Contingency tables from the algebraic statistics view point Gérard Letac, Université Paul Sabatier, Toulouse
|
|
|
- Morris Edwards
- 5 years ago
- Views:
Transcription
1 Contingency tables from the algebraic statistics view point Gérard Letac, Université Paul Sabatier, Toulouse College Park, October 14 th, Joint work with Hélène Massam 1
2 Contingency tables Let I = I 1... I k = v V I v a product of finite sets and a probability p on I such that p(i) > 0 for all i I. The Bernoulli distribution B p is the distribution of X valued in R I such that Pr(X = e i ) = p i where (e i ) i I is the basis of R I. If X 1,...,X N are iid with distribution B p then S N = X 1 + +X N follows a multinomial distribution B p,n. An observation S N is a contingency table. In general p is unknown and we are willing to estimate it under some reasonable constraints like p(i 1,i 2 ) = p(i 1,.)p(.,i 2 ) = f(i 1 )g(i 2 ) for k = 2 p(i 1,i 2,i 3 ) = f(i 1,i 2 )g(i 2,i 3 ) for k = 3 or in a more linear way logp(i 1,i 2,i 3 ) = λ 12 (i 1,i 2 )+λ 23 (i 2,i 3 ). 2
3 Hierarchical model We formalize this type of constraints under the name of hierarchical model : given a family D of subsets of V = {1,...,k} such that D 1 D 2 for D 1,D 2 D is impossible (unless D 1 = D 2 ) the hierarchical model M D governed by D is the set of probabilities on I such that logp(i 1,...,i k ) = D D λ D (i) where i λ D (i) is a function depending only on the coordinates i j of i such that j D. In the sequel D < is the family of non empty subsets of the elements of D. An important point for performing the estimation of p under these constraints is the fact that M D is an exponential family. 3
4 Examples of hierarchical models (1)The most famous hierarchical model are the one given by an undirected graph with V as set of vertices. In this case D is the family of the cliques of the graph and the hierarchical model is called a graphical model. We mention two trivial models (2) D = {V} : no constraints at all, called the saturated model. (3) D is the set of singletons : that means that p(i) = p 1 (i 1 )...p k (i k ) and each components are independent. (4) V = {a,b,c} and D = {ab,bc,ac} is an example of hierarchical but not graphical model. 4
5 From now on we select a point called zero in each component I v = {0,1,...,c v }. 0 I is the point with all coordinates 0. If D = {V} (saturated model), the exponential family is generated by the counting measure on the basis (e i ) I\0 of R I\0 and we get for i 0 p(i) = e ξ,e i 1+ j I\0 e ξ,e j = e ξi 1+ j I\0 eξ j. For a general hierarchical model we define the support of i = (i 1,...,i k ) I as the subset S(i) of V of the v V such that i v 0. We define the set J I of the j I such that S(j) is in D < we write j i if j J is such that S(j) S(i) and the restriction of i to S(j) coincide with j. The exponential family is now concentrated on R J and is generated by the counting measure on the vectors f i = j ie j for i I. The parameterization is now θ j = j i( 1) S(i)\S(j) logp(i). 5
6 Therefore the exponential family is concentrated on the polytope of R J with extreme points (f i ) i I. Example : we take I = I a I b I c where I a = I b = I c = {0,1} (a binary model) and the hierarchical model given by the pair ab and bc. This is the graphical model a b c Here J = {a,b,c,ab,bc} and f 0 = 0, f a = e a, f b = e b, f c = e c, f ab = e a +e b +e ab, f bc = e b +e c +e bc, f ac = e a +e c, f abc = e a +e b +e c +e ab +e bc The polytope C has 8 vertices in a space of 5 dimensions. 6
7 Bayesian methods for selecting models The estimation of p by maximum likelihood is difficult to perform and we are here actually more interested in deciding if the hierarchical model is the good one or not. Since the model is an exponential family we rather take a Bayesian approach by using the Diaconis Ylvisaker conjugate family as a priori distributions on the natural parameter namely θ = (θ j ) j J R J, π m,α (dθ) = 1 I(m,α) e α θ,m ( i I e θ,f i ) αdθ Here, α > 0, m is an interior point of the convex polytope C with vertices (f i ) i I and I(m, α) is the normalization constant such that π m,α is a probability. 7
8 The characteristic function of a convex set Introduce a new general tool. Given a convex set C in R n its support function is h C (θ) = max{ θ,x ; x C} and its characteristic function is defined on the interior of C by J C (m) = R ne θ,m h C(θ) dθ = n!vol(c m) o = n! where C o dθ (1 θ,m ) n+1 C o = {θ ; θ,x 1 x C} is the polar set of C. This concept is useful here since we have the following result Theorem 1 : lim α 0 αn I(m,α) = J C (m) (just apply f p f in the theory of L p spaces to prove this). 8
9 Note that this remarkable limit depends only on the convex support of the measure µ, not on the measure itself. For example if E = R the measures and µ = δ 1 +δ 1 ν(dx) = 1 ( 1,1) (x)dx share the same C = ( 1,1) (which satisfies h ( 1,1) (θ) = θ. Therefore if 1 < m < 1 the two functions αi µ (m,α) = α 2 α+1b(α 2 (1+m),α 2 (1 m)) and the untractable αi ν (m,α) = α 2 2α 0 have the same limit J ( 1,1) (m) = ( ) logu α u α 2 (1+m) 1 du u 1 eθm θ dθ = 2 1 m 2. 9
10 Comparing two exponential models We now use this result for comparing two hierarchical models by the method of the Bayes factor. We are given two general exponential families and F 1 = {e θ 1,t 1 (w) k 1 (θ 1 ) ν 1 (dw) ; θ 1 Θ 1 } F 2 = {e θ 2,t 2 (w) k 2 (θ 2 ) ν 2 (dw) ; θ 1 Θ 1 } on the same abstract space Ω. On Ω we observe (w 1,...,w N ) and from this sample we have to choose between F 1 and F 2. The technique of the Bayesian factor is the following : F 1 and F 2 have natural associated exponential families with respective domains of the means M 1 and M 2 in which we choose m 1 and m 2 as close as possible. The normalisation constants for the a priori densities of D.-Y. are I 1 (m 1,α) and I 2 (m 2,α). We denote et S (1) N = t 1(ω 1 )+...+t 1 (ω N ) S (2) N = t 2(ω 1 )+...+t 2 (ω N ) 10
11 Here comes the Bayesian factor f = I 1( αm (1) 1+SN α+n,α+n) I 1 (m 1,α) I 2 (m 2,α) I 2 ( αm 2+S (2) N α+n,α+n) If f is big we choose the model F 1. If f is close to zero we choose the model F 2. 11
12 Suppose now that we are comparing two hierarchical models : for instance the graphical model a b c (say M 1 ) against the saturated one, say M 2. The observed contigency table has entries Nt (2) i and its projection to model M 1 has entries Nt (1) j. Thus the Bayesian factor f is f = I 1( αm 1+Nt (1) α+n,α+n) I 1 (m 1,α) I 2 (m 2,α) I 2 ( αm 2+Nt (2) α+n,α+n) Now suppose that t (1) and t (2) are interior points of the corresponding polytopes C 1 and C 2. In this case the limiting behavior of f when α goes to zero is f I 1(t (1),N) I 2 (t (2),N) J 2(m 2 ) J 1 (m 1 ) α J 1 J 2. 12
13 The real first difficulty arises when the observations t are on the boundary of the polytope since I 1 (t (1),N) is now infinite. We use the following delicate result : let y belonging to a face F(y) of C of codimension M(y) and let m be in interior of the polytope C. Then Theorem 2 : λ M(y) J C (λm+(1 λ)y) λ 0 J F(y) (y)j C2 (m 2 ) where C 2 is the cone generated by (C y) F(y) The consequence is that if the observation t is on the boundary of C we have, with the simpler notation λ = α α+n λ M(t) I(λm+(1 λ)t,n) λ 0 Cte which implies that the Bayesian factor behaves as f α D(t(1)) D(t (2)) Cte where D(t) is the dimension of the face containing t. 13
14 Linking the facets of C and the characteristic function J C How do we check that t is on the boundary? By knowing the facets of C. Theorem 3 : If F is the family of facets of the polytope C and if g F (m) = 0 is the affine equation of the facet m, then m J C (m) F F g F (m) is a polynomial of degree < F. Example 1 : C = [ 1,1] Its facets are { 1,1} with equations g 1 (m) = 1 + m, g 1 (m) = 1 m and (1 m 2 )J ( 1,1) (m) = 2. A consequence is that J C (m) is a rational function whose denominator is factorisable in affine forms which give the equations of the facets. 14
