Security enhancement on efficient verifier-based key agreement protocol for three parties without server s public key
|
|
|
- Rudolf Cain
- 5 years ago
- Views:
Transcription
1 Inernaional Mahemaical Forum, 1, no. 20, 2006, Securiy enhancemen on efficien erifier-based key agreemen proocol for hree paries wihou serer s public key Ren-Chiun Wang 1 and un-ru Mo 2 Deparmen of Informaion Managemen 1 Chaoyang Uniersiy of Technology 1F., No.9, lley 10, Lane 278, Cingshuei Rd., Tucheng Ciy, Taipei Couny 236, Taiwan R.O.C. Corresponding auhor chiunchiunwang@yahoo.com.w Deparmen of Informaion Managemen 2 Min Chuan Uniersiy No. 250, secion 5, Chung Shan Norh Road, Taipei Ciy 111, Taiwan R.O.C. sephen@sanyo.com.w bsrac Recenly Lee e al. proposed an efficien erifier-based key agreemen proocol for hree paries wihou serer s public key. Lee e al. claimed he proposed proocol could resis arious aacks and proide he perfec forward secrecy. Howeer, in his paper, auhors shall show ha heir proocol suffers from he impersonaion aack. he same ime, auhors shall propose an improed mehod o wihsand he aboe aack. eyword: auhenicaion, crypanalysis, impersonaion aack, key agreemen, password. 1. Inroducion When wo paries wan o communicae each oher, he erificaion of he ideniy of he oher pary is an imporan requiremen. For enhancing he performance of he proocol, elloin and Merri [1] proposed an encryped exchange proocol based on password called EE for auhenicaion and key agreemen in 1992.
2 966 Ren-Chiun Wang and un-ru Mo Following and exending he concepions of elloin and Merri s proocol, many hree-pary proocols were proposed [2, 5, 7-10]. Howeer, he preious proocols sill exised some securiy problems such as on-line undeecable password guessing aack [4] and off-line password guessing aack [7] ec. No only ha, some proocols also required serer s public key o proec he shared password [7, 10]. For enhancing he efficiency and preening arious aacks, Lee e al. [6] proposed an efficien erifier-based key agreemen proocol for hree paries wihou serer s public key. Lee e al. s proocol proides he perfec forward secrecy by employing he concepions of he Diffie-Hellman scheme [3] and each clien only needs o remember a memorable password. The proocol is suiable for some applicaions of low compuaions. Howeer, auhors shall show ha Lee e al. s proocol is ulnerable o he impersonaion aack wihou making an off-line password guessing aack. he same ime, auhors shall propose an improed mehod o wihsand he aboe aack. Nex Secion, auhors shall go oer Lee e al. s proocol and show ha heir proocol s weakness. In Secion 3, auhors shall propose an improemen. Finally, auhors shall make a conclusion for his paper. 2. Reiew of Lee e al. s proocol In his secion, auhors shall reiew Lee e al. s proocol show ha he proocol s weakness. efore he inroducion of he proocol, auhors firs denoe some parameers as follows., and denoes he ideniies of lice, ob and uhenicaion Serer respeciely. p is a large prime and g is a generaor in he cyclic group Z p *. uhors omi mod p from expressions for simpliciy. h( denoes a collision-free one-way hash funcion. π is a password and shared beween and. is a erifier ha is compued fromπ. h, ( π is a password and shared beween and. is a erifier ha is compued fromπ. h, ( 2.1 Lee e al. s proocol efore he running of he proocol, lice and ob sends heir erifiers and o
3 , Securiy enhancemen on efficien 967 hrough a secure channel. sores and in a password able. Sep 1: lice ob: lice compues X a and sends he compued resul wih he ideniy o ob, where * a R Z p. Sep 2: ob :, ob lice: b * R Z p ob compues X, where b and respeciely.. ob sends X and (, o lice Sep 3: lice: X ob: X S fer receiing he messages, reriees and from password able. Then c compues X = ( and X S = ( d, where c and d R Z * p. sends X and X S o lice and ob respeciely. Finally, compues = (X and S = (X d bd. c ac Sep 4: lice : ob : S a ac lice compues = ( X and = h(,, X. b bd lice sends o. Similarly, ob compues = ( X and S = h(,, X S, S. ob sends S o. Noe ha = h, and = h(,. ( S S
4 968 Ren-Chiun Wang and un-ru Mo Sep 5: lice: ob: S, erifies wheher and S are rue or no. If hey are rue, sends and S o lice and ob respeciely, where = h,, X, and S = h(,, X, S. ( Sep 6: lice and ob erify wheher and S are rue or no respeciely. If hey are a ba rue, lice compues = (X and ob compues = (X. Finally, lice and ob negoiae a common session key = h(,, = h(,,. We use figure 1 o inroduce Lee e al. s proocol. b ab lice ob = h, = h, ( a ( h(, S, π h(, S, π, X b, X = ( c X X X S = ( d S = (X c ac a ac b bd = ( X S = ( X S S = (X c bc = h(,, S, S = h(,, S S, S = h( S,,, X, S S = h( S,,, X, S Verify and S Verify = (X a ab = h(,, Verify S = (X b ab = h(,, Fig. 1 Inroducion of Lee e al. s proocol 2.2 Weakness on Lee e al. s proocol Once lice s erifier has solen by he aacker. The aacker can impersonae ob o communicae wih lice by performing he following seps. We use figure 2 o inroduce our aack. Sep 1 : When lice wans o communicae wih ob. lice sends ( o ob. Now, he aacker inerceps i and sends ( = o ob. Sep 2 : ob forwards he receied message wih ( o and sends X o he
5 Securiy enhancemen on efficien 969 aacker respeciely. Then, he aacker sends X o lice, where b is chosen by he aacker. b Sep 3 : compues X = ( c d and X S = ( and sends he compued resuls o he aacker and ob respeciely. Finally, compues = (X c = ( c d bd and S = (X. Sep 4 : The aacker sends X = ( c o lice, where c is chosen by he aacker. Sep 5 : The aacker compues = X = (c and sends ' = h(,, X, ' o. We can find can pass he erificaion of because = = (c. Sep 6 : The aacker compues = (X c ac, ab and = h(,, X,. Sep 7 : lice compues a = ( X ' ac', ab and = h,, X,. lice sends o he aacker. The aacker sends o ( lice. We can find lice will accep he receied message because = = g ac. Sep 8 :Finally, lice beliees he common session key = h(,, b a is rue. he same, ob also beliees he owned session key = h(,, = ( b is rue. In fac, he aacker ges he session key = (X b ab and impersonaes ob o communicae wih lice.
