Successive Refinement via Broadcast: Optimizing Expected Distortion of a Gaussian Source over a Gaussian Fading Channel
|
|
|
- Agatha Wilkerson
- 5 years ago
- Views:
Transcription
1 Succeive Refinement via Broadcat: Optimizing Expected Ditortion of a Gauian Source over a Gauian Fading Channel Chao Tian, Member, IEEE, Avi Steiner, Student Member, IEEE, Shlomo Shamai (Shitz, Fellow, IEEE and Suha N. Diggavi, Member, IEEE Abtract We conider the problem of tranmitting a Gauian ource on a lowly fading Gauian channel, ubject to the mean quared error ditortion meaure. The channel tate information i known only at the receiver but not at the tranmitter. The ource i aumed to be encoded in a ucceive refinement manner, and then tranmitted over the channel uing the broadcat trategy. In order to minimize the expected ditortion at the receiver, optimal power allocation i eential. We propoe an efficient algorithm to compute the optimal olution in linear time O(M, when the total number of poible dicrete fading tate i M. Moreover, we provide a derivation of the optimal power allocation when the fading tate i a continuum, uing the claical variational method. The propoed algorithm a well a the continuou olution i baed on an alternative repreentation of the capacity region of the Gauian broadcat channel. Index Term Broadcat trategy, joint ource-channel coding, power allocation, ucceive refinement. I. INTRODUCTION Fading channel occur naturally a a model in wirele communication. For low fading, the receiver can uually recover the channel tate information (CSI accurately, however the tranmitter only know the probability ditribution of CSI, but not the realization. Such uncertainty can caue ignificant ytem performance degradation, and the broadcat trategy wa ued in [], [] a an approach to combat thi detrimental effect. In thi trategy, ome information can only be decoded when the fading i le evere, which i uperimpoed on the information that can till be decoded when the fading i more evere. Thu the receiver can decode the information adaptively according to the realization of the channel tate. The imilarity to the degraded broadcat channel [3] (ee alo [4] i clear in thi context, particularly for channel with a finite number of fading tate. Generalizing thi view, when The work by C. Tian and S. Diggavi wa upported in part by Swi National Competence Center on Mobile Information and Communication Sytem (NCCR-MICS. The reearch by A. Steiner and S. Shamai wa upported by the EU, 7th framework program via NEWCOM++. The material in thi paper wa preented in part at 7 IEEE Information Theory Workhop on Information Theory for Wirele Network, Jul. 7, Bergen, Norway. C. Tian wa with School of Computer and Communication Science, Ecole Polytechnique Federale de Lauanne, Lauanne, CH5, Switzerland. He i now with AT&T Lab Reearch, 8 Park Avenue, Florham Park, NJ 793. A. Steiner and S. Shamai are with the Department of Electrical Engineering, Technion Irael Intitute of Technology, Haifa 3, Irael. S. Diggavi i with the School of Computer and Communication Science, Ecole Polytechnique Federale de Lauanne, Lauanne, CH5, Switzerland. the fading gain can take continuou value, the receiver can be taken a a continuum of uer in a broadcat channel. The broadcat trategy naturally matche the ucceive refinement (SR ource coding framework [5] [7], a the information decodable under the mot evere fading i protected the mot, and hould be ued to convey the bae layer information in the SR ource coding. A more information can be decoded when the channel i ubject to le fading, more SR encoded layer can be decoded, and the recontruction quality improve. In thi work, we conider thi cheme for a quadratic Gauian ource on a ingle input ingle output (SISO channel. In order to minimize the expected ditortion at the receiver, it i eential to find the optimal power allocation in the broadcat trategy, and thi i indeed our focu. It i worth noting that though in [] the objective function to be maximized i the expected rate, the cro layer deign approach of combining SR ource coding with broadcat trategy wa in fact uggeted (though not treated in that work. Initial effort on thi problem wa made by Seia et al. in [8], where the broadcat trategy coupled with SR ource coding wa compared with everal other cheme. The optimization problem wa formulated by dicretizing the continuou fading tate, and an algorithm wa devied when the ource coding layer are aumed to have the ame rate. Thi algorithm, however, doe not directly yield the optimal power allocation when the fading tate are dicrete and pre-pecified, nor doe it give a cloed-form olution for the continuou cae. Etemadi and Jafarkhani alo conidered thi problem in [9], and provided an iterative algorithm by eparating the optimization problem into two ub-problem. In two intereting recent work [], [], Ng et al. provided a recurive algorithm to compute the optimal power allocation for the cae with M poible fading tate, with wort cae complexity of O( M ; moreover, by directly taking the limit of the optimal olution for the dicrete cae, a olution wa given for the continuou cae optimal power allocation, under the aumption that the optimal power allocation i concentrated in a ingle interval. Similar problem were conidered in [] [5] in the high SNR regime from the perpective of ditortion exponent. Our contribution in the preent work i two-fold: firtly, we propoe a new algorithm that can compute in linear time, i.e., of O(M complexity, the optimal power allocation for the cae with M fading tate; econdly, we provide a derivation of the continuou cae optimal power allocation olution by
2 the claical variational method [6]. Our derivation for the continuou cae olution i more general than that in [] a it remove the retriction that the optimal power allocation i concentrated in a ingle interval. Both the algorithm and the derivation rely on an alternative repreentation of the Gauian broadcat channel capacity, which appeared in [7]. The dual problem of minimizing power conumption ubject to a given expected ditortion contraint i alo dicued. Several pecific example are given a illutration. The broadcat trategy coupled with SR ource coding can be conidered a a ource-channel eparation approach with optimized cro-layer reource allocation. More explicit joint ource-channel coding approache, for example thoe in [3], [8] [], may provide better performance in the cenario being conidered, however thi apect i beyond the cope of the preent work. We neverthele note that the algorithm propoed in the current work i extremely efficient, which make it poible to ue the broadcat trategy coupled with SR coding a a benchmark for future invetigation into thi joint ource-channel coding problem. Thi i indeed ueful ince an outer bound which i non-trivial yet imple to compute i o far lacking depite extenive reearch (ee [] and the comment therein. Moreover, a pointed out recently by Steinberg [], in certain application uch a medical imaging, it i important to enforce the requirement that the recontruction i a determinitic function of the ource obervation (the common knowledge requirement, and under thi requirement, the broadcat trategy coupled with SR ource coding i in fact optimal for the Gauian ource and channel etting conidered in thi work. The ret of the paper i organized a follow. In Section II we give the ytem model and ome preliminarie, and in Section III the new algorithm i provided and it optimality i proved; the dual problem of minimizing the power conumption ubject to an expected ditortion contraint i alo conidered. In Section IV we give the derivation for the continuou cae olution, and Section V ome pecial cae of fading ditribution are conidered. Finally Section VI conclude the paper. II. SYSTEM MODEL AND PRELIMINARIES We aume a memoryle ource {X i } i generated independently and identically according to a zero-mean unit variance real-valued Gauian ditribution. The channel i given by the model Y c = hx c + N c, ( where X c i the complex-valued channel input and Y c i the channel output, h i the (random multiplicative channel fading coefficient with h =, and N c CN(, i the zero-mean complex circularly-ymmetric independently and identically ditributed (i.i.d. Gauian additive noie. We conider a lowly fading channel model, where each channel codeword conit of a length-l c channel ymbol block, and the realization of the multiplicative fading coefficient i independent acro block. Source ymbol of block length-l are encoded into a ingle channel codeword, X l Fig.. l c X c p ( i = p i R M M M R i } M R Xˆ l D = exp( b i j= The broadcat approach for minimizing the expected ditortion. and there i a ource channel mimatch factor defined a b = l c /l ; thi mimatch factor can alo be interpreted a the bandwidth expanion/compreion factor. Thi ytem i illutrated in Fig.. Each channel block i aumed to be ufficiently long to approach channel capacity, a well a the rate-ditortion limit, however till much horter than the dynamic of the lowly fading proce. It i clear that without lo of generality each channel ue in the complex domain i equivalent to two channel ue in the real domain ubject to the ame power contraint a Y r = X r + N r, ( where X r i the real-value channel input, and R i the (random channel power gain, and N r N(, i the zeromean unit-variance real-valued Gauian additive noie in the channel. From here on, we hall adopt thi equivalent channel, and it i clear that the definition of ource-channel mimatch factor b already take thi into conideration. For the cae with a finite number of fading tate, the M poible power gain in an increaing order < <... < M are ditributed according to a probability ma function p i uch that M p i =. The tranmitter ha an average power contraint P, and if power P i i allocated to the i-th layer in the broadcat trategy, the i-th layer channel rate R i i given by R i = log( + i P i M + i j=i+ P j = log( + P i / i + M j=i+ P, (3 j where we ue natural logarithm. From the econd expreion, the equivalence to broadcat on a et of channel with different noie variance i clear. Let n i / i, which implie n > n >... > n M are the equivalent noie power on the channel. The layer correponding to maller value of i (and larger value of n i will be referred to a the lower layer, which i conitent with the intuition that they are ued to tranmit the better protected lower layer of the SR ource coding. Since the Gauian ource i ucceively refinable [6], the receiver with power gain i can thu recontruct the ource i
