CONTINUOUS phase modulation (CPM) [1] is a
|
|
|
- Gillian Baker
- 6 years ago
- Views:
Transcription
1 1 Timing, Carrier, and Frame Synchronization of Burst-Mode CPM Ehsan Hosseini, Student Member, IEEE, and Erik Perrins, Senior Member, IEEE arxiv: v3 [cs.it] 3 Jan 1 Abstract In this paper, we propose a complete synchronization algorithm for continuous phase modulation (CPM) signals in burst-mode transmission over additive white Gaussian noise (AWGN) channels. The timing and carrier recovery are performed through a data-aided (DA) maximum likelihood algorithm, which jointly estimates symbol timing, carrier phase, and frequency offsets based on an optimized synchronization preamble. Our algorithm estimates the frequency offset via a one-dimensional grid search, after which symbol timing and carrier phase are computed via simple closed-form expressions. The mean-square error (MSE) of the algorithm s estimates reveals that it performs very close to the theoretical Cramér- Rao bound (CRB) for various CPMs at signal-to-noise ratios (SNRs) as low as db. Furthermore, we present a frame synchronization algorithm that detects the arrival of bursts and estimates the start-of-signal. We simulate the performance of the frame synchronization algorithm along with the timing and carrier recovery algorithm. The bit error rate results demonstrate near ideal synchronization performance for low SNRs and short preambles. Index Terms Continuous Phase Modulation, Estimation Theory, Synchronization. I. INTRODUCTION CONTINUOUS phase modulation (CPM) [1] is a highly bandwidth and power-efficient digital transmission scheme, which allows designers to employ non-linear power amplifiers. It has been an attractive choice for timedivision multiple-access (TDMA) networks where data or voice is transmitted in a burst-mode fashion. Examples of such systems are the well-known GSM cellular standard [] and the next generation aeronautical telemetry standard [3]. Despite the attractive features of CPM, the receiver complexity is high due to the inherent memory of the modulation, and it requires maximum likelihood sequence detection (MLSD) for the best performance []. Another source of receiver complexity is the synchronization task, especially in burst-mode transmissions where the This paper will be presented in part at the IEEE Global Telecommunications Conference, Atlanta, Georgia, USA, December 13. E. Hosseini and E. Perrins are with the Department of Electrical Engineering and Computer Science, University of Kansas, Lawrence, KS 665 USA ( ehsan@ku.edu, esp@ieee.org). Copyright 13 IEEE. Personal use of this material is permitted. However, permission to reprint/republish this material for advertising or promotional purposes or for creating new collective works for resale or redistribution to servers or lists, or to reuse any copyrighted component of this work in other works must be obtained from the IEEE. Published in: Ehsan Hosseini and Erik Perrins, Timing, Carrier, and Frame Synchronization of Burst-Mode CPM, IEEE Transactions on Communications, vol.61, no.1, pp , December 13 DOI: 1.119/TCOMM URL: &isnumber= warm-up or acquisition time must be kept as small as possible. This task has become even more challenging due to the introduction of powerful error correction codes such as lowdensity parity check (LDPC) codes, which require accurate synchronization at low signal-to-noise ratios (SNRs) in order to achieve the full coding gain. Feedforward synchronization is a common approach in this type of application since it requires a shorter acquisition time compared to closed-loop methods [5]. Moreover, a known synchronization preamble is usually appended to the beginning of each burst, which assists the synchronization via data-aided (DA) algorithms. The majority of works on synchronization of CPM in burstmode transmissions have addressed minimum-shift keying (MSK)-type modulations using non-data-aided (NDA) algorithms, e.g. [6] [8]. In addition to their limited application, these methods do not perform as well as DA algorithms in low SNRs. Huang et al. [9] have proposed a feedforward DA joint symbol timing and frequency offset estimation algorithm for Gaussian MSK (GMSK) signals. The performance of this ad-hoc method relies on the amount of frequency offset and sample timing error. A feedforward NDA symbol timing estimation is presented in [1], which can work for general CPMs in principle. However, its performance degrades in case of partial response schemes. A few DA synchronization algorithms have been presented in the literature for general CPM signals in different environments [11] [1]. Huber and Liu [11] proposed a maximum likelihood (ML) joint timing and phase synchronization algorithm for additive white Gaussian noise (AWGN) channels. In a related work [1], the Walsh transform is used in order to derive the synchronization algorithm. Both of these algorithms assume the timing offset is much smaller than the symbol duration in order to function properly. This limits their application in burst-mode feedforward receivers as the timing offset in practice can have any arbitrary value. Another DA joint phase and timing estimation algorithm is proposed in [13], which is based on the minimum mean-square error (MMSE) and Kalman filter criteria. Despite its robustness in time-variant channels and short preambles, this method is implemented in a closed-loop manner which requires multiple initialization steps. Moreover, its meansquare error (MSE) is shown to be significantly larger than the Cramér-Rao bound (CRB) even at high SNRs. Another DA algorithm is proposed in [1] for space-time coded CPM over Rayleigh channels, which only tackles the symbol timing estimation. One important issue with all the aforementioned DA algorithms is that the carrier frequency offset has not been taken into account. Blind frequency estimators such as [15], [16] can be employed prior to symbol timing and phase estimations. However, the accuracy of these frequency
2 estimators is far above the CRB [15] especially in low to moderate SNRs [16]. Residual frequency offsets result in poor timing and phase estimators as well as signal demodulation. Another challenge in synchronization of burst-mode signals is estimation of the burst start point, i.e. start-of-signal (SoS). This task, which will be referred to as frame synchronization, is crucial in DA algorithms where the boundaries of the known preamble have to be identified. Several sophisticated frame synchronization algorithms [17] [19] have been proposed for phase shift-keying (PSK) signals in AWGN where frequency offset is present. The performance of the algorithm in [17] depends on the amount of frequency offset, which has to be much smaller than the symbol rate. Choi and Lee [18] have assumed continuous transmissions, where the preamble is surrounded by random data. Although burst-mode transmission is introduced in [19], the authors have assumed there is no guard interval between bursts and the preamble is preceded by random data (similar to the continuous mode). Moreover, it assumes the tentative location of the preamble is known within an uncertainty window. Such a knowledge might not be always available particularly when the receiver is just powered on. In this work, we present a feedforward DA ML algorithm for joint estimation of frequency offset, symbol timing, and carrier phase in burst-mode CPM signals. The proposed approach takes advantage of the optimized preamble of [], which jointly minimizes the CRBs for all three synchronization parameters. We show that the proposed algorithm is capable of performing quite close to the CRB for various CPMs and SNRs. Although we consider an AWGN channel, the results can be applied to time-varying channels too since practical wireless channels can be assumed to be static during the preamble period. In such environments, the estimation results should be used in conjunction with tracking algorithms such as [1]. Additionally, we present a frame synchronization algorithm that detects the arrival of bursts and estimates the SoS within ideally one sample time. We discuss how our approach extends the frame synchronization algorithms in [17], [18] to our problem, i.e. CPM signals and burst-mode transmissions. We note that the order in which these two problems are addressed in this paper is the reverse of their implementation in practice where frame synchronization must be applied prior to timing and carrier recovery. The remainder of this paper is organized as follows. Section II introduces our burst-mode transmission model. In Section III, the joint ML timing and carrier estimation is proposed. Section IV describes the frame synchronization algorithm. Simulation results of the synchronization algorithm are reported in Section V, and Section VI concludes the paper. II. BURST-MODE TRANSMISSION MODEL In our model, we consider transmission of disjoint packets of data, i.e. bursts. The transmitter is assumed to be turned on at an unknown time in order to transmit a single burst after which it is turned off again. Each burst has a known duration and structure at the receiver, which is depicted in Fig. 1 and consists of three parts. The first part is the synchronization preamble or training sequence. It consists of Guard Interval Preamble UW Payload Guard Interval Fig. 1: The Burst-Mode Transmission Model. L known and optimized data symbols which are used to estimate synchronization parameters. Although the preamble can be used for channel estimation too, we only focus on the synchronization task. The next section in the burst is denoted as the unique word (UW), which is utilized to identify the bursts and determine the location of data symbols within a burst. It is assumed to be a pseudo-random sequence of L UW symbols. The last part is the payload, which carries L pay information symbols. We consider CPM signaling for transmission of bursts in our model. The complex baseband CPM signal during transmission of each burst can be expressed as Es s(t) = expjφ(t; α)} (1) T s where E s is the energy per transmitted symbol. The phase of the signal φ(t; α) is represented as L b 1 φ(t; α) = πh α i q(t it s ) () i= where α i is the sequence of M-ary data symbols selected from the set of ±1, ±3,..., ±(M 1)}. L b is the total number of such symbols in a burst, that is L b = L + L uw + L pay. The variable h is the modulation index, which can vary from symbol to symbol in the case of multi-h CPM. The waveform q(t) is the phase response of CPM and in general is represented as the integral of the frequency pulse g(t) with a duration of LT s. If L = 1, the signal is called full response CPM, and for L > 1, it is called partial response CPM. In CPM literature, there are two well-known frequency pulses denoted by length L rectangular (LREC) and length L raised cosine (LRC) []. Another commonly-used frequency pulse is the Gaussian minimum-shift keying (GMSK) pulse with bandwidth parameter BT s. In our discussion, we will use BT s =.3, which is the bandwidth parameter in the GSM standard. Assuming transmission over an AWGN channel, the complex baseband representation of the received signal is r(t) = e j(πf dt+θ) s(t τ) + w(t) (3) where θ is the unknown carrier phase, f d is the frequency offset, τ is the timing offset, and w(t) is complex baseband AWGN with zero mean and power spectral density N. We denote the transmitted data symbols during the preamble by α = [α, α 1,, α L 1]. Our goal is to determine the synchronization parameters, i.e. u = [f d, θ, τ] T, by observing the preamble portion of the burst, which corresponds to α. Here, it is assumed that u is a vector of unknown but deterministic parameters which are to be jointly estimated at the receiver. Note that α is implicit in the definition of s(t). Since data arrives in bursts at the receiver, τ can assume any value. However, a DA estimator requires the approximate
