Selection and Adversary Arguments. COMP 215 Lecture 19
|
|
|
- Marilynn Evans
- 5 years ago
- Views:
Transcription
1 Selection and Adversary Arguments COMP 215 Lecture 19
2 Selection Problems We want to find the k'th largest entry in an unsorted array. Could be the largest, smallest, median, etc. Ideas for an n lg n algorithm? We will think about: Largest, smallest Largest AND smallest Second largest Kth.
3 Finding the Largest Item We have seen a simple algorithm that requires n 1 comparisons in the worst case. That's optimal.
4 Largest and Smallest We could run the previous algorithm twice, which would give us 2n 2 comparisons. We have seen an algorithm that requires comparisons in the worst case. Anyone remember? Is this optimal? First idea is to consider a decision tree. There must be at least n leaves. Therefore the height must be at least lg n. Obviously not a very tight bound. 3 n 2 2
5 Adversary Arguments We design an adversary that forces any algorithm to do as much work as possible. The adversary does not have a particular solution in mind all answers are chosen to reveal as little information as possible while being consistent with earlier answers. The analysis proceeds by Determining what information the algorithm needs to solve the problem. Determining how long it will take to get that information from the adversary.
6 Adversary for Largest/Smallest In order to determine both the largest and the smallest we assign states to keys: X Key has not been involved in comparison. (0 unit) L Key has lost at least one comparison. (1 unit) W Key has won at least one comparison. (1 unit) WL Key has won and lost a comparison. (2 units) We cannot determine the largest and smallest keys until All keys except one have lost a comparison: n 1 units. All keys except one have won a comparison: n 1 units. We need to learn 2n 2 things overall. We design an adversary that reveals as little as possible.
7 Adversary for Largest/Smallest Before Winner After Information X X 1 W L 2 X L 1 W L 1 X W 2 L W 1 X WL 1 W WL 1 L L 1 WL W 1 L W 2 L W 0 L WL 2 L WL 0 W W 1 W WL 1 W WL 1 W WL 0 WL WL be consistent W WL 0
8 Adversary for Largest/Smallest We need to get 2n 2 items of information. How many comparisons are necessary? The most information per comparison (2) occurs when neither item has one or lost. This can happen at most n/2 times for a total of n items of information. Any other comparison results in at most 1 unit of information. We need at least 2n 2 n = n 2 of these. Total number of comparisons is n 2 + n/2 = 3n/2 2. This lower bound matches the worst case of our algorithm.
9 Second Largest Item One possibility is to find the largest, remove it, then find the largest remaining: (n 1) + (n 2) = 2n 3 comparisons. A better alternative is the tournament approach. Hold a tournament to determine the largest key. Since the second largest key must be defeated by the largest key at some point, We look for the largest key among those keys beaten by the largest key.
10 Second Largest Analysis We will just do the analysis for powers of 2. First, how many comparisons in the tournament: n 2 n 2 n lg n = n 2 2 lg n i=1 1 2 i = n 1 Next, how many keys did the max key defeat? lg n Therefore searching for the max among the defeated keys will take lg n 1 comparisons. Total comparisons: (n 1) + (lg n 1) = n + lg n 2. If n is not a power of 2: n lg n 2 Is this optimal?
11 Second Largest Adversary For any algorithm, the largest key is involved in some number of comparisons m. Discounting the largest key, there are n 1 keys. It takes at least n 2 comparisons to find the second largest among those keys. The m comparisons with the largest key cannot count toward that n 2. Therefore the total number of comparisons required is at least m + n 2. We will construct an adversary that forces m to be at least lg n.
12 Second Largest Adversary Adversary builds a tree, and uses it to guide answers. Initially all nodes are roots (throughout a root node will represent a key that hasn't lost a comparison.) Two roots compared: If both trees are the same size, answer is arbitrary, smaller is made child of larger. If one tree is larger, the root of the smaller tree loses, and is made a child of the root of the larger tree. A root and a non root are compared. The non root is declared smaller, and trees are not changed. Two non roots are compared. Answer is consistent with previous answers, and trees are not changed.
13 Second Largest Adversary When any correct algorithm terminates, there can be at most one root. Otherwise there are two keys that never lost a comparison. The rules on the previous slide are designed so that the tree with the largest key as a root grows as slowly as possible.
14 Second Largest Adversary The question is: how many comparisons must a key have been involved in to end up at the root of the final tree? The size of the tree rooted at the largest tree at most doubles after each comparison, after the kth comparison: size k 2 size k 1 Initial size of the tree rooted at the largest tree is 1. size 0 =1 Homogeneous linear recurrence. Solution is: size k 2 k. n=size m 2 m lg n m lg n m
15 Second Largest Adversary Final result is a n lg n 2 lower bound. Recall that our tournament algorithm required comparisons. n lg n 2
16 Kth Smallest Entry We can solve this problem with order n comparisons (average case) with a small modification to quicksort. Recall, that after each call to partition, the pivot item is in its final sorted position. If the pivot item is at the kth position, then we have the kth smallest item. Here is the algorithm: Partition the data, if pivot point = k, terminate. if pivot point > k, partition the array up to pivot position. if pivot point < k, partition the array after the pivot position. Repeat until pivot position = k.
17 Selection Analysis Worst case comparisons? Average case comparisons?
18 Selection Analysis Worst case comparisons? Same as quicksort: n 2. Average case comparisons? In order to do an average case analysis we sum up the cost associated with every possible input, divide by the number of possible inputs. Assume that every k is equally possible, and every pivot point is equally possible after a partition.
19 Selection Analysis Average Case Input size of recursive calls can be anything from 0 to n 1. Size is 0 if k = p (pivot point) after first partition. There are n ways for that to happen. Size is 1 if k = 1 and p = 2, or if k=n and p = n 1... two possible ways. Four ways for size to be (n 1) ways for size to be n 1.
20 Selection Analysis Average Case This leads to an ugly recurrence: A n = na 0 2 A 1 4 A 2 2 n 1 A n 1 n 1 n n 1 The book informs us that this works out to: A n 3 n
21 Selection in Worst Case Linear Time In our previous algorithm we wanted the pivot item to be near the median. This causes the size of the array to be roughly halved on each recursive call. No obvious way to select a pivot item near the median, without knowing what the median is. Determining the median requires solving the selection problem. Doh. Amazingly, there is a way forward...
22 Linear Time Selection Alter our partition function as follows: First break the array into n/5 groups. Compute the median of each of those groups. This can be done with six comparisons per group. Alternately, just use insertion sort on each group. Now, recursively call the selection algorithm to determine the median of our n/5 medians. It turns out that this median of medians will be reasonably close to the median. Use the result as the pivot point and partition as usual. The resulting algorithm is worst case linear time.
