Algorithms and Data Structures in the noisy comparison model and applications
|
|
|
- Cori Cole
- 5 years ago
- Views:
Transcription
1 Algorithms and Data Structures in the noisy comparison model and applications Nishanth Dikkala, Anil Shanbhag, Emmanouil Zampetakis Massachusetts Institute of Technology Abstract In contrast to classical computational models where every operation gives the correct answer always, we consider models with noise introduced in the operations they perform. In particular we look at the scenario when comparisions between elements turns noisy, i.e, gives the wrong result with a small probability. In this setting, we present existing algorithms in literature for binary search and sorting. We develop algorithms for finding the minimum among n elements and implementing a noisy binary search tree. We also present various applications of the above algorithms to areas such as learning theory, shortest paths in graphs with edge uncertainties and strategic voting. Keywords: Algorithms, Noisy Comparisons, Uncertainty 1. Introduction The classical design of algorithms and data structures assumes that the values of the items are known accurately and any operation involving them, such as comparisons or arithmetic, always returns the correct answer. This assumption doesn t hold true in many real world scenarios where the true value of object may not be known and hence comparisons between objects can return the wrong result with some small probability. Consider for example a sport tournament, in this case every time a match is played we have a winner but, there is always a probability that the weaker team will win. So we can see every match as a noisy comparison with some probability of failure. In settings like this we are interested in finding the best team or the complete ordering of all the teams. The goal of this project is to study existing literature and design algorithms and data structures which work well in presence of noise. We restrict ourselves to studying the following three problems in a noisy setting : 1. Binary search for an item in a sorted array of items 2. Implementing a binary search tree 3. Sorting a set of items Existing literature considers three different models for noisy setting. Note that, in all these models, the true value of the items is unknown. addresses: ndikkala@mit.edu (Nishanth Dikkala), anils@mit.edu (Anil Shanbhag), mzampet@mit.edu (Emmanouil Zampetakis) Preprint submitted to Advanced Algorithms December 10, 2014
2 1. Noisy Comparator Model: We are given a noisy comparison operator which takes as input two items and produces a binary output. This comparator gives the wrong answer with probability δ < 1 2. The only operation allowed in this model is picking two items and asking the noisy comparator which one is greater. If we repeat a comparison 2k + 1 times, the probability that at least k of the comparisons give the wrong answer is at most ɛ k where ɛ is a function of δ such that 0 ɛ < 1. This will be shown precisely in Section Coin Flip Model: Every item i is a coin whose heads probability, p i, is unknown. We can no longer compare elements directly. We are only allowed to toss the given coins and answer questions regarding their heads probabilities. If we toss a coin i, 1/ɛ 2 times, then the probability that the estimated heads probability differs from p i by more than ɛ, is bounded by a constant from Chernoff bound. 3. Noisy Input Model: In this model every comparison has a probability of failure δ. The difference is that in this case by repeating a comparison we don t get a better comparator because the uncertainty comes from the input and therefore the comparisons are not independent Guarantees of the results of the algorithms It is obvious that in these models we cannot have algorithms that always work, because there is always a probability, even though small, that all the comparisons of the algorithm went wrong. So the guarantees provided in this work can again be of two forms: 1. Probability of wrong answer upper bounded. For instance it could be bounded by a constant 1 2 or by a function of the size of the input e.x. 1/n. 2. Given a number of samples, output the provable best solution, with respect to some objective function, based on these samples. For the binary search and sorting algorithms we have a guarantee of the first type. In the fourth section we also consider a noisy sorting algorithm with guarantee of the second type. Although these guarantees are incomparable, it is well accepted that the second guarantee is harder to achieve than the first one Performance of the algorithms The well-known measure that is used to measure the performance in the classical theory of algorithms is running time of an algorithm. Apart from the total running time, in these models it is sometimes reasonable to measure the performance of our algorithms based on the number of samples that they use from the noisy comparisons. For instance, in the case of a sport tournament, it is reasonable to not let an arbitrary pair of teams play each other more than one or two times. We refer to this objective as the query complexity of the algorithm Roadmap At first we present a naive reduction that can be used in order to transform an algorithm that solves a problem using the classical comparison model, to an algorithm that solves with high probability the same problem in the noisy comparison model. After that we present our algorithm for finding the minimum among n elements in linear time. Then we present our binary search tree data structure that is based on the work of [1] in the noisy comparison model. Next we present an optimal algorithm for binary search in the coin flip model based on the work of Karp and Kleinberg 2
3 [2]. Then we give some interesting applications of these models to the design of algorithms for some problems in theoretical computer science. Finally we present an algorithm for sorting n elements in the noisy input model based on the work of Braverman and Mossel [3] and state a nice application of this to social choice theory. In the appendix we have some proofs that are omitted from Section 5 of the paper and also some results that we had developed on sorting algorithms before we noticed that there were some better results in the work of [1]. These results include : 1. We develop a noisy Fibonacci heap with O(log log n) insert and O(log n log log n) delete amortized runtime. The primary reason for developing such a heap is for its application in the sorting algorithm we develop next. 2. Using the heap developed above, we give a sorting algorithm which takes O(n log n log log n) time to output the sorted order with high confidence, which is the major contribution of this paper. 3. Finally, we present a reduction of sorting to a heap with specific guarantees in order to improve the time bound of the sorting algorithm to O(n log n log n). We start by stating the Chernoff bound that we are going to use throughout the paper Lemma 1.1. Chernoff Bound[4] Suppose X 1, X 2,..X n be independent random variables taking values in 0,1. Let X denote the sum of random variables and µ = E[X]. Then we have for any δ, Pr(X µ δµ) e δ2 µ 3 Pr(X µ δµ) e δ2 µ 2 2. Naive Solution Every problem in the noisy setting has a classical analogue which is noise-free. In this section, we show how we can derive a naive solution for a general comparision-based problem in the noisy setting, using a polynomial-time solution to its noise-free analogue. Lemma 2.1. Given a noisy comparator operator X which has error probability δ, it is possible to create another noisy comparator operator Y which invokes X O(c log n) times and has an error probability O(1/n c ), where c is a constant. Proof Let Y make 2k comparisons where k = c log n. The answer returned is the majority answer among the k comparisons. This comparison has a wrong answer if greater than half the comparisons returned the wrong result. By Lemma 1.1, this probability can be upper bounded by: P r[σx i > k] = P r[σx i 2kδ > k 2kδ] = P r[σx i 2kδ > (1/2δ 1)2kδ] < e (1/2δ 1)2 kδ < n (1/2δ 1)2 cδ 3
4 Consider an algorithm which makes O(n c ) comparisons in the worse-case to get the right solution. Now in the noisy setting, each of these comparisons can return wrong result with probability δ. Let us repeat each of these comparisons O(c log n) times. By Lemma 2.1, each can go wrong with probability O(1/n c ). Since we are making O(n c ) comparisons, by union bound over all the comparisons we have that the order thus returned is wrong with a constant probability. The naive solution leads to a multiplicative O((log n) c ) factor in the running time of the algorithm. In the rest of the paper, we will study or design algorithms which have better than log n multiplicative factor. 3. Noisy minimum The simplest thing to find given a comparison operator is the minimum/maximum. For the noise-free case, this can be done trivially using O(n) comparisons. We present an algorithm to do the same in noisy setting with O(n) time complexity which is strictly better than the naive solution based on Section 2 which gives a O(n log n) solution. The goal is to find the minimum of a set of elements given a noisy comparison operator (model 1). Given the set of n elements, we construct a tournament graph as follows. Create a leaf node corresponding to every element. Construct a tournament tree over these leaves. Figure 1 shows the graph for 8 elements. Each internal node of the tree contains the minimum of its children. Hence the root of the tree represents the minimum. If we perform a single comparision to find out the item at each internal node, the error probability scales with the depth giving an O(log n) probability of failure. On the other hand, performing 2 O(log log n) 1 comparisions and taking the majority outcome at every internal node ensures a constant failure probability but the total number of comparisions needed is now O(n log log n) (number of internal nodes is O(n)). The trick to achieve both the goals is to perform more repeated comparisions higher up the tree and less repeated comparisions lower in the tree. In particular, at each level of the tree, we do 2h 1 comparisions where h is height of the level. This uses O(n) comparisions to give a constant failure probability. 5 comparisons 3 comparisons 1 comparison Figure 1: Finding minimum using tournament graph for 8 items 4
5 The total number of comparisons forms an arithmetico-geometric sequence and its value is S = n/2 1 + n/ (2 log 2 (n) 1) < n/2 (1/(1 0.5) /(1 0.5) 2 ) < 3n An individual comparison can be wrong with probability δ. We want to upper bound the probability of error in minimum. Consider figure 1 again, let element 5 be the minimum. The answer would be correct if all the internal nodes from 5 to the root are correct. The result of rest of comparisons is immaterial. Hence the probability of failure is the probability that the minimum element didn t make it up to the root which is upper bounded by the sum of error probabilities along the path from the minimum leaf to the root. At every level, the node has the wrong result if atleast h of the 2h 1 the comparisons returned the wrong result. Hence, the probability the minimum is wrong is p δ + δ 2 +..δ log 2 n δ 1 δ Since δ < 1/2, p < 1. Hence, with probability > 1 p the algorithm finds the right minimum. 4. Dynamic noisy binary search tree In this section we present how we can use the ideas of [1] in order to build a dynamic binary search tree with the guarantee that at every point all the elements are in their correct positions with probability > 1 1/n where n is the number of elements in the data structure. One basic issue that [1] didn t deal with is what happens if we don t know n a priori or if we have a long sequence of insertions and deletions. So, we first present an algorithm that finds the correct place to insert an element in a binary search tree conditioned on the ordering of the binary search tree being correct. After that we use this basic operation to describe a dynamic binary search tree when n is unknown at the beginning of the algorithm s execution Inserting into a correct binary search tree The basic idea is to use binary search with backtracking. In order to be able to understand whether we have to backtrack during the execution of the binary search on the tree, we have to design a test such that each time we reach a node u the test will indicate whether u is on the correct path that we had to follow from the root. If it found to not be on the correct path, we backtrack to the parent of u. Of course this test will also have a probability of failure because our comparisons are noisy. We now describe a single step of the insert algorithm. The number of steps that the algorithm runs for is a fixed number m that will be specified later. Suppose we wish to find the position of the element x, and after k steps of execution we reach the node u. We wish to check whether x belongs to the subtree T u with root u. 5
