Throughput Optimal Control of Cooperative Relay Networks
|
|
|
- Bruce Lee
- 5 years ago
- Views:
Transcription
1 hroughput Optimal Control of Cooperative Relay Networks Emun Yeh Dept. of Electrical Engineering Yale University New Haven, C 06520, USA emun.yeh@yale.eu Ranall Berry Dept. of Electrical an Computer Engineering Northwestern University Evanston, IL 60208, USA rberry@ece.northwestern.eu Abstract We give a moel for cooperative communication in a parallel relay network that inclues the stochastic arrival of packets an queueing. For this moel we provie a throughput optimal network control policy which stabilizes the network for any arrival rate in its stability region. his policy is a generalization of imum ifferential backpressure policies which takes into account the potential cooperative gains in the network. I. INRODUCION In recent years, motivate chiefly by wireless networking applications, there has been interest in moels which jointly aress network layer issues such as the ranom generation of traffic, elay, an buffer occupancy, along with traitional physical layer issues such as moulation, coing, an channel moeling. In [1], [2], moels for multiaccess an broacast channels taking into account both queueing ynamics as well as information-theoretic capacity regions have been consiere. For these moels, the network stability region is characterize; this is the set of arrival rates for which all queues can be stabilize by a feasible rate an power allocation policy. Furthermore, simple throughput optimal resource allocation policies are specifie, which stabilize the system for any arrival rates in the stability region, without requiring any a priori knowlege of the arrival statistics. Results using similar techniques have been shown in [3], [4] for other non-information theoretic physical layer moels, where joint power/rate allocation an routing are performe for multi-hop transmission. A feature of all the above moels is that each packet follows a single route from the source to the estination. In particular, this oes not incorporate the potential gains from various cooperative relaying techniques e.g. [5], [6], [7], [8], [9], [10]. With such techniques, multiple noes may cooperate in relaying a packet, essentially forming a istribute antenna array. Cooperative communication has mainly been aresse from the physical layer viewpoint, i.e. by stuying the achievable rates or iversity gains of given cooperative schemes. A goal of this paper is to stuy a moel of cooperative communication which incorporates the stochastic arrival of traffic an queueing ynamics at the various noes in the 1 his research was supporte in part by NSF uner grants CCR an CCR , an by ARO uner grant DAAD Fig A four noe parallel relay network moel. network. In the next section, we escribe such a moel base on the parallel Gaussian relay channel stuie in [5], [6]. For this moel we characterize the network s stability region an give a throughput optimal network control policy. Compare to the moels in [1], [2], [3], [4], a new potential trae-off emerges: in orer to exploit cooperative gains, information has to be sent along multiple routes; this in turn temporarily increases the congestion within the network. II. NEWORK MODEL Consier a simple network with cooperative communication as shown in Figure 1. his network G consists of four noes V = {1, 2, 3, 4}. raffic originates at noes 1, 2, an 3, an the estination of all traffic in the network is noe 4. At the physical layer, we moel this as a moifie version of a Gaussian parallel relay network [5], [6]. Each noe i V has an average power constraint P. Noe 1 communicates with noes 2 an 3 over a Gaussian broacast channel with banwith W. If X 1 t is the transmitte signal by noe 1, then the receive signal at noe i = 2, 3, is given by Y i t = h 1i X 1 t + Z i t, 1 where Z i t is a white Gaussian noise process with noise ensity N 0 /2 an h 1i is the channel gain between noe 1 an i. 1 Noes 2 an 3 the communicate to noe 4 over a 2- user Gaussian multiaccess channel, also with banwith W. 1 Note all channel gains are fixe an known at the transmitters an receivers. Hence, using cooperative transmissions for iversity gains as in [9] is not relevant.
2 he receive signal at noe 4 is given by Y 4 t = hi4 X i t + Z 4 t, i=2,3 where Z 4 t is a white Gaussian noise process with noise ensity N 0 /2. All noise processes are mutually inepenent an inepenent of the channel inputs. For convenience, we normalize both the banwith an the noise power: W = 1, N 0 W = 1. We efine a symmetric network to be one where h 12 = h 13 = 1 an h 24 = h 34 = 1. o simplify our iscussion, we assume that at any time the network is either operating in the multi-access moe or the broacast moe, i.e., if X 1 t > 0 then X 2 t = 0 an X 3 t = 0, an likewise if X 2 t > 0 or X 3 t > 0 then X 1 t = 0. From the point of view of noes 2 an 3, this enforces a half-uplexing constraint [9], [10], i.e. these noes cannot transmit an receive simultaneously. his is consiere a realistic constraint in practical systems. However, we note that our assumption also prohibits scheules which o not violate the half-uplexing constraint, such as noe 1 transmitting to noe 2, while noe 3 transmits to noe 4. Also, as in [5], we o not consier irect transmissions from noe 1 to noe 4. his is reasonable when the istance between these noes in large. Both of the above-mentione possibilities coul in principle be inclue in our moel at the expense of more complicate notation. Cooperation in this network is achieve by having noes 2 an 3 cooperate to relay information from noe 1 to noe 4. We assume that this is accomplishe by having both noes use a ecoe an forwar strategy. Namely, they will both receive an ecoe the same packet from noe 1; eventually, they will simultaneously transmit this packet to noe 4 by coherently beamforming the receive signal at noe 4. For example, in a symmetric network, if noe 2 an 3 cooperatively transmit a packet using the imum power, P, then the receive signal power will be 4P. Of course, this requires that the noes must be perfectly synchronize. In the absence of perfect synchronization, other cooperative techniques coul be use. Also, we note that in general this is not the optimal cooperative strategy from the view of imizing capacity. 2 We o not require that all traffic from noe 1 to 4 is relaye using this cooperative moe; noe 1 can also sen irect traffic to either noe 2 or 3, which the receiving noe then iniviually relays to noe 4. Exogenous traffic arrives at noe i = 1, 2, 3 accoring to an ergoic counting process A i t, where A i t is the number of packet arrivals up to time t. he packet lengths Z i of exogenous traffic at noe i are i.i.. with E[Z i ] < an E[Zi 2 ] <. Each noe will store all arriving packets in an infinite capacity buffer until they are transmitte. Let U 1 t be the number of untransmitte bits unfinishe work at noe 1, an let U i t an U ic t respectively be the unfinishe work of irect an cooperative traffic at noe i = 2, 3. All exogenous arrivals at noes 2 2 Inee, the optimal strategy an the capacity of the parallel Gaussian relay channel is an open problem [6]. an 3 are inclue in the irect traffic. By assumption, all cooperative traffic is receive at both noes 2 an 3. Hence, for all t, U 2c t = U 3c t, an so we will enote both of these quantities by U c t. Let Ut = U 1 t, U c t, U 2 t, U 3 t enote the joint queue state at time t. We consier the case where given Ut at time t, a network controller specifies a rate allocation Rt = R1, c R12, R13, R4, c R24, R34, where Rij is the rate of irect traffic between noes i an j, Rc 1 is the rate noe 1 sens cooperative traffic to noes 2 an 3, an R4 c is the rate noes 2 an 3 cooperatively forwar traffic to noe 4. At times, it will be more convenient to enote the components of Rt as R 1 t, R 2 t,..., R 6 t, where for example R 6 R34. he rate allocation chosen for time t must respect the halfuplex constraint escribe above an given that the network operates in the broacast or multiaccess moe, the rates must lie in the corresponing capacity region. 3 We escribe these capacity regions next. First consier the broacast moe an without loss of generality assume that h 12 h 13. Let C BC be the capacity region of the two-user Gaussian broacast channel efine by 1. hen it follows that the rates R1, c R12, R13 must satisfy R12 + R1, c R13 C BC. Let the cooperative broacast region C CBC be the set of all such allowable R1, c R12, R13. For a symmetric network h 12 = h 13 C CBC reuces to the set of non-negative rates that lie in the simplex efine by R i log 1 + P. 2 In the multiaccess moe, if noes 2 an 3 only sen irect traffic R4 c = 0, then the transmission rates R24, R34 must lie in the corresponing multiaccess capacity region C MAC ; this is the set of non-negative rates that satisfy Ri4 log 1 + h i4 P S {2, 3}. If both noes sen only cooperative traffic R24 = R34 = 0 then the transmission rate R4 c must satisfy R4 c log 1 + h 24 + h 34 2 P. In aition, we allow the noes to transmit both cooperative an irect traffic simultaneously. One way to moel this is to allow time-sharing between the above two moes. More generally, we can view this as a type of 3-user multiaccess channel, with 2 users corresponing to the irect traffic for noes 2 an 3, respectively, an a thir user corresponing to the cooperative traffic. 4 he ifference here is that the power constraints of the users are couple. If both users 2 an 3, evote a fraction α [0, 1] of their power to 3 It is reasonable to assume that we can achieve any rate in these regions if the times at which we apply the controls are sufficiently separate as to allow the use of long coewors. 4 A key assumption here is that the encoing of the traffic by these three users is one only base on their own message an that the messages are inepenent.
