Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018
|
|
|
- Milton Ward
- 5 years ago
- Views:
Transcription
1 CS17 Integrated Introduction to Computer Science Klein Contents Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, Tree definitions 1 2 Analysis of mergesort using a binary tree 1 3 Analysis of mergesort using induction 2 4 The importance of O(n log n) 4 5 Returning to analysis of recurrence relation 4 6 Lower bound on comparison sorting 5 1 Tree definitions Depth of node Is 1 Internal nodes v Depth of node Is 1 Internal nodes v Subtree (consists of descendants of v) Depth of node Is 1 Internal nodes v Subtree (consists of descendants of v) Leaf Leaf Leaf Leaf Depth of tree is 3 Depth of tree is 3 Depth of node is 3 Depth of node is 3... Let s begin by reviewing some tree terminology. Here are some terms Leaf Leaf Subtree Depth of tree is 3 Depth of node is 3... ˆ node: an entity in a tree that contains a value or data ˆ edge: branches that connect one node to another ˆ : the topmost node in the tree ˆ leaves: nodes that do not have child nodes ˆ internal node: any node of a tree that has child nodes (any nodes that are not leaves) ˆ children: nodes that have parent nodes (all nodes are children except for the node) ˆ parents: nodes that have at least one edge to a child node
2 ˆ depth: depth of a node is the length of the path to its ˆ arity: maximum number of children (binary tree has arity two) 2 Analysis of mergesort using a binary tree Sometimes we consider the order of children significant. This is the case of binary trees, which come up all the time in computer science. A nonempty binary tree has a, and possibly a left subtree and possibly a right subtree. In lab you saw one use for binary trees. Here we use binary trees to help us analyze mergesort. As we went over briefly in last lecture, consider the tree representing the invocations resulting from an initial call to mergesort with a list of n numbers. The represents the initial call. That initial call makes two recursive calls, one with the first half of the list (represented by the left child) and one with the second half of the list (represented by the right child). The recursions continue similarly, until you get to calls for lists of size one or zero. At each depth d, for each item in the original input list, there is at most one invocation at that depth that handles that item. Therefore, for any depth d, the sum over the invocations of depth d of the number of items handled is at most n. In each invocation, the number of operations (aside from recursive invocations) is proportional to the number of items in the input list. Therefore, for each depth d, the total number of operations done by invocations at depth d is at most cn where c is a constant and n is the size of the original input. Therefore the total number of operations is at most cn times the depth of the tree. How large is the depth of the tree? Every time you go from parent to child, the number of items in the input list goes down by a factor of two (the number of items that you are dealing with is halved). This means that in order to find our maximum depth, we must ask How many times can you divide n by two before it gets down to 1 or less This is the same as asking the question: how many 2 s do you have to multiply together before the product is n or greater? That is, what is the smallest integer x such that 2 x n? The inverse of the function that maps x to 2 x is the function that maps y to log 2 y. x x y log 2 y These functions also take real numbers, e.g = and log = Starting with the equation 2 x = n, we take logs of both sides, and we get x = log 2 n. Now log 2 n is 2
3 not necessarily an integer, so the depth of the tree is log 2 n. This shows that the total number of operations is at most cn log 2 n. Therefore we say that mergesort is O(n log 2 n). 3 Analysis of mergesort using induction Now that we have an idea of what the running time should be, we can use a recurrence relation and induction to prove it. Let s use the following recurrence relation. It s a little sketchy but we ll come back to that. Let f(n) be the worst-case number of operations done by mergesort on a list of length n. Aside from the recursive calls, the number of operations done by mergesort is O(n). That is, there are positive constants n 0 and c such that, for n n 0, the number of operations is at most cn (again, not counting recursive calls.) f(n) a for n n 0 f(n) cn + f(n/2) + f(n/2) for n n 0 Note that f(n/2) occurs twice on the right-hand side because there are two recursive calls. That seems good. Anything wrong with this recurrence relation? What if n is an odd number? Then the recurrence relation is not quite right. So for now let s only state it for even n: f(n) a for n n 0 f(n) cn + f(n/2) + f(n/2) for even n > n 0 To simplify, set b = max{a, c}. That way, if n > 1 and n n 0, a bn, so we can state the recurrence as: f(n) a for n 1 f(n) cn + f(n/2) + f(n/2) for even n > 1 The fact tht we only state the recurrence for even n limits what we can prove using induction. We need all the list sizes in all recursive calls to be either even or 1. This means we can only prove something using this recurrence for values of n that are powers of 2, i.e. numbers of the form 2 k where k is a nonnegative integer. Claim: For n a power of two, f(n) an + b n log 2 n. 3
4 Proof: By induction on n. For n 1, f(n) a. In this case, the right-hand side of the claimed inequality is a, so the claim holds. For n 2, f(n) bn + 2f(n/2) by recurrence bn + 2 (a (n/2) + b (n/2) log 2 (n/2)) by inductive hypothesis bn + 2 (a (n/2) + b (n/2)(log 2 n 1)) because log 2 (n/2) = log 2 n 1 bn + a n + b n(log 2 n 1)by multiplying through bn + an + bn log 2 n bn an + bn log 2 n This completes the induction step and the proof. QED. What about sorting when the number n of items is not a power of two? Two approaches to this: ˆ Can show that the worst-case running time for input size n is no more than the worst-case running time for larger inputs, and for any positive integer n, there is a power of two 2 k n such that 2 k 2n. Therefore, the running time for for arbitrary n is no more than a (2n) + b (2n) log 2 (2n). ˆ One can get a better recurrence for mergesort, one that does not depend on n being even. Then can analyze that recurrence. I will show this in a little bit. 4 The importance of O(n log n) For some of the most important algorithmic problems, we don t have a good way to achieve lineartime algorithms but we do know of O(n log n) algorithms. That extra factor of log n is not negligible but it is not very big. When you go from an O(n 2 ) algorithm to an O(n log n) algorithm, it is tremendous. One example (which we will not do in this class but which you can study in Algorithms class (and sometimes in Coding the Matrix) is the Fast Fourier Transform (FFT). This is an O(n log n) algorithm for something that you would think would require O(n 2 ). This algorithm is core to the whole field of digital signal processing. It comes up in GPS. It comes up in image analysis. It even comes up in Bignum multiplication: it is used in an O(n log n) algorithm for multiplication of n-digit numbers. 5 Returning to analysis of recurrence relation Referring back to our code for mergesort, you can give a recurrence relation that works for odd numbers. The two recursive calls are: 4
