IN synchronous Code Division Multiple Access (CDMA)
|
|
|
- Grant Harmon
- 6 years ago
- Views:
Transcription
1 1 Optmal Groupng Algorthm for a Group Decson Feedbac Detector n Synchronous CDMA Communcatons J. Luo, K. Pattpat, P. Wllett, G. Levchu Abstract he Group Decson Feedbac (GDF) detector s studed n ths paper. he computatonal complexty of a GDF detector s exponentaln the largest sze of the groups. Gven the maxmum group sze, a groupng algorthm s proposed. It s shown that the proposed groupng algorthm maxmzes the Asymptotc Symmetrc Energy (ASE) of the multuser detecton system. Furthermore, based on a set of lower bounds on Asymptotc Group SymmetrcEnergy (AGSE) of the GDF detector, t s shown that the proposed groupng algorthm, n fact, maxmzes the AGSE lower bound for every group of users. ogether wth a fast computatonal method based on branch-and-bound, the theoretcal analyss of the groupng algorthm enables the o²ne estmaton of the computatonal cost and the performance of GDF detector. Smulaton results on both small and large sze problems are presented to verfy the theoretcal conclusons. All the results n ths paper can be appled to the Decson Feedbac (DF) detector by smply settng the maxmum group sze to 1. Keywords Multuser detecton, decson feedbac, optmzaton methods, code dvson multple access. I. Introducton IN synchronous Code Dvson Multple Access (CDMA) communcaton systems, the near-far problem caused by the nteruser nterference has been wdely studed. Wth the addtve whte Gaussan nose assumpton and when the source sgnal s bnary- or nteger-valued, the conventonal detector does not produce relable decsons for the CDMA channel [?]. he computaton of theoptmal detecton, however, s generally NP-hard and thus s exponental n the number of users [], unless the sgnature wave form correlaton matrx has a specal structure [10] [9]. Several new algorthms have been proposed to provde relable solutons wth relatvely low computatonal cost. Among the sub-optmal algorthm groups, the decson-drven detecton methods, ncludng decson feedbac (DF) [5] [11], group detecton [6], and multstage detecton [3] [4], are popular. Although the DF method s smple and performs well, there are stuatons when a margnal ncrease n computaton can provde sgn cant mprovement n performance [1]. he man drawbac of DF s that detectons are made for one user at a tme; the decson on the strong user s obtaned by treatng the wea users as nose. However, when user chp sequences are correlated, ths nose becomes he Authors are wth the Electrcal and Computer Engneerng Department, Unversty of Connectcut, Storrs, C0669, USA. E- mal:rshna@engr.uconn.edu 1 hs wor was supported by the O±ce of Naval Research under contract N , N , and by NUWC under contract N based, and thus s naturally harmful to the userwse detecton. he dea of sequental group detecton was rst ntroduced by Varanas n [6] and can be vewed as the Group Decson Feedbac (GDF) detector. GDF detector dvdes users nto several groups. he users wth relatvely hgh correlatons are assgned to the same group, and the correlaton between users n d erent groups are relatvely low. Smlar to DF detector, GDF detector maes decsons sequentally based on successve cancelaton. However, nstead of mang decsons on sngle user at a tme, GDF detector maes decsons groupwse,.e., the decsons on users n the same group (the correlated users) are made smultaneously. he computatonal expense for a GDF detector s approxmately exponental n the largest group sze, and ths s expected to be small f the largest group sze s small. In [6], the szes of the groups are desgn parameters. However, n practce, gven a user sgnal set, t s not easy for one to nd the correlated users and assgn them to groups. Snce the largest group sze s closely related to the overall computatonal cost, n ths paper, we consder the largest group sze as the only desgn parameter. A groupng and orderng algorthm s proposed to nd the optmal sze and users for each group. heoretcal results are gven to show the optmalty n terms of the Asymptotc Symmetrc Energy (ASE). ogether wth a fast computatonal method mod ed from [1], the proposed GDF detecton method provdes an e±cent way to mprove the DF detecton wth margnal ncrease n computatonal cost. Smulaton results on small and large sze problems are presented to verfy the theoretcal conclusons. he rest of the paper s organzed as follows. In secton II, we revew the problem model and the theoretcal results on the performance measure gven n [6]. In secton III, gven the largest group sze, a groupng and orderng algorthm s proposed to maxmze the ASE of the system. Proof of optmalty s gven n the appendx. A fast computatonal method s proposed for the GDF detector and a theoretcal upper bound on computatonal cost s derved. Smulaton results on a small example as well as on a system of 100 users are presented n secton IV. Conclusons are provded n secton V. II. Problem Formulaton and Performance Measure of GDF Detector A dscrete-tme equvalent model for the matched- lter outputs at the recever of a CDMA channel s gven by the