3 3 within ditortion D i = exp( b. (4 Combining (3 and (4, the problem we wih to olve i eentially the following minimization over the power allocation (P,P,...,P M, b M i min p i P j ( + / j + M k=j+ P (5 k ubject to: P i, i =,,...,M, M P i P. When the fading tate i continuou, the denity of the power gain ditribution i then given by f(, which i aumed to be continuou, and differentiable almot everywhere. In thi cae, the tak i to find a power allocation denity function P(, or it cumulative function, which minimize the expected ditortion. III. THE NEW ALGORITHM AND ITS OPTIMALITY In thi ection, we conider the optimization problem when the channel ha a finite number of fading tate. The difficulty i that the optimization problem a defined in (5 i not convenient for computation due to it complicated form. In fact it i not immediately clear that the function being optimized i a convex function of (P,P,...,P M, neverthele it i indeed clear that the rate-region of the degraded broadcat channel i alway convex. Thu our approach i to convert the problem given in (5 into a convex problem, by utilizing another characterization of R = (R,R,...,R M for the Gauian broadcat channel capacity. Such an alternative characterization wa given in [7], and we tart by tranlating it into our notation. A. Rederivation of the equivalent repreentation The rate vector R on the boundary of the Gauian broadcat capacity region correpond to a power allocation P,P,...,P M. Solving the value of P i in term of the rate vector R give an equivalent ytem of equation, and through further implification, we have i = i mp (n i n i+ exp n m, i m j=m m =,,3,...,M, (6 where we define n M+. The RHS of the above equation i monotonically decreaing in m, hence for any non-negative rate vector R, provided that (6 i atified for m =, i.e., P = i n i+ exp n, i (n The equation given in [7] appear to have a minor typographical error that the inner ummation wa given a i Rj. there mut be a power allocation uch that (6 i atified for all m, and it i on the boundary of the capacity region. Thu we can alternatively characterize the capacity region a C = (R,R,...,R M : R m, m =,,...,M, M (n i n i+ exp n P. (7 Moreover, the function on the left hand ide of thi inequality i convex in (R,R,...,R M, which i clear by oberving it um-exponential form. We can now reformulate the optimization problem a a tandard convex programming problem: min M p i exp( b ubject to: R i, i =,,...,M, M (n i n i+ exp ( i n P. If the optimal rate allocation R can be found, then the correponding optimal power allocation can be recovered from thi olution. B. The Lagrangian formulation and the algorithm Now conider the Lagrangian form L = M p i exp( b M ν i R i M + λ (n i n i+ exp n P. (8 The Karuh-Kuhn-Tucker (KKT condition require that L R m = for the optimal olution [], which ubequently yield L R m = + λ M bp i exp( b i=m M (n i n i+ exp i=m ν m =, m =,,...,M. (9 Taking the difference between L L R m = and R m+ = give m m bp m exp( b + λ(n m n m+ exp = ν m ν m+, m =,,...,M, ( where for convenience we define ν M+. λ and ν m, m =,,...,M are the Lagrangian multiplier. Furthermore, the complementary lackne require ν m R m =, m =,,...,M; the power contraint hould be atified with
4 4 equility, or λ =. Note that the et of equation in ( alo implie the et of equation (9, and thu they are equivalent. Since the optimization problem i a convex programming problem, the KKT condition i both neceary and ufficient for an optimal olution []. Clearly if the quantity bp m κ m n m n m+ i monotonically increaing, we can et ν i = for i =,,..., M and find an explicit olution, provided that the power contraint i not violated; however thi i not true in general. Neverthele, the κ factor play an extremely important role, which in fact reveal certain inherent tructure of the layer. We oberve the following imple fact to motivate the algorithm: whenever two conecutive layer yield two κ factor that are not increaing, ome combination of the layer mut occur uch that one layer i aigned zero rate. Thi i becaue otherwie the reulting rate vector would include negative rate, which i invalid. To be more precie, two conecutive layer are aid to be combined when the higher layer i not allocated any poitive rate (power, uch that the two layer can be treated a a ingle aggregated layer with the um-probability ma, and the power gain of the lower layer. The following algorithm can be ued to find the optimal rate allocation. In the equel, when a layer i aigned zero rate, it will be called ineffective; otherwie it will be called effective. For implicity, define κ M+ =. A layer i labeled active if it i a reult of combination of layer in the immediate previou loop. An intuitive explanation i given in the next ubection; the reader are encouraged to browe the algorithm below and read the intuitive explanation firt in their initial reading. Combination of layer to reach a monotonic κ equence. a Aign n m = n m n m+ and calculate κ m for m =,,...,M. Label all the layer effective and active. Let r =. b Denote the lower effective neighbor of layer i a i, and it upper effective neighbor layer a i +. Start from i k = i, for all the a r active layer i,i,...,i ar : i If i k > and κ i κ ik : label layer i k k ineffective and combine it with it current lower effective neighbor layer j. Update p j = p j + p ik, n j = n j + n ik, a well a κ j value accordingly. Label j a active. ii If κ ik κ i + : label layer i + k ineffective and k combine it with it current lower effective neighbor layer j. Update p j, n j and κ j value accordingly. Label j a active. iii If k < a r, increment k by and return to ((bi. c If after the above loop, any layer remain active: increment r by and return to (b. Denote the number of effective layer by K. For all the effective layer i k, k =,,...,K, let exp(r ik = κ /(b+ i k /κ /(b+ i k ; in other word for all the effective = κ /(b+. Aign the layer we have exp( i k i k ineffective layer rate zero. 3 Check power conumption. a Let i ko be the lowet effective layer, and define P n = P + n iko. b Let c If λ /(b+ = K k=k o (n ik n ik+ exp ( i k P n. bp iko, ( λ(n iko n iko+ then reduce R iko by (b+ log λ, and the algorithm terminate; otherwie, label i ko ineffective (R iko =, increment k o by, update P n = P + n iko, and return to (3b. C. The correctne of the algorithm and it complexity Intuitively, the layer are claified into two kind: thoe with κ value lower than or equal to their lower neighbor (the firt kind, and thoe with κ value higher than their lower neighbor (the econd kind; ee Fig.. The algorithm combine the firt kind layer to their lower neighbor in each tep, and then continue thi operation until no layer of the firt kind exit in the reulting equence. The reulting rate allocation i valid, if the κ equence i indeed monotonically increaing, the rate are non-negative and the power contraint i atified. A few more comment are in order: In Step, we eek to form a monotonic equence of κ i by combining conecutive layer, uch that Step can provide meaningful rate. To do thi, we combine (remove all the layer that are monotonically non-increaing. Only the neighbor of thoe layer whoe κ value were updated in the immediate previou loop need to be conidered, becaue thi i the only cae that a change of claification may occur. In Step 3, we need to aure that the total power i ued up by adjuting the value of λ. However, thi ha to be done uch that the lowet layer till ha poitive rate, which i the condition in (. If thi i not poible, the lowet effective layer i eliminated; thi condition i checked repeatedly for the reduced layer until it i atified. 3 In the loop of Step (b, we emphaize that the layer i combined with it current effective lower layer, becaue the layer i k (or i k may become ineffective in the previou tep. The complexity of the algorithm i O(M. Step i clearly of O(M complexity. In Step 3, λ i updated le than M time. A cloe inpection of the ummation in the numerator reveal that each time it can be done with O( complexity, and thu Step 3 i of O(M complexity. The complexity of Step i more ubtle. The value of κ i can be computed in O(M complexity. Denote the number of loop in Step a r ; denote the number of layer with κ value lower than or equal to it lower neighbor (the firt kind in the r-th loop
5 5 i Original value D. The optimality of the algorithm i i i i-th layer The t -loop i-th layer The nd -loop i-th layer Since we are olving a convex optimization problem, and it obviouly atifie Slater condition, the KKT condition are ufficient for optimality. Thu the proof for optimality reduce to finding ν i, that atify ( and the complementary lackne condition ν i R i =, i =,,...,M, with the olution found by the algorithm; note that the power contraint i already atified with equality. Theorem : The algorithm given above find the optimal rate allocation. Proof: Since for the effective layer R ik > by definition, we may et ν ik = to atify the complementary lackne condition. There are everal cae that we need to conider next: The ineffective layer above the lowet effective layer. The (originally effective layer which are rendered ineffective by the power contraint, i.e., the layer that become ineffective in Step 3. 3 Other ineffective layer below the lowet effective layer, i.e., the layer that become ineffective in Step and are below the lowet effective layer. The 3 rd -loop i-th layer Fig.. An example of the algorithm: the line with dot on the top are the layer of the firt kind, and dahed line are the active layer after the previou loop; the active layer are not labeled before the firt tep. In the example, Step- of the algorithm terminate after three loop. At each loop, ome layer are combined with it lower neighbor layer (and removed. a b r. The complexity in the r-th loop i bounded by linear term of b r, however b r a r, becaue only the active layer and their lower effective neighbor layer can be of the firt kind. Moreover, notice that r r= a r M, ince it i upper bounded by the total number of layer made ineffective, further implied by the fact that a layer i active only when a layer i made ineffective and combined into it. Clearly we have a = M, and thu r a r M. The overall complexity i thu O(M, and then the converion into power allocation i of O(M complexity. We note that in order to achieve the O(M complexity of the given algorithm, a fairly involved data tructure i needed. More preciely, a doubly-linked lit to update effective layer, coupled together with a ingly-linked lit to update the active layer (which can be combined into one linked-lit appear mot appropriate. However, even a naive implementation without uch data tructure i of O(M complexity, ince Step terminate within at mot M iteration, and each iteration ha maximum complexity O(M. For the firt cae, uppoe ome of thee layer are between two effective layer I and J, I J; if there are ineffective layer above the highet effective layer, we take J = M +. From Step 3 of the algorithm we can eentially aign the value of ρ exp( I uch that b[p I + p I p J + p J ]ρ b + λ(n I n J ρ =. ( Since layer I and J are effective, we et ν I = ν J =. By expanding the condition in (, we have bp k ρ b + λ(n k n k+ ρ ν k + ν k+ =, k = I,I +,...,J. (3 Though the above equation (under the olution found by the algorithm uniquely pecify ν i, I < i < J, it i not clear yet whether thoe value are indeed non-negative. We need the following lemma to proceed, the proof of which i given after the proof of the theorem. Lemma : For the combined layer between layer-i and layer-j, given any j uch that I j J, we have κ j b j i=i p i j i=i n i b J i=j + p i J i=j + n κ + j. (4 i Now we are ready to prove the non-negativene of ν i for the firt kind of ineffective layer. The value of ν i, where I < i < J, i alo pecified by J J b p i ρ b + λ n i ρ ν i =, i=i i=i (5 b p i ρ b + λ n i ρ + ν i =. (6 i=i i=i