6 970 Ren-Chiun Wang and un-ru Mo lice acker ob a = X b X b, X = ( c X S = ( d X = ( c X X S = (X c = ( c S = (X c bc = ( X' ab' a ' = h(,, X ac' = X = ( c ac ab, ' ' = h(,, X S S, ' Verify and S Verify = h(,, Fig. 2 Impersonaion aack in he Lee e al. s proocol 3. Improemen on Lee e al. s proocol uhors shall propose an improed mehod o wihsand he aboe aack. lice and ob should send = h(,, X, c ( X, and S = h(,, X, d ( X, S o respeciely in he Sep 4 of Lee e al. s S proocol. Een if boh lice and ob s erifiers and are solen by he aacker. The aacker sill canno make an impersonaion aack on our improemen wihou = h, and = h(,. We use figure 3 o inroduce our improemen. (
7 Securiy enhancemen on efficien 971 lice ob = h, = h, = ( X ( = h(,, X a X b a X, g ac c, S S ( = ( X S = h(,, X, b X S, g bd d, S h(, h(, X = ( c X S = ( d = (X c ac S = (X c bc, = h(,, X, X, S S = h(,, X, X, S Verify and S Verify = (X a ab = h(,, Verify S = (X b ab = h(,, Fig. 3 Our improemen 4. Conclusion In his paper, auhors show ha Lee e al. s efficien erifier-based key agreemen proocol for hree paries is ulnerable o he impersonaion aack wihou making an off-line password guessing aack. he same ime, auhors propose heir improemen o wihsand he aboe aack. Reference [1] S. M. elloin and M. Merri, Encryped key exchange: password-based proocols secure agains dicionary aacks, Proceedings of he IEEE Symposium on Research in Securiy and Priacy, (1992, [2] C.-C. Chang and Y.-F. Cheng, noel hree-pary encryped key exchange proocol, Compuer Sandards & Inerfaces, 26 (5 (2004, [3] W. Diffie and M. Hellman, New direcions in crypography, IEEE Trans. Inform. Theory, 22 (1976, [4] Y. Ding and P. Horser, Undeecable on-line password guessing aack, CM
8 972 Ren-Chiun Wang and un-ru Mo SIGOPS Operaing Sysems Reiew, 29 (4 (1995, [5] T.-F. Lee, T. Hwang and C.-L. Lin, Enhanced hree-pary encryped key exchange wihou serer public keys, Compuers & Securiy, 23 (2004, [6] S.-W. Lee, H.-S. im and.-y. Yoo, Efficien erifier-based key agreemen proocol for hree paries wihou serer s public key, pplied Mahemaics and Compuaion, 167 (2005, [7] C.-L. Lin, H.-M. Sun and T. Hwang, Three-pary encryped key exchange: aacks and a soluion, CM Operaing Sysems Reiew, 34 (4 (2000, [8] C.-L. Lin, H.-M. Sun, M. Seiner and T. Hwang, Three-pary encryped key exchange wihou serer public-keys, IEEE Communicaion Leers, 5 (12 (2001, [9] M. Seiner, G. Tsudik and M. Waidner, Refinemen and exension of encryped key exchange, CM Operaing Sysems Reiew, 29 (3 (1995, [10] H.-M. Sun,.-C. Chen and T. Hwang, Secure key agreemen proocols for hree-pary agains guessing aacks, The Journal of Sysems and Sofware, 75 (1-2 (2005, Receied: Sepember 24, 2005
An Efficient Deniable Authentication Protocol from Pairings to Protect Users Privacy
 1384 Chiang Mai J. Sci. 2014; 41(5.2 Chiang Mai J. Sci. 2014; 41(5.2 : 1384-1391 hp://epg.science.cmu.ac.h/ejournal/ Conribued Paper An Efficien Deniable Auhenicaion Proocol from Pairings o Proec Users
1384 Chiang Mai J. Sci. 2014; 41(5.2 Chiang Mai J. Sci. 2014; 41(5.2 : 1384-1391 hp://epg.science.cmu.ac.h/ejournal/ Conribued Paper An Efficien Deniable Auhenicaion Proocol from Pairings o Proec Users
Matrix Versions of Some Refinements of the Arithmetic-Geometric Mean Inequality
 Marix Versions of Some Refinemens of he Arihmeic-Geomeric Mean Inequaliy Bao Qi Feng and Andrew Tonge Absrac. We esablish marix versions of refinemens due o Alzer ], Carwrigh and Field 4], and Mercer 5]
Marix Versions of Some Refinemens of he Arihmeic-Geomeric Mean Inequaliy Bao Qi Feng and Andrew Tonge Absrac. We esablish marix versions of refinemens due o Alzer ], Carwrigh and Field 4], and Mercer 5]
Single-Pass-Based Heuristic Algorithms for Group Flexible Flow-shop Scheduling Problems
 Single-Pass-Based Heurisic Algorihms for Group Flexible Flow-shop Scheduling Problems PEI-YING HUANG, TZUNG-PEI HONG 2 and CHENG-YAN KAO, 3 Deparmen of Compuer Science and Informaion Engineering Naional
Single-Pass-Based Heurisic Algorihms for Group Flexible Flow-shop Scheduling Problems PEI-YING HUANG, TZUNG-PEI HONG 2 and CHENG-YAN KAO, 3 Deparmen of Compuer Science and Informaion Engineering Naional
Mathematical Theory and Modeling ISSN (Paper) ISSN (Online) Vol.2, No.4, 2012
 Soluion of Telegraph quaion by Modified of Double Sumudu Transform "lzaki Transform" Tarig. M. lzaki * man M. A. Hilal. Mahemaics Deparmen, Faculy of Sciences and Ars-Alkamil, King Abdulaziz Uniersiy,
Soluion of Telegraph quaion by Modified of Double Sumudu Transform "lzaki Transform" Tarig. M. lzaki * man M. A. Hilal. Mahemaics Deparmen, Faculy of Sciences and Ars-Alkamil, King Abdulaziz Uniersiy,
arxiv: v1 [math.ca] 15 Nov 2016
![arxiv: v1 [math.ca] 15 Nov 2016 arxiv: v1 [math.ca] 15 Nov 2016](/thumbs/90/102217337.jpg) arxiv:6.599v [mah.ca] 5 Nov 26 Counerexamples on Jumarie s hree basic fracional calculus formulae for non-differeniable coninuous funcions Cheng-shi Liu Deparmen of Mahemaics Norheas Peroleum Universiy
arxiv:6.599v [mah.ca] 5 Nov 26 Counerexamples on Jumarie s hree basic fracional calculus formulae for non-differeniable coninuous funcions Cheng-shi Liu Deparmen of Mahemaics Norheas Peroleum Universiy
An introduction to the theory of SDDP algorithm
 An inroducion o he heory of SDDP algorihm V. Leclère (ENPC) Augus 1, 2014 V. Leclère Inroducion o SDDP Augus 1, 2014 1 / 21 Inroducion Large scale sochasic problem are hard o solve. Two ways of aacking
An inroducion o he heory of SDDP algorihm V. Leclère (ENPC) Augus 1, 2014 V. Leclère Inroducion o SDDP Augus 1, 2014 1 / 21 Inroducion Large scale sochasic problem are hard o solve. Two ways of aacking
Chapter 2. First Order Scalar Equations
 Chaper. Firs Order Scalar Equaions We sar our sudy of differenial equaions in he same way he pioneers in his field did. We show paricular echniques o solve paricular ypes of firs order differenial equaions.
Chaper. Firs Order Scalar Equaions We sar our sudy of differenial equaions in he same way he pioneers in his field did. We show paricular echniques o solve paricular ypes of firs order differenial equaions.
A new flexible Weibull distribution
 Communicaions for Saisical Applicaions and Mehods 2016, Vol. 23, No. 5, 399 409 hp://dx.doi.org/10.5351/csam.2016.23.5.399 Prin ISSN 2287-7843 / Online ISSN 2383-4757 A new flexible Weibull disribuion
Communicaions for Saisical Applicaions and Mehods 2016, Vol. 23, No. 5, 399 409 hp://dx.doi.org/10.5351/csam.2016.23.5.399 Prin ISSN 2287-7843 / Online ISSN 2383-4757 A new flexible Weibull disribuion
On Two Integrability Methods of Improper Integrals
 Inernaional Journal of Mahemaics and Compuer Science, 13(218), no. 1, 45 5 M CS On Two Inegrabiliy Mehods of Improper Inegrals H. N. ÖZGEN Mahemaics Deparmen Faculy of Educaion Mersin Universiy, TR-33169
Inernaional Journal of Mahemaics and Compuer Science, 13(218), no. 1, 45 5 M CS On Two Inegrabiliy Mehods of Improper Inegrals H. N. ÖZGEN Mahemaics Deparmen Faculy of Educaion Mersin Universiy, TR-33169
Anonymity in Shared Symmetric Key Primitives
 Anonymiy in Shared Symmeric Key Primiives Gregory M. Zaverucha and Douglas R. Sinson David R. Cherion School of Compuer Science Universiy of Waerloo Waerloo ON, N2L 3G1, Canada {gzaveruc, dsinson}@uwaerloo.ca
Anonymiy in Shared Symmeric Key Primiives Gregory M. Zaverucha and Douglas R. Sinson David R. Cherion School of Compuer Science Universiy of Waerloo Waerloo ON, N2L 3G1, Canada {gzaveruc, dsinson}@uwaerloo.ca
Vehicle Arrival Models : Headway
 Chaper 12 Vehicle Arrival Models : Headway 12.1 Inroducion Modelling arrival of vehicle a secion of road is an imporan sep in raffic flow modelling. I has imporan applicaion in raffic flow simulaion where
Chaper 12 Vehicle Arrival Models : Headway 12.1 Inroducion Modelling arrival of vehicle a secion of road is an imporan sep in raffic flow modelling. I has imporan applicaion in raffic flow simulaion where
Fractional Method of Characteristics for Fractional Partial Differential Equations
 Fracional Mehod of Characerisics for Fracional Parial Differenial Equaions Guo-cheng Wu* Modern Teile Insiue, Donghua Universiy, 188 Yan-an ilu Road, Shanghai 51, PR China Absrac The mehod of characerisics
Fracional Mehod of Characerisics for Fracional Parial Differenial Equaions Guo-cheng Wu* Modern Teile Insiue, Donghua Universiy, 188 Yan-an ilu Road, Shanghai 51, PR China Absrac The mehod of characerisics
