Node Density and Delay in Large-Scale Wireless Networks with Unreliable Links
|
|
|
- Gwen Willis
- 5 years ago
- Views:
Transcription
1 Noe Density an Delay in Large-Scale Wireless Networks with Unreliable Links Shizhen Zhao, Xinbing Wang Department of Electronic Engineering Shanghai Jiao Tong University, China Abstract We stuy the elay performance in large-scale wireless multi-hop networks with unreliable links from percolation perspective. Previous works [][3][] have showe that the en-to-en elay scales linearly with the source-to-estination istance, an thus the elay performance can be characterize by the elay-istance ratio γ. However, the range of γ, which may be the most important parameter for elay, remains unknown. We expect that γ may epen heavily on the noe ensity of a wireless multi-hop network. In this paper, we investigate the funamental relationship between γ an. Obtaining the exact value of γ() is extremely har, mainly because of the ynamically changing network topologies cause by the link unreliability. Instea, we provie both upper boun an lower boun to the elay-istance ratio γ(). Simulations are conucte to verify our theoretical analysis. Inex Terms Connectivity, Delay, Density I. INTRODUCTION Large-scale wireless multi-hop networks are fast becoming the most preferre way for communication in outoor environment []. Each user in a wireless multi-hop network coul initiate a communication in a multi-hop fashion without of the ai of any network infrastructure. Thus, the maintenance cost for communication networks can be significantly reuce. However, relays of a wireless multi-hop network may be also users, which are highly unreliable ue to the unexpecte user behavior an the time-varying wireless channel. Thus, it is highly possible that a connection may get lost uring ata transmission, in which case the ata has to wait at some noe an resume its transmission after the reestablishment of the network connection. The lost of connection coul cause significant elay to ata transmission. Therefore, it is very critical to provie some elay guarantee for wireless multi-hop networks. Note that the ata communication reliability can be improve by some back-up routes, an it is usually easier to fin more routes when the noe ensity is higher. Hence, we expect that the ata communication elay may epen heavily on the noe ensity. Our goal in this paper is to quantify the funamental relationship between noe ensity an elay. To make our stuy meaningful, we assume that the largescale wireless network is connecte. Full connectivity [] can ensure the successful communication between each noe pair in a wireless network. However, it is overly power consuming to achieve full connectivity in large-scale networks (i.e., the An earlier version of this paper appeare in ACM MobiCom [9] power require to maintain full connectivity increases with the size of the network). Hence, it is necessary to introuce a slightly weaker connectivity criterion, in which we only ensure that a large portion of the network noes are connecte via multiple hops with each other. Thanks to percolation theory [][5], it is possible to achieve this weaker connectivity in large-scale networks with power boune per noe. Percolation theory [], especially continuum percolation, is a powerful mathematical tool when analyzing the connectivity an the elay of wireless networks. An important an general moel of Continuum Percolation is Ranom Connection Moel (RCM). RCM escribes the behavior of connecte components in an infinitely large ranom geometric graph, in which noes are istribute accoring to poisson point process with noe ensity, an two noes share a link with probability h(r) (r is the istance between the two noes). A classical result of RCM points out a funamental phase transition effect at a critical noe ensity c (, ). For > c (supercritical), there exists a unique connecte component containing a large portion of noes in the infinitely large network (we also say the network is percolate). However, for < c (subcritical), all connecte component in the network are finite almost surely. Applying percolation theory to large-scale wireless multihop networks, we introuce two important concepts, i.e., the instantaneous connectivity an the long-term connectivity. The Instantaneous connectivity requires wireless networks percolate at all the time instances. While the long-term connectivity only requires wireless network percolate in the long run (we will elaborate it more clearly later in sectionii-b). The instantaneous critical ensity, enote by I, is the critical ensity for the instantaneous connectivity an the long-term critical ensity, enote by L, is the critical ensity for the long-term connectivity. Long-term connectivity is a weaker criterion for connectivity, thus L < I. To ensure connectivity, we assume that > L throughout this paper. In large-scale wireless networks, elay is mainly compose of the waiting elay an the propagation elay. The waiting elay is cause by the loss of connection at some time instances, which is ue to the lack of instantaneous connectivity. Packets must wait for some time until the connection is reestablishe. Usually, such a waiting time is in the orer of secons, minutes or more. The propagation elay is the time require for a packet to transverse a link whenever the link is active. Mostly, the propagation elay is in the orer of millisecons.
2 Therefore, it is negligibly small compare to the waiting elay. For ease of analysis, we first ignore the impact of propagation elay an will consier its effect in the last. We stuy the elay performance for flooing in large-scale wireless networks. Ignoring the propagation elay, previous works [][3][] have showe that if L < < I, the en-to-en elay scales linearly with the source-to-estination istance (γ() > ), an that if > I, the en-to-en elay scales sub-linearly with istance (γ() = ). However, these results are far from enough to provie reasonable elay guarantee. It remains extremely important to fin out the exact value or the lower an upper bouns of γ(). In this paper, we present a theoretical analysis about the flooing elay in wireless multi-hop networks with unreliable links. We first ignore the propagation elay an fin the upper an lower bouns of γ(). For the upper boun, we first fin a path between two noes using percolation theory. An then we calculate the number of hops along this path using another coupling technique an the elay at each hop. We obtain the result of upper boun by multiplying the above two items. For the lower boun, we first introuce a concept calle cluster to cluster transmission process an establish the relationship between elay an the cluster to cluster transmission process, which reveals the essence of the flooing elay in wireless multi-hop networks. Then, base on the elay of the cluster to cluster transmission, we obtain a lower boun of γ(). We then generalize the previous result to the case with nonzero propagation elay. Propagation elay will aggravate the elay performance in Large-Scale wireless Networks, making γ() > even when > I. Using similar methos, we present new upper an lower bouns to γ() for all > L. Finally, we conuct simulation to verify our theoretical results. The original contributions that we have mae in the paper are highlighte as follows: We present two properties to γ(), i.e., γ() = whenever propagation elay is an > I ; γ() is a monotone ecreasing function. Ignoring propagation elay, we provie the upper boun an the lower boun to reflect the range of variation on γ(). Taking propagation elay into consieration, we obtain further results. We conuct simulations to obtain experimental values of γ() in the above two cases. The new observation arises from our comparison between theoretical an simulation results is that the elay-istance ratio γ() can be approximate by the lower boun in relative ense networks while the experimental values of γ() get closer to the upper boun in relative sparse networks. This also justifies the sounness of our theoretical conclusion. The rest of the paper is organize as follows. In section II, we introuce our network moel, several useful mathematical tools an some important notations. In section III, we first give two properties of γ(), an then present our main results concerning the upper an lower boun of γ(). The analysis for obtaining the upper an lower bouns is given in section IV. Simulation results are presente in Section VI to justify our theoretical finings. We summarize the paper in Section VII. Some proofs of the theorems an lemmas are presente in section V. II. BACKGROUND AND NETWORK MODEL In this section, we introuce some backgroun knowlege an the network moel. A. Backgroun ) Poisson Point Process: In large-scale wireless multi-hop networks, it is extremely ifficult to preict the exact locations of ifferent users (noes) ue to the ranom behavior of ifferent users. To moel the location-ranomness, we use Poisson Point Process []. One way to visualize the Poisson Point Process is to assume that all users are istribute uniformly in a given area, e.g., n noes are evenly istribute in a n n area. If we let n, then the istribution of these ranom processes (inexe by n) will converge in istribution to Poisson Point Process with rate. Poisson Point Process has the following two properties: The superposition of two inepenent Poisson Point Processes is still a Poisson Point Process. The number of noes counte in isjoint areas are inepenent from each other (spatial inepenence). As reaers will see, the above two properties are extremely useful in our analysis. ) Ranom Connection Moel: Before introucing the network moel, we nee a brief introuction to Continuum Percolation. Connectivity is a significant issue in wireless network, which has been extensively explore by [][5][][7][][9]. In this paper, we present the efinition of connectivity in the percolation perspective. To make the results in this paper applicable to the most scenarios, we focus on a fairly general moel in Continuum Percolation Theory, i.e., the Ranom Connection Moel(RCM) [5]. In the RCM, noes are istribute accoring to Poisson point process in R. Here we only focus on the case of R with noe ensity >. Each noe x connects to another noe y accoring to some preefine connection function h(r), where r = x y is the istance between x an y. Specifically, noes x an y are connecte with probability h(r). We assume that h(r) satisfies < R h(r)xy <, which ensures the phase transition effect [5] in the Ranom Connection Moel. We enote a RCM by G(, r, h(r)), where is the noe ensity, r = sup{r h(r) > }, h(r) is the connection function. Then G(, r, h(r)) is a set of noes connecte by ranom links. For convenience, we assume that the origin G(, r, h(r)). Obviously, G(, r, h(r)) is compose of a set of isjointe connecte components. Let us enote W (A), A G(, r, h(r)), the set of noes attainable from noes in set A, i.e., W (A) = {x G(, r, h(r)) a A, a x}, In general, a RCM can be fully etermine by an h(r) only. We just use r to emphasize that we only focus on functions h(r) that are for r larger than some finite value r.
3 3 where, a x means that noes a an x are in the same connecte component. Besies, we use W to represent the carinality of the set W. Further, we efine θ h () = P,h ( W ({}) = ) 3 an χ h () = E,h ( W ({}) ). Then, the critical ensity can be etermine in two ways, i.e., θ (h) = inf{ θ h () > }; () (a) Illustration of connection function g(r). (b) Illustration of connection function f(r). χ (h) = inf{ χ h () = }. () Fig.. Illustration of two connection functions. Accoring to Theorem. in [5], < θ (h) = χ (h) = c (h) <. Furthermore, there exists a unique infinite connecte component containing a large portion of the noes in G(, r, h(r)) with probability if > c (h) (supercritical). This infinite connecte component is also calle the giant component, enote by C(G(, r, h(r))). In this case, we call G(, r, h(r)) percolate. On the other han, if < c (h) (subcritical), all the connecte components are finite almost surely. Another useful moel in Continuum Percolation is Poisson Boolean Moel, enote by B(, r). In the Poisson Boolean Moel B(, r), noes are istribute accoring to Poisson Point Process with ensity, an two noes can communicate if an only if their istance is smaller than r. Poisson Boolean Moel can be viewe as a special case of Ranom Connection Moel. Thus, the conclusions for Ranom Connection Moel also hol for Poisson Boolean Moel. B. Moel ) Network Moel: We moel the large-scale wireless multi-hop network as a ranom graph with ynamically varying eges. We assume that the network noes are istribute accoring to Poisson Point Process with noe ensity in an infinite two-imensional space R. For each noe u, we use u to represent both this noe an its location without causing confusion. We say two noes share a link if an only if their istance is smaller than r. However, ue to the unreliability of the wireless channel an the unexpecte user behaviors, each link suffers the possibility to fail. We say a link open at a time slot if this link can successfully transmit a packet, an close otherwise. We moel the link failure as each link opening or closing intermittently. Specifically, we assume that time is slotte, an the uration of each time slot is. Consier a link with length r, at time slot t. We let it open with probability g(r) (Fig. ), inepenent of its former states. In reality, the farther two noes are apart, the more ifficult for a successful communication. Moveover, when r > r, there exists no link. Thus, it is reasonable to assume that g(r) is a monotone ecreasing function an g(r) = whenever r > r. Further, we place another constraint on g(r), i.e., > g() g(r) g(r ) >, r r. (3) As reaers will see, constraint (3) is use to ensure that the expecte traversing elay over each possible link is boune above. 3 P is the probability of a event. E(x) is the expectation of ranom variable x Base on the above iscussion, the network at each time slot t can be represente by a RCM G t (, r, g(r)). Here, we use subscript t to inicate that the network is ynamic. Note that if > c (g(r)), G t (, r, g(r)) is percolate for all t (we also say the network has instantaneous connectivity); while if < c (g(r)), G t (, r, g(r)) is not percolate for all t. Thus, the instantaneous critical ensity I = c (g(r)). Next, we introuce the concept of the long-term connectivity. We first construct a new graph. The location of all noes in this graph is the same as that in G t (, r, g(r)). Two noes x an y share a link in this graph if an only if there exist t, such that x an y share an open link in G t (, r, g(r)). Note that x an y has the potential to share a link in G t (, r, g(r)) for some t, whenever g(r) > (equivalently, r < r ). Thus this new geometric graph can be represente by a RCM G(, r, f(r)) (it can be also represente by Poisson Boolean Moel B(, r )). Here, f(r) = when r < r, an f(r) = when r > r (Fig. ). We say the wireless network has longterm connectivity if an only if G(, r, f(r)) is percolate, an the critical ensity L = c (f(r)) is efine as the longterm critical ensity. Note that the long-term connectivity graph G(, r, f(r)) is a super-graph of all the instantaneous connectivity graph G t (, r, g(r)). Thus, whenever G t (, r, g(r)) is percolate, G(, r, f(r)) is percolate. Base on this observation, it is easy to know that L I. Since the prerequisite for communication in large-scale wireless network is connectivity, it is enough to only focus on the case > L. ) Moeling Delay in Large-Scale Wireless Networks: The efinition of elay of large-scale network is base on the First Passage Percolation []. Specifically, given a Ranom Connection Moel G(, r, h(r)), we attach each link e of G(, r, h(r)) a ranom variable T c (e), representing the time neee to pass through the link e. Consier a path π, the passage time is efine as T p (π) = e π(t c (e)). We then efine the first-passage time T (x, y) for any two noes x an y (x, y are not necessarily ajacent) as the minimum elay among all possible routes, i.e., T (x, y) = inf {T p (π) : π is a path from x to y}. () We now give the etaile efinition of T c (e). Generally, the time neee to cross the link e is compose of two parts. The first part is calle waiting elay, which is cause by the unreliability of this link. The secon part is calle propagation