5 ˆ (mergesort (take (quotient (length L) 2))) ˆ (mergesort (drop (quotient (length L) 2))) The first call is on a list of length n/2 and the second is on a list of length n n/2. Here x is the greatest integer less than or equal to x: 17.5 = 17 and 17 = 17. Note that n n/2 = n/2. So we get a recurrence relation f(n) a for n 1 f(n) bn + f( n/2 ) + f(n n/2 ) Claim: For any n 1, f(n) an + b n log 3/2 n. Proof: By induction on n. For n 1, f(n) a. In this case, the right-hand side of the claimed inequality is a, so the claim holds. For n 2, f(n) bn + f( n/2 ) + f(n n/2 ) by recurrence ( ) bn + a ( n/2 ) + b ( n/2 ) log 3/2 n/2 + ( ) a (n n/2 ) + b (n n/2 ) log 3/2 (n n/2 ) by inductive hypothesis For n = 2, n/2 = n/2. For n 3, n/2 (n 1)/2 1 3 n. Therefore n n/2 2 3n. Therefore 2 log 3/2 (n n/2 ) log 3/2 3 n log 3/2 n 1. Of course, n/2 n/2 2 3 n so also log 3/2 n/2 log 3/2 n 1. Using these, and continuing with the sequence of inequalities, we get ( ) ( ) f(n) bn + a ( n/2 ) + b ( n/2 ) log 3/2 n/2 + a (n n/2 ) + b (n n/2 ) log 3/2 (n n/2 ) ( ) ( ) bn + a ( n/2 ) + b ( n/2 )(log 3/2 n 1) + a (n n/2 ) + b (n n/2 )(log 3/2 n 1) bn + a ( n/2 + n n/2 ) + b ( n/2 + n n/2 )(log 3/2 n 1) bn + a n + b n(log 3/2 n 1) bn + an + bn log 3/2 n bn an + bn log 3/2 n This completes the induction step and the proof. QED. 6 Lower bound on comparison sorting How fast can we expect to sort things? To answer that question, we will think about an algorithm in a different way. We use the idea of ed trees. Rooted trees come up all the time in computer science, so you need to learn about them. We will use them in three completely different ways in the coming lectures. 5
6 Idea: Consider a given value of n. For the purpose of analysis, we represent the algorithm by a decision tree. This is a binary ed tree (a tree where every node has at most two children). Each internal node represents a comparison between two input items. Each represents a conclusion the algorithm makes about the order of the input items. I ll give an example of a decision tree. Suppose a sorting algorithm is given the list with numbers a, b, c. At the end, the algorithm has to produce an ordered list. To do so, it must discover the ordering among the input items. It discovers that ordering by comparing pairs of items. a < b? b < c? a < c? a < b < c a < c? b < a < c b < c? a < c < b c < a < b b < c < a c < b < a Try out this algorithm. Let s say a = 25, b = 15, c = 7. For any given input, the algorithm must start at the and make its way to a. Every internal node represents a comparison that the algorithm makes. Because each comparison takes at least one operation, the number of operations on a given input is the number of internal nodes on a -to- path. For any given, the number of comparisons is then the depth of that. The worst-case number of comparisons is the maximum depth. For every value of n, you need a separate decision tree. The number of leaves is the number of orderings of n numbers, which is n! (n factorial). For any algorithm that sorts items by comparing them, for every value of n, there is a decision tree that mimics the algorithm s behavior on inputs of size n. Here s a fact about binary trees: Lemma Every binary tree of depth d has at most 2 d leaves. Proof By induction on d. Base case: Any binary tree of depth 0 has only one. Induction Step: Assume it for d = k 1, and prove it for d = k. Induction hypothesis: Assume that every binary tree of depth k 1 has at most 2 k 1 leaves. Let T be any tree of depth k where k > 0. It consists of a and some internal nodes... 6
7 The descendants of the left child form a left subtree and the descendants of the right child form a right subtree. The left subtree is a ed tree of depth k 1 so it has at most 2 k 1 leaves. The right subtree is a ed tree of depth k 1 so it has at most 2 k 1 leaves. The total number of leaves is just the number of leaves in the two subtrees, which is at most 2 k k 1, which is 2 2 k 1, which is 2 k. This proves the induction step, completing the proof. QED For example, a binary tree with 6 leaves cannot have depth 2 because 2 2 is less than 6. It must have depth at least three (and our decision tree for sorting three numbers has depth three). Suppose we want to sort 4 numbers. There are different outcomes, so any decision tree for this has this many leaves. It s 24, so any decision tree with this many leaves has depth at least 5 because 2 4 < 24. In general, for any positive integer n, when sorting n numbers, there are n! possible results, so a decision tree for sorting n numbers has n! leaves. This can tell us how big the depth must be. Let the depth be d. Then we must have 2 d n!. Stirling s Approximation tells us that n! is at least How do we find out how large d must be? (n/e) n The function log 2 y is monotonically increasing (higher y means higher log 2 y). That means we can start with an inequality and take logs of both sides, and we get another inequality. We have Take logs of both sides: which is 2 d n! (n/e) n log 2 (2 d ) log 2 ((n/e) n ) d n log 2 (n/e) = n(log 2 n log 2 e) = n log 2 n n log 2 e This shows that the depth must be at least n log 2 n n log 2 e, which is at least 1 2 n log 2 n for n > 7. 7
8 This shows that any sorting algorithm that makes order decisions based on comparing pairs of numbers has a running time that is Ω(n log 2 n). After lecture, a student in class, David Gao, pointed out that you don t really need Stirling s approximation to prove that log 2 n! is Ω(n log n). Here s an outline: For n 6, log 2 n! = log 2 (n (n 1) (n 2) ( n/2 ) ( n/2 1) 3 2 1) = log 2 n + log 2 (n 1) + log 2 (n 2) + + log( n/2 ) + log( n/2 1) + + log 3 + log 2 + log 1 log 2 n + log 2 (n 1) + log 2 (n 2) + + log( n/2 ) log( n/2 ) }{{} (n n/2 +1times (n/2) log( 1 3 n) (n/2)(log n log 3) (n/2)(log n 1.585) (n/2) 2 3 log n 1 3 n log n which shows that log n! is Ω(n log n). Can this running time be beaten? Is there a linear-time sorting algorithm? Remember, we assumed that the only way the algorithm knows about the numbers is by comparing them in pairs. There is an algorithm that beats this running time by doing things differently. Please let us know if you find any mistakes, inconsistencies, or confusing language in this or any other CS 17 document by filling out the anonymous feedback form: courses/csci0170/feedback. 8
Asymptotic Analysis and Recurrences
 Appendix A Asymptotic Analysis and Recurrences A.1 Overview We discuss the notion of asymptotic analysis and introduce O, Ω, Θ, and o notation. We then turn to the topic of recurrences, discussing several
Appendix A Asymptotic Analysis and Recurrences A.1 Overview We discuss the notion of asymptotic analysis and introduce O, Ω, Θ, and o notation. We then turn to the topic of recurrences, discussing several
Data Structures and Algorithms
 Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
CS 2110: INDUCTION DISCUSSION TOPICS
 CS 110: INDUCTION DISCUSSION TOPICS The following ideas are suggestions for how to handle your discussion classes. You can do as much or as little of this as you want. You can either present at the board,
CS 110: INDUCTION DISCUSSION TOPICS The following ideas are suggestions for how to handle your discussion classes. You can do as much or as little of this as you want. You can either present at the board,
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Asymptotic Analysis, recurrences Date: 9/7/17
 601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Asymptotic Analysis, recurrences Date: 9/7/17 2.1 Notes Homework 1 will be released today, and is due a week from today by the beginning
601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Asymptotic Analysis, recurrences Date: 9/7/17 2.1 Notes Homework 1 will be released today, and is due a week from today by the beginning
CS 395T Computational Learning Theory. Scribe: Mike Halcrow. x 4. x 2. x 6
 CS 395T Computational Learning Theory Lecture 3: September 0, 2007 Lecturer: Adam Klivans Scribe: Mike Halcrow 3. Decision List Recap In the last class, we determined that, when learning a t-decision list,
CS 395T Computational Learning Theory Lecture 3: September 0, 2007 Lecturer: Adam Klivans Scribe: Mike Halcrow 3. Decision List Recap In the last class, we determined that, when learning a t-decision list,
Methods for solving recurrences
 Methods for solving recurrences Analyzing the complexity of mergesort The merge function Consider the following implementation: 1 int merge ( int v1, int n1, int v, int n ) { 3 int r = malloc ( ( n1+n
Methods for solving recurrences Analyzing the complexity of mergesort The merge function Consider the following implementation: 1 int merge ( int v1, int n1, int v, int n ) { 3 int r = malloc ( ( n1+n
Selection and Adversary Arguments. COMP 215 Lecture 19
 Selection and Adversary Arguments COMP 215 Lecture 19 Selection Problems We want to find the k'th largest entry in an unsorted array. Could be the largest, smallest, median, etc. Ideas for an n lg n algorithm?
