Lecture 2 Sep 5, 2017
|
|
|
- Godwin Norris
- 5 years ago
- Views:
Transcription
1 CS 388R: Randomized Algorithms Fall 2017 Lecture 2 Sep 5, 2017 Prof. Eric Price Scribe: V. Orestis Papadigenopoulos and Patrick Rall NOTE: THESE NOTES HAVE NOT BEEN EDITED OR CHECKED FOR CORRECTNESS 1 Overview In the last lecture we got a first taste of randomized algorithms, from definition to conception. We demonstrated the main reasons why randomization is useful and presented different types of such algorithms, as well as two examples, QuickSort and Karger s Min-Cut. In this lecture we make a brief introduction to several fundamental concepts of probabilistic analysis as well as some basic and extremely useful concentration inequalities. Moreover, we discuss the basic randomized complexity classes, as well as some basic relations among them and among other classes of the complexity zoo [?]. 2 Probability Basics and Fundamental Inequalities In this section, we present some basic concepts on the probabilistic analysis, as well as some concentration inequalities that are going to be useful in the reasoning of algorithms during this course. 2.1 Motivation Say we flip an unbiased coin 1000 times. How many heads? Sure, probably 500. But then is it more likely to not get exactly 500? So around 500 I guess? How close to 500? If I get 600 is that a surprise? The number of heads X is given by the binomial distribution: ( ) 1000 X B(1000, 1/2) P[X = x] = x But that gives me no intuition! Let s explore some tools to estimate the probabilities. 2.2 Central Limit Theorem Let X 1...X n be independent, identically distributed (i.i.d.) random variables. Define X = n i=1 X i. Then as n +, we have X N(n E(X i ), nvar(x i )). In other words X approaches the normal distribution with n times the mean and n times the variance. This implies that the average of n 1
2 i.i.d. random variables approaches X N(E(X i ), Var(X i) n ), a fact that explains our intuition that by averaging samples from the same distribution, we become more and more confident about its actual mean value. Let s apply this to our coins. By definition of the variance, we have Var(X i ) = E((X i E(X i )) 2 ) = 1/4. Therefore, for n = 1000 we have σ = Var i X i = i VarX i = n/4 = We can expect to be within 2σ (95% chance), so we probably get 470 to 530 heads. 600 is a big surprise! Unfortunately, even though the Central Limit Theorem is a result of great importance in probability theory, it does not appear to be particularly useful in theoretical computer science and randomized analysis where we care about quantitative results and finite number of elements. In the following, we present several tail inequalities that appear to be extremely useful in our context. 2.3 Chebyshev s inequality The first and simpler concentration bound we present is Markov s inequality. Even though this trivial bound appears to be very loose in many applications, it is useful for proving other, more powerful inequalities. Markov s inequality: t P[y t], therefore: Let X be a non-negative random variable. It is the case that: E(X) P[y t] E(X) t Now, we can use Markov s inequality to prove a way more useful bound: Chebyshev s inequality: values. It is the case that: Let X a random variable of variance σ 2 that can now take negative P [ X E(X) > tσ] 1 t 2 Proof. We would like to bound the probability that X away from its expected value more than t times its standard deviation, that is: P[ X E(X) > tσ]. Since X E(X) is a non-negative random variable, we can show using Markov s that: P[ X E(X) > tσ] = P[(X E(X)) 2 > t 2 σ 2 ] E((X E(X)) 2 ) t 2 σ 2 = 1 t 2 Back to our coin problem, using Chebyshev s inequality for n coins such that E(X) = np and Var(X) = n 4 we have: P [ X E(X) > tσ] 1 t 2 In that case, for n = 1000 coins, the probability of X 500 > 2σ is less than 1 4. In other words, we expect with probability greater than 3/4, the number of heads to be between [468, 516]. 2
3 2.4 Chernoff s inequalities Chebyshev s inequality works well for a constant chance: 1/n. But we really want that Gaussian e x2 fall off! Can we do better? Let X = n i=1 X i, where X i are independent and x i [0, 1] for all i. In this case, it holds that: P [X E(X) + t] e 2t2 n P [X E(X) + t] e 2t2 n Moreover, the multiplicative versions of the above inequalities can be proved useful: P [X (1 + ɛ) E(X)] e ɛ2 2+ɛ µ P [X (1 ɛ) E(X)] e ɛ2 2 µ Back to our coin experiment, we would like to bound using Chernoff the following probability: P [X 500 2σ] e 2 Say we toss 10 6 coins with probability of heads If X = n i=1 X i, we have E(X) = Then: P[negative number of heads] = P[X E(X) 1000] e 2 13% So Chernoff s inequality is the most useful when E(X i ) 1/2, since it gives the best bound so far. At a first glance, it seems weird the fact that on the last case study where the probability of heads is really small the bound stays the same. The reason why this happens is that by definition, Chernoff bounds make no use of the variance of the distribution of each individual sample but only the fact that the value of every sample lays within [0, 1]. 2.5 Application: Amplification Suppose we are given an algorithm to estimate some value V that outputs x i such that x i = V with probability 2 3. How can we learn V with 1 δ probability? Suppose we repeat the algorithm k times and let x 1,, x k the outputs of our trials. If we order them in a non-decreasing way and take the median then the probability that the median is not the correct answer implies that more than half of the k trials gave the wrong answer. Therefore, if we set y i = 1[x i = V ], the event that the i-th sample returned the correct answer, then we know for sure that y i [0, 1] (actually we know the stronger y i {0, 1}). Moreover, we know that E[y i ] = P[y i ] 2 3. Therefore, using the additive Chernoff bound, we can see that: [ k ] [ k ] P y i k k P y i E( y i ) k e 2(k/6)2 k = e k i=1 Therefore, for k 18 log( 1 δ ) we learn V with probability 1 δ. i=1 i=1 3
4 2.6 Application 2: Estimating a biased coin Say we have a coin with unknown bias p. Let s estimate p using ˆp = 1 n need to achieve ˆp p ɛ with probability 1 δ? i X i. How large n do we We are wrong, i.e. ˆp p ɛ, iff X i np nɛ. Using σ = 1/ɛ 2, the Chernoff bound tells us our failure probability is less than 2e 2(ɛn)2 /n = δ. (The factor of 2 comes from the fact that we have to deal with both inequalities above.) Thus we need n 1 2ɛ 2 log 2 δ. What about multiplicative error? Suppose now that we would like to find a ˆp, such that ˆp [1 ɛ, 1 + ɛ]p. Using the multiplicative version of the Chernoff bound to bound P[ ˆp p > ɛp], we get a bound of the form O( 1 1 p log( 1 ɛ 2 δ )). Note that the sample complexity of this bound includes a factor of 1 p, compared to that of the additive estimation. As a result, for small enough p, the sample complexity may increase dramatically! Intuitively, this makes complete sense given the fact that for really small p, the multiplicative error, even for relatively large ɛ depends also on p, a fact that translates into a small additive error. More information about concentration inequalities and their applications can be found in [?,?]. 3 Randomized Complexity Classes Yes-no questions can be expressed as a language L: the set of all inputs x for which the answer is yes. A complexity class is a set of languages, usually defined by the amount of resources given to decide membership: x L or x L. If an algorithm A claims that x L we say A accepts x, or vice-versa A rejects x. An algorithm decides a language L if it accepts iff x L, and rejects iff x L. Here are some relevant classes: P Deterministic Polynomial Time. algorithm that decides L. We have L P iff there exists a polynomial-time NP Nondeterministic Polynomial-Time. We have L NP iff for every input x L there exists some advice string y such that a polynomial-time algorithm can accept x if x L given the advice y. Randomized algorithms follow a similar advice string structure, except that the advice string is random. Think of it as a random seed. In NP there exists an advice string that can help you decide yes-instances. For randomized algorithms we would ideally like most advice strings to work. ZPP Zero-error probabilistic Polynomial-Time. L ZPP iff there exists an algorithm that decides L, and the expected value of its running time is polynomial. Note that this class describes the so-called Las Vegas algorithms. RP Randomized polynomial time. This class has tolerance for one-sided error, that is, L RP iff there exists a polynomial-time algorithm A such that: If x L then A accepts with probability 1/2. If x L then A rejects. 4