23 Linear Selection Analysis First, how close is the median of medians to the median? Let's draw a picture... So, roughly speaking, there are at most 3(n/10) items larger than the median of medians, and at most that many smaller. So the worst case size of the input to the recursive call is about 7n/10. Book comes up with 7n/10 3/2.
24 Linear Selection Analysis We can write the following recurrence to describe the worst case number of comparisons: W n = W 7 n W n 5 6 n 5 n Worst case cost of the next recursive call cost of finding the median of n/5 medians cost of finding the n/5 medians cost of partition
25 Linear Selection Analysis We don't really have any tools for dealing with this recurrence: Revert to guess and check. We guess that it is W(n) is linear, i.e. W(n) <= cn. Therefore: W n = W 7 n 10 3 W n 11 n c 7 n 10 3 c n n 5 Solving this, we get 22 <= c. c n We then use induction to prove that W(n) <= 22n.
26 Linear Selection Analysis There are selection algorithms that are closer to 3n in the worst case. We could construct an adversary argument to provide a lower bound for this problem. The highest lower bound determined so far is a bit more than 2n. Computer Algorithms, Baase and Van Gelder, 2000.
Data Structures and Algorithms
 Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
Quick Sort Notes , Spring 2010
 Quick Sort Notes 18.310, Spring 2010 0.1 Randomized Median Finding In a previous lecture, we discussed the problem of finding the median of a list of m elements, or more generally the element of rank m.
Quick Sort Notes 18.310, Spring 2010 0.1 Randomized Median Finding In a previous lecture, we discussed the problem of finding the median of a list of m elements, or more generally the element of rank m.
Algorithms and Data Structures 2016 Week 5 solutions (Tues 9th - Fri 12th February)
 Algorithms and Data Structures 016 Week 5 solutions (Tues 9th - Fri 1th February) 1. Draw the decision tree (under the assumption of all-distinct inputs) Quicksort for n = 3. answer: (of course you should
Algorithms and Data Structures 016 Week 5 solutions (Tues 9th - Fri 1th February) 1. Draw the decision tree (under the assumption of all-distinct inputs) Quicksort for n = 3. answer: (of course you should
Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018
 CS17 Integrated Introduction to Computer Science Klein Contents Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018 1 Tree definitions 1 2 Analysis of mergesort using a binary tree 1 3 Analysis of
CS17 Integrated Introduction to Computer Science Klein Contents Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018 1 Tree definitions 1 2 Analysis of mergesort using a binary tree 1 3 Analysis of
1 Terminology and setup
 15-451/651: Design & Analysis of Algorithms August 31, 2017 Lecture #2 last changed: August 29, 2017 In this lecture, we will examine some simple, concrete models of computation, each with a precise definition
15-451/651: Design & Analysis of Algorithms August 31, 2017 Lecture #2 last changed: August 29, 2017 In this lecture, we will examine some simple, concrete models of computation, each with a precise definition
Partition and Select
 Divide-Conquer-Glue Algorithms Quicksort, Quickselect and the Master Theorem Quickselect algorithm Tyler Moore CSE 3353, SMU, Dallas, TX Lecture 11 Selection Problem: find the kth smallest number of an
Divide-Conquer-Glue Algorithms Quicksort, Quickselect and the Master Theorem Quickselect algorithm Tyler Moore CSE 3353, SMU, Dallas, TX Lecture 11 Selection Problem: find the kth smallest number of an
N/4 + N/2 + N = 2N 2.
 CS61B Summer 2006 Instructor: Erin Korber Lecture 24, 7 Aug. 1 Amortized Analysis For some of the data structures we ve discussed (namely hash tables and splay trees), it was claimed that the average time
CS61B Summer 2006 Instructor: Erin Korber Lecture 24, 7 Aug. 1 Amortized Analysis For some of the data structures we ve discussed (namely hash tables and splay trees), it was claimed that the average time
Find Min and Max. Find them independantly: 2n 2. Can easily modify to get 2n 3. Should be able to do better(?) Try divide and conquer.
 Find Min and Max Find them independantly: 2n 2. Can easily modify to get 2n 3. Should be able to do better(?) Try divide and conquer. Find_Max_Min(ELEM *L, int lower, int upper) { if (upper == lower) return
Find Min and Max Find them independantly: 2n 2. Can easily modify to get 2n 3. Should be able to do better(?) Try divide and conquer. Find_Max_Min(ELEM *L, int lower, int upper) { if (upper == lower) return
Algorithms Test 1. Question 1. (10 points) for (i = 1; i <= n; i++) { j = 1; while (j < n) {
 Question 1. (10 points) for (i = 1; i
Question 1. (10 points) for (i = 1; i
Algorithms And Programming I. Lecture 5 Quicksort
 Algorithms And Programming I Lecture 5 Quicksort Quick Sort Partition set into two using randomly chosen pivot 88 31 25 52 14 98 62 30 23 79 14 31 2530 23 52 88 62 98 79 Quick Sort 14 31 2530 23 52 88
Algorithms And Programming I Lecture 5 Quicksort Quick Sort Partition set into two using randomly chosen pivot 88 31 25 52 14 98 62 30 23 79 14 31 2530 23 52 88 62 98 79 Quick Sort 14 31 2530 23 52 88
Lecture 4. Quicksort
 Lecture 4. Quicksort T. H. Cormen, C. E. Leiserson and R. L. Rivest Introduction to Algorithms, 3rd Edition, MIT Press, 2009 Sungkyunkwan University Hyunseung Choo choo@skku.edu Copyright 2000-2018 Networking
Lecture 4. Quicksort T. H. Cormen, C. E. Leiserson and R. L. Rivest Introduction to Algorithms, 3rd Edition, MIT Press, 2009 Sungkyunkwan University Hyunseung Choo choo@skku.edu Copyright 2000-2018 Networking
15.1 Introduction to Lower Bounds Proofs
 15 Lower Bounds How do I know if I have a good algorithm to solve a problem? If my algorithm runs in Θ(n log n) time, is that good? It would be if I were sorting the records stored in an array. But it
15 Lower Bounds How do I know if I have a good algorithm to solve a problem? If my algorithm runs in Θ(n log n) time, is that good? It would be if I were sorting the records stored in an array. But it
Lecture 1: Asymptotics, Recurrences, Elementary Sorting
 Lecture 1: Asymptotics, Recurrences, Elementary Sorting Instructor: Outline 1 Introduction to Asymptotic Analysis Rate of growth of functions Comparing and bounding functions: O, Θ, Ω Specifying running
Lecture 1: Asymptotics, Recurrences, Elementary Sorting Instructor: Outline 1 Introduction to Asymptotic Analysis Rate of growth of functions Comparing and bounding functions: O, Θ, Ω Specifying running
Divide and Conquer Algorithms. CSE 101: Design and Analysis of Algorithms Lecture 14
 Divide and Conquer Algorithms CSE 101: Design and Analysis of Algorithms Lecture 14 CSE 101: Design and analysis of algorithms Divide and conquer algorithms Reading: Sections 2.3 and 2.4 Homework 6 will
Divide and Conquer Algorithms CSE 101: Design and Analysis of Algorithms Lecture 14 CSE 101: Design and analysis of algorithms Divide and conquer algorithms Reading: Sections 2.3 and 2.4 Homework 6 will