6 6 To ee ν i thu pecified i indeed non-negative, uppoe ν i < wa true, then J J b p i ρ b + λ n i ρ = ν i < (7 i=i i=i Lemma aert that for i we have κ i = b i i=i p i i i=i n i which implie that b p i ρ b + λ n i ρ i=i κ + i = b J i=i p i J i=i n. (8 i i=i J b p i ρ b + λ i=i However thi ubequently implie J b i=i J p i ρ b + λ i=i J i=i n i ρ < (9 n i ρ <, ( which would contradict (; alternatively we ee that (9 would contradict (6 if the uppoition wa true. Thi prove that for the firt kind of ineffective layer, the given ν i are non-negative. We next conider the econd kind of ineffective layer. Suppoe the originally effective layer i k, i k+,...,i k+h become ineffective due to the power contraint. Since they are all effective originally, we have by the monotonicity of the κ factor bp i k n ik n ik+ bp i k+ n ik+ n ik+... bp i k+h n ik+h n ik+h+, ( where we have ued p to denote the accumulated probability ma after the combining of layer in Step but before Step 3. By Step 3 of the algorithm we have λ > bp i k+h n ik+h n ik+h+. ( Thu we only need to how the following equation pecify a et of non-negative ν i for i = i k,i k+,...,i k+h : bp i k+h +λ(n ik+h n ik+h+ ν ik+h =, bp i k+h +λ(n ik+h n ik+h ν ik+h + ν ik+h =, bp i k+ +λ(n ik+ n ik+ ν ik+ + ν ik+ =, bp i k +λ(n ik n ik+ ν ik + ν ik+ =. (3 From the firt equation, we get ν ik+h = bp i k+h + λ(n ik+h n ik+h+, and it i non-negative becaue of (. From the econd equation, we have ν ik+h = bp i k+h + λ(n ik+h n ik+h + ν ik+h, (4 which i alo non-negative, becaue bp i k+h + λ(n ik+h n ik+h due to ( and (, and the lat term i non-negative from the proceeding argument. Continue thi line of argument, then it i clear ν ik ν ik+... ν ik+h. (5 By thi we conclude that ν i for the econd kind of ineffective layer are indeed non-negative. For the third kind of ineffective layer, we might have to plit any given layer in the i k,i k+,...,i k+h layer, in order to recover the original layer a well a the correponding ν value. However, from any one of equation in (3, it i een that bp i k+a + λ(n ik+a n ik+a+ = ν ik+a ν ik+a+. (6 Now following the ame line of argument a the firt kind ineffective layer, we can indeed find the deired non-negative ν value for all the plit layer in Step of the algorithm. Thi complete the proof for the optimality of the algorithm. It now remain to prove Lemma, before which we firt give the following ueful fact. Lemma : When all the quantitie are poitive If a b a b... a n b n e f e f... e n f n, then we have ai ei. bi fi If a a... a n c + c e e... e m, b b b n d + d f f f m c and c, d d then we have ai + c ei + c. bi + d fi + d Thee fact are traightforward by elementary calculation and thu the detailed proof i omitted. Proof of Lemma We ue an induction approach and how thi fact i true after any loop in Step of the algorithm. The tatement i clearly true after the firt loop, by the given monotonicity of the κ equence for any combined layer before the operation, and the firt fact in Lemma. Then conider r-th tep for Step (b. For a given index j, let κ j,r and κ+ j,r denote the appropriate quantitie after tep r ; i.e., the quantitie defined in Lemma in the interval I to J for which layer j i in. Denote the updated layer that the original layer j i in a i. By the procedure, uppoe the aggregated layer after the (r -th loop i < i <... < i n < i < j < j <... < j m are to be combined into a new aggregated layer in the r-th loop, which atify κ i κ i... κ in κ i κ j κ j... κ jm, (7 a well a κ j,r κ+ j,r. (8
7 7 Then by the econd fact in Lemma, we have κ j,r κ+ j,r. Thi induction i apparently true for any loop in Step of the algorithm, thu the lemma i proved. E. The dual problem We can alo conider the dual problem of minimizing the power conumption for a given expected ditortion value. Thi can be done with eentially no change to the problem a M min (n i n i+ exp n P, ubject to: R i, i =,,...,M, M p i exp( b i D. The Lagrangian form i almot without change a L = λ M p i exp( b M ν i R i M + (n i n i+ exp n P. (9 The following condition imilar to ( can be derived, where again ν M+ m m λbp m exp( b + (n m n m+ exp = ν m ν m+ =, m =,,...,M. (3 From thi form we ee that the firt and econd tep of the algorithm can be ued without any change, and in the third tep of the algorithm, only very minor change are needed for thi dual problem. For implicity we combine the layer into the aggregated one and take the aggregated probability ma a p i. 3a Let i ko be the lowet effective layer, and define D = D p i ko. 3b Let 3c If λ /(b+ = D ( kk k=k o p i exp b. (3 i k λbp iko (n iko n iko+, then reduce R iko by (b+ log λ; otherwie, label i k o ineffective (R iko =, increment k o by, update D = D p i ko, and return to 3b. The proof of correctne and optimality remain virtually unchanged, and the complexity i alo unchanged. IV. VARIATIONAL DERIVATION OF THE CONTINUOUS CASE SOLUTION We next turn our attention to the cae of continuum of layer, which i in fact the cae conidered in []. To facilitate undertanding, we firt give a le technical derivation under the aumption that the optimal power allocation concentrate on a ingle interval of the power gain range, and how that thi i indeed true for ome probability denity function f(. Thi imple derivation provide important intuition for the general cae, baed on which a more general derivation i then given. For implicity, we firt aume f( ha upport on the entire non-negative real line [, ; later it i hown that thi aumption can be relaxed. A. A imple derivation for the ingle interval olution In thi ub-ection we give a imple derivation under the aumption that there i a unique interval [, ] which the power allocation concentrate on. The optimization problem can be reformulated a follow. Define I(i = exp(. (3 We take the number of layer to infinity, and the objective function the contraint become integral. The function I( we need to find i I( = exp( R(udu (33 where we convert back to the power gain intead of noie power n, and R( i the rate denity aociated with a fading gain. It i clear we can replace the inequality contraint by equality contraint without lo of optimality by writing the continuou counterpart of (6 a exp( R(udud = The term to be minimized i ( D(I = f(exp b I( d = P. (34 f( R(udu d = I( b d. (35 Note the additional condition that I( ha to be monotonically non-decreaing, and the boundary condition I( =. Ignoring the poitivity contraint I ( for now, take J(,I,I = f( I( b, G(,I,I = I(, the optimization problem can thu be written in the uual variational notation a minimize ubject to J(,I,I d, (36 G(,I,I d = P. (37
8 8 Next we aume there i a unique interval [, ] for which power allocation i non-zero. Under thi aumption, the objective function reduce to D(I = = J(,I,I d f( I( b d + F( + F( I( b, (38 where F( i the cumulative ditribution function of the fading gain random variable, i.e. F( = f(udu, and the contraint become P(I = = G(,I,I d I( d + I( = P. (39 We can write the Lagrangian form L(I = D(I+λ(P(I P. To find the extremal olution, we conider an increment q( on I(, and the increment of the Lagrangian functional i given by (q = L(I +q L(I. Take an arbitrary increment q( with q( = for / [, ] and q( =, and the principal linear part of the increment given in the following equation hould be zero (ee (7 p. 5, and pp. 4-5 in [6] h = δl(i = (J I + λg I dd [J I + λg I ] q(d h [ b( F( + (J I + λg I = q( + I( b+ + λ ] q( (4 where the lat term in the ummation i due to the term outide of the integration in (38 and (39. Since q( can be arbitrary, we have with J I + λg I d d [J I + λg I ] =, (4 J I = bf( I b+ (, G I =, J I = G I =, (4 which further implifie to ( bf( /(b+ I( =. (43 λ At thi point, it i clear that for I ( to be true, which i neceary for I( to be a valid olution, f( hould have non-negative derivative in any interval uch that (43 hold; in fact for any interval that poitive rate i allocated to, f( hould have trictly poitive derivative uch that I( i trictly increaing. If there i only one interval over the upport of f( where f( ha trictly poitive derivative, then the ingle interval olution aumption i indeed true. Now ince q( can be arbitrary, at thi variable end (pp. 5-9 in [6] a neceary condition for an extremum i b( F( I( b+ + λ =, (44 which give λ = b ( F( I( b+. (45 Becaue I( =, λ = bf(, the expreion of I( give one boundary condition F( = f(. (46 The lower bound i determined by the power contraint, from which we have I( ( /(b+ f( d = f( b/(b+ d + ( f( /(b+ f( = P +, (47 where in the econd equation we plit the integral into two part partitioned by =. We have thu found the unique extremal olution ( f( /(b+ I( = f( (48 in [, ] with the boundary condition pecified by (46 and (47. To find the correponding power allocation, define T( = T( = = P(rdr. We derive from (6 that ( f( f( I(r I(r dr /(b+ + ( f(rr f( /(b+ r dr. (49 For the continuou cae being conidered, the relation between T( and I( can alo be derived directly by olving a linear differential equation without uing (6, i.e., without taking the limit of the alternative channel capacity repreentation with a finite number of uer; ee the Appendix for detail. In fact, the derivation given in the Appendix can lead naturally to the contraint in (34 and (39. Through ome baic algebra, it can now be hown that (49 i in fact the ame olution a that in []. Thu the limit of the optimal olution of the dicrete cae in [] indeed converge to the extremal olution derived through the claical variational method. Moreover, the variational method derivation directly aert that f( ha a poitive derivative for any poitive power allocation interval; thi condition wa however lacking in the derivation in []. B. Derivation of the general cae olution Next we provide a more technical and complete derivation for the general cae when the power allocation doe not necearily concentrate in a ingle interval of the range of power gain. From the phyical meaning of I(, we aume that I( i a piecewie mooth continuou and differentiable function, and it i within thi function pace we eek the optimal olution. With the poitivity condition of I (,