2 K -length vector [] y Hb + n (1) where bf 1; +1g K denotes the vector of bts transmtted by thek actve users. Here H s a nonnegatve de nte sgnature waveform correlaton matrx, n s a real-valued zero-mean Gaussan random vector wth a covarance matrx H. It has been shown that ths model holds for both baseband [] and passband [11] channels wth addtve Gaussan nose. When all the user sgnals are equally probable, the optmal soluton of (1) s the output of a Maxmum Lelhood (ML) detector [] Á ML : ^b arg mn b Hb y b () bf 1;+1g K whch s generally NP-hard and exponentally complex to mplement. he sequental group detecton based on the dea of successve cancellaton was rst ntroduced by Varanas n [6]. Suppose users are parttoned nto an ordered set of P groups, G 0 ;:::;G. he number of users n group G s denoted by G, and naturally P 0 G K. he decson on group fg 0 g s made by " ^b G0 arg mn mn b Hb y b (3) b G0 f 1;+1g G 0 b ¹G0 where b G0 denotes the part of vector b that corresponds to users n group G 0, and ¹G 0 denotes the complement of G 0,.e., the unon of G 1 ;:::;G. he decsons of (3) are then used to subtract the multple-access nterference due to users n G 0 from the remanng decson statstcs y ¹G 0. he detector for the next group G 1 s desgned under the assumpton that the multple-access nterference cancelaton s perfect. hs process of nterference cancelaton and group detecton s carred out sequentally for users n groups G ;:::;G, wth the group detector for group G tang advantage of the decsons made by group detectors for G 0 ;:::;G 1. Denote the channel model for the user expurgated channel that only has users n groups G ;:::;G by y () H () b () + n () (4) he decsons on group G can be represented as ^b G arg mn 4mn ³b () 3 () H () b () y () b 5 b () f 1;+1g G G b () (5) In mult-user detecton, the Asymptotc Symmetrc Energy (ASE) s an mportant performance measure. De ne the probablty that not all users are detected correctly as P (;Á), then the ASE for the detector Á [11] s gven by 9 < P (;Á) (Á) sup e 0; lm <1 :!0 Q ; ³p e (6) where s the addtve nose varance (see (1)), and Q(x) R 1 p 1 x ¼ e x dx. he ASE for the optmal detector Á ML s gven by (Á ML ) d mn mn ef 1;0;1g K nf0g e He (7) K where d mn s nown as the mnmum dstance of matrx H [] and \n" s the set subtracton. Smlarly, we can de ne the Asymptotc Group Symmetrc Energy (AGSE) for each user group. For a group detector, de ne the probablty that not all users n group fgg are detected correctly as P G (;Á), and correspondngly we have 9 < P G (;Á) G (Á) sup e 0; lm ³ pe <1 () :!0 Q ; as the AGSE for group fg g. Although an exact performance analyss of GDF detector s ntractable [6], one can obtan upper and lower bounds for the AGSE of all groups. Inhthe above descrpton of the GDF detector, de- ne J () H () 1, and denote J () G G to be the sub-matrx of J () that only contans the columns and rows correspondng to users n G. De ne d G ;mn to be the mnmum dstance of matrx J () G G 1, ³.e., d G ;mn ³ mn e J () ef 1;0;1g G nf0g G G G 1 e (9) hen the AGSE for group G can be bounded by mn(d G 0;mn;:::;d G ;mn) G (Á)d G ;mn (10) A smlar result can be found n [6]. he upper bound n (10) s reached when all decsons on the users n group G 1 through group G 1 are correct. III. Optmal Groupng and Detecton Order for GDF Detector It s nown that the performance of the decson-drven mult-user detector s sgn cantly a ected by the order of the users [?]. Snce the overall computaton for GDF detector s exponental n the maxmum group sze, whch s de ned by G max max(g 0 ;:::;G ), n ths secton, we develop a groupng and orderng algorthm that maxmzes the ASE of the GDF detector gven G max as a desgn parameter. Denote the Cholesy decomposton of H by L L H, where L s a lower trangular matrx. Multply both sdes of (1) by (L 1 ) to obtan the whte nose model [5] (L 1 ) y Lb + (L 1 ) n (11) De ne ~y (L 1 ) y, ~n (L 1 ) n, partton the matrces and the vectors accordng to G 0 and ¹G 0 to obtan ~yg0 LG0 G 0 0 bg0 ~ng0 + (1) ~y ¹G 0 L ¹G 0 ¹G 0 b ¹G 0 ~n ¹G 0 L ¹G 0G 0