6 If u is an internal node, for this to hold x must be greater than the smallest and smaller than the largest element of T u. So let a u = min v Tu v and b u = max v Tu v then we test whether a u x b u. So at every node u we also maintain pointers to a u and b u. Now once x has reached u we compare it with a u and b u and if the test fails, we backtrack and x goes to its parent. If the test succeeds then we compare x with u in order to decide to which child of u to move to in the next step. If u is a leaf then a u is defined as the greatest element in the tree which is less than u and b u is defined as the smallest element in the tree that is greater than u. Therefore the test on the leaf is again a u x b u. On reaching a leaf, our algorithm doesn t stop. It continues executing until it finishes m steps. If the test at a leaf succeeds we stay at the leaf. We can model the above search algorithm as a Markov process. Consider a leaf w of the tree and suppose that x belongs to the interval labeling this leaf. Orient all the edges of the tree towards w. Note that for every node u, exactly one adjacent edge is directed away from u and the other adjacent edges are directed towards u. It is easy to see that at every point, the probability that the algorithm will follow the direction of the edges is at least 1 δ. This is because if the comparisons are correct then the algorithm will follow the direction of the edges. Now we define X t as the random variable that is 1 if at step t, the execution of the algorithm follows the correct direction and equal to 1 if it follows the opposite direction. Because of the previous arguments, we have that E[ t X t] = (1 δ)m and so by applying Chernoff bound we can get that Pr[ t X t (1 δ)m/2] ɛ m for some 0 ɛ 1. So if we let m = (4/ log ɛ)(1/δ) log n then with high probability 1/n 2, t X t > log n. But t X t = m f m b where m f is the number of forward movements and m b is the number of backward movements. Therefore m f m b > log n which implies that the random walk ends to the correct leaf. Since m = O(log n) this procedure takes logarithmic time and gives the result with high probability Building a dynamic tree Using the above procedure we can repeatedly add elements to the tree. Each time when we find the correct position that an element should be placed we know with high probability the ordering of the elements in the tree. So we can use a self balancing binary tree like AVL-trees and once we have the correct position of the elements we can do the balancing without making any additional noisy comparisons by just assume that the correct ordering is the one that we have in the tree at this point. Therefore if we know the number of operations n, that will be done, a priory, then using a self balancing tree and the above procedure we can create a dynamic binary search tree using m = O(log n) which takes time O(log n) for insertion, deletion and search. At every point the probability of error of the data structure is less than n(1/n 2 ) = 1/n. Now if n is unknown then we keep two counters n and n old. At every point m = O(log(2n old )) and n old n 2n old. Each time we do an insert we increase n by 1. When n becomes equal to 2n old, we destroy the data structure and we build it from scratch with m = O(log(2n)) and n old = n. This will take O(n log n) time but we can charge the re-building operations to the last n/2 operations performed without reconstructing the data structure. Hence each element gets charged O(log n) for the initial operation and 2O(log n) for the renewing process. So the amortized cost for each operation is still O(log n) and the probability that there is a mistake in our data structure is less that 1/n at any point because m = O(log n) at any point. Therefore we have a dynamic binary search tree that works in the model with noisy comparisons, has the same amortized complexity as the regular binary search trees and at any point during it s 6
7 operation, has probability at most 1/n of failure. All these guarantees are achieved without knowing n in advance. 5. Noisy Binary Search We now present the noisy binary search algorithm of Karp and Kleinberg[2] which works with the noisy model 2. We are given n biased coins in order of their increasing heads probabilities. Let them be p 1, p 2,... p n where p 1 p 2 p n. The algorithm doesn t know {p i } but is allowed to toss coins and observe the outcomes. For simplicity of analysis, we assume p 0 = 0 and p n+1 = 1 and consider the set {p 0,..., p n+1 } as our search space. A target value τ [0, 1] and a small number ɛ are specified as part of the input and the goal is to find two consecutive indices i and i + 1 such that [τ ɛ, τ + ɛ] intersects [p i, p i+1 ]. Such a solution is called an ɛ-good solution. It is easy to see that this goal cannot be achieved always as our estimates of p i might go wrong so the algorithm finds the right interval with 3 4 probability A naive algorithm A naive algorithm would use binary search to locate a good coin, maintaining a pair of indices a and b (initialized to 1 and n) and always testing the coin midway in the current interval [a, b]. The heads probability p of the midway coin is to be compared with τ. If p lies outside the interval [τ ɛ, τ + ɛ], using O(1/ɛ 2 ) tosses of the coin, the algorithm tests whether p < τ or p > τ with at most a constant error probability (from the Chernoff bound). Since, we do log n such comparisons over the course of a binary search, and wish for a constant overall error bound, we ensure that each comparison has O(1/ log n) error probability. To do this, we toss the coin O( of just O( 1 log n log log n ) times, giving an algorithm of running time O( ). ɛ 2 ɛ A Faster Algorithm: Binary Search with Backtracking log log n ɛ 2 ) times instead The naive algorithm introduces an additional O(log log n) factor in the running time of the classical binary search algorithm which is removed by a more clever binary search. This algorithm uses backtracking and finds a 1/3-good solution. Later, we see how to get an ɛ-good solution, for an arbitrary ɛ, given the 1/3-good solution. We will present the algorithm when the target τ = 1/2 as this simplifies the analysis of the algorithm. Later, we will show how to reduce the problem of searching for a general τ to one with τ = 1 2. Algorithm for τ = 1/2: Let T be an infinite rooted binary tree. Each node of the tree is labeled with a pair of indices from the set {0, 1,..., n + 1}. The labeling is defined recursively as follows. First, the root is labeled (0, n + 1). For every vertex v with label (a, b), let m = (a + b)/2 and label the left child L(v) with (a, m) and the right child R(v) with (b, m). Note that if the label (a, b) of a node satisfies b = a + 1, both its children will be labeled (a, b) as well and hence an infinite tree exists (We need an infinite tree due to the randomized nature of the algorithm). Let P (v) denote the parent of v. If v is the root, we let P (v) = v. 1. Start round 0 at the root of T. 2. In round t, suppose we are at node v(t) with label (a, b) and whose children are labeled (a, m) and (m, b). We flip coin a twice and coin b twice. If both a-flips are heads or both b-flips are tails, we take this as evidence of p a > 1/2 or p b < 1/2 and we backtrack to the parent node. That is v(t + 1) = P (v(t)). 7
8 3. Otherwise, we flip coin m and move to L(v(t)) if the flip yields heads and move to R(v(t)) if the flip yields tails. 4. At the end of every round t, with probability 1/ log n, we perform a termination test to decide if we should halt before proceeding to round t + 1. The termination test essentially checks if either coin a or coin b is close to the target. 5. Termination Test: Let k = 300 log n. We perform k flips of coin a and k flips of coin b. Let the number of heads be h a and h b respectively. (a) If 1 4 h a/k 3 4, halt and output a. (b) If 1 4 h b/k 3 4, halt and output b. (c) If b = a + 1 and h a /k < 1 2 < h b/k, halt and output a. (d) If none of the above happen, proceed to round t + 1. Analysis of the algorithm: The above mentioned algorithm outputs a coin which is 1/3-good and has expected running time O(log n). The constant 300 in the termination test isn t unique. Any constant > 2(12) 2 = 288 would have worked. We sketch the steps of the proof below in 4 lemmas. We defer the full proofs of 3 of the sub lemmas we use to Appendix A. We define a node of T to be promising if one of the following conditions holds for its label (a, b): 1. p a [1/4, 3/4] 2. p b [1/4, 3/4] 3. b = a + 1 and 1 2 [p a, p b ] Denote by W the set of all promising nodes in T. Lemma 5.1. For any t, if v(t) W, and a termination test is performed at time t, then the algorithm halts with at least a constant probability. Lemma 5.2. Let d(v(t), W ) denote the distance in T, from v(t) to the closest node of W. v(t) / W, the probability that d(v(t + 1), W ) = d(v(t), W ) 1 is at least 9/16. If Using the above two lemmas, we now show that the expected number of rounds for which the algorithm runs is O(log n). Since each round takes O(1) time in expectation (termination test is performed only with O(1/ log n) probability), this will imply the O(log n) time complexity of the algorithm. To prove this we will use Azuma s inequality for submartingales which we will state here. Definition A sequence of random variables X 0, X 1,... X n is called a submartingale if E [X i+1 X 0,... X i ] X i i Lemma 5.3. Azuma s inequality: Suppose X 0, X) 1,..., X n is a submartingale and X i+1 X i 1 for 0 i < n. Then P r (X n X 0 t) exp. ( t 2 2n Lemma 5.4. The expected number of rounds for which the algorithm runs is O(log n). 8
9 We start the proof by defining a potential function Φ. Let Y t = d(v(t), W ) and Z t = #{s < t v(s) W } Φ t = log 2 n + Z t Y t 1 8 (t Z t) Now, Φ 0 = log 2 n d(v(0), W ) 0 because the closest promising node to the root is at a depth log 2 n. Next, we show that {Φ t } is a submartingale. If v(t) W, then Z t+1 = Z t + 1 and Y t+1 Y t + 1. Hence, Φ t+1 Φ t which implies E [Φ t+1 Φ t, v(t)] Φ t. If v(t) / W, then Z t+1 = Z t. From Lemma 5.2, we have that d(v(t + 1), W ) = d(v(t), W ) + 1 with probability at most 7/16 and hence, E [Y t+1 Y t, v(t)] Y t 1/8 which implies E [Φ t+1 Φ t, v(t)] Φ t proving that {Φ t } is a submartingale. Now, if the algorithm did not terminate before round t and t > 160(1 + log 2 (n)), then Φ t log 2 (n) Z t t 8. If Z t t/10, then log 2 (n) Z t t 8 < t/160. From Azuma s inequality, we have Pr(Φ t < t/160) < (1 δ) t for some constant δ. If Z t > t/10, then from Lemma 5.1, we have Pr(Z t > t/10) < (1 δ ) (t/ log n) for some other constant δ. Hence when t > 160(1 + log 2 (n)), the probability of the algorithm running for t rounds decays exponentially in t/ log(n) giving an expected number of rounds as O(log n). Lemma 5.5. If the algorithm halts, the probability that the result is not 1/3-good is at most 4/n. Getting an ɛ-good solution from a 1/3-good solution: Now all that s left is to get an ɛ-good solution given the above algorithm which outputs a 1/3-good solution. We will sketch the idea in brief and leave out the details. Intuitively, the construction runs by amplifying the deviation of the heads probability of each coin from that of a fair coin. The amplification is such that a 1/3-good solution among the amplified coins corresponds to an ɛ-good solution in the original coin set. Such an amplification is achieved by repeated tosses of the coin and an application of the Chernoff bound. This introduces an additional 1/ɛ 2 factor in the running time of the algorithm. This completes the analysis of the algorithm for τ = 1/2. Reduction from a general τ to τ = 1/2: The principle behind the reduction is to construct a simulation procedure which, given a coin i with heads probability p i, simulates a coin with heads probability f(p i ) where f is a strictly increasing linear function such that f(τ) = 0.5. To construct such a procedure, we assume the availability of a fair coin. It is a well-known result in literature that using two tosses of a fair coin in expectation, a coin with an arbitrary heads probability can be simulated. We will use this result to construct the above procedure. If τ > 1/2, the procedure flips coin i and a simulated coin with heads probability 1/2τ, and declares heads if both outcomes are heads. Probability of heads being declared by the procedure is p i 1/2 τ 2τ. If τ 1/2, the procedure flips coin i and a simulated coin with heads probability 1 τ and declares heads if at least one of the outcomes is heads. Probability of heads being declared in this case is 1 minus the probability that both the flips resulted in tails, which is, (1 p i) 2(1 τ). Hence probability of heads being declared is 1 (1 p i) 2(1 τ) = 1+p i 2τ 2(1 τ). Finally note that, if f(τ(1 ɛ)) = 1/2(1 ɛ ) for some constant ɛ, then f(τ(1 + ɛ)) = 1/2(1 + ɛ ) due to linearity of f. Hence we are still searching for overlap with a symmetric interval. The only difference being that it is now centered at 1/2 instead of τ. Given this simulation procedure, for an arbitrary τ, we do the following. Whenever we wish to compare τ with p i, using 3 tosses in expectation for every toss of coin i, we compare instead 1/2 9
