A Genetic Algorithm for Designing Constellations with Low Error Floors
|
|
|
- Tracey Long
- 6 years ago
- Views:
Transcription
1 A Genetic Algorithm for Deigning Contellation with Low Error Floor Matthew C. Valenti and Raghu Doppalapudi Wet Virginia Univerity Morgantown, WV Don Torrieri U.S. Army Reearch Lab Adelphi, MD Abtract The error floor of bit-interleaved coded modulation with iterative decoding BICM-ID) can be minimized for a particular contellation by maximizing the harmonic mean of the quared-euclidian ditance of ignal whoe label differ in jut one bit poition. Thi problem ha been formulated a an intance of the Quadratic Aignment Problem QAP) and olved uing the Reactive Tabu Search RTS). In thi paper, we propoe a genetic algorithm for olving the ymbol labeling problem and how that it uually yield deign that are iomorphic to thoe obtained uing RTS. We then extend the algorithm to optimize not only the labeling of the ignal point, but alo their location in the ignal pace. Uing thi approach, new contellation of cardinality 16,, and 64 are evolved that have an error floor lower than that of QAM or PSK modulation. The new contellation exhibit gain of 1. and 0.88 db over the bet 16-QAM and 64-QAM contellation reported previouly. I. INTRODUCTION Bit-interleaved coded-modulation BICM) i a tandard approach for coding in modern wirele ytem involving a binary encoder followed by a bit interleaver and a nonbinary modulator [1]. Relative to trelli-coded modulation TCM), BICM increae diverity by replacing a ymbol interleaver with a bit interleaver, and hence ha improved performance over fading channel. Due to it imple implementation and uperior performance over fading channel, BICM ha become a tandard feature in all propoed future-generation cellular, atellite, and wirele networing ytem. Performance in a BICM ytem can be improved by allowing the demodulator and decoder to iteratively exchange extrinic information. Such ytem are nown a BICM with iterative decoding and demodulation BICM-ID) []. Plot of the bit error rate for BICM-ID ytem generally exhibit a waterfall region, which i characterized by a rapid decreae in the bit error rate a the ignal-to-noie ratio increae, and an error-floor region, in which the bit error rate decreae much more lowly. For a given ignal et, the performance in both region i determined by the labeling map, which pecifie the log M) bit equence aociated with each of the M ymbol in the ignal et. In thi paper, we are concerned with deigning contellation and labeling map that reduce the error floor. Method for generating good labeling map that provide low error floor for a given ignal et have been previouly decribed in [] [5]. In [4] it i hown that the minimization of the o-called error-free feedbac EFF) bound, which i an approximation of the actual error floor, can be formulated a an intance of the combinatorial optimization problem nown a the quadratic aignment problem QAP) [6]. In particular, the goal i to maximize the harmonic mean of the Euclidian ditance of ignal whoe label differ in jut one bit poition. The optimization i done over the M! poible labeling map. In [4], Reactive Tabu Search RTS) [7] wa ued to perform thi optimization. However, the optimization can be olved in other way, and in thi paper we propoe a genetic algorithm for optimizing the labeling map of an arbitrary ignal et. The error floor depend not only on the labeling map, but alo on the location of the ignal point. Previou wor ha only focued on the deign of the labeling map and aumed a fixed modulation type, typically QAM or PSK. However, the error floor can be reduced further by moving the contellation point. We modify the genetic algorithm to deign not only the labeling map, but alo the placement of the point in the contellation. By evolving the deign acro multiple generation, new modulation format are found with error floor that are lower than previouly nown reult involving QAM or PSK. The remainder of the paper i organized a follow. Section II provide a model of the ytem under conideration, while Section III derive the error-free feedbac bound and identifie the main contributor to the bound. Section IV formulate the problem of minimizing the EFF bound for a given contellation a a combinatorial optimization problem, and Section V propoe a genetic algorithm for olving the problem. Section VI modifie the genetic algorithm to allow the point in the contellation to be moved. Numerical reult howing the EFF bound for optimized QAM, PSK, and evolved contellation with M = {16,, 64} are given in Section VII and compared againt the imulated error rate of actual BICM-ID ytem. Finally, Section VIII conclude the paper. II. SYSTEM MODEL A BICM-ID ytem i hown in Fig. 1. In the tranmitter, a vector u of meage bit i paed through a rate r c binary convolutional encoder to produce a codeword c. The codeword i bitwie interleaved by a permutation matrix Π to produce the bit-interleaved codeword c = c Π. The bitinterleaved codeword i then paed through a modulator to produce the vector of complex ymbol X L where X
2 i a contellation of ymbol with cardinality M and average energy E. The overall rate of the ytem i R = mr c, where m = log M, and the average energy per information bit i E b = E /R. The modulator elect ymbol from X baed on the contellation labeling map and the correponding group of m conecutive bit at the modulator input. Each ignal in X i labeled with a unique m-bit equence b. Define the integer repreentation of a length-m binary vector b a qb) = =0 b m 1. 1) Let x = [x 0, x 1,..., x ] be a vector containing each ignal in X. The ignal in vector x are indexed according to a natural mapping o that the label b of x i atifie qb) = i. Let x be an interleaved verion of the vector x uch that x = x µ) where µ) i a permutation function. Let µ = [µ0), µ1),..., µm 1)] be a vector containing the integer 0 through M 1 permuted according to the function µ). When the input to the modulator i b, then the modulator elect ymbol = x qb) = x µqb)) for tranmiion. Thu, the vector µ pecifie the labeling map for a particular ordered ignal et x. Each coded ymbol pae through a frequency-nonelective channel with complex-fading amplitude c. In thi paper, we aume uncorrelated Rayleigh fading uch that the c are i.i.d. zero-mean complex Gauian with unit power. The output of the channel i y = c + n where n i a ample of a white complex-gauian proce with variance / per dimenion. At the receiver, a demapper within the demodulator procee each received ymbol to produce a vector z of bit lielihood. Thi vector provide extrinic information that i deinterleaved and paed to the decoder. The oft-output decoder produce extriniic information that i interleaved and provided to the demapper a a vector v of a priori information. The output of the demodulator for bit i [8] z = log x X 0) py x ) exp [β j x )v j ] j py x ) exp [β j x )v j ] j where the function β j x ) return the j th bit of the label of x and X b) i the et of all ymbol in X labeled with b = b. III. CRITERIA FOR LOW ERROR FLOORS The union bound on the bit error probability i [1] P b 1 W I d)f p d, E ) c d=d f where d f i the minimum ditance of the convolutional code, W I d) i the total input weight of error event in the convolutional code at Hamming ditance d, and f p d, E / ) i ) ) Fig. 1. u c c Encoder Π Modulator u z z Decoder Π -1 v v Π Demodulator Model of a BICM-ID ytem. Π indicate a bitwie interleaver. the pairwie error probability PEP). The PEP depend on the choice of contellation X and it labeling map µ. Let the function g x) return the ymbol whoe label i identical to the label of ymbol x except for the th poition, which i complemented. The ignal x and g x) form an errorfree feedbac EFF) ignal et. In the following, {x, g x)} i called an EFF pair and g x) i aid to be the EFF companion of x. The EFF bound on BER i found from ) under the aumption that the demodulator i provided with perfect a priori information by the decoder, in which cae the LLR of the unnown bit ha the form z = log py x ) log py g x )) 4) where x i one of the ymbol whoe th poition i labeled with a one, i.e. β x ) = 1. The deciion rule for bit involve jut one EFF pair for that bit, and the identity of the pair depend on the a priori information fed bac from the decoder. Becaue the decoder doe not alway provide perfect a priori information to the demodulator, and becaue ) i an upper bound, the EFF bound i not actually a bound but rather i an approximation. However, the EFF bound i uually able to accurately predict the performance at high SNR. Conider how to determine f p 1, E / ), i.e. the probability of a olitary bit error. Aume without lo of generality that a bit b = 1 i tranmitted. An error will occur if the correponding LLR z i negative f p 1, E ) = P r[z < 0 b = 1] 5) Since there are m bit labeling each ymbol, the PEP i found by averaging the m bit error probabilitie f p 1, E ) = 1 m =0 c P r[z < 0 b = 1] 6) The error probability for each bit may be found by averaging over the ymbol that are labeled with b = 1 P r[z > 0 b = 1] = 1 n y P r[z < 0 x ]. 7)