Concrete models and tight upper/lower bounds
 Lecture 3 Concrete models and tight upper/lower bounds 3.1 Overview In this lecture, we will examine some simple, concrete models of computation, each with a precise definition of what counts as a step,
Lecture 3 Concrete models and tight upper/lower bounds 3.1 Overview In this lecture, we will examine some simple, concrete models of computation, each with a precise definition of what counts as a step,
CS 2110: INDUCTION DISCUSSION TOPICS
 CS 110: INDUCTION DISCUSSION TOPICS The following ideas are suggestions for how to handle your discussion classes. You can do as much or as little of this as you want. You can either present at the board,
CS 110: INDUCTION DISCUSSION TOPICS The following ideas are suggestions for how to handle your discussion classes. You can do as much or as little of this as you want. You can either present at the board,
Data selection. Lower complexity bound for sorting
 Data selection. Lower complexity bound for sorting Lecturer: Georgy Gimel farb COMPSCI 220 Algorithms and Data Structures 1 / 12 1 Data selection: Quickselect 2 Lower complexity bound for sorting 3 The
Data selection. Lower complexity bound for sorting Lecturer: Georgy Gimel farb COMPSCI 220 Algorithms and Data Structures 1 / 12 1 Data selection: Quickselect 2 Lower complexity bound for sorting 3 The
CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015
 CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015 1 Introduction The divide-and-conquer strategy is a general paradigm for algorithm design. This strategy
CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015 1 Introduction The divide-and-conquer strategy is a general paradigm for algorithm design. This strategy
Finding the Median. 1 The problem of finding the median. 2 A good strategy? lecture notes September 2, Lecturer: Michel Goemans
 18.310 lecture notes September 2, 2013 Finding the Median Lecturer: Michel Goemans 1 The problem of finding the median Suppose we have a list of n keys that are completely unsorted. If we want to find
18.310 lecture notes September 2, 2013 Finding the Median Lecturer: Michel Goemans 1 The problem of finding the median Suppose we have a list of n keys that are completely unsorted. If we want to find
CPSC 320 Sample Final Examination December 2013
 CPSC 320 Sample Final Examination December 2013 [10] 1. Answer each of the following questions with true or false. Give a short justification for each of your answers. [5] a. 6 n O(5 n ) lim n + This is
CPSC 320 Sample Final Examination December 2013 [10] 1. Answer each of the following questions with true or false. Give a short justification for each of your answers. [5] a. 6 n O(5 n ) lim n + This is
b + O(n d ) where a 1, b > 1, then O(n d log n) if a = b d d ) if a < b d O(n log b a ) if a > b d
 CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
Linear Time Selection
 Linear Time Selection Given (x,y coordinates of N houses, where should you build road These lecture slides are adapted from CLRS.. Princeton University COS Theory of Algorithms Spring 0 Kevin Wayne Given
Linear Time Selection Given (x,y coordinates of N houses, where should you build road These lecture slides are adapted from CLRS.. Princeton University COS Theory of Algorithms Spring 0 Kevin Wayne Given
Review Of Topics. Review: Induction
 Review Of Topics Asymptotic notation Solving recurrences Sorting algorithms Insertion sort Merge sort Heap sort Quick sort Counting sort Radix sort Medians/order statistics Randomized algorithm Worst-case
Review Of Topics Asymptotic notation Solving recurrences Sorting algorithms Insertion sort Merge sort Heap sort Quick sort Counting sort Radix sort Medians/order statistics Randomized algorithm Worst-case
Lecture 2: Divide and conquer and Dynamic programming
 Chapter 2 Lecture 2: Divide and conquer and Dynamic programming 2.1 Divide and Conquer Idea: - divide the problem into subproblems in linear time - solve subproblems recursively - combine the results in
Chapter 2 Lecture 2: Divide and conquer and Dynamic programming 2.1 Divide and Conquer Idea: - divide the problem into subproblems in linear time - solve subproblems recursively - combine the results in
1 Introduction (January 21)
 CS 97: Concrete Models of Computation Spring Introduction (January ). Deterministic Complexity Consider a monotonically nondecreasing function f : {,,..., n} {, }, where f() = and f(n) =. We call f a step
CS 97: Concrete Models of Computation Spring Introduction (January ). Deterministic Complexity Consider a monotonically nondecreasing function f : {,,..., n} {, }, where f() = and f(n) =. We call f a step
Data Structures and Algorithms CSE 465
 Data Structures and Algorithms CSE 465 LECTURE 8 Analyzing Quick Sort Sofya Raskhodnikova and Adam Smith Reminder: QuickSort Quicksort an n-element array: 1. Divide: Partition the array around a pivot
Data Structures and Algorithms CSE 465 LECTURE 8 Analyzing Quick Sort Sofya Raskhodnikova and Adam Smith Reminder: QuickSort Quicksort an n-element array: 1. Divide: Partition the array around a pivot
Algorithms. Quicksort. Slide credit: David Luebke (Virginia)
 1 Algorithms Quicksort Slide credit: David Luebke (Virginia) Sorting revisited We have seen algorithms for sorting: INSERTION-SORT, MERGESORT More generally: given a sequence of items Each item has a characteristic
1 Algorithms Quicksort Slide credit: David Luebke (Virginia) Sorting revisited We have seen algorithms for sorting: INSERTION-SORT, MERGESORT More generally: given a sequence of items Each item has a characteristic
Design and Analysis of Algorithms
 CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 5: Divide and Conquer (Part 2) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ A Lower Bound on Convex Hull Lecture 4 Task: sort the
CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 5: Divide and Conquer (Part 2) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ A Lower Bound on Convex Hull Lecture 4 Task: sort the
Week 5: Quicksort, Lower bound, Greedy
 Week 5: Quicksort, Lower bound, Greedy Agenda: Quicksort: Average case Lower bound for sorting Greedy method 1 Week 5: Quicksort Recall Quicksort: The ideas: Pick one key Compare to others: partition into
Week 5: Quicksort, Lower bound, Greedy Agenda: Quicksort: Average case Lower bound for sorting Greedy method 1 Week 5: Quicksort Recall Quicksort: The ideas: Pick one key Compare to others: partition into
CS 161 Summer 2009 Homework #2 Sample Solutions
 CS 161 Summer 2009 Homework #2 Sample Solutions Regrade Policy: If you believe an error has been made in the grading of your homework, you may resubmit it for a regrade. If the error consists of more than
CS 161 Summer 2009 Homework #2 Sample Solutions Regrade Policy: If you believe an error has been made in the grading of your homework, you may resubmit it for a regrade. If the error consists of more than
Divide-and-conquer. Curs 2015