10 with f(p i ). 6. Applications on the noisy comparison model 6.1. Application to Machine Learning One very interesting application of the model that we are presenting in this paper is an application to machine learning and computational learning theory. A very common problem in this field is the following. Given access to a sample generator of an unknown distribution D that belongs to a class of distributions C, compute a distribution D that is ɛ close to D with respect to some distance measure such as the total variation distance. A common technique for this problem is to find an ɛ cover C ɛ of C. This means that for every D C there exists D C ɛ such that the distance between D and D is less than ɛ. After finding such a cover of polynomial size, we would like to choose a D C ɛ such that the distance between D and D is less than ɛ. Since C ɛ is an ɛ cover it suffices to find the D C ɛ which is closest to D. So we set up a noisy comparison that given D, D C ɛ finds the one that is closest to D. To do so we use the samples from D and we also generate some samples from D and D and after O(log(1/δ)/ɛ 2 ) samples we can conclude the winner if the distance is greater than ɛ with probability of failure δ. For more details on this construction we suggest looking here [5]. There appears to be an analogy between this model and the coin comparison that we described in detail before. To solve this find minimum problem we set up a tournament as we did in section 3 and we get a winner with the same guarantees doing just O(n) comparisons and using O(log n/ɛ 2 ) samples, i.e. constant number of samples for every comparison Finding shortest paths in graphs with uncertainty In many real life applications the input that we are given has a lot of uncertainty. One very common example is the case of finding shortest paths in computer networks. A classical problem in this direction is the so called stochastic shortest path problem. In this problem the cost of each edge is a random variable and the goal is to find a path which is optimal in expectation[6]. Here, we assume that we don t know exactly the distribution of the costs of the edges in the network. We assume that we know the topology of the network. First we have to set up a noisy comparison model. So assume that we want to compare the cost of an edge e 1 = (u 1, v 1 ) with the cost of the edge e 2 = (u 2, v 2 ). To do this, we send a constant number of packets from u 1 to v 1 and the same number of packets from u 2 to v 2. After that we compare the average times for sending the packets along each of the edges and we output the edge with smaller average time as the winner of this comparison. Here we make the assumption that after this procedure the above comparison has a constant probability of failure δ which is bounded away from 1/2. We also assume that we have a lower bound on δ, lets say that we know that we know that the means of the weights are separated by at least a constant. Now we run the usual Dijkstra s algorithm but using the noisy binary search tree that we described in 4, as a heap instead of using a classical binary heap. Then we can ensure that we will find all the optimal paths with high 10
11 probability because the binary search tree is guaranteed to work will high probability at any point. So our solution is optimal, with a small probability of error compared to the algorithms that find the optimal in expectation solution. The interesting part here is that we do so with running time which is the same as the usual Dijkstra s algorithm which runs is O( E log V ) time. 7. Noisy sorting without resampling In this section we describe the work of Braverman and Mossel [3] to deal with sorting in the noisy input model. A challenge that arises in noisy comparison model is that sometimes it is impossible to do a specific comparison more than one or two times. Such a restriction is natural when we want to report a ranking of n sport teams and we are not allowed to ask the teams to play more than once since every tournament has a specific duration. In this case we have to be able to sort the teams, as well as possible, based on the results of the games that they have already played. So since the number of teams is maybe limited we are not interested so much in the total running time of our algorithm but we are interested in the total number of samples that we use conditioned on the fact that every pair should be compared at most once. In another interpretation of this problem we have as input a directed graph on the n items where the direction of each edge in the graph describes the result of the noisy comparison between them. Now our goal is to find a topological ordering of the items in which the least number of edges are backward and do not follow the topological ordering. This problem is a well known NP-hard problem [7] called feedback arc set problem for tournaments. For this problem a PTAS is known, so we can, in polynomial time, approximate as well as we want the best ordering. In this work we are interested in finding the best ordering with high probability and looking at just O(n log n) comparisons. Let q(a i, a j ) = 1 if the result of the comparison between the results a i a j and let q(a i, a j ) = 1 otherwise. For any σ a permutation of the n elements, we define the score of this permutation to be s q (σ) = i,j:σ(i)>σ(j) q(a σ(i), a σ(j) ). Our goal in this section is to find a permutation τ that minimizes the quantity s q (τ) with high probability. After finding this permutation s q (τ) we have to prove that if the comparisons that we made were noisy, but a real ordering π exists, then τ is very close to π. The algorithm that produces τ consists of two parts Sorting an almost sorted list Producing an almost sorted list via insertion sort After having the above procedures the algorithm produces an almost sorted list and then finds the optimal ordering using the first procedure for sorting an almost sorted list Sorting an almost sorted list Let a list be k almost sorted if, for all 1 i n, the ith element of the list satisfies i τ(i) k. Then using dynamic programming we can prove the following Theorem 7.1. There is an algorithm with running time O(n 2 2 6k ), which produces an optimal ordering τ from an k almost sorted list. 11
12 Suppose we want to find the set of elements S I that will be indexed in the interval I = [i, j] in the optimal ordering, then based on the assumption of the k almost sorted list we know that all the elements with current index [i + k, j k] will belong to S I. For the rest we know that they will be at most k positions away, so their current index will be in either I 1 = [i k, i + 1] or I 2 = [j k, j + k]. So in order to find the whole S I we need to choose the correct 2k elements from the set of 4k elements in the intervals I 1 and I 2. We have 2 4k different choices for doing this. We can enumerate each one of them and choose the best one. Based on this idea the algorithm proceeds by finding S I for big interval and recursively finds S I for I I until we get an ordering with high probability. Also memoization is used in order to avoid repeated work Producing an almost sorted list via insertion sort We call a list of elements almost sorted if for all 1 i n the ith element of the list satisfies i τ(i) c log n. Using a careful variation of insertion sort we can prove the following Theorem 7.2. There is an algorithm that runs in time n r, where r = O(γ 4 (β + 1)) that outputs an almost sorted list with probability 1 n β /2. Here we use a randomized version of insertion sort. Let l = c log n and assume that we have an l almost sorted sublist S k 1 with S k 1 = k 1. We choose a random element a k from the list that is not in S k 1. We want to insert a k in the correct position in S k 1. To do so we split S k 1 into parts B 1,..., B s with length l = (c/4) log n each. So our first goal is to find the B i in which a k should be placed. We do a binary search through B j s in order to find B i and each time we compare a k with B j we compare a k with every element in B j and take the majority. Because S k 1 is l almost sorted we can prove that with high probability the comparisons between a k and B j with i j > 1 are correct. Therefore after the binary search we will find j = i ± 2. If we place a k arbitrarily in B j then we will get an l almost sorted list S k. We now repeat by randomly choosing the next element to insert Performance of the algorithm It is easy to show that has the above algorithm has running time n r, where r = O(γ 4 (β + 1)) by carefully calculating the number of steps that we described above. The analysis of the number of comparisons that the algorithm needs is a more complicated procedure and we refer to the paper for the proof that with high probability the number of comparisons made is O(n log n). The most interesting and non obvious guarantee of this algorithm is that it approximates the initial ordering π. This is not obvious because the result of our algorithm is the ordering τ that minimizes s q (τ) and therefore has no direct relation with π. Despite that we can show that τ approximates π. In order to be able to express this approximation we define d(a i ) = π(i) τ(i). We have two kinds of approximation, approximation in expectation and approximation with high probability. If we let I be the random variable that uniformly takes a value from 1 to n, in expectation the result is For the high probability result we have E[d(a I )] = constant Pr[d(a i ) c log n] Õ(n c ) i 12
13 7.4. Application to Voting [8] Social choice theory studies the aggregation of individual preferences towards a collective choice. In one of the most common models, both the individual preferences and the collective decision are represented as rankings of the alternatives. A voting rule takes the individual rankings as input and outputs a social ranking. One can imagine many different voting rules; which are better than others? The popular axiomatic approach suggests that the best voting rules are the ones that satisfy intuitive social choice axioms. For example, if we replicate the votes, the outcome should not change; or, if each and every voter prefers one alternative to another, the social ranking should follow suit. It is well-known though that natural combinations of axioms are impossible to achieve [9], hence the axiomatic approach cannot give a crisp answer to the above question. A different in a sense competing approach views voting rules as estimators. From this viewpoint, some alternatives are objectively better than others, i.e., the votes are sim- ply noisy estimates of an underlying ground truth. One voting rule is therefore better than another if it is more likely to output the true underlying ranking; the best voting rule is a maximum likelihood estimator (MLE) of the true ranking. From this point we can view the work of Braverman and Mossel [3]. Given samples from the rankings of the agent, they aim to compute the Kemeny rule; which is the maximum likelihood estimator of the ordering in this model with noisy comparisons. And so we have an efficient algorithm that computes the Kemeny ranking with arbitrarily high probability. 8. Conclusions In this paper we presented basic algorithms and data structures in different, commonly used, noisy comparison models. We also present some applications of these in a variety of settings in theoretical computer science proving the importance of the research in this field. One future direction that is maybe interesting especially for real life applications is the investigate what happens when the probability of error in a comparison depends on the actual distance between the elements. This case is captured by the coin flip model and this is the main importance of this model. So it would be interesting if we could extend the binary search tree construction to this model in order to be able to run more complicated algorithms which will have applications in solving real life problem. References [1] U. Feige, P. Raghavan, D. Peleg, E. Upfal, Computing with noisy information, SIAM J. Comput. 23 (1994) [2] R. M. Karp, R. Kleinberg, Noisy binary search and its applications, in: Proceedings of the eighteenth annual ACM-SIAM symposium on Discrete algorithms, Society for Industrial and Applied Mathematics, pp [3] M. Braverman, E. Mossel, Noisy sorting without resampling, in: Proceedings of the nineteenth annual ACM-SIAM symposium on Discrete algorithms, pp