3 cooperative traffic, then we assume that they can achieve any rates R c 4, R 24, R 34 R 4, R 5, R 6 which satisfy R i log 1 + P i α S {4, 5, 6}, 3 where P 4 α = h 24 + h 34 2 αp, P 5 α = h 24 1 αp, an P 6 α = h 34 1 αp. Let C CMAC α enote this set of feasible rates for a particular power splitting parameter α. hen we assume that the controller can choose any rates from the cooperative-mac capacity region given by C CMAC = α [0,1] C CMACα. It can be verifie that the resulting region is convex. Let C CBC an C CMAC be C CBC an C CMAC embee in R 6 +, respectively. hat is, R c 1, R 12, R 13 C CBC if an only if R c 1, R 12, R 13, 0, 0, 0 C CBC, an R c 4, R 24, R 34 C CMAC if an only if 0, 0, 0, R c 4, R 24, R 34 C CMAC. Uner the uplex constraint, the overall physical-layer capacity region is C = convc CBC, C CMAC, i.e. the convex hull of these two sets. III. NEWORK SABILIY REGION AND HROUGHPU OPIMAL RAE ALLOCAION Given the moel in Section II, we procee to characterize the network stability region an the throughput optimal rate allocation policy. Although the results we obtain here may be reminiscent of results for conventional networks [3], [4], we shall fin that the cooperative nature of the parallel relay network introuces some significantly new elements. A. Stability Region Let λ i = lim t A i t/t be the packet arrival rate of traffic to noe i. Let ρ i = λ i E[Z i ] be the corresponing bit arrival rate. We say that queue i is stable if 1 t lim sup t t 0 1 [U iτ>ξ]τ 0 as ξ, where 1 { } is the inicator function. he network stability region S is the closure of the set of all ρ 1, ρ 2, ρ 3 R 3 + for which there exists some feasible rate allocation policy R efine by R = Ru C, where u = u 1, u c, u 2, u 3, which can guarantee that all queues are stable. Note that R is a function of the queue state u an can assign any rate from the physicallayer capacity region C. Using arguments similar to those in [3], [4], we can establish the following. heorem 1: he stability region S of the parallel relay network of Figure 1 is set of all ρ 1, ρ 2, ρ 3 R 3 + for which there exist non-negative flow variables f c, f 12, f 13, f 24, f 34 which support ρ 1, ρ 2, ρ 3 relative to the weighte graph efine by the long-term rates given by C. hat is, the following flow conservation relations must be satisfie: ρ 1 = f c + f 12 + f 13, ρ 2 = f 24 f 12, ρ 2 = f 34 f 13. In aition, f c, f 12, f 13, f c, f 24, f 34 C. B. hroughput Optimal Rate Allocation heorem 1 states that if ρ = ρ 1, ρ 2, ρ 3 ints, then the queues can be stabilize. In general, however, this may require knowing the value of ρ. In reality, ρ can be learne only over time, an may be variable. One woul prefer to fin aaptive rate allocation policies which can stabilize the network without knowing ρ, as long as ρ ints. hese rate allocation policies are calle throughput optimal. As shown in [4], a throughput optimal resource allocation policy for stochastic networks with physical-layer capacity regions turns out to be a generalization of the imum ifferential backlog MDB policy first propose by assiulas [3]. Due to cooperative transmissions, however, the parallel relay network consiere here is somewhat ifferent from the networks consiere in [4]. Nevertheless, we show that the MDB policy can be aapte to prouce a throughput optimal rate allocation policy for the parallel relay network. We consier examine the evolution of the network at time instants separate by > 0 units of time, where is sufficiently large to allow for large coing lengths. We make the following assumptions for the packet arrival processes. Let A k = A 1k, A 2k, A 3k be the arrival vector for the kth -slot. We assume {A k : k Z + } are i.i.. accoring to istribution π A with mean E[A] = λ, where λ = λ 1, λ 2, λ 3 are the arrival rates. Furthermore, assume that for each i, E[A 2 i ] <, an Pr 3 {A i = 0} > 0. hese assumptions on the arrival process, for example, clearly hol for inepenent homogeneous Poisson arrival processes. he above assumptions can be relaxe to the Markov moulate case. heorem 2: A throughput optimal rate allocation policy R u for the parallel relay network of Figure 1 is given by the solution to the following optimization: R C u 1 2u c R c 1 + u 1 u 2 R 12 + u 1 u 3 R 13 +u 2 R 24 + u 3 R u c R c 4 4 Note that the policy in 4 is the not the same as the conventional MDB policy of [3], [4]. In particular, the coefficient terms u 1 2u c an 2u c reflect the queue coupling effect inuce by the cooperative transmission structure. We refer to the policy of 4 as the Cooperative Maximum Differential Backlog CMDB policy. Proof of heorem 2: o show that the CMDB policy stabilizes the network for any ρ = ρ 1, ρ 2, ρ 3 ints, it is convenient to consier a fictitious network G f which is the same as the network G, except that arrivals are allowe to enter the queues 2c an 3c. Let S f be the stability region of the network G f. It is clear that if the CMDB policy stabilizes G f for all ρ 1, ρ 2c, ρ 2, ρ 3c, ρ 3 ints f such that ρ 2c = ρ 3c = 0, then CMDB also stabilizes G for all ρ = ρ 1, ρ 2, ρ 3 ints. herefore, from now on, we concentrate on the artificial network G f.
4 o show that the CMDB policy stabilizes G f for all ρ 1, 0, ρ 2, 0, ρ 3 ints f, we use an extension of Foster s Criterion for the convergence of Markov chains [1], [2], [4]. Consier the Lyapunov function V u u i=2 u2 ic + u 2 i. We wish to show that there exists a compact subset Λ R 5 + such that uner the CMDB policy, E[V Ut + V Ut Ut = u] < ɛ for all u / Λ, where ɛ > 0. his, along with some other technical conitions [4], implies the existence of a steay state istribution for U. We have: U 2 1 t + = [U 1 t + B 1 t R c 1t + R 12t + R 13t + ] 2 U 1 t + B 1 t R1t c + R12t + R13t 2 U1 2 t 2 U 1 t R1t c + R12t + R13t B 1t +B1t 2 + R1t c + R12t + R13t 2 2 Here B 1 t is the number of bits arriving to queue 1 in the tth slot, an x + enotes x, 0. Similarly, for i = 2, 3, U 2 ict + U 2 ict 2 U ic tr c 4t R c 1t where β > 0 is an upper boun on a sum of terms involving the secon moments of the bit arrivals in the tth slot which are boune since the secon moments of the packet arrivals an the packet sizes are boune, an powers of transmission rates which are boune since C is boune. Let E u [X] enote E[X Ut = u]. Note that u 1 E u [R1t c + R12t + R13t] + 2u c E u [R4t c R1t] c + u i E u [Ri4t R1it] i=2 = u 1 2u c E u [R c 1t] + u 1 u 2 E u [R 12t] +u 1 u 3 E u [R 13t] + u 2 E u [R 24t] u 3 E u [R 34t] + 2u c E u [R c 4t] 6 For any ρ 1, 0, ρ 2, 0, ρ 3 ints f, there exists δ > 0 such that ρ 1 + δ, δ, ρ 2 + δ, δ, ρ 3 + δ S f. herefore, there exist non-negative flow variables f c 1, f 12, f 13, f c 4, f 24, f 34 C such that ρ 1 + δ = f 1 c + f 12 + f 13, ρ 2 + δ = f 24 f 12, ρ 3 + δ = f 34 f 13, an δ = f 4 c f 1 c. We therefore have u 1 ρ 1 + δ + u 2 ρ 2 + δ + u 3 ρ 3 + δ + 2u c δ = u 1 f 1 c + f 12 + f 13 + u 2 f 24 f 12 + u 3 f 34 f 13 +2u c f 4 c f 1 c = u 1 2u c f c 1 + u 1 u 2 f 12 + u 1 u 3 f 13 +u 2 f 24 + u 3 f u c f c 4 Let Rt = R c 1t, R 12t, R 13t, R c 4t, R 24t, R 34t be chosen accoring to the CMDB rule escribe in 4. hen, since f c 1, f 12, f 13, f c 4, f 24, f 34 C, u 1 ρ 1 + δ + u 2 ρ 2 + δ + u 3 ρ 3 + δ + 2u c δ is less than or equal to the RHS of 6. Since E[B 1 t/ ] = ρ 1 an E[B i t/ ] = ρ i for i = 1, 2, the RHS of 5 implies E[V Ut + V Ut Ut = u] β 2 δu 1 + u 2 + u 3 + 2u c. +R1t c 2 + R4t c 2 2 Let Λ = {u : u 1 + u 2 + u 3 + 2u c β+ɛ, 2 δ }. hen, for any ɛ > 0, an any u / Λ, E[V Ut + V Ut Ut = Uit 2 + Uit 2 2 U i tri4t R1it u] < ɛ. B i t/ + B i t 2 + 2B i tr1it We have shown that the CMDB policy stabilizes G f +R1it 2 + Ri4t 2 2 for all ρ 1, 0, ρ 2, 0, ρ 3 ints f. hus, we have also shown that the CMDB policy stabilizes G for all Note that since ρ 2c = ρ 3c = 0, there are no exogenous arrivals to queues 2c an 3c. aking conitional expecte value of both sies of the above inequalities given the event Ut = u, an re-arranging, we have ρ = ρ 1, ρ 2, ρ 3 ints. IV. CALCULAING HE CMBD POLICY We now focus on solving the optimization problem 4 E[V Ut + V Ut Ut = u] [ 2 u 1 E R1t c + R12t + R13t B ] require by the CMBD policy. We focus on a symmetric 1t Ut = u network h 12 = h 13 = h 24 = h 34 = 1 in this section. In this case, C CBC is given by 2 an the power variables 2 2u c E[R4t c R1t Ut c = u] use in the efinition of C CMAC α become P 4 α = 4αP, [ 2 u i E Ri4t R1it B ] P it 5 α = P 6 α = 1 αp. Ut = u For simplicity of notation, let w 1, w 2, w 3, w 4, w 5, w 6 enote u 1 2u c, u 1 u 2, u 1 u 3, 2u c, u 2, u 3, an let i=2 +β 5 R 1, R 2, R 3, R 4, R 5, R 6 enote R c 1,R 12,R 13,R c 4,R 24, R 34. he CMBD policy can now be expresse as R C w i R i, 7 Note that the solution R to 7 lies in convc CBC, C CMAC α for some α [0, 1], where C CMAC α is the appropriate embeing of C CMAC α in R 6 +. Since C CBC an C CMAC α are both convex polytopes, convc CBC, C CMAC α is also a convex polytope. Now since R also imizes the linear objective of 7 over convc CBC, C CMAC α, R is without loss of optimality an extreme point of convc CBC, C CMAC α. hus, R is an extreme point either of C CBC or an extreme point of C CMAC α. We now consier these cases separately.