 Divide-and-conquer Curs 2015 The divide-and-conquer strategy. 1. Break the problem into smaller subproblems, 2. recursively solve each problem, 3. appropriately combine their answers. Known Examples: Binary
Divide-and-conquer Curs 2015 The divide-and-conquer strategy. 1. Break the problem into smaller subproblems, 2. recursively solve each problem, 3. appropriately combine their answers. Known Examples: Binary
Fast Sorting and Selection. A Lower Bound for Worst Case
 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 0 Fast Sorting and Selection USGS NEIC. Public domain government image. A Lower Bound
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 0 Fast Sorting and Selection USGS NEIC. Public domain government image. A Lower Bound
data structures and algorithms lecture 2
 data structures and algorithms 2018 09 06 lecture 2 recall: insertion sort Algorithm insertionsort(a, n): for j := 2 to n do key := A[j] i := j 1 while i 1 and A[i] > key do A[i + 1] := A[i] i := i 1 A[i
data structures and algorithms 2018 09 06 lecture 2 recall: insertion sort Algorithm insertionsort(a, n): for j := 2 to n do key := A[j] i := j 1 while i 1 and A[i] > key do A[i + 1] := A[i] i := i 1 A[i
Quicksort (CLRS 7) We previously saw how the divide-and-conquer technique can be used to design sorting algorithm Merge-sort
 Quicksort (CLRS 7) We previously saw how the divide-and-conquer technique can be used to design sorting algorithm Merge-sort Partition n elements array A into two subarrays of n/2 elements each Sort the
Quicksort (CLRS 7) We previously saw how the divide-and-conquer technique can be used to design sorting algorithm Merge-sort Partition n elements array A into two subarrays of n/2 elements each Sort the
COMP Analysis of Algorithms & Data Structures
 COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 5 - Jan. 12, 2018 CLRS 1.1, 1.2, 2.2, 3.1, 4.3, 4.5 University of Manitoba Picture is from the cover of the textbook CLRS. 1 /
COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 5 - Jan. 12, 2018 CLRS 1.1, 1.2, 2.2, 3.1, 4.3, 4.5 University of Manitoba Picture is from the cover of the textbook CLRS. 1 /
CSCE 750 Final Exam Answer Key Wednesday December 7, 2005
 CSCE 750 Final Exam Answer Key Wednesday December 7, 2005 Do all problems. Put your answers on blank paper or in a test booklet. There are 00 points total in the exam. You have 80 minutes. Please note
CSCE 750 Final Exam Answer Key Wednesday December 7, 2005 Do all problems. Put your answers on blank paper or in a test booklet. There are 00 points total in the exam. You have 80 minutes. Please note
IS 709/809: Computational Methods in IS Research Fall Exam Review
 IS 709/809: Computational Methods in IS Research Fall 2017 Exam Review Nirmalya Roy Department of Information Systems University of Maryland Baltimore County www.umbc.edu Exam When: Tuesday (11/28) 7:10pm
IS 709/809: Computational Methods in IS Research Fall 2017 Exam Review Nirmalya Roy Department of Information Systems University of Maryland Baltimore County www.umbc.edu Exam When: Tuesday (11/28) 7:10pm
Asymptotic Analysis and Recurrences
 Appendix A Asymptotic Analysis and Recurrences A.1 Overview We discuss the notion of asymptotic analysis and introduce O, Ω, Θ, and o notation. We then turn to the topic of recurrences, discussing several
Appendix A Asymptotic Analysis and Recurrences A.1 Overview We discuss the notion of asymptotic analysis and introduce O, Ω, Θ, and o notation. We then turn to the topic of recurrences, discussing several
Randomized Sorting Algorithms Quick sort can be converted to a randomized algorithm by picking the pivot element randomly. In this case we can show th
 CSE 3500 Algorithms and Complexity Fall 2016 Lecture 10: September 29, 2016 Quick sort: Average Run Time In the last lecture we started analyzing the expected run time of quick sort. Let X = k 1, k 2,...,
CSE 3500 Algorithms and Complexity Fall 2016 Lecture 10: September 29, 2016 Quick sort: Average Run Time In the last lecture we started analyzing the expected run time of quick sort. Let X = k 1, k 2,...,
Kartsuba s Algorithm and Linear Time Selection
 CS 374: Algorithms & Models of Computation, Fall 2015 Kartsuba s Algorithm and Linear Time Selection Lecture 09 September 22, 2015 Chandra & Manoj (UIUC) CS374 1 Fall 2015 1 / 32 Part I Fast Multiplication
CS 374: Algorithms & Models of Computation, Fall 2015 Kartsuba s Algorithm and Linear Time Selection Lecture 09 September 22, 2015 Chandra & Manoj (UIUC) CS374 1 Fall 2015 1 / 32 Part I Fast Multiplication
Algorithm Design and Analysis
 Algorithm Design and Analysis LECTURE 9 Divide and Conquer Merge sort Counting Inversions Binary Search Exponentiation Solving Recurrences Recursion Tree Method Master Theorem Sofya Raskhodnikova S. Raskhodnikova;
Algorithm Design and Analysis LECTURE 9 Divide and Conquer Merge sort Counting Inversions Binary Search Exponentiation Solving Recurrences Recursion Tree Method Master Theorem Sofya Raskhodnikova S. Raskhodnikova;
Analysis of Algorithms - Using Asymptotic Bounds -
 Analysis of Algorithms - Using Asymptotic Bounds - Andreas Ermedahl MRTC (Mälardalens Real-Time Research Center) andreas.ermedahl@mdh.se Autumn 004 Rehersal: Asymptotic bounds Gives running time bounds
Analysis of Algorithms - Using Asymptotic Bounds - Andreas Ermedahl MRTC (Mälardalens Real-Time Research Center) andreas.ermedahl@mdh.se Autumn 004 Rehersal: Asymptotic bounds Gives running time bounds
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Asymptotic Analysis, recurrences Date: 9/7/17
 601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Asymptotic Analysis, recurrences Date: 9/7/17 2.1 Notes Homework 1 will be released today, and is due a week from today by the beginning
601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Asymptotic Analysis, recurrences Date: 9/7/17 2.1 Notes Homework 1 will be released today, and is due a week from today by the beginning
CS361 Homework #3 Solutions
 CS6 Homework # Solutions. Suppose I have a hash table with 5 locations. I would like to know how many items I can store in it before it becomes fairly likely that I have a collision, i.e., that two items
CS6 Homework # Solutions. Suppose I have a hash table with 5 locations. I would like to know how many items I can store in it before it becomes fairly likely that I have a collision, i.e., that two items
Recurrences COMP 215
 Recurrences COMP 215 Analysis of Iterative Algorithms //return the location of the item matching x, or 0 if //no such item is found. index SequentialSearch(keytype[] S, in, keytype x) { index location
Recurrences COMP 215 Analysis of Iterative Algorithms //return the location of the item matching x, or 0 if //no such item is found. index SequentialSearch(keytype[] S, in, keytype x) { index location
Divide-and-conquer: Order Statistics. Curs: Fall 2017
 Divide-and-conquer: Order Statistics Curs: Fall 2017 The divide-and-conquer strategy. 1. Break the problem into smaller subproblems, 2. recursively solve each problem, 3. appropriately combine their answers.