3 3 Snce L ¹ G0 ¹ G0 s a full ran matrx by assumpton, the decson on group G 0 n (3) can be wrtten as ^b G0 arg mn LG0 G 0 b G0 ~y G0 b G0 f 1;+1g G 0 (13) herefore, the AGSE of group G 0 s determned by the mnmum dstance of matrx L G 0G 0 L G0G0. Snce H L L, we have L G 0G 0 LG 0 G 0 (H 1 1 h 1 )G 0 G 0 J (0) G 0 G 0 G0 (Á GDFD ) d G 0 ;mn (14) A smlar result can be obtaned for group G. In the descrpton of GDFD n secton II, f we let H () L () L (), ³ then L () G L () G J () G G 1. Snce H () s the southeast sub-dagonal matrx of H, L () s the south-east subdagonal matrx of L and L () G L G. Hence, ³ L G G L G G J () G G 1 (15) he above result shows that d G;mn s determned by the dagonal bloc-matrx L G of L. Now, gven all the decsons on group G 0 to group G 1 are correct, denote the probablty that not all the users n group ³ G are detected dg ;mn correctly by P e (G G 0 ;:::;G 1 )¼ Q. he probablty that not all the K users are detected correctly can be represented as P (;Á)¼1 Y 0 1 Q µ dg;mn herefore, the ASE of GDF detector s gven by (16) (Á GDFD ) mn(d G 0;mn;:::;d G ;mn) (17) SnceG max s gven as a desgn parameter, the problem s then to nd an optmal partton and detecton order that maxmzes mn(d G 0;mn;:::;d G ;mn ). Notce that d erent GDF detectors may have the sameg max but d erent numbers of groups snce P s not a desgn parameter. Groupng and Order Algorthm : Fnd the optmal groupng and detecton order va the followng steps. Step 1: Partton the K users nto two groups fg 0 g and f ¹G 0 g wth G 0 G max. Among these parttons (fg 0 g and G 0 are not xed), select the one that maxmzes d G0;mn (whch s the mnmum dstance of matrx h 1). J (0) G 0G 0 Step : Partton the remanng K G 0 users nto two groups G 1 and G ¹ 1 wth G 1 G max. Among these parttons, select the one that maxmzes d G1 ;mn. Step 3: Contnue ths process untl all the users are assgned to groups. Example 1 : he algorthm s llustrated by the followng 4-user example. Suppose theh matrx s gven by H 4 4:30 1:00 0:60 0:30 1:00 3:00 1:70 0:50 0:60 1:70 :0 0:70 0:30 0:50 0:70 1: (1) Assume that the desred maxmum group sze sg max. In step 1 of the algorthm, the possble choces for group G 0 and the resultng d G 0;mn are shown n able I. he User(s) ,1 d G 0 ;mn User(s) 0, 0,3 1, 1,3,3 d G 0 ;mn ABLE I Dfferent choces of group G 0 and the correspondng d G 0;mn best choce for group G 0 s fuser 0g. hen, for the user expurgated channel, we have " 3:00 1:70 0:50 H (1) 1:70 :0 0:70 (19) 0:50 0:70 1:90 he possble choces for group G 1 and the resultng d G1;mn are shown n able II. We can see that the best choce for User(s) 1 3 1, 1,3,3 d G 1;mn ABLE II Dfferent choces of group G1 and the correspondng d G1 ;mn group G 1 s fuser 1, user g. Naturally fuser 3g wll be the last group. he resultng ASE for ths parttonng and orderng s 1:7. Note that the above example has 4 users andg max. One may thn that parttonng users nto groups wth users n each group s a good choce. However, snce user 0 s a strong user, t has to be detected rst. And snce user 1 and user are serously correlated, they have to be assgned to the same group. If, for example, we assgn two groups as fuser0;user3g and fuser1;userg. As a punshment of detectng the wea user (user 3) rst, we get 1:6 < 1:7. Proposton 1 : he proposed groupng and orderng algorthm maxmzes the ASE n (17). See Appendx for the proof. he proposed groupng and orderng algorthm s also optmal n the followng sense. Proposton : he proposed groupng and orderng algorthm maxmzes the performance lower bound n (10) for every group. In other words, suppose G s the groupng and orderng result obtaned from the proposed algorthm, and G s one of the groups n G. Further suppose there s another group and detecton sequence ^G wth ^G l beng one of the groups n ^G, and ^G l G. hen the followng result holds, mn(d G 1 ;mn;:::;d G ;mn) mn(d ^G 1 ;mn ;:::;d G l ;mn) (0)
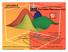
4 4 See Appendx for the proof. In addton to the above propostons, we can derve a fast computatonal method for GDF detector, whch s a mod ed verson of the method proposed n [1]. We propose the followng steps for the group detecton. Computatonal Method for GDF Detector: Suppose the GDF detector has P groups, G 0,..., G 1) Intalze ~y (1) (L 1 ) y, L (1) L. Let 1; ) Form the whte nose system model for the userexpurgated channel, and partton the vectors and matrces accordng to group G and ts complement G ¹ as " ~y () G ~y () " L () G G 0 L () G L () ¹ G " b () G b () + " ~n () G ~n () (1) Fnd the decson on group G by LGG ^b G arg mn b G ~y () b G f 1;+1g G G 3) Compute ~y (+1) by () Fg. 1. Performance of varous methods (4 users, Monte- Carlo runs. Á D s the conventonal decorrelator; Á D DF s the decorrelaton-based decson feedbac detector; Á GDFD s the group decson feedbac detector wth G max ; and Á ML s the maxmum lelhood detector.) Let ~y (+1) ~y () L () G ^bg (3) L (+1) L () ¹ G (4) 4) Let + 1. If < P, go to step ; otherwse, stop the computaton. he computatonal cost for step 1 s K(K+1) multplcatons and K(K 1) addtons. Assume