERIA FOR T-S FUZZY SYSTEM WITH TIME-DELAYS Xinping Guan ;1 Fenglei Li Cailian Chen Insiue of Elecrical Engineering, Yanshan Universiy, Qinhuangdao, 066004, China. Deparmen
CHAPTER 10 VALIDATION OF TEST WITH ARTIFICAL NEURAL NETWORK
 175 CHAPTER 10 VALIDATION OF TEST WITH ARTIFICAL NEURAL NETWORK 10.1 INTRODUCTION Amongs he research work performed, he bes resuls of experimenal work are validaed wih Arificial Neural Nework. From he
175 CHAPTER 10 VALIDATION OF TEST WITH ARTIFICAL NEURAL NETWORK 10.1 INTRODUCTION Amongs he research work performed, he bes resuls of experimenal work are validaed wih Arificial Neural Nework. From he
Overview. COMP14112: Artificial Intelligence Fundamentals. Lecture 0 Very Brief Overview. Structure of this course
 OMP: Arificial Inelligence Fundamenals Lecure 0 Very Brief Overview Lecurer: Email: Xiao-Jun Zeng x.zeng@mancheser.ac.uk Overview This course will focus mainly on probabilisic mehods in AI We shall presen
OMP: Arificial Inelligence Fundamenals Lecure 0 Very Brief Overview Lecurer: Email: Xiao-Jun Zeng x.zeng@mancheser.ac.uk Overview This course will focus mainly on probabilisic mehods in AI We shall presen
Designing Information Devices and Systems I Spring 2019 Lecture Notes Note 17
 EES 16A Designing Informaion Devices and Sysems I Spring 019 Lecure Noes Noe 17 17.1 apaciive ouchscreen In he las noe, we saw ha a capacior consiss of wo pieces on conducive maerial separaed by a nonconducive
EES 16A Designing Informaion Devices and Sysems I Spring 019 Lecure Noes Noe 17 17.1 apaciive ouchscreen In he las noe, we saw ha a capacior consiss of wo pieces on conducive maerial separaed by a nonconducive
Pade and Laguerre Approximations Applied. to the Active Queue Management Model. of Internet Protocol
 Applied Mahemaical Sciences, Vol. 7, 013, no. 16, 663-673 HIKARI Ld, www.m-hikari.com hp://dx.doi.org/10.1988/ams.013.39499 Pade and Laguerre Approximaions Applied o he Acive Queue Managemen Model of Inerne
Applied Mahemaical Sciences, Vol. 7, 013, no. 16, 663-673 HIKARI Ld, www.m-hikari.com hp://dx.doi.org/10.1988/ams.013.39499 Pade and Laguerre Approximaions Applied o he Acive Queue Managemen Model of Inerne
Security enhancement on efficient verifier-based key agreement protocol for three parties without server s public key
 Inernaional Mahemaical Forum, 1, no. 20, 2006, 965 972 Securiy enhancemen on efficien erifier-based key agreemen proocol for hree paries wihou serer s public key Ren-Chiun Wang 1 and un-ru Mo 2 Deparmen
Inernaional Mahemaical Forum, 1, no. 20, 2006, 965 972 Securiy enhancemen on efficien erifier-based key agreemen proocol for hree paries wihou serer s public key Ren-Chiun Wang 1 and un-ru Mo 2 Deparmen
Improved Approximate Solutions for Nonlinear Evolutions Equations in Mathematical Physics Using the Reduced Differential Transform Method
 Journal of Applied Mahemaics & Bioinformaics, vol., no., 01, 1-14 ISSN: 179-660 (prin), 179-699 (online) Scienpress Ld, 01 Improved Approimae Soluions for Nonlinear Evoluions Equaions in Mahemaical Physics
Journal of Applied Mahemaics & Bioinformaics, vol., no., 01, 1-14 ISSN: 179-660 (prin), 179-699 (online) Scienpress Ld, 01 Improved Approimae Soluions for Nonlinear Evoluions Equaions in Mahemaical Physics
EXERCISES FOR SECTION 1.5
 1.5 Exisence and Uniqueness of Soluions 43 20. 1 v c 21. 1 v c 1 2 4 6 8 10 1 2 2 4 6 8 10 Graph of approximae soluion obained using Euler s mehod wih = 0.1. Graph of approximae soluion obained using Euler
1.5 Exisence and Uniqueness of Soluions 43 20. 1 v c 21. 1 v c 1 2 4 6 8 10 1 2 2 4 6 8 10 Graph of approximae soluion obained using Euler s mehod wih = 0.1. Graph of approximae soluion obained using Euler