3 Let P z x z) denote the conditional CDF of z given that ymbol x wa ent. Subtituting 7) into 6) allow the PEP to be expreed a f p 1, E ) = 1 m =0 P z x 0). 8) The PEP can be found uing moment generating function technique [1], [9]. Define φ z x ) = L { p z x z)} to be the Laplace tranform of the pdf of z given that ymbol x wa ent. In Rayleigh fading [10], φ z x ) = ) x g x ). 9) From the integration property of the Laplace tranform and the fact that the CDF i the integral of the pdf { P z x z) = φz L 1 x ) } 10) The PEP can thu be found by ubtituting 10) into 8), reulting in f p 1, E ) { } ψ) = L 1 11) z=0 where ψ) = 1 m =0 φ z x ). 1) When d > 1, the PEP i the probability that the um of d independent bit LLR i le than zero given that the correponding tranmitted bit are all one. Replacing z in the firt line of 6) with thi um and conditioning on the event that all bit are one reult in f p d, E ) [ d 1 ] d 1 = P r z i < 0 b i = 1 1) where i i ued to index bit error event, which will generally be in different ymbol. By uing the convolution property of the Laplace tranform, the PEP may be found uing f p d, E ) { } = L 1 [ψ)] d 14) z=0 Once the PEP i found for each d, the the bit error probability i found by ubtituting into ). Aymptotically, a, the BER can be approximated by [1], [9] [ ] df E P b κ 15) where κ i a contant and d h = 1 m =0 d h x g x ) 1 16) i the harmonic mean of the quared-euclidian ditance between ignal in each EFF ignal et. Taing the bae-10 logarithm of 15), defining X db = 10 log 10 X, and recalling that E = RE b yield log 10 P b d f 10 [ Rd h )db + Eb ) db ] + κ db. 17) A plot of log 10 P b veru E b / ) db will be a traight line with negative lope given by d f, which i the diverity gain. The horizontal offet of the curve i controlled by d h, with larger value of d h tranlating into lower error rate. From 16), it i clear that the choice of ignal et X and ymbol labeling map µ influence the harmonic mean, and from 17) the harmonic mean determine the offet of the BER curve. Thu, to minimize the EFF bound for a given outer code, it i neceary to maximize d h. For a given X, the maximization i performed over the et of all poible µ. Such maximization i dicued in Section IV and V. If one i free to choe not only µ but alo the ignal et X, then the maximization i over both function, a decribed in Section VI. IV. LABEL MAPPING OPTIMIZATION Maximizing the harmonic mean given by 16) over all µ i equivalent to finding the minimum of a cot function: min µ =0 x X 1) x g x). 18) A dicued in [4], the minimization given by 18) can be formulated a an intance of the Quadradic Aignment Problem QAP) [6]. Define the flow matrix F uch that element f i,j = 1 if the label of x i and x j are different in jut one bit poition. Since the vector x i indexed according to a natural labeling, f i,j = 1 whenever the binary expanion of the integer i and j have a Hamming ditance of one. Otherwie, f i,j = 0. Define the ditance matrix D with element { xi x d i,j = j, i j 19) 0, i = j For a given F and D, the cot function in 18) may be found a f i,j d i,j. 0) The previou expreion i the cot function when a natural mapping i applied. If another mapping i applied by permuting x to obtain x, then a new ditance matrix D mut be found. However, ince x = x µ), D i merely a columnand-row permuted verion of D. Thu, the cot function under mapping µ can be expreed a [4] f i,j d µi),µj). 1)
4 The optimization i to minimize the above expreion with repect to all poible mapping function permutation) µ. The QAP i NP-hard and may be olved in a variety of way [6]. Exact olution can be found uing dynamic programming, cutting plane technique, and branch and bound procedure. For M, uch technique are generally not tractable. For larger problem, heuritic earch method have been conidered, including RTS [7], genetic algorithm [11] [1], and imulated annealing [14]. Conventional genetic algorithm [11] are not competitive with RTS in term of accuracy and efficiency. However, with recent modification [1], genetic algorithm have emerged a a very promiing candidate for olving the QAP. In [4], the problem of maximizing d h wa olved uing RTS. In thi paper, our goal i to maximize d h by uing a genetic algorithm. V. A GENETIC ALGORITHM FOR MAPPING OPTIMIZATION The genetic algorithm ued to optimize the mapping i baed on the algorithm propoed in [1]. The algorithm i initialized with a population of N randomly drawn mapping function µ i, 0 i N 1. The mapping function are indexed in increaing order of cot o that mapping µ 0 i the bet. Whenever the population change, it i reindexed. Breeding require the election of two parent µ j and µ. The firt parent i elected at random from the entire population except for the bet 1 j N 1), while the econd i elected at random from thoe mapping that are better than the firt 0 j). Thi preferential parent election rule wa not contemplated in [11] [1] and improve the rate of convergence. The two parent produce two children µ j and µ. The children are initially empty vector of length M. A child direct parent i the parent with the ame index, while it indirect parent i the parent with a different index. The children are generated by randomly electing λ croover point, where λ i a fixed number for all breeding. The croover point indicate the poition of each child that are inherited from it indirect parent. At the croover point, value from µ are copied into µ j and value from µ j are copied into µ. The remaining poition of a child µ l are inherited from it direct parent µ l, where l = {j, }. Whenever poible, value of parent µ l that are not already in it child µ l are copied into µ l at the ame poition. The remaining value that could not be copied from parent to child into the ame poition are copied into the cloet open poition. The cot of each of the two children are evaluated. If a child µ l ha a lower cot than it parent µ l, then the parent i replaced with the child. If the child i not better than the parent, then an optional mutation proce i tarted. A mutant i generated from µ l by exchanging the value tored in randomly choen pair of poition in µ l. The mutation rate ρ i the probability that any given poition in µ l will become exchanged with ome other randomly choen poition. During the mutation proce, a total of L mutant are created and the cot of each i evaluated. If any of the mutant have a lower quared harmonic mean ary -ary 64-ary 0.5 PSK QAM generation Fig.. Harmonic mean of the quared-euclidian ditance between EFF ignal pair after each generation of the genetic algorithm. cot than parent µ l, then the parent i replaced with the lowet cot mutant. During each generation, a certain number of breeding occur. While thi number i arbitrary, we have et the number of breeding per generation to equal N, the overall population ize. A propoed in [1], our algorithm periodically perform a culling operation once every T c generation. During a culling generation, each child µ l i no longer compared againt it direct parent. Intead, the child i compared againt the current wort mapping µ N 1 and if the child i better than the wort mapping, it will replace the wort mapping. It i poible that the population produced by thi genetic algorithm will contain duplicate of the ame mapping. During culling generation, thee duplicate are removed and replaced with new random mapping. The genetic algorithm wa run to optimize the mapping of PSK and QAM with M = {16,, 64}. For each cae, the population wa N = 100, the number of croover point λ = M/5, the mutation rate ρ = 0.0, and the culling period T c = M. The number of mutant L per child wa variable. Initially, L = 0. If after T c generation a new bet mapping i not identified, then L i incremented up to a maximum of 0. On the other hand, if a new mapping i identified within T c generation, then L i decremented. The value of d h after each generation, up to generation , i hown in Fig.. The final value of d h along with the generation that the bet mapping wa identified i lited in Table I. Alo hown are the value of d h obtained uing RTS. A can be een, the genetic algorithm ha found the ame optimal value a wa found uing RTS with the exception of 64-QAM, in which cae the genetic algorithm reult i lightly inferior to that of RTS. The contellation labeling map found by the genetic algorithm for M = 16 are hown in Fig.. VI. CONSTELLATION OPTIMIZATION In the previou ection, the contellation X wa fixed and only the labeling map µ wa optimized. However, d h depend not only on the labeling map but alo on the contellation. We
