Randomized Algorithms I. Spring 2013, period III Jyrki Kivinen
|
|
|
- Susan Woods
- 5 years ago
- Views:
Transcription
1 Randomized Algorithms I Spring 2013, period III Jyrki Kivinen 1
2 Position of the course in the studies 4 credits advanced course (syventävät opinnot) in algorithms and machine learning prerequisites: basic understanding of probabilities and design and analysis of algorithms covers application of probabilities in designing and analysing algorithms continues in Randomized algorithms II which can also be taken separately applications of probability theory figure prominently also on a number of courses about machine learning theory of probability is the topic for many courses in mathematics this course is mainly theoretical from a computer science point of view, fairly application-oriented from maths point of view 2
3 Passing the course, grading Maximum score 60 points: course exam 48 points homework 12 points Minimum passing score is about 30 points, requirement for best grade about 50 points. Homework sessions begin on the second week of lectures. Solutions to homework problems are turned in in writing before the session. Details and deadlines will be announced on the course web page. Each problem is graded from 0 to 3: 1 a reasonable attempt 2 work in the right direction, largely successful 3 seems to be more or less correct. The homework points will be scaled to course points as follows: 0 % of the maximum gives 0 points 80 % or more of the maximum gives 12 points linear interpolation in between. 3
4 Material The course is based on the textbook M. Mitzenmacher, E. Upfal: Probability and Computing to which the students are expected to have access. References to the textbook in these notes are in style [M&U Thm 3.2]. The lecture notes will appear on the course home page but are not intended to cover the material in full. Also the homework will be based on problems from the textbook. 4
5 Why randomization? Randomness is an important tool in modeling natural and other fenomena. In design and analysis of algorithms, sources of randomness include randomized algorithms: the computations even on the same input may vary depending on internal randomization of the algorithm ( coin tosses ) the algorithm may act in a random environment (average case analysis, data communications,... ) Theory of probability is a powerful general tool for these situations. 5
6 Randomizations may allow us to find an algorithm that compared to a deterministic one is faster or more memory efficient or easier to implement. Basic techniques and situations include random sampling, Monte Carlo methods randomized search, simulated annealing fingerprinting technique. In some situation randomization is compulsory to get any acceptable solution: hiding information from an adversary (cryptography, games) distributed systems: load balancing, leader election etc. Randomization may make the algorithm more robust against unwanted situations. Example: randomized quicksort avoids having any particular worst-case input. 6
7 Typical questions Usually a randomized algorithm has some non-zero probability of giving an incorrect result. if the result is yes/no: what s the probability of error? if the result is a numerical value: what s the probability of a large error? Some randomized algorithms (sometimes called Las Vegas algorithms) always give the correct result, but the run time is random. what s the expected run time? what s the probability of the run time exceeding some boundary? 7
8 Contents of the course Main topics for Randomized algorithms I include 1. theory of probability (quick refresher) 2. discrete random variables (quick refresher) 3. moments of a random variable 4. Chernoff bounds 5. balls and bins 6. the probabilistic method Randomized algorithms II continues with 1. Markov chains 2. continuous random variables, Poisson processes 3. Monte Carlo methods 4. (martingales, if there s time). 8
9 1. Probability Let Ω be any set and F P(Ω) a collection of subsets of Ω. (We use P(Ω) to denote the power set of Ω.) A function Pr : F R is a probability function (or probability measure) [M&U Def. 1.2] if 1. Pr(E) 0 for all E F, 2. Pr(Ω) = 1 and 3. if E 1, E 2, E 3,... is a sequence of pairwise disjoint sets (meaning E i E j = when i j) such that E i F for all i, we have (countable additivity). Pr ( i=1 E i ) = Pr(E i ) i=1 9
10 For the conditions we just set for a probability function Pr to be interesting, its domain F must have some closure properties. A collection of subsets F P(Ω) is a σ algebra if 1. Ω F 2. A F implies A F, where A = Ω A 3. if A 1, A 2, A 3,... is a sequence such that A i F for all i { 1, 2, 3,... }, we have A i F. Remark No assumption is made about the union i I A i of a family { A i i I } if the index set I is not countable. i=1 10
11 We now define a probability space as a triple (Ω, F, Pr) where 1. the sample space Ω is an arbitrary set 2. F P(Ω) is a σ algebra over Ω 3. Pr : F R is a probability function. Subsets E Ω of the sample space are called events. In particular, the sets E F are allowable events. For any property φ of the elements of the sample space, we write simply Pr(φ(x)) = Pr({ x Ω φ(x) }). For example, Pr(g(x) = 3) denotes the probability Pr({ x Ω g(x) = 3 }). 11
12 Example 1.1: For a finite sample space with Ω = n N, we define the symmetrical (or uniform) probability for Ω as (Ω, P(Ω), Pr) where Pr(E) = E /n kaikilla E Ω. More generally, if a probability space is of the form (Ω, P(Ω), Pr) for a finite or countably infinite Ω, we say it s discrete. A discrete probability space can be specified by just giving all the probabilities Pr({ x }) of the individual elements x Ω. On this course we ll mainly deal with discrete spaces. Therefore we often don t mention assumptions of the type if E F (which often would anyway be clear from the context). Occasionally even in a finite or countable Ω it s useful to consider other σ algebras than just P(Ω). 12
13 Example 1.2: Let Ω = R, and let F be the smallest σ algebra that includes all the closed intervals [a, b], a, b R. The elements of this σ algebra are called Borel sets. We define the uniform probability over the interval [0, 1] by setting for all 0 a b 1 the probability of the interval [a, b] to be the same as its length: Pr([a, b]) = b a. The probabilities of other Borel sets follow by the properties of a probability function. Remark We have Pr({ x }) = 0 for any individual x R, so the probability of any countable set is zero, too. However, this implies nothing about uncountable sets. It might seem nice to pick F = P(R), in other words make any set of real numbers an allowable event. However, it turns out to be impossible to define Pr(A) for all A R so that all the requirements of a probability function would be satisfied. Luckily, in practice, we have little need to go beyond Borel sets. 13
14 Probability of the union Straight from the definition, for any two allowable events we have Pr(E F ) = Pr(E) + Pr(F ) Pr(E F ). For any countable I and a sequence of allowable events (E i ) i I we have ( ) Pr E i Pr(E i ) i I i I which is called the union bound [M&U Lemma 1.2]. This is a very useful but sometimes quite loose inequality. When I = n N, the exact probability of the union can be obtained as ( ) n Pr E i = ( 1) k+1 Pr E j j J i I k=1 J I, J =k which is known as the inclusion-exclusion principle [M&U Lemma 1.3]. 14
15 By taking the sum only up to some limit k < n we get alternating upper and lower bounds: For odd l we have ( ) Pr E i i I For even l we have ( ) Pr E i i I (Bonferroni inequalities). l ( 1) k+1 k=1 l ( 1) k+1 k=1 J I, J =k J I, J =k Pr E j. j J Pr E j j J 15
16 Independence Two events E and F are independent [M&U Def. 1.3] if Pr(E F ) = Pr(E) Pr(F ). More generally, events E 1,..., E k are mutually independent (or just independent) if for all I { 1,..., k } we have ( ) Pr E i = Pr(E i ). i I i I Events E 1,..., E k are pairwise independent if for all i j the events E i and E j are independent. Remark Pairwise independence does not in general imply mutual independence for more than two events. If Pr(F ) > 0, we define the conditional probability of E given F as Pr(E F ) = Pr(E F ). Pr(F ) Thus, if Pr(F ) > 0, then E and F are independent iff Pr(E F ) = Pr(E). 16
17 Given two probability spaces (Ω 1, F 1, Pr 1 ) and (Ω 2, F 2, Pr 2 ), we define their product space as (Ω 1, F 1, Pr 1 ) (Ω 2, F 2, Pr 2 ) = (Ω 1 Ω 2, F 1 F 2, Pr 1 Pr 2 ) where F 1 F 2 is the smallest σ algebra that includes all the sets E 1 E 2 where E i F i, and (Pr 1 Pr 2 )(E 1 E 2 ) = Pr 1 (E 1 ) Pr 2 (E 2 ) for E i F i. This means that if we draw a pair (x, y) from Pr 1 Pr 2, then the events x E 1 and y E 2 are independent for any E 1 F 1 and E 2 F 2. An important special case is the n-fold product of a space with itself (Ω, F, Pr) n = (Ω n, F n, Pr n ). This represents n independent repetitions of the random experiment represented by the original space. In this case we often (inaccurately) simply use Pr to denote Pr n. 17
18 Example 1.3: Suppose we have two procedures F and G that compute integer-valued functions f and g. We only know that the functions f and g are polynomials of degree at most d. We wish to find out whether f = g by just making calls to F and G (which we assume are black boxes ). If f = g, then f(x) g(x) = 0 for all x. If f g, then f g is a polynomial of degree at most d which is not identically zero. Hence f(x) g(x) holds for at most d values x N. In particular, the set { 1,..., rd } for any r N includes at least (r 1)d elements x for which f(x) g(x) 0. 18
19 We take the following basic algorithm as a starting point: 1. Pick a random x { 1,..., rd }. 2. If f(x) g(x) 0, print not equal. 3. Otherwise print equal. Based on the previous observations, if f = g, the algorithm always prints equal if f g, the algorithm has at least probability (r 1)d/(rd) = 1 1/r of printing not equal. We say the algorithm has one-sided probability of error at most 1/r. 19
20 Let s now make k independent trials as follows: 1. Pick mutually independent x 1,..., x k uniformly from { 1,..., rd }. 2. If f(x i ) g(x i ) 0 for at least one i, print not equal. 3. Otherwise print equal. If f = g we again always get equal. If f g and we got equal, we had at k independent trials in a row an event with probability at most 1/r. This can happen with probability at most (1/r) k. Hence, by increasing the number of iterations we can make the error probability approach zero at an exponential rate. 20
21 Law of Total Probability [M&U Thm. 1.6] Let { E i i I } be a finite or countably infinite set of disjoint events such that i I E i = Ω. Directly from definitions we get Pr(B) = i I Pr(B E i ) = i I Pr(B E i ) Pr(E i ). One application for this is the principle of deferred decisions. Suppose we want to prove a statement of the form Pr(x B) ɛ. We split x into two suitable components x = (x 1, x 2 ). We think of x 1 as being fixed first and x 2 only later. We then prove that whatever the choice of x 1, the probability of choosing x 2 such that (x 1, x 2 ) B holds is at most ɛ. The desired result follows by applying the law of total probability with I = range of x 1 E i = { (x 1, x 2 ) x 1 = i }. 21
22 Example 1.4 [M&U Thm. 1.4]: We are given three n n matrices A, B and C. We want to check whether AB = C holds but don t want to calculate the whole matrix product AB. We proceed as in the previous example: 1. Pick a random r { 0, 1 } n. 2. If ABr Cr, print not equal. 3. Otherwise print equal. Let D = AB C. We claim that if D is not the zero matrix, then Dr 0 holds with probability at least 1/2. 22