5 Case 1: R is an extreme point of C CBC. In this case, R has the form R 1, R 2, R 3, 0, 0, 0. hus, R 1, R 2, R 3 solves R C CBC w i R i. 8 Since C CBC is a simplex, R1, R2, R3 is easily given as follows. Let w [1] w [2] w [3] be w 1, w 2, w 3 arrange in ecreasing orer. hen R[1] = log1+p an R [2] = R [3] = 0. hus, whenever the CMDB policy operates in the broacast moe, it allocates imum rate log1 + P to the traffic type with the largest weight w i. he optimal value of 8 is then L CBC w 1, w 2, w 3 =,2,3 w i log1 + P. Uner the assumption that R is an extreme point of C CBC, L CBC w 1, w 2, w 3 is equal to the optimal value of 7, L w 1,..., w 6. Case 2: R is an extreme point of C CMAC α. In this case, R has the form 0, 0, 0, R4, R5, R6. hus, R4, R5, R6 solves w i R i 9 R C CMAC α i=4 Since C CMAC α is a polymatroi [11], R4, R5, R6 can be explicitly given as follows. Let w [4], w [5], w [6] be the largest, secon largest, an smallest element of {w 4, w 5, w 6 }, respectively. hen R[i] 1 = log P [i] α j<i P [j]α, i = 4, 5, For instance, if w 4 w 5 w 6, then R 4 = log1 + 4α P, R 5 = log α P 1+4α P, R 6 = log α P 1+3α +1P. Next, to fin α, we can solve P [i] α w [i] log 1 + α [0,1] 1 + j<i P. 11 [j]α i=4 Let Lα be the objective in 11. For the case of w 4 w 5 w 6, it can be verifie that Lα is concave in α over [0, 1], an that L α 0 for all α [0, 1]. hus, α = 1, i.e. all power is allocate to cooperative transmission over the MAC. In other cases, Lα may not be concave, an one nees to solve for the stationary points of Lα an compare the value of Lα at the stationary points with its values on the bounaries. Let L CMAC w 4, w 5, w 6 be the optimal objective of 11. Uner the assumption that R is an extreme point of C CMAC, we have L CMAC w 4, w 5, w 6 = L w 1,..., w 6. log1 + P an R [2] = R [3] = 0. Otherwise, R = 0, 0, 0, R 4, R 5, R 6, where R [i] is given by 10 an α is given by 11. V. CONCLUSIONS In this paper we consiere a moel of a parallel relay network that incorporates the stochastic arrival of traffic within the network. For this moel we showe that a variation of a imum back pressure policy is throughput optimal, where this policy is moifie to incorporate the potential gains of cooperative communication. We only consiere one type of cooperation, namely ecoe an forwar combine with beamforming. Potential future irections inclue consiering other types of cooperation as well as other network topologies. REFERENCES [1] E. Yeh an A. Cohen, hroughput optimal power an rate control for queue multiaccess an broacast communications, in Proceeings of the International Symposium on Information heory, Chicago, IL, [2] E. Yeh an A. Cohen, Information theory, queueing, an resource allocation in multi-user faing communications, in Proceeings of the Conference on Information Sciences an Systems, Princeton, NJ, [3] L. assiulas an A. Ephremies, Stability properties of constraine queueing systems an scheuling policies for imum throughput in multihop raio networks, IEEE ransactions on Automatic Control, vol. 37, no. 12, pp , [4] M. J. Neely, E. Moiano, an C. E. Rohrs, Dynamic power allocation an routing for time varying wireless networks. Proceeings of Infocom, [5] B. Schein an R. G. Gallager, he gaussian parallel relay network, in Proc. IEEE Int. Symp. Information heory ISI, Sorrento, Italy, p. 22, June [6] B. Schein, Distribute Coorination in Network Information heory. PhD thesis, Massachusetts Institute of echnology, Cambrige, MA, [7] A. Senonaris, E. Erkip, an B. Aazhang, User cooperation iversity - part i: System escription, IEEE rans. On Communications, vol. 51, pp , November [8] A. Senonaris, E. Erkip, an B. Aazhang, User cooperation iversity - part ii: Implementation aspects an performance analysis, IEEE rans. On Communications, vol. 51, pp , November [9] J. N. Laneman, D. N. C. se, an G. W. Wornell, Cooperative iversity in wireless networks: Efficient protocols an outage behavior, IEEE rans. Inform. heory, vol. 50, pp , Dec [10] A. Hst-Masen an J. Zhang, Capacity bouns an power allocation for the wireless relay channel.. [11] D. se an S. Hanly, Multi-access faing channels: Part I: Polymatroi structure, optimal resource allocation an throughput capacities, IEEE ransactions on Information heory, vol. 44, no. 7, pp , he previous iscussion for Cases 1 an 2 operate uner the assumption that R is an extreme point of C CBC or that R is an extreme point of C CMAC. Using these arguments, on the other han, it is easy to see that the following is true: heorem 3: Consier the four-noe parallel relay network with ifferential queue backlogs w 1, w 2,..., w 6. If L CBC w 1, w 2, w 3 L CMAC w 4, w 5, w 6, then the optimal solution R to 7 is R 1, R 2, R 3, 0, 0, 0, where R [1] =
On Characterizing the Delay-Performance of Wireless Scheduling Algorithms
 On Characterizing the Delay-Performance of Wireless Scheuling Algorithms Xiaojun Lin Center for Wireless Systems an Applications School of Electrical an Computer Engineering, Purue University West Lafayette,
On Characterizing the Delay-Performance of Wireless Scheuling Algorithms Xiaojun Lin Center for Wireless Systems an Applications School of Electrical an Computer Engineering, Purue University West Lafayette,
Lyapunov Functions. V. J. Venkataramanan and Xiaojun Lin. Center for Wireless Systems and Applications. School of Electrical and Computer Engineering,
 On the Queue-Overflow Probability of Wireless Systems : A New Approach Combining Large Deviations with Lyapunov Functions V. J. Venkataramanan an Xiaojun Lin Center for Wireless Systems an Applications
On the Queue-Overflow Probability of Wireless Systems : A New Approach Combining Large Deviations with Lyapunov Functions V. J. Venkataramanan an Xiaojun Lin Center for Wireless Systems an Applications
Closed and Open Loop Optimal Control of Buffer and Energy of a Wireless Device
 Close an Open Loop Optimal Control of Buffer an Energy of a Wireless Device V. S. Borkar School of Technology an Computer Science TIFR, umbai, Inia. borkar@tifr.res.in A. A. Kherani B. J. Prabhu INRIA
Close an Open Loop Optimal Control of Buffer an Energy of a Wireless Device V. S. Borkar School of Technology an Computer Science TIFR, umbai, Inia. borkar@tifr.res.in A. A. Kherani B. J. Prabhu INRIA
An Analytical Expression of the Probability of Error for Relaying with Decode-and-forward
 An Analytical Expression of the Probability of Error for Relaying with Decoe-an-forwar Alexanre Graell i Amat an Ingmar Lan Department of Electronics, Institut TELECOM-TELECOM Bretagne, Brest, France Email:
An Analytical Expression of the Probability of Error for Relaying with Decoe-an-forwar Alexanre Graell i Amat an Ingmar Lan Department of Electronics, Institut TELECOM-TELECOM Bretagne, Brest, France Email:
Time-of-Arrival Estimation in Non-Line-Of-Sight Environments
 2 Conference on Information Sciences an Systems, The Johns Hopkins University, March 2, 2 Time-of-Arrival Estimation in Non-Line-Of-Sight Environments Sinan Gezici, Hisashi Kobayashi an H. Vincent Poor
2 Conference on Information Sciences an Systems, The Johns Hopkins University, March 2, 2 Time-of-Arrival Estimation in Non-Line-Of-Sight Environments Sinan Gezici, Hisashi Kobayashi an H. Vincent Poor
Space-time Linear Dispersion Using Coordinate Interleaving
 Space-time Linear Dispersion Using Coorinate Interleaving Jinsong Wu an Steven D Blostein Department of Electrical an Computer Engineering Queen s University, Kingston, Ontario, Canaa, K7L3N6 Email: wujs@ieeeorg
Space-time Linear Dispersion Using Coorinate Interleaving Jinsong Wu an Steven D Blostein Department of Electrical an Computer Engineering Queen s University, Kingston, Ontario, Canaa, K7L3N6 Email: wujs@ieeeorg
On the Aloha throughput-fairness tradeoff