Hamilton- J acobi Equation: Explicit Formulas In this lecture we try to apply the method of characteristics to the Hamilton-Jacobi equation: u t
 M ah 5 2 7 Fall 2 0 0 9 L ecure 1 0 O c. 7, 2 0 0 9 Hamilon- J acobi Equaion: Explici Formulas In his lecure we ry o apply he mehod of characerisics o he Hamilon-Jacobi equaion: u + H D u, x = 0 in R n
M ah 5 2 7 Fall 2 0 0 9 L ecure 1 0 O c. 7, 2 0 0 9 Hamilon- J acobi Equaion: Explici Formulas In his lecure we ry o apply he mehod of characerisics o he Hamilon-Jacobi equaion: u + H D u, x = 0 in R n
Particle Swarm Optimization Combining Diversification and Intensification for Nonlinear Integer Programming Problems
 Paricle Swarm Opimizaion Combining Diversificaion and Inensificaion for Nonlinear Ineger Programming Problems Takeshi Masui, Masaoshi Sakawa, Kosuke Kao and Koichi Masumoo Hiroshima Universiy 1-4-1, Kagamiyama,
Paricle Swarm Opimizaion Combining Diversificaion and Inensificaion for Nonlinear Ineger Programming Problems Takeshi Masui, Masaoshi Sakawa, Kosuke Kao and Koichi Masumoo Hiroshima Universiy 1-4-1, Kagamiyama,
Chapter 3 Boundary Value Problem
 Chaper 3 Boundary Value Problem A boundary value problem (BVP) is a problem, ypically an ODE or a PDE, which has values assigned on he physical boundary of he domain in which he problem is specified. Le
Chaper 3 Boundary Value Problem A boundary value problem (BVP) is a problem, ypically an ODE or a PDE, which has values assigned on he physical boundary of he domain in which he problem is specified. Le
Lab 10: RC, RL, and RLC Circuits
 Lab 10: RC, RL, and RLC Circuis In his experimen, we will invesigae he behavior of circuis conaining combinaions of resisors, capaciors, and inducors. We will sudy he way volages and currens change in
Lab 10: RC, RL, and RLC Circuis In his experimen, we will invesigae he behavior of circuis conaining combinaions of resisors, capaciors, and inducors. We will sudy he way volages and currens change in
Some Ramsey results for the n-cube
 Some Ramsey resuls for he n-cube Ron Graham Universiy of California, San Diego Jozsef Solymosi Universiy of Briish Columbia, Vancouver, Canada Absrac In his noe we esablish a Ramsey-ype resul for cerain
Some Ramsey resuls for he n-cube Ron Graham Universiy of California, San Diego Jozsef Solymosi Universiy of Briish Columbia, Vancouver, Canada Absrac In his noe we esablish a Ramsey-ype resul for cerain
Matlab and Python programming: how to get started
 Malab and Pyhon programming: how o ge sared Equipping readers he skills o wrie programs o explore complex sysems and discover ineresing paerns from big daa is one of he main goals of his book. In his chaper,
Malab and Pyhon programming: how o ge sared Equipping readers he skills o wrie programs o explore complex sysems and discover ineresing paerns from big daa is one of he main goals of his book. In his chaper,
Bias in Conditional and Unconditional Fixed Effects Logit Estimation: a Correction * Tom Coupé
 Bias in Condiional and Uncondiional Fixed Effecs Logi Esimaion: a Correcion * Tom Coupé Economics Educaion and Research Consorium, Naional Universiy of Kyiv Mohyla Academy Address: Vul Voloska 10, 04070
Bias in Condiional and Uncondiional Fixed Effecs Logi Esimaion: a Correcion * Tom Coupé Economics Educaion and Research Consorium, Naional Universiy of Kyiv Mohyla Academy Address: Vul Voloska 10, 04070
Course Notes for EE227C (Spring 2018): Convex Optimization and Approximation