5 TABLE I VALUE OF d h OBTAINED USING RTS AND THE PROPOSED GENETIC ALGORITHM. ALSO LISTED IS THE NUMBER OF GENERATIONS REQUIRED FOR THE GA TO CONVERGE. M Modulation d h from RTS d h from GA generation 16 QAM PSK ,49 QAM PSK QAM ,41 PSK , Fig.. Contellation labeling map that maximize d h found uing the genetic algorithm. 16-QAM i on the left, and 16-PSK i on the right. ee to increae d h beyond the value poible for QAM and PSK by moving ignal point in the contellation. Ideally, the goal i to perform the following optimization min X,µ = x g x ). ) Becaue the number of poible X i infinite, thi optimization i more challenging than the one given by 18). We propoe a heuritic method for performing the optimization in ). The optimization begin with a tandard contellation. Becaue PSK ha a better potential d h than QAM, it i a more appropriate tarting contellation. Several generation of the genetic algorithm are run on the PSK contellation to obtain an initial mapping. Next, the contellation i modified in an attempt to increae d h. Thi can be done by firt picing an EFF pair whoe ditance i i at the minimum d e, where d e = min x g x ). ) 0 If there are multiple EFF pair that are ditance d e apart, then a pair i elected at random. The two point are then forced to be further apart. Let α > 1 repreent a cale factor, uch that the elected EFF pair i forced to be ditance αd e apart with the ame centroid. When thi adjutment i made, the average energy of the contellation will typically increae, and o it mut be renormalized to E. Alo, after the pair i puhed apart, the previouly choen labeling map might no longer be optimal, and thu it i redeigned by running one generation of the genetic algorithm with an initial population of mapping et to the final population of the previouly optimized contellation. The proce continue iteratively, with Fig ary contellation optimized uing a genetic algorithm. Tilted axe have been uperimpoed to emphaize the ymmetry that ha evolved. TABLE II SIGNAL VALUES FOR THE CONSTELLATION SHOWN IN FIG. 4. Labeling Real Imaginary Labeling Real Imaginary each iteration coniting of moving one pair of point apart, renormalizing the contellation, and genetically reoptimizing the contellation labeling map. Starting with the 16-PSK contellation hown in Fig., the optimization wa run with 1000 iteration and α = The reulting contellation i hown in Fig. 4. The optimization reulted in d h =.6841, which i coniderably larger than the bet d h found with QAM and PSK. The ignal value for the contellation are lited in Table II. Inpecting the contellation reveal an intereting geometry. Tilted axe have been uperimpoed on the figure to emphaize the ymmetry in the evolved contellation. Each quadrant of the tilted contellation contain four ymbol whoe label differ in exactly two bit poition; thu, there are no EFF pair in the ame quadrant. Of the four ymbol in each quadrant, the firt two ymbol are nearly colocated, a third ymbol i ditance 0.1 from the colocated pair, and a fourth ymbol i ditance 0.6 from the colocated pair. The fourth ymbol EFF companion all lie on the oppoite quadrant for intance the EFF companion of 8 are {0, 9, 10, 1}). For all other ymbol, two of their EFF companion are in one quadrant and the other two EFF companion are in another quadrant. Contellation for M = and M = 64 were optimized in a imilar fahion. The reulting contellation had d h =.5477 for M = 16 and d h =.5178 for M = 64 which are again better than the value found for PSK and QAM. Note that for the genetically-deigned contellation, d h actually decreae with increaing M, which i oppoite the trend oberved for QAM and PSK modulation. Thu the relative gain achieved by evolving the contellation decreae with increaing M.
6 10-7 M= QAM PSK GA Simulated EFF bound QAM PSK M= Genetic Deign BER BER 10-6 M= E b /N o in db Fig. 5. The EFF bound on BER when uing a 7, 5) convolutional code. For each M, QAM ha the highet error floor and the contellation deigned with the genetic algorithm GA) ha the lowet error floor. VII. NUMERICAL RESULTS The EFF bound wa calculated for the PSK and QAM contellation decribed in Section V a well a the geneticallydeigned contellation decribed in Section VI. The bound are hown in Fig. 5 for the rate-1/ convolutional code with octal generator 7, 5) and d f = 5. While all curve have the ame lope due to the common value of d f, there are gain in moving from one modulation choice to another. In general, there i a gain in moving to a larger alphabet and there are gain in moving from QAM to PSK and from PSK to the genetically-deigned contellation. For intance, the genetically-deigned contellation provide gain of 1. and 0.88 db, repectively, over the 16-QAM and 64-QAM contellation. Thee trend are the oppoite of the trend oberved with uncoded modulation or BICM without feedbac, indicating that BICM-ID achieve it gain in a much different manner. Indeed, the contellation hown in Fig. 4 would perform quite poorly without coding and iterative decoding. To demontrate the tightne of the EFF bound at high SNR, the three 16-ary BICM-ID ytem were imulated. The imulation ued a codeword length of N = 4, 000 bit over an uncorrelated Rayleigh fading channel. The reult of the imulation are hown in Fig. 6. Alo hown on the plot are the correponding EFF bound. A can be een, the EFF bound accurately predict the performance at high SNR. However, it can alo be een that lowering the EFF bound come at a cot. The waterfall region, i.e. the range of SNR characterized by a rapid drop in BER, occur at a higher SNR for each modulation that ha a lower EFF bound. VIII. CONCLUSIONS Evolutionary computing may be ued to not only optimize the labeling map of a contellation, but alo to optimize the placement of the point in the contellation. By applying an appropriate genetic algorithm, a new contellation may be E b /N o in db Fig. 6. Simulated bit error performance uing 16-ary modulation, a 7, 5) covolutional code, and 4, 000-bit codeword. evolved for BICM-ID with a predicted error floor that i on the order of 1 db better than the bet nown QAM contellation. The lower error floor of the evolved contellation come at the cot of the waterfall region being hifted to a higher SNR. REFERENCES [1] G. Caire, G. Taricco, and E. Biglieri, Bit-interleaved coded modulation, IEEE Tran. Inform. Theory, vol. 44, pp , May [] X. Li and J. A. Ritcey, Bit-interleaved coded modulation with iterative decoding, IEEE Commun. Letter, vol. 1, pp , Nov [] J. Tan and G. L. Stüber, Analyi and deign of ymbol mapper for iteratively decoded BICM, IEEE Tran. Wirele Comm., vol. 4, pp , Mar [4] Y. Huang and J. A. Ritcey, Optimal contellation labeling for iteratively decoded bit-interleaved pace-time coded modulation, IEEE Tran. Inform. Theory, vol. 51, pp , May 005. [5] D. Torrieri and M. C. Valenti, Contellation labeling map for low error floor, in Proc. IEEE Military Commun. Conf. MILCOM), Orlando, FL, Oct [6] E. Cela, The Quadratic Aignment Problem: Theory and Algorithm. Kluwer Academic Pre, [7] R. Battiti and G. Tecchiolli, The reactive tabu earch, ORSA J. Comp., vol. 6, pp , [8] M. C. Valenti and S. Cheng, Iterative demodulation and decoding of turbo coded M-ary noncoherent orthogonal modulation, IEEE J. Select. Area Commun., vol., pp , Sept [9] A. Chindapol and J. A. Ritcey, Deign, analyi, and performance evaluation of BICM-ID with quare QAM contellation in Rayleigh fading channel, IEEE J. Select. Area Commun., vol. 19, pp , May 001. [10] S. Benedetto and E. Biglieri, Principle of Digital Tranmiion with Wirele Application. Kluwer, [11] C. Fleurent and J. Ferland, Genetic hybrid for the quadradic aignment problem, DIMACS Serie in Dicrete Mathematic and Theoretical Computer Science, pp , [1] Z. Drezner, A new genetic algorithm for the quadratic aignment problem, INFORMS J. Computing, vol. 15, pp. 0 0, 00. [1] Y. Wu and P. Ji, Solving the quadratic aignment problem by a genetic algorithm with a new replacement trategy, Int. J. Humanitie and Social Science, vol. 1, no., pp , 007. [14] D. T. Conolly, An improved annealing mechanim for the QAP, European J. of Operational Reearch, vol. 46, pp , 1990.
