On Characterizing the Delay-Performance of Wireless Scheduling Algorithms
|
|
|
- Rolf Hopkins
- 6 years ago
- Views:
Transcription
1 On Characterizing the Delay-Performance of Wireless Scheuling Algorithms Xiaojun Lin Center for Wireless Systems an Applications School of Electrical an Computer Engineering, Purue University West Lafayette, IN 47907, U.S.A. Abstract In this paper we stuy the problem of characterizing the elay performance of wireless scheuling algorithms. In wireless networks operate uner these wireless scheuling algorithms, there often exists a tight coupling between the service-rate process, the system backlog process, the arrival process an the channel variations. Although one can use sample-path large-eviation techniques to form an estimate of the elay-violation probability uner a given offere loa, the formulation leas to a multi-imensional calculus of variations problem that is often very ifficult to solve. In this paper, we evelop a new technique for aressing this complexity issue. Using ieas from the Lyapunov function approach in control theory, our new technique maps the complex multi-imensional calculus of variations problem to a one-imensional calculus of variations problem, an the latter is often much easier to solve. This new technique can potentially be use to stuy the elayperformance of a large class of wireless scheuling algorithms. I. INTRODUCTION A wireless network may be moele as a system of queues with time-varying service rates. The variability in service rates is ue to a number of factors. First, channel faing an mobility can lea to variations in the link capacity even if the transmission power is fixe. Secon, the transmission power can vary over time accoring to the power control policy. Thir, ue to raio interference, it is usually preferable to scheule only a subset of links to be active at each time, an to alternate the subset of activate links over time. All of these factors lea to a variable service rate at each link. When one is to stuy the performance of any system that involves queues, the first question we can ask is whether the system is stable or not. Here, stability means that all queue length (or equivalently, the elay experience by the packets) remains finite. Conversely, we can ask the question that, in orer to maintain stability, what is the largest offere loa that the system can carry. In other wors, what is the capacity region of the system subject to stability. For wireless networks, these questions have le to results on throughput-optimal scheuling algorithms for scheuling wireless resources. (Here we use the term scheuling in the broaer sense, i.e., it can inclue various control mechanisms at the MAC/PHY layer, e.g., link scheuling, power control, an aaptive coing/moulation.) A scheuling algorithm is throughput-optimal if this algorithm can sustain the largest offere loa while keeping the system stable. In other wors, if this algorithm cannot stabilize the system, no other algorithms can. For example, one such throughput-optimal scheuling algorithm is the algorithm propose in the seminal work by Tassiulas an Ephremies in []. This algorithm chooses at each time, among all possible scheules, the one that maximizes the sum of the queue-weighte-rate over all links. This algorithm has been shown to be throughputoptimal, an it has been the basis for many other throughputoptimal scheuling algorithms for both cellular an multihop wireless networks. Once we know about stability, we are then tempte to ask further questions regaring the istribution of queue length (or elay). For example, at a given offere loa, what is the probability that the elay experience by a packet is greater than a given threshol? Or, conversely, what is the largest offere loa that the system can support at a given elay constraint? (In other wors, what is the effective capacity region of the system uner elay constraints?) Clearly, these question are important for applications that require more stringent elay guarantees than just stability. These elay characterization problem for wireless networks can be ifficult to solve. Here we raw a comparison to the elay characterization problem in wireline networks. In wireline networks, even through the exact elay istribution can be ifficult to obtain, there have been a large boy of work, especially those using large-eviation techniques, to obtain sharp estimates of the elay violation probability of a queue. These wireline network results usually assume that the service rate of the queue is fixe (i.e., time-invariant), an the packet arrival process is known. These results allow us to compute the effective banwith of the arrival process from its (known) statistics [2] [7], which can then be use to etermine the traffic carrying capability of the queue at a given elay constraint. In contrast, in wireless networks, the service rate is time-varying. If the service rate process is again known a priori, large-eviation techniques can be use to compute the effective capacity of the service rate process [8], [9], which is a notion similar to the effective banwith of the arrival process. This effective capacity can again be use to etermine the traffic carrying capability of the queue at a given elay constraint. Unfortunately, uner many wireless scheuling algorithms of interest, even the service rate process is unknown a priori. For example, for
2 a system operate uner the throughput-optimal Tassiulas- Ephremies algorithm of [], or any queue-length base scheuling algorithms, the service rates epen on the queue length, which in turn epen on the arrival process an the channel state, etc. Hence, the statistics of the service rate process is unknown before han. In this case, the elay characterization problem is known to be very ifficult. For these systems, although it is still possible to use samplepath large-eviation techniques to form an estimate of the elay-violation probability [0] [2], such a formulation leas to a multi-imensional calculus of variations problem. Due to the complex coupling between the service rate, the queue length, the arrival process, an the channel state, this multi-imensional calculus of variations problem is very ifficult to solve. Prior successes have been limite to simple systems: either the problem has some restrictive structure (e.g., symmetry among all links) [], or the size of the system is very small (e.g., two links) [0], [2], [3]. In this paper, we propose a new approach to aress this complexity issue. Motivate by the Lyapunov function approach for proving stability of complex systems, we evelop a new technique that maps the complex multi-imensional calculus of variations problem into a one-imensional calculus of variations problem, an the latter is often very easy to solve. The solution to the one-imensional calculus of variations problem will then provie us with an upper boun estimate of the elay violation probability, an consequently, a lower boun estimate of the effective capacity region of the system. For many practical applications, the resulting effective capacity region is useful because the elay constraint is known to be satisfie. We believe that this marriage between sample-path largeeviations an Lyapunov functions can evelop into a powerful theory to characterize the elay performance of wireless systems uner sophisticate scheuling algorithms. We can potentially lower the ifficulty level of the elaycharacterization problem to that of a stability problem. In other wors, for any scheuling algorithm that is provably stable, which usually means that there exists a Lyapunov function, we coul then apply the propose technique to characterize the elay performance. We provie an example of how this approach can be use to solve a more ifficult problem than those stuie in the literature. The rest of the paper is organize as follows. We present the network moel in Section II. We review a formulation of the sample-path large-eviation principle, an ientify the complexity of the associate calculus of variations problem in Section III. Then, in Section IV, we provie a Lyapunov function base approach to aress the complexity issue. In Section V, we provie an example to show how such an approach can be use. Then we conclue. II. THE SYSTEM MODEL We consier the following moel for a wireless system with L links. In orer to moel channel faing, we assume that the system can be in one of S states. We assume a slotte system, an enote the state of the system at time t to be C(t). Further, we assume that the states C(t), t =, 2,... are i.i.., an let p j = P[C(t) = j] enote the probability that the state of the system at time t is j. Let p = [p,..., p S ]. For ease of exposition, in the rest of the paper we also efine Φ j (t) = {C(t)=j} to be the inicator function that the state of the system at time t is j. Let Φ(t) = [Φ (t),..., Φ S (t)]. Clearly, there is a one-to-one mapping between C(t) an Φ(t). Each link correspons to a queue with time-varying service rate. The arrivals at each link i are at a constant rate λ i. The service offere to link i is etermine by the scheuling algorithm, an in general correlates with the service at other links an epens on the system backlog. Let X i (t) enote the backlog at link i at time t, an let X(t) = [X (t),..., X L (t)]. We assume that the service rate offere to link i is a function of the global backlog X(t) an the system state C(t). In particular, let D ij ( X) enote the service offere to link i when the state of the system is j an the global backlog is X. The evolution of the backlog at link i is then given by X i (t+) = [X i (t)+λ i Φ j (t)d ij ( X(t))] +, i =,..., L () where [ ] + enotes the projection to [0, + ). Assume that the system is stationary an ergoic. In this paper, we will focus on stuying the probability that the system backlog excees a certain threshol B. In particular, let ɛ enote our target on the overflow probability, we woul like to ensure that P[ X(0) B] ɛ, (2) where is an appropriately chosen norm, an B is the overflow threshol. Note that the constraint in (2) is equivalent to a constraint on the elay-violation probability when the arrival rates λ i are constant, because the two types of constraints are relate by P[Delay at link i i ] = P[X i (0) λ i i ]. Hence, in the rest of the paper we will often refer to (2) as a elay constraint [9], []. Unfortunately, the problem of calculating the exact probability P[ X(0) B] is often mathematically intractable. In this paper, we are intereste in using large-eviation techniques to compute estimates of this probability. We assume that the following large-eviation result for the backlog process X(t) hols. That is, when B is large, the following limit exists lim B B log P[ X(0) B] = I 0 ( λ), (3) where I 0 ( λ) can be etermine from a sample-path largeeviation principle that we will escribe in Section III. Equation (3) implies that, when B is large, the overflow probability can be approximate as P[ X(0) B] exp( BI 0 ( λ)).