Selection and Adversary Arguments COMP 215 Lecture 19 Selection Problems We want to find the k'th largest entry in an unsorted array. Could be the largest, smallest, median, etc. Ideas for an n lg n algorithm?
5 + 9(10) + 3(100) + 0(1000) + 2(10000) =
 Chapter 5 Analyzing Algorithms So far we have been proving statements about databases, mathematics and arithmetic, or sequences of numbers. Though these types of statements are common in computer science,
Chapter 5 Analyzing Algorithms So far we have been proving statements about databases, mathematics and arithmetic, or sequences of numbers. Though these types of statements are common in computer science,
Algorithms and Data Structures 2016 Week 5 solutions (Tues 9th - Fri 12th February)
 Algorithms and Data Structures 016 Week 5 solutions (Tues 9th - Fri 1th February) 1. Draw the decision tree (under the assumption of all-distinct inputs) Quicksort for n = 3. answer: (of course you should
Algorithms and Data Structures 016 Week 5 solutions (Tues 9th - Fri 1th February) 1. Draw the decision tree (under the assumption of all-distinct inputs) Quicksort for n = 3. answer: (of course you should
Data selection. Lower complexity bound for sorting
 Data selection. Lower complexity bound for sorting Lecturer: Georgy Gimel farb COMPSCI 220 Algorithms and Data Structures 1 / 12 1 Data selection: Quickselect 2 Lower complexity bound for sorting 3 The
Data selection. Lower complexity bound for sorting Lecturer: Georgy Gimel farb COMPSCI 220 Algorithms and Data Structures 1 / 12 1 Data selection: Quickselect 2 Lower complexity bound for sorting 3 The
Big O 2/14/13. Administrative. Does it terminate? David Kauchak cs302 Spring 2013
 /4/3 Administrative Big O David Kauchak cs3 Spring 3 l Assignment : how d it go? l Assignment : out soon l CLRS code? l Videos Insertion-sort Insertion-sort Does it terminate? /4/3 Insertion-sort Loop
/4/3 Administrative Big O David Kauchak cs3 Spring 3 l Assignment : how d it go? l Assignment : out soon l CLRS code? l Videos Insertion-sort Insertion-sort Does it terminate? /4/3 Insertion-sort Loop
Solving with Absolute Value
 Solving with Absolute Value Who knew two little lines could cause so much trouble? Ask someone to solve the equation 3x 2 = 7 and they ll say No problem! Add just two little lines, and ask them to solve
Solving with Absolute Value Who knew two little lines could cause so much trouble? Ask someone to solve the equation 3x 2 = 7 and they ll say No problem! Add just two little lines, and ask them to solve
b + O(n d ) where a 1, b > 1, then O(n d log n) if a = b d d ) if a < b d O(n log b a ) if a > b d
 CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
Quick Sort Notes , Spring 2010
 Quick Sort Notes 18.310, Spring 2010 0.1 Randomized Median Finding In a previous lecture, we discussed the problem of finding the median of a list of m elements, or more generally the element of rank m.
Quick Sort Notes 18.310, Spring 2010 0.1 Randomized Median Finding In a previous lecture, we discussed the problem of finding the median of a list of m elements, or more generally the element of rank m.
CS 4349 Lecture August 30th, 2017
 CS 4349 Lecture August 30th, 2017 Main topics for #lecture include #recurrances. Prelude I will hold an extra office hour Friday, September 1st from 3:00pm to 4:00pm. Please fill out prerequisite forms
CS 4349 Lecture August 30th, 2017 Main topics for #lecture include #recurrances. Prelude I will hold an extra office hour Friday, September 1st from 3:00pm to 4:00pm. Please fill out prerequisite forms
1 Terminology and setup
 15-451/651: Design & Analysis of Algorithms August 31, 2017 Lecture #2 last changed: August 29, 2017 In this lecture, we will examine some simple, concrete models of computation, each with a precise definition
15-451/651: Design & Analysis of Algorithms August 31, 2017 Lecture #2 last changed: August 29, 2017 In this lecture, we will examine some simple, concrete models of computation, each with a precise definition
Divide and Conquer Algorithms
 Divide and Conquer Algorithms T. M. Murali March 17, 2014 Divide and Conquer Break up a problem into several parts. Solve each part recursively. Solve base cases by brute force. Efficiently combine solutions
Divide and Conquer Algorithms T. M. Murali March 17, 2014 Divide and Conquer Break up a problem into several parts. Solve each part recursively. Solve base cases by brute force. Efficiently combine solutions
When we use asymptotic notation within an expression, the asymptotic notation is shorthand for an unspecified function satisfying the relation:
 CS 124 Section #1 Big-Oh, the Master Theorem, and MergeSort 1/29/2018 1 Big-Oh Notation 1.1 Definition Big-Oh notation is a way to describe the rate of growth of functions. In CS, we use it to describe
CS 124 Section #1 Big-Oh, the Master Theorem, and MergeSort 1/29/2018 1 Big-Oh Notation 1.1 Definition Big-Oh notation is a way to describe the rate of growth of functions. In CS, we use it to describe
When we use asymptotic notation within an expression, the asymptotic notation is shorthand for an unspecified function satisfying the relation:
 CS 124 Section #1 Big-Oh, the Master Theorem, and MergeSort 1/29/2018 1 Big-Oh Notation 1.1 Definition Big-Oh notation is a way to describe the rate of growth of functions. In CS, we use it to describe
CS 124 Section #1 Big-Oh, the Master Theorem, and MergeSort 1/29/2018 1 Big-Oh Notation 1.1 Definition Big-Oh notation is a way to describe the rate of growth of functions. In CS, we use it to describe
Design and Analysis of Algorithms
 CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 4: Divide and Conquer (I) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ Divide and Conquer ( DQ ) First paradigm or framework DQ(S)
CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 4: Divide and Conquer (I) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ Divide and Conquer ( DQ ) First paradigm or framework DQ(S)
CS1800: Mathematical Induction. Professor Kevin Gold
 CS1800: Mathematical Induction Professor Kevin Gold Induction: Used to Prove Patterns Just Keep Going For an algorithm, we may want to prove that it just keeps working, no matter how big the input size
CS1800: Mathematical Induction Professor Kevin Gold Induction: Used to Prove Patterns Just Keep Going For an algorithm, we may want to prove that it just keeps working, no matter how big the input size
Divide and Conquer. Recurrence Relations
 Divide and Conquer Recurrence Relations Divide-and-Conquer Strategy: Break up problem into parts. Solve each part recursively. Combine solutions to sub-problems into overall solution. 2 MergeSort Mergesort.
Divide and Conquer Recurrence Relations Divide-and-Conquer Strategy: Break up problem into parts. Solve each part recursively. Combine solutions to sub-problems into overall solution. 2 MergeSort Mergesort.