5 In Lecture 1 we gave a randomized algorithm for min-cut, which shows that min-cut RP. In this case we can define G min-cut if G is a graph with min-cut c, where c is some constant. The algorithm we gave computed an upper bound c for the input s min-cut, so if we say c c accepts and c > c rejects, then the algorithm sometimes rejects yes-inputs but never accepts no-inputs. PP Probabilistic Polynomial. L PP iff there exists a polynomial-time algorithm A s.t.: If x L then A accepts with probability 1/2. If x L then A rejects with probability 1/2. This class is huge. More specifically: NP PP. (Proof. Guess a random advice string and check it. If it works, accept. If it fails, toss a coin to accept or reject. The tiny bias introduced by possibly guessing the advice string satisfies both inequalities. QED.) PP algorithms are useless in the real world because the success probability cannot be amplified with a reasonable number of repetitions. BPP Bounded Probabilistic Polynomial. L BPP iff a poly-time algorithm A s.t.: If x L then A accepts with probability 2/3. If x L then A rejects with probability 1/3. Actually the numbers 2/3 and 1/3 are arbitrary provided they are not equal. If there is a constant gap between the accept and reject probabilities, then we can amplify the probability as much as we like, just by repeating the algorithm and taking the majority-vote. BPP is probably the best complexity class to reflect the power of randomized algorithms in the real world. What do we know? In general, we know very little about how complexity classes relate. In this case, we do know that: P ZPP RP BPP NP PP What else can we say about BPP other than that BPP NP? The class P/poly is similar to P but algorithms are provided a polynomial-size advice string that cannot depend on the instance x, but only on the language and the size of the instance n. Adelman s theorem: BPP P/poly. Proof. Say we have some L BPP. Take the BPP algorithm and amplify until the failure probability is 1/2 n+1. We will need log(2 n+1 ) n + 1 repetitions, so the algorithm still runs in polynomial time. Say we use y as our advice string, i.e. random seed. For a fixed input x, less than 1/2 n+1 of all possible y cause the algorithm to be incorrect. There exist 2 n possible inputs x of length n. Thus less than 2 n /2 n+1 = 1/2 possible y cause some x to fail. Thus there exist advice strings for which the algorithm always succeeds! Thus L P/poly. A good source for further information on structural (randomized) complexity theory is the book of Arora and Barak: Computational Complexity: A Modern Approach [?] 5
6 References [CZ] Complexity Zoo [MU05] Michael Mitzenmacher and Eli Upfal Probability and Computing: Randomized Algorithms and Probabilistic Analysis Cambridge University Press, New York, [MR95] Rajeev Motwani and Prabhakar Raghavan Randomized Algorithms Cambridge University Press, New York, [AB09] Sanjeev Arora and Boaz Barak Computational Complexity: A Modern Approach Cambridge University Press, New York,
Randomness and non-uniformity
 Randomness and non-uniformity JASS 2006 Course 1: Proofs and Computers Felix Weninger TU München April 2006 Outline Randomized computation 1 Randomized computation 2 Computation with advice Non-uniform
Randomness and non-uniformity JASS 2006 Course 1: Proofs and Computers Felix Weninger TU München April 2006 Outline Randomized computation 1 Randomized computation 2 Computation with advice Non-uniform
20.1 2SAT. CS125 Lecture 20 Fall 2016
 CS125 Lecture 20 Fall 2016 20.1 2SAT We show yet another possible way to solve the 2SAT problem. Recall that the input to 2SAT is a logical expression that is the conunction (AND) of a set of clauses,
CS125 Lecture 20 Fall 2016 20.1 2SAT We show yet another possible way to solve the 2SAT problem. Recall that the input to 2SAT is a logical expression that is the conunction (AND) of a set of clauses,
Randomized Complexity Classes; RP
 Randomized Complexity Classes; RP Let N be a polynomial-time precise NTM that runs in time p(n) and has 2 nondeterministic choices at each step. N is a polynomial Monte Carlo Turing machine for a language
Randomized Complexity Classes; RP Let N be a polynomial-time precise NTM that runs in time p(n) and has 2 nondeterministic choices at each step. N is a polynomial Monte Carlo Turing machine for a language
Lecture 24: Randomized Complexity, Course Summary
 6.045 Lecture 24: Randomized Complexity, Course Summary 1 1/4 1/16 1/4 1/4 1/32 1/16 1/32 Probabilistic TMs 1/16 A probabilistic TM M is a nondeterministic TM where: Each nondeterministic step is called
6.045 Lecture 24: Randomized Complexity, Course Summary 1 1/4 1/16 1/4 1/4 1/32 1/16 1/32 Probabilistic TMs 1/16 A probabilistic TM M is a nondeterministic TM where: Each nondeterministic step is called
Kousha Etessami. U. of Edinburgh, UK. Kousha Etessami (U. of Edinburgh, UK) Discrete Mathematics (Chapter 7) 1 / 13
 Discrete Mathematics & Mathematical Reasoning Chapter 7 (continued): Markov and Chebyshev s Inequalities; and Examples in probability: the birthday problem Kousha Etessami U. of Edinburgh, UK Kousha Etessami
Discrete Mathematics & Mathematical Reasoning Chapter 7 (continued): Markov and Chebyshev s Inequalities; and Examples in probability: the birthday problem Kousha Etessami U. of Edinburgh, UK Kousha Etessami
Notes on Complexity Theory Last updated: November, Lecture 10
 Notes on Complexity Theory Last updated: November, 2015 Lecture 10 Notes by Jonathan Katz, lightly edited by Dov Gordon. 1 Randomized Time Complexity 1.1 How Large is BPP? We know that P ZPP = RP corp
Notes on Complexity Theory Last updated: November, 2015 Lecture 10 Notes by Jonathan Katz, lightly edited by Dov Gordon. 1 Randomized Time Complexity 1.1 How Large is BPP? We know that P ZPP = RP corp
1 Randomized complexity
 80240233: Complexity of Computation Lecture 6 ITCS, Tsinghua Univesity, Fall 2007 23 October 2007 Instructor: Elad Verbin Notes by: Zhang Zhiqiang and Yu Wei 1 Randomized complexity So far our notion of
80240233: Complexity of Computation Lecture 6 ITCS, Tsinghua Univesity, Fall 2007 23 October 2007 Instructor: Elad Verbin Notes by: Zhang Zhiqiang and Yu Wei 1 Randomized complexity So far our notion of
Essentials on the Analysis of Randomized Algorithms
 Essentials on the Analysis of Randomized Algorithms Dimitris Diochnos Feb 0, 2009 Abstract These notes were written with Monte Carlo algorithms primarily in mind. Topics covered are basic (discrete) random
Essentials on the Analysis of Randomized Algorithms Dimitris Diochnos Feb 0, 2009 Abstract These notes were written with Monte Carlo algorithms primarily in mind. Topics covered are basic (discrete) random
Randomized Computation