14 [4] M. Tulsiani, S. K. Kundu, M. Mitzenmacher, E. Upfal, J. H. Spencer, Probability and computing: Randomized algorithms and probabilistic analysis, [5] C. Daskalakis, G. Kamath, Faster and sample near-optimal algorithms for proper learning mixtures of gaussians, in: Proceedings of The 27th Conference on Learning Theory, COLT 2014, Barcelona, Spain, June 13-15, 2014, pp [6] C. H. Papadimitriou, M. Yannakakis, Shortest paths without a map, Theor. Comput. Sci. 84 (1991) [7] N. Alon, Ranking tournaments, SIAM J. Discrete Math. 20 (2006) [8] I. Caragiannis, A. D. Procaccia, N. Shah, When do noisy votes reveal the truth?, in: ACM Conference on Electronic Commerce, EC 13, Philadelphia, PA, USA, June 16-20, 2013, pp [9] K. Arrow, Social choice and individual values, John Wiley and Sons (1951). [10] M. L. Fredman, R. E. Tarjan, Fibonacci heaps and their uses in improved network optimization algorithms, J. ACM 34 (1987)
15 Appendix A. Lemmas from Section 5 Lemma Appendix A.1. For any t, if v(t) W, and a termination test is performed at time t, then the algorithm halts with at least a constant probability. Proof: Since v(t) W, one of the following three cases holds. 1. p a [1/4, 3/4]. In this case, the algorithm will halt if h a /k [1/4, 3/4]. The probability that h a /k [0, 1/4) is bounded by the probability that h a /k [p a 1/4, p a ] since p a 1/4. This is in turn bounded by a constant (from the Chernoff bound and the fact that h a /k is symmetrically distributed around p a ). Similarly, the probability that h a /k (3/4, 1] is bounded by a constant, implying that the algorithm halts with at least a constant probability. 2. p b [1/4, 3/4]. Use a similar analysis as above. 3. b = a + 1 and 1/2 [p a, p b ]. The algorithm will halt if h a /k < 1/2 and 1/2 < h b /k, each of which happens with at least a constant probability using a similar argument as above. Hence the algorithm will halt with a probability at least as much as the product of two constants, which is a constant. Lemma Appendix A.2. Let d(v(t), W ) denote the distance from v(t) to the closest node in W. If v(t) / W, the probability that d(v(t + 1), W ) = d(v(t), W ) 1 is at least 9/16. Proof: Note that the path from v(t) to the closest promising node might go up from v(t). Let (a, b) be the label of v(t). If it isn t a promising node, either 1. p a < 1/4 and p b < 1/4. Note that any descendant of v(t) in this case will have p a < 1/4 and p b < 1/4 and hence won t be in the promising set. So the path from v(t) to the closest promising node goes up from v(t). Hence when we backtrack, d(v(t + 1), W ) decreases by 1. The probability that both b tosses yield tails is at least 9/16 and hence we backtrack with at least 9/16 probability. 2. p a > 3/4 and p b > 3/4. We use a similar analysis as above. 3. p a < 1/4 and p b > 3/4 but b a > 1. Now note that, no ancestor of v(t) is in W. Let NB denote the event that we do not backtrack at round t. This happens if at least one of the a tosses is tails and one of the b tosses is heads. Hence Pr(NB) (15/16) 2. Consider the midway coin m = (a + b)/2. There are two cases p m [1/4, 3/4]. In this case, both children of v(t) are in W and hence we move to a mode in W with probablity at least (15/16) 2 > 9/16. p m < 1/4 or p m > 3/4. Assume, wlog, the former. In this case, all of W is contained in the right subtree of v(t) and we move to the right when the m toss results in tails which happens with probability 1 p m 3/4. Hence we move closer to a node in W with probability at least 3/4(15/16) 2 > 9/16. Hence, in all cases we move closer to a node in W with a probability at least 9/16. Lemma Appendix at most 4/n. A.3. If the algorithm halts, the probability that the result is not 1/3-good is 15
16 Proof: Informally, we show that h a /k and h b /k are close to p a and p b. And since ha k, h b k satisfy the conditions for halting, they must in turn be close to 1/2 ensuring the closeness of p a, p b, or far enough such that the interval [p a, p b ] includes 1/2 (in this case b = a + 1 also). Formally, the probability that h a /k p a > 1/12, using the Chernoff bound 1.1 is upper bounded by 2 exp( k/288) 2/n. Similarly h a /k p a > 1/12 with at most 2/n probability. If neither of the above 2 events happen, given that the algorithm halted one of the following must happen: 1. h a /k [1/4, 3/4] and the algorithm outputs a. In this case p a [1/6, 5/6]. 2. h b /k [1/4, 3/4] and the algorithm outputs b. In this case p b [1/6, 5/6]. 3. b = a + 1 and 1/2 [h a /k, h b /k]. Also, h a /k < 1/4 and h b /k > 3/4. In this case, p a < 1/4 + 1/12 = 1/3 and p b > 3/4 1/12 = 2/3 and hence 1/2 [p a, p b ]. In all 3 cases we output a coin which is 1/3-good, and since the probability of one of the above not holding is at most 4/n this proves our statement. Appendix B. Our Results Appendix B.1. Noisy Fibonacci Heap We design a noisy heap which can perform insert and delete-minimum operations efficiently. The intention is to use this heap to develop an efficient sorting algorithm which we present in??. We assume that we know the maximum number of elements in the heap at any time. We denote this number by n. We do not need the decrease-key operation for our sorting algorithm and hence our heap does not support decrease-key. We modify the classical Fibonacci heap to get our noisy heap which performs insert in O(log log n) amortized time and delete-min in O(log n log log n) amortized time. This noisy heap has the guarantee that every call to delete-min can independently be wrong with at most O(1/ log 2 (n)) probability. We present the sketch of the design and the analysis below. We assume the reader has working knowledge of Fibonacci heaps [10]. Choose as the potential function Φ = Number of roots k log log n. INSERT: We add the item to be inserted into the list of root nodes. Real cost is O(1) but increase in potential is O(log log n). Hence amortized cost = O(log log n). MERGE: To merge two trees, classically, Fibonacci heaps would compare the roots of the two trees and would make one the child of the other. This took constant time. Now, we perform O(3 log log n) repeated comparisons. The decrease in potential is also O(log log n) and hence the amortized cost of a merge is O(1). DELETE-MIN: We maintain a pointer to the minimum root and when delete-min is called, we delete the root and add all it s children to the list of root nodes. Then we consolidate all the heap-ordered trees until there is at most one tree of each rank, by using the merge operation. Since our heap doesn t support decrease-key, each heap-ordered tree we have is a perfect binomial tree and hence every root has rank O(log n). Therefore, the number of roots after the consolidate operation is at most O(log n). Now, we scan all the roots to find the new minimum using the offline minimum finding algorithm of Section 3. This finishes in O(log n) time. The total real cost of delete-min is O(No. roots) log log n+o(log n). The total change in potential is O(log log n)(log n No. roots). Hence the amortized cost of delete-min is O(log n log log n). 16
17 Now, all that s left to show is the constant error guarantee for delete-min. The probability that the minimum element isn t one of the roots of the HOTs, is upper bounded by the probability of the failure of at least one of the merge operations applied on the minimum element during the formation of the tree. Since the depth of each HOT is at most O(log n), the number of merge operations on the minimum element is at most O(log n). And the probability of failure of any single merge operation independently is O(1/ log 3 (n)). Hence by the union bound, we achieve the a failure probability O(1/ log 2 (n)) for the minimum element not being among the root nodes. The offline minimum finding algorithm fails to find the minimum among the root nodes with constant probability δ 2. By increasing the number of repeated comparisions in that algorithm by a multiplicative factor of 3, we achieve an error bound of O(1/ log 2 (n). Hence by union bound, the probability that delete-min goes wrong is O(1/ log 2 (n). Appendix B.2. Sorting in O(n log n log log n) time As we have said before the naive solution to the noisy sorting problem takes time O(n log 2 n). In this section we reduce the multiplicative factor of log n and to log log n. Inspired by [3] our sorting algorithm consists of two steps Producing a list in which O(n/ log n) items are misplaced Sorting the above list using insertion sort Producing a list in which O(n/ log n) items are misplaced We run a heapsort algorithm using the heap presented in the previous section. As we have seen, with O(log n log log n) complexity we can ensure that every time delete-min gives the minimum with probability at least 1 1/ log 2 n and so with high probability at most O(n/ log n) items will be misplaced after this heap sort step. So in total this step costs O(n log n log log n) time. Next we formalize this argument. Sorting the list with O(n/ log n) misplaced items To do this step, we take the list obtained in the previous part and start comparing sequentially every item i with its successor i + 1, repeating each comparison O(log n) times, in order to get the answer of this comparison with very high probability. If a i a i+1 then we continue with the next item. Otherwise we remove both the ith and the i + 1th elements and we add them to a set S. After this procedures finishes (which takes O(n log n) time) we have a sorted list with O(n(1 1/ log n)) items and an unsorted set S with O(n/ log n) items. We sort S using any standard sorting algorithm for the noisy setting, which takes O((n/ log n) log 2 n) = O(n log n) time. So finally we have two sorted lists and we have to merge them. We do so using the merging procedure of the mergesort, but now repeating each comparison O(log n) times. The noise-free merge takes linear time and when we repeat each comparison O(log n) times it takes O(n log n) time. So in total we have O(n log n) time for noisy merge. Therefore the total running time of our algorithms is dominated by the previous part and it is O(n log n log log n). Appendix B.3. Sorting in O(n log n log n) time Suppose we have a heap with O(log n) insertion, O(log n) delete-min and each time we ask for the minimum it gives the answer with constant probability of error. In this case by multiplying the number of repetitions of every comparison by O(k) we can have a heap with O(k log n) insertion, O(k log n) delete-min and each time we ask for the minimum gives the answer with probability of 17
