On Permissions, Inheritance and Role Hierarchies
|
|
|
- Eric Patterson
- 5 years ago
- Views:
Transcription
1 On Permissions, Inheritance and Role Hierarchies Information Security Group Royal Holloway, University of London
2 Introduction The role hierarchy is central to most RBAC models Modelled as a partially ordered set R The hierarchy makes use of two types of inheritance If permission p is assigned to role r then p is implicitly assigned to all roles s such that r < s If user u is assigned to role r then u is implicitly assigned to all roles s such that s < r
3 Introduction Motivation Consequences of role hierarchy and inheritance Simplification of administration through reduction in number of permission-role and user-role assignments Natural mapping of enterprise characteristics (organizational hierarchy) onto access control model (role hierarchy) Senior roles have access to all permissions assigned to junior roles Difficult to implement separation of duty requirements on roles that have a common senior role Semantics of inheritance make implementation of multilevel secure systems difficult using RBAC models
4 Introduction The Idea An alternative approach to permission inheritance Each permission has an orientation Define explicit and implicit assignment Consider consequences for the implementation of multi-level secure systems
5 Introduction Overview of Talk Define new model for permission inheritance Consider the correspondence between RBAC and MAC Define constraints that are required for new model to implement MAC Concluding remarks Contribution Future work
6 The Basic Model Partially ordered set of roles R User-role assignment relation UA U R We say u is explicitly assigned to r if (u, r) UA We say u is implicitly assigned to r if there exists s such that (u, s) UA and r 6 s Permission-role assignment relation PA P R We say p is explicitly assigned to r if (p, r) PA We denote the set of roles explicitly assigned to p by R(p)
7 Permission Inheritance The set of permissions P is the disjoint union of P +, P and P 0 P + is the set of up permissions P is the set of down permissions P 0 is the set of neutral permissions If every permission is an up permission (P = P 0 = ) then we have the usual permission inheritance semantics of RBAC
8 Implicit Assignment Each permission p is implicitly assigned to a subset of R denoted R I (p) If p P + then R I (p) = {s R : r R(p), r 6 s} If p P then R I (p) = {s R : r R(p), r > s} If p P 0 then R I (p) = R(p) We refer to R I (p) as the effective roles of p
9 Permission Usage In RBAC a user u activates a session S R by selecting a subset of the roles to which u is implicitly assigned A user u will be granted the use of permission p provided u has activated one of the effective roles of p In other words S R I (p)
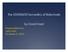
10 Permission Usage p 1, p 2 P + (p 1, r 1 ) PA (p 2, r 2 ) PA u can make use of both p 1 and p 2 by activating r 3 Standard RBAC R I (p 1 ) r 3 r 1 r 2 R I (p 2 ) interpretation
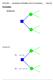
11 Permission Usage p 1 P + (p 1, r 1 ) PA p 2 P (p 2, r 2 ) PA u must activate both r 1 and r 2 to make use of p 1 and p 2 Separation of duty constraints can be defined to prevent this if required R I (p 1 ) r 3 r 1 r 2 R I (p 2 )
12 Permissions A permission p has the form (o, M) where o is an object and M is a set of (access) methods Typically the orientation of a permission will depend on M We define p 6 q if p = (o, M) and q = (o, N) and M N We write p < q if p 6 q and p q This is not the only model for permissions A permission could have the form (O, m) A permission could have the form {(o 1, m 1 ),, (o n, m n )}
13 Constraints If p < q then either p and q have the same orientation or q P 0 The direction of inheritance is consistent with weaker permissions This is essentially a consistency constraint If p < q then R I (p) * R I (q) A permission cannot be implicitly assigned to more roles than a weaker permission This is essentially a redundancy check (what is the point of the weaker permission otherwise?) These constraints are applicable to any model where the set of permissions is partially ordered
14 RBAC and MAC Similarities Permissions Semantics of read permission inheritance in standard RBAC are consistent with interpretation in MAC Security labels Set of roles assigned to u can be regarded as the security label of u Set of roles activated by u in a session can be regarded as the current security label of u The *-property Dynamic permission-based separation of duty
15 RBAC and MAC Differences Permissions Write permissions are not consistent Existing approaches use two different hierarchies Usage is incompatible In RBAC usage is based on existential criterion In MAC usage is based on universal criterion Security labels What is the security label of an object or of a permission?
16 Simulating BLP Permissions We assume there exists a set of access modes M = M r M w It is not necessarily the case that M r M w = A permission of the form (o,{m}) is called an atomic permission (o, M r ) is called a read permission (o, M w ) is called a write permission
17 Simulating BLP Permissions A permission is simple if it is a read or write permission and compound otherwise A permission is minimal (respectively maximal) if it is assigned to a role and any weaker (stronger) permission is not assigned to any role If (o, {m}) is assigned to a role then it is necessarily minimal If a permission is minimal then it is assigned to a unique role
18 Simulating BLP Constraints PA is a function (not a relation) Every permission p is assigned to a unique role r The security level of p is r For each object o there is a unique minimal read permission p r and a unique maximal write permission p w Hence there exists roles r and r min max such that (p r, r min ) PA and (p w, r max ) PA We define the security level of an object to be the range [r min, r max ] = {r R : r min 6 r 6 r max }
19 Simulating BLP Constraints If p < q then R I (q) R I (p) The stronger the permission, the fewer the roles to which it is implicitly assigned This is a stronger condition than the ones defined earlier If p is a write permission then p P If p is a read permission then p P +
20 Simulating BLP Constraints If p is a compound permission then p P 0 A compound permission can only be assigned to a role within the security level of o If r max < r min for o then a compound permission cannot be assigned to any role An audit log file which low level users (must be able to) write to and which only certain high level users can read but no user should be able to both read and write
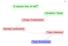
21 Simulating BLP Example M = {r, w} p 1 = (o, {r}) (p 1, r 1 ) PA p 2 = (o, {w}) (p 2, r 1 ) PA Security level of o is {r 1 } p 3 = (o, {r, w}) p 3 can only be assigned to role r 1 Corresponds to security level in BLP R I (p 1 ) r 1 R I (p 2 )
22 Simulating BLP Example M = {r, w} p 1 = (o, {r}) (p 1, r 1 ) PA p 2 = (o, {w}) (p 2, r 2 ) PA Security level of o is {r 1, r 2 } p 3 = (o, {r, w}) p 3 can be assigned to r 1 or r 2 R I (p 1 ) r 1 r 2 R I (p 2 )
23 Simulating BLP Example M = {r, w} p 1 = (o, {r}) (p 1, r 1 ) PA p 2 = (o, {w}) (p 2, r 2 ) PA Security level of o is p 3 = (o, {r, w}) p 3 cannot be assigned to any role R I (p 1 ) r 1 r 2 R I (p 2 )