3 Thus, the problem of estimating the overflow probability is reuce to that of computing the rate I 0 ( λ). Alternatively, using the above approximation, in orer to satisfy the constraint (2), we only nee to ensure that I 0 ( λ) θ log ɛ B. (4) We can then efine the effective capacity region uner the constraint (2) as the set of arrival rates λ such that the above inequality hols. III. THE SAMPLE-PATH LARGE DEVIATION PRINCIPLE In this paper, we will stuy the problem of computing the rate I 0 ( λ) an characterizing the effective capacity region uner the constraint (2). We first escribe how I 0 ( λ) can be etermine from a sample-path large-eviation principle for the backlog process X(t). (Note that establishing such a large-eviation principle is not the main focus of the paper. We refer the reaers to [0] [2] for etails on the technical assumptions uner which such a large-eviation principle hols.) A. Notations We follow the convention in [0], []. For a large enough T, efine the empirical measure process on the time interval [, 0] as s B j (t) = B B(T +t) l=0 {C(l)=j}, for t = k B T, k = 0,..., BT, an by linear interpolation otherwise. Note that, in the above efinition, we have scale both the time an the magnitue. The quantity s B j (t) can be interprete as the sum of the (scale) time in [, t] that the system is at state j. Further, it is easy to check that sb j (t) = t + T for all t [, 0]. Let sb (t) = [s B (t),...s B S (t)]. Further, let φb j (t) = t sb j (t). (Note that the erivative is well efine almost everywhere on [, 0] except when t = k/b T for some integer k.) Let φ B (t) = [φ B (t),..., φ B S (t)]. Note that φb j (t) = for almost all t. Analogously, efine the scale backlog process as, x B i (t) = B X i(b(t + t)), for t = k B T, k = 0,..., BT, an by linear interpolation otherwise. Let x B (t) = [x B (t),..., x B L (t)]. Note that accoring to (), the backlog process x B (t) is relate to the process φ B (t) by x B i (t + /B) xb i (t) /B = λ i D ij ( x B (t)) t+/b t φ B j (s)s, for t = k B T, k = 0,..., BT. (5) Thus, given a particular initial conition x B ( ), Equation (5) efines a mapping f B from the empirical measure process s B (t) to the backlog process x B (t). Further, although we have assume s B (t) to be piecewise linear to begin with, the efinition of the mapping f B can be naturally extene to all absolute continuous functions s B (t). B. The Large-Deviation Principle Let B. We now have a sequence of scale ranom walks s B (t), an they map to a sequence of scale backlog processes x B (t) through the sequence of mappings f B. For any φ 0 an φ j =, efine H( φ p) = φ j log φj p j. The sequence of empirical measure processes s B (t) are known to satisfy a sample-path large eviation principle [4, p76] with large-eviation rate-function Is T ( s( )) given as follows: I T s ( s( )) = H( φ(t) p)t, if s(t) is absolute continuous an component-wise nonecreasing on [, 0], s( ) = 0, an s j(t) = t + T for all t; where φ(t) = t x(t). (Note that φ(t) is well efine almost everywhere on [, 0] since s(t) is absolute continuous on [, 0].) Otherwise, I T s ( s( )) = +. Such a large-eviation principle means that, for any set Γ of trajectories on [, 0] that is a continuity set [4, p5] accoring to the essential supremum norm [4, p76, p352], the probability that the sequence of empirical measure processes s B (t) fall into Γ must satisfy lim B B log P[ sb ( ) Γ] = s( ) Γ IT s ( s( )). (6) The large-eviation rate-function Is T ( ) characterizes how rarely each trajectory is. Note that Is T ( s( )) 0 for all trajectory s( ). The larger the value of Is T ( s( )) is, the further the empirical probability istribution φ(t) eviates from the prior probability istribution p. Hence, the less likely the trajectory s( ) will occur. Equation (6) reflects the wellknown large-eviation philosophy that rare events occur in the most-likely way. Precisely, when B is large, the probability that the empirical measure process s B (t) falls into a set Γ is etermine by the trajectory in Γ that is most likely to occur, i.e., with the smallest Is T ( s( )). Next, assume that the sequence of mappings f B has a limiting mapping f that also maps any absolute continuous empirical measure process s(t) to a backlog processes x(t). Assume that the limiting mapping f is of the form t x i(t) = λ i φ j (t) ij ( x(t)), (7) where φ(t) = t s(t). (Note that this equation may be viewe as the limit of (5) when B, although the function ij ( x(t)) may not be exactly the same as D ij ( x(t)) as we will see in the example in Section V.) Further, assume that the sequence of mappings f B are exponentially equivalent to f [4, p30], an the mapping f is continuous (see [0] for
4 Fig.. Top: The overflow probability P[ X(0) B] is relate to the most likely path to overflow. Bottom: our new approach maps any multiimensional path x(t) to a one-imensional path V (t). etails of how the continuity of f may be verifie). For any sequence of backlog processes that start from x B ( ) = 0, we can then invoke the contraction principle [4, p3] an obtain a sample-path large-eviation principle for the sequence of backlog processes x B (t) with large-eviation rate-function given by: I T x ( x( )) = s( ): x( )=f( s( )) { } H( φ(t) p)t where φ(t) = t s(t), an the imum is taken over all empirical measure processes s( ) that map to the backlog process x( ) given that x( ) = 0, uner the mapping f. Finally, the event of overflow correspons to x B (0). As B, we have, I 0 ( λ) lim B B log P[ xb (0) ] = {Ix T ( x( )) over all trajectory x( ) that goes from x( ) = 0 for some T > 0 to x(0) = }. (8) The trajectory that attains the imum in (8) is often calle the most likely path to overflow (see Figure ). Clearly, in orer to estimate the overflow probability P[ X(0) B], all we nee is to fin out which trajectory in (8) is the mostlikely path to overflow. C. The Path-Explosion Challenge Unfortunately, the imum in (8) (a calculus of variations problem) is often very ifficult to evaluate, because it is taken over an inite number of multi-imensional paths x(t). To see this, let us efine the local rate-function l( x, y) = {H( φ p) over all φ such that φ j = an y i = λ i φ j ij ( x) for all i}. (9) Then, we have I T x ( x( )) = l( x(t), x (t))t. Note that the local rate-function l( x, y) characterizes how rarely that, given x(t) = x at some time t, x(t) will follow the irection t x(t) = y immeiately after t. Suppose now we enforce a elay constraint in the form of P[ X(0) B] ɛ. Using (8) to approximate this probability, we then nee to ensure that I T x ( x( )) = l( x(t), x (t))t θ log ɛ/b (0) for all sample paths x(t) that go from 0 at some past time to x(0) =. For avance wireless scheuling algorithms like the Tassiulas-Ephremies algorithm [], the complexity of enumerating all such paths soon becomes prohibitive. Prior successes have been limite to simple systems: either the problem has some restrictive structure (e.g., symmetry among all links) [], or the size of the system is very small (e.g., two links) [0], [2], [3]. IV. A NEW APPROACH COMBINING LARGE-DEVIATIONS WITH LYAPUNOV STABILITY In this section, we will evelop a general approach for solving problems (8) an (0). As we iscusse earlier, fining the most likely path to overflow is often a very ifficult problem. In this section, instea of solving the calculus of variations problem on the right-han-sie of (8), we construct a lower boun for it. That is, we will fin a quantity θ 0 such that I T x ( x( )) θ 0 for all trajectory x( ) that goes from x( ) = 0 at some past time to x(0) =. Hence, we obtain an upper boun on the overflow probability. If θ 0 θ, we then obtain a sufficient conition for meeting the constraint (4) on the overflow probability. Consequently, we also obtain a lower boun on the effective capacity region of the system uner the constraint (2). How to fin such a lower boun θ 0? In this section, we evelop a new approach that is motivate by the Lyapunov function approach for proving stability for complex systems [5]. Note that for a complex system like (), it becomes ifficult to even establish stability, i.e., to show that all queues will remain finite. To see this, take the limit B + again for (5). The flui limit of the system is governe by [6] t x i(t) = λ i p j D ij ( x(t)) h i ( x(t)), for all i () or, in vector form t x(t) = h( x(t)). This flui limit ynamics can be viewe as the mean behavior of the system. The original system woul be stable if the solution of the ODE (orinary ifferential equation) in () can be shown to converge to zero from any initial conition [6]. However, solving the above orinary ifferential equation is often very ifficult. Thus, it is usually impossible
5 to establish the stability of the system by irectly solving the ODE. To circumvent this ifficulty, we usually fin a Lyapunov function V ( x), such that V ( x) 0, an V ( x) = 0 if an only if x = 0. We then prove stability by showing a negative rift for V ( ), i.e. t V ( x(t)) = ( V x ) T x t δv ( x(t)), (2) where δ is a small positive constant. Thus, if x(t), or equivalently, V ( x(t)), is away from zero, the negative rift will pull them back to zero. The negative rift then provies a sufficient conition for V ( x(t)) 0, which implies that x(t) 0, as t. Here, the key to the Lyapunov function approach is to map the convergence of a multi-imensional path x(t), to the convergence of a oneimensional path V ( x(t)), which is then much easier to show. Since V ( x(t)) 0 provies a sufficient conition for all solutions x(t) of the ODE to go to zero, the Lyapunov function approach allows us to ientify a lower boun on the capacity region of the system (subject to stability). Can we use a similar Lyapunov function approach to characterize the elay performance (an the overlow probability) of wireless scheuling algorithms? Inee, we now show that such an approach is feasible. Without loss of generality, assume that the Lyapunov function V ( ) are chosen such that x = implies V ( x). Accoring to (2), for any w > δv ( x(t)), the trajectory with t V ( x(t)) = w becomes a rare event. Define l V (v, w) = {l( x, y) over all ( x, y) such that ( ) T V V ( x) = v an y = w}. (3) x Let us abuse notation an let V (t) = V ( x(t)). Compare with (9), l V (v, w) becomes the local rate-function for V (t), i.e., it characterizes how rarely that, given V (t) = v at some time t, V (t) will follow the irection t V (t) = w immeiately after t. It is easy to show that Ix T ( x( )) in (0) satisfies I T x ( x( )) = Let θ 0 = { l( x(t), x (t))t l V (V (t), V (t))t. l V (V (t), V (t))t over all trajectory V ( ) that goes from V ( ) = 0 for some T > 0 to V (0) = }. (4) We then obtain a lower boun θ 0 for the calculus of variations problem (8). It is also easy to see that a sufficient conition for all samples paths x(t) to meet the constraint (0) is l V (V (t), V (t))t θ (5) for all one-imension path V (t) that goes from V ( ) = 0 to V (0) =. Again, we have successfully reuce the original multi-imensional calculus of variations problem to a one-imensional problem. The one-imensional calculus of variations problem in (4) an (5) is usually much easier to solve (Fig. ). A Unifie Theory Combining Large-Deviation an Lyapunov Stability: As we have just seen, by combining large-eviations with Lyapunov stability, we