On correcting bursts (and random errors) in vector symbol (n, k) cyclic codes
|
|
|
- Russell McCormick
- 6 years ago
- Views:
Transcription
1 On correcting bursts (and random errors) in vector symbol (n, k) cyclic codes John J. Metzner Pennsylvania State University Department of Computer Science and Engineering University Park, Pennsylvania Abstract. Simple methods are shown for correcting bursts of large size and bursts combined with random errors using vector symbols and primarily vector XOR and feedback shift register operations. One result is that any (n, k) cyclic code with minimum distance > 2 can correct all full error bursts of length n-k-1 or less if the error vectors are linearly independent. If the bursts are not full but contain some error-free components the capability of correcting bursts up to n-k-1 or less is code-dependent. The techniques often work when there is linear dependence. For the case where most errors are in a burst but a small number of errors are outside, the solution, given error-correcting capability, can be broken down into a simple solution for the small number of outside errors, followed by a simple subtraction to reveal all the error values in the burst part. Index terms: Burst error correction, Cyclic codes, vector symbol decoding I. INTRODUCTION It is well-known that any binary (n, k) cyclic code is capable of filling in any cyclic burst of n-k erasures, given the other bits are error-free. However, if there are bit errors in unknown positions, the Rieger bound [1] on the ability to correct any cyclic error burst of length b requires n-k 2b, only half the limit for erasure correction. Gallager s method [2] of finding the shortest burst that could have occurred can often find bursts of greater length than the Rieger bound. However, if a burst of length significantly above the Rieger bound occurs, there is a rather high probability that a burst of shorter length has the same syndrome, giving a wrong result. Burst correction can be done with a very simple feedback shift register circuit. Gallager s method requires two passes, one to find the shortest burst and one to trap it. With nonbinary symbols, the prospect of correcting greater bursts is more promising. In [3], Reed- Solomon codes have been shown able to decoded bursts of length up to n-k-2, not always, but with high probability. The decoding in this case uses field operations and is much 1
2 more complex. Another approach is to use binary vectors as symbols, with operations primarily vector XOR. Vector symbol coding/decoding [4-6 ] is a technique for the outer code of a concatenated code scheme. The technique is most effective when symbol errors are linearly independent with high probability. Individual invertible transformation of data within each symbol can be employed, different for different symbols, so that error events within a symbol are inverse transformed into random patterns that, as vectors, are likely to be linearly independent. A data symbol could be part of an inner code, which can attempt to correct the errors and then inverse transform the symbol data decision. An inner code with good correction capability, possibly using combined coding and modulation, could leave pseudo-random error patterns when it fails. This might remove the need for data transformation. The use of vector XOR also has proved of value in packet-based decoding, where each symbol can be a packet or a large part of a packet. In reliable multicasting [7-10 ], where spare packets called repair packets are sent, the repair packets are derived either by vector XOR or Reed-Solomon codes. These techniques are mostly erasure decoding. Cases where the error positions are unknown are more challenging. In Vector Symbol decoding, a 1" in some position p in an error location vector (ELV) indicates position p is almost surely correct, with certainty if the symbol errors are linearly independent vectors. The property that certain symbols can be declared correct or verified is inherent in Vector Symbol Decoding, and has been amplified in [11] and [12]. It is a property of great potential use. In [12], the use of verification with low density codes and vector XOR operations allows simple decoding. Majority-logic-like codes in [11] and short constraint length vector symbol convolutional codes in [13,14] are also somewhat low density and allow some simplicity. For burst error correction, [15] shows certain classes of Vector Symbol cyclic codes that can correct all bursts where the errors are linearly independent, up to length b = n-k-1. This was shown possible only for a limited set of cyclic codes, all at rate less than ½, often with not very good minimum distance. Some higher rate codes were also shown, at a small reduction in b. Decoding is with feedback shift registers, with almost the same operations as regular burst error correction, except that r-bit vector XOR replaces single-bit modulo two addition, and the register 2
3 elements must each hold r bits. Use of the ELV is not employed in [15]. The ELV has some important properties: 1) A study of its properties shows the ability to use a much wider class of cyclic codes for burst error correction up to n-k-1 than described in [15]. 2) For cases where a burst error of length < n-k-1 cannot be found, Vector symbol decoding of a random error pattern can still be employed. The ELV can locate the error positions and allow solution of their values. Computation of the ELV adds some complexity, but feedback shift registers can help by computing syndromes and in simplifying solution for the error values. If the pattern is a burst, shifting the register to the proper position can discover all vector values directly. If the pattern is a burst plus a small number of outside errors, shifting to cover the burst part can allow quick computation of all error values. A full error burst is a burst where all symbols in the burst are incorrect. For the case of a full burst, the current paper presents a much more general result than in [15 ]. It is shown that all cyclic codes whose minimum distance is greater than 2 are capable of correcting all full error bursts of length n-k-1 or less, given that all errors are linearly independent. Simple shift register operations are used as in [15 ]. The technique can work in many cases even when not all errors are linearly independent. At first thought it would seem that if one could decode all full error bursts up to length n- k-1, one should also be able to correct all such bursts even if some of the symbols in the burst happen to be correct. Unfortunately, this is not the case in general, as will be shown. 3
4 II. VECTOR SYMBOL DECODING WITH CYCLIC CODES A. Vector Symbol decoding Vector Symbol decoding involves deriving an error location vector (ELV). Given an (n, k) binary code with binary check matrix H, the decoder can use H, operating on r-bit symbol inner code decisions, to derive a (n-k) by r syndrome matrix S, as in equation (1). The Vector symbol decoder then performs column operations on S and discovers both the rank of S and null combinations, which span the subspace of the row space of H that is the orthogonal complement of the space of the error vectors. The symbol positions that are 1" in any null combination are very likely to be correct (certain given the errors are linearly independent). The logical OR of these null combinations forms the ELV. Once the ELV is found, if the rank of S matches the number of zeroes in the ELV, the error values can be solved for. Note that a vector symbol code is not simply an interleaved code, in the same sense that turbo codes are not simply interleaved codes. In a turbo code, the data is scrambled over a long period involving many symbols. In a vector symbol decoding code, the data symbols are individually scrambled into an inner code or modulator, as described in the introduction. Most of the power of vector symbol decoding comes when the error vectors are linearly independent, but some dependency does not necessarily preclude correctability [6,11]. For randomly-placed errors, the general result for linearly independent errors is that all errors can be corrected if the error set does not cover all but zero or one position of any code word. The probability that n-k r-bit random vectors are dependent is roughly 2 -[ r-(n-k) ], so for 4
5 effectiveness r should be substantially greater than n-k. The trend to greatly increased data transmission sizes encourages use of multi-bit symbols. The r-bit symbols may in fact represent the data in one of a series of packets, as in [12]. B. Cyclic code representation for Vector Symbol decoding For cyclic codes a vector XOR feedback shift register can be used to compute syndromes. It will be shown that, for cyclic codes, the set of correctable error patterns can be expanded to include many burst patterns that actually do cover all but one position of a code word, without sacrificing the ability to correct all random errors in the correctable error set. Also, the use of cyclic codes greatly simplifies decoding. Useful forms of the check matrix: In 2), the bottom row is the coefficients of h(x), high to low. In 3) the top row is the coefficients of X n-k-1 h(x). Also, any cyclic shift of any of these forms is a possible H matrix. All have the same row space, since each can be derived from any other by elementary row operations. The syndromes will be different for different choices of H, but since the row space is the same for all, they will all compute the same rank, the same null combinations and the same ELV. This is because the null combinations are derived from the same row space. For form 3) the syndromes are computed automatically by feeding of the incoming received sequence (after inner code processing and unscrambling) into a feedback shift register with feedback connections 5
6 determined by g(x), but the register entries are r-bit vectors and addition is vector XOR. By shifting that register with no further input, the error positions and the ELV are cyclically shifted by the amount of the shift. We wish to find the set of correctable cyclic bursts if the error vectors are linearly independent. Additional goals are to correct random errors if there is no burst found, and to see effects of linear dependence. If the inner code adjusted received sequence experiences a burst of errors of length not exceeding n-k, the row space of syndrome matrix S will be the same as the space of error vectors. A burst of n-k successive independent errors cannot be decoded, since, with syndrome rank n-k, there are no dependencies and no error-locating vector can be found. All that is known is that at least n-k errors have occurred. III. THEOREMS Let be the set of all binary cyclic codes that have minimum distance > 2. Theorem 1. If a binary (n, k) cyclic code, h(x) cannot have n-k-1 consecutive zeroes Proof. The generator polynomial g(x) has at least three nonzero terms. We can find the shortest length cyclic code and the associated h(x) from g(x) = 1+X i + +X n-k by first adding X i g(x) to g(x) to cancel X i. If the result is 1+X m, then m = n and h(x) = 1+ X i. Since i < n-k, there are fewer than n-k-1 zeroes between 1 and i. If not, 1+ X i is the first part of h(x), and there are at least three nonzero terms in (1+X i )g(x), where the first is power 0 and the second is power > i, and the last is power n-k+i. Again, to cancel the second term requires a shift by less than n-k, so the number of zeroes in the next gap between nonzero powers in h(x) is again < n-k-1. Continuing until power n is reached, the gap between successive nonzero powers in h(x) is always < n-k-1. If we found a longer length n > n cyclic code with the same g(x), g(x)h(x) = 1+X n with the above computed h(x) would be a code word of weight 2 in this longer code, so the code would not be in. 6
7 To consider the capabilities of burst error correction up to some length, it is easier to start with the case that all symbols in the burst are erroneous. Call this a full burst. Theorem 2. Let the errors be linearly independent and a full cyclic burst of length n-k-1, rank n- k-1. The error location vector will have a string of n-k-1 consecutive zeroes cyclically. The true burst is the only burst (full or not) of length < n-k consistent with the ELV and rank of S. Proof. Suppose the burst is in the first n-k-1 positions. By the cyclic code nature there is no loss in generality to assume this. Any form of the H matrix could be used to find the error-locating vector, so assume form 1). The first n-k-1 rows of S will be linearly independent, and the last row will be zero, since it doesn t include any error positions. This gives the ELV from the last row: h k h k-1...h 0 n-k-1 zeroes By theorem 1, there is no other string of greater than n-k-2 zeroes. Furthermore, the rank is n-k-1, so there must be at least n-k-1 errors. To have a burst of n-k-1 other independent vectors including a length n-k-2 string, the string has a 1" on each side, so two more positions would be needed, giving a burst of length n-k with n-k-1 errors. If the burst were j units shorter than n-k-2, it would have to encompass a 1 and j more zeroes at least, and would also have to be a burst of length > n-k-1. Given the n-k-1 known locations for the burst, there are n-k-1 independent equations to solve for the unknown error values. It is not actually necessary to solve these equations. Once the burst location is known, a feedback shift register can shift the syndromes to where the known burst location is trapped, and the solution then appears identical to the syndromes. In fact we will see it may not even be necessary to find the ELV or rank. 7
