CPSC 536N: Randomized Algorithms Term 2. Lecture 2
|
|
|
- Piers Rose
- 5 years ago
- Views:
Transcription
1 CPSC 536N: Randomized Algorithms Term 2 Prof. Nick Harvey Lecture 2 University of British Columbia In this lecture we continue our introduction to randomized algorithms by discussing the Max Cut problem. We will achieve a non-trivial result for this problem using only some elementary tools of discrete probability. An important technical point that arises is the difference between algorithms that are good in expectation and those that are good with high probability. 1 Example: Max Cut The Max Cut problem is a foundational problem in combinatorial optimization and approximation algorithms; many important techniques have been developed during the study of this problem. It is defined as follows. Let G = (V, E) be an undirected graph. For U V, let δ(u) = { uv E : u U and v U }. The set δ(u) is called the cut determined by vertex set U. The Max Cut problem is to solve max { δ(u) : U V }. This is NP-hard (and in fact was one of the original problems shown to be NP-hard by Karp in his famous 1972 paper), so we cannot hope to solve it exactly. Instead, we will be content to find a cut that is sufficiently large. More precisely, let OPT denote the size of the maximum cut. We want an algorithm for which there exists a factor α > 0 (independent of G) such that the set U output by the algorithm is guaranteed to have δ(u) αopt. If the algorithm is randomized, we want this guarantee to hold with some probability close to 1. Here is a brief summary of what is known about this problem. Folklore: there is an algorithm with α = 1/2. In fact, there are several such algorithms. Goemans and Williamson 1995: there is an algorithm with α = Håstad 2001: no efficient algorithm has α > 16/17, unless P = NP. Khot, Kindler, Mossel, O Donnel and Oleszkiewicz : no efficient algorithm has α > , assuming the Unique Games Conjecture. Khot won the Nevanlinna Prize in 2014 partially for this result. We will give a randomized algorithm achieving α = 1/2. In fact, this algorithm appears in an old paper of Erdos [1]. The algorithm couldn t possibly be any simpler: it simply lets U be a uniformly random subset of V. One can check that this is equivalent to independently adding each vertex to U with probability 1/2. (This relates to the first question in assignment 0.) Note that the algorithm does not even look at the edges of G! Philosophically, this algorithm as trying to find hay in a haystack, where the cuts are the haystack and the near-maximum cuts are the hay. The following claim analyzes this algorithm. 1
2 Claim 1 Let U be the set chosen by the algorithm. Then E [ δ(u) ] OPT/2. Proof: For every edge uv E, let X uv be the indicator random variable which is 1 if uv δ(u). Then [ ] E [ δ(u) ] = E X uv Now we note that = uv E = uv E uv E E [ X uv ] Pr [ X uv = 1 ] (linearity of expectation) Pr [ X uv = 1 ] = Pr [ (u U v U) (u U v U) ] = Pr [ u U v U ] + Pr [ u U v U ] (these are disjoint events) = Pr [ u U ] Pr [ v U ] + Pr [ u U ] Pr [ v U ] (independence) = 1/2. Thus E [ δ(u) ] = E /2 OPT/2, since clearly OPT E. So we have shown that the algorithm outputs a cut whose expected size is large. We might instead prefer a different sort of guarantee: perhaps we d like to know that, with high probability, the algorithm outputs a cut that is large. Mathematically, we have shown that E [ δ(u) ] OPT/2, but perhaps we want to know that Pr [ δ(u) OPT/2 ] is large. To connect these two statements, we need to show that δ(u) is likely to be close to its expectation. 2 Concentration Inequalities One of the most important tasks in analyzing randomized algorithms is to understand what random variables arise and how well they are concentrated. A variable with good concentration is one that is close to its mean with good probability. A concentration inequality is a theorem proving that a random variable has good concentration. Such theorems are also known as tail bounds. 2.1 Markov s inequality This is the simplest concentration inequality. The downside is that it only gives very weak bounds, but the upside is that needs almost no assumptions about the random variable. It is often useful in scenarios where not much concentration is needed, or where the random variable is too complicated to be analyzed by more powerful inequalities. Theorem 2 Let Y be a real-valued random variable that assumes only nonnegative values 1. Then, for all a > 0, Pr [ Y a ] E [ Y ]. a 1 Pedantic detail: we should also assume that E [ Y ] is finite. 2
3 References: Mitzenmacher-Upfal Theorem 3.1, Motwani-Raghavan Theorem 3.2, Wikipedia, Grimmett-Stirzaker Lemma 7.2.7, Durrett Theorem Note that if a E [ Y ] then the right-hand side of the inequality is at least 1, and so the statement is trivial. So Markov s inequality is only useful if a > E [ Y ]. Typically we use Markov s inequality to prove that Y has only a constant probability of exceeding its mean by a constant factor, e.g., Pr [ Y 2 E [ Y ] ] 1/2. Proof: Let X be the indicator random variable that is 1 if Y a. Since Y is non-negative, we have Then X Y/a. (1) Pr [ Y a ] = Pr [ X 1 ] = E [ X ] E [ Y/a ] = E [ Y ], a where the inequality comes from taking the expectation of both sides of (1). Note that Markov s inequality only bounds the right tail of Y, i.e., the probability that Y is much greater than its mean. 2.2 The Reverse Markov inequality In some scenarios, we would also like to bound the probability that Y is much smaller than its mean. Markov s inequality can be used for this purpose if we know an upper-bound on Y. The following result is an immediate corollary of Theorem 2. Corollary 3 Let Y be a random variable that is never larger than B. Then, for all a < B, References: Grimmett-Stirzaker Theorem Pr [ Y a ] E [ B Y ]. B a 2.3 Application to Max Cut Let s now analyze the probability that our randomized algorithm for Max Cut gives a large cut. Let Y = δ(u) and B = E, and note that Y is never larger than B. Fix any ɛ [0, 1/2] and set a = ( 1 2 ɛ) E. By the Reverse Markov inequality, Pr [ δ(u) (1/2 ɛ) E ] E [ E δ(u) ] E (1/2 ɛ) E = E E [ δ(u) ] (1/2 + ɛ) E (linearity of expectation) = ɛ since E [ δ(u) ] = E /2 1 ɛ, where we have used Inequality 2 from the Notes on Convexity Inequalities. This shows that, with probability at least ɛ, the algorithm outputs a set U satisfying δ(u) > (1/2 ɛ) OPT. This statement is quite unsatisfying. If we want a approximation, then we have only shown that the algorithm has probability of succeeding. Next we will show how to increase the probability of success. 3