A Study on Simulating Convolutional Codes and Turbo Codes
 A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
Chapter 2 Sampling and Quantization. In order to investigate sampling and quantization, the difference between analog
 Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Jul 4, 2005 turbo_code_primer Revision 0.0. Turbo Code Primer
 Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Improved Interference Cancellation Scheme for Two-User Detection of Alamouti Code
 Improved Interference Cancellation Scheme for Two-Uer Detection of Alamouti Code Manav R hatnagar and Are Hjørungne Abtract In thi correpondence, we propoe an improved interference cancellation method
Improved Interference Cancellation Scheme for Two-Uer Detection of Alamouti Code Manav R hatnagar and Are Hjørungne Abtract In thi correpondence, we propoe an improved interference cancellation method
Fading Channels: Capacity, BER and Diversity
 Fading Channel: Capacity, BER and Diverity Mater Univeritario en Ingeniería de Telecomunicación I. Santamaría Univeridad de Cantabria Introduction Capacity BER Diverity Concluion Content Introduction Capacity
Fading Channel: Capacity, BER and Diverity Mater Univeritario en Ingeniería de Telecomunicación I. Santamaría Univeridad de Cantabria Introduction Capacity BER Diverity Concluion Content Introduction Capacity
Problem Set 8 Solutions
 Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Social Studies 201 Notes for November 14, 2003
 1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
Bogoliubov Transformation in Classical Mechanics
 Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Clustering Methods without Given Number of Clusters
 Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Chapter 5 Optimum Receivers for the Additive White Gaussian Noise Channel
 Chapter 5 Optimum Receiver for the Additive White Gauian Noie Channel Table of Content 5.1 Optimum Receiver for Signal Corrupted by Additive White Noie 5.1.1 Correlation Demodulator 5.1. Matched-Filter
Chapter 5 Optimum Receiver for the Additive White Gauian Noie Channel Table of Content 5.1 Optimum Receiver for Signal Corrupted by Additive White Noie 5.1.1 Correlation Demodulator 5.1. Matched-Filter
Evolutionary Algorithms Based Fixed Order Robust Controller Design and Robustness Performance Analysis
 Proceeding of 01 4th International Conference on Machine Learning and Computing IPCSIT vol. 5 (01) (01) IACSIT Pre, Singapore Evolutionary Algorithm Baed Fixed Order Robut Controller Deign and Robutne
Proceeding of 01 4th International Conference on Machine Learning and Computing IPCSIT vol. 5 (01) (01) IACSIT Pre, Singapore Evolutionary Algorithm Baed Fixed Order Robut Controller Deign and Robutne
Channel Coding 2.
 Channel Coding Dr.-Ing. Dirk Wübben Intitute for Telecommunication and High-Frequency Technique Department of Communication Engineering Room: N3, Phone: /8-6385 wuebben@ant.uni-bremen.de Lecture Tueday,
Channel Coding Dr.-Ing. Dirk Wübben Intitute for Telecommunication and High-Frequency Technique Department of Communication Engineering Room: N3, Phone: /8-6385 wuebben@ant.uni-bremen.de Lecture Tueday,
GNSS Solutions: What is the carrier phase measurement? How is it generated in GNSS receivers? Simply put, the carrier phase
 GNSS Solution: Carrier phae and it meaurement for GNSS GNSS Solution i a regular column featuring quetion and anwer about technical apect of GNSS. Reader are invited to end their quetion to the columnit,
GNSS Solution: Carrier phae and it meaurement for GNSS GNSS Solution i a regular column featuring quetion and anwer about technical apect of GNSS. Reader are invited to end their quetion to the columnit,
Codes Correcting Two Deletions
 1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
Trellis Shaping Techniques for Satellite Telecommunication Systems
 > 1 Trelli Technique for Satellite Telecommunication Sytem M. Álvarez-Díaz 1, M. Neri, C. Moquera 1 and G. E. Corazza 1 Dept. Signal Theory and Communication (TSC), Univerity of Vigo Campu Univeritario
> 1 Trelli Technique for Satellite Telecommunication Sytem M. Álvarez-Díaz 1, M. Neri, C. Moquera 1 and G. E. Corazza 1 Dept. Signal Theory and Communication (TSC), Univerity of Vigo Campu Univeritario
Signaling over MIMO Multi-Base Systems: Combination of Multi-Access and Broadcast Schemes
 Signaling over MIMO Multi-Bae Sytem: Combination of Multi-Acce and Broadcat Scheme Mohammad Ali Maddah-Ali Abolfazl S. Motahari and Amir K. Khandani Coding & Signal Tranmiion Laboratory (www.ct.uwaterloo.ca)
Signaling over MIMO Multi-Bae Sytem: Combination of Multi-Acce and Broadcat Scheme Mohammad Ali Maddah-Ali Abolfazl S. Motahari and Amir K. Khandani Coding & Signal Tranmiion Laboratory (www.ct.uwaterloo.ca)
Suggested Answers To Exercises. estimates variability in a sampling distribution of random means. About 68% of means fall
 Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
LDPC Convolutional Codes Based on Permutation Polynomials over Integer Rings
 LDPC Convolutional Code Baed on Permutation Polynomial over Integer Ring Marco B. S. Tavare and Gerhard P. Fettwei Vodafone Chair Mobile Communication Sytem, Dreden Univerity of Technology, 01062 Dreden,
LDPC Convolutional Code Baed on Permutation Polynomial over Integer Ring Marco B. S. Tavare and Gerhard P. Fettwei Vodafone Chair Mobile Communication Sytem, Dreden Univerity of Technology, 01062 Dreden,
Çankaya University ECE Department ECE 376 (MT)
 Çankaya Univerity ECE Department ECE 376 (M) Student Name : Date : 13.4.15 Student Number : Open Source Exam Quetion 1. (7 Point) he time waveform of the ignal et, and t t are given in Fig. 1.1. a. Identify
Çankaya Univerity ECE Department ECE 376 (M) Student Name : Date : 13.4.15 Student Number : Open Source Exam Quetion 1. (7 Point) he time waveform of the ignal et, and t t are given in Fig. 1.1. a. Identify
A Note on the Sum of Correlated Gamma Random Variables
 1 A Note on the Sum of Correlated Gamma Random Variable Joé F Pari Abtract arxiv:11030505v1 [cit] 2 Mar 2011 The um of correlated gamma random variable appear in the analyi of many wirele communication
1 A Note on the Sum of Correlated Gamma Random Variable Joé F Pari Abtract arxiv:11030505v1 [cit] 2 Mar 2011 The um of correlated gamma random variable appear in the analyi of many wirele communication
Social Studies 201 Notes for March 18, 2005
 1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
The continuous time random walk (CTRW) was introduced by Montroll and Weiss 1.
 1 I. CONTINUOUS TIME RANDOM WALK The continuou time random walk (CTRW) wa introduced by Montroll and Wei 1. Unlike dicrete time random walk treated o far, in the CTRW the number of jump n made by the walker
1 I. CONTINUOUS TIME RANDOM WALK The continuou time random walk (CTRW) wa introduced by Montroll and Wei 1. Unlike dicrete time random walk treated o far, in the CTRW the number of jump n made by the walker
Factor Analysis with Poisson Output
 Factor Analyi with Poion Output Gopal Santhanam Byron Yu Krihna V. Shenoy, Department of Electrical Engineering, Neurocience Program Stanford Univerity Stanford, CA 94305, USA {gopal,byronyu,henoy}@tanford.edu
Factor Analyi with Poion Output Gopal Santhanam Byron Yu Krihna V. Shenoy, Department of Electrical Engineering, Neurocience Program Stanford Univerity Stanford, CA 94305, USA {gopal,byronyu,henoy}@tanford.edu
Design By Emulation (Indirect Method)
 Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
A Constraint Propagation Algorithm for Determining the Stability Margin. The paper addresses the stability margin assessment for linear systems
 A Contraint Propagation Algorithm for Determining the Stability Margin of Linear Parameter Circuit and Sytem Lubomir Kolev and Simona Filipova-Petrakieva Abtract The paper addree the tability margin aement
A Contraint Propagation Algorithm for Determining the Stability Margin of Linear Parameter Circuit and Sytem Lubomir Kolev and Simona Filipova-Petrakieva Abtract The paper addree the tability margin aement
A Comparison of Soft In/Soft Out Algorithms for Turbo Detection
 A Comparion of Soft In/Soft Out Algorithm for Turbo Detection Gerhard Bauch 1, Volker Franz 2 1 Munich Univerity of Technology (TUM), Intitute for Communication Engineering (LNT) D-80290 Munich, Germany
A Comparion of Soft In/Soft Out Algorithm for Turbo Detection Gerhard Bauch 1, Volker Franz 2 1 Munich Univerity of Technology (TUM), Intitute for Communication Engineering (LNT) D-80290 Munich, Germany
Digital Control System
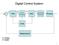 Digital Control Sytem - A D D A Micro ADC DAC Proceor Correction Element Proce Clock Meaurement A: Analog D: Digital Continuou Controller and Digital Control Rt - c Plant yt Continuou Controller Digital
Digital Control Sytem - A D D A Micro ADC DAC Proceor Correction Element Proce Clock Meaurement A: Analog D: Digital Continuou Controller and Digital Control Rt - c Plant yt Continuou Controller Digital
Lecture 9: Shor s Algorithm
 Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Digital Communications I: Modulation and Coding Course. Term Catharina Logothetis Lecture 8
 Digital Communication I: odulation and Coding Coure Term 3-8 Catharina Logotheti Lecture 8 Lat time we talked about: Some bandpa modulation cheme -A, -SK, -FSK, -QA How to perform coherent and noncoherent
Digital Communication I: odulation and Coding Coure Term 3-8 Catharina Logotheti Lecture 8 Lat time we talked about: Some bandpa modulation cheme -A, -SK, -FSK, -QA How to perform coherent and noncoherent
Inference for Two Stage Cluster Sampling: Equal SSU per PSU. Projections of SSU Random Variables on Each SSU selection.