3 3 1RC (M =,h = 1/) Unwrapped Phase π π Fig. : The optimum synchronization preamble (training sequence) for M-ary CPM signals containing L symbols. knowledge of τ in order to perform the estimation algorithm on the received preamble. Therefore, we decompose τ into two parts based on τ = µt s + εt s () where µ is an integer that represents the integer delay and.5 < ε <.5 represents the fractional delay. In this work, we address these two components separately. First we assume µ is known and the goal is to estimate ε, f d and θ. Later in Section IV, we consider estimation of µ, i.e. the SoS location, regardless of f d and θ values. The last item we need to specify is the synchronization preamble. In our recent work [], we proposed the optimum training sequence for joint estimation of u based on the CRB criterion. This sequence, which is depicted in Fig., minimizes the CRBs for f d, θ and ε simultaneously. It also has a similar pattern for the entire CPM family. We exploit the structure of the preamble in order to facilitate the algorithm design process and then to reduce its complexity. III. MAXIMUM LIKELIHOOD TIMING AND CARRIER SYNCHRONIZATION A. Derivation of the Algorithm Reliable detection of CPM signals depends on accurate timing and carrier synchronization, which requires knowledge of f d, θ and τ. These parameters can be estimated via various techniques. In this work, we apply joint ML estimation in which α is known to the receiver. The likelihood function for the estimation of a set of parameters from a waveform in AWGN is given in []. It can be easily shown that in our problem, i.e. when the signal is complex and constant envelope, the joint log-likelihood function (LLF) for the synchronization parameters is expressed within a constant factor of [ ] T+ εt Λ[r(t); f d, θ, s ε]=re e j(π fd t+ θ) r(t)s (t εt s ) dt εt s (5) where f d, θ and ε are hypothetical values for fd, θ and ε respectively, and T = L T s is the preamble duration. Note that we disregard µ in this section for the sake of clarity. According to the ML criterion, we choose the trial values that maximize (5) as the best estimates for the unknown parameters u. We denote the ML estimates as û = [ ˆf d, ˆθ, ˆτ] T. In practice, r(t) is sampled N times per symbol. This results in a discrete-time version of the LLF as [ NL 1 ] Λ(r; ν, θ, ε) Re e j(πn ν+ θ) r[n]s ε[n] (6) n= Unwrapped Phase Unwrapped Phase π π π π t/ts RC (M =,h = 1/) t/ts GMSK (BTs =.3,M =,h = 1/) t/ts Fig. 3: The phase response of different CPMs to the optimum training sequence (shown in solid lines). The dashed lines show the response of the same sequence to the 1REC CPM with the same h. where ν = f d T s /N, i.e. the normalized frequency offset with respect to the sampling frequency. r[n] and s ε [n] are the sampled versions of r(t) and s(t εt s ) at t = nt s /N respectively. Note that ε is assumed to be zero in the integral limits of (5) in order to derive (6). This is the main contributor to the approximation in the above given that the sampling frequency is large enough to avoid aliasing. Based on (6), the maximization of the LLF requires at least a two-dimensional grid search on ( ν, ε) in general because both of these parameters are embedded inside the above summation. Therefore, we are interested in a method that decouples ε and ν. We note that the preamble of Fig., regardless of its underlying CPM, can be divided into three parts, each of which having the same data symbols. This distinct pattern causes the CPM phase to change with a uniform rate of approximately πh(m 1) radians per symbol in the same direction for each part. We have illustrated this fact in Fig. 3 by plotting the unwrapped phase response of three different CPMs when preamble of Fig. with L = 16 is utilized. The first signal phase corresponds to the 1RC frequency pulse with binary data symbols and h = 1/. Additionally, the partial-response -ary RC CPM is provided in which h = 1/. The GMSK scheme with BT s =.3 is also included, which is binary, L = and h = 1/. We have compared each case with the phase response of 1REC frequency pulse to the same α and h. It is observed that despite the fundamental differences between their frequency pulses, the overall phase response of all CPM signals are approximately similar. More detailed observations can be made as the following: 1) GMSK and RC phase responses follow a straight line
4 within each part similar to the 1REC pulse shape in spite of their bell-shaped pulses. This is due to the overlap of the frequency pulses when the subsequent data symbols are the same, which leads to uniform phase variations. ) The overall phase response is delayed when partialresponse CPMs such as RC and GMSK are employed. We denote this lag time by T l which is equivalent to N l samples. 3) 1RC CPM shows the largest deviations from the 1REC phase response because its frequency pulse is full response (non-overlapping) and has the highest peak. Based on the above discussion, we approximate the phase response of any given CPM signal to the optimum preamble α with a delayed version of 1REC CPM to α and the same h. In fact, the optimum preamble enables us to accurately apply a piecewise linear approximation to the phase of CPM. Therefore, the approximated phase response can be mathematically expressed as (M 1)πh t T l T s T l < t T + T l φ(t, α (M 1)πh t T l T / T ) T s + T l < t 3T + T l (M 1)πh t T l T 3T T s + T l < t T + T l otherwise (7) where T l is fixed for a given CPM and is known to the receiver. In the Appendix, it is shown that T l = (L 1) T s for symmetric g(t), which is the case for rectangular, raised-cosine and Gaussian pulse shapes. In the rest of our discussion, we assume the channel observation starts from t = T l, and hence, we ignore T l. In practice, we can append T l /T s (M 1) symbols to the end of the preamble for partial-response CPMs in order to avoid unwanted variations at the end of the observation interval, which is now shifted by T l. Thus, we use (7) to express s ε [n] during the preamble transmission as exp[ j(m 1)πh( n N ε)] < n NL s ε [n] exp[+j(m 1)πh( n N L ε)] NL < n 3NL exp[ j(m 1)πh( n N L 3NL ε)] < n NL. (8) We take advantage of the above approximation in order to simplify the LLF and its maximization algorithm. Using (8) in (6) results in Λ (r; ν, θ, ε) Re e 3NL / n=nl / NL 1 n=3nl / j θ [NL/ 1 n= e jπ νn r[n]e j(m 1)πh(n/N ε) e jπ νn r[n]e j(m 1)πh(n/N L/ ε) e jπ νn r[n]e j(m 1)πh(n/N L ε)]} where Λ ( ) represents the joint LLF given α. It is evident from (9) that the symbol timing is now decoupled from the frequency offset and can be moved outside the summations of (9) the LLF. Hence, (9) can be simplified as Λ (r; ν, θ, ε) [ ] } Re e j θ e j(m 1)πh ε λ 1 ( ν) + e j(m 1)πh ε (1) λ ( ν) where NL / 1 λ 1 ( ν) = e jπ νn r[n]e j(m 1)πhn/N and n= NL 1 + e j(m 1)πhL e jπ νn r[n]e j(m 1)πhn/N n=3nl / (11) 3NL / 1 λ ( ν)= e j(m 1)πhL/ e jπ νn r[n]e j(m 1)πhn/N. n=nl / (1) As the estimation parameters are now decoupled, the maximization of the LLF becomes straightforward. Let us proceed by denoting the term in (1) which corresponds to symbol timing and frequency offset as Γ( ν, ε) = e j(m 1)πh ε λ 1 ( ν) + e j(m 1)πh ε λ ( ν). (13) It is easily seen that for any value of ( ν, ε), Λ ( ) is maximized by choosing θ such that it rotates Γ( ν, ε) towards the real axis, i.e., θ = argγ( ν, ε)}. (1) which reduces the LLF to Γ( ν, ε). Thus, the ML estimates of ν and ε are found by maximizing Γ( ν, ε) = λ 1 ( ν) + λ ( ν) +Re[e j(m 1)πh ε λ 1 ( ν)λ ( ν)] (15) with respect to ( ν, ε). The first two terms on the right-hand side of (15) do not depend on ε. Using a similar argument as θ, the third term is maximized by selecting ε according to ε = argλ 1( ν)λ ( ν)} (M 1)πh (16) so that the term inside the real part operator in (15) becomes purely real and equal to λ 1 ( ν)λ ( ν). Therefore, the maximization of the LLF is now a one-dimensional problem that results in the ML estimate of ν. This can be expressed mathematically in the form of ˆν = argmax X( ν) = λ 1 ( ν) + λ ( ν) } (17) ν which in turn leads to the ML estimates of the normalized symbol timing and phase offset via and ˆθ = arg respectively. ˆε = argλ 1(ˆν)λ (ˆν)} (M 1)πh (18) } e j(m 1)πhˆε λ 1 (ˆν) + e j(m 1)πhˆε λ (ˆν). (19)
5 5 B. Implementation of the Frequency Offset Estimator In the previous section, we derived simple closed-form expressions for estimation of phase and symbol timing. However, the frequency offset estimation requires computing the maximum of a one-dimensional function as defined in (17). λ 1 (ν) and λ (ν) have the form of Fourier transforms of r(t) and should be expected to have fluctuations due to the presence of noise, which results in several local maxima. Thus, a grid search is inevitable in order to find the correct frequency offset with confidence. According to (11) and (1), computations of λ 1 (ν) and λ (ν) require a different number of summations with different limits. In order to make both of them consistent, we define two new signals, i.e. r 1 [n] and r [n], such that r[n] n < NL / r 1 [n] = exp[ j(m 1)πhL ]r[n] 3NL / n < NL otherwise () and exp[j(m 1)πhL /]r[n] NL / n< 3NL / r [n]= otherwise. (1) The above modifications to r[n] leads to similar forms for λ 1 (ν) and λ (ν), where each one requires computation of one summation with NL terms, i.e., and λ 1 ( ν) = λ ( ν) = NL 1 n= NL 1 n= r 1 [n]e j(m 1)πhn/N e jπn ν () r [n]e j(m 1)πhn/N e jπn ν. (3) The computations of () and (3) for different ν values resemble the discrete Fourier transform (DFT) operation, where ν is replaced by trial discrete frequencies. These operations can be performed efficiently using the fast Fourier transform (FFT). The FFT size will be equal to the summation length assuming NL is a power of two. This process results in trial values for λ 1 ( ν) and λ ( ν) such that ν [, 1/NL,..., (NL 1)/NL ], which are then inserted in (17) in order to find ˆν. Therefore, the frequency offset estimate requires two FFTs of the same size. The frequency estimation performance is limited by the resolution of the FFT operations, i.e. the distance between the discrete frequency components. A low resolution estimate may cause a ripple effect on the estimation performance of other parameters. In order to increase the accuracy of the frequency estimate, two approaches are considered. The first approach is to zero pad the FFT operands in () and (3) such that both FFTs have a size of N f = K f NL where K f is a power of two. This procedure results in a frequency resolution of 1/K f L with respect to the symbol rate. The second approach is to employ an interpolator in order to estimate the true maximum of (17) between the discrete frequency values. In [3], it was shown that the Gaussian interpolator is superior to X X FFT FFT X X Frequency Offset ( ) + MAX Interpolator X X X + Symbol Timing ( ) Carrier Phase ( ) Fig. : Block diagram of the feedforward joint frequency offset, symbol timing and carrier phase estimator. a parabolic one in terms of improving FFT resolution. The only added complexity is an extra look-up table for computation of the logarithm function. The Gaussian interpolation can be expressed as 1 log X(ˆν 1 ) log X(ˆν 1 ) ˆν = ˆν + K f NL log X(ˆν 1 ) + log X(ˆν 1 ) log X(ˆν ) () where ˆν represents the maximizing frequency resulting from (17). ˆν 1 and ˆν 1 denote the discrete frequency components immediately before and after ˆν respectively in terms of the FFT operation. The above operation can be regarded as a fine search while FFTs perform a coarse search on the frequency offset. Based on DFT properties, FFT operations are periodic with a period of NL. Therefore, values of 1/ ˆν < 1 represent negative frequency offsets, and hence, ˆν is estimated over [ 1/, 1/). This limits the frequency estimation range to N T s ˆf d < N T s (5) which can be increased by increasing the sampling frequency. Therefore, the proposed algorithm can easily handle applications in which the frequency offset is greater than the symbol rate. The final design for our feedforward joint frequency offset, symbol timing and carrier phase estimator is illustrated in Fig.. Based on () and (1), r 1 [n] and r [n] should be multiplied by exp[ j(m 1)πhL ] and exp[j(m 1)πhL /] respectively. However, we have not shown this in Fig. for the sake of clarity, and because the aforementioned factors are basically equal to one in our examples. Based on the above block diagram, the joint estimator requires NL +3 complex multiplications, NL real multiplications, NL + 1 complex additions and K f NL real additions. These exclude blocks such as FFT, interpolation,, exp( ), and arg( ) as their complexity depends on their implementation method.