9 9 the Lagrangian functional ubject to optimization can be written a ( f( L(I = I( b + λi( I (v( d (5 where v( i an arbitrary non-negative function; ee page 49 in [3]. The general extremum and ubidiary condition are then imilar a in the lat ub-ection, and we tate here for completene b f( I( b+ + λ + v ( = (5 and the complementary lackne condition are λ I( d P =, (5 I (v( = (53 We thu have the general olution for I( in ome interval where I (, ( bf( /b+ I( =, (54 λ which ha the ame form a given in the previou ub-ection. We firt oberve from the complementary lackne in (53 that for any I (, it mut be true that v( =. Thu for any interval [a,b] for which I (, it i een that bf( I b+ ( + λ =. (55 Thi implie that λ, becaue otherwie, I( = in thi interval, which clearly violate the power contraint. Then the firt complementary lackne condition require I( d P =. (56 Becaue for any interval [a,b] for which I ( >, we have bf( I b+ ( = λ, (57 it i clear that f( ha to have poitive derivative in any interval which are allocated with poitive rate (and power; if on the other hand thi condition i not atified, then I ( = for thi interval, and accordingly v( can be trictly poitive. Given the above dicuion, it i clear that dijoint interval with poitive rate (power allocation are eparated by interval where I ( =. Moreover, it will be hown in the equel that only a ingle continuou allocation interval may occur within a ingle interval where the derivative of f( i trictly poitive; we hall aume that the number of uch interval i finite. For implicity, aume that the firt uch interval ha the form [,a], i.e., the lower boundary i zero; thi condition can be relaxed a hown in the next ub-ection. Denote there are a total of K poitive power allocation interval, and let the i-th poitive power allocation interval be pecified by [ i,l, i,u ], and label the poitive f( derivative interval it belong to a the i-th uch interval, pecified by [l i,u i ]; i.e., [ i,l, i,u ] [l i,u i ]. For a piecewie mooth continuou extremal olution, the Weiertra-Erdmann (corner condition mut be atified (page 63 in [6]. Thee are given for every corner point c { i,l, i,u } K. The two condition are L I = c = L I = + c (L I L I = c = (L I. (58 L I = + c By ubtituting L(I from (5 into the corner condition (58, we get v( c = v( + c (59 and ( f( I( b + λi( + I (v( I (v( = c ( f( = I( b + λi( + I (v( I (v( = + c which further implifie into f( c I( c + b λi( c = f( c c I( + c + b λi(+ c c (6 (6 where (59 and (6 impoe certain continuity condition on v( and on I(, repectively. Thu v( = for [ i,l, i,u ] for all i =,,...,K, and i non-negative otherwie; from (59, we have v( + i,u = and v( i,l = for all i =,,...,K. The continuity of v( at the corner point doe not rely on the preumption that in the extremal olution, the power allocation in a ingle interval [l n,u n ] with poitive f( derivative doe not have within it more than one dijoint poitive power allocation ub-interval. We now prove that the preumption i indeed true. Suppoe otherwie, which implie the range (c,d [l n,u n ] i aigned with I ( =, and there exit c [l n,c and d (d,u n ] uch that I ( > in [c,c] and [d,d ]. We have that v(c = v(d =, (6 v ( = bf( I b+ (c λ for (c,d (63 bf(c I b+ (c λ =, c (64 where (6 i due to the preceding dicuion, (63 i due to (5, and (64 i due to (57, the continuity of I( and the continuou aumption on f(. Since f( ha trictly poitive derivative in (c,d, we have that in thi interval v ( = bf( I b+ (c λ >. (65 But thi contradict (6. Thu the uppoition can not be true, and there can be only one effective allocation interval in each uch firt kind interval [l n,u n ]. In order to determine all corner point c { i,l, i,u } K, we rewrite the original functional (5, a a piecewie opti-
10 δl(i = = K i,u i,l K i,u i,l (D I dd D I q(d + D I =i,u q( i,u D I =i,l q( i,l + K [ b F( ( i+,l F( i,u I( i,u b+ + λ ] q( i,u i,u i+,l ( bf( I b+ ( + λ K q(d + [ b F( ( i+,l F( i,u I( i,u b+ + λ ] q( i,u (67 i,u i+,l mization problem, and derive the variation. L(I = F(,l λ,l I (v(d,l K i,u ( f( + I( b + λi( I (v( d + i,l K F( i+,l F( i,u ( I( i,u b + λi( i,u i+,l i,u i,u i+,l I (v(dh (66 where we define K+,l, and thu F( K+,l =. The variation of L(I in (66 w.r.t. an arbitrary function q(, which atifie q ( = for / [ i,l, i,u ], i given by (67 at the top of thi page, where D(I f( + λ I( I( b I (v(. Note that for I( to remain a continuou function, it mut be true that q( i,u = q( i+,l. Hence the general olution extremal expreion i the ame a that afore-pecified, with an additional condition, ariing from the variable end-point problem imilar a in the previou ub-ection. Thi condition i given by b F( i+,l F( i,u I( i,u b+ + λ ( i,u i+,l =, (68 By uing the general olution for I( within [ i,l, i,u ] a given in (54, the condition (68 become ( F( i+,l F( i,u f( i,u =. (69 i,u i,u i+,l From the continuity condition on the corner point, i.e. I( i,u = I( i+,l the next condition i obtained f( i+,l i+,l = f( i,u i,u. (7 For i = K, the condition (69 implifie into which i (46 when K =. F( i,u = f( i,u i,u, (7 To ummarize, the extremal olution i given by ( /(b+ f( I( = f(,l, (7,l in the interval [ i,l, i,u ], i =,,...,K, and the boundary value are determined by F( i+,l F( i,u / i,u / i+,l = f( i,u i,u = f( i+,l i+,l, a well a the power contraint i =,,...,K, (73 I( d = P (74 Thee are the neceary condition to determine an extremum. C. Comment on relaxing the upport condition Until thi point, we have aumed that the pdf f( ha upport on the entire non-negative real line [, ], uch that the condition (69 and (7 (or (46 and (47 are ufficient to determine boundary value. Thi aumption can be relaxed to the cae that f( ha a compact upport, however certain complication will be introduced. To illutrate thi, we next treat one pecial cae where the upport of f( i on a ingle finite interval [ a, b ] and f( ha a unique poitive derivative interval [l,u ], uch that a l and b u ; the ame approach can be extended to more general upport. Without lo of generality, we can aume a = l and b > u. We hall follow the le general derivation a given in Section IV-A for implicity. The main difference now i that I( = i not necearily true if = a, i.e., it i poible for I( to be dicontinuou at a. In order to reolve thi difficult, firt aume > a, then indeed we have I( =, from which (46 and (47 follow. If the olution given by them indeed atifie l < u, then an extremal olution i pecified by thee boundarie. If on the other hand thi i not true, then = a and the condition I( = i not necearily true. Denote the value a I( a I. In thi cae, i.e. = a, the olution in [, ] can be written a I( = I ( f( f( a a /(b+. (75
11 The boundary condition (46 can till be derived. The other boundary condition derived from the power contraint i now given by ( f( /(b+ I f( a a d ( f( /(b+ ( + I f( a P =. a b (76 Thu for thi cae that = a, the olution i given by (75 with the value of and boundary function value I determined by (46 and (76. V. NUMERICAL EXAMPLES In thi ection, everal example are olved uing the olution developed in the previou ection. We tart with one example motivated by multiple acce with uer interference, then dicu the Rayleigh fading cae, finally a imple example i given for the general olution when the optimal power allocation doe not concentrate in a ingle interval. A. Interference multiple acce channel Conider here an additive white Gauian noie (AWGN channel with interfering uer. The goal by a ingle uer i to find the optimal power allocation of tranmitting in the preence of unknown interference by the other uer. The level of interference depend on the number of uer uing the multiple acce channel at a given tranmiion block. Such channel model were conidered, for example, in [4] [6]. More preciely, conider the following model y = x + N z i i + w (77 where y i the received ignal, and x i the multi-layer tranmitted real-valued ignal the uer can deign ubject to an average power contraint P. The additive interference z i are aumed to be Gauian ditributed, which are the ignal ent by other uer in thi time lot. Finally, w N(, i the additive noie in the channel. Every interference element z i i aociated with an average power level σi, and a random binary variable i to determine whether uer i i tranmitting at thi time lot. i i aumed to be i.i.d. Bernoulli random variable with Pr( i = = p on. The exact realization of the i are not known to uer j i, however it i aumed that the value of p on i known. Since the receiver ha no knowledge of z i and cannot attempt joint decoding, it ha to treat z i a AWGN when decoding x. Thu an equivalent channel model repreentation may be ueful, y = x + w, (78 + N σi i where w N(,. The equivalent fading gain j i then ( N j = + σi i, j =,.., N. (79 It i clear that there are N poible fading gain tate, which correpond to all poible tate of i. The optimal power allocation for multi-layer coding can be found by the dicrete layering algorithm preented in Section III-B. We demontrate by example of the optimal power allocation for two cae of interference ditribution. Figure 3.(a - 3.(d how the fading gain dicrete denity p i, the optimal dicrete power allocation P i and I i exp( i, repectively, where there are N = 4 interfering uer; the tranmit power i P = db; the bandwidth expanion i b = ; σ i, and p on are σ = (.95,.45,.55,.8, p on =.3 (8 The econd example i given in Figure 4.(a - 4.(d, where there are N = 6 interfering uer, with σ i, and p on pecified by σ = (.49,.9,.5,.87,.8,.46, p on =.5 (8 where the tranmit power and bandwidth expanion are the ame in both example. The reult may jut a well be generalized to the cae that p on i different for every uer, depending on the cheduling method in the ytem. B. The Rayleigh fading cae We conider here the SISO Rayleigh fading channel. Starting with the outage approach minimal ditortion, which i a ingle level coding ditortion bound. Thi i later compared to the minimal average ditortion with continuou broadcating. Outage approach: In cae there i only a ingle ource code and channel code, the tranmiion cheme i known a the outage approach. When channel condition allow, the data can be completely recovered, otherwie an outage event occur. Let the tranmiion rate be R R = log( + P, (8 where can be conidered a the fading gain threhold. For any, a rate R may be achieved, otherwie a failure occur uch that D =. Thi i in contrat with the continuou broadcating, where there i an outage region with different decodable rate depending on the fading gain realization. The obtained ditortion when decoding R i D = ( + P b. Under thi coding trategy, one can alo optimize the expected ditortion D,opt = min F( + ( + P b ( F(. (83 [, For a flat Rayleigh fading channel, the fading power ditribution i F( = e, the average ditortion then correpond to D,opt = min D( [, = min [, e + ( + P b e. (84
12 .4.3 p i, 4 interfering uer p i (a i 4 3 κ i κ i (b i.8.6 P i dicrete power allocation P i (c i I( i I( i (d i Fig. 3. An example of AWGN interference channel with N = 4 interfering uer (p on =.3, b =, P = db. (a pdf of the fading gain i, denoted by p i. (b The aociated κ i. (c Optimal dicrete power allocation P i. (d Optimal cumulative rate exponent I( i. The condition for extremum, i.e. following polynomial, d d D( =, yield the x b+ x + Pb = (85 where x + P. An explicit olution for,opt cannot be derived analytically in general for every b. However, for particular cae it can be analytically olved. For example, for b =, olving (85 give,,opt (b = = P ( + + 4P /P. (86 Continuou cae broadcat: We conider the average achievable ditortion for a SISO Rayleigh fading channel. Conider the following fading gain ditribution, F( = exp (, (87 where i the expected fading gain power. For thi ditribution the optimal power allocation i ingle interval continuou, and zero outide the interval [, ]. That can be immediately oberved from f( by taking it firt derivative d d f( = ( ( exp, (88 where d d f( on a ingle interval [,]. Then the upper bound [,] i determined by (46, which reduce to ( exp = ( exp (89 yielding =. Solving (47 give the other boundary value, denoted a,opt ; the condition (47 doe not lead to an analytical expreion, but can be olved numerically. Then the general expreion for I(, for the Rayleigh fading channel i given by,opt ( ( /(b+ I( = exp,opt,opt,opt < ( ( /(b+ >,opt exp,opt In Fig. 5, the average ditortion bound for Rayleigh fading channel are demontrated for three different value of bandwidth expanion value (b =.5,,. For every bandwidth expanion, the minimal average ditortion of the outage approach and broadcat approach are compared. It can be noticed that the larger b i, the larger i the broadcat.