 Inference for Two Stage Cluter Sampling: Equal SSU per PSU Projection of SSU andom Variable on Eac SSU election By Ed Stanek Introduction We review etimating equation for PSU mean in a two tage cluter
Inference for Two Stage Cluter Sampling: Equal SSU per PSU Projection of SSU andom Variable on Eac SSU election By Ed Stanek Introduction We review etimating equation for PSU mean in a two tage cluter
List coloring hypergraphs
 Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
Sampling and the Discrete Fourier Transform
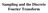 Sampling and the Dicrete Fourier Tranform Sampling Method Sampling i mot commonly done with two device, the ample-and-hold (S/H) and the analog-to-digital-converter (ADC) The S/H acquire a CT ignal at
Sampling and the Dicrete Fourier Tranform Sampling Method Sampling i mot commonly done with two device, the ample-and-hold (S/H) and the analog-to-digital-converter (ADC) The S/H acquire a CT ignal at
Source slideplayer.com/fundamentals of Analytical Chemistry, F.J. Holler, S.R.Crouch. Chapter 6: Random Errors in Chemical Analysis
 Source lideplayer.com/fundamental of Analytical Chemitry, F.J. Holler, S.R.Crouch Chapter 6: Random Error in Chemical Analyi Random error are preent in every meaurement no matter how careful the experimenter.
Source lideplayer.com/fundamental of Analytical Chemitry, F.J. Holler, S.R.Crouch Chapter 6: Random Error in Chemical Analyi Random error are preent in every meaurement no matter how careful the experimenter.
Orthogonal Signals With orthogonal signals, we select only one of the orthogonal basis functions for transmission:
 4..4 Orthogonal, Biorthogonal and Simplex Signal 4.- In PAM, QAM and PSK, we had only one ai function. For orthogonal, iorthogonal and implex ignal, however, we ue more than one orthogonal ai function,
4..4 Orthogonal, Biorthogonal and Simplex Signal 4.- In PAM, QAM and PSK, we had only one ai function. For orthogonal, iorthogonal and implex ignal, however, we ue more than one orthogonal ai function,
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS
 CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
μ + = σ = D 4 σ = D 3 σ = σ = All units in parts (a) and (b) are in V. (1) x chart: Center = μ = 0.75 UCL =
 Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Lecture 21. The Lovasz splitting-off lemma Topics in Combinatorial Optimization April 29th, 2004
 18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
Gain and Phase Margins Based Delay Dependent Stability Analysis of Two- Area LFC System with Communication Delays
 Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Avoiding Forbidden Submatrices by Row Deletions
 Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Real Sources (Secondary Sources) Phantom Source (Primary source) LS P. h rl. h rr. h ll. h lr. h pl. h pr
 Ecient frequency domain ltered-x realization of phantom ource iet C.W. ommen, Ronald M. Aart, Alexander W.M. Mathijen, John Gara, Haiyan He Abtract A phantom ound ource i a virtual ound image which can
Ecient frequency domain ltered-x realization of phantom ource iet C.W. ommen, Ronald M. Aart, Alexander W.M. Mathijen, John Gara, Haiyan He Abtract A phantom ound ource i a virtual ound image which can
Lecture 4 Topic 3: General linear models (GLMs), the fundamentals of the analysis of variance (ANOVA), and completely randomized designs (CRDs)
 Lecture 4 Topic 3: General linear model (GLM), the fundamental of the analyi of variance (ANOVA), and completely randomized deign (CRD) The general linear model One population: An obervation i explained
Lecture 4 Topic 3: General linear model (GLM), the fundamental of the analyi of variance (ANOVA), and completely randomized deign (CRD) The general linear model One population: An obervation i explained
The Hassenpflug Matrix Tensor Notation
 The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
Lecture 10 Filtering: Applied Concepts
 Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
Suggestions - Problem Set (a) Show the discriminant condition (1) takes the form. ln ln, # # R R
 Suggetion - Problem Set 3 4.2 (a) Show the dicriminant condition (1) take the form x D Ð.. Ñ. D.. D. ln ln, a deired. We then replace the quantitie. 3ß D3 by their etimate to get the proper form for thi
Suggetion - Problem Set 3 4.2 (a) Show the dicriminant condition (1) take the form x D Ð.. Ñ. D.. D. ln ln, a deired. We then replace the quantitie. 3ß D3 by their etimate to get the proper form for thi
Root Locus Diagram. Root loci: The portion of root locus when k assume positive values: that is 0
 Objective Root Locu Diagram Upon completion of thi chapter you will be able to: Plot the Root Locu for a given Tranfer Function by varying gain of the ytem, Analye the tability of the ytem from the root
Objective Root Locu Diagram Upon completion of thi chapter you will be able to: Plot the Root Locu for a given Tranfer Function by varying gain of the ytem, Analye the tability of the ytem from the root
RaneNote BESSEL FILTER CROSSOVER
 RaneNote BESSEL FILTER CROSSOVER A Beel Filter Croover, and It Relation to Other Croover Beel Function Phae Shift Group Delay Beel, 3dB Down Introduction One of the way that a croover may be contructed
RaneNote BESSEL FILTER CROSSOVER A Beel Filter Croover, and It Relation to Other Croover Beel Function Phae Shift Group Delay Beel, 3dB Down Introduction One of the way that a croover may be contructed
Linear Motion, Speed & Velocity
 Add Important Linear Motion, Speed & Velocity Page: 136 Linear Motion, Speed & Velocity NGSS Standard: N/A MA Curriculum Framework (006): 1.1, 1. AP Phyic 1 Learning Objective: 3.A.1.1, 3.A.1.3 Knowledge/Undertanding
Add Important Linear Motion, Speed & Velocity Page: 136 Linear Motion, Speed & Velocity NGSS Standard: N/A MA Curriculum Framework (006): 1.1, 1. AP Phyic 1 Learning Objective: 3.A.1.1, 3.A.1.3 Knowledge/Undertanding
SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lectures 41-48)
 Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Preemptive scheduling on a small number of hierarchical machines
 Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Successive Refinement via Broadcast: Optimizing Expected Distortion of a Gaussian Source over a Gaussian Fading Channel
 Succeive Refinement via Broadcat: Optimizing Expected Ditortion of a Gauian Source over a Gauian Fading Channel Chao Tian, Member, IEEE, Avi Steiner, Student Member, IEEE, Shlomo Shamai (Shitz, Fellow,
Succeive Refinement via Broadcat: Optimizing Expected Ditortion of a Gauian Source over a Gauian Fading Channel Chao Tian, Member, IEEE, Avi Steiner, Student Member, IEEE, Shlomo Shamai (Shitz, Fellow,
7.2 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 281
 72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
Automatic Control Systems. Part III: Root Locus Technique
 www.pdhcenter.com PDH Coure E40 www.pdhonline.org Automatic Control Sytem Part III: Root Locu Technique By Shih-Min Hu, Ph.D., P.E. Page of 30 www.pdhcenter.com PDH Coure E40 www.pdhonline.org VI. Root
www.pdhcenter.com PDH Coure E40 www.pdhonline.org Automatic Control Sytem Part III: Root Locu Technique By Shih-Min Hu, Ph.D., P.E. Page of 30 www.pdhcenter.com PDH Coure E40 www.pdhonline.org VI. Root