Divide-and-conquer: Order Statistics Curs: Fall 2017 The divide-and-conquer strategy. 1. Break the problem into smaller subproblems, 2. recursively solve each problem, 3. appropriately combine their answers.
Divide-Conquer-Glue. Divide-Conquer-Glue Algorithm Strategy. Skyline Problem as an Example of Divide-Conquer-Glue
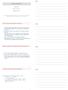 Divide-Conquer-Glue Tyler Moore CSE 3353, SMU, Dallas, TX February 19, 2013 Portions of these slides have been adapted from the slides written by Prof. Steven Skiena at SUNY Stony Brook, author of Algorithm
Divide-Conquer-Glue Tyler Moore CSE 3353, SMU, Dallas, TX February 19, 2013 Portions of these slides have been adapted from the slides written by Prof. Steven Skiena at SUNY Stony Brook, author of Algorithm
COMP 382: Reasoning about algorithms
 Fall 2014 Unit 4: Basics of complexity analysis Correctness and efficiency So far, we have talked about correctness and termination of algorithms What about efficiency? Running time of an algorithm For
Fall 2014 Unit 4: Basics of complexity analysis Correctness and efficiency So far, we have talked about correctness and termination of algorithms What about efficiency? Running time of an algorithm For
CSE 421, Spring 2017, W.L.Ruzzo. 8. Average-Case Analysis of Algorithms + Randomized Algorithms
 CSE 421, Spring 2017, W.L.Ruzzo 8. Average-Case Analysis of Algorithms + Randomized Algorithms 1 outline and goals 1) Probability tools you've seen allow formal definition of "average case" running time
CSE 421, Spring 2017, W.L.Ruzzo 8. Average-Case Analysis of Algorithms + Randomized Algorithms 1 outline and goals 1) Probability tools you've seen allow formal definition of "average case" running time
CS173 Lecture B, November 3, 2015
 CS173 Lecture B, November 3, 2015 Tandy Warnow November 3, 2015 CS 173, Lecture B November 3, 2015 Tandy Warnow Announcements Examlet 7 is a take-home exam, and is due November 10, 11:05 AM, in class.
CS173 Lecture B, November 3, 2015 Tandy Warnow November 3, 2015 CS 173, Lecture B November 3, 2015 Tandy Warnow Announcements Examlet 7 is a take-home exam, and is due November 10, 11:05 AM, in class.
Outline. 1 Introduction. 3 Quicksort. 4 Analysis. 5 References. Idea. 1 Choose an element x and reorder the array as follows:
 Outline Computer Science 331 Quicksort Mike Jacobson Department of Computer Science University of Calgary Lecture #28 1 Introduction 2 Randomized 3 Quicksort Deterministic Quicksort Randomized Quicksort
Outline Computer Science 331 Quicksort Mike Jacobson Department of Computer Science University of Calgary Lecture #28 1 Introduction 2 Randomized 3 Quicksort Deterministic Quicksort Randomized Quicksort
Divide and Conquer Algorithms
 Divide and Conquer Algorithms T. M. Murali February 19, 2013 Divide and Conquer Break up a problem into several parts. Solve each part recursively. Solve base cases by brute force. Efficiently combine
Divide and Conquer Algorithms T. M. Murali February 19, 2013 Divide and Conquer Break up a problem into several parts. Solve each part recursively. Solve base cases by brute force. Efficiently combine
CSE 312, Winter 2011, W.L.Ruzzo. 8. Average-Case Analysis of Algorithms + Randomized Algorithms
 CSE 312, Winter 2011, W.L.Ruzzo 8. Average-Case Analysis of Algorithms + Randomized Algorithms 1 insertion sort Array A[1]..A[n] for i = 1..n-1 { T = A[i] Sorted j swap j = i-1 compare while j >= 0 &&
CSE 312, Winter 2011, W.L.Ruzzo 8. Average-Case Analysis of Algorithms + Randomized Algorithms 1 insertion sort Array A[1]..A[n] for i = 1..n-1 { T = A[i] Sorted j swap j = i-1 compare while j >= 0 &&
1 Divide and Conquer (September 3)
 The control of a large force is the same principle as the control of a few men: it is merely a question of dividing up their numbers. Sun Zi, The Art of War (c. 400 C.E.), translated by Lionel Giles (1910)
The control of a large force is the same principle as the control of a few men: it is merely a question of dividing up their numbers. Sun Zi, The Art of War (c. 400 C.E.), translated by Lionel Giles (1910)
Algorithms, CSE, OSU Quicksort. Instructor: Anastasios Sidiropoulos
 6331 - Algorithms, CSE, OSU Quicksort Instructor: Anastasios Sidiropoulos Sorting Given an array of integers A[1... n], rearrange its elements so that A[1] A[2]... A[n]. Quicksort Quicksort(A, p, r) if
6331 - Algorithms, CSE, OSU Quicksort Instructor: Anastasios Sidiropoulos Sorting Given an array of integers A[1... n], rearrange its elements so that A[1] A[2]... A[n]. Quicksort Quicksort(A, p, r) if
An analogy from Calculus: limits
 COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
CSE 4502/5717: Big Data Analytics
 CSE 4502/5717: Big Data Analytics otes by Anthony Hershberger Lecture 4 - January, 31st, 2018 1 Problem of Sorting A known lower bound for sorting is Ω is the input size; M is the core memory size; and
CSE 4502/5717: Big Data Analytics otes by Anthony Hershberger Lecture 4 - January, 31st, 2018 1 Problem of Sorting A known lower bound for sorting is Ω is the input size; M is the core memory size; and
Asymptotic Algorithm Analysis & Sorting
 Asymptotic Algorithm Analysis & Sorting (Version of 5th March 2010) (Based on original slides by John Hamer and Yves Deville) We can analyse an algorithm without needing to run it, and in so doing we can
Asymptotic Algorithm Analysis & Sorting (Version of 5th March 2010) (Based on original slides by John Hamer and Yves Deville) We can analyse an algorithm without needing to run it, and in so doing we can
CSCI 3110 Assignment 6 Solutions
 CSCI 3110 Assignment 6 Solutions December 5, 2012 2.4 (4 pts) Suppose you are choosing between the following three algorithms: 1. Algorithm A solves problems by dividing them into five subproblems of half
CSCI 3110 Assignment 6 Solutions December 5, 2012 2.4 (4 pts) Suppose you are choosing between the following three algorithms: 1. Algorithm A solves problems by dividing them into five subproblems of half
Divide and Conquer. Maximum/minimum. Median finding. CS125 Lecture 4 Fall 2016
 CS125 Lecture 4 Fall 2016 Divide and Conquer We have seen one general paradigm for finding algorithms: the greedy approach. We now consider another general paradigm, known as divide and conquer. We have
CS125 Lecture 4 Fall 2016 Divide and Conquer We have seen one general paradigm for finding algorithms: the greedy approach. We now consider another general paradigm, known as divide and conquer. We have
Find an Element x in an Unsorted Array
 Find an Element x in an Unsorted Array What if we try to find a lower bound for the case where the array is not necessarily sorted? J.-L. De Carufel (U. of O.) Design & Analysis of Algorithms Fall 2017
Find an Element x in an Unsorted Array What if we try to find a lower bound for the case where the array is not necessarily sorted? J.-L. De Carufel (U. of O.) Design & Analysis of Algorithms Fall 2017
Sorting. Chapter 11. CSE 2011 Prof. J. Elder Last Updated: :11 AM
 Sorting Chapter 11-1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
Sorting Chapter 11-1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
Design and Analysis of Algorithms
 CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 4: Divide and Conquer (I) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ Divide and Conquer ( DQ ) First paradigm or framework DQ(S)
CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 4: Divide and Conquer (I) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ Divide and Conquer ( DQ ) First paradigm or framework DQ(S)
CS161: Algorithm Design and Analysis Recitation Section 3 Stanford University Week of 29 January, Problem 3-1.