Inventory Control of Perishable Items in a Two-Echelon Supply Chain
 Journal of Indusrial Engineering, Universiy of ehran, Special Issue,, PP. 69-77 69 Invenory Conrol of Perishable Iems in a wo-echelon Supply Chain Fariborz Jolai *, Elmira Gheisariha and Farnaz Nojavan
Journal of Indusrial Engineering, Universiy of ehran, Special Issue,, PP. 69-77 69 Invenory Conrol of Perishable Iems in a wo-echelon Supply Chain Fariborz Jolai *, Elmira Gheisariha and Farnaz Nojavan
Random Walk with Anti-Correlated Steps
 Random Walk wih Ani-Correlaed Seps John Noga Dirk Wagner 2 Absrac We conjecure he expeced value of random walks wih ani-correlaed seps o be exacly. We suppor his conjecure wih 2 plausibiliy argumens and
Random Walk wih Ani-Correlaed Seps John Noga Dirk Wagner 2 Absrac We conjecure he expeced value of random walks wih ani-correlaed seps o be exacly. We suppor his conjecure wih 2 plausibiliy argumens and
Improved Approximate Solutions for Nonlinear Evolutions Equations in Mathematical Physics Using the Reduced Differential Transform Method
 Journal of Applied Mahemaics & Bioinformaics, vol., no., 01, 1-14 ISSN: 179-660 (prin), 179-699 (online) Scienpress Ld, 01 Improved Approimae Soluions for Nonlinear Evoluions Equaions in Mahemaical Physics
Journal of Applied Mahemaics & Bioinformaics, vol., no., 01, 1-14 ISSN: 179-660 (prin), 179-699 (online) Scienpress Ld, 01 Improved Approimae Soluions for Nonlinear Evoluions Equaions in Mahemaical Physics
Bifurcation Analysis of a Stage-Structured Prey-Predator System with Discrete and Continuous Delays
 Applied Mahemaics 4 59-64 hp://dx.doi.org/.46/am..4744 Published Online July (hp://www.scirp.org/ournal/am) Bifurcaion Analysis of a Sage-Srucured Prey-Predaor Sysem wih Discree and Coninuous Delays Shunyi
Applied Mahemaics 4 59-64 hp://dx.doi.org/.46/am..4744 Published Online July (hp://www.scirp.org/ournal/am) Bifurcaion Analysis of a Sage-Srucured Prey-Predaor Sysem wih Discree and Coninuous Delays Shunyi
Intermediate Macro In-Class Problems
 Inermediae Macro In-Class Problems Exploring Romer Model June 14, 016 Today we will explore he mechanisms of he simply Romer model by exploring how economies described by his model would reac o exogenous
Inermediae Macro In-Class Problems Exploring Romer Model June 14, 016 Today we will explore he mechanisms of he simply Romer model by exploring how economies described by his model would reac o exogenous
Internet Traffic Modeling for Efficient Network Research Management Prof. Zhili Sun, UniS Zhiyong Liu, CATR
 Inerne Traffic Modeling for Efficien Nework Research Managemen Prof. Zhili Sun, UniS Zhiyong Liu, CATR UK-China Science Bridge Workshop 13-14 December 2011, London Ouline Inroducion Background Classical
Inerne Traffic Modeling for Efficien Nework Research Managemen Prof. Zhili Sun, UniS Zhiyong Liu, CATR UK-China Science Bridge Workshop 13-14 December 2011, London Ouline Inroducion Background Classical
Bias in Conditional and Unconditional Fixed Effects Logit Estimation: a Correction * Tom Coupé
 Bias in Condiional and Uncondiional Fixed Effecs Logi Esimaion: a Correcion * Tom Coupé Economics Educaion and Research Consorium, Naional Universiy of Kyiv Mohyla Academy Address: Vul Voloska 10, 04070
Bias in Condiional and Uncondiional Fixed Effecs Logi Esimaion: a Correcion * Tom Coupé Economics Educaion and Research Consorium, Naional Universiy of Kyiv Mohyla Academy Address: Vul Voloska 10, 04070
Pade and Laguerre Approximations Applied. to the Active Queue Management Model. of Internet Protocol
 Applied Mahemaical Sciences, Vol. 7, 013, no. 16, 663-673 HIKARI Ld, www.m-hikari.com hp://dx.doi.org/10.1988/ams.013.39499 Pade and Laguerre Approximaions Applied o he Acive Queue Managemen Model of Inerne
Applied Mahemaical Sciences, Vol. 7, 013, no. 16, 663-673 HIKARI Ld, www.m-hikari.com hp://dx.doi.org/10.1988/ams.013.39499 Pade and Laguerre Approximaions Applied o he Acive Queue Managemen Model of Inerne
Evaluation of Mean Time to System Failure of a Repairable 3-out-of-4 System with Online Preventive Maintenance
 American Journal of Applied Mahemaics and Saisics, 0, Vol., No., 9- Available online a hp://pubs.sciepub.com/ajams/// Science and Educaion Publishing DOI:0.69/ajams--- Evaluaion of Mean Time o Sysem Failure
American Journal of Applied Mahemaics and Saisics, 0, Vol., No., 9- Available online a hp://pubs.sciepub.com/ajams/// Science and Educaion Publishing DOI:0.69/ajams--- Evaluaion of Mean Time o Sysem Failure
t is a basis for the solution space to this system, then the matrix having these solutions as columns, t x 1 t, x 2 t,... x n t x 2 t...
 Mah 228- Fri Mar 24 5.6 Marix exponenials and linear sysems: The analogy beween firs order sysems of linear differenial equaions (Chaper 5) and scalar linear differenial equaions (Chaper ) is much sronger
Mah 228- Fri Mar 24 5.6 Marix exponenials and linear sysems: The analogy beween firs order sysems of linear differenial equaions (Chaper 5) and scalar linear differenial equaions (Chaper ) is much sronger
Applying Genetic Algorithms for Inventory Lot-Sizing Problem with Supplier Selection under Storage Capacity Constraints
 IJCSI Inernaional Journal of Compuer Science Issues, Vol 9, Issue 1, No 1, January 2012 wwwijcsiorg 18 Applying Geneic Algorihms for Invenory Lo-Sizing Problem wih Supplier Selecion under Sorage Capaciy
IJCSI Inernaional Journal of Compuer Science Issues, Vol 9, Issue 1, No 1, January 2012 wwwijcsiorg 18 Applying Geneic Algorihms for Invenory Lo-Sizing Problem wih Supplier Selecion under Sorage Capaciy
THE NEW HEURISTIC GUESS AND DETERMINE ATTACK ON SNOW 2.0 STREAM CIPHER
 THE NEW HEURISTIC GUESS AND DETERMINE ATTACK ON SNOW 0 STREAM CIPHER Mohammad Sadegh Nemai Nia 1, Ali Payandeh 1, Faculy of Informaion, Telecommunicaion and Securiy Technologies, Malek-e- Ashar Universiy
THE NEW HEURISTIC GUESS AND DETERMINE ATTACK ON SNOW 0 STREAM CIPHER Mohammad Sadegh Nemai Nia 1, Ali Payandeh 1, Faculy of Informaion, Telecommunicaion and Securiy Technologies, Malek-e- Ashar Universiy
Stability and Bifurcation in a Neural Network Model with Two Delays
 Inernaional Mahemaical Forum, Vol. 6, 11, no. 35, 175-1731 Sabiliy and Bifurcaion in a Neural Nework Model wih Two Delays GuangPing Hu and XiaoLing Li School of Mahemaics and Physics, Nanjing Universiy
Inernaional Mahemaical Forum, Vol. 6, 11, no. 35, 175-1731 Sabiliy and Bifurcaion in a Neural Nework Model wih Two Delays GuangPing Hu and XiaoLing Li School of Mahemaics and Physics, Nanjing Universiy
A Note on the Equivalence of Fractional Relaxation Equations to Differential Equations with Varying Coefficients
 mahemaics Aricle A Noe on he Equivalence of Fracional Relaxaion Equaions o Differenial Equaions wih Varying Coefficiens Francesco Mainardi Deparmen of Physics and Asronomy, Universiy of Bologna, and he
mahemaics Aricle A Noe on he Equivalence of Fracional Relaxaion Equaions o Differenial Equaions wih Varying Coefficiens Francesco Mainardi Deparmen of Physics and Asronomy, Universiy of Bologna, and he
arxiv: v1 [cs.dc] 8 Mar 2012
![arxiv: v1 [cs.dc] 8 Mar 2012 arxiv: v1 [cs.dc] 8 Mar 2012](/thumbs/88/117681969.jpg) Consensus on Moving Neighborhood Model of Peerson Graph arxiv:.9v [cs.dc] 8 Mar Hannah Arend and Jorgensen Jos Absrac In his paper, we sudy he consensus problem of muliple agens on a kind of famous graph,
Consensus on Moving Neighborhood Model of Peerson Graph arxiv:.9v [cs.dc] 8 Mar Hannah Arend and Jorgensen Jos Absrac In his paper, we sudy he consensus problem of muliple agens on a kind of famous graph,
A Specification Test for Linear Dynamic Stochastic General Equilibrium Models
 Journal of Saisical and Economeric Mehods, vol.1, no.2, 2012, 65-70 ISSN: 2241-0384 (prin), 2241-0376 (online) Scienpress Ld, 2012 A Specificaion Tes for Linear Dynamic Sochasic General Equilibrium Models
Journal of Saisical and Economeric Mehods, vol.1, no.2, 2012, 65-70 ISSN: 2241-0384 (prin), 2241-0376 (online) Scienpress Ld, 2012 A Specificaion Tes for Linear Dynamic Sochasic General Equilibrium Models
Sliding Mode Controller for Unstable Systems
 S. SIVARAMAKRISHNAN e al., Sliding Mode Conroller for Unsable Sysems, Chem. Biochem. Eng. Q. 22 (1) 41 47 (28) 41 Sliding Mode Conroller for Unsable Sysems S. Sivaramakrishnan, A. K. Tangirala, and M.