 On the Aloha throughput-fairness traeoff 1 Nan Xie, Member, IEEE, an Steven Weber, Senior Member, IEEE Abstract arxiv:1605.01557v1 [cs.it] 5 May 2016 A well-known inner boun of the stability region of
On the Aloha throughput-fairness traeoff 1 Nan Xie, Member, IEEE, an Steven Weber, Senior Member, IEEE Abstract arxiv:1605.01557v1 [cs.it] 5 May 2016 A well-known inner boun of the stability region of
Delay Limited Capacity of Ad hoc Networks: Asymptotically Optimal Transmission and Relaying Strategy
 Delay Limite Capacity of A hoc Networks: Asymptotically Optimal Transmission an Relaying Strategy Eugene Perevalov Lehigh University Bethlehem, PA 85 Email: eup2@lehigh.eu Rick Blum Lehigh University Bethlehem,
Delay Limite Capacity of A hoc Networks: Asymptotically Optimal Transmission an Relaying Strategy Eugene Perevalov Lehigh University Bethlehem, PA 85 Email: eup2@lehigh.eu Rick Blum Lehigh University Bethlehem,
Capacity Analysis of MIMO Systems with Unknown Channel State Information
 Capacity Analysis of MIMO Systems with Unknown Channel State Information Jun Zheng an Bhaskar D. Rao Dept. of Electrical an Computer Engineering University of California at San Diego e-mail: juzheng@ucs.eu,
Capacity Analysis of MIMO Systems with Unknown Channel State Information Jun Zheng an Bhaskar D. Rao Dept. of Electrical an Computer Engineering University of California at San Diego e-mail: juzheng@ucs.eu,
Improved Rate-Based Pull and Push Strategies in Large Distributed Networks
 Improve Rate-Base Pull an Push Strategies in Large Distribute Networks Wouter Minnebo an Benny Van Hout Department of Mathematics an Computer Science University of Antwerp - imins Mielheimlaan, B-00 Antwerp,
Improve Rate-Base Pull an Push Strategies in Large Distribute Networks Wouter Minnebo an Benny Van Hout Department of Mathematics an Computer Science University of Antwerp - imins Mielheimlaan, B-00 Antwerp,
On the Broadcast Capacity of Multihop Wireless Networks: Interplay of Power, Density and Interference
 On the Broacast Capacity of Multihop Wireless Networks: Interplay of Power, Density an Interference Alireza Keshavarz-Haa Ruolf Riei Department of Electrical an Computer Engineering an Department of Statistics
On the Broacast Capacity of Multihop Wireless Networks: Interplay of Power, Density an Interference Alireza Keshavarz-Haa Ruolf Riei Department of Electrical an Computer Engineering an Department of Statistics
An M/G/1 Retrial Queue with Priority, Balking and Feedback Customers
 Journal of Convergence Information Technology Volume 5 Number April 1 An M/G/1 Retrial Queue with Priority Balking an Feeback Customers Peishu Chen * 1 Yiuan Zhu 1 * 1 Faculty of Science Jiangsu University
Journal of Convergence Information Technology Volume 5 Number April 1 An M/G/1 Retrial Queue with Priority Balking an Feeback Customers Peishu Chen * 1 Yiuan Zhu 1 * 1 Faculty of Science Jiangsu University
Introduction to the Vlasov-Poisson system
 Introuction to the Vlasov-Poisson system Simone Calogero 1 The Vlasov equation Consier a particle with mass m > 0. Let x(t) R 3 enote the position of the particle at time t R an v(t) = ẋ(t) = x(t)/t its
Introuction to the Vlasov-Poisson system Simone Calogero 1 The Vlasov equation Consier a particle with mass m > 0. Let x(t) R 3 enote the position of the particle at time t R an v(t) = ẋ(t) = x(t)/t its
Least-Squares Regression on Sparse Spaces
 Least-Squares Regression on Sparse Spaces Yuri Grinberg, Mahi Milani Far, Joelle Pineau School of Computer Science McGill University Montreal, Canaa {ygrinb,mmilan1,jpineau}@cs.mcgill.ca 1 Introuction
Least-Squares Regression on Sparse Spaces Yuri Grinberg, Mahi Milani Far, Joelle Pineau School of Computer Science McGill University Montreal, Canaa {ygrinb,mmilan1,jpineau}@cs.mcgill.ca 1 Introuction
Generalizing Kronecker Graphs in order to Model Searchable Networks
 Generalizing Kronecker Graphs in orer to Moel Searchable Networks Elizabeth Boine, Babak Hassibi, Aam Wierman California Institute of Technology Pasaena, CA 925 Email: {eaboine, hassibi, aamw}@caltecheu
Generalizing Kronecker Graphs in orer to Moel Searchable Networks Elizabeth Boine, Babak Hassibi, Aam Wierman California Institute of Technology Pasaena, CA 925 Email: {eaboine, hassibi, aamw}@caltecheu
Decoding Delay and Outage Performance Analysis of Full-Duplex Decode-Forward Relaying: Backward or Sliding Window Decoding
 Decoing Delay an Outage Performance Analysis of Full-Duplex Decoe-Forwar Relaying: Backwar or Sliing Winow Decoing Ahma Abu Al Haija Member IEEE an Chintha Tellambura Fellow IEEE Abstract High reliability
Decoing Delay an Outage Performance Analysis of Full-Duplex Decoe-Forwar Relaying: Backwar or Sliing Winow Decoing Ahma Abu Al Haija Member IEEE an Chintha Tellambura Fellow IEEE Abstract High reliability
Math 342 Partial Differential Equations «Viktor Grigoryan
 Math 342 Partial Differential Equations «Viktor Grigoryan 6 Wave equation: solution In this lecture we will solve the wave equation on the entire real line x R. This correspons to a string of infinite
Math 342 Partial Differential Equations «Viktor Grigoryan 6 Wave equation: solution In this lecture we will solve the wave equation on the entire real line x R. This correspons to a string of infinite
Fluid model for a data network with α-fair bandwidth sharing and general document size distributions: two examples of stability
 IMS Lecture Notes Monograph Series??? Vol. 0 (0000) 1 c Institute of Mathematical Statistics, 0000 Flui moel for a ata network with α-fair banwith sharing an general ocument size istributions: two examples
IMS Lecture Notes Monograph Series??? Vol. 0 (0000) 1 c Institute of Mathematical Statistics, 0000 Flui moel for a ata network with α-fair banwith sharing an general ocument size istributions: two examples
NOTES ON EULER-BOOLE SUMMATION (1) f (l 1) (n) f (l 1) (m) + ( 1)k 1 k! B k (y) f (k) (y) dy,
 NOTES ON EULER-BOOLE SUMMATION JONATHAN M BORWEIN, NEIL J CALKIN, AND DANTE MANNA Abstract We stuy a connection between Euler-MacLaurin Summation an Boole Summation suggeste in an AMM note from 196, which
NOTES ON EULER-BOOLE SUMMATION JONATHAN M BORWEIN, NEIL J CALKIN, AND DANTE MANNA Abstract We stuy a connection between Euler-MacLaurin Summation an Boole Summation suggeste in an AMM note from 196, which
The total derivative. Chapter Lagrangian and Eulerian approaches
 Chapter 5 The total erivative 51 Lagrangian an Eulerian approaches The representation of a flui through scalar or vector fiels means that each physical quantity uner consieration is escribe as a function
Chapter 5 The total erivative 51 Lagrangian an Eulerian approaches The representation of a flui through scalar or vector fiels means that each physical quantity uner consieration is escribe as a function
Survey Sampling. 1 Design-based Inference. Kosuke Imai Department of Politics, Princeton University. February 19, 2013
 Survey Sampling Kosuke Imai Department of Politics, Princeton University February 19, 2013 Survey sampling is one of the most commonly use ata collection methos for social scientists. We begin by escribing
Survey Sampling Kosuke Imai Department of Politics, Princeton University February 19, 2013 Survey sampling is one of the most commonly use ata collection methos for social scientists. We begin by escribing
Lower Bounds for the Smoothed Number of Pareto optimal Solutions
 Lower Bouns for the Smoothe Number of Pareto optimal Solutions Tobias Brunsch an Heiko Röglin Department of Computer Science, University of Bonn, Germany brunsch@cs.uni-bonn.e, heiko@roeglin.org Abstract.
Lower Bouns for the Smoothe Number of Pareto optimal Solutions Tobias Brunsch an Heiko Röglin Department of Computer Science, University of Bonn, Germany brunsch@cs.uni-bonn.e, heiko@roeglin.org Abstract.