4 3 Amplification by Independent Trials In many cases where the probability of success is positive but small, we can amplify that probability by perfoming several independent trials and taking the best outcome. We already used this technique in the first lecture to improve the success probability of our equality test. For Max Cut, consider the following algorithm. First it picks several sets U 1,..., U k V, independently and uniformly at random. Let j be the index for which δ(u j ) is largest. The algorithm simply outputs the set U j. (Our initial Max Cut algorithm above did not even look at the edges of the graph, but this new algorithm must look at the edges to compute δ(u j ).) To analyze this algorithm, we wish to argue that δ(u j ) is large. Well, δ(u j ) is small only if all δ(u i ) are small, and this is rather unlikely. Pr [ δ(u i ) (1/2 ɛ) E i = 1,..., k ] = k Pr [ δ(u i ) (1/2 ɛ) E ] i=1 (1 ɛ) k (by our analysis above) e ɛk. (by independence) Here we have used the standard trick 1 + x e x, which is Inequality 1 from the Notes on Convexity Inequalities. Thus, setting k = log(1/δ)/ɛ, we obtain that Pr [ every δ(u i ) (1/2 ɛ) E ] δ. In summary, our new Max Cut algorithm picks k = log(1/δ)/ɛ sets U 1,..., U k, finds the j which maximizes δ(u j ), then outputs U j. With probability at least 1 δ we have Pr [ δ(u j ) (1/2 ɛ) E ]. In this analysis we used the following general fact, which is elementary but often very useful. Claim 4 Consider a random trial in which the probability of success is p. If we perform k mutually independent trials, then Pr [ all failures ] = (1 p) k e pk and therefore Pr [ at least one success ] = 1 (1 p) k 1 e pk. 3.1 Example: Flipping Coins Consider flipping a fair coin. If the coin turns up heads, call this a success. So the probability of success is p = 1/2. By Claim 4, Pr [ at least one heads after k trials ] = 1 1/2 k. This is a true statement, but not all that interesting: it is quite obvious that after k coin flips, the probability of seeing at least one head is very close to 1. Note that the expected number of heads is k/2. Can t we say that there are probably close to k/2 heads? This takes us beyond the subject of amplification and into a discussion of the binomial distribution. 4
5 4 The binomial distribution Again, let us flip a fair coin k times and let X be the number of heads seen. Then X has the binomial distribution. So ( ) k Pr [ exactly i heads ] = 2 k. i How can we show that X is probably close to its expected value (which is k/2). Well, the probability of X being small is: Pr [ at most i heads ] = ( ) k 2 k. (2) j Here the meaning of small depends on the choice of i. For what values of i is this sum small? Unfortunately the sum is a bit too complicated to get a feel for its magnitude. Can we simplify the expression so it s easier to see what s going on? As far as I know, this sum does not have a simple closed-form expression. Instead, can we usefully approximate that sum? It would be great to have a provable upper bound for the sum that is simple, useful and asymptotically nearly tight. The Chernoff bound, which we discuss in Section 5, is a very general and powerful tool for analyzing tails of probability distributions, and it gives a fantastic bound on (2). But first, to motivate the bound that we will obtain, let us describe some interesting behavior of binomial distributions. 0 j i 4.1 Different behavior in different regimes In most introductory courses on probability theory, one often encounters statements that describe the limiting behavior of the binomial distribution. For example: Fact 5 Let X be a binomially distributed random variable with parameters n and p. (That is, X gives the number of successes in n independent trials where each trial succeeds with probability p.) As n gets large while p remains fixed, the distribution of X is well approximated by the normal distribution with mean np and variance np(1 p). References: Durrett Theorem and Example The following plot shows the binomial distribution for n = 20 and p = 1/2 in red and the corresponding normal approximation in blue. 5
6 However the binomial distribution has qualitatively different behavior when p is very small. Fact 6 Let X be a binomially distributed random variable with parameters n and p. As n gets large while np remains fixed, the distribution of X is well approximated by the Poisson distribution with parameter λ = np. References: Mitzenmacher-Upfal Theorem 5.5, Durrett Theorem The following plot shows the binomial distribution for n = 50 and p = 4/n in red and the corresponding Poisson approximation in blue. Note that the red plot is quite asymmetric, so we would not expect a normal distribution (which is symmetric) to approximate it well. Ideally would like an upper bound on (2) which works well for all ranges of parameters, and captures the phenomena described in Fact 5 and Fact 6. Remarkably, the Chernoff bound is able to capture both of these phenomena. 6
7 5 The Chernoff Bound The Chernoff bound is used to bound the tails of the distribution for a sum of independent random variables, under a few mild assumptions. Since binomial random variables are sums of independent Bernoulli random variables, it can be used to bound (2). Not only is the Chernoff bound itself very useful, but its proof techniques are very general and can be applied in a wide variety of settings. The Chernoff bound is by far the most useful tool in randomized algorithms. Numerous papers on randomized algorithms have only three ingredients: Chernoff bounds, union bounds and cleverness. Of course, there is an art in being clever and finding the right way to assemble these ingredients! 5.1 Formal Statement Let X 1,..., X n be independent random variables such that X i always lies in the interval [0, 1]. Define X = n i=1 X i and p i = E [ X i ]. Let µ min i E [ X i ] µ max. Theorem 7 For all δ > 0, Pr [ X (1 + δ)µ max ] Pr [ X (1 δ)µ min ] (a) (c) ( ) e δ µmax (1+δ) 1+δ ( e δ (1 δ) 1 δ ) µmin (b) e δ2 µ max/3 (if δ 1) e (1+δ) ln(1+δ)µmax/4 (if δ 1) e δµmax/3 (if δ 1) (d) e δ2 µ min /2. Inequalities (c) and (d) are only valid for δ < 1, but Pr [ X (1 δ)µ min ] = 0 if δ > 1. Remarks. All of these bounds are useful in different scenarios. In inequality (b), the cases δ 1 and δ > 1 are different due to the different phenomena illustrated in Facts 5 and 6. Historical remark. Chernoff actually only considered the case in which the X i random variables are identically distributed. The more general form stated here is due to Hoeffding. References [1] P. Erdős. Gráfok páros körüljárású részgráfjairól (On bipartite subgraphs of graphs, in Hungarian). Mat. Lapok, 18: ,
CSE 548: Analysis of Algorithms. Lectures 18, 19, 20 & 21 ( Randomized Algorithms & High Probability Bounds )
 CSE 548: Analysis of Algorithms Lectures 18, 19, 20 & 21 ( Randomized Algorithms & High Probability Bounds ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Fall 2012 Markov s Inequality
CSE 548: Analysis of Algorithms Lectures 18, 19, 20 & 21 ( Randomized Algorithms & High Probability Bounds ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Fall 2012 Markov s Inequality
CPSC 536N: Randomized Algorithms Term 2. Lecture 9
 CPSC 536N: Randomized Algorithms 2011-12 Term 2 Prof. Nick Harvey Lecture 9 University of British Columbia 1 Polynomial Identity Testing In the first lecture we discussed the problem of testing equality
CPSC 536N: Randomized Algorithms 2011-12 Term 2 Prof. Nick Harvey Lecture 9 University of British Columbia 1 Polynomial Identity Testing In the first lecture we discussed the problem of testing equality
Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( )
![Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( ) Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( )](/thumbs/95/125074181.jpg) Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr Pr = Pr Pr Pr() Pr Pr. We are given three coins and are told that two of the coins are fair and the
Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr Pr = Pr Pr Pr() Pr Pr. We are given three coins and are told that two of the coins are fair and the
Machine Learning Theory Lecture 4
 Machine Learning Theory Lecture 4 Nicholas Harvey October 9, 018 1 Basic Probability One of the first concentration bounds that you learn in probability theory is Markov s inequality. It bounds the right-tail