18 error O(1/(2 k )) by applying the Chernoff bounds as in the previous sections. Now we assume that we have a sorting algorithm with running time O(n log n2 k ) then we do the same procedure as in the previous section. Producing a list in which O(n/2 k ) items are misplaced To do this step we run a heapsort using the heap that is presented in the previous section. As we have seen there with O(k log n) complexity for delete-min we can ensure that every time we get the minimum with probability at least 1 1/2 k and so with high probability at most O(n/2 k ) items will be misplaced after this heap sort step. So in total this step costs O(n log nk) time. Next we formalize this argument. Sorting the list with O(n/2 k ) misplaced items As we before to do this step we take the list of the previous part and we start comparing sequentially every item i with the next item i + 1 O(log n) times in order to get the answer of this comparison with very high probability. If a i a i+1 then we continue with the next item. Otherwise we remove both the ith and the i + 1th elements and we add them to a set S. After this procedures finishes, which takes O(n log n) time, we have a sorted list with O(n(1 1/2 k ) items and an unsorted set S with O(n/2 k ) items. We sort S using the hypothetical algorithm which takes O((n/2 k ) log n2 k ) = O(n log n) time. So finally we have to sorted lists and we have to merge them. We do so using the merging procedure of the mergesort repeating each comparison O(log n) times. The merging procedure takes linear time and when we repeat each comparison O(log n) times it takes O(n log n) time. So in total we have O(n log n) time for this procedure. Therefore the total running time of our algorithms comes from the previous part and it is O(kn log n). The above result give that we can have an algorithm with running time O(kn log n) from an algorithm with running time O(2 k n log n) by spending an additional O(n log n) time. So by repeating this procedure O(log n) times we end up with an algorithm with running time O(n log n log n). 18
CMPUT 675: Approximation Algorithms Fall 2014
 CMPUT 675: Approximation Algorithms Fall 204 Lecture 25 (Nov 3 & 5): Group Steiner Tree Lecturer: Zachary Friggstad Scribe: Zachary Friggstad 25. Group Steiner Tree In this problem, we are given a graph
CMPUT 675: Approximation Algorithms Fall 204 Lecture 25 (Nov 3 & 5): Group Steiner Tree Lecturer: Zachary Friggstad Scribe: Zachary Friggstad 25. Group Steiner Tree In this problem, we are given a graph
Lecture: Aggregation of General Biased Signals
 Social Networks and Social Choice Lecture Date: September 7, 2010 Lecture: Aggregation of General Biased Signals Lecturer: Elchanan Mossel Scribe: Miklos Racz So far we have talked about Condorcet s Jury
Social Networks and Social Choice Lecture Date: September 7, 2010 Lecture: Aggregation of General Biased Signals Lecturer: Elchanan Mossel Scribe: Miklos Racz So far we have talked about Condorcet s Jury
Assignment 4: Solutions
 Math 340: Discrete Structures II Assignment 4: Solutions. Random Walks. Consider a random walk on an connected, non-bipartite, undirected graph G. Show that, in the long run, the walk will traverse each
Math 340: Discrete Structures II Assignment 4: Solutions. Random Walks. Consider a random walk on an connected, non-bipartite, undirected graph G. Show that, in the long run, the walk will traverse each
Randomized Algorithms
 Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Lecture 1 : Probabilistic Method
 IITM-CS6845: Theory Jan 04, 01 Lecturer: N.S.Narayanaswamy Lecture 1 : Probabilistic Method Scribe: R.Krithika The probabilistic method is a technique to deal with combinatorial problems by introducing
IITM-CS6845: Theory Jan 04, 01 Lecturer: N.S.Narayanaswamy Lecture 1 : Probabilistic Method Scribe: R.Krithika The probabilistic method is a technique to deal with combinatorial problems by introducing
CPSC 536N: Randomized Algorithms Term 2. Lecture 2
 CPSC 536N: Randomized Algorithms 2014-15 Term 2 Prof. Nick Harvey Lecture 2 University of British Columbia In this lecture we continue our introduction to randomized algorithms by discussing the Max Cut
CPSC 536N: Randomized Algorithms 2014-15 Term 2 Prof. Nick Harvey Lecture 2 University of British Columbia In this lecture we continue our introduction to randomized algorithms by discussing the Max Cut
20.1 2SAT. CS125 Lecture 20 Fall 2016
 CS125 Lecture 20 Fall 2016 20.1 2SAT We show yet another possible way to solve the 2SAT problem. Recall that the input to 2SAT is a logical expression that is the conunction (AND) of a set of clauses,
CS125 Lecture 20 Fall 2016 20.1 2SAT We show yet another possible way to solve the 2SAT problem. Recall that the input to 2SAT is a logical expression that is the conunction (AND) of a set of clauses,
Computing with voting trees
 Computing with voting trees Jennifer Iglesias Nathaniel Ince Po-Shen Loh Abstract The classical paradox of social choice theory asserts that there is no fair way to deterministically select a winner in
Computing with voting trees Jennifer Iglesias Nathaniel Ince Po-Shen Loh Abstract The classical paradox of social choice theory asserts that there is no fair way to deterministically select a winner in
Machine Learning, Midterm Exam: Spring 2008 SOLUTIONS. Q Topic Max. Score Score. 1 Short answer questions 20.
 10-601 Machine Learning, Midterm Exam: Spring 2008 Please put your name on this cover sheet If you need more room to work out your answer to a question, use the back of the page and clearly mark on the
10-601 Machine Learning, Midterm Exam: Spring 2008 Please put your name on this cover sheet If you need more room to work out your answer to a question, use the back of the page and clearly mark on the
Aditya Bhaskara CS 5968/6968, Lecture 1: Introduction and Review 12 January 2016
 Lecture 1: Introduction and Review We begin with a short introduction to the course, and logistics. We then survey some basics about approximation algorithms and probability. We also introduce some of
Lecture 1: Introduction and Review We begin with a short introduction to the course, and logistics. We then survey some basics about approximation algorithms and probability. We also introduce some of
11.1 Set Cover ILP formulation of set cover Deterministic rounding
 CS787: Advanced Algorithms Lecture 11: Randomized Rounding, Concentration Bounds In this lecture we will see some more examples of approximation algorithms based on LP relaxations. This time we will use
CS787: Advanced Algorithms Lecture 11: Randomized Rounding, Concentration Bounds In this lecture we will see some more examples of approximation algorithms based on LP relaxations. This time we will use
Chapter 11. Min Cut Min Cut Problem Definition Some Definitions. By Sariel Har-Peled, December 10, Version: 1.
 Chapter 11 Min Cut By Sariel Har-Peled, December 10, 013 1 Version: 1.0 I built on the sand And it tumbled down, I built on a rock And it tumbled down. Now when I build, I shall begin With the smoke from
Chapter 11 Min Cut By Sariel Har-Peled, December 10, 013 1 Version: 1.0 I built on the sand And it tumbled down, I built on a rock And it tumbled down. Now when I build, I shall begin With the smoke from
CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015
 CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015 1 Introduction The divide-and-conquer strategy is a general paradigm for algorithm design. This strategy
CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015 1 Introduction The divide-and-conquer strategy is a general paradigm for algorithm design. This strategy
On improving matchings in trees, via bounded-length augmentations 1
 On improving matchings in trees, via bounded-length augmentations 1 Julien Bensmail a, Valentin Garnero a, Nicolas Nisse a a Université Côte d Azur, CNRS, Inria, I3S, France Abstract Due to a classical
On improving matchings in trees, via bounded-length augmentations 1 Julien Bensmail a, Valentin Garnero a, Nicolas Nisse a a Université Côte d Azur, CNRS, Inria, I3S, France Abstract Due to a classical
CS361 Homework #3 Solutions
 CS6 Homework # Solutions. Suppose I have a hash table with 5 locations. I would like to know how many items I can store in it before it becomes fairly likely that I have a collision, i.e., that two items
CS6 Homework # Solutions. Suppose I have a hash table with 5 locations. I would like to know how many items I can store in it before it becomes fairly likely that I have a collision, i.e., that two items
CS6999 Probabilistic Methods in Integer Programming Randomized Rounding Andrew D. Smith April 2003
 CS6999 Probabilistic Methods in Integer Programming Randomized Rounding April 2003 Overview 2 Background Randomized Rounding Handling Feasibility Derandomization Advanced Techniques Integer Programming
CS6999 Probabilistic Methods in Integer Programming Randomized Rounding April 2003 Overview 2 Background Randomized Rounding Handling Feasibility Derandomization Advanced Techniques Integer Programming
Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts)
![Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts) Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts)](/thumbs/87/95581149.jpg) Introduction to Algorithms October 13, 2010 Massachusetts Institute of Technology 6.006 Fall 2010 Professors Konstantinos Daskalakis and Patrick Jaillet Quiz 1 Solutions Quiz 1 Solutions Problem 1. We
Introduction to Algorithms October 13, 2010 Massachusetts Institute of Technology 6.006 Fall 2010 Professors Konstantinos Daskalakis and Patrick Jaillet Quiz 1 Solutions Quiz 1 Solutions Problem 1. We
Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( )
![Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( ) Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( )](/thumbs/95/125074181.jpg) Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr Pr = Pr Pr Pr() Pr Pr. We are given three coins and are told that two of the coins are fair and the
Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr Pr = Pr Pr Pr() Pr Pr. We are given three coins and are told that two of the coins are fair and the
Algorithms and Data Structures 2016 Week 5 solutions (Tues 9th - Fri 12th February)
 Algorithms and Data Structures 016 Week 5 solutions (Tues 9th - Fri 1th February) 1. Draw the decision tree (under the assumption of all-distinct inputs) Quicksort for n = 3. answer: (of course you should
Algorithms and Data Structures 016 Week 5 solutions (Tues 9th - Fri 1th February) 1. Draw the decision tree (under the assumption of all-distinct inputs) Quicksort for n = 3. answer: (of course you should
(x 1 +x 2 )(x 1 x 2 )+(x 2 +x 3 )(x 2 x 3 )+(x 3 +x 1 )(x 3 x 1 ).
 CMPSCI611: Verifying Polynomial Identities Lecture 13 Here is a problem that has a polynomial-time randomized solution, but so far no poly-time deterministic solution. Let F be any field and let Q(x 1,...,
CMPSCI611: Verifying Polynomial Identities Lecture 13 Here is a problem that has a polynomial-time randomized solution, but so far no poly-time deterministic solution. Let F be any field and let Q(x 1,...,
CS 6820 Fall 2014 Lectures, October 3-20, 2014
 Analysis of Algorithms Linear Programming Notes CS 6820 Fall 2014 Lectures, October 3-20, 2014 1 Linear programming The linear programming (LP) problem is the following optimization problem. We are given
Analysis of Algorithms Linear Programming Notes CS 6820 Fall 2014 Lectures, October 3-20, 2014 1 Linear programming The linear programming (LP) problem is the following optimization problem. We are given
CS 161 Summer 2009 Homework #2 Sample Solutions
 CS 161 Summer 2009 Homework #2 Sample Solutions Regrade Policy: If you believe an error has been made in the grading of your homework, you may resubmit it for a regrade. If the error consists of more than
CS 161 Summer 2009 Homework #2 Sample Solutions Regrade Policy: If you believe an error has been made in the grading of your homework, you may resubmit it for a regrade. If the error consists of more than
Lecture 2 Sep 5, 2017
 CS 388R: Randomized Algorithms Fall 2017 Lecture 2 Sep 5, 2017 Prof. Eric Price Scribe: V. Orestis Papadigenopoulos and Patrick Rall NOTE: THESE NOTES HAVE NOT BEEN EDITED OR CHECKED FOR CORRECTNESS 1
CS 388R: Randomized Algorithms Fall 2017 Lecture 2 Sep 5, 2017 Prof. Eric Price Scribe: V. Orestis Papadigenopoulos and Patrick Rall NOTE: THESE NOTES HAVE NOT BEEN EDITED OR CHECKED FOR CORRECTNESS 1
Social Choice and Social Networks. Aggregation of General Biased Signals (DRAFT)
 Social Choice and Social Networks Aggregation of General Biased Signals (DRAFT) All rights reserved Elchanan Mossel UC Berkeley 8 Sep 2010 Extending Condorect s Jury Theorem We want to consider extensions
Social Choice and Social Networks Aggregation of General Biased Signals (DRAFT) All rights reserved Elchanan Mossel UC Berkeley 8 Sep 2010 Extending Condorect s Jury Theorem We want to consider extensions
CSE525: Randomized Algorithms and Probabilistic Analysis April 2, Lecture 1
 CSE525: Randomized Algorithms and Probabilistic Analysis April 2, 2013 Lecture 1 Lecturer: Anna Karlin Scribe: Sonya Alexandrova and Eric Lei 1 Introduction The main theme of this class is randomized algorithms.