4 elay 5, which is the time require for a packet to transverse the link e whenever the link is on. We assume that the uration of a time slot is long enough for a packet to be successfully transmitte over a link. Equivalently, the propagation elay over a link is smaller than time slot. For ease of analysis, we assume that all active links can transmit simultaneously with the same propagation elay, where < time slot. Base on the above iscussion, we can express the crossing time T c (e) as a geometrically istribute ranom variable. Specifically, assume that the length of the link e is < r < r, then we have P(T c (e) = k + ) = ( g(r)) k g(r). (5) Now we are reay to introuce the elay-istance ratio γ(). Consier two noes x, y C(G(, r, f(r))). Previous works [][3][] have prove that, the two its T (x,y) E(T (x,y) (x,y) an (x,y)) (x,y) (x,y) exist almost surely. Furthermore, T (x, y) (x,y) (x, y) = (x,y) E(T (x, y)), a.s. () (x, y) We enote the above it by γ(). γ() characterizes the first passage elay T (x, y) with respect to the istance (x, y). We nee to emphasize that γ() epens on. In fact, previous results also show that if = an > I, γ =. Otherwise, γ >. However, none of the previous works stuies the exact relationship between γ() an, especially, how γ() varies with respect to in the region ( L, I ]. In this paper, we will give a more etaile quantification of γ(). C. Useful Notations Some useful notations are liste as follows. (Section II-A) G(, r, h(r)) is a Ranom Connection Moel, an h(r) is the connection function; B(, r) is the Poisson Boolean Moel; we use C(G(, r, h(r))) an C(B(, r)) to represent the giant component of G(, r, h(r)) an B(, r) respectively. (Section II-B) G t (, r, g(r)) is the instantaneous geometric graph at time slot t an its critical ensity is I ; G(, r, f(r)) is the long-term geometric graph an its critical ensity is L. P( ) represents the probability of some event; E( ) represents the expectation of a ranom variable; z x (z y ) represents the x(y)-coorinate of z; (u, v) = u v is the Eucliean istance between noe u an v. (Section IV-B) H(z, a) is a circular region efine as H(z, a) = {z = (z x, z y ) R z z < a}. The ranom variable S g,t,u () is efine as S g,t,u () = sup{a noe v H c (u, a), v an u are connecte in G t (, r, g(r))}. In fact, all S g,t,u () s (inexe by t an u) have the same istribution. Thus, we write the expectation of S g,t,u () as E(S g ()) for short. 5 To be precise, this propagation elay inclues both the processing elay at the sening noe, an the propagation elay along the link Such a giant component exists with probability, because we focus on the case > L in this paper. (Section II-B) T c (e) is the passage time for a link e; T p (π) is the passage time for a path π; T (x, y) is the first passage time from noe x to y; (Section IV-B) T p (Π) is the passage time for a cluster to cluster transmission process Π; (Section IV-A) N ((u, v)) is the minimum number of hops from noe u to v. π represents a path; Π represents a cluster to cluster transmission process. III. MAIN RESULTS In this section, we first give two properties on the elayistance ratio γ(). After that, we present our main results concerning the relationship between noe ensity an γ(), in which an upper boun an a lower boun for γ(), are given. A. Properties of γ() γ() can be viewe as a function mapping from ( L, ) to R. The properties of γ() are liste below. Theorem. γ() has the following two properties: ) if =, then > I, γ() = ; ) γ() is a monotone ecreasing function. Proof: The first property has alreay been prove by previous literatures [][][3][7]. Thus, we only present the proof of the property () here. Given >, consier two Ranom Connection Moels G t (, r, g(r)) an G t (, r, g(r)). We use coupling technique to prove γ( ) γ( ). Noes in G t (, r, g(r)) an G t (, r, g(r)) are istribute accoring to Poisson Point Processes, enote by Γ an Γ, with noe ensities an, respectively. Note that Γ can be viewe as the superposition of Γ an another Poisson Point Process Γ with noe ensity. Consier noes x, y Γ, since Γ Γ, we obtain x, y Γ. For any path π connecting x an y in G t (, r, g(r)), this path also exists in G t (, r, g(r)). By the efinition of T (x, y), we must have T (x, y) T (x, y). Divie the above inequality by (x, y), an let (x, y), we obtain B. Main results on γ() γ( ) γ( ). We have obtaine several properties of γ(). Now we are reay to present our main results.
5 5 Theorem. Given a RCM G t (, r, g(r)) with L ( + ϵ) < I (ϵ > ) an =, the corresponing γ() satisfies E(S g () + r ) γ() κ ϵ inf [ L (+ϵ),] L where κ ϵ is a constant inepenent of. ) g (r,(7) L (+ϵ) Theorem ignores the propagation elay. If we take propagation elay into consieration, we have the following results. Theorem 3. Given a RCM G t (, r, g(r)) with L (+ϵ) (ϵ > ) an < <. Then the corresponing γ() satisfies E(min{S g (), r γ() }) + r inf [ L (+ϵ),] where κ ϵ is a constant inepenent of. κ ϵ / L ) () g (r L (+ϵ) We nee to emphasize that the two κ ϵ s in Theorem an Theorem 3 are the same. The rigorous efinition of κ ϵ is postpone to Section IV-A (see Lemma 3). Our results provie a way to estimate elay in Large-scale wireless multi-hop networks. Our result is also very general. By changing the connection function g(r), our results can be easily applie to ifferent scenarios in real networks. IV. UPPER AND LOWER BOUNDS OF γ() In this section, we first give an upper boun to the elayistance ratio, γ(). Then, we make further analysis on first passage elay an introuce a concept calle cluster to cluster transmission. Using this concept, we erive a lower boun. Finally, we take propagation elay into consieration, an formulate its impact on γ(). A. Upper Boun of γ() Recall the efinition of γ() (Eqn. ) that γ() = T (x,y) (x,y) (x,y), where x, y belongs to the giant component of G(, r, f(r)). To compute such a it, we o not have to calculate γ() for all x, y C(G(, r, f(r))). The correctness of this assertion is assure by the following lemma. Lemma. Given a convergent sequence {x k }, k =,,..., an k x k = x. {y k }, k =,,..., is a subsequence of {x k }, an k y k = y. Then x = y. It is easy to see that the number of noes in C(G(, r, f(r))) is countable. We enumerate for all noes. We ranomly select a noe an label it as x, an then label other noes accoring to the istance from x (larger subscript means larger istance from x ). Define sequence {m k, k =,,..., }, m k = T (x,x k ) (x,x k ), then k m k = γ(). Accoring to lemma, we only nee to fin a subset of noes of C(G(, r, f(r))) (the carinality of this subset must be infinity), an calculate γ() from this subset. This technique is use in eriving the upper boun. Now we are to obtain the upper boun of γ(). The elay T (x, y) is efine as the minimum elay along all paths connecting noes x an y. Thus, it must be smaller than or equal to the elay along one specific path. In this part, we first fin a subset of noes of C(G(, r, f(r))). Then, we fin a path for each noe pair in this subset. After that, we calculate the elay along this path. Finally, iviing the elay by istance, we obtain an upper boun of γ(). Before proceeing, we nee the following lemma. Lemma. Consier Poisson Boolean moels in R. Let c (r) enote the critical ensity in the case where the transmission range is r. Then it is the case that where r, r >. c (r )r = c (r )r, Proof: See Proposition. in [5]. The long-term critical ensity L is also the critical ensity of Poisson Boolean Moel with transmission range r. Consier the network with ensity > L, accoring to lemma, we immeiately know that when r > L r, i.e., r > L r, Poisson Boolean Moel B(, r) is percolate. Let r = r L (+ϵ), then B(, r) is percolate. Further, since L ( + ϵ), we must have r r. Note that, the Ranom Connection Moel G(, r, f(r)) is essentially a Poisson Boolean Moel B(, r ) with r r. Hence, B(, r) is a subgraph of G(, r, f(r)). (Here, B(, r) has the same noe locations as G(, r, f(r)).) We enote the giant component of B(, r) by C(B(, r)). Accoring to the uniqueness of giant component in supercritical case, there must be C(B(, r)) C(G(, r, f(r))). Accoring to lemma, when calculating γ(), we only nee to focus on the case that both noes belong to C(B(, r)). Assume that noes u, v C(B(, r)). Then there exists at least one path in B(, r) from u to v. We choose the path with minimum number of hops, an enote it by π m. Up to now, we have foun a path connecting u an v. Next, we are to calculate the elay along this path. To start with, we nee to compute the number of hops, enote by N ((u, v)), in π m. We can fin a relationship between N ((u, v)) an using the following scaling arguments. Scale the network B(, r) up by L, then the network B(, r) becomes another network B( L, r + ϵ). Further, the original istance (u, v) between u an v becomes (u, v) L. Then to compute N ((u, v)), it is equivalent to compute N L ((u, v) L ). Next, we present the lemma concerning N L (). Lemma 3. Given B( L, r + ϵ), an u, v C(B( L, r + ϵ)), the minimal number of hops among all paths from u to v is N L ((u, v)). Then there exist κ ϵ such that N L ((u, v)) = κ ϵ. (u,v) (u, v)
6 Lemma 3 gives the rigorous efinition of κ ϵ, which is a useful parameter in Theorem an Theorem 3. The proof of Lemma 3 is base on a conclusion on subaitivity an is given in section V-A. Accoring to lemma 3, we immeiately get N ((u, v)) (u,v) (u, v) N L ((u, v) = (u,v) (u, v) L ) = κ ϵ L. (9) Then we calculate the elay T p (π m ) along path π m. Accoring to the Strong Law of Large Numbers, with probability, we have (u,v) Therefore, T p (π m ) N ((u, v)) = (u,v) e π m T c (e) N ((u, v)) = E[T c(e)]. γ() = T (u, v) (u, v) T p (π m ) (u, v) = T p (π m ) (u,v) N ((u, v)) N ((u, v)) (u, v) = κ ϵ L E[T c (e)]. () From the efinition of the path π m, we know that the length of each hop is smaller than r = r L (+ϵ). Besies, the connection function g(r) is monotone ecreasing. Thus, for a link e whose length is r, there must be E[T c (e)] E[T c (e )] = kp(t c (e ) = k) = k= k= k( g( r)) k g( r) =. () g( r) Thus, ( ) γ() = κ ϵ E[T c (e)] κ ϵ L L g( r) = κ ϵ L g (r L (+ϵ) ). Furthermore, from property () of theorem, we know γ() is a monotone ecreasing function. Thus, γ() inf κ ( ) ). [ L (+ϵ),] L g (r L (+ϵ) B. Lower Boun of γ() ) Cluster to Cluster Transmission: In section IV-A, we have obtaine the upper boun of γ() by calculating the elay along one path. However, the metho use in section IV-A cannot be use to stuy the lower boun of γ(). It is har to obtain the number of paths connecting two noes. The elay along each path is ranom an may correlate with that of other paths. Therefore, it is usually intractable to obtain the elay from Eqn. (). To overcome this ifficulty, we introuce the concept of cluster to cluster transmission. Consier the packet transmission process from noe u to noe v. Assume that at time slot t, noe u (u = u) transmits a packet to other noes. Since we have ignore the propagation elay, all noes connecte to u in G t (, r, g(r)), enote by W, receive the information instantaneously. Then, the transmission process stops. This is because all outgoing connections from W are unavailable at this time instance. The transmission process will restart at time slot t > t 7, when at least one noe in W fin the opportunity to forwar the packet to a new noe, enote by u. At this time slot, u transmits the packet to a set of new noes (not in W ) which are connecte to u in G t (, r, g(r)), enote by W, instantaneously. This process goes on, until at time slot t M, noe u M an the estination noe v are in the same connecte cluster an the packet is transmitte to noe v instantaneously. We can see that the cluster to cluster transmission as a series of outbursts. During each outburst, a set of new noes receive the packet. W k, k =,,..., M is the set of noes which receive the information right at the kth outburst. u k W k is the starting noe at the kth outburst. It is possible that at time t k, two noes u k an u k fin transmission opportunity simultaneously. Choosing ifferent starting noes will lea to ifferent cluster to cluster transmission processes. A cluster to cluster transmission process can be fully escribe by Π = {(t, u ), (t, u ),..., (t M, u M )}. Packets can be transmitte from u to v through Π. Define the passage time for the cluster to cluster transmission process Π as T p (Π) = t M t. Then, we have the following lemma. Lemma. Given noes u, v C(G(, r, f(r))), the first passage time T (u, v) = inf{t p (Π) Π is a cluster to cluster transmission process from u to v}. () Proof: For convenience, we use L to enote the set of all the cluster to cluster transmission processes from u to v. Then Eqn.() can be rewritten as T (u, v) = inf{t p (Π) Π L }. It is easy to see that for each cluster to cluster transmission process Π from u to v, Thus, Next, we show that T p (Π) T (u, v). inf{t p (Π) Π L } T (u, v). (3) inf{t p (Π) Π L } T (u, v). 7 Here, we o not require t to be the smallest, i.e., there may exist t < t < t, such that at least one noe in w have the opportunity to forwar the information to a new noe at time slot t.