8 Theorem 3. For any full burst of length b, b< n-k, independent error symbols, there is no other burst, full or not, of length < n-k, that is consistent with the computed syndrome. Proof. Suppose the burst length is instead n-k-2. Again, without loss of generality, we can place the burst in the first n-k-2 positions and use form (1) of H. Now the rank will be found to be n-k- 2, and the last 2 rows of H will be null combinations. They are: h k h k-1... h h k h k-1...h 0 n-k-1 zeroes Logical OR: (..0 or 1...) 1 1 n-k-2 zeroes The error-location vector will be a logical OR of these two rows. Recall that h(x) has no internal string of more than n-k-2 zeroes. If there is such a string, n-k-2 zeroes the logical OR with a left shift knocks out the rightmost zero and reduces the string length to n-k- 3 or less. Also, there now are at least two ones on both sides of this shorter burst. Each reduction by one of the burst length will further reduce any apparent error position string in the ELV by at least one and increase the number of 1's on each side by at least 1. Thus, if the true burst length is b, the maximum other apparent error position string will remain at most b-1, and there will be at least n-k- b 1's on each side of the false string. To give it enough error locations to match the rank, which is b, it would have to include another zero and all the 1 positions between, which would make its length at least b-1+(n-k-b) + 1 = n-k, which is outside the correction range. So, whenever errors are linearly independent, a full burst with length b < n-k will match the rank and will always be the only possible burst of length < n-k consistent with the rank of S. 8
9 IV. EXAMPLE OF A (21,11) CODE g(x) = 1+X 2 +X 4 +X 6 +X 7 +X 10 or ; h(x) = 1+X 2 +X 7 +X 8 +X 11 or H matrix: Form 1 Form 2 Form First, let s look at full bursts. Consider the first 9 positions, a full burst of n-k-1 errors. If the burst error vectors are linearly independent, column operations on S will yield a rank of 9. From form 1 or 2, the last syndrome will be zero, leaving an ELV equal to the last row: To illustrate that any form leads to the same ELV, note that, in form 3, rows 2,3,8,10 add to zero in the first 9 positions. The vector XOR sum of these rows adds to the same error location vector. The rank 9 means there must be at least 9 errors. The longest string of possible error positions outside the burst is 4. For another burst to include 9 apparent error positions it has to cross over a 1" position, which makes its length n-k = 10. For a full burst of length b independent errors in the first b positions, the ELV is the logical OR of the last n-k-b rows of form 1. b ELV
10 V. FEEDBACK SHIFT REGISTER IMPLEMENTATION For the (21, 11) code, if the full burst positions are the last 9 positions, after all vectors were shifted in, the the following shift register reveals all the burst error values: 0 e 1 e 2 e 3 e 4 e 5 e 6 e 7 e 8 e 9 If the burst is in a different range, shifting can continue with no further input until this pattern appears. At this point there is just one zero syndrome, and the ELV is just the first row of H in form 3. If the error space has a rank of 9, there is only one null combination, namely the ELV just mentioned. If the ELV has been computed from a zero syndrome found in some different shift, it still reveals the correct burst location, and can be shifted the proper amount to reveal all the burst errors. In general, for any case where the errors are all confined cyclically to a span of n-k or less, whether independent or not, the correct error values and positions will appear in some shift of the register. Furthermore, if the burst is length b, n-k-b successive shifts where the burst is trapped will show the same pattern of syndromes shifted. However, additional information, such as the ELV and possibly the rank of S, may be needed to verify the uniqueness of the error solution among the set of correctable errors. Say there are errors of rank, all confined to a span of n-k cyclically consecutive positions. Since, in a cyclic code, any n-k cyclically successive columns of H must be linearly independent, the rank of the row space of S will be.if =, no shift will show more than 10
11 n-k- zero syndrome rows, and the places where the errors are trapped will show exactly n-k- zero syndrome rows. In this case, the complete ELV is computable by taking any shift that has the maximum number of zero syndrome rows, and taking the vector logical OR of the n-k- rows of H in form 3. The ELV may verify the uniqueness of the burst solution. If needed, the rank of the e proposed error values can be computed for further verification. As shown in Theorem 3, if there is a full burst of length b < n-k independent errors, there will be a unique, correct pattern found in this way. If the burst of b< n-k independent errors is not full, there are cases where the solution is not unique, but the ambiguity can be recognized by the ELV, as will be described. If the errors are linearly dependent, <, the shift that traps all the errors still will show n-k- zero syndrome rows. Suppose we pick a position of the shift register that yields the maximum number of zero syndrome rows, as we would also do if the errors were linearly independent. In most cases this maximum will be where the errors are trapped, because errors outside the trap zone will contribute usually to numerous syndrome rows (half on average), so that the rare cases of error vectors adding to zero will not compensate for otherwise zero-valued syndrome rows eliminated by the outside error. From a maximum zero syndrome rows case a (partial) ELV can be computed. This may yield sufficient information about error location. If necessary, the nonzero rows of S could be investigated to find the total ELV and rank, to check consistency with the burst assumption.. If the burst is not full, the correct pattern will be seen in some shift, but it is not true that there will be a unique result for any code in, as will be discussed. For cases where the result is not unique, there usually are just 2 or, rarely, a small number greater than 2 of candidates. Since the code block is likely to cover thousands of bits, it is a small rate sacrifice to include a CRC check hidden in the data to eliminate the wrong alternative(s). 11
12 VI. REMOVING ERRORS INTERIOR TO A BURST Assume the burst starts in the first position and form 2, [I n-k P ], is used to compute the error location vector (ELV). The bottom row is the same row h(x) in form 1. If the full burst is length b < n-k, the last n-k-b rows are null combinations, and the ELV is their vector logical OR. Removing an error in position i introduces row i as an additional null combination. Outside the first n-k positions, a number of 1's occur, some of which will cancel false zeroes. Thus these false zeroes tend to get reduced, but the effects will vary with the code chosen. Let s look at the (21,11) code again. A. Removal of one of the errors in a burst of 9 in the (21,11) code Say the burst of length 9 had a correct entry in position 5. From form 2, the null combinations would be rows 5 and 10.The rank is 8: Row Row ELV For a rank of 8 there must be 8 zeroes. Positions 1-9 are a burst of length 9 with the proper number of zeroes. Positions 2-12 are a burst of length 11 with the proper number of zeroes, but this length is outside the range. So the correct burst is discovered, uniquely. Say the correct entry was in position 2 instead of position 5. Row Row ELV zeroes. Now the ELV shows two results - 1 to 9 and 3 to 11 - both bursts of length 9 with 8 ELV 12
13 B. Why did the first case work while the second didn t? In vector symbol decoding, decoding always is successful for independent errors if the error positions are linearly independent and don t come within one position of covering a code word of the binary code. In cyclic codes, a burst of length n-k or less can t cover a code word, but it can come within one of covering a code word. If it comes within one of a code word, the position it doesn t cover always gives a false zero. This prevents unique random error correction. For burst correction, it is OK if the false zero is far away (cyclically), but if it is close to the burst it can give a false zero that could link to the true zeroes to give a false alternative cyclic burst. The shortest code word burst is g(x), which is a burst of length n-k+1 (11 in this example). g(x) = has ones in positions 1,3,5,7,8,11. These are covered except in position 11 by the burst 1,3,4,5,6,7,8,9, so the false zero in position 11 can t be eliminated. If we make any of the interior positions 3,5,7, or 8 error-free, we are 2 away from covering g(x). In the example where the error in position 5 is eliminated, although the zero in position 11 is eliminated, there is another code word one away that creates a false zero in position 12. But no false alternative burst of length < 10 exists, as explained in VI.A. If we make only interior position 2 error-free, we don t eliminate the false zero in position 11, since we still are one away from covering g(x). But now, there are two bursts of length 9 that are both one away from covering g(x). Cyclically, X n-2 g(x) mod X n -1 is another trouble candidate, with 1's in positions 20,1,3,5,6,9. Removing an error in position 8 will leave an alternative burst due to this code word. Removing an error in position 7 only will not leave an alternative burst of length < 10 in this code word. This is because rank 8 requires linking positions 1-6 and 8 to the false zero in position 20, which is a burst of length 10. If we make position 4 the zero error position, it does not eliminate a false zero, but the false burst would then have to extend past the ELV 1 in position 4 as well as the 1 in position 10 or position 1, and cover 8 zeroes, giving a length of 10. So the ambiguous cases with one errorfree interior symbol are making positions 2 or 8 error-free. Other ambiguous cases with different amounts of error-free symbols can be found. 13
14 C. Relating false zeroes to code words one away from a burst. Look at the systematic form of the generator matrix. This form allows easy discovery of all the code words covered one away from a full burst starting in the first position. The jth row, 1 j k, is c j (X) = r j (X) + X n-k-1+j where r j (X) = X n-k-1+j mod g(x) For any j where deg{r j (X) } < b, where b is the full burst length, c j (X) is a code word one away from coverage by the burst. These are the only code words one away. No code word that is a combination of two or more rows in the systematic G can be only one away, since the combination would have to have at least two 1's in the last k columns, which are all outside the burst. Each code word one away from the burst contributes exactly one false zero to the ELV. For non-full bursts, removing an error in position c will eliminate any one-away c j (X) that has a 1' in column c, row j of G. The error removal cannot increase the number of false zeroes, and usually reduces the number. By the argument of theorem 3, removing an error from the end of a burst reduces all false zero strings by one. If the same burst is in a different position, the systematic G can be shifted so the nonidentity part starts at the burst start, and all the one-from-covered code words and the ELV will shift by the same amount. As an example, consider the (21,11) code with a burst of length 9 and eight errors, with position 2 error-free, as illustrated in VI.3, Relative to form 2, H = [I n-k P ], G = [P T I k ] n-k=10 ELV position power code word covered all but one Row of G g(x) X 16 +r 7 (X) X 17 +r 8 (X) X 19 +r 10 (X)