the computatonal cost for step can be bounded by \ " M(G ) ; \ + "S(G ) (5) where \ " denotes the number of multplcatons and \+" denotes the number of addtons. In step 3, snce b can only tae nown dscrete values, Lb can be precomputed and stored. hus, only G P +1 G addtons are needed. herefore, the overall computatonal cost s bounded by s assumed to be 3. Fgure shows one of the smulaton results. he respectve computatonal costs for the three detectors are Á D \ " \ + " 9900 Á D DFD \ " 5050 \ + " 9900 Á GDFD \ " 530 \ + " 1000 (7) Ben tng from the optmal groupng and the branch-andbound-based computatonal method, GDFD shows a sgn cant mpreovement on the performance whle the computatonal cost s even less than that of the conventonal decorrelator. Due to the NP-hard nature of the optmal ML detector, the results on optmal detector could not be computed. \ " K(K + 1) \ + " K(K 1) X [M(G )] + 0 X + 4S(G ) +G 0 X +1 3 G 5 (6) IV. Smulaton Results Example 1 - contnued : In the prevous 4-user example, (Á GDFD ) 1:7. he ASE for optmal DDFD and the ML detector can be obtaned from [11] as (Á DDFD ) 1:69 and (Á ML ) 1:. he smulaton results are shown n Fgure 1, whch are consstent wth the theoretcal analyss. Example : Suppose we have 100 users. he sgnature sequences for each user are bnary and of length 115. hey are generated randomly. he maxmum group sze Fg.. Performance of varous methods (100 users, Monte- Carlo runs. Á D s the conventonal decorrelator; Á D DF s the decorrelaton-based decson feedbac detector; Á GDFD s the group decson feedbac detector wthg max 3)
5 5 V. Concluson An optmal groupng and orderng algorthm for Group Decson Feedbac Detector s proposed. ogether wth a fast computatonal method based on the dea of branch and bound, the proposed algorthm provdes a systematc way of mprovng the Decson Feedbac Detector, especally when correlaton exsts among the users. Smulaton results show that GDF detector wth the optmal groupng and orderng algorthm provdes a sgn cant mprovement over DF detector, whle the ncrease n computatonal cost s margnal and even negatve n some cases. he proposed method can be easly extended to nte-alphabet sgnals nstead of bnary ones. Appendx I. Pre-proved Lemmas Before provng the propostons n ths paper, we present the followng three lemmas that wll be used n the proof. Lemma 1: Suppose H L L s parttoned on two arbtrary dagonal elements as H11 H 1 H 1 H L11 0 L11 0 L 1 L L 1 L () For any permutaton matrx P of the same sze as H, f I 0 H11 H 1 I 0 0 P H 1 H 0 P ~L11 0 ~L11 0 ~L 1 L ~ ~L 1 L ~ (9) then the followng results hold. ~L 11 L 11 ; ~ L ~ L PL L P (30) he proof s qute straght forward and s therefore gnored n ths paper. Lemma : Suppose H s a m m symmetrc and postve de nte matrx. Suppose H L L s the Cholesy decomposton. Partton H and L on the last (south-east) dagonal component as H11 h 1 L11 0 L11 0 h 1 h l 1 l l 1 l (31) Now \move up" the last \user" to the rst, denote the acton and the new Cholesy decomposton matrx by 0 1 H11 h 1 0 I I 0 h 1 h 1 0 ~l 11 0 ~l 11 0 ~ l1 L ~ ~ l1 L ~ (3) hen matrx ~ L ~ L L 11 L 11 s non-negatve de nte. Pro of : Substtutng (31) nto (3) yelds ~L ~ L L 11 L 11 l 1 l 1 0 (33) Lemma 3: Suppose L and ~ L are two lower trangular matrces of sze m m, assume that L L L ~ L 0. ~ Partton L on an arbtrary dagonal component, and partton ~L accordngly as L11 0 L ; ~ ~L11 0 L L ~L 1 L ~ (34) We have L 1 L 11 L 11 ~ L 11 ~ L 11 0 ; L L ~ L ~ L 0 (35) Proof : Snce L L ~ L ~ L 0, we can nd a lower trangular matrx C whch sats es Accordng to (34), partton C as C11 0 C L L ~ L I + C C ~L (36) C 1 C Substtute (34)(37) nto (36) to obtan L L ~ L I + C C ~L (37) L 11 L 11 ~ L 11 I + C 11 C 11 ~L11 +4 (3) where 4 s a symmetrc non-negatve de nte matrx. he proof s complete. Note that n Lemma 3, we can contnue parttonng the sub-dagonal bloc matrces, and apply Lemma 3 teratvely to get a result smlar to (35) for an arbtrary partton. II. Proof of Proposton 1 Denote the optmal group and detecton sequence determned by the proposed algorthm as G, whch has groups G 0 ;:::;G. Denote the group decson feedbac detector usng detecton sequence G by Á G GDFD. he dea of the proof can be summarzed as follows. Suppose there s another group and detecton sequence G (), whch has groups G () 0 ;:::;G() P () 1. Wthout loss of generalty, assume (0 < ) G () G (he superscrpt () means that the rst groups n G () are dentcal to the rst groups n G). Now construct a new group and detecton sequence. he groups of are de ned by G () G 0 < G G () 1 n G > (39) o smplfy the notaton, n the above constructon, f NULL, we stll eep group and de ne d (+1) G ;mn 1. Evdently, G(+1) has one more group than G (). he followng result holds for.