 Course Noes for EE7C Spring 018: Convex Opimizaion and Approximaion Insrucor: Moriz Hard Email: hard+ee7c@berkeley.edu Graduae Insrucor: Max Simchowiz Email: msimchow+ee7c@berkeley.edu Ocober 15, 018 3
Course Noes for EE7C Spring 018: Convex Opimizaion and Approximaion Insrucor: Moriz Hard Email: hard+ee7c@berkeley.edu Graduae Insrucor: Max Simchowiz Email: msimchow+ee7c@berkeley.edu Ocober 15, 018 3
Approximation Algorithms for Unique Games via Orthogonal Separators
 Approximaion Algorihms for Unique Games via Orhogonal Separaors Lecure noes by Konsanin Makarychev. Lecure noes are based on he papers [CMM06a, CMM06b, LM4]. Unique Games In hese lecure noes, we define
Approximaion Algorihms for Unique Games via Orhogonal Separaors Lecure noes by Konsanin Makarychev. Lecure noes are based on he papers [CMM06a, CMM06b, LM4]. Unique Games In hese lecure noes, we define
EECE 301 Signals & Systems Prof. Mark Fowler
 EECE 31 Signals & Sysems Prof. Mark Fowler Noe Se #1 C-T Sysems: Convoluion Represenaion Reading Assignmen: Secion 2.6 of Kamen and Heck 1/11 Course Flow Diagram The arrows here show concepual flow beween
EECE 31 Signals & Sysems Prof. Mark Fowler Noe Se #1 C-T Sysems: Convoluion Represenaion Reading Assignmen: Secion 2.6 of Kamen and Heck 1/11 Course Flow Diagram The arrows here show concepual flow beween
Ensemble Confidence Estimates Posterior Probability
 Ensemble Esimaes Poserior Probabiliy Michael Muhlbaier, Aposolos Topalis, and Robi Polikar Rowan Universiy, Elecrical and Compuer Engineering, Mullica Hill Rd., Glassboro, NJ 88, USA {muhlba6, opali5}@sudens.rowan.edu
Ensemble Esimaes Poserior Probabiliy Michael Muhlbaier, Aposolos Topalis, and Robi Polikar Rowan Universiy, Elecrical and Compuer Engineering, Mullica Hill Rd., Glassboro, NJ 88, USA {muhlba6, opali5}@sudens.rowan.edu
23.2. Representing Periodic Functions by Fourier Series. Introduction. Prerequisites. Learning Outcomes
 Represening Periodic Funcions by Fourier Series 3. Inroducion In his Secion we show how a periodic funcion can be expressed as a series of sines and cosines. We begin by obaining some sandard inegrals
Represening Periodic Funcions by Fourier Series 3. Inroducion In his Secion we show how a periodic funcion can be expressed as a series of sines and cosines. We begin by obaining some sandard inegrals
Lecture 1 Overview. course mechanics. outline & topics. what is a linear dynamical system? why study linear systems? some examples
 EE263 Auumn 27-8 Sephen Boyd Lecure 1 Overview course mechanics ouline & opics wha is a linear dynamical sysem? why sudy linear sysems? some examples 1 1 Course mechanics all class info, lecures, homeworks,
EE263 Auumn 27-8 Sephen Boyd Lecure 1 Overview course mechanics ouline & opics wha is a linear dynamical sysem? why sudy linear sysems? some examples 1 1 Course mechanics all class info, lecures, homeworks,
Finish reading Chapter 2 of Spivak, rereading earlier sections as necessary. handout and fill in some missing details!
 MAT 257, Handou 6: Ocober 7-2, 20. I. Assignmen. Finish reading Chaper 2 of Spiva, rereading earlier secions as necessary. handou and fill in some missing deails! II. Higher derivaives. Also, read his
MAT 257, Handou 6: Ocober 7-2, 20. I. Assignmen. Finish reading Chaper 2 of Spiva, rereading earlier secions as necessary. handou and fill in some missing deails! II. Higher derivaives. Also, read his
The electromagnetic interference in case of onboard navy ships computers - a new approach
 The elecromagneic inerference in case of onboard navy ships compuers - a new approach Prof. dr. ing. Alexandru SOTIR Naval Academy Mircea cel Bărân, Fulgerului Sree, Consanţa, soiralexandru@yahoo.com Absrac.