 Randomized Computation Slides based on S.Aurora, B.Barak. Complexity Theory: A Modern Approach. Ahto Buldas Ahto.Buldas@ut.ee We do not assume anything about the distribution of the instances of the problem
Randomized Computation Slides based on S.Aurora, B.Barak. Complexity Theory: A Modern Approach. Ahto Buldas Ahto.Buldas@ut.ee We do not assume anything about the distribution of the instances of the problem
1 Randomized Computation
 CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
6.842 Randomness and Computation Lecture 5
 6.842 Randomness and Computation 2012-02-22 Lecture 5 Lecturer: Ronitt Rubinfeld Scribe: Michael Forbes 1 Overview Today we will define the notion of a pairwise independent hash function, and discuss its
6.842 Randomness and Computation 2012-02-22 Lecture 5 Lecturer: Ronitt Rubinfeld Scribe: Michael Forbes 1 Overview Today we will define the notion of a pairwise independent hash function, and discuss its
CSC 5170: Theory of Computational Complexity Lecture 5 The Chinese University of Hong Kong 8 February 2010
 CSC 5170: Theory of Computational Complexity Lecture 5 The Chinese University of Hong Kong 8 February 2010 So far our notion of realistic computation has been completely deterministic: The Turing Machine
CSC 5170: Theory of Computational Complexity Lecture 5 The Chinese University of Hong Kong 8 February 2010 So far our notion of realistic computation has been completely deterministic: The Turing Machine
Handout 1: Mathematical Background
 Handout 1: Mathematical Background Boaz Barak September 18, 2007 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete
Handout 1: Mathematical Background Boaz Barak September 18, 2007 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete
Discrete Mathematics for CS Spring 2007 Luca Trevisan Lecture 20
 CS 70 Discrete Mathematics for CS Spring 2007 Luca Trevisan Lecture 20 Today we shall discuss a measure of how close a random variable tends to be to its expectation. But first we need to see how to compute
CS 70 Discrete Mathematics for CS Spring 2007 Luca Trevisan Lecture 20 Today we shall discuss a measure of how close a random variable tends to be to its expectation. But first we need to see how to compute
Lecture 12: Randomness Continued
 CS 710: Complexity Theory 2/25/2010 Lecture 12: Randomness Continued Instructor: Dieter van Melkebeek Scribe: Beth Skubak & Nathan Collins In the last lecture we introduced randomized computation in terms
CS 710: Complexity Theory 2/25/2010 Lecture 12: Randomness Continued Instructor: Dieter van Melkebeek Scribe: Beth Skubak & Nathan Collins In the last lecture we introduced randomized computation in terms
X = X X n, + X 2
 CS 70 Discrete Mathematics for CS Fall 2003 Wagner Lecture 22 Variance Question: At each time step, I flip a fair coin. If it comes up Heads, I walk one step to the right; if it comes up Tails, I walk
CS 70 Discrete Mathematics for CS Fall 2003 Wagner Lecture 22 Variance Question: At each time step, I flip a fair coin. If it comes up Heads, I walk one step to the right; if it comes up Tails, I walk
Notes for Lecture 3... x 4
 Stanford University CS254: Computational Complexity Notes 3 Luca Trevisan January 18, 2012 Notes for Lecture 3 In this lecture we introduce the computational model of boolean circuits and prove that polynomial
Stanford University CS254: Computational Complexity Notes 3 Luca Trevisan January 18, 2012 Notes for Lecture 3 In this lecture we introduce the computational model of boolean circuits and prove that polynomial
Lecture 5. 1 Review (Pairwise Independence and Derandomization)
 6.842 Randomness and Computation September 20, 2017 Lecture 5 Lecturer: Ronitt Rubinfeld Scribe: Tom Kolokotrones 1 Review (Pairwise Independence and Derandomization) As we discussed last time, we can
6.842 Randomness and Computation September 20, 2017 Lecture 5 Lecturer: Ronitt Rubinfeld Scribe: Tom Kolokotrones 1 Review (Pairwise Independence and Derandomization) As we discussed last time, we can
Handout 5. α a1 a n. }, where. xi if a i = 1 1 if a i = 0.
 Notes on Complexity Theory Last updated: October, 2005 Jonathan Katz Handout 5 1 An Improved Upper-Bound on Circuit Size Here we show the result promised in the previous lecture regarding an upper-bound
Notes on Complexity Theory Last updated: October, 2005 Jonathan Katz Handout 5 1 An Improved Upper-Bound on Circuit Size Here we show the result promised in the previous lecture regarding an upper-bound
Overview. Confidence Intervals Sampling and Opinion Polls Error Correcting Codes Number of Pet Unicorns in Ireland
 Overview Confidence Intervals Sampling and Opinion Polls Error Correcting Codes Number of Pet Unicorns in Ireland Confidence Intervals When a random variable lies in an interval a X b with a specified
Overview Confidence Intervals Sampling and Opinion Polls Error Correcting Codes Number of Pet Unicorns in Ireland Confidence Intervals When a random variable lies in an interval a X b with a specified
Adleman Theorem and Sipser Gács Lautemann Theorem. CS422 Computation Theory CS422 Complexity Theory
 Adleman Theorem and Sipser Gács Lautemann Theorem CS422 Computation Theory CS422 Complexity Theory Complexity classes, N, co N, SACE, EXTIME, H, R, RE, ALL, Complexity theorists: "Which is contained in
Adleman Theorem and Sipser Gács Lautemann Theorem CS422 Computation Theory CS422 Complexity Theory Complexity classes, N, co N, SACE, EXTIME, H, R, RE, ALL, Complexity theorists: "Which is contained in
Lecture 8 (Notes) 1. The book Computational Complexity: A Modern Approach by Sanjeev Arora and Boaz Barak;
 Topics in Theoretical Computer Science April 18, 2016 Lecturer: Ola Svensson Lecture 8 (Notes) Scribes: Ola Svensson Disclaimer: These notes were written for the lecturer only and may contain inconsistent
Topics in Theoretical Computer Science April 18, 2016 Lecturer: Ola Svensson Lecture 8 (Notes) Scribes: Ola Svensson Disclaimer: These notes were written for the lecturer only and may contain inconsistent
Lecture Notes 3 Convergence (Chapter 5)
 Lecture Notes 3 Convergence (Chapter 5) 1 Convergence of Random Variables Let X 1, X 2,... be a sequence of random variables and let X be another random variable. Let F n denote the cdf of X n and let
Lecture Notes 3 Convergence (Chapter 5) 1 Convergence of Random Variables Let X 1, X 2,... be a sequence of random variables and let X be another random variable. Let F n denote the cdf of X n and let
CPSC 536N: Randomized Algorithms Term 2. Lecture 2
 CPSC 536N: Randomized Algorithms 2014-15 Term 2 Prof. Nick Harvey Lecture 2 University of British Columbia In this lecture we continue our introduction to randomized algorithms by discussing the Max Cut
CPSC 536N: Randomized Algorithms 2014-15 Term 2 Prof. Nick Harvey Lecture 2 University of British Columbia In this lecture we continue our introduction to randomized algorithms by discussing the Max Cut
Handout 1: Mathematical Background
 Handout 1: Mathematical Background Boaz Barak February 2, 2010 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete math
Handout 1: Mathematical Background Boaz Barak February 2, 2010 This is a brief review of some mathematical tools, especially probability theory that we will use. This material is mostly from discrete math
Stanford University CS254: Computational Complexity Handout 8 Luca Trevisan 4/21/2010
 Stanford University CS254: Computational Complexity Handout 8 Luca Trevisan 4/2/200 Counting Problems Today we describe counting problems and the class #P that they define, and we show that every counting
Stanford University CS254: Computational Complexity Handout 8 Luca Trevisan 4/2/200 Counting Problems Today we describe counting problems and the class #P that they define, and we show that every counting
Lecture Examples of problems which have randomized algorithms