24 Contributions Permission-based separation of duty is now possible R I (p) R I (q) = Our approach offers more flexibility than standard RBAC models Can assign a permission to a role and propagate that to less senior roles May be useful for assigning permissions to a tree-like directory structure Our approach does not introduce any significant overheads to permission usage checking Provides a simple way to implement multi-level properties using RBAC Previous approaches have typically required the use of a second hierarchy and cannot cope with compound permissions
25 Future Work Simple Security Theorem Define state transitions Define administrative framework (covered in proceedings) We still have the problem that any user assigned to a top role can access all permissions although the problem is less acute because the effective set of roles for a permission means that the user may have to activate a less senior role to make use of it The principle of least privilege is more accurately implemented Assign a floor to each user A floor partitions the role hierarchy A user can only activate roles between the floor and the roles to which he is explicitly assigned
DG/UX System. MAC Regions
 DG/UX System Provides mandatory access controls MAC label identifies security level Default labels, but can define others Initially Subjects assigned MAC label of parent Initial label assigned to user,
DG/UX System Provides mandatory access controls MAC label identifies security level Default labels, but can define others Initially Subjects assigned MAC label of parent Initial label assigned to user,
A formal model for access control with supporting spatial context
 Science in China Series F: Information Sciences 2007 Science in China Press Springer-Verlag A formal model for access control with supporting spatial context ZHANG Hong 1,2, HE YePing 1 & SHI ZhiGuo 1,2
Science in China Series F: Information Sciences 2007 Science in China Press Springer-Verlag A formal model for access control with supporting spatial context ZHANG Hong 1,2, HE YePing 1 & SHI ZhiGuo 1,2
Policy Analysis for Administrative Role Based Access Control
 Policy Analysis for Administrative Role Based Access Control Amit Sasturkar Yahoo! Inc. Ping Yang Binghamton University C.R. Ramakrishnan Stony Brook University Scott D. Stoller Stony Brook University
Policy Analysis for Administrative Role Based Access Control Amit Sasturkar Yahoo! Inc. Ping Yang Binghamton University C.R. Ramakrishnan Stony Brook University Scott D. Stoller Stony Brook University
CityGML in Detail Part 2
 CityGML in Detail Part 2 Prof. Dr. Thomas H. Kolbe Institute for Geodesy and Geoinformation Science Berlin University of Technology kolbe@igg.tu-berlin.de May 2008 EduServ6 Course on CityGML Copyright
CityGML in Detail Part 2 Prof. Dr. Thomas H. Kolbe Institute for Geodesy and Geoinformation Science Berlin University of Technology kolbe@igg.tu-berlin.de May 2008 EduServ6 Course on CityGML Copyright
A Theory for Comparing the Expressive Power of Access Control Models
 A Theory for Comparing the Expressive Power of Access Control Models Mahesh V. Tripunitara Ninghui Li Department of Computer Sciences and CERIAS, Purdue University, West Lafayette, IN 47905. {tripunit,ninghui}@cerias.purdue.edu
A Theory for Comparing the Expressive Power of Access Control Models Mahesh V. Tripunitara Ninghui Li Department of Computer Sciences and CERIAS, Purdue University, West Lafayette, IN 47905. {tripunit,ninghui}@cerias.purdue.edu
CERIAS Tech Report Access Control Policy Management by Qihua Wang Center for Education and Research Information Assurance and Security Purdue
 CERIAS Tech Report 2009-23 Access Control Policy Management by Qihua Wang Center for Education and Research Information Assurance and Security Purdue University, West Lafayette, IN 47907-2086 ACCESS CONTROL
CERIAS Tech Report 2009-23 Access Control Policy Management by Qihua Wang Center for Education and Research Information Assurance and Security Purdue University, West Lafayette, IN 47907-2086 ACCESS CONTROL
An Investigation on an Extension of Mullineux Involution
 An Investigation on an Extension of Mullineux Involution SPUR Final Paper, Summer 06 Arkadiy Frasinich Mentored by Augustus Lonergan Project Suggested By Roman Bezrukavnikov August 3, 06 Abstract In this
An Investigation on an Extension of Mullineux Involution SPUR Final Paper, Summer 06 Arkadiy Frasinich Mentored by Augustus Lonergan Project Suggested By Roman Bezrukavnikov August 3, 06 Abstract In this
Patrol: Revealing Zero-day Attack Paths through Network-wide System Object Dependencies
 Patrol: Revealing Zero-day Attack Paths through Network-wide System Object Dependencies Jun Dai, Xiaoyan Sun, and Peng Liu College of Information Sciences and Technology Pennsylvania State University,
Patrol: Revealing Zero-day Attack Paths through Network-wide System Object Dependencies Jun Dai, Xiaoyan Sun, and Peng Liu College of Information Sciences and Technology Pennsylvania State University,
ORBIT-HOMOGENEITY. Abstract
 Submitted exclusively to the London Mathematical Society DOI: 10.1112/S0000000000000000 ORBIT-HOMOGENEITY PETER J. CAMERON and ALEXANDER W. DENT Abstract We introduce the concept of orbit-homogeneity of
Submitted exclusively to the London Mathematical Society DOI: 10.1112/S0000000000000000 ORBIT-HOMOGENEITY PETER J. CAMERON and ALEXANDER W. DENT Abstract We introduce the concept of orbit-homogeneity of
Some Background Material
 Chapter 1 Some Background Material In the first chapter, we present a quick review of elementary - but important - material as a way of dipping our toes in the water. This chapter also introduces important
Chapter 1 Some Background Material In the first chapter, we present a quick review of elementary - but important - material as a way of dipping our toes in the water. This chapter also introduces important
Analyzing First-order Role Based Access Control
 Analyzing First-order Role Based Access Control Carlos Cotrini, Thilo Weghorn, David Basin, and Manuel Clavel Department of Computer Science ETH Zurich, Switzerland {basin, ccarlos, thiloweghorn}@infethzch
Analyzing First-order Role Based Access Control Carlos Cotrini, Thilo Weghorn, David Basin, and Manuel Clavel Department of Computer Science ETH Zurich, Switzerland {basin, ccarlos, thiloweghorn}@infethzch
SWER ENG 2DM3 Tutorial 2
 Tutorial 2 Min Jing Liu Department of Computing and Software McMaster University Sept 22, 2011 Tutorial 2 Outline 1 Set 2 Function 3 Sequences and Summation Set Set Definition: A set is an unordered collection
Tutorial 2 Min Jing Liu Department of Computing and Software McMaster University Sept 22, 2011 Tutorial 2 Outline 1 Set 2 Function 3 Sequences and Summation Set Set Definition: A set is an unordered collection
Semantic comparison of security policies : from access control policies to flow properties
 2012 IEEE IEEE Sympium CS Security on Security and Privacy and Workshops Privacy Workshops Semantic comparin of security policies : from access control policies to flow properties Mathieu Jaume SPI LIP6
2012 IEEE IEEE Sympium CS Security on Security and Privacy and Workshops Privacy Workshops Semantic comparin of security policies : from access control policies to flow properties Mathieu Jaume SPI LIP6