The elecromagneic inerference in case of onboard navy ships compuers - a new approach Prof. dr. ing. Alexandru SOTIR Naval Academy Mircea cel Bărân, Fulgerului Sree, Consanţa, soiralexandru@yahoo.com Absrac.
A Dynamic Model of Economic Fluctuations
 CHAPTER 15 A Dynamic Model of Economic Flucuaions Modified for ECON 2204 by Bob Murphy 2016 Worh Publishers, all righs reserved IN THIS CHAPTER, OU WILL LEARN: how o incorporae dynamics ino he AD-AS model
CHAPTER 15 A Dynamic Model of Economic Flucuaions Modified for ECON 2204 by Bob Murphy 2016 Worh Publishers, all righs reserved IN THIS CHAPTER, OU WILL LEARN: how o incorporae dynamics ino he AD-AS model
Orientation. Connections between network coding and stochastic network theory. Outline. Bruce Hajek. Multicast with lost packets
 Connecions beween nework coding and sochasic nework heory Bruce Hajek Orienaion On Thursday, Ralf Koeer discussed nework coding: coding wihin he nework Absrac: Randomly generaed coded informaion blocks
Connecions beween nework coding and sochasic nework heory Bruce Hajek Orienaion On Thursday, Ralf Koeer discussed nework coding: coding wihin he nework Absrac: Randomly generaed coded informaion blocks
Notes for Lecture 17-18
 U.C. Berkeley CS278: Compuaional Complexiy Handou N7-8 Professor Luca Trevisan April 3-8, 2008 Noes for Lecure 7-8 In hese wo lecures we prove he firs half of he PCP Theorem, he Amplificaion Lemma, up
U.C. Berkeley CS278: Compuaional Complexiy Handou N7-8 Professor Luca Trevisan April 3-8, 2008 Noes for Lecure 7-8 In hese wo lecures we prove he firs half of he PCP Theorem, he Amplificaion Lemma, up
Block Diagram of a DCS in 411
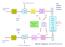 Informaion source Forma A/D From oher sources Pulse modu. Muliplex Bandpass modu. X M h: channel impulse response m i g i s i Digial inpu Digial oupu iming and synchronizaion Digial baseband/ bandpass
Informaion source Forma A/D From oher sources Pulse modu. Muliplex Bandpass modu. X M h: channel impulse response m i g i s i Digial inpu Digial oupu iming and synchronizaion Digial baseband/ bandpass
Modeling the Dynamics of an Ice Tank Carriage
 Modeling he Dynamics of an Ice Tank Carriage The challenge: To model he dynamics of an Ice Tank Carriage and idenify a mechanism o alleviae he backlash inheren in he design of he gearbox. Maplesof, a division
Modeling he Dynamics of an Ice Tank Carriage The challenge: To model he dynamics of an Ice Tank Carriage and idenify a mechanism o alleviae he backlash inheren in he design of he gearbox. Maplesof, a division
Orthogonal Rational Functions, Associated Rational Functions And Functions Of The Second Kind
 Proceedings of he World Congress on Engineering 2008 Vol II Orhogonal Raional Funcions, Associaed Raional Funcions And Funcions Of The Second Kind Karl Deckers and Adhemar Bulheel Absrac Consider he sequence
Proceedings of he World Congress on Engineering 2008 Vol II Orhogonal Raional Funcions, Associaed Raional Funcions And Funcions Of The Second Kind Karl Deckers and Adhemar Bulheel Absrac Consider he sequence
11!Hí MATHEMATICS : ERDŐS AND ULAM PROC. N. A. S. of decomposiion, properly speaking) conradics he possibiliy of defining a counably addiive real-valu
 ON EQUATIONS WITH SETS AS UNKNOWNS BY PAUL ERDŐS AND S. ULAM DEPARTMENT OF MATHEMATICS, UNIVERSITY OF COLORADO, BOULDER Communicaed May 27, 1968 We shall presen here a number of resuls in se heory concerning
ON EQUATIONS WITH SETS AS UNKNOWNS BY PAUL ERDŐS AND S. ULAM DEPARTMENT OF MATHEMATICS, UNIVERSITY OF COLORADO, BOULDER Communicaed May 27, 1968 We shall presen here a number of resuls in se heory concerning