15 From the ELV, we saw that two bursts of length 9 with position 2 error-free are possible, covering within one of g(x). The false zero in the fourth code word would need a cyclic burst of 10 to encompass the needed 8 zero locations to get the rank of 8. The second and third false zeroes would need still longer bursts. D. Conditions for two possible bursts of length < n-k covering within one of a code word Let s take a closer look at the case where the the error burst was a0cdefghi, length 9, and alternative length 9 burst 00a b c d e f g 0 i. Both of these are one from the code word g(x), so we can concentrate on that case. ELV position power code word covered all but one Row of G g(x) Let s compare the syndrome sets beginning from where these bursts start coming in the window of the feedback shift register. True syndromes False syndromes a+c 0 a a 0, i d a+c 0 b a a+e d c c b a +i f a+e d d c b a+g f e e d c +i a+h a+g f f e d i a+h g g f e +i i h 0 g f +i a 0 i i 0 g a 0 0 i 0 a 0 c d e f g h i a b c d e f g 0 i Note that the column where the a lines up shows that a doesn t affect the second, fourth, seventh, eighth or tenth syndrome. These syndromes should be d, f, i, 0, 0, respectively, with no contribution from other errors. Under the second hypothesis, these places would be b, d, g, 0, 0, also with no contribution from other errors. Thus d = b, f = d, and i = g, and we have found 3 of the errors. 15
16 Despite finding three of the errors, there still is not a unique solution. The remaining zeroes in the ELV exactly match the one-from-covered g(x). Both have 5 errors but one is burst 8, the other burst 9. remaining patterns: a 0 c 0 e 0 g h a 0 c 0 e f 0 0 i ELV g(x) It is easy to see the reason for this failure to resolve when two different bursts exactly cover one from the same code word. Suppose the code word c(x) has weight m. The m nonzero positions are not necessarily consecutive. Say the correct burst is precisely [e 1, e 2,...,e m-1, 0] in the first m - 1 positions of c(x). Take any vector symbol v. The pattern [v,v,,v,...,v] in these m nonzero positions of c(x), zero elsewhere has a zero syndrome. If v = e 1, the pattern [0, e 1 +e 2, e 1 +e 3,...e 1 +e m-1, e 1 ] has the same syndrome as [e 1, e 2,...,e m-1, 0] and they cannot be distinguished. With the v = e i, the zero could appear in any position, but cases where the zero appears elsewhere, or does not appear, correspond to a burst of length at least n-k+1. Thus there are only at most two candidates, one with a zero at the beginning, and one with a zero at the end. As a burst, they have the same number of errors, but may be different lengths, due to the irregular spacings of the m code word 1's. When are two candidates within a one-from-covered code word not possible? With burst correction, if either [e 1, e 2,...,e m-1, 0] or [0, e 1 ', e 2 ',...,e m-1 '] is of length > n-k-1, it is not a possible candidate. In particular, suppose c(x) starts with 1+X. Then the span including e 1 ' and e m-1 ' would stretch from X to at least X n-k, a span of length at least n-k, which is not a candidate. A similar statement applies to e 1 and e m-1 if c(x) ends with two 1's. If c(x) both starts and ends with two ones, no two bursts of length < n-k can cover one from that c(x). In particular, this applies to g(x), the least length code word burst. 16
17 E. Shorter bursts with the (21, 11) code. ELV, full burst of position power code word covered all but one row of G g(x) X 14 +r 5 (X) X 15 +r 6 (X) X 16 +r 7 (X) Removal of error in position 2. 8 New ELV position power code word covered all but one A false burst of length 9 would look the same as a true burst of length 8, both of rank 7, and vice versa. Thus this case is not unique. ELV, full burst of OR of last 3 rows position power code word covered all but one X 14 +r 5 (X) X 15 +r 6 (X) Removal of any interior error except solely position 5 or solely position 6 would remove both false zeroes, as would removing both 5 and 6. But removing just one of these would reduce the rank to 5, and it would not be possible to link a burst of length less than ten having 5 zero positions including the one remaining false zero Thus all independent error bursts of length 7 or less are uniquely decodable with this code F. Relation to the methods in [15]. In [15], the ability to correct all bursts of length < n-k, assuming linearly independent errors is obtained only when h(x) is a vector of all 1's. This limits the class of codes to a relatively small number, all with rate < ½. By allowing h(x) to have no more than j consecutive interior ones, [15] shows that all bursts of independent errors up to length n-k-1-j could be corrected uniquely. In these cases rates > ½ can be used. An example of this from [15] is a 17
18 (30,19) code capable of correcting all independent bursts of length up to 9, with g(x) = h(x) = burst length ELV (assuming burst in first part) 10 (full) (full) It is obvious that there are no false zeroes with a burst length of 9, so removing interior errors would not lead to any false burst. However, what was not shown in [15] is that the same code can also correct a full burst of length 10, as well as most other bursts of length 10. Put the burst in a center place to see the effects on both ends. x ELV centered one-from-covered words 1) ) ) ) Also, 5) and 6) (not shown) are symmetric versions of 3) and 4). g(x) and h(x) are each their own reciprocals in this code. Removing any two or more internal errors will keep the errors from being from one of any code word, since each code word in 1) to 6) has only a single zero in the burst range. Removing any error except the one in position 2 (see x) or the one in position 9 of the burst will keep the errors from being within one of code words 1) and 2), and remove the nearby false zeroes. Making position 5 error-free to keep within one of word 3) would not make it possible to span a burst of length < 11 including the outside zero position and 8 other zero positions. Similar statements can be mad about 4) to 6). Thus, of all the bursts of length 10 or less, the only ones that would lead to an ambiguity due to 1) and 2) are x0xxxxxxx and xxxxxxxx0x. In these cases there will be two bursts with the same syndrome. Thus only 2 of the 256 inner patterns of a burst of independent errors with length 10 could cause an ambiguity. This is a significant extension over the ability to correct all independent error bursts of length up to 9 or less unambiguously. 18
19 G. Codes where g(x) begins and ends with two ones If g(x) begins and ends with two ones, so does h(x), from the properties h 0 = h k = g 0 = g n-k =1 and g 0 h 1 + g 1 h 0 = 0 h 1 = g 1 g n-k h k-1 + g n-k-1 h k = 0 h k-1 = g n-k-1 Thus, the ELV for a full burst independent errors of length n-k-1 would be of the form: x...x 1 1. n-k-1 zeroes Removing one interior error would leave an unambiguous burst of length n-k-1, because any burst with n-k-2 errors and a false zero would have to cross at least two 1's and encompass n- k-3 true zeroes, giving it a length of at least n-k. There would still be possible cases of ambiguity on removal of two or more interior ones. For a full burst of length n-k-2, there would be strings of minimum three 1's on each end: x...x n-k-2 zeroes Again, in this case or any case of length < n-k, removal of one interior error can t cause ambiguity. Removal of the two leftmost or the two rightmost interior errors could result in an alternative of length n-k-1, depending on the rest of g(x). Table I summarizes the cases where there are possible alternative bursts. Actually, the possible alternatives are worst case and may be nonexistent for some codes. Burst length removals possible alternative burst length n-k-1 2 n-k-1 >2 shorter n-k-2 2 n-k-1 3 n-k-2 4 shorter n-k-3 2 n-k-1 3 n-k-2 4 n-k-3 5 shorter Table 1. Possible alternative bursts for codes where g(x) starts and begins with two ones. 19
20 H. The (23,12) Golay code This well-known code [16] has g(x) = 1 + X 2 + X 4 + X 5 + X 6 + X 10 + X 11 and a minimum distance of 7. It can be shown that the Golay code can correct unambiguously any burst of independent vector symbol errors of length n-k-1 = 10 or less, whether full or not. The details are omitted to save space. The arguments are similar to those in the (21,11) code example. In addition, as a vector symbol code, it can correct any random pattern of 7-2 = 5 independent errors, as well as any other random independent error pattern of > 5 errors that doesn t come within one of covering a code word. The probabilities that a certain number of random errors > 5 can be decoded can be computed since the weight distribution of the Golay code is known. For example, since there are 253 words of minimum nonzero weight 7, there are = 1771 patterns of 6 errors that cannot be decoded, which is 1/57 of all 6-error patterns. VII. DEPENDENT ERRORS AND ZERO SYNDROME COUNTS IN SHIFTS The method of just shifting the feedback shift register to find the maximum number of zero syndromes often works even if errors are linearly dependent. When there are errors, there will be exactly n-k- zero syndrome rows, whether or not the errors are independent. If they are independent, thy reveal all n-k- null combinations. As explained in Section V, the maximum number of zero syndrome rows usually occurs where the burst is trapped, even with some dependencies.. Consider the (21,11) code. For b = 6, let a,b,c,d,e,f be the error values in a full burst Below is shown the number of zero syndrome rows for various starting positions in the cases 1) all 6 errors are linearly independent, and 2) = 5 with b+d+e=0, and 3) = 4 with a = c and b+d+e = 0. Part of the matrix is reproduced on both sides to show all cases. 20
21 abcd ef case 1, = case 2, = case 3, = Even for these cases of = 5 and = 4, the decoder sees that the shortest possible burst is length 6, and traps the correct burst of length 6. The method works even without computing any ELV. Obviously it wouldn t work for rank 1, such as binary symbols, since in g(x) two bursts of length 5 add to a code word so the binary burst correcting capability of this code can t be more than 4. Let s look at the ELV, relative to when the burst is moved just into the last n-k positions: case 1, = case 2, = case 3, = For cases 2 and 3 the case 1 ELV is a partial ELV, whose zeroes only can be reduced by other null combinations. Note it already indicates the burst location. Investigation of the found errors can discover their dependencies and the actual ELV, due to the logical OR combination. but this would probably not be necessary. In [6], it has been shown how to correct most cases of t errors of rank t-1 when the error pattern doesn t cover one from a code word. However, no method has been given for when the rank is t-2. Here the error pattern actually is one from a code word, and in case 3 is rank t-2. So these results go beyond the capability shown in [6]. 21
22 In the same code, consider a burst of length 6 with 3 errors: a00d0f a00d0f independent a=d, rank ELV, independent a=d additional ELV, dependent The observations of 7 zero syndromes finds the burst location and values. Again, the correct burst is found simply, even with a dependency. The partial ELV identifies the three errors. The total ELV identifies only the error not in the dependency. In this case the errors don t cover one from a code word, and the rank is t-1. Thus in this case the vector symbol decoding method in [6] also would have found the errors and values, but with greater effort. VIII. CORRECTING BOTH BURSTS AND RANDOM ERRORS There are many cases where most errors in a block code are clustered in a burst, but there are one or two errors outside the cluster. Trapping the cluster part can simplify decoding of all the errors. A. A burst plus a single outside error Suppose there are e errors clustered in a span of n-k positions, and one error outside the span. Assume the e+1 errors are linearly independent and do not cover all but one position of any code word. Vector symbol decoding can find the error locations and solve for their values, but decoding can be simplified by using some principals related to the burst correction methods. Do the usual feedback shift register computations of syndromes in different cyclic 22