6 6 Noise Only Preamble Random Data Fig. 5: The observation window for the SoS estimation algorithm. IV. FRAME SYNCHRONIZATION So far, we have assumed the carrier and timing synchronization algorithm have the knowledge of the SoS within ±T s /, which has to be carried out by the frame synchronization algorithm. In this work, we decompose the frame synchronization into two tasks: SoS detection and SoS Estimation. The SoS detector determines the arrival of a new burst such that the preamble is located within an observation or uncertainty window. The SoS estimation algorithm then tries to find the exact location of the SoS within that window. Using a reverse approach, we initially derive the SoS estimation algorithm. Based on its results, we propose a simple SoS detection algorithm. It should be mentioned that if the observation window does not contain the whole preamble due to SoS detection failures, the SoS estimation results are no longer reliable, and hence, an entire burst might be missed. A. SoS Estimation Algorithm The framework for the SoS estimation algorithm is depicted in Fig. 5 where an observation window of N w samples is considered. The first δ samples contain only WGN which correspond to the guard interval prior to the beginning of signal transmission. Note that δ differs from µ in () where the latter one represents the overall delay from the transmitter to the receiver. It is followed by N p samples of the preamble. Finally, there are N w δ N p samples which are assumed to be generated from a random CPM signal, and are associated with the UW and/or payload portion of the burst. The SoS estimation algorithm attempts to find the best estimate of δ according to the above observation window. The received and sampled signal within the observation window can be expressed as r[n] = w[n] n < δ e j(πνn+θ) (6) s[n δ] + w[n] δ n < N w where w[n] is complex white Gaussian random sequence with a variance of σ = N(E s /N ) 1. Additionally, we have assumed T s = 1 and s[n] = 1. It should be noted that θ in (6) is different from its value in (3) due to the frequency offset and different reference points. Finally, we denote the values of r[n] within the observation window by r. Based on the ML rules, the best estimate of δ is the value which maximizes the likelihood function p(r; δ). However, let us first consider the likelihood function as a function of all unknown parameters, i.e., ( ) 1 p(r; δ, ν, θ, α d )= (πσ ) exp 1 δ 1 Nw σ r[n] n= ( ).exp 1 N w 1 σ r[n] s[n δ]e j(πνn+θ) (7) where α d represents the random data sequence (uniformly distributed among all sequences of that length) in the nonpreamble portion of s[n] and r is the received signal vector. If we omit constant factors in the likelihood function, it becomes ( ) δ Nw p(r; δ, ν, θ, α d )= exp σ ( N w 1.exp σ Re r [n]s[n δ]e j(πνn+θ)}). (8) In order to compute p(r; δ) from (8), we must either estimate or average out the nuisance parameters, i.e. ν, θ and α d, which is not trivial due to the form of the above function. Instead, we initially approximate the exponential function with its second degree Taylor s series in the neighborhood of zero, i.e., p(r; δ, ν, θ, α d ) ( C(δ) 1+ N w 1 σ Re r [n]s[n δ]e j(πνn+θ)} + 1 w 1N σ Re r [n]r [m]s[n δ]s[m δ]e j(πν(m+n)+θ)} m=δ N w N w 1 σ Re r [n]r[m]s[n δ]s [m δ]e j(πν(n m))}) m=δ (9) where C(δ) represents exp( δ Nw σ ) in (8), which is not a function of the nuisance parameters. However, we avoid using it in its original form because it can be very small and adversely affect the approximated likelihood function. Nevertheless, we will propose an approximation for C(δ) once the final form of the likelihood function becomes available. Assuming θ is uniformly distributed over [ π, π), it can be eliminated from the likelihood function by averaging (9) over θ, i.e., p(r; δ, ν, α d ) = 1 π C(δ) 1 N w 1 σ π π N w 1 m=δ p(r; δ, ν, θ, α d ) dθ Re r [n]r[m]s[n δ].s [m δ]e j(πν(n m)) }. (3) Note that we have neglected 1 in (9) because it is much smaller than the fourth term especially when noise variance is small. We also omit 1/σ from the above as it is a constant
7 7 factor. If we denote d = m n in (3), it can be rearranged as p(r; δ, ν, α d ) C(δ) Re N w δ 1 + d=1 ( Nw 1 N w d 1 e jπdν r[n] r [n]r[n+d]s[n δ]s [n+d δ] }) (31) which allows us to investigate signal correlation due to the presence of random α d. The computation of E αd p(r; δ, ν, α d )} leads us to compute E αd s[n δ]s [n + d δ]} which, in our problem, is E αd s[n δ]s [n + d δ]} s[n δ]s [n + d δ] δ n < N p + δ d = N p + δ d n < N p + δ R ss (d) n N p + δ (3) where R ss (d) is the autocorrelation function of the CPM signal normalized to the sample duration. R ss (d) can be computed numerically as described in [, p. 8]. The first case in (3) corresponds to the preamble, which has no randomness. The second case is zero because s[n δ] is deterministic whereas s [n+d δ] is generated by the random data and its expected value is zero. Therefore, taking the expected value of (31) with respect to α d results in p(r; δ, ν) C(δ) ( Nw 1 ( Np+δ d 1. N p 1 r[n] + Re d=1 e jπdν r [n]r[n + d]s[n δ]s [n + d δ] )}) N w d 1 +R ss (d) r [n]r[n + d]. n=n p+δ (33) In general, CPM autocorrelation function becomes zero for lag times greater than LT s. Therefore, R ss (d) is zero except for its first few values. The last step to obtain p(r; δ) is removing ν from (33). It can be verified that averaging (33) with respect to ν, uniformly distributed over [-.5,.5), completely eliminates the second summation. This indeed results in a poor ML estimate for δ because it ignores the knowledge of the known preamble. A better approach is to estimate ν by maximizing the second summation in the above. However, a closed-form solution seems to be unavailable due to the range of d. Instead, we can derive different estimates ˆν d based on single terms inside the summation via ˆν d = 1 πd arg Np+δ d 1 r [n]r[n + d]s[n δ]s [n + d δ] } N w d 1 + R ss (d) r [n]r[n + d]. n=n p+δ (3) The above method is the basis for some well-known carrier frequency estimation algorithms, such as []. If we use ˆν d values and plug them back into (33), the likelihood function becomes independent of the frequency offset. Thus, p(r; δ) C(δ) N p 1 + d=1 ( Nw 1 N p+δ d 1 r[n] r [n]r[n + d]s[n δ]s [n + d δ] ) N w d 1 + R ss (d) r [n]r[n + d] n=n p+δ (35) which must be maximized with respect to δ in order to derive ˆδ. The computational complexity of (35) can be reduced by truncating the summation over d. This results in a suboptimum, reduced-complexity estimator, i.e., ˆδ = argmax C( δ) δ ( Nw 1 D N p+ δ d 1. r[n] + r [n]r[n+d]s[n δ]s [n+d δ] n= δ d=1 n= δ N w d 1 + R ss (d) r [n]r[n + d] n=n p+ δ )} (36) where 1 D < N p is a design parameter, which allows a trade-off between complexity and performance. In fact, if we assume R ss (d) = for d, it is observed that computation of the argument of (36) requires D(N p D 1) + N w N p complex multiplications, real multiplications, D(N p D+1 ) + N w N p complex additions, D real additions, and D computations of the absolute value. Therefore, the complexity of proposed algorithm is approximately a linear function of D. As mentioned earlier, C(δ) needs to be adjusted based on the final form of the likelihood function. We note that (35) is dominated by the summation over d. If we ignore R ss (d) due to its short length, the computations inside the absolute value are performed over a sliding window that covers the hypothetical preamble. If this window is shifted to the left by one sample, one signal-plus-noise sample will be replace by one noise-only sample, which has a smaller energy compared to the former one. However, shifting the window to the right replaces it with a different signal-plus-noise sample. Therefore, we expect p(r; δ + 1) > p(r; δ 1), if δ is its true value. This makes the likelihood test biased, i.e. ˆδ is more likely to tend towards δ + 1 than δ 1. We introduce a simple solution to this issue by proposing C(δ) (N w δ) q (37) where q is another design parameter which has to be chosen according to D. As we will see in the simulation
8 8 results, q = 1 is a good choice for the full-complexity estimator, i.e. D = N p 1, while it has to be reduced for smaller values of D. Choi and Lee [18] have presented a ML frame synchronization algorithm through a different path for PSK signals where the preamble is surrounded by random data. Despite similarities to (36), our estimator addresses a different scenario in which the preamble is preceded by the noise-only samples so that C(δ) was introduced. Additionally, the memory of CPM signals is handled via the presence of R ss (d). Finally, it should be mentioned that each of the summations n r [n]r[n + d]s[n δ]s [n + d δ] in (36) is referred to as a double-correlation in [18]. B. SoS Detection Algorithm As the last piece of our synchronization algorithm, we present a simple ML detection algorithm, which is closely related to our previous discussion. Let us assume a receiver which collects vectors of N p samples using a sliding window. We denote this vector by r p. Additionally, consider two hypotheses H and H 1. H is the hypothesis where the entire vector of samples in r p are noise-only samples, which happens when no burst is received. On the other hand, H 1 is the hypothesis where r p is perfectly aligned with the preamble. We can distinguish these two hypotheses by performing a likelihood ratio test (LRT) according to L(r p ) = p(r p; H 1 ) H 1 γ (38) p(r p, H ) H where p(r p ; H i ) is the likelihood function under H i. Based on the above test, H 1 is selected when L(r p ) is greater than a threshold γ. Otherwise, we select H, i.e. no preamble is present. Obviously, several other hypotheses also occur in between these two in which r p contains only a fraction of the preamble, i.e. a mixed-signal scenario. However, we note that the LRT is performed on a sliding window, which makes it a generalized LRT (GLRT). In this manner, the unknown time delay is being estimated at the same time as the preamble is detected. The point at which the above test exceeds the threshold indicates the presence of the preamble and an estimate of the SoS. Later, the SoS estimator improves this estimate by going over an additional N p samples to find the peak when it considers the full structure of a burst, i.e. the preamble is followed by CPM signal rather than noise. The likelihood ratio of (38) can be easily obtained from (35). In fact, p(r p ; H 1 ) becomes equal to p(r; δ) when δ = and N w = N p. We also note that we can multiply p(r p ; δ = ) by exp( 1 Np 1 σ n= r[n] ) because it is not a function of δ. The latter factor is basically equal to p(r p ; H ). Thus, the likelihood test can be approximated by L(r p ) = p(r p; δ = )p(r p ; H ) p(r p ; H ) N p 1 Np 1 Np d 1 r[n] + r [n]r[n + d]s[n]s [n + d] γ. n= d=1 n= (39) Similar to (36), we propose a reduced-complexity test, i.e. D Np d 1 L D (r p ) r [n]r[n + d]s[n]s [n + d] γ D. d=1 n= () where 1 D < N p is a design parameter and γ D represents the test threshold for a given D. It can be verified that computation of () requires D (N p D 1) complex multiplications, D (N p D +1 ) complex additions, D real additions, and D absolute value functions. Moreover, the majority of computations in SoS detection and SoS estimation are the same, which allows a high degree of resource sharing between these two blocks. The threshold γ D can be chosen based on the Neyman- Pearson criterion [5] in which the probability of false alarm is fixed. Here, the probability of false alarm is defined as P FA = PrL D (r p ) > γ D H }. Once the threshold is chosen, the probability of missed detection can be calculated via P MD = PrL D (r p ) < γ D H 1 }. The probability of correct detection is P D = 1 P MD. Exact closed-form expressions for P FA and P D may not be realized due to the magnitude operators and multiplications in (). For instance, if we denote the output of each double-correlation as a random variable, i.e., X d = N p d 1 n= r [n]r[n + d]s[n]s [n + d], a simple yet acceptable (for large N p d) approximation is to consider X d as a complex Gaussian random variable (RV). This forces X d to become a Rayleigh RV under H and Rician RV under H 1 due to the presence of signal. Thus, L D (r p ) can be approximated as sum of Rayleigh or Rician RVs depending on the hypothesis. In [6], [7], approximate cumulative distribution functions (CDFs) are provided for such RVs. However, our investigations show that the approximation error is considerable because we are interested in regions where P FA and P MD are very low. Therefore, we resort to Monte-Carlo simulations with a large sample size in order to compute these probabilities, γ D, and the receiver operating characteristic (ROC). A. Approximation Error V. RESULTS AND DISCUSSION In this section, we study the error in representing the CPM phase during preamble transmission using (7). For the sake of clarity, we denote the original CPM phase by φ(t), and its approximated value in (7) by φ (t). Therefore, the representation error is e(t) = φ(t) φ (t). We define the approximation error as the ratio of the energy in the error (E e ) to the signal energy during the preamble transmission, i.e., T e jφ(t) e jφ (t) T dt e a T = 1 eje(t) dt = E e. ejφ(t) dt L T s L T s (1) In the above, 1 e je(t) can be approximated by e (t) for small values of e(t), which gives us an approximate value of E e T e (t) dt. The computation of E e for full response