CSE 3802 / ECE Numerical Methods in Scientific Computation. Jinbo Bi. Department of Computer Science & Engineering
 CSE 3802 / ECE 3431 Numerical Mehods in Scienific Compuaion Jinbo Bi Deparmen of Compuer Science & Engineering hp://www.engr.uconn.edu/~jinbo 1 Ph.D in Mahemaics The Insrucor Previous professional experience:
CSE 3802 / ECE 3431 Numerical Mehods in Scienific Compuaion Jinbo Bi Deparmen of Compuer Science & Engineering hp://www.engr.uconn.edu/~jinbo 1 Ph.D in Mahemaics The Insrucor Previous professional experience:
14 Autoregressive Moving Average Models
 14 Auoregressive Moving Average Models In his chaper an imporan parameric family of saionary ime series is inroduced, he family of he auoregressive moving average, or ARMA, processes. For a large class
14 Auoregressive Moving Average Models In his chaper an imporan parameric family of saionary ime series is inroduced, he family of he auoregressive moving average, or ARMA, processes. For a large class
Lecture 2 October ε-approximation of 2-player zero-sum games
 Opimizaion II Winer 009/10 Lecurer: Khaled Elbassioni Lecure Ocober 19 1 ε-approximaion of -player zero-sum games In his lecure we give a randomized ficiious play algorihm for obaining an approximae soluion
Opimizaion II Winer 009/10 Lecurer: Khaled Elbassioni Lecure Ocober 19 1 ε-approximaion of -player zero-sum games In his lecure we give a randomized ficiious play algorihm for obaining an approximae soluion
The Rosenblatt s LMS algorithm for Perceptron (1958) is built around a linear neuron (a neuron with a linear
 In The name of God Lecure4: Percepron and AALIE r. Majid MjidGhoshunih Inroducion The Rosenbla s LMS algorihm for Percepron 958 is buil around a linear neuron a neuron ih a linear acivaion funcion. Hoever,
In The name of God Lecure4: Percepron and AALIE r. Majid MjidGhoshunih Inroducion The Rosenbla s LMS algorihm for Percepron 958 is buil around a linear neuron a neuron ih a linear acivaion funcion. Hoever,
A problem related to Bárány Grünbaum conjecture
 Filoma 27:1 (2013), 109 113 DOI 10.2298/FIL1301109B Published by Faculy of Sciences and Mahemaics, Universiy of Niš, Serbia Available a: hp://www.pmf.ni.ac.rs/filoma A problem relaed o Bárány Grünbaum
Filoma 27:1 (2013), 109 113 DOI 10.2298/FIL1301109B Published by Faculy of Sciences and Mahemaics, Universiy of Niš, Serbia Available a: hp://www.pmf.ni.ac.rs/filoma A problem relaed o Bárány Grünbaum
control properties under both Gaussian and burst noise conditions. In the ~isappointing in comparison with convolutional code systems designed
 535 SOFT-DECSON THRESHOLD DECODNG OF CONVOLUTONAL CODES R.M.F. Goodman*, B.Sc., Ph.D. W.H. Ng*, M.S.E.E. Sunnnary Exising majoriy-decision hreshold decoders have so far been limied o his paper a new mehod
535 SOFT-DECSON THRESHOLD DECODNG OF CONVOLUTONAL CODES R.M.F. Goodman*, B.Sc., Ph.D. W.H. Ng*, M.S.E.E. Sunnnary Exising majoriy-decision hreshold decoders have so far been limied o his paper a new mehod
d 1 = c 1 b 2 - b 1 c 2 d 2 = c 1 b 3 - b 1 c 3
 and d = c b - b c c d = c b - b c c This process is coninued unil he nh row has been compleed. The complee array of coefficiens is riangular. Noe ha in developing he array an enire row may be divided or
and d = c b - b c c d = c b - b c c This process is coninued unil he nh row has been compleed. The complee array of coefficiens is riangular. Noe ha in developing he array an enire row may be divided or
Adaptive Noise Estimation Based on Non-negative Matrix Factorization