23 positions. When the cluster of e is trapped, there would be n-k-e zero syndromes, except that the one outside error on average will change about half of the otherwise zero syndromes to the value of the outside error. If it doesn t change any it would mean that the column of the H matrix corresponding to the outside error is the sum of only positions of the other errors, and the errors cover a code word, contrary to the assumption. If it removes only one zero syndrome, that means that the error pattern is only one from covering a code word, which is also contrary to assumption. So the outside value will appear at least 2 times in the set of syndromes. The following illustrates how easily the errors can be found and evaluated. Errors a b cd e syndrome rows obvious null combinations b a a+c a+d a a+e Partial ELV Additional zero syndrome, row 3 + row 6: Total ELV The duplicate a is the outside error value, and the Partial ELV identifies the outside position. Thus the outside value a is revealed. ( Or the total ELV can be computed by including row 3+row 6 as a null combination.) Then, add a to each syndrome where the outside column is a 1", and all the burst error values appear directly as the syndrome values in the indicated positions.. In the (21,11) code, dmin = 6, so any case of 4 independent errors, 3 in a burst and one outside, can be corrected. In this case it worked with 5 errors because the errors happened not to all be in 5 of the one positions of some weight 6 code word. Following is a case of two errors outside and three inside. In this case the Partial ELV from the two direct zero syndromes is not enough to identify the outside error locations or values. However, two duplicates can be observed readily, creating a further partial ELV, which shows 23
24 the two outside error positions and the first three syndromes are free of any errors inside the diagonal part.from the first two rows, we have the submatrix results 10 a syndrome 11 a+b syndrome We can then subtract the found values a and b from the contributions shown by columns 5 and 6. This reveals directly all the other errors: c, d, and e. Errors ab cd e syndromes a a+b a+b a+b+c b+d a b e Partial ELV Additional zero syndrome, row 2 + row 3: Additional zero syndrome, row 1 + row Further partial ELV Additional zero syndrome, rows 1,2, total ELV In general, if any calculation of the ELV splits into a part with 1 or 2 location zeroes and the rest of the zeroes in a span of n-k places, with the rank matching the number of zeroes, then by moving the register to trap the burst part, the solution for the 1 or 2 isolated errors involves just one or two equations, and all the other values are found by subtraction. Calculation of the ELV itself can be simplified by doing it in the shift position that shows the greatest number of obvious null combinations - zero syndromes and duplicate values. 24
25 IX. CONCLUSIONS It has been shown how to expand prior capabilities of burst error correction with vector symbol cyclic codes to correct in a simple manner most events of most burst errors of length < n- k and random error patterns that do not cover all but one position of any code word. By borrowing some simple methods used in burst error correction, a way of correcting random vector symbol errors more simply than in prior work is proposed. If most errors are clustered in a span of n-k, with a few outside errors, the outside errors can be discovered simply, and effects subtracted. Then the clustered errors are revealed immediately in a shift register. A general result has been proven, for the special case of a full burst of independent errors, that all full bursts of length less than n-k can be uniquely decoded by any cyclic code with minimum distance greater than 2. Unfortunately, this property does not extend in general to nonfull bursts, where capabilities are code-dependent. The property does extend to some cyclic codes, including the (23,12) Golay code. Methods have been described for finding burst capabilities based on the ELV and code word coverage. It has been shown that burst correction capability often extends to cases where the errors cover all but one position of a code word. Previous vector symbol decoding for random errors has been restricted to cases where errors are at least two away from coding any code word. Extension with bursts is possible because, if two different patterns with the same number of errors have the same syndrome, decoding is consider as failed for randomly-place errors, but if one pattern is a burst of length < n-k and the other is not, it is decoded as the burst. It also has been demonstrated that much of the burst correction capability holds even when there is some dependence. A previous result for general parity check codes with Vector Symbol decoding is that most cases of t errors of rank t-1 can be decoded with some extra effort. It is shown here that such cases can be decoded very simply for cyclic codes, extending to many cases of rank even less than t-1. There is considerable room for additional research on the ideas presented here. Although the paper describes some guiding principles, precise recipes for designing good burst-errorcorrecting codes are not given. Based on general results for randomly- chosen codes for vector 25
26 symbol decoding, it is suspected that the choice of code might not be too critical. It was shown in this paper that simply observing zero syndrome rows over a succession of feedback shift register shifts can allow simple decoding with dependent errors that is beyond the capabilities of previous methods of vector symbol decoding. However, general results defining precisely how much dependency can be tolerated have not been found. Simulations with different codes and error events could clarify capabilities. REFERENCES. [1 ] S. H. Rieger, Codes for the correction of clustered errors, IRE Trans. Inform. Theory, Vol. IT-6, pp , [2] R. G. Gallager, Information Theory and Reliable Communication, pp New York: Wiley, [3] G. Chen and P. Owsley, A burst-error algorithm for Reed-Solomon codes, IEEE Trans. Inform. Theory, pp , November [4] J.J. Metzner and E.J. Kapturowski, "a general decoding technique applicable to replicated file disagreement location and concatenated code decoding", IEEE Trans. Inform. Theory, Vol. 36, pp , July [5] K.T. Oh and J.J. Metzner, "Performance of a general decoding technique over the class of randomly chosen parity check codes," IEEE Trans. Inform. Theory, vol. 40, pp , January 1994 [6] J. J. Metzner, Vector Symbol Decoding with List Inner Symbol Decisions and Dependent Errors. IEEE Trans. Commun., vol. 51, pp , March [7] J. J. Metzner,. An Improved Broadcast Retransmission Protocol, IEEE Trans. Commun., vol. COM-32, pp , June 1984 [8] B. Whetten and G. Taskale, "An Overview of Reliable Multicast Transport Protocol II", IEEE Network Magazine, pp , Jan/Feb [9] M. Luby, M. Mitzenmacher, M. Shokrollahi, and D. Spielman, Efficient Erasure Correcting Codes, IEEE Trans. Inform. Theory., v. 47, pp , February 2001.[10] J. W. Byers, M. Luby and M. Mitzenmacher, "A Digital Fountain approach to Asynchronous Reliable Multicast," IEEE J. Selec. Areas Comm., v. 20, pp , October [11] J. J. Metzner, Majority-Logic-Like Vector Symbol Decoding with Alternative Symbol Lists,. IEEE Trans. Commun. v. 48, pp , December 2000 [12] M. G. Luby and M. Mitzenmacher, Verification-based decoding for packet-based lowdensity parity check codes, IEEE Trans. Inform. Theory, vol. 51, pp , January [13] J. J. Metzner, Convolutionally Encoded Memory Protection, IEEE Trans. Computers, vol. C-31, pp ,.June [14] U. Tuntoolavest and J. J. Metzner, Vector Symbol Convolutional Decoding with List Symbol Decisions, Integrated Computer-Aided Engineering, vol. 9 no. 2, pp IOS 26
27 Press, Netherlands [15] J. J. Metzner and Y. T. Cha, On Simple Correction of Bursts up to Nearly Twice the Guaranteed Correction Bound, Proceedings of the 1994 Princeton Conference on Information Systems and Sciences. pp , Princeton, NJ,.March See also US Patent 5,657,331, August [16] M. J. E. Golay, Notes on digital coding, Proc. IRE, vol. 37, p. 657, June
The Pennsylvania State University. The Graduate School. Department of Computer Science and Engineering
 The Pennsylvania State University The Graduate School Department of Computer Science and Engineering A SIMPLE AND FAST VECTOR SYMBOL REED-SOLOMON BURST ERROR DECODING METHOD A Thesis in Computer Science
The Pennsylvania State University The Graduate School Department of Computer Science and Engineering A SIMPLE AND FAST VECTOR SYMBOL REED-SOLOMON BURST ERROR DECODING METHOD A Thesis in Computer Science
Chapter 7. Error Control Coding. 7.1 Historical background. Mikael Olofsson 2005
 Chapter 7 Error Control Coding Mikael Olofsson 2005 We have seen in Chapters 4 through 6 how digital modulation can be used to control error probabilities. This gives us a digital channel that in each
Chapter 7 Error Control Coding Mikael Olofsson 2005 We have seen in Chapters 4 through 6 how digital modulation can be used to control error probabilities. This gives us a digital channel that in each
Chapter 5. Cyclic Codes
 Wireless Information Transmission System Lab. Chapter 5 Cyclic Codes Institute of Communications Engineering National Sun Yat-sen University Outlines Description of Cyclic Codes Generator and Parity-Check
Wireless Information Transmission System Lab. Chapter 5 Cyclic Codes Institute of Communications Engineering National Sun Yat-sen University Outlines Description of Cyclic Codes Generator and Parity-Check
Lecture 12. Block Diagram
 Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Information redundancy
 Information redundancy Information redundancy add information to date to tolerate faults error detecting codes error correcting codes data applications communication memory p. 2 - Design of Fault Tolerant
Information redundancy Information redundancy add information to date to tolerate faults error detecting codes error correcting codes data applications communication memory p. 2 - Design of Fault Tolerant
Cyclic codes: overview
 Cyclic codes: overview EE 387, Notes 14, Handout #22 A linear block code is cyclic if the cyclic shift of a codeword is a codeword. Cyclic codes have many advantages. Elegant algebraic descriptions: c(x)
Cyclic codes: overview EE 387, Notes 14, Handout #22 A linear block code is cyclic if the cyclic shift of a codeword is a codeword. Cyclic codes have many advantages. Elegant algebraic descriptions: c(x)
Chapter 3 Linear Block Codes
 Wireless Information Transmission System Lab. Chapter 3 Linear Block Codes Institute of Communications Engineering National Sun Yat-sen University Outlines Introduction to linear block codes Syndrome and
Wireless Information Transmission System Lab. Chapter 3 Linear Block Codes Institute of Communications Engineering National Sun Yat-sen University Outlines Introduction to linear block codes Syndrome and
Guess & Check Codes for Deletions, Insertions, and Synchronization
 Guess & Check Codes for Deletions, Insertions, and Synchronization Serge Kas Hanna, Salim El Rouayheb ECE Department, Rutgers University sergekhanna@rutgersedu, salimelrouayheb@rutgersedu arxiv:759569v3
Guess & Check Codes for Deletions, Insertions, and Synchronization Serge Kas Hanna, Salim El Rouayheb ECE Department, Rutgers University sergekhanna@rutgersedu, salimelrouayheb@rutgersedu arxiv:759569v3
Linear Cyclic Codes. Polynomial Word 1 + x + x x 4 + x 5 + x x + x
 Coding Theory Massoud Malek Linear Cyclic Codes Polynomial and Words A polynomial of degree n over IK is a polynomial p(x) = a 0 + a 1 x + + a n 1 x n 1 + a n x n, where the coefficients a 0, a 1, a 2,,
Coding Theory Massoud Malek Linear Cyclic Codes Polynomial and Words A polynomial of degree n over IK is a polynomial p(x) = a 0 + a 1 x + + a n 1 x n 1 + a n x n, where the coefficients a 0, a 1, a 2,,
Error Correction Review
 Error Correction Review A single overall parity-check equation detects single errors. Hamming codes used m equations to correct one error in 2 m 1 bits. We can use nonbinary equations if we create symbols
Error Correction Review A single overall parity-check equation detects single errors. Hamming codes used m equations to correct one error in 2 m 1 bits. We can use nonbinary equations if we create symbols
x n k m(x) ) Codewords can be characterized by (and errors detected by): c(x) mod g(x) = 0 c(x)h(x) = 0 mod (x n 1)
 Cyclic codes: review EE 387, Notes 15, Handout #26 A cyclic code is a LBC such that every cyclic shift of a codeword is a codeword. A cyclic code has generator polynomial g(x) that is a divisor of every
Cyclic codes: review EE 387, Notes 15, Handout #26 A cyclic code is a LBC such that every cyclic shift of a codeword is a codeword. A cyclic code has generator polynomial g(x) that is a divisor of every
ERROR CORRECTING CODES
 ERROR CORRECTING CODES To send a message of 0 s and 1 s from my computer on Earth to Mr. Spock s computer on the planet Vulcan we use codes which include redundancy to correct errors. n q Definition. A
ERROR CORRECTING CODES To send a message of 0 s and 1 s from my computer on Earth to Mr. Spock s computer on the planet Vulcan we use codes which include redundancy to correct errors. n q Definition. A
Error Correction Methods
 Technologies and Services on igital Broadcasting (7) Error Correction Methods "Technologies and Services of igital Broadcasting" (in Japanese, ISBN4-339-06-) is published by CORONA publishing co., Ltd.