 CS161: Algorithm Design and Analysis Recitation Section 3 Stanford University Week of 29 January, 2018 Problem 3-1. (Quicksort Median-of-3 Partition) One way to improve the randomized quicksort procedure
CS161: Algorithm Design and Analysis Recitation Section 3 Stanford University Week of 29 January, 2018 Problem 3-1. (Quicksort Median-of-3 Partition) One way to improve the randomized quicksort procedure
Data Structures and Algorithm Analysis (CSC317) Randomized Algorithms (part 3)
 Data Structures and Algorithm Analysis (CSC317) Randomized Algorithms (part 3) Quicksort p r Quicksort(A, p, r) 1. If p
Data Structures and Algorithm Analysis (CSC317) Randomized Algorithms (part 3) Quicksort p r Quicksort(A, p, r) 1. If p
Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts)
![Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts) Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts)](/thumbs/87/95581149.jpg) Introduction to Algorithms October 13, 2010 Massachusetts Institute of Technology 6.006 Fall 2010 Professors Konstantinos Daskalakis and Patrick Jaillet Quiz 1 Solutions Quiz 1 Solutions Problem 1. We
Introduction to Algorithms October 13, 2010 Massachusetts Institute of Technology 6.006 Fall 2010 Professors Konstantinos Daskalakis and Patrick Jaillet Quiz 1 Solutions Quiz 1 Solutions Problem 1. We
Divide and Conquer Algorithms
 Divide and Conquer Algorithms T. M. Murali March 17, 2014 Divide and Conquer Break up a problem into several parts. Solve each part recursively. Solve base cases by brute force. Efficiently combine solutions
Divide and Conquer Algorithms T. M. Murali March 17, 2014 Divide and Conquer Break up a problem into several parts. Solve each part recursively. Solve base cases by brute force. Efficiently combine solutions
Introduction to Randomized Algorithms: Quick Sort and Quick Selection
 Chapter 14 Introduction to Randomized Algorithms: Quick Sort and Quick Selection CS 473: Fundamental Algorithms, Spring 2011 March 10, 2011 14.1 Introduction to Randomized Algorithms 14.2 Introduction
Chapter 14 Introduction to Randomized Algorithms: Quick Sort and Quick Selection CS 473: Fundamental Algorithms, Spring 2011 March 10, 2011 14.1 Introduction to Randomized Algorithms 14.2 Introduction
Multidimensional Divide and Conquer 1 Skylines
 Yufei Tao ITEE University of Queensland The next few lectures will be dedicated to an important technique: divide and conquer. You may have encountered the technique in an earlier algorithm course, but
Yufei Tao ITEE University of Queensland The next few lectures will be dedicated to an important technique: divide and conquer. You may have encountered the technique in an earlier algorithm course, but
1 Closest Pair of Points on the Plane
 CS 31: Algorithms (Spring 2019): Lecture 5 Date: 4th April, 2019 Topic: Divide and Conquer 3: Closest Pair of Points on a Plane Disclaimer: These notes have not gone through scrutiny and in all probability
CS 31: Algorithms (Spring 2019): Lecture 5 Date: 4th April, 2019 Topic: Divide and Conquer 3: Closest Pair of Points on a Plane Disclaimer: These notes have not gone through scrutiny and in all probability
MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3
 MA008 p.1/37 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/37 Exercise 1 (from LN 2) Asymptotic Notation When constants appear in exponents
MA008 p.1/37 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/37 Exercise 1 (from LN 2) Asymptotic Notation When constants appear in exponents
Data Structures and Algorithms CSE 465
 Data Structures and Algorithms CSE 465 LECTURE 3 Asymptotic Notation O-, Ω-, Θ-, o-, ω-notation Divide and Conquer Merge Sort Binary Search Sofya Raskhodnikova and Adam Smith /5/0 Review Questions If input
Data Structures and Algorithms CSE 465 LECTURE 3 Asymptotic Notation O-, Ω-, Θ-, o-, ω-notation Divide and Conquer Merge Sort Binary Search Sofya Raskhodnikova and Adam Smith /5/0 Review Questions If input
Divide and Conquer CPE 349. Theresa Migler-VonDollen
 Divide and Conquer CPE 349 Theresa Migler-VonDollen Divide and Conquer Divide and Conquer is a strategy that solves a problem by: 1 Breaking the problem into subproblems that are themselves smaller instances
Divide and Conquer CPE 349 Theresa Migler-VonDollen Divide and Conquer Divide and Conquer is a strategy that solves a problem by: 1 Breaking the problem into subproblems that are themselves smaller instances
Problem Set 1. CSE 373 Spring Out: February 9, 2016
 Problem Set 1 CSE 373 Spring 2016 Out: February 9, 2016 1 Big-O Notation Prove each of the following using the definition of big-o notation (find constants c and n 0 such that f(n) c g(n) for n > n o.