15 Example 2 : quadrangle in the plane. In R 2 with canonical basis (e 1,e 2 ) consider for a,b > 1 the vector f = ae 1 +be 2 and the convex C generated by 0,e 1,e 2,f. We get by direct calculation J C (m) = R 2e θ,m h C(θ) dθ = (1+ a 1 b m 2)(1+ b 1 a m 1) m 1 m 2 (1 m 1 + a 1 b m 2)(1+ b 1 a m 1 m 2 ). ae 1 +be 2 e 2 0 e 1 This illustrates the preceeding theorem : m 1 = m 2 = 1 m 1 + a 1 b m 2 = 1+ b 1 a m 1 m 2 = 0 define the 4 facets of the quadrangle C. 15
16 Example 3 : Octahedron in R d. In the Euclidean space E = R d denote by (e j ) d j=1 the canonical basis. The octahedron is the convex hull C of the 2d vectors (±e j ) d j=1. Thus we have m C if and only if d j=1 It is easily seen that m j < 1. h C (θ) = max{ θ j ;j = 1,...,d}. If ɛ = (ɛ 1,...,ɛ d ) { 1,1} d = E d we write s(ɛ) = ɛ 1 ɛ d. We define the linear form f ɛ (m) = d j=1 We get the general formula J C (m) = 1 dj=1 m j ɛ j m j. R de θ,m h C(θ) dθ = ɛ E d s(ɛ) 1 f ɛ (m). 16
17 Example 3, continued : Octahedron in R 3. For instance in the particular case d = 3 we get after reduction to the same denominator J C (m) 1 8 ɛ E 3 (1 f ɛ (m)) = 3 2(m 2 1 +m2 2 +m2 3 ) +2(m 2 1 m2 2 +m2 2 m2 3 +m2 3 m2 1 ) m4 1 m4 2 m4 3 We observe that the numerator of J C (m) is a polynomial with degree 4, while the denominator has eight factors describing the facets of the classical regular octahedron. One important point of the present example is the following : the numerator has in general no special properties of factorization as it occurs in the quadrangle or in the hierarchical model in the decomposable case. 17
18 Decomposable graphs Theorem 4 : Let (V,E) be a decomposable graph, let D be the family of the complete subsets of V, let C be the family of its cliques, let S be the family of its minimal separators and let ν(s) be the multiplicity of the minimal separator S. For each D D and each j J such that S(j) D consider the affine forms defined by g 0,D (m) = 1+ g j0,d(m) = j;s(j) D j;s(j) D, j 0 j ( 1) S(j) m j ( 1) S(j) S(j 0) m j Then for m in the interior C of the convex hull of the f i s we have I(m,α) = C CΓ(αg 0,C (m)) {j J;S(j) C} Γ(αg j,c(m)) Γ(α) [ S S Γ(αg0,S (m)) {j J;S(j) S} Γ(αg j,s(m)) ] ν(s 18
19 J C (m) for a decomposable graph In particular for m C we have S S limα J I(m,α) = J α C (m) = [ g0,s (m) {j J;S(j) S} g j,s(m) ] ν(s) C Cg 0,C (m) {j J;S(j) C} g j,c(m) As a consequence of Theorem 3, the family facets of C are parameterized by the set C C {j J {0};S(j) C} and the corresponding equation for the facet F associated to the clique C and to the point j J {0} such that S(j) C is g j,c (m) = 0. 19
20 Basic facets. Consider now a general hierarchical model governed by the family D of non empty subsets of V (recall such that D D and D 1 D implies D D). Denote by C D the family of maximal elements (if the hierarchical model was a graphical one, C would be the family of cliques. Theorem 5 : Let D be a maximal element of D. The affine equations g 0,C (m) = 1+ g j0,d(m) = j;s(j) D j;s(j) D, j 0 j ( 1) S(j) m j ( 1) S(j) S(j 0) m j define facets of C (called basic facets) Clearly this is an extension of Theorem 4 which was devoted to the decomposable case. In Theorem 4 ALL facets where basic. In the present general case, there are non basic facets. We have the following conjecture : if all facets are basic, the hierarchical model is a decomposable graphical model. 20
21 Facets for a cycle The binary graphical model governed by a cycle has been much studied. It happens that the facets of the corresponding polytope C have been studied in different contexts. Since we are in the binary case and since V has n elements, there exist 4n basic facets. But there also exist other ones, as discovered by Deza and Laurent (1995), or Hosten and Sullivant (2002). Theorem 6 : The non basic facets of the binary graphical model governed by a cycle V = {1,2,...,n} are indexed by the 2 n 1 odd subsets F of the set E of the n edges of the cycle. The corresponding affine equation is g F (m) = (a,b) F (m a +m b 2m ab ) ( v V m v e E m e ) F 1 2 Hence in the case of a cycle the polytope C has 4n + 2 n 1 facets : 24 for n = 4 and 36 for n = 5. 21
22 Two way interaction models They are the hierarchical models such that all maximal elements of D have only two elements. We can therefore represent such a model by a graph, but the interpretation of this graph should not be the interpretation of a graph in the case of a graphical model (unless the cliques of this graphical model have always two elements, like in a cycle of size 4 or a tree). A binary two way interaction model whose graph has m edges has exactly 4m basic facets. 22
23 The correlation polytope The binary two way interaction model obtained by considering the complete graph K n is supported by the polytope C n. The polytope C n has been the subject of intense studies in different contexts (see Deza and Laurent 1995) where it is called the correlation polytope. The number J = n(n + 1)/2 is the dimension of the space of symmetric matrices of order n and C n can be seen as the convex hull of the 2 n symmetric matrices f T where T {1,...,n} and f T (i,j) = 1 if i,j T and f T (i,j) = 0 if not. The set of facets of C n and their number F n has been studied for the first values of n 7. One gets in particular F 3 = 16, F 4 = 56, F 5 = 368, F 6 = 116,764, F 7 = 49,594,
24 The two way interaction model C 3 Let us insist on the fact that the two way interaction model C 3 is the hierarchical model of probabilities (p(i)) i I on I = I 1 I 2 I 3 such that there exists 3 functions λ j such that logp(i 1,i 2,i 3 ) = λ 3 (i 1,i 2 )+λ 2 (i 1,i 3 )+λ 1 (i 2,i 3 ), and that we consider only the binary case I j = {0,1}. 24
25 For the correlation polytope C 3, we now explain how to compute I(m,α) and J C3 (m). Theorem 7 : Define the positive numbers A = m ab, B = m ac, C = m a, A = m b m ab, B = m c m ac, C = 1 m a, D = m bc. Then the sixth order integral I(m,α) is equal to the one dimensional Mellin transform 0 xαd 1 2F 1 (αa,αb;αc;1 x) 2 F 1 (αa,αb ;αc ;1 x)dx multiplied by the following product of gamma functions Γ(αA)Γ(αB)Γ(αA )Γ(αB ) Γ(α)Γ(αC)Γ(αC ) Γ(α(C A))Γ(α(C B))Γ(α(C A ))Γ(α(C B ) 25
26 Let us indicate the sources of the Gauss hypergeometric function in this calculation. In I(m,α) we use the change of variable u a = e θ, u ab = e θ ab,... Consider the polynomial P = 1+u a +u b +u c +u a u b u ab +u b u c u bc +u a u c u ac +u a u b u c u ab u bc u ac. The integral I(m, α) becomes (0, )6 u αm a 1 a u αm b 1 b u αm c 1 c u αm ab 1 ab u αm bc 1 bc u αm ac 1 ac P α du a du b du c du ab du bc du ac We first integrate with respect to u a. This leads to an integral on (0, ) 5 that we treat by the following observation 26
27 If a,b,c,r are positive numbers denote I = 0 Then I = 0 Γ(a)Γ(b)Γ(b+c)Γ(a+c) Γ(a+b+c) 2 x a 1 y b 1 (1+x+y +Rxy) a+b+cdxdy. 2F 1 (a,b,a+b+c;1 R). Applying it twice reduces the integral on (0, ) 5 to an integral on (0, ) involving a product of two hypergeometric functions. 27
28 Why this horrible I(m, α)? Because it provides the only known way to compute J C3 (m) = lim α 0 α 6 I(m,α). Recall that = 2F 1 (αa,αb;αc;1 e v α) n=0 (αa) n (αb) n n!(αc) n (1 e v α) n. We need two difficult limits. If v > 0 : and if v < 0 : lim α 0 2 F 1 (αa,αb;αc;1 e v α) = B(C A) C(B A) e va A(C B) C(B A) e vb lim α 0 2 F 1 (αa,αb;αc;1 eα) v = (C A)(C B) ABe v(c A B) C(C A B) 28
29 Among other things, the proof of the last statement uses the following undergraduate exercise : Let a,b > 0. If X α has beta distribution β αa,αb what is the limiting distribution of X α α when α 0? Answer : a a+b δ 1 + b a+b β a,1 (use Mellin transform). Consequence : if X α β αa,αb then Pr(X α < x 1/α ) α 0 b a+b xa. 29