6 6 Proposton 3: If s constructed accordng to the above de nton, then (1) (0 < ), d ;mn d G () ;mn. () d ;mn d. G () ;mn (3) ( < P () ), d ;mn d G () ;mn. 1 Proof : (1) For any <, the decson for group G () s made by treatng the sgnal correspondng to G () +1,..., G() P () 1 as nose and mnmzng the probablty of error n ML sense. herefore, any swappng of users wthn groups of ndex larger than wll not a ect the performance of G (). hs result can be formally proved by usng Lemma 1. () Snce G () ( < ), ths result can be drectly obtaned from the de nton of the optmal groupng and orderng algorthm. (3) he proof for ths part s relatvely trcy. In fact, the constructon of from G () can be dvded nto three stages. De ne the users n group G as K 0,..., K G 1. For the convenence of dscusson, we rst consder user K 0. Stage 1 Suppose, n G (), user K 0 belongs to group G () ( ). De ne the the acton \tae out user K 0 from group G () ", whch converts G () to, as, G () < fuserk 0 g G () fuserk 0 g + 1 G () 1 > + 1 (40) Stage Now n, we have fuserk 0 g. De ne the acton \move up user K 0 to follow group 1 ", whch converts to G (S), as follows, G (S) G (S) G (S) G (S) < fuserk 0 g 1 < > (41) Contnue performng the above two stages on all users K 0,..., K G 1. Denote the resultng group and detecton sequence as G (S3). Denote the number of groups n G (S3) by P (S3). Stage 3 In G (S3), combne groups fk G 1g,..., fk 0 g, whch converts G (S3) to, as, G (S3) < fuserk 0 ;:::;K G 1g G (S3) G +1 > (4) In the rst stage, wthout loss of generalty, suppose user K 0 s the rst user n group G (). he \tae out" acton does not change the order of the users, thus the Cholesy decomposton matrx L remans unchanged. hs shows that L (S1) G s the south-east dagonal sub-bloc of +1 G(S1) +1 L () G G(). herefore, d +1 ;mn d G () ;mn (43) In the second stage, snce the \mnmum dstance" of a sub-bloc s the performance measure for the correspondng user group gven all the user groups wth smaller ndces are correctly detected, puttng more users nto the detected user lst wll result n a better performance and a larger \mnmum dstance". In fact, from Lemma and Lemma 3, for any groups G (S) L G (S) herefore, G (S) 1 L (S) G G (S) L, <, we have, L 1 G(S1) (S1) 1 G 1 G(S1) 1 0 (44) d G (S) ;mn d (45) 1 ;mn Hence, n, for any >, d ;mn d G () ;mn, 1 whch proves part (3) of proposton 3. Based on proposton 3, suppose (Á GDFD ) d ;mn. hen, we have (Á GDFD) (Á G () GDFD) (46) By teratvely usng the above constructon procedure n the proof of Proposton 1, we wll nally get G (P) G and (Á G (P) GDFD) (Á G () GDFD) (47) whch completes the proof. III. Proof of Proposton In the above proof for proposton 1, let G () ^G. Construct usng the same procedure. Note that G () l ^G l G, and G \ G NULL. herefore, n, we have l+1 G. Suppose mn(d 0 ;mn ;:::;d ;mn) d. From l+1 ;mn Proposton 3, ² If <, we have d ;mn mn(d ^G 0 ;mn ;:::;d^g ). l ;mn ² If, we have d ;mn mn(d ^G ;:::;d^g ). 0;mn l;mn ² If >, we have d ;mn mn(d ^G ;:::;d^g ). 0;mn l;mn Hence, d G () ;mn d G () ;mn d G () 1 ;mn mn(d 0 ;mn ;:::;d l+1 ;mn) mn(d^g ;:::;d^g ) 0;mn l;mn (4) By teratvely usng the constructon procedure, we wll nally get G (P) G whch sats es mn(d G 0;mn ;:::;d G ;mn ) mn(d^g0;mn ;:::;d^gl;mn ) (49) Hence the proof s complete.