 dvanced cience and Technology Leers Vol.3 (ICC 213), pp.159-163 hp://dx.doi.org/1.14257/asl.213 dapive Noise Esimaion ased on Non-negaive Marix Facorizaion Kwang Myung Jeon and Hong Kook Kim chool of Informaion
dvanced cience and Technology Leers Vol.3 (ICC 213), pp.159-163 hp://dx.doi.org/1.14257/asl.213 dapive Noise Esimaion ased on Non-negaive Marix Facorizaion Kwang Myung Jeon and Hong Kook Kim chool of Informaion
Chapter 8 The Complete Response of RL and RC Circuits
 Chaper 8 The Complee Response of RL and RC Circuis Seoul Naional Universiy Deparmen of Elecrical and Compuer Engineering Wha is Firs Order Circuis? Circuis ha conain only one inducor or only one capacior
Chaper 8 The Complee Response of RL and RC Circuis Seoul Naional Universiy Deparmen of Elecrical and Compuer Engineering Wha is Firs Order Circuis? Circuis ha conain only one inducor or only one capacior
Anti-Disturbance Control for Multiple Disturbances
 Workshop a 3 ACC Ani-Disurbance Conrol for Muliple Disurbances Lei Guo (lguo@buaa.edu.cn) Naional Key Laboraory on Science and Technology on Aircraf Conrol, Beihang Universiy, Beijing, 9, P.R. China. Presened
Workshop a 3 ACC Ani-Disurbance Conrol for Muliple Disurbances Lei Guo (lguo@buaa.edu.cn) Naional Key Laboraory on Science and Technology on Aircraf Conrol, Beihang Universiy, Beijing, 9, P.R. China. Presened
State-Space Models. Initialization, Estimation and Smoothing of the Kalman Filter
 Sae-Space Models Iniializaion, Esimaion and Smoohing of he Kalman Filer Iniializaion of he Kalman Filer The Kalman filer shows how o updae pas predicors and he corresponding predicion error variances when
Sae-Space Models Iniializaion, Esimaion and Smoohing of he Kalman Filer Iniializaion of he Kalman Filer The Kalman filer shows how o updae pas predicors and he corresponding predicion error variances when
Robust estimation based on the first- and third-moment restrictions of the power transformation model
 h Inernaional Congress on Modelling and Simulaion, Adelaide, Ausralia, 6 December 3 www.mssanz.org.au/modsim3 Robus esimaion based on he firs- and hird-momen resricions of he power ransformaion Nawaa,
h Inernaional Congress on Modelling and Simulaion, Adelaide, Ausralia, 6 December 3 www.mssanz.org.au/modsim3 Robus esimaion based on he firs- and hird-momen resricions of he power ransformaion Nawaa,
RL Lecture 7: Eligibility Traces. R. S. Sutton and A. G. Barto: Reinforcement Learning: An Introduction 1
 RL Lecure 7: Eligibiliy Traces R. S. Suon and A. G. Baro: Reinforcemen Learning: An Inroducion 1 N-sep TD Predicion Idea: Look farher ino he fuure when you do TD backup (1, 2, 3,, n seps) R. S. Suon and
RL Lecure 7: Eligibiliy Traces R. S. Suon and A. G. Baro: Reinforcemen Learning: An Inroducion 1 N-sep TD Predicion Idea: Look farher ino he fuure when you do TD backup (1, 2, 3,, n seps) R. S. Suon and
20. Applications of the Genetic-Drift Model
 0. Applicaions of he Geneic-Drif Model 1) Deermining he probabiliy of forming any paricular combinaion of genoypes in he nex generaion: Example: If he parenal allele frequencies are p 0 = 0.35 and q 0
0. Applicaions of he Geneic-Drif Model 1) Deermining he probabiliy of forming any paricular combinaion of genoypes in he nex generaion: Example: If he parenal allele frequencies are p 0 = 0.35 and q 0
Linear Response Theory: The connection between QFT and experiments
 Phys540.nb 39 3 Linear Response Theory: The connecion beween QFT and experimens 3.1. Basic conceps and ideas Q: How do we measure he conduciviy of a meal? A: we firs inroduce a weak elecric field E, and