S. SIVARAMAKRISHNAN e al., Sliding Mode Conroller for Unsable Sysems, Chem. Biochem. Eng. Q. 22 (1) 41 47 (28) 41 Sliding Mode Conroller for Unsable Sysems S. Sivaramakrishnan, A. K. Tangirala, and M.
Removing Useless Productions of a Context Free Grammar through Petri Net
 Journal of Compuer Science 3 (7): 494-498, 2007 ISSN 1549-3636 2007 Science Publicaions Removing Useless Producions of a Conex Free Grammar hrough Peri Ne Mansoor Al-A'ali and Ali A Khan Deparmen of Compuer
Journal of Compuer Science 3 (7): 494-498, 2007 ISSN 1549-3636 2007 Science Publicaions Removing Useless Producions of a Conex Free Grammar hrough Peri Ne Mansoor Al-A'ali and Ali A Khan Deparmen of Compuer
T L. t=1. Proof of Lemma 1. Using the marginal cost accounting in Equation(4) and standard arguments. t )+Π RB. t )+K 1(Q RB
 Elecronic Companion EC.1. Proofs of Technical Lemmas and Theorems LEMMA 1. Le C(RB) be he oal cos incurred by he RB policy. Then we have, T L E[C(RB)] 3 E[Z RB ]. (EC.1) Proof of Lemma 1. Using he marginal
Elecronic Companion EC.1. Proofs of Technical Lemmas and Theorems LEMMA 1. Le C(RB) be he oal cos incurred by he RB policy. Then we have, T L E[C(RB)] 3 E[Z RB ]. (EC.1) Proof of Lemma 1. Using he marginal
11!Hí MATHEMATICS : ERDŐS AND ULAM PROC. N. A. S. of decomposiion, properly speaking) conradics he possibiliy of defining a counably addiive real-valu
 ON EQUATIONS WITH SETS AS UNKNOWNS BY PAUL ERDŐS AND S. ULAM DEPARTMENT OF MATHEMATICS, UNIVERSITY OF COLORADO, BOULDER Communicaed May 27, 1968 We shall presen here a number of resuls in se heory concerning
ON EQUATIONS WITH SETS AS UNKNOWNS BY PAUL ERDŐS AND S. ULAM DEPARTMENT OF MATHEMATICS, UNIVERSITY OF COLORADO, BOULDER Communicaed May 27, 1968 We shall presen here a number of resuls in se heory concerning
Shiva Akhtarian MSc Student, Department of Computer Engineering and Information Technology, Payame Noor University, Iran
 Curren Trends in Technology and Science ISSN : 79-055 8hSASTech 04 Symposium on Advances in Science & Technology-Commission-IV Mashhad, Iran A New for Sofware Reliabiliy Evaluaion Based on NHPP wih Imperfec
Curren Trends in Technology and Science ISSN : 79-055 8hSASTech 04 Symposium on Advances in Science & Technology-Commission-IV Mashhad, Iran A New for Sofware Reliabiliy Evaluaion Based on NHPP wih Imperfec
PENALIZED LEAST SQUARES AND PENALIZED LIKELIHOOD
 PENALIZED LEAST SQUARES AND PENALIZED LIKELIHOOD HAN XIAO 1. Penalized Leas Squares Lasso solves he following opimizaion problem, ˆβ lasso = arg max β R p+1 1 N y i β 0 N x ij β j β j (1.1) for some 0.
PENALIZED LEAST SQUARES AND PENALIZED LIKELIHOOD HAN XIAO 1. Penalized Leas Squares Lasso solves he following opimizaion problem, ˆβ lasso = arg max β R p+1 1 N y i β 0 N x ij β j β j (1.1) for some 0.
The Asymptotic Behavior of Nonoscillatory Solutions of Some Nonlinear Dynamic Equations on Time Scales
 Advances in Dynamical Sysems and Applicaions. ISSN 0973-5321 Volume 1 Number 1 (2006, pp. 103 112 c Research India Publicaions hp://www.ripublicaion.com/adsa.hm The Asympoic Behavior of Nonoscillaory Soluions
Advances in Dynamical Sysems and Applicaions. ISSN 0973-5321 Volume 1 Number 1 (2006, pp. 103 112 c Research India Publicaions hp://www.ripublicaion.com/adsa.hm The Asympoic Behavior of Nonoscillaory Soluions
Solution of Integro-Differential Equations by Using ELzaki Transform
 Global Journal of Mahemaical Sciences: Theory and Pracical. Volume, Number (), pp. - Inernaional Research Publicaion House hp://www.irphouse.com Soluion of Inegro-Differenial Equaions by Using ELzaki Transform
Global Journal of Mahemaical Sciences: Theory and Pracical. Volume, Number (), pp. - Inernaional Research Publicaion House hp://www.irphouse.com Soluion of Inegro-Differenial Equaions by Using ELzaki Transform
Spring Ammar Abu-Hudrouss Islamic University Gaza
 Chaper 7 Reed-Solomon Code Spring 9 Ammar Abu-Hudrouss Islamic Universiy Gaza ١ Inroducion A Reed Solomon code is a special case of a BCH code in which he lengh of he code is one less han he size of he
Chaper 7 Reed-Solomon Code Spring 9 Ammar Abu-Hudrouss Islamic Universiy Gaza ١ Inroducion A Reed Solomon code is a special case of a BCH code in which he lengh of he code is one less han he size of he
Application of a Stochastic-Fuzzy Approach to Modeling Optimal Discrete Time Dynamical Systems by Using Large Scale Data Processing
 Applicaion of a Sochasic-Fuzzy Approach o Modeling Opimal Discree Time Dynamical Sysems by Using Large Scale Daa Processing AA WALASZE-BABISZEWSA Deparmen of Compuer Engineering Opole Universiy of Technology
Applicaion of a Sochasic-Fuzzy Approach o Modeling Opimal Discree Time Dynamical Sysems by Using Large Scale Daa Processing AA WALASZE-BABISZEWSA Deparmen of Compuer Engineering Opole Universiy of Technology
Technical Report Doc ID: TR March-2013 (Last revision: 23-February-2016) On formulating quadratic functions in optimization models.