13 3..5 p i, 6 interfering uer p i (a i 4 3 κ i κ i (b i.8.6 P i dicrete power allocation P i (c i.4.3 I( i I( i (d i Fig. 4. An example of AWGN interference channel with N = 6 interfering uer (p on =.3, b =, P = db. (a pdf of the fading gain i, denoted by p i. (b The aociated κ i. (c Optimal dicrete power allocation P i. (d Optimal cumulative rate exponent I( i.. parameter b. Average Ditortion 3 Continuou Broadcating, b=.5 Continuou Broadcating, b= Continuou Broadcating, b= Outage Approach, b=.5 Outage Approach, b= Outage Approach, b= SNR [db] Fig. 5. Minimal average ditortion, a comparion of outage approach and broadcat approach, for b =.5,,. C. An example with more than one power allocation interval Conider the following piece-wie mooth pdf f( (7c f (. + / [.,. ( 7c f( = f (. + 8/ [.,. (39c f (. + / (9 [.,3. ( 8c f ( / [3.,4.] where c f i a normalizing contant uch that f(d =, which can be computed to be c f Fig. 6 how pdf f(, f( and the optimal continuou power allocation denity P( with P = db. It i worth noting that at the upper bound for the firt effective power allocation interval and the lower bound of the econd interval, the value of f( i exactly the ame, a required by (73. gain, which can be defined a the SNR gain of the broadcat approach over the outage approach for the ame average ditortion value. Thu the benefit of the broadcat approach compared to the outage directly depend on the ytem deign VI. CONCLUSION We conidered the optimal power/rate allocation in the broadcat trategy, in order to minimize the expected ditortion of a quadratic Gauian ource tranmitted over a fading channel. A linear complexity algorithm i propoed, and it
14 f( f( P( Fig. 6. Optimal power allocation P( for f( given in (9 with the total power P = db. correctne and optimality are proved. Moreover, a derivation for the optimal allocation with a continuum of layer i given, uing the claical variational method. APPENDIX In thi appendix, we derive directly the relation between the power allocation and the rate allocation when there exit a continuum of uer, without relying on the alternative repreentation of the Gauian broadcat channel capacity with a finite number of uer given in [7]. Thi alo provide naturally the power contraint for the continuou cae given in (34 and (39. Denote the complementary power ditribution function by T(, i.e., T( = P(rdr a defined above (49; note that = without lo of generality we may aume T( = P. Then the incremental broadcating rate i R(d = T (d + T(. (9 By uing the definition I( = exp( we have the following relation R(udu a in (33, R(udu = log(i( (9 R(d = I (d I(. (93 In order to expre the power contraint a a function of I(, we need to olve the equation obtainable from (9 and (93, I (d I( = T (d + T(. (94 The above implifie by defining Q( I ( I( into T ( + Q(T( = Q(/. (95 The olution for the above tandard firt order differential equation i given by T( = c exp{ + exp{ duq(u} duq(u} c dr Q(r r exp{ r duq(u} (96 where c,c are contant. By ubtituting Q(u = I ( I(, the expreion for T( i implified a, T( = c I( + I( c dr I (r. (97 r Following the boundary condition T( = it i required to et c =, and by definition T( for every, therefore c =, hence T( = I( dr I (r. (98 r The above expreion i identical to (49, which i verified by another tep of of integration in part, that i T( = I( [I(r r ]r= r= + I( = I( dr I(r r (99 dr I(r r. ( It i worth noting that thi formula hold generally regardle the number of poitive power allocation interval. In the ingle interval cae, where T( i a decreaing function over [, ], and T( = P for and T( = for, (99 become the ubidiary condition a given in (39. In the general cae, (99 i equivalent to (56. REFERENCES [] S. Shamai, A broadcat trategy for the Gauian lowly fading channel, in Proc. IEEE International Sympoium on Information Theory, Ulm, Germany, 9 June-4 July 997, p. 5. [] S. Shamai and A. Steiner, A broadcat approach for ingle-uer lowly fading MIMO channel, IEEE Tran. Information Theory, vol. 49, no., pp , Oct. 3. [3] T. Cover, Broadcat channel, IEEE Tranaction on Information Theory, vol. 8, no., pp. 4, Jan. 97. [4] T. M. Cover and J. A. Thoma, Element of information theory. New York: Wiley, 99. [5] V. N. Kohelev, Hierarchical coding of dicrete ource, Probl. Pered. Inform., vol. 6, no. 3, pp. 3 49, 98. [6] W. H. R. Equitz and T. M. Cover, Succeive refinement of information, IEEE Tran. Information Theory, vol. 37, no., pp , Mar. 99. [7] B. Rimoldi, Succeive refinement of information: characterization of achievable rate, IEEE Tran. Information Theory, vol. 4, no., pp , Jan [8] S. Seia, G. Caire, and G. Vivier, Loy tranmiion over low-fading awgn channel: a comparion of progreive, uperpoition and hybrid approache, in Proc. IEEE International Sympoium on Information Theory, Adelaide, Autralia, Sep. 5, pp [9] F. Etemadi and H. Jafarkhani, Optimal layered tranmiion over quaitatic fading channel, in Proc. IEEE Sympoium Information Theory, Seattle, WA, Jul 6, pp
7.2 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 281
 72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
Lecture 21. The Lovasz splitting-off lemma Topics in Combinatorial Optimization April 29th, 2004
 18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
Amplify and Forward Relaying; Channel Model and Outage Behaviour
 Amplify and Forward Relaying; Channel Model and Outage Behaviour Mehdi Mortazawi Molu Intitute of Telecommunication Vienna Univerity of Technology Guhautr. 5/E389, 4 Vienna, Autria Email: mmortaza@nt.tuwien.ac.at
Amplify and Forward Relaying; Channel Model and Outage Behaviour Mehdi Mortazawi Molu Intitute of Telecommunication Vienna Univerity of Technology Guhautr. 5/E389, 4 Vienna, Autria Email: mmortaza@nt.tuwien.ac.at
Jul 4, 2005 turbo_code_primer Revision 0.0. Turbo Code Primer
 Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Signaling over MIMO Multi-Base Systems: Combination of Multi-Access and Broadcast Schemes
 Signaling over MIMO Multi-Bae Sytem: Combination of Multi-Acce and Broadcat Scheme Mohammad Ali Maddah-Ali Abolfazl S. Motahari and Amir K. Khandani Coding & Signal Tranmiion Laboratory (www.ct.uwaterloo.ca)
Signaling over MIMO Multi-Bae Sytem: Combination of Multi-Acce and Broadcat Scheme Mohammad Ali Maddah-Ali Abolfazl S. Motahari and Amir K. Khandani Coding & Signal Tranmiion Laboratory (www.ct.uwaterloo.ca)
IEOR 3106: Fall 2013, Professor Whitt Topics for Discussion: Tuesday, November 19 Alternating Renewal Processes and The Renewal Equation
 IEOR 316: Fall 213, Profeor Whitt Topic for Dicuion: Tueday, November 19 Alternating Renewal Procee and The Renewal Equation 1 Alternating Renewal Procee An alternating renewal proce alternate between
IEOR 316: Fall 213, Profeor Whitt Topic for Dicuion: Tueday, November 19 Alternating Renewal Procee and The Renewal Equation 1 Alternating Renewal Procee An alternating renewal proce alternate between
Preemptive scheduling on a small number of hierarchical machines
 Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
CDMA Signature Sequences with Low Peak-to-Average-Power Ratio via Alternating Projection
 CDMA Signature Sequence with Low Peak-to-Average-Power Ratio via Alternating Projection Joel A Tropp Int for Comp Engr and Sci (ICES) The Univerity of Texa at Autin 1 Univerity Station C0200 Autin, TX
CDMA Signature Sequence with Low Peak-to-Average-Power Ratio via Alternating Projection Joel A Tropp Int for Comp Engr and Sci (ICES) The Univerity of Texa at Autin 1 Univerity Station C0200 Autin, TX
Improved Interference Cancellation Scheme for Two-User Detection of Alamouti Code
 Improved Interference Cancellation Scheme for Two-Uer Detection of Alamouti Code Manav R hatnagar and Are Hjørungne Abtract In thi correpondence, we propoe an improved interference cancellation method
Improved Interference Cancellation Scheme for Two-Uer Detection of Alamouti Code Manav R hatnagar and Are Hjørungne Abtract In thi correpondence, we propoe an improved interference cancellation method
Codes Correcting Two Deletions
 1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
Social Studies 201 Notes for November 14, 2003
 1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
Control Systems Analysis and Design by the Root-Locus Method
 6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
Clustering Methods without Given Number of Clusters
 Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Social Studies 201 Notes for March 18, 2005
 1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
Bogoliubov Transformation in Classical Mechanics
 Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Convex Hulls of Curves Sam Burton
 Convex Hull of Curve Sam Burton 1 Introduction Thi paper will primarily be concerned with determining the face of convex hull of curve of the form C = {(t, t a, t b ) t [ 1, 1]}, a < b N in R 3. We hall
Convex Hull of Curve Sam Burton 1 Introduction Thi paper will primarily be concerned with determining the face of convex hull of curve of the form C = {(t, t a, t b ) t [ 1, 1]}, a < b N in R 3. We hall
A Constraint Propagation Algorithm for Determining the Stability Margin. The paper addresses the stability margin assessment for linear systems
 A Contraint Propagation Algorithm for Determining the Stability Margin of Linear Parameter Circuit and Sytem Lubomir Kolev and Simona Filipova-Petrakieva Abtract The paper addree the tability margin aement
A Contraint Propagation Algorithm for Determining the Stability Margin of Linear Parameter Circuit and Sytem Lubomir Kolev and Simona Filipova-Petrakieva Abtract The paper addree the tability margin aement
DYNAMIC MODELS FOR CONTROLLER DESIGN
 DYNAMIC MODELS FOR CONTROLLER DESIGN M.T. Tham (996,999) Dept. of Chemical and Proce Engineering Newcatle upon Tyne, NE 7RU, UK.. INTRODUCTION The problem of deigning a good control ytem i baically that
DYNAMIC MODELS FOR CONTROLLER DESIGN M.T. Tham (996,999) Dept. of Chemical and Proce Engineering Newcatle upon Tyne, NE 7RU, UK.. INTRODUCTION The problem of deigning a good control ytem i baically that
Problem Set 8 Solutions
 Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Theoretical Computer Science. Optimal algorithms for online scheduling with bounded rearrangement at the end
 Theoretical Computer Science 4 (0) 669 678 Content lit available at SciVere ScienceDirect Theoretical Computer Science journal homepage: www.elevier.com/locate/tc Optimal algorithm for online cheduling
Theoretical Computer Science 4 (0) 669 678 Content lit available at SciVere ScienceDirect Theoretical Computer Science journal homepage: www.elevier.com/locate/tc Optimal algorithm for online cheduling
Physics 741 Graduate Quantum Mechanics 1 Solutions to Final Exam, Fall 2014
 Phyic 7 Graduate Quantum Mechanic Solution to inal Eam all 0 Each quetion i worth 5 point with point for each part marked eparately Some poibly ueful formula appear at the end of the tet In four dimenion
Phyic 7 Graduate Quantum Mechanic Solution to inal Eam all 0 Each quetion i worth 5 point with point for each part marked eparately Some poibly ueful formula appear at the end of the tet In four dimenion
ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS. Volker Ziegler Technische Universität Graz, Austria
 GLASNIK MATEMATIČKI Vol. 1(61)(006), 9 30 ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS Volker Ziegler Techniche Univerität Graz, Autria Abtract. We conider the parameterized Thue
GLASNIK MATEMATIČKI Vol. 1(61)(006), 9 30 ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS Volker Ziegler Techniche Univerität Graz, Autria Abtract. We conider the parameterized Thue
A Study on Simulating Convolutional Codes and Turbo Codes
 A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