Problem Set 1 CSE 373 Spring 2016 Out: February 9, 2016 1 Big-O Notation Prove each of the following using the definition of big-o notation (find constants c and n 0 such that f(n) c g(n) for n > n o.
ITEC2620 Introduction to Data Structures
 ITEC2620 Introduction to Data Structures Lecture 6a Complexity Analysis Recursive Algorithms Complexity Analysis Determine how the processing time of an algorithm grows with input size What if the algorithm
ITEC2620 Introduction to Data Structures Lecture 6a Complexity Analysis Recursive Algorithms Complexity Analysis Determine how the processing time of an algorithm grows with input size What if the algorithm
Algorithms, Design and Analysis. Order of growth. Table 2.1. Big-oh. Asymptotic growth rate. Types of formulas for basic operation count
 Types of formulas for basic operation count Exact formula e.g., C(n) = n(n-1)/2 Algorithms, Design and Analysis Big-Oh analysis, Brute Force, Divide and conquer intro Formula indicating order of growth
Types of formulas for basic operation count Exact formula e.g., C(n) = n(n-1)/2 Algorithms, Design and Analysis Big-Oh analysis, Brute Force, Divide and conquer intro Formula indicating order of growth
15. LECTURE 15. I can calculate the dot product of two vectors and interpret its meaning. I can find the projection of one vector onto another one.
 5. LECTURE 5 Objectives I can calculate the dot product of two vectors and interpret its meaning. I can find the projection of one vector onto another one. In the last few lectures, we ve learned that
5. LECTURE 5 Objectives I can calculate the dot product of two vectors and interpret its meaning. I can find the projection of one vector onto another one. In the last few lectures, we ve learned that
CSCE 750, Spring 2001 Notes 2 Page 1 4 Chapter 4 Sorting ffl Reasons for studying sorting is a big deal pedagogically useful Λ the application itself
 CSCE 750, Spring 2001 Notes 2 Page 1 4 Chapter 4 Sorting ffl Reasons for studying sorting is a big deal pedagogically useful Λ the application itself is easy to understand Λ a complete analysis can often
CSCE 750, Spring 2001 Notes 2 Page 1 4 Chapter 4 Sorting ffl Reasons for studying sorting is a big deal pedagogically useful Λ the application itself is easy to understand Λ a complete analysis can often
TTIC / CMSC Algorithms. Lectures 1 and 2 + background material
 TTIC 31010 / CMSC 37000 - Algorithms Lectures 1 and 2 + background material Avrim Blum Toyota Technological Institute at Chicago January 7, 2019 ii Contents 1 Introduction to Algorithms, and the Divide
TTIC 31010 / CMSC 37000 - Algorithms Lectures 1 and 2 + background material Avrim Blum Toyota Technological Institute at Chicago January 7, 2019 ii Contents 1 Introduction to Algorithms, and the Divide
Introduction to Algorithms
 Lecture 1 Introduction to Algorithms 1.1 Overview The purpose of this lecture is to give a brief overview of the topic of Algorithms and the kind of thinking it involves: why we focus on the subjects that
Lecture 1 Introduction to Algorithms 1.1 Overview The purpose of this lecture is to give a brief overview of the topic of Algorithms and the kind of thinking it involves: why we focus on the subjects that
Today s Outline. CS 362, Lecture 4. Annihilator Method. Lookup Table. Annihilators for recurrences with non-homogeneous terms Transformations
 Today s Outline CS 362, Lecture 4 Jared Saia University of New Mexico Annihilators for recurrences with non-homogeneous terms Transformations 1 Annihilator Method Lookup Table Write down the annihilator
Today s Outline CS 362, Lecture 4 Jared Saia University of New Mexico Annihilators for recurrences with non-homogeneous terms Transformations 1 Annihilator Method Lookup Table Write down the annihilator
Fundamental Algorithms
 Chapter 2: Sorting, Winter 2018/19 1 Fundamental Algorithms Chapter 2: Sorting Jan Křetínský Winter 2018/19 Chapter 2: Sorting, Winter 2018/19 2 Part I Simple Sorts Chapter 2: Sorting, Winter 2018/19 3
Chapter 2: Sorting, Winter 2018/19 1 Fundamental Algorithms Chapter 2: Sorting Jan Křetínský Winter 2018/19 Chapter 2: Sorting, Winter 2018/19 2 Part I Simple Sorts Chapter 2: Sorting, Winter 2018/19 3
Fundamental Algorithms
 Fundamental Algorithms Chapter 2: Sorting Harald Räcke Winter 2015/16 Chapter 2: Sorting, Winter 2015/16 1 Part I Simple Sorts Chapter 2: Sorting, Winter 2015/16 2 The Sorting Problem Definition Sorting
Fundamental Algorithms Chapter 2: Sorting Harald Räcke Winter 2015/16 Chapter 2: Sorting, Winter 2015/16 1 Part I Simple Sorts Chapter 2: Sorting, Winter 2015/16 2 The Sorting Problem Definition Sorting
Solutions. Prelim 2[Solutions]
![Solutions. Prelim 2[Solutions] Solutions. Prelim 2[Solutions]](/thumbs/93/112342343.jpg) Prelim [Solutions]. Short Answer [ pts] (a) [ pts] A traversal of an expression tree produces the string + + 3. i. What kind of traversal is it? Preorder; the operator is printed before the operands. ii.
Prelim [Solutions]. Short Answer [ pts] (a) [ pts] A traversal of an expression tree produces the string + + 3. i. What kind of traversal is it? Preorder; the operator is printed before the operands. ii.
CS173 Running Time and Big-O. Tandy Warnow
 CS173 Running Time and Big-O Tandy Warnow CS 173 Running Times and Big-O analysis Tandy Warnow Today s material We will cover: Running time analysis Review of running time analysis of Bubblesort Review
CS173 Running Time and Big-O Tandy Warnow CS 173 Running Times and Big-O analysis Tandy Warnow Today s material We will cover: Running time analysis Review of running time analysis of Bubblesort Review
CS 4104 Data and Algorithm Analysis. Recurrence Relations. Modeling Recursive Function Cost. Solving Recurrences. Clifford A. Shaffer.
 Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2010,2017 by Clifford A. Shaffer Data and Algorithm Analysis Title page Data and Algorithm Analysis Clifford A. Shaffer Spring
Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2010,2017 by Clifford A. Shaffer Data and Algorithm Analysis Title page Data and Algorithm Analysis Clifford A. Shaffer Spring
Violating the normal distribution assumption. So what do you do if the data are not normal and you still need to perform a test?