 Technical Repor Doc ID: TR--203 06-March-203 (Las revision: 23-Februar-206) On formulaing quadraic funcions in opimizaion models. Auhor: Erling D. Andersen Convex quadraic consrains quie frequenl appear
Technical Repor Doc ID: TR--203 06-March-203 (Las revision: 23-Februar-206) On formulaing quadraic funcions in opimizaion models. Auhor: Erling D. Andersen Convex quadraic consrains quie frequenl appear
LAB # 2 - Equilibrium (static)
 AB # - Equilibrium (saic) Inroducion Isaac Newon's conribuion o physics was o recognize ha despie he seeming compleiy of he Unierse, he moion of is pars is guided by surprisingly simple aws. Newon's inspiraion
AB # - Equilibrium (saic) Inroducion Isaac Newon's conribuion o physics was o recognize ha despie he seeming compleiy of he Unierse, he moion of is pars is guided by surprisingly simple aws. Newon's inspiraion
THE 2-BODY PROBLEM. FIGURE 1. A pair of ellipses sharing a common focus. (c,b) c+a ROBERT J. VANDERBEI
 THE 2-BODY PROBLEM ROBERT J. VANDERBEI ABSTRACT. In his shor noe, we show ha a pair of ellipses wih a common focus is a soluion o he 2-body problem. INTRODUCTION. Solving he 2-body problem from scrach
THE 2-BODY PROBLEM ROBERT J. VANDERBEI ABSTRACT. In his shor noe, we show ha a pair of ellipses wih a common focus is a soluion o he 2-body problem. INTRODUCTION. Solving he 2-body problem from scrach
Physics 235 Chapter 2. Chapter 2 Newtonian Mechanics Single Particle
 Chaper 2 Newonian Mechanics Single Paricle In his Chaper we will review wha Newon s laws of mechanics ell us abou he moion of a single paricle. Newon s laws are only valid in suiable reference frames,
Chaper 2 Newonian Mechanics Single Paricle In his Chaper we will review wha Newon s laws of mechanics ell us abou he moion of a single paricle. Newon s laws are only valid in suiable reference frames,
A DELAY-DEPENDENT STABILITY CRITERIA FOR T-S FUZZY SYSTEM WITH TIME-DELAYS
 A DELAY-DEPENDENT STABILITY CRITERIA FOR T-S FUZZY SYSTEM WITH TIME-DELAYS Xinping Guan ;1 Fenglei Li Cailian Chen Insiue of Elecrical Engineering, Yanshan Universiy, Qinhuangdao, 066004, China. Deparmen
A DELAY-DEPENDENT STABILITY CRITERIA FOR T-S FUZZY SYSTEM WITH TIME-DELAYS Xinping Guan ;1 Fenglei Li Cailian Chen Insiue of Elecrical Engineering, Yanshan Universiy, Qinhuangdao, 066004, China. Deparmen
Solving a System of Nonlinear Functional Equations Using Revised New Iterative Method
 Solving a Sysem of Nonlinear Funcional Equaions Using Revised New Ieraive Mehod Sachin Bhalekar and Varsha Dafardar-Gejji Absrac In he presen paper, we presen a modificaion of he New Ieraive Mehod (NIM
Solving a Sysem of Nonlinear Funcional Equaions Using Revised New Ieraive Mehod Sachin Bhalekar and Varsha Dafardar-Gejji Absrac In he presen paper, we presen a modificaion of he New Ieraive Mehod (NIM
Final Spring 2007
 .615 Final Spring 7 Overview The purpose of he final exam is o calculae he MHD β limi in a high-bea oroidal okamak agains he dangerous n = 1 exernal ballooning-kink mode. Effecively, his corresponds o
.615 Final Spring 7 Overview The purpose of he final exam is o calculae he MHD β limi in a high-bea oroidal okamak agains he dangerous n = 1 exernal ballooning-kink mode. Effecively, his corresponds o
Essential Maps and Coincidence Principles for General Classes of Maps
 Filoma 31:11 (2017), 3553 3558 hps://doi.org/10.2298/fil1711553o Published by Faculy of Sciences Mahemaics, Universiy of Niš, Serbia Available a: hp://www.pmf.ni.ac.rs/filoma Essenial Maps Coincidence
Filoma 31:11 (2017), 3553 3558 hps://doi.org/10.2298/fil1711553o Published by Faculy of Sciences Mahemaics, Universiy of Niš, Serbia Available a: hp://www.pmf.ni.ac.rs/filoma Essenial Maps Coincidence
UNIVERSITY OF CALIFORNIA College of Engineering Department of Electrical Engineering and Computer Sciences EECS 121 FINAL EXAM
 Name: UNIVERSIY OF CALIFORNIA College of Engineering Deparmen of Elecrical Engineering and Compuer Sciences Professor David se EECS 121 FINAL EXAM 21 May 1997, 5:00-8:00 p.m. Please wrie answers on blank
Name: UNIVERSIY OF CALIFORNIA College of Engineering Deparmen of Elecrical Engineering and Compuer Sciences Professor David se EECS 121 FINAL EXAM 21 May 1997, 5:00-8:00 p.m. Please wrie answers on blank
Cryptanalysis of Reduced NORX initially discussed at ASK 2016
 Crypanalysis of Reduced NORX iniiy discussed a ASK 2016 Nasour Bagheri (SRTTU, Iran), Tao Huang (NTU, Singaopre), Keing Jia (Tsinghua Univ., Sae Key Lab, China), Florian Mendel (TUGraz, Ausria), Yu Sasaki
Crypanalysis of Reduced NORX iniiy discussed a ASK 2016 Nasour Bagheri (SRTTU, Iran), Tao Huang (NTU, Singaopre), Keing Jia (Tsinghua Univ., Sae Key Lab, China), Florian Mendel (TUGraz, Ausria), Yu Sasaki
SUPPLEMENTARY INFORMATION
 SUPPLEMENTARY INFORMATION DOI: 0.038/NCLIMATE893 Temporal resoluion and DICE * Supplemenal Informaion Alex L. Maren and Sephen C. Newbold Naional Cener for Environmenal Economics, US Environmenal Proecion
SUPPLEMENTARY INFORMATION DOI: 0.038/NCLIMATE893 Temporal resoluion and DICE * Supplemenal Informaion Alex L. Maren and Sephen C. Newbold Naional Cener for Environmenal Economics, US Environmenal Proecion
Undetermined coefficients for local fractional differential equations
 Available online a www.isr-publicaions.com/jmcs J. Mah. Compuer Sci. 16 (2016), 140 146 Research Aricle Undeermined coefficiens for local fracional differenial equaions Roshdi Khalil a,, Mohammed Al Horani
Available online a www.isr-publicaions.com/jmcs J. Mah. Compuer Sci. 16 (2016), 140 146 Research Aricle Undeermined coefficiens for local fracional differenial equaions Roshdi Khalil a,, Mohammed Al Horani
Amit Mehra. Indian School of Business, Hyderabad, INDIA Vijay Mookerjee
 RESEARCH ARTICLE HUMAN CAPITAL DEVELOPMENT FOR PROGRAMMERS USING OPEN SOURCE SOFTWARE Ami Mehra Indian Shool of Business, Hyderabad, INDIA {Ami_Mehra@isb.edu} Vijay Mookerjee Shool of Managemen, Uniersiy
RESEARCH ARTICLE HUMAN CAPITAL DEVELOPMENT FOR PROGRAMMERS USING OPEN SOURCE SOFTWARE Ami Mehra Indian Shool of Business, Hyderabad, INDIA {Ami_Mehra@isb.edu} Vijay Mookerjee Shool of Managemen, Uniersiy
Cryptanalysis of RAKAPOSHI Stream Cipher
 Crypanalysis of RAKAPOSHI Sream Cipher Lin Ding, Jie Guan Zhengzhou Informaion Science and Technology Insiue, China E-mail: dinglin_cipher@63.com; guanie7@63.com Absrac. RAKAPOSHI is a hardware oriened
Crypanalysis of RAKAPOSHI Sream Cipher Lin Ding, Jie Guan Zhengzhou Informaion Science and Technology Insiue, China E-mail: dinglin_cipher@63.com; guanie7@63.com Absrac. RAKAPOSHI is a hardware oriened
Solutions for Assignment 2
 Faculy of rs and Science Universiy of Torono CSC 358 - Inroducion o Compuer Neworks, Winer 218 Soluions for ssignmen 2 Quesion 1 (2 Poins): Go-ack n RQ In his quesion, we review how Go-ack n RQ can be
Faculy of rs and Science Universiy of Torono CSC 358 - Inroducion o Compuer Neworks, Winer 218 Soluions for ssignmen 2 Quesion 1 (2 Poins): Go-ack n RQ In his quesion, we review how Go-ack n RQ can be
di Bernardo, M. (1995). A purely adaptive controller to synchronize and control chaotic systems.