have create a powerful theory for characterizing the elay-performance of wireless scheuling algorithms. We can potentially lower the ifficulty level of the elay-characterization problem to that of a stability problem. In other wors, for any scheuling algorithm that is provably stable, which usually means that there exists a Lyapunov function, we coul then apply the above techniques to characterize the elay performance. Since (5) is a sufficient conition to (0), we can obtain an upper boun on the overflow probability, an corresponingly, if a constraint on the overflow proability is impose, we obtain a lower boun on the effective capacity region. The hope of this approach is that, if the function V ( ) is appropriately chosen, we may recover a large fraction of, or even the entire effective capacity region. V. AN EXAMPLE In this section, we apply the methoology of Section IV to the elay-characterization problem in []. The moel of [] is a base-station serving N users (Fig. 2). Packets for user i arrive at a constant rate λ i. Only one user can be scheule for transmission at any time. The faing channel between the base-station an each user is i.i... At each timeslot, a user s channel is ON with probability p, an OFF with probability p. Let F enote the banwith of the system. Hence, if a user s channel is ON an it is scheule for transmission, its service rate is F. The throughput-optimal Tassiulas-Ephremies algorithm [] in this case is the QLB (Queue-Length Base) algorithm, i.e., the base-station shoul scheule the ON user with the longest queue []. The more challenging question is to etermine the effective capacity region of the system, subject to the buffer overflow constraint P[ max X i B] ɛ, where X i is the ranom variable i=,...,n that enotes the backlog of user i. The authors of [] assume that all users have the same offere loa, i.e., λ i = λ for all i =, 2,..., N. Uner this assumption, the most likely path to overflow in (8) can be explicitly solve. They then establish the following effective capacity region: [ Nλ min N M N θ log ( p) M +( ( p) M ) exp( F θ M ) ] (6) where θ = log ɛ/b. However, for non-ientical offere loas, it appears very ifficult to follow the solution approach of []. We now use the methoology of Section IV to solve the elay characterization problem when the offere loas λ i are non-ientical. Following the notations in Sections II an III, the set of possible channel states are
6 l( x, y) as l( x, y) = φ j= H( φ p) subject to y i = λ i φ j ij ( x) for all i. Fig. 2. The scheuling problem in cellular networks uner faing channel. S = {(a,..., a N ) a,..., a N = ON or OFF}. The probability that the channel state C(t) at time t is j is given by, p j = p n(j) ( p) N n(j), where n(j) is the number of users with ON channel at state j. When the state is j an the system backlog is x, let I ( x, j) enote the set of those users whose channels are ON an who have the (ientically) largest queue x i among ON users. The evolution of the backlog is then given by (), where the function can be chosen as D ij ( x(t)) = F/ I ( x(t), j) if i I ( x(t), j), an D ij ( x(t)) = 0 otherwise. We can efine f B accoring to (5). As B, the limiting mapping f is given by (7). It is easy to show that the function ij ( ) in (7) must satisfy ij ( x(t)) = 0 if i / I ( x(t), j). Further, if the set I ( x(t), j) contains only one user i, i.e., there is a unique ON user i that has the largest queue at time t, then ij ( x(t)) = F. However, if I ( x(t), j) contains multiple users, the efinition of ij ( x(t)) becomes somewhat involve [0] [2]. Roughly speaking, ij ( x(t)) shoul be efine so that the users in I ( x(t), j) can maintain ientical queues as much as possible. Regarless of the exact form of ij ( ), the following relationship can be shown. For a given trajectory x( ), let I ( x(t)) = {i x i (t) = max k x k (t)} be the set of users with the (ientically) largest queue at time t. (Note that I ( x) is ifferent from I ( x, j) since in the efinition of I ( x) we o not check whether a user is ON or OFF.) Further, let I 2 ( x(t), x (t)) = {i I ( x(t)) t x i(t) = max k I ( x(t)) t x k(t)}. That is, I 2 ( x(t), x (t)) is the set of users that, among those users with the largest queue at time t, also have the largest queue growth rate. In other wors, these set of users will have the largest queue immeiately after time t. Then, immeiately after time t, as long as one user in I 2 ( x(t), x (t) is ON, this group of users collectively must receive the full service rate F. Therefore, using (7), we must have = i I 2( x(t), x (t)) i I 2( x(t), x (t)) t x i(t) λ i F (I 2( x(t), x (t))) φ j. (7) where for any subset A {, 2,...N}, S(A) enotes the set of states j such that some user i A is ON. We can then use (9) an write own the formulation for Let the Lyapunov function be V ( x) = max i x i. Although V ( ) is not ifferentiable at every point, it is sufficient to eal with its one-sie erivative. In the rest of this section, when we use the notation g(t) g(t+s) g(t) t, we will mean lim s 0 s. We thus have V ( x(t)) t = max i I ( x(t)) x i (t), t (Recall that I ( x) = {i x i = max k x k } is the set of users with the ientically largest queue when the system backlog is x.) Thus, using (3), we have, l V (v, w) = subject to l( x, y) max x i = v i max y i = w. i I ( x) Combining the above two optimization problems, we thus have l V (v, w) = φ j= subject to H( φ p) (8) max x i = v i max y i = w i I ( x) y i = λ i φ j ij ( x), for all i. This optimization problem is still quite ifficult to solve. We will be contente to obtain a lower boun for the optimal value. First, recall that I 2 ( x, y) = {i I ( x) y i = max y k}. k I ( x) Let us first compute the imum of (8) for all x, y such that I 2 ( x, y) = M, where M is a given subset of {,..., N}. This sub-optimization can be written as l V,M (v, w) = φ j= subject to H( φ p) (9) x i = v for i M x i v for i / M y i = w for i M y i < w for i I ( x)/m y i = λ i φ j ij ( x) for all i. Note that for all i M = I 2 ( x, y), we have w = λ i φ j ij ( x).
7 Summing over all i I 2 ( x, y), an using (7), we have, M w = λ i F φ j, i M (M) where M enotes the carinality of M. (Recall also that S(M) is the set of states j such that some user in M is ON.) We can then relax the constraints of (9) as: lv,m (v, w) = φ j= subject to H( φ p) (20) M w = λ i F i M (M) φ j. This subproblem is solve in [], an the solution is given by lv,m (v, w) = u log where u = u ( p) +( u) log u M ( p). M i M λi M w F lv (v, w) =. Let lv,m (v, w). (2) M {,2,...,N} Since (20) is a relaxation of (9), we have, l V (v, w) = l V,M(v, w) lv,m (v, w) = l V (v, w). M M Therefore, in orer to ensure that l( x(t), x (t))t θ for all trajectory x( ) that goes from x( ) = 0 at some past time to x(0) =, it is sufficient to ensure that θ { lv (V (t), V (t))t over all trajectory V ( ) that goes from V ( ) = 0 for some T > 0 to V (0) = }. (22) Note that l V (v, w) in (2) oes not epen on v. Therefore, the trajectory V ( ) that attains the imum in (22) is in fact very easy to solve [7, p520], an the imum is equal to w 0 lv (v, w)/w. Therefore, using the efinition of l V (, ) an l V,M (, ), it is then sufficient to ensure that where θ w 0 = M w 0 = M w l V (v, w) w l V,M (v, w) 0 u i M λ i F M i M λ i uf D M (u p) D M (u p) = u u log ( p) + ( u) log u M ( p). M Note that the above conition is equivalent to θ 0 u i M λ i F M i M λ i uf D M (u p) (23) for all M {, 2,..., N}. For a fixe M, the conition (23) is shown in [] to be equivalent to λ i M [ log ( p) M θ i M +( ( p) M ) exp( F θ ] M ). (24) Thus, we obtain a lower boun on the effective capacity region as { λ Inequality (24) hols for all M {, 2,..., N}}. (25) Remark: Note that (25) reuces to (6) when all λ i are equal. Thus, we not only reprouce a lower boun on the effective capacity region for the case with ientical offere loas (which is the same as the effective capacity region foun in []), but also solve the more general problem with non-ientical offer loas. VI. CONCLUSIONS In this paper we stuy the problem of characterizing the elay performance of complex wireless scheuling algorithms. Our main contribution is to evelop a new technique for aressing the complexity issue of the calculus of variations problem involve in the sample-path large eviation approach. Our new technique combines samplepath large eviations with Lyapunov stability, which may evelop into a powerful approach to stuy a large class of scheuling algorithms. We also illustrate the potential of such an approach through an example. REFERENCES [] L. Tassiulas an A. Ephremies, Stability Properties of Constraine Queueing Systems an Scheuling Policies for Maximum Throughput in Multihop Raio Networks, IEEE Transactions on Automatic Control, vol. 37, no. 2, pp , December 992. [2] F. P. Kelly, Effective Banwith in Multiclass Queues, Queueing Systems, vol. 9, pp. 5 6, 99. [3] A. I. Elwali an D. Mitra, Effective Banwith of General Markovian Traffic Sources an Amission Control of High Spee Networks, IEEE/ACM Transactions on Networking, vol., no. 3, pp , June 993. [4] G. Kesiis, J. Walran, an C.-S. Chang, Effective Banwith for Multiclass Markov Flui an other ATM Sources, IEEE/ACM Transactions on Networking, vol., no. 4, pp , Aug [5] D. D. Botvich an N. G. Duffiel, Large Deviations, the Shape of the Loss Curve, an Economies of Scale in Large Multiplexers, Queueing Systems, vol. 20, pp , 995. [6] N. G. Duffiel an N. O Connell, Large eviations an overflow probabilities for the general single server queue, with application, Math. Proc. Cambr. Phil. Soc., vol. 8, pp , 995. [7] C. Courcoubetis an R. Weber, Buffer Overflow Asymptotics for a Buffer Hanling Many Traffic Sources, Journal of Applie Probability, vol. 33, pp , 996. [8] D. Wu an R. Negi, Effective Capacity: A Wireless Link Moel for Support of Quality of Service, IEEE Transactions on Wireless Communications, vol. 2, no. 4, pp , July [9] A. Eryilmaz an R. Srikant, Scheuling with Quality of Service Constraints over Rayleigh Faing Channels, in Proceeings of the IEEE Conference on Decision an Control, [0] S. Shakkottai, Effective Capacity an QoS for Wireless Scheuling, available at shakkott/pub.html, [] L. Ying, R. Srikant, A. Eryilmaz, an G. E. Dulleru, A Large Deviations Analysis of Scheuling in Wireless Networks, in Workshop on Rare Events in Communication Networks, EURANDOM, February 2005.
8 [2] D. Bertsimas, I. C. Paschaliis, an J. N. Tsitsiklis, Asymptotic Buffer Overflow Probabilities in Multiclass Multiplexers: An Optimal Control Approach, IEEE Transactions on Automatic Control, vol. 43, no. 3, pp , March 998. [3] S. Shakkottai, Moes of overflow, effective capacity an qos for wireless scheuling, in Proceeings of IEEE International Symposium on Information Theory, Yokohama, Japan, July [4] A. Dembo an O. Zeitouni, Large Deviations Techniques an Applications, 2n e. New York: Springer-Verlag, 998. [5] H. K. Khalil, Nonlinear Systems, 2n e. Upper Sale River, New Jersey: Prentice-Hall, 996. [6] J. G. Dai, On Positive Harris Recurrence of Multiclass Queueing Networks: A Unifie Approach via Flui Limit Moels, Annals of Applie Probability, vol. 5, no., pp , 995. [7] A. Shwartz an A. Weiss, Large Deviations for Performance Analysis: Queues, Communications, an Computing. Lonon: Chapman & Hall, 995.