 6.841 Advanced Complexity Theory March 9, 2009 Lecture 10 Lecturer: Madhu Sudan Scribe: Asilata Bapat Meeting to talk about final projects on Wednesday, 11 March 2009, from 5pm to 7pm. Location: TBA. Includes
6.841 Advanced Complexity Theory March 9, 2009 Lecture 10 Lecturer: Madhu Sudan Scribe: Asilata Bapat Meeting to talk about final projects on Wednesday, 11 March 2009, from 5pm to 7pm. Location: TBA. Includes
Randomness and non-uniformity
 Randomness and non-uniformity Felix Weninger April 2006 Abstract In the first part, we introduce randomized algorithms as a new notion of efficient algorithms for decision problems. We classify randomized
Randomness and non-uniformity Felix Weninger April 2006 Abstract In the first part, we introduce randomized algorithms as a new notion of efficient algorithms for decision problems. We classify randomized
Randomized Algorithms
 Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
COMP2610/COMP Information Theory
 COMP2610/COMP6261 - Information Theory Lecture 9: Probabilistic Inequalities Mark Reid and Aditya Menon Research School of Computer Science The Australian National University August 19th, 2014 Mark Reid
COMP2610/COMP6261 - Information Theory Lecture 9: Probabilistic Inequalities Mark Reid and Aditya Menon Research School of Computer Science The Australian National University August 19th, 2014 Mark Reid
Lecture Notes 5 Convergence and Limit Theorems. Convergence with Probability 1. Convergence in Mean Square. Convergence in Probability, WLLN
 Lecture Notes 5 Convergence and Limit Theorems Motivation Convergence with Probability Convergence in Mean Square Convergence in Probability, WLLN Convergence in Distribution, CLT EE 278: Convergence and
Lecture Notes 5 Convergence and Limit Theorems Motivation Convergence with Probability Convergence in Mean Square Convergence in Probability, WLLN Convergence in Distribution, CLT EE 278: Convergence and
3 Multiple Discrete Random Variables
 3 Multiple Discrete Random Variables 3.1 Joint densities Suppose we have a probability space (Ω, F,P) and now we have two discrete random variables X and Y on it. They have probability mass functions f
3 Multiple Discrete Random Variables 3.1 Joint densities Suppose we have a probability space (Ω, F,P) and now we have two discrete random variables X and Y on it. They have probability mass functions f
Topics in Probabilistic Combinatorics and Algorithms Winter, Basic Derandomization Techniques
 Topics in Probabilistic Combinatorics and Algorithms Winter, 016 3. Basic Derandomization Techniques Definition. DTIME(t(n)) : {L : L can be decided deterministically in time O(t(n)).} EXP = { L: L can
Topics in Probabilistic Combinatorics and Algorithms Winter, 016 3. Basic Derandomization Techniques Definition. DTIME(t(n)) : {L : L can be decided deterministically in time O(t(n)).} EXP = { L: L can
Homework 4 Solutions
 CS 174: Combinatorics and Discrete Probability Fall 01 Homework 4 Solutions Problem 1. (Exercise 3.4 from MU 5 points) Recall the randomized algorithm discussed in class for finding the median of a set
CS 174: Combinatorics and Discrete Probability Fall 01 Homework 4 Solutions Problem 1. (Exercise 3.4 from MU 5 points) Recall the randomized algorithm discussed in class for finding the median of a set
CSE 103 Homework 8: Solutions November 30, var(x) = np(1 p) = P r( X ) 0.95 P r( X ) 0.
 () () a. X is a binomial distribution with n = 000, p = /6 b. The expected value, variance, and standard deviation of X is: E(X) = np = 000 = 000 6 var(x) = np( p) = 000 5 6 666 stdev(x) = np( p) = 000
() () a. X is a binomial distribution with n = 000, p = /6 b. The expected value, variance, and standard deviation of X is: E(X) = np = 000 = 000 6 var(x) = np( p) = 000 5 6 666 stdev(x) = np( p) = 000
PROBABILISTIC COMPUTATION. By Remanth Dabbati
 PROBABILISTIC COMPUTATION By Remanth Dabbati INDEX Probabilistic Turing Machine Probabilistic Complexity Classes Probabilistic Algorithms PROBABILISTIC TURING MACHINE It is a turing machine with ability
PROBABILISTIC COMPUTATION By Remanth Dabbati INDEX Probabilistic Turing Machine Probabilistic Complexity Classes Probabilistic Algorithms PROBABILISTIC TURING MACHINE It is a turing machine with ability
Example continued. Math 425 Intro to Probability Lecture 37. Example continued. Example
 continued : Coin tossing Math 425 Intro to Probability Lecture 37 Kenneth Harris kaharri@umich.edu Department of Mathematics University of Michigan April 8, 2009 Consider a Bernoulli trials process with
continued : Coin tossing Math 425 Intro to Probability Lecture 37 Kenneth Harris kaharri@umich.edu Department of Mathematics University of Michigan April 8, 2009 Consider a Bernoulli trials process with
11.1 Set Cover ILP formulation of set cover Deterministic rounding
 CS787: Advanced Algorithms Lecture 11: Randomized Rounding, Concentration Bounds In this lecture we will see some more examples of approximation algorithms based on LP relaxations. This time we will use
CS787: Advanced Algorithms Lecture 11: Randomized Rounding, Concentration Bounds In this lecture we will see some more examples of approximation algorithms based on LP relaxations. This time we will use
Umans Complexity Theory Lectures
 Umans Complexity Theory Lectures Lecture 8: Introduction to Randomized Complexity: - Randomized complexity classes, - Error reduction, - in P/poly - Reingold s Undirected Graph Reachability in RL Randomized
Umans Complexity Theory Lectures Lecture 8: Introduction to Randomized Complexity: - Randomized complexity classes, - Error reduction, - in P/poly - Reingold s Undirected Graph Reachability in RL Randomized
Hypothesis tests
 6.1 6.4 Hypothesis tests Prof. Tesler Math 186 February 26, 2014 Prof. Tesler 6.1 6.4 Hypothesis tests Math 186 / February 26, 2014 1 / 41 6.1 6.2 Intro to hypothesis tests and decision rules Hypothesis
6.1 6.4 Hypothesis tests Prof. Tesler Math 186 February 26, 2014 Prof. Tesler 6.1 6.4 Hypothesis tests Math 186 / February 26, 2014 1 / 41 6.1 6.2 Intro to hypothesis tests and decision rules Hypothesis
2 Natural Proofs: a barrier for proving circuit lower bounds
 Topics in Theoretical Computer Science April 4, 2016 Lecturer: Ola Svensson Lecture 6 (Notes) Scribes: Ola Svensson Disclaimer: These notes were written for the lecturer only and may contain inconsistent
Topics in Theoretical Computer Science April 4, 2016 Lecturer: Ola Svensson Lecture 6 (Notes) Scribes: Ola Svensson Disclaimer: These notes were written for the lecturer only and may contain inconsistent
Lecture 13 (Part 2): Deviation from mean: Markov s inequality, variance and its properties, Chebyshev s inequality
 Lecture 13 (Part 2): Deviation from mean: Markov s inequality, variance and its properties, Chebyshev s inequality Discrete Structures II (Summer 2018) Rutgers University Instructor: Abhishek Bhrushundi
Lecture 13 (Part 2): Deviation from mean: Markov s inequality, variance and its properties, Chebyshev s inequality Discrete Structures II (Summer 2018) Rutgers University Instructor: Abhishek Bhrushundi
Lecture 4: Sampling, Tail Inequalities
 Lecture 4: Sampling, Tail Inequalities Variance and Covariance Moment and Deviation Concentration and Tail Inequalities Sampling and Estimation c Hung Q. Ngo (SUNY at Buffalo) CSE 694 A Fun Course 1 /
Lecture 4: Sampling, Tail Inequalities Variance and Covariance Moment and Deviation Concentration and Tail Inequalities Sampling and Estimation c Hung Q. Ngo (SUNY at Buffalo) CSE 694 A Fun Course 1 /
6.045: Automata, Computability, and Complexity (GITCS) Class 17 Nancy Lynch
 6.045: Automata, Computability, and Complexity (GITCS) Class 17 Nancy Lynch Today Probabilistic Turing Machines and Probabilistic Time Complexity Classes Now add a new capability to standard TMs: random