23 Write D = (d ij ). We assume that D 0; let d pq 0. If Dr = 0, we have in particular from which we can solve n d pj r j = 0, j=1 r q = d 1 pq d pj r j. Now imagine that we first picked r = (r 1,..., r q 1, r q+1,..., r n ), and then consider choices for the missing component r q. Because the choice of r fixes some value v for the expression d 1 pq j q d pj r j, the probability of r q = v is at most 1/2 (as r q { 0, 1 }). j q By the principle of deferred decisions, we see that Pr(Dr = 0)
24 Bayes Law [M&U Thm. 1.7] Again, directly from the defitions we get Pr(E j B) = Pr(E j B) Pr(B) where again E j are assumed disjoint. = Pr(B E j) Pr(E j ) i Pr(B E i) Pr(E i ) A usual interpretation for the formula is based on updating our beliefs when new data arrive: The events E j are mutually exclusive hypotheses (with the rough interpretation E j = theory number j is true for some mutually contradictory competing theories). The even B describes some observation, measurement data etc. Pr(E j ) is the prior probability that indicates our degree of belief in hypothesis E j before we have seen any data. Pr(B E j ) measures how well the hypothesis E j explains data B. Pr(E j B) is the posterior probability that indicates our degree of belief in hypothesis E j after data B were observed. 24
25 Example 1.5: We are given three coins. Two of them are balanced, while one of them will give heads with probability 2/3; we don t know which one. We assing the coins arbitrary numbers 1, 2 and 3 and toss them once. Suppose we get the results (1: heads, 2: heads, 3: tails). What is the probability that coin 1 is the unbalanced one? The Bayes Law gives the answer 2/5. Remark The denominator in Bayes Law is the same for all E j. If we only wish to compare the posterior probabilities, we can ignore the constant factor Pr(B) and write Pr(E j B) Pr(B E j ) Pr(E j ). However, in many machine learning applications computing Pr(B) cannot be avoided and is actually a crucial problem for efficient algorithms. 25
26 Randomised minimum cut [M&U Section 1.4] Let G = (V, E) be a connected undirected multigraph. (Unlike in a normal graph, a multigraph may have multiple edges between two vertices.) A set of edges C E is a cut of the (multi)graph if (V, E C) is not connected. Minimum cut (or min cut) is the cut that contains the least number of edges. We use an operation called edge contraction. Contracting an edge (u, v) replaces the vertices u and v with a new vertex. The edge (u, v) (all the copies, if there were multiple) is removed. The other edges are retained, and the new vertex replaces u and v when they occur as an endpoint of an egde. If now C was a cut in the original graph and (u, v) C, then C is a cut also after the contraction. On the other hand, contrations do not introduce any new cuts. 26
27 Consider the following algorithm: 1. Pick a random edge (u, v) E so that each edge has the same probability of being picked. 2. Contract (u, v). 3. If at least three vertices remain, return to Step Otherwise print the remaining edges. (We assume that the original edges retain their identity even if their end points are contracted.) Let C be a min cut. We know that if no edge in C is picked for contraction, then the algorithm gives the right output. What s the probability of this desired outcome? 27
28 Let E i denote the event that in iteration i the edge picked for contraction is not in C. Let F i = i j=1 E i. We need a lower bound for the probability Pr(F n 2 ) where n = V. Let k = C be the size of the min cut. Then in particular each vertex has degree at least k, so the graph has at least kn/2 edges. Therefore, Pr(E 1 ) = E C E 1 k nk/2 = 1 2 n. More generally, if the first i 1 iterations have avoided picking from C, then C is still a min cut. However, the number of vertices has beed reduced, so we get 2 Pr(E i F i 1 ) 1 n i
29 We get Pr(F n 2 ) = Pr(E n 2 F n 3 ) = Pr(E n 2 F n 3 ) Pr(F n 3 ) =... = Pr(E n 2 F n 3 ) Pr(E n 3 F n 4 )... Pr(E 2 F 1 ) Pr(F 1 ) n 2 ( ) 2 1 n i + 1 i=1 ( ) ( ) ( ) ( ) ( ) n 2 n =... n n = 2 n(n 1). 29
30 The algorithm always outputs a cut, and with probability at least 2/(n(n 1)) a min cut. We repeat the algorithm m times and choose the smallest of the m cuts. The probability that we fail to get a min cut is at most ( ) m ( 2 1 exp 2m ) n(n 1) n(n 1) where we used the bound 1 x e x. For example choosing m = n(n 1) ln n makes the error probability at most 1/n 2. 30
31 2. Random variables Consider a probability space (Ω, F, Pr). A real-valued function X : Ω R is a random variable if { s Ω X(s) a } F for all a R. A random variable is discrete if its range is finite or countably infinite. Later we ll also consider continuous random variables, but for now we assume our random variables to be discrete. Usually the probability Pr({ s Ω X(s) = a }) is denoted simply by Pr(X = a), and so on. The distribution of the random variable is defined by giving the values Pr(X = a) for all a R. The distribution contains all the information we usually want to know. 31
32 A sequence (X 1,..., X k ) of random variables is mutually independent, if for all I { 1,..., k } and for all x 1,..., x k R we have Pr( i I (X i = x i )) = i I Pr(X i = x i ). Let V be the range of a random variable X. If the sum x V converges, we define the expectation of X as x Pr(X = x) E[X] = x V x Pr(X = x). Otherwise the expectation does not exist, which is often denoted by E[X] =. 32
33 The expectation is linear [M&U Thm. 2.1]: for all a, b R and random variables X, Y we have E[aX + by ] = ae[x] + be[y ]. Linearity does not automatically extend to infinite sums. Whether the equality [ ] E X i = E [X i ] i=1 holds is non-trivial. One sufficient condition is that all the expectations E[ X i ] are defined and i=1 E[ X i ] converges. i=1 If additionally X and Y are independent, we have E[XY ] = E[X]E[Y ]. 33
34 Jensen s Inequality [M&U luku 2.1.2] From definitions we can easily see E[X 2 ] (E[X]) 2. (In general this is a strict inequality as X is not independent of itself.) This is a special case of Jensen s inequality. A function f : [a, b] R is convex if f(λx 1 + (1 λ)x 2 ) λf(x 1 ) + (1 λ)f(x 2 ) for all a x 1, x 2 b and 0 λ 1. A sufficient condition for convexity is that f is twice differentiable and f (x) is non-negative. Theorem 2.1 [M&U Jensen]: If f is convex then for all random variables X. E[f(X)] f(e[x]) The special case at the top of the page is obtained by f(x) = x 2. 34
35 Jensen in a picture f(x 2 ) Ef(X) f(x 1 ) f(ex) Recall that f is convex if for all x 1 and x 2 and 0 α 1 we have f(αx 1 + (1 α)x 2 ) αf(x 1 ) + (1 α)f(x 2 ). A sufficient condition is that f (x) 0 for all x. x 1 EX x 2 35
36 Binomial distribution [M&U Section 2.2] A random variable Y has Bernoulli distribution with parameter p if Then clearly E[Y ] = p. Pr(Y = 1) = p and Pr(Y = 0) = 1 p. A random variable X has binomial distribution with parameters n and p if X is the sum of n independent random variables each of which has Bernoulli distribution with parameter p. We denote this by X Bin(n, p). By linearity of expectation we have E[X] = np. The distribution can be written as ( n ) Pr(X = j) = p j (1 p) n j, j = 0,..., n. j 36
37 Conditional expectation [M&U Section 2.3] When Y and Z are random variables, the range of Y is V, and z R, we write. E[Y Z = z] = y V y Pr(Y = y Z = z). Example 2.2: Let X 1 and X 2 be the results of two independent throws of a six-sided die, and X = X 1 + X 2. Then E[X X 1 = 3] = and E[X 1 X = 4] = = 2. For all X and Y we have E[X] = y V E[X Y = y] Pr(Y = y) assuming the expectations are defined. 37
38 The conditional expectation E[Y Z] is a random variable defined as follows: Let Y and Z be random variables over sample space Ω (that is, functions Ω R). Now E[Y Z]: Ω R is the random variable for which for all ω Ω. E[Y Z](ω) = E[Y Z = Z(ω)] Example 2.3: Let again X = X 1 + X 2 where X 1 and X 2 are independent die rolls. Now E[X X 1 ] = X Conditional expectation follows the basic rules of normal expectations: E[X 1 + X 2 Z] = E[X 1 Z] + E[X 2 Z] etc. Additionally, we have E[Y ] = E[E[Y Z]]. 38
39 Example 2.4: Branching processes [M&U pp ]. Consider a situations where a process executes a certain procedure. This can in turn create more similar processes. Let s assume that the number of new processes a process creates during its life time has distribution Bin(n, p). If we start with one process, how many do we get in expectation? Let Y i be the number of processes in generation i. Thus, Y 0 = 1 and Y 1 Bin(n, p). Fix now some i and denote by Z k the number of children of process number k in generation i. Therefore Z k Bin(n, p). 39
40 Consider the conditional expectations: E[Y i Y i 1 = y i 1 ] = E = E [ yi 1 k=1 [ yi 1 Z k Y i 1 = y i 1 ] ] Z k k=1 = y i 1 np since Z k and Y i 1 are independent. Therefore E[Y i Y i 1 ] = npy i 1, so E[Y i ] = E[E[Y i Y i 1 ]] = E[npY i 1 ] = npe[y i 1 ]. As Y 0 = 1, induction yields E[Y i ] = (np) i. The expected total number of processes is E Y i = i 0 i 0(np) i which is finite if and only if np < 1. 40
41 Geometric distribution [M&U Section 2.4] A random variable X has a geometric distribution with parameter p, denoted by X Geom(p), if Pr(X = n) = (1 p) n 1 p, n = 1, 2,.... That is, X is the number of trials needed to get the first success in a sequence of independent trials each with probability p of success. The geometric distribution is memoryless: Pr(X = n + k X > k) = Pr(X = n). The expectation of a geometric random variable is We show this in two different ways. E[X] = 1 p. 41
42 Method 1: Use the equation E[X] = Pr(X i), that holds for any X that gets only non-negative integer values. For X Geom(p) we get Pr(X i) = (1 p) n 1 p = (1 p) i 1. n=i i=1 Therefore E[X] = (1 p) i 1 = 1 p. i=1 42
43 Method 2: We use the memoryless property. Let X = min { i Y i = 1 }, where Y i, i = 1, 2,... are independent Bernoulli(p) random variables. By a well-known basic property, E[X] = E[X Y 1 = 0] Pr(Y 1 = 0) + E[X Y 1 = 1] Pr(Y 1 = 1). Now Pr(Y 1 = 1) = p, and X = 1 whenever Y 1 = 1. On the other hand, Y 1 = 0 means the same as X > 1. By the memoryless property, which by writing Z = X + 1 becomes Pr(X = n + 1 X > 1) = Pr(X = n) Pr(X = m X > 1) = Pr(X = m 1) = Pr(Z = m), m 2. Therefore E[X X > 1] = E[Z] = E[X] + 1. We have E[X] = (1 p)(e[x] + 1) + p, from which we can solve E[X] = 1/p. 43
44 Example 2.5: Coupon collector s problem [M&U Section 2.4.1] A cereal box always contains one coupon. There are n different coupons. How many boxes of cereals do we need to buy to collect the whole set? Let X be the random variable denoting the number of boxes needed for a full set. Let X i be the number of boxes we bought while we already had exactly i 1 different coupons. Therefore n X = X i. When i 1 coupons have been found, the probability that the next box contains a new one is p i = (n i + 1)/n. Therefore, X i Geom(p i ). i=1 44
45 We get E[X] = = = = n n E[X i ] i=1 n i=1 n i=1 1 p i n n i + 1 n 1 j=1 j = nh(n), where H(n) = n i=1 (1/i). Since it is known [M&U Lemma 2.10] that we get ln n H(n) ln n + 1, E[X] = n ln n + Θ(n). 45
46 Example 2.6: Quicksort [M&U Section 2.5] Consider a randomized version of the algorithm: Quicksort(S[1..n]) If n 1, then return S. Pick a random i { 1,..., n }. Let x = S[i]. Partition S into two sublists: L contains elements less than x H contains elements greater than x. Return [Quicksort(L), x, Quicksort(H)]. The element x is called the pivot. Worst case: The pivot is always the smallest or largest element of the list. We need n(n 1)/2 = Θ(n 2 ) comparisons. 46
47 Average case: Let X be the number of comparisons made by Quicksort. Let the elements of S in ascending order be y 1,..., y n. Write X ij = 1 if during the procedure the elements y i and y j are compared, otherwise X ij = 0. Since no pair of elements is compared twice, we have X = n 1 n i=1 j=i+1 Fix some i < j. By studying the algorithm we can see that X ij = 1 holds if and only if either y i or y j is the first pivot picked from the set Y ij = { y i, y i+1,..., y j 1, y j }. Since all pivots are equally likely, we get E[X ij ] = Pr(X ij = 1) = X ij. 2 j i