9 9 CPMs is E e = L 1 k= (k+1)ts kt s e (t) dt = L π h (M 1) Ts ( q(t) t T s ) dt () which is basically proportional to the difference between q(t) and the 1REC phase response over a single symbol interval. The computation of E e for partial response signals can be divided into four parts based on the preamble structure as follows. For each part, we denote E e and e(t) by E i and e i (t) respectively. e 1 (t) corresponds to the first L 1 symbols where CPM modulator does not have any memory of t <. Moreover, we have introduced a shift of T l for partial response signals. Therefore, e 1 (t) during t < (L 1)T s / is expressed as e 1 (t) = πh(m 1) t T s L i= ( q t + ( L 1 ) } i)t s (3) which is used to compute E 1. E and E 3 correspond to the two intervals, i.e. T and T 3, where there are transitions in the preamble. Each of these intervals has a duration of (L 1)T s in which there are at least two symbols with different signs. Due to the symmetry, E = E 3, we need only to derive e (t). At the beginning of T, the responses of the L 1 previous symbols are still in effect, and hence, we must consider (L 1) symbols, where the first half have a value of (M 1), and the second half have a value of M 1. Additionally, we assume that the time origin is moved to the start of T such that φ(t) is replaced by φ (t). Therefore, φ (t) is expressed as (L 1) φ (t) = πh(m 1) q(t + (L i)t s ) i=l } L 1 q(t + (L i)t s ). i=1 () We also note that φ (t) is symmetric with respect to t = (L 1)/T s. Thus, it is sufficient to compare it with the 1REC phase response only for t < (L 1)/T s, i.e., e (t) = e 3 (t) = φ (t) + πh(m 1)t T s + πh(l 1). (5) Finally, we need to investigate time intervals where the past (L 1) symbols are similar to the current one. These intervals make up the majority of the preamble with an overall duration of [L (L 1)]T s seconds. The absolute value of the error within each such symbol interval is where e(t) = πh(m 1) p(t) p(t) = (L 1) i= t T s (L 1) (6) q(t + it s ) (7) for t < T s. p(t) can be simplified based on g(t), i.e., p(t)= (L 1) its+t i= = L 1 = L 1 + g(τ) dτ = (L 1) its+t + i= t L 1 (L 1) its i= g(τ) dτ + (L 1) its+t i= it s g(τ) dτ (8a) it s g(τ) dτ (8b) g(τ + it s ) dτ i= (8c) where (8b) is due to (5). It is straightforward to show that the second term in (8c) is equal to t/t s for partial response LREC, LRC, and Gaussian pulse shapes. Using LRC as an example, the integrand in (8c) can be written as L 1 g(τ + it s )dτ = i= L 1 i= 1 LT s = 1 T s L 1 i= ( 1 cos π(t + it ) s) LT s cos π(t + it s) LT s = 1 T s (9) where the last equality holds because the summation of complex points that are uniformly distributed over the unit circle is equal to zero. Hence, e(t) = for our partial response examples except for T, T 3, and the start of the preamble. This results in e a 1 L T s [ (L 1)/Ts ] (L 1)/Ts e 1(t)dt + e (t)dt (5) for partial response CPMs of our interest. We note that the integrals in (5) are independent of L. Therefore, the approximation error decreases as L increases. We also observe that the approximation error occurs whenever there is a transition in the preamble. Since the optimized preamble has only two transitions, it conveniently limits the approximation error in our approach. On the other hand, if we use () in (1), we observe that e a for full response CPMs is constant with respect to L. We have computed e a for different CPMs based on the above relations and have plotted them in Fig. 6 with respect to L. We have normalized the curves by h (M 1) in order to isolate the effect of L and q(t) on the approximation error. We observe that longer frequency pulses result in larger approximation errors because the interval for which they exhibit deviations from 1REC is proportional to L. It is also seen that the approximation error for 1RC is much larger than other examples. Its effect on the estimation performance will be seen in the next section. B. Timing and Carrier Recovery Performance In this section, we compute the error variances of frequency offset, carrier phase, and symbol timing for the proposed ML estimation algorithm using simulations. We have considered
10 Approximation Error (ea) RC 3RC REC 3REC Gaussian (BT s =.3) Gaussian (BT s =.5) 1RC L Fig. 6: The approximation error for different phase responses. These values should be scaled by h (M 1) for a specific CPM. Normalized Frequency Error Variance 1 7 MSK 1RC (M=,h=1/) GMSK RC (M=,h=1/) CRB Es/N (db) 1 1 (a) the three examples of Fig. 3 along with MSK, which is a binary CPM with h = 1/ and 1REC frequency pulse. In all examples, the optimum preamble with L = 6 is deployed. In addition to AWGN, we apply ν, θ and ε that are uniformly distributed over [.5,.5), [, π) and [.5,.5) respectively. Additionally, we have considered N =, K f =, and the Gaussian interpolator () for the estimation. Our simulations show that both interpolation and zero padding must be present in order to have reliable estimates [8, Fig. 3]. The estimation error variances corresponding to the normalized frequency offset and carrier phase are depicted in Figs. 7 (a) and 7 (b) respectively for different CPM schemes. The frequency estimation plots demonstrate that the proposed estimator performs with almost the same accuracy for all the schemes and is less than.5 db away from the CRB for low to moderate SNRs. As it was shown in [], the frequency and phase estimation CRBs for the optimum training sequence are independent of the particular CPM scheme. Hence, only one CRB plot is shown in each figure. Moreover, it is observed that the 1RC scheme performs slightly worse than the other schemes because it has the largest deviations from the 1REC template (refer to Fig. 3). For the remaining schemes, the gap between the error variances and the CRB is mostly due to the FFT precision and can be reduced by increasing K f. This divergence is the beginning of a floor at high SNRs because errors caused by the thermal noise become less significant than the FFT and interpolation precision, which are constant at all SNR. The normalized timing error variances are plotted in Fig. 8. It reveals that the proposed estimator reaches the CRB for the majority of the examples. The only exception is again the 1RC scheme as discussed above. For all other examples, the ML estimator attains the lower limit of the CRB despite the visible loss in the frequency estimation. This is because the optimum training sequence decouples timing from frequency in terms of the Fisher information matrix (FIM) [], which means that small errors in the frequency estimate do not affect the symbol timing estimate. The optimum training sequence Phase Error Variance 1 MSK 1RC (M=,h=1/) GMSK RC (M=,h=1/) CRB Es/N (db) (b) Fig. 7: The error variance of frequency offset (a) and carrier phase (b) estimations for different CPM schemes when L = 6. The frequency is normalized with respect to the symbol rate. does not decouple frequency and phase, and hence, errors in the frequency estimate leak into the phase estimator, which results in a slight performance degradation that is visible in Fig. 7 (b). It should be mentioned that the FFT operations will be replaced by simple correlations when f d =. In such applications, () and (3) are computed for ν = without any need to perform the maximization of (17) and the interpolation. This leads to a joint symbol timing and carrier phase estimator, which is efficient yet less complex compared to other DA works such as [11] [13]. This simplicity is a direct result of unique structure of the optimized preamble. C. Frame Synchronization Performance The performance of the SoS estimation algorithm is characterized by the probability of false lock, which is P FL = Prˆδ δ}. This probability is computed given that the preamble is correctly detected and fully resides within the observation window.
11 Normalized Timing Error Variance 1 3 MSK CRB (MSK) 1RC (M=,h=1/) CRB (1RC) GMSK CRB (GMSK) RC (M=,h=1/) CRB (RC) Es/N (db) Probability of False Lock (PFL) L=6, D=63, q=1 L=6, D=8, q=.5 L=6, D=, q=. L=6, D=, q=.3 L=3, D=31, q=1 L=3, D=8, q=.5 L=3, D=, q=. L=3, D=, q= Es/N (db) Fig. 8: The variance of symbol timing estimation for different CPM schemes when L = 6. The symbol timing is normalized with respect to the symbol duration. Fig. 1: The probability of false lock versus SNR for different preamble lengths. The values of q are optimized for each case using simulations at E s /N = 1 db. The signal is sampled at N = 1, which results in N p = L Probability of False Lock (PFL) D= D= D = 8 D= q Fig. 9: The effect of correction term C(δ) (Equation (37)) and its exponent q on P FL. GMSK signaling is used when N p = 6 and E s /N = 1 db. Probability of Detection (PD) D=, L =3 D=3, L =3 D=, L =3 D=, L = Probability of False Alarm (PFA) x 1 Fig. 11: Receiver operating characteristics for the proposed detector. The optimum preamble is transmitted over an AWGN channel when E s /N = 1 db and GMSK modulation is used. The effect of the C(δ) as a function of q on P FL is studied in Fig. 9 using simulations. The GMSK scheme is used where L = N p = 6, N w = 96 and E s /N = 1 db. Additionally, we have varied q over the range of [, ] and computed P FL for several values of D. It is observed that the introduction of C(δ) reduces P F L given that q is carefully selected. We observe that a value of q = 1 is suitable for D = 63, while it needs to be decreased for smaller values of D. In fact, C(δ) becomes less important for small values of D such as D = and can simply be ignored, i.e. q =. Nevertheless, it visibly improves the performance for D = 63 such that it becomes superior to D = 8 only in the presence of C(δ). Our simulations also confirm that the SoS estimator becomes unbiased only for the optimized q, which was the main motivation for introduction of C(δ) as in (37). The SoS estimator s performance with respect to SNR is shown in Fig. 1 for two different preamble lengths and multiple values of D. Our simulations show that variations of the optimum q with respect to SNR is less than.1 for the plotted range. Therefore, we use a fixed q for each plot. We note that the proposed parameter of D allows us to avoid unwieldy complexity of D = N p 1. For instance, choosing D = results in only a loss of.7 db for L = 6 in comparison with D = 63. Yet, the computational complexity is reduced by a factor of approximately 16. Another important observation that can be made is that increasing L from 3 to 6 yields a gain of only a fraction of db in terms of the SNR. The performance of the SoS detection algorithm can be examined through the ROC plots. A few examples of the ROC are plotted in Fig. 11 where P FA and P D are calculated using simulations by varying γ D. These ROCs are obtained for the GMSK scheme when E s /N = 1 db, and N = 1 (N p = L ). It is observed that we are able to attain a very low P FA at low SNR even with a relatively short preamble of L = 3. It is also seen the improvement becomes less significant when D is changed from to 8. Therefore, a
12 1 Bit Error Rate (BER) Bit Error Rate (BER) L =3 L =6 Perfect Synchronization E b /N (db) (a) GMSK (BT s =.3) L =3 L =6 Perfect Synchronization E b /N (db) (b) RC (h = 1/, M = ) Fig. 1: BER for the burst-mode CPM receiver. L is the preamble length in terms of data symbols. small value of D looks sufficient to achieve a P D that is close to the full-complexity detector, i.e. D = N p 1. This is similar to the performance improvement of the SoS estimation algorithm versus D (Figs. 9 and 1). On the other hand, the performance is improved substantially when L = 6. For instance, P D = and P FA = for γ =. Comparing these metrics with P FL in Fig. 1 reveals that the performance of the frame synchronization algorithm is limited by the false locks rather than false alarms or missed detections. D. BER Performance In this section, we evaluate the overall BER performance of the proposed synchronization scheme, including SoS detection, SoS estimation, and timing and carrier recovery, using simulations. We have considered two examples of GMSK and -ary, h = 1/ CPM with RC frequency pulse. Each burst consists of a preamble of L symbols, a UW of 6 random but known bits and 96 information bits. The UW is used in order to adjust the beginning of each burst by correlating it with the demodulated bits. In our simulations, the transmitter sends individual bursts that are preceded by a fixed but unknown amount of guard time. The AWGN is then added to the waveform along with random frequency and phase offsets. The received signal is sampled at N = samples per symbol. The MLSD CPM demodulator is designed according to [], which uses the Viterbi algorithm (VA). We have also employed a decision-directed (DD) phase and timing tracking loop [1] in which phase and timing error signals are generated according the decisions made inside the VA. The phase tracking loop is essential because even very small residual frequency offsets, after the DA synchronization, result in large phase rotations as the burst is being demodulated. The phase and timing loop bandwidths are both set to 1 3 /T s. Finally, we have set D = D = and N w = NL for the frame synchronization. The BER performance of the burst-mode receiver for the GMSK scheme with two different preamble lengths is depicted in Fig. 1 (a). It is observed that the receiver operates within less than.1 db of the ideal synchronization for L = 6 over the whole range of E b /N. However, there is a substantial BER degradation at the low SNR region for the short preamble of L = 3. Our simulation results show that this is mainly due to the SoS false locks that are more likely to happen at low SNRs and short preamble lengths. False locks reduce the accuracy of the timing and carrier recovery algorithm, which impact the BER. At higher SNRs, there is about. db gap that is caused by estimation errors, which are increased when L is reduced. The BER performance for the RC scheme is reported in Fig. 1 (b). Similar to GMSK, L = 6 performs almost ideal and within about.1 db of perfect synchronization. However, the preamble of L = 3 shows slightly different behavior than that of GMSK, where no BER degradation at low SNRs is visible. This is because E s = E b for the -ary scheme and both Figs. 1 (a) and 1 (b) are expressed in E b /N. In other words, E s /N for GMSK is 3 db less than for the RC, and hence, P FL becomes larger. In fact, RC with L = 3 should be compared to GMSK with L = 6 in order to have a fair comparison where both preambles contain 6 bits. We also note there is no visible difference between the two preambles in terms of the BER, and hence, L = 3 is an adequate length in practice. Finally, this scheme, i.e. nonbinary and partial response, is known to be prone to false locks when DD timing estimation algorithms such as [11] or [1] are implemented. Here, we showed that our proposed DA algorithm with a short preamble can be another method to solve the false lock problem while it significantly reduces the acquisition time. VI. CONCLUSION In this paper, we addressed the synchronization problem for CPM signals in burst-mode transmissions. Thanks to the unique structure of the optimized synchronization preamble, we developed a DA ML algorithm, which jointly estimates
Synchronization Techniques for Burst-Mode Continuous Phase Modulation
 Synchronization Techniques for Burst-Mode Continuous Phase Modulation By Seyed Mohammad Ehsan Hosseini Submitted to the graduate degree program in the Department of Electrical Engineering & Computer Science
Synchronization Techniques for Burst-Mode Continuous Phase Modulation By Seyed Mohammad Ehsan Hosseini Submitted to the graduate degree program in the Department of Electrical Engineering & Computer Science
Parameter Estimation
 1 / 44 Parameter Estimation Saravanan Vijayakumaran sarva@ee.iitb.ac.in Department of Electrical Engineering Indian Institute of Technology Bombay October 25, 2012 Motivation System Model used to Derive
1 / 44 Parameter Estimation Saravanan Vijayakumaran sarva@ee.iitb.ac.in Department of Electrical Engineering Indian Institute of Technology Bombay October 25, 2012 Motivation System Model used to Derive
Direct-Sequence Spread-Spectrum
 Chapter 3 Direct-Sequence Spread-Spectrum In this chapter we consider direct-sequence spread-spectrum systems. Unlike frequency-hopping, a direct-sequence signal occupies the entire bandwidth continuously.