6.045: Automata, Computability, and Complexity (GITCS) Class 17 Nancy Lynch Today Probabilistic Turing Machines and Probabilistic Time Complexity Classes Now add a new capability to standard TMs: random
Chapter 5 : Randomized computation
 Dr. Abhijit Das, Chapter 5 : Randomized computation Probabilistic or randomized computation often provides practical methods to solve certain computational problems. In order to define probabilistic complexity
Dr. Abhijit Das, Chapter 5 : Randomized computation Probabilistic or randomized computation often provides practical methods to solve certain computational problems. In order to define probabilistic complexity
3 Probabilistic Turing Machines
 CS 252 - Probabilistic Turing Machines (Algorithms) Additional Reading 3 and Homework problems 3 Probabilistic Turing Machines When we talked about computability, we found that nondeterminism was sometimes
CS 252 - Probabilistic Turing Machines (Algorithms) Additional Reading 3 and Homework problems 3 Probabilistic Turing Machines When we talked about computability, we found that nondeterminism was sometimes
Lecture 8. October 22, Department of Biostatistics Johns Hopkins Bloomberg School of Public Health Johns Hopkins University.
 Lecture 8 Department of Biostatistics Johns Hopkins Bloomberg School of Public Health Johns Hopkins University October 22, 2007 1 2 3 4 5 6 1 Define convergent series 2 Define the Law of Large Numbers
Lecture 8 Department of Biostatistics Johns Hopkins Bloomberg School of Public Health Johns Hopkins University October 22, 2007 1 2 3 4 5 6 1 Define convergent series 2 Define the Law of Large Numbers
CS Communication Complexity: Applications and New Directions
 CS 2429 - Communication Complexity: Applications and New Directions Lecturer: Toniann Pitassi 1 Introduction In this course we will define the basic two-party model of communication, as introduced in the
CS 2429 - Communication Complexity: Applications and New Directions Lecturer: Toniann Pitassi 1 Introduction In this course we will define the basic two-party model of communication, as introduced in the
6.895 Randomness and Computation March 19, Lecture Last Lecture: Boosting Weak Learners Into Strong Learners
 6.895 Randomness and Computation March 9, 2008 Lecture 3 Lecturer: Ronitt Rubinfeld Scribe: Edwin Chen Overview. Last Lecture: Boosting Weak Learners Into Strong Learners In the last two lectures, we showed
6.895 Randomness and Computation March 9, 2008 Lecture 3 Lecturer: Ronitt Rubinfeld Scribe: Edwin Chen Overview. Last Lecture: Boosting Weak Learners Into Strong Learners In the last two lectures, we showed
By allowing randomization in the verification process, we obtain a class known as MA.
 Lecture 2 Tel Aviv University, Spring 2006 Quantum Computation Witness-preserving Amplification of QMA Lecturer: Oded Regev Scribe: N. Aharon In the previous class, we have defined the class QMA, which
Lecture 2 Tel Aviv University, Spring 2006 Quantum Computation Witness-preserving Amplification of QMA Lecturer: Oded Regev Scribe: N. Aharon In the previous class, we have defined the class QMA, which
Lecture 12: Interactive Proofs
 princeton university cos 522: computational complexity Lecture 12: Interactive Proofs Lecturer: Sanjeev Arora Scribe:Carl Kingsford Recall the certificate definition of NP. We can think of this characterization
princeton university cos 522: computational complexity Lecture 12: Interactive Proofs Lecturer: Sanjeev Arora Scribe:Carl Kingsford Recall the certificate definition of NP. We can think of this characterization
6.045 Final Exam Solutions
 6.045J/18.400J: Automata, Computability and Complexity Prof. Nancy Lynch, Nati Srebro 6.045 Final Exam Solutions May 18, 2004 Susan Hohenberger Name: Please write your name on each page. This exam is open
6.045J/18.400J: Automata, Computability and Complexity Prof. Nancy Lynch, Nati Srebro 6.045 Final Exam Solutions May 18, 2004 Susan Hohenberger Name: Please write your name on each page. This exam is open
PAC Learning. prof. dr Arno Siebes. Algorithmic Data Analysis Group Department of Information and Computing Sciences Universiteit Utrecht
 PAC Learning prof. dr Arno Siebes Algorithmic Data Analysis Group Department of Information and Computing Sciences Universiteit Utrecht Recall: PAC Learning (Version 1) A hypothesis class H is PAC learnable
PAC Learning prof. dr Arno Siebes Algorithmic Data Analysis Group Department of Information and Computing Sciences Universiteit Utrecht Recall: PAC Learning (Version 1) A hypothesis class H is PAC learnable
CS 151 Complexity Theory Spring Solution Set 5
 CS 151 Complexity Theory Spring 2017 Solution Set 5 Posted: May 17 Chris Umans 1. We are given a Boolean circuit C on n variables x 1, x 2,..., x n with m, and gates. Our 3-CNF formula will have m auxiliary
CS 151 Complexity Theory Spring 2017 Solution Set 5 Posted: May 17 Chris Umans 1. We are given a Boolean circuit C on n variables x 1, x 2,..., x n with m, and gates. Our 3-CNF formula will have m auxiliary
Model Counting for Logical Theories
 Model Counting for Logical Theories Wednesday Dmitry Chistikov Rayna Dimitrova Department of Computer Science University of Oxford, UK Max Planck Institute for Software Systems (MPI-SWS) Kaiserslautern
Model Counting for Logical Theories Wednesday Dmitry Chistikov Rayna Dimitrova Department of Computer Science University of Oxford, UK Max Planck Institute for Software Systems (MPI-SWS) Kaiserslautern
Basic Probability. Introduction
 Basic Probability Introduction The world is an uncertain place. Making predictions about something as seemingly mundane as tomorrow s weather, for example, is actually quite a difficult task. Even with
Basic Probability Introduction The world is an uncertain place. Making predictions about something as seemingly mundane as tomorrow s weather, for example, is actually quite a difficult task. Even with
CSE 312 Final Review: Section AA
 CSE 312 TAs December 8, 2011 General Information General Information Comprehensive Midterm General Information Comprehensive Midterm Heavily weighted toward material after the midterm Pre-Midterm Material
CSE 312 TAs December 8, 2011 General Information General Information Comprehensive Midterm General Information Comprehensive Midterm Heavily weighted toward material after the midterm Pre-Midterm Material
Lecture 26: Arthur-Merlin Games
 CS 710: Complexity Theory 12/09/2011 Lecture 26: Arthur-Merlin Games Instructor: Dieter van Melkebeek Scribe: Chetan Rao and Aaron Gorenstein Last time we compared counting versus alternation and showed
CS 710: Complexity Theory 12/09/2011 Lecture 26: Arthur-Merlin Games Instructor: Dieter van Melkebeek Scribe: Chetan Rao and Aaron Gorenstein Last time we compared counting versus alternation and showed
Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds
 Randomized Algorithms Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized
Randomized Algorithms Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized
Topic: Sampling, Medians of Means method and DNF counting Date: October 6, 2004 Scribe: Florin Oprea
 15-859(M): Randomized Algorithms Lecturer: Shuchi Chawla Topic: Sampling, Medians of Means method and DNF counting Date: October 6, 200 Scribe: Florin Oprea 8.1 Introduction In this lecture we will consider
15-859(M): Randomized Algorithms Lecturer: Shuchi Chawla Topic: Sampling, Medians of Means method and DNF counting Date: October 6, 200 Scribe: Florin Oprea 8.1 Introduction In this lecture we will consider
1 Agenda. 2 History. 3 Probabilistically Checkable Proofs (PCPs). Lecture Notes Definitions. PCPs. Approximation Algorithms.