An Inequality for Nonnegative Matrices and the Inverse Eigenvalue Problem
 An Inequality for Nonnegative Matrice and the Invere Eigenvalue Problem Robert Ream Program in Mathematical Science The Univerity of Texa at Dalla Box 83688, Richardon, Texa 7583-688 Abtract We preent
An Inequality for Nonnegative Matrice and the Invere Eigenvalue Problem Robert Ream Program in Mathematical Science The Univerity of Texa at Dalla Box 83688, Richardon, Texa 7583-688 Abtract We preent
Singular perturbation theory
 Singular perturbation theory Marc R. Rouel June 21, 2004 1 Introduction When we apply the teady-tate approximation (SSA) in chemical kinetic, we typically argue that ome of the intermediate are highly
Singular perturbation theory Marc R. Rouel June 21, 2004 1 Introduction When we apply the teady-tate approximation (SSA) in chemical kinetic, we typically argue that ome of the intermediate are highly
New bounds for Morse clusters
 New bound for More cluter Tamá Vinkó Advanced Concept Team, European Space Agency, ESTEC Keplerlaan 1, 2201 AZ Noordwijk, The Netherland Tama.Vinko@ea.int and Arnold Neumaier Fakultät für Mathematik, Univerität
New bound for More cluter Tamá Vinkó Advanced Concept Team, European Space Agency, ESTEC Keplerlaan 1, 2201 AZ Noordwijk, The Netherland Tama.Vinko@ea.int and Arnold Neumaier Fakultät für Mathematik, Univerität
List coloring hypergraphs
 Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
Lit coloring hypergraph Penny Haxell Jacque Vertraete Department of Combinatoric and Optimization Univerity of Waterloo Waterloo, Ontario, Canada pehaxell@uwaterloo.ca Department of Mathematic Univerity
Unavoidable Cycles in Polynomial-Based Time-Invariant LDPC Convolutional Codes
 European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
Chapter 2 Sampling and Quantization. In order to investigate sampling and quantization, the difference between analog
 Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Stochastic Optimization with Inequality Constraints Using Simultaneous Perturbations and Penalty Functions
 Stochatic Optimization with Inequality Contraint Uing Simultaneou Perturbation and Penalty Function I-Jeng Wang* and Jame C. Spall** The John Hopkin Univerity Applied Phyic Laboratory 11100 John Hopkin
Stochatic Optimization with Inequality Contraint Uing Simultaneou Perturbation and Penalty Function I-Jeng Wang* and Jame C. Spall** The John Hopkin Univerity Applied Phyic Laboratory 11100 John Hopkin
ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION. Xiaoqun Wang
 Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS
 ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS VOLKER ZIEGLER Abtract We conider the parameterized Thue equation X X 3 Y (ab + (a + bx Y abxy 3 + a b Y = ±1, where a, b 1 Z uch that
ON A CERTAIN FAMILY OF QUARTIC THUE EQUATIONS WITH THREE PARAMETERS VOLKER ZIEGLER Abtract We conider the parameterized Thue equation X X 3 Y (ab + (a + bx Y abxy 3 + a b Y = ±1, where a, b 1 Z uch that
Convergence criteria and optimization techniques for beam moments
 Pure Appl. Opt. 7 (1998) 1221 1230. Printed in the UK PII: S0963-9659(98)90684-5 Convergence criteria and optimization technique for beam moment G Gbur and P S Carney Department of Phyic and Atronomy and
Pure Appl. Opt. 7 (1998) 1221 1230. Printed in the UK PII: S0963-9659(98)90684-5 Convergence criteria and optimization technique for beam moment G Gbur and P S Carney Department of Phyic and Atronomy and
Lecture 8: Period Finding: Simon s Problem over Z N
 Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
Energy-Distortion Tradeoff for the Gaussian Broadcast Channel with Feedback
 016 IEEE International Sympoium on Information Theory Energy-itortion Tradeoff for the Gauian Broadcat Channel with Feedback Yonathan Murin 1, Yonatan Kapi, Ron abora 3, and eniz Gündüz 4 1 Stanford Univerity,
016 IEEE International Sympoium on Information Theory Energy-itortion Tradeoff for the Gauian Broadcat Channel with Feedback Yonathan Murin 1, Yonatan Kapi, Ron abora 3, and eniz Gündüz 4 1 Stanford Univerity,
C up (E) C low (E) E 2 E 1 E 0
 Spreading in lock-fading hannel. Muriel Médard David N.. Te medardmit.edu Maachuett Intitute of Technoy dteeec.berkeley.edu Univerity of alifornia at erkeley btract We conider wideband fading channel which
Spreading in lock-fading hannel. Muriel Médard David N.. Te medardmit.edu Maachuett Intitute of Technoy dteeec.berkeley.edu Univerity of alifornia at erkeley btract We conider wideband fading channel which
Lecture 9: Shor s Algorithm
 Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS
 www.arpapre.com/volume/vol29iue1/ijrras_29_1_01.pdf RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS Sevcan Demir Atalay 1,* & Özge Elmataş Gültekin
www.arpapre.com/volume/vol29iue1/ijrras_29_1_01.pdf RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS Sevcan Demir Atalay 1,* & Özge Elmataş Gültekin
UNIT 15 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS
 UNIT 1 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS Structure 1.1 Introduction Objective 1.2 Redundancy 1.3 Reliability of k-out-of-n Sytem 1.4 Reliability of Standby Sytem 1. Summary 1.6 Solution/Anwer
UNIT 1 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS Structure 1.1 Introduction Objective 1.2 Redundancy 1.3 Reliability of k-out-of-n Sytem 1.4 Reliability of Standby Sytem 1. Summary 1.6 Solution/Anwer
Assignment for Mathematics for Economists Fall 2016
 Due date: Mon. Nov. 1. Reading: CSZ, Ch. 5, Ch. 8.1 Aignment for Mathematic for Economit Fall 016 We now turn to finihing our coverage of concavity/convexity. There are two part: Jenen inequality for concave/convex
Due date: Mon. Nov. 1. Reading: CSZ, Ch. 5, Ch. 8.1 Aignment for Mathematic for Economit Fall 016 We now turn to finihing our coverage of concavity/convexity. There are two part: Jenen inequality for concave/convex
Chapter 4. The Laplace Transform Method
 Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
The Hassenpflug Matrix Tensor Notation
 The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
THE THERMOELASTIC SQUARE
 HE HERMOELASIC SQUARE A mnemonic for remembering thermodynamic identitie he tate of a material i the collection of variable uch a tre, train, temperature, entropy. A variable i a tate variable if it integral
HE HERMOELASIC SQUARE A mnemonic for remembering thermodynamic identitie he tate of a material i the collection of variable uch a tre, train, temperature, entropy. A variable i a tate variable if it integral
EE Control Systems LECTURE 6
 Copyright FL Lewi 999 All right reerved EE - Control Sytem LECTURE 6 Updated: Sunday, February, 999 BLOCK DIAGRAM AND MASON'S FORMULA A linear time-invariant (LTI) ytem can be repreented in many way, including:
Copyright FL Lewi 999 All right reerved EE - Control Sytem LECTURE 6 Updated: Sunday, February, 999 BLOCK DIAGRAM AND MASON'S FORMULA A linear time-invariant (LTI) ytem can be repreented in many way, including:
Suggested Answers To Exercises. estimates variability in a sampling distribution of random means. About 68% of means fall
 Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Lecture 10 Filtering: Applied Concepts
 Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
Gain and Phase Margins Based Delay Dependent Stability Analysis of Two- Area LFC System with Communication Delays
 Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
CONGESTION control is a key functionality in modern
 IEEE TRANSACTIONS ON INFORMATION TEORY, VOL. X, NO. X, XXXXXXX 2008 On the Connection-Level Stability of Congetion-Controlled Communication Network Xiaojun Lin, Member, IEEE, Ne B. Shroff, Fellow, IEEE,
IEEE TRANSACTIONS ON INFORMATION TEORY, VOL. X, NO. X, XXXXXXX 2008 On the Connection-Level Stability of Congetion-Controlled Communication Network Xiaojun Lin, Member, IEEE, Ne B. Shroff, Fellow, IEEE,
A SIMPLE NASH-MOSER IMPLICIT FUNCTION THEOREM IN WEIGHTED BANACH SPACES. Sanghyun Cho
 A SIMPLE NASH-MOSER IMPLICIT FUNCTION THEOREM IN WEIGHTED BANACH SPACES Sanghyun Cho Abtract. We prove a implified verion of the Nah-Moer implicit function theorem in weighted Banach pace. We relax the
A SIMPLE NASH-MOSER IMPLICIT FUNCTION THEOREM IN WEIGHTED BANACH SPACES Sanghyun Cho Abtract. We prove a implified verion of the Nah-Moer implicit function theorem in weighted Banach pace. We relax the
SOME RESULTS ON INFINITE POWER TOWERS
 NNTDM 16 2010) 3, 18-24 SOME RESULTS ON INFINITE POWER TOWERS Mladen Vailev - Miana 5, V. Hugo Str., Sofia 1124, Bulgaria E-mail:miana@abv.bg Abtract To my friend Kratyu Gumnerov In the paper the infinite
NNTDM 16 2010) 3, 18-24 SOME RESULTS ON INFINITE POWER TOWERS Mladen Vailev - Miana 5, V. Hugo Str., Sofia 1124, Bulgaria E-mail:miana@abv.bg Abtract To my friend Kratyu Gumnerov In the paper the infinite
Technical Appendix: Auxiliary Results and Proofs
 A Technical Appendix: Auxiliary Reult and Proof Lemma A. The following propertie hold for q (j) = F r [c + ( ( )) ] de- ned in Lemma. (i) q (j) >, 8 (; ]; (ii) R q (j)d = ( ) q (j) + R q (j)d ; (iii) R
A Technical Appendix: Auxiliary Reult and Proof Lemma A. The following propertie hold for q (j) = F r [c + ( ( )) ] de- ned in Lemma. (i) q (j) >, 8 (; ]; (ii) R q (j)d = ( ) q (j) + R q (j)d ; (iii) R
One Class of Splitting Iterative Schemes
 One Cla of Splitting Iterative Scheme v Ciegi and V. Pakalnytė Vilniu Gedimina Technical Univerity Saulėtekio al. 11, 2054, Vilniu, Lithuania rc@fm.vtu.lt Abtract. Thi paper deal with the tability analyi
One Cla of Splitting Iterative Scheme v Ciegi and V. Pakalnytė Vilniu Gedimina Technical Univerity Saulėtekio al. 11, 2054, Vilniu, Lithuania rc@fm.vtu.lt Abtract. Thi paper deal with the tability analyi
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS
 CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
Multicolor Sunflowers
 Multicolor Sunflower Dhruv Mubayi Lujia Wang October 19, 2017 Abtract A unflower i a collection of ditinct et uch that the interection of any two of them i the ame a the common interection C of all of
Multicolor Sunflower Dhruv Mubayi Lujia Wang October 19, 2017 Abtract A unflower i a collection of ditinct et uch that the interection of any two of them i the ame a the common interection C of all of
The Secret Life of the ax + b Group
 The Secret Life of the ax + b Group Linear function x ax + b are prominent if not ubiquitou in high chool mathematic, beginning in, or now before, Algebra I. In particular, they are prime exhibit in any
The Secret Life of the ax + b Group Linear function x ax + b are prominent if not ubiquitou in high chool mathematic, beginning in, or now before, Algebra I. In particular, they are prime exhibit in any
SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lectures 41-48)
 Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Design By Emulation (Indirect Method)
 Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
Alternate Dispersion Measures in Replicated Factorial Experiments
 Alternate Diperion Meaure in Replicated Factorial Experiment Neal A. Mackertich The Raytheon Company, Sudbury MA 02421 Jame C. Benneyan Northeatern Univerity, Boton MA 02115 Peter D. Krau The Raytheon
Alternate Diperion Meaure in Replicated Factorial Experiment Neal A. Mackertich The Raytheon Company, Sudbury MA 02421 Jame C. Benneyan Northeatern Univerity, Boton MA 02115 Peter D. Krau The Raytheon
Source slideplayer.com/fundamentals of Analytical Chemistry, F.J. Holler, S.R.Crouch. Chapter 6: Random Errors in Chemical Analysis
 Source lideplayer.com/fundamental of Analytical Chemitry, F.J. Holler, S.R.Crouch Chapter 6: Random Error in Chemical Analyi Random error are preent in every meaurement no matter how careful the experimenter.