Chapter 3 Direct-Sequence Spread-Spectrum In this chapter we consider direct-sequence spread-spectrum systems. Unlike frequency-hopping, a direct-sequence signal occupies the entire bandwidth continuously.
Timing Recovery at Low SNR Cramer-Rao bound, and outperforming the PLL
 T F T I G E O R G A I N S T I T U T E O H E O F E A L P R O G R ESS S A N D 1 8 8 5 S E R V L O G Y I C E E C H N O Timing Recovery at Low SNR Cramer-Rao bound, and outperforming the PLL Aravind R. Nayak
T F T I G E O R G A I N S T I T U T E O H E O F E A L P R O G R ESS S A N D 1 8 8 5 S E R V L O G Y I C E E C H N O Timing Recovery at Low SNR Cramer-Rao bound, and outperforming the PLL Aravind R. Nayak
Data-aided and blind synchronization
 PHYDYAS Review Meeting 2009-03-02 Data-aided and blind synchronization Mario Tanda Università di Napoli Federico II Dipartimento di Ingegneria Biomedica, Elettronicae delle Telecomunicazioni Via Claudio
PHYDYAS Review Meeting 2009-03-02 Data-aided and blind synchronization Mario Tanda Università di Napoli Federico II Dipartimento di Ingegneria Biomedica, Elettronicae delle Telecomunicazioni Via Claudio
Data Detection for Controlled ISI. h(nt) = 1 for n=0,1 and zero otherwise.
 Data Detection for Controlled ISI *Symbol by symbol suboptimum detection For the duobinary signal pulse h(nt) = 1 for n=0,1 and zero otherwise. The samples at the output of the receiving filter(demodulator)
Data Detection for Controlled ISI *Symbol by symbol suboptimum detection For the duobinary signal pulse h(nt) = 1 for n=0,1 and zero otherwise. The samples at the output of the receiving filter(demodulator)
Digital Band-pass Modulation PROF. MICHAEL TSAI 2011/11/10
 Digital Band-pass Modulation PROF. MICHAEL TSAI 211/11/1 Band-pass Signal Representation a t g t General form: 2πf c t + φ t g t = a t cos 2πf c t + φ t Envelope Phase Envelope is always non-negative,
Digital Band-pass Modulation PROF. MICHAEL TSAI 211/11/1 Band-pass Signal Representation a t g t General form: 2πf c t + φ t g t = a t cos 2πf c t + φ t Envelope Phase Envelope is always non-negative,
Signal Design for Band-Limited Channels
 Wireless Information Transmission System Lab. Signal Design for Band-Limited Channels Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal
Wireless Information Transmission System Lab. Signal Design for Band-Limited Channels Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal
Detection theory. H 0 : x[n] = w[n]
![Detection theory. H 0 : x[n] = w[n] Detection theory. H 0 : x[n] = w[n]](/thumbs/89/98950636.jpg) Detection Theory Detection theory A the last topic of the course, we will briefly consider detection theory. The methods are based on estimation theory and attempt to answer questions such as Is a signal
Detection Theory Detection theory A the last topic of the course, we will briefly consider detection theory. The methods are based on estimation theory and attempt to answer questions such as Is a signal
Iterative Timing Recovery
 Iterative Timing Recovery John R. Barry School of Electrical and Computer Engineering, Georgia Tech Atlanta, Georgia U.S.A. barry@ece.gatech.edu 0 Outline Timing Recovery Tutorial Problem statement TED:
Iterative Timing Recovery John R. Barry School of Electrical and Computer Engineering, Georgia Tech Atlanta, Georgia U.S.A. barry@ece.gatech.edu 0 Outline Timing Recovery Tutorial Problem statement TED:
that efficiently utilizes the total available channel bandwidth W.
 Signal Design for Band-Limited Channels Wireless Information Transmission System Lab. Institute of Communications Engineering g National Sun Yat-sen University Introduction We consider the problem of signal
Signal Design for Band-Limited Channels Wireless Information Transmission System Lab. Institute of Communications Engineering g National Sun Yat-sen University Introduction We consider the problem of signal
EE6604 Personal & Mobile Communications. Week 15. OFDM on AWGN and ISI Channels
 EE6604 Personal & Mobile Communications Week 15 OFDM on AWGN and ISI Channels 1 { x k } x 0 x 1 x x x N- 2 N- 1 IDFT X X X X 0 1 N- 2 N- 1 { X n } insert guard { g X n } g X I n { } D/A ~ si ( t) X g X
EE6604 Personal & Mobile Communications Week 15 OFDM on AWGN and ISI Channels 1 { x k } x 0 x 1 x x x N- 2 N- 1 IDFT X X X X 0 1 N- 2 N- 1 { X n } insert guard { g X n } g X I n { } D/A ~ si ( t) X g X
Digital Communications
 Digital Communications Chapter 5 Carrier and Symbol Synchronization Po-Ning Chen, Professor Institute of Communications Engineering National Chiao-Tung University, Taiwan Digital Communications Ver 218.7.26
Digital Communications Chapter 5 Carrier and Symbol Synchronization Po-Ning Chen, Professor Institute of Communications Engineering National Chiao-Tung University, Taiwan Digital Communications Ver 218.7.26
Chapter 2 Signal Processing at Receivers: Detection Theory
 Chapter Signal Processing at Receivers: Detection Theory As an application of the statistical hypothesis testing, signal detection plays a key role in signal processing at receivers of wireless communication
Chapter Signal Processing at Receivers: Detection Theory As an application of the statistical hypothesis testing, signal detection plays a key role in signal processing at receivers of wireless communication
Optimal Placement of Training Symbols for Frequency Acquisition: A Cramér-Rao Bound Approach
 1 Optimal Placement of Training Symbols for Frequency Acquisition: A Cramér-Rao Bound Approach Aravind R. Nayak, Member, IEEE, John R. Barry, Senior Member, IEEE, and Steven W. McLaughlin, Senior Member,
1 Optimal Placement of Training Symbols for Frequency Acquisition: A Cramér-Rao Bound Approach Aravind R. Nayak, Member, IEEE, John R. Barry, Senior Member, IEEE, and Steven W. McLaughlin, Senior Member,
EE4512 Analog and Digital Communications Chapter 4. Chapter 4 Receiver Design
 Chapter 4 Receiver Design Chapter 4 Receiver Design Probability of Bit Error Pages 124-149 149 Probability of Bit Error The low pass filtered and sampled PAM signal results in an expression for the probability
Chapter 4 Receiver Design Chapter 4 Receiver Design Probability of Bit Error Pages 124-149 149 Probability of Bit Error The low pass filtered and sampled PAM signal results in an expression for the probability
Generalize from CPFSK to continuous phase modulation (CPM) by allowing: non-rectangular frequency pulses frequency pulses with durations LT, L > 1
 8.3 Generalize to CPM [P4.3.3] 8.3-8.3. CPM Signals Generalize from CPFSK to continuous phase modulation (CPM) by allowing: non-rectangular frequency pulses frequency pulses with durations LT, L > o Example:
8.3 Generalize to CPM [P4.3.3] 8.3-8.3. CPM Signals Generalize from CPFSK to continuous phase modulation (CPM) by allowing: non-rectangular frequency pulses frequency pulses with durations LT, L > o Example:
5. Pilot Aided Modulations. In flat fading, if we have a good channel estimate of the complex gain gt, ( ) then we can perform coherent detection.
 5. Pilot Aided Modulations In flat fading, if we have a good channel estimate of the complex gain gt, ( ) then we can perform coherent detection. Obtaining a good estimate is difficult. As we have seen,
5. Pilot Aided Modulations In flat fading, if we have a good channel estimate of the complex gain gt, ( ) then we can perform coherent detection. Obtaining a good estimate is difficult. As we have seen,
ANALYSIS OF A PARTIAL DECORRELATOR IN A MULTI-CELL DS/CDMA SYSTEM
 ANAYSIS OF A PARTIA DECORREATOR IN A MUTI-CE DS/CDMA SYSTEM Mohammad Saquib ECE Department, SU Baton Rouge, A 70803-590 e-mail: saquib@winlab.rutgers.edu Roy Yates WINAB, Rutgers University Piscataway
ANAYSIS OF A PARTIA DECORREATOR IN A MUTI-CE DS/CDMA SYSTEM Mohammad Saquib ECE Department, SU Baton Rouge, A 70803-590 e-mail: saquib@winlab.rutgers.edu Roy Yates WINAB, Rutgers University Piscataway
This examination consists of 11 pages. Please check that you have a complete copy. Time: 2.5 hrs INSTRUCTIONS
 THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 6 December 2006 This examination consists of
THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 6 December 2006 This examination consists of
Tracking of Spread Spectrum Signals
 Chapter 7 Tracking of Spread Spectrum Signals 7. Introduction As discussed in the last chapter, there are two parts to the synchronization process. The first stage is often termed acquisition and typically
Chapter 7 Tracking of Spread Spectrum Signals 7. Introduction As discussed in the last chapter, there are two parts to the synchronization process. The first stage is often termed acquisition and typically
Lecture 12. Block Diagram
 Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Digital Communications
 Digital Communications Chapter 9 Digital Communications Through Band-Limited Channels Po-Ning Chen, Professor Institute of Communications Engineering National Chiao-Tung University, Taiwan Digital Communications:
Digital Communications Chapter 9 Digital Communications Through Band-Limited Channels Po-Ning Chen, Professor Institute of Communications Engineering National Chiao-Tung University, Taiwan Digital Communications:
Lecture 7 Introduction to Statistical Decision Theory
 Lecture 7 Introduction to Statistical Decision Theory I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 20, 2016 1 / 55 I-Hsiang Wang IT Lecture 7
Lecture 7 Introduction to Statistical Decision Theory I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 20, 2016 1 / 55 I-Hsiang Wang IT Lecture 7
Es e j4φ +4N n. 16 KE s /N 0. σ 2ˆφ4 1 γ s. p(φ e )= exp 1 ( 2πσ φ b cos N 2 φ e 0
 Problem 6.15 : he received signal-plus-noise vector at the output of the matched filter may be represented as (see (5-2-63) for example) : r n = E s e j(θn φ) + N n where θ n =0,π/2,π,3π/2 for QPSK, and
Problem 6.15 : he received signal-plus-noise vector at the output of the matched filter may be represented as (see (5-2-63) for example) : r n = E s e j(θn φ) + N n where θ n =0,π/2,π,3π/2 for QPSK, and
Expectation propagation for signal detection in flat-fading channels
 Expectation propagation for signal detection in flat-fading channels Yuan Qi MIT Media Lab Cambridge, MA, 02139 USA yuanqi@media.mit.edu Thomas Minka CMU Statistics Department Pittsburgh, PA 15213 USA
Expectation propagation for signal detection in flat-fading channels Yuan Qi MIT Media Lab Cambridge, MA, 02139 USA yuanqi@media.mit.edu Thomas Minka CMU Statistics Department Pittsburgh, PA 15213 USA
EE5713 : Advanced Digital Communications
 EE5713 : Advanced Digital Communications Week 12, 13: Inter Symbol Interference (ISI) Nyquist Criteria for ISI Pulse Shaping and Raised-Cosine Filter Eye Pattern Equalization (On Board) 20-May-15 Muhammad
EE5713 : Advanced Digital Communications Week 12, 13: Inter Symbol Interference (ISI) Nyquist Criteria for ISI Pulse Shaping and Raised-Cosine Filter Eye Pattern Equalization (On Board) 20-May-15 Muhammad
Carrier frequency estimation. ELEC-E5410 Signal processing for communications
 Carrier frequency estimation ELEC-E54 Signal processing for communications Contents. Basic system assumptions. Data-aided DA: Maximum-lielihood ML estimation of carrier frequency 3. Data-aided: Practical