7 7 Recall the efinition of T (u, v), i.e., T (u, v) = inf {T p (π) : π is a path from u to v}. Let π be the path with minimum elay from u to v, we prove that there exists a cluster to cluster transmission process Π, such that T p (Π ) = T p (π ). Assume that π = i i i...i K (i = u, i K = v). At time slot t, some noes in path π may be in the same connecte cluster as i. Let i η be the noe attainable from i with largest subinex, then the link between i η an i η must be off at this time slot. Let t > t be the first time slot that this link is on. At time slot t, let i η be the noe attainable from i η with largest subinex. Then the link between i η an i η must be off until time slot t 3 > t...at time slot t k, noe i ηk an estination noe v are in the same connecte cluster an the information transmit to v instantaneously. We enote by Π this cluster to cluster transmission process. An Π = {(t, i ), (t, i η ),..., (t k, i ηk )}. From the construction of Π, it is obvious that T p (Π ) = T p (π ). Thus, T (u, v) = T p (π ) = T p (Π ) inf{t p (Π) Π L }. () Combining Eqn.() an Eqn.(), we obtain T (u, v) = inf{t p (Π) Π L }. Base on the cluster to cluster transmission process, we are now reay to compute a lower boun of γ(). ) Compute the Lower Boun: In this section, we use the concept of cluster to cluster transmission to erive a lower boun of γ(). To start with, we nee to introuce a ranom variable S g,t,u () (g is the connection function, u is a noe) to represent the raius of the connecte cluster W ({u}) in the instantaneous geometric ranom graph G t (, r, g(r)). We establish a cartesian coorinate in R. We efine H(z, a) as H(z, a) = {z = (z x, z y ) R z z < a}. The ranom variable S g,t,u () is efine as S g,t,u () = sup{a noe v H(u, a), v u at time slot t}. Accoring to the spacial stationarity an time inepenence of our ynamic RCM G t (, r, g(r)), the istribution of S g,t,u () is inepenent of t an u. Thus, we can write S g,t,u () as S g () if causing no confusion. Now, given two noes u (source) an v (estination), consier a cluster to cluster transmission process(fig. ) Π = {(u (), t ), (u (), t ),..., (u (M), t M )}, where u () = u, an u (M), v are in the same connecte cluster at the time instance t M. Then the elay along this cluster to cluster transmission process is T p (Π) = t M t = (t k+ t k ) M. M k= Fig.. S S ()( ) gt,, u ()( ) gt,, u r r r Illustration of a cluster to cluster transmission process. S ( M) ( ) gt, M, u Note that, k =,,..., M, u (k+) is connecte to a noe in W k, enote by u. Then, u (k+) u (k) u (k+) u + u u (k) As for k = M, S g,tk,u (k)() + r. v x u (M) S g,tm,u (M)(). Combining the above two inequalities together, we obtain, (u, v) = v u < M k= M k= u (k+) u (k) + v u (M) (S g,tk,u (k)() + r ) + S g,tm,u (M) x () M (S g,tk,u (k)() + r ). (5) k= For each k, it is easy to check that S g,tk,u(k)() amits the same istribution as another ranom variable S g (). Further, we can prove the following lemma. Lemma 5. With probability, we have M k= S g,t k,u (k)() = E(S g ()). () M M We nee to emphasize that Lemma 5 cannot be obtaine irectly from the Strong Law of Large Number, because S g,tk,u(k)() s may not be inepenent for ifferent k s. However, we can show that the ranom process {S g,tk,u (k)()} k is in fact ergoic. Then, accoring to Birkhoff Ergoic Theorem, the time average of S g,tk,u(k)() (left han sie of Eqn. ()) will be equal to the spacial average of S g,tk,u(k)() (right han sie of Eqn. ()). See Section V-E for the etaile proof. Accoring to Lemma 5, ϵ >, M ϵ, such that M > M ϵ (this conition is satisfie for large enough (u, v)), we have M k= (S g,t k,u (k)() + r ) < E(S g () + r ) + ϵ. M Combine with Eqn. (5), we have (u, v) < M(E(S g () + r ) + ϵ ).
8 Then T p (Π) M > (u, v) E(S g () + r ) + ϵ. Note that the right han sie of the above inequality oes not epen on the selection of the cluster to cluster transmission processes. Thus, Therefore, T (u, v) (u, v) E(S g () + r ) + ϵ. γ() = T (u, v) (u,v) (u, v) E(S g () + r ) + ϵ (7) Let ϵ, we finally obtain γ() C. Impact of Propagation Delay E(S g () + r ). The elay in large-scale Wireless Networks is compose of two parts, i.e., the waiting elay an the propagation elay. In previous sections, we ignore the propagation elay. Now, we will consier its impact on γ(). The propagation elay will not have much influence on γ() when is relatively small, because the first passage elay is ominate by the waiting elay. However, when is relatively large, e.g., > I, the network connectivity is maintaine at each time slot, an thus the propagation elay will increase γ() substantially (γ() is now boune below away from ). The proof of Theorem 3 is in fact a generalization of that of Theorem. Proof: We first consier the upper boun. We have alreay obtaine Eqn. (), i.e., γ() κ ϵ L E[T c (e)], where the length of link e is smaller than r = r L (+ϵ). Using similar metho in eriving Eqn. (), we obtain E[T c (e)] E[T c (e )] = (k + )P(T c (e ) = k) < = k= (k + )( g( r)) k g( r) = g( r) k= g (r L (+ϵ) ) () where e is link whose length is r. The inequality above is slightly ifferent from Eqn. (). This is because we have taken propagation elay into consieration. Thus, γ() κ ϵ ). L g (r L (+ϵ) Note that γ() is a monotone ecreasing function, thus γ() inf κ ϵ ). (9) [ L (+ϵ),] L g (r L (+ϵ) Then we consier the lower boun. Similar to the previous part, we still focus on the cluster to cluster transmission. Consier a cluster to cluster transmission process Π = {(u (), t ), (u (), t ),..., (u (M), t M )}. Similarly, we have, k =,,..., M, As for k = M, u (k+) u (k) S g,tk,u (k)() + r. v u (M) S g,tm () < S,u (M) g,tm,u (M)() + r. x Besies, the istance transmitte is also ite by the finite hops in one time slot. Since each hop takes fraction of a time slot, then a packet can transmit at most hops in one time slot. As a result, the longest istance transmitte in one time slot is upper boune by r. Then k =,,..., M, u (k+) u (k) r + r. As for k = M, v u (M) r < r + r. Integrating the above four inequalities, we obtain, k =,,..., M, u (k+) u (k) min{s g,tk,u (k)(), r } + r. As for k = M, v u (M) min{s g,tm,u (M)(), r } + r. Again, using the metho in section IV-B, we immeiately obtain γ() E(min{S g (), r }) + r. A. Proof of Lemma 3 V. PROOF The metho use in this proof is similar to that use by Dousse et al. in [] an Kong et al. in []. We first construct a cartesian coorinate system. Without loss of generality, we assume that there is a noe at the origin. Let z n = arg min z C(B(L,r +ϵ)) {(z, (, n))}. We efine N L (m, n) = N L ((z n, z m )). We first prove that N L (, m) scales linearly with respect to m (Lemma ). As we will see later, Lemma 3 follows irectly from Lemma. Lemma. There exists κ ϵ, such that N L (, m) = κ ϵ. m m To prove Lemma, we use Liggett s subaitive ergoic theorem, which is formally restate below.
9 9 Lemma 7. (Liggett [])Let {S l,m } be a collection of ranom variables inexe by integers l m. Suppose {S l,m } has the following properties: ) S,m S,l + S l,m, l m; ) {S (m )k,mk, m } is a stationary process for each k; 3) {S l,l+k, k } = {S l+,l+k+, k } in istribution for each l; ) E[ S,m ] < for each m. E[S Then α,m ] E[S m m = inf,m ] m m ; S S,m m m exists with probability an E[S] = α. Furthermore, if 5. the stationary process {S (m )k,mk, m } is ergoic; then S = α with probability. It is easy to see that N L (, m) N L (, l) + N L (l, m)( l m). Then the first conition of lemma 7 is satisfie. Since Poisson Boolean Moel B( L, r + ϵ)) is homogeneous, the secon an the thir conitions of lemma 7 are also satisfie. Now, we only nee to prove that conitions an 5 are also satisfie. Lemma. E(N L (, m)) <. Note that E(N L (, m)) = i= P(N L (, m) i). If we can show that P(N L (, m) i) ecays exponentially with respect to i, then Lemma follows irectly. The basic iea is to fin a sequence of toruses circling noes z an z m using noes in the giant component of B( L, r + ϵ)). Then, we can show that the least number of hops N L (, m) from z to z m cannot be arbitrarily large (see Fig. 5). Due to the supercriticality of B( L, r + ϵ)), we can show that such toruses exist with probability close to. Therefore, the probability that N L (, m) is greater than a large threshol is close to. The etaile proof is provie in Section V-B. Then conition of lemma 7 is satisfie. Next, we prove that N L (m, n) satisfies conition 5. To emonstrate that N L (mk, (m + )k) is ergoic, we show that it is strong mixing, which is a stronger property. Lemma 9. N L (mk, (m + )k) is strong mixing. The strong mixing property essentially states that the epenence between N L (mk, (m+)k) an N L ((m+n)k, (m+ n + )k) becomes negligibly small as n becomes large. The strategy to prove this statement resembles some parts of the proof of Lemma. We first fin two toruses circling the shortest path from z mk to z (m+)k an the shortest path from z (m+n)k to z (m+n+)k, respectively. By the stationarity of Poisson Point Process, we know that the size of the two toruses o not epen on n. Hence, as n increases, the two toruses will become isjoint eventually. By the spatial inepenence of Poisson Point Process, we can see that N L (mk, (m + )k) an N L ((m + n)k, (m + n + )k) becomes approximately inepenent when n is large enough. The etaile proof is provie in Section V-C. Now, we have prove that N L (m, n) satisfy conitions 5 of Lemma 7. Thus, there exists κ ϵ, such that N L (, m) = κ ϵ. m m Before proving Lemma 3, we also nee the following lemma. Lemma. (z n, (, n)) < with probability. Intuitively, if (z n, (, n)) =, there oes not exist any giant component in B( L, r + ϵ)) (otherwise, (z n, (, n)) < ). This contraict to the supercriticality of B( L, r + ϵ)). The etaile proof is presente in section V-D. Now, we are reay to prove Lemma 3. Proof: Consier N L ((u, v)). Without loss of generality, we suppose that u is at the origin, v is at the +x axis. Assume that integer n satisfy n (u, v) < n +, then an N L ((u, v)) N L ((, z n )) + N L ((z n, v)), () N L ((u, v)) N L ((, z n )) N L ((z n, v)). () Note that (z n, v) (z n, (, n )) + ((, n ), v) (z n, (, n )) + <. Using similar metho in the proof of Lemma, we can prove E(N L ((z n, v))) < (to avoi verbosity, we o not elaborate it here). Therefore, N L ((z n, v)) < with probability. Further, by the stationarity of Poisson Point Process, N L ((z n, v)) oes not epen on (u, v). Then, ivie Eqn. () an Eqn. () by (u, v), an let (u, v). We immeiately obtain B. Proof of Lemma N L ((u, v)) = κ ϵ. (u,v) (u, v) Proof: Consier N L (, m). Let z = z +z m. We raw a series of squares centering at z (Fig. 3), an the sie lengths are,,,..., k,... z Fig. 3. A series of squares centering at z. We use R() to enote the rectangle with sie lengths an. We say R() is goo if an only if there exists a crossing connecting the two short sies in R() (Fig..(a)). We enote