7 7 References [1] S. Verdu, Mnmum Probablty of Error for asynchronous Gaussan Multple-Access Channel, IEEE rans. Inform. heory, vol. I-3, pp. 5{96, Jan [] R. Lupas and S. Verdu, Lnear multuser detectors for synchronous code-devson multple-access channels, IEEE rans. Inform. heory, vol. 35, pp. 13{136, Jan [3] M. K. Varanas, Multstage detecton for asynchronous codedvson multple-access communcatons, IEEE rans. Comun., vol. 3, pp. 509{519, Apr [4] M. K. Varanas and B. Aazhang, Near-optmum detecton n synchronous code-dvson multple access systems, IEEE rans. Comun., vol. 39, pp. 75{736, May [5] A. Duel-Hallen, Decorrelatng Decson-Feedbac Multuser Detector for Synchronous Code-Dvson Multple-Access Channel, IEEE rans. Comun., vol. 41, pp. 5{90, Feb [6] M. K. Varanas, Group Detecton for Synchronous Gaussan Code-Dvson Multple-Access Channels, IEEE rans. Inform. heory, vol. 41, pp. 103{1096, July [7] A. Duel-Hallen, AFamly ofmultuser Decson-Feedbac Detectors for Asynchronous Code-Dvson Multple-Access Channels, IEEE rans. Comun., vol. 43, pp. 41{43, Feb./Mar./Aprl [] C. Schlegel and L. We, A smple way to compute the mnmum dstance nmultusercdma systems, IEEE rans. Communcatons, vol. 45, pp. 53{535, May [9] C. SanKaran and A. Ephremdes, Solvng a Class of Optmum Multuser Detecton Problems wth Polynomal Complexty, IEEE rans. Inform. heory, vol. 44, pp , Sep [10] S. Uluus, R. Yates, Optmum multuser detecton s tractable for synchronous CDMA systems usng M-sequences, IEEE Commun. Lett., vol., pp. 9-91, 199. [11] M. K. Varanas, Decson feedbac multuser detecton: a systematc approach, IEEE rans. Inform. heory, vol. 45, pp. 19{ 40, Jan [1] J. Luo, K. Pattpat, P. Wllett, G. Levchu, Fast Optmal and Sub-optmal Any-me Algorthms for CWMA Multuser Detecton based on Branch and Bound, submtted to IEEE rans. Commun., July 000.
Linear Approximation with Regularization and Moving Least Squares
 Lnear Approxmaton wth Regularzaton and Movng Least Squares Igor Grešovn May 007 Revson 4.6 (Revson : March 004). 5 4 3 0.5 3 3.5 4 Contents: Lnear Fttng...4. Weghted Least Squares n Functon Approxmaton...
Lnear Approxmaton wth Regularzaton and Movng Least Squares Igor Grešovn May 007 Revson 4.6 (Revson : March 004). 5 4 3 0.5 3 3.5 4 Contents: Lnear Fttng...4. Weghted Least Squares n Functon Approxmaton...