Carrier frequency estimation ELEC-E54 Signal processing for communications Contents. Basic system assumptions. Data-aided DA: Maximum-lielihood ML estimation of carrier frequency 3. Data-aided: Practical
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi
 Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
The Detection Efficiency of ARTM CPM in Aeronautical Telemetry
 Brigham Young University BYU ScholarsArchive All Faculty Publications 2005-02-27 The Detection Efficiency of ARTM CPM in Aeronautical Telemetry Michael D. Rice mdr@byu.edu Erik Perrins Follow this and
Brigham Young University BYU ScholarsArchive All Faculty Publications 2005-02-27 The Detection Efficiency of ARTM CPM in Aeronautical Telemetry Michael D. Rice mdr@byu.edu Erik Perrins Follow this and
University of Siena. Multimedia Security. Watermark extraction. Mauro Barni University of Siena. M. Barni, University of Siena
 Multimedia Security Mauro Barni University of Siena : summary Optimum decoding/detection Additive SS watermarks Decoding/detection of QIM watermarks The dilemma of de-synchronization attacks Geometric
Multimedia Security Mauro Barni University of Siena : summary Optimum decoding/detection Additive SS watermarks Decoding/detection of QIM watermarks The dilemma of de-synchronization attacks Geometric
LECTURE 16 AND 17. Digital signaling on frequency selective fading channels. Notes Prepared by: Abhishek Sood
 ECE559:WIRELESS COMMUNICATION TECHNOLOGIES LECTURE 16 AND 17 Digital signaling on frequency selective fading channels 1 OUTLINE Notes Prepared by: Abhishek Sood In section 2 we discuss the receiver design
ECE559:WIRELESS COMMUNICATION TECHNOLOGIES LECTURE 16 AND 17 Digital signaling on frequency selective fading channels 1 OUTLINE Notes Prepared by: Abhishek Sood In section 2 we discuss the receiver design
Detecting Parametric Signals in Noise Having Exactly Known Pdf/Pmf
 Detecting Parametric Signals in Noise Having Exactly Known Pdf/Pmf Reading: Ch. 5 in Kay-II. (Part of) Ch. III.B in Poor. EE 527, Detection and Estimation Theory, # 5c Detecting Parametric Signals in Noise
Detecting Parametric Signals in Noise Having Exactly Known Pdf/Pmf Reading: Ch. 5 in Kay-II. (Part of) Ch. III.B in Poor. EE 527, Detection and Estimation Theory, # 5c Detecting Parametric Signals in Noise
Digital Transmission Methods S
 Digital ransmission ethods S-7.5 Second Exercise Session Hypothesis esting Decision aking Gram-Schmidt method Detection.K.K. Communication Laboratory 5//6 Konstantinos.koufos@tkk.fi Exercise We assume
Digital ransmission ethods S-7.5 Second Exercise Session Hypothesis esting Decision aking Gram-Schmidt method Detection.K.K. Communication Laboratory 5//6 Konstantinos.koufos@tkk.fi Exercise We assume
A First Course in Digital Communications
 A First Course in Digital Communications Ha H. Nguyen and E. Shwedyk February 9 A First Course in Digital Communications 1/46 Introduction There are benefits to be gained when M-ary (M = 4 signaling methods
A First Course in Digital Communications Ha H. Nguyen and E. Shwedyk February 9 A First Course in Digital Communications 1/46 Introduction There are benefits to be gained when M-ary (M = 4 signaling methods
10. Composite Hypothesis Testing. ECE 830, Spring 2014
 10. Composite Hypothesis Testing ECE 830, Spring 2014 1 / 25 In many real world problems, it is difficult to precisely specify probability distributions. Our models for data may involve unknown parameters
10. Composite Hypothesis Testing ECE 830, Spring 2014 1 / 25 In many real world problems, it is difficult to precisely specify probability distributions. Our models for data may involve unknown parameters
Residual Versus Suppressed-Carrier Coherent Communications
 TDA Progress Report -7 November 5, 996 Residual Versus Suppressed-Carrier Coherent Communications M. K. Simon and S. Million Communications and Systems Research Section This article addresses the issue
TDA Progress Report -7 November 5, 996 Residual Versus Suppressed-Carrier Coherent Communications M. K. Simon and S. Million Communications and Systems Research Section This article addresses the issue
Performance Analysis of Spread Spectrum CDMA systems
 1 Performance Analysis of Spread Spectrum CDMA systems 16:33:546 Wireless Communication Technologies Spring 5 Instructor: Dr. Narayan Mandayam Summary by Liang Xiao lxiao@winlab.rutgers.edu WINLAB, Department
1 Performance Analysis of Spread Spectrum CDMA systems 16:33:546 Wireless Communication Technologies Spring 5 Instructor: Dr. Narayan Mandayam Summary by Liang Xiao lxiao@winlab.rutgers.edu WINLAB, Department
Square Root Raised Cosine Filter
 Wireless Information Transmission System Lab. Square Root Raised Cosine Filter Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal design
Wireless Information Transmission System Lab. Square Root Raised Cosine Filter Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal design
NEW ADVANCES IN SYMBOL TIMING SYNCHRONIZATION OF SINGLE-CARRIER, MULTI-CARRIER AND SPACE-TIME MULTIPLE-ANTENNA SYSTEMS. A Dissertation YIK CHUNG WU
 NEW ADVANCES IN SYMBOL TIMING SYNCHRONIZATION OF SINGLE-CARRIER, MULTI-CARRIER AND SPACE-TIME MULTIPLE-ANTENNA SYSTEMS A Dissertation by YIK CHUNG WU Submitted to the Office of Graduate Studies of Texas
NEW ADVANCES IN SYMBOL TIMING SYNCHRONIZATION OF SINGLE-CARRIER, MULTI-CARRIER AND SPACE-TIME MULTIPLE-ANTENNA SYSTEMS A Dissertation by YIK CHUNG WU Submitted to the Office of Graduate Studies of Texas
RADIO SYSTEMS ETIN15. Lecture no: Equalization. Ove Edfors, Department of Electrical and Information Technology
 RADIO SYSTEMS ETIN15 Lecture no: 8 Equalization Ove Edfors, Department of Electrical and Information Technology Ove.Edfors@eit.lth.se Contents Inter-symbol interference Linear equalizers Decision-feedback
RADIO SYSTEMS ETIN15 Lecture no: 8 Equalization Ove Edfors, Department of Electrical and Information Technology Ove.Edfors@eit.lth.se Contents Inter-symbol interference Linear equalizers Decision-feedback
sine wave fit algorithm
 TECHNICAL REPORT IR-S3-SB-9 1 Properties of the IEEE-STD-57 four parameter sine wave fit algorithm Peter Händel, Senior Member, IEEE Abstract The IEEE Standard 57 (IEEE-STD-57) provides algorithms for
TECHNICAL REPORT IR-S3-SB-9 1 Properties of the IEEE-STD-57 four parameter sine wave fit algorithm Peter Händel, Senior Member, IEEE Abstract The IEEE Standard 57 (IEEE-STD-57) provides algorithms for
Performance of Coherent Binary Phase-Shift Keying (BPSK) with Costas-Loop Tracking in the Presence of Interference
 TMO Progress Report 4-139 November 15, 1999 Performance of Coherent Binary Phase-Shift Keying (BPSK) with Costas-Loop Tracking in the Presence of Interference M. K. Simon 1 The bit-error probability performance
TMO Progress Report 4-139 November 15, 1999 Performance of Coherent Binary Phase-Shift Keying (BPSK) with Costas-Loop Tracking in the Presence of Interference M. K. Simon 1 The bit-error probability performance
This examination consists of 10 pages. Please check that you have a complete copy. Time: 2.5 hrs INSTRUCTIONS
 THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 08 December 2009 This examination consists of
THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 08 December 2009 This examination consists of
Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics. 1 Executive summary
 ECE 830 Spring 207 Instructor: R. Willett Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we saw that the likelihood
ECE 830 Spring 207 Instructor: R. Willett Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we saw that the likelihood
TECHNICAL RESEARCH REPORT
 TECHNICAL RESEARCH REPORT On the True Cramer-Rao Lower Bound for the DA Joint Estimation of Carrier Phase and Timing Offsets by Y. Jiang, F.W. Sun and John S. Baras CSHCN T.R. 000-14 (ISR T.R. 000-36)
TECHNICAL RESEARCH REPORT On the True Cramer-Rao Lower Bound for the DA Joint Estimation of Carrier Phase and Timing Offsets by Y. Jiang, F.W. Sun and John S. Baras CSHCN T.R. 000-14 (ISR T.R. 000-36)
BASICS OF DETECTION AND ESTIMATION THEORY
 BASICS OF DETECTION AND ESTIMATION THEORY 83050E/158 In this chapter we discuss how the transmitted symbols are detected optimally from a noisy received signal (observation). Based on these results, optimal
BASICS OF DETECTION AND ESTIMATION THEORY 83050E/158 In this chapter we discuss how the transmitted symbols are detected optimally from a noisy received signal (observation). Based on these results, optimal
On Noncoherent Detection of CPM
 Brigham Young University BYU ScholarsArchive All Faculty Publications 2004-04-28 On Noncoherent Detection of CPM Michael D. Rice mdr@byu.edu Erik Perrins Follow this and additional works at: https://scholarsarchive.byu.edu/facpub
Brigham Young University BYU ScholarsArchive All Faculty Publications 2004-04-28 On Noncoherent Detection of CPM Michael D. Rice mdr@byu.edu Erik Perrins Follow this and additional works at: https://scholarsarchive.byu.edu/facpub
F2E5216/TS1002 Adaptive Filtering and Change Detection. Course Organization. Lecture plan. The Books. Lecture 1
 Adaptive Filtering and Change Detection Bo Wahlberg (KTH and Fredrik Gustafsson (LiTH Course Organization Lectures and compendium: Theory, Algorithms, Applications, Evaluation Toolbox and manual: Algorithms,
Adaptive Filtering and Change Detection Bo Wahlberg (KTH and Fredrik Gustafsson (LiTH Course Organization Lectures and compendium: Theory, Algorithms, Applications, Evaluation Toolbox and manual: Algorithms,
Channel Estimation with Low-Precision Analog-to-Digital Conversion
 Channel Estimation with Low-Precision Analog-to-Digital Conversion Onkar Dabeer School of Technology and Computer Science Tata Institute of Fundamental Research Mumbai India Email: onkar@tcs.tifr.res.in
Channel Estimation with Low-Precision Analog-to-Digital Conversion Onkar Dabeer School of Technology and Computer Science Tata Institute of Fundamental Research Mumbai India Email: onkar@tcs.tifr.res.in
STONY BROOK UNIVERSITY. CEAS Technical Report 829
 1 STONY BROOK UNIVERSITY CEAS Technical Report 829 Variable and Multiple Target Tracking by Particle Filtering and Maximum Likelihood Monte Carlo Method Jaechan Lim January 4, 2006 2 Abstract In most applications
1 STONY BROOK UNIVERSITY CEAS Technical Report 829 Variable and Multiple Target Tracking by Particle Filtering and Maximum Likelihood Monte Carlo Method Jaechan Lim January 4, 2006 2 Abstract In most applications
Power Spectral Density of Digital Modulation Schemes
 Digital Communication, Continuation Course Power Spectral Density of Digital Modulation Schemes Mikael Olofsson Emil Björnson Department of Electrical Engineering ISY) Linköping University, SE-581 83 Linköping,
Digital Communication, Continuation Course Power Spectral Density of Digital Modulation Schemes Mikael Olofsson Emil Björnson Department of Electrical Engineering ISY) Linköping University, SE-581 83 Linköping,
CHAPTER 14. Based on the info about the scattering function we know that the multipath spread is T m =1ms, and the Doppler spread is B d =0.2 Hz.