On Event-Triggered and Self-Triggered Control over Sensor/Actuator Networks
 Proceeings of the th IEEE Conference on Decision an Control Cancun, Mexico, Dec. 9-11, 8 TuA1. On Event-Triggere an Self-Triggere Control over Sensor/Actuator Networks Manuel Mazo Jr. an Paulo Tabuaa Abstract
Proceeings of the th IEEE Conference on Decision an Control Cancun, Mexico, Dec. 9-11, 8 TuA1. On Event-Triggere an Self-Triggere Control over Sensor/Actuator Networks Manuel Mazo Jr. an Paulo Tabuaa Abstract
Node Density and Delay in Large-Scale Wireless Networks with Unreliable Links
 Noe Density an Delay in Large-Scale Wireless Networks with Unreliable Links Shizhen Zhao, Xinbing Wang Department of Electronic Engineering Shanghai Jiao Tong University, China Email: {shizhenzhao,xwang}@sjtu.eu.cn
Noe Density an Delay in Large-Scale Wireless Networks with Unreliable Links Shizhen Zhao, Xinbing Wang Department of Electronic Engineering Shanghai Jiao Tong University, China Email: {shizhenzhao,xwang}@sjtu.eu.cn
An Optimal Algorithm for Bandit and Zero-Order Convex Optimization with Two-Point Feedback
 Journal of Machine Learning Research 8 07) - Submitte /6; Publishe 5/7 An Optimal Algorithm for Banit an Zero-Orer Convex Optimization with wo-point Feeback Oha Shamir Department of Computer Science an
Journal of Machine Learning Research 8 07) - Submitte /6; Publishe 5/7 An Optimal Algorithm for Banit an Zero-Orer Convex Optimization with wo-point Feeback Oha Shamir Department of Computer Science an
Sliding mode approach to congestion control in connection-oriented communication networks
 JOURNAL OF APPLIED COMPUTER SCIENCE Vol. xx. No xx (200x), pp. xx-xx Sliing moe approach to congestion control in connection-oriente communication networks Anrzej Bartoszewicz, Justyna Żuk Technical University
JOURNAL OF APPLIED COMPUTER SCIENCE Vol. xx. No xx (200x), pp. xx-xx Sliing moe approach to congestion control in connection-oriente communication networks Anrzej Bartoszewicz, Justyna Żuk Technical University
New Bounds for Distributed Storage Systems with Secure Repair
 New Bouns for Distribute Storage Systems with Secure Repair Ravi Tanon 1 an Soheil Mohajer 1 Discovery Analytics Center & Department of Computer Science, Virginia Tech, Blacksburg, VA Department of Electrical
New Bouns for Distribute Storage Systems with Secure Repair Ravi Tanon 1 an Soheil Mohajer 1 Discovery Analytics Center & Department of Computer Science, Virginia Tech, Blacksburg, VA Department of Electrical
Conservation Laws. Chapter Conservation of Energy
 20 Chapter 3 Conservation Laws In orer to check the physical consistency of the above set of equations governing Maxwell-Lorentz electroynamics [(2.10) an (2.12) or (1.65) an (1.68)], we examine the action
20 Chapter 3 Conservation Laws In orer to check the physical consistency of the above set of equations governing Maxwell-Lorentz electroynamics [(2.10) an (2.12) or (1.65) an (1.68)], we examine the action
Optimal Cooperative Spectrum Sensing in Cognitive Sensor Networks
 Optimal Cooperative Spectrum Sensing in Cognitive Sensor Networks Hai Ngoc Pham, an Zhang, Paal E. Engelsta,,3, Tor Skeie,, Frank Eliassen, Department of Informatics, University of Oslo, Norway Simula
Optimal Cooperative Spectrum Sensing in Cognitive Sensor Networks Hai Ngoc Pham, an Zhang, Paal E. Engelsta,,3, Tor Skeie,, Frank Eliassen, Department of Informatics, University of Oslo, Norway Simula
Generalization of the persistent random walk to dimensions greater than 1
 PHYSICAL REVIEW E VOLUME 58, NUMBER 6 DECEMBER 1998 Generalization of the persistent ranom walk to imensions greater than 1 Marián Boguñá, Josep M. Porrà, an Jaume Masoliver Departament e Física Fonamental,
PHYSICAL REVIEW E VOLUME 58, NUMBER 6 DECEMBER 1998 Generalization of the persistent ranom walk to imensions greater than 1 Marián Boguñá, Josep M. Porrà, an Jaume Masoliver Departament e Física Fonamental,
Control-Data Separation across Edge and Cloud for Uplink Communications in C-RAN
 1 Control-Data Separation across Ege an Clou for Uplink Communications in C-RAN Jinkyu Kang, Osvalo Simeone, Joonhyuk Kang an Shlomo Shamai (Shitz) School of Engineering an Applie Sciences, Harvar University,
1 Control-Data Separation across Ege an Clou for Uplink Communications in C-RAN Jinkyu Kang, Osvalo Simeone, Joonhyuk Kang an Shlomo Shamai (Shitz) School of Engineering an Applie Sciences, Harvar University,
A Fair Comparison of Pull and Push Strategies in Large Distributed Networks
 1 A Fair Comparison of Pull an Push Strategies in Large Distribute Networks Wouter Minnebo an Benny Van Hout, Member, IEEE Abstract In this paper we compare the performance of the pull an push strategy
1 A Fair Comparison of Pull an Push Strategies in Large Distribute Networks Wouter Minnebo an Benny Van Hout, Member, IEEE Abstract In this paper we compare the performance of the pull an push strategy
Multi-edge Optimization of Low-Density Parity-Check Codes for Joint Source-Channel Coding
 Multi-ege Optimization of Low-Density Parity-Check Coes for Joint Source-Channel Coing H. V. Beltrão Neto an W. Henkel Jacobs University Bremen Campus Ring 1 D-28759 Bremen, Germany Email: {h.beltrao,
Multi-ege Optimization of Low-Density Parity-Check Coes for Joint Source-Channel Coing H. V. Beltrão Neto an W. Henkel Jacobs University Bremen Campus Ring 1 D-28759 Bremen, Germany Email: {h.beltrao,
On the Connectivity Analysis over Large-Scale Hybrid Wireless Networks
 This full text paper was peer reviewe at the irection of IEEE Communications Society subject matter experts for publication in the IEEE INFOCOM proceeings This paper was presente as part of the main Technical
This full text paper was peer reviewe at the irection of IEEE Communications Society subject matter experts for publication in the IEEE INFOCOM proceeings This paper was presente as part of the main Technical
WUCHEN LI AND STANLEY OSHER
 CONSTRAINED DYNAMICAL OPTIMAL TRANSPORT AND ITS LAGRANGIAN FORMULATION WUCHEN LI AND STANLEY OSHER Abstract. We propose ynamical optimal transport (OT) problems constraine in a parameterize probability
CONSTRAINED DYNAMICAL OPTIMAL TRANSPORT AND ITS LAGRANGIAN FORMULATION WUCHEN LI AND STANLEY OSHER Abstract. We propose ynamical optimal transport (OT) problems constraine in a parameterize probability
Qubit channels that achieve capacity with two states
 Qubit channels that achieve capacity with two states Dominic W. Berry Department of Physics, The University of Queenslan, Brisbane, Queenslan 4072, Australia Receive 22 December 2004; publishe 22 March
Qubit channels that achieve capacity with two states Dominic W. Berry Department of Physics, The University of Queenslan, Brisbane, Queenslan 4072, Australia Receive 22 December 2004; publishe 22 March
Rate-optimal schemes for Peer-to-Peer live streaming
 Rate-optimal schemes for Peer-to-Peer live streaming Laurent Massoulié an Any Twigg Thomson, Corporate Research Abstract In this paper we consier the problem of sening ata in real time from information
Rate-optimal schemes for Peer-to-Peer live streaming Laurent Massoulié an Any Twigg Thomson, Corporate Research Abstract In this paper we consier the problem of sening ata in real time from information
Optimal Power Allocation for Parallel Gaussian Broadcast Channels with Independent and Common Information
 SUBMIED O IEEE INERNAIONAL SYMPOSIUM ON INFORMAION HEORY, DE. 23 1 Optimal Power Allocation for Parallel Gaussian Broadcast hannels with Independent and ommon Information Nihar Jindal and Andrea Goldsmith
SUBMIED O IEEE INERNAIONAL SYMPOSIUM ON INFORMAION HEORY, DE. 23 1 Optimal Power Allocation for Parallel Gaussian Broadcast hannels with Independent and ommon Information Nihar Jindal and Andrea Goldsmith
Situation awareness of power system based on static voltage security region
 The 6th International Conference on Renewable Power Generation (RPG) 19 20 October 2017 Situation awareness of power system base on static voltage security region Fei Xiao, Zi-Qing Jiang, Qian Ai, Ran
The 6th International Conference on Renewable Power Generation (RPG) 19 20 October 2017 Situation awareness of power system base on static voltage security region Fei Xiao, Zi-Qing Jiang, Qian Ai, Ran
Calculus of Variations
 16.323 Lecture 5 Calculus of Variations Calculus of Variations Most books cover this material well, but Kirk Chapter 4 oes a particularly nice job. x(t) x* x*+ αδx (1) x*- αδx (1) αδx (1) αδx (1) t f t
16.323 Lecture 5 Calculus of Variations Calculus of Variations Most books cover this material well, but Kirk Chapter 4 oes a particularly nice job. x(t) x* x*+ αδx (1) x*- αδx (1) αδx (1) αδx (1) t f t
Optimal power-delay trade-offs in fading channels: small delay asymptotics
 Optimal power-delay trade-offs in fading channels: small delay asymptotics Randall A. Berry Dept. of EECS, Northwestern University 45 Sheridan Rd., Evanston IL 6008 Email: rberry@ece.northwestern.edu Abstract
Optimal power-delay trade-offs in fading channels: small delay asymptotics Randall A. Berry Dept. of EECS, Northwestern University 45 Sheridan Rd., Evanston IL 6008 Email: rberry@ece.northwestern.edu Abstract
Euler equations for multiple integrals
 Euler equations for multiple integrals January 22, 2013 Contents 1 Reminer of multivariable calculus 2 1.1 Vector ifferentiation......................... 2 1.2 Matrix ifferentiation........................
Euler equations for multiple integrals January 22, 2013 Contents 1 Reminer of multivariable calculus 2 1.1 Vector ifferentiation......................... 2 1.2 Matrix ifferentiation........................