Technologies and Services on igital Broadcasting (7) Error Correction Methods "Technologies and Services of igital Broadcasting" (in Japanese, ISBN4-339-06-) is published by CORONA publishing co., Ltd.
MATH3302. Coding and Cryptography. Coding Theory
 MATH3302 Coding and Cryptography Coding Theory 2010 Contents 1 Introduction to coding theory 2 1.1 Introduction.......................................... 2 1.2 Basic definitions and assumptions..............................
MATH3302 Coding and Cryptography Coding Theory 2010 Contents 1 Introduction to coding theory 2 1.1 Introduction.......................................... 2 1.2 Basic definitions and assumptions..............................
Coding Theory: Linear-Error Correcting Codes Anna Dovzhik Math 420: Advanced Linear Algebra Spring 2014
 Anna Dovzhik 1 Coding Theory: Linear-Error Correcting Codes Anna Dovzhik Math 420: Advanced Linear Algebra Spring 2014 Sharing data across channels, such as satellite, television, or compact disc, often
Anna Dovzhik 1 Coding Theory: Linear-Error Correcting Codes Anna Dovzhik Math 420: Advanced Linear Algebra Spring 2014 Sharing data across channels, such as satellite, television, or compact disc, often
Structured Low-Density Parity-Check Codes: Algebraic Constructions
 Structured Low-Density Parity-Check Codes: Algebraic Constructions Shu Lin Department of Electrical and Computer Engineering University of California, Davis Davis, California 95616 Email:shulin@ece.ucdavis.edu
Structured Low-Density Parity-Check Codes: Algebraic Constructions Shu Lin Department of Electrical and Computer Engineering University of California, Davis Davis, California 95616 Email:shulin@ece.ucdavis.edu
Chapter 6. BCH Codes
 Chapter 6 BCH Codes Description of the Codes Decoding of the BCH Codes Outline Implementation of Galois Field Arithmetic Implementation of Error Correction Nonbinary BCH Codes and Reed-Solomon Codes Weight
Chapter 6 BCH Codes Description of the Codes Decoding of the BCH Codes Outline Implementation of Galois Field Arithmetic Implementation of Error Correction Nonbinary BCH Codes and Reed-Solomon Codes Weight
2. Polynomials. 19 points. 3/3/3/3/3/4 Clearly indicate your correctly formatted answer: this is what is to be graded. No need to justify!
 1. Short Modular Arithmetic/RSA. 16 points: 3/3/3/3/4 For each question, please answer in the correct format. When an expression is asked for, it may simply be a number, or an expression involving variables
1. Short Modular Arithmetic/RSA. 16 points: 3/3/3/3/4 For each question, please answer in the correct format. When an expression is asked for, it may simply be a number, or an expression involving variables
THIS paper is aimed at designing efficient decoding algorithms
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 45, NO. 7, NOVEMBER 1999 2333 Sort-and-Match Algorithm for Soft-Decision Decoding Ilya Dumer, Member, IEEE Abstract Let a q-ary linear (n; k)-code C be used
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 45, NO. 7, NOVEMBER 1999 2333 Sort-and-Match Algorithm for Soft-Decision Decoding Ilya Dumer, Member, IEEE Abstract Let a q-ary linear (n; k)-code C be used
Some Easily Decoded, Efficient, Burst Error Correcting Block Codes
 INFORMATION AND CONTROL 23, 234--244 (1973) Some Easily Decoded, Efficient, Burst Error Correcting Block Codes DAVID MANDELBAUM P.O. Box 645, Eatontown, New Jersey 07724 Single phased burst correcting
INFORMATION AND CONTROL 23, 234--244 (1973) Some Easily Decoded, Efficient, Burst Error Correcting Block Codes DAVID MANDELBAUM P.O. Box 645, Eatontown, New Jersey 07724 Single phased burst correcting
Generator Matrix. Theorem 6: If the generator polynomial g(x) of C has degree n-k then C is an [n,k]-cyclic code. If g(x) = a 0. a 1 a n k 1.
![Generator Matrix. Theorem 6: If the generator polynomial g(x) of C has degree n-k then C is an [n,k]-cyclic code. If g(x) = a 0. a 1 a n k 1. Generator Matrix. Theorem 6: If the generator polynomial g(x) of C has degree n-k then C is an [n,k]-cyclic code. If g(x) = a 0. a 1 a n k 1.](/thumbs/72/66951550.jpg) Cyclic Codes II Generator Matrix We would now like to consider how the ideas we have previously discussed for linear codes are interpreted in this polynomial version of cyclic codes. Theorem 6: If the
Cyclic Codes II Generator Matrix We would now like to consider how the ideas we have previously discussed for linear codes are interpreted in this polynomial version of cyclic codes. Theorem 6: If the
Optical Storage Technology. Error Correction
 Optical Storage Technology Error Correction Introduction With analog audio, there is no opportunity for error correction. With digital audio, the nature of binary data lends itself to recovery in the event
Optical Storage Technology Error Correction Introduction With analog audio, there is no opportunity for error correction. With digital audio, the nature of binary data lends itself to recovery in the event
Coset Decomposition Method for Decoding Linear Codes
 International Journal of Algebra, Vol. 5, 2011, no. 28, 1395-1404 Coset Decomposition Method for Decoding Linear Codes Mohamed Sayed Faculty of Computer Studies Arab Open University P.O. Box: 830 Ardeya
International Journal of Algebra, Vol. 5, 2011, no. 28, 1395-1404 Coset Decomposition Method for Decoding Linear Codes Mohamed Sayed Faculty of Computer Studies Arab Open University P.O. Box: 830 Ardeya
Fault Tolerance & Reliability CDA Chapter 2 Cyclic Polynomial Codes
 Fault Tolerance & Reliability CDA 5140 Chapter 2 Cyclic Polynomial Codes - cylic code: special type of parity check code such that every cyclic shift of codeword is a codeword - for example, if (c n-1,
Fault Tolerance & Reliability CDA 5140 Chapter 2 Cyclic Polynomial Codes - cylic code: special type of parity check code such that every cyclic shift of codeword is a codeword - for example, if (c n-1,
ECE 4450:427/527 - Computer Networks Spring 2017
 ECE 4450:427/527 - Computer Networks Spring 2017 Dr. Nghi Tran Department of Electrical & Computer Engineering Lecture 5.2: Error Detection & Correction Dr. Nghi Tran (ECE-University of Akron) ECE 4450:427/527
ECE 4450:427/527 - Computer Networks Spring 2017 Dr. Nghi Tran Department of Electrical & Computer Engineering Lecture 5.2: Error Detection & Correction Dr. Nghi Tran (ECE-University of Akron) ECE 4450:427/527
Windowed Erasure Codes
 Windowed Erasure Codes Chris Studholme Department of Computer Science University of Toronto Email: cvs@csutorontoca Ian Blake Department of Electrical and Computer Eng University of Toronto Email: ifblake@commutorontoca
Windowed Erasure Codes Chris Studholme Department of Computer Science University of Toronto Email: cvs@csutorontoca Ian Blake Department of Electrical and Computer Eng University of Toronto Email: ifblake@commutorontoca
Linear Algebra, Summer 2011, pt. 2
 Linear Algebra, Summer 2, pt. 2 June 8, 2 Contents Inverses. 2 Vector Spaces. 3 2. Examples of vector spaces..................... 3 2.2 The column space......................... 6 2.3 The null space...........................
Linear Algebra, Summer 2, pt. 2 June 8, 2 Contents Inverses. 2 Vector Spaces. 3 2. Examples of vector spaces..................... 3 2.2 The column space......................... 6 2.3 The null space...........................
Binary Primitive BCH Codes. Decoding of the BCH Codes. Implementation of Galois Field Arithmetic. Implementation of Error Correction
 BCH Codes Outline Binary Primitive BCH Codes Decoding of the BCH Codes Implementation of Galois Field Arithmetic Implementation of Error Correction Nonbinary BCH Codes and Reed-Solomon Codes Preface The
BCH Codes Outline Binary Primitive BCH Codes Decoding of the BCH Codes Implementation of Galois Field Arithmetic Implementation of Error Correction Nonbinary BCH Codes and Reed-Solomon Codes Preface The
B. Cyclic Codes. Primitive polynomials are the generator polynomials of cyclic codes.
 B. Cyclic Codes A cyclic code is a linear block code with the further property that a shift of a codeword results in another codeword. These are based on polynomials whose elements are coefficients from
B. Cyclic Codes A cyclic code is a linear block code with the further property that a shift of a codeword results in another codeword. These are based on polynomials whose elements are coefficients from
Error Detection & Correction
 Error Detection & Correction Error detection & correction noisy channels techniques in networking error detection error detection capability retransmition error correction reconstruction checksums redundancy
Error Detection & Correction Error detection & correction noisy channels techniques in networking error detection error detection capability retransmition error correction reconstruction checksums redundancy
EECS150 - Digital Design Lecture 23 - FFs revisited, FIFOs, ECCs, LSFRs. Cross-coupled NOR gates
 EECS150 - Digital Design Lecture 23 - FFs revisited, FIFOs, ECCs, LSFRs April 16, 2009 John Wawrzynek Spring 2009 EECS150 - Lec24-blocks Page 1 Cross-coupled NOR gates remember, If both R=0 & S=0, then
EECS150 - Digital Design Lecture 23 - FFs revisited, FIFOs, ECCs, LSFRs April 16, 2009 John Wawrzynek Spring 2009 EECS150 - Lec24-blocks Page 1 Cross-coupled NOR gates remember, If both R=0 & S=0, then
Math 512 Syllabus Spring 2017, LIU Post
 Week Class Date Material Math 512 Syllabus Spring 2017, LIU Post 1 1/23 ISBN, error-detecting codes HW: Exercises 1.1, 1.3, 1.5, 1.8, 1.14, 1.15 If x, y satisfy ISBN-10 check, then so does x + y. 2 1/30
Week Class Date Material Math 512 Syllabus Spring 2017, LIU Post 1 1/23 ISBN, error-detecting codes HW: Exercises 1.1, 1.3, 1.5, 1.8, 1.14, 1.15 If x, y satisfy ISBN-10 check, then so does x + y. 2 1/30
A Brief Encounter with Linear Codes
 Boise State University ScholarWorks Mathematics Undergraduate Theses Department of Mathematics 8-2014 A Brief Encounter with Linear Codes Brent El-Bakri Boise State University, brentelbakri@boisestate.edu
Boise State University ScholarWorks Mathematics Undergraduate Theses Department of Mathematics 8-2014 A Brief Encounter with Linear Codes Brent El-Bakri Boise State University, brentelbakri@boisestate.edu
Iterative Encoding of Low-Density Parity-Check Codes
 Iterative Encoding of Low-Density Parity-Check Codes David Haley, Alex Grant and John Buetefuer Institute for Telecommunications Research University of South Australia Mawson Lakes Blvd Mawson Lakes SA
Iterative Encoding of Low-Density Parity-Check Codes David Haley, Alex Grant and John Buetefuer Institute for Telecommunications Research University of South Australia Mawson Lakes Blvd Mawson Lakes SA
MATH3302 Coding Theory Problem Set The following ISBN was received with a smudge. What is the missing digit? x9139 9
 Problem Set 1 These questions are based on the material in Section 1: Introduction to coding theory. You do not need to submit your answers to any of these questions. 1. The following ISBN was received
Problem Set 1 These questions are based on the material in Section 1: Introduction to coding theory. You do not need to submit your answers to any of these questions. 1. The following ISBN was received
Outline. EECS Components and Design Techniques for Digital Systems. Lec 18 Error Coding. In the real world. Our beautiful digital world.