 CS 221: Computational Complexity Prof. Salil Vadhan Lecture Notes 20 April 12, 2010 Scribe: Jonathan Pines 1 Agenda. PCPs. Approximation Algorithms. PCPs = Inapproximability. 2 History. First, some history
CS 221: Computational Complexity Prof. Salil Vadhan Lecture Notes 20 April 12, 2010 Scribe: Jonathan Pines 1 Agenda. PCPs. Approximation Algorithms. PCPs = Inapproximability. 2 History. First, some history
UC Berkeley, CS 174: Combinatorics and Discrete Probability (Fall 2008) Midterm 1. October 7, 2008
 UC Berkeley, CS 74: Combinatorics and Discrete Probability (Fall 2008) Midterm Instructor: Prof. Yun S. Song October 7, 2008 Your Name : Student ID# : Read these instructions carefully:. This is a closed-book
UC Berkeley, CS 74: Combinatorics and Discrete Probability (Fall 2008) Midterm Instructor: Prof. Yun S. Song October 7, 2008 Your Name : Student ID# : Read these instructions carefully:. This is a closed-book
Lecture 4: Two-point Sampling, Coupon Collector s problem
 Randomized Algorithms Lecture 4: Two-point Sampling, Coupon Collector s problem Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized Algorithms
Randomized Algorithms Lecture 4: Two-point Sampling, Coupon Collector s problem Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized Algorithms
Lecture 1: January 16
 CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 1: January 16 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 1: January 16 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
Quantitative Introduction ro Risk and Uncertainty in Business Module 5: Hypothesis Testing
 Quantitative Introduction ro Risk and Uncertainty in Business Module 5: Hypothesis Testing M. Vidyasagar Cecil & Ida Green Chair The University of Texas at Dallas Email: M.Vidyasagar@utdallas.edu October
Quantitative Introduction ro Risk and Uncertainty in Business Module 5: Hypothesis Testing M. Vidyasagar Cecil & Ida Green Chair The University of Texas at Dallas Email: M.Vidyasagar@utdallas.edu October
Lecture 2: Streaming Algorithms
 CS369G: Algorithmic Techniques for Big Data Spring 2015-2016 Lecture 2: Streaming Algorithms Prof. Moses Chariar Scribes: Stephen Mussmann 1 Overview In this lecture, we first derive a concentration inequality
CS369G: Algorithmic Techniques for Big Data Spring 2015-2016 Lecture 2: Streaming Algorithms Prof. Moses Chariar Scribes: Stephen Mussmann 1 Overview In this lecture, we first derive a concentration inequality
Lecture 23: More PSPACE-Complete, Randomized Complexity
 6.045 Lecture 23: More PSPACE-Complete, Randomized Complexity 1 Final Exam Information Who: You On What: Everything through PSPACE (today) With What: One sheet (double-sided) of notes are allowed When:
6.045 Lecture 23: More PSPACE-Complete, Randomized Complexity 1 Final Exam Information Who: You On What: Everything through PSPACE (today) With What: One sheet (double-sided) of notes are allowed When:
Lecture 2: Review of Basic Probability Theory
 ECE 830 Fall 2010 Statistical Signal Processing instructor: R. Nowak, scribe: R. Nowak Lecture 2: Review of Basic Probability Theory Probabilistic models will be used throughout the course to represent
ECE 830 Fall 2010 Statistical Signal Processing instructor: R. Nowak, scribe: R. Nowak Lecture 2: Review of Basic Probability Theory Probabilistic models will be used throughout the course to represent
Complexity Theory. Jörg Kreiker. Summer term Chair for Theoretical Computer Science Prof. Esparza TU München
 Complexity Theory Jörg Kreiker Chair for Theoretical Computer Science Prof. Esparza TU München Summer term 2010 2 Lecture 15 Public Coins and Graph (Non)Isomorphism 3 Intro Goal and Plan Goal understand
Complexity Theory Jörg Kreiker Chair for Theoretical Computer Science Prof. Esparza TU München Summer term 2010 2 Lecture 15 Public Coins and Graph (Non)Isomorphism 3 Intro Goal and Plan Goal understand
Simulation. Where real stuff starts
 1 Simulation Where real stuff starts ToC 1. What is a simulation? 2. Accuracy of output 3. Random Number Generators 4. How to sample 5. Monte Carlo 6. Bootstrap 2 1. What is a simulation? 3 What is a simulation?
1 Simulation Where real stuff starts ToC 1. What is a simulation? 2. Accuracy of output 3. Random Number Generators 4. How to sample 5. Monte Carlo 6. Bootstrap 2 1. What is a simulation? 3 What is a simulation?
U.C. Berkeley CS278: Computational Complexity Professor Luca Trevisan 1/29/2002. Notes for Lecture 3
 U.C. Bereley CS278: Computational Complexity Handout N3 Professor Luca Trevisan 1/29/2002 Notes for Lecture 3 In this lecture we will define the probabilistic complexity classes BPP, RP, ZPP and we will
U.C. Bereley CS278: Computational Complexity Handout N3 Professor Luca Trevisan 1/29/2002 Notes for Lecture 3 In this lecture we will define the probabilistic complexity classes BPP, RP, ZPP and we will
CSE 312: Foundations of Computing II Quiz Section #10: Review Questions for Final Exam (solutions)
 CSE 312: Foundations of Computing II Quiz Section #10: Review Questions for Final Exam (solutions) 1. (Confidence Intervals, CLT) Let X 1,..., X n be iid with unknown mean θ and known variance σ 2. Assume
CSE 312: Foundations of Computing II Quiz Section #10: Review Questions for Final Exam (solutions) 1. (Confidence Intervals, CLT) Let X 1,..., X n be iid with unknown mean θ and known variance σ 2. Assume
CS 160: Lecture 16. Quantitative Studies. Outline. Random variables and trials. Random variables. Qualitative vs. Quantitative Studies
 Qualitative vs. Quantitative Studies CS 160: Lecture 16 Professor John Canny Qualitative: What we ve been doing so far: * Contextual Inquiry: trying to understand user s tasks and their conceptual model.