30 Here is J C3 (m) = + 1 ABA B (C A)(C B)(C A )(C B ) 1 (B A)(B A ) { (C A)(C A )BB (A+A D) (C B)(C A )AB (B +A D) (C A)(C B )BA (A+B D) + (C B)(C B )AA (B +B } D) 1 ABA B (C A)(C B)(C A )(C B ) 1 (C A B)(C A B ) { (C A)(C B)(C A )(C B ) D (C A)(C B)A B (C +D A B ) AB(C A )(C B ) (C +D A B) ABA B + (C +C +D A A B B ) } 30
31 Recall that A = m ab, B = m ac, C = m a, A = m b m ab, B = m c m ac, C = 1 m a, D = m bc. After simplification, the four undesirable denominators B A,B A,C A B,C A B disappear (but the numerator according to Maple is the sum of four thousand monomials). The sixteen remaining denominators give the sixteen facets. The 12 basic facets are given by the annulation of the 12 forms A,B,C A,C B,A,B,C A,C B,D, D A A,D B B,D+C+C A A B B. The 4 non basic facets are given by D+C A B,D A B,D A B,D+C A B. 31
32 A = m ab, B = m ac, D = m bc, A = m b m ab, C A = m a m ab, B = m c m ac, C B = m a m ac, A+A D = m b m bc, B+B D = m c m bc, C A = 1 m a m b +m ab, C B = 1 m a m c +m ac, C+C +D A A B B = 1 m b m c +m bc, A+B D = m c +m ab m ac m bc, A +B D = m b +m ac m ab m bc, C+D A B = m a +m bc m ac m ab, C +D A B = 1 m a m b m c +m ac +m ab +m bc. 32
The tiling by the minimal separators of a junction tree and applications to graphical models Durham, 2008
 The tiling by the minimal separators of a junction tree and applications to graphical models Durham, 2008 G. Letac, Université Paul Sabatier, Toulouse. Joint work with H. Massam 1 Motivation : the Wishart
The tiling by the minimal separators of a junction tree and applications to graphical models Durham, 2008 G. Letac, Université Paul Sabatier, Toulouse. Joint work with H. Massam 1 Motivation : the Wishart
ACO Comprehensive Exam October 18 and 19, Analysis of Algorithms
 Consider the following two graph problems: 1. Analysis of Algorithms Graph coloring: Given a graph G = (V,E) and an integer c 0, a c-coloring is a function f : V {1,,...,c} such that f(u) f(v) for all
Consider the following two graph problems: 1. Analysis of Algorithms Graph coloring: Given a graph G = (V,E) and an integer c 0, a c-coloring is a function f : V {1,,...,c} such that f(u) f(v) for all
14 : Theory of Variational Inference: Inner and Outer Approximation
 10-708: Probabilistic Graphical Models 10-708, Spring 2014 14 : Theory of Variational Inference: Inner and Outer Approximation Lecturer: Eric P. Xing Scribes: Yu-Hsin Kuo, Amos Ng 1 Introduction Last lecture
10-708: Probabilistic Graphical Models 10-708, Spring 2014 14 : Theory of Variational Inference: Inner and Outer Approximation Lecturer: Eric P. Xing Scribes: Yu-Hsin Kuo, Amos Ng 1 Introduction Last lecture
An Algebraic and Geometric Perspective on Exponential Families
 An Algebraic and Geometric Perspective on Exponential Families Caroline Uhler (IST Austria) Based on two papers: with Mateusz Micha lek, Bernd Sturmfels, and Piotr Zwiernik, and with Liam Solus and Ruriko
An Algebraic and Geometric Perspective on Exponential Families Caroline Uhler (IST Austria) Based on two papers: with Mateusz Micha lek, Bernd Sturmfels, and Piotr Zwiernik, and with Liam Solus and Ruriko
Stat 5421 Lecture Notes Proper Conjugate Priors for Exponential Families Charles J. Geyer March 28, 2016
 Stat 5421 Lecture Notes Proper Conjugate Priors for Exponential Families Charles J. Geyer March 28, 2016 1 Theory This section explains the theory of conjugate priors for exponential families of distributions,
Stat 5421 Lecture Notes Proper Conjugate Priors for Exponential Families Charles J. Geyer March 28, 2016 1 Theory This section explains the theory of conjugate priors for exponential families of distributions,
Sums and Products. a i = a 1. i=1. a i = a i a n. n 1
 Sums and Products -27-209 In this section, I ll review the notation for sums and products Addition and multiplication are binary operations: They operate on two numbers at a time If you want to add or
Sums and Products -27-209 In this section, I ll review the notation for sums and products Addition and multiplication are binary operations: They operate on two numbers at a time If you want to add or
Notes, March 4, 2013, R. Dudley Maximum likelihood estimation: actual or supposed
 18.466 Notes, March 4, 2013, R. Dudley Maximum likelihood estimation: actual or supposed 1. MLEs in exponential families Let f(x,θ) for x X and θ Θ be a likelihood function, that is, for present purposes,
18.466 Notes, March 4, 2013, R. Dudley Maximum likelihood estimation: actual or supposed 1. MLEs in exponential families Let f(x,θ) for x X and θ Θ be a likelihood function, that is, for present purposes,
Lecture 2. (See Exercise 7.22, 7.23, 7.24 in Casella & Berger)
 8 HENRIK HULT Lecture 2 3. Some common distributions in classical and Bayesian statistics 3.1. Conjugate prior distributions. In the Bayesian setting it is important to compute posterior distributions.
8 HENRIK HULT Lecture 2 3. Some common distributions in classical and Bayesian statistics 3.1. Conjugate prior distributions. In the Bayesian setting it is important to compute posterior distributions.
PIOTR GRACZYK LAREMA, UNIVERSITÉ D ANGERS, FRANCJA. Estymatory kowariancji dla modeli graficznych
 PIOTR GRACZYK LAREMA, UNIVERSITÉ D ANGERS, FRANCJA Estymatory kowariancji dla modeli graficznych wspó lautorzy: H. Ishi(Nagoya), B. Ko lodziejek(warszawa), S. Mamane(Johannesburg), H. Ochiai(Fukuoka) XLV
PIOTR GRACZYK LAREMA, UNIVERSITÉ D ANGERS, FRANCJA Estymatory kowariancji dla modeli graficznych wspó lautorzy: H. Ishi(Nagoya), B. Ko lodziejek(warszawa), S. Mamane(Johannesburg), H. Ochiai(Fukuoka) XLV
GROUPS. Chapter-1 EXAMPLES 1.1. INTRODUCTION 1.2. BINARY OPERATION
 Chapter-1 GROUPS 1.1. INTRODUCTION The theory of groups arose from the theory of equations, during the nineteenth century. Originally, groups consisted only of transformations. The group of transformations
Chapter-1 GROUPS 1.1. INTRODUCTION The theory of groups arose from the theory of equations, during the nineteenth century. Originally, groups consisted only of transformations. The group of transformations
Likelihood Analysis of Gaussian Graphical Models
 Faculty of Science Likelihood Analysis of Gaussian Graphical Models Ste en Lauritzen Department of Mathematical Sciences Minikurs TUM 2016 Lecture 2 Slide 1/43 Overview of lectures Lecture 1 Markov Properties
Faculty of Science Likelihood Analysis of Gaussian Graphical Models Ste en Lauritzen Department of Mathematical Sciences Minikurs TUM 2016 Lecture 2 Slide 1/43 Overview of lectures Lecture 1 Markov Properties
We could express the left side as a sum of vectors and obtain the Vector Form of a Linear System: a 12 a x n. a m2
 Week 22 Equations, Matrices and Transformations Coefficient Matrix and Vector Forms of a Linear System Suppose we have a system of m linear equations in n unknowns a 11 x 1 + a 12 x 2 + + a 1n x n b 1
Week 22 Equations, Matrices and Transformations Coefficient Matrix and Vector Forms of a Linear System Suppose we have a system of m linear equations in n unknowns a 11 x 1 + a 12 x 2 + + a 1n x n b 1
STA 4273H: Statistical Machine Learning
 STA 4273H: Statistical Machine Learning Russ Salakhutdinov Department of Statistics! rsalakhu@utstat.toronto.edu! http://www.utstat.utoronto.ca/~rsalakhu/ Sidney Smith Hall, Room 6002 Lecture 3 Linear
STA 4273H: Statistical Machine Learning Russ Salakhutdinov Department of Statistics! rsalakhu@utstat.toronto.edu! http://www.utstat.utoronto.ca/~rsalakhu/ Sidney Smith Hall, Room 6002 Lecture 3 Linear
Probabilistic Graphical Models
 Parameter Estimation December 14, 2015 Overview 1 Motivation 2 3 4 What did we have so far? 1 Representations: how do we model the problem? (directed/undirected). 2 Inference: given a model and partially