CSE525: Randomized Algorithms and Probabilistic Analysis April 2, 2013 Lecture 1 Lecturer: Anna Karlin Scribe: Sonya Alexandrova and Eric Lei 1 Introduction The main theme of this class is randomized algorithms.
Balanced Allocation Through Random Walk
 Balanced Allocation Through Random Walk Alan Frieze Samantha Petti November 25, 2017 Abstract We consider the allocation problem in which m (1 ε)dn items are to be allocated to n bins with capacity d.
Balanced Allocation Through Random Walk Alan Frieze Samantha Petti November 25, 2017 Abstract We consider the allocation problem in which m (1 ε)dn items are to be allocated to n bins with capacity d.
From Batch to Transductive Online Learning
 From Batch to Transductive Online Learning Sham Kakade Toyota Technological Institute Chicago, IL 60637 sham@tti-c.org Adam Tauman Kalai Toyota Technological Institute Chicago, IL 60637 kalai@tti-c.org
From Batch to Transductive Online Learning Sham Kakade Toyota Technological Institute Chicago, IL 60637 sham@tti-c.org Adam Tauman Kalai Toyota Technological Institute Chicago, IL 60637 kalai@tti-c.org
Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018
 CS17 Integrated Introduction to Computer Science Klein Contents Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018 1 Tree definitions 1 2 Analysis of mergesort using a binary tree 1 3 Analysis of
CS17 Integrated Introduction to Computer Science Klein Contents Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018 1 Tree definitions 1 2 Analysis of mergesort using a binary tree 1 3 Analysis of
N/4 + N/2 + N = 2N 2.
 CS61B Summer 2006 Instructor: Erin Korber Lecture 24, 7 Aug. 1 Amortized Analysis For some of the data structures we ve discussed (namely hash tables and splay trees), it was claimed that the average time
CS61B Summer 2006 Instructor: Erin Korber Lecture 24, 7 Aug. 1 Amortized Analysis For some of the data structures we ve discussed (namely hash tables and splay trees), it was claimed that the average time
A An Overview of Complexity Theory for the Algorithm Designer
 A An Overview of Complexity Theory for the Algorithm Designer A.1 Certificates and the class NP A decision problem is one whose answer is either yes or no. Two examples are: SAT: Given a Boolean formula
A An Overview of Complexity Theory for the Algorithm Designer A.1 Certificates and the class NP A decision problem is one whose answer is either yes or no. Two examples are: SAT: Given a Boolean formula
Compute the Fourier transform on the first register to get x {0,1} n x 0.
 CS 94 Recursive Fourier Sampling, Simon s Algorithm /5/009 Spring 009 Lecture 3 1 Review Recall that we can write any classical circuit x f(x) as a reversible circuit R f. We can view R f as a unitary
CS 94 Recursive Fourier Sampling, Simon s Algorithm /5/009 Spring 009 Lecture 3 1 Review Recall that we can write any classical circuit x f(x) as a reversible circuit R f. We can view R f as a unitary
Optimal Tree-decomposition Balancing and Reachability on Low Treewidth Graphs
 Optimal Tree-decomposition Balancing and Reachability on Low Treewidth Graphs Krishnendu Chatterjee Rasmus Ibsen-Jensen Andreas Pavlogiannis IST Austria Abstract. We consider graphs with n nodes together
Optimal Tree-decomposition Balancing and Reachability on Low Treewidth Graphs Krishnendu Chatterjee Rasmus Ibsen-Jensen Andreas Pavlogiannis IST Austria Abstract. We consider graphs with n nodes together
14.1 Finding frequent elements in stream
 Chapter 14 Streaming Data Model 14.1 Finding frequent elements in stream A very useful statistics for many applications is to keep track of elements that occur more frequently. It can come in many flavours
Chapter 14 Streaming Data Model 14.1 Finding frequent elements in stream A very useful statistics for many applications is to keep track of elements that occur more frequently. It can come in many flavours
Dominating Set Counting in Graph Classes
 Dominating Set Counting in Graph Classes Shuji Kijima 1, Yoshio Okamoto 2, and Takeaki Uno 3 1 Graduate School of Information Science and Electrical Engineering, Kyushu University, Japan kijima@inf.kyushu-u.ac.jp
Dominating Set Counting in Graph Classes Shuji Kijima 1, Yoshio Okamoto 2, and Takeaki Uno 3 1 Graduate School of Information Science and Electrical Engineering, Kyushu University, Japan kijima@inf.kyushu-u.ac.jp
Noisy binary search and its applications
 Noisy binary search and its applications Richard M. Karp Robert Kleinberg Abstract We study a noisy version of the classic binary search problem of inserting an element into its proper place within an
Noisy binary search and its applications Richard M. Karp Robert Kleinberg Abstract We study a noisy version of the classic binary search problem of inserting an element into its proper place within an
1 Approximate Quantiles and Summaries
 CS 598CSC: Algorithms for Big Data Lecture date: Sept 25, 2014 Instructor: Chandra Chekuri Scribe: Chandra Chekuri Suppose we have a stream a 1, a 2,..., a n of objects from an ordered universe. For simplicity
CS 598CSC: Algorithms for Big Data Lecture date: Sept 25, 2014 Instructor: Chandra Chekuri Scribe: Chandra Chekuri Suppose we have a stream a 1, a 2,..., a n of objects from an ordered universe. For simplicity
Lecture 7: Passive Learning
 CS 880: Advanced Complexity Theory 2/8/2008 Lecture 7: Passive Learning Instructor: Dieter van Melkebeek Scribe: Tom Watson In the previous lectures, we studied harmonic analysis as a tool for analyzing
CS 880: Advanced Complexity Theory 2/8/2008 Lecture 7: Passive Learning Instructor: Dieter van Melkebeek Scribe: Tom Watson In the previous lectures, we studied harmonic analysis as a tool for analyzing
Chapter 5 Data Structures Algorithm Theory WS 2017/18 Fabian Kuhn
 Chapter 5 Data Structures Algorithm Theory WS 2017/18 Fabian Kuhn Priority Queue / Heap Stores (key,data) pairs (like dictionary) But, different set of operations: Initialize-Heap: creates new empty heap
Chapter 5 Data Structures Algorithm Theory WS 2017/18 Fabian Kuhn Priority Queue / Heap Stores (key,data) pairs (like dictionary) But, different set of operations: Initialize-Heap: creates new empty heap
Lower Bounds for Dynamic Connectivity (2004; Pǎtraşcu, Demaine)
 Lower Bounds for Dynamic Connectivity (2004; Pǎtraşcu, Demaine) Mihai Pǎtraşcu, MIT, web.mit.edu/ mip/www/ Index terms: partial-sums problem, prefix sums, dynamic lower bounds Synonyms: dynamic trees 1
Lower Bounds for Dynamic Connectivity (2004; Pǎtraşcu, Demaine) Mihai Pǎtraşcu, MIT, web.mit.edu/ mip/www/ Index terms: partial-sums problem, prefix sums, dynamic lower bounds Synonyms: dynamic trees 1
1 Randomized Computation
 CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds
 Randomized Algorithms Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized
Randomized Algorithms Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized
Biased Quantiles. Flip Korn Graham Cormode S. Muthukrishnan
 Biased Quantiles Graham Cormode cormode@bell-labs.com S. Muthukrishnan muthu@cs.rutgers.edu Flip Korn flip@research.att.com Divesh Srivastava divesh@research.att.com Quantiles Quantiles summarize data
Biased Quantiles Graham Cormode cormode@bell-labs.com S. Muthukrishnan muthu@cs.rutgers.edu Flip Korn flip@research.att.com Divesh Srivastava divesh@research.att.com Quantiles Quantiles summarize data
1 Terminology and setup
 15-451/651: Design & Analysis of Algorithms August 31, 2017 Lecture #2 last changed: August 29, 2017 In this lecture, we will examine some simple, concrete models of computation, each with a precise definition
15-451/651: Design & Analysis of Algorithms August 31, 2017 Lecture #2 last changed: August 29, 2017 In this lecture, we will examine some simple, concrete models of computation, each with a precise definition
Proof Techniques (Review of Math 271)
 Chapter 2 Proof Techniques (Review of Math 271) 2.1 Overview This chapter reviews proof techniques that were probably introduced in Math 271 and that may also have been used in a different way in Phil
Chapter 2 Proof Techniques (Review of Math 271) 2.1 Overview This chapter reviews proof techniques that were probably introduced in Math 271 and that may also have been used in a different way in Phil
Fibonacci Heaps These lecture slides are adapted from CLRS, Chapter 20.
 Fibonacci Heaps These lecture slides are adapted from CLRS, Chapter 20. Princeton University COS 4 Theory of Algorithms Spring 2002 Kevin Wayne Priority Queues Operation mae-heap insert find- delete- union
Fibonacci Heaps These lecture slides are adapted from CLRS, Chapter 20. Princeton University COS 4 Theory of Algorithms Spring 2002 Kevin Wayne Priority Queues Operation mae-heap insert find- delete- union
Ramanujan Graphs of Every Size
 Spectral Graph Theory Lecture 24 Ramanujan Graphs of Every Size Daniel A. Spielman December 2, 2015 Disclaimer These notes are not necessarily an accurate representation of what happened in class. The
Spectral Graph Theory Lecture 24 Ramanujan Graphs of Every Size Daniel A. Spielman December 2, 2015 Disclaimer These notes are not necessarily an accurate representation of what happened in class. The
An analogy from Calculus: limits
 COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
Formalizing Probability. Choosing the Sample Space. Probability Measures
 Formalizing Probability Choosing the Sample Space What do we assign probability to? Intuitively, we assign them to possible events (things that might happen, outcomes of an experiment) Formally, we take
Formalizing Probability Choosing the Sample Space What do we assign probability to? Intuitively, we assign them to possible events (things that might happen, outcomes of an experiment) Formally, we take
Lecture 10 Algorithmic version of the local lemma
 Lecture 10 Algorithmic version of the local lemma Uriel Feige Department of Computer Science and Applied Mathematics The Weizman Institute Rehovot 76100, Israel uriel.feige@weizmann.ac.il June 9, 2014
Lecture 10 Algorithmic version of the local lemma Uriel Feige Department of Computer Science and Applied Mathematics The Weizman Institute Rehovot 76100, Israel uriel.feige@weizmann.ac.il June 9, 2014
CPSC 320 Sample Final Examination December 2013
 CPSC 320 Sample Final Examination December 2013 [10] 1. Answer each of the following questions with true or false. Give a short justification for each of your answers. [5] a. 6 n O(5 n ) lim n + This is
CPSC 320 Sample Final Examination December 2013 [10] 1. Answer each of the following questions with true or false. Give a short justification for each of your answers. [5] a. 6 n O(5 n ) lim n + This is
Homework 4 Solutions
 CS 174: Combinatorics and Discrete Probability Fall 01 Homework 4 Solutions Problem 1. (Exercise 3.4 from MU 5 points) Recall the randomized algorithm discussed in class for finding the median of a set
CS 174: Combinatorics and Discrete Probability Fall 01 Homework 4 Solutions Problem 1. (Exercise 3.4 from MU 5 points) Recall the randomized algorithm discussed in class for finding the median of a set
RANDOM WALKS IN ONE DIMENSION
 RANDOM WALKS IN ONE DIMENSION STEVEN P. LALLEY 1. THE GAMBLER S RUIN PROBLEM 1.1. Statement of the problem. I have A dollars; my colleague Xinyi has B dollars. A cup of coffee at the Sacred Grounds in
RANDOM WALKS IN ONE DIMENSION STEVEN P. LALLEY 1. THE GAMBLER S RUIN PROBLEM 1.1. Statement of the problem. I have A dollars; my colleague Xinyi has B dollars. A cup of coffee at the Sacred Grounds in
CS6375: Machine Learning Gautam Kunapuli. Decision Trees
 Gautam Kunapuli Example: Restaurant Recommendation Example: Develop a model to recommend restaurants to users depending on their past dining experiences. Here, the features are cost (x ) and the user s
Gautam Kunapuli Example: Restaurant Recommendation Example: Develop a model to recommend restaurants to users depending on their past dining experiences. Here, the features are cost (x ) and the user s
F 99 Final Quiz Solutions
 Massachusetts Institute of Technology Handout 53 6.04J/18.06J: Mathematics for Computer Science May 11, 000 Professors David Karger and Nancy Lynch F 99 Final Quiz Solutions Problem 1 [18 points] Injections
Massachusetts Institute of Technology Handout 53 6.04J/18.06J: Mathematics for Computer Science May 11, 000 Professors David Karger and Nancy Lynch F 99 Final Quiz Solutions Problem 1 [18 points] Injections
CS264: Beyond Worst-Case Analysis Lecture #18: Smoothed Complexity and Pseudopolynomial-Time Algorithms
 CS264: Beyond Worst-Case Analysis Lecture #18: Smoothed Complexity and Pseudopolynomial-Time Algorithms Tim Roughgarden March 9, 2017 1 Preamble Our first lecture on smoothed analysis sought a better theoretical
CS264: Beyond Worst-Case Analysis Lecture #18: Smoothed Complexity and Pseudopolynomial-Time Algorithms Tim Roughgarden March 9, 2017 1 Preamble Our first lecture on smoothed analysis sought a better theoretical
Computer Science 385 Analysis of Algorithms Siena College Spring Topic Notes: Limitations of Algorithms
 Computer Science 385 Analysis of Algorithms Siena College Spring 2011 Topic Notes: Limitations of Algorithms We conclude with a discussion of the limitations of the power of algorithms. That is, what kinds
Computer Science 385 Analysis of Algorithms Siena College Spring 2011 Topic Notes: Limitations of Algorithms We conclude with a discussion of the limitations of the power of algorithms. That is, what kinds
MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3
 MA008 p.1/37 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/37 Exercise 1 (from LN 2) Asymptotic Notation When constants appear in exponents
MA008 p.1/37 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/37 Exercise 1 (from LN 2) Asymptotic Notation When constants appear in exponents
CS Communication Complexity: Applications and New Directions
 CS 2429 - Communication Complexity: Applications and New Directions Lecturer: Toniann Pitassi 1 Introduction In this course we will define the basic two-party model of communication, as introduced in the
CS 2429 - Communication Complexity: Applications and New Directions Lecturer: Toniann Pitassi 1 Introduction In this course we will define the basic two-party model of communication, as introduced in the
Midterm Exam 1 (Solutions)
 EECS 6 Probability and Random Processes University of California, Berkeley: Spring 07 Kannan Ramchandran February 3, 07 Midterm Exam (Solutions) Last name First name SID Name of student on your left: Name
EECS 6 Probability and Random Processes University of California, Berkeley: Spring 07 Kannan Ramchandran February 3, 07 Midterm Exam (Solutions) Last name First name SID Name of student on your left: Name
Santa Claus Schedules Jobs on Unrelated Machines
 Santa Claus Schedules Jobs on Unrelated Machines Ola Svensson (osven@kth.se) Royal Institute of Technology - KTH Stockholm, Sweden March 22, 2011 arxiv:1011.1168v2 [cs.ds] 21 Mar 2011 Abstract One of the
Santa Claus Schedules Jobs on Unrelated Machines Ola Svensson (osven@kth.se) Royal Institute of Technology - KTH Stockholm, Sweden March 22, 2011 arxiv:1011.1168v2 [cs.ds] 21 Mar 2011 Abstract One of the
Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16
 600.463 Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16 25.1 Introduction Today we re going to talk about machine learning, but from an
600.463 Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16 25.1 Introduction Today we re going to talk about machine learning, but from an
Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Note 14
 CS 70 Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Note 14 Introduction One of the key properties of coin flips is independence: if you flip a fair coin ten times and get ten
CS 70 Discrete Mathematics and Probability Theory Spring 2016 Rao and Walrand Note 14 Introduction One of the key properties of coin flips is independence: if you flip a fair coin ten times and get ten
RANDOM WALKS AND THE PROBABILITY OF RETURNING HOME
 RANDOM WALKS AND THE PROBABILITY OF RETURNING HOME ELIZABETH G. OMBRELLARO Abstract. This paper is expository in nature. It intuitively explains, using a geometrical and measure theory perspective, why
RANDOM WALKS AND THE PROBABILITY OF RETURNING HOME ELIZABETH G. OMBRELLARO Abstract. This paper is expository in nature. It intuitively explains, using a geometrical and measure theory perspective, why
PRIMES Math Problem Set
 PRIMES Math Problem Set PRIMES 017 Due December 1, 01 Dear PRIMES applicant: This is the PRIMES 017 Math Problem Set. Please send us your solutions as part of your PRIMES application by December 1, 01.
PRIMES Math Problem Set PRIMES 017 Due December 1, 01 Dear PRIMES applicant: This is the PRIMES 017 Math Problem Set. Please send us your solutions as part of your PRIMES application by December 1, 01.
CSC 5170: Theory of Computational Complexity Lecture 4 The Chinese University of Hong Kong 1 February 2010
 CSC 5170: Theory of Computational Complexity Lecture 4 The Chinese University of Hong Kong 1 February 2010 Computational complexity studies the amount of resources necessary to perform given computations.
CSC 5170: Theory of Computational Complexity Lecture 4 The Chinese University of Hong Kong 1 February 2010 Computational complexity studies the amount of resources necessary to perform given computations.
We are going to discuss what it means for a sequence to converge in three stages: First, we define what it means for a sequence to converge to zero
 Chapter Limits of Sequences Calculus Student: lim s n = 0 means the s n are getting closer and closer to zero but never gets there. Instructor: ARGHHHHH! Exercise. Think of a better response for the instructor.
Chapter Limits of Sequences Calculus Student: lim s n = 0 means the s n are getting closer and closer to zero but never gets there. Instructor: ARGHHHHH! Exercise. Think of a better response for the instructor.
Sliding Windows with Limited Storage
 Electronic Colloquium on Computational Complexity, Report No. 178 (2012) Sliding Windows with Limited Storage Paul Beame Computer Science and Engineering University of Washington Seattle, WA 98195-2350
Electronic Colloquium on Computational Complexity, Report No. 178 (2012) Sliding Windows with Limited Storage Paul Beame Computer Science and Engineering University of Washington Seattle, WA 98195-2350
What can you prove by induction?
 MEI CONFERENCE 013 What can you prove by induction? Martyn Parker M.J.Parker@keele.ac.uk Contents Contents iii 1 Splitting Coins.................................................. 1 Convex Polygons................................................
MEI CONFERENCE 013 What can you prove by induction? Martyn Parker M.J.Parker@keele.ac.uk Contents Contents iii 1 Splitting Coins.................................................. 1 Convex Polygons................................................
Final Examination. Adrian Georgi Josh Karen Lee Min Nikos Tina. There are 12 problems totaling 150 points. Total time is 170 minutes.
 Massachusetts Institute of Technology 6.042J/18.062J, Fall 02: Mathematics for Computer Science Prof. Albert Meyer and Dr. Radhika Nagpal Final Examination Your name: Circle the name of your Tutorial Instructor:
Massachusetts Institute of Technology 6.042J/18.062J, Fall 02: Mathematics for Computer Science Prof. Albert Meyer and Dr. Radhika Nagpal Final Examination Your name: Circle the name of your Tutorial Instructor:
Quick Sort Notes , Spring 2010
 Quick Sort Notes 18.310, Spring 2010 0.1 Randomized Median Finding In a previous lecture, we discussed the problem of finding the median of a list of m elements, or more generally the element of rank m.
Quick Sort Notes 18.310, Spring 2010 0.1 Randomized Median Finding In a previous lecture, we discussed the problem of finding the median of a list of m elements, or more generally the element of rank m.
CS 350 Algorithms and Complexity
 CS 350 Algorithms and Complexity Winter 2019 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
CS 350 Algorithms and Complexity Winter 2019 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
Design and Analysis of Algorithms
 Design and Analysis of Algorithms 6.046J/18.401J LECTURE 7 Skip Lists Data structure Randomized insertion With high probability (w.h.p.) bound 7/10/15 Copyright 2001-8 by Leiserson et al L9.1 Skip lists
Design and Analysis of Algorithms 6.046J/18.401J LECTURE 7 Skip Lists Data structure Randomized insertion With high probability (w.h.p.) bound 7/10/15 Copyright 2001-8 by Leiserson et al L9.1 Skip lists
CS 350 Algorithms and Complexity
 1 CS 350 Algorithms and Complexity Fall 2015 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
1 CS 350 Algorithms and Complexity Fall 2015 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
Notes on Logarithmic Lower Bounds in the Cell Probe Model
 Notes on Logarithmic Lower Bounds in the Cell Probe Model Kevin Zatloukal November 10, 2010 1 Overview Paper is by Mihai Pâtraşcu and Erik Demaine. Both were at MIT at the time. (Mihai is now at AT&T Labs.)
Notes on Logarithmic Lower Bounds in the Cell Probe Model Kevin Zatloukal November 10, 2010 1 Overview Paper is by Mihai Pâtraşcu and Erik Demaine. Both were at MIT at the time. (Mihai is now at AT&T Labs.)
1 Maintaining a Dictionary
 15-451/651: Design & Analysis of Algorithms February 1, 2016 Lecture #7: Hashing last changed: January 29, 2016 Hashing is a great practical tool, with an interesting and subtle theory too. In addition
15-451/651: Design & Analysis of Algorithms February 1, 2016 Lecture #7: Hashing last changed: January 29, 2016 Hashing is a great practical tool, with an interesting and subtle theory too. In addition
Randomized Algorithms III Min Cut
 Chapter 11 Randomized Algorithms III Min Cut CS 57: Algorithms, Fall 01 October 1, 01 11.1 Min Cut 11.1.1 Problem Definition 11. Min cut 11..0.1 Min cut G = V, E): undirected graph, n vertices, m edges.