Qualitative vs. Quantitative Studies CS 160: Lecture 16 Professor John Canny Qualitative: What we ve been doing so far: * Contextual Inquiry: trying to understand user s tasks and their conceptual model.
Lecture 2: Relativization
 18.405J/6.841J: Advanced Complexity Theory Spring 2016 Lecture 2: Relativization Prof. Dana Moshkovitz Scribe: Di Liu Scribe Date: Fall 2012 Overview. Last week we showed NT IME(n) T ISP (n 1.2, n 0.2
18.405J/6.841J: Advanced Complexity Theory Spring 2016 Lecture 2: Relativization Prof. Dana Moshkovitz Scribe: Di Liu Scribe Date: Fall 2012 Overview. Last week we showed NT IME(n) T ISP (n 1.2, n 0.2
Lecture 10: Probability distributions TUESDAY, FEBRUARY 19, 2019
 Lecture 10: Probability distributions DANIEL WELLER TUESDAY, FEBRUARY 19, 2019 Agenda What is probability? (again) Describing probabilities (distributions) Understanding probabilities (expectation) Partial
Lecture 10: Probability distributions DANIEL WELLER TUESDAY, FEBRUARY 19, 2019 Agenda What is probability? (again) Describing probabilities (distributions) Understanding probabilities (expectation) Partial
CSE 548: Analysis of Algorithms. Lectures 18, 19, 20 & 21 ( Randomized Algorithms & High Probability Bounds )
 CSE 548: Analysis of Algorithms Lectures 18, 19, 20 & 21 ( Randomized Algorithms & High Probability Bounds ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Fall 2012 Markov s Inequality
CSE 548: Analysis of Algorithms Lectures 18, 19, 20 & 21 ( Randomized Algorithms & High Probability Bounds ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Fall 2012 Markov s Inequality
Umans Complexity Theory Lectures
 Complexity Theory Umans Complexity Theory Lectures Lecture 1a: Problems and Languages Classify problems according to the computational resources required running time storage space parallelism randomness
Complexity Theory Umans Complexity Theory Lectures Lecture 1a: Problems and Languages Classify problems according to the computational resources required running time storage space parallelism randomness
6.867 Machine Learning
 6.867 Machine Learning Problem set 1 Solutions Thursday, September 19 What and how to turn in? Turn in short written answers to the questions explicitly stated, and when requested to explain or prove.
6.867 Machine Learning Problem set 1 Solutions Thursday, September 19 What and how to turn in? Turn in short written answers to the questions explicitly stated, and when requested to explain or prove.
Lecture 5: Two-point Sampling
 Randomized Algorithms Lecture 5: Two-point Sampling Sotiris Nikoletseas Professor CEID - ETY Course 2017-2018 Sotiris Nikoletseas, Professor Randomized Algorithms - Lecture 5 1 / 26 Overview A. Pairwise
Randomized Algorithms Lecture 5: Two-point Sampling Sotiris Nikoletseas Professor CEID - ETY Course 2017-2018 Sotiris Nikoletseas, Professor Randomized Algorithms - Lecture 5 1 / 26 Overview A. Pairwise
CS145: Probability & Computing
 CS45: Probability & Computing Lecture 5: Concentration Inequalities, Law of Large Numbers, Central Limit Theorem Instructor: Eli Upfal Brown University Computer Science Figure credits: Bertsekas & Tsitsiklis,
CS45: Probability & Computing Lecture 5: Concentration Inequalities, Law of Large Numbers, Central Limit Theorem Instructor: Eli Upfal Brown University Computer Science Figure credits: Bertsekas & Tsitsiklis,
Learning Theory. Sridhar Mahadevan. University of Massachusetts. p. 1/38
 Learning Theory Sridhar Mahadevan mahadeva@cs.umass.edu University of Massachusetts p. 1/38 Topics Probability theory meet machine learning Concentration inequalities: Chebyshev, Chernoff, Hoeffding, and
Learning Theory Sridhar Mahadevan mahadeva@cs.umass.edu University of Massachusetts p. 1/38 Topics Probability theory meet machine learning Concentration inequalities: Chebyshev, Chernoff, Hoeffding, and
CS261: A Second Course in Algorithms Lecture #18: Five Essential Tools for the Analysis of Randomized Algorithms
 CS261: A Second Course in Algorithms Lecture #18: Five Essential Tools for the Analysis of Randomized Algorithms Tim Roughgarden March 3, 2016 1 Preamble In CS109 and CS161, you learned some tricks of
CS261: A Second Course in Algorithms Lecture #18: Five Essential Tools for the Analysis of Randomized Algorithms Tim Roughgarden March 3, 2016 1 Preamble In CS109 and CS161, you learned some tricks of
Non-Interactive Zero Knowledge (II)
 Non-Interactive Zero Knowledge (II) CS 601.442/642 Modern Cryptography Fall 2017 S 601.442/642 Modern CryptographyNon-Interactive Zero Knowledge (II) Fall 2017 1 / 18 NIZKs for NP: Roadmap Last-time: Transformation
Non-Interactive Zero Knowledge (II) CS 601.442/642 Modern Cryptography Fall 2017 S 601.442/642 Modern CryptographyNon-Interactive Zero Knowledge (II) Fall 2017 1 / 18 NIZKs for NP: Roadmap Last-time: Transformation
Conditional distributions (discrete case)
 Conditional distributions (discrete case) The basic idea behind conditional distributions is simple: Suppose (XY) is a jointly-distributed random vector with a discrete joint distribution. Then we can
Conditional distributions (discrete case) The basic idea behind conditional distributions is simple: Suppose (XY) is a jointly-distributed random vector with a discrete joint distribution. Then we can
Math 105 Course Outline
 Math 105 Course Outline Week 9 Overview This week we give a very brief introduction to random variables and probability theory. Most observable phenomena have at least some element of randomness associated
Math 105 Course Outline Week 9 Overview This week we give a very brief introduction to random variables and probability theory. Most observable phenomena have at least some element of randomness associated
Computability Theory
 CS:4330 Theory of Computation Spring 2018 Computability Theory The class NP Haniel Barbosa Readings for this lecture Chapter 7 of [Sipser 1996], 3rd edition. Section 7.3. Question Why are we unsuccessful
CS:4330 Theory of Computation Spring 2018 Computability Theory The class NP Haniel Barbosa Readings for this lecture Chapter 7 of [Sipser 1996], 3rd edition. Section 7.3. Question Why are we unsuccessful
-bit integers are all in ThC. Th The following problems are complete for PSPACE NPSPACE ATIME QSAT, GEOGRAPHY, SUCCINCT REACH.