Source lideplayer.com/fundamental of Analytical Chemitry, F.J. Holler, S.R.Crouch Chapter 6: Random Error in Chemical Analyi Random error are preent in every meaurement no matter how careful the experimenter.
Fast Convolutional Sparse Coding (FCSC)
 Fat Convolutional Spare Coding (FCSC) Bailey ong Department of Computer Science Univerity of California, Irvine bhkong@ic.uci.edu Charle C. Fowlke Department of Computer Science Univerity of California,
Fat Convolutional Spare Coding (FCSC) Bailey ong Department of Computer Science Univerity of California, Irvine bhkong@ic.uci.edu Charle C. Fowlke Department of Computer Science Univerity of California,
Dimensional Analysis A Tool for Guiding Mathematical Calculations
 Dimenional Analyi A Tool for Guiding Mathematical Calculation Dougla A. Kerr Iue 1 February 6, 2010 ABSTRACT AND INTRODUCTION In converting quantitie from one unit to another, we may know the applicable
Dimenional Analyi A Tool for Guiding Mathematical Calculation Dougla A. Kerr Iue 1 February 6, 2010 ABSTRACT AND INTRODUCTION In converting quantitie from one unit to another, we may know the applicable
Performance Degradation due to I/Q Imbalance in Multi-Carrier Direct Conversion Receivers: A Theoretical Analysis
 Performance egradation due to I/Q Imbalance in Multi-Carrier irect Converion Receiver: A Theoretical Analyi Marcu Windich, Gerhard Fettwei reden Univerity of Technology, Vodafone Chair Mobile Communication
Performance egradation due to I/Q Imbalance in Multi-Carrier irect Converion Receiver: A Theoretical Analyi Marcu Windich, Gerhard Fettwei reden Univerity of Technology, Vodafone Chair Mobile Communication
arxiv: v1 [math.mg] 25 Aug 2011
![arxiv: v1 [math.mg] 25 Aug 2011 arxiv: v1 [math.mg] 25 Aug 2011](/thumbs/72/67862976.jpg) ABSORBING ANGLES, STEINER MINIMAL TREES, AND ANTIPODALITY HORST MARTINI, KONRAD J. SWANEPOEL, AND P. OLOFF DE WET arxiv:08.5046v [math.mg] 25 Aug 20 Abtract. We give a new proof that a tar {op i : i =,...,
ABSORBING ANGLES, STEINER MINIMAL TREES, AND ANTIPODALITY HORST MARTINI, KONRAD J. SWANEPOEL, AND P. OLOFF DE WET arxiv:08.5046v [math.mg] 25 Aug 20 Abtract. We give a new proof that a tar {op i : i =,...,
Optimal revenue management in two class pre-emptive delay dependent Markovian queues
 Optimal revenue management in two cla pre-emptive delay dependent Markovian queue Manu K. Gupta, N. Hemachandra and J. Venkatewaran Indutrial Engineering and Operation Reearch, IIT Bombay March 15, 2015
Optimal revenue management in two cla pre-emptive delay dependent Markovian queue Manu K. Gupta, N. Hemachandra and J. Venkatewaran Indutrial Engineering and Operation Reearch, IIT Bombay March 15, 2015
III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SUBSTANCES
 III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SBSTANCES. Work purpoe The analyi of the behaviour of a ferroelectric ubtance placed in an eternal electric field; the dependence of the electrical polariation
III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SBSTANCES. Work purpoe The analyi of the behaviour of a ferroelectric ubtance placed in an eternal electric field; the dependence of the electrical polariation
The Impact of Imperfect Scheduling on Cross-Layer Rate. Control in Multihop Wireless Networks
 The mpact of mperfect Scheduling on Cro-Layer Rate Control in Multihop Wirele Network Xiaojun Lin and Ne B. Shroff Center for Wirele Sytem and Application (CWSA) School of Electrical and Computer Engineering,
The mpact of mperfect Scheduling on Cro-Layer Rate Control in Multihop Wirele Network Xiaojun Lin and Ne B. Shroff Center for Wirele Sytem and Application (CWSA) School of Electrical and Computer Engineering,
Utility Proportional Fair Bandwidth Allocation: An Optimization Oriented Approach
 Utility Proportional Fair Bandwidth Allocation: An Optimization Oriented Approach 61 Tobia Hark Konrad-Zue-Zentrum für Informationtechnik Berlin (ZIB), Department Optimization, Takutr. 7, 14195 Berlin,
Utility Proportional Fair Bandwidth Allocation: An Optimization Oriented Approach 61 Tobia Hark Konrad-Zue-Zentrum für Informationtechnik Berlin (ZIB), Department Optimization, Takutr. 7, 14195 Berlin,
Efficient Methods of Doppler Processing for Coexisting Land and Weather Clutter
 Efficient Method of Doppler Proceing for Coexiting Land and Weather Clutter Ça gatay Candan and A Özgür Yılmaz Middle Eat Technical Univerity METU) Ankara, Turkey ccandan@metuedutr, aoyilmaz@metuedutr
Efficient Method of Doppler Proceing for Coexiting Land and Weather Clutter Ça gatay Candan and A Özgür Yılmaz Middle Eat Technical Univerity METU) Ankara, Turkey ccandan@metuedutr, aoyilmaz@metuedutr
ALLOCATING BANDWIDTH FOR BURSTY CONNECTIONS
 SIAM J. COMPUT. Vol. 30, No. 1, pp. 191 217 c 2000 Society for Indutrial and Applied Mathematic ALLOCATING BANDWIDTH FOR BURSTY CONNECTIONS JON KLEINBERG, YUVAL RABANI, AND ÉVA TARDOS Abtract. In thi paper,
SIAM J. COMPUT. Vol. 30, No. 1, pp. 191 217 c 2000 Society for Indutrial and Applied Mathematic ALLOCATING BANDWIDTH FOR BURSTY CONNECTIONS JON KLEINBERG, YUVAL RABANI, AND ÉVA TARDOS Abtract. In thi paper,
EC381/MN308 Probability and Some Statistics. Lecture 7 - Outline. Chapter Cumulative Distribution Function (CDF) Continuous Random Variables
 EC38/MN38 Probability and Some Statitic Yanni Pachalidi yannip@bu.edu, http://ionia.bu.edu/ Lecture 7 - Outline. Continuou Random Variable Dept. of Manufacturing Engineering Dept. of Electrical and Computer
EC38/MN38 Probability and Some Statitic Yanni Pachalidi yannip@bu.edu, http://ionia.bu.edu/ Lecture 7 - Outline. Continuou Random Variable Dept. of Manufacturing Engineering Dept. of Electrical and Computer
Then C pid (s) S h -stabilizes G(s) if and only if Ĉpid(ŝ) S 0 - stabilizes Ĝ(ŝ). For any ρ R +, an RCF of Ĉ pid (ŝ) is given by
 9 American Control Conference Hyatt Regency Riverfront, St. Loui, MO, USA June -, 9 WeC5.5 PID Controller Synthei with Shifted Axi Pole Aignment for a Cla of MIMO Sytem A. N. Gündeş and T. S. Chang Abtract
9 American Control Conference Hyatt Regency Riverfront, St. Loui, MO, USA June -, 9 WeC5.5 PID Controller Synthei with Shifted Axi Pole Aignment for a Cla of MIMO Sytem A. N. Gündeş and T. S. Chang Abtract
Online Appendix for Managerial Attention and Worker Performance by Marina Halac and Andrea Prat
 Online Appendix for Managerial Attention and Worker Performance by Marina Halac and Andrea Prat Thi Online Appendix contain the proof of our reult for the undicounted limit dicued in Section 2 of the paper,
Online Appendix for Managerial Attention and Worker Performance by Marina Halac and Andrea Prat Thi Online Appendix contain the proof of our reult for the undicounted limit dicued in Section 2 of the paper,
EXTENDED STABILITY MARGINS ON CONTROLLER DESIGN FOR NONLINEAR INPUT DELAY SYSTEMS. Otto J. Roesch, Hubert Roth, Asif Iqbal
 EXTENDED STABILITY MARGINS ON CONTROLLER DESIGN FOR NONLINEAR INPUT DELAY SYSTEMS Otto J. Roech, Hubert Roth, Aif Iqbal Intitute of Automatic Control Engineering Univerity Siegen, Germany {otto.roech,
EXTENDED STABILITY MARGINS ON CONTROLLER DESIGN FOR NONLINEAR INPUT DELAY SYSTEMS Otto J. Roech, Hubert Roth, Aif Iqbal Intitute of Automatic Control Engineering Univerity Siegen, Germany {otto.roech,
Nonlinear Single-Particle Dynamics in High Energy Accelerators
 Nonlinear Single-Particle Dynamic in High Energy Accelerator Part 6: Canonical Perturbation Theory Nonlinear Single-Particle Dynamic in High Energy Accelerator Thi coure conit of eight lecture: 1. Introduction
Nonlinear Single-Particle Dynamic in High Energy Accelerator Part 6: Canonical Perturbation Theory Nonlinear Single-Particle Dynamic in High Energy Accelerator Thi coure conit of eight lecture: 1. Introduction
Advanced D-Partitioning Analysis and its Comparison with the Kharitonov s Theorem Assessment
 Journal of Multidiciplinary Engineering Science and Technology (JMEST) ISSN: 59- Vol. Iue, January - 5 Advanced D-Partitioning Analyi and it Comparion with the haritonov Theorem Aement amen M. Yanev Profeor,
Journal of Multidiciplinary Engineering Science and Technology (JMEST) ISSN: 59- Vol. Iue, January - 5 Advanced D-Partitioning Analyi and it Comparion with the haritonov Theorem Aement amen M. Yanev Profeor,
Optimal Coordination of Samples in Business Surveys
 Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
1. The F-test for Equality of Two Variances
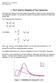 . The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
. The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
March 18, 2014 Academic Year 2013/14
 POLITONG - SHANGHAI BASIC AUTOMATIC CONTROL Exam grade March 8, 4 Academic Year 3/4 NAME (Pinyin/Italian)... STUDENT ID Ue only thee page (including the back) for anwer. Do not ue additional heet. Ue of
POLITONG - SHANGHAI BASIC AUTOMATIC CONTROL Exam grade March 8, 4 Academic Year 3/4 NAME (Pinyin/Italian)... STUDENT ID Ue only thee page (including the back) for anwer. Do not ue additional heet. Ue of
A Note on the Sum of Correlated Gamma Random Variables
 1 A Note on the Sum of Correlated Gamma Random Variable Joé F Pari Abtract arxiv:11030505v1 [cit] 2 Mar 2011 The um of correlated gamma random variable appear in the analyi of many wirele communication
1 A Note on the Sum of Correlated Gamma Random Variable Joé F Pari Abtract arxiv:11030505v1 [cit] 2 Mar 2011 The um of correlated gamma random variable appear in the analyi of many wirele communication
Learning Multiplicative Interactions
 CSC2535 2011 Lecture 6a Learning Multiplicative Interaction Geoffrey Hinton Two different meaning of multiplicative If we take two denity model and multiply together their probability ditribution at each
CSC2535 2011 Lecture 6a Learning Multiplicative Interaction Geoffrey Hinton Two different meaning of multiplicative If we take two denity model and multiply together their probability ditribution at each
FUNDAMENTALS OF POWER SYSTEMS
 1 FUNDAMENTALS OF POWER SYSTEMS 1 Chapter FUNDAMENTALS OF POWER SYSTEMS INTRODUCTION The three baic element of electrical engineering are reitor, inductor and capacitor. The reitor conume ohmic or diipative
1 FUNDAMENTALS OF POWER SYSTEMS 1 Chapter FUNDAMENTALS OF POWER SYSTEMS INTRODUCTION The three baic element of electrical engineering are reitor, inductor and capacitor. The reitor conume ohmic or diipative
Evolutionary Algorithms Based Fixed Order Robust Controller Design and Robustness Performance Analysis
 Proceeding of 01 4th International Conference on Machine Learning and Computing IPCSIT vol. 5 (01) (01) IACSIT Pre, Singapore Evolutionary Algorithm Baed Fixed Order Robut Controller Deign and Robutne
Proceeding of 01 4th International Conference on Machine Learning and Computing IPCSIT vol. 5 (01) (01) IACSIT Pre, Singapore Evolutionary Algorithm Baed Fixed Order Robut Controller Deign and Robutne
Inference for Two Stage Cluster Sampling: Equal SSU per PSU. Projections of SSU Random Variables on Each SSU selection.