 di ernardo, M. (995). A purely adapive conroller o synchronize and conrol chaoic sysems. hps://doi.org/.6/375-96(96)8-x Early version, also known as pre-prin Link o published version (if available):.6/375-96(96)8-x
di ernardo, M. (995). A purely adapive conroller o synchronize and conrol chaoic sysems. hps://doi.org/.6/375-96(96)8-x Early version, also known as pre-prin Link o published version (if available):.6/375-96(96)8-x
THE GENERALIZED PASCAL MATRIX VIA THE GENERALIZED FIBONACCI MATRIX AND THE GENERALIZED PELL MATRIX
 J Korean Mah Soc 45 008, No, pp 479 49 THE GENERALIZED PASCAL MATRIX VIA THE GENERALIZED FIBONACCI MATRIX AND THE GENERALIZED PELL MATRIX Gwang-yeon Lee and Seong-Hoon Cho Reprined from he Journal of he
J Korean Mah Soc 45 008, No, pp 479 49 THE GENERALIZED PASCAL MATRIX VIA THE GENERALIZED FIBONACCI MATRIX AND THE GENERALIZED PELL MATRIX Gwang-yeon Lee and Seong-Hoon Cho Reprined from he Journal of he
arxiv: v1 [math.pr] 6 Oct 2008
![arxiv: v1 [math.pr] 6 Oct 2008 arxiv: v1 [math.pr] 6 Oct 2008](/thumbs/78/77081458.jpg) MEASURIN THE NON-STOPPIN TIMENESS OF ENDS OF PREVISIBLE SETS arxiv:8.59v [mah.pr] 6 Oc 8 JU-YI YEN ),) AND MARC YOR 3),4) Absrac. In his paper, we propose several measuremens of he nonsopping imeness of
MEASURIN THE NON-STOPPIN TIMENESS OF ENDS OF PREVISIBLE SETS arxiv:8.59v [mah.pr] 6 Oc 8 JU-YI YEN ),) AND MARC YOR 3),4) Absrac. In his paper, we propose several measuremens of he nonsopping imeness of
Roughness in ordered Semigroups. Muhammad Shabir and Shumaila Irshad
 World Applied Sciences Journal 22 (Special Issue of Applied Mah): 84-105, 2013 ISSN 1818-4952 IDOSI Publicaions, 2013 DOI: 105829/idosiwasj22am102013 Roughness in ordered Semigroups Muhammad Shabir and
World Applied Sciences Journal 22 (Special Issue of Applied Mah): 84-105, 2013 ISSN 1818-4952 IDOSI Publicaions, 2013 DOI: 105829/idosiwasj22am102013 Roughness in ordered Semigroups Muhammad Shabir and
Brock University Physics 1P21/1P91 Fall 2013 Dr. D Agostino. Solutions for Tutorial 3: Chapter 2, Motion in One Dimension
 Brock Uniersiy Physics 1P21/1P91 Fall 2013 Dr. D Agosino Soluions for Tuorial 3: Chaper 2, Moion in One Dimension The goals of his uorial are: undersand posiion-ime graphs, elociy-ime graphs, and heir
Brock Uniersiy Physics 1P21/1P91 Fall 2013 Dr. D Agosino Soluions for Tuorial 3: Chaper 2, Moion in One Dimension The goals of his uorial are: undersand posiion-ime graphs, elociy-ime graphs, and heir
Existence of positive solution for a third-order three-point BVP with sign-changing Green s function
 Elecronic Journal of Qualiaive Theory of Differenial Equaions 13, No. 3, 1-11; hp://www.mah.u-szeged.hu/ejqde/ Exisence of posiive soluion for a hird-order hree-poin BVP wih sign-changing Green s funcion
Elecronic Journal of Qualiaive Theory of Differenial Equaions 13, No. 3, 1-11; hp://www.mah.u-szeged.hu/ejqde/ Exisence of posiive soluion for a hird-order hree-poin BVP wih sign-changing Green s funcion
Math-Net.Ru All Russian mathematical portal
 Mah-NeRu All Russian mahemaical poral Roman Popovych, On elemens of high order in general finie fields, Algebra Discree Mah, 204, Volume 8, Issue 2, 295 300 Use of he all-russian mahemaical poral Mah-NeRu
Mah-NeRu All Russian mahemaical poral Roman Popovych, On elemens of high order in general finie fields, Algebra Discree Mah, 204, Volume 8, Issue 2, 295 300 Use of he all-russian mahemaical poral Mah-NeRu
Theoretical Computer Science. Approximately optimal trees for group key management with batch updates
 Theoreical Compuer Science 410 2009) 101 1021 Conens liss available a ScienceDirec Theoreical Compuer Science journal homepage: www.elsevier.com/locae/cs Approximaely opimal rees for group key managemen
Theoreical Compuer Science 410 2009) 101 1021 Conens liss available a ScienceDirec Theoreical Compuer Science journal homepage: www.elsevier.com/locae/cs Approximaely opimal rees for group key managemen
IMPLICIT-EXPLICIT SCHEME FOR THE ALLEN-CAHN EQUATION PRESERVES THE MAXIMUM PRINCIPLE * 1. Introduction
 Journal of Compuaional Mahemaics Vol.34, No.5, 206, 45 46. hp://www.global-sci.org/jcm doi:0.4208/jcm.603-m204-007 IMPLICIT-EXPLICIT SCHEME FOR THE ALLEN-CAHN EQUATION PRESERVES THE MAXIMUM PRINCIPLE *
Journal of Compuaional Mahemaics Vol.34, No.5, 206, 45 46. hp://www.global-sci.org/jcm doi:0.4208/jcm.603-m204-007 IMPLICIT-EXPLICIT SCHEME FOR THE ALLEN-CAHN EQUATION PRESERVES THE MAXIMUM PRINCIPLE *
3.1.3 INTRODUCTION TO DYNAMIC OPTIMIZATION: DISCRETE TIME PROBLEMS. A. The Hamiltonian and First-Order Conditions in a Finite Time Horizon
 3..3 INRODUCION O DYNAMIC OPIMIZAION: DISCREE IME PROBLEMS A. he Hamilonian and Firs-Order Condiions in a Finie ime Horizon Define a new funcion, he Hamilonian funcion, H. H he change in he oal value of
3..3 INRODUCION O DYNAMIC OPIMIZAION: DISCREE IME PROBLEMS A. he Hamilonian and Firs-Order Condiions in a Finie ime Horizon Define a new funcion, he Hamilonian funcion, H. H he change in he oal value of
Single and Double Pendulum Models
 Single and Double Pendulum Models Mah 596 Projec Summary Spring 2016 Jarod Har 1 Overview Differen ypes of pendulums are used o model many phenomena in various disciplines. In paricular, single and double
Single and Double Pendulum Models Mah 596 Projec Summary Spring 2016 Jarod Har 1 Overview Differen ypes of pendulums are used o model many phenomena in various disciplines. In paricular, single and double
INVERSE RESPONSE COMPENSATION BY ESTIMATING PARAMETERS OF A PROCESS COMPRISING OF TWO FIRST ORDER SYSTEMS
 Inernaional Journal of Informaion Technology and nowledge Managemen July-December 0, Volume 5, No., pp. 433-438 INVERSE RESPONSE COMPENSATION BY ESTIMATING PARAMETERS OF A PROCESS COMPRISING OF TWO FIRST
Inernaional Journal of Informaion Technology and nowledge Managemen July-December 0, Volume 5, No., pp. 433-438 INVERSE RESPONSE COMPENSATION BY ESTIMATING PARAMETERS OF A PROCESS COMPRISING OF TWO FIRST
Robust estimation based on the first- and third-moment restrictions of the power transformation model
 h Inernaional Congress on Modelling and Simulaion, Adelaide, Ausralia, 6 December 3 www.mssanz.org.au/modsim3 Robus esimaion based on he firs- and hird-momen resricions of he power ransformaion Nawaa,
h Inernaional Congress on Modelling and Simulaion, Adelaide, Ausralia, 6 December 3 www.mssanz.org.au/modsim3 Robus esimaion based on he firs- and hird-momen resricions of he power ransformaion Nawaa,
An Iterative Method for Solving Two Special Cases of Nonlinear PDEs
 Conemporary Engineering Sciences, Vol. 10, 2017, no. 11, 55-553 HIKARI Ld, www.m-hikari.com hps://doi.org/10.12988/ces.2017.7651 An Ieraive Mehod for Solving Two Special Cases of Nonlinear PDEs Carlos
Conemporary Engineering Sciences, Vol. 10, 2017, no. 11, 55-553 HIKARI Ld, www.m-hikari.com hps://doi.org/10.12988/ces.2017.7651 An Ieraive Mehod for Solving Two Special Cases of Nonlinear PDEs Carlos
Application of He s Variational Iteration Method for Solving Seventh Order Sawada-Kotera Equations
 Applied Mahemaical Sciences, Vol. 2, 28, no. 1, 471-477 Applicaion of He s Variaional Ieraion Mehod for Solving Sevenh Order Sawada-Koera Equaions Hossein Jafari a,1, Allahbakhsh Yazdani a, Javad Vahidi
Applied Mahemaical Sciences, Vol. 2, 28, no. 1, 471-477 Applicaion of He s Variaional Ieraion Mehod for Solving Sevenh Order Sawada-Koera Equaions Hossein Jafari a,1, Allahbakhsh Yazdani a, Javad Vahidi
dt = C exp (3 ln t 4 ). t 4 W = C exp ( ln(4 t) 3) = C(4 t) 3.