Machine Learning Theory Lecture 4 Nicholas Harvey October 9, 018 1 Basic Probability One of the first concentration bounds that you learn in probability theory is Markov s inequality. It bounds the right-tail
Lecture 2 Sep 5, 2017
 CS 388R: Randomized Algorithms Fall 2017 Lecture 2 Sep 5, 2017 Prof. Eric Price Scribe: V. Orestis Papadigenopoulos and Patrick Rall NOTE: THESE NOTES HAVE NOT BEEN EDITED OR CHECKED FOR CORRECTNESS 1
CS 388R: Randomized Algorithms Fall 2017 Lecture 2 Sep 5, 2017 Prof. Eric Price Scribe: V. Orestis Papadigenopoulos and Patrick Rall NOTE: THESE NOTES HAVE NOT BEEN EDITED OR CHECKED FOR CORRECTNESS 1
Randomized Algorithms
 Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
princeton univ. F 17 cos 521: Advanced Algorithm Design Lecture 6: Provable Approximation via Linear Programming
 princeton univ. F 17 cos 521: Advanced Algorithm Design Lecture 6: Provable Approximation via Linear Programming Lecturer: Matt Weinberg Scribe: Sanjeev Arora One of the running themes in this course is
princeton univ. F 17 cos 521: Advanced Algorithm Design Lecture 6: Provable Approximation via Linear Programming Lecturer: Matt Weinberg Scribe: Sanjeev Arora One of the running themes in this course is
Lecture 5: January 30
 CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 5: January 30 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 5: January 30 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
11.1 Set Cover ILP formulation of set cover Deterministic rounding
 CS787: Advanced Algorithms Lecture 11: Randomized Rounding, Concentration Bounds In this lecture we will see some more examples of approximation algorithms based on LP relaxations. This time we will use
CS787: Advanced Algorithms Lecture 11: Randomized Rounding, Concentration Bounds In this lecture we will see some more examples of approximation algorithms based on LP relaxations. This time we will use
CSE548, AMS542: Analysis of Algorithms, Fall 2016 Date: Nov 30. Final In-Class Exam. ( 7:05 PM 8:20 PM : 75 Minutes )
 CSE548, AMS542: Analysis of Algorithms, Fall 2016 Date: Nov 30 Final In-Class Exam ( 7:05 PM 8:20 PM : 75 Minutes ) This exam will account for either 15% or 30% of your overall grade depending on your
CSE548, AMS542: Analysis of Algorithms, Fall 2016 Date: Nov 30 Final In-Class Exam ( 7:05 PM 8:20 PM : 75 Minutes ) This exam will account for either 15% or 30% of your overall grade depending on your
The first bound is the strongest, the other two bounds are often easier to state and compute. Proof: Applying Markov's inequality, for any >0 we have
 The first bound is the strongest, the other two bounds are often easier to state and compute Proof: Applying Markov's inequality, for any >0 we have Pr (1 + ) = Pr For any >0, we can set = ln 1+ (4.4.1):
The first bound is the strongest, the other two bounds are often easier to state and compute Proof: Applying Markov's inequality, for any >0 we have Pr (1 + ) = Pr For any >0, we can set = ln 1+ (4.4.1):
Example 1. The sample space of an experiment where we flip a pair of coins is denoted by:
 Chapter 8 Probability 8. Preliminaries Definition (Sample Space). A Sample Space, Ω, is the set of all possible outcomes of an experiment. Such a sample space is considered discrete if Ω has finite cardinality.
Chapter 8 Probability 8. Preliminaries Definition (Sample Space). A Sample Space, Ω, is the set of all possible outcomes of an experiment. Such a sample space is considered discrete if Ω has finite cardinality.
Notes 6 : First and second moment methods
 Notes 6 : First and second moment methods Math 733-734: Theory of Probability Lecturer: Sebastien Roch References: [Roc, Sections 2.1-2.3]. Recall: THM 6.1 (Markov s inequality) Let X be a non-negative
Notes 6 : First and second moment methods Math 733-734: Theory of Probability Lecturer: Sebastien Roch References: [Roc, Sections 2.1-2.3]. Recall: THM 6.1 (Markov s inequality) Let X be a non-negative
Lecture 5: Probabilistic tools and Applications II
 T-79.7003: Graphs and Networks Fall 2013 Lecture 5: Probabilistic tools and Applications II Lecturer: Charalampos E. Tsourakakis Oct. 11, 2013 5.1 Overview In the first part of today s lecture we will
T-79.7003: Graphs and Networks Fall 2013 Lecture 5: Probabilistic tools and Applications II Lecturer: Charalampos E. Tsourakakis Oct. 11, 2013 5.1 Overview In the first part of today s lecture we will
CS6999 Probabilistic Methods in Integer Programming Randomized Rounding Andrew D. Smith April 2003
 CS6999 Probabilistic Methods in Integer Programming Randomized Rounding April 2003 Overview 2 Background Randomized Rounding Handling Feasibility Derandomization Advanced Techniques Integer Programming
CS6999 Probabilistic Methods in Integer Programming Randomized Rounding April 2003 Overview 2 Background Randomized Rounding Handling Feasibility Derandomization Advanced Techniques Integer Programming
Assignment 4: Solutions
 Math 340: Discrete Structures II Assignment 4: Solutions. Random Walks. Consider a random walk on an connected, non-bipartite, undirected graph G. Show that, in the long run, the walk will traverse each
Math 340: Discrete Structures II Assignment 4: Solutions. Random Walks. Consider a random walk on an connected, non-bipartite, undirected graph G. Show that, in the long run, the walk will traverse each
Convex and Semidefinite Programming for Approximation
 Convex and Semidefinite Programming for Approximation We have seen linear programming based methods to solve NP-hard problems. One perspective on this is that linear programming is a meta-method since
Convex and Semidefinite Programming for Approximation We have seen linear programming based methods to solve NP-hard problems. One perspective on this is that linear programming is a meta-method since
Approximation & Complexity
 Summer school on semidefinite optimization Approximation & Complexity David Steurer Cornell University Part 1 September 6, 2012 Overview Part 1 Unique Games Conjecture & Basic SDP Part 2 SDP Hierarchies:
Summer school on semidefinite optimization Approximation & Complexity David Steurer Cornell University Part 1 September 6, 2012 Overview Part 1 Unique Games Conjecture & Basic SDP Part 2 SDP Hierarchies:
Lecture 20: LP Relaxation and Approximation Algorithms. 1 Introduction. 2 Vertex Cover problem. CSCI-B609: A Theorist s Toolkit, Fall 2016 Nov 8
 CSCI-B609: A Theorist s Toolkit, Fall 2016 Nov 8 Lecture 20: LP Relaxation and Approximation Algorithms Lecturer: Yuan Zhou Scribe: Syed Mahbub Hafiz 1 Introduction When variables of constraints of an
CSCI-B609: A Theorist s Toolkit, Fall 2016 Nov 8 Lecture 20: LP Relaxation and Approximation Algorithms Lecturer: Yuan Zhou Scribe: Syed Mahbub Hafiz 1 Introduction When variables of constraints of an
Lecture 18: Inapproximability of MAX-3-SAT
 CS 880: Advanced Complexity Theory 3/7/2008 Lecture 18: Inapproximability of MAX-3-SAT Instructor: Dieter van Melkebeek Scribe: Jeff Kinne In this lecture we prove a tight inapproximability result for
CS 880: Advanced Complexity Theory 3/7/2008 Lecture 18: Inapproximability of MAX-3-SAT Instructor: Dieter van Melkebeek Scribe: Jeff Kinne In this lecture we prove a tight inapproximability result for
Chernoff Bounds. Theme: try to show that it is unlikely a random variable X is far away from its expectation.