Phys540.nb 39 3 Linear Response Theory: The connecion beween QFT and experimens 3.1. Basic conceps and ideas Q: How do we measure he conduciviy of a meal? A: we firs inroduce a weak elecric field E, and
CSE Computer Architecture I
 Single cycle Conrol Implemenaion CSE 332 Compuer Archiecure I l x I Lecure 7 - uli Cycle achines i i [ ] I I r l ichael Niemier Deparmen of Compuer Science and Engineering I ] i X.S. Hu 5- X.S. Hu 5-2
Single cycle Conrol Implemenaion CSE 332 Compuer Archiecure I l x I Lecure 7 - uli Cycle achines i i [ ] I I r l ichael Niemier Deparmen of Compuer Science and Engineering I ] i X.S. Hu 5- X.S. Hu 5-2
3.1.3 INTRODUCTION TO DYNAMIC OPTIMIZATION: DISCRETE TIME PROBLEMS. A. The Hamiltonian and First-Order Conditions in a Finite Time Horizon
 3..3 INRODUCION O DYNAMIC OPIMIZAION: DISCREE IME PROBLEMS A. he Hamilonian and Firs-Order Condiions in a Finie ime Horizon Define a new funcion, he Hamilonian funcion, H. H he change in he oal value of
3..3 INRODUCION O DYNAMIC OPIMIZAION: DISCREE IME PROBLEMS A. he Hamilonian and Firs-Order Condiions in a Finie ime Horizon Define a new funcion, he Hamilonian funcion, H. H he change in he oal value of
Variational Iteration Method for Solving System of Fractional Order Ordinary Differential Equations
 IOSR Journal of Mahemaics (IOSR-JM) e-issn: 2278-5728, p-issn: 2319-765X. Volume 1, Issue 6 Ver. II (Nov - Dec. 214), PP 48-54 Variaional Ieraion Mehod for Solving Sysem of Fracional Order Ordinary Differenial
IOSR Journal of Mahemaics (IOSR-JM) e-issn: 2278-5728, p-issn: 2319-765X. Volume 1, Issue 6 Ver. II (Nov - Dec. 214), PP 48-54 Variaional Ieraion Mehod for Solving Sysem of Fracional Order Ordinary Differenial
ON THE DEGREES OF RATIONAL KNOTS
 ON THE DEGREES OF RATIONAL KNOTS DONOVAN MCFERON, ALEXANDRA ZUSER Absrac. In his paper, we explore he issue of minimizing he degrees on raional knos. We se a bound on hese degrees using Bézou s heorem,
ON THE DEGREES OF RATIONAL KNOTS DONOVAN MCFERON, ALEXANDRA ZUSER Absrac. In his paper, we explore he issue of minimizing he degrees on raional knos. We se a bound on hese degrees using Bézou s heorem,
WATER LEVEL TRACKING WITH CONDENSATION ALGORITHM
 WATER LEVEL TRACKING WITH CONDENSATION ALGORITHM Shinsuke KOBAYASHI, Shogo MURAMATSU, Hisakazu KIKUCHI, Masahiro IWAHASHI Dep. of Elecrical and Elecronic Eng., Niigaa Universiy, 8050 2-no-cho Igarashi,
WATER LEVEL TRACKING WITH CONDENSATION ALGORITHM Shinsuke KOBAYASHI, Shogo MURAMATSU, Hisakazu KIKUCHI, Masahiro IWAHASHI Dep. of Elecrical and Elecronic Eng., Niigaa Universiy, 8050 2-no-cho Igarashi,
10. State Space Methods
 . Sae Space Mehods. Inroducion Sae space modelling was briefly inroduced in chaper. Here more coverage is provided of sae space mehods before some of heir uses in conrol sysem design are covered in he
. Sae Space Mehods. Inroducion Sae space modelling was briefly inroduced in chaper. Here more coverage is provided of sae space mehods before some of heir uses in conrol sysem design are covered in he
V AK (t) I T (t) I TRM. V AK( full area) (t) t t 1 Axial turn-on. Switching losses for Phase Control and Bi- Directionally Controlled Thyristors
 Applicaion Noe Swiching losses for Phase Conrol and Bi- Direcionally Conrolled Thyrisors V AK () I T () Causing W on I TRM V AK( full area) () 1 Axial urn-on Plasma spread 2 Swiching losses for Phase Conrol
Applicaion Noe Swiching losses for Phase Conrol and Bi- Direcionally Conrolled Thyrisors V AK () I T () Causing W on I TRM V AK( full area) () 1 Axial urn-on Plasma spread 2 Swiching losses for Phase Conrol