Parameter Estimation December 14, 2015 Overview 1 Motivation 2 3 4 What did we have so far? 1 Representations: how do we model the problem? (directed/undirected). 2 Inference: given a model and partially
Learning Bayesian network : Given structure and completely observed data
 Learning Bayesian network : Given structure and completely observed data Probabilistic Graphical Models Sharif University of Technology Spring 2017 Soleymani Learning problem Target: true distribution
Learning Bayesian network : Given structure and completely observed data Probabilistic Graphical Models Sharif University of Technology Spring 2017 Soleymani Learning problem Target: true distribution
SOUTH AFRICAN TERTIARY MATHEMATICS OLYMPIAD
 SOUTH AFRICAN TERTIARY MATHEMATICS OLYMPIAD. Determine the following value: 7 August 6 Solutions π + π. Solution: Since π
SOUTH AFRICAN TERTIARY MATHEMATICS OLYMPIAD. Determine the following value: 7 August 6 Solutions π + π. Solution: Since π
Decomposable and Directed Graphical Gaussian Models
 Decomposable Decomposable and Directed Graphical Gaussian Models Graphical Models and Inference, Lecture 13, Michaelmas Term 2009 November 26, 2009 Decomposable Definition Basic properties Wishart density
Decomposable Decomposable and Directed Graphical Gaussian Models Graphical Models and Inference, Lecture 13, Michaelmas Term 2009 November 26, 2009 Decomposable Definition Basic properties Wishart density
CS 361: Probability & Statistics
 October 17, 2017 CS 361: Probability & Statistics Inference Maximum likelihood: drawbacks A couple of things might trip up max likelihood estimation: 1) Finding the maximum of some functions can be quite
October 17, 2017 CS 361: Probability & Statistics Inference Maximum likelihood: drawbacks A couple of things might trip up max likelihood estimation: 1) Finding the maximum of some functions can be quite
1 The distributive law
 THINGS TO KNOW BEFORE GOING INTO DISCRETE MATHEMATICS The distributive law The distributive law is this: a(b + c) = ab + bc This can be generalized to any number of terms between parenthesis; for instance:
THINGS TO KNOW BEFORE GOING INTO DISCRETE MATHEMATICS The distributive law The distributive law is this: a(b + c) = ab + bc This can be generalized to any number of terms between parenthesis; for instance:
Generating Functions
 Semester 1, 2004 Generating functions Another means of organising enumeration. Two examples we have seen already. Example 1. Binomial coefficients. Let X = {1, 2,..., n} c k = # k-element subsets of X
Semester 1, 2004 Generating functions Another means of organising enumeration. Two examples we have seen already. Example 1. Binomial coefficients. Let X = {1, 2,..., n} c k = # k-element subsets of X
The random continued fractions of Dyson and their extensions. La Sapientia, January 25th, G. Letac, Université Paul Sabatier, Toulouse.
 The random continued fractions of Dyson and their extensions La Sapientia, January 25th, 2010. G. Letac, Université Paul Sabatier, Toulouse. 1 56 years ago Freeman J. Dyson the Princeton physicist and
The random continued fractions of Dyson and their extensions La Sapientia, January 25th, 2010. G. Letac, Université Paul Sabatier, Toulouse. 1 56 years ago Freeman J. Dyson the Princeton physicist and
Preliminaries and Complexity Theory
 Preliminaries and Complexity Theory Oleksandr Romanko CAS 746 - Advanced Topics in Combinatorial Optimization McMaster University, January 16, 2006 Introduction Book structure: 2 Part I Linear Algebra
Preliminaries and Complexity Theory Oleksandr Romanko CAS 746 - Advanced Topics in Combinatorial Optimization McMaster University, January 16, 2006 Introduction Book structure: 2 Part I Linear Algebra
Intrinsic products and factorizations of matrices
 Available online at www.sciencedirect.com Linear Algebra and its Applications 428 (2008) 5 3 www.elsevier.com/locate/laa Intrinsic products and factorizations of matrices Miroslav Fiedler Academy of Sciences
Available online at www.sciencedirect.com Linear Algebra and its Applications 428 (2008) 5 3 www.elsevier.com/locate/laa Intrinsic products and factorizations of matrices Miroslav Fiedler Academy of Sciences
Variable Elimination: Algorithm
 Variable Elimination: Algorithm Sargur srihari@cedar.buffalo.edu 1 Topics 1. Types of Inference Algorithms 2. Variable Elimination: the Basic ideas 3. Variable Elimination Sum-Product VE Algorithm Sum-Product
Variable Elimination: Algorithm Sargur srihari@cedar.buffalo.edu 1 Topics 1. Types of Inference Algorithms 2. Variable Elimination: the Basic ideas 3. Variable Elimination Sum-Product VE Algorithm Sum-Product
Variable Elimination: Algorithm
 Variable Elimination: Algorithm Sargur srihari@cedar.buffalo.edu 1 Topics 1. Types of Inference Algorithms 2. Variable Elimination: the Basic ideas 3. Variable Elimination Sum-Product VE Algorithm Sum-Product
Variable Elimination: Algorithm Sargur srihari@cedar.buffalo.edu 1 Topics 1. Types of Inference Algorithms 2. Variable Elimination: the Basic ideas 3. Variable Elimination Sum-Product VE Algorithm Sum-Product
PMR Learning as Inference
 Outline PMR Learning as Inference Probabilistic Modelling and Reasoning Amos Storkey Modelling 2 The Exponential Family 3 Bayesian Sets School of Informatics, University of Edinburgh Amos Storkey PMR Learning
Outline PMR Learning as Inference Probabilistic Modelling and Reasoning Amos Storkey Modelling 2 The Exponential Family 3 Bayesian Sets School of Informatics, University of Edinburgh Amos Storkey PMR Learning
Normal form for the non linear Schrödinger equation
 Normal form for the non linear Schrödinger equation joint work with Claudio Procesi and Nguyen Bich Van Universita di Roma La Sapienza S. Etienne de Tinee 4-9 Feb. 2013 Nonlinear Schrödinger equation Consider
Normal form for the non linear Schrödinger equation joint work with Claudio Procesi and Nguyen Bich Van Universita di Roma La Sapienza S. Etienne de Tinee 4-9 Feb. 2013 Nonlinear Schrödinger equation Consider
14 : Theory of Variational Inference: Inner and Outer Approximation
 10-708: Probabilistic Graphical Models 10-708, Spring 2017 14 : Theory of Variational Inference: Inner and Outer Approximation Lecturer: Eric P. Xing Scribes: Maria Ryskina, Yen-Chia Hsu 1 Introduction
10-708: Probabilistic Graphical Models 10-708, Spring 2017 14 : Theory of Variational Inference: Inner and Outer Approximation Lecturer: Eric P. Xing Scribes: Maria Ryskina, Yen-Chia Hsu 1 Introduction
Bayesian (conditionally) conjugate inference for discrete data models. Jon Forster (University of Southampton)
 Bayesian (conditionally) conjugate inference for discrete data models Jon Forster (University of Southampton) with Mark Grigsby (Procter and Gamble?) Emily Webb (Institute of Cancer Research) Table 1:
Bayesian (conditionally) conjugate inference for discrete data models Jon Forster (University of Southampton) with Mark Grigsby (Procter and Gamble?) Emily Webb (Institute of Cancer Research) Table 1:
Partial cubes: structures, characterizations, and constructions
 Partial cubes: structures, characterizations, and constructions Sergei Ovchinnikov San Francisco State University, Mathematics Department, 1600 Holloway Ave., San Francisco, CA 94132 Abstract Partial cubes
Partial cubes: structures, characterizations, and constructions Sergei Ovchinnikov San Francisco State University, Mathematics Department, 1600 Holloway Ave., San Francisco, CA 94132 Abstract Partial cubes
Algebra I. Book 2. Powered by...
 Algebra I Book 2 Powered by... ALGEBRA I Units 4-7 by The Algebra I Development Team ALGEBRA I UNIT 4 POWERS AND POLYNOMIALS......... 1 4.0 Review................ 2 4.1 Properties of Exponents..........
Algebra I Book 2 Powered by... ALGEBRA I Units 4-7 by The Algebra I Development Team ALGEBRA I UNIT 4 POWERS AND POLYNOMIALS......... 1 4.0 Review................ 2 4.1 Properties of Exponents..........