 CHAPTER 4 Problem 4. : Based on the info about the scattering function we know that the multipath spread is T m =ms, and the Doppler spread is B d =. Hz. (a) (i) T m = 3 sec (ii) B d =. Hz (iii) ( t) c
CHAPTER 4 Problem 4. : Based on the info about the scattering function we know that the multipath spread is T m =ms, and the Doppler spread is B d =. Hz. (a) (i) T m = 3 sec (ii) B d =. Hz (iii) ( t) c
2. SPECTRAL ANALYSIS APPLIED TO STOCHASTIC PROCESSES
 2. SPECTRAL ANALYSIS APPLIED TO STOCHASTIC PROCESSES 2.0 THEOREM OF WIENER- KHINTCHINE An important technique in the study of deterministic signals consists in using harmonic functions to gain the spectral
2. SPECTRAL ANALYSIS APPLIED TO STOCHASTIC PROCESSES 2.0 THEOREM OF WIENER- KHINTCHINE An important technique in the study of deterministic signals consists in using harmonic functions to gain the spectral
Principles of Communications Lecture 8: Baseband Communication Systems. Chih-Wei Liu 劉志尉 National Chiao Tung University
 Principles of Communications Lecture 8: Baseband Communication Systems Chih-Wei Liu 劉志尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.tw Outlines Introduction Line codes Effects of filtering Pulse
Principles of Communications Lecture 8: Baseband Communication Systems Chih-Wei Liu 劉志尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.tw Outlines Introduction Line codes Effects of filtering Pulse
CFAR DETECTION OF SPATIALLY DISTRIBUTED TARGETS IN K- DISTRIBUTED CLUTTER WITH UNKNOWN PARAMETERS
 CFAR DETECTION OF SPATIALLY DISTRIBUTED TARGETS IN K- DISTRIBUTED CLUTTER WITH UNKNOWN PARAMETERS N. Nouar and A.Farrouki SISCOM Laboratory, Department of Electrical Engineering, University of Constantine,
CFAR DETECTION OF SPATIALLY DISTRIBUTED TARGETS IN K- DISTRIBUTED CLUTTER WITH UNKNOWN PARAMETERS N. Nouar and A.Farrouki SISCOM Laboratory, Department of Electrical Engineering, University of Constantine,
PATTERN RECOGNITION AND MACHINE LEARNING
 PATTERN RECOGNITION AND MACHINE LEARNING Slide Set 3: Detection Theory January 2018 Heikki Huttunen heikki.huttunen@tut.fi Department of Signal Processing Tampere University of Technology Detection theory
PATTERN RECOGNITION AND MACHINE LEARNING Slide Set 3: Detection Theory January 2018 Heikki Huttunen heikki.huttunen@tut.fi Department of Signal Processing Tampere University of Technology Detection theory
IEEE copyright notice
 IEEE copyright notice Personal use of this material is permitted. However, permission to reprint/republish this material for advertising or promotional purposes or for creating new collective works for
IEEE copyright notice Personal use of this material is permitted. However, permission to reprint/republish this material for advertising or promotional purposes or for creating new collective works for
Synchronization of Spread Spectrum Signals
 Chapter 6 Synchronization of Spread Spectrum Signals 6. Introduction All digital communication systems must perform synchronization. Synchronization is the process of aligning any locally generated reference
Chapter 6 Synchronization of Spread Spectrum Signals 6. Introduction All digital communication systems must perform synchronization. Synchronization is the process of aligning any locally generated reference
2. What are the tradeoffs among different measures of error (e.g. probability of false alarm, probability of miss, etc.)?
 ECE 830 / CS 76 Spring 06 Instructors: R. Willett & R. Nowak Lecture 3: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we
ECE 830 / CS 76 Spring 06 Instructors: R. Willett & R. Nowak Lecture 3: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we
Review of Doppler Spread The response to exp[2πift] is ĥ(f, t) exp[2πift]. ĥ(f, t) = β j exp[ 2πifτ j (t)] = exp[2πid j t 2πifτ o j ]
![Review of Doppler Spread The response to exp[2πift] is ĥ(f, t) exp[2πift]. ĥ(f, t) = β j exp[ 2πifτ j (t)] = exp[2πid j t 2πifτ o j ] Review of Doppler Spread The response to exp[2πift] is ĥ(f, t) exp[2πift]. ĥ(f, t) = β j exp[ 2πifτ j (t)] = exp[2πid j t 2πifτ o j ]](/thumbs/92/110143360.jpg) Review of Doppler Spread The response to exp[2πift] is ĥ(f, t) exp[2πift]. ĥ(f, t) = β exp[ 2πifτ (t)] = exp[2πid t 2πifτ o ] Define D = max D min D ; The fading at f is ĥ(f, t) = 1 T coh = 2D exp[2πi(d
Review of Doppler Spread The response to exp[2πift] is ĥ(f, t) exp[2πift]. ĥ(f, t) = β exp[ 2πifτ (t)] = exp[2πid t 2πifτ o ] Define D = max D min D ; The fading at f is ĥ(f, t) = 1 T coh = 2D exp[2πi(d
ECE 564/645 - Digital Communications, Spring 2018 Homework #2 Due: March 19 (In Lecture)
 ECE 564/645 - Digital Communications, Spring 018 Homework # Due: March 19 (In Lecture) 1. Consider a binary communication system over a 1-dimensional vector channel where message m 1 is sent by signaling
ECE 564/645 - Digital Communications, Spring 018 Homework # Due: March 19 (In Lecture) 1. Consider a binary communication system over a 1-dimensional vector channel where message m 1 is sent by signaling
Efficient Maximum-Likelihood Based Clock and Phase Estimators for OQPSK Signals
 1 Efficient Maximum-Likelihood Based Clock and Phase Estimators for OQPSK Signals Antonio A. D Amico Abstract In this paper we propose an algorithm for joint carrier phase and timing estimation with OQPSK
1 Efficient Maximum-Likelihood Based Clock and Phase Estimators for OQPSK Signals Antonio A. D Amico Abstract In this paper we propose an algorithm for joint carrier phase and timing estimation with OQPSK
Lecture 8: Information Theory and Statistics
 Lecture 8: Information Theory and Statistics Part II: Hypothesis Testing and I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 23, 2015 1 / 50 I-Hsiang
Lecture 8: Information Theory and Statistics Part II: Hypothesis Testing and I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 23, 2015 1 / 50 I-Hsiang
Chapter 12 Variable Phase Interpolation
 Chapter 12 Variable Phase Interpolation Contents Slide 1 Reason for Variable Phase Interpolation Slide 2 Another Need for Interpolation Slide 3 Ideal Impulse Sampling Slide 4 The Sampling Theorem Slide
Chapter 12 Variable Phase Interpolation Contents Slide 1 Reason for Variable Phase Interpolation Slide 2 Another Need for Interpolation Slide 3 Ideal Impulse Sampling Slide 4 The Sampling Theorem Slide
Efficient Semi-Blind Channel Estimation and Equalization Based on a Parametric Channel Representation
 Efficient Semi-Blind Channel Estimation and Equalization Based on a Parametric Channel Representation Presenter: Kostas Berberidis University of Patras Computer Engineering & Informatics Department Signal
Efficient Semi-Blind Channel Estimation and Equalization Based on a Parametric Channel Representation Presenter: Kostas Berberidis University of Patras Computer Engineering & Informatics Department Signal
Analysis of Receiver Quantization in Wireless Communication Systems
 Analysis of Receiver Quantization in Wireless Communication Systems Theory and Implementation Gareth B. Middleton Committee: Dr. Behnaam Aazhang Dr. Ashutosh Sabharwal Dr. Joseph Cavallaro 18 April 2007
Analysis of Receiver Quantization in Wireless Communication Systems Theory and Implementation Gareth B. Middleton Committee: Dr. Behnaam Aazhang Dr. Ashutosh Sabharwal Dr. Joseph Cavallaro 18 April 2007
Burst Markers in EPoC Syed Rahman, Huawei Nicola Varanese, Qualcomm
 Burst Markers in EPoC Syed Rahman, Huawei Nicola Varanese, Qualcomm Page 1 Introduction Burst markers are used to indicate the start and end of each burst in EPoC burst mode The same marker delimits the
Burst Markers in EPoC Syed Rahman, Huawei Nicola Varanese, Qualcomm Page 1 Introduction Burst markers are used to indicate the start and end of each burst in EPoC burst mode The same marker delimits the
DETECTION theory deals primarily with techniques for
 ADVANCED SIGNAL PROCESSING SE Optimum Detection of Deterministic and Random Signals Stefan Tertinek Graz University of Technology turtle@sbox.tugraz.at Abstract This paper introduces various methods for
ADVANCED SIGNAL PROCESSING SE Optimum Detection of Deterministic and Random Signals Stefan Tertinek Graz University of Technology turtle@sbox.tugraz.at Abstract This paper introduces various methods for
UNIFORMLY MOST POWERFUL CYCLIC PERMUTATION INVARIANT DETECTION FOR DISCRETE-TIME SIGNALS
 UNIFORMLY MOST POWERFUL CYCLIC PERMUTATION INVARIANT DETECTION FOR DISCRETE-TIME SIGNALS F. C. Nicolls and G. de Jager Department of Electrical Engineering, University of Cape Town Rondebosch 77, South
UNIFORMLY MOST POWERFUL CYCLIC PERMUTATION INVARIANT DETECTION FOR DISCRETE-TIME SIGNALS F. C. Nicolls and G. de Jager Department of Electrical Engineering, University of Cape Town Rondebosch 77, South
INFORMATION PROCESSING ABILITY OF BINARY DETECTORS AND BLOCK DECODERS. Michael A. Lexa and Don H. Johnson
 INFORMATION PROCESSING ABILITY OF BINARY DETECTORS AND BLOCK DECODERS Michael A. Lexa and Don H. Johnson Rice University Department of Electrical and Computer Engineering Houston, TX 775-892 amlexa@rice.edu,
INFORMATION PROCESSING ABILITY OF BINARY DETECTORS AND BLOCK DECODERS Michael A. Lexa and Don H. Johnson Rice University Department of Electrical and Computer Engineering Houston, TX 775-892 amlexa@rice.edu,
Chapter [4] "Operations on a Single Random Variable"
![Chapter [4] Operations on a Single Random Variable Chapter [4] Operations on a Single Random Variable](/thumbs/93/112549011.jpg) Chapter [4] "Operations on a Single Random Variable" 4.1 Introduction In our study of random variables we use the probability density function or the cumulative distribution function to provide a complete
Chapter [4] "Operations on a Single Random Variable" 4.1 Introduction In our study of random variables we use the probability density function or the cumulative distribution function to provide a complete
A Family of Nyquist Filters Based on Generalized Raised-Cosine Spectra
 Proc. Biennial Symp. Commun. (Kingston, Ont.), pp. 3-35, June 99 A Family of Nyquist Filters Based on Generalized Raised-Cosine Spectra Nader Sheikholeslami Peter Kabal Department of Electrical Engineering
Proc. Biennial Symp. Commun. (Kingston, Ont.), pp. 3-35, June 99 A Family of Nyquist Filters Based on Generalized Raised-Cosine Spectra Nader Sheikholeslami Peter Kabal Department of Electrical Engineering
NON-DATA AIDED DIGITAL FEEDFORWARD TIMING ESTIMATORS FOR LINEAR AND NONLINEAR MODULATIONS. A Thesis PRADEEP KIRAN SARVEPALLI
 NON-DATA AIDED DIGITAL FEEDFORWARD TIMING ESTIMATORS FOR LINEAR AND NONLINEAR MODULATIONS A Thesis by PRADEEP KIRAN SARVEPALLI Submitted to the Office of Graduate Studies of Texas A&M University in partial
NON-DATA AIDED DIGITAL FEEDFORWARD TIMING ESTIMATORS FOR LINEAR AND NONLINEAR MODULATIONS A Thesis by PRADEEP KIRAN SARVEPALLI Submitted to the Office of Graduate Studies of Texas A&M University in partial
REVIEW OF ORIGINAL SEMBLANCE CRITERION SUMMARY
 Semblance Criterion Modification to Incorporate Signal Energy Threshold Sandip Bose*, Henri-Pierre Valero and Alain Dumont, Schlumberger Oilfield Services SUMMARY The semblance criterion widely used for
Semblance Criterion Modification to Incorporate Signal Energy Threshold Sandip Bose*, Henri-Pierre Valero and Alain Dumont, Schlumberger Oilfield Services SUMMARY The semblance criterion widely used for
Optimal Power Control in Decentralized Gaussian Multiple Access Channels
 1 Optimal Power Control in Decentralized Gaussian Multiple Access Channels Kamal Singh Department of Electrical Engineering Indian Institute of Technology Bombay. arxiv:1711.08272v1 [eess.sp] 21 Nov 2017