10 the event that R() is goo by A R (). Note that the Poisson Boolean Moel B( L, r + ϵ) is percolate. By Corollary. in [5], we have P(A R()) =. () [z y k, z y+ k ], it must intersect with the circuit in C( k )(Fig 5). We can replace the part of the path ACB with ADB, then the resulting path is shorter. Thus, the shortest path from z to z m must be containe in [z x k, z x + k ] [z y k, z y + k ]. (a) Illustration of a goo rectangle R(). (b) Illustration of a goo square torus C(). Here, z = (z x, z y). Fig.. Illustration of a goo rectangle an a goo square torus. We use C() to enote the square torus ([z x, z x + ] [z y, z y + ]) \ ([z x, z x + ] [z y, z y + ]). We say C() is goo if an only if there exists a circuit in C() (Fig..(b)). We enote the event that C() is goo by A C (). From Fig..(b), we can see that C() is compose of four rectangles, i.e., R () = [z x, z x ] [z y, z y + ], R () = [z x+, x+] [z y, z y+], R z 3 () = [z x, z x+ ] [z y +, z y +], R () = [z x, z x +] [z y, z y ]. An we use A Ri ()(i =,, 3, ) to represent the event that R i () is goo. Obviously, if i =,, 3,, R i () is goo, C() must be goo. Thus, P(A C ()) P(A R () A R () A R3 () A R ()). Note that i =,, 3,, A Ri () is an increasing event. Accoring to the FKG Inequality (Theorem. in []), we have P(A C ()) P(A R () A R () A R3 () A R ()) P(A R ())P(A R ())P(A R3 ())P(A R ()) = P(A R ()). (3) Combine Eqn. () with Eqn. (3), an we obtain P(A C()) =. Thus, < ρ <, there exists ρ, such that,, P(A C ()) ρ. Let k = min{k k z m z, k ρ }, then for all k k, P(A C ( k )) ρ. Assume that C( k )(k k ) is goo, if the shortest path from z to z m is not containe in the square [z x k, z x+ k ] A ranom variable N is on the measurable pair (Ω, F ) is calle increasing if N(ω) N(ω ) whenever ω ω. Fig. 5. The contraiction if the shortest path from z to z m is not containe in [z x k, z x + k ] [z y k, z y + k ]. Suppose u, v, w are three consecutive noes along this shortest path. Then u w > ( + ϵ)r, or we can einate noe v, an get a shorter path. This also inicates that if we raw isks with raius (+ϵ)r centering at u an w respectively, the two isks are isjoint. Assume the number of hops of the shortest path is N, then we can raw L isjoint isks in total. An these isks are all locate in a square with sie length k+ + ( + ϵ)r. Thus, Then, L π(( + ϵ)r ) ( k+ + ( + ϵ)r ). L (k+ + ( + ϵ)r ) π(( + ϵ)r ). Note that N L (, m) is the minimum number of hops from x to x m, thus N L (, m) L (k+ + ( + ϵ)r ) π(( + ϵ)r ). Now, if N L (, m) > (k+ +(+ϵ)r ) π((+ϵ)r ), then none of C( k+ ), C( k+ ),..., C( k ) is goo. Thus, P(N L (, m) > (k+ + ( + ϵ)r ) π(( + ϵ)r ) ) k P(A c C( i )) ( ρ) k k. i=k + Let l k = (k+ +(+ϵ)r ) π((+ϵ)r ), then,
11 E(N L (, m)) = P(N L (, m) i) i= l k = P(N L (, m) i) + i= l j+ j=k i=l j + P(N L (, m) i) l k + P(N L (, m) > l j ) (l j+ l j ) j=k < l k + ( ρ) j k (j+ + ( + ϵ)r ) π(( + ϵ)r ) j=k <. C. Proof of Lemma 9 Proof: In previous analysis, we have prove that P(A C ( k )) ρ whenever k k. Summing over k yiels P(A C ( k )) = ρ =. () k=k k=k Since A C ( k ), k = k, k +,... are inepenent events, accoring to the Borel-Cantelli Theorem, with probability, there exist k < 9, such that A C ( k ) occurs. We now construct squares B an B centere at x mk +x (m+)k an x (m+n)k+x (m+n+)k with sie length k + k + an respectively, such that the path with minimum number of hops from x mk to x (m+)k, an the path with minimum number of hops from x (m+n)k to x (m+n+)k are containe in B an B. Due to the stationarity, k oes not rely on n. Besies, k an k are all finite(we enote this event by A f ) with probability. Thus, when n is large enough, B an B are isjointe. Hence, N L (mk, (m+)k) an N L ((m+n)k, (m+n+)k) become inepenent. Therefore, P({N n L (mk, (m + )k) < i} {N L ((m +n)k, (m + n + )k) < i}) = n P({N L (mk, (m + )k) < i} {N L ((m +n)k, (m + n + )k) < i} A f )P(A f ) + n P({N L (mk, (m + )k) < i} {N L ((m +n)k, (m + n + )k) < i} A c f )P(A c f ) = P({N L (mk, (m + )k) < i} A f ) P({N L ((m +n)k, (m + n + )k) < i} A f ) = P({N L (mk, (m + )k) < i}) P({N L ((m+ n)k, (m + n + )k) < i}). Then, N L (mk, (m + )k) is strong mixing. 9 Actually, the number of such k is infinite. D. Proof of Lemma Proof: Similar to that in the proof of lemma, we construct a series of squares centere at (, n) with sie length,,,..., k,...(fig. 3). C() is efine similarly. We say C() is perfect if an only if C() is goo an the circuit in C() belongs to the giant component. Again, we apply Borel-Cantelli Theorem to Eqn. (). With probability, there exists {k }, such that event A C ( k ) occurs. Then, (z n, (, n)) < k < with probability. E. Proof of Lemma 5 Proof: Accoring to Birkhoff Ergoic Theorem, we only nee to show that {S g,tk,u (k)()} k is ergoic. In fact, we will show that {S g,tk,u (k)()} k is strong mixing, an thus ergoic. Consier S g,tk,u (k)() an S g,t k+n,u(k+n)(). We only nee to show that for any constants s, s >, P({S g,t n k,u (k)() < s } {S g,tk+n,u (k+n)() < s }) = P(S g,tk,u (k)() < s )P(S g,tk+n,u (k+n)() < s ). (5) Note that all S g,tk,u(k)() s are equal in istribution to a ranom variable S g (), an E(S g ()) < ue to the subcriticality of RCM G t (, r, g(r)). Therefore, for any fixe ϵ >, there exists M ϵ, such that P(S g () > M ϵ ) < ϵ. We efine Ŝg,t k,u (k)() = min{s g,t k,u (k)(), M ϵ} for k =,,... Then, Ŝ g,tk,u(k)() only epens on the realization of noes an links in the circler region H(u (k), M ϵ ). Consier the istance (u (k), u (k+n) ) between noe u (k) an u (k+n). By the construction of u (k) s, we know that as n increases to infinity, (u (k), u (k+n) ) also increases to infinity. We choose N >, such that for all n > N, (u (k), u (k+n) ) > M ϵ. Then H(u (k), M ϵ ) an H(u (k+n), M ϵ ) will become isjoint. By the spacial inepenence of Poisson Point Process, we then obtain that for any n > N, P({Ŝg,t k,u (k)() < s } {Ŝg,t k+n,u (k+n)() < s }) = P(Ŝg,t k,u (k)() < s )P(Ŝg,t k+n,u (k+n)() < s ).() From the construction of Ŝg,t k,u(k)(), we know that for s M ϵ, P(S g,tk,u (k)() < s) = P(Ŝg,t k,u(k)() < s); while for s > M ϵ, P(M ϵ S g,tk,u(k)() < s) ϵ. Then, using Eqn. (), it is easy to show that P({S g,t n k,u (k)() < s } {S g,tk+n,u (k+n)() < s }) P(S g,tk,u (k)() < s )P(S g,tk+n,u (k+n)() < s ) < ϵ. Let ϵ, we then obtain Eqn. (5).
12 VI. DISCUSSION In this section, we make simulations to uphol our theoretical results. First, we give a further iscussion on some parameters in our expressions. Then, enormous simulations are one to justify several assertions in this paper. Our theoretical results are base on a relatively general moel, Ranom Connection Moel. Many Network Moels can be converte to a Ranom Connection Moel, making our results applicable to many ifferent cases. The ifference is that the connection functions are ifferent in ifferent cases. In the following iscussion, we simply let r =, an the connection function g be efine as { g(r) = ( r) : r : r > Moreover, if we take propagation elay into consieration, we let =.. A. Discussion on Several Parameters In our expression of theoretical bouns Eqn. (7), two terms κ ϵ an E(S g ()) are applie. Besies, In Eqn. (), E(min{S g (), r }) is applie. κ ϵ is a constant, an we simply obtain its value through simulation; while E(S g ()) an E(min{S g (), r }) are functions epening on, an we fin two analytical expressions to approximate them. We first focus on κ ϵ (efine in lemma 3). Here, we set ϵ =.. In our simulation, we simulate 3 points in a region. The noe ensity is = L., an the transmission range is r + ϵ.. A packet is originate from a noe locate at the center of the region, we recor own the minimum number of hops an the istance from the source for each noe, an plot it in Fig..(a). N () (a) Illustration of the relationship between N () an (b) The probability istribution graph of N () Fig.. Simulation results on κ. The first Figure reveals the linear relationship between N () an, an the secon inicates κ ϵ.753. From Fig..(a), we can see that N () grows linearly with. To fin κ, we calculate N () for each noe, an present its probability istribution graph in Fig..(b). It can be seen from Fig..(b) that the probability N () =.753 is the largest. Thus, κ ϵ.753. Next, we turn to E(S g ()). The physical meaning of E(S g ()) is the average size of the connecte component intersecte with the origin. It is obvious that when =, E(S g ()) =. An when = I, E(S g ()) = since the network is percolate in this case. Thus, we give a conjecture about the analytical expression of E(S g ()), i.e., E(S g ()) = c I. (7) We make enormous numerical computations to fin the experimental values of E(S g ()) with respect to ifferent, ranging from.5 ( L ( + ϵ) <.5) to.. We then rewrite Eqn. (7) as E(S g ()) = I c. c Using the least square fitting, we can easily obtain c., I.. Then we make a comparison between the fitting value an the experimental value of E(S g ()). From Fig. 7, It can be seen that there is a goo agreement between fitting an experimental results. Fig. 7. E(S g ()) Experimental Result Fitting Result Comparison between experimental an fitting value of E(S g ()). Now, we come to E(min{S g (), r }). Obviously, E(min{S g (), r }) = whenever =. Besies, E(min{S g (), r }) r,, an E(min{S g (), r }) is monotone increasing with. Thus, we conjecture that the analytical expression of E(min{S g (), r }) has the format E(min{S g (), r }) = c c 3 +. () Similarly, we conuct numerical computations to fin the experimental values of E(min{S g (), r }) with respect to ifferent, ranging from. to. We rewrite Eqn. () as E(min{S g (), r }) = c 3 c +. c Using the least square fitting, we can easily obtain c.5, c 3.3. Then we make a comparison between the fitting value an the experimental value of E(min{S g (), r }). From Fig., It can be seen that there is a goo agreement between fitting an experimental results. B. Comparison between Two Bouns This paper is originate from the iea that the elay-istance ratio γ() may epen on the noe ensity. We calculate γ() uner ifferent noe ensities. From Fig. 9, we can see T that γ(.) = ()., γ(.9).35, γ(.)