 Outline EECS 150 - Components and esign Techniques for igital Systems Lec 18 Error Coding Errors and error models Parity and Hamming Codes (SECE) Errors in Communications LFSRs Cyclic Redundancy Check
Outline EECS 150 - Components and esign Techniques for igital Systems Lec 18 Error Coding Errors and error models Parity and Hamming Codes (SECE) Errors in Communications LFSRs Cyclic Redundancy Check
Linear Cyclic Codes. Polynomial Word 1 + x + x x 4 + x 5 + x x + x f(x) = q(x)h(x) + r(x),
 Coding Theory Massoud Malek Linear Cyclic Codes Polynomial and Words A polynomial of degree n over IK is a polynomial p(x) = a 0 + a 1 + + a n 1 x n 1 + a n x n, where the coefficients a 1, a 2,, a n are
Coding Theory Massoud Malek Linear Cyclic Codes Polynomial and Words A polynomial of degree n over IK is a polynomial p(x) = a 0 + a 1 + + a n 1 x n 1 + a n x n, where the coefficients a 1, a 2,, a n are
Optimum Soft Decision Decoding of Linear Block Codes
 Optimum Soft Decision Decoding of Linear Block Codes {m i } Channel encoder C=(C n-1,,c 0 ) BPSK S(t) (n,k,d) linear modulator block code Optimal receiver AWGN Assume that [n,k,d] linear block code C is
Optimum Soft Decision Decoding of Linear Block Codes {m i } Channel encoder C=(C n-1,,c 0 ) BPSK S(t) (n,k,d) linear modulator block code Optimal receiver AWGN Assume that [n,k,d] linear block code C is
Vector spaces. EE 387, Notes 8, Handout #12
 Vector spaces EE 387, Notes 8, Handout #12 A vector space V of vectors over a field F of scalars is a set with a binary operator + on V and a scalar-vector product satisfying these axioms: 1. (V, +) is
Vector spaces EE 387, Notes 8, Handout #12 A vector space V of vectors over a field F of scalars is a set with a binary operator + on V and a scalar-vector product satisfying these axioms: 1. (V, +) is
Lecture 3: Error Correcting Codes
 CS 880: Pseudorandomness and Derandomization 1/30/2013 Lecture 3: Error Correcting Codes Instructors: Holger Dell and Dieter van Melkebeek Scribe: Xi Wu In this lecture we review some background on error
CS 880: Pseudorandomness and Derandomization 1/30/2013 Lecture 3: Error Correcting Codes Instructors: Holger Dell and Dieter van Melkebeek Scribe: Xi Wu In this lecture we review some background on error
Turbo Codes are Low Density Parity Check Codes
 Turbo Codes are Low Density Parity Check Codes David J. C. MacKay July 5, 00 Draft 0., not for distribution! (First draft written July 5, 998) Abstract Turbo codes and Gallager codes (also known as low
Turbo Codes are Low Density Parity Check Codes David J. C. MacKay July 5, 00 Draft 0., not for distribution! (First draft written July 5, 998) Abstract Turbo codes and Gallager codes (also known as low
Linear Algebra II. 2 Matrices. Notes 2 21st October Matrix algebra
 MTH6140 Linear Algebra II Notes 2 21st October 2010 2 Matrices You have certainly seen matrices before; indeed, we met some in the first chapter of the notes Here we revise matrix algebra, consider row
MTH6140 Linear Algebra II Notes 2 21st October 2010 2 Matrices You have certainly seen matrices before; indeed, we met some in the first chapter of the notes Here we revise matrix algebra, consider row
Outline. MSRI-UP 2009 Coding Theory Seminar, Week 2. The definition. Link to polynomials
 Outline MSRI-UP 2009 Coding Theory Seminar, Week 2 John B. Little Department of Mathematics and Computer Science College of the Holy Cross Cyclic Codes Polynomial Algebra More on cyclic codes Finite fields
Outline MSRI-UP 2009 Coding Theory Seminar, Week 2 John B. Little Department of Mathematics and Computer Science College of the Holy Cross Cyclic Codes Polynomial Algebra More on cyclic codes Finite fields
Low-density parity-check (LDPC) codes
 Low-density parity-check (LDPC) codes Performance similar to turbo codes Do not require long interleaver to achieve good performance Better block error performance Error floor occurs at lower BER Decoding
Low-density parity-check (LDPC) codes Performance similar to turbo codes Do not require long interleaver to achieve good performance Better block error performance Error floor occurs at lower BER Decoding
Part 1: Digital Logic and Gates. Analog vs. Digital waveforms. The digital advantage. In real life...
 Part 1: Digital Logic and Gates Analog vs Digital waveforms An analog signal assumes a continuous range of values: v(t) ANALOG A digital signal assumes discrete (isolated, separate) values Usually there
Part 1: Digital Logic and Gates Analog vs Digital waveforms An analog signal assumes a continuous range of values: v(t) ANALOG A digital signal assumes discrete (isolated, separate) values Usually there
Notes 10: Public-key cryptography
 MTH6115 Cryptography Notes 10: Public-key cryptography In this section we look at two other schemes that have been proposed for publickey ciphers. The first is interesting because it was the earliest such
MTH6115 Cryptography Notes 10: Public-key cryptography In this section we look at two other schemes that have been proposed for publickey ciphers. The first is interesting because it was the earliest such
Solutions of Exam Coding Theory (2MMC30), 23 June (1.a) Consider the 4 4 matrices as words in F 16
 Solutions of Exam Coding Theory (2MMC30), 23 June 2016 (1.a) Consider the 4 4 matrices as words in F 16 2, the binary vector space of dimension 16. C is the code of all binary 4 4 matrices such that the
Solutions of Exam Coding Theory (2MMC30), 23 June 2016 (1.a) Consider the 4 4 matrices as words in F 16 2, the binary vector space of dimension 16. C is the code of all binary 4 4 matrices such that the
EECS150 - Digital Design Lecture 27 - misc2
 EECS150 - Digital Design Lecture 27 - misc2 May 1, 2002 John Wawrzynek Spring 2002 EECS150 - Lec27-misc2 Page 1 Outline Linear Feedback Shift Registers Theory and practice Simple hardware division algorithms
EECS150 - Digital Design Lecture 27 - misc2 May 1, 2002 John Wawrzynek Spring 2002 EECS150 - Lec27-misc2 Page 1 Outline Linear Feedback Shift Registers Theory and practice Simple hardware division algorithms
Lecture 4 : Introduction to Low-density Parity-check Codes
 Lecture 4 : Introduction to Low-density Parity-check Codes LDPC codes are a class of linear block codes with implementable decoders, which provide near-capacity performance. History: 1. LDPC codes were
Lecture 4 : Introduction to Low-density Parity-check Codes LDPC codes are a class of linear block codes with implementable decoders, which provide near-capacity performance. History: 1. LDPC codes were
Objective: To become acquainted with the basic concepts of cyclic codes and some aspects of encoder implementations for them.
 ECE 7670 Lecture 5 Cyclic codes Objective: To become acquainted with the basic concepts of cyclic codes and some aspects of encoder implementations for them. Reading: Chapter 5. 1 Cyclic codes Definition
ECE 7670 Lecture 5 Cyclic codes Objective: To become acquainted with the basic concepts of cyclic codes and some aspects of encoder implementations for them. Reading: Chapter 5. 1 Cyclic codes Definition
Low-density parity-check codes
 Low-density parity-check codes From principles to practice Dr. Steve Weller steven.weller@newcastle.edu.au School of Electrical Engineering and Computer Science The University of Newcastle, Callaghan,
Low-density parity-check codes From principles to practice Dr. Steve Weller steven.weller@newcastle.edu.au School of Electrical Engineering and Computer Science The University of Newcastle, Callaghan,
Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Discussion 6A Solution
 CS 70 Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Discussion 6A Solution 1. Polynomial intersections Find (and prove) an upper-bound on the number of times two distinct degree
CS 70 Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Discussion 6A Solution 1. Polynomial intersections Find (and prove) an upper-bound on the number of times two distinct degree
Optimization of the Hamming Code for Error Prone Media
 278 IJCSNS International Journal of Computer Science and Network Security, VOL.8 No.3, March 2008 Optimization of the Hamming Code for Error Prone Media Eltayeb S. Abuelyaman and Abdul-Aziz S. Al-Sehibani
278 IJCSNS International Journal of Computer Science and Network Security, VOL.8 No.3, March 2008 Optimization of the Hamming Code for Error Prone Media Eltayeb S. Abuelyaman and Abdul-Aziz S. Al-Sehibani
Graph-based codes for flash memory
 1/28 Graph-based codes for flash memory Discrete Mathematics Seminar September 3, 2013 Katie Haymaker Joint work with Professor Christine Kelley University of Nebraska-Lincoln 2/28 Outline 1 Background
1/28 Graph-based codes for flash memory Discrete Mathematics Seminar September 3, 2013 Katie Haymaker Joint work with Professor Christine Kelley University of Nebraska-Lincoln 2/28 Outline 1 Background
Coding Theory and Applications. Solved Exercises and Problems of Cyclic Codes. Enes Pasalic University of Primorska Koper, 2013
 Coding Theory and Applications Solved Exercises and Problems of Cyclic Codes Enes Pasalic University of Primorska Koper, 2013 Contents 1 Preface 3 2 Problems 4 2 1 Preface This is a collection of solved
Coding Theory and Applications Solved Exercises and Problems of Cyclic Codes Enes Pasalic University of Primorska Koper, 2013 Contents 1 Preface 3 2 Problems 4 2 1 Preface This is a collection of solved
EE 229B ERROR CONTROL CODING Spring 2005
 EE 229B ERROR CONTROL CODING Spring 2005 Solutions for Homework 1 1. Is there room? Prove or disprove : There is a (12,7) binary linear code with d min = 5. If there were a (12,7) binary linear code with
EE 229B ERROR CONTROL CODING Spring 2005 Solutions for Homework 1 1. Is there room? Prove or disprove : There is a (12,7) binary linear code with d min = 5. If there were a (12,7) binary linear code with
Mathematics Department
 Mathematics Department Matthew Pressland Room 7.355 V57 WT 27/8 Advanced Higher Mathematics for INFOTECH Exercise Sheet 2. Let C F 6 3 be the linear code defined by the generator matrix G = 2 2 (a) Find
Mathematics Department Matthew Pressland Room 7.355 V57 WT 27/8 Advanced Higher Mathematics for INFOTECH Exercise Sheet 2. Let C F 6 3 be the linear code defined by the generator matrix G = 2 2 (a) Find
Chapter 6 Reed-Solomon Codes. 6.1 Finite Field Algebra 6.2 Reed-Solomon Codes 6.3 Syndrome Based Decoding 6.4 Curve-Fitting Based Decoding