Power Generation and Distribution via Distributed Coordination Control
 Power Generation an Distribution via Distribute Coorination Control Byeong-Yeon Kim, Kwang-Kyo Oh, an Hyo-Sung Ahn arxiv:407.4870v [math.oc] 8 Jul 204 Abstract This paper presents power coorination, power
Power Generation an Distribution via Distribute Coorination Control Byeong-Yeon Kim, Kwang-Kyo Oh, an Hyo-Sung Ahn arxiv:407.4870v [math.oc] 8 Jul 204 Abstract This paper presents power coorination, power
Lecture XII. where Φ is called the potential function. Let us introduce spherical coordinates defined through the relations
 Lecture XII Abstract We introuce the Laplace equation in spherical coorinates an apply the metho of separation of variables to solve it. This will generate three linear orinary secon orer ifferential equations:
Lecture XII Abstract We introuce the Laplace equation in spherical coorinates an apply the metho of separation of variables to solve it. This will generate three linear orinary secon orer ifferential equations:
Switching Time Optimization in Discretized Hybrid Dynamical Systems
 Switching Time Optimization in Discretize Hybri Dynamical Systems Kathrin Flaßkamp, To Murphey, an Sina Ober-Blöbaum Abstract Switching time optimization (STO) arises in systems that have a finite set
Switching Time Optimization in Discretize Hybri Dynamical Systems Kathrin Flaßkamp, To Murphey, an Sina Ober-Blöbaum Abstract Switching time optimization (STO) arises in systems that have a finite set
Adaptive Gain-Scheduled H Control of Linear Parameter-Varying Systems with Time-Delayed Elements
 Aaptive Gain-Scheule H Control of Linear Parameter-Varying Systems with ime-delaye Elements Yoshihiko Miyasato he Institute of Statistical Mathematics 4-6-7 Minami-Azabu, Minato-ku, okyo 6-8569, Japan
Aaptive Gain-Scheule H Control of Linear Parameter-Varying Systems with ime-delaye Elements Yoshihiko Miyasato he Institute of Statistical Mathematics 4-6-7 Minami-Azabu, Minato-ku, okyo 6-8569, Japan
Error Floors in LDPC Codes: Fast Simulation, Bounds and Hardware Emulation
 Error Floors in LDPC Coes: Fast Simulation, Bouns an Harware Emulation Pamela Lee, Lara Dolecek, Zhengya Zhang, Venkat Anantharam, Borivoje Nikolic, an Martin J. Wainwright EECS Department University of
Error Floors in LDPC Coes: Fast Simulation, Bouns an Harware Emulation Pamela Lee, Lara Dolecek, Zhengya Zhang, Venkat Anantharam, Borivoje Nikolic, an Martin J. Wainwright EECS Department University of
Lecture 6: Calculus. In Song Kim. September 7, 2011
 Lecture 6: Calculus In Song Kim September 7, 20 Introuction to Differential Calculus In our previous lecture we came up with several ways to analyze functions. We saw previously that the slope of a linear
Lecture 6: Calculus In Song Kim September 7, 20 Introuction to Differential Calculus In our previous lecture we came up with several ways to analyze functions. We saw previously that the slope of a linear
Robust Forward Algorithms via PAC-Bayes and Laplace Distributions. ω Q. Pr (y(ω x) < 0) = Pr A k
 A Proof of Lemma 2 B Proof of Lemma 3 Proof: Since the support of LL istributions is R, two such istributions are equivalent absolutely continuous with respect to each other an the ivergence is well-efine
A Proof of Lemma 2 B Proof of Lemma 3 Proof: Since the support of LL istributions is R, two such istributions are equivalent absolutely continuous with respect to each other an the ivergence is well-efine
Convergence of Random Walks
 Chapter 16 Convergence of Ranom Walks This lecture examines the convergence of ranom walks to the Wiener process. This is very important both physically an statistically, an illustrates the utility of
Chapter 16 Convergence of Ranom Walks This lecture examines the convergence of ranom walks to the Wiener process. This is very important both physically an statistically, an illustrates the utility of
Schrödinger s equation.
 Physics 342 Lecture 5 Schröinger s Equation Lecture 5 Physics 342 Quantum Mechanics I Wenesay, February 3r, 2010 Toay we iscuss Schröinger s equation an show that it supports the basic interpretation of
Physics 342 Lecture 5 Schröinger s Equation Lecture 5 Physics 342 Quantum Mechanics I Wenesay, February 3r, 2010 Toay we iscuss Schröinger s equation an show that it supports the basic interpretation of
Perturbation Analysis and Optimization of Stochastic Flow Networks
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. XX, NO. Y, MMM 2004 1 Perturbation Analysis an Optimization of Stochastic Flow Networks Gang Sun, Christos G. Cassanras, Yorai Wari, Christos G. Panayiotou,
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. XX, NO. Y, MMM 2004 1 Perturbation Analysis an Optimization of Stochastic Flow Networks Gang Sun, Christos G. Cassanras, Yorai Wari, Christos G. Panayiotou,
Markov Chains in Continuous Time
 Chapter 23 Markov Chains in Continuous Time Previously we looke at Markov chains, where the transitions betweenstatesoccurreatspecifietime- steps. That it, we mae time (a continuous variable) avance in
Chapter 23 Markov Chains in Continuous Time Previously we looke at Markov chains, where the transitions betweenstatesoccurreatspecifietime- steps. That it, we mae time (a continuous variable) avance in
JUST THE MATHS UNIT NUMBER DIFFERENTIATION 2 (Rates of change) A.J.Hobson
 JUST THE MATHS UNIT NUMBER 10.2 DIFFERENTIATION 2 (Rates of change) by A.J.Hobson 10.2.1 Introuction 10.2.2 Average rates of change 10.2.3 Instantaneous rates of change 10.2.4 Derivatives 10.2.5 Exercises
JUST THE MATHS UNIT NUMBER 10.2 DIFFERENTIATION 2 (Rates of change) by A.J.Hobson 10.2.1 Introuction 10.2.2 Average rates of change 10.2.3 Instantaneous rates of change 10.2.4 Derivatives 10.2.5 Exercises
inflow outflow Part I. Regular tasks for MAE598/494 Task 1
 MAE 494/598, Fall 2016 Project #1 (Regular tasks = 20 points) Har copy of report is ue at the start of class on the ue ate. The rules on collaboration will be release separately. Please always follow the
MAE 494/598, Fall 2016 Project #1 (Regular tasks = 20 points) Har copy of report is ue at the start of class on the ue ate. The rules on collaboration will be release separately. Please always follow the
Numerical Key Results for Studying the Performance of TCP Traffic under Class-Based Weighted Fair Queuing System
 Journal of ommunication an omputer 13 (2016) 195-201 oi:10.17265/1548-7709/2016.04.007 D DAVID PUBLISHING Numerical Key Results for Stuying the Performance of TP Traffic uner lass-base Weighte Fair Queuing
Journal of ommunication an omputer 13 (2016) 195-201 oi:10.17265/1548-7709/2016.04.007 D DAVID PUBLISHING Numerical Key Results for Stuying the Performance of TP Traffic uner lass-base Weighte Fair Queuing
Separation of Variables
 Physics 342 Lecture 1 Separation of Variables Lecture 1 Physics 342 Quantum Mechanics I Monay, January 25th, 2010 There are three basic mathematical tools we nee, an then we can begin working on the physical
Physics 342 Lecture 1 Separation of Variables Lecture 1 Physics 342 Quantum Mechanics I Monay, January 25th, 2010 There are three basic mathematical tools we nee, an then we can begin working on the physical
Dynamic Power Allocation and Routing for Time Varying Wireless Networks
 Dynamic Power Allocation and Routing for Time Varying Wireless Networks X 14 (t) X 12 (t) 1 3 4 k a P ak () t P a tot X 21 (t) 2 N X 2N (t) X N4 (t) µ ab () rate µ ab µ ab (p, S 3 ) µ ab µ ac () µ ab (p,
Dynamic Power Allocation and Routing for Time Varying Wireless Networks X 14 (t) X 12 (t) 1 3 4 k a P ak () t P a tot X 21 (t) 2 N X 2N (t) X N4 (t) µ ab () rate µ ab µ ab (p, S 3 ) µ ab µ ac () µ ab (p,
Exponential Tracking Control of Nonlinear Systems with Actuator Nonlinearity
 Preprints of the 9th Worl Congress The International Feeration of Automatic Control Cape Town, South Africa. August -9, Exponential Tracking Control of Nonlinear Systems with Actuator Nonlinearity Zhengqiang
Preprints of the 9th Worl Congress The International Feeration of Automatic Control Cape Town, South Africa. August -9, Exponential Tracking Control of Nonlinear Systems with Actuator Nonlinearity Zhengqiang
IPA Derivatives for Make-to-Stock Production-Inventory Systems With Backorders Under the (R,r) Policy
 IPA Derivatives for Make-to-Stock Prouction-Inventory Systems With Backorers Uner the (Rr) Policy Yihong Fan a Benamin Melame b Yao Zhao c Yorai Wari Abstract This paper aresses Infinitesimal Perturbation
IPA Derivatives for Make-to-Stock Prouction-Inventory Systems With Backorers Uner the (Rr) Policy Yihong Fan a Benamin Melame b Yao Zhao c Yorai Wari Abstract This paper aresses Infinitesimal Perturbation
12.11 Laplace s Equation in Cylindrical and
 SEC. 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential 593 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential One of the most important PDEs in physics an engineering
SEC. 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential 593 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential One of the most important PDEs in physics an engineering
Applications of First Order Equations
 Applications of First Orer Equations Viscous Friction Consier a small mass that has been roppe into a thin vertical tube of viscous flui lie oil. The mass falls, ue to the force of gravity, but falls more