48 We can now calculate E[X] = = = = n 1 n i=1 j=i+1 n 1 i=1 n k=2 n i+1 k=2 n+1 k i=1 2 j i k 2 k n (n + 1 k) 2 k k=2 = (n + 1) n k=2 2 k 2(n 1) = (2n + 2)H(n) 4n. Therefore, the expected number of comparisons is E[X] = 2n ln n + Θ(n). 48
49 For comparison, consider a simplified deterministic Quicksort where the pivot is always the first element of the list: x = S[1]. If now the input is originally in random order, with all permutations equally likely, the expected number of comparisons is again 2n ln n + Θ(n). This can be seen with a similar argument as above. Now y i and y j will be compared if either one of them is in the input before other elements of Y ij. Remark In this second version the expectations is over inputs, not over any randomness in the algorithm (since there is none). Whether the underlying assumption about the distribution of the inputs is correct is often debatable. Of course in theory we could make sure by randomly permuting the input before sorting. 49
50 3. Moments and deviations The expectation by itself does not give a very good picture of the distribution of a random varible. The next step is typically to calculate the variance. Variance and other quantities describing the width of the distribution are also useful for proving tail bounds (upper bounds for the probability of getting very large or very small values). Often in computer science (and also in statistics) these may be topics of primary interest. 50
51 The first technique for estimating tails is based on Markov s Inequality [M&U Thm. 3.1]: if X is a non-negative random variable, then Proof: Pr(X a) E[X] a. E[X] = x x Pr(X = x) = x<a x Pr(X = x) + x a x Pr(X = x) 0 + a x a Pr(X = x) where summations are over the range of X. 51
52 Example 3.1: We toss a symmetrical coin n times. We want an upper bound for the probability of getting at least 3n/4 heads. If X is the number of heads, then X 0 and E[X] = n/2. Therefore, Pr(X 3n/4) n/2 3n/4 = 2 3. This is a very crude estimate that did not even try to take into account any information about the shape of the distribution. Indeed, because of symmetry it s clear that the probability in question cannot be larger than 1/2. 52
53 Moments and variance [M&U Section 3.2] The kth moment of a random variable X is E[X k ]. The variance of X is and standard deviation The covariance of X and Y is Var[X] = E[(X E[X]) 2 ] σ[x] = Var[X]. Cov(X, Y ) = E[(X E[X])(Y E[Y ])]. From definitions and the linearity of expectation we get Var[X] = E[X 2 ] (E[X]) 2 Var[X + Y ] = Var[X] + Var[Y ] + 2Cov[X, Y ]. 53
54 If X and Y are independent, we have E[XY ] = E[X]E[Y ] Cov(X, Y ) = 0 Var[X + Y ] = Var[X] + Var[Y ] By induction, this can be generalized for sums and products of more than two random variables. Example 3.2: If X i Bernoulli(p), a direct calculation gives Var[X i ] = p(1 p). Therefore, if X is the sum of n independent Bernoulli(p) random variables, that is X Bin(n, p), we have Var[X] = np(1 p). 54
55 Chebyshev s inequality [M&U Section 3.3] Theorem 3.3 [M&U Thm 3.6]: For any a > 0 we have Pr( X E[X] a) Var[X] a 2. Proof: Write the probability in question as Pr( X E[X] a) = Pr((X E[X]) 2 a 2 ). Applying Markov s Inequality to the non-negative random variable Y = (X E[X]) 2 gives us Pr(Y a 2 ) E[Y ] a 2 = Var[X] a 2. 55
56 Example 3.4: Consider the same question we already analysed using Markov s Inequality: What is the probability of getting at least 3n/4 heads when a symmetric coin is tosses n times? Since X is binomially distributed, we have E[X] = n/2 and Var[X] = n 1 2 (1 1 ) = n/4. Therefore, 2 Pr( X n n 2 4 ) Var[X] (n/4) = 4 2 n. By symmetry, so Pr( X n n 2 4 ) = 2 Pr(X n 2 n 4 ), Pr(X 3n 4 ) 2 n. Actually even this is extremely loose for large n. We get much better estimates by using Chernoff bounds that will be introduced soon. 56
57 Example 3.5: Coupon Collector s Problem (Example 2.5 continued) We obtained nh(n) as the expectation of the number X of cereal boxes we need to buy. Markov s Inequality then yields Pr(X 2nH(n)) 1 2. To apply Chebyshev, we also need the variance Var[X]. Remember X = n i=1 X i where X i Geom(p i ) and p i = (n i + 1)/n. The variance of X Geom(p) is known [M&U Lemma 3.8] to be Var[X] = 1 p p 2. The random variables X i are mutually independent, so n Var[X] = Var[X i ]. i=1 57
58 By estimating Var[X i ] 1/p 2 i we get n n ( ) 2 n Var[X i ] n 2 n i + 1 i=1 i=1 Therefore, Chebyshev s Inequality gives us i=1 Pr( X nh(n) nh(n)) π2 n 2 /6 (nh(n)) 2 = O 1 i = π2 n ( 1 (log n) 2 This is not a very tight bound, either. The probability that the first n(c + ln n) fail to contain a given specific coupon is ( 1 1 n) n(c+ln n) exp( (c + ln n)). Therefore, the probability that some coupon has failed to appear in the first n(c + ln n) boxes is by union bound at most n exp( (c + ln n)) = e c. Substituting c = ln n yields Pr(X 2n ln n) 1 n. ). 58
59 Randomized algorithm for the median [M&U Section 3.4] Let S be a set of numbers for which we want to determine the median. For simplicity we consider the case where n = S is odd, so the median is the element at position n/2 in the ordering of the elements of S. The median can easily be determined in time O(n log n) by sorting. There is also a (somewhat complicated) deterministic algorithm that runs in time O(n). We give here a simple randomized algorithm with running time O(n). The idea is to use randomization to pick a lower bound d and upper bound u such that with high probability, 1. the median is between d and u and 2. there are not too many elements of S between d and u. 59
60 Ignoring for the moment how exactly we choose d and u, the algorithm is then 1. Choose d and u. 2. Create the set C = { x S d x u } and calculate l d = { x S x < d } and l u = { x S u < x }. 3. If l d > n/2 or l u > n/2, then fail. 4. If C > 4n 3/4, then fail. 5. Otherwise sort C and return its element number n/2 l d
61 If d and u are chosen in time O(n), then clearly the whole algorithm runs in time O(n). If the algorithm does not fail, it gives the right answer. By repeating until it succeeds we therefore get a Las Vegas algorithm that always gives the right answer but may sometimes run for a long time. The interesting part of the analysis is to determine d and u such that the failure probability is small. (From now on we ignore rounding.) 61
62 We propose choosing d and u as follows: 1. Choose a (multi)set R S by choosing independently n 3/4 elements uniformly (with replacement) from S. 2. Sort R. 3. Now d is the element number 1 2 n3/4 n 1/2 and u the element number 1 2 n3/4 + n 1/2 in the ordering of R. 62
63 Intuitively, the median of R, that is the element number 1 2 n3/4, is also an estimate for the median of whole S. The first fail branch is the case where this estimate is badly off. Between d and u there are 2n 1/2 elements of R. Therefore, if sampling has been uniform, then between d and u there are 2n 1/2 (n/n 3/4 ) = 2n 3/4 elements of S. The second fail branch is the case where the sample is not sufficiently uniform. The numbers n 3/4, n 1/2 etc. come from known bounds for sampling accuracy. (In other words, they have been chosen so that the following proof goes through.) 63
64 We ll now derive an upper bound for the failure probability. Let m be the actual median of S, and k = R = n 3/4. Consider the following three events: E 1 : { r R r m } < k 2 n1/2 E 2 : { r R r m } < k 2 n1/2 E 3 : C > 4k. The event E 3 obviously represents the second fail case. The events E 1 and E 2 correspond to m < d ja m > u. Hence, together they cover the first fail case. 64
65 To estimate Pr(E 1 ) write Y 1 = { r R r m }. Thus, Y 1 = k i=1 X i where { 1 if sample point number i is less than or equal to m X i = 0 otherwise. There are (n 1)/2 + 1 elements in S that are less than or equal to m. Therefore, Y 1 Bin(k, p) where p = 1/2 + 1/(2n). Hence, E[Y 1 ] k/2, and ( 1 Var[Y 1 ] = k ) ( 1 2n 2 1 ) < k 2n 4. We apply Chebyshev s Inequality: Pr(E 1 ) Pr( Y 1 E[Y 1 ] > n 1/2 ) Var[Y 1] n 1 4 n 1/4. 65
66 Similarly we see that Pr(E 2 ) 1 4 n 1/4. For the event E 3 we consider two subevents: E 3,1 : { c C c > m } 2k E 3,2 : { c C c < m } 2k. If C > 4k, then at least one of these has occurred. The subevents are symmetrical, so let s consider E 3,1. Now the position of u in S is at least n/2 + 2k. Hence, u and any larger elements in R are among the n/2 2k largest elements of S. By definition of u, there are k/2 n 1/2 such elements. 66
67 Define { 1 if smaple point number i is among the n/2 2k largest elements in S X i = 0 otherwise and X = k i=1 X i. Again, X has binomial distribution, and Therefore, Var[X] = k E[X] = k 2 2n1/2 ( ) ( ) n 1/ n 1/4 < k 4. Pr(E 3,1 ) Pr( X E[X] n 1/2 ) Var[X] < 1 n 4 n 1/4. Altogether, the probability of failure is at most Pr(E 1 ) + Pr(E 2 ) + Pr(E 3,1 ) + Pr(E 3,1 ) < n 1/4. 67
68 4. Chernoff bounds Chernoff bounds is a general name for several inequalities that estimate how tightly the value of a random variable is concentrated around its expectation. Basic example: If X Bin(n, p), then for all 0 < δ 1 we have ( ) X np Pr δ exp ( 13 ) np npδ2. For example, this implies that with probability 1/2 we have X np + 3np ln 2. This bounds can be made (a) more general and (b) tighter. In this section we review some bounds of this variety, including their proofs and applications. 68
69 Moment Generating Function [M&U Section 4.1] The moment generating function of a random variable X is defined as assuming this expectation is finite. M X (t) = E[e tx ], By differentiating the moment generating function n times in the origin we get the nth moment. Theorem 4.1: If M X (t) is defined in some neighbourhood t ( δ, δ) of 0, we have E[X n ] = M (n) X (0) for all n = 1, 2,.... Proof: We defined M X (t) = Pr(X = x) exp(tx). x Under the given assumptions, we can differentiate termwise: M (n) X (t) = Pr(X = x)x n exp(tx). x Substituting t = 0 gives the result. 69
70 Example 4.2: When X Geom(p), we have E[e tx ] = (1 p) k 1 pe tk = = k=1 from which we get the derivatives M X (t) = pe t (1 (1 p)e t ) 2 p ((1 p)e t ) k 1 p k=1 ( ) p 1 1 p 1 (1 p)e 1 t M X 2p(1 p)e2t (t) = (1 (1 p)e t ) + pe t 3 (1 (1 p)e t ) 2. By substituting t = 0 we get the familiar results E[X] = 1/p and E[X 2 ] = (2 p)/p 2. 70
71 It can be proved (but we will not do so on this course) that giving the moment generating function (or alternatively giving all the moments) specifies the distribution uniquely. Theorem 4.3: If X and Y are random variables such that for some δ > 0 we have M X (t) = M Y (t) for all δ < t < δ, the X and Y have the same distribution. This can be used for example to determine the distribution of the product of two independent random variables together with the following. Theorem 4.4: If X and Y are independent, we have M X+Y (t) = M X (t)m Y (t). Proof: Now also e tx and e ty are independent, so E[e t(x+y ) ] = E[e tx e ty ] = E[e tx ]E[e ty ]. 71
72 Deriving Chernoff bounds [M&U Section 4.2.1] The basic technique is to apply Markov s Inequality to the random variable e tx for a suitable t R. Thus, Pr(X a) = Pr(e tx e ta ) E[etX ] e ta for any t > 0, so in particular Pr(X a) min t>0 E[e tx ] e ta. For a negative t the direction of the inequality changes, so Pr(X a) min t<0 E[e tx ] e ta. To make use of this observation, we need an estimate for the moment generating function E[e tx ] and a good choice for t. Often we introduce bounds that are a bit loose to make the formulas more intelligible. 72
73 In the most widely used variant we take X = n i=1 X i where X i Bernoulli(p i ) are independent. We call the random variables X i Poisson trials. If the distributions are identical, with p i = p for all i, we call them Bernoulli trials. Write µ = E[X] = n i=1 p i. We estimate the probabilities Pr(X (1 + δ)µ) and Pr(X (1 δ)µ). First let us consider the moment generating functions for the individual trials M Xi (t) = p i e t 1 + (1 p i )e t 0 = 1 + p i (e t 1) exp(p i (e t 1)) where we applied the inequality 1 + z e z. This implies ( n n ) M X (t) = M Xi (t) exp p i (e t 1) = exp ( (e t 1)µ ). i=1 i=1 We now derive bounds for the probability that X gets very large or very small values. 73
74 We first prove a bound that s (fairly) tight but somewhat difficult to use. From this we can derive variants that are easier to use but less tight. Theorem 4.5 [M&U Thm 4.4.1]: For all δ > 0 we have ( ) e δ µ Pr(X (1 + δ)µ) <. (1 + δ) 1+δ Proof: As noted above, for t > 0 Markov s Inequality yields Pr(X (1 + δ)µ) = Pr(e tx e t(1+δ)µ ) We choose t = ln(1 + δ), which gives us and E[e tx ] exp((e t 1)µ) = e δµ exp(t(1 + δ)µ) = (1 + δ) (1+δ)µ. E[e tx ] exp(t(1 + δ)µ). 74
75 The following simplification is often useful: Theorem 4.6 [M&U Thm 4.4.2]: For 0 < δ 1 we have Proof: It is sufficient to show Pr(X (1 + δ)µ) exp( µδ 2 /3). e δ (1 + δ) 1+δ e δ2 /3 or equivalently (by taking log of both sides) f(δ) 0 where f(δ) = δ (1 + δ) ln(1 + δ) δ2. 75
76 Take now derivatives: f(δ) = δ (1 + δ) ln(1 + δ) δ2 f (δ) = ln(1 + δ) δ f (δ) = δ Thus, f (δ) < 0 for 0 δ < 1/2, so f (δ) is decreasing. On the other hand, f (δ) > 0 for 1/2 < δ < 1, so f (δ) is increasing. Since f (0) = 0 and f (1) = 2/3 ln 2 2/3 0,69 < 0, we get f (δ) 0 for all 0 δ 1. Since f(0) = 0, we get f(δ) 0 for all 0 < δ < 1. 76
77 Another simplification is the following: Theorem 4.7 [M&U Thm 4.4.3]: For R 6µ we have Pr(X R) 2 R. Proof: Write R = (1 + δ)µ, so δ = R/µ 1 5. We get ( ) e δ µ ( ) (1+δ)µ e (1 + δ) 1+δ 1 + δ ( e R 6) 2 R. 77
78 Next consider the probability that X is very small. Theorem 4.8 [M&U Thm 4.5.1]: For all 0 < δ < 1 we have ( ) e δ µ Pr(X (1 δ)µ). (1 δ) 1 δ Proof: As earlier, for all t < 0 we have Pr(X (1 δ)µ) E[etX ] e t(1 δ)µ exp((et 1)µ) exp(t(1 δ)µ). Substituting t = ln(1 δ) gives the desired bound. 78
79 We can simplify this as earlier. Theorem 4.9 [M&U Thm 4.5.2]: For all 0 < δ < 1 we have Pr(X (1 δ)µ) exp( µδ 2 /2). Proof: similar to the case for (1 + δ) ; details omitted. We can use the union bound to get a combined bound. Corollary 4.10 [M&U Cor 4.6]: For all 0 < δ < 1 we have Pr( X µ δµ) 2 exp( µδ 2 /3). 79
80 Coin flips [M&U Section 4.2.2] We flip a fair coin n times. Thus, µ = n/2. What kind of a bound can we have with probability 2/n (that is, the probability of violation gets vanishingly small for large n)? We want exp( (n/2)δ 2 /3) = 1/n, so we take δ = (6 ln n)/n. By plugging this into the bound we get ( Pr X n 1 ) 6n ln n n. Therefore, with a very high probability the deviations are at most O( n log n). Compare this with the earlier Chebyshev bound ( Pr X n 2 n ) 4 4 n. By using Chernoff to estimate the same probability we get ( Pr X n 2 n ) 2e n/24 4 which is exponentially tighter. 80
81 Application: parameter estimation [M&U Section 4.2.3] We pick repeated independent samples from a fixed distribution that is known to be Bernoulli(p) for some unknown p. We wish to estimate p based on the sample. Let X = n i=1 X i be the result of n trials and p = X/n. Clearly E[ p] = µ/n = p. What about error probabilities? We call an interval [ p δ, p + δ] a (1 γ) confidence interval for parameter p if Pr(p [ p δ, p + δ]) 1 γ. Interpretation: After seeing a trial sequence with relative frequency p of ones, we have confidence 1 γ for the true parameter value p belonging to the interval [ p δ, p + δ]. If p is not in the interval, then we have just observed a very unlikely deviation (probability less than γ). Notice The parameter p is a constant, it does not have any disribution (unless we assign a prior to it which is a quite different way of thinking about this). 81
82 If p [ p δ, p + δ], then one of the following events has occurred: p < p δ: therefore, X = n p > n(p + δ) = µ(1 + δ/p). p > p + δ: therefore, X = n p < n(p δ) = µ(1 δ/p). Chernoff bounds give us Pr(p [ p δ, p + δ]) e µ(δ/p)2 /2 + e µ(δ/p)2 /3 = e nδ2 /(2p) + e nδ2 /(3p). Since p is not known, we use the conservative upper bound p 1. Based on that we can choose γ = e nδ2 /2 + e nδ2 /3 (or conversely solve δ from here if γ has been chosen). 82
83 Bounds for some special cases [M&U Section 4.3] Consider the case where X i is has two symmetrical values. Theorem 4.11 [M&U Thm 4.7]: If Pr(X i = 1) = Pr(X i = 1) = 1/2, then for all a > 0 we have ) Pr(X a) exp ( a2 2n. Proof: For all t > 0 we have E[e tx i ] = 1 2 et e t. We apply e t = j=0 t j j!. 83
84 This yields E[e tx i ] = 1 2 (1 + t + = 1 + t2 2 + t4 4! +... t 2j = (2j)! j=0 ( ) 1 t 2 j j! 2 j=0 ( ) t 2 = exp. 2 ) t22 t3 + 3! + t4 4! (1 t + 2 ) t22 t3 3! + t4 4!... 84
85 Therefore, so E[e tx ] = n i=1 Pr(X a) E[etX ] e ta Choosing t = a/n gives the desired result Pr(X a) exp ( ) E[e tx i t 2 ] exp n, 2 exp ( a2 ( ) t 2 n 2 ta. Corollary 4.12: If Pr(X i = 1) = Pr(X i = 1) = 1/2, then for all a > 0 we have ) Pr( X a) 2 exp 2n ) ( a2 2n.. 85
86 Corollary 4.13 [M&U Cor 4.8]: Let Y i be mutually independent with Pr(Y i = 1) = Pr(Y i = 0) = 1/2. Write Y = n i=1 Y i and µ = E[Y ] = n/2. Now for all a > 0 we have ) Pr(Y µ + a) exp ( 2a2 n and for all δ > 0 we have Pr(Y (1 + δ)µ) exp ( ) δ2 µ. 2 Proof: Let X i be as before and Y i = 1 2 (X i + 1). In particular, Y = 1 2 X + µ. 86
87 From the previous theorem we get ) Pr(Y µ + a) = Pr(X 2a) exp ( 4a2. 2n For the second part, choose a = δµ, so ) Pr(Y (1 + δ)µ) = Pr(X 2δµ) exp ( 4δ2 µ 2 = exp 2n Similarly we can prove ( ) δ2 µ. 2 Corollary 4.14 [M&U Cor 4.9]: Let Y i be mutually independent and Pr(Y i = 1) = Pr(Y i = 0) = 1/2. Write Y = n i=1 Y i and µ = E[Y ] = n/2. Now for all 0 < a < µ we have ) Pr(Y µ a) exp ( 2a2 n and for all δ > 0 we have Pr(Y (1 δ)µ) exp ( ) δ2 µ. 2 87
88 Application: set balancing [M&U Section 4.4] Suppose we have a set of m people and n properties. We wish to partition the people into two sets A and A such that for i = 1,..., n we have { p A p has property i } { p A p has property i }. Let s define an array A = (a ij ) { 0, 1 } n m where a ij = 1 if person j has property i. We represent a partition (A, A) as a vector b { 1, 1 } m where b j = 1 if person j is in the set A. With these notations, we thus wish to minimise the quantity where c i = j a ijb j. Ab = max i c i 88
89 How good a result do we get by choosing b at random so that each b j is 1 with probability 1/2 independently of each other? We claim that Pr( Ab 4m ln n) 2 n. We prove this by showing for each individual row i { 1,..., n } that the event c i 4m ln n has probability at most 2/n 2. Write k = j a ij. If k 4m ln n, the claim clearly holds. Otherwise a ij b j get values 1 and 1 symmetrically and independently for those j for which a ij 0. Therefore, Pr a ij b j > ( ) 4m ln n 4m ln n 2 exp 2 2k n 2 since k m. j 89
90 Example: packet routing [M&U Section 4.5] Consider a graph of N nodes, some of which may be connected with an edge. We assume the edges to be directed, but the particular topologies we consider are symmetrical: there s an edge (v, v ) if and only if there s an edge (v, v). The task is to transmit a set of packets through the network. Each packet has a start node and a destination node (address). The route of a packet is a path in the graph from the start node to the destination. During one time step, each packet may travel at most one edge at most one packet may travel along any single edge. We assume sufficient buffer memory in the nodes so packets can wait for an edge to become available. 90
91 To determine how the network works, we must fix how to choose the route of a packet when the start node and address are known if several packets wish to use the same edge, how are they priorized (queueing). For the results we are going to present, the queueing strategy is not important, as long as we never let an edge sit idle if there are packets for it. Possible congestion in the network of course depends on between which nodes the packets are addressed. Here we consider permutation routing: each node has exactly one packet starting from it, and one addressed to it. 91
92 Routing in hypercube [M&U Section 4.5.1] The routing problem is interesting mainly in sparse graphs (number of edges much less than N(N 1)). As an example we consider the hypercube topology. In an n-dimensional hypercube, or n-cube, there are N = 2 n nodes, and we identify the nodes with elements of the set { 0, 1 } n. In a hypercube, the nodes (a 1,..., a n ) and (b 1,..., b n ) are connected if there is exactly one index i such that a i b i. Thus, there are N log 2 N edges in the hypercube, and the diameter (longest distance between two nodes) is log 2 N. 92
93 The starting point for routing in an n-cube is the bit-fixing algorithm. Consider a packet starting from node a = (a 1,..., a n ) with destination b = (b 1,..., b n ). For i = 1,..., n + 1, define v i = (b 1,..., b i 1, a i,..., a n ). The packet is now routed via the nodes a = v 1, v 2,..., v n+1 = b. (The actual path is obtained by removing from this the repetitions that occur when a i = b i.) Hence, we fix the address of the packet bit by bit, from left to right. The bit fixing algorithm has good average case performance when the addresses are picked at random. However, it can be shown that in some cases it leads to congestion and takes Ω(N 1/2 ) steps to deliver all the packets. 93
94 To avoid the worst case of bit-fixing we consider randomized two-phase routing: Phase I: Pick for each packet a random node as an intermediate point. Route the packets to their intermediate points by bit-fixing. Phase II: Route the packets from the intermediate points to their actual destinations. We will show that with probability 1 O(N 1 ) this two-phase routing delivers all packets in time O(log N). Since log 2 N is the diameter of the graph, this is optimal (up to a constant factor). 94
95 How we handle queues will clearly have on effect on when a given packet crosses a given edge on its route. To simplify the analysis, let T (M) be the time packet M takes to reach its destination. Each of these T (M) steps is consumed by one of the following actions: 1. packet M crosses an edge on its route, or 2. packet M is in queue as some other packet crosses an edge M would need. Let X(e) be the number of packets that have edge e on their route. Based on the above, we can make Observation: If the route of packet M consists of edges e 1,..., e m, then T (M) m X(e i ). i=1 95
96 The preceding observation allows us to ignore the queue behaviour and concentrate on the paths. For a path P consisting of edges e 1,..., e m, define T (P ) = m X(e i ). i=1 Based on our observation, the time taken by the routing is always upper bounded by max P R T (P ) where R is the set of all the paths used in routing. This applies to any routing scenario. In particular, let T 1 and X 1 be the quantities T and X when we consider only Phase I of our algorithm. We will show that with a high probability we have T 1 (P ) 30n for all possible paths P. 96
97 Fix now some paths P = (v 0,..., v m ) which is a possible route in bit-fixing. We want a high-probability upper bound for T 1 (P ) = m i=1 X 1(e i ). As the random variables X 1 (e i ) are not independent, we cannot directly apply Chernoff bounds. To resolve the problem, we first estimate the probability that at least 6n different packets cross at least one edge that belongs to P. After this we show that with high probability no individual packet will use too many edges on P. 97
98 Let v i 1 be the ith node on path P, and j the bit on which v i 1 and v i differ. We say a packet k is active in node v i 1, if 1. packet k is routed through v i 1 and 2. when packet k reaches v i 1, its jth bit has not been fixed yet, but bits 1,..., j 1 either have been fixed or were correct to start with. Notice that we do not require that the packet actually goes from v i 1 to v i. However, depending on bit j of the address, it has the potential of doing that. For k = 1,..., N, let H k = 1 if packet k is active in at least one node on P, and H k = 0 otherwise. Let H = N k=1 H k. Notice that random variables H k are mutually independent. 98
99 Let v i 1 = (b 1,..., b j 1, a j, a j+1,..., a n ) v i = (b 1,..., b j 1, b j, a j+1,..., a n ). By condition 2, a packet that is active in v i 1 started in a node of form (,...,, a j,..., a n ) where can be 0 or 1. Therefore, there are 2 j 1 possible start nodes. By condition 1, if a packet is active in v i 1, its destination must be of form (b 1,..., b j 1,,..., ). Therefore, if we consider some fixed node among the possible start nodes, the packet starting from the node will become active with probability 2 j+1. Therefore, the expected number of active packets in v i 1 is 1, so E[H] m 1 n. 99
100 Since the random variables H k are mutually independent, we may apply Chernoff bounds (Theorem 4.7 [M&U Thm 4.4.3]): Pr(H 6n) 2 6n. We choose B = { H 6n } in the estimate Therefore, Pr(A) = Pr(A B) Pr(B) + Pr(A B) Pr(B) Pr(B) + Pr(A B). Pr(T 1 (P )) 30n) 2 6n + Pr(T 1 (P ) 30n H < 6n). We will next estimate the latter conditional probability. 100
101 Assume that packet k is active in v i 1. For k to actually cross the edge (v i 1, v i ), we require its jth address bit to be b j. This has probability 1/2. However, we also require that the packet does not need to fix any earlier bits 1,..., j 1. Thus, the actual probability for a packet that is active in v i 1 to cross the edge (v i 1, v i ) is at most 1/2. More generally, if the packet is on path P in node v l 1, l > i, then the probability that it next goes to v l is at most 1/2. On the other hand, if the packet enters v l 1 but does not go to v l in the next step, it won t ever return to path P. This is because in this case one of the address bits 1,..., l of the packet must differ from the corresponding bit of the destination node of path P. As these earlier bits won t be touched again by the bit-fixing algorithm, the route of the packet remains separate from P. 101
102 Assume that there are a total of h active packets for the nodes of P. What is the probability that together they make a total of at least 30n steps along path P? Consider as an individual trial a situation where a given active packet is in some given node on P. With probability at most 1/2 we get success, meaning that the packet proceeds along an edge on P. At least with probability 1/2 we get failure, so the packet leaves path P and never returns. When a failure occurs, we move to considering the next active packet. Hence, each success contributes one transition along P, but each failure removes one packet from consideration. To get 30n transitions, the first 30n + h trials may have at most h failures. 102
Randomized Algorithms
 Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( )
![Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( ) Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( )](/thumbs/95/125074181.jpg) Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr Pr = Pr Pr Pr() Pr Pr. We are given three coins and are told that two of the coins are fair and the
Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr Pr = Pr Pr Pr() Pr Pr. We are given three coins and are told that two of the coins are fair and the
Random Variable. Pr(X = a) = Pr(s)
 Random Variable Definition A random variable X on a sample space Ω is a real-valued function on Ω; that is, X : Ω R. A discrete random variable is a random variable that takes on only a finite or countably
Random Variable Definition A random variable X on a sample space Ω is a real-valued function on Ω; that is, X : Ω R. A discrete random variable is a random variable that takes on only a finite or countably
Lecture 4: Two-point Sampling, Coupon Collector s problem
 Randomized Algorithms Lecture 4: Two-point Sampling, Coupon Collector s problem Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized Algorithms
Randomized Algorithms Lecture 4: Two-point Sampling, Coupon Collector s problem Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized Algorithms
Chernoff Bounds. Theme: try to show that it is unlikely a random variable X is far away from its expectation.
 Chernoff Bounds Theme: try to show that it is unlikely a random variable X is far away from its expectation. The more you know about X, the better the bound you obtain. Markov s inequality: use E[X ] Chebyshev
Chernoff Bounds Theme: try to show that it is unlikely a random variable X is far away from its expectation. The more you know about X, the better the bound you obtain. Markov s inequality: use E[X ] Chebyshev
11.1 Set Cover ILP formulation of set cover Deterministic rounding
 CS787: Advanced Algorithms Lecture 11: Randomized Rounding, Concentration Bounds In this lecture we will see some more examples of approximation algorithms based on LP relaxations. This time we will use
CS787: Advanced Algorithms Lecture 11: Randomized Rounding, Concentration Bounds In this lecture we will see some more examples of approximation algorithms based on LP relaxations. This time we will use
Lecture 4: Sampling, Tail Inequalities
 Lecture 4: Sampling, Tail Inequalities Variance and Covariance Moment and Deviation Concentration and Tail Inequalities Sampling and Estimation c Hung Q. Ngo (SUNY at Buffalo) CSE 694 A Fun Course 1 /
Lecture 4: Sampling, Tail Inequalities Variance and Covariance Moment and Deviation Concentration and Tail Inequalities Sampling and Estimation c Hung Q. Ngo (SUNY at Buffalo) CSE 694 A Fun Course 1 /
Tail Inequalities Randomized Algorithms. Sariel Har-Peled. December 20, 2002
 Tail Inequalities 497 - Randomized Algorithms Sariel Har-Peled December 0, 00 Wir mssen wissen, wir werden wissen (We must know, we shall know) David Hilbert 1 Tail Inequalities 1.1 The Chernoff Bound
Tail Inequalities 497 - Randomized Algorithms Sariel Har-Peled December 0, 00 Wir mssen wissen, wir werden wissen (We must know, we shall know) David Hilbert 1 Tail Inequalities 1.1 The Chernoff Bound
CS155: Probability and Computing: Randomized Algorithms and Probabilistic Analysis
 CS155: Probability and Computing: Randomized Algorithms and Probabilistic Analysis Eli Upfal Eli Upfal@brown.edu Office: 319 TA s: Lorenzo De Stefani and Sorin Vatasoiu cs155tas@cs.brown.edu It is remarkable
CS155: Probability and Computing: Randomized Algorithms and Probabilistic Analysis Eli Upfal Eli Upfal@brown.edu Office: 319 TA s: Lorenzo De Stefani and Sorin Vatasoiu cs155tas@cs.brown.edu It is remarkable
X = X X n, + X 2
 CS 70 Discrete Mathematics for CS Fall 2003 Wagner Lecture 22 Variance Question: At each time step, I flip a fair coin. If it comes up Heads, I walk one step to the right; if it comes up Tails, I walk
CS 70 Discrete Mathematics for CS Fall 2003 Wagner Lecture 22 Variance Question: At each time step, I flip a fair coin. If it comes up Heads, I walk one step to the right; if it comes up Tails, I walk
variance of independent variables: sum of variances So chebyshev predicts won t stray beyond stdev.
 Announcements No class monday. Metric embedding seminar. Review expectation notion of high probability. Markov. Today: Book 4.1, 3.3, 4.2 Chebyshev. Remind variance, standard deviation. σ 2 = E[(X µ X
Announcements No class monday. Metric embedding seminar. Review expectation notion of high probability. Markov. Today: Book 4.1, 3.3, 4.2 Chebyshev. Remind variance, standard deviation. σ 2 = E[(X µ X
Disjointness and Additivity
 Midterm 2: Format Midterm 2 Review CS70 Summer 2016 - Lecture 6D David Dinh 28 July 2016 UC Berkeley 8 questions, 190 points, 110 minutes (same as MT1). Two pages (one double-sided sheet) of handwritten
Midterm 2: Format Midterm 2 Review CS70 Summer 2016 - Lecture 6D David Dinh 28 July 2016 UC Berkeley 8 questions, 190 points, 110 minutes (same as MT1). Two pages (one double-sided sheet) of handwritten
Midterm 2 Review. CS70 Summer Lecture 6D. David Dinh 28 July UC Berkeley
 Midterm 2 Review CS70 Summer 2016 - Lecture 6D David Dinh 28 July 2016 UC Berkeley Midterm 2: Format 8 questions, 190 points, 110 minutes (same as MT1). Two pages (one double-sided sheet) of handwritten
Midterm 2 Review CS70 Summer 2016 - Lecture 6D David Dinh 28 July 2016 UC Berkeley Midterm 2: Format 8 questions, 190 points, 110 minutes (same as MT1). Two pages (one double-sided sheet) of handwritten
Aditya Bhaskara CS 5968/6968, Lecture 1: Introduction and Review 12 January 2016
 Lecture 1: Introduction and Review We begin with a short introduction to the course, and logistics. We then survey some basics about approximation algorithms and probability. We also introduce some of
Lecture 1: Introduction and Review We begin with a short introduction to the course, and logistics. We then survey some basics about approximation algorithms and probability. We also introduce some of
CSE 525 Randomized Algorithms & Probabilistic Analysis Spring Lecture 3: April 9
 CSE 55 Randomized Algorithms & Probabilistic Analysis Spring 01 Lecture : April 9 Lecturer: Anna Karlin Scribe: Tyler Rigsby & John MacKinnon.1 Kinds of randomization in algorithms So far in our discussion
CSE 55 Randomized Algorithms & Probabilistic Analysis Spring 01 Lecture : April 9 Lecturer: Anna Karlin Scribe: Tyler Rigsby & John MacKinnon.1 Kinds of randomization in algorithms So far in our discussion
Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Note 14
 CS 70 Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Note 14 Introduction One of the key properties of coin flips is independence: if you flip a fair coin ten times and get ten
CS 70 Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Note 14 Introduction One of the key properties of coin flips is independence: if you flip a fair coin ten times and get ten
Introduction to Randomized Algorithms: Quick Sort and Quick Selection
 Chapter 14 Introduction to Randomized Algorithms: Quick Sort and Quick Selection CS 473: Fundamental Algorithms, Spring 2011 March 10, 2011 14.1 Introduction to Randomized Algorithms 14.2 Introduction
Chapter 14 Introduction to Randomized Algorithms: Quick Sort and Quick Selection CS 473: Fundamental Algorithms, Spring 2011 March 10, 2011 14.1 Introduction to Randomized Algorithms 14.2 Introduction
CS 246 Review of Proof Techniques and Probability 01/14/19
 Note: This document has been adapted from a similar review session for CS224W (Autumn 2018). It was originally compiled by Jessica Su, with minor edits by Jayadev Bhaskaran. 1 Proof techniques Here we
Note: This document has been adapted from a similar review session for CS224W (Autumn 2018). It was originally compiled by Jessica Su, with minor edits by Jayadev Bhaskaran. 1 Proof techniques Here we
CS261: A Second Course in Algorithms Lecture #18: Five Essential Tools for the Analysis of Randomized Algorithms
 CS261: A Second Course in Algorithms Lecture #18: Five Essential Tools for the Analysis of Randomized Algorithms Tim Roughgarden March 3, 2016 1 Preamble In CS109 and CS161, you learned some tricks of
CS261: A Second Course in Algorithms Lecture #18: Five Essential Tools for the Analysis of Randomized Algorithms Tim Roughgarden March 3, 2016 1 Preamble In CS109 and CS161, you learned some tricks of
Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds
 Randomized Algorithms Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized
Randomized Algorithms Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized
Tail Inequalities. The Chernoff bound works for random variables that are a sum of indicator variables with the same distribution (Bernoulli trials).
 Tail Inequalities William Hunt Lane Department of Computer Science and Electrical Engineering, West Virginia University, Morgantown, WV William.Hunt@mail.wvu.edu Introduction In this chapter, we are interested
Tail Inequalities William Hunt Lane Department of Computer Science and Electrical Engineering, West Virginia University, Morgantown, WV William.Hunt@mail.wvu.edu Introduction In this chapter, we are interested
Essentials on the Analysis of Randomized Algorithms
 Essentials on the Analysis of Randomized Algorithms Dimitris Diochnos Feb 0, 2009 Abstract These notes were written with Monte Carlo algorithms primarily in mind. Topics covered are basic (discrete) random
Essentials on the Analysis of Randomized Algorithms Dimitris Diochnos Feb 0, 2009 Abstract These notes were written with Monte Carlo algorithms primarily in mind. Topics covered are basic (discrete) random
SUMMARY OF PROBABILITY CONCEPTS SO FAR (SUPPLEMENT FOR MA416)
 SUMMARY OF PROBABILITY CONCEPTS SO FAR (SUPPLEMENT FOR MA416) D. ARAPURA This is a summary of the essential material covered so far. The final will be cumulative. I ve also included some review problems
SUMMARY OF PROBABILITY CONCEPTS SO FAR (SUPPLEMENT FOR MA416) D. ARAPURA This is a summary of the essential material covered so far. The final will be cumulative. I ve also included some review problems
Discrete Mathematics for CS Spring 2007 Luca Trevisan Lecture 20
 CS 70 Discrete Mathematics for CS Spring 2007 Luca Trevisan Lecture 20 Today we shall discuss a measure of how close a random variable tends to be to its expectation. But first we need to see how to compute
CS 70 Discrete Mathematics for CS Spring 2007 Luca Trevisan Lecture 20 Today we shall discuss a measure of how close a random variable tends to be to its expectation. But first we need to see how to compute
Assignment 4: Solutions
 Math 340: Discrete Structures II Assignment 4: Solutions. Random Walks. Consider a random walk on an connected, non-bipartite, undirected graph G. Show that, in the long run, the walk will traverse each
Math 340: Discrete Structures II Assignment 4: Solutions. Random Walks. Consider a random walk on an connected, non-bipartite, undirected graph G. Show that, in the long run, the walk will traverse each
Homework 4 Solutions
 CS 174: Combinatorics and Discrete Probability Fall 01 Homework 4 Solutions Problem 1. (Exercise 3.4 from MU 5 points) Recall the randomized algorithm discussed in class for finding the median of a set
CS 174: Combinatorics and Discrete Probability Fall 01 Homework 4 Solutions Problem 1. (Exercise 3.4 from MU 5 points) Recall the randomized algorithm discussed in class for finding the median of a set
Randomized algorithms. Inge Li Gørtz
 Randomized algorithms Inge Li Gørtz Randomized algorithms Today What are randomized algorithms? Properties of randomized algorithms Two examples: Median/Select. Quick-sort Randomized Algorithms Randomized
Randomized algorithms Inge Li Gørtz Randomized algorithms Today What are randomized algorithms? Properties of randomized algorithms Two examples: Median/Select. Quick-sort Randomized Algorithms Randomized
Discrete Mathematics and Probability Theory Fall 2014 Anant Sahai Note 15. Random Variables: Distributions, Independence, and Expectations
 EECS 70 Discrete Mathematics and Probability Theory Fall 204 Anant Sahai Note 5 Random Variables: Distributions, Independence, and Expectations In the last note, we saw how useful it is to have a way of
EECS 70 Discrete Mathematics and Probability Theory Fall 204 Anant Sahai Note 5 Random Variables: Distributions, Independence, and Expectations In the last note, we saw how useful it is to have a way of
1. When applied to an affected person, the test comes up positive in 90% of cases, and negative in 10% (these are called false negatives ).
 CS 70 Discrete Mathematics for CS Spring 2006 Vazirani Lecture 8 Conditional Probability A pharmaceutical company is marketing a new test for a certain medical condition. According to clinical trials,
CS 70 Discrete Mathematics for CS Spring 2006 Vazirani Lecture 8 Conditional Probability A pharmaceutical company is marketing a new test for a certain medical condition. According to clinical trials,
Part IA Probability. Definitions. Based on lectures by R. Weber Notes taken by Dexter Chua. Lent 2015
 Part IA Probability Definitions Based on lectures by R. Weber Notes taken by Dexter Chua Lent 2015 These notes are not endorsed by the lecturers, and I have modified them (often significantly) after lectures.
Part IA Probability Definitions Based on lectures by R. Weber Notes taken by Dexter Chua Lent 2015 These notes are not endorsed by the lecturers, and I have modified them (often significantly) after lectures.
Lecture 13 (Part 2): Deviation from mean: Markov s inequality, variance and its properties, Chebyshev s inequality
 Lecture 13 (Part 2): Deviation from mean: Markov s inequality, variance and its properties, Chebyshev s inequality Discrete Structures II (Summer 2018) Rutgers University Instructor: Abhishek Bhrushundi
Lecture 13 (Part 2): Deviation from mean: Markov s inequality, variance and its properties, Chebyshev s inequality Discrete Structures II (Summer 2018) Rutgers University Instructor: Abhishek Bhrushundi
Expectation is linear. So far we saw that E(X + Y ) = E(X) + E(Y ). Let α R. Then,
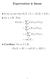 Expectation is linear So far we saw that E(X + Y ) = E(X) + E(Y ). Let α R. Then, E(αX) = ω = ω (αx)(ω) Pr(ω) αx(ω) Pr(ω) = α ω X(ω) Pr(ω) = αe(x). Corollary. For α, β R, E(αX + βy ) = αe(x) + βe(y ).
Expectation is linear So far we saw that E(X + Y ) = E(X) + E(Y ). Let α R. Then, E(αX) = ω = ω (αx)(ω) Pr(ω) αx(ω) Pr(ω) = α ω X(ω) Pr(ω) = αe(x). Corollary. For α, β R, E(αX + βy ) = αe(x) + βe(y ).
Example 1. The sample space of an experiment where we flip a pair of coins is denoted by:
 Chapter 8 Probability 8. Preliminaries Definition (Sample Space). A Sample Space, Ω, is the set of all possible outcomes of an experiment. Such a sample space is considered discrete if Ω has finite cardinality.
Chapter 8 Probability 8. Preliminaries Definition (Sample Space). A Sample Space, Ω, is the set of all possible outcomes of an experiment. Such a sample space is considered discrete if Ω has finite cardinality.
The first bound is the strongest, the other two bounds are often easier to state and compute. Proof: Applying Markov's inequality, for any >0 we have
 The first bound is the strongest, the other two bounds are often easier to state and compute Proof: Applying Markov's inequality, for any >0 we have Pr (1 + ) = Pr For any >0, we can set = ln 1+ (4.4.1):
The first bound is the strongest, the other two bounds are often easier to state and compute Proof: Applying Markov's inequality, for any >0 we have Pr (1 + ) = Pr For any >0, we can set = ln 1+ (4.4.1):
Discrete Mathematics and Probability Theory Fall 2013 Vazirani Note 12. Random Variables: Distribution and Expectation
 CS 70 Discrete Mathematics and Probability Theory Fall 203 Vazirani Note 2 Random Variables: Distribution and Expectation We will now return once again to the question of how many heads in a typical sequence
CS 70 Discrete Mathematics and Probability Theory Fall 203 Vazirani Note 2 Random Variables: Distribution and Expectation We will now return once again to the question of how many heads in a typical sequence
Lecture 4. P r[x > ce[x]] 1/c. = ap r[x = a] + a>ce[x] P r[x = a]
![Lecture 4. P r[x > ce[x]] 1/c. = ap r[x = a] + a>ce[x] P r[x = a] Lecture 4. P r[x > ce[x]] 1/c. = ap r[x = a] + a>ce[x] P r[x = a]](/thumbs/96/126571961.jpg) U.C. Berkeley CS273: Parallel and Distributed Theory Lecture 4 Professor Satish Rao September 7, 2010 Lecturer: Satish Rao Last revised September 13, 2010 Lecture 4 1 Deviation bounds. Deviation bounds
U.C. Berkeley CS273: Parallel and Distributed Theory Lecture 4 Professor Satish Rao September 7, 2010 Lecturer: Satish Rao Last revised September 13, 2010 Lecture 4 1 Deviation bounds. Deviation bounds
Discrete Mathematics
 Discrete Mathematics Workshop Organized by: ACM Unit, ISI Tutorial-1 Date: 05.07.2017 (Q1) Given seven points in a triangle of unit area, prove that three of them form a triangle of area not exceeding
Discrete Mathematics Workshop Organized by: ACM Unit, ISI Tutorial-1 Date: 05.07.2017 (Q1) Given seven points in a triangle of unit area, prove that three of them form a triangle of area not exceeding
3 Multiple Discrete Random Variables
 3 Multiple Discrete Random Variables 3.1 Joint densities Suppose we have a probability space (Ω, F,P) and now we have two discrete random variables X and Y on it. They have probability mass functions f
3 Multiple Discrete Random Variables 3.1 Joint densities Suppose we have a probability space (Ω, F,P) and now we have two discrete random variables X and Y on it. They have probability mass functions f
Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Note 16. Random Variables: Distribution and Expectation
 CS 70 Discrete Mathematics and Probability Theory Spring 206 Rao and Walrand Note 6 Random Variables: Distribution and Expectation Example: Coin Flips Recall our setup of a probabilistic experiment as
CS 70 Discrete Mathematics and Probability Theory Spring 206 Rao and Walrand Note 6 Random Variables: Distribution and Expectation Example: Coin Flips Recall our setup of a probabilistic experiment as
Midterm Exam 1 (Solutions)
 EECS 6 Probability and Random Processes University of California, Berkeley: Spring 07 Kannan Ramchandran February 3, 07 Midterm Exam (Solutions) Last name First name SID Name of student on your left: Name
EECS 6 Probability and Random Processes University of California, Berkeley: Spring 07 Kannan Ramchandran February 3, 07 Midterm Exam (Solutions) Last name First name SID Name of student on your left: Name
Discrete Mathematics and Probability Theory Fall 2012 Vazirani Note 14. Random Variables: Distribution and Expectation
 CS 70 Discrete Mathematics and Probability Theory Fall 202 Vazirani Note 4 Random Variables: Distribution and Expectation Random Variables Question: The homeworks of 20 students are collected in, randomly
CS 70 Discrete Mathematics and Probability Theory Fall 202 Vazirani Note 4 Random Variables: Distribution and Expectation Random Variables Question: The homeworks of 20 students are collected in, randomly
Overview. CSE 21 Day 5. Image/Coimage. Monotonic Lists. Functions Probabilistic analysis
 Day 5 Functions/Probability Overview Functions Probabilistic analysis Neil Rhodes UC San Diego Image/Coimage The image of f is the set of values f actually takes on (a subset of the codomain) The inverse
Day 5 Functions/Probability Overview Functions Probabilistic analysis Neil Rhodes UC San Diego Image/Coimage The image of f is the set of values f actually takes on (a subset of the codomain) The inverse
1 Proof techniques. CS 224W Linear Algebra, Probability, and Proof Techniques
 1 Proof techniques Here we will learn to prove universal mathematical statements, like the square of any odd number is odd. It s easy enough to show that this is true in specific cases for example, 3 2
1 Proof techniques Here we will learn to prove universal mathematical statements, like the square of any odd number is odd. It s easy enough to show that this is true in specific cases for example, 3 2
Lecture 5: Two-point Sampling
 Randomized Algorithms Lecture 5: Two-point Sampling Sotiris Nikoletseas Professor CEID - ETY Course 2017-2018 Sotiris Nikoletseas, Professor Randomized Algorithms - Lecture 5 1 / 26 Overview A. Pairwise
Randomized Algorithms Lecture 5: Two-point Sampling Sotiris Nikoletseas Professor CEID - ETY Course 2017-2018 Sotiris Nikoletseas, Professor Randomized Algorithms - Lecture 5 1 / 26 Overview A. Pairwise
Week 12-13: Discrete Probability
 Week 12-13: Discrete Probability November 21, 2018 1 Probability Space There are many problems about chances or possibilities, called probability in mathematics. When we roll two dice there are possible
Week 12-13: Discrete Probability November 21, 2018 1 Probability Space There are many problems about chances or possibilities, called probability in mathematics. When we roll two dice there are possible
STAT2201. Analysis of Engineering & Scientific Data. Unit 3
 STAT2201 Analysis of Engineering & Scientific Data Unit 3 Slava Vaisman The University of Queensland School of Mathematics and Physics What we learned in Unit 2 (1) We defined a sample space of a random
STAT2201 Analysis of Engineering & Scientific Data Unit 3 Slava Vaisman The University of Queensland School of Mathematics and Physics What we learned in Unit 2 (1) We defined a sample space of a random
CS6999 Probabilistic Methods in Integer Programming Randomized Rounding Andrew D. Smith April 2003
 CS6999 Probabilistic Methods in Integer Programming Randomized Rounding April 2003 Overview 2 Background Randomized Rounding Handling Feasibility Derandomization Advanced Techniques Integer Programming
CS6999 Probabilistic Methods in Integer Programming Randomized Rounding April 2003 Overview 2 Background Randomized Rounding Handling Feasibility Derandomization Advanced Techniques Integer Programming
Sample Spaces, Random Variables
 Sample Spaces, Random Variables Moulinath Banerjee University of Michigan August 3, 22 Probabilities In talking about probabilities, the fundamental object is Ω, the sample space. (elements) in Ω are denoted
Sample Spaces, Random Variables Moulinath Banerjee University of Michigan August 3, 22 Probabilities In talking about probabilities, the fundamental object is Ω, the sample space. (elements) in Ω are denoted
Expectation, inequalities and laws of large numbers
 Chapter 3 Expectation, inequalities and laws of large numbers 3. Expectation and Variance Indicator random variable Let us suppose that the event A partitions the sample space S, i.e. A A S. The indicator
Chapter 3 Expectation, inequalities and laws of large numbers 3. Expectation and Variance Indicator random variable Let us suppose that the event A partitions the sample space S, i.e. A A S. The indicator
CS280, Spring 2004: Final
 CS280, Spring 2004: Final 1. [4 points] Which of the following relations on {0, 1, 2, 3} is an equivalence relation. (If it is, explain why. If it isn t, explain why not.) Just saying Yes or No with no
CS280, Spring 2004: Final 1. [4 points] Which of the following relations on {0, 1, 2, 3} is an equivalence relation. (If it is, explain why. If it isn t, explain why not.) Just saying Yes or No with no
Lecture 4: Probability and Discrete Random Variables
 Error Correcting Codes: Combinatorics, Algorithms and Applications (Fall 2007) Lecture 4: Probability and Discrete Random Variables Wednesday, January 21, 2009 Lecturer: Atri Rudra Scribe: Anonymous 1
Error Correcting Codes: Combinatorics, Algorithms and Applications (Fall 2007) Lecture 4: Probability and Discrete Random Variables Wednesday, January 21, 2009 Lecturer: Atri Rudra Scribe: Anonymous 1
Notes on Discrete Probability
 Columbia University Handout 3 W4231: Analysis of Algorithms September 21, 1999 Professor Luca Trevisan Notes on Discrete Probability The following notes cover, mostly without proofs, the basic notions
Columbia University Handout 3 W4231: Analysis of Algorithms September 21, 1999 Professor Luca Trevisan Notes on Discrete Probability The following notes cover, mostly without proofs, the basic notions
Summary of basic probability theory Math 218, Mathematical Statistics D Joyce, Spring 2016
 8. For any two events E and F, P (E) = P (E F ) + P (E F c ). Summary of basic probability theory Math 218, Mathematical Statistics D Joyce, Spring 2016 Sample space. A sample space consists of a underlying
8. For any two events E and F, P (E) = P (E F ) + P (E F c ). Summary of basic probability theory Math 218, Mathematical Statistics D Joyce, Spring 2016 Sample space. A sample space consists of a underlying
Lecture 2: Review of Basic Probability Theory
 ECE 830 Fall 2010 Statistical Signal Processing instructor: R. Nowak, scribe: R. Nowak Lecture 2: Review of Basic Probability Theory Probabilistic models will be used throughout the course to represent
ECE 830 Fall 2010 Statistical Signal Processing instructor: R. Nowak, scribe: R. Nowak Lecture 2: Review of Basic Probability Theory Probabilistic models will be used throughout the course to represent
Discrete Probability Refresher
 ECE 1502 Information Theory Discrete Probability Refresher F. R. Kschischang Dept. of Electrical and Computer Engineering University of Toronto January 13, 1999 revised January 11, 2006 Probability theory
ECE 1502 Information Theory Discrete Probability Refresher F. R. Kschischang Dept. of Electrical and Computer Engineering University of Toronto January 13, 1999 revised January 11, 2006 Probability theory
CME 106: Review Probability theory
 : Probability theory Sven Schmit April 3, 2015 1 Overview In the first half of the course, we covered topics from probability theory. The difference between statistics and probability theory is the following:
: Probability theory Sven Schmit April 3, 2015 1 Overview In the first half of the course, we covered topics from probability theory. The difference between statistics and probability theory is the following:
2. AXIOMATIC PROBABILITY
 IA Probability Lent Term 2. AXIOMATIC PROBABILITY 2. The axioms The formulation for classical probability in which all outcomes or points in the sample space are equally likely is too restrictive to develop
IA Probability Lent Term 2. AXIOMATIC PROBABILITY 2. The axioms The formulation for classical probability in which all outcomes or points in the sample space are equally likely is too restrictive to develop
With high probability
 With high probability So far we have been mainly concerned with expected behaviour: expected running times, expected competitive ratio s. But it would often be much more interesting if we would be able
With high probability So far we have been mainly concerned with expected behaviour: expected running times, expected competitive ratio s. But it would often be much more interesting if we would be able
Randomized Algorithms Week 2: Tail Inequalities
 Randomized Algorithms Week 2: Tail Inequalities Rao Kosaraju In this section, we study three ways to estimate the tail probabilities of random variables. Please note that the more information we know about
Randomized Algorithms Week 2: Tail Inequalities Rao Kosaraju In this section, we study three ways to estimate the tail probabilities of random variables. Please note that the more information we know about
Lecture 1 Measure concentration
 CSE 29: Learning Theory Fall 2006 Lecture Measure concentration Lecturer: Sanjoy Dasgupta Scribe: Nakul Verma, Aaron Arvey, and Paul Ruvolo. Concentration of measure: examples We start with some examples
CSE 29: Learning Theory Fall 2006 Lecture Measure concentration Lecturer: Sanjoy Dasgupta Scribe: Nakul Verma, Aaron Arvey, and Paul Ruvolo. Concentration of measure: examples We start with some examples
. Find E(V ) and var(v ).
 Math 6382/6383: Probability Models and Mathematical Statistics Sample Preliminary Exam Questions 1. A person tosses a fair coin until she obtains 2 heads in a row. She then tosses a fair die the same number
Math 6382/6383: Probability Models and Mathematical Statistics Sample Preliminary Exam Questions 1. A person tosses a fair coin until she obtains 2 heads in a row. She then tosses a fair die the same number
Math Bootcamp 2012 Miscellaneous
 Math Bootcamp 202 Miscellaneous Factorial, combination and permutation The factorial of a positive integer n denoted by n!, is the product of all positive integers less than or equal to n. Define 0! =.
Math Bootcamp 202 Miscellaneous Factorial, combination and permutation The factorial of a positive integer n denoted by n!, is the product of all positive integers less than or equal to n. Define 0! =.
2. Suppose (X, Y ) is a pair of random variables uniformly distributed over the triangle with vertices (0, 0), (2, 0), (2, 1).
 Name M362K Final Exam Instructions: Show all of your work. You do not have to simplify your answers. No calculators allowed. There is a table of formulae on the last page. 1. Suppose X 1,..., X 1 are independent
Name M362K Final Exam Instructions: Show all of your work. You do not have to simplify your answers. No calculators allowed. There is a table of formulae on the last page. 1. Suppose X 1,..., X 1 are independent
Quick Tour of Basic Probability Theory and Linear Algebra
 Quick Tour of and Linear Algebra Quick Tour of and Linear Algebra CS224w: Social and Information Network Analysis Fall 2011 Quick Tour of and Linear Algebra Quick Tour of and Linear Algebra Outline Definitions
Quick Tour of and Linear Algebra Quick Tour of and Linear Algebra CS224w: Social and Information Network Analysis Fall 2011 Quick Tour of and Linear Algebra Quick Tour of and Linear Algebra Outline Definitions
Discrete Mathematics for CS Spring 2006 Vazirani Lecture 22
 CS 70 Discrete Mathematics for CS Spring 2006 Vazirani Lecture 22 Random Variables and Expectation Question: The homeworks of 20 students are collected in, randomly shuffled and returned to the students.
CS 70 Discrete Mathematics for CS Spring 2006 Vazirani Lecture 22 Random Variables and Expectation Question: The homeworks of 20 students are collected in, randomly shuffled and returned to the students.
CSE 548: Analysis of Algorithms. Lectures 18, 19, 20 & 21 ( Randomized Algorithms & High Probability Bounds )
 CSE 548: Analysis of Algorithms Lectures 18, 19, 20 & 21 ( Randomized Algorithms & High Probability Bounds ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Fall 2012 Markov s Inequality
CSE 548: Analysis of Algorithms Lectures 18, 19, 20 & 21 ( Randomized Algorithms & High Probability Bounds ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Fall 2012 Markov s Inequality
Handout 1: Mathematical Background
 Handout 1: Mathematical Background Boaz Barak February 2, 2010 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete math
Handout 1: Mathematical Background Boaz Barak February 2, 2010 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete math
Lectures on Elementary Probability. William G. Faris
 Lectures on Elementary Probability William G. Faris February 22, 2002 2 Contents 1 Combinatorics 5 1.1 Factorials and binomial coefficients................. 5 1.2 Sampling with replacement.....................
Lectures on Elementary Probability William G. Faris February 22, 2002 2 Contents 1 Combinatorics 5 1.1 Factorials and binomial coefficients................. 5 1.2 Sampling with replacement.....................
CS 125 Section #12 (More) Probability and Randomized Algorithms 11/24/14. For random numbers X which only take on nonnegative integer values, E(X) =
 CS 125 Section #12 (More) Probability and Randomized Algorithms 11/24/14 1 Probability First, recall a couple useful facts from last time about probability: Linearity of expectation: E(aX + by ) = ae(x)
CS 125 Section #12 (More) Probability and Randomized Algorithms 11/24/14 1 Probability First, recall a couple useful facts from last time about probability: Linearity of expectation: E(aX + by ) = ae(x)
CPSC 536N: Randomized Algorithms Term 2. Lecture 2
 CPSC 536N: Randomized Algorithms 2014-15 Term 2 Prof. Nick Harvey Lecture 2 University of British Columbia In this lecture we continue our introduction to randomized algorithms by discussing the Max Cut
CPSC 536N: Randomized Algorithms 2014-15 Term 2 Prof. Nick Harvey Lecture 2 University of British Columbia In this lecture we continue our introduction to randomized algorithms by discussing the Max Cut
Midterm Exam 1 Solution
 EECS 126 Probability and Random Processes University of California, Berkeley: Fall 2015 Kannan Ramchandran September 22, 2015 Midterm Exam 1 Solution Last name First name SID Name of student on your left:
EECS 126 Probability and Random Processes University of California, Berkeley: Fall 2015 Kannan Ramchandran September 22, 2015 Midterm Exam 1 Solution Last name First name SID Name of student on your left:
CS 6820 Fall 2014 Lectures, October 3-20, 2014
 Analysis of Algorithms Linear Programming Notes CS 6820 Fall 2014 Lectures, October 3-20, 2014 1 Linear programming The linear programming (LP) problem is the following optimization problem. We are given
Analysis of Algorithms Linear Programming Notes CS 6820 Fall 2014 Lectures, October 3-20, 2014 1 Linear programming The linear programming (LP) problem is the following optimization problem. We are given
Probability. Lecture Notes. Adolfo J. Rumbos
 Probability Lecture Notes Adolfo J. Rumbos October 20, 204 2 Contents Introduction 5. An example from statistical inference................ 5 2 Probability Spaces 9 2. Sample Spaces and σ fields.....................
Probability Lecture Notes Adolfo J. Rumbos October 20, 204 2 Contents Introduction 5. An example from statistical inference................ 5 2 Probability Spaces 9 2. Sample Spaces and σ fields.....................
EECS 70 Discrete Mathematics and Probability Theory Fall 2015 Walrand/Rao Final
 EECS 70 Discrete Mathematics and Probability Theory Fall 2015 Walrand/Rao Final PRINT Your Name:, (last) SIGN Your Name: (first) PRINT Your Student ID: CIRCLE your exam room: 220 Hearst 230 Hearst 237
EECS 70 Discrete Mathematics and Probability Theory Fall 2015 Walrand/Rao Final PRINT Your Name:, (last) SIGN Your Name: (first) PRINT Your Student ID: CIRCLE your exam room: 220 Hearst 230 Hearst 237
CSE525: Randomized Algorithms and Probabilistic Analysis April 2, Lecture 1
 CSE525: Randomized Algorithms and Probabilistic Analysis April 2, 2013 Lecture 1 Lecturer: Anna Karlin Scribe: Sonya Alexandrova and Eric Lei 1 Introduction The main theme of this class is randomized algorithms.
CSE525: Randomized Algorithms and Probabilistic Analysis April 2, 2013 Lecture 1 Lecturer: Anna Karlin Scribe: Sonya Alexandrova and Eric Lei 1 Introduction The main theme of this class is randomized algorithms.
Module 1. Probability
 Module 1 Probability 1. Introduction In our daily life we come across many processes whose nature cannot be predicted in advance. Such processes are referred to as random processes. The only way to derive
Module 1 Probability 1. Introduction In our daily life we come across many processes whose nature cannot be predicted in advance. Such processes are referred to as random processes. The only way to derive
MARKING A BINARY TREE PROBABILISTIC ANALYSIS OF A RANDOMIZED ALGORITHM
 MARKING A BINARY TREE PROBABILISTIC ANALYSIS OF A RANDOMIZED ALGORITHM XIANG LI Abstract. This paper centers on the analysis of a specific randomized algorithm, a basic random process that involves marking
MARKING A BINARY TREE PROBABILISTIC ANALYSIS OF A RANDOMIZED ALGORITHM XIANG LI Abstract. This paper centers on the analysis of a specific randomized algorithm, a basic random process that involves marking
Lecture 1 : Probabilistic Method
 IITM-CS6845: Theory Jan 04, 01 Lecturer: N.S.Narayanaswamy Lecture 1 : Probabilistic Method Scribe: R.Krithika The probabilistic method is a technique to deal with combinatorial problems by introducing
IITM-CS6845: Theory Jan 04, 01 Lecturer: N.S.Narayanaswamy Lecture 1 : Probabilistic Method Scribe: R.Krithika The probabilistic method is a technique to deal with combinatorial problems by introducing
Week 2. Review of Probability, Random Variables and Univariate Distributions
 Week 2 Review of Probability, Random Variables and Univariate Distributions Probability Probability Probability Motivation What use is Probability Theory? Probability models Basis for statistical inference
Week 2 Review of Probability, Random Variables and Univariate Distributions Probability Probability Probability Motivation What use is Probability Theory? Probability models Basis for statistical inference
RANDOM WALKS AND THE PROBABILITY OF RETURNING HOME
 RANDOM WALKS AND THE PROBABILITY OF RETURNING HOME ELIZABETH G. OMBRELLARO Abstract. This paper is expository in nature. It intuitively explains, using a geometrical and measure theory perspective, why
RANDOM WALKS AND THE PROBABILITY OF RETURNING HOME ELIZABETH G. OMBRELLARO Abstract. This paper is expository in nature. It intuitively explains, using a geometrical and measure theory perspective, why
Lecture 5: January 30
 CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 5: January 30 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 5: January 30 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
MATHEMATICS 154, SPRING 2009 PROBABILITY THEORY Outline #11 (Tail-Sum Theorem, Conditional distribution and expectation)
 MATHEMATICS 154, SPRING 2009 PROBABILITY THEORY Outline #11 (Tail-Sum Theorem, Conditional distribution and expectation) Last modified: March 7, 2009 Reference: PRP, Sections 3.6 and 3.7. 1. Tail-Sum Theorem
MATHEMATICS 154, SPRING 2009 PROBABILITY THEORY Outline #11 (Tail-Sum Theorem, Conditional distribution and expectation) Last modified: March 7, 2009 Reference: PRP, Sections 3.6 and 3.7. 1. Tail-Sum Theorem
MATH 3510: PROBABILITY AND STATS June 15, 2011 MIDTERM EXAM
 MATH 3510: PROBABILITY AND STATS June 15, 2011 MIDTERM EXAM YOUR NAME: KEY: Answers in Blue Show all your work. Answers out of the blue and without any supporting work may receive no credit even if they
MATH 3510: PROBABILITY AND STATS June 15, 2011 MIDTERM EXAM YOUR NAME: KEY: Answers in Blue Show all your work. Answers out of the blue and without any supporting work may receive no credit even if they
PCMI Introduction to Random Matrix Theory Handout # REVIEW OF PROBABILITY THEORY. Chapter 1 - Events and Their Probabilities
 PCMI 207 - Introduction to Random Matrix Theory Handout #2 06.27.207 REVIEW OF PROBABILITY THEORY Chapter - Events and Their Probabilities.. Events as Sets Definition (σ-field). A collection F of subsets
PCMI 207 - Introduction to Random Matrix Theory Handout #2 06.27.207 REVIEW OF PROBABILITY THEORY Chapter - Events and Their Probabilities.. Events as Sets Definition (σ-field). A collection F of subsets
Topic 3: The Expectation of a Random Variable
 Topic 3: The Expectation of a Random Variable Course 003, 2017 Page 0 Expectation of a discrete random variable Definition (Expectation of a discrete r.v.): The expected value (also called the expectation
Topic 3: The Expectation of a Random Variable Course 003, 2017 Page 0 Expectation of a discrete random variable Definition (Expectation of a discrete r.v.): The expected value (also called the expectation
Solutions to Problem Set 4
 UC Berkeley, CS 174: Combinatorics and Discrete Probability (Fall 010 Solutions to Problem Set 4 1. (MU 5.4 In a lecture hall containing 100 people, you consider whether or not there are three people in
UC Berkeley, CS 174: Combinatorics and Discrete Probability (Fall 010 Solutions to Problem Set 4 1. (MU 5.4 In a lecture hall containing 100 people, you consider whether or not there are three people in
Probability and random variables
 Probability and random variables Events A simple event is the outcome of an experiment. For example, the experiment of tossing a coin twice has four possible outcomes: HH, HT, TH, TT. A compound event
Probability and random variables Events A simple event is the outcome of an experiment. For example, the experiment of tossing a coin twice has four possible outcomes: HH, HT, TH, TT. A compound event
CSE 312 Final Review: Section AA
 CSE 312 TAs December 8, 2011 General Information General Information Comprehensive Midterm General Information Comprehensive Midterm Heavily weighted toward material after the midterm Pre-Midterm Material
CSE 312 TAs December 8, 2011 General Information General Information Comprehensive Midterm General Information Comprehensive Midterm Heavily weighted toward material after the midterm Pre-Midterm Material
Review of Probability Theory
 Review of Probability Theory Arian Maleki and Tom Do Stanford University Probability theory is the study of uncertainty Through this class, we will be relying on concepts from probability theory for deriving
Review of Probability Theory Arian Maleki and Tom Do Stanford University Probability theory is the study of uncertainty Through this class, we will be relying on concepts from probability theory for deriving
ACO Comprehensive Exam October 14 and 15, 2013
 1. Computability, Complexity and Algorithms (a) Let G be the complete graph on n vertices, and let c : V (G) V (G) [0, ) be a symmetric cost function. Consider the following closest point heuristic for
1. Computability, Complexity and Algorithms (a) Let G be the complete graph on n vertices, and let c : V (G) V (G) [0, ) be a symmetric cost function. Consider the following closest point heuristic for
Lecture 16. Lectures 1-15 Review
 18.440: Lecture 16 Lectures 1-15 Review Scott Sheffield MIT 1 Outline Counting tricks and basic principles of probability Discrete random variables 2 Outline Counting tricks and basic principles of probability
18.440: Lecture 16 Lectures 1-15 Review Scott Sheffield MIT 1 Outline Counting tricks and basic principles of probability Discrete random variables 2 Outline Counting tricks and basic principles of probability
Discrete Random Variable
 Discrete Random Variable Outcome of a random experiment need not to be a number. We are generally interested in some measurement or numerical attribute of the outcome, rather than the outcome itself. n
Discrete Random Variable Outcome of a random experiment need not to be a number. We are generally interested in some measurement or numerical attribute of the outcome, rather than the outcome itself. n
Discrete Mathematics and Probability Theory Fall 2011 Rao Midterm 2 Solutions
 CS 70 Discrete Mathematics and Probability Theory Fall 20 Rao Midterm 2 Solutions True/False. [24 pts] Circle one of the provided answers please! No negative points will be assigned for incorrect answers.
CS 70 Discrete Mathematics and Probability Theory Fall 20 Rao Midterm 2 Solutions True/False. [24 pts] Circle one of the provided answers please! No negative points will be assigned for incorrect answers.
Lecture Notes 1 Probability and Random Variables. Conditional Probability and Independence. Functions of a Random Variable
 Lecture Notes 1 Probability and Random Variables Probability Spaces Conditional Probability and Independence Random Variables Functions of a Random Variable Generation of a Random Variable Jointly Distributed
Lecture Notes 1 Probability and Random Variables Probability Spaces Conditional Probability and Independence Random Variables Functions of a Random Variable Generation of a Random Variable Jointly Distributed
An analogy from Calculus: limits
 COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
Homework 4 Solution, due July 23
 Homework 4 Solution, due July 23 Random Variables Problem 1. Let X be the random number on a die: from 1 to. (i) What is the distribution of X? (ii) Calculate EX. (iii) Calculate EX 2. (iv) Calculate Var
Homework 4 Solution, due July 23 Random Variables Problem 1. Let X be the random number on a die: from 1 to. (i) What is the distribution of X? (ii) Calculate EX. (iii) Calculate EX 2. (iv) Calculate Var
Handout 1: Mathematical Background
 Handout 1: Mathematical Background Boaz Barak September 18, 2007 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete
Handout 1: Mathematical Background Boaz Barak September 18, 2007 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete
Probability 1 (MATH 11300) lecture slides
 Probability 1 (MATH 11300) lecture slides Márton Balázs School of Mathematics University of Bristol Autumn, 2015 December 16, 2015 To know... http://www.maths.bris.ac.uk/ mb13434/prob1/ m.balazs@bristol.ac.uk
Probability 1 (MATH 11300) lecture slides Márton Balázs School of Mathematics University of Bristol Autumn, 2015 December 16, 2015 To know... http://www.maths.bris.ac.uk/ mb13434/prob1/ m.balazs@bristol.ac.uk
Lecture 2: Random Variables and Expectation
 Econ 514: Probability and Statistics Lecture 2: Random Variables and Expectation Definition of function: Given sets X and Y, a function f with domain X and image Y is a rule that assigns to every x X one
Econ 514: Probability and Statistics Lecture 2: Random Variables and Expectation Definition of function: Given sets X and Y, a function f with domain X and image Y is a rule that assigns to every x X one
Topic 3 Random variables, expectation, and variance, II
 CSE 103: Probability and statistics Fall 2010 Topic 3 Random variables, expectation, and variance, II 3.1 Linearity of expectation If you double each value of X, then you also double its average; that
CSE 103: Probability and statistics Fall 2010 Topic 3 Random variables, expectation, and variance, II 3.1 Linearity of expectation If you double each value of X, then you also double its average; that