 Chapter 6 Reed-Solomon Codes 6. Finite Field Algebra 6. Reed-Solomon Codes 6.3 Syndrome Based Decoding 6.4 Curve-Fitting Based Decoding 6. Finite Field Algebra Nonbinary codes: message and codeword symbols
Chapter 6 Reed-Solomon Codes 6. Finite Field Algebra 6. Reed-Solomon Codes 6.3 Syndrome Based Decoding 6.4 Curve-Fitting Based Decoding 6. Finite Field Algebra Nonbinary codes: message and codeword symbols
Construction of LDPC codes
 Construction of LDPC codes Telecommunications Laboratory Alex Balatsoukas-Stimming Technical University of Crete July 1, 2009 Telecommunications Laboratory (TUC) Construction of LDPC codes July 1, 2009
Construction of LDPC codes Telecommunications Laboratory Alex Balatsoukas-Stimming Technical University of Crete July 1, 2009 Telecommunications Laboratory (TUC) Construction of LDPC codes July 1, 2009
EE512: Error Control Coding
 EE512: Error Control Coding Solution for Assignment on Cyclic Codes March 22, 2007 1. A cyclic code, C, is an ideal genarated by its minimal degree polynomial, g(x). C = < g(x) >, = {m(x)g(x) : m(x) is
EE512: Error Control Coding Solution for Assignment on Cyclic Codes March 22, 2007 1. A cyclic code, C, is an ideal genarated by its minimal degree polynomial, g(x). C = < g(x) >, = {m(x)g(x) : m(x) is
And for polynomials with coefficients in F 2 = Z/2 Euclidean algorithm for gcd s Concept of equality mod M(x) Extended Euclid for inverses mod M(x)
 Outline Recall: For integers Euclidean algorithm for finding gcd s Extended Euclid for finding multiplicative inverses Extended Euclid for computing Sun-Ze Test for primitive roots And for polynomials
Outline Recall: For integers Euclidean algorithm for finding gcd s Extended Euclid for finding multiplicative inverses Extended Euclid for computing Sun-Ze Test for primitive roots And for polynomials
IN this paper, we will introduce a new class of codes,
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 44, NO 5, SEPTEMBER 1998 1861 Subspace Subcodes of Reed Solomon Codes Masayuki Hattori, Member, IEEE, Robert J McEliece, Fellow, IEEE, and Gustave Solomon,
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 44, NO 5, SEPTEMBER 1998 1861 Subspace Subcodes of Reed Solomon Codes Masayuki Hattori, Member, IEEE, Robert J McEliece, Fellow, IEEE, and Gustave Solomon,
ECE8771 Information Theory & Coding for Digital Communications Villanova University ECE Department Prof. Kevin M. Buckley Lecture Set 2 Block Codes
 Kevin Buckley - 2010 109 ECE8771 Information Theory & Coding for Digital Communications Villanova University ECE Department Prof. Kevin M. Buckley Lecture Set 2 Block Codes m GF(2 ) adder m GF(2 ) multiplier
Kevin Buckley - 2010 109 ECE8771 Information Theory & Coding for Digital Communications Villanova University ECE Department Prof. Kevin M. Buckley Lecture Set 2 Block Codes m GF(2 ) adder m GF(2 ) multiplier
An Introduction to Low Density Parity Check (LDPC) Codes
 An Introduction to Low Density Parity Check (LDPC) Codes Jian Sun jian@csee.wvu.edu Wireless Communication Research Laboratory Lane Dept. of Comp. Sci. and Elec. Engr. West Virginia University June 3,
An Introduction to Low Density Parity Check (LDPC) Codes Jian Sun jian@csee.wvu.edu Wireless Communication Research Laboratory Lane Dept. of Comp. Sci. and Elec. Engr. West Virginia University June 3,
Efficient Decoding of Permutation Codes Obtained from Distance Preserving Maps
 2012 IEEE International Symposium on Information Theory Proceedings Efficient Decoding of Permutation Codes Obtained from Distance Preserving Maps Yeow Meng Chee and Punarbasu Purkayastha Division of Mathematical
2012 IEEE International Symposium on Information Theory Proceedings Efficient Decoding of Permutation Codes Obtained from Distance Preserving Maps Yeow Meng Chee and Punarbasu Purkayastha Division of Mathematical
Linear Systems. Carlo Tomasi
 Linear Systems Carlo Tomasi Section 1 characterizes the existence and multiplicity of the solutions of a linear system in terms of the four fundamental spaces associated with the system s matrix and of
Linear Systems Carlo Tomasi Section 1 characterizes the existence and multiplicity of the solutions of a linear system in terms of the four fundamental spaces associated with the system s matrix and of
Cyclic codes. Vahid Meghdadi Reference: Error Correction Coding by Todd K. Moon. February 2008
 Cyclic codes Vahid Meghdadi Reference: Error Correction Coding by Todd K. Moon February 2008 1 Definitions Definition 1. A ring < R, +,. > is a set R with two binary operation + (addition) and. (multiplication)
Cyclic codes Vahid Meghdadi Reference: Error Correction Coding by Todd K. Moon February 2008 1 Definitions Definition 1. A ring < R, +,. > is a set R with two binary operation + (addition) and. (multiplication)
 CS6304 / Analog and Digital Communication UNIT IV - SOURCE AND ERROR CONTROL CODING PART A 1. What is the use of error control coding? The main use of error control coding is to reduce the overall probability
CS6304 / Analog and Digital Communication UNIT IV - SOURCE AND ERROR CONTROL CODING PART A 1. What is the use of error control coding? The main use of error control coding is to reduce the overall probability
Cyclic Redundancy Check Codes
 Cyclic Redundancy Check Codes Lectures No. 17 and 18 Dr. Aoife Moloney School of Electronics and Communications Dublin Institute of Technology Overview These lectures will look at the following: Cyclic
Cyclic Redundancy Check Codes Lectures No. 17 and 18 Dr. Aoife Moloney School of Electronics and Communications Dublin Institute of Technology Overview These lectures will look at the following: Cyclic
STUDY OF PERMUTATION MATRICES BASED LDPC CODE CONSTRUCTION
 EE229B PROJECT REPORT STUDY OF PERMUTATION MATRICES BASED LDPC CODE CONSTRUCTION Zhengya Zhang SID: 16827455 zyzhang@eecs.berkeley.edu 1 MOTIVATION Permutation matrices refer to the square matrices with
EE229B PROJECT REPORT STUDY OF PERMUTATION MATRICES BASED LDPC CODE CONSTRUCTION Zhengya Zhang SID: 16827455 zyzhang@eecs.berkeley.edu 1 MOTIVATION Permutation matrices refer to the square matrices with
Reed-Solomon codes. Chapter Linear codes over finite fields
 Chapter 8 Reed-Solomon codes In the previous chapter we discussed the properties of finite fields, and showed that there exists an essentially unique finite field F q with q = p m elements for any prime
Chapter 8 Reed-Solomon codes In the previous chapter we discussed the properties of finite fields, and showed that there exists an essentially unique finite field F q with q = p m elements for any prime
CHAPTER 7. Exercises 17/ / /2 2 0
 CHAPTER 7 Exercises E7. (a) For the whole part, we have: Quotient Remainders 23/2 /2 5 5/2 2 2/2 0 /2 0 Reading the remainders in reverse order, we obtain: 23 0 = 0 2 For the fractional part we have 2
CHAPTER 7 Exercises E7. (a) For the whole part, we have: Quotient Remainders 23/2 /2 5 5/2 2 2/2 0 /2 0 Reading the remainders in reverse order, we obtain: 23 0 = 0 2 For the fractional part we have 2
Punctured Convolutional Codes Revisited: the Exact State Diagram and Its Implications
 Punctured Convolutional Codes Revisited: the Exact State iagram and Its Implications Jing Li Tiffany) Erozan Kurtas epartment of Electrical and Computer Engineering Seagate Research Lehigh University Bethlehem
Punctured Convolutional Codes Revisited: the Exact State iagram and Its Implications Jing Li Tiffany) Erozan Kurtas epartment of Electrical and Computer Engineering Seagate Research Lehigh University Bethlehem
Lecture 12: November 6, 2017
 Information and Coding Theory Autumn 017 Lecturer: Madhur Tulsiani Lecture 1: November 6, 017 Recall: We were looking at codes of the form C : F k p F n p, where p is prime, k is the message length, and
Information and Coding Theory Autumn 017 Lecturer: Madhur Tulsiani Lecture 1: November 6, 017 Recall: We were looking at codes of the form C : F k p F n p, where p is prime, k is the message length, and
Combinational Logic. Mantıksal Tasarım BBM231. section instructor: Ufuk Çelikcan
 Combinational Logic Mantıksal Tasarım BBM23 section instructor: Ufuk Çelikcan Classification. Combinational no memory outputs depends on only the present inputs expressed by Boolean functions 2. Sequential
Combinational Logic Mantıksal Tasarım BBM23 section instructor: Ufuk Çelikcan Classification. Combinational no memory outputs depends on only the present inputs expressed by Boolean functions 2. Sequential
Computer Science 324 Computer Architecture Mount Holyoke College Fall Topic Notes: Digital Logic
 Computer Science 324 Computer Architecture Mount Holyoke College Fall 2007 Topic Notes: Digital Logic Our goal for the next few weeks is to paint a a reasonably complete picture of how we can go from transistor
Computer Science 324 Computer Architecture Mount Holyoke College Fall 2007 Topic Notes: Digital Logic Our goal for the next few weeks is to paint a a reasonably complete picture of how we can go from transistor
VHDL Implementation of Reed Solomon Improved Encoding Algorithm
 VHDL Implementation of Reed Solomon Improved Encoding Algorithm P.Ravi Tej 1, Smt.K.Jhansi Rani 2 1 Project Associate, Department of ECE, UCEK, JNTUK, Kakinada A.P. 2 Assistant Professor, Department of
VHDL Implementation of Reed Solomon Improved Encoding Algorithm P.Ravi Tej 1, Smt.K.Jhansi Rani 2 1 Project Associate, Department of ECE, UCEK, JNTUK, Kakinada A.P. 2 Assistant Professor, Department of
Dr. Cathy Liu Dr. Michael Steinberger. A Brief Tour of FEC for Serial Link Systems
 Prof. Shu Lin Dr. Cathy Liu Dr. Michael Steinberger U.C.Davis Avago SiSoft A Brief Tour of FEC for Serial Link Systems Outline Introduction Finite Fields and Vector Spaces Linear Block Codes Cyclic Codes
Prof. Shu Lin Dr. Cathy Liu Dr. Michael Steinberger U.C.Davis Avago SiSoft A Brief Tour of FEC for Serial Link Systems Outline Introduction Finite Fields and Vector Spaces Linear Block Codes Cyclic Codes
Optimization of the Hamming Code for Error Prone Media
 Optimization of the Hamming Code for Error Prone Media Eltayeb Abuelyaman and Abdul-Aziz Al-Sehibani College of Computer and Information Sciences Prince Sultan University Abuelyaman@psu.edu.sa Summery
Optimization of the Hamming Code for Error Prone Media Eltayeb Abuelyaman and Abdul-Aziz Al-Sehibani College of Computer and Information Sciences Prince Sultan University Abuelyaman@psu.edu.sa Summery
Modular numbers and Error Correcting Codes. Introduction. Modular Arithmetic.