 CMPSCI 601: Recall From Last Time Lecture 26 Theorem: All CFL s are in sac. Facts: ITADD, MULT, ITMULT and DIVISION on -bit integers are all in ThC. Th The following problems are complete for PSPACE NPSPACE
CMPSCI 601: Recall From Last Time Lecture 26 Theorem: All CFL s are in sac. Facts: ITADD, MULT, ITMULT and DIVISION on -bit integers are all in ThC. Th The following problems are complete for PSPACE NPSPACE
MA 1125 Lecture 33 - The Sign Test. Monday, December 4, Objectives: Introduce an example of a non-parametric test.
 MA 1125 Lecture 33 - The Sign Test Monday, December 4, 2017 Objectives: Introduce an example of a non-parametric test. For the last topic of the semester we ll look at an example of a non-parametric test.
MA 1125 Lecture 33 - The Sign Test Monday, December 4, 2017 Objectives: Introduce an example of a non-parametric test. For the last topic of the semester we ll look at an example of a non-parametric test.
Expectation is linear. So far we saw that E(X + Y ) = E(X) + E(Y ). Let α R. Then,
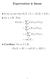 Expectation is linear So far we saw that E(X + Y ) = E(X) + E(Y ). Let α R. Then, E(αX) = ω = ω (αx)(ω) Pr(ω) αx(ω) Pr(ω) = α ω X(ω) Pr(ω) = αe(x). Corollary. For α, β R, E(αX + βy ) = αe(x) + βe(y ).
Expectation is linear So far we saw that E(X + Y ) = E(X) + E(Y ). Let α R. Then, E(αX) = ω = ω (αx)(ω) Pr(ω) αx(ω) Pr(ω) = α ω X(ω) Pr(ω) = αe(x). Corollary. For α, β R, E(αX + βy ) = αe(x) + βe(y ).
Lecture 16 November 6th, 2012 (Prasad Raghavendra)
 6.841: Advanced Complexity Theory Fall 2012 Lecture 16 November 6th, 2012 (Prasad Raghavendra) Prof. Dana Moshkovitz Scribe: Geng Huang 1 Overview In this lecture, we will begin to talk about the PCP Theorem
6.841: Advanced Complexity Theory Fall 2012 Lecture 16 November 6th, 2012 (Prasad Raghavendra) Prof. Dana Moshkovitz Scribe: Geng Huang 1 Overview In this lecture, we will begin to talk about the PCP Theorem
Average Case Complexity: Levin s Theory
 Chapter 15 Average Case Complexity: Levin s Theory 1 needs more work Our study of complexity - NP-completeness, #P-completeness etc. thus far only concerned worst-case complexity. However, algorithms designers
Chapter 15 Average Case Complexity: Levin s Theory 1 needs more work Our study of complexity - NP-completeness, #P-completeness etc. thus far only concerned worst-case complexity. However, algorithms designers
CMPUT 675: Approximation Algorithms Fall 2014
 CMPUT 675: Approximation Algorithms Fall 204 Lecture 25 (Nov 3 & 5): Group Steiner Tree Lecturer: Zachary Friggstad Scribe: Zachary Friggstad 25. Group Steiner Tree In this problem, we are given a graph
CMPUT 675: Approximation Algorithms Fall 204 Lecture 25 (Nov 3 & 5): Group Steiner Tree Lecturer: Zachary Friggstad Scribe: Zachary Friggstad 25. Group Steiner Tree In this problem, we are given a graph
: On the P vs. BPP problem. 30/12/2016 Lecture 11
 03684155: On the P vs. BPP problem. 30/12/2016 Lecture 11 Promise problems Amnon Ta-Shma and Dean Doron 1 Definitions and examples In a promise problem, we are interested in solving a problem only on a
03684155: On the P vs. BPP problem. 30/12/2016 Lecture 11 Promise problems Amnon Ta-Shma and Dean Doron 1 Definitions and examples In a promise problem, we are interested in solving a problem only on a
On the efficient approximability of constraint satisfaction problems
 On the efficient approximability of constraint satisfaction problems July 13, 2007 My world Max-CSP Efficient computation. P Polynomial time BPP Probabilistic Polynomial time (still efficient) NP Non-deterministic
On the efficient approximability of constraint satisfaction problems July 13, 2007 My world Max-CSP Efficient computation. P Polynomial time BPP Probabilistic Polynomial time (still efficient) NP Non-deterministic
Handout 7. and Pr [M(x) = χ L (x) M(x) =? ] = 1.
![Handout 7. and Pr [M(x) = χ L (x) M(x) =? ] = 1. Handout 7. and Pr [M(x) = χ L (x) M(x) =? ] = 1.](/thumbs/77/76481813.jpg) Notes on Coplexity Theory Last updated: October, 2005 Jonathan Katz Handout 7 1 More on Randoized Coplexity Classes Reinder: so far we have seen RP,coRP, and BPP. We introduce two ore tie-bounded randoized
Notes on Coplexity Theory Last updated: October, 2005 Jonathan Katz Handout 7 1 More on Randoized Coplexity Classes Reinder: so far we have seen RP,coRP, and BPP. We introduce two ore tie-bounded randoized
Lecture 7: Chapter 7. Sums of Random Variables and Long-Term Averages
 Lecture 7: Chapter 7. Sums of Random Variables and Long-Term Averages ELEC206 Probability and Random Processes, Fall 2014 Gil-Jin Jang gjang@knu.ac.kr School of EE, KNU page 1 / 15 Chapter 7. Sums of Random
Lecture 7: Chapter 7. Sums of Random Variables and Long-Term Averages ELEC206 Probability and Random Processes, Fall 2014 Gil-Jin Jang gjang@knu.ac.kr School of EE, KNU page 1 / 15 Chapter 7. Sums of Random
CS6999 Probabilistic Methods in Integer Programming Randomized Rounding Andrew D. Smith April 2003
 CS6999 Probabilistic Methods in Integer Programming Randomized Rounding April 2003 Overview 2 Background Randomized Rounding Handling Feasibility Derandomization Advanced Techniques Integer Programming
CS6999 Probabilistic Methods in Integer Programming Randomized Rounding April 2003 Overview 2 Background Randomized Rounding Handling Feasibility Derandomization Advanced Techniques Integer Programming
Poisson approximations
 Chapter 9 Poisson approximations 9.1 Overview The Binn, p) can be thought of as the distribution of a sum of independent indicator random variables X 1 + + X n, with {X i = 1} denoting a head on the ith
Chapter 9 Poisson approximations 9.1 Overview The Binn, p) can be thought of as the distribution of a sum of independent indicator random variables X 1 + + X n, with {X i = 1} denoting a head on the ith
Probabilistically Checkable Proofs. 1 Introduction to Probabilistically Checkable Proofs
 Course Proofs and Computers, JASS 06 Probabilistically Checkable Proofs Lukas Bulwahn May 21, 2006 1 Introduction to Probabilistically Checkable Proofs 1.1 History of Inapproximability Results Before introducing
Course Proofs and Computers, JASS 06 Probabilistically Checkable Proofs Lukas Bulwahn May 21, 2006 1 Introduction to Probabilistically Checkable Proofs 1.1 History of Inapproximability Results Before introducing
Non-Interactive ZK:The Feige-Lapidot-Shamir protocol
 Non-Interactive ZK: The Feige-Lapidot-Shamir protocol April 20, 2009 Remainders FLS protocol Definition (Interactive proof system) A pair of interactive machines (P, V ) is called an interactive proof
Non-Interactive ZK: The Feige-Lapidot-Shamir protocol April 20, 2009 Remainders FLS protocol Definition (Interactive proof system) A pair of interactive machines (P, V ) is called an interactive proof