Applications of First Orer Equations Viscous Friction Consier a small mass that has been roppe into a thin vertical tube of viscous flui lie oil. The mass falls, ue to the force of gravity, but falls more
Math 1271 Solutions for Fall 2005 Final Exam
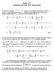 Math 7 Solutions for Fall 5 Final Eam ) Since the equation + y = e y cannot be rearrange algebraically in orer to write y as an eplicit function of, we must instea ifferentiate this relation implicitly
Math 7 Solutions for Fall 5 Final Eam ) Since the equation + y = e y cannot be rearrange algebraically in orer to write y as an eplicit function of, we must instea ifferentiate this relation implicitly
Online Appendix for Trade Policy under Monopolistic Competition with Firm Selection
 Online Appenix for Trae Policy uner Monopolistic Competition with Firm Selection Kyle Bagwell Stanfor University an NBER Seung Hoon Lee Georgia Institute of Technology September 6, 2018 In this Online
Online Appenix for Trae Policy uner Monopolistic Competition with Firm Selection Kyle Bagwell Stanfor University an NBER Seung Hoon Lee Georgia Institute of Technology September 6, 2018 In this Online
Channel Allocation Using Pricing in Satellite Networks
 Channel Allocation Using Pricing in Satellite Networks Jun Sun and Eytan Modiano Laboratory for Information and Decision Systems Massachusetts Institute of Technology {junsun, modiano}@mitedu Abstract
Channel Allocation Using Pricing in Satellite Networks Jun Sun and Eytan Modiano Laboratory for Information and Decision Systems Massachusetts Institute of Technology {junsun, modiano}@mitedu Abstract
Energy Harvesting Multiple Access Channel with Peak Temperature Constraints
 Energy Harvesting Multiple Access Channel with Peak Temperature Constraints Abdulrahman Baknina, Omur Ozel 2, and Sennur Ulukus Department of Electrical and Computer Engineering, University of Maryland,
Energy Harvesting Multiple Access Channel with Peak Temperature Constraints Abdulrahman Baknina, Omur Ozel 2, and Sennur Ulukus Department of Electrical and Computer Engineering, University of Maryland,
Proof of SPNs as Mixture of Trees
 A Proof of SPNs as Mixture of Trees Theorem 1. If T is an inuce SPN from a complete an ecomposable SPN S, then T is a tree that is complete an ecomposable. Proof. Argue by contraiction that T is not a
A Proof of SPNs as Mixture of Trees Theorem 1. If T is an inuce SPN from a complete an ecomposable SPN S, then T is a tree that is complete an ecomposable. Proof. Argue by contraiction that T is not a
Minimum-time constrained velocity planning
 7th Meiterranean Conference on Control & Automation Makeonia Palace, Thessaloniki, Greece June 4-6, 9 Minimum-time constraine velocity planning Gabriele Lini, Luca Consolini, Aurelio Piazzi Università
7th Meiterranean Conference on Control & Automation Makeonia Palace, Thessaloniki, Greece June 4-6, 9 Minimum-time constraine velocity planning Gabriele Lini, Luca Consolini, Aurelio Piazzi Università
Yaakov (Jonathan) Stein, RAD Data Communications and Brian Stroehlein, TranSwitch Corporation
 Using ynchronization over PN Does IEEE 1588 M Really Mae a Difference? Yaaov (Jonathan) tein, RAD Data Communications an Brian troehlein, ranwitch Corporation pecial thans to Alon Geva, DP Algorithm eam
Using ynchronization over PN Does IEEE 1588 M Really Mae a Difference? Yaaov (Jonathan) tein, RAD Data Communications an Brian troehlein, ranwitch Corporation pecial thans to Alon Geva, DP Algorithm eam
Lecture 2 Lagrangian formulation of classical mechanics Mechanics
 Lecture Lagrangian formulation of classical mechanics 70.00 Mechanics Principle of stationary action MATH-GA To specify a motion uniquely in classical mechanics, it suffices to give, at some time t 0,
Lecture Lagrangian formulation of classical mechanics 70.00 Mechanics Principle of stationary action MATH-GA To specify a motion uniquely in classical mechanics, it suffices to give, at some time t 0,
A note on asymptotic formulae for one-dimensional network flow problems Carlos F. Daganzo and Karen R. Smilowitz
 A note on asymptotic formulae for one-imensional network flow problems Carlos F. Daganzo an Karen R. Smilowitz (to appear in Annals of Operations Research) Abstract This note evelops asymptotic formulae
A note on asymptotic formulae for one-imensional network flow problems Carlos F. Daganzo an Karen R. Smilowitz (to appear in Annals of Operations Research) Abstract This note evelops asymptotic formulae
PDE Notes, Lecture #11
 PDE Notes, Lecture # from Professor Jalal Shatah s Lectures Febuary 9th, 2009 Sobolev Spaces Recall that for u L loc we can efine the weak erivative Du by Du, φ := udφ φ C0 If v L loc such that Du, φ =
PDE Notes, Lecture # from Professor Jalal Shatah s Lectures Febuary 9th, 2009 Sobolev Spaces Recall that for u L loc we can efine the weak erivative Du by Du, φ := udφ φ C0 If v L loc such that Du, φ =
7.1 Support Vector Machine
 67577 Intro. to Machine Learning Fall semester, 006/7 Lecture 7: Support Vector Machines an Kernel Functions II Lecturer: Amnon Shashua Scribe: Amnon Shashua 7. Support Vector Machine We return now to
67577 Intro. to Machine Learning Fall semester, 006/7 Lecture 7: Support Vector Machines an Kernel Functions II Lecturer: Amnon Shashua Scribe: Amnon Shashua 7. Support Vector Machine We return now to
Agmon Kolmogorov Inequalities on l 2 (Z d )
 Journal of Mathematics Research; Vol. 6, No. ; 04 ISSN 96-9795 E-ISSN 96-9809 Publishe by Canaian Center of Science an Eucation Agmon Kolmogorov Inequalities on l (Z ) Arman Sahovic Mathematics Department,
Journal of Mathematics Research; Vol. 6, No. ; 04 ISSN 96-9795 E-ISSN 96-9809 Publishe by Canaian Center of Science an Eucation Agmon Kolmogorov Inequalities on l (Z ) Arman Sahovic Mathematics Department,
The continuity equation
 Chapter 6 The continuity equation 61 The equation of continuity It is evient that in a certain region of space the matter entering it must be equal to the matter leaving it Let us consier an infinitesimal
Chapter 6 The continuity equation 61 The equation of continuity It is evient that in a certain region of space the matter entering it must be equal to the matter leaving it Let us consier an infinitesimal
Non-deterministic Social Laws
 Non-eterministic Social Laws Michael H. Coen MIT Artificial Intelligence Lab 55 Technology Square Cambrige, MA 09 mhcoen@ai.mit.eu Abstract The paper generalizes the notion of a social law, the founation
Non-eterministic Social Laws Michael H. Coen MIT Artificial Intelligence Lab 55 Technology Square Cambrige, MA 09 mhcoen@ai.mit.eu Abstract The paper generalizes the notion of a social law, the founation
Equilibrium in Queues Under Unknown Service Times and Service Value
 University of Pennsylvania ScholarlyCommons Finance Papers Wharton Faculty Research 1-2014 Equilibrium in Queues Uner Unknown Service Times an Service Value Laurens Debo Senthil K. Veeraraghavan University
University of Pennsylvania ScholarlyCommons Finance Papers Wharton Faculty Research 1-2014 Equilibrium in Queues Uner Unknown Service Times an Service Value Laurens Debo Senthil K. Veeraraghavan University
d dx But have you ever seen a derivation of these results? We ll prove the first result below. cos h 1
 Lecture 5 Some ifferentiation rules Trigonometric functions (Relevant section from Stewart, Seventh Eition: Section 3.3) You all know that sin = cos cos = sin. () But have you ever seen a erivation of
Lecture 5 Some ifferentiation rules Trigonometric functions (Relevant section from Stewart, Seventh Eition: Section 3.3) You all know that sin = cos cos = sin. () But have you ever seen a erivation of
Stopping-Set Enumerator Approximations for Finite-Length Protograph LDPC Codes
 Stopping-Set Enumerator Approximations for Finite-Length Protograph LDPC Coes Kaiann Fu an Achilleas Anastasopoulos Electrical Engineering an Computer Science Dept. University of Michigan, Ann Arbor, MI
Stopping-Set Enumerator Approximations for Finite-Length Protograph LDPC Coes Kaiann Fu an Achilleas Anastasopoulos Electrical Engineering an Computer Science Dept. University of Michigan, Ann Arbor, MI
Nested Saturation with Guaranteed Real Poles 1
 Neste Saturation with Guarantee Real Poles Eric N Johnson 2 an Suresh K Kannan 3 School of Aerospace Engineering Georgia Institute of Technology, Atlanta, GA 3332 Abstract The global stabilization of asymptotically
Neste Saturation with Guarantee Real Poles Eric N Johnson 2 an Suresh K Kannan 3 School of Aerospace Engineering Georgia Institute of Technology, Atlanta, GA 3332 Abstract The global stabilization of asymptotically
Multi-agent Systems Reaching Optimal Consensus with Time-varying Communication Graphs
 Preprints of the 8th IFAC Worl Congress Multi-agent Systems Reaching Optimal Consensus with Time-varying Communication Graphs Guoong Shi ACCESS Linnaeus Centre, School of Electrical Engineering, Royal
Preprints of the 8th IFAC Worl Congress Multi-agent Systems Reaching Optimal Consensus with Time-varying Communication Graphs Guoong Shi ACCESS Linnaeus Centre, School of Electrical Engineering, Royal