Lyapunov Functions. V. J. Venkataramanan and Xiaojun Lin. Center for Wireless Systems and Applications. School of Electrical and Computer Engineering,
 On the Queue-Overflow Probability of Wireless Systems : A New Approach Combining Large Deviations with Lyapunov Functions V. J. Venkataramanan an Xiaojun Lin Center for Wireless Systems an Applications
On the Queue-Overflow Probability of Wireless Systems : A New Approach Combining Large Deviations with Lyapunov Functions V. J. Venkataramanan an Xiaojun Lin Center for Wireless Systems an Applications
6 General properties of an autonomous system of two first order ODE
 6 General properties of an autonomous system of two first orer ODE Here we embark on stuying the autonomous system of two first orer ifferential equations of the form ẋ 1 = f 1 (, x 2 ), ẋ 2 = f 2 (, x
6 General properties of an autonomous system of two first orer ODE Here we embark on stuying the autonomous system of two first orer ifferential equations of the form ẋ 1 = f 1 (, x 2 ), ẋ 2 = f 2 (, x
Closed and Open Loop Optimal Control of Buffer and Energy of a Wireless Device
 Close an Open Loop Optimal Control of Buffer an Energy of a Wireless Device V. S. Borkar School of Technology an Computer Science TIFR, umbai, Inia. borkar@tifr.res.in A. A. Kherani B. J. Prabhu INRIA
Close an Open Loop Optimal Control of Buffer an Energy of a Wireless Device V. S. Borkar School of Technology an Computer Science TIFR, umbai, Inia. borkar@tifr.res.in A. A. Kherani B. J. Prabhu INRIA
Schrödinger s equation.
 Physics 342 Lecture 5 Schröinger s Equation Lecture 5 Physics 342 Quantum Mechanics I Wenesay, February 3r, 2010 Toay we iscuss Schröinger s equation an show that it supports the basic interpretation of
Physics 342 Lecture 5 Schröinger s Equation Lecture 5 Physics 342 Quantum Mechanics I Wenesay, February 3r, 2010 Toay we iscuss Schröinger s equation an show that it supports the basic interpretation of
Time-of-Arrival Estimation in Non-Line-Of-Sight Environments
 2 Conference on Information Sciences an Systems, The Johns Hopkins University, March 2, 2 Time-of-Arrival Estimation in Non-Line-Of-Sight Environments Sinan Gezici, Hisashi Kobayashi an H. Vincent Poor
2 Conference on Information Sciences an Systems, The Johns Hopkins University, March 2, 2 Time-of-Arrival Estimation in Non-Line-Of-Sight Environments Sinan Gezici, Hisashi Kobayashi an H. Vincent Poor
Throughput Optimal Control of Cooperative Relay Networks
 hroughput Optimal Control of Cooperative Relay Networks Emun Yeh Dept. of Electrical Engineering Yale University New Haven, C 06520, USA E-mail: emun.yeh@yale.eu Ranall Berry Dept. of Electrical an Computer
hroughput Optimal Control of Cooperative Relay Networks Emun Yeh Dept. of Electrical Engineering Yale University New Haven, C 06520, USA E-mail: emun.yeh@yale.eu Ranall Berry Dept. of Electrical an Computer
Improved Rate-Based Pull and Push Strategies in Large Distributed Networks
 Improve Rate-Base Pull an Push Strategies in Large Distribute Networks Wouter Minnebo an Benny Van Hout Department of Mathematics an Computer Science University of Antwerp - imins Mielheimlaan, B-00 Antwerp,
Improve Rate-Base Pull an Push Strategies in Large Distribute Networks Wouter Minnebo an Benny Van Hout Department of Mathematics an Computer Science University of Antwerp - imins Mielheimlaan, B-00 Antwerp,
NOTES ON EULER-BOOLE SUMMATION (1) f (l 1) (n) f (l 1) (m) + ( 1)k 1 k! B k (y) f (k) (y) dy,
 NOTES ON EULER-BOOLE SUMMATION JONATHAN M BORWEIN, NEIL J CALKIN, AND DANTE MANNA Abstract We stuy a connection between Euler-MacLaurin Summation an Boole Summation suggeste in an AMM note from 196, which
NOTES ON EULER-BOOLE SUMMATION JONATHAN M BORWEIN, NEIL J CALKIN, AND DANTE MANNA Abstract We stuy a connection between Euler-MacLaurin Summation an Boole Summation suggeste in an AMM note from 196, which
θ x = f ( x,t) could be written as
 9. Higher orer PDEs as systems of first-orer PDEs. Hyperbolic systems. For PDEs, as for ODEs, we may reuce the orer by efining new epenent variables. For example, in the case of the wave equation, (1)
9. Higher orer PDEs as systems of first-orer PDEs. Hyperbolic systems. For PDEs, as for ODEs, we may reuce the orer by efining new epenent variables. For example, in the case of the wave equation, (1)
Lectures - Week 10 Introduction to Ordinary Differential Equations (ODES) First Order Linear ODEs
 Lectures - Week 10 Introuction to Orinary Differential Equations (ODES) First Orer Linear ODEs When stuying ODEs we are consiering functions of one inepenent variable, e.g., f(x), where x is the inepenent
Lectures - Week 10 Introuction to Orinary Differential Equations (ODES) First Orer Linear ODEs When stuying ODEs we are consiering functions of one inepenent variable, e.g., f(x), where x is the inepenent
Switching Time Optimization in Discretized Hybrid Dynamical Systems
 Switching Time Optimization in Discretize Hybri Dynamical Systems Kathrin Flaßkamp, To Murphey, an Sina Ober-Blöbaum Abstract Switching time optimization (STO) arises in systems that have a finite set
Switching Time Optimization in Discretize Hybri Dynamical Systems Kathrin Flaßkamp, To Murphey, an Sina Ober-Blöbaum Abstract Switching time optimization (STO) arises in systems that have a finite set
Math 342 Partial Differential Equations «Viktor Grigoryan
 Math 342 Partial Differential Equations «Viktor Grigoryan 6 Wave equation: solution In this lecture we will solve the wave equation on the entire real line x R. This correspons to a string of infinite
Math 342 Partial Differential Equations «Viktor Grigoryan 6 Wave equation: solution In this lecture we will solve the wave equation on the entire real line x R. This correspons to a string of infinite
The Exact Form and General Integrating Factors
 7 The Exact Form an General Integrating Factors In the previous chapters, we ve seen how separable an linear ifferential equations can be solve using methos for converting them to forms that can be easily
7 The Exact Form an General Integrating Factors In the previous chapters, we ve seen how separable an linear ifferential equations can be solve using methos for converting them to forms that can be easily
Computing Exact Confidence Coefficients of Simultaneous Confidence Intervals for Multinomial Proportions and their Functions
 Working Paper 2013:5 Department of Statistics Computing Exact Confience Coefficients of Simultaneous Confience Intervals for Multinomial Proportions an their Functions Shaobo Jin Working Paper 2013:5
Working Paper 2013:5 Department of Statistics Computing Exact Confience Coefficients of Simultaneous Confience Intervals for Multinomial Proportions an their Functions Shaobo Jin Working Paper 2013:5
Calculus in the AP Physics C Course The Derivative
 Limits an Derivatives Calculus in the AP Physics C Course The Derivative In physics, the ieas of the rate change of a quantity (along with the slope of a tangent line) an the area uner a curve are essential.
Limits an Derivatives Calculus in the AP Physics C Course The Derivative In physics, the ieas of the rate change of a quantity (along with the slope of a tangent line) an the area uner a curve are essential.
Lower Bounds for the Smoothed Number of Pareto optimal Solutions
 Lower Bouns for the Smoothe Number of Pareto optimal Solutions Tobias Brunsch an Heiko Röglin Department of Computer Science, University of Bonn, Germany brunsch@cs.uni-bonn.e, heiko@roeglin.org Abstract.
Lower Bouns for the Smoothe Number of Pareto optimal Solutions Tobias Brunsch an Heiko Röglin Department of Computer Science, University of Bonn, Germany brunsch@cs.uni-bonn.e, heiko@roeglin.org Abstract.
Euler equations for multiple integrals
 Euler equations for multiple integrals January 22, 2013 Contents 1 Reminer of multivariable calculus 2 1.1 Vector ifferentiation......................... 2 1.2 Matrix ifferentiation........................
Euler equations for multiple integrals January 22, 2013 Contents 1 Reminer of multivariable calculus 2 1.1 Vector ifferentiation......................... 2 1.2 Matrix ifferentiation........................