1 Optimal Power Control in Decentralized Gaussian Multiple Access Channels Kamal Singh Department of Electrical Engineering Indian Institute of Technology Bombay. arxiv:1711.08272v1 [eess.sp] 21 Nov 2017
Detection Theory. Chapter 3. Statistical Decision Theory I. Isael Diaz Oct 26th 2010
 Detection Theory Chapter 3. Statistical Decision Theory I. Isael Diaz Oct 26th 2010 Outline Neyman-Pearson Theorem Detector Performance Irrelevant Data Minimum Probability of Error Bayes Risk Multiple
Detection Theory Chapter 3. Statistical Decision Theory I. Isael Diaz Oct 26th 2010 Outline Neyman-Pearson Theorem Detector Performance Irrelevant Data Minimum Probability of Error Bayes Risk Multiple
Detection theory 101 ELEC-E5410 Signal Processing for Communications
 Detection theory 101 ELEC-E5410 Signal Processing for Communications Binary hypothesis testing Null hypothesis H 0 : e.g. noise only Alternative hypothesis H 1 : signal + noise p(x;h 0 ) γ p(x;h 1 ) Trade-off
Detection theory 101 ELEC-E5410 Signal Processing for Communications Binary hypothesis testing Null hypothesis H 0 : e.g. noise only Alternative hypothesis H 1 : signal + noise p(x;h 0 ) γ p(x;h 1 ) Trade-off
Copyright license. Exchanging Information with the Stars. The goal. Some challenges
 Copyright license Exchanging Information with the Stars David G Messerschmitt Department of Electrical Engineering and Computer Sciences University of California at Berkeley messer@eecs.berkeley.edu Talk
Copyright license Exchanging Information with the Stars David G Messerschmitt Department of Electrical Engineering and Computer Sciences University of California at Berkeley messer@eecs.berkeley.edu Talk
Advanced 3 G and 4 G Wireless Communication Prof. Aditya K Jagannathan Department of Electrical Engineering Indian Institute of Technology, Kanpur
 Advanced 3 G and 4 G Wireless Communication Prof. Aditya K Jagannathan Department of Electrical Engineering Indian Institute of Technology, Kanpur Lecture - 19 Multi-User CDMA Uplink and Asynchronous CDMA
Advanced 3 G and 4 G Wireless Communication Prof. Aditya K Jagannathan Department of Electrical Engineering Indian Institute of Technology, Kanpur Lecture - 19 Multi-User CDMA Uplink and Asynchronous CDMA
Revision of Lecture 4
 Revision of Lecture 4 We have discussed all basic components of MODEM Pulse shaping Tx/Rx filter pair Modulator/demodulator Bits map symbols Discussions assume ideal channel, and for dispersive channel
Revision of Lecture 4 We have discussed all basic components of MODEM Pulse shaping Tx/Rx filter pair Modulator/demodulator Bits map symbols Discussions assume ideal channel, and for dispersive channel
Performance Analysis and Code Optimization of Low Density Parity-Check Codes on Rayleigh Fading Channels
 Performance Analysis and Code Optimization of Low Density Parity-Check Codes on Rayleigh Fading Channels Jilei Hou, Paul H. Siegel and Laurence B. Milstein Department of Electrical and Computer Engineering
Performance Analysis and Code Optimization of Low Density Parity-Check Codes on Rayleigh Fading Channels Jilei Hou, Paul H. Siegel and Laurence B. Milstein Department of Electrical and Computer Engineering
Digital Modulation 2
 Digital Modulation 2 Lecture Notes Ingmar Land and Bernard H. Fleury Department of Electronic Systems Aalborg University Version: November 15, 2006 i Contents 1 Continuous-Phase Modulation 1 1.1 General
Digital Modulation 2 Lecture Notes Ingmar Land and Bernard H. Fleury Department of Electronic Systems Aalborg University Version: November 15, 2006 i Contents 1 Continuous-Phase Modulation 1 1.1 General
Principles of Communications
 Principles of Communications Chapter V: Representation and Transmission of Baseband Digital Signal Yongchao Wang Email: ychwang@mail.xidian.edu.cn Xidian University State Key Lab. on ISN November 18, 2012
Principles of Communications Chapter V: Representation and Transmission of Baseband Digital Signal Yongchao Wang Email: ychwang@mail.xidian.edu.cn Xidian University State Key Lab. on ISN November 18, 2012
Introduction to Detection Theory
 Introduction to Detection Theory Detection Theory (a.k.a. decision theory or hypothesis testing) is concerned with situations where we need to make a decision on whether an event (out of M possible events)
Introduction to Detection Theory Detection Theory (a.k.a. decision theory or hypothesis testing) is concerned with situations where we need to make a decision on whether an event (out of M possible events)
Projects in Wireless Communication Lecture 1
 Projects in Wireless Communication Lecture 1 Fredrik Tufvesson/Fredrik Rusek Department of Electrical and Information Technology Lund University, Sweden Lund, Sept 2018 Outline Introduction to the course
Projects in Wireless Communication Lecture 1 Fredrik Tufvesson/Fredrik Rusek Department of Electrical and Information Technology Lund University, Sweden Lund, Sept 2018 Outline Introduction to the course
Digital Modulation 1
 Digital Modulation 1 Lecture Notes Ingmar Land and Bernard H. Fleury Navigation and Communications () Department of Electronic Systems Aalborg University, DK Version: February 5, 27 i Contents I Basic
Digital Modulation 1 Lecture Notes Ingmar Land and Bernard H. Fleury Navigation and Communications () Department of Electronic Systems Aalborg University, DK Version: February 5, 27 i Contents I Basic
POLYNOMIAL-BASED INTERPOLATION FILTERS PART I: FILTER SYNTHESIS*
 CIRCUITS SYSTEMS SIGNAL PROCESSING c Birkhäuser Boston (27) VOL. 26, NO. 2, 27, PP. 115 146 DOI: 1.17/s34-5-74-8 POLYNOMIAL-BASED INTERPOLATION FILTERS PART I: FILTER SYNTHESIS* Jussi Vesma 1 and Tapio
CIRCUITS SYSTEMS SIGNAL PROCESSING c Birkhäuser Boston (27) VOL. 26, NO. 2, 27, PP. 115 146 DOI: 1.17/s34-5-74-8 POLYNOMIAL-BASED INTERPOLATION FILTERS PART I: FILTER SYNTHESIS* Jussi Vesma 1 and Tapio
Evaluation of Uncertainty in AC Power Calculation with Asynchronously Sampled Data
 Journal of Physics: Conference Series OPEN ACCESS Evaluation of Uncertainty in AC Power Calculation with Asynchronously Sampled Data To cite this article: D Lindenthaler and H Zangl 01 J. Phys.: Conf.
Journal of Physics: Conference Series OPEN ACCESS Evaluation of Uncertainty in AC Power Calculation with Asynchronously Sampled Data To cite this article: D Lindenthaler and H Zangl 01 J. Phys.: Conf.
SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land
 SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land Ingmar Land, SIPCom8-1: Information Theory and Coding (2005 Spring) p.1 Overview Basic Concepts of Channel Coding Block Codes I:
SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land Ingmar Land, SIPCom8-1: Information Theory and Coding (2005 Spring) p.1 Overview Basic Concepts of Channel Coding Block Codes I:
QPSK and OQPSK in Frequency Nonselective Fading
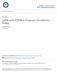 Brigham Young University BYU ScholarsArchive All Faculty Publications 2010-09-17 QPSK and OQPSK in Frequency Nonselective Fading Michael D. Rice mdr@byu.edu Follow this and additional works at: https://scholarsarchive.byu.edu/facpub
Brigham Young University BYU ScholarsArchive All Faculty Publications 2010-09-17 QPSK and OQPSK in Frequency Nonselective Fading Michael D. Rice mdr@byu.edu Follow this and additional works at: https://scholarsarchive.byu.edu/facpub
CONTINUOUS phase modulation (CPM) is an important
 IEEE TRANSACTIONS ON COMMUNICATIONS, VOL. 52, NO. 7, JULY 2004 1169 Training-Based Time-Delay Estimation for CPM Signals Over Time-Selective Fading Channels Ron Dabora, Jason Goldberg, Senior Member, IEEE,
IEEE TRANSACTIONS ON COMMUNICATIONS, VOL. 52, NO. 7, JULY 2004 1169 Training-Based Time-Delay Estimation for CPM Signals Over Time-Selective Fading Channels Ron Dabora, Jason Goldberg, Senior Member, IEEE,
E&CE 358, Winter 2016: Solution #2. Prof. X. Shen
 E&CE 358, Winter 16: Solution # Prof. X. Shen Email: xshen@bbcr.uwaterloo.ca Prof. X. Shen E&CE 358, Winter 16 ( 1:3-:5 PM: Solution # Problem 1 Problem 1 The signal g(t = e t, t T is corrupted by additive
E&CE 358, Winter 16: Solution # Prof. X. Shen Email: xshen@bbcr.uwaterloo.ca Prof. X. Shen E&CE 358, Winter 16 ( 1:3-:5 PM: Solution # Problem 1 Problem 1 The signal g(t = e t, t T is corrupted by additive
A Systematic Description of Source Significance Information
 A Systematic Description of Source Significance Information Norbert Goertz Institute for Digital Communications School of Engineering and Electronics The University of Edinburgh Mayfield Rd., Edinburgh
A Systematic Description of Source Significance Information Norbert Goertz Institute for Digital Communications School of Engineering and Electronics The University of Edinburgh Mayfield Rd., Edinburgh
IN the mobile communication systems, the channel parameters
 Joint Data-Channel Estimation using the Particle Filtering on Multipath Fading Channels Tanya Bertozzi *, Didier Le Ruyet, Gilles Rigal * and Han Vu-Thien * DIGINEXT, 45 Impasse de la Draille, 3857 Aix
Joint Data-Channel Estimation using the Particle Filtering on Multipath Fading Channels Tanya Bertozzi *, Didier Le Ruyet, Gilles Rigal * and Han Vu-Thien * DIGINEXT, 45 Impasse de la Draille, 3857 Aix
Performance of DS-CDMA Systems With Optimal Hard-Decision Parallel Interference Cancellation
 2918 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 11, NOVEMBER 2003 Performance of DS-CDMA Systems With Optimal Hard-Decision Parallel Interference Cancellation Remco van der Hofstad Marten J.
2918 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 11, NOVEMBER 2003 Performance of DS-CDMA Systems With Optimal Hard-Decision Parallel Interference Cancellation Remco van der Hofstad Marten J.
ELEC546 Review of Information Theory
 ELEC546 Review of Information Theory Vincent Lau 1/1/004 1 Review of Information Theory Entropy: Measure of uncertainty of a random variable X. The entropy of X, H(X), is given by: If X is a discrete random
ELEC546 Review of Information Theory Vincent Lau 1/1/004 1 Review of Information Theory Entropy: Measure of uncertainty of a random variable X. The entropy of X, H(X), is given by: If X is a discrete random
Modulation Classification and Parameter Estimation in Wireless Networks
 Syracuse University SURFACE Electrical Engineering - Theses College of Engineering and Computer Science 6-202 Modulation Classification and Parameter Estimation in Wireless Networks Ruoyu Li Syracuse University,
Syracuse University SURFACE Electrical Engineering - Theses College of Engineering and Computer Science 6-202 Modulation Classification and Parameter Estimation in Wireless Networks Ruoyu Li Syracuse University,
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 8, AUGUST For convenience and ease of presentation only, we assume that
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 8, AUGUST 2006 3411 Statistical and Information-Theoretic Analysis of Resolution in Imaging Morteza Shahram, Member, IEEE, and Peyman Milanfar, Senior
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 8, AUGUST 2006 3411 Statistical and Information-Theoretic Analysis of Resolution in Imaging Morteza Shahram, Member, IEEE, and Peyman Milanfar, Senior
Ranging detection algorithm for indoor UWB channels
 Ranging detection algorithm for indoor UWB channels Choi Look LAW and Chi XU Positioning and Wireless Technology Centre Nanyang Technological University 1. Measurement Campaign Objectives Obtain a database
Ranging detection algorithm for indoor UWB channels Choi Look LAW and Chi XU Positioning and Wireless Technology Centre Nanyang Technological University 1. Measurement Campaign Objectives Obtain a database