Chapter 11 Randomized Algorithms III Min Cut CS 57: Algorithms, Fall 01 October 1, 01 11.1 Min Cut 11.1.1 Problem Definition 11. Min cut 11..0.1 Min cut G = V, E): undirected graph, n vertices, m edges.
Lecture 5: Probabilistic tools and Applications II
 T-79.7003: Graphs and Networks Fall 2013 Lecture 5: Probabilistic tools and Applications II Lecturer: Charalampos E. Tsourakakis Oct. 11, 2013 5.1 Overview In the first part of today s lecture we will
T-79.7003: Graphs and Networks Fall 2013 Lecture 5: Probabilistic tools and Applications II Lecturer: Charalampos E. Tsourakakis Oct. 11, 2013 5.1 Overview In the first part of today s lecture we will
Notes on Discrete Probability
 Columbia University Handout 3 W4231: Analysis of Algorithms September 21, 1999 Professor Luca Trevisan Notes on Discrete Probability The following notes cover, mostly without proofs, the basic notions
Columbia University Handout 3 W4231: Analysis of Algorithms September 21, 1999 Professor Luca Trevisan Notes on Discrete Probability The following notes cover, mostly without proofs, the basic notions
Exercise Sheet #1 Solutions, Computer Science, A M. Hallett, K. Smith a k n b k = n b + k. a k n b k c 1 n b k. a k n b.
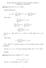 Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Complexity Theory VU , SS The Polynomial Hierarchy. Reinhard Pichler
 Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Outline. Complexity Theory EXACT TSP. The Class DP. Definition. Problem EXACT TSP. Complexity of EXACT TSP. Proposition VU 181.
 Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
CS 246 Review of Proof Techniques and Probability 01/14/19
 Note: This document has been adapted from a similar review session for CS224W (Autumn 2018). It was originally compiled by Jessica Su, with minor edits by Jayadev Bhaskaran. 1 Proof techniques Here we
Note: This document has been adapted from a similar review session for CS224W (Autumn 2018). It was originally compiled by Jessica Su, with minor edits by Jayadev Bhaskaran. 1 Proof techniques Here we
Algorithms for pattern involvement in permutations
 Algorithms for pattern involvement in permutations M. H. Albert Department of Computer Science R. E. L. Aldred Department of Mathematics and Statistics M. D. Atkinson Department of Computer Science D.
Algorithms for pattern involvement in permutations M. H. Albert Department of Computer Science R. E. L. Aldred Department of Mathematics and Statistics M. D. Atkinson Department of Computer Science D.
past balancing schemes require maintenance of balance info at all times, are aggresive use work of searches to pay for work of rebalancing
 1 Splay Trees Sleator and Tarjan, Self Adjusting Binary Search Trees JACM 32(3) 1985 The claim planning ahead. But matches previous idea of being lazy, letting potential build up, using it to pay for expensive
1 Splay Trees Sleator and Tarjan, Self Adjusting Binary Search Trees JACM 32(3) 1985 The claim planning ahead. But matches previous idea of being lazy, letting potential build up, using it to pay for expensive
Search and Lookahead. Bernhard Nebel, Julien Hué, and Stefan Wölfl. June 4/6, 2012
 Search and Lookahead Bernhard Nebel, Julien Hué, and Stefan Wölfl Albert-Ludwigs-Universität Freiburg June 4/6, 2012 Search and Lookahead Enforcing consistency is one way of solving constraint networks:
Search and Lookahead Bernhard Nebel, Julien Hué, and Stefan Wölfl Albert-Ludwigs-Universität Freiburg June 4/6, 2012 Search and Lookahead Enforcing consistency is one way of solving constraint networks:
arxiv: v2 [cs.ds] 3 Oct 2017
![arxiv: v2 [cs.ds] 3 Oct 2017 arxiv: v2 [cs.ds] 3 Oct 2017](/thumbs/84/90870651.jpg) Orthogonal Vectors Indexing Isaac Goldstein 1, Moshe Lewenstein 1, and Ely Porat 1 1 Bar-Ilan University, Ramat Gan, Israel {goldshi,moshe,porately}@cs.biu.ac.il arxiv:1710.00586v2 [cs.ds] 3 Oct 2017 Abstract
Orthogonal Vectors Indexing Isaac Goldstein 1, Moshe Lewenstein 1, and Ely Porat 1 1 Bar-Ilan University, Ramat Gan, Israel {goldshi,moshe,porately}@cs.biu.ac.il arxiv:1710.00586v2 [cs.ds] 3 Oct 2017 Abstract
Assignment 5: Solutions
 Comp 21: Algorithms and Data Structures Assignment : Solutions 1. Heaps. (a) First we remove the minimum key 1 (which we know is located at the root of the heap). We then replace it by the key in the position
Comp 21: Algorithms and Data Structures Assignment : Solutions 1. Heaps. (a) First we remove the minimum key 1 (which we know is located at the root of the heap). We then replace it by the key in the position
Combining Shared Coin Algorithms
 Combining Shared Coin Algorithms James Aspnes Hagit Attiya Keren Censor Abstract This paper shows that shared coin algorithms can be combined to optimize several complexity measures, even in the presence
Combining Shared Coin Algorithms James Aspnes Hagit Attiya Keren Censor Abstract This paper shows that shared coin algorithms can be combined to optimize several complexity measures, even in the presence
CS264: Beyond Worst-Case Analysis Lecture #15: Smoothed Complexity and Pseudopolynomial-Time Algorithms
 CS264: Beyond Worst-Case Analysis Lecture #15: Smoothed Complexity and Pseudopolynomial-Time Algorithms Tim Roughgarden November 5, 2014 1 Preamble Previous lectures on smoothed analysis sought a better
CS264: Beyond Worst-Case Analysis Lecture #15: Smoothed Complexity and Pseudopolynomial-Time Algorithms Tim Roughgarden November 5, 2014 1 Preamble Previous lectures on smoothed analysis sought a better
Lower Bounds for Testing Bipartiteness in Dense Graphs
 Lower Bounds for Testing Bipartiteness in Dense Graphs Andrej Bogdanov Luca Trevisan Abstract We consider the problem of testing bipartiteness in the adjacency matrix model. The best known algorithm, due
Lower Bounds for Testing Bipartiteness in Dense Graphs Andrej Bogdanov Luca Trevisan Abstract We consider the problem of testing bipartiteness in the adjacency matrix model. The best known algorithm, due
Divide-and-Conquer Algorithms Part Two
 Divide-and-Conquer Algorithms Part Two Recap from Last Time Divide-and-Conquer Algorithms A divide-and-conquer algorithm is one that works as follows: (Divide) Split the input apart into multiple smaller
Divide-and-Conquer Algorithms Part Two Recap from Last Time Divide-and-Conquer Algorithms A divide-and-conquer algorithm is one that works as follows: (Divide) Split the input apart into multiple smaller
Skip Lists. What is a Skip List. Skip Lists 3/19/14
 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Skip Lists 15 15 23 10 15 23 36 Skip Lists
Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Skip Lists 15 15 23 10 15 23 36 Skip Lists
Provable Approximation via Linear Programming
 Chapter 7 Provable Approximation via Linear Programming One of the running themes in this course is the notion of approximate solutions. Of course, this notion is tossed around a lot in applied work: whenever
Chapter 7 Provable Approximation via Linear Programming One of the running themes in this course is the notion of approximate solutions. Of course, this notion is tossed around a lot in applied work: whenever
IS 709/809: Computational Methods in IS Research Fall Exam Review
 IS 709/809: Computational Methods in IS Research Fall 2017 Exam Review Nirmalya Roy Department of Information Systems University of Maryland Baltimore County www.umbc.edu Exam When: Tuesday (11/28) 7:10pm
IS 709/809: Computational Methods in IS Research Fall 2017 Exam Review Nirmalya Roy Department of Information Systems University of Maryland Baltimore County www.umbc.edu Exam When: Tuesday (11/28) 7:10pm
Inaccessible Entropy and its Applications. 1 Review: Psedorandom Generators from One-Way Functions
 Columbia University - Crypto Reading Group Apr 27, 2011 Inaccessible Entropy and its Applications Igor Carboni Oliveira We summarize the constructions of PRGs from OWFs discussed so far and introduce the
Columbia University - Crypto Reading Group Apr 27, 2011 Inaccessible Entropy and its Applications Igor Carboni Oliveira We summarize the constructions of PRGs from OWFs discussed so far and introduce the
1 Probability Review. CS 124 Section #8 Hashing, Skip Lists 3/20/17. Expectation (weighted average): the expectation of a random quantity X is:
 CS 24 Section #8 Hashing, Skip Lists 3/20/7 Probability Review Expectation (weighted average): the expectation of a random quantity X is: x= x P (X = x) For each value x that X can take on, we look at
CS 24 Section #8 Hashing, Skip Lists 3/20/7 Probability Review Expectation (weighted average): the expectation of a random quantity X is: x= x P (X = x) For each value x that X can take on, we look at
2 How many distinct elements are in a stream?
 Dealing with Massive Data January 31, 2011 Lecture 2: Distinct Element Counting Lecturer: Sergei Vassilvitskii Scribe:Ido Rosen & Yoonji Shin 1 Introduction We begin by defining the stream formally. Definition
Dealing with Massive Data January 31, 2011 Lecture 2: Distinct Element Counting Lecturer: Sergei Vassilvitskii Scribe:Ido Rosen & Yoonji Shin 1 Introduction We begin by defining the stream formally. Definition
Lecture 5. 1 Review (Pairwise Independence and Derandomization)
 6.842 Randomness and Computation September 20, 2017 Lecture 5 Lecturer: Ronitt Rubinfeld Scribe: Tom Kolokotrones 1 Review (Pairwise Independence and Derandomization) As we discussed last time, we can
6.842 Randomness and Computation September 20, 2017 Lecture 5 Lecturer: Ronitt Rubinfeld Scribe: Tom Kolokotrones 1 Review (Pairwise Independence and Derandomization) As we discussed last time, we can
Stochastic Processes
 qmc082.tex. Version of 30 September 2010. Lecture Notes on Quantum Mechanics No. 8 R. B. Griffiths References: Stochastic Processes CQT = R. B. Griffiths, Consistent Quantum Theory (Cambridge, 2002) DeGroot
qmc082.tex. Version of 30 September 2010. Lecture Notes on Quantum Mechanics No. 8 R. B. Griffiths References: Stochastic Processes CQT = R. B. Griffiths, Consistent Quantum Theory (Cambridge, 2002) DeGroot
1 Ways to Describe a Stochastic Process
 purdue university cs 59000-nmc networks & matrix computations LECTURE NOTES David F. Gleich September 22, 2011 Scribe Notes: Debbie Perouli 1 Ways to Describe a Stochastic Process We will use the biased
purdue university cs 59000-nmc networks & matrix computations LECTURE NOTES David F. Gleich September 22, 2011 Scribe Notes: Debbie Perouli 1 Ways to Describe a Stochastic Process We will use the biased