Proof Techniques (Review of Math 271)
 Chapter 2 Proof Techniques (Review of Math 271) 2.1 Overview This chapter reviews proof techniques that were probably introduced in Math 271 and that may also have been used in a different way in Phil
Chapter 2 Proof Techniques (Review of Math 271) 2.1 Overview This chapter reviews proof techniques that were probably introduced in Math 271 and that may also have been used in a different way in Phil
Concrete models and tight upper/lower bounds
 Lecture 3 Concrete models and tight upper/lower bounds 3.1 Overview In this lecture, we will examine some simple, concrete models of computation, each with a precise definition of what counts as a step,
Lecture 3 Concrete models and tight upper/lower bounds 3.1 Overview In this lecture, we will examine some simple, concrete models of computation, each with a precise definition of what counts as a step,
CSC236 Week 3. Larry Zhang
 CSC236 Week 3 Larry Zhang 1 Announcements Problem Set 1 due this Friday Make sure to read Submission Instructions on the course web page. Search for Teammates on Piazza Educational memes: http://www.cs.toronto.edu/~ylzhang/csc236/memes.html
CSC236 Week 3 Larry Zhang 1 Announcements Problem Set 1 due this Friday Make sure to read Submission Instructions on the course web page. Search for Teammates on Piazza Educational memes: http://www.cs.toronto.edu/~ylzhang/csc236/memes.html
1 Closest Pair of Points on the Plane
 CS 31: Algorithms (Spring 2019): Lecture 5 Date: 4th April, 2019 Topic: Divide and Conquer 3: Closest Pair of Points on a Plane Disclaimer: These notes have not gone through scrutiny and in all probability
CS 31: Algorithms (Spring 2019): Lecture 5 Date: 4th April, 2019 Topic: Divide and Conquer 3: Closest Pair of Points on a Plane Disclaimer: These notes have not gone through scrutiny and in all probability
Divide and Conquer Algorithms
 Divide and Conquer Algorithms T. M. Murali February 19, 2013 Divide and Conquer Break up a problem into several parts. Solve each part recursively. Solve base cases by brute force. Efficiently combine
Divide and Conquer Algorithms T. M. Murali February 19, 2013 Divide and Conquer Break up a problem into several parts. Solve each part recursively. Solve base cases by brute force. Efficiently combine
An analogy from Calculus: limits
 COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
CSE 4502/5717: Big Data Analytics
 CSE 4502/5717: Big Data Analytics otes by Anthony Hershberger Lecture 4 - January, 31st, 2018 1 Problem of Sorting A known lower bound for sorting is Ω is the input size; M is the core memory size; and
CSE 4502/5717: Big Data Analytics otes by Anthony Hershberger Lecture 4 - January, 31st, 2018 1 Problem of Sorting A known lower bound for sorting is Ω is the input size; M is the core memory size; and
CS 577 Introduction to Algorithms: Strassen s Algorithm and the Master Theorem
 CS 577 Introduction to Algorithms: Jin-Yi Cai University of Wisconsin Madison In the last class, we described InsertionSort and showed that its worst-case running time is Θ(n 2 ). Check Figure 2.2 for
CS 577 Introduction to Algorithms: Jin-Yi Cai University of Wisconsin Madison In the last class, we described InsertionSort and showed that its worst-case running time is Θ(n 2 ). Check Figure 2.2 for
Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts)
![Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts) Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts)](/thumbs/87/95581149.jpg) Introduction to Algorithms October 13, 2010 Massachusetts Institute of Technology 6.006 Fall 2010 Professors Konstantinos Daskalakis and Patrick Jaillet Quiz 1 Solutions Quiz 1 Solutions Problem 1. We
Introduction to Algorithms October 13, 2010 Massachusetts Institute of Technology 6.006 Fall 2010 Professors Konstantinos Daskalakis and Patrick Jaillet Quiz 1 Solutions Quiz 1 Solutions Problem 1. We
CS Data Structures and Algorithm Analysis
 CS 483 - Data Structures and Algorithm Analysis Lecture II: Chapter 2 R. Paul Wiegand George Mason University, Department of Computer Science February 1, 2006 Outline 1 Analysis Framework 2 Asymptotic
CS 483 - Data Structures and Algorithm Analysis Lecture II: Chapter 2 R. Paul Wiegand George Mason University, Department of Computer Science February 1, 2006 Outline 1 Analysis Framework 2 Asymptotic
Notes on induction proofs and recursive definitions
 Notes on induction proofs and recursive definitions James Aspnes December 13, 2010 1 Simple induction Most of the proof techniques we ve talked about so far are only really useful for proving a property
Notes on induction proofs and recursive definitions James Aspnes December 13, 2010 1 Simple induction Most of the proof techniques we ve talked about so far are only really useful for proving a property
Problem 5. Use mathematical induction to show that when n is an exact power of two, the solution of the recurrence
 A. V. Gerbessiotis CS 610-102 Spring 2014 PS 1 Jan 27, 2014 No points For the remainder of the course Give an algorithm means: describe an algorithm, show that it works as claimed, analyze its worst-case
A. V. Gerbessiotis CS 610-102 Spring 2014 PS 1 Jan 27, 2014 No points For the remainder of the course Give an algorithm means: describe an algorithm, show that it works as claimed, analyze its worst-case
CS361 Homework #3 Solutions
 CS6 Homework # Solutions. Suppose I have a hash table with 5 locations. I would like to know how many items I can store in it before it becomes fairly likely that I have a collision, i.e., that two items
CS6 Homework # Solutions. Suppose I have a hash table with 5 locations. I would like to know how many items I can store in it before it becomes fairly likely that I have a collision, i.e., that two items
UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis
![UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis](/thumbs/89/98802725.jpg) UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis Lecture 14 Class URL: http://vlsicad.ucsd.edu/courses/cse21-s14/ Lecture 14 Notes Goals for this week Big-O complexity
UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis Lecture 14 Class URL: http://vlsicad.ucsd.edu/courses/cse21-s14/ Lecture 14 Notes Goals for this week Big-O complexity
V. Adamchik 1. Recurrences. Victor Adamchik Fall of 2005
 V. Adamchi Recurrences Victor Adamchi Fall of 00 Plan Multiple roots. More on multiple roots. Inhomogeneous equations 3. Divide-and-conquer recurrences In the previous lecture we have showed that if the
V. Adamchi Recurrences Victor Adamchi Fall of 00 Plan Multiple roots. More on multiple roots. Inhomogeneous equations 3. Divide-and-conquer recurrences In the previous lecture we have showed that if the
N/4 + N/2 + N = 2N 2.