 Mah Rahman Exam Review Soluions () Consider he IVP: ( 4)y 3y + 4y = ; y(3) = 0, y (3) =. (a) Please deermine he longes inerval for which he IVP is guaraneed o have a unique soluion. Soluion: The disconinuiies
Mah Rahman Exam Review Soluions () Consider he IVP: ( 4)y 3y + 4y = ; y(3) = 0, y (3) =. (a) Please deermine he longes inerval for which he IVP is guaraneed o have a unique soluion. Soluion: The disconinuiies
IMPROVED HYPERBOLIC FUNCTION METHOD AND EXACT SOLUTIONS FOR VARIABLE COEFFICIENT BENJAMIN-BONA-MAHONY-BURGERS EQUATION
 THERMAL SCIENCE, Year 015, Vol. 19, No. 4, pp. 1183-1187 1183 IMPROVED HYPERBOLIC FUNCTION METHOD AND EXACT SOLUTIONS FOR VARIABLE COEFFICIENT BENJAMIN-BONA-MAHONY-BURGERS EQUATION by Hong-Cai MA a,b*,
THERMAL SCIENCE, Year 015, Vol. 19, No. 4, pp. 1183-1187 1183 IMPROVED HYPERBOLIC FUNCTION METHOD AND EXACT SOLUTIONS FOR VARIABLE COEFFICIENT BENJAMIN-BONA-MAHONY-BURGERS EQUATION by Hong-Cai MA a,b*,
Pair-wise Network Topology Authenticated Hybrid Cryptographic Keys for Wireless Sensor Networks using Vector Algebra
 Pair-wise Newor Topology Auhenicaed Hybrid Crypographic Keys for Wireless Sensor Newors using Vecor Algebra Marco Pugliese Forunao Sanucci Cener of Excellence DEWS Universiy of L Aquila L Aquila, ITALY
Pair-wise Newor Topology Auhenicaed Hybrid Crypographic Keys for Wireless Sensor Newors using Vecor Algebra Marco Pugliese Forunao Sanucci Cener of Excellence DEWS Universiy of L Aquila L Aquila, ITALY
Generalized Chebyshev polynomials
 Generalized Chebyshev polynomials Clemene Cesarano Faculy of Engineering, Inernaional Telemaic Universiy UNINETTUNO Corso Viorio Emanuele II, 39 86 Roma, Ialy email: c.cesarano@unineunouniversiy.ne ABSTRACT
Generalized Chebyshev polynomials Clemene Cesarano Faculy of Engineering, Inernaional Telemaic Universiy UNINETTUNO Corso Viorio Emanuele II, 39 86 Roma, Ialy email: c.cesarano@unineunouniversiy.ne ABSTRACT
EXERCISES FOR SECTION 1.5
 1.5 Exisence and Uniqueness of Soluions 43 20. 1 v c 21. 1 v c 1 2 4 6 8 10 1 2 2 4 6 8 10 Graph of approximae soluion obained using Euler s mehod wih = 0.1. Graph of approximae soluion obained using Euler
1.5 Exisence and Uniqueness of Soluions 43 20. 1 v c 21. 1 v c 1 2 4 6 8 10 1 2 2 4 6 8 10 Graph of approximae soluion obained using Euler s mehod wih = 0.1. Graph of approximae soluion obained using Euler
Solutions for homework 12
 y Soluions for homework Secion Nonlinear sysems: The linearizaion of a nonlinear sysem Consider he sysem y y y y y (i) Skech he nullclines Use a disincive marking for each nullcline so hey can be disinguished
y Soluions for homework Secion Nonlinear sysems: The linearizaion of a nonlinear sysem Consider he sysem y y y y y (i) Skech he nullclines Use a disincive marking for each nullcline so hey can be disinguished
Written HW 9 Sol. CS 188 Fall Introduction to Artificial Intelligence
 CS 188 Fall 2018 Inroducion o Arificial Inelligence Wrien HW 9 Sol. Self-assessmen due: Tuesday 11/13/2018 a 11:59pm (submi via Gradescope) For he self assessmen, fill in he self assessmen boxes in your
CS 188 Fall 2018 Inroducion o Arificial Inelligence Wrien HW 9 Sol. Self-assessmen due: Tuesday 11/13/2018 a 11:59pm (submi via Gradescope) For he self assessmen, fill in he self assessmen boxes in your
ERROR LOCATING CODES AND EXTENDED HAMMING CODE. Pankaj Kumar Das. 1. Introduction and preliminaries
 MATEMATIČKI VESNIK MATEMATIQKI VESNIK 70, 1 (2018), 89 94 March 2018 research paper originalni nauqni rad ERROR LOCATING CODES AND EXTENDED HAMMING CODE Pankaj Kumar Das Absrac. Error-locaing codes, firs
MATEMATIČKI VESNIK MATEMATIQKI VESNIK 70, 1 (2018), 89 94 March 2018 research paper originalni nauqni rad ERROR LOCATING CODES AND EXTENDED HAMMING CODE Pankaj Kumar Das Absrac. Error-locaing codes, firs
Li An-Ping. Beijing , P.R.China
 A NEW TYPE OF CIPHER: DICING_CSB Li An-Ping Beijing 100085, P.R.China apli0001@sina.com Absrac: In his paper, we will propose a new ype of cipher named DICING_CSB, which come from our previous a synchronous
A NEW TYPE OF CIPHER: DICING_CSB Li An-Ping Beijing 100085, P.R.China apli0001@sina.com Absrac: In his paper, we will propose a new ype of cipher named DICING_CSB, which come from our previous a synchronous
NEWTON S SECOND LAW OF MOTION
 Course and Secion Dae Names NEWTON S SECOND LAW OF MOTION The acceleraion of an objec is defined as he rae of change of elociy. If he elociy changes by an amoun in a ime, hen he aerage acceleraion during
Course and Secion Dae Names NEWTON S SECOND LAW OF MOTION The acceleraion of an objec is defined as he rae of change of elociy. If he elociy changes by an amoun in a ime, hen he aerage acceleraion during
Ann. Funct. Anal. 2 (2011), no. 2, A nnals of F unctional A nalysis ISSN: (electronic) URL:
 Ann. Func. Anal. 2 2011, no. 2, 34 41 A nnals of F uncional A nalysis ISSN: 2008-8752 elecronic URL: www.emis.de/journals/afa/ CLASSIFICAION OF POSIIVE SOLUIONS OF NONLINEAR SYSEMS OF VOLERRA INEGRAL EQUAIONS
Ann. Func. Anal. 2 2011, no. 2, 34 41 A nnals of F uncional A nalysis ISSN: 2008-8752 elecronic URL: www.emis.de/journals/afa/ CLASSIFICAION OF POSIIVE SOLUIONS OF NONLINEAR SYSEMS OF VOLERRA INEGRAL EQUAIONS
A Note on Superlinear Ambrosetti-Prodi Type Problem in a Ball
 A Noe on Superlinear Ambrosei-Prodi Type Problem in a Ball by P. N. Srikanh 1, Sanjiban Sanra 2 Absrac Using a careful analysis of he Morse Indices of he soluions obained by using he Mounain Pass Theorem
A Noe on Superlinear Ambrosei-Prodi Type Problem in a Ball by P. N. Srikanh 1, Sanjiban Sanra 2 Absrac Using a careful analysis of he Morse Indices of he soluions obained by using he Mounain Pass Theorem
Econ107 Applied Econometrics Topic 7: Multicollinearity (Studenmund, Chapter 8)
 I. Definiions and Problems A. Perfec Mulicollineariy Econ7 Applied Economerics Topic 7: Mulicollineariy (Sudenmund, Chaper 8) Definiion: Perfec mulicollineariy exiss in a following K-variable regression
I. Definiions and Problems A. Perfec Mulicollineariy Econ7 Applied Economerics Topic 7: Mulicollineariy (Sudenmund, Chaper 8) Definiion: Perfec mulicollineariy exiss in a following K-variable regression
23.5. Half-Range Series. Introduction. Prerequisites. Learning Outcomes
 Half-Range Series 2.5 Inroducion In his Secion we address he following problem: Can we find a Fourier series expansion of a funcion defined over a finie inerval? Of course we recognise ha such a funcion
Half-Range Series 2.5 Inroducion In his Secion we address he following problem: Can we find a Fourier series expansion of a funcion defined over a finie inerval? Of course we recognise ha such a funcion
On the Infinitude of Covering Systems with Least Modulus Equal to 2
 Annals of Pure and Applied Mahemaics Vol. 4, No. 2, 207, 307-32 ISSN: 2279-087X (P), 2279-0888(online) Published on 23 Sepember 207 www.researchmahsci.org DOI: hp://dx.doi.org/0.22457/apam.v4n2a3 Annals
Annals of Pure and Applied Mahemaics Vol. 4, No. 2, 207, 307-32 ISSN: 2279-087X (P), 2279-0888(online) Published on 23 Sepember 207 www.researchmahsci.org DOI: hp://dx.doi.org/0.22457/apam.v4n2a3 Annals
EE100 Lab 3 Experiment Guide: RC Circuits
 I. Inroducion EE100 Lab 3 Experimen Guide: A. apaciors A capacior is a passive elecronic componen ha sores energy in he form of an elecrosaic field. The uni of capaciance is he farad (coulomb/vol). Pracical
I. Inroducion EE100 Lab 3 Experimen Guide: A. apaciors A capacior is a passive elecronic componen ha sores energy in he form of an elecrosaic field. The uni of capaciance is he farad (coulomb/vol). Pracical
Unsteady Flow Problems
 School of Mechanical Aerospace and Civil Engineering Unseady Flow Problems T. J. Craf George Begg Building, C41 TPFE MSc CFD-1 Reading: J. Ferziger, M. Peric, Compuaional Mehods for Fluid Dynamics H.K.
School of Mechanical Aerospace and Civil Engineering Unseady Flow Problems T. J. Craf George Begg Building, C41 TPFE MSc CFD-1 Reading: J. Ferziger, M. Peric, Compuaional Mehods for Fluid Dynamics H.K.