Predicting the Performance of Teams of Bounded Rational Decision-makers Using a Markov Chain Model
 The InTITuTe for ytem reearch Ir TechnIcal report 2013-14 Predicting the Performance of Team of Bounded Rational Deciion-maer Uing a Marov Chain Model Jeffrey Herrmann Ir develop, applie and teache advanced
The InTITuTe for ytem reearch Ir TechnIcal report 2013-14 Predicting the Performance of Team of Bounded Rational Deciion-maer Uing a Marov Chain Model Jeffrey Herrmann Ir develop, applie and teache advanced
One Class of Splitting Iterative Schemes
 One Cla of Splitting Iterative Scheme v Ciegi and V. Pakalnytė Vilniu Gedimina Technical Univerity Saulėtekio al. 11, 2054, Vilniu, Lithuania rc@fm.vtu.lt Abtract. Thi paper deal with the tability analyi
One Cla of Splitting Iterative Scheme v Ciegi and V. Pakalnytė Vilniu Gedimina Technical Univerity Saulėtekio al. 11, 2054, Vilniu, Lithuania rc@fm.vtu.lt Abtract. Thi paper deal with the tability analyi
5.5 Application of Frequency Response: Signal Filters
 44 Dynamic Sytem Second order lowpa filter having tranfer function H()=H ()H () u H () H () y Firt order lowpa filter Figure 5.5: Contruction of a econd order low-pa filter by combining two firt order
44 Dynamic Sytem Second order lowpa filter having tranfer function H()=H ()H () u H () H () y Firt order lowpa filter Figure 5.5: Contruction of a econd order low-pa filter by combining two firt order
[Saxena, 2(9): September, 2013] ISSN: Impact Factor: INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY
![[Saxena, 2(9): September, 2013] ISSN: Impact Factor: INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY [Saxena, 2(9): September, 2013] ISSN: Impact Factor: INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY](/thumbs/90/102186320.jpg) [Saena, (9): September, 0] ISSN: 77-9655 Impact Factor:.85 IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY Contant Stre Accelerated Life Teting Uing Rayleigh Geometric Proce
[Saena, (9): September, 0] ISSN: 77-9655 Impact Factor:.85 IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY Contant Stre Accelerated Life Teting Uing Rayleigh Geometric Proce
HELICAL TUBES TOUCHING ONE ANOTHER OR THEMSELVES
 15 TH INTERNATIONAL CONFERENCE ON GEOMETRY AND GRAPHICS 0 ISGG 1-5 AUGUST, 0, MONTREAL, CANADA HELICAL TUBES TOUCHING ONE ANOTHER OR THEMSELVES Peter MAYRHOFER and Dominic WALTER The Univerity of Innbruck,
15 TH INTERNATIONAL CONFERENCE ON GEOMETRY AND GRAPHICS 0 ISGG 1-5 AUGUST, 0, MONTREAL, CANADA HELICAL TUBES TOUCHING ONE ANOTHER OR THEMSELVES Peter MAYRHOFER and Dominic WALTER The Univerity of Innbruck,
RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS
 www.arpapre.com/volume/vol29iue1/ijrras_29_1_01.pdf RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS Sevcan Demir Atalay 1,* & Özge Elmataş Gültekin
www.arpapre.com/volume/vol29iue1/ijrras_29_1_01.pdf RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS Sevcan Demir Atalay 1,* & Özge Elmataş Gültekin
Moment of Inertia of an Equilateral Triangle with Pivot at one Vertex
 oment of nertia of an Equilateral Triangle with Pivot at one Vertex There are two wa (at leat) to derive the expreion f an equilateral triangle that i rotated about one vertex, and ll how ou both here.
oment of nertia of an Equilateral Triangle with Pivot at one Vertex There are two wa (at leat) to derive the expreion f an equilateral triangle that i rotated about one vertex, and ll how ou both here.
SINGLE CARRIER BLOCK TRANSMISSION WITHOUT GUARD INTERVAL
 SINGLE CARRIER BLOCK TRANSMISSION WITHOUT GUARD INTERVAL Kazunori Hayahi Hideaki Sakai Graduate School of Informatic, Kyoto Univerity Kyoto, JAPAN ABSTRACT Thi paper propoe a imple detection cheme for
SINGLE CARRIER BLOCK TRANSMISSION WITHOUT GUARD INTERVAL Kazunori Hayahi Hideaki Sakai Graduate School of Informatic, Kyoto Univerity Kyoto, JAPAN ABSTRACT Thi paper propoe a imple detection cheme for
A Simple Example Binary Hypothesis Testing Optimal Receiver Frontend M-ary Signal Sets Message Sequences. = 4 for QPSK) E b Q 2. 2E b.
 Exercie: QPSK I Find the error rate for the ignal et n (t) = p 2E /T co(2pf c t + n p/2 + p/4), for n = 0,, 3 I Anwer: (Recall h P = d min 2 E b = 4 for QPSK) E Pr{e} = 2Q Q 2 = 2Q = 2Q 2E b h P E b 2
Exercie: QPSK I Find the error rate for the ignal et n (t) = p 2E /T co(2pf c t + n p/2 + p/4), for n = 0,, 3 I Anwer: (Recall h P = d min 2 E b = 4 for QPSK) E Pr{e} = 2Q Q 2 = 2Q = 2Q 2E b h P E b 2
Determination of the local contrast of interference fringe patterns using continuous wavelet transform
 Determination of the local contrat of interference fringe pattern uing continuou wavelet tranform Jong Kwang Hyok, Kim Chol Su Intitute of Optic, Department of Phyic, Kim Il Sung Univerity, Pyongyang,
Determination of the local contrat of interference fringe pattern uing continuou wavelet tranform Jong Kwang Hyok, Kim Chol Su Intitute of Optic, Department of Phyic, Kim Il Sung Univerity, Pyongyang,
Physics 741 Graduate Quantum Mechanics 1 Solutions to Final Exam, Fall 2014
 Phyic 7 Graduate Quantum Mechanic Solution to inal Eam all 0 Each quetion i worth 5 point with point for each part marked eparately Some poibly ueful formula appear at the end of the tet In four dimenion
Phyic 7 Graduate Quantum Mechanic Solution to inal Eam all 0 Each quetion i worth 5 point with point for each part marked eparately Some poibly ueful formula appear at the end of the tet In four dimenion
New bounds for Morse clusters
 New bound for More cluter Tamá Vinkó Advanced Concept Team, European Space Agency, ESTEC Keplerlaan 1, 2201 AZ Noordwijk, The Netherland Tama.Vinko@ea.int and Arnold Neumaier Fakultät für Mathematik, Univerität
New bound for More cluter Tamá Vinkó Advanced Concept Team, European Space Agency, ESTEC Keplerlaan 1, 2201 AZ Noordwijk, The Netherland Tama.Vinko@ea.int and Arnold Neumaier Fakultät für Mathematik, Univerität
REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS. Logic and Applications 2015 (LAP 2015) September 21-25, 2015, Dubrovnik, Croatia
 REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS SMILE MARKOVSKI Faculty of Computer Science and Engineering, S Ciryl and Methodiu Univerity in Skopje, MACEDONIA mile.markovki@gmail.com Logic
REPRESENTATION OF ALGEBRAIC STRUCTURES BY BOOLEAN FUNCTIONS SMILE MARKOVSKI Faculty of Computer Science and Engineering, S Ciryl and Methodiu Univerity in Skopje, MACEDONIA mile.markovki@gmail.com Logic
IEOR 3106: Fall 2013, Professor Whitt Topics for Discussion: Tuesday, November 19 Alternating Renewal Processes and The Renewal Equation
 IEOR 316: Fall 213, Profeor Whitt Topic for Dicuion: Tueday, November 19 Alternating Renewal Procee and The Renewal Equation 1 Alternating Renewal Procee An alternating renewal proce alternate between
IEOR 316: Fall 213, Profeor Whitt Topic for Dicuion: Tueday, November 19 Alternating Renewal Procee and The Renewal Equation 1 Alternating Renewal Procee An alternating renewal proce alternate between
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD
 SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
Amplify and Forward Relaying; Channel Model and Outage Behaviour
 Amplify and Forward Relaying; Channel Model and Outage Behaviour Mehdi Mortazawi Molu Intitute of Telecommunication Vienna Univerity of Technology Guhautr. 5/E389, 4 Vienna, Autria Email: mmortaza@nt.tuwien.ac.at