. ISSN (print), (online) International Journal of Nonlinear Science Vol.6(2008) No.3,pp
 . ISSN 1749-3889 (print), 1749-3897 (online) International Journal of Nonlinear Science Vol.6(8) No.3,pp.195-1 A Bouneness Criterion for Fourth Orer Nonlinear Orinary Differential Equations with Delay
. ISSN 1749-3889 (print), 1749-3897 (online) International Journal of Nonlinear Science Vol.6(8) No.3,pp.195-1 A Bouneness Criterion for Fourth Orer Nonlinear Orinary Differential Equations with Delay
Lecture 6: Calculus. In Song Kim. September 7, 2011
 Lecture 6: Calculus In Song Kim September 7, 20 Introuction to Differential Calculus In our previous lecture we came up with several ways to analyze functions. We saw previously that the slope of a linear
Lecture 6: Calculus In Song Kim September 7, 20 Introuction to Differential Calculus In our previous lecture we came up with several ways to analyze functions. We saw previously that the slope of a linear
An M/G/1 Retrial Queue with Priority, Balking and Feedback Customers
 Journal of Convergence Information Technology Volume 5 Number April 1 An M/G/1 Retrial Queue with Priority Balking an Feeback Customers Peishu Chen * 1 Yiuan Zhu 1 * 1 Faculty of Science Jiangsu University
Journal of Convergence Information Technology Volume 5 Number April 1 An M/G/1 Retrial Queue with Priority Balking an Feeback Customers Peishu Chen * 1 Yiuan Zhu 1 * 1 Faculty of Science Jiangsu University
Math Notes on differentials, the Chain Rule, gradients, directional derivative, and normal vectors
 Math 18.02 Notes on ifferentials, the Chain Rule, graients, irectional erivative, an normal vectors Tangent plane an linear approximation We efine the partial erivatives of f( xy, ) as follows: f f( x+
Math 18.02 Notes on ifferentials, the Chain Rule, graients, irectional erivative, an normal vectors Tangent plane an linear approximation We efine the partial erivatives of f( xy, ) as follows: f f( x+
Survey Sampling. 1 Design-based Inference. Kosuke Imai Department of Politics, Princeton University. February 19, 2013
 Survey Sampling Kosuke Imai Department of Politics, Princeton University February 19, 2013 Survey sampling is one of the most commonly use ata collection methos for social scientists. We begin by escribing
Survey Sampling Kosuke Imai Department of Politics, Princeton University February 19, 2013 Survey sampling is one of the most commonly use ata collection methos for social scientists. We begin by escribing
Sliding mode approach to congestion control in connection-oriented communication networks
 JOURNAL OF APPLIED COMPUTER SCIENCE Vol. xx. No xx (200x), pp. xx-xx Sliing moe approach to congestion control in connection-oriente communication networks Anrzej Bartoszewicz, Justyna Żuk Technical University
JOURNAL OF APPLIED COMPUTER SCIENCE Vol. xx. No xx (200x), pp. xx-xx Sliing moe approach to congestion control in connection-oriente communication networks Anrzej Bartoszewicz, Justyna Żuk Technical University
Agmon Kolmogorov Inequalities on l 2 (Z d )
 Journal of Mathematics Research; Vol. 6, No. ; 04 ISSN 96-9795 E-ISSN 96-9809 Publishe by Canaian Center of Science an Eucation Agmon Kolmogorov Inequalities on l (Z ) Arman Sahovic Mathematics Department,
Journal of Mathematics Research; Vol. 6, No. ; 04 ISSN 96-9795 E-ISSN 96-9809 Publishe by Canaian Center of Science an Eucation Agmon Kolmogorov Inequalities on l (Z ) Arman Sahovic Mathematics Department,
Least-Squares Regression on Sparse Spaces
 Least-Squares Regression on Sparse Spaces Yuri Grinberg, Mahi Milani Far, Joelle Pineau School of Computer Science McGill University Montreal, Canaa {ygrinb,mmilan1,jpineau}@cs.mcgill.ca 1 Introuction
Least-Squares Regression on Sparse Spaces Yuri Grinberg, Mahi Milani Far, Joelle Pineau School of Computer Science McGill University Montreal, Canaa {ygrinb,mmilan1,jpineau}@cs.mcgill.ca 1 Introuction
Equilibrium in Queues Under Unknown Service Times and Service Value
 University of Pennsylvania ScholarlyCommons Finance Papers Wharton Faculty Research 1-2014 Equilibrium in Queues Uner Unknown Service Times an Service Value Laurens Debo Senthil K. Veeraraghavan University
University of Pennsylvania ScholarlyCommons Finance Papers Wharton Faculty Research 1-2014 Equilibrium in Queues Uner Unknown Service Times an Service Value Laurens Debo Senthil K. Veeraraghavan University
State-Space Model for a Multi-Machine System
 State-Space Moel for a Multi-Machine System These notes parallel section.4 in the text. We are ealing with classically moele machines (IEEE Type.), constant impeance loas, an a network reuce to its internal
State-Space Moel for a Multi-Machine System These notes parallel section.4 in the text. We are ealing with classically moele machines (IEEE Type.), constant impeance loas, an a network reuce to its internal
Linear First-Order Equations
 5 Linear First-Orer Equations Linear first-orer ifferential equations make up another important class of ifferential equations that commonly arise in applications an are relatively easy to solve (in theory)
5 Linear First-Orer Equations Linear first-orer ifferential equations make up another important class of ifferential equations that commonly arise in applications an are relatively easy to solve (in theory)
Integration Review. May 11, 2013
 Integration Review May 11, 2013 Goals: Review the funamental theorem of calculus. Review u-substitution. Review integration by parts. Do lots of integration eamples. 1 Funamental Theorem of Calculus In
Integration Review May 11, 2013 Goals: Review the funamental theorem of calculus. Review u-substitution. Review integration by parts. Do lots of integration eamples. 1 Funamental Theorem of Calculus In
Power Generation and Distribution via Distributed Coordination Control
 Power Generation an Distribution via Distribute Coorination Control Byeong-Yeon Kim, Kwang-Kyo Oh, an Hyo-Sung Ahn arxiv:407.4870v [math.oc] 8 Jul 204 Abstract This paper presents power coorination, power
Power Generation an Distribution via Distribute Coorination Control Byeong-Yeon Kim, Kwang-Kyo Oh, an Hyo-Sung Ahn arxiv:407.4870v [math.oc] 8 Jul 204 Abstract This paper presents power coorination, power
Delay Limited Capacity of Ad hoc Networks: Asymptotically Optimal Transmission and Relaying Strategy
 Delay Limite Capacity of A hoc Networks: Asymptotically Optimal Transmission an Relaying Strategy Eugene Perevalov Lehigh University Bethlehem, PA 85 Email: eup2@lehigh.eu Rick Blum Lehigh University Bethlehem,
Delay Limite Capacity of A hoc Networks: Asymptotically Optimal Transmission an Relaying Strategy Eugene Perevalov Lehigh University Bethlehem, PA 85 Email: eup2@lehigh.eu Rick Blum Lehigh University Bethlehem,
1 dx. where is a large constant, i.e., 1, (7.6) and Px is of the order of unity. Indeed, if px is given by (7.5), the inequality (7.
 Lectures Nine an Ten The WKB Approximation The WKB metho is a powerful tool to obtain solutions for many physical problems It is generally applicable to problems of wave propagation in which the frequency
Lectures Nine an Ten The WKB Approximation The WKB metho is a powerful tool to obtain solutions for many physical problems It is generally applicable to problems of wave propagation in which the frequency
A Fair Comparison of Pull and Push Strategies in Large Distributed Networks
 1 A Fair Comparison of Pull an Push Strategies in Large Distribute Networks Wouter Minnebo an Benny Van Hout, Member, IEEE Abstract In this paper we compare the performance of the pull an push strategy
1 A Fair Comparison of Pull an Push Strategies in Large Distribute Networks Wouter Minnebo an Benny Van Hout, Member, IEEE Abstract In this paper we compare the performance of the pull an push strategy
IPA Derivatives for Make-to-Stock Production-Inventory Systems With Backorders Under the (R,r) Policy
 IPA Derivatives for Make-to-Stock Prouction-Inventory Systems With Backorers Uner the (Rr) Policy Yihong Fan a Benamin Melame b Yao Zhao c Yorai Wari Abstract This paper aresses Infinitesimal Perturbation
IPA Derivatives for Make-to-Stock Prouction-Inventory Systems With Backorers Uner the (Rr) Policy Yihong Fan a Benamin Melame b Yao Zhao c Yorai Wari Abstract This paper aresses Infinitesimal Perturbation
On the Aloha throughput-fairness tradeoff
 On the Aloha throughput-fairness traeoff 1 Nan Xie, Member, IEEE, an Steven Weber, Senior Member, IEEE Abstract arxiv:1605.01557v1 [cs.it] 5 May 2016 A well-known inner boun of the stability region of
On the Aloha throughput-fairness traeoff 1 Nan Xie, Member, IEEE, an Steven Weber, Senior Member, IEEE Abstract arxiv:1605.01557v1 [cs.it] 5 May 2016 A well-known inner boun of the stability region of
Topic 7: Convergence of Random Variables
 Topic 7: Convergence of Ranom Variables Course 003, 2016 Page 0 The Inference Problem So far, our starting point has been a given probability space (S, F, P). We now look at how to generate information
Topic 7: Convergence of Ranom Variables Course 003, 2016 Page 0 The Inference Problem So far, our starting point has been a given probability space (S, F, P). We now look at how to generate information
Generalized Tractability for Multivariate Problems
 Generalize Tractability for Multivariate Problems Part II: Linear Tensor Prouct Problems, Linear Information, an Unrestricte Tractability Michael Gnewuch Department of Computer Science, University of Kiel,
Generalize Tractability for Multivariate Problems Part II: Linear Tensor Prouct Problems, Linear Information, an Unrestricte Tractability Michael Gnewuch Department of Computer Science, University of Kiel,
The total derivative. Chapter Lagrangian and Eulerian approaches
 Chapter 5 The total erivative 51 Lagrangian an Eulerian approaches The representation of a flui through scalar or vector fiels means that each physical quantity uner consieration is escribe as a function