Outline. Structure-Based Partitioning of Large Concept Hierarchies. Ontologies and the Semantic Web. The Case for Partitioning
 Outline Structure-Based Partitioning of Large Concept Hierarchies Heiner Stuckenschmidt, Michel Klein Vrije Universiteit Amsterdam Motivation: The Case for Ontology Partitioning Lots of Pictures A Partitioning
Outline Structure-Based Partitioning of Large Concept Hierarchies Heiner Stuckenschmidt, Michel Klein Vrije Universiteit Amsterdam Motivation: The Case for Ontology Partitioning Lots of Pictures A Partitioning
On Role Mappings for RBAC-based Secure Interoperation
 2009 Third International Conference on Network and System Security On Role Mappings for RBAC-based Secure Interoperation Jinwei Hu, Ruixuan Li and Zhengding Lu Intelligent and Distributed Computing Lab
2009 Third International Conference on Network and System Security On Role Mappings for RBAC-based Secure Interoperation Jinwei Hu, Ruixuan Li and Zhengding Lu Intelligent and Distributed Computing Lab
Expressing Security Properties Using Selective Interleaving Functions
 Expressing Security Properties Using Selective Interleaving Functions Joseph Halpern and Sabina Petride August 8, 2008 Abstract McLean s notion of Selective Interleaving Functions (SIFs) is perhaps the
Expressing Security Properties Using Selective Interleaving Functions Joseph Halpern and Sabina Petride August 8, 2008 Abstract McLean s notion of Selective Interleaving Functions (SIFs) is perhaps the
A theory for comparing the expressive power of access control models 1
 Journal of Computer Security 15 (2007) 231 272 231 IOS Press A theory for comparing the expressive power of access control models 1 Mahesh V. Tripunitara a, and Ninghui Li b a Motorola Labs, Schaumburg,
Journal of Computer Security 15 (2007) 231 272 231 IOS Press A theory for comparing the expressive power of access control models 1 Mahesh V. Tripunitara a, and Ninghui Li b a Motorola Labs, Schaumburg,
Resiliency Policies in Access Control
 Resiliency Policies in Access Control Ninghui Li Dept of Computer Science Purdue University ninghui@cspurdueedu Mahesh V Tripunitara Motorola Labs tripunit@motorolacom Qihua Wang Dept of Computer Science
Resiliency Policies in Access Control Ninghui Li Dept of Computer Science Purdue University ninghui@cspurdueedu Mahesh V Tripunitara Motorola Labs tripunit@motorolacom Qihua Wang Dept of Computer Science
CS256/Spring 2008 Lecture #11 Zohar Manna. Beyond Temporal Logics
 CS256/Spring 2008 Lecture #11 Zohar Manna Beyond Temporal Logics Temporal logic expresses properties of infinite sequences of states, but there are interesting properties that cannot be expressed, e.g.,
CS256/Spring 2008 Lecture #11 Zohar Manna Beyond Temporal Logics Temporal logic expresses properties of infinite sequences of states, but there are interesting properties that cannot be expressed, e.g.,
Role Mining. Mario Frank and Ian Molloy* 17 th ACM Conference on Computer and Communications Security
 Role Mining Mario Frank and Ian Molloy* 17 th ACM Conference on Computer and Communications Security *M. Frank, I. Molloy (equally contributing) October 5, 2010 CCS 2010, Chicago Problem Definition Role
Role Mining Mario Frank and Ian Molloy* 17 th ACM Conference on Computer and Communications Security *M. Frank, I. Molloy (equally contributing) October 5, 2010 CCS 2010, Chicago Problem Definition Role
Dynamic Enforcement of Abstract Separation of Duty Constraints
 Dynamic Enforcement of Abstract Separation of Duty Constraints David Basin 1, Samuel J. Burri 1,2, and Günter Karjoth 2 1 ETH Zurich, Department of Computer Science, Switzerland 2 IBM Research, Zurich
Dynamic Enforcement of Abstract Separation of Duty Constraints David Basin 1, Samuel J. Burri 1,2, and Günter Karjoth 2 1 ETH Zurich, Department of Computer Science, Switzerland 2 IBM Research, Zurich
SETS AND FUNCTIONS JOSHUA BALLEW
 SETS AND FUNCTIONS JOSHUA BALLEW 1. Sets As a review, we begin by considering a naive look at set theory. For our purposes, we define a set as a collection of objects. Except for certain sets like N, Z,
SETS AND FUNCTIONS JOSHUA BALLEW 1. Sets As a review, we begin by considering a naive look at set theory. For our purposes, we define a set as a collection of objects. Except for certain sets like N, Z,
The Bell-LaPadula Model
 The Bell-LaPadula Model CSM27 Computer Security Dr Hans Georg Schaathun University of Surrey Autumn 2007 Dr Hans Georg Schaathun The Bell-LaPadula Model Autumn 2007 1 / 25 The session Session objectives
The Bell-LaPadula Model CSM27 Computer Security Dr Hans Georg Schaathun University of Surrey Autumn 2007 Dr Hans Georg Schaathun The Bell-LaPadula Model Autumn 2007 1 / 25 The session Session objectives
1 Chapter 1: SETS. 1.1 Describing a set
 1 Chapter 1: SETS set is a collection of objects The objects of the set are called elements or members Use capital letters :, B, C, S, X, Y to denote the sets Use lower case letters to denote the elements:
1 Chapter 1: SETS set is a collection of objects The objects of the set are called elements or members Use capital letters :, B, C, S, X, Y to denote the sets Use lower case letters to denote the elements:
arxiv: v1 [cs.cc] 5 Dec 2018
![arxiv: v1 [cs.cc] 5 Dec 2018 arxiv: v1 [cs.cc] 5 Dec 2018](/thumbs/91/106499182.jpg) Consistency for 0 1 Programming Danial Davarnia 1 and J. N. Hooker 2 1 Iowa state University davarnia@iastate.edu 2 Carnegie Mellon University jh38@andrew.cmu.edu arxiv:1812.02215v1 [cs.cc] 5 Dec 2018
Consistency for 0 1 Programming Danial Davarnia 1 and J. N. Hooker 2 1 Iowa state University davarnia@iastate.edu 2 Carnegie Mellon University jh38@andrew.cmu.edu arxiv:1812.02215v1 [cs.cc] 5 Dec 2018
Lecture 8: Equivalence Relations
 Lecture 8: Equivalence Relations 1 Equivalence Relations Next interesting relation we will study is equivalence relation. Definition 1.1 (Equivalence Relation). Let A be a set and let be a relation on
Lecture 8: Equivalence Relations 1 Equivalence Relations Next interesting relation we will study is equivalence relation. Definition 1.1 (Equivalence Relation). Let A be a set and let be a relation on
Tutorial on Venn-ABERS prediction
 Tutorial on Venn-ABERS prediction Paolo Toccaceli (joint work with Alex Gammerman and Ilia Nouretdinov) Computer Learning Research Centre Royal Holloway, University of London 6th Symposium on Conformal
Tutorial on Venn-ABERS prediction Paolo Toccaceli (joint work with Alex Gammerman and Ilia Nouretdinov) Computer Learning Research Centre Royal Holloway, University of London 6th Symposium on Conformal
Incomplete version for students of easllc2012 only. 6.6 The Model Existence Game 99
 98 First-Order Logic 6.6 The Model Existence Game In this section we learn a new game associated with trying to construct a model for a sentence or a set of sentences. This is of fundamental importance
98 First-Order Logic 6.6 The Model Existence Game In this section we learn a new game associated with trying to construct a model for a sentence or a set of sentences. This is of fundamental importance
3. FORCING NOTION AND GENERIC FILTERS
 3. FORCING NOTION AND GENERIC FILTERS January 19, 2010 BOHUSLAV BALCAR, balcar@math.cas.cz 1 TOMÁŠ PAZÁK, pazak@math.cas.cz 1 JONATHAN VERNER, jonathan.verner@matfyz.cz 2 We now come to the important definition.