13 3 3. Experimental Result Fitting Result Expeimental Results Upper Boun Lower Boun. The experimental results get closer to the upper boun when is small γ() E(min{Sg(),r/}) T()/ T()/ 5 () =.5 Simulation results on ifferent.., γ(.5). This justifies the fact that γ() is monotone ecreasing with respect to. Now, we are reay to compare our theoretical bouns an the experimental values of γ(). We first ignore the propagation elay, Fig. shows the comparison between the experimental value an our theoretical value of both the upper boun an the lower boun. In our simulations, We work out the experimental values of γ() where is set to be evenly istribute in the interval of [L ( + ϵ), I ]. From Fig., we fin that the experimental values are right boune by both the upper an the lower bouns. Then, we take propagation elay into consieration. In the following part, we take =.. We first examine the effect of introucing propagation elay to the elay-istance ratio γ(). We consier two networks, whose noe ensities are.5 an. (.5 is near L,. is near I ) respectively. For each network, we make simulations to fin γ() in the cases = an =.. The result is show in Fig.. From Fig., we can also see that when is small, the influence of to γ() is small; an the influence becomes more significant as grows larger. This also inicate that when the noe ensity is small, elay is mainly cause by (c) =. (a) =.5, =, γ() (b) =.5, =., γ() Fig. 9. (b) =.9 T()/ T()/ (a) =.. Fig.. Comparison between upper boun an lower boun(propagation elay is ignore). T()/ T()/ T()/ I Fig.. Comparison between experimental an fitting value of E(min{Sg (), r }). 3 The experimantal results get closer to the lower boun when get closer to T()/. (c) =., =, γ() () =., =., γ().. Fig.. γ(). The influence of propagation elay to the elay-istance ratio the waiting elay (waiting elay is mainly cause by the loss of wireless connections); while when the noe ensity is large, elay is mainly cause by the propagation elay. Next, we compare our theoretical bouns an experimental results of γ() in the case =.. In our simulation, the noe ensities are chosen from [.5, ]. Since the change of γ() is larger when is small, we choose more simulation points for smaller noe ensity. The comparison between our theoretical bouns an experimental results is shown in Fig.. The experimental values are right boune by both the upper an the lower bouns. From Fig. an Fig., it can be seen that when is large, γ() is much closer to the lower boun. An explanation to this phenomena is that the larger the noe ensity is, the larger the size of clusters in the cluster to cluster transmission process. Larger cluster size provies more opportunity for forwaring packets. Thus, when the noe ensity is large enough, it is probably that the message can transmit again right at the next time slot. This makes our lower boun more accurate. However, our upper boun is a little bit loose. But
14 3 Experimental Results Upper Boun Lower Boun The Experimantal Results get closer to the upper boun when is small γ() The Experimantal Results get closer to the lower boun when is large Fig.. Comparison between upper boun an lower boun(propagation elay is consiere). we can see that γ() gets closer to the upper boun when the noe ensity ecreases. This is because our upper boun is obtaine from the elay of just one path. An the smaller is, the smaller the number of paths connecting two noes. This makes γ() get closer to the upper boun. VII. C ONCLUSION In this paper, we stuy the funamental relationship between γ() an using percolation theory. We point out that unreliability of wireless connections brings about waiting elay an analytically characterize the upper an lower boun for γ(). Then we take propagation elay into consieration, an obtain further results. Finally, through simulations base on the exact value of γ(), we further obtain a new observation that the lower boun serves as a goo approximation to the value of γ() in ense networks. An γ() gets closer to the upper boun when ecreases. Simulation results conform our theoretical finings. VIII. ACKNOWLEDGMENT This paper is supporte by National Funamental Research Grant (No. CB37); NSF China (No. 79); Shanghai Basic Research Key Project (No. JC5); China Ministry of Eucation Fok Ying Tung Fun (No. ); China Ministry of Eucation New Century Excellent Talent (No. NCET--5). R EFERENCES [] Next-Generation Wireless Mesh Networks: Combining a multi-raio architecture with high-performance routing to optimize vieo surveillance an other multimeia-grae applications, in Aruba Networks, Mar.. [online]. Available: gy/whitepapers/wp wirelessmesh.pf [] J.M.Hammersley an D.J.A.Welsh, First Passage Percolatin, Subaitive Processes, Stacastic Networks, an Generalize Renewal Theory, in Proc. Internat. Res. Semin., Statist. Lab., Univ. California, Berkeley, Calif., pages -. Springer-Verlag, New York, 95. [3] Z. Kong an E. M. Yeh, On the Latency for Information Dissemination in Mobile Wireless Networks, in Proc. ACM MobiHoc, Hong Kong SAR, China, May.. [] P. Gupta an P. R. Kumar, Critical Power for Asymptotic Connectivity in Wireless Networks, in Stochastic Analysis, Control, Optimization an Applications: A Volume in Honor of W.H. Fleming, W. M. McEneany, G. Yin, Q. Zhang, Es. Boston, MA: Birkhauser, pp. 57-5, 99. [5] P. Wan an C. W. Yi, Asymptotic Critical Transmission Raius an Critical Neighbor Number for K-connectivity in Wireless A Hoc Networks, in Proc. 5th ACM int. symp. Mobile A Hoc Networking an Computing, Roppongi Hills, Tokyo, Japan, May -,. [] M. D. Penrose, On K-connectivity for a Geometric Ranom Graph, Ranom Structure an Algorithms, vol. 5, no., pp. 5-, Sept [7] Q. Wang, X. Wang an X. Lin, Mobility Increases the Connectivity of K-hop Clustere Wireless Networks, ACM Mobicom 9, Beijing, Sept. 9. [] D. Goeckel, B. Liu, D. Towsley, L. Wang an C. Westphal, Asymptotic connectivity properties of cooperative wireless a hoc network, ACM Mobihoc, May.. [9] O. Dousse, F. Baccelli an P. Thiran, Impact of Interferences on Connectivity in A Hoc Networks, in Proc. of IEEE Infocom, pp. 7733, Apr. 5. [] G. R. Grimmett, Percolaiton, Springer, 999. [] O. Dousse, P. Mannersalo an P. Thiran, Latency of Wireless Sensor Networks with Uncoorinate Power Saving Mechnisms, in Proc. ACM MobiHoc, pp. 9-, May.. [] Z. Kong, an E. M. Yeh. Connectivity an Information Dissemination in Large-Scale Wireless Networks with Dynamic Links, submitte to IEEE Trans. Inform. Theory,. [3] D. J. Daley an D. Vere-Jones, An Introuction to the Theory of Point Process, New York: Springer, 9. [] J.F.C. Kingman, Poisson Processes, Clarenon Press, Oxfor, 993. [5] R. Meester an R. Roy, Continuum Percolation, NewYork: Cambrige University Press, 99. [] T. Liggett, An Improve Subaitive Ergoic Theorem, Annals of Prob., vol. 3, pp. 79-5, 95. [7] W.Ren, Q.Zhao, an A.Swami, On the Connectivity an Multihop Delay of A Hoc Cognitive Raio Networks to appear in Proc. of IEEE International Conference on Communications(ICC), May,. [] A. Baeley, Spatial point processes an their applications, Lecture Notes in Mathematics, 9:-75, 7. [9] S. Zhao, L. Fu, X. Wang, Q. Zhang, Funamental Relationship between Noe Density an Delay in Wireless A Hoc Networks with Unreliable Links, ACM MobiCom, Las Vegas, Sept. Shizhen Zhao receive the BE egree in electronic engineering from Shanghai Jiao Tong University, China in, an is pursuing a Ph.D. egree at the school of ECE, Purue University, West Lafayette, IN, USA. His research interests focus on the scheuling problem in wireless networks an smart gri. Xinbing Wang receive the B.S. egree (with hons.) from the Department of Automation, Shanghai Jiaotong University, Shanghai, China, in 99, an the M.S. egree from the Department of Computer Science an Technology, Tsinghua University, Beijing, China, in. He receive the Ph.D. egree, major in the Department of electrical an Computer Engineering, minor in the Department of Mathematics, North Carolina State University, Raleigh, in. Currently, he is a professor in the Department of Electronic Engineering, Shanghai Jiaotong University, Shanghai, China. Dr. Wang has been an associate eitor for IEEE/ACM Transactions on Networking an IEEE Transactions on Mobile Computing, an the member of the Technical Program Committees of several conferences incluing ACM MobiCom, ACM MobiHoc, 3, IEEE INFOCOM 9-.
Time-of-Arrival Estimation in Non-Line-Of-Sight Environments
 2 Conference on Information Sciences an Systems, The Johns Hopkins University, March 2, 2 Time-of-Arrival Estimation in Non-Line-Of-Sight Environments Sinan Gezici, Hisashi Kobayashi an H. Vincent Poor
2 Conference on Information Sciences an Systems, The Johns Hopkins University, March 2, 2 Time-of-Arrival Estimation in Non-Line-Of-Sight Environments Sinan Gezici, Hisashi Kobayashi an H. Vincent Poor
Lower Bounds for the Smoothed Number of Pareto optimal Solutions
 Lower Bouns for the Smoothe Number of Pareto optimal Solutions Tobias Brunsch an Heiko Röglin Department of Computer Science, University of Bonn, Germany brunsch@cs.uni-bonn.e, heiko@roeglin.org Abstract.
Lower Bouns for the Smoothe Number of Pareto optimal Solutions Tobias Brunsch an Heiko Röglin Department of Computer Science, University of Bonn, Germany brunsch@cs.uni-bonn.e, heiko@roeglin.org Abstract.
Survey Sampling. 1 Design-based Inference. Kosuke Imai Department of Politics, Princeton University. February 19, 2013
 Survey Sampling Kosuke Imai Department of Politics, Princeton University February 19, 2013 Survey sampling is one of the most commonly use ata collection methos for social scientists. We begin by escribing
Survey Sampling Kosuke Imai Department of Politics, Princeton University February 19, 2013 Survey sampling is one of the most commonly use ata collection methos for social scientists. We begin by escribing
Math 342 Partial Differential Equations «Viktor Grigoryan
 Math 342 Partial Differential Equations «Viktor Grigoryan 6 Wave equation: solution In this lecture we will solve the wave equation on the entire real line x R. This correspons to a string of infinite
Math 342 Partial Differential Equations «Viktor Grigoryan 6 Wave equation: solution In this lecture we will solve the wave equation on the entire real line x R. This correspons to a string of infinite
6 General properties of an autonomous system of two first order ODE
 6 General properties of an autonomous system of two first orer ODE Here we embark on stuying the autonomous system of two first orer ifferential equations of the form ẋ 1 = f 1 (, x 2 ), ẋ 2 = f 2 (, x
6 General properties of an autonomous system of two first orer ODE Here we embark on stuying the autonomous system of two first orer ifferential equations of the form ẋ 1 = f 1 (, x 2 ), ẋ 2 = f 2 (, x
12.11 Laplace s Equation in Cylindrical and
 SEC. 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential 593 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential One of the most important PDEs in physics an engineering
SEC. 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential 593 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential One of the most important PDEs in physics an engineering
On the Connectivity Analysis over Large-Scale Hybrid Wireless Networks
 This full text paper was peer reviewe at the irection of IEEE Communications Society subject matter experts for publication in the IEEE INFOCOM proceeings This paper was presente as part of the main Technical
This full text paper was peer reviewe at the irection of IEEE Communications Society subject matter experts for publication in the IEEE INFOCOM proceeings This paper was presente as part of the main Technical
Lectures - Week 10 Introduction to Ordinary Differential Equations (ODES) First Order Linear ODEs
 Lectures - Week 10 Introuction to Orinary Differential Equations (ODES) First Orer Linear ODEs When stuying ODEs we are consiering functions of one inepenent variable, e.g., f(x), where x is the inepenent
Lectures - Week 10 Introuction to Orinary Differential Equations (ODES) First Orer Linear ODEs When stuying ODEs we are consiering functions of one inepenent variable, e.g., f(x), where x is the inepenent
Least-Squares Regression on Sparse Spaces
 Least-Squares Regression on Sparse Spaces Yuri Grinberg, Mahi Milani Far, Joelle Pineau School of Computer Science McGill University Montreal, Canaa {ygrinb,mmilan1,jpineau}@cs.mcgill.ca 1 Introuction
Least-Squares Regression on Sparse Spaces Yuri Grinberg, Mahi Milani Far, Joelle Pineau School of Computer Science McGill University Montreal, Canaa {ygrinb,mmilan1,jpineau}@cs.mcgill.ca 1 Introuction
Diophantine Approximations: Examining the Farey Process and its Method on Producing Best Approximations
 Diophantine Approximations: Examining the Farey Process an its Metho on Proucing Best Approximations Kelly Bowen Introuction When a person hears the phrase irrational number, one oes not think of anything
Diophantine Approximations: Examining the Farey Process an its Metho on Proucing Best Approximations Kelly Bowen Introuction When a person hears the phrase irrational number, one oes not think of anything
A new proof of the sharpness of the phase transition for Bernoulli percolation on Z d
 A new proof of the sharpness of the phase transition for Bernoulli percolation on Z Hugo Duminil-Copin an Vincent Tassion October 8, 205 Abstract We provie a new proof of the sharpness of the phase transition
A new proof of the sharpness of the phase transition for Bernoulli percolation on Z Hugo Duminil-Copin an Vincent Tassion October 8, 205 Abstract We provie a new proof of the sharpness of the phase transition
Separation of Variables
 Physics 342 Lecture 1 Separation of Variables Lecture 1 Physics 342 Quantum Mechanics I Monay, January 25th, 2010 There are three basic mathematical tools we nee, an then we can begin working on the physical
Physics 342 Lecture 1 Separation of Variables Lecture 1 Physics 342 Quantum Mechanics I Monay, January 25th, 2010 There are three basic mathematical tools we nee, an then we can begin working on the physical
Lower bounds on Locality Sensitive Hashing
 Lower bouns on Locality Sensitive Hashing Rajeev Motwani Assaf Naor Rina Panigrahy Abstract Given a metric space (X, X ), c 1, r > 0, an p, q [0, 1], a istribution over mappings H : X N is calle a (r,
Lower bouns on Locality Sensitive Hashing Rajeev Motwani Assaf Naor Rina Panigrahy Abstract Given a metric space (X, X ), c 1, r > 0, an p, q [0, 1], a istribution over mappings H : X N is calle a (r,
The Press-Schechter mass function
 The Press-Schechter mass function To state the obvious: It is important to relate our theories to what we can observe. We have looke at linear perturbation theory, an we have consiere a simple moel for
The Press-Schechter mass function To state the obvious: It is important to relate our theories to what we can observe. We have looke at linear perturbation theory, an we have consiere a simple moel for
Lecture Introduction. 2 Examples of Measure Concentration. 3 The Johnson-Lindenstrauss Lemma. CS-621 Theory Gems November 28, 2012
 CS-6 Theory Gems November 8, 0 Lecture Lecturer: Alesaner Mąry Scribes: Alhussein Fawzi, Dorina Thanou Introuction Toay, we will briefly iscuss an important technique in probability theory measure concentration
CS-6 Theory Gems November 8, 0 Lecture Lecturer: Alesaner Mąry Scribes: Alhussein Fawzi, Dorina Thanou Introuction Toay, we will briefly iscuss an important technique in probability theory measure concentration
The total derivative. Chapter Lagrangian and Eulerian approaches
 Chapter 5 The total erivative 51 Lagrangian an Eulerian approaches The representation of a flui through scalar or vector fiels means that each physical quantity uner consieration is escribe as a function
Chapter 5 The total erivative 51 Lagrangian an Eulerian approaches The representation of a flui through scalar or vector fiels means that each physical quantity uner consieration is escribe as a function
Lecture XII. where Φ is called the potential function. Let us introduce spherical coordinates defined through the relations
 Lecture XII Abstract We introuce the Laplace equation in spherical coorinates an apply the metho of separation of variables to solve it. This will generate three linear orinary secon orer ifferential equations:
Lecture XII Abstract We introuce the Laplace equation in spherical coorinates an apply the metho of separation of variables to solve it. This will generate three linear orinary secon orer ifferential equations:
Convergence of Random Walks
 Chapter 16 Convergence of Ranom Walks This lecture examines the convergence of ranom walks to the Wiener process. This is very important both physically an statistically, an illustrates the utility of
Chapter 16 Convergence of Ranom Walks This lecture examines the convergence of ranom walks to the Wiener process. This is very important both physically an statistically, an illustrates the utility of
A Sketch of Menshikov s Theorem
 A Sketch of Menshikov s Theorem Thomas Bao March 14, 2010 Abstract Let Λ be an infinite, locally finite oriente multi-graph with C Λ finite an strongly connecte, an let p
A Sketch of Menshikov s Theorem Thomas Bao March 14, 2010 Abstract Let Λ be an infinite, locally finite oriente multi-graph with C Λ finite an strongly connecte, an let p
Lyapunov Functions. V. J. Venkataramanan and Xiaojun Lin. Center for Wireless Systems and Applications. School of Electrical and Computer Engineering,
 On the Queue-Overflow Probability of Wireless Systems : A New Approach Combining Large Deviations with Lyapunov Functions V. J. Venkataramanan an Xiaojun Lin Center for Wireless Systems an Applications
On the Queue-Overflow Probability of Wireless Systems : A New Approach Combining Large Deviations with Lyapunov Functions V. J. Venkataramanan an Xiaojun Lin Center for Wireless Systems an Applications
Table of Common Derivatives By David Abraham
 Prouct an Quotient Rules: Table of Common Derivatives By Davi Abraham [ f ( g( ] = [ f ( ] g( + f ( [ g( ] f ( = g( [ f ( ] g( g( f ( [ g( ] Trigonometric Functions: sin( = cos( cos( = sin( tan( = sec
Prouct an Quotient Rules: Table of Common Derivatives By Davi Abraham [ f ( g( ] = [ f ( ] g( + f ( [ g( ] f ( = g( [ f ( ] g( g( f ( [ g( ] Trigonometric Functions: sin( = cos( cos( = sin( tan( = sec
On colour-blind distinguishing colour pallets in regular graphs
 J Comb Optim (2014 28:348 357 DOI 10.1007/s10878-012-9556-x On colour-blin istinguishing colour pallets in regular graphs Jakub Przybyło Publishe online: 25 October 2012 The Author(s 2012. This article
J Comb Optim (2014 28:348 357 DOI 10.1007/s10878-012-9556-x On colour-blin istinguishing colour pallets in regular graphs Jakub Przybyło Publishe online: 25 October 2012 The Author(s 2012. This article
All s Well That Ends Well: Supplementary Proofs
 All s Well That Ens Well: Guarantee Resolution of Simultaneous Rigi Boy Impact 1:1 All s Well That Ens Well: Supplementary Proofs This ocument complements the paper All s Well That Ens Well: Guarantee
All s Well That Ens Well: Guarantee Resolution of Simultaneous Rigi Boy Impact 1:1 All s Well That Ens Well: Supplementary Proofs This ocument complements the paper All s Well That Ens Well: Guarantee
Iterated Point-Line Configurations Grow Doubly-Exponentially
 Iterate Point-Line Configurations Grow Doubly-Exponentially Joshua Cooper an Mark Walters July 9, 008 Abstract Begin with a set of four points in the real plane in general position. A to this collection
Iterate Point-Line Configurations Grow Doubly-Exponentially Joshua Cooper an Mark Walters July 9, 008 Abstract Begin with a set of four points in the real plane in general position. A to this collection
Delay Limited Capacity of Ad hoc Networks: Asymptotically Optimal Transmission and Relaying Strategy
 Delay Limite Capacity of A hoc Networks: Asymptotically Optimal Transmission an Relaying Strategy Eugene Perevalov Lehigh University Bethlehem, PA 85 Email: eup2@lehigh.eu Rick Blum Lehigh University Bethlehem,
Delay Limite Capacity of A hoc Networks: Asymptotically Optimal Transmission an Relaying Strategy Eugene Perevalov Lehigh University Bethlehem, PA 85 Email: eup2@lehigh.eu Rick Blum Lehigh University Bethlehem,
SYNCHRONOUS SEQUENTIAL CIRCUITS
 CHAPTER SYNCHRONOUS SEUENTIAL CIRCUITS Registers an counters, two very common synchronous sequential circuits, are introuce in this chapter. Register is a igital circuit for storing information. Contents
CHAPTER SYNCHRONOUS SEUENTIAL CIRCUITS Registers an counters, two very common synchronous sequential circuits, are introuce in this chapter. Register is a igital circuit for storing information. Contents
JUST THE MATHS UNIT NUMBER DIFFERENTIATION 2 (Rates of change) A.J.Hobson
 JUST THE MATHS UNIT NUMBER 10.2 DIFFERENTIATION 2 (Rates of change) by A.J.Hobson 10.2.1 Introuction 10.2.2 Average rates of change 10.2.3 Instantaneous rates of change 10.2.4 Derivatives 10.2.5 Exercises
JUST THE MATHS UNIT NUMBER 10.2 DIFFERENTIATION 2 (Rates of change) by A.J.Hobson 10.2.1 Introuction 10.2.2 Average rates of change 10.2.3 Instantaneous rates of change 10.2.4 Derivatives 10.2.5 Exercises
Capacity Analysis of MIMO Systems with Unknown Channel State Information
 Capacity Analysis of MIMO Systems with Unknown Channel State Information Jun Zheng an Bhaskar D. Rao Dept. of Electrical an Computer Engineering University of California at San Diego e-mail: juzheng@ucs.eu,
Capacity Analysis of MIMO Systems with Unknown Channel State Information Jun Zheng an Bhaskar D. Rao Dept. of Electrical an Computer Engineering University of California at San Diego e-mail: juzheng@ucs.eu,
REAL ANALYSIS I HOMEWORK 5
 REAL ANALYSIS I HOMEWORK 5 CİHAN BAHRAN The questions are from Stein an Shakarchi s text, Chapter 3. 1. Suppose ϕ is an integrable function on R with R ϕ(x)x = 1. Let K δ(x) = δ ϕ(x/δ), δ > 0. (a) Prove
REAL ANALYSIS I HOMEWORK 5 CİHAN BAHRAN The questions are from Stein an Shakarchi s text, Chapter 3. 1. Suppose ϕ is an integrable function on R with R ϕ(x)x = 1. Let K δ(x) = δ ϕ(x/δ), δ > 0. (a) Prove
Robust Forward Algorithms via PAC-Bayes and Laplace Distributions. ω Q. Pr (y(ω x) < 0) = Pr A k
 A Proof of Lemma 2 B Proof of Lemma 3 Proof: Since the support of LL istributions is R, two such istributions are equivalent absolutely continuous with respect to each other an the ivergence is well-efine
A Proof of Lemma 2 B Proof of Lemma 3 Proof: Since the support of LL istributions is R, two such istributions are equivalent absolutely continuous with respect to each other an the ivergence is well-efine
Acute sets in Euclidean spaces
 Acute sets in Eucliean spaces Viktor Harangi April, 011 Abstract A finite set H in R is calle an acute set if any angle etermine by three points of H is acute. We examine the maximal carinality α() of
Acute sets in Eucliean spaces Viktor Harangi April, 011 Abstract A finite set H in R is calle an acute set if any angle etermine by three points of H is acute. We examine the maximal carinality α() of
Linear First-Order Equations
 5 Linear First-Orer Equations Linear first-orer ifferential equations make up another important class of ifferential equations that commonly arise in applications an are relatively easy to solve (in theory)
5 Linear First-Orer Equations Linear first-orer ifferential equations make up another important class of ifferential equations that commonly arise in applications an are relatively easy to solve (in theory)
Computing Exact Confidence Coefficients of Simultaneous Confidence Intervals for Multinomial Proportions and their Functions
 Working Paper 2013:5 Department of Statistics Computing Exact Confience Coefficients of Simultaneous Confience Intervals for Multinomial Proportions an their Functions Shaobo Jin Working Paper 2013:5
Working Paper 2013:5 Department of Statistics Computing Exact Confience Coefficients of Simultaneous Confience Intervals for Multinomial Proportions an their Functions Shaobo Jin Working Paper 2013:5
Math 1271 Solutions for Fall 2005 Final Exam
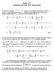 Math 7 Solutions for Fall 5 Final Eam ) Since the equation + y = e y cannot be rearrange algebraically in orer to write y as an eplicit function of, we must instea ifferentiate this relation implicitly
Math 7 Solutions for Fall 5 Final Eam ) Since the equation + y = e y cannot be rearrange algebraically in orer to write y as an eplicit function of, we must instea ifferentiate this relation implicitly
arxiv: v4 [cs.ds] 7 Mar 2014
![arxiv: v4 [cs.ds] 7 Mar 2014 arxiv: v4 [cs.ds] 7 Mar 2014](/thumbs/91/106752949.jpg) Analysis of Agglomerative Clustering Marcel R. Ackermann Johannes Blömer Daniel Kuntze Christian Sohler arxiv:101.697v [cs.ds] 7 Mar 01 Abstract The iameter k-clustering problem is the problem of partitioning
Analysis of Agglomerative Clustering Marcel R. Ackermann Johannes Blömer Daniel Kuntze Christian Sohler arxiv:101.697v [cs.ds] 7 Mar 01 Abstract The iameter k-clustering problem is the problem of partitioning
On Characterizing the Delay-Performance of Wireless Scheduling Algorithms
 On Characterizing the Delay-Performance of Wireless Scheuling Algorithms Xiaojun Lin Center for Wireless Systems an Applications School of Electrical an Computer Engineering, Purue University West Lafayette,
On Characterizing the Delay-Performance of Wireless Scheuling Algorithms Xiaojun Lin Center for Wireless Systems an Applications School of Electrical an Computer Engineering, Purue University West Lafayette,
Equilibrium in Queues Under Unknown Service Times and Service Value
 University of Pennsylvania ScholarlyCommons Finance Papers Wharton Faculty Research 1-2014 Equilibrium in Queues Uner Unknown Service Times an Service Value Laurens Debo Senthil K. Veeraraghavan University
University of Pennsylvania ScholarlyCommons Finance Papers Wharton Faculty Research 1-2014 Equilibrium in Queues Uner Unknown Service Times an Service Value Laurens Debo Senthil K. Veeraraghavan University
1 dx. where is a large constant, i.e., 1, (7.6) and Px is of the order of unity. Indeed, if px is given by (7.5), the inequality (7.
 Lectures Nine an Ten The WKB Approximation The WKB metho is a powerful tool to obtain solutions for many physical problems It is generally applicable to problems of wave propagation in which the frequency
Lectures Nine an Ten The WKB Approximation The WKB metho is a powerful tool to obtain solutions for many physical problems It is generally applicable to problems of wave propagation in which the frequency
Role of parameters in the stochastic dynamics of a stick-slip oscillator
 Proceeing Series of the Brazilian Society of Applie an Computational Mathematics, v. 6, n. 1, 218. Trabalho apresentao no XXXVII CNMAC, S.J. os Campos - SP, 217. Proceeing Series of the Brazilian Society
Proceeing Series of the Brazilian Society of Applie an Computational Mathematics, v. 6, n. 1, 218. Trabalho apresentao no XXXVII CNMAC, S.J. os Campos - SP, 217. Proceeing Series of the Brazilian Society
Introduction to the Vlasov-Poisson system
 Introuction to the Vlasov-Poisson system Simone Calogero 1 The Vlasov equation Consier a particle with mass m > 0. Let x(t) R 3 enote the position of the particle at time t R an v(t) = ẋ(t) = x(t)/t its
Introuction to the Vlasov-Poisson system Simone Calogero 1 The Vlasov equation Consier a particle with mass m > 0. Let x(t) R 3 enote the position of the particle at time t R an v(t) = ẋ(t) = x(t)/t its
3.7 Implicit Differentiation -- A Brief Introduction -- Student Notes
 Fin these erivatives of these functions: y.7 Implicit Differentiation -- A Brief Introuction -- Stuent Notes tan y sin tan = sin y e = e = Write the inverses of these functions: y tan y sin How woul we
Fin these erivatives of these functions: y.7 Implicit Differentiation -- A Brief Introuction -- Stuent Notes tan y sin tan = sin y e = e = Write the inverses of these functions: y tan y sin How woul we
Tractability results for weighted Banach spaces of smooth functions
 Tractability results for weighte Banach spaces of smooth functions Markus Weimar Mathematisches Institut, Universität Jena Ernst-Abbe-Platz 2, 07740 Jena, Germany email: markus.weimar@uni-jena.e March
Tractability results for weighte Banach spaces of smooth functions Markus Weimar Mathematisches Institut, Universität Jena Ernst-Abbe-Platz 2, 07740 Jena, Germany email: markus.weimar@uni-jena.e March
Generalized Tractability for Multivariate Problems
 Generalize Tractability for Multivariate Problems Part II: Linear Tensor Prouct Problems, Linear Information, an Unrestricte Tractability Michael Gnewuch Department of Computer Science, University of Kiel,
Generalize Tractability for Multivariate Problems Part II: Linear Tensor Prouct Problems, Linear Information, an Unrestricte Tractability Michael Gnewuch Department of Computer Science, University of Kiel,
u!i = a T u = 0. Then S satisfies
 Deterministic Conitions for Subspace Ientifiability from Incomplete Sampling Daniel L Pimentel-Alarcón, Nigel Boston, Robert D Nowak University of Wisconsin-Maison Abstract Consier an r-imensional subspace
Deterministic Conitions for Subspace Ientifiability from Incomplete Sampling Daniel L Pimentel-Alarcón, Nigel Boston, Robert D Nowak University of Wisconsin-Maison Abstract Consier an r-imensional subspace
Improved Rate-Based Pull and Push Strategies in Large Distributed Networks
 Improve Rate-Base Pull an Push Strategies in Large Distribute Networks Wouter Minnebo an Benny Van Hout Department of Mathematics an Computer Science University of Antwerp - imins Mielheimlaan, B-00 Antwerp,
Improve Rate-Base Pull an Push Strategies in Large Distribute Networks Wouter Minnebo an Benny Van Hout Department of Mathematics an Computer Science University of Antwerp - imins Mielheimlaan, B-00 Antwerp,
θ x = f ( x,t) could be written as
 9. Higher orer PDEs as systems of first-orer PDEs. Hyperbolic systems. For PDEs, as for ODEs, we may reuce the orer by efining new epenent variables. For example, in the case of the wave equation, (1)
9. Higher orer PDEs as systems of first-orer PDEs. Hyperbolic systems. For PDEs, as for ODEs, we may reuce the orer by efining new epenent variables. For example, in the case of the wave equation, (1)
The Three-dimensional Schödinger Equation
 The Three-imensional Schöinger Equation R. L. Herman November 7, 016 Schröinger Equation in Spherical Coorinates We seek to solve the Schröinger equation with spherical symmetry using the metho of separation
The Three-imensional Schöinger Equation R. L. Herman November 7, 016 Schröinger Equation in Spherical Coorinates We seek to solve the Schröinger equation with spherical symmetry using the metho of separation
05 The Continuum Limit and the Wave Equation
 Utah State University DigitalCommons@USU Founations of Wave Phenomena Physics, Department of 1-1-2004 05 The Continuum Limit an the Wave Equation Charles G. Torre Department of Physics, Utah State University,
Utah State University DigitalCommons@USU Founations of Wave Phenomena Physics, Department of 1-1-2004 05 The Continuum Limit an the Wave Equation Charles G. Torre Department of Physics, Utah State University,
. Using a multinomial model gives us the following equation for P d. , with respect to same length term sequences.