Chapter 5 The total erivative 51 Lagrangian an Eulerian approaches The representation of a flui through scalar or vector fiels means that each physical quantity uner consieration is escribe as a function
Math 1271 Solutions for Fall 2005 Final Exam
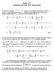 Math 7 Solutions for Fall 5 Final Eam ) Since the equation + y = e y cannot be rearrange algebraically in orer to write y as an eplicit function of, we must instea ifferentiate this relation implicitly
Math 7 Solutions for Fall 5 Final Eam ) Since the equation + y = e y cannot be rearrange algebraically in orer to write y as an eplicit function of, we must instea ifferentiate this relation implicitly
The derivative of a function f(x) is another function, defined in terms of a limiting expression: f(x + δx) f(x)
 Y. D. Chong (2016) MH2801: Complex Methos for the Sciences 1. Derivatives The erivative of a function f(x) is another function, efine in terms of a limiting expression: f (x) f (x) lim x δx 0 f(x + δx)
Y. D. Chong (2016) MH2801: Complex Methos for the Sciences 1. Derivatives The erivative of a function f(x) is another function, efine in terms of a limiting expression: f (x) f (x) lim x δx 0 f(x + δx)
Lagrangian and Hamiltonian Mechanics
 Lagrangian an Hamiltonian Mechanics.G. Simpson, Ph.. epartment of Physical Sciences an Engineering Prince George s Community College ecember 5, 007 Introuction In this course we have been stuying classical
Lagrangian an Hamiltonian Mechanics.G. Simpson, Ph.. epartment of Physical Sciences an Engineering Prince George s Community College ecember 5, 007 Introuction In this course we have been stuying classical
Tractability results for weighted Banach spaces of smooth functions
 Tractability results for weighte Banach spaces of smooth functions Markus Weimar Mathematisches Institut, Universität Jena Ernst-Abbe-Platz 2, 07740 Jena, Germany email: markus.weimar@uni-jena.e March
Tractability results for weighte Banach spaces of smooth functions Markus Weimar Mathematisches Institut, Universität Jena Ernst-Abbe-Platz 2, 07740 Jena, Germany email: markus.weimar@uni-jena.e March
Vectors in two dimensions
 Vectors in two imensions Until now, we have been working in one imension only The main reason for this is to become familiar with the main physical ieas like Newton s secon law, without the aitional complication
Vectors in two imensions Until now, we have been working in one imension only The main reason for this is to become familiar with the main physical ieas like Newton s secon law, without the aitional complication
Perturbation Analysis and Optimization of Stochastic Flow Networks
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. XX, NO. Y, MMM 2004 1 Perturbation Analysis an Optimization of Stochastic Flow Networks Gang Sun, Christos G. Cassanras, Yorai Wari, Christos G. Panayiotou,
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. XX, NO. Y, MMM 2004 1 Perturbation Analysis an Optimization of Stochastic Flow Networks Gang Sun, Christos G. Cassanras, Yorai Wari, Christos G. Panayiotou,
A Note on Exact Solutions to Linear Differential Equations by the Matrix Exponential
 Avances in Applie Mathematics an Mechanics Av. Appl. Math. Mech. Vol. 1 No. 4 pp. 573-580 DOI: 10.4208/aamm.09-m0946 August 2009 A Note on Exact Solutions to Linear Differential Equations by the Matrix
Avances in Applie Mathematics an Mechanics Av. Appl. Math. Mech. Vol. 1 No. 4 pp. 573-580 DOI: 10.4208/aamm.09-m0946 August 2009 A Note on Exact Solutions to Linear Differential Equations by the Matrix
Polynomial Inclusion Functions
 Polynomial Inclusion Functions E. e Weert, E. van Kampen, Q. P. Chu, an J. A. Muler Delft University of Technology, Faculty of Aerospace Engineering, Control an Simulation Division E.eWeert@TUDelft.nl
Polynomial Inclusion Functions E. e Weert, E. van Kampen, Q. P. Chu, an J. A. Muler Delft University of Technology, Faculty of Aerospace Engineering, Control an Simulation Division E.eWeert@TUDelft.nl
Adaptive Gain-Scheduled H Control of Linear Parameter-Varying Systems with Time-Delayed Elements
 Aaptive Gain-Scheule H Control of Linear Parameter-Varying Systems with ime-delaye Elements Yoshihiko Miyasato he Institute of Statistical Mathematics 4-6-7 Minami-Azabu, Minato-ku, okyo 6-8569, Japan
Aaptive Gain-Scheule H Control of Linear Parameter-Varying Systems with ime-delaye Elements Yoshihiko Miyasato he Institute of Statistical Mathematics 4-6-7 Minami-Azabu, Minato-ku, okyo 6-8569, Japan
Sharp Thresholds. Zachary Hamaker. March 15, 2010
 Sharp Threshols Zachary Hamaker March 15, 2010 Abstract The Kolmogorov Zero-One law states that for tail events on infinite-imensional probability spaces, the probability must be either zero or one. Behavior
Sharp Threshols Zachary Hamaker March 15, 2010 Abstract The Kolmogorov Zero-One law states that for tail events on infinite-imensional probability spaces, the probability must be either zero or one. Behavior
Lecture 2 Lagrangian formulation of classical mechanics Mechanics
 Lecture Lagrangian formulation of classical mechanics 70.00 Mechanics Principle of stationary action MATH-GA To specify a motion uniquely in classical mechanics, it suffices to give, at some time t 0,
Lecture Lagrangian formulation of classical mechanics 70.00 Mechanics Principle of stationary action MATH-GA To specify a motion uniquely in classical mechanics, it suffices to give, at some time t 0,
Criteria for Global Stability of Coupled Systems with Application to Robust Output Feedback Design for Active Surge Control
 Criteria for Global Stability of Couple Systems with Application to Robust Output Feeback Design for Active Surge Control Shiriaev, Anton; Johansson, Rolf; Robertsson, Aners; Freiovich, Leoni 9 Link to
Criteria for Global Stability of Couple Systems with Application to Robust Output Feeback Design for Active Surge Control Shiriaev, Anton; Johansson, Rolf; Robertsson, Aners; Freiovich, Leoni 9 Link to
Qubit channels that achieve capacity with two states
 Qubit channels that achieve capacity with two states Dominic W. Berry Department of Physics, The University of Queenslan, Brisbane, Queenslan 4072, Australia Receive 22 December 2004; publishe 22 March
Qubit channels that achieve capacity with two states Dominic W. Berry Department of Physics, The University of Queenslan, Brisbane, Queenslan 4072, Australia Receive 22 December 2004; publishe 22 March
Accelerate Implementation of Forwaring Control Laws using Composition Methos Yves Moreau an Roolphe Sepulchre June 1997 Abstract We use a metho of int
 Katholieke Universiteit Leuven Departement Elektrotechniek ESAT-SISTA/TR 1997-11 Accelerate Implementation of Forwaring Control Laws using Composition Methos 1 Yves Moreau, Roolphe Sepulchre, Joos Vanewalle
Katholieke Universiteit Leuven Departement Elektrotechniek ESAT-SISTA/TR 1997-11 Accelerate Implementation of Forwaring Control Laws using Composition Methos 1 Yves Moreau, Roolphe Sepulchre, Joos Vanewalle
State Dependent Control of Closed Queueing Networks
 Submitte to Stochastic Systems manuscript MS-000-922.65 Authors are encourage to submit new papers to INFORMS journals by means of a style file template, which inclues the journal title. However, use of
Submitte to Stochastic Systems manuscript MS-000-922.65 Authors are encourage to submit new papers to INFORMS journals by means of a style file template, which inclues the journal title. However, use of
Chapter 6: Energy-Momentum Tensors
 49 Chapter 6: Energy-Momentum Tensors This chapter outlines the general theory of energy an momentum conservation in terms of energy-momentum tensors, then applies these ieas to the case of Bohm's moel.
49 Chapter 6: Energy-Momentum Tensors This chapter outlines the general theory of energy an momentum conservation in terms of energy-momentum tensors, then applies these ieas to the case of Bohm's moel.
JUST THE MATHS UNIT NUMBER DIFFERENTIATION 2 (Rates of change) A.J.Hobson
 JUST THE MATHS UNIT NUMBER 10.2 DIFFERENTIATION 2 (Rates of change) by A.J.Hobson 10.2.1 Introuction 10.2.2 Average rates of change 10.2.3 Instantaneous rates of change 10.2.4 Derivatives 10.2.5 Exercises
JUST THE MATHS UNIT NUMBER 10.2 DIFFERENTIATION 2 (Rates of change) by A.J.Hobson 10.2.1 Introuction 10.2.2 Average rates of change 10.2.3 Instantaneous rates of change 10.2.4 Derivatives 10.2.5 Exercises
PDE Notes, Lecture #11
 PDE Notes, Lecture # from Professor Jalal Shatah s Lectures Febuary 9th, 2009 Sobolev Spaces Recall that for u L loc we can efine the weak erivative Du by Du, φ := udφ φ C0 If v L loc such that Du, φ =
PDE Notes, Lecture # from Professor Jalal Shatah s Lectures Febuary 9th, 2009 Sobolev Spaces Recall that for u L loc we can efine the weak erivative Du by Du, φ := udφ φ C0 If v L loc such that Du, φ =
Online Appendix for Trade Policy under Monopolistic Competition with Firm Selection
 Online Appenix for Trae Policy uner Monopolistic Competition with Firm Selection Kyle Bagwell Stanfor University an NBER Seung Hoon Lee Georgia Institute of Technology September 6, 2018 In this Online
Online Appenix for Trae Policy uner Monopolistic Competition with Firm Selection Kyle Bagwell Stanfor University an NBER Seung Hoon Lee Georgia Institute of Technology September 6, 2018 In this Online
ELEC3114 Control Systems 1
 ELEC34 Control Systems Linear Systems - Moelling - Some Issues Session 2, 2007 Introuction Linear systems may be represente in a number of ifferent ways. Figure shows the relationship between various representations.
ELEC34 Control Systems Linear Systems - Moelling - Some Issues Session 2, 2007 Introuction Linear systems may be represente in a number of ifferent ways. Figure shows the relationship between various representations.