 Inference for Two Stage Cluter Sampling: Equal SSU per PSU Projection of SSU andom Variable on Eac SSU election By Ed Stanek Introduction We review etimating equation for PSU mean in a two tage cluter
Inference for Two Stage Cluter Sampling: Equal SSU per PSU Projection of SSU andom Variable on Eac SSU election By Ed Stanek Introduction We review etimating equation for PSU mean in a two tage cluter
Beyond Cut-Set Bounds - The Approximate Capacity of D2D Networks
 Beyond Cut-Set Bound - The Approximate Capacity of DD Network Avik Sengupta Hume Center for National Security and Technology Department of Electrical and Computer Engineering Virginia Tech, Blackburg,
Beyond Cut-Set Bound - The Approximate Capacity of DD Network Avik Sengupta Hume Center for National Security and Technology Department of Electrical and Computer Engineering Virginia Tech, Blackburg,
Bayesian-Based Decision Making for Object Search and Characterization
 9 American Control Conference Hyatt Regency Riverfront, St. Loui, MO, USA June -, 9 WeC9. Bayeian-Baed Deciion Making for Object Search and Characterization Y. Wang and I. I. Huein Abtract Thi paper focue
9 American Control Conference Hyatt Regency Riverfront, St. Loui, MO, USA June -, 9 WeC9. Bayeian-Baed Deciion Making for Object Search and Characterization Y. Wang and I. I. Huein Abtract Thi paper focue
Lecture 4 Topic 3: General linear models (GLMs), the fundamentals of the analysis of variance (ANOVA), and completely randomized designs (CRDs)
 Lecture 4 Topic 3: General linear model (GLM), the fundamental of the analyi of variance (ANOVA), and completely randomized deign (CRD) The general linear model One population: An obervation i explained
Lecture 4 Topic 3: General linear model (GLM), the fundamental of the analyi of variance (ANOVA), and completely randomized deign (CRD) The general linear model One population: An obervation i explained
THE SPLITTING SUBSPACE CONJECTURE
 THE SPLITTING SUBSPAE ONJETURE ERI HEN AND DENNIS TSENG Abtract We anwer a uetion by Niederreiter concerning the enumeration of a cla of ubpace of finite dimenional vector pace over finite field by proving
THE SPLITTING SUBSPAE ONJETURE ERI HEN AND DENNIS TSENG Abtract We anwer a uetion by Niederreiter concerning the enumeration of a cla of ubpace of finite dimenional vector pace over finite field by proving
Multicast Network Coding and Field Sizes
 Multicat Network Coding and Field Size Qifu (Tyler) Sun, Xunrui Yin, Zongpeng Li, and Keping Long Intitute of Advanced Networking Technology and New Service, Univerity of Science and Technology Beijing,
Multicat Network Coding and Field Size Qifu (Tyler) Sun, Xunrui Yin, Zongpeng Li, and Keping Long Intitute of Advanced Networking Technology and New Service, Univerity of Science and Technology Beijing,
arxiv: v2 [math.nt] 30 Apr 2015
![arxiv: v2 [math.nt] 30 Apr 2015 arxiv: v2 [math.nt] 30 Apr 2015](/thumbs/74/69750607.jpg) A THEOREM FOR DISTINCT ZEROS OF L-FUNCTIONS École Normale Supérieure arxiv:54.6556v [math.nt] 3 Apr 5 943 Cachan November 9, 7 Abtract In thi paper, we etablih a imple criterion for two L-function L and
A THEOREM FOR DISTINCT ZEROS OF L-FUNCTIONS École Normale Supérieure arxiv:54.6556v [math.nt] 3 Apr 5 943 Cachan November 9, 7 Abtract In thi paper, we etablih a imple criterion for two L-function L and
Calculation of the temperature of boundary layer beside wall with time-dependent heat transfer coefficient
 Ŕ periodica polytechnica Mechanical Engineering 54/1 21 15 2 doi: 1.3311/pp.me.21-1.3 web: http:// www.pp.bme.hu/ me c Periodica Polytechnica 21 RESERCH RTICLE Calculation of the temperature of boundary
Ŕ periodica polytechnica Mechanical Engineering 54/1 21 15 2 doi: 1.3311/pp.me.21-1.3 web: http:// www.pp.bme.hu/ me c Periodica Polytechnica 21 RESERCH RTICLE Calculation of the temperature of boundary
arxiv: v2 [nucl-th] 3 May 2018
![arxiv: v2 [nucl-th] 3 May 2018 arxiv: v2 [nucl-th] 3 May 2018](/thumbs/89/101162462.jpg) DAMTP-207-44 An Alpha Particle Model for Carbon-2 J. I. Rawlinon arxiv:72.05658v2 [nucl-th] 3 May 208 Department of Applied Mathematic and Theoretical Phyic, Univerity of Cambridge, Wilberforce Road, Cambridge
DAMTP-207-44 An Alpha Particle Model for Carbon-2 J. I. Rawlinon arxiv:72.05658v2 [nucl-th] 3 May 208 Department of Applied Mathematic and Theoretical Phyic, Univerity of Cambridge, Wilberforce Road, Cambridge
Proactive Serving Decreases User Delay Exponentially: The Light-tailed Service Time Case
 Proactive Serving Decreae Uer Delay Exponentially: The Light-tailed Service Time Cae Shaoquan Zhang, Longbo Huang, Minghua Chen, and Xin Liu Abtract In online ervice ytem, the delay experienced by uer
Proactive Serving Decreae Uer Delay Exponentially: The Light-tailed Service Time Cae Shaoquan Zhang, Longbo Huang, Minghua Chen, and Xin Liu Abtract In online ervice ytem, the delay experienced by uer
CHEAP CONTROL PERFORMANCE LIMITATIONS OF INPUT CONSTRAINED LINEAR SYSTEMS
 Copyright 22 IFAC 5th Triennial World Congre, Barcelona, Spain CHEAP CONTROL PERFORMANCE LIMITATIONS OF INPUT CONSTRAINED LINEAR SYSTEMS Tritan Pérez Graham C. Goodwin Maria M. Serón Department of Electrical
Copyright 22 IFAC 5th Triennial World Congre, Barcelona, Spain CHEAP CONTROL PERFORMANCE LIMITATIONS OF INPUT CONSTRAINED LINEAR SYSTEMS Tritan Pérez Graham C. Goodwin Maria M. Serón Department of Electrical
Lecture 17: Analytic Functions and Integrals (See Chapter 14 in Boas)
 Lecture 7: Analytic Function and Integral (See Chapter 4 in Boa) Thi i a good point to take a brief detour and expand on our previou dicuion of complex variable and complex function of complex variable.
Lecture 7: Analytic Function and Integral (See Chapter 4 in Boa) Thi i a good point to take a brief detour and expand on our previou dicuion of complex variable and complex function of complex variable.
Fading Channels: Capacity, BER and Diversity
 Fading Channel: Capacity, BER and Diverity Mater Univeritario en Ingeniería de Telecomunicación I. Santamaría Univeridad de Cantabria Introduction Capacity BER Diverity Concluion Content Introduction Capacity
Fading Channel: Capacity, BER and Diverity Mater Univeritario en Ingeniería de Telecomunicación I. Santamaría Univeridad de Cantabria Introduction Capacity BER Diverity Concluion Content Introduction Capacity
Notes on Phase Space Fall 2007, Physics 233B, Hitoshi Murayama
 Note on Phae Space Fall 007, Phyic 33B, Hitohi Murayama Two-Body Phae Space The two-body phae i the bai of computing higher body phae pace. We compute it in the ret frame of the two-body ytem, P p + p
Note on Phae Space Fall 007, Phyic 33B, Hitohi Murayama Two-Body Phae Space The two-body phae i the bai of computing higher body phae pace. We compute it in the ret frame of the two-body ytem, P p + p
Avoiding Forbidden Submatrices by Row Deletions
 Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
μ + = σ = D 4 σ = D 3 σ = σ = All units in parts (a) and (b) are in V. (1) x chart: Center = μ = 0.75 UCL =
 Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Factor Analysis with Poisson Output
 Factor Analyi with Poion Output Gopal Santhanam Byron Yu Krihna V. Shenoy, Department of Electrical Engineering, Neurocience Program Stanford Univerity Stanford, CA 94305, USA {gopal,byronyu,henoy}@tanford.edu
Factor Analyi with Poion Output Gopal Santhanam Byron Yu Krihna V. Shenoy, Department of Electrical Engineering, Neurocience Program Stanford Univerity Stanford, CA 94305, USA {gopal,byronyu,henoy}@tanford.edu
Trellis Shaping Techniques for Satellite Telecommunication Systems
 > 1 Trelli Technique for Satellite Telecommunication Sytem M. Álvarez-Díaz 1, M. Neri, C. Moquera 1 and G. E. Corazza 1 Dept. Signal Theory and Communication (TSC), Univerity of Vigo Campu Univeritario
> 1 Trelli Technique for Satellite Telecommunication Sytem M. Álvarez-Díaz 1, M. Neri, C. Moquera 1 and G. E. Corazza 1 Dept. Signal Theory and Communication (TSC), Univerity of Vigo Campu Univeritario