3. FORCING NOTION AND GENERIC FILTERS January 19, 2010 BOHUSLAV BALCAR, balcar@math.cas.cz 1 TOMÁŠ PAZÁK, pazak@math.cas.cz 1 JONATHAN VERNER, jonathan.verner@matfyz.cz 2 We now come to the important definition.
Correcting Access Restrictions: a Range-based Approach
 Fakultät Informatik EMCL Master Thesis Correcting Access Restrictions: a Range-based Approach by Eldora born on February 20 th, 1985, Jakarta, Indonesia Supervisor : Prof. Dr.-Ing. Franz Baader Advisors
Fakultät Informatik EMCL Master Thesis Correcting Access Restrictions: a Range-based Approach by Eldora born on February 20 th, 1985, Jakarta, Indonesia Supervisor : Prof. Dr.-Ing. Franz Baader Advisors
Self-Adaptation and Information Flow in Multiparty Communications
 Self-Adaptation and Information Flow in Multiparty Communications Joint work with Ilaria Castellani (INRIA, FR) Jorge A. Pérez (University of Groningen, NL) ABCD meeting London, 20th April, 2015 1 / 36
Self-Adaptation and Information Flow in Multiparty Communications Joint work with Ilaria Castellani (INRIA, FR) Jorge A. Pérez (University of Groningen, NL) ABCD meeting London, 20th April, 2015 1 / 36
SPATIAL DATA MINING. Ms. S. Malathi, Lecturer in Computer Applications, KGiSL - IIM
 SPATIAL DATA MINING Ms. S. Malathi, Lecturer in Computer Applications, KGiSL - IIM INTRODUCTION The main difference between data mining in relational DBS and in spatial DBS is that attributes of the neighbors
SPATIAL DATA MINING Ms. S. Malathi, Lecturer in Computer Applications, KGiSL - IIM INTRODUCTION The main difference between data mining in relational DBS and in spatial DBS is that attributes of the neighbors
Text Mining. Dr. Yanjun Li. Associate Professor. Department of Computer and Information Sciences Fordham University
 Text Mining Dr. Yanjun Li Associate Professor Department of Computer and Information Sciences Fordham University Outline Introduction: Data Mining Part One: Text Mining Part Two: Preprocessing Text Data
Text Mining Dr. Yanjun Li Associate Professor Department of Computer and Information Sciences Fordham University Outline Introduction: Data Mining Part One: Text Mining Part Two: Preprocessing Text Data
Multi-Embedding and Path Approximation of Metric Spaces
 Multi-Embedding and Path Approximation of Metric Spaces Yair Bartal and Manor Mendel mendelma@cshujiacil The Hebrew University Multi-Embedding and Path Approximation of Metric Spaces p1/4 Metric Embedding
Multi-Embedding and Path Approximation of Metric Spaces Yair Bartal and Manor Mendel mendelma@cshujiacil The Hebrew University Multi-Embedding and Path Approximation of Metric Spaces p1/4 Metric Embedding
Equivalence Relations and Partitions, Normal Subgroups, Quotient Groups, and Homomorphisms
 Equivalence Relations and Partitions, Normal Subgroups, Quotient Groups, and Homomorphisms Math 356 Abstract We sum up the main features of our last three class sessions, which list of topics are given
Equivalence Relations and Partitions, Normal Subgroups, Quotient Groups, and Homomorphisms Math 356 Abstract We sum up the main features of our last three class sessions, which list of topics are given
Approximation Metrics for Discrete and Continuous Systems
 University of Pennsylvania ScholarlyCommons Departmental Papers (CIS) Department of Computer & Information Science May 2007 Approximation Metrics for Discrete Continuous Systems Antoine Girard University
University of Pennsylvania ScholarlyCommons Departmental Papers (CIS) Department of Computer & Information Science May 2007 Approximation Metrics for Discrete Continuous Systems Antoine Girard University
Math 564 Homework 1. Solutions.
 Math 564 Homework 1. Solutions. Problem 1. Prove Proposition 0.2.2. A guide to this problem: start with the open set S = (a, b), for example. First assume that a >, and show that the number a has the properties
Math 564 Homework 1. Solutions. Problem 1. Prove Proposition 0.2.2. A guide to this problem: start with the open set S = (a, b), for example. First assume that a >, and show that the number a has the properties
(Permutations Arising from) Hook Coefficients of Chromatic Symmetric Functions
 (Permutations Arising from) Hook Coefficients of Chromatic Symmetric Functions Ryan Kaliszewski Drexel University rlk72@drexel.edu July 17, 2014 Ryan Kaliszewski (Drexel University) Hook Coefficients July
(Permutations Arising from) Hook Coefficients of Chromatic Symmetric Functions Ryan Kaliszewski Drexel University rlk72@drexel.edu July 17, 2014 Ryan Kaliszewski (Drexel University) Hook Coefficients July
2.5.2 Basic CNF/DNF Transformation
 2.5. NORMAL FORMS 39 On the other hand, checking the unsatisfiability of CNF formulas or the validity of DNF formulas is conp-complete. For any propositional formula φ there is an equivalent formula in
2.5. NORMAL FORMS 39 On the other hand, checking the unsatisfiability of CNF formulas or the validity of DNF formulas is conp-complete. For any propositional formula φ there is an equivalent formula in
The STATEMATE Semantics of Statecharts. Presentation by: John Finn October 5, by David Harel
 The STATEMATE Semantics of Statecharts Presentation by: John Finn October 5, 2010 by David Harel Outline Introduction The Basics System Reactions Compound Transitions History Scope of Transitions Conflicting
The STATEMATE Semantics of Statecharts Presentation by: John Finn October 5, 2010 by David Harel Outline Introduction The Basics System Reactions Compound Transitions History Scope of Transitions Conflicting
Automated Symbolic Analysis of ARBAC-Policies
 Automated Symbolic Analysis of ARBAC-Policies (Extended Version) Alessandro Armando 1,2 and Silvio Ranise 2 1 DIST, Università degli Studi di Genova, Italia 2 Security and Trust Unit, FBK, Trento, Italia
Automated Symbolic Analysis of ARBAC-Policies (Extended Version) Alessandro Armando 1,2 and Silvio Ranise 2 1 DIST, Università degli Studi di Genova, Italia 2 Security and Trust Unit, FBK, Trento, Italia
MATHEMATICAL ENGINEERING TECHNICAL REPORTS. Boundary cliques, clique trees and perfect sequences of maximal cliques of a chordal graph
 MATHEMATICAL ENGINEERING TECHNICAL REPORTS Boundary cliques, clique trees and perfect sequences of maximal cliques of a chordal graph Hisayuki HARA and Akimichi TAKEMURA METR 2006 41 July 2006 DEPARTMENT
MATHEMATICAL ENGINEERING TECHNICAL REPORTS Boundary cliques, clique trees and perfect sequences of maximal cliques of a chordal graph Hisayuki HARA and Akimichi TAKEMURA METR 2006 41 July 2006 DEPARTMENT
Designing and Evaluating Generic Ontologies
 Designing and Evaluating Generic Ontologies Michael Grüninger Department of Industrial Engineering University of Toronto gruninger@ie.utoronto.ca August 28, 2007 1 Introduction One of the many uses of
Designing and Evaluating Generic Ontologies Michael Grüninger Department of Industrial Engineering University of Toronto gruninger@ie.utoronto.ca August 28, 2007 1 Introduction One of the many uses of
Distributed storage systems from combinatorial designs
 Distributed storage systems from combinatorial designs Aditya Ramamoorthy November 20, 2014 Department of Electrical and Computer Engineering, Iowa State University, Joint work with Oktay Olmez (Ankara
Distributed storage systems from combinatorial designs Aditya Ramamoorthy November 20, 2014 Department of Electrical and Computer Engineering, Iowa State University, Joint work with Oktay Olmez (Ankara
The Decision List Machine
 The Decision List Machine Marina Sokolova SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 sokolova@site.uottawa.ca Nathalie Japkowicz SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 nat@site.uottawa.ca
The Decision List Machine Marina Sokolova SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 sokolova@site.uottawa.ca Nathalie Japkowicz SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 nat@site.uottawa.ca
Optimal design of experiments
 Optimal design of experiments Session 4: Some theory Peter Goos / 40 Optimal design theory continuous or approximate optimal designs implicitly assume an infinitely large number of observations are available
Optimal design of experiments Session 4: Some theory Peter Goos / 40 Optimal design theory continuous or approximate optimal designs implicitly assume an infinitely large number of observations are available
Sets and Functions. (As we will see, in describing a set the order in which elements are listed is irrelevant).