 CS61B Summer 2006 Instructor: Erin Korber Lecture 24, 7 Aug. 1 Amortized Analysis For some of the data structures we ve discussed (namely hash tables and splay trees), it was claimed that the average time
CS61B Summer 2006 Instructor: Erin Korber Lecture 24, 7 Aug. 1 Amortized Analysis For some of the data structures we ve discussed (namely hash tables and splay trees), it was claimed that the average time
Quiz 3 Reminder and Midterm Results
 Quiz 3 Reminder and Midterm Results Reminder: Quiz 3 will be in the first 15 minutes of Monday s class. You can use any resources you have during the quiz. It covers all four sections of Unit 3. It has
Quiz 3 Reminder and Midterm Results Reminder: Quiz 3 will be in the first 15 minutes of Monday s class. You can use any resources you have during the quiz. It covers all four sections of Unit 3. It has
arxiv: v1 [math.co] 22 Jan 2013
![arxiv: v1 [math.co] 22 Jan 2013 arxiv: v1 [math.co] 22 Jan 2013](/thumbs/85/92098505.jpg) NESTED RECURSIONS, SIMULTANEOUS PARAMETERS AND TREE SUPERPOSITIONS ABRAHAM ISGUR, VITALY KUZNETSOV, MUSTAZEE RAHMAN, AND STEPHEN TANNY arxiv:1301.5055v1 [math.co] 22 Jan 2013 Abstract. We apply a tree-based
NESTED RECURSIONS, SIMULTANEOUS PARAMETERS AND TREE SUPERPOSITIONS ABRAHAM ISGUR, VITALY KUZNETSOV, MUSTAZEE RAHMAN, AND STEPHEN TANNY arxiv:1301.5055v1 [math.co] 22 Jan 2013 Abstract. We apply a tree-based
CS173 Running Time and Big-O. Tandy Warnow
 CS173 Running Time and Big-O Tandy Warnow CS 173 Running Times and Big-O analysis Tandy Warnow Today s material We will cover: Running time analysis Review of running time analysis of Bubblesort Review
CS173 Running Time and Big-O Tandy Warnow CS 173 Running Times and Big-O analysis Tandy Warnow Today s material We will cover: Running time analysis Review of running time analysis of Bubblesort Review
University of the Virgin Islands, St. Thomas January 14, 2015 Algorithms and Programming for High Schoolers. Lecture 5
 University of the Virgin Islands, St. Thomas January 14, 2015 Algorithms and Programming for High Schoolers Numerical algorithms: Lecture 5 Today we ll cover algorithms for various numerical problems:
University of the Virgin Islands, St. Thomas January 14, 2015 Algorithms and Programming for High Schoolers Numerical algorithms: Lecture 5 Today we ll cover algorithms for various numerical problems:
Lecture 1 : Data Compression and Entropy
 CPS290: Algorithmic Foundations of Data Science January 8, 207 Lecture : Data Compression and Entropy Lecturer: Kamesh Munagala Scribe: Kamesh Munagala In this lecture, we will study a simple model for
CPS290: Algorithmic Foundations of Data Science January 8, 207 Lecture : Data Compression and Entropy Lecturer: Kamesh Munagala Scribe: Kamesh Munagala In this lecture, we will study a simple model for
In-Class Soln 1. CS 361, Lecture 4. Today s Outline. In-Class Soln 2
 In-Class Soln 1 Let f(n) be an always positive function and let g(n) = f(n) log n. Show that f(n) = o(g(n)) CS 361, Lecture 4 Jared Saia University of New Mexico For any positive constant c, we want to
In-Class Soln 1 Let f(n) be an always positive function and let g(n) = f(n) log n. Show that f(n) = o(g(n)) CS 361, Lecture 4 Jared Saia University of New Mexico For any positive constant c, we want to
Lecture 4: Constructing the Integers, Rationals and Reals
 Math/CS 20: Intro. to Math Professor: Padraic Bartlett Lecture 4: Constructing the Integers, Rationals and Reals Week 5 UCSB 204 The Integers Normally, using the natural numbers, you can easily define
Math/CS 20: Intro. to Math Professor: Padraic Bartlett Lecture 4: Constructing the Integers, Rationals and Reals Week 5 UCSB 204 The Integers Normally, using the natural numbers, you can easily define
Induction and Recursion
 . All rights reserved. Authorized only for instructor use in the classroom. No reproduction or further distribution permitted without the prior written consent of McGraw-Hill Education. Induction and Recursion
. All rights reserved. Authorized only for instructor use in the classroom. No reproduction or further distribution permitted without the prior written consent of McGraw-Hill Education. Induction and Recursion
Chapter Summary. Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms
 1 Chapter Summary Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms 2 Section 5.1 3 Section Summary Mathematical Induction Examples of
1 Chapter Summary Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms 2 Section 5.1 3 Section Summary Mathematical Induction Examples of
Hon.Algorithms (CSCI-GA 3520), Professor Yap Fall 2012 MIDTERM EXAM. Oct 11, 2012 SOLUTION
 Hon.Algorithms (CSCI-GA 352), Professor Yap Fall 22 MIDTERM EXAM Oct, 22 SOLUTIONS Problem. ( Points) Consider the recurrence T(n) = 4T(n/2)+ n2 lgn. Reduce this to standard form and solve it to Θ-order.
Hon.Algorithms (CSCI-GA 352), Professor Yap Fall 22 MIDTERM EXAM Oct, 22 SOLUTIONS Problem. ( Points) Consider the recurrence T(n) = 4T(n/2)+ n2 lgn. Reduce this to standard form and solve it to Θ-order.
8.1 Polynomial Threshold Functions
 CS 395T Computational Learning Theory Lecture 8: September 22, 2008 Lecturer: Adam Klivans Scribe: John Wright 8.1 Polynomial Threshold Functions In the previous lecture, we proved that any function over
CS 395T Computational Learning Theory Lecture 8: September 22, 2008 Lecturer: Adam Klivans Scribe: John Wright 8.1 Polynomial Threshold Functions In the previous lecture, we proved that any function over
CS Data Structures and Algorithm Analysis
 CS 483 - Data Structures and Algorithm Analysis Lecture VII: Chapter 6, part 2 R. Paul Wiegand George Mason University, Department of Computer Science March 22, 2006 Outline 1 Balanced Trees 2 Heaps &
CS 483 - Data Structures and Algorithm Analysis Lecture VII: Chapter 6, part 2 R. Paul Wiegand George Mason University, Department of Computer Science March 22, 2006 Outline 1 Balanced Trees 2 Heaps &
CPSC 121: Models of Computation. Module 9: Proof Techniques (part 2) Mathematical Induction
 CPSC 121: Models of Computation Module 9: Proof Techniques (part 2) Mathematical Induction Module 9: Announcements Midterm #2: th Monday November 14, 2016 at 17:00 Modules 5 (from multiple quantifiers
CPSC 121: Models of Computation Module 9: Proof Techniques (part 2) Mathematical Induction Module 9: Announcements Midterm #2: th Monday November 14, 2016 at 17:00 Modules 5 (from multiple quantifiers
Algorithm Design and Analysis
 Algorithm Design and Analysis LECTURE 9 Divide and Conquer Merge sort Counting Inversions Binary Search Exponentiation Solving Recurrences Recursion Tree Method Master Theorem Sofya Raskhodnikova S. Raskhodnikova;
Algorithm Design and Analysis LECTURE 9 Divide and Conquer Merge sort Counting Inversions Binary Search Exponentiation Solving Recurrences Recursion Tree Method Master Theorem Sofya Raskhodnikova S. Raskhodnikova;
Math 324 Summer 2012 Elementary Number Theory Notes on Mathematical Induction
 Math 4 Summer 01 Elementary Number Theory Notes on Mathematical Induction Principle of Mathematical Induction Recall the following axiom for the set of integers. Well-Ordering Axiom for the Integers If
Math 4 Summer 01 Elementary Number Theory Notes on Mathematical Induction Principle of Mathematical Induction Recall the following axiom for the set of integers. Well-Ordering Axiom for the Integers If
CIS 121. Analysis of Algorithms & Computational Complexity. Slides based on materials provided by Mary Wootters (Stanford University)
 CIS 121 Analysis of Algorithms & Computational Complexity Slides based on materials provided by Mary Wootters (Stanford University) Today Sorting: InsertionSort vs MergeSort Analyzing the correctness of
CIS 121 Analysis of Algorithms & Computational Complexity Slides based on materials provided by Mary Wootters (Stanford University) Today Sorting: InsertionSort vs MergeSort Analyzing the correctness of
CS383, Algorithms Spring 2009 HW1 Solutions
 Prof. Sergio A. Alvarez http://www.cs.bc.edu/ alvarez/ 21 Campanella Way, room 569 alvarez@cs.bc.edu Computer Science Department voice: (617) 552-4333 Boston College fax: (617) 552-6790 Chestnut Hill,
Prof. Sergio A. Alvarez http://www.cs.bc.edu/ alvarez/ 21 Campanella Way, room 569 alvarez@cs.bc.edu Computer Science Department voice: (617) 552-4333 Boston College fax: (617) 552-6790 Chestnut Hill,
CS173 Strong Induction and Functions. Tandy Warnow
 CS173 Strong Induction and Functions Tandy Warnow CS 173 Introduction to Strong Induction (also Functions) Tandy Warnow Preview of the class today What are functions? Weak induction Strong induction A
CS173 Strong Induction and Functions Tandy Warnow CS 173 Introduction to Strong Induction (also Functions) Tandy Warnow Preview of the class today What are functions? Weak induction Strong induction A
Sequences of Real Numbers
 Chapter 8 Sequences of Real Numbers In this chapter, we assume the existence of the ordered field of real numbers, though we do not yet discuss or use the completeness of the real numbers. In the next
Chapter 8 Sequences of Real Numbers In this chapter, we assume the existence of the ordered field of real numbers, though we do not yet discuss or use the completeness of the real numbers. In the next
Binary Decision Diagrams. Graphs. Boolean Functions
 Binary Decision Diagrams Graphs Binary Decision Diagrams (BDDs) are a class of graphs that can be used as data structure for compactly representing boolean functions. BDDs were introduced by R. Bryant
Binary Decision Diagrams Graphs Binary Decision Diagrams (BDDs) are a class of graphs that can be used as data structure for compactly representing boolean functions. BDDs were introduced by R. Bryant
Lecture 2 September 4, 2014
 CS 224: Advanced Algorithms Fall 2014 Prof. Jelani Nelson Lecture 2 September 4, 2014 Scribe: David Liu 1 Overview In the last lecture we introduced the word RAM model and covered veb trees to solve the
CS 224: Advanced Algorithms Fall 2014 Prof. Jelani Nelson Lecture 2 September 4, 2014 Scribe: David Liu 1 Overview In the last lecture we introduced the word RAM model and covered veb trees to solve the
CS/COE 1501 cs.pitt.edu/~bill/1501/ Integer Multiplication
 CS/COE 1501 cs.pitt.edu/~bill/1501/ Integer Multiplication Integer multiplication Say we have 5 baskets with 8 apples in each How do we determine how many apples we have? Count them all? That would take
CS/COE 1501 cs.pitt.edu/~bill/1501/ Integer Multiplication Integer multiplication Say we have 5 baskets with 8 apples in each How do we determine how many apples we have? Count them all? That would take
CSE101: Design and Analysis of Algorithms. Ragesh Jaiswal, CSE, UCSD
 Greedy s Greedy s Shortest path Claim 2: Let S be a subset of vertices containing s such that we know the shortest path length l(s, u) from s to any vertex in u S. Let e = (u, v) be an edge such that 1
Greedy s Greedy s Shortest path Claim 2: Let S be a subset of vertices containing s such that we know the shortest path length l(s, u) from s to any vertex in u S. Let e = (u, v) be an edge such that 1
Lecture 2: Divide and conquer and Dynamic programming
 Chapter 2 Lecture 2: Divide and conquer and Dynamic programming 2.1 Divide and Conquer Idea: - divide the problem into subproblems in linear time - solve subproblems recursively - combine the results in
Chapter 2 Lecture 2: Divide and conquer and Dynamic programming 2.1 Divide and Conquer Idea: - divide the problem into subproblems in linear time - solve subproblems recursively - combine the results in
Lecture 1: Asymptotics, Recurrences, Elementary Sorting
 Lecture 1: Asymptotics, Recurrences, Elementary Sorting Instructor: Outline 1 Introduction to Asymptotic Analysis Rate of growth of functions Comparing and bounding functions: O, Θ, Ω Specifying running
Lecture 1: Asymptotics, Recurrences, Elementary Sorting Instructor: Outline 1 Introduction to Asymptotic Analysis Rate of growth of functions Comparing and bounding functions: O, Θ, Ω Specifying running
Compute the Fourier transform on the first register to get x {0,1} n x 0.
 CS 94 Recursive Fourier Sampling, Simon s Algorithm /5/009 Spring 009 Lecture 3 1 Review Recall that we can write any classical circuit x f(x) as a reversible circuit R f. We can view R f as a unitary
CS 94 Recursive Fourier Sampling, Simon s Algorithm /5/009 Spring 009 Lecture 3 1 Review Recall that we can write any classical circuit x f(x) as a reversible circuit R f. We can view R f as a unitary
Preparing for the CS 173 (A) Fall 2018 Midterm 1
 Preparing for the CS 173 (A) Fall 2018 Midterm 1 1 Basic information Midterm 1 is scheduled from 7:15-8:30 PM. We recommend you arrive early so that you can start exactly at 7:15. Exams will be collected
Preparing for the CS 173 (A) Fall 2018 Midterm 1 1 Basic information Midterm 1 is scheduled from 7:15-8:30 PM. We recommend you arrive early so that you can start exactly at 7:15. Exams will be collected
CS 173: Induction. Madhusudan Parthasarathy University of Illinois at Urbana-Champaign. February 7, 2016
 CS 173: Induction Madhusudan Parthasarathy University of Illinois at Urbana-Champaign 1 Induction February 7, 016 This chapter covers mathematical induction, and is an alternative resource to the one in
CS 173: Induction Madhusudan Parthasarathy University of Illinois at Urbana-Champaign 1 Induction February 7, 016 This chapter covers mathematical induction, and is an alternative resource to the one in
Fall 2017 Test II review problems
 Fall 2017 Test II review problems Dr. Holmes October 18, 2017 This is a quite miscellaneous grab bag of relevant problems from old tests. Some are certainly repeated. 1. Give the complete addition and
Fall 2017 Test II review problems Dr. Holmes October 18, 2017 This is a quite miscellaneous grab bag of relevant problems from old tests. Some are certainly repeated. 1. Give the complete addition and
Divide and Conquer. CSE21 Winter 2017, Day 9 (B00), Day 6 (A00) January 30,
 Divide and Conquer CSE21 Winter 2017, Day 9 (B00), Day 6 (A00) January 30, 2017 http://vlsicad.ucsd.edu/courses/cse21-w17 Merging sorted lists: WHAT Given two sorted lists a 1 a 2 a 3 a k b 1 b 2 b 3 b
Divide and Conquer CSE21 Winter 2017, Day 9 (B00), Day 6 (A00) January 30, 2017 http://vlsicad.ucsd.edu/courses/cse21-w17 Merging sorted lists: WHAT Given two sorted lists a 1 a 2 a 3 a k b 1 b 2 b 3 b
Analysis of Algorithms I: Asymptotic Notation, Induction, and MergeSort
 Analysis of Algorithms I: Asymptotic Notation, Induction, and MergeSort Xi Chen Columbia University We continue with two more asymptotic notation: o( ) and ω( ). Let f (n) and g(n) are functions that map
Analysis of Algorithms I: Asymptotic Notation, Induction, and MergeSort Xi Chen Columbia University We continue with two more asymptotic notation: o( ) and ω( ). Let f (n) and g(n) are functions that map
CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015
 CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015 1 Introduction The divide-and-conquer strategy is a general paradigm for algorithm design. This strategy
CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015 1 Introduction The divide-and-conquer strategy is a general paradigm for algorithm design. This strategy
Induction and recursion. Chapter 5
 Induction and recursion Chapter 5 Chapter Summary Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms Mathematical Induction Section 5.1
Induction and recursion Chapter 5 Chapter Summary Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms Mathematical Induction Section 5.1
Divide & Conquer. CS 320, Fall Dr. Geri Georg, Instructor CS320 Div&Conq 1
 Divide & Conquer CS 320, Fall 2017 Dr. Geri Georg, Instructor georg@colostate.edu CS320 Div&Conq 1 Strategy 1. Divide the problem up into equal sized sub problems 2. Solve the sub problems recursively
Divide & Conquer CS 320, Fall 2017 Dr. Geri Georg, Instructor georg@colostate.edu CS320 Div&Conq 1 Strategy 1. Divide the problem up into equal sized sub problems 2. Solve the sub problems recursively
CMPSCI611: Three Divide-and-Conquer Examples Lecture 2
 CMPSCI611: Three Divide-and-Conquer Examples Lecture 2 Last lecture we presented and analyzed Mergesort, a simple divide-and-conquer algorithm. We then stated and proved the Master Theorem, which gives
CMPSCI611: Three Divide-and-Conquer Examples Lecture 2 Last lecture we presented and analyzed Mergesort, a simple divide-and-conquer algorithm. We then stated and proved the Master Theorem, which gives
Solving Recurrences. Lecture 23 CS2110 Fall 2011
 Solving Recurrences Lecture 23 CS2110 Fall 2011 1 Announcements Makeup Prelim 2 Monday 11/21 7:30-9pm Upson 5130 Please do not discuss the prelim with your classmates! Quiz 4 next Tuesday in class Topics:
Solving Recurrences Lecture 23 CS2110 Fall 2011 1 Announcements Makeup Prelim 2 Monday 11/21 7:30-9pm Upson 5130 Please do not discuss the prelim with your classmates! Quiz 4 next Tuesday in class Topics:
Exercise Sheet #1 Solutions, Computer Science, A M. Hallett, K. Smith a k n b k = n b + k. a k n b k c 1 n b k. a k n b.
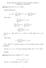 Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Reductions, Recursion and Divide and Conquer
 Chapter 5 Reductions, Recursion and Divide and Conquer CS 473: Fundamental Algorithms, Fall 2011 September 13, 2011 5.1 Reductions and Recursion 5.1.0.1 Reduction Reducing problem A to problem B: (A) Algorithm
Chapter 5 Reductions, Recursion and Divide and Conquer CS 473: Fundamental Algorithms, Fall 2011 September 13, 2011 5.1 Reductions and Recursion 5.1.0.1 Reduction Reducing problem A to problem B: (A) Algorithm
Solving Recurrences. 1. Express the running time (or use of some other resource) as a recurrence.
 1 Recurrences and Recursive Code Solving Recurrences Many (perhaps most) recursive algorithms fall into one of two categories: tail recursion and divide-andconquer recursion. We would like to develop some
1 Recurrences and Recursive Code Solving Recurrences Many (perhaps most) recursive algorithms fall into one of two categories: tail recursion and divide-andconquer recursion. We would like to develop some
CS 4104 Data and Algorithm Analysis. Recurrence Relations. Modeling Recursive Function Cost. Solving Recurrences. Clifford A. Shaffer.
 Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2010,2017 by Clifford A. Shaffer Data and Algorithm Analysis Title page Data and Algorithm Analysis Clifford A. Shaffer Spring
Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2010,2017 by Clifford A. Shaffer Data and Algorithm Analysis Title page Data and Algorithm Analysis Clifford A. Shaffer Spring
CSE373: Data Structures and Algorithms Lecture 3: Math Review; Algorithm Analysis. Catie Baker Spring 2015
 CSE373: Data Structures and Algorithms Lecture 3: Math Review; Algorithm Analysis Catie Baker Spring 2015 Today Registration should be done. Homework 1 due 11:59pm next Wednesday, April 8 th. Review math
CSE373: Data Structures and Algorithms Lecture 3: Math Review; Algorithm Analysis Catie Baker Spring 2015 Today Registration should be done. Homework 1 due 11:59pm next Wednesday, April 8 th. Review math
More Asymptotic Analysis Spring 2018 Discussion 8: March 6, 2018
 CS 61B More Asymptotic Analysis Spring 2018 Discussion 8: March 6, 2018 Here is a review of some formulas that you will find useful when doing asymptotic analysis. ˆ N i=1 i = 1 + 2 + 3 + 4 + + N = N(N+1)
CS 61B More Asymptotic Analysis Spring 2018 Discussion 8: March 6, 2018 Here is a review of some formulas that you will find useful when doing asymptotic analysis. ˆ N i=1 i = 1 + 2 + 3 + 4 + + N = N(N+1)
Lecture 3: Big-O and Big-Θ
 Lecture 3: Big-O and Big-Θ COSC4: Algorithms and Data Structures Brendan McCane Department of Computer Science, University of Otago Landmark functions We saw that the amount of work done by Insertion Sort,
Lecture 3: Big-O and Big-Θ COSC4: Algorithms and Data Structures Brendan McCane Department of Computer Science, University of Otago Landmark functions We saw that the amount of work done by Insertion Sort,
Module 9: Mathematical Induction
 Module 9: Mathematical Induction Module 9: Announcements There is a chance that this Friday s class may be cancelled. Assignment #4 is due Thursday March 16 th at 4pm. Midterm #2 Monday March 20 th, 2017
Module 9: Mathematical Induction Module 9: Announcements There is a chance that this Friday s class may be cancelled. Assignment #4 is due Thursday March 16 th at 4pm. Midterm #2 Monday March 20 th, 2017
1 Introduction (January 21)
 CS 97: Concrete Models of Computation Spring Introduction (January ). Deterministic Complexity Consider a monotonically nondecreasing function f : {,,..., n} {, }, where f() = and f(n) =. We call f a step
CS 97: Concrete Models of Computation Spring Introduction (January ). Deterministic Complexity Consider a monotonically nondecreasing function f : {,,..., n} {, }, where f() = and f(n) =. We call f a step
Analysis of Algorithms - Using Asymptotic Bounds -
 Analysis of Algorithms - Using Asymptotic Bounds - Andreas Ermedahl MRTC (Mälardalens Real-Time Research Center) andreas.ermedahl@mdh.se Autumn 004 Rehersal: Asymptotic bounds Gives running time bounds
Analysis of Algorithms - Using Asymptotic Bounds - Andreas Ermedahl MRTC (Mälardalens Real-Time Research Center) andreas.ermedahl@mdh.se Autumn 004 Rehersal: Asymptotic bounds Gives running time bounds
MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3
 MA008 p.1/37 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/37 Exercise 1 (from LN 2) Asymptotic Notation When constants appear in exponents
MA008 p.1/37 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/37 Exercise 1 (from LN 2) Asymptotic Notation When constants appear in exponents
Day 1: Over + Over Again
 Welcome to Morning Math! The current time is... huh, that s not right. Day 1: Over + Over Again Welcome to PCMI! We know you ll learn a great deal of mathematics here maybe some new tricks, maybe some
Welcome to Morning Math! The current time is... huh, that s not right. Day 1: Over + Over Again Welcome to PCMI! We know you ll learn a great deal of mathematics here maybe some new tricks, maybe some
AN ALGEBRA PRIMER WITH A VIEW TOWARD CURVES OVER FINITE FIELDS
 AN ALGEBRA PRIMER WITH A VIEW TOWARD CURVES OVER FINITE FIELDS The integers are the set 1. Groups, Rings, and Fields: Basic Examples Z := {..., 3, 2, 1, 0, 1, 2, 3,...}, and we can add, subtract, and multiply
AN ALGEBRA PRIMER WITH A VIEW TOWARD CURVES OVER FINITE FIELDS The integers are the set 1. Groups, Rings, and Fields: Basic Examples Z := {..., 3, 2, 1, 0, 1, 2, 3,...}, and we can add, subtract, and multiply
Finding the Median. 1 The problem of finding the median. 2 A good strategy? lecture notes September 2, Lecturer: Michel Goemans
 18.310 lecture notes September 2, 2013 Finding the Median Lecturer: Michel Goemans 1 The problem of finding the median Suppose we have a list of n keys that are completely unsorted. If we want to find
18.310 lecture notes September 2, 2013 Finding the Median Lecturer: Michel Goemans 1 The problem of finding the median Suppose we have a list of n keys that are completely unsorted. If we want to find
Design and Analysis of Algorithms
 CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 5: Divide and Conquer (Part 2) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ A Lower Bound on Convex Hull Lecture 4 Task: sort the
CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 5: Divide and Conquer (Part 2) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ A Lower Bound on Convex Hull Lecture 4 Task: sort the
Solving Recurrences. 1. Express the running time (or use of some other resource) as a recurrence.