Markov Chains in Continuous Time
 Chapter 23 Markov Chains in Continuous Time Previously we looke at Markov chains, where the transitions betweenstatesoccurreatspecifietime- steps. That it, we mae time (a continuous variable) avance in
Chapter 23 Markov Chains in Continuous Time Previously we looke at Markov chains, where the transitions betweenstatesoccurreatspecifietime- steps. That it, we mae time (a continuous variable) avance in
II. First variation of functionals
 II. First variation of functionals The erivative of a function being zero is a necessary conition for the etremum of that function in orinary calculus. Let us now tackle the question of the equivalent
II. First variation of functionals The erivative of a function being zero is a necessary conition for the etremum of that function in orinary calculus. Let us now tackle the question of the equivalent
Implicit Differentiation
 Implicit Differentiation Thus far, the functions we have been concerne with have been efine explicitly. A function is efine explicitly if the output is given irectly in terms of the input. For instance,
Implicit Differentiation Thus far, the functions we have been concerne with have been efine explicitly. A function is efine explicitly if the output is given irectly in terms of the input. For instance,
Introduction to the Vlasov-Poisson system
 Introuction to the Vlasov-Poisson system Simone Calogero 1 The Vlasov equation Consier a particle with mass m > 0. Let x(t) R 3 enote the position of the particle at time t R an v(t) = ẋ(t) = x(t)/t its
Introuction to the Vlasov-Poisson system Simone Calogero 1 The Vlasov equation Consier a particle with mass m > 0. Let x(t) R 3 enote the position of the particle at time t R an v(t) = ẋ(t) = x(t)/t its
arxiv: v1 [physics.flu-dyn] 8 May 2014
![arxiv: v1 [physics.flu-dyn] 8 May 2014 arxiv: v1 [physics.flu-dyn] 8 May 2014](/thumbs/87/97199974.jpg) Energetics of a flui uner the Boussinesq approximation arxiv:1405.1921v1 [physics.flu-yn] 8 May 2014 Kiyoshi Maruyama Department of Earth an Ocean Sciences, National Defense Acaemy, Yokosuka, Kanagawa
Energetics of a flui uner the Boussinesq approximation arxiv:1405.1921v1 [physics.flu-yn] 8 May 2014 Kiyoshi Maruyama Department of Earth an Ocean Sciences, National Defense Acaemy, Yokosuka, Kanagawa
Lecture Introduction. 2 Examples of Measure Concentration. 3 The Johnson-Lindenstrauss Lemma. CS-621 Theory Gems November 28, 2012
 CS-6 Theory Gems November 8, 0 Lecture Lecturer: Alesaner Mąry Scribes: Alhussein Fawzi, Dorina Thanou Introuction Toay, we will briefly iscuss an important technique in probability theory measure concentration
CS-6 Theory Gems November 8, 0 Lecture Lecturer: Alesaner Mąry Scribes: Alhussein Fawzi, Dorina Thanou Introuction Toay, we will briefly iscuss an important technique in probability theory measure concentration
Separation of Variables
 Physics 342 Lecture 1 Separation of Variables Lecture 1 Physics 342 Quantum Mechanics I Monay, January 25th, 2010 There are three basic mathematical tools we nee, an then we can begin working on the physical
Physics 342 Lecture 1 Separation of Variables Lecture 1 Physics 342 Quantum Mechanics I Monay, January 25th, 2010 There are three basic mathematical tools we nee, an then we can begin working on the physical
BEYOND THE CONSTRUCTION OF OPTIMAL SWITCHING SURFACES FOR AUTONOMOUS HYBRID SYSTEMS. Mauro Boccadoro Magnus Egerstedt Paolo Valigi Yorai Wardi
 BEYOND THE CONSTRUCTION OF OPTIMAL SWITCHING SURFACES FOR AUTONOMOUS HYBRID SYSTEMS Mauro Boccaoro Magnus Egerstet Paolo Valigi Yorai Wari {boccaoro,valigi}@iei.unipg.it Dipartimento i Ingegneria Elettronica
BEYOND THE CONSTRUCTION OF OPTIMAL SWITCHING SURFACES FOR AUTONOMOUS HYBRID SYSTEMS Mauro Boccaoro Magnus Egerstet Paolo Valigi Yorai Wari {boccaoro,valigi}@iei.unipg.it Dipartimento i Ingegneria Elettronica
Numerical Key Results for Studying the Performance of TCP Traffic under Class-Based Weighted Fair Queuing System
 Journal of ommunication an omputer 13 (2016) 195-201 oi:10.17265/1548-7709/2016.04.007 D DAVID PUBLISHING Numerical Key Results for Stuying the Performance of TP Traffic uner lass-base Weighte Fair Queuing
Journal of ommunication an omputer 13 (2016) 195-201 oi:10.17265/1548-7709/2016.04.007 D DAVID PUBLISHING Numerical Key Results for Stuying the Performance of TP Traffic uner lass-base Weighte Fair Queuing
Estimation of the Maximum Domination Value in Multi-Dimensional Data Sets
 Proceeings of the 4th East-European Conference on Avances in Databases an Information Systems ADBIS) 200 Estimation of the Maximum Domination Value in Multi-Dimensional Data Sets Eleftherios Tiakas, Apostolos.
Proceeings of the 4th East-European Conference on Avances in Databases an Information Systems ADBIS) 200 Estimation of the Maximum Domination Value in Multi-Dimensional Data Sets Eleftherios Tiakas, Apostolos.
Generalization of the persistent random walk to dimensions greater than 1
 PHYSICAL REVIEW E VOLUME 58, NUMBER 6 DECEMBER 1998 Generalization of the persistent ranom walk to imensions greater than 1 Marián Boguñá, Josep M. Porrà, an Jaume Masoliver Departament e Física Fonamental,
PHYSICAL REVIEW E VOLUME 58, NUMBER 6 DECEMBER 1998 Generalization of the persistent ranom walk to imensions greater than 1 Marián Boguñá, Josep M. Porrà, an Jaume Masoliver Departament e Física Fonamental,
Convergence of Random Walks
 Chapter 16 Convergence of Ranom Walks This lecture examines the convergence of ranom walks to the Wiener process. This is very important both physically an statistically, an illustrates the utility of
Chapter 16 Convergence of Ranom Walks This lecture examines the convergence of ranom walks to the Wiener process. This is very important both physically an statistically, an illustrates the utility of
Table of Common Derivatives By David Abraham
 Prouct an Quotient Rules: Table of Common Derivatives By Davi Abraham [ f ( g( ] = [ f ( ] g( + f ( [ g( ] f ( = g( [ f ( ] g( g( f ( [ g( ] Trigonometric Functions: sin( = cos( cos( = sin( tan( = sec
Prouct an Quotient Rules: Table of Common Derivatives By Davi Abraham [ f ( g( ] = [ f ( ] g( + f ( [ g( ] f ( = g( [ f ( ] g( g( f ( [ g( ] Trigonometric Functions: sin( = cos( cos( = sin( tan( = sec
LATTICE-BASED D-OPTIMUM DESIGN FOR FOURIER REGRESSION
 The Annals of Statistics 1997, Vol. 25, No. 6, 2313 2327 LATTICE-BASED D-OPTIMUM DESIGN FOR FOURIER REGRESSION By Eva Riccomagno, 1 Rainer Schwabe 2 an Henry P. Wynn 1 University of Warwick, Technische
The Annals of Statistics 1997, Vol. 25, No. 6, 2313 2327 LATTICE-BASED D-OPTIMUM DESIGN FOR FOURIER REGRESSION By Eva Riccomagno, 1 Rainer Schwabe 2 an Henry P. Wynn 1 University of Warwick, Technische
Fluid model for a data network with α-fair bandwidth sharing and general document size distributions: two examples of stability
 IMS Lecture Notes Monograph Series??? Vol. 0 (0000) 1 c Institute of Mathematical Statistics, 0000 Flui moel for a ata network with α-fair banwith sharing an general ocument size istributions: two examples
IMS Lecture Notes Monograph Series??? Vol. 0 (0000) 1 c Institute of Mathematical Statistics, 0000 Flui moel for a ata network with α-fair banwith sharing an general ocument size istributions: two examples
How the potentials in different gauges yield the same retarded electric and magnetic fields
 How the potentials in ifferent gauges yiel the same retare electric an magnetic fiels José A. Heras a Departamento e Física, E. S. F. M., Instituto Politécnico Nacional, México D. F. México an Department
How the potentials in ifferent gauges yiel the same retare electric an magnetic fiels José A. Heras a Departamento e Física, E. S. F. M., Instituto Politécnico Nacional, México D. F. México an Department
Assignment 1. g i (x 1,..., x n ) dx i = 0. i=1
 Assignment 1 Golstein 1.4 The equations of motion for the rolling isk are special cases of general linear ifferential equations of constraint of the form g i (x 1,..., x n x i = 0. i=1 A constraint conition
Assignment 1 Golstein 1.4 The equations of motion for the rolling isk are special cases of general linear ifferential equations of constraint of the form g i (x 1,..., x n x i = 0. i=1 A constraint conition
12.11 Laplace s Equation in Cylindrical and
 SEC. 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential 593 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential One of the most important PDEs in physics an engineering
SEC. 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential 593 2. Laplace s Equation in Cylinrical an Spherical Coorinates. Potential One of the most important PDEs in physics an engineering
Calculus of Variations
 16.323 Lecture 5 Calculus of Variations Calculus of Variations Most books cover this material well, but Kirk Chapter 4 oes a particularly nice job. x(t) x* x*+ αδx (1) x*- αδx (1) αδx (1) αδx (1) t f t
16.323 Lecture 5 Calculus of Variations Calculus of Variations Most books cover this material well, but Kirk Chapter 4 oes a particularly nice job. x(t) x* x*+ αδx (1) x*- αδx (1) αδx (1) αδx (1) t f t
Conservation Laws. Chapter Conservation of Energy
 20 Chapter 3 Conservation Laws In orer to check the physical consistency of the above set of equations governing Maxwell-Lorentz electroynamics [(2.10) an (2.12) or (1.65) an (1.68)], we examine the action
20 Chapter 3 Conservation Laws In orer to check the physical consistency of the above set of equations governing Maxwell-Lorentz electroynamics [(2.10) an (2.12) or (1.65) an (1.68)], we examine the action
Calculus of Variations
 Calculus of Variations Lagrangian formalism is the main tool of theoretical classical mechanics. Calculus of Variations is a part of Mathematics which Lagrangian formalism is base on. In this section,
Calculus of Variations Lagrangian formalism is the main tool of theoretical classical mechanics. Calculus of Variations is a part of Mathematics which Lagrangian formalism is base on. In this section,
Learning Automata in Games with Memory with Application to Circuit-Switched Routing