 Chernoff Bounds Theme: try to show that it is unlikely a random variable X is far away from its expectation. The more you know about X, the better the bound you obtain. Markov s inequality: use E[X ] Chebyshev
Chernoff Bounds Theme: try to show that it is unlikely a random variable X is far away from its expectation. The more you know about X, the better the bound you obtain. Markov s inequality: use E[X ] Chebyshev
Approximation algorithm for Max Cut with unit weights
 Definition Max Cut Definition: Given an undirected graph G=(V, E), find a partition of V into two subsets A, B so as to maximize the number of edges having one endpoint in A and the other in B. Definition:
Definition Max Cut Definition: Given an undirected graph G=(V, E), find a partition of V into two subsets A, B so as to maximize the number of edges having one endpoint in A and the other in B. Definition:
Provable Approximation via Linear Programming
 Chapter 7 Provable Approximation via Linear Programming One of the running themes in this course is the notion of approximate solutions. Of course, this notion is tossed around a lot in applied work: whenever
Chapter 7 Provable Approximation via Linear Programming One of the running themes in this course is the notion of approximate solutions. Of course, this notion is tossed around a lot in applied work: whenever
Tail Inequalities. The Chernoff bound works for random variables that are a sum of indicator variables with the same distribution (Bernoulli trials).
 Tail Inequalities William Hunt Lane Department of Computer Science and Electrical Engineering, West Virginia University, Morgantown, WV William.Hunt@mail.wvu.edu Introduction In this chapter, we are interested
Tail Inequalities William Hunt Lane Department of Computer Science and Electrical Engineering, West Virginia University, Morgantown, WV William.Hunt@mail.wvu.edu Introduction In this chapter, we are interested
Lecture 19: Interactive Proofs and the PCP Theorem
 Lecture 19: Interactive Proofs and the PCP Theorem Valentine Kabanets November 29, 2016 1 Interactive Proofs In this model, we have an all-powerful Prover (with unlimited computational prover) and a polytime
Lecture 19: Interactive Proofs and the PCP Theorem Valentine Kabanets November 29, 2016 1 Interactive Proofs In this model, we have an all-powerful Prover (with unlimited computational prover) and a polytime
An Algorithmist s Toolkit September 24, Lecture 5
 8.49 An Algorithmist s Toolkit September 24, 29 Lecture 5 Lecturer: Jonathan Kelner Scribe: Shaunak Kishore Administrivia Two additional resources on approximating the permanent Jerrum and Sinclair s original
8.49 An Algorithmist s Toolkit September 24, 29 Lecture 5 Lecturer: Jonathan Kelner Scribe: Shaunak Kishore Administrivia Two additional resources on approximating the permanent Jerrum and Sinclair s original
Errata: First Printing of Mitzenmacher/Upfal Probability and Computing
 Errata: First Printing of Mitzenmacher/Upfal Probability and Computing Michael Mitzenmacher and Eli Upfal October 10, 2006 We would like to thank the many of you who have bought our book, and we would
Errata: First Printing of Mitzenmacher/Upfal Probability and Computing Michael Mitzenmacher and Eli Upfal October 10, 2006 We would like to thank the many of you who have bought our book, and we would
CS261: A Second Course in Algorithms Lecture #18: Five Essential Tools for the Analysis of Randomized Algorithms
 CS261: A Second Course in Algorithms Lecture #18: Five Essential Tools for the Analysis of Randomized Algorithms Tim Roughgarden March 3, 2016 1 Preamble In CS109 and CS161, you learned some tricks of
CS261: A Second Course in Algorithms Lecture #18: Five Essential Tools for the Analysis of Randomized Algorithms Tim Roughgarden March 3, 2016 1 Preamble In CS109 and CS161, you learned some tricks of
CS155: Probability and Computing: Randomized Algorithms and Probabilistic Analysis
 CS155: Probability and Computing: Randomized Algorithms and Probabilistic Analysis Eli Upfal Eli Upfal@brown.edu Office: 319 TA s: Lorenzo De Stefani and Sorin Vatasoiu cs155tas@cs.brown.edu It is remarkable
CS155: Probability and Computing: Randomized Algorithms and Probabilistic Analysis Eli Upfal Eli Upfal@brown.edu Office: 319 TA s: Lorenzo De Stefani and Sorin Vatasoiu cs155tas@cs.brown.edu It is remarkable
Lectures 6: Degree Distributions and Concentration Inequalities
 University of Washington Lecturer: Abraham Flaxman/Vahab S Mirrokni CSE599m: Algorithms and Economics of Networks April 13 th, 007 Scribe: Ben Birnbaum Lectures 6: Degree Distributions and Concentration
University of Washington Lecturer: Abraham Flaxman/Vahab S Mirrokni CSE599m: Algorithms and Economics of Networks April 13 th, 007 Scribe: Ben Birnbaum Lectures 6: Degree Distributions and Concentration
Lecture 16: Constraint Satisfaction Problems
 A Theorist s Toolkit (CMU 18-859T, Fall 2013) Lecture 16: Constraint Satisfaction Problems 10/30/2013 Lecturer: Ryan O Donnell Scribe: Neal Barcelo 1 Max-Cut SDP Approximation Recall the Max-Cut problem
A Theorist s Toolkit (CMU 18-859T, Fall 2013) Lecture 16: Constraint Satisfaction Problems 10/30/2013 Lecturer: Ryan O Donnell Scribe: Neal Barcelo 1 Max-Cut SDP Approximation Recall the Max-Cut problem
3 Multiple Discrete Random Variables
 3 Multiple Discrete Random Variables 3.1 Joint densities Suppose we have a probability space (Ω, F,P) and now we have two discrete random variables X and Y on it. They have probability mass functions f
3 Multiple Discrete Random Variables 3.1 Joint densities Suppose we have a probability space (Ω, F,P) and now we have two discrete random variables X and Y on it. They have probability mass functions f
Lower Bounds for Testing Bipartiteness in Dense Graphs
 Lower Bounds for Testing Bipartiteness in Dense Graphs Andrej Bogdanov Luca Trevisan Abstract We consider the problem of testing bipartiteness in the adjacency matrix model. The best known algorithm, due
Lower Bounds for Testing Bipartiteness in Dense Graphs Andrej Bogdanov Luca Trevisan Abstract We consider the problem of testing bipartiteness in the adjacency matrix model. The best known algorithm, due
Notes on Discrete Probability
 Columbia University Handout 3 W4231: Analysis of Algorithms September 21, 1999 Professor Luca Trevisan Notes on Discrete Probability The following notes cover, mostly without proofs, the basic notions
Columbia University Handout 3 W4231: Analysis of Algorithms September 21, 1999 Professor Luca Trevisan Notes on Discrete Probability The following notes cover, mostly without proofs, the basic notions
PCP Course; Lectures 1, 2
 PCP Course; Lectures 1, 2 Mario Szegedy September 10, 2011 Easy and Hard Problems Easy: Polynomial Time 5n; n 2 ; 4n 3 + n Hard: Super-polynomial Time n log n ; 2 n ; n! Proving that a problem is easy:
PCP Course; Lectures 1, 2 Mario Szegedy September 10, 2011 Easy and Hard Problems Easy: Polynomial Time 5n; n 2 ; 4n 3 + n Hard: Super-polynomial Time n log n ; 2 n ; n! Proving that a problem is easy:
X = X X n, + X 2
 CS 70 Discrete Mathematics for CS Fall 2003 Wagner Lecture 22 Variance Question: At each time step, I flip a fair coin. If it comes up Heads, I walk one step to the right; if it comes up Tails, I walk