Fundamentals. CS 281A: Statistical Learning Theory. Yangqing Jia. August, Based on tutorial slides by Lester Mackey and Ariel Kleiner
 Fundamentals CS 281A: Statistical Learning Theory Yangqing Jia Based on tutorial slides by Lester Mackey and Ariel Kleiner August, 2011 Outline 1 Probability 2 Statistics 3 Linear Algebra 4 Optimization
Fundamentals CS 281A: Statistical Learning Theory Yangqing Jia Based on tutorial slides by Lester Mackey and Ariel Kleiner August, 2011 Outline 1 Probability 2 Statistics 3 Linear Algebra 4 Optimization
Steven J. Leon University of Massachusetts, Dartmouth
 INSTRUCTOR S SOLUTIONS MANUAL LINEAR ALGEBRA WITH APPLICATIONS NINTH EDITION Steven J. Leon University of Massachusetts, Dartmouth Boston Columbus Indianapolis New York San Francisco Amsterdam Cape Town
INSTRUCTOR S SOLUTIONS MANUAL LINEAR ALGEBRA WITH APPLICATIONS NINTH EDITION Steven J. Leon University of Massachusetts, Dartmouth Boston Columbus Indianapolis New York San Francisco Amsterdam Cape Town
Mathematics Course 111: Algebra I Part I: Algebraic Structures, Sets and Permutations
 Mathematics Course 111: Algebra I Part I: Algebraic Structures, Sets and Permutations D. R. Wilkins Academic Year 1996-7 1 Number Systems and Matrix Algebra Integers The whole numbers 0, ±1, ±2, ±3, ±4,...
Mathematics Course 111: Algebra I Part I: Algebraic Structures, Sets and Permutations D. R. Wilkins Academic Year 1996-7 1 Number Systems and Matrix Algebra Integers The whole numbers 0, ±1, ±2, ±3, ±4,...
Integer Programming ISE 418. Lecture 12. Dr. Ted Ralphs
 Integer Programming ISE 418 Lecture 12 Dr. Ted Ralphs ISE 418 Lecture 12 1 Reading for This Lecture Nemhauser and Wolsey Sections II.2.1 Wolsey Chapter 9 ISE 418 Lecture 12 2 Generating Stronger Valid
Integer Programming ISE 418 Lecture 12 Dr. Ted Ralphs ISE 418 Lecture 12 1 Reading for This Lecture Nemhauser and Wolsey Sections II.2.1 Wolsey Chapter 9 ISE 418 Lecture 12 2 Generating Stronger Valid
Matrix & Linear Algebra
 Matrix & Linear Algebra Jamie Monogan University of Georgia For more information: http://monogan.myweb.uga.edu/teaching/mm/ Jamie Monogan (UGA) Matrix & Linear Algebra 1 / 84 Vectors Vectors Vector: A
Matrix & Linear Algebra Jamie Monogan University of Georgia For more information: http://monogan.myweb.uga.edu/teaching/mm/ Jamie Monogan (UGA) Matrix & Linear Algebra 1 / 84 Vectors Vectors Vector: A
Notes on the Matrix-Tree theorem and Cayley s tree enumerator
 Notes on the Matrix-Tree theorem and Cayley s tree enumerator 1 Cayley s tree enumerator Recall that the degree of a vertex in a tree (or in any graph) is the number of edges emanating from it We will
Notes on the Matrix-Tree theorem and Cayley s tree enumerator 1 Cayley s tree enumerator Recall that the degree of a vertex in a tree (or in any graph) is the number of edges emanating from it We will
0 Sets and Induction. Sets
 0 Sets and Induction Sets A set is an unordered collection of objects, called elements or members of the set. A set is said to contain its elements. We write a A to denote that a is an element of the set
0 Sets and Induction Sets A set is an unordered collection of objects, called elements or members of the set. A set is said to contain its elements. We write a A to denote that a is an element of the set
Chapter 3. Rings. The basic commutative rings in mathematics are the integers Z, the. Examples
 Chapter 3 Rings Rings are additive abelian groups with a second operation called multiplication. The connection between the two operations is provided by the distributive law. Assuming the results of Chapter
Chapter 3 Rings Rings are additive abelian groups with a second operation called multiplication. The connection between the two operations is provided by the distributive law. Assuming the results of Chapter
1.1 Line Reflections and Point Reflections
 1.1 Line Reflections and Point Reflections Since this is a book on Transformation Geometry, we shall start by defining transformations of the Euclidean plane and giving basic examples. Definition 1. A
1.1 Line Reflections and Point Reflections Since this is a book on Transformation Geometry, we shall start by defining transformations of the Euclidean plane and giving basic examples. Definition 1. A
CS6901: review of Theory of Computation and Algorithms
 CS6901: review of Theory of Computation and Algorithms Any mechanically (automatically) discretely computation of problem solving contains at least three components: - problem description - computational
CS6901: review of Theory of Computation and Algorithms Any mechanically (automatically) discretely computation of problem solving contains at least three components: - problem description - computational
1 What is the area model for multiplication?
 for multiplication represents a lovely way to view the distribution property the real number exhibit. This property is the link between addition and multiplication. 1 1 What is the area model for multiplication?
for multiplication represents a lovely way to view the distribution property the real number exhibit. This property is the link between addition and multiplication. 1 1 What is the area model for multiplication?
EQ: What are limits, and how do we find them? Finite limits as x ± Horizontal Asymptote. Example Horizontal Asymptote
 Finite limits as x ± The symbol for infinity ( ) does not represent a real number. We use to describe the behavior of a function when the values in its domain or range outgrow all finite bounds. For example,
Finite limits as x ± The symbol for infinity ( ) does not represent a real number. We use to describe the behavior of a function when the values in its domain or range outgrow all finite bounds. For example,
Fundamentals of Linear Algebra. Marcel B. Finan Arkansas Tech University c All Rights Reserved
 Fundamentals of Linear Algebra Marcel B. Finan Arkansas Tech University c All Rights Reserved 2 PREFACE Linear algebra has evolved as a branch of mathematics with wide range of applications to the natural
Fundamentals of Linear Algebra Marcel B. Finan Arkansas Tech University c All Rights Reserved 2 PREFACE Linear algebra has evolved as a branch of mathematics with wide range of applications to the natural
(1) A frac = b : a, b A, b 0. We can define addition and multiplication of fractions as we normally would. a b + c d
 The Algebraic Method 0.1. Integral Domains. Emmy Noether and others quickly realized that the classical algebraic number theory of Dedekind could be abstracted completely. In particular, rings of integers
The Algebraic Method 0.1. Integral Domains. Emmy Noether and others quickly realized that the classical algebraic number theory of Dedekind could be abstracted completely. In particular, rings of integers
Decomposable Graphical Gaussian Models
 CIMPA Summerschool, Hammamet 2011, Tunisia September 12, 2011 Basic algorithm This simple algorithm has complexity O( V + E ): 1. Choose v 0 V arbitrary and let v 0 = 1; 2. When vertices {1, 2,..., j}
CIMPA Summerschool, Hammamet 2011, Tunisia September 12, 2011 Basic algorithm This simple algorithm has complexity O( V + E ): 1. Choose v 0 V arbitrary and let v 0 = 1; 2. When vertices {1, 2,..., j}
Solutions for Chapter 3
 Solutions for Chapter Solutions for exercises in section 0 a X b x, y 6, and z 0 a Neither b Sew symmetric c Symmetric d Neither The zero matrix trivially satisfies all conditions, and it is the only possible
Solutions for Chapter Solutions for exercises in section 0 a X b x, y 6, and z 0 a Neither b Sew symmetric c Symmetric d Neither The zero matrix trivially satisfies all conditions, and it is the only possible
CHAPTER 8: Matrices and Determinants
 (Exercises for Chapter 8: Matrices and Determinants) E.8.1 CHAPTER 8: Matrices and Determinants (A) means refer to Part A, (B) means refer to Part B, etc. Most of these exercises can be done without a
(Exercises for Chapter 8: Matrices and Determinants) E.8.1 CHAPTER 8: Matrices and Determinants (A) means refer to Part A, (B) means refer to Part B, etc. Most of these exercises can be done without a
Real Analysis Math 131AH Rudin, Chapter #1. Dominique Abdi
 Real Analysis Math 3AH Rudin, Chapter # Dominique Abdi.. If r is rational (r 0) and x is irrational, prove that r + x and rx are irrational. Solution. Assume the contrary, that r+x and rx are rational.
Real Analysis Math 3AH Rudin, Chapter # Dominique Abdi.. If r is rational (r 0) and x is irrational, prove that r + x and rx are irrational. Solution. Assume the contrary, that r+x and rx are rational.
five line proofs Victor Ufnarovski, Frank Wikström 20 december 2016 Matematikcentrum, LTH
 five line proofs Victor Ufnarovski, Frank Wikström 20 december 2016 Matematikcentrum, LTH projections The orthogonal projections of a body on two different planes are disks. Prove that they have the same
five line proofs Victor Ufnarovski, Frank Wikström 20 december 2016 Matematikcentrum, LTH projections The orthogonal projections of a body on two different planes are disks. Prove that they have the same
Identity. "At least one dog has fleas" is translated by an existential quantifier"
 Identity Quantifiers are so-called because they say how many. So far, we've only used the quantifiers to give the crudest possible answers to the question "How many dogs have fleas?": "All," "None," "Some,"
Identity Quantifiers are so-called because they say how many. So far, we've only used the quantifiers to give the crudest possible answers to the question "How many dogs have fleas?": "All," "None," "Some,"
Pattern Recognition and Machine Learning. Bishop Chapter 2: Probability Distributions
 Pattern Recognition and Machine Learning Chapter 2: Probability Distributions Cécile Amblard Alex Kläser Jakob Verbeek October 11, 27 Probability Distributions: General Density Estimation: given a finite
Pattern Recognition and Machine Learning Chapter 2: Probability Distributions Cécile Amblard Alex Kläser Jakob Verbeek October 11, 27 Probability Distributions: General Density Estimation: given a finite
X X (2) X Pr(X = x θ) (3)
 Notes for 848 lecture 6: A ML basis for compatibility and parsimony Notation θ Θ (1) Θ is the space of all possible trees (and model parameters) θ is a point in the parameter space = a particular tree
Notes for 848 lecture 6: A ML basis for compatibility and parsimony Notation θ Θ (1) Θ is the space of all possible trees (and model parameters) θ is a point in the parameter space = a particular tree
Combinatorial and physical content of Kirchhoff polynomials
 Combinatorial and physical content of Kirchhoff polynomials Karen Yeats May 19, 2009 Spanning trees Let G be a connected graph, potentially with multiple edges and loops in the sense of a graph theorist.
Combinatorial and physical content of Kirchhoff polynomials Karen Yeats May 19, 2009 Spanning trees Let G be a connected graph, potentially with multiple edges and loops in the sense of a graph theorist.
Lecture 7: More Arithmetic and Fun With Primes
 IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Advanced Course on Computational Complexity Lecture 7: More Arithmetic and Fun With Primes David Mix Barrington and Alexis Maciel July
IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Advanced Course on Computational Complexity Lecture 7: More Arithmetic and Fun With Primes David Mix Barrington and Alexis Maciel July
LMI MODELLING 4. CONVEX LMI MODELLING. Didier HENRION. LAAS-CNRS Toulouse, FR Czech Tech Univ Prague, CZ. Universidad de Valladolid, SP March 2009
 LMI MODELLING 4. CONVEX LMI MODELLING Didier HENRION LAAS-CNRS Toulouse, FR Czech Tech Univ Prague, CZ Universidad de Valladolid, SP March 2009 Minors A minor of a matrix F is the determinant of a submatrix
LMI MODELLING 4. CONVEX LMI MODELLING Didier HENRION LAAS-CNRS Toulouse, FR Czech Tech Univ Prague, CZ Universidad de Valladolid, SP March 2009 Minors A minor of a matrix F is the determinant of a submatrix
Probabilistic Graphical Models
 Probabilistic Graphical Models Lecture 11 CRFs, Exponential Family CS/CNS/EE 155 Andreas Krause Announcements Homework 2 due today Project milestones due next Monday (Nov 9) About half the work should
Probabilistic Graphical Models Lecture 11 CRFs, Exponential Family CS/CNS/EE 155 Andreas Krause Announcements Homework 2 due today Project milestones due next Monday (Nov 9) About half the work should
Order of Operations. Real numbers
 Order of Operations When simplifying algebraic expressions we use the following order: 1. Perform operations within a parenthesis. 2. Evaluate exponents. 3. Multiply and divide from left to right. 4. Add
Order of Operations When simplifying algebraic expressions we use the following order: 1. Perform operations within a parenthesis. 2. Evaluate exponents. 3. Multiply and divide from left to right. 4. Add
Undergraduate Notes in Mathematics. Arkansas Tech University Department of Mathematics. College Algebra for STEM
 Undergraduate Notes in Mathematics Arkansas Tech University Department of Mathematics College Algebra for STEM Marcel B. Finan c All Rights Reserved 2015 Edition To my children Amin & Nadia Preface From
Undergraduate Notes in Mathematics Arkansas Tech University Department of Mathematics College Algebra for STEM Marcel B. Finan c All Rights Reserved 2015 Edition To my children Amin & Nadia Preface From
Exercises for Unit I I (Vector algebra and Euclidean geometry)
 Exercises for Unit I I (Vector algebra and Euclidean geometry) I I.1 : Approaches to Euclidean geometry Ryan : pp. 5 15 1. What is the minimum number of planes containing three concurrent noncoplanar lines
Exercises for Unit I I (Vector algebra and Euclidean geometry) I I.1 : Approaches to Euclidean geometry Ryan : pp. 5 15 1. What is the minimum number of planes containing three concurrent noncoplanar lines
Algebraic Representations of Gaussian Markov Combinations
 Submitted to the Bernoulli Algebraic Representations of Gaussian Markov Combinations M. SOFIA MASSA 1 and EVA RICCOMAGNO 2 1 Department of Statistics, University of Oxford, 1 South Parks Road, Oxford,
Submitted to the Bernoulli Algebraic Representations of Gaussian Markov Combinations M. SOFIA MASSA 1 and EVA RICCOMAGNO 2 1 Department of Statistics, University of Oxford, 1 South Parks Road, Oxford,
Overview of Course. Nevin L. Zhang (HKUST) Bayesian Networks Fall / 58
 Overview of Course So far, we have studied The concept of Bayesian network Independence and Separation in Bayesian networks Inference in Bayesian networks The rest of the course: Data analysis using Bayesian
Overview of Course So far, we have studied The concept of Bayesian network Independence and Separation in Bayesian networks Inference in Bayesian networks The rest of the course: Data analysis using Bayesian
Bayesian Learning in Undirected Graphical Models
 Bayesian Learning in Undirected Graphical Models Zoubin Ghahramani Gatsby Computational Neuroscience Unit University College London, UK http://www.gatsby.ucl.ac.uk/ Work with: Iain Murray and Hyun-Chul
Bayesian Learning in Undirected Graphical Models Zoubin Ghahramani Gatsby Computational Neuroscience Unit University College London, UK http://www.gatsby.ucl.ac.uk/ Work with: Iain Murray and Hyun-Chul
15-780: LinearProgramming
 15-780: LinearProgramming J. Zico Kolter February 1-3, 2016 1 Outline Introduction Some linear algebra review Linear programming Simplex algorithm Duality and dual simplex 2 Outline Introduction Some linear
15-780: LinearProgramming J. Zico Kolter February 1-3, 2016 1 Outline Introduction Some linear algebra review Linear programming Simplex algorithm Duality and dual simplex 2 Outline Introduction Some linear
Graphical Gaussian models and their groups
 Piotr Zwiernik TU Eindhoven (j.w. Jan Draisma, Sonja Kuhnt) Workshop on Graphical Models, Fields Institute, Toronto, 16 Apr 2012 1 / 23 Outline and references Outline: 1. Invariance of statistical models
Piotr Zwiernik TU Eindhoven (j.w. Jan Draisma, Sonja Kuhnt) Workshop on Graphical Models, Fields Institute, Toronto, 16 Apr 2012 1 / 23 Outline and references Outline: 1. Invariance of statistical models
STATISTICAL METHODS FOR SIGNAL PROCESSING c Alfred Hero
 STATISTICAL METHODS FOR SIGNAL PROCESSING c Alfred Hero 1999 32 Statistic used Meaning in plain english Reduction ratio T (X) [X 1,..., X n ] T, entire data sample RR 1 T (X) [X (1),..., X (n) ] T, rank
STATISTICAL METHODS FOR SIGNAL PROCESSING c Alfred Hero 1999 32 Statistic used Meaning in plain english Reduction ratio T (X) [X 1,..., X n ] T, entire data sample RR 1 T (X) [X (1),..., X (n) ] T, rank
13: Variational inference II
 10-708: Probabilistic Graphical Models, Spring 2015 13: Variational inference II Lecturer: Eric P. Xing Scribes: Ronghuo Zheng, Zhiting Hu, Yuntian Deng 1 Introduction We started to talk about variational
10-708: Probabilistic Graphical Models, Spring 2015 13: Variational inference II Lecturer: Eric P. Xing Scribes: Ronghuo Zheng, Zhiting Hu, Yuntian Deng 1 Introduction We started to talk about variational
Examples and MatLab. Vector and Matrix Material. Matrix Addition R = A + B. Matrix Equality A = B. Matrix Multiplication R = A * B.
 Vector and Matrix Material Examples and MatLab Matrix = Rectangular array of numbers, complex numbers or functions If r rows & c columns, r*c elements, r*c is order of matrix. A is n * m matrix Square
Vector and Matrix Material Examples and MatLab Matrix = Rectangular array of numbers, complex numbers or functions If r rows & c columns, r*c elements, r*c is order of matrix. A is n * m matrix Square
λ(x + 1)f g (x) > θ 0
 Stat 8111 Final Exam December 16 Eleven students took the exam, the scores were 92, 78, 4 in the 5 s, 1 in the 4 s, 1 in the 3 s and 3 in the 2 s. 1. i) Let X 1, X 2,..., X n be iid each Bernoulli(θ) where
Stat 8111 Final Exam December 16 Eleven students took the exam, the scores were 92, 78, 4 in the 5 s, 1 in the 4 s, 1 in the 3 s and 3 in the 2 s. 1. i) Let X 1, X 2,..., X n be iid each Bernoulli(θ) where
Theory of Computation
 Theory of Computation Lecture #2 Sarmad Abbasi Virtual University Sarmad Abbasi (Virtual University) Theory of Computation 1 / 1 Lecture 2: Overview Recall some basic definitions from Automata Theory.
Theory of Computation Lecture #2 Sarmad Abbasi Virtual University Sarmad Abbasi (Virtual University) Theory of Computation 1 / 1 Lecture 2: Overview Recall some basic definitions from Automata Theory.
Nonlinear Programming Models
 Nonlinear Programming Models Fabio Schoen 2008 http://gol.dsi.unifi.it/users/schoen Nonlinear Programming Models p. Introduction Nonlinear Programming Models p. NLP problems minf(x) x S R n Standard form:
Nonlinear Programming Models Fabio Schoen 2008 http://gol.dsi.unifi.it/users/schoen Nonlinear Programming Models p. Introduction Nonlinear Programming Models p. NLP problems minf(x) x S R n Standard form:
COURSE ON LMI PART I.2 GEOMETRY OF LMI SETS. Didier HENRION henrion
 COURSE ON LMI PART I.2 GEOMETRY OF LMI SETS Didier HENRION www.laas.fr/ henrion October 2006 Geometry of LMI sets Given symmetric matrices F i we want to characterize the shape in R n of the LMI set F
COURSE ON LMI PART I.2 GEOMETRY OF LMI SETS Didier HENRION www.laas.fr/ henrion October 2006 Geometry of LMI sets Given symmetric matrices F i we want to characterize the shape in R n of the LMI set F
Maximum likelihood in log-linear models
 Graphical Models, Lecture 4, Michaelmas Term 2010 October 22, 2010 Generating class Dependence graph of log-linear model Conformal graphical models Factor graphs Let A denote an arbitrary set of subsets
Graphical Models, Lecture 4, Michaelmas Term 2010 October 22, 2010 Generating class Dependence graph of log-linear model Conformal graphical models Factor graphs Let A denote an arbitrary set of subsets
Quantum Correlations: From Bell inequalities to Tsirelson s theorem
 Quantum Correlations: From Bell inequalities to Tsirelson s theorem David Avis April, 7 Abstract The cut polytope and its relatives are good models of the correlations that can be obtained between events
Quantum Correlations: From Bell inequalities to Tsirelson s theorem David Avis April, 7 Abstract The cut polytope and its relatives are good models of the correlations that can be obtained between events
FLEXIBLE COVARIANCE ESTIMATION IN GRAPHICAL GAUSSIAN MODELS
 Submitted to the Annals of Statistics FLEXIBLE COVARIANCE ESTIMATION IN GRAPHICAL GAUSSIAN MODELS By Bala Rajaratnam, Hélène Massam and Carlos M. Carvalho Stanford University, York University, The University
Submitted to the Annals of Statistics FLEXIBLE COVARIANCE ESTIMATION IN GRAPHICAL GAUSSIAN MODELS By Bala Rajaratnam, Hélène Massam and Carlos M. Carvalho Stanford University, York University, The University
Solving a linear equation in a set of integers II
 ACTA ARITHMETICA LXXII.4 (1995) Solving a linear equation in a set of integers II by Imre Z. Ruzsa (Budapest) 1. Introduction. We continue the study of linear equations started in Part I of this paper.
ACTA ARITHMETICA LXXII.4 (1995) Solving a linear equation in a set of integers II by Imre Z. Ruzsa (Budapest) 1. Introduction. We continue the study of linear equations started in Part I of this paper.
ELEMENTARY LINEAR ALGEBRA
 ELEMENTARY LINEAR ALGEBRA K R MATTHEWS DEPARTMENT OF MATHEMATICS UNIVERSITY OF QUEENSLAND First Printing, 99 Chapter LINEAR EQUATIONS Introduction to linear equations A linear equation in n unknowns x,
ELEMENTARY LINEAR ALGEBRA K R MATTHEWS DEPARTMENT OF MATHEMATICS UNIVERSITY OF QUEENSLAND First Printing, 99 Chapter LINEAR EQUATIONS Introduction to linear equations A linear equation in n unknowns x,
1 The General Definition
 MS&E 336 Lecture 1: Dynamic games Ramesh Johari April 4, 2007 1 The General Definition A dynamic game (or extensive game, or game in extensive form) consists of: A set of players N; A set H of sequences
MS&E 336 Lecture 1: Dynamic games Ramesh Johari April 4, 2007 1 The General Definition A dynamic game (or extensive game, or game in extensive form) consists of: A set of players N; A set H of sequences
arxiv: v1 [math.st] 16 Aug 2011
![arxiv: v1 [math.st] 16 Aug 2011 arxiv: v1 [math.st] 16 Aug 2011](/thumbs/84/89155979.jpg) Retaining positive definiteness in thresholded matrices Dominique Guillot Stanford University Bala Rajaratnam Stanford University August 17, 2011 arxiv:1108.3325v1 [math.st] 16 Aug 2011 Abstract Positive
Retaining positive definiteness in thresholded matrices Dominique Guillot Stanford University Bala Rajaratnam Stanford University August 17, 2011 arxiv:1108.3325v1 [math.st] 16 Aug 2011 Abstract Positive
Things to remember: x n a 1. x + a 0. x n + a n-1. P(x) = a n. Therefore, lim g(x) = 1. EXERCISE 3-2
 lim f() = lim (0.8-0.08) = 0, " "!10!10 lim f() = lim 0 = 0.!10!10 Therefore, lim f() = 0.!10 lim g() = lim (0.8 - "!10!10 0.042-3) = 1, " lim g() = lim 1 = 1.!10!0 Therefore, lim g() = 1.!10 EXERCISE
lim f() = lim (0.8-0.08) = 0, " "!10!10 lim f() = lim 0 = 0.!10!10 Therefore, lim f() = 0.!10 lim g() = lim (0.8 - "!10!10 0.042-3) = 1, " lim g() = lim 1 = 1.!10!0 Therefore, lim g() = 1.!10 EXERCISE
IMC 2015, Blagoevgrad, Bulgaria
 IMC 05, Blagoevgrad, Bulgaria Day, July 9, 05 Problem. For any integer n and two n n matrices with real entries, B that satisfy the equation + B ( + B prove that det( det(b. Does the same conclusion follow
IMC 05, Blagoevgrad, Bulgaria Day, July 9, 05 Problem. For any integer n and two n n matrices with real entries, B that satisfy the equation + B ( + B prove that det( det(b. Does the same conclusion follow
UNIT 3. Rational Functions Limits at Infinity (Horizontal and Slant Asymptotes) Infinite Limits (Vertical Asymptotes) Graphing Rational Functions
 UNIT 3 Rational Functions Limits at Infinity (Horizontal and Slant Asymptotes) Infinite Limits (Vertical Asymptotes) Graphing Rational Functions Recall From Unit Rational Functions f() is a rational function
UNIT 3 Rational Functions Limits at Infinity (Horizontal and Slant Asymptotes) Infinite Limits (Vertical Asymptotes) Graphing Rational Functions Recall From Unit Rational Functions f() is a rational function
Math 360 Linear Algebra Fall Class Notes. a a a a a a. a a a
 Math 360 Linear Algebra Fall 2008 9-10-08 Class Notes Matrices As we have already seen, a matrix is a rectangular array of numbers. If a matrix A has m columns and n rows, we say that its dimensions are
Math 360 Linear Algebra Fall 2008 9-10-08 Class Notes Matrices As we have already seen, a matrix is a rectangular array of numbers. If a matrix A has m columns and n rows, we say that its dimensions are
Notes on Complex Analysis
 Michael Papadimitrakis Notes on Complex Analysis Department of Mathematics University of Crete Contents The complex plane.. The complex plane...................................2 Argument and polar representation.........................
Michael Papadimitrakis Notes on Complex Analysis Department of Mathematics University of Crete Contents The complex plane.. The complex plane...................................2 Argument and polar representation.........................
Invariant HPD credible sets and MAP estimators
 Bayesian Analysis (007), Number 4, pp. 681 69 Invariant HPD credible sets and MAP estimators Pierre Druilhet and Jean-Michel Marin Abstract. MAP estimators and HPD credible sets are often criticized in
Bayesian Analysis (007), Number 4, pp. 681 69 Invariant HPD credible sets and MAP estimators Pierre Druilhet and Jean-Michel Marin Abstract. MAP estimators and HPD credible sets are often criticized in
BASIC NOTIONS. x + y = 1 3, 3x 5y + z = A + 3B,C + 2D, DC are not defined. A + C =
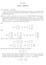 CHAPTER I BASIC NOTIONS (a) 8666 and 8833 (b) a =6,a =4 will work in the first case, but there are no possible such weightings to produce the second case, since Student and Student 3 have to end up with
CHAPTER I BASIC NOTIONS (a) 8666 and 8833 (b) a =6,a =4 will work in the first case, but there are no possible such weightings to produce the second case, since Student and Student 3 have to end up with
(4.2) Equivalence Relations. 151 Math Exercises. Malek Zein AL-Abidin. King Saud University College of Science Department of Mathematics
 King Saud University College of Science Department of Mathematics 151 Math Exercises (4.2) Equivalence Relations Malek Zein AL-Abidin 1440 ه 2018 Equivalence Relations DEFINITION 1 A relation on a set
King Saud University College of Science Department of Mathematics 151 Math Exercises (4.2) Equivalence Relations Malek Zein AL-Abidin 1440 ه 2018 Equivalence Relations DEFINITION 1 A relation on a set
ALGEBRA II: RINGS AND MODULES OVER LITTLE RINGS.
 ALGEBRA II: RINGS AND MODULES OVER LITTLE RINGS. KEVIN MCGERTY. 1. RINGS The central characters of this course are algebraic objects known as rings. A ring is any mathematical structure where you can add
ALGEBRA II: RINGS AND MODULES OVER LITTLE RINGS. KEVIN MCGERTY. 1. RINGS The central characters of this course are algebraic objects known as rings. A ring is any mathematical structure where you can add
CS3719 Theory of Computation and Algorithms
 CS3719 Theory of Computation and Algorithms Any mechanically (automatically) discretely computation of problem solving contains at least three components: - problem description - computational tool - analysis
CS3719 Theory of Computation and Algorithms Any mechanically (automatically) discretely computation of problem solving contains at least three components: - problem description - computational tool - analysis
One-to-one functions and onto functions
 MA 3362 Lecture 7 - One-to-one and Onto Wednesday, October 22, 2008. Objectives: Formalize definitions of one-to-one and onto One-to-one functions and onto functions At the level of set theory, there are
MA 3362 Lecture 7 - One-to-one and Onto Wednesday, October 22, 2008. Objectives: Formalize definitions of one-to-one and onto One-to-one functions and onto functions At the level of set theory, there are
REVIEW Chapter 1 The Real Number System
 REVIEW Chapter The Real Number System In class work: Complete all statements. Solve all exercises. (Section.4) A set is a collection of objects (elements). The Set of Natural Numbers N N = {,,, 4, 5, }
REVIEW Chapter The Real Number System In class work: Complete all statements. Solve all exercises. (Section.4) A set is a collection of objects (elements). The Set of Natural Numbers N N = {,,, 4, 5, }
Definition: A binary relation R from a set A to a set B is a subset R A B. Example:
 Chapter 9 1 Binary Relations Definition: A binary relation R from a set A to a set B is a subset R A B. Example: Let A = {0,1,2} and B = {a,b} {(0, a), (0, b), (1,a), (2, b)} is a relation from A to B.
Chapter 9 1 Binary Relations Definition: A binary relation R from a set A to a set B is a subset R A B. Example: Let A = {0,1,2} and B = {a,b} {(0, a), (0, b), (1,a), (2, b)} is a relation from A to B.
Matrices and Linear Algebra
 Contents Quantitative methods for Economics and Business University of Ferrara Academic year 2017-2018 Contents 1 Basics 2 3 4 5 Contents 1 Basics 2 3 4 5 Contents 1 Basics 2 3 4 5 Contents 1 Basics 2
Contents Quantitative methods for Economics and Business University of Ferrara Academic year 2017-2018 Contents 1 Basics 2 3 4 5 Contents 1 Basics 2 3 4 5 Contents 1 Basics 2 3 4 5 Contents 1 Basics 2
BASIC MATHEMATICAL TECHNIQUES
 CHAPTER 1 ASIC MATHEMATICAL TECHNIQUES 1.1 Introduction To understand automata theory, one must have a strong foundation about discrete mathematics. Discrete mathematics is a branch of mathematics dealing
CHAPTER 1 ASIC MATHEMATICAL TECHNIQUES 1.1 Introduction To understand automata theory, one must have a strong foundation about discrete mathematics. Discrete mathematics is a branch of mathematics dealing
In class midterm Exam - Answer key
 Fall 2013 In class midterm Exam - Answer key ARE211 Problem 1 (20 points). Metrics: Let B be the set of all sequences x = (x 1,x 2,...). Define d(x,y) = sup{ x i y i : i = 1,2,...}. a) Prove that d is
Fall 2013 In class midterm Exam - Answer key ARE211 Problem 1 (20 points). Metrics: Let B be the set of all sequences x = (x 1,x 2,...). Define d(x,y) = sup{ x i y i : i = 1,2,...}. a) Prove that d is
JUST THE MATHS UNIT NUMBER 1.5. ALGEBRA 5 (Manipulation of algebraic expressions) A.J.Hobson
 JUST THE MATHS UNIT NUMBER 1.5 ALGEBRA 5 (Manipulation of algebraic expressions) by A.J.Hobson 1.5.1 Simplification of expressions 1.5.2 Factorisation 1.5.3 Completing the square in a quadratic expression
JUST THE MATHS UNIT NUMBER 1.5 ALGEBRA 5 (Manipulation of algebraic expressions) by A.J.Hobson 1.5.1 Simplification of expressions 1.5.2 Factorisation 1.5.3 Completing the square in a quadratic expression
Projective Spaces. Chapter The Projective Line
 Chapter 3 Projective Spaces 3.1 The Projective Line Suppose you want to describe the lines through the origin O = (0, 0) in the Euclidean plane R 2. The first thing you might think of is to write down
Chapter 3 Projective Spaces 3.1 The Projective Line Suppose you want to describe the lines through the origin O = (0, 0) in the Euclidean plane R 2. The first thing you might think of is to write down
UNIVERSITY OF MICHIGAN UNDERGRADUATE MATH COMPETITION 28 APRIL 7, 2011
 UNIVERSITY OF MICHIGAN UNDERGRADUATE MATH COMPETITION 28 APRIL 7, 20 Instructions. Write on the front of your blue book your student ID number. Do not write your name anywhere on your blue book. Each question
UNIVERSITY OF MICHIGAN UNDERGRADUATE MATH COMPETITION 28 APRIL 7, 20 Instructions. Write on the front of your blue book your student ID number. Do not write your name anywhere on your blue book. Each question
Semidefinite and Second Order Cone Programming Seminar Fall 2001 Lecture 5
 Semidefinite and Second Order Cone Programming Seminar Fall 2001 Lecture 5 Instructor: Farid Alizadeh Scribe: Anton Riabov 10/08/2001 1 Overview We continue studying the maximum eigenvalue SDP, and generalize
Semidefinite and Second Order Cone Programming Seminar Fall 2001 Lecture 5 Instructor: Farid Alizadeh Scribe: Anton Riabov 10/08/2001 1 Overview We continue studying the maximum eigenvalue SDP, and generalize
Dynamic Programming. Shuang Zhao. Microsoft Research Asia September 5, Dynamic Programming. Shuang Zhao. Outline. Introduction.
 Microsoft Research Asia September 5, 2005 1 2 3 4 Section I What is? Definition is a technique for efficiently recurrence computing by storing partial results. In this slides, I will NOT use too many formal
Microsoft Research Asia September 5, 2005 1 2 3 4 Section I What is? Definition is a technique for efficiently recurrence computing by storing partial results. In this slides, I will NOT use too many formal