 S 63 Lecture 8 2/2/26 Lecturer Lillian Lee Scribes Peter Babinski, Davi Lin Basic Language Moeling Approach I. Special ase of LM-base Approach a. Recap of Formulas an Terms b. Fixing θ? c. About that Multinomial
S 63 Lecture 8 2/2/26 Lecturer Lillian Lee Scribes Peter Babinski, Davi Lin Basic Language Moeling Approach I. Special ase of LM-base Approach a. Recap of Formulas an Terms b. Fixing θ? c. About that Multinomial
Ramsey numbers of some bipartite graphs versus complete graphs
 Ramsey numbers of some bipartite graphs versus complete graphs Tao Jiang, Michael Salerno Miami University, Oxfor, OH 45056, USA Abstract. The Ramsey number r(h, K n ) is the smallest positive integer
Ramsey numbers of some bipartite graphs versus complete graphs Tao Jiang, Michael Salerno Miami University, Oxfor, OH 45056, USA Abstract. The Ramsey number r(h, K n ) is the smallest positive integer
Perfect Matchings in Õ(n1.5 ) Time in Regular Bipartite Graphs
 Perfect Matchings in Õ(n1.5 ) Time in Regular Bipartite Graphs Ashish Goel Michael Kapralov Sanjeev Khanna Abstract We consier the well-stuie problem of fining a perfect matching in -regular bipartite
Perfect Matchings in Õ(n1.5 ) Time in Regular Bipartite Graphs Ashish Goel Michael Kapralov Sanjeev Khanna Abstract We consier the well-stuie problem of fining a perfect matching in -regular bipartite
The Principle of Least Action
 Chapter 7. The Principle of Least Action 7.1 Force Methos vs. Energy Methos We have so far stuie two istinct ways of analyzing physics problems: force methos, basically consisting of the application of
Chapter 7. The Principle of Least Action 7.1 Force Methos vs. Energy Methos We have so far stuie two istinct ways of analyzing physics problems: force methos, basically consisting of the application of
Closed and Open Loop Optimal Control of Buffer and Energy of a Wireless Device
 Close an Open Loop Optimal Control of Buffer an Energy of a Wireless Device V. S. Borkar School of Technology an Computer Science TIFR, umbai, Inia. borkar@tifr.res.in A. A. Kherani B. J. Prabhu INRIA
Close an Open Loop Optimal Control of Buffer an Energy of a Wireless Device V. S. Borkar School of Technology an Computer Science TIFR, umbai, Inia. borkar@tifr.res.in A. A. Kherani B. J. Prabhu INRIA
Thermal conductivity of graded composites: Numerical simulations and an effective medium approximation
 JOURNAL OF MATERIALS SCIENCE 34 (999)5497 5503 Thermal conuctivity of grae composites: Numerical simulations an an effective meium approximation P. M. HUI Department of Physics, The Chinese University
JOURNAL OF MATERIALS SCIENCE 34 (999)5497 5503 Thermal conuctivity of grae composites: Numerical simulations an an effective meium approximation P. M. HUI Department of Physics, The Chinese University
Lower Bounds for Local Monotonicity Reconstruction from Transitive-Closure Spanners
 Lower Bouns for Local Monotonicity Reconstruction from Transitive-Closure Spanners Arnab Bhattacharyya Elena Grigorescu Mahav Jha Kyomin Jung Sofya Raskhonikova Davi P. Wooruff Abstract Given a irecte
Lower Bouns for Local Monotonicity Reconstruction from Transitive-Closure Spanners Arnab Bhattacharyya Elena Grigorescu Mahav Jha Kyomin Jung Sofya Raskhonikova Davi P. Wooruff Abstract Given a irecte
II. First variation of functionals
 II. First variation of functionals The erivative of a function being zero is a necessary conition for the etremum of that function in orinary calculus. Let us now tackle the question of the equivalent
II. First variation of functionals The erivative of a function being zero is a necessary conition for the etremum of that function in orinary calculus. Let us now tackle the question of the equivalent
TOEPLITZ AND POSITIVE SEMIDEFINITE COMPLETION PROBLEM FOR CYCLE GRAPH
 English NUMERICAL MATHEMATICS Vol14, No1 Series A Journal of Chinese Universities Feb 2005 TOEPLITZ AND POSITIVE SEMIDEFINITE COMPLETION PROBLEM FOR CYCLE GRAPH He Ming( Λ) Michael K Ng(Ξ ) Abstract We
English NUMERICAL MATHEMATICS Vol14, No1 Series A Journal of Chinese Universities Feb 2005 TOEPLITZ AND POSITIVE SEMIDEFINITE COMPLETION PROBLEM FOR CYCLE GRAPH He Ming( Λ) Michael K Ng(Ξ ) Abstract We
Solutions to Math 41 Second Exam November 4, 2010
 Solutions to Math 41 Secon Exam November 4, 2010 1. (13 points) Differentiate, using the metho of your choice. (a) p(t) = ln(sec t + tan t) + log 2 (2 + t) (4 points) Using the rule for the erivative of
Solutions to Math 41 Secon Exam November 4, 2010 1. (13 points) Differentiate, using the metho of your choice. (a) p(t) = ln(sec t + tan t) + log 2 (2 + t) (4 points) Using the rule for the erivative of
Qubit channels that achieve capacity with two states
 Qubit channels that achieve capacity with two states Dominic W. Berry Department of Physics, The University of Queenslan, Brisbane, Queenslan 4072, Australia Receive 22 December 2004; publishe 22 March
Qubit channels that achieve capacity with two states Dominic W. Berry Department of Physics, The University of Queenslan, Brisbane, Queenslan 4072, Australia Receive 22 December 2004; publishe 22 March
Calculus of Variations
 Calculus of Variations Lagrangian formalism is the main tool of theoretical classical mechanics. Calculus of Variations is a part of Mathematics which Lagrangian formalism is base on. In this section,
Calculus of Variations Lagrangian formalism is the main tool of theoretical classical mechanics. Calculus of Variations is a part of Mathematics which Lagrangian formalism is base on. In this section,
On the Broadcast Capacity of Multihop Wireless Networks: Interplay of Power, Density and Interference
 On the Broacast Capacity of Multihop Wireless Networks: Interplay of Power, Density an Interference Alireza Keshavarz-Haa Ruolf Riei Department of Electrical an Computer Engineering an Department of Statistics
On the Broacast Capacity of Multihop Wireless Networks: Interplay of Power, Density an Interference Alireza Keshavarz-Haa Ruolf Riei Department of Electrical an Computer Engineering an Department of Statistics
18 EVEN MORE CALCULUS
 8 EVEN MORE CALCULUS Chapter 8 Even More Calculus Objectives After stuing this chapter you shoul be able to ifferentiate an integrate basic trigonometric functions; unerstan how to calculate rates of change;
8 EVEN MORE CALCULUS Chapter 8 Even More Calculus Objectives After stuing this chapter you shoul be able to ifferentiate an integrate basic trigonometric functions; unerstan how to calculate rates of change;
Chapter 5. Factorization of Integers
 Chapter 5 Factorization of Integers 51 Definition: For a, b Z we say that a ivies b (or that a is a factor of b, or that b is a multiple of a, an we write a b, when b = ak for some k Z 52 Theorem: (Basic
Chapter 5 Factorization of Integers 51 Definition: For a, b Z we say that a ivies b (or that a is a factor of b, or that b is a multiple of a, an we write a b, when b = ak for some k Z 52 Theorem: (Basic
Leaving Randomness to Nature: d-dimensional Product Codes through the lens of Generalized-LDPC codes
 Leaving Ranomness to Nature: -Dimensional Prouct Coes through the lens of Generalize-LDPC coes Tavor Baharav, Kannan Ramchanran Dept. of Electrical Engineering an Computer Sciences, U.C. Berkeley {tavorb,
Leaving Ranomness to Nature: -Dimensional Prouct Coes through the lens of Generalize-LDPC coes Tavor Baharav, Kannan Ramchanran Dept. of Electrical Engineering an Computer Sciences, U.C. Berkeley {tavorb,
The Exact Form and General Integrating Factors
 7 The Exact Form an General Integrating Factors In the previous chapters, we ve seen how separable an linear ifferential equations can be solve using methos for converting them to forms that can be easily
7 The Exact Form an General Integrating Factors In the previous chapters, we ve seen how separable an linear ifferential equations can be solve using methos for converting them to forms that can be easily
Calculus in the AP Physics C Course The Derivative
 Limits an Derivatives Calculus in the AP Physics C Course The Derivative In physics, the ieas of the rate change of a quantity (along with the slope of a tangent line) an the area uner a curve are essential.
Limits an Derivatives Calculus in the AP Physics C Course The Derivative In physics, the ieas of the rate change of a quantity (along with the slope of a tangent line) an the area uner a curve are essential.
Physics 2212 K Quiz #2 Solutions Summer 2016
 Physics 1 K Quiz # Solutions Summer 016 I. (18 points) A positron has the same mass as an electron, but has opposite charge. Consier a positron an an electron at rest, separate by a istance = 1.0 nm. What
Physics 1 K Quiz # Solutions Summer 016 I. (18 points) A positron has the same mass as an electron, but has opposite charge. Consier a positron an an electron at rest, separate by a istance = 1.0 nm. What
APPROXIMATE SOLUTION FOR TRANSIENT HEAT TRANSFER IN STATIC TURBULENT HE II. B. Baudouy. CEA/Saclay, DSM/DAPNIA/STCM Gif-sur-Yvette Cedex, France
 APPROXIMAE SOLUION FOR RANSIEN HEA RANSFER IN SAIC URBULEN HE II B. Bauouy CEA/Saclay, DSM/DAPNIA/SCM 91191 Gif-sur-Yvette Ceex, France ABSRAC Analytical solution in one imension of the heat iffusion equation
APPROXIMAE SOLUION FOR RANSIEN HEA RANSFER IN SAIC URBULEN HE II B. Bauouy CEA/Saclay, DSM/DAPNIA/SCM 91191 Gif-sur-Yvette Ceex, France ABSRAC Analytical solution in one imension of the heat iffusion equation
Convergence of random variables, and the Borel-Cantelli lemmas
 Stat 205A Setember, 12, 2002 Convergence of ranom variables, an the Borel-Cantelli lemmas Lecturer: James W. Pitman Scribes: Jin Kim (jin@eecs) 1 Convergence of ranom variables Recall that, given a sequence
Stat 205A Setember, 12, 2002 Convergence of ranom variables, an the Borel-Cantelli lemmas Lecturer: James W. Pitman Scribes: Jin Kim (jin@eecs) 1 Convergence of ranom variables Recall that, given a sequence
Implicit Differentiation
 Implicit Differentiation Thus far, the functions we have been concerne with have been efine explicitly. A function is efine explicitly if the output is given irectly in terms of the input. For instance,
Implicit Differentiation Thus far, the functions we have been concerne with have been efine explicitly. A function is efine explicitly if the output is given irectly in terms of the input. For instance,
Lecture 5. Symmetric Shearer s Lemma
 Stanfor University Spring 208 Math 233: Non-constructive methos in combinatorics Instructor: Jan Vonrák Lecture ate: January 23, 208 Original scribe: Erik Bates Lecture 5 Symmetric Shearer s Lemma Here
Stanfor University Spring 208 Math 233: Non-constructive methos in combinatorics Instructor: Jan Vonrák Lecture ate: January 23, 208 Original scribe: Erik Bates Lecture 5 Symmetric Shearer s Lemma Here
On combinatorial approaches to compressed sensing
 On combinatorial approaches to compresse sensing Abolreza Abolhosseini Moghaam an Hayer Raha Department of Electrical an Computer Engineering, Michigan State University, East Lansing, MI, U.S. Emails:{abolhos,raha}@msu.eu
On combinatorial approaches to compresse sensing Abolreza Abolhosseini Moghaam an Hayer Raha Department of Electrical an Computer Engineering, Michigan State University, East Lansing, MI, U.S. Emails:{abolhos,raha}@msu.eu
Lecture 2 Lagrangian formulation of classical mechanics Mechanics
 Lecture Lagrangian formulation of classical mechanics 70.00 Mechanics Principle of stationary action MATH-GA To specify a motion uniquely in classical mechanics, it suffices to give, at some time t 0,
Lecture Lagrangian formulation of classical mechanics 70.00 Mechanics Principle of stationary action MATH-GA To specify a motion uniquely in classical mechanics, it suffices to give, at some time t 0,
Stopping-Set Enumerator Approximations for Finite-Length Protograph LDPC Codes
 Stopping-Set Enumerator Approximations for Finite-Length Protograph LDPC Coes Kaiann Fu an Achilleas Anastasopoulos Electrical Engineering an Computer Science Dept. University of Michigan, Ann Arbor, MI
Stopping-Set Enumerator Approximations for Finite-Length Protograph LDPC Coes Kaiann Fu an Achilleas Anastasopoulos Electrical Engineering an Computer Science Dept. University of Michigan, Ann Arbor, MI
1. Aufgabenblatt zur Vorlesung Probability Theory
 24.10.17 1. Aufgabenblatt zur Vorlesung By (Ω, A, P ) we always enote the unerlying probability space, unless state otherwise. 1. Let r > 0, an efine f(x) = 1 [0, [ (x) exp( r x), x R. a) Show that p f
24.10.17 1. Aufgabenblatt zur Vorlesung By (Ω, A, P ) we always enote the unerlying probability space, unless state otherwise. 1. Let r > 0, an efine f(x) = 1 [0, [ (x) exp( r x), x R. a) Show that p f
An M/G/1 Retrial Queue with Priority, Balking and Feedback Customers
 Journal of Convergence Information Technology Volume 5 Number April 1 An M/G/1 Retrial Queue with Priority Balking an Feeback Customers Peishu Chen * 1 Yiuan Zhu 1 * 1 Faculty of Science Jiangsu University
Journal of Convergence Information Technology Volume 5 Number April 1 An M/G/1 Retrial Queue with Priority Balking an Feeback Customers Peishu Chen * 1 Yiuan Zhu 1 * 1 Faculty of Science Jiangsu University
Chromatic number for a generalization of Cartesian product graphs
 Chromatic number for a generalization of Cartesian prouct graphs Daniel Král Douglas B. West Abstract Let G be a class of graphs. The -fol gri over G, enote G, is the family of graphs obtaine from -imensional
Chromatic number for a generalization of Cartesian prouct graphs Daniel Král Douglas B. West Abstract Let G be a class of graphs. The -fol gri over G, enote G, is the family of graphs obtaine from -imensional
Proof of SPNs as Mixture of Trees
 A Proof of SPNs as Mixture of Trees Theorem 1. If T is an inuce SPN from a complete an ecomposable SPN S, then T is a tree that is complete an ecomposable. Proof. Argue by contraiction that T is not a
A Proof of SPNs as Mixture of Trees Theorem 1. If T is an inuce SPN from a complete an ecomposable SPN S, then T is a tree that is complete an ecomposable. Proof. Argue by contraiction that T is not a
Some Examples. Uniform motion. Poisson processes on the real line
 Some Examples Our immeiate goal is to see some examples of Lévy processes, an/or infinitely-ivisible laws on. Uniform motion Choose an fix a nonranom an efine X := for all (1) Then, {X } is a [nonranom]
Some Examples Our immeiate goal is to see some examples of Lévy processes, an/or infinitely-ivisible laws on. Uniform motion Choose an fix a nonranom an efine X := for all (1) Then, {X } is a [nonranom]
Quantum Mechanics in Three Dimensions
 Physics 342 Lecture 20 Quantum Mechanics in Three Dimensions Lecture 20 Physics 342 Quantum Mechanics I Monay, March 24th, 2008 We begin our spherical solutions with the simplest possible case zero potential.