Amplify and Forward Relaying; Channel Model and Outage Behaviour Mehdi Mortazawi Molu Intitute of Telecommunication Vienna Univerity of Technology Guhautr. 5/E389, 4 Vienna, Autria Email: mmortaza@nt.tuwien.ac.at
Control Systems Analysis and Design by the Root-Locus Method
 6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
Network based Sensor Localization in Multi-Media Application of Precision Agriculture Part 2: Time of Arrival
 Network baed Senor Localization in Multi-Media Application of Preciion Agriculture Part : Time of Arrival Herman Sahota IBM, Silicon Valley Laboratory Email: hahota@u.ibm.com Ratneh Kumar, IEEE Fellow
Network baed Senor Localization in Multi-Media Application of Preciion Agriculture Part : Time of Arrival Herman Sahota IBM, Silicon Valley Laboratory Email: hahota@u.ibm.com Ratneh Kumar, IEEE Fellow
Optimal Coordination of Samples in Business Surveys
 Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
into a discrete time function. Recall that the table of Laplace/z-transforms is constructed by (i) selecting to get
 Lecture 25 Introduction to Some Matlab c2d Code in Relation to Sampled Sytem here are many way to convert a continuou time function, { h( t) ; t [0, )} into a dicrete time function { h ( k) ; k {0,,, }}
Lecture 25 Introduction to Some Matlab c2d Code in Relation to Sampled Sytem here are many way to convert a continuou time function, { h( t) ; t [0, )} into a dicrete time function { h ( k) ; k {0,,, }}
QAM Constellations for BICM-ID
 Efficient Multi-Dimensional Mapping Using 1 QAM Constellations for BICM-ID Hassan M. Navazi and Md. Jahangir Hossain, Member, IEEE arxiv:1701.01167v1 [cs.it] 30 Dec 2016 The University of British Columbia,
Efficient Multi-Dimensional Mapping Using 1 QAM Constellations for BICM-ID Hassan M. Navazi and Md. Jahangir Hossain, Member, IEEE arxiv:1701.01167v1 [cs.it] 30 Dec 2016 The University of British Columbia,
Complex CORDIC-like Algorithms for Linearly Constrained MVDR Beamforming
 Complex CORDIC-like Algorithm for Linearly Contrained MVDR Beamforming Mariu Otte (otte@dt.e-technik.uni-dortmund.de) Information Proceing Lab Univerity of Dortmund Otto Hahn Str. 4 44221 Dortmund, Germany
Complex CORDIC-like Algorithm for Linearly Contrained MVDR Beamforming Mariu Otte (otte@dt.e-technik.uni-dortmund.de) Information Proceing Lab Univerity of Dortmund Otto Hahn Str. 4 44221 Dortmund, Germany
Alternate Dispersion Measures in Replicated Factorial Experiments
 Alternate Diperion Meaure in Replicated Factorial Experiment Neal A. Mackertich The Raytheon Company, Sudbury MA 02421 Jame C. Benneyan Northeatern Univerity, Boton MA 02115 Peter D. Krau The Raytheon
Alternate Diperion Meaure in Replicated Factorial Experiment Neal A. Mackertich The Raytheon Company, Sudbury MA 02421 Jame C. Benneyan Northeatern Univerity, Boton MA 02115 Peter D. Krau The Raytheon
Lecture 17: Analytic Functions and Integrals (See Chapter 14 in Boas)
 Lecture 7: Analytic Function and Integral (See Chapter 4 in Boa) Thi i a good point to take a brief detour and expand on our previou dicuion of complex variable and complex function of complex variable.
Lecture 7: Analytic Function and Integral (See Chapter 4 in Boa) Thi i a good point to take a brief detour and expand on our previou dicuion of complex variable and complex function of complex variable.
Design of Digital Filters
 Deign of Digital Filter Paley-Wiener Theorem [ ] ( ) If h n i a caual energy ignal, then ln H e dω< B where B i a finite upper bound. One implication of the Paley-Wiener theorem i that a tranfer function
Deign of Digital Filter Paley-Wiener Theorem [ ] ( ) If h n i a caual energy ignal, then ln H e dω< B where B i a finite upper bound. One implication of the Paley-Wiener theorem i that a tranfer function
Random vs. Deterministic Deployment of Sensors in the Presence of Failures and Placement Errors
 Random v. Determinitic Deployment of Senor in the Preence of Failure and Placement Error Paul Baliter Univerity of Memphi pbalitr@memphi.edu Santoh Kumar Univerity of Memphi antoh.kumar@memphi.edu Abtract
Random v. Determinitic Deployment of Senor in the Preence of Failure and Placement Error Paul Baliter Univerity of Memphi pbalitr@memphi.edu Santoh Kumar Univerity of Memphi antoh.kumar@memphi.edu Abtract
Math 273 Solutions to Review Problems for Exam 1
 Math 7 Solution to Review Problem for Exam True or Fale? Circle ONE anwer for each Hint: For effective tudy, explain why if true and give a counterexample if fale (a) T or F : If a b and b c, then a c
Math 7 Solution to Review Problem for Exam True or Fale? Circle ONE anwer for each Hint: For effective tudy, explain why if true and give a counterexample if fale (a) T or F : If a b and b c, then a c
At the end of this lesson, the students should be able to understand:
 Intructional Objective: At the end of thi leon, the tudent hould be able to undertand: Baic failure mechanim of riveted joint. Concept of deign of a riveted joint. 1. Strength of riveted joint: Strength
Intructional Objective: At the end of thi leon, the tudent hould be able to undertand: Baic failure mechanim of riveted joint. Concept of deign of a riveted joint. 1. Strength of riveted joint: Strength
White Rose Research Online URL for this paper: Version: Accepted Version
 Thi i a repoitory copy of Identification of nonlinear ytem with non-peritent excitation uing an iterative forward orthogonal leat quare regreion algorithm. White Roe Reearch Online URL for thi paper: http://eprint.whiteroe.ac.uk/107314/
Thi i a repoitory copy of Identification of nonlinear ytem with non-peritent excitation uing an iterative forward orthogonal leat quare regreion algorithm. White Roe Reearch Online URL for thi paper: http://eprint.whiteroe.ac.uk/107314/
STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND
 OPERATIONS RESEARCH AND DECISIONS No. 4 203 DOI: 0.5277/ord30402 Marcin ANHOLCER STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND The generalized tranportation problem
OPERATIONS RESEARCH AND DECISIONS No. 4 203 DOI: 0.5277/ord30402 Marcin ANHOLCER STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND The generalized tranportation problem
On the Channel Capacity of Multilevel Modulation Schemes with Coherent Detection
 On the Channel Capacity of Multilevel Modulation Scheme with Coherent Detection Ivan B Djordjevic a Lei Xu b Ting Wang b a Univerity of Arizona Department of Electrical & Computer Engineering Tucon AZ
On the Channel Capacity of Multilevel Modulation Scheme with Coherent Detection Ivan B Djordjevic a Lei Xu b Ting Wang b a Univerity of Arizona Department of Electrical & Computer Engineering Tucon AZ
POWER SYSTEM SMALL SIGNAL STABILITY ANALYSIS BASED ON TEST SIGNAL
 POWE YEM MALL INAL ABILIY ANALYI BAE ON E INAL Zheng Xu, Wei hao, Changchun Zhou Zheang Univerity, Hangzhou, 37 PChina Email: hvdc@ceezueducn Abtract - In thi paper, a method baed on ome tet ignal (et
POWE YEM MALL INAL ABILIY ANALYI BAE ON E INAL Zheng Xu, Wei hao, Changchun Zhou Zheang Univerity, Hangzhou, 37 PChina Email: hvdc@ceezueducn Abtract - In thi paper, a method baed on ome tet ignal (et
By Xiaoquan Wen and Matthew Stephens University of Michigan and University of Chicago