Supplement for Stochastic Convex Optimization: Faster Local Growth Implies Faster Global Convergence
 Supplemen for Sochasic Convex Opimizaion: Faser Local Growh Implies Faser Global Convergence Yi Xu Qihang Lin ianbao Yang Proof of heorem heorem Suppose Assumpion holds and F (w) obeys he LGC (6) Given
Supplemen for Sochasic Convex Opimizaion: Faser Local Growh Implies Faser Global Convergence Yi Xu Qihang Lin ianbao Yang Proof of heorem heorem Suppose Assumpion holds and F (w) obeys he LGC (6) Given
Online Appendix to Solution Methods for Models with Rare Disasters
 Online Appendix o Soluion Mehods for Models wih Rare Disasers Jesús Fernández-Villaverde and Oren Levinal In his Online Appendix, we presen he Euler condiions of he model, we develop he pricing Calvo block,
Online Appendix o Soluion Mehods for Models wih Rare Disasers Jesús Fernández-Villaverde and Oren Levinal In his Online Appendix, we presen he Euler condiions of he model, we develop he pricing Calvo block,
MATH 5720: Gradient Methods Hung Phan, UMass Lowell October 4, 2018
 MATH 5720: Gradien Mehods Hung Phan, UMass Lowell Ocober 4, 208 Descen Direcion Mehods Consider he problem min { f(x) x R n}. The general descen direcions mehod is x k+ = x k + k d k where x k is he curren
MATH 5720: Gradien Mehods Hung Phan, UMass Lowell Ocober 4, 208 Descen Direcion Mehods Consider he problem min { f(x) x R n}. The general descen direcions mehod is x k+ = x k + k d k where x k is he curren
0.1 MAXIMUM LIKELIHOOD ESTIMATION EXPLAINED
 0.1 MAXIMUM LIKELIHOOD ESTIMATIO EXPLAIED Maximum likelihood esimaion is a bes-fi saisical mehod for he esimaion of he values of he parameers of a sysem, based on a se of observaions of a random variable
0.1 MAXIMUM LIKELIHOOD ESTIMATIO EXPLAIED Maximum likelihood esimaion is a bes-fi saisical mehod for he esimaion of he values of he parameers of a sysem, based on a se of observaions of a random variable
The Asymptotic Behavior of Nonoscillatory Solutions of Some Nonlinear Dynamic Equations on Time Scales
 Advances in Dynamical Sysems and Applicaions. ISSN 0973-5321 Volume 1 Number 1 (2006, pp. 103 112 c Research India Publicaions hp://www.ripublicaion.com/adsa.hm The Asympoic Behavior of Nonoscillaory Soluions
Advances in Dynamical Sysems and Applicaions. ISSN 0973-5321 Volume 1 Number 1 (2006, pp. 103 112 c Research India Publicaions hp://www.ripublicaion.com/adsa.hm The Asympoic Behavior of Nonoscillaory Soluions
Waveform Transmission Method, A New Waveform-relaxation Based Algorithm. to Solve Ordinary Differential Equations in Parallel
 Waveform Transmission Mehod, A New Waveform-relaxaion Based Algorihm o Solve Ordinary Differenial Equaions in Parallel Fei Wei Huazhong Yang Deparmen of Elecronic Engineering, Tsinghua Universiy, Beijing,
Waveform Transmission Mehod, A New Waveform-relaxaion Based Algorihm o Solve Ordinary Differenial Equaions in Parallel Fei Wei Huazhong Yang Deparmen of Elecronic Engineering, Tsinghua Universiy, Beijing,
Testing for a Single Factor Model in the Multivariate State Space Framework
 esing for a Single Facor Model in he Mulivariae Sae Space Framework Chen C.-Y. M. Chiba and M. Kobayashi Inernaional Graduae School of Social Sciences Yokohama Naional Universiy Japan Faculy of Economics
esing for a Single Facor Model in he Mulivariae Sae Space Framework Chen C.-Y. M. Chiba and M. Kobayashi Inernaional Graduae School of Social Sciences Yokohama Naional Universiy Japan Faculy of Economics