Physics 342 Lecture 20 Quantum Mechanics in Three Dimensions Lecture 20 Physics 342 Quantum Mechanics I Monay, March 24th, 2008 We begin our spherical solutions with the simplest possible case zero potential.
Perturbation Analysis and Optimization of Stochastic Flow Networks
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. XX, NO. Y, MMM 2004 1 Perturbation Analysis an Optimization of Stochastic Flow Networks Gang Sun, Christos G. Cassanras, Yorai Wari, Christos G. Panayiotou,
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. XX, NO. Y, MMM 2004 1 Perturbation Analysis an Optimization of Stochastic Flow Networks Gang Sun, Christos G. Cassanras, Yorai Wari, Christos G. Panayiotou,
1 Heisenberg Representation
 1 Heisenberg Representation What we have been ealing with so far is calle the Schröinger representation. In this representation, operators are constants an all the time epenence is carrie by the states.
1 Heisenberg Representation What we have been ealing with so far is calle the Schröinger representation. In this representation, operators are constants an all the time epenence is carrie by the states.
inflow outflow Part I. Regular tasks for MAE598/494 Task 1
 MAE 494/598, Fall 2016 Project #1 (Regular tasks = 20 points) Har copy of report is ue at the start of class on the ue ate. The rules on collaboration will be release separately. Please always follow the
MAE 494/598, Fall 2016 Project #1 (Regular tasks = 20 points) Har copy of report is ue at the start of class on the ue ate. The rules on collaboration will be release separately. Please always follow the
arxiv: v1 [math.co] 15 Sep 2015
![arxiv: v1 [math.co] 15 Sep 2015 arxiv: v1 [math.co] 15 Sep 2015](/thumbs/93/112169665.jpg) Circular coloring of signe graphs Yingli Kang, Eckhar Steffen arxiv:1509.04488v1 [math.co] 15 Sep 015 Abstract Let k, ( k) be two positive integers. We generalize the well stuie notions of (k, )-colorings
Circular coloring of signe graphs Yingli Kang, Eckhar Steffen arxiv:1509.04488v1 [math.co] 15 Sep 015 Abstract Let k, ( k) be two positive integers. We generalize the well stuie notions of (k, )-colorings
Probabilistic Analysis of Power Assignments
 Probabilistic Analysis of Power Assignments Maurits e Graaf 1,2 an Boo Manthey 1 1 University of Twente, Department of Applie Mathematics, Enschee, Netherlans m.egraaf/b.manthey@utwente.nl 2 Thales Neerlan
Probabilistic Analysis of Power Assignments Maurits e Graaf 1,2 an Boo Manthey 1 1 University of Twente, Department of Applie Mathematics, Enschee, Netherlans m.egraaf/b.manthey@utwente.nl 2 Thales Neerlan
Quantum Search on the Spatial Grid
 Quantum Search on the Spatial Gri Matthew D. Falk MIT 2012, 550 Memorial Drive, Cambrige, MA 02139 (Date: December 11, 2012) This paper explores Quantum Search on the two imensional spatial gri. Recent
Quantum Search on the Spatial Gri Matthew D. Falk MIT 2012, 550 Memorial Drive, Cambrige, MA 02139 (Date: December 11, 2012) This paper explores Quantum Search on the two imensional spatial gri. Recent
Math 1B, lecture 8: Integration by parts
 Math B, lecture 8: Integration by parts Nathan Pflueger 23 September 2 Introuction Integration by parts, similarly to integration by substitution, reverses a well-known technique of ifferentiation an explores
Math B, lecture 8: Integration by parts Nathan Pflueger 23 September 2 Introuction Integration by parts, similarly to integration by substitution, reverses a well-known technique of ifferentiation an explores
FLUCTUATIONS IN THE NUMBER OF POINTS ON SMOOTH PLANE CURVES OVER FINITE FIELDS. 1. Introduction
 FLUCTUATIONS IN THE NUMBER OF POINTS ON SMOOTH PLANE CURVES OVER FINITE FIELDS ALINA BUCUR, CHANTAL DAVID, BROOKE FEIGON, MATILDE LALÍN 1 Introuction In this note, we stuy the fluctuations in the number
FLUCTUATIONS IN THE NUMBER OF POINTS ON SMOOTH PLANE CURVES OVER FINITE FIELDS ALINA BUCUR, CHANTAL DAVID, BROOKE FEIGON, MATILDE LALÍN 1 Introuction In this note, we stuy the fluctuations in the number
Calculus of Variations
 16.323 Lecture 5 Calculus of Variations Calculus of Variations Most books cover this material well, but Kirk Chapter 4 oes a particularly nice job. x(t) x* x*+ αδx (1) x*- αδx (1) αδx (1) αδx (1) t f t
16.323 Lecture 5 Calculus of Variations Calculus of Variations Most books cover this material well, but Kirk Chapter 4 oes a particularly nice job. x(t) x* x*+ αδx (1) x*- αδx (1) αδx (1) αδx (1) t f t
d dx But have you ever seen a derivation of these results? We ll prove the first result below. cos h 1
 Lecture 5 Some ifferentiation rules Trigonometric functions (Relevant section from Stewart, Seventh Eition: Section 3.3) You all know that sin = cos cos = sin. () But have you ever seen a erivation of
Lecture 5 Some ifferentiation rules Trigonometric functions (Relevant section from Stewart, Seventh Eition: Section 3.3) You all know that sin = cos cos = sin. () But have you ever seen a erivation of
On the Aloha throughput-fairness tradeoff
 On the Aloha throughput-fairness traeoff 1 Nan Xie, Member, IEEE, an Steven Weber, Senior Member, IEEE Abstract arxiv:1605.01557v1 [cs.it] 5 May 2016 A well-known inner boun of the stability region of
On the Aloha throughput-fairness traeoff 1 Nan Xie, Member, IEEE, an Steven Weber, Senior Member, IEEE Abstract arxiv:1605.01557v1 [cs.it] 5 May 2016 A well-known inner boun of the stability region of
The derivative of a function f(x) is another function, defined in terms of a limiting expression: f(x + δx) f(x)
 Y. D. Chong (2016) MH2801: Complex Methos for the Sciences 1. Derivatives The erivative of a function f(x) is another function, efine in terms of a limiting expression: f (x) f (x) lim x δx 0 f(x + δx)
Y. D. Chong (2016) MH2801: Complex Methos for the Sciences 1. Derivatives The erivative of a function f(x) is another function, efine in terms of a limiting expression: f (x) f (x) lim x δx 0 f(x + δx)
Schrödinger s equation.
 Physics 342 Lecture 5 Schröinger s Equation Lecture 5 Physics 342 Quantum Mechanics I Wenesay, February 3r, 2010 Toay we iscuss Schröinger s equation an show that it supports the basic interpretation of
Physics 342 Lecture 5 Schröinger s Equation Lecture 5 Physics 342 Quantum Mechanics I Wenesay, February 3r, 2010 Toay we iscuss Schröinger s equation an show that it supports the basic interpretation of
An Analytical Expression of the Probability of Error for Relaying with Decode-and-forward
 An Analytical Expression of the Probability of Error for Relaying with Decoe-an-forwar Alexanre Graell i Amat an Ingmar Lan Department of Electronics, Institut TELECOM-TELECOM Bretagne, Brest, France Email:
An Analytical Expression of the Probability of Error for Relaying with Decoe-an-forwar Alexanre Graell i Amat an Ingmar Lan Department of Electronics, Institut TELECOM-TELECOM Bretagne, Brest, France Email:
Permanent vs. Determinant
 Permanent vs. Determinant Frank Ban Introuction A major problem in theoretical computer science is the Permanent vs. Determinant problem. It asks: given an n by n matrix of ineterminates A = (a i,j ) an
Permanent vs. Determinant Frank Ban Introuction A major problem in theoretical computer science is the Permanent vs. Determinant problem. It asks: given an n by n matrix of ineterminates A = (a i,j ) an
New bounds on Simonyi s conjecture
 New bouns on Simonyi s conjecture Daniel Soltész soltesz@math.bme.hu Department of Computer Science an Information Theory, Buapest University of Technology an Economics arxiv:1510.07597v1 [math.co] 6 Oct
New bouns on Simonyi s conjecture Daniel Soltész soltesz@math.bme.hu Department of Computer Science an Information Theory, Buapest University of Technology an Economics arxiv:1510.07597v1 [math.co] 6 Oct
Math Notes on differentials, the Chain Rule, gradients, directional derivative, and normal vectors
 Math 18.02 Notes on ifferentials, the Chain Rule, graients, irectional erivative, an normal vectors Tangent plane an linear approximation We efine the partial erivatives of f( xy, ) as follows: f f( x+
Math 18.02 Notes on ifferentials, the Chain Rule, graients, irectional erivative, an normal vectors Tangent plane an linear approximation We efine the partial erivatives of f( xy, ) as follows: f f( x+
Balancing Expected and Worst-Case Utility in Contracting Models with Asymmetric Information and Pooling
 Balancing Expecte an Worst-Case Utility in Contracting Moels with Asymmetric Information an Pooling R.B.O. erkkamp & W. van en Heuvel & A.P.M. Wagelmans Econometric Institute Report EI2018-01 9th January
Balancing Expecte an Worst-Case Utility in Contracting Moels with Asymmetric Information an Pooling R.B.O. erkkamp & W. van en Heuvel & A.P.M. Wagelmans Econometric Institute Report EI2018-01 9th January
PDE Notes, Lecture #11
 PDE Notes, Lecture # from Professor Jalal Shatah s Lectures Febuary 9th, 2009 Sobolev Spaces Recall that for u L loc we can efine the weak erivative Du by Du, φ := udφ φ C0 If v L loc such that Du, φ =
PDE Notes, Lecture # from Professor Jalal Shatah s Lectures Febuary 9th, 2009 Sobolev Spaces Recall that for u L loc we can efine the weak erivative Du by Du, φ := udφ φ C0 If v L loc such that Du, φ =
Chapter 6: Energy-Momentum Tensors
 49 Chapter 6: Energy-Momentum Tensors This chapter outlines the general theory of energy an momentum conservation in terms of energy-momentum tensors, then applies these ieas to the case of Bohm's moel.
49 Chapter 6: Energy-Momentum Tensors This chapter outlines the general theory of energy an momentum conservation in terms of energy-momentum tensors, then applies these ieas to the case of Bohm's moel.