CS 70 Discrete Mathematics for CS Fall 2003 Wagner Lecture 22 Variance Question: At each time step, I flip a fair coin. If it comes up Heads, I walk one step to the right; if it comes up Tails, I walk
Homework 4 Solutions
 CS 174: Combinatorics and Discrete Probability Fall 01 Homework 4 Solutions Problem 1. (Exercise 3.4 from MU 5 points) Recall the randomized algorithm discussed in class for finding the median of a set
CS 174: Combinatorics and Discrete Probability Fall 01 Homework 4 Solutions Problem 1. (Exercise 3.4 from MU 5 points) Recall the randomized algorithm discussed in class for finding the median of a set
Lecture 18: March 15
 CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 18: March 15 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They may
CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 18: March 15 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They may
Discrete Mathematics
 Discrete Mathematics Workshop Organized by: ACM Unit, ISI Tutorial-1 Date: 05.07.2017 (Q1) Given seven points in a triangle of unit area, prove that three of them form a triangle of area not exceeding
Discrete Mathematics Workshop Organized by: ACM Unit, ISI Tutorial-1 Date: 05.07.2017 (Q1) Given seven points in a triangle of unit area, prove that three of them form a triangle of area not exceeding
Learning symmetric non-monotone submodular functions
 Learning symmetric non-monotone submodular functions Maria-Florina Balcan Georgia Institute of Technology ninamf@cc.gatech.edu Nicholas J. A. Harvey University of British Columbia nickhar@cs.ubc.ca Satoru
Learning symmetric non-monotone submodular functions Maria-Florina Balcan Georgia Institute of Technology ninamf@cc.gatech.edu Nicholas J. A. Harvey University of British Columbia nickhar@cs.ubc.ca Satoru
CS 6820 Fall 2014 Lectures, October 3-20, 2014
 Analysis of Algorithms Linear Programming Notes CS 6820 Fall 2014 Lectures, October 3-20, 2014 1 Linear programming The linear programming (LP) problem is the following optimization problem. We are given
Analysis of Algorithms Linear Programming Notes CS 6820 Fall 2014 Lectures, October 3-20, 2014 1 Linear programming The linear programming (LP) problem is the following optimization problem. We are given
Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds
 Randomized Algorithms Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized
Randomized Algorithms Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized
Graph Theory. Thomas Bloom. February 6, 2015
 Graph Theory Thomas Bloom February 6, 2015 1 Lecture 1 Introduction A graph (for the purposes of these lectures) is a finite set of vertices, some of which are connected by a single edge. Most importantly,
Graph Theory Thomas Bloom February 6, 2015 1 Lecture 1 Introduction A graph (for the purposes of these lectures) is a finite set of vertices, some of which are connected by a single edge. Most importantly,
More Approximation Algorithms
 CS 473: Algorithms, Spring 2018 More Approximation Algorithms Lecture 25 April 26, 2018 Most slides are courtesy Prof. Chekuri Ruta (UIUC) CS473 1 Spring 2018 1 / 28 Formal definition of approximation
CS 473: Algorithms, Spring 2018 More Approximation Algorithms Lecture 25 April 26, 2018 Most slides are courtesy Prof. Chekuri Ruta (UIUC) CS473 1 Spring 2018 1 / 28 Formal definition of approximation
COMP2610/COMP Information Theory
 COMP2610/COMP6261 - Information Theory Lecture 9: Probabilistic Inequalities Mark Reid and Aditya Menon Research School of Computer Science The Australian National University August 19th, 2014 Mark Reid
COMP2610/COMP6261 - Information Theory Lecture 9: Probabilistic Inequalities Mark Reid and Aditya Menon Research School of Computer Science The Australian National University August 19th, 2014 Mark Reid
What Computers Can Compute (Approximately) David P. Williamson TU Chemnitz 9 June 2011
 What Computers Can Compute (Approximately) David P. Williamson TU Chemnitz 9 June 2011 Outline The 1930s-40s: What can computers compute? The 1960s-70s: What can computers compute efficiently? The 1990s-:
What Computers Can Compute (Approximately) David P. Williamson TU Chemnitz 9 June 2011 Outline The 1930s-40s: What can computers compute? The 1960s-70s: What can computers compute efficiently? The 1990s-:
Lecture 4: Probability and Discrete Random Variables
 Error Correcting Codes: Combinatorics, Algorithms and Applications (Fall 2007) Lecture 4: Probability and Discrete Random Variables Wednesday, January 21, 2009 Lecturer: Atri Rudra Scribe: Anonymous 1
Error Correcting Codes: Combinatorics, Algorithms and Applications (Fall 2007) Lecture 4: Probability and Discrete Random Variables Wednesday, January 21, 2009 Lecturer: Atri Rudra Scribe: Anonymous 1
Approximating MAX-E3LIN is NP-Hard
 Approximating MAX-E3LIN is NP-Hard Evan Chen May 4, 2016 This lecture focuses on the MAX-E3LIN problem. We prove that approximating it is NP-hard by a reduction from LABEL-COVER. 1 Introducing MAX-E3LIN
Approximating MAX-E3LIN is NP-Hard Evan Chen May 4, 2016 This lecture focuses on the MAX-E3LIN problem. We prove that approximating it is NP-hard by a reduction from LABEL-COVER. 1 Introducing MAX-E3LIN
Lecture 10 February 4, 2013
 UBC CPSC 536N: Sparse Approximations Winter 2013 Prof Nick Harvey Lecture 10 February 4, 2013 Scribe: Alexandre Fréchette This lecture is about spanning trees and their polyhedral representation Throughout
UBC CPSC 536N: Sparse Approximations Winter 2013 Prof Nick Harvey Lecture 10 February 4, 2013 Scribe: Alexandre Fréchette This lecture is about spanning trees and their polyhedral representation Throughout
Near-Optimal Algorithms for Maximum Constraint Satisfaction Problems
 Near-Optimal Algorithms for Maximum Constraint Satisfaction Problems Moses Charikar Konstantin Makarychev Yury Makarychev Princeton University Abstract In this paper we present approximation algorithms
Near-Optimal Algorithms for Maximum Constraint Satisfaction Problems Moses Charikar Konstantin Makarychev Yury Makarychev Princeton University Abstract In this paper we present approximation algorithms
Probability reminders
 CS246 Winter 204 Mining Massive Data Sets Probability reminders Sammy El Ghazzal selghazz@stanfordedu Disclaimer These notes may contain typos, mistakes or confusing points Please contact the author so
CS246 Winter 204 Mining Massive Data Sets Probability reminders Sammy El Ghazzal selghazz@stanfordedu Disclaimer These notes may contain typos, mistakes or confusing points Please contact the author so
Lecture 13 (Part 2): Deviation from mean: Markov s inequality, variance and its properties, Chebyshev s inequality
 Lecture 13 (Part 2): Deviation from mean: Markov s inequality, variance and its properties, Chebyshev s inequality Discrete Structures II (Summer 2018) Rutgers University Instructor: Abhishek Bhrushundi
Lecture 13 (Part 2): Deviation from mean: Markov s inequality, variance and its properties, Chebyshev s inequality Discrete Structures II (Summer 2018) Rutgers University Instructor: Abhishek Bhrushundi
Approximating Submodular Functions. Nick Harvey University of British Columbia