 Submitted to the Annal of Applied Statitic SUPPLEMENTARY APPENDIX TO BAYESIAN METHODS FOR GENETIC ASSOCIATION ANALYSIS WITH HETEROGENEOUS SUBGROUPS: FROM META-ANALYSES TO GENE-ENVIRONMENT INTERACTIONS
Submitted to the Annal of Applied Statitic SUPPLEMENTARY APPENDIX TO BAYESIAN METHODS FOR GENETIC ASSOCIATION ANALYSIS WITH HETEROGENEOUS SUBGROUPS: FROM META-ANALYSES TO GENE-ENVIRONMENT INTERACTIONS
Characterizing the Effect of Channel Estimation Error on Distributed Reception with Hard Decision Exchanges
 Characterizing the Effect of Channel Etimation Error on Ditributed Reception with Hard Deciion Exchange Sabah Razavi and D. Richard Brown III Department of Electrical and Computer Engineering Worceter
Characterizing the Effect of Channel Etimation Error on Ditributed Reception with Hard Deciion Exchange Sabah Razavi and D. Richard Brown III Department of Electrical and Computer Engineering Worceter
NCAAPMT Calculus Challenge Challenge #3 Due: October 26, 2011
 NCAAPMT Calculu Challenge 011 01 Challenge #3 Due: October 6, 011 A Model of Traffic Flow Everyone ha at ome time been on a multi-lane highway and encountered road contruction that required the traffic
NCAAPMT Calculu Challenge 011 01 Challenge #3 Due: October 6, 011 A Model of Traffic Flow Everyone ha at ome time been on a multi-lane highway and encountered road contruction that required the traffic
C up (E) C low (E) E 2 E 1 E 0
 Spreading in lock-fading hannel. Muriel Médard David N.. Te medardmit.edu Maachuett Intitute of Technoy dteeec.berkeley.edu Univerity of alifornia at erkeley btract We conider wideband fading channel which
Spreading in lock-fading hannel. Muriel Médard David N.. Te medardmit.edu Maachuett Intitute of Technoy dteeec.berkeley.edu Univerity of alifornia at erkeley btract We conider wideband fading channel which
NULL HELIX AND k-type NULL SLANT HELICES IN E 4 1
 REVISTA DE LA UNIÓN MATEMÁTICA ARGENTINA Vol. 57, No. 1, 2016, Page 71 83 Publihed online: March 3, 2016 NULL HELIX AND k-type NULL SLANT HELICES IN E 4 1 JINHUA QIAN AND YOUNG HO KIM Abtract. We tudy
REVISTA DE LA UNIÓN MATEMÁTICA ARGENTINA Vol. 57, No. 1, 2016, Page 71 83 Publihed online: March 3, 2016 NULL HELIX AND k-type NULL SLANT HELICES IN E 4 1 JINHUA QIAN AND YOUNG HO KIM Abtract. We tudy
On the Isomorphism of Fractional Factorial Designs 1
 journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
V = 4 3 πr3. d dt V = d ( 4 dv dt. = 4 3 π d dt r3 dv π 3r2 dv. dt = 4πr 2 dr
 0.1 Related Rate In many phyical ituation we have a relationhip between multiple quantitie, and we know the rate at which one of the quantitie i changing. Oftentime we can ue thi relationhip a a convenient
0.1 Related Rate In many phyical ituation we have a relationhip between multiple quantitie, and we know the rate at which one of the quantitie i changing. Oftentime we can ue thi relationhip a a convenient
EXTENDED STABILITY MARGINS ON CONTROLLER DESIGN FOR NONLINEAR INPUT DELAY SYSTEMS. Otto J. Roesch, Hubert Roth, Asif Iqbal
 EXTENDED STABILITY MARGINS ON CONTROLLER DESIGN FOR NONLINEAR INPUT DELAY SYSTEMS Otto J. Roech, Hubert Roth, Aif Iqbal Intitute of Automatic Control Engineering Univerity Siegen, Germany {otto.roech,
EXTENDED STABILITY MARGINS ON CONTROLLER DESIGN FOR NONLINEAR INPUT DELAY SYSTEMS Otto J. Roech, Hubert Roth, Aif Iqbal Intitute of Automatic Control Engineering Univerity Siegen, Germany {otto.roech,
Convergence criteria and optimization techniques for beam moments
 Pure Appl. Opt. 7 (1998) 1221 1230. Printed in the UK PII: S0963-9659(98)90684-5 Convergence criteria and optimization technique for beam moment G Gbur and P S Carney Department of Phyic and Atronomy and
Pure Appl. Opt. 7 (1998) 1221 1230. Printed in the UK PII: S0963-9659(98)90684-5 Convergence criteria and optimization technique for beam moment G Gbur and P S Carney Department of Phyic and Atronomy and
Lecture #9 Continuous time filter
 Lecture #9 Continuou time filter Oliver Faut December 5, 2006 Content Review. Motivation......................................... 2 2 Filter pecification 2 2. Low pa..........................................
Lecture #9 Continuou time filter Oliver Faut December 5, 2006 Content Review. Motivation......................................... 2 2 Filter pecification 2 2. Low pa..........................................
Advanced Digital Signal Processing. Stationary/nonstationary signals. Time-Frequency Analysis... Some nonstationary signals. Time-Frequency Analysis
 Advanced Digital ignal Proceing Prof. Nizamettin AYDIN naydin@yildiz.edu.tr Time-Frequency Analyi http://www.yildiz.edu.tr/~naydin 2 tationary/nontationary ignal Time-Frequency Analyi Fourier Tranform
Advanced Digital ignal Proceing Prof. Nizamettin AYDIN naydin@yildiz.edu.tr Time-Frequency Analyi http://www.yildiz.edu.tr/~naydin 2 tationary/nontationary ignal Time-Frequency Analyi Fourier Tranform
arxiv: v2 [nucl-th] 3 May 2018
![arxiv: v2 [nucl-th] 3 May 2018 arxiv: v2 [nucl-th] 3 May 2018](/thumbs/89/101162462.jpg) DAMTP-207-44 An Alpha Particle Model for Carbon-2 J. I. Rawlinon arxiv:72.05658v2 [nucl-th] 3 May 208 Department of Applied Mathematic and Theoretical Phyic, Univerity of Cambridge, Wilberforce Road, Cambridge
DAMTP-207-44 An Alpha Particle Model for Carbon-2 J. I. Rawlinon arxiv:72.05658v2 [nucl-th] 3 May 208 Department of Applied Mathematic and Theoretical Phyic, Univerity of Cambridge, Wilberforce Road, Cambridge
If Y is normally Distributed, then and 2 Y Y 10. σ σ
 ull Hypothei Significance Teting V. APS 50 Lecture ote. B. Dudek. ot for General Ditribution. Cla Member Uage Only. Chi-Square and F-Ditribution, and Diperion Tet Recall from Chapter 4 material on: ( )
ull Hypothei Significance Teting V. APS 50 Lecture ote. B. Dudek. ot for General Ditribution. Cla Member Uage Only. Chi-Square and F-Ditribution, and Diperion Tet Recall from Chapter 4 material on: ( )
Solving Differential Equations by the Laplace Transform and by Numerical Methods
 36CH_PHCalter_TechMath_95099 3//007 :8 PM Page Solving Differential Equation by the Laplace Tranform and by Numerical Method OBJECTIVES When you have completed thi chapter, you hould be able to: Find the
36CH_PHCalter_TechMath_95099 3//007 :8 PM Page Solving Differential Equation by the Laplace Tranform and by Numerical Method OBJECTIVES When you have completed thi chapter, you hould be able to: Find the
An estimation approach for autotuning of event-based PI control systems
 Acta de la XXXIX Jornada de Automática, Badajoz, 5-7 de Septiembre de 08 An etimation approach for autotuning of event-baed PI control ytem Joé Sánchez Moreno, María Guinaldo Loada, Sebatián Dormido Departamento
Acta de la XXXIX Jornada de Automática, Badajoz, 5-7 de Septiembre de 08 An etimation approach for autotuning of event-baed PI control ytem Joé Sánchez Moreno, María Guinaldo Loada, Sebatián Dormido Departamento
Multi-dimensional Fuzzy Euler Approximation
 Mathematica Aeterna, Vol 7, 2017, no 2, 163-176 Multi-dimenional Fuzzy Euler Approximation Yangyang Hao College of Mathematic and Information Science Hebei Univerity, Baoding 071002, China hdhyywa@163com
Mathematica Aeterna, Vol 7, 2017, no 2, 163-176 Multi-dimenional Fuzzy Euler Approximation Yangyang Hao College of Mathematic and Information Science Hebei Univerity, Baoding 071002, China hdhyywa@163com