 Solving Recurrences Recurrences and Recursive Code Many (perhaps most) recursive algorithms fall into one of two categories: tail recursion and divide-andconquer recursion. We would like to develop some
Solving Recurrences Recurrences and Recursive Code Many (perhaps most) recursive algorithms fall into one of two categories: tail recursion and divide-andconquer recursion. We would like to develop some
10-704: Information Processing and Learning Fall Lecture 10: Oct 3
 0-704: Information Processing and Learning Fall 206 Lecturer: Aarti Singh Lecture 0: Oct 3 Note: These notes are based on scribed notes from Spring5 offering of this course. LaTeX template courtesy of
0-704: Information Processing and Learning Fall 206 Lecturer: Aarti Singh Lecture 0: Oct 3 Note: These notes are based on scribed notes from Spring5 offering of this course. LaTeX template courtesy of
STEP Support Programme. Hints and Partial Solutions for Assignment 1
 STEP Support Programme Hints and Partial Solutions for Assignment 1 Warm-up 1 You can check many of your answers to this question by using Wolfram Alpha. Only use this as a check though and if your answer
STEP Support Programme Hints and Partial Solutions for Assignment 1 Warm-up 1 You can check many of your answers to this question by using Wolfram Alpha. Only use this as a check though and if your answer
We have been going places in the car of calculus for years, but this analysis course is about how the car actually works.
 Analysis I We have been going places in the car of calculus for years, but this analysis course is about how the car actually works. Copier s Message These notes may contain errors. In fact, they almost
Analysis I We have been going places in the car of calculus for years, but this analysis course is about how the car actually works. Copier s Message These notes may contain errors. In fact, they almost
Lecture 2. Fundamentals of the Analysis of Algorithm Efficiency
 Lecture 2 Fundamentals of the Analysis of Algorithm Efficiency 1 Lecture Contents 1. Analysis Framework 2. Asymptotic Notations and Basic Efficiency Classes 3. Mathematical Analysis of Nonrecursive Algorithms
Lecture 2 Fundamentals of the Analysis of Algorithm Efficiency 1 Lecture Contents 1. Analysis Framework 2. Asymptotic Notations and Basic Efficiency Classes 3. Mathematical Analysis of Nonrecursive Algorithms
Park School Mathematics Curriculum Book 9, Lesson 2: Introduction to Logarithms
 Park School Mathematics Curriculum Book 9, Lesson : Introduction to Logarithms We re providing this lesson as a sample of the curriculum we use at the Park School of Baltimore in grades 9-11. If you d
Park School Mathematics Curriculum Book 9, Lesson : Introduction to Logarithms We re providing this lesson as a sample of the curriculum we use at the Park School of Baltimore in grades 9-11. If you d
CSCE 750, Spring 2001 Notes 2 Page 1 4 Chapter 4 Sorting ffl Reasons for studying sorting is a big deal pedagogically useful Λ the application itself
 CSCE 750, Spring 2001 Notes 2 Page 1 4 Chapter 4 Sorting ffl Reasons for studying sorting is a big deal pedagogically useful Λ the application itself is easy to understand Λ a complete analysis can often
CSCE 750, Spring 2001 Notes 2 Page 1 4 Chapter 4 Sorting ffl Reasons for studying sorting is a big deal pedagogically useful Λ the application itself is easy to understand Λ a complete analysis can often
MIDTERM Fundamental Algorithms, Spring 2008, Professor Yap March 10, 2008
 INSTRUCTIONS: MIDTERM Fundamental Algorithms, Spring 2008, Professor Yap March 10, 2008 0. This is a closed book exam, with one 8 x11 (2-sided) cheat sheet. 1. Please answer ALL questions (there is ONE
INSTRUCTIONS: MIDTERM Fundamental Algorithms, Spring 2008, Professor Yap March 10, 2008 0. This is a closed book exam, with one 8 x11 (2-sided) cheat sheet. 1. Please answer ALL questions (there is ONE
Find an Element x in an Unsorted Array
 Find an Element x in an Unsorted Array What if we try to find a lower bound for the case where the array is not necessarily sorted? J.-L. De Carufel (U. of O.) Design & Analysis of Algorithms Fall 2017
Find an Element x in an Unsorted Array What if we try to find a lower bound for the case where the array is not necessarily sorted? J.-L. De Carufel (U. of O.) Design & Analysis of Algorithms Fall 2017
Asymptotic Running Time of Algorithms
 Asymptotic Complexity: leading term analysis Asymptotic Running Time of Algorithms Comparing searching and sorting algorithms so far: Count worst-case of comparisons as function of array size. Drop lower-order
Asymptotic Complexity: leading term analysis Asymptotic Running Time of Algorithms Comparing searching and sorting algorithms so far: Count worst-case of comparisons as function of array size. Drop lower-order
4.4 Recurrences and Big-O
 4.4. RECURRENCES AND BIG-O 91 4.4 Recurrences and Big-O In this section, we will extend our knowledge of recurrences, showing how to solve recurrences with big-o s in them, recurrences in which n b k,
4.4. RECURRENCES AND BIG-O 91 4.4 Recurrences and Big-O In this section, we will extend our knowledge of recurrences, showing how to solve recurrences with big-o s in them, recurrences in which n b k,