 Modular numbers and Error Correcting Codes Introduction Modular Arithmetic Finite fields n-space over a finite field Error correcting codes Exercises Introduction. Data transmission is not normally perfect;
Modular numbers and Error Correcting Codes Introduction Modular Arithmetic Finite fields n-space over a finite field Error correcting codes Exercises Introduction. Data transmission is not normally perfect;
Cyclic Codes. Saravanan Vijayakumaran August 26, Department of Electrical Engineering Indian Institute of Technology Bombay
 1 / 25 Cyclic Codes Saravanan Vijayakumaran sarva@ee.iitb.ac.in Department of Electrical Engineering Indian Institute of Technology Bombay August 26, 2014 2 / 25 Cyclic Codes Definition A cyclic shift
1 / 25 Cyclic Codes Saravanan Vijayakumaran sarva@ee.iitb.ac.in Department of Electrical Engineering Indian Institute of Technology Bombay August 26, 2014 2 / 25 Cyclic Codes Definition A cyclic shift
BASIC NOTIONS. x + y = 1 3, 3x 5y + z = A + 3B,C + 2D, DC are not defined. A + C =
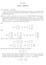 CHAPTER I BASIC NOTIONS (a) 8666 and 8833 (b) a =6,a =4 will work in the first case, but there are no possible such weightings to produce the second case, since Student and Student 3 have to end up with
CHAPTER I BASIC NOTIONS (a) 8666 and 8833 (b) a =6,a =4 will work in the first case, but there are no possible such weightings to produce the second case, since Student and Student 3 have to end up with
The E8 Lattice and Error Correction in Multi-Level Flash Memory
 The E8 Lattice and Error Correction in Multi-Level Flash Memory Brian M Kurkoski University of Electro-Communications Tokyo, Japan kurkoski@iceuecacjp Abstract A construction using the E8 lattice and Reed-Solomon
The E8 Lattice and Error Correction in Multi-Level Flash Memory Brian M Kurkoski University of Electro-Communications Tokyo, Japan kurkoski@iceuecacjp Abstract A construction using the E8 lattice and Reed-Solomon
4 ORTHOGONALITY ORTHOGONALITY OF THE FOUR SUBSPACES 4.1
 4 ORTHOGONALITY ORTHOGONALITY OF THE FOUR SUBSPACES 4.1 Two vectors are orthogonal when their dot product is zero: v w = orv T w =. This chapter moves up a level, from orthogonal vectors to orthogonal
4 ORTHOGONALITY ORTHOGONALITY OF THE FOUR SUBSPACES 4.1 Two vectors are orthogonal when their dot product is zero: v w = orv T w =. This chapter moves up a level, from orthogonal vectors to orthogonal
Chapter 2. Error Correcting Codes. 2.1 Basic Notions
 Chapter 2 Error Correcting Codes The identification number schemes we discussed in the previous chapter give us the ability to determine if an error has been made in recording or transmitting information.
Chapter 2 Error Correcting Codes The identification number schemes we discussed in the previous chapter give us the ability to determine if an error has been made in recording or transmitting information.
A SHORT SUMMARY OF VECTOR SPACES AND MATRICES
 A SHORT SUMMARY OF VECTOR SPACES AND MATRICES This is a little summary of some of the essential points of linear algebra we have covered so far. If you have followed the course so far you should have no
A SHORT SUMMARY OF VECTOR SPACES AND MATRICES This is a little summary of some of the essential points of linear algebra we have covered so far. If you have followed the course so far you should have no
1.6: Solutions 17. Solution to exercise 1.6 (p.13).
 1.6: Solutions 17 A slightly more careful answer (short of explicit computation) goes as follows. Taking the approximation for ( N K) to the next order, we find: ( N N/2 ) 2 N 1 2πN/4. (1.40) This approximation
1.6: Solutions 17 A slightly more careful answer (short of explicit computation) goes as follows. Taking the approximation for ( N K) to the next order, we find: ( N N/2 ) 2 N 1 2πN/4. (1.40) This approximation
MAT2342 : Introduction to Applied Linear Algebra Mike Newman, fall Projections. introduction
 MAT4 : Introduction to Applied Linear Algebra Mike Newman fall 7 9. Projections introduction One reason to consider projections is to understand approximate solutions to linear systems. A common example
MAT4 : Introduction to Applied Linear Algebra Mike Newman fall 7 9. Projections introduction One reason to consider projections is to understand approximate solutions to linear systems. A common example
Coding for loss tolerant systems
 Coding for loss tolerant systems Workshop APRETAF, 22 janvier 2009 Mathieu Cunche, Vincent Roca INRIA, équipe Planète INRIA Rhône-Alpes Mathieu Cunche, Vincent Roca The erasure channel Erasure codes Reed-Solomon
Coding for loss tolerant systems Workshop APRETAF, 22 janvier 2009 Mathieu Cunche, Vincent Roca INRIA, équipe Planète INRIA Rhône-Alpes Mathieu Cunche, Vincent Roca The erasure channel Erasure codes Reed-Solomon
EECS150 - Digital Design Lecture 26 Error Correction Codes, Linear Feedback Shift Registers (LFSRs)
 EECS150 - igital esign Lecture 26 Error Correction Codes, Linear Feedback Shift Registers (LFSRs) Nov 21, 2002 John Wawrzynek Fall 2002 EECS150 Lec26-ECC Page 1 Outline Error detection using parity Hamming
EECS150 - igital esign Lecture 26 Error Correction Codes, Linear Feedback Shift Registers (LFSRs) Nov 21, 2002 John Wawrzynek Fall 2002 EECS150 Lec26-ECC Page 1 Outline Error detection using parity Hamming
CSCI3390-Assignment 2 Solutions
 CSCI3390-Assignment 2 Solutions due February 3, 2016 1 TMs for Deciding Languages Write the specification of a Turing machine recognizing one of the following three languages. Do one of these problems.
CSCI3390-Assignment 2 Solutions due February 3, 2016 1 TMs for Deciding Languages Write the specification of a Turing machine recognizing one of the following three languages. Do one of these problems.
Guess & Check Codes for Deletions, Insertions, and Synchronization
 Guess & Chec Codes for Deletions, Insertions, and Synchronization Serge Kas Hanna, Salim El Rouayheb ECE Department, IIT, Chicago sashann@hawiitedu, salim@iitedu Abstract We consider the problem of constructing
Guess & Chec Codes for Deletions, Insertions, and Synchronization Serge Kas Hanna, Salim El Rouayheb ECE Department, IIT, Chicago sashann@hawiitedu, salim@iitedu Abstract We consider the problem of constructing
EECS150 - Digital Design Lecture 26 - Faults and Error Correction. Types of Faults in Digital Designs
 EECS150 - Digital Design Lecture 26 - Faults and Error Correction April 25, 2013 John Wawrzynek 1 Types of Faults in Digital Designs Design Bugs (function, timing, power draw) detected and corrected at
EECS150 - Digital Design Lecture 26 - Faults and Error Correction April 25, 2013 John Wawrzynek 1 Types of Faults in Digital Designs Design Bugs (function, timing, power draw) detected and corrected at
EECS Components and Design Techniques for Digital Systems. Lec 26 CRCs, LFSRs (and a little power)
 EECS 150 - Components and esign Techniques for igital Systems Lec 26 CRCs, LFSRs (and a little power) avid Culler Electrical Engineering and Computer Sciences University of California, Berkeley http://www.eecs.berkeley.edu/~culler
EECS 150 - Components and esign Techniques for igital Systems Lec 26 CRCs, LFSRs (and a little power) avid Culler Electrical Engineering and Computer Sciences University of California, Berkeley http://www.eecs.berkeley.edu/~culler
Proof: Let the check matrix be
 Review/Outline Recall: Looking for good codes High info rate vs. high min distance Want simple description, too Linear, even cyclic, plausible Gilbert-Varshamov bound for linear codes Check matrix criterion
Review/Outline Recall: Looking for good codes High info rate vs. high min distance Want simple description, too Linear, even cyclic, plausible Gilbert-Varshamov bound for linear codes Check matrix criterion
MT5821 Advanced Combinatorics
 MT5821 Advanced Combinatorics 1 Error-correcting codes In this section of the notes, we have a quick look at coding theory. After a motivating introduction, we discuss the weight enumerator of a code,
MT5821 Advanced Combinatorics 1 Error-correcting codes In this section of the notes, we have a quick look at coding theory. After a motivating introduction, we discuss the weight enumerator of a code,
Introducing Low-Density Parity-Check Codes
 Introducing Low-Density Parity-Check Codes Sarah J. Johnson School of Electrical Engineering and Computer Science The University of Newcastle Australia email: sarah.johnson@newcastle.edu.au Topic 1: Low-Density
Introducing Low-Density Parity-Check Codes Sarah J. Johnson School of Electrical Engineering and Computer Science The University of Newcastle Australia email: sarah.johnson@newcastle.edu.au Topic 1: Low-Density
Error Detection, Correction and Erasure Codes for Implementation in a Cluster File-system
 Error Detection, Correction and Erasure Codes for Implementation in a Cluster File-system Steve Baker December 6, 2011 Abstract. The evaluation of various error detection and correction algorithms and
Error Detection, Correction and Erasure Codes for Implementation in a Cluster File-system Steve Baker December 6, 2011 Abstract. The evaluation of various error detection and correction algorithms and
A Proposed Quantum Low Density Parity Check Code
 arxiv:quant-ph/83v 29 Aug 2 A Proposed Quantum Low Density Parity Check Code Michael S. Postol National Security Agency 98 Savage Road Fort Meade, MD 2755 Email: msposto@zombie.ncsc.mil June 3, 28 2 LOW
arxiv:quant-ph/83v 29 Aug 2 A Proposed Quantum Low Density Parity Check Code Michael S. Postol National Security Agency 98 Savage Road Fort Meade, MD 2755 Email: msposto@zombie.ncsc.mil June 3, 28 2 LOW
Polynomial Codes over Certain Finite Fields
 Polynomial Codes over Certain Finite Fields A paper by: Irving Reed and Gustave Solomon presented by Kim Hamilton March 31, 2000 Significance of this paper: Introduced ideas that form the core of current
Polynomial Codes over Certain Finite Fields A paper by: Irving Reed and Gustave Solomon presented by Kim Hamilton March 31, 2000 Significance of this paper: Introduced ideas that form the core of current