 Violating the normal distribution assumption So what do you do if the data are not normal and you still need to perform a test? Remember, if your n is reasonably large, don t bother doing anything. Your
Violating the normal distribution assumption So what do you do if the data are not normal and you still need to perform a test? Remember, if your n is reasonably large, don t bother doing anything. Your
Data structures Exercise 1 solution. Question 1. Let s start by writing all the functions in big O notation:
 Data structures Exercise 1 solution Question 1 Let s start by writing all the functions in big O notation: f 1 (n) = 2017 = O(1), f 2 (n) = 2 log 2 n = O(n 2 ), f 3 (n) = 2 n = O(2 n ), f 4 (n) = 1 = O
Data structures Exercise 1 solution Question 1 Let s start by writing all the functions in big O notation: f 1 (n) = 2017 = O(1), f 2 (n) = 2 log 2 n = O(n 2 ), f 3 (n) = 2 n = O(2 n ), f 4 (n) = 1 = O
CS 4407 Algorithms Lecture 2: Iterative and Divide and Conquer Algorithms
 CS 4407 Algorithms Lecture 2: Iterative and Divide and Conquer Algorithms Prof. Gregory Provan Department of Computer Science University College Cork 1 Lecture Outline CS 4407, Algorithms Growth Functions
CS 4407 Algorithms Lecture 2: Iterative and Divide and Conquer Algorithms Prof. Gregory Provan Department of Computer Science University College Cork 1 Lecture Outline CS 4407, Algorithms Growth Functions
MIDTERM I CMPS Winter 2013 Warmuth
 test I 1 MIDTERM I CMPS 101 - Winter 2013 Warmuth With Solutions NAME: Student ID: This exam is closed book, notes, computer and cell phone. Show partial solutions to get partial credit. Make sure you
test I 1 MIDTERM I CMPS 101 - Winter 2013 Warmuth With Solutions NAME: Student ID: This exam is closed book, notes, computer and cell phone. Show partial solutions to get partial credit. Make sure you
Analysis of Algorithms - Midterm (Solutions)
 Analysis of Algorithms - Midterm (Solutions) K Subramani LCSEE, West Virginia University, Morgantown, WV {ksmani@cseewvuedu} 1 Problems 1 Recurrences: Solve the following recurrences exactly or asymototically
Analysis of Algorithms - Midterm (Solutions) K Subramani LCSEE, West Virginia University, Morgantown, WV {ksmani@cseewvuedu} 1 Problems 1 Recurrences: Solve the following recurrences exactly or asymototically
Prelim 2[Solutions] Solutions. 1. Short Answer [18 pts]
![Prelim 2[Solutions] Solutions. 1. Short Answer [18 pts] Prelim 2[Solutions] Solutions. 1. Short Answer [18 pts]](/thumbs/93/113693785.jpg) Prelim [Solutions]. Short Answer [8 pts] (a) [3 pts] In a model/view/controller, Swing is likely to be part of (there may be more than one): i. the model ii. the view iii. the controller The view and the
Prelim [Solutions]. Short Answer [8 pts] (a) [3 pts] In a model/view/controller, Swing is likely to be part of (there may be more than one): i. the model ii. the view iii. the controller The view and the
1. [10 marks] Consider the following two algorithms that find the two largest elements in an array A[1..n], where n >= 2.
![1. [10 marks] Consider the following two algorithms that find the two largest elements in an array A[1..n], where n >= 2. 1. [10 marks] Consider the following two algorithms that find the two largest elements in an array A[1..n], where n >= 2.](/thumbs/73/68822500.jpg) CSC 6 H5S Homework Assignment # 1 Spring 010 Worth: 11% Due: Monday February 1 (at class) For each question, please write up detailed answers carefully. Make sure that you use notation and terminology
CSC 6 H5S Homework Assignment # 1 Spring 010 Worth: 11% Due: Monday February 1 (at class) For each question, please write up detailed answers carefully. Make sure that you use notation and terminology
CPS 616 DIVIDE-AND-CONQUER 6-1
 CPS 616 DIVIDE-AND-CONQUER 6-1 DIVIDE-AND-CONQUER Approach 1. Divide instance of problem into two or more smaller instances 2. Solve smaller instances recursively 3. Obtain solution to original (larger)
CPS 616 DIVIDE-AND-CONQUER 6-1 DIVIDE-AND-CONQUER Approach 1. Divide instance of problem into two or more smaller instances 2. Solve smaller instances recursively 3. Obtain solution to original (larger)
Exercise Sheet #1 Solutions, Computer Science, A M. Hallett, K. Smith a k n b k = n b + k. a k n b k c 1 n b k. a k n b.
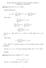 Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Math Models of OR: Branch-and-Bound
 Math Models of OR: Branch-and-Bound John E. Mitchell Department of Mathematical Sciences RPI, Troy, NY 12180 USA November 2018 Mitchell Branch-and-Bound 1 / 15 Branch-and-Bound Outline 1 Branch-and-Bound
Math Models of OR: Branch-and-Bound John E. Mitchell Department of Mathematical Sciences RPI, Troy, NY 12180 USA November 2018 Mitchell Branch-and-Bound 1 / 15 Branch-and-Bound Outline 1 Branch-and-Bound
Limitations of Algorithm Power
 Limitations of Algorithm Power Objectives We now move into the third and final major theme for this course. 1. Tools for analyzing algorithms. 2. Design strategies for designing algorithms. 3. Identifying
Limitations of Algorithm Power Objectives We now move into the third and final major theme for this course. 1. Tools for analyzing algorithms. 2. Design strategies for designing algorithms. 3. Identifying
(Refer Slide Time: 0:21)
 Theory of Computation Prof. Somenath Biswas Department of Computer Science and Engineering Indian Institute of Technology Kanpur Lecture 7 A generalisation of pumping lemma, Non-deterministic finite automata
Theory of Computation Prof. Somenath Biswas Department of Computer Science and Engineering Indian Institute of Technology Kanpur Lecture 7 A generalisation of pumping lemma, Non-deterministic finite automata
What we have learned What is algorithm Why study algorithm The time and space efficiency of algorithm The analysis framework of time efficiency Asympt
 Lecture 3 The Analysis of Recursive Algorithm Efficiency What we have learned What is algorithm Why study algorithm The time and space efficiency of algorithm The analysis framework of time efficiency
Lecture 3 The Analysis of Recursive Algorithm Efficiency What we have learned What is algorithm Why study algorithm The time and space efficiency of algorithm The analysis framework of time efficiency
Class Note #14. In this class, we studied an algorithm for integer multiplication, which. 2 ) to θ(n
 Class Note #14 Date: 03/01/2006 [Overall Information] In this class, we studied an algorithm for integer multiplication, which improved the running time from θ(n 2 ) to θ(n 1.59 ). We then used some of
Class Note #14 Date: 03/01/2006 [Overall Information] In this class, we studied an algorithm for integer multiplication, which improved the running time from θ(n 2 ) to θ(n 1.59 ). We then used some of