 Approximating Submodular Functions Nick Harvey University of British Columbia Approximating Submodular Functions Part 1 Nick Harvey University of British Columbia Department of Computer Science July 11th,
Approximating Submodular Functions Nick Harvey University of British Columbia Approximating Submodular Functions Part 1 Nick Harvey University of British Columbia Department of Computer Science July 11th,
Lecture 5. Shearer s Lemma
 Stanford University Spring 2016 Math 233: Non-constructive methods in combinatorics Instructor: Jan Vondrák Lecture date: April 6, 2016 Scribe: László Miklós Lovász Lecture 5. Shearer s Lemma 5.1 Introduction
Stanford University Spring 2016 Math 233: Non-constructive methods in combinatorics Instructor: Jan Vondrák Lecture date: April 6, 2016 Scribe: László Miklós Lovász Lecture 5. Shearer s Lemma 5.1 Introduction
Price of Stability in Survivable Network Design
 Noname manuscript No. (will be inserted by the editor) Price of Stability in Survivable Network Design Elliot Anshelevich Bugra Caskurlu Received: January 2010 / Accepted: Abstract We study the survivable
Noname manuscript No. (will be inserted by the editor) Price of Stability in Survivable Network Design Elliot Anshelevich Bugra Caskurlu Received: January 2010 / Accepted: Abstract We study the survivable
POISSON PROCESSES 1. THE LAW OF SMALL NUMBERS
 POISSON PROCESSES 1. THE LAW OF SMALL NUMBERS 1.1. The Rutherford-Chadwick-Ellis Experiment. About 90 years ago Ernest Rutherford and his collaborators at the Cavendish Laboratory in Cambridge conducted
POISSON PROCESSES 1. THE LAW OF SMALL NUMBERS 1.1. The Rutherford-Chadwick-Ellis Experiment. About 90 years ago Ernest Rutherford and his collaborators at the Cavendish Laboratory in Cambridge conducted
Handout 1: Mathematical Background
 Handout 1: Mathematical Background Boaz Barak September 18, 2007 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete
Handout 1: Mathematical Background Boaz Barak September 18, 2007 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete
On the efficient approximability of constraint satisfaction problems
 On the efficient approximability of constraint satisfaction problems July 13, 2007 My world Max-CSP Efficient computation. P Polynomial time BPP Probabilistic Polynomial time (still efficient) NP Non-deterministic
On the efficient approximability of constraint satisfaction problems July 13, 2007 My world Max-CSP Efficient computation. P Polynomial time BPP Probabilistic Polynomial time (still efficient) NP Non-deterministic
Lecture 10. Semidefinite Programs and the Max-Cut Problem Max Cut
 Lecture 10 Semidefinite Programs and the Max-Cut Problem In this class we will finally introduce the content from the second half of the course title, Semidefinite Programs We will first motivate the discussion
Lecture 10 Semidefinite Programs and the Max-Cut Problem In this class we will finally introduce the content from the second half of the course title, Semidefinite Programs We will first motivate the discussion
Lecture 17 (Nov 3, 2011 ): Approximation via rounding SDP: Max-Cut
 CMPUT 675: Approximation Algorithms Fall 011 Lecture 17 (Nov 3, 011 ): Approximation via rounding SDP: Max-Cut Lecturer: Mohammad R. Salavatipour Scribe: based on older notes 17.1 Approximation Algorithm
CMPUT 675: Approximation Algorithms Fall 011 Lecture 17 (Nov 3, 011 ): Approximation via rounding SDP: Max-Cut Lecturer: Mohammad R. Salavatipour Scribe: based on older notes 17.1 Approximation Algorithm
Unique Games and Small Set Expansion
 Proof, beliefs, and algorithms through the lens of sum-of-squares 1 Unique Games and Small Set Expansion The Unique Games Conjecture (UGC) (Khot [2002]) states that for every ɛ > 0 there is some finite
Proof, beliefs, and algorithms through the lens of sum-of-squares 1 Unique Games and Small Set Expansion The Unique Games Conjecture (UGC) (Khot [2002]) states that for every ɛ > 0 there is some finite
Randomized Complexity Classes; RP
 Randomized Complexity Classes; RP Let N be a polynomial-time precise NTM that runs in time p(n) and has 2 nondeterministic choices at each step. N is a polynomial Monte Carlo Turing machine for a language
Randomized Complexity Classes; RP Let N be a polynomial-time precise NTM that runs in time p(n) and has 2 nondeterministic choices at each step. N is a polynomial Monte Carlo Turing machine for a language
Some Open Problems in Approximation Algorithms
 Some Open Problems in Approximation Algorithms David P. Williamson School of Operations Research and Information Engineering Cornell University November 2, 2010 Egerváry Research Group on Combinatorial
Some Open Problems in Approximation Algorithms David P. Williamson School of Operations Research and Information Engineering Cornell University November 2, 2010 Egerváry Research Group on Combinatorial
Foundations of Machine Learning and Data Science. Lecturer: Avrim Blum Lecture 9: October 7, 2015
 10-806 Foundations of Machine Learning and Data Science Lecturer: Avrim Blum Lecture 9: October 7, 2015 1 Computational Hardness of Learning Today we will talk about some computational hardness results
10-806 Foundations of Machine Learning and Data Science Lecturer: Avrim Blum Lecture 9: October 7, 2015 1 Computational Hardness of Learning Today we will talk about some computational hardness results
Lecture 7: February 6
 CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 7: February 6 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 7: February 6 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
Some Open Problems in Approximation Algorithms
 Some Open Problems in Approximation Algorithms David P. Williamson School of Operations Research and Information Engineering Cornell University February 28, 2011 University of Bonn Bonn, Germany David
Some Open Problems in Approximation Algorithms David P. Williamson School of Operations Research and Information Engineering Cornell University February 28, 2011 University of Bonn Bonn, Germany David
A An Overview of Complexity Theory for the Algorithm Designer
 A An Overview of Complexity Theory for the Algorithm Designer A.1 Certificates and the class NP A decision problem is one whose answer is either yes or no. Two examples are: SAT: Given a Boolean formula
A An Overview of Complexity Theory for the Algorithm Designer A.1 Certificates and the class NP A decision problem is one whose answer is either yes or no. Two examples are: SAT: Given a Boolean formula
Lecture 6,7 (Sept 27 and 29, 2011 ): Bin Packing, MAX-SAT
 ,7 CMPUT 675: Approximation Algorithms Fall 2011 Lecture 6,7 (Sept 27 and 29, 2011 ): Bin Pacing, MAX-SAT Lecturer: Mohammad R. Salavatipour Scribe: Weitian Tong 6.1 Bin Pacing Problem Recall the bin pacing
,7 CMPUT 675: Approximation Algorithms Fall 2011 Lecture 6,7 (Sept 27 and 29, 2011 ): Bin Pacing, MAX-SAT Lecturer: Mohammad R. Salavatipour Scribe: Weitian Tong 6.1 Bin Pacing Problem Recall the bin pacing
Preliminaries and Complexity Theory
 Preliminaries and Complexity Theory Oleksandr Romanko CAS 746 - Advanced Topics in Combinatorial Optimization McMaster University, January 16, 2006 Introduction Book structure: 2 Part I Linear Algebra
Preliminaries and Complexity Theory Oleksandr Romanko CAS 746 - Advanced Topics in Combinatorial Optimization McMaster University, January 16, 2006 Introduction Book structure: 2 Part I Linear Algebra
Lecture 13 March 7, 2017
 CS 224: Advanced Algorithms Spring 2017 Prof. Jelani Nelson Lecture 13 March 7, 2017 Scribe: Hongyao Ma Today PTAS/FPTAS/FPRAS examples PTAS: knapsack FPTAS: knapsack FPRAS: DNF counting Approximation
CS 224: Advanced Algorithms Spring 2017 Prof. Jelani Nelson Lecture 13 March 7, 2017 Scribe: Hongyao Ma Today PTAS/FPTAS/FPRAS examples PTAS: knapsack FPTAS: knapsack FPRAS: DNF counting Approximation
Lecture 24: April 12
 CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 24: April 12 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 24: April 12 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
Aditya Bhaskara CS 5968/6968, Lecture 1: Introduction and Review 12 January 2016
 Lecture 1: Introduction and Review We begin with a short introduction to the course, and logistics. We then survey some basics about approximation algorithms and probability. We also introduce some of
Lecture 1: Introduction and Review We begin with a short introduction to the course, and logistics. We then survey some basics about approximation algorithms and probability. We also introduce some of
Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Note 14
 CS 70 Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Note 14 Introduction One of the key properties of coin flips is independence: if you flip a fair coin ten times and get ten
CS 70 Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Note 14 Introduction One of the key properties of coin flips is independence: if you flip a fair coin ten times and get ten
Handout 1: Mathematical Background
 Handout 1: Mathematical Background Boaz Barak February 2, 2010 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete math
Handout 1: Mathematical Background Boaz Barak February 2, 2010 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete math
CS 246 Review of Proof Techniques and Probability 01/14/19
 Note: This document has been adapted from a similar review session for CS224W (Autumn 2018). It was originally compiled by Jessica Su, with minor edits by Jayadev Bhaskaran. 1 Proof techniques Here we
Note: This document has been adapted from a similar review session for CS224W (Autumn 2018). It was originally compiled by Jessica Su, with minor edits by Jayadev Bhaskaran. 1 Proof techniques Here we
The expansion of random regular graphs
 The expansion of random regular graphs David Ellis Introduction Our aim is now to show that for any d 3, almost all d-regular graphs on {1, 2,..., n} have edge-expansion ratio at least c d d (if nd is
The expansion of random regular graphs David Ellis Introduction Our aim is now to show that for any d 3, almost all d-regular graphs on {1, 2,..., n} have edge-expansion ratio at least c d d (if nd is
Decomposing oriented graphs into transitive tournaments
 Decomposing oriented graphs into transitive tournaments Raphael Yuster Department of Mathematics University of Haifa Haifa 39105, Israel Abstract For an oriented graph G with n vertices, let f(g) denote
Decomposing oriented graphs into transitive tournaments Raphael Yuster Department of Mathematics University of Haifa Haifa 39105, Israel Abstract For an oriented graph G with n vertices, let f(g) denote
1 Maintaining a Dictionary
 15-451/651: Design & Analysis of Algorithms February 1, 2016 Lecture #7: Hashing last changed: January 29, 2016 Hashing is a great practical tool, with an interesting and subtle theory too. In addition
15-451/651: Design & Analysis of Algorithms February 1, 2016 Lecture #7: Hashing last changed: January 29, 2016 Hashing is a great practical tool, with an interesting and subtle theory too. In addition
1 Normal Distribution.
 Normal Distribution.. Introduction A Bernoulli trial is simple random experiment that ends in success or failure. A Bernoulli trial can be used to make a new random experiment by repeating the Bernoulli
Normal Distribution.. Introduction A Bernoulli trial is simple random experiment that ends in success or failure. A Bernoulli trial can be used to make a new random experiment by repeating the Bernoulli
Chapter 5. Means and Variances
 1 Chapter 5 Means and Variances Our discussion of probability has taken us from a simple classical view of counting successes relative to total outcomes and has brought us to the idea of a probability
1 Chapter 5 Means and Variances Our discussion of probability has taken us from a simple classical view of counting successes relative to total outcomes and has brought us to the idea of a probability
Approximation Algorithms and Hardness of Approximation May 14, Lecture 22
 Approximation Algorithms and Hardness of Approximation May 4, 03 Lecture Lecturer: Alantha Newman Scribes: Christos Kalaitzis The Unique Games Conjecture The topic of our next lectures will be the Unique
Approximation Algorithms and Hardness of Approximation May 4, 03 Lecture Lecturer: Alantha Newman Scribes: Christos Kalaitzis The Unique Games Conjecture The topic of our next lectures will be the Unique
On the Optimality of Some Semidefinite Programming-Based. Approximation Algorithms under the Unique Games Conjecture. A Thesis presented
 On the Optimality of Some Semidefinite Programming-Based Approximation Algorithms under the Unique Games Conjecture A Thesis presented by Seth Robert Flaxman to Computer Science in partial fulfillment
On the Optimality of Some Semidefinite Programming-Based Approximation Algorithms under the Unique Games Conjecture A Thesis presented by Seth Robert Flaxman to Computer Science in partial fulfillment
Lecture 4. P r[x > ce[x]] 1/c. = ap r[x = a] + a>ce[x] P r[x = a]
![Lecture 4. P r[x > ce[x]] 1/c. = ap r[x = a] + a>ce[x] P r[x = a] Lecture 4. P r[x > ce[x]] 1/c. = ap r[x = a] + a>ce[x] P r[x = a]](/thumbs/96/126571961.jpg) U.C. Berkeley CS273: Parallel and Distributed Theory Lecture 4 Professor Satish Rao September 7, 2010 Lecturer: Satish Rao Last revised September 13, 2010 Lecture 4 1 Deviation bounds. Deviation bounds
U.C. Berkeley CS273: Parallel and Distributed Theory Lecture 4 Professor Satish Rao September 7, 2010 Lecturer: Satish Rao Last revised September 13, 2010 Lecture 4 1 Deviation bounds. Deviation bounds
Kousha Etessami. U. of Edinburgh, UK. Kousha Etessami (U. of Edinburgh, UK) Discrete Mathematics (Chapter 7) 1 / 13
 Discrete Mathematics & Mathematical Reasoning Chapter 7 (continued): Markov and Chebyshev s Inequalities; and Examples in probability: the birthday problem Kousha Etessami U. of Edinburgh, UK Kousha Etessami
Discrete Mathematics & Mathematical Reasoning Chapter 7 (continued): Markov and Chebyshev s Inequalities; and Examples in probability: the birthday problem Kousha Etessami U. of Edinburgh, UK Kousha Etessami
Uncertainty. Michael Peters December 27, 2013
 Uncertainty Michael Peters December 27, 20 Lotteries In many problems in economics, people are forced to make decisions without knowing exactly what the consequences will be. For example, when you buy
Uncertainty Michael Peters December 27, 20 Lotteries In many problems in economics, people are forced to make decisions without knowing exactly what the consequences will be. For example, when you buy
A simple algorithmic explanation for the concentration of measure phenomenon
 A simple algorithmic explanation for the concentration of measure phenomenon Igor C. Oliveira October 10, 014 Abstract We give an elementary algorithmic argument that sheds light on the concentration of
A simple algorithmic explanation for the concentration of measure phenomenon Igor C. Oliveira October 10, 014 Abstract We give an elementary algorithmic argument that sheds light on the concentration of
Approximation Resistance from Pairwise Independent Subgroups
 1/19 Approximation Resistance from Pairwise Independent Subgroups Siu On Chan UC Berkeley 2/19 Max-CSP Goal: Satisfy the maximum fraction of constraints Examples: 1 MAX-3XOR: x 1 + x 10 + x 27 = 1 x 4
1/19 Approximation Resistance from Pairwise Independent Subgroups Siu On Chan UC Berkeley 2/19 Max-CSP Goal: Satisfy the maximum fraction of constraints Examples: 1 MAX-3XOR: x 1 + x 10 + x 27 = 1 x 4
Lecture 5 January 16, 2013
 UBC CPSC 536N: Sparse Approximations Winter 2013 Prof. Nick Harvey Lecture 5 January 16, 2013 Scribe: Samira Samadi 1 Combinatorial IPs 1.1 Mathematical programs { min c Linear Program (LP): T x s.t. a
UBC CPSC 536N: Sparse Approximations Winter 2013 Prof. Nick Harvey Lecture 5 January 16, 2013 Scribe: Samira Samadi 1 Combinatorial IPs 1.1 Mathematical programs { min c Linear Program (LP): T x s.t. a
1 Review of The Learning Setting
 COS 5: Theoretical Machine Learning Lecturer: Rob Schapire Lecture #8 Scribe: Changyan Wang February 28, 208 Review of The Learning Setting Last class, we moved beyond the PAC model: in the PAC model we
COS 5: Theoretical Machine Learning Lecturer: Rob Schapire Lecture #8 Scribe: Changyan Wang February 28, 208 Review of The Learning Setting Last class, we moved beyond the PAC model: in the PAC model we
CS 361: Probability & Statistics
 February 26, 2018 CS 361: Probability & Statistics Random variables The discrete uniform distribution If every value of a discrete random variable has the same probability, then its distribution is called
February 26, 2018 CS 361: Probability & Statistics Random variables The discrete uniform distribution If every value of a discrete random variable has the same probability, then its distribution is called
IN this paper, we consider the capacity of sticky channels, a
 72 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 1, JANUARY 2008 Capacity Bounds for Sticky Channels Michael Mitzenmacher, Member, IEEE Abstract The capacity of sticky channels, a subclass of insertion
72 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 1, JANUARY 2008 Capacity Bounds for Sticky Channels Michael Mitzenmacher, Member, IEEE Abstract The capacity of sticky channels, a subclass of insertion
COS 341: Discrete Mathematics
 COS 341: Discrete Mathematics Final Exam Fall 2006 Print your name General directions: This exam is due on Monday, January 22 at 4:30pm. Late exams will not be accepted. Exams must be submitted in hard
COS 341: Discrete Mathematics Final Exam Fall 2006 Print your name General directions: This exam is due on Monday, January 22 at 4:30pm. Late exams will not be accepted. Exams must be submitted in hard
MATH MW Elementary Probability Course Notes Part I: Models and Counting
 MATH 2030 3.00MW Elementary Probability Course Notes Part I: Models and Counting Tom Salisbury salt@yorku.ca York University Winter 2010 Introduction [Jan 5] Probability: the mathematics used for Statistics
MATH 2030 3.00MW Elementary Probability Course Notes Part I: Models and Counting Tom Salisbury salt@yorku.ca York University Winter 2010 Introduction [Jan 5] Probability: the mathematics used for Statistics
Lectures One Way Permutations, Goldreich Levin Theorem, Commitments
 Lectures 11 12 - One Way Permutations, Goldreich Levin Theorem, Commitments Boaz Barak March 10, 2010 From time immemorial, humanity has gotten frequent, often cruel, reminders that many things are easier
Lectures 11 12 - One Way Permutations, Goldreich Levin Theorem, Commitments Boaz Barak March 10, 2010 From time immemorial, humanity has gotten frequent, often cruel, reminders that many things are easier
Inapproximability Ratios for Crossing Number
 Universidade de São Paulo September 14, 2017 Drawings A drawing of a graph G is a function D : G R 2 that maps each vertex to a distinct point and each edge uv E(G) to an arc connecting D(u) to D(v) that
Universidade de São Paulo September 14, 2017 Drawings A drawing of a graph G is a function D : G R 2 that maps each vertex to a distinct point and each edge uv E(G) to an arc connecting D(u) to D(v) that
Lecture 10 + additional notes
 CSE533: Information Theorn Computer Science November 1, 2010 Lecturer: Anup Rao Lecture 10 + additional notes Scribe: Mohammad Moharrami 1 Constraint satisfaction problems We start by defining bivariate
CSE533: Information Theorn Computer Science November 1, 2010 Lecturer: Anup Rao Lecture 10 + additional notes Scribe: Mohammad Moharrami 1 Constraint satisfaction problems We start by defining bivariate
Chapter 6 Randomization Algorithm Theory WS 2012/13 Fabian Kuhn
 Chapter 6 Randomization Algorithm Theory WS 2012/13 Fabian Kuhn Randomization Randomized Algorithm: An algorithm that uses (or can use) random coin flips in order to make decisions We will see: randomization
Chapter 6 Randomization Algorithm Theory WS 2012/13 Fabian Kuhn Randomization Randomized Algorithm: An algorithm that uses (or can use) random coin flips in order to make decisions We will see: randomization
Lecture 6: The Pigeonhole Principle and Probability Spaces
 Lecture 6: The Pigeonhole Principle and Probability Spaces Anup Rao January 17, 2018 We discuss the pigeonhole principle and probability spaces. Pigeonhole Principle The pigeonhole principle is an extremely
Lecture 6: The Pigeonhole Principle and Probability Spaces Anup Rao January 17, 2018 We discuss the pigeonhole principle and probability spaces. Pigeonhole Principle The pigeonhole principle is an extremely
Expectation is linear. So far we saw that E(X + Y ) = E(X) + E(Y ). Let α R. Then,
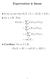 Expectation is linear So far we saw that E(X + Y ) = E(X) + E(Y ). Let α R. Then, E(αX) = ω = ω (αx)(ω) Pr(ω) αx(ω) Pr(ω) = α ω X(ω) Pr(ω) = αe(x). Corollary. For α, β R, E(αX + βy ) = αe(x) + βe(y ).
Expectation is linear So far we saw that E(X + Y ) = E(X) + E(Y ). Let α R. Then, E(αX) = ω = ω (αx)(ω) Pr(ω) αx(ω) Pr(ω) = α ω X(ω) Pr(ω) = αe(x). Corollary. For α, β R, E(αX + βy ) = αe(x) + βe(y ).
Decomposition of random graphs into complete bipartite graphs
 Decomposition of random graphs into complete bipartite graphs Fan Chung Xing Peng Abstract We consider the problem of partitioning the edge set of a graph G into the minimum number τg) of edge-disjoint
Decomposition of random graphs into complete bipartite graphs Fan Chung Xing Peng Abstract We consider the problem of partitioning the edge set of a graph G into the minimum number τg) of edge-disjoint