 Learning Automata in Games with Memory with Application to Circuit-Switche Routing Murat Alanyali Abstract A general setting is consiere in which autonomous users interact by means of a finite-state controlle
Learning Automata in Games with Memory with Application to Circuit-Switche Routing Murat Alanyali Abstract A general setting is consiere in which autonomous users interact by means of a finite-state controlle
Approximate reduction of dynamic systems
 Systems & Control Letters 57 2008 538 545 www.elsevier.com/locate/sysconle Approximate reuction of ynamic systems Paulo Tabuaa a,, Aaron D. Ames b, Agung Julius c, George J. Pappas c a Department of Electrical
Systems & Control Letters 57 2008 538 545 www.elsevier.com/locate/sysconle Approximate reuction of ynamic systems Paulo Tabuaa a,, Aaron D. Ames b, Agung Julius c, George J. Pappas c a Department of Electrical
CHAPTER 1 : DIFFERENTIABLE MANIFOLDS. 1.1 The definition of a differentiable manifold
 CHAPTER 1 : DIFFERENTIABLE MANIFOLDS 1.1 The efinition of a ifferentiable manifol Let M be a topological space. This means that we have a family Ω of open sets efine on M. These satisfy (1), M Ω (2) the
CHAPTER 1 : DIFFERENTIABLE MANIFOLDS 1.1 The efinition of a ifferentiable manifol Let M be a topological space. This means that we have a family Ω of open sets efine on M. These satisfy (1), M Ω (2) the
Optimal Cooperative Spectrum Sensing in Cognitive Sensor Networks
 Optimal Cooperative Spectrum Sensing in Cognitive Sensor Networks Hai Ngoc Pham, an Zhang, Paal E. Engelsta,,3, Tor Skeie,, Frank Eliassen, Department of Informatics, University of Oslo, Norway Simula
Optimal Cooperative Spectrum Sensing in Cognitive Sensor Networks Hai Ngoc Pham, an Zhang, Paal E. Engelsta,,3, Tor Skeie,, Frank Eliassen, Department of Informatics, University of Oslo, Norway Simula
arxiv: v4 [math.pr] 27 Jul 2016
![arxiv: v4 [math.pr] 27 Jul 2016 arxiv: v4 [math.pr] 27 Jul 2016](/thumbs/93/113740839.jpg) The Asymptotic Distribution of the Determinant of a Ranom Correlation Matrix arxiv:309768v4 mathpr] 7 Jul 06 AM Hanea a, & GF Nane b a Centre of xcellence for Biosecurity Risk Analysis, University of Melbourne,
The Asymptotic Distribution of the Determinant of a Ranom Correlation Matrix arxiv:309768v4 mathpr] 7 Jul 06 AM Hanea a, & GF Nane b a Centre of xcellence for Biosecurity Risk Analysis, University of Melbourne,
Nonlinear Adaptive Ship Course Tracking Control Based on Backstepping and Nussbaum Gain
 Nonlinear Aaptive Ship Course Tracking Control Base on Backstepping an Nussbaum Gain Jialu Du, Chen Guo Abstract A nonlinear aaptive controller combining aaptive Backstepping algorithm with Nussbaum gain
Nonlinear Aaptive Ship Course Tracking Control Base on Backstepping an Nussbaum Gain Jialu Du, Chen Guo Abstract A nonlinear aaptive controller combining aaptive Backstepping algorithm with Nussbaum gain
Minimum-time constrained velocity planning
 7th Meiterranean Conference on Control & Automation Makeonia Palace, Thessaloniki, Greece June 4-6, 9 Minimum-time constraine velocity planning Gabriele Lini, Luca Consolini, Aurelio Piazzi Università
7th Meiterranean Conference on Control & Automation Makeonia Palace, Thessaloniki, Greece June 4-6, 9 Minimum-time constraine velocity planning Gabriele Lini, Luca Consolini, Aurelio Piazzi Università
Dissipative numerical methods for the Hunter-Saxton equation
 Dissipative numerical methos for the Hunter-Saton equation Yan Xu an Chi-Wang Shu Abstract In this paper, we present further evelopment of the local iscontinuous Galerkin (LDG) metho esigne in [] an a
Dissipative numerical methos for the Hunter-Saton equation Yan Xu an Chi-Wang Shu Abstract In this paper, we present further evelopment of the local iscontinuous Galerkin (LDG) metho esigne in [] an a
Monotonicity for excited random walk in high dimensions
 Monotonicity for excite ranom walk in high imensions Remco van er Hofsta Mark Holmes March, 2009 Abstract We prove that the rift θ, β) for excite ranom walk in imension is monotone in the excitement parameter
Monotonicity for excite ranom walk in high imensions Remco van er Hofsta Mark Holmes March, 2009 Abstract We prove that the rift θ, β) for excite ranom walk in imension is monotone in the excitement parameter
An Analytical Expression of the Probability of Error for Relaying with Decode-and-forward
 An Analytical Expression of the Probability of Error for Relaying with Decoe-an-forwar Alexanre Graell i Amat an Ingmar Lan Department of Electronics, Institut TELECOM-TELECOM Bretagne, Brest, France Email:
An Analytical Expression of the Probability of Error for Relaying with Decoe-an-forwar Alexanre Graell i Amat an Ingmar Lan Department of Electronics, Institut TELECOM-TELECOM Bretagne, Brest, France Email:
arxiv: v1 [cs.it] 21 Aug 2017
![arxiv: v1 [cs.it] 21 Aug 2017 arxiv: v1 [cs.it] 21 Aug 2017](/thumbs/96/127713176.jpg) Performance Gains of Optimal Antenna Deployment for Massive MIMO ystems Erem Koyuncu Department of Electrical an Computer Engineering, University of Illinois at Chicago arxiv:708.06400v [cs.it] 2 Aug 207
Performance Gains of Optimal Antenna Deployment for Massive MIMO ystems Erem Koyuncu Department of Electrical an Computer Engineering, University of Illinois at Chicago arxiv:708.06400v [cs.it] 2 Aug 207
The Principle of Least Action
 Chapter 7. The Principle of Least Action 7.1 Force Methos vs. Energy Methos We have so far stuie two istinct ways of analyzing physics problems: force methos, basically consisting of the application of
Chapter 7. The Principle of Least Action 7.1 Force Methos vs. Energy Methos We have so far stuie two istinct ways of analyzing physics problems: force methos, basically consisting of the application of
Robustness and Perturbations of Minimal Bases
 Robustness an Perturbations of Minimal Bases Paul Van Dooren an Froilán M Dopico December 9, 2016 Abstract Polynomial minimal bases of rational vector subspaces are a classical concept that plays an important
Robustness an Perturbations of Minimal Bases Paul Van Dooren an Froilán M Dopico December 9, 2016 Abstract Polynomial minimal bases of rational vector subspaces are a classical concept that plays an important
A new proof of the sharpness of the phase transition for Bernoulli percolation on Z d
 A new proof of the sharpness of the phase transition for Bernoulli percolation on Z Hugo Duminil-Copin an Vincent Tassion October 8, 205 Abstract We provie a new proof of the sharpness of the phase transition
A new proof of the sharpness of the phase transition for Bernoulli percolation on Z Hugo Duminil-Copin an Vincent Tassion October 8, 205 Abstract We provie a new proof of the sharpness of the phase transition
The canonical controllers and regular interconnection
 Systems & Control Letters ( www.elsevier.com/locate/sysconle The canonical controllers an regular interconnection A.A. Julius a,, J.C. Willems b, M.N. Belur c, H.L. Trentelman a Department of Applie Mathematics,
Systems & Control Letters ( www.elsevier.com/locate/sysconle The canonical controllers an regular interconnection A.A. Julius a,, J.C. Willems b, M.N. Belur c, H.L. Trentelman a Department of Applie Mathematics,
APPROXIMATE SOLUTION FOR TRANSIENT HEAT TRANSFER IN STATIC TURBULENT HE II. B. Baudouy. CEA/Saclay, DSM/DAPNIA/STCM Gif-sur-Yvette Cedex, France
 APPROXIMAE SOLUION FOR RANSIEN HEA RANSFER IN SAIC URBULEN HE II B. Bauouy CEA/Saclay, DSM/DAPNIA/SCM 91191 Gif-sur-Yvette Ceex, France ABSRAC Analytical solution in one imension of the heat iffusion equation
APPROXIMAE SOLUION FOR RANSIEN HEA RANSFER IN SAIC URBULEN HE II B. Bauouy CEA/Saclay, DSM/DAPNIA/SCM 91191 Gif-sur-Yvette Ceex, France ABSRAC Analytical solution in one imension of the heat iffusion equation
Exponential Tracking Control of Nonlinear Systems with Actuator Nonlinearity
 Preprints of the 9th Worl Congress The International Feeration of Automatic Control Cape Town, South Africa. August -9, Exponential Tracking Control of Nonlinear Systems with Actuator Nonlinearity Zhengqiang
Preprints of the 9th Worl Congress The International Feeration of Automatic Control Cape Town, South Africa. August -9, Exponential Tracking Control of Nonlinear Systems with Actuator Nonlinearity Zhengqiang
On the number of isolated eigenvalues of a pair of particles in a quantum wire
 On the number of isolate eigenvalues of a pair of particles in a quantum wire arxiv:1812.11804v1 [math-ph] 31 Dec 2018 Joachim Kerner 1 Department of Mathematics an Computer Science FernUniversität in
On the number of isolate eigenvalues of a pair of particles in a quantum wire arxiv:1812.11804v1 [math-ph] 31 Dec 2018 Joachim Kerner 1 Department of Mathematics an Computer Science FernUniversität in
Necessary and Sufficient Conditions for Sketched Subspace Clustering
 Necessary an Sufficient Conitions for Sketche Subspace Clustering Daniel Pimentel-Alarcón, Laura Balzano 2, Robert Nowak University of Wisconsin-Maison, 2 University of Michigan-Ann Arbor Abstract This
Necessary an Sufficient Conitions for Sketche Subspace Clustering Daniel Pimentel-Alarcón, Laura Balzano 2, Robert Nowak University of Wisconsin-Maison, 2 University of Michigan-Ann Arbor Abstract This
Quantum Mechanics in Three Dimensions
 Physics 342 Lecture 20 Quantum Mechanics in Three Dimensions Lecture 20 Physics 342 Quantum Mechanics I Monay, March 24th, 2008 We begin our spherical solutions with the simplest possible case zero potential.
Physics 342 Lecture 20 Quantum Mechanics in Three Dimensions Lecture 20 Physics 342 Quantum Mechanics I Monay, March 24th, 2008 We begin our spherical solutions with the simplest possible case zero potential.
05 The Continuum Limit and the Wave Equation
 Utah State University DigitalCommons@USU Founations of Wave Phenomena Physics, Department of 1-1-2004 05 The Continuum Limit an the Wave Equation Charles G. Torre Department of Physics, Utah State University,
Utah State University DigitalCommons@USU Founations of Wave Phenomena Physics, Department of 1-1-2004 05 The Continuum Limit an the Wave Equation Charles G. Torre Department of Physics, Utah State University,