Block Diagram of a DCS in 411
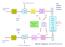 Informaion source Forma A/D From oher sources Pulse modu. Muliplex Bandpass modu. X M h: channel impulse response m i g i s i Digial inpu Digial oupu iming and synchronizaion Digial baseband/ bandpass
Informaion source Forma A/D From oher sources Pulse modu. Muliplex Bandpass modu. X M h: channel impulse response m i g i s i Digial inpu Digial oupu iming and synchronizaion Digial baseband/ bandpass
BBP-type formulas, in general bases, for arctangents of real numbers
 Noes on Number Theory and Discree Mahemaics Vol. 19, 13, No. 3, 33 54 BBP-ype formulas, in general bases, for arcangens of real numbers Kunle Adegoke 1 and Olawanle Layeni 2 1 Deparmen of Physics, Obafemi
Noes on Number Theory and Discree Mahemaics Vol. 19, 13, No. 3, 33 54 BBP-ype formulas, in general bases, for arcangens of real numbers Kunle Adegoke 1 and Olawanle Layeni 2 1 Deparmen of Physics, Obafemi
Logic in computer science
 Logic in compuer science Logic plays an imporan role in compuer science Logic is ofen called he calculus of compuer science Logic plays a similar role in compuer science o ha played by calculus in he physical
Logic in compuer science Logic plays an imporan role in compuer science Logic is ofen called he calculus of compuer science Logic plays a similar role in compuer science o ha played by calculus in he physical
Bernoulli numbers. Francesco Chiatti, Matteo Pintonello. December 5, 2016
 UNIVERSITÁ DEGLI STUDI DI PADOVA, DIPARTIMENTO DI MATEMATICA TULLIO LEVI-CIVITA Bernoulli numbers Francesco Chiai, Maeo Pinonello December 5, 206 During las lessons we have proved he Las Ferma Theorem
UNIVERSITÁ DEGLI STUDI DI PADOVA, DIPARTIMENTO DI MATEMATICA TULLIO LEVI-CIVITA Bernoulli numbers Francesco Chiai, Maeo Pinonello December 5, 206 During las lessons we have proved he Las Ferma Theorem
ACE 562 Fall Lecture 5: The Simple Linear Regression Model: Sampling Properties of the Least Squares Estimators. by Professor Scott H.
 ACE 56 Fall 005 Lecure 5: he Simple Linear Regression Model: Sampling Properies of he Leas Squares Esimaors by Professor Sco H. Irwin Required Reading: Griffihs, Hill and Judge. "Inference in he Simple
ACE 56 Fall 005 Lecure 5: he Simple Linear Regression Model: Sampling Properies of he Leas Squares Esimaors by Professor Sco H. Irwin Required Reading: Griffihs, Hill and Judge. "Inference in he Simple
On Gronwall s Type Integral Inequalities with Singular Kernels
 Filoma 31:4 (217), 141 149 DOI 1.2298/FIL17441A Published by Faculy of Sciences and Mahemaics, Universiy of Niš, Serbia Available a: hp://www.pmf.ni.ac.rs/filoma On Gronwall s Type Inegral Inequaliies
Filoma 31:4 (217), 141 149 DOI 1.2298/FIL17441A Published by Faculy of Sciences and Mahemaics, Universiy of Niš, Serbia Available a: hp://www.pmf.ni.ac.rs/filoma On Gronwall s Type Inegral Inequaliies
Approximation Algorithms for Unique Games via Orthogonal Separators
 Approximaion Algorihms for Unique Games via Orhogonal Separaors Lecure noes by Konsanin Makarychev. Lecure noes are based on he papers [CMM06a, CMM06b, LM4]. Unique Games In hese lecure noes, we define
Approximaion Algorihms for Unique Games via Orhogonal Separaors Lecure noes by Konsanin Makarychev. Lecure noes are based on he papers [CMM06a, CMM06b, LM4]. Unique Games In hese lecure noes, we define
arxiv: v1 [math.fa] 9 Dec 2018
![arxiv: v1 [math.fa] 9 Dec 2018 arxiv: v1 [math.fa] 9 Dec 2018](/thumbs/95/124071290.jpg) AN INVERSE FUNCTION THEOREM CONVERSE arxiv:1812.03561v1 [mah.fa] 9 Dec 2018 JIMMIE LAWSON Absrac. We esablish he following converse of he well-known inverse funcion heorem. Le g : U V and f : V U be inverse
AN INVERSE FUNCTION THEOREM CONVERSE arxiv:1812.03561v1 [mah.fa] 9 Dec 2018 JIMMIE LAWSON Absrac. We esablish he following converse of he well-known inverse funcion heorem. Le g : U V and f : V U be inverse
control properties under both Gaussian and burst noise conditions. In the ~isappointing in comparison with convolutional code systems designed
 535 SOFT-DECSON THRESHOLD DECODNG OF CONVOLUTONAL CODES R.M.F. Goodman*, B.Sc., Ph.D. W.H. Ng*, M.S.E.E. Sunnnary Exising majoriy-decision hreshold decoders have so far been limied o his paper a new mehod
535 SOFT-DECSON THRESHOLD DECODNG OF CONVOLUTONAL CODES R.M.F. Goodman*, B.Sc., Ph.D. W.H. Ng*, M.S.E.E. Sunnnary Exising majoriy-decision hreshold decoders have so far been limied o his paper a new mehod
Book Corrections for Optimal Estimation of Dynamic Systems, 2 nd Edition
 Boo Correcions for Opimal Esimaion of Dynamic Sysems, nd Ediion John L. Crassidis and John L. Junins November 17, 017 Chaper 1 This documen provides correcions for he boo: Crassidis, J.L., and Junins,
Boo Correcions for Opimal Esimaion of Dynamic Sysems, nd Ediion John L. Crassidis and John L. Junins November 17, 017 Chaper 1 This documen provides correcions for he boo: Crassidis, J.L., and Junins,
Fuzzy Private Matching (Extended Abstract)
 Fuzzy Privae Maching (Exended Absrac Łukasz Chmielewski 1 Jaap-Henk Hoepman 1,2 1 Radboud Universiy Nijmegen, he Neherlands, emails: {lukaszc,jhh}@cs.ru.nl 2 NO, he Neherlands, email: jaap-henk.hoepman@no.nl
Fuzzy Privae Maching (Exended Absrac Łukasz Chmielewski 1 Jaap-Henk Hoepman 1,2 1 Radboud Universiy Nijmegen, he Neherlands, emails: {lukaszc,jhh}@cs.ru.nl 2 NO, he Neherlands, email: jaap-henk.hoepman@no.nl
INDEPENDENT SETS IN GRAPHS WITH GIVEN MINIMUM DEGREE
 INDEPENDENT SETS IN GRAPHS WITH GIVEN MINIMUM DEGREE JAMES ALEXANDER, JONATHAN CUTLER, AND TIM MINK Absrac The enumeraion of independen ses in graphs wih various resricions has been a opic of much ineres
INDEPENDENT SETS IN GRAPHS WITH GIVEN MINIMUM DEGREE JAMES ALEXANDER, JONATHAN CUTLER, AND TIM MINK Absrac The enumeraion of independen ses in graphs wih various resricions has been a opic of much ineres
Increase Our Learning Horizon with Evolving Technology
 Increase Our Learning Horizon wih Evolving Technology Wei-Chi Yang Radford Universiy Radford, Virginia 24142, USA e-mail: wyang@radford.edu Asrac. In his shor noe, we demonsrae how evolving echnological
Increase Our Learning Horizon wih Evolving Technology Wei-Chi Yang Radford Universiy Radford, Virginia 24142, USA e-mail: wyang@radford.edu Asrac. In his shor noe, we demonsrae how evolving echnological
Variational Iteration Method for Solving System of Fractional Order Ordinary Differential Equations
 IOSR Journal of Mahemaics (IOSR-JM) e-issn: 2278-5728, p-issn: 2319-765X. Volume 1, Issue 6 Ver. II (Nov - Dec. 214), PP 48-54 Variaional Ieraion Mehod for Solving Sysem of Fracional Order Ordinary Differenial
IOSR Journal of Mahemaics (IOSR-JM) e-issn: 2278-5728, p-issn: 2319-765X. Volume 1, Issue 6 Ver. II (Nov - Dec. 214), PP 48-54 Variaional Ieraion Mehod for Solving Sysem of Fracional Order Ordinary Differenial
Air Traffic Forecast Empirical Research Based on the MCMC Method
 Compuer and Informaion Science; Vol. 5, No. 5; 0 ISSN 93-8989 E-ISSN 93-8997 Published by Canadian Cener of Science and Educaion Air Traffic Forecas Empirical Research Based on he MCMC Mehod Jian-bo Wang,
Compuer and Informaion Science; Vol. 5, No. 5; 0 ISSN 93-8989 E-ISSN 93-8997 Published by Canadian Cener of Science and Educaion Air Traffic Forecas Empirical Research Based on he MCMC Mehod Jian-bo Wang,