 Sets and Functions 1. The language of sets Informally, a set is any collection of objects. The objects may be mathematical objects such as numbers, functions and even sets, or letters or symbols of any
Sets and Functions 1. The language of sets Informally, a set is any collection of objects. The objects may be mathematical objects such as numbers, functions and even sets, or letters or symbols of any
Efficient Symbolic Automated Analysis of Administrative Attribute-based RBAC-Policies
 Efficient Symbolic Automated Analysis of Administrative Attribute-based RBAC-Policies Francesco Alberti Università della Svizzera Italiana, Lugano francesco.alberti@usi.ch Alessandro Armando Università
Efficient Symbolic Automated Analysis of Administrative Attribute-based RBAC-Policies Francesco Alberti Università della Svizzera Italiana, Lugano francesco.alberti@usi.ch Alessandro Armando Università
Expressive number restrictions in Description Logics
 Expressive number restrictions in Description Logics Franz Baader and Ulrike Sattler August 12, 1999 Abstract Number restrictions are concept constructors that are available in almost all implemented Description
Expressive number restrictions in Description Logics Franz Baader and Ulrike Sattler August 12, 1999 Abstract Number restrictions are concept constructors that are available in almost all implemented Description
Standard forms for writing numbers
 Standard forms for writing numbers In order to relate the abstract mathematical descriptions of familiar number systems to the everyday descriptions of numbers by decimal expansions and similar means,
Standard forms for writing numbers In order to relate the abstract mathematical descriptions of familiar number systems to the everyday descriptions of numbers by decimal expansions and similar means,
COMPLEXITY OF SHORT RECTANGLES AND PERIODICITY
 COMPLEXITY OF SHORT RECTANGLES AND PERIODICITY VAN CYR AND BRYNA KRA Abstract. The Morse-Hedlund Theorem states that a bi-infinite sequence η in a finite alphabet is periodic if and only if there exists
COMPLEXITY OF SHORT RECTANGLES AND PERIODICITY VAN CYR AND BRYNA KRA Abstract. The Morse-Hedlund Theorem states that a bi-infinite sequence η in a finite alphabet is periodic if and only if there exists
On two-intersection sets with respect to hyperplanes in projective spaces
 with respect to hyperplanes in projective spaces Aart Blokhuis Technische Universiteit Eindhoven, Postbox 513, 5600 MB Eindhoven, The Netherlands and Michel Lavrauw Technische Universiteit Eindhoven, Postbox
with respect to hyperplanes in projective spaces Aart Blokhuis Technische Universiteit Eindhoven, Postbox 513, 5600 MB Eindhoven, The Netherlands and Michel Lavrauw Technische Universiteit Eindhoven, Postbox
Authorized workflow schemas
 Software Tools for Technology Transfer manuscript No. (will be inserted by the editor) Authorized workflow schemas Deciding realizability through LTL(F) model checking Jason Crampton 1, Michael Huth 2,
Software Tools for Technology Transfer manuscript No. (will be inserted by the editor) Authorized workflow schemas Deciding realizability through LTL(F) model checking Jason Crampton 1, Michael Huth 2,
Venn Diagrams; Probability Laws. Notes. Set Operations and Relations. Venn Diagram 2.1. Venn Diagrams; Probability Laws. Notes
 Lecture 2 s; Text: A Course in Probability by Weiss 2.4 STAT 225 Introduction to Probability Models January 8, 2014 s; Whitney Huang Purdue University 2.1 Agenda s; 1 2 2.2 Intersection: the intersection
Lecture 2 s; Text: A Course in Probability by Weiss 2.4 STAT 225 Introduction to Probability Models January 8, 2014 s; Whitney Huang Purdue University 2.1 Agenda s; 1 2 2.2 Intersection: the intersection
EQUIVALENCE OF THE INFORMATION STRUCTURE WITH UNAWARENESS TO THE LOGIC OF AWARENESS. 1. Introduction
 EQUIVALENCE OF THE INFORMATION STRUCTURE WITH UNAWARENESS TO THE LOGIC OF AWARENESS SANDER HEINSALU Abstract. Here it is shown that the unawareness structure in Li (29) is equivalent to a single-agent
EQUIVALENCE OF THE INFORMATION STRUCTURE WITH UNAWARENESS TO THE LOGIC OF AWARENESS SANDER HEINSALU Abstract. Here it is shown that the unawareness structure in Li (29) is equivalent to a single-agent
ORBIT-HOMOGENEITY IN PERMUTATION GROUPS
 Submitted exclusively to the London Mathematical Society DOI: 10.1112/S0000000000000000 ORBIT-HOMOGENEITY IN PERMUTATION GROUPS PETER J. CAMERON and ALEXANDER W. DENT Abstract This paper introduces the
Submitted exclusively to the London Mathematical Society DOI: 10.1112/S0000000000000000 ORBIT-HOMOGENEITY IN PERMUTATION GROUPS PETER J. CAMERON and ALEXANDER W. DENT Abstract This paper introduces the
Reverse Mathematics. Benedict Eastaugh December 13, 2011
 Reverse Mathematics Benedict Eastaugh December 13, 2011 In ordinary mathematical practice, mathematicians prove theorems, reasoning from a fixed 1 set of axioms to a logically derivable conclusion. The
Reverse Mathematics Benedict Eastaugh December 13, 2011 In ordinary mathematical practice, mathematicians prove theorems, reasoning from a fixed 1 set of axioms to a logically derivable conclusion. The
7 The structure of graphs excluding a topological minor
 7 The structure of graphs excluding a topological minor Grohe and Marx [39] proved the following structure theorem for graphs excluding a topological minor: Theorem 7.1 ([39]). For every positive integer
7 The structure of graphs excluding a topological minor Grohe and Marx [39] proved the following structure theorem for graphs excluding a topological minor: Theorem 7.1 ([39]). For every positive integer
ENGI 4421 Introduction to Probability; Sets & Venn Diagrams Page α 2 θ 1 u 3. wear coat. θ 2 = warm u 2 = sweaty! θ 1 = cold u 3 = brrr!
 ENGI 4421 Introduction to Probability; Sets & Venn Diagrams Page 2-01 Probability Decision trees u 1 u 2 α 2 θ 1 u 3 θ 2 u 4 Example 2.01 θ 1 = cold u 1 = snug! α 1 wear coat θ 2 = warm u 2 = sweaty! θ
ENGI 4421 Introduction to Probability; Sets & Venn Diagrams Page 2-01 Probability Decision trees u 1 u 2 α 2 θ 1 u 3 θ 2 u 4 Example 2.01 θ 1 = cold u 1 = snug! α 1 wear coat θ 2 = warm u 2 = sweaty! θ
Finite Model Theory: First-Order Logic on the Class of Finite Models
 1 Finite Model Theory: First-Order Logic on the Class of Finite Models Anuj Dawar University of Cambridge Modnet Tutorial, La Roche, 21 April 2008 2 Finite Model Theory In the 1980s, the term finite model
1 Finite Model Theory: First-Order Logic on the Class of Finite Models Anuj Dawar University of Cambridge Modnet Tutorial, La Roche, 21 April 2008 2 Finite Model Theory In the 1980s, the term finite model
A unifying theory of control dependence and its application to arbitrary program structures
 A unifying theory of control dependence and its application to arbitrary program structures Sebastian Danicic a Richard W. Barraclough b Mark Harman c John D. Howroyd a Ákos Kiss d Michael R. Laurence
A unifying theory of control dependence and its application to arbitrary program structures Sebastian Danicic a Richard W. Barraclough b Mark Harman c John D. Howroyd a Ákos Kiss d Michael R. Laurence
Portal for ArcGIS: An Introduction. Catherine Hynes and Derek Law
 Portal for ArcGIS: An Introduction Catherine Hynes and Derek Law Agenda Web GIS pattern Product overview Installation and deployment Configuration options Security options and groups Portal for ArcGIS
Portal for ArcGIS: An Introduction Catherine Hynes and Derek Law Agenda Web GIS pattern Product overview Installation and deployment Configuration options Security options and groups Portal for ArcGIS
Enhancing the Updatability of Projective Views
 Enhancing the Updatability of Projective Views (Extended Abstract) Paolo Guagliardo 1, Reinhard Pichler 2, and Emanuel Sallinger 2 1 KRDB Research Centre, Free University of Bozen-Bolzano 2 Vienna University
Enhancing the Updatability of Projective Views (Extended Abstract) Paolo Guagliardo 1, Reinhard Pichler 2, and Emanuel Sallinger 2 1 KRDB Research Centre, Free University of Bozen-Bolzano 2 Vienna University
(Type) Constraints. Solving constraints Type inference
 A (quick) tour of ML F (Graphic) Types (Type) Constraints Solving constraints Type inference Type Soundness A Fully Graphical Presentation of ML F Didier Rémy & Boris Yakobowski Didier Le Botlan INRIA
A (quick) tour of ML F (Graphic) Types (Type) Constraints Solving constraints Type inference Type Soundness A Fully Graphical Presentation of ML F Didier Rémy & Boris Yakobowski Didier Le Botlan INRIA
On the number of cycles in a graph with restricted cycle lengths
 On the number of cycles in a graph with restricted cycle lengths Dániel Gerbner, Balázs Keszegh, Cory Palmer, Balázs Patkós arxiv:1610.03476v1 [math.co] 11 Oct 2016 October 12, 2016 Abstract Let L be a
On the number of cycles in a graph with restricted cycle lengths Dániel Gerbner, Balázs Keszegh, Cory Palmer, Balázs Patkós arxiv:1610.03476v1 [math.co] 11 Oct 2016 October 12, 2016 Abstract Let L be a
3. R = = on Z. R, S, A, T.
 6 Relations Let R be a relation on a set A, i.e., a subset of AxA. Notation: xry iff (x, y) R AxA. Recall: A relation need not be a function. Example: The relation R 1 = {(x, y) RxR x 2 + y 2 = 1} is not
6 Relations Let R be a relation on a set A, i.e., a subset of AxA. Notation: xry iff (x, y) R AxA. Recall: A relation need not be a function. Example: The relation R 1 = {(x, y) RxR x 2 + y 2 = 1} is not
Some Formal Analysis of Rocchio s Similarity-Based Relevance Feedback Algorithm
 Some Formal Analysis of Rocchio s Similarity-Based Relevance Feedback Algorithm Zhixiang Chen (chen@cs.panam.edu) Department of Computer Science, University of Texas-Pan American, 1201 West University
Some Formal Analysis of Rocchio s Similarity-Based Relevance Feedback Algorithm Zhixiang Chen (chen@cs.panam.edu) Department of Computer Science, University of Texas-Pan American, 1201 West University
Performing Map Cartography. using Esri Production Mapping
 AGENDA Performing Map Cartography Presentation Title using Esri Production Mapping Name of Speaker Company Name Kannan Jayaraman Agenda Introduction What s New in ArcGIS 10.1 ESRI Production Mapping Mapping
AGENDA Performing Map Cartography Presentation Title using Esri Production Mapping Name of Speaker Company Name Kannan Jayaraman Agenda Introduction What s New in ArcGIS 10.1 ESRI Production Mapping Mapping
Part I. System call overview. Secure Operating System Design and Implementation System Calls. Overview. Abstraction. Jon A. Solworth.
 Secure Operating System Design and Implementation System Calls Jon A. Solworth Part I System call overview Dept. of Computer Science University of Illinois at Chicago February 1, 2011 Overview Abstraction
Secure Operating System Design and Implementation System Calls Jon A. Solworth Part I System call overview Dept. of Computer Science University of Illinois at Chicago February 1, 2011 Overview Abstraction
A Refined Tableau Calculus with Controlled Blocking for the Description Logic SHOI
 A Refined Tableau Calculus with Controlled Blocking for the Description Logic Mohammad Khodadadi, Renate A. Schmidt, and Dmitry Tishkovsky School of Computer Science, The University of Manchester, UK Abstract
A Refined Tableau Calculus with Controlled Blocking for the Description Logic Mohammad Khodadadi, Renate A. Schmidt, and Dmitry Tishkovsky School of Computer Science, The University of Manchester, UK Abstract
The Mixed Chinese Postman Problem Parameterized by Pathwidth and Treedepth
 The Mixed Chinese Postman Problem Parameterized by Pathwidth and Treedepth Gregory Gutin, Mark Jones, and Magnus Wahlström Royal Holloway, University of London Egham, Surrey TW20 0EX, UK Abstract In the
The Mixed Chinese Postman Problem Parameterized by Pathwidth and Treedepth Gregory Gutin, Mark Jones, and Magnus Wahlström Royal Holloway, University of London Egham, Surrey TW20 0EX, UK Abstract In the
COMP9020 Lecture 3 Session 2, 2014 Sets, Functions, and Sequences. Revision: 1.3
 1 COMP9020 Lecture 3 Session 2, 2014 Sets, Functions, and Sequences Revision: 1.3 2 Notation for Numbers Definition Integers Z = {... 2, 1, 0, 1, 2,...} Reals R. : R Z floor of x, the greatest integer
1 COMP9020 Lecture 3 Session 2, 2014 Sets, Functions, and Sequences Revision: 1.3 2 Notation for Numbers Definition Integers Z = {... 2, 1, 0, 1, 2,...} Reals R. : R Z floor of x, the greatest integer
Amobile satellite communication system, like Motorola s
 I TRANSACTIONS ON INFORMATION THORY, VOL. 45, NO. 4, MAY 1999 1111 Distributed Source Coding for Satellite Communications Raymond W. Yeung, Senior Member, I, Zhen Zhang, Senior Member, I Abstract Inspired
I TRANSACTIONS ON INFORMATION THORY, VOL. 45, NO. 4, MAY 1999 1111 Distributed Source Coding for Satellite Communications Raymond W. Yeung, Senior Member, I, Zhen Zhang, Senior Member, I Abstract Inspired
D, such that f(u) = f(v) whenever u = v, has a multiplicative refinement g : [λ] <ℵ 0
![D, such that f(u) = f(v) whenever u = v, has a multiplicative refinement g : [λ] <ℵ 0 D, such that f(u) = f(v) whenever u = v, has a multiplicative refinement g : [λ] <ℵ 0](/thumbs/88/117459599.jpg) Maryanthe Malliaris and Saharon Shelah. Cofinality spectrum problems in model theory, set theory and general topology. J. Amer. Math. Soc., vol. 29 (2016), pp. 237-297. Maryanthe Malliaris and Saharon
Maryanthe Malliaris and Saharon Shelah. Cofinality spectrum problems in model theory, set theory and general topology. J. Amer. Math. Soc., vol. 29 (2016), pp. 237-297. Maryanthe Malliaris and Saharon
Connectivity of addable graph classes
 Connectivity of addable graph classes Paul Balister Béla Bollobás Stefanie Gerke July 6, 008 A non-empty class A of labelled graphs is weakly addable if for each graph G A and any two distinct components
Connectivity of addable graph classes Paul Balister Béla Bollobás Stefanie Gerke July 6, 008 A non-empty class A of labelled graphs is weakly addable if for each graph G A and any two distinct components
The matrix approach for abstract argumentation frameworks
 The matrix approach for abstract argumentation frameworks Claudette CAYROL, Yuming XU IRIT Report RR- -2015-01- -FR February 2015 Abstract The matrices and the operation of dual interchange are introduced
The matrix approach for abstract argumentation frameworks Claudette CAYROL, Yuming XU IRIT Report RR- -2015-01- -FR February 2015 Abstract The matrices and the operation of dual interchange are introduced
Part 1: Fundamentals
 Provläsningsexemplar / Preview INTERNATIONAL STANDARD ISO 19101-1 First edition 2014-11-15 Geographic information Reference model Part 1: Fundamentals Information géographique Modèle de référence Partie
Provläsningsexemplar / Preview INTERNATIONAL STANDARD ISO 19101-1 First edition 2014-11-15 Geographic information Reference model Part 1: Fundamentals Information géographique Modèle de référence Partie
Non-impeding Noisy-AND Tree Causal Models Over Multi-valued Variables
 Non-impeding Noisy-AND Tree Causal Models Over Multi-valued Variables Yang Xiang School of Computer Science, University of Guelph, Canada Abstract To specify a Bayesian network (BN), a conditional probability
Non-impeding Noisy-AND Tree Causal Models Over Multi-valued Variables Yang Xiang School of Computer Science, University of Guelph, Canada Abstract To specify a Bayesian network (BN), a conditional probability
Orbitopes. Marc Pfetsch. joint work with Volker Kaibel. Zuse Institute Berlin
 Orbitopes Marc Pfetsch joint work with Volker Kaibel Zuse Institute Berlin What this talk is about We introduce orbitopes. A polyhedral way to break symmetries in integer programs. Introduction 2 Orbitopes
Orbitopes Marc Pfetsch joint work with Volker Kaibel Zuse Institute Berlin What this talk is about We introduce orbitopes. A polyhedral way to break symmetries in integer programs. Introduction 2 Orbitopes
12th AGILE International Conference on Geographic Information Science 2009 page 1 of 9 Leibniz Universität Hannover, Germany
 12th AGILE International Conference on Geographic Information Science 2009 page 1 of 9 A Framework for the Generalization of 3D City Models Richard Guercke and Claus Brenner Institute of Cartography and
12th AGILE International Conference on Geographic Information Science 2009 page 1 of 9 A Framework for the Generalization of 3D City Models Richard Guercke and Claus Brenner Institute of Cartography and
Definite Logic Programs
 Chapter 2 Definite Logic Programs 2.1 Definite Clauses The idea of logic programming is to use a computer for drawing conclusions from declarative descriptions. Such descriptions called logic programs
Chapter 2 Definite Logic Programs 2.1 Definite Clauses The idea of logic programming is to use a computer for drawing conclusions from declarative descriptions. Such descriptions called logic programs
Distinct Difference Configurations
 Distinct Difference Configurations Simon R. Blackburn Joint work with: Tuvi Etzion, Keith M. Martin, Maura B. Paterson Royal Holloway, University of London 16th July 009 S.R. Blackburn (RHUL) Distinct
Distinct Difference Configurations Simon R. Blackburn Joint work with: Tuvi Etzion, Keith M. Martin, Maura B. Paterson Royal Holloway, University of London 16th July 009 S.R. Blackburn (RHUL) Distinct
3. Only sequences that were formed by using finitely many applications of rules 1 and 2, are propositional formulas.
 1 Chapter 1 Propositional Logic Mathematical logic studies correct thinking, correct deductions of statements from other statements. Let us make it more precise. A fundamental property of a statement is
1 Chapter 1 Propositional Logic Mathematical logic studies correct thinking, correct deductions of statements from other statements. Let us make it more precise. A fundamental property of a statement is
Diagrams for Meaning Preservation
 Diagrams for Meaning Preservation 2003-06-13 Joe Wells Detlef Plump Fairouz Kamareddine Heriot-Watt University University of York www.cee.hw.ac.uk/ultra www.cs.york.ac.uk/ det Diagrams for Meaning Preservation
Diagrams for Meaning Preservation 2003-06-13 Joe Wells Detlef Plump Fairouz Kamareddine Heriot-Watt University University of York www.cee.hw.ac.uk/ultra www.cs.york.ac.uk/ det Diagrams for Meaning Preservation
Mandatory Access Control (MAC)
 CS 5323 Mandatory Access Control (MAC) Prof. Ravi Sandhu Executive Director and Endowed Chair Lecture 3 ravi.utsa@gmail.com www.profsandhu.com Ravi Sandhu 1 CS 5323 Lattice-Based Access Control (LBAC)
CS 5323 Mandatory Access Control (MAC) Prof. Ravi Sandhu Executive Director and Endowed Chair Lecture 3 ravi.utsa@gmail.com www.profsandhu.com Ravi Sandhu 1 CS 5323 Lattice-Based Access Control (LBAC)
Secure Indexes* Eu-Jin Goh Stanford University 15 March 2004
 Secure Indexes* Eu-Jin Goh Stanford University 15 March 2004 * Generalizes an early version of my paper How to search on encrypted data on eprint Cryptology Archive on 7 October 2003 Secure Indexes Data
Secure Indexes* Eu-Jin Goh Stanford University 15 March 2004 * Generalizes an early version of my paper How to search on encrypted data on eprint Cryptology Archive on 7 October 2003 Secure Indexes Data
Computing Least Common Subsumers in Description Logics with Existential Restrictions*
 Computing Least Common Subsumers in Description Logics with Existential Restrictions* Franz Baader, Ralf Kiisters, Ralf Molitor LuFg Theoretische Informatik, RWTH Aachen email: {baader,kuesters,molitor}@infonnatik.rwth-aachcn.dc
Computing Least Common Subsumers in Description Logics with Existential Restrictions* Franz Baader, Ralf Kiisters, Ralf Molitor LuFg Theoretische Informatik, RWTH Aachen email: {baader,kuesters,molitor}@infonnatik.rwth-aachcn.dc
Note that in the example in Lecture 1, the state Home is recurrent (and even absorbing), but all other states are transient. f ii (n) f ii = n=1 < +
 Random Walks: WEEK 2 Recurrence and transience Consider the event {X n = i for some n > 0} by which we mean {X = i}or{x 2 = i,x i}or{x 3 = i,x 2 i,x i},. Definition.. A state i S is recurrent if P(X n
Random Walks: WEEK 2 Recurrence and transience Consider the event {X n = i for some n > 0} by which we mean {X = i}or{x 2 = i,x i}or{x 3 = i,x 2 i,x i},. Definition.. A state i S is recurrent if P(X n
Finitude and Infinitude in the Atomic Calculus of Individuals
 Finitude and Infinitude in the Atomic Calculus of Individuals WILFRID HODGES AND DAVID LEWIS BEDFORD COLLEGE, LONDON, AND UNIVERSITY OF CALIFORNIA AT LOS ANGELES Nelson Goodman has asked' whether there
Finitude and Infinitude in the Atomic Calculus of Individuals WILFRID HODGES AND DAVID LEWIS BEDFORD COLLEGE, LONDON, AND UNIVERSITY OF CALIFORNIA AT LOS ANGELES Nelson Goodman has asked' whether there
First-Fit chromatic number of interval graphs
 1 / 35 First-Fit chromatic number of interval graphs Peng Li (o+), Yaokun Wu (Ljn) Shanghai Jiao Tong University Halifax, June 20, 2012 Outline 2 / 35 Overview Lower bound: A direct construction Upper
1 / 35 First-Fit chromatic number of interval graphs Peng Li (o+), Yaokun Wu (Ljn) Shanghai Jiao Tong University Halifax, June 20, 2012 Outline 2 / 35 Overview Lower bound: A direct construction Upper
TECHNISCHE UNIVERSITEIT EINDHOVEN Faculteit Wiskunde en Informatica. Final exam Logic & Set Theory (2IT61) (correction model)
 TECHNISCHE UNIVERSITEIT EINDHOVEN Faculteit Wiskunde en Informatica Final exam Logic & Set Theory (2IT61) (correction model) Thursday November 4, 2016, 9:00 12:00 hrs. (2) 1. Determine whether the abstract
TECHNISCHE UNIVERSITEIT EINDHOVEN Faculteit Wiskunde en Informatica Final exam Logic & Set Theory (2IT61) (correction model) Thursday November 4, 2016, 9:00 12:00 hrs. (2) 1. Determine whether the abstract
Rough Set Theory Fundamental Assumption Approximation Space Information Systems Decision Tables (Data Tables)
 Rough Set Theory Fundamental Assumption Objects from the domain are perceived only through the values of attributes that can be evaluated on these objects. Objects with the same information are indiscernible.
Rough Set Theory Fundamental Assumption Objects from the domain are perceived only through the values of attributes that can be evaluated on these objects. Objects with the same information are indiscernible.
Computational Tasks and Models
 1 Computational Tasks and Models Overview: We assume that the reader is familiar with computing devices but may associate the notion of computation with specific incarnations of it. Our first goal is to
1 Computational Tasks and Models Overview: We assume that the reader is familiar with computing devices but may associate the notion of computation with specific incarnations of it. Our first goal is to
On the Security of RC4 in TLS
 On the Security of RC4 in TLS Nadhem AlFardan, Dan Bernstein, Kenny Paterson, Bertram Poettering, Jacob Schuldt Royal Holloway, University of London University of Illinois at Chicago http://www.isg.rhul.ac.uk/tls/
On the Security of RC4 in TLS Nadhem AlFardan, Dan Bernstein, Kenny Paterson, Bertram Poettering, Jacob Schuldt Royal Holloway, University of London University of Illinois at Chicago http://www.isg.rhul.ac.uk/tls/
Characterizing Ideal Weighted Threshold Secret Sharing
 Characterizing Ideal Weighted Threshold Secret Sharing Amos Beimel Tamir Tassa Enav Weinreb August 12, 2004 Abstract Weighted threshold secret sharing was introduced by Shamir in his seminal work on secret
Characterizing Ideal Weighted Threshold Secret Sharing Amos Beimel Tamir Tassa Enav Weinreb August 12, 2004 Abstract Weighted threshold secret sharing was introduced by Shamir in his seminal work on secret
2.2.3 Workshop: RBAC Revised: Core-based RBAC. Goal. Problem. Method. Right proliferation analysis for RBAC policies
 2.2.3 Workshop: RBAC Revised: Core-based RBAC Goal Right proliferation analysis for RBAC policies Problem Can t do that with existing RBAC 0..3 models Method Devise a core-based dynamic RBAC 0 model: DRBAC
2.2.3 Workshop: RBAC Revised: Core-based RBAC Goal Right proliferation analysis for RBAC policies Problem Can t do that with existing RBAC 0..3 models Method Devise a core-based dynamic RBAC 0 model: DRBAC
Security as a Resource in Process-Aware Information Systems
 Security as a Resource in Process-Aware Information Systems 14 October 2011 Joint Work with: Jason Crampton Information Security Group Royal Holloway Jim Huan-Pu Kuo Department of Computing Imperial College
Security as a Resource in Process-Aware Information Systems 14 October 2011 Joint Work with: Jason Crampton Information Security Group Royal Holloway Jim Huan-Pu Kuo Department of Computing Imperial College
Uniqueness of the maximal entropy measure on essential spanning forests. A One-Act Proof by Scott Sheffield
 Uniqueness of the maximal entropy measure on essential spanning forests A One-Act Proof by Scott Sheffield First, we introduce some notation... An essential spanning forest of an infinite graph G is a
Uniqueness of the maximal entropy measure on essential spanning forests A One-Act Proof by Scott Sheffield First, we introduce some notation... An essential spanning forest of an infinite graph G is a
The Lefthanded Local Lemma characterizes chordal dependency graphs
 The Lefthanded Local Lemma characterizes chordal dependency graphs Wesley Pegden March 30, 2012 Abstract Shearer gave a general theorem characterizing the family L of dependency graphs labeled with probabilities
The Lefthanded Local Lemma characterizes chordal dependency graphs Wesley Pegden March 30, 2012 Abstract Shearer gave a general theorem characterizing the family L of dependency graphs labeled with probabilities
Follow links for Class Use and other Permissions. For more information send to:
 COPYRIGHT NOTICE: Ariel Rubinstein: Lecture Notes in Microeconomic Theory is published by Princeton University Press and copyrighted, c 2006, by Princeton University Press. All rights reserved. No part
COPYRIGHT NOTICE: Ariel Rubinstein: Lecture Notes in Microeconomic Theory is published by Princeton University Press and copyrighted, c 2006, by Princeton University Press. All rights reserved. No part