CMSC 858F: Algorithmic Game Theory Fall 2010 BGP and Interdomain Routing
 CMSC 858F: Algorithmic Game Theory Fall 2010 BGP an Interomain Routing Instructor: Mohamma T. Hajiaghayi Scribe: Yuk Hei Chan November 3, 2010 1 Overview In this lecture, we cover BGP (Borer Gateway Protocol)
CMSC 858F: Algorithmic Game Theory Fall 2010 BGP an Interomain Routing Instructor: Mohamma T. Hajiaghayi Scribe: Yuk Hei Chan November 3, 2010 1 Overview In this lecture, we cover BGP (Borer Gateway Protocol)
Any Work-conserving Policy Stabilizes the Ring with Spatial Reuse
 Any Work-conserving Policy Stabilizes the Ring with Spatial Reuse L. assiulas y Dept. of Electrical Engineering Polytechnic University Brooklyn, NY 20 leandros@olympos.poly.edu L. Georgiadis IBM. J. Watson
Any Work-conserving Policy Stabilizes the Ring with Spatial Reuse L. assiulas y Dept. of Electrical Engineering Polytechnic University Brooklyn, NY 20 leandros@olympos.poly.edu L. Georgiadis IBM. J. Watson
Relative Entropy and Score Function: New Information Estimation Relationships through Arbitrary Additive Perturbation
 Relative Entropy an Score Function: New Information Estimation Relationships through Arbitrary Aitive Perturbation Dongning Guo Department of Electrical Engineering & Computer Science Northwestern University
Relative Entropy an Score Function: New Information Estimation Relationships through Arbitrary Aitive Perturbation Dongning Guo Department of Electrical Engineering & Computer Science Northwestern University
Laplacian Cooperative Attitude Control of Multiple Rigid Bodies
 Laplacian Cooperative Attitue Control of Multiple Rigi Boies Dimos V. Dimarogonas, Panagiotis Tsiotras an Kostas J. Kyriakopoulos Abstract Motivate by the fact that linear controllers can stabilize the
Laplacian Cooperative Attitue Control of Multiple Rigi Boies Dimos V. Dimarogonas, Panagiotis Tsiotras an Kostas J. Kyriakopoulos Abstract Motivate by the fact that linear controllers can stabilize the
Single Server Retrial Bulk Queue With Two Phases Of Essential Server And Vacation Policy
 Single Server Retrial Bul Queue With Two Phases Of Essential Server An Vacation Policy Dr. S.Anan Gnana Selvam, 2 Dr.. Reni Sagayara, 3 S. Janci Rani Department of athematics, A.E.T Arts an Science College,
Single Server Retrial Bul Queue With Two Phases Of Essential Server An Vacation Policy Dr. S.Anan Gnana Selvam, 2 Dr.. Reni Sagayara, 3 S. Janci Rani Department of athematics, A.E.T Arts an Science College,
Fast Structuring of Radio Networks
 Fast Structuring of Raio Networks for Multi-Message Communications Mohsen Ghaffari ghaffari@mit.eu MIT Bernhar Haeupler haeupler@mit.eu MIT Abstract We introuce collision free layerings as a powerful way
Fast Structuring of Raio Networks for Multi-Message Communications Mohsen Ghaffari ghaffari@mit.eu MIT Bernhar Haeupler haeupler@mit.eu MIT Abstract We introuce collision free layerings as a powerful way
Quantum mechanical approaches to the virial
 Quantum mechanical approaches to the virial S.LeBohec Department of Physics an Astronomy, University of Utah, Salt Lae City, UT 84112, USA Date: June 30 th 2015 In this note, we approach the virial from
Quantum mechanical approaches to the virial S.LeBohec Department of Physics an Astronomy, University of Utah, Salt Lae City, UT 84112, USA Date: June 30 th 2015 In this note, we approach the virial from
Optimal Variable-Structure Control Tracking of Spacecraft Maneuvers
 Optimal Variable-Structure Control racking of Spacecraft Maneuvers John L. Crassiis 1 Srinivas R. Vaali F. Lanis Markley 3 Introuction In recent years, much effort has been evote to the close-loop esign
Optimal Variable-Structure Control racking of Spacecraft Maneuvers John L. Crassiis 1 Srinivas R. Vaali F. Lanis Markley 3 Introuction In recent years, much effort has been evote to the close-loop esign
Flow Control for Cost-Efficient Peer-to-Peer Streaming
 This full text paper was peer reviewe at the irection of IEEE Communications Society subject matter experts for publication in the IEEE INFOCOM 21 proceeings This paper was presente as part of the main
This full text paper was peer reviewe at the irection of IEEE Communications Society subject matter experts for publication in the IEEE INFOCOM 21 proceeings This paper was presente as part of the main
Output Feedback Stabilization of Networked Control Systems With Random Delays Modeled by Markov Chains
 668 IEEE RANSACIONS ON AUOMAIC CONROL, VOL 54, NO 7, JULY 29 Output Feeback Stabilization of Networke Control Systems With Ranom Delays Moele by Markov Chains Yang Shi, Member, IEEE, an Bo Yu, Stuent Member,
668 IEEE RANSACIONS ON AUOMAIC CONROL, VOL 54, NO 7, JULY 29 Output Feeback Stabilization of Networke Control Systems With Ranom Delays Moele by Markov Chains Yang Shi, Member, IEEE, an Bo Yu, Stuent Member,
Slide10 Haykin Chapter 14: Neurodynamics (3rd Ed. Chapter 13)
 Slie10 Haykin Chapter 14: Neuroynamics (3r E. Chapter 13) CPSC 636-600 Instructor: Yoonsuck Choe Spring 2012 Neural Networks with Temporal Behavior Inclusion of feeback gives temporal characteristics to
Slie10 Haykin Chapter 14: Neuroynamics (3r E. Chapter 13) CPSC 636-600 Instructor: Yoonsuck Choe Spring 2012 Neural Networks with Temporal Behavior Inclusion of feeback gives temporal characteristics to
On the Throughput, Capacity and Stability Regions of Random Multiple Access over Standard Multi-Packet Reception Channels
 On the Throughput, Capacity and Stability Regions of Random Multiple Access over Standard Multi-Packet Reception Channels Jie Luo, Anthony Ephremides ECE Dept. Univ. of Maryland College Park, MD 20742
On the Throughput, Capacity and Stability Regions of Random Multiple Access over Standard Multi-Packet Reception Channels Jie Luo, Anthony Ephremides ECE Dept. Univ. of Maryland College Park, MD 20742
Lower bounds on Locality Sensitive Hashing
 Lower bouns on Locality Sensitive Hashing Rajeev Motwani Assaf Naor Rina Panigrahy Abstract Given a metric space (X, X ), c 1, r > 0, an p, q [0, 1], a istribution over mappings H : X N is calle a (r,
Lower bouns on Locality Sensitive Hashing Rajeev Motwani Assaf Naor Rina Panigrahy Abstract Given a metric space (X, X ), c 1, r > 0, an p, q [0, 1], a istribution over mappings H : X N is calle a (r,
Chapter 4. Electrostatics of Macroscopic Media
 Chapter 4. Electrostatics of Macroscopic Meia 4.1 Multipole Expansion Approximate potentials at large istances 3 x' x' (x') x x' x x Fig 4.1 We consier the potential in the far-fiel region (see Fig. 4.1
Chapter 4. Electrostatics of Macroscopic Meia 4.1 Multipole Expansion Approximate potentials at large istances 3 x' x' (x') x x' x x Fig 4.1 We consier the potential in the far-fiel region (see Fig. 4.1
FLUCTUATIONS IN THE NUMBER OF POINTS ON SMOOTH PLANE CURVES OVER FINITE FIELDS. 1. Introduction
 FLUCTUATIONS IN THE NUMBER OF POINTS ON SMOOTH PLANE CURVES OVER FINITE FIELDS ALINA BUCUR, CHANTAL DAVID, BROOKE FEIGON, MATILDE LALÍN 1 Introuction In this note, we stuy the fluctuations in the number
FLUCTUATIONS IN THE NUMBER OF POINTS ON SMOOTH PLANE CURVES OVER FINITE FIELDS ALINA BUCUR, CHANTAL DAVID, BROOKE FEIGON, MATILDE LALÍN 1 Introuction In this note, we stuy the fluctuations in the number
The derivative of a function f(x) is another function, defined in terms of a limiting expression: f(x + δx) f(x)
 Y. D. Chong (2016) MH2801: Complex Methos for the Sciences 1. Derivatives The erivative of a function f(x) is another function, efine in terms of a limiting expression: f (x) f (x) lim x δx 0 f(x + δx)
Y. D. Chong (2016) MH2801: Complex Methos for the Sciences 1. Derivatives The erivative of a function f(x) is another function, efine in terms of a limiting expression: f (x) f (x) lim x δx 0 f(x + δx)
Towards Achieving Full Secrecy Rate and Low Delays in Wireless Networks
 owards Achieving Full Secrecy Rate and Low Delays in Wireless Networks Zhoujia Mao Department of ECE he Ohio State University maoz@ece.osu.edu Can Emre Koksal Department of ECE he Ohio State University
owards Achieving Full Secrecy Rate and Low Delays in Wireless Networks Zhoujia Mao Department of ECE he Ohio State University maoz@ece.osu.edu Can Emre Koksal Department of ECE he Ohio State University
Power Allocation and Coverage for a Relay-Assisted Downlink with Voice Users
 Power Allocation and Coverage for a Relay-Assisted Downlink with Voice Users Junjik Bae, Randall Berry, and Michael L. Honig Department of Electrical Engineering and Computer Science Northwestern University,
Power Allocation and Coverage for a Relay-Assisted Downlink with Voice Users Junjik Bae, Randall Berry, and Michael L. Honig Department of Electrical Engineering and Computer Science Northwestern University,
A Simple Model for the Calculation of Plasma Impedance in Atmospheric Radio Frequency Discharges
 Plasma Science an Technology, Vol.16, No.1, Oct. 214 A Simple Moel for the Calculation of Plasma Impeance in Atmospheric Raio Frequency Discharges GE Lei ( ) an ZHANG Yuantao ( ) Shanong Provincial Key
Plasma Science an Technology, Vol.16, No.1, Oct. 214 A Simple Moel for the Calculation of Plasma Impeance in Atmospheric Raio Frequency Discharges GE Lei ( ) an ZHANG Yuantao ( ) Shanong Provincial Key