VQ widely used in coding speech, image, and video
 at Scalar quantzers are specal cases of vector quantzers (VQ): they are constraned to look at one sample at a tme (memoryless) VQ does not have such constrant better RD perfomance expected Source codng
at Scalar quantzers are specal cases of vector quantzers (VQ): they are constraned to look at one sample at a tme (memoryless) VQ does not have such constrant better RD perfomance expected Source codng
ECE559VV Project Report
 ECE559VV Project Report (Supplementary Notes Loc Xuan Bu I. MAX SUM-RATE SCHEDULING: THE UPLINK CASE We have seen (n the presentaton that, for downlnk (broadcast channels, the strategy maxmzng the sum-rate
ECE559VV Project Report (Supplementary Notes Loc Xuan Bu I. MAX SUM-RATE SCHEDULING: THE UPLINK CASE We have seen (n the presentaton that, for downlnk (broadcast channels, the strategy maxmzng the sum-rate
Econ107 Applied Econometrics Topic 3: Classical Model (Studenmund, Chapter 4)
 I. Classcal Assumptons Econ7 Appled Econometrcs Topc 3: Classcal Model (Studenmund, Chapter 4) We have defned OLS and studed some algebrac propertes of OLS. In ths topc we wll study statstcal propertes
I. Classcal Assumptons Econ7 Appled Econometrcs Topc 3: Classcal Model (Studenmund, Chapter 4) We have defned OLS and studed some algebrac propertes of OLS. In ths topc we wll study statstcal propertes
2E Pattern Recognition Solutions to Introduction to Pattern Recognition, Chapter 2: Bayesian pattern classification
 E395 - Pattern Recognton Solutons to Introducton to Pattern Recognton, Chapter : Bayesan pattern classfcaton Preface Ths document s a soluton manual for selected exercses from Introducton to Pattern Recognton
E395 - Pattern Recognton Solutons to Introducton to Pattern Recognton, Chapter : Bayesan pattern classfcaton Preface Ths document s a soluton manual for selected exercses from Introducton to Pattern Recognton
Problem Set 9 Solutions
 Desgn and Analyss of Algorthms May 4, 2015 Massachusetts Insttute of Technology 6.046J/18.410J Profs. Erk Demane, Srn Devadas, and Nancy Lynch Problem Set 9 Solutons Problem Set 9 Solutons Ths problem
Desgn and Analyss of Algorthms May 4, 2015 Massachusetts Insttute of Technology 6.046J/18.410J Profs. Erk Demane, Srn Devadas, and Nancy Lynch Problem Set 9 Solutons Problem Set 9 Solutons Ths problem
Iterative Multiuser Receiver Utilizing Soft Decoding Information
 teratve Multuser Recever Utlzng Soft Decodng nformaton Kmmo Kettunen and Tmo Laaso Helsn Unversty of Technology Laboratory of Telecommuncatons Technology emal: Kmmo.Kettunen@hut.f, Tmo.Laaso@hut.f Abstract
teratve Multuser Recever Utlzng Soft Decodng nformaton Kmmo Kettunen and Tmo Laaso Helsn Unversty of Technology Laboratory of Telecommuncatons Technology emal: Kmmo.Kettunen@hut.f, Tmo.Laaso@hut.f Abstract
Application of Nonbinary LDPC Codes for Communication over Fading Channels Using Higher Order Modulations
 Applcaton of Nonbnary LDPC Codes for Communcaton over Fadng Channels Usng Hgher Order Modulatons Rong-Hu Peng and Rong-Rong Chen Department of Electrcal and Computer Engneerng Unversty of Utah Ths work
Applcaton of Nonbnary LDPC Codes for Communcaton over Fadng Channels Usng Hgher Order Modulatons Rong-Hu Peng and Rong-Rong Chen Department of Electrcal and Computer Engneerng Unversty of Utah Ths work
Lecture Notes on Linear Regression
 Lecture Notes on Lnear Regresson Feng L fl@sdueducn Shandong Unversty, Chna Lnear Regresson Problem In regresson problem, we am at predct a contnuous target value gven an nput feature vector We assume
Lecture Notes on Lnear Regresson Feng L fl@sdueducn Shandong Unversty, Chna Lnear Regresson Problem In regresson problem, we am at predct a contnuous target value gven an nput feature vector We assume
Lecture 3. Ax x i a i. i i
 18.409 The Behavor of Algorthms n Practce 2/14/2 Lecturer: Dan Spelman Lecture 3 Scrbe: Arvnd Sankar 1 Largest sngular value In order to bound the condton number, we need an upper bound on the largest
18.409 The Behavor of Algorthms n Practce 2/14/2 Lecturer: Dan Spelman Lecture 3 Scrbe: Arvnd Sankar 1 Largest sngular value In order to bound the condton number, we need an upper bound on the largest
Chapter 5. Solution of System of Linear Equations. Module No. 6. Solution of Inconsistent and Ill Conditioned Systems
 Numercal Analyss by Dr. Anta Pal Assstant Professor Department of Mathematcs Natonal Insttute of Technology Durgapur Durgapur-713209 emal: anta.bue@gmal.com 1 . Chapter 5 Soluton of System of Lnear Equatons
Numercal Analyss by Dr. Anta Pal Assstant Professor Department of Mathematcs Natonal Insttute of Technology Durgapur Durgapur-713209 emal: anta.bue@gmal.com 1 . Chapter 5 Soluton of System of Lnear Equatons
Foundations of Arithmetic
 Foundatons of Arthmetc Notaton We shall denote the sum and product of numbers n the usual notaton as a 2 + a 2 + a 3 + + a = a, a 1 a 2 a 3 a = a The notaton a b means a dvdes b,.e. ac = b where c s an
Foundatons of Arthmetc Notaton We shall denote the sum and product of numbers n the usual notaton as a 2 + a 2 + a 3 + + a = a, a 1 a 2 a 3 a = a The notaton a b means a dvdes b,.e. ac = b where c s an
A new construction of 3-separable matrices via an improved decoding of Macula s construction
 Dscrete Optmzaton 5 008 700 704 Contents lsts avalable at ScenceDrect Dscrete Optmzaton journal homepage: wwwelsevercom/locate/dsopt A new constructon of 3-separable matrces va an mproved decodng of Macula
Dscrete Optmzaton 5 008 700 704 Contents lsts avalable at ScenceDrect Dscrete Optmzaton journal homepage: wwwelsevercom/locate/dsopt A new constructon of 3-separable matrces va an mproved decodng of Macula
Example: (13320, 22140) =? Solution #1: The divisors of are 1, 2, 3, 4, 5, 6, 9, 10, 12, 15, 18, 20, 27, 30, 36, 41,
 The greatest common dvsor of two ntegers a and b (not both zero) s the largest nteger whch s a common factor of both a and b. We denote ths number by gcd(a, b), or smply (a, b) when there s no confuson
The greatest common dvsor of two ntegers a and b (not both zero) s the largest nteger whch s a common factor of both a and b. We denote ths number by gcd(a, b), or smply (a, b) when there s no confuson
Chapter Newton s Method
 Chapter 9. Newton s Method After readng ths chapter, you should be able to:. Understand how Newton s method s dfferent from the Golden Secton Search method. Understand how Newton s method works 3. Solve
Chapter 9. Newton s Method After readng ths chapter, you should be able to:. Understand how Newton s method s dfferent from the Golden Secton Search method. Understand how Newton s method works 3. Solve
College of Computer & Information Science Fall 2009 Northeastern University 20 October 2009
 College of Computer & Informaton Scence Fall 2009 Northeastern Unversty 20 October 2009 CS7880: Algorthmc Power Tools Scrbe: Jan Wen and Laura Poplawsk Lecture Outlne: Prmal-dual schema Network Desgn:
College of Computer & Informaton Scence Fall 2009 Northeastern Unversty 20 October 2009 CS7880: Algorthmc Power Tools Scrbe: Jan Wen and Laura Poplawsk Lecture Outlne: Prmal-dual schema Network Desgn:
Chapter - 2. Distribution System Power Flow Analysis
 Chapter - 2 Dstrbuton System Power Flow Analyss CHAPTER - 2 Radal Dstrbuton System Load Flow 2.1 Introducton Load flow s an mportant tool [66] for analyzng electrcal power system network performance. Load
Chapter - 2 Dstrbuton System Power Flow Analyss CHAPTER - 2 Radal Dstrbuton System Load Flow 2.1 Introducton Load flow s an mportant tool [66] for analyzng electrcal power system network performance. Load
Copyright 2017 by Taylor Enterprises, Inc., All Rights Reserved. Adjusted Control Limits for P Charts. Dr. Wayne A. Taylor
 Taylor Enterprses, Inc. Control Lmts for P Charts Copyrght 2017 by Taylor Enterprses, Inc., All Rghts Reserved. Control Lmts for P Charts Dr. Wayne A. Taylor Abstract: P charts are used for count data
Taylor Enterprses, Inc. Control Lmts for P Charts Copyrght 2017 by Taylor Enterprses, Inc., All Rghts Reserved. Control Lmts for P Charts Dr. Wayne A. Taylor Abstract: P charts are used for count data
Lecture 12: Classification
 Lecture : Classfcaton g Dscrmnant functons g The optmal Bayes classfer g Quadratc classfers g Eucldean and Mahalanobs metrcs g K Nearest Neghbor Classfers Intellgent Sensor Systems Rcardo Guterrez-Osuna
Lecture : Classfcaton g Dscrmnant functons g The optmal Bayes classfer g Quadratc classfers g Eucldean and Mahalanobs metrcs g K Nearest Neghbor Classfers Intellgent Sensor Systems Rcardo Guterrez-Osuna
Lecture 5 Decoding Binary BCH Codes
 Lecture 5 Decodng Bnary BCH Codes In ths class, we wll ntroduce dfferent methods for decodng BCH codes 51 Decodng the [15, 7, 5] 2 -BCH Code Consder the [15, 7, 5] 2 -code C we ntroduced n the last lecture
Lecture 5 Decodng Bnary BCH Codes In ths class, we wll ntroduce dfferent methods for decodng BCH codes 51 Decodng the [15, 7, 5] 2 -BCH Code Consder the [15, 7, 5] 2 -code C we ntroduced n the last lecture
Yong Joon Ryang. 1. Introduction Consider the multicommodity transportation problem with convex quadratic cost function. 1 2 (x x0 ) T Q(x x 0 )
 Kangweon-Kyungk Math. Jour. 4 1996), No. 1, pp. 7 16 AN ITERATIVE ROW-ACTION METHOD FOR MULTICOMMODITY TRANSPORTATION PROBLEMS Yong Joon Ryang Abstract. The optmzaton problems wth quadratc constrants often
Kangweon-Kyungk Math. Jour. 4 1996), No. 1, pp. 7 16 AN ITERATIVE ROW-ACTION METHOD FOR MULTICOMMODITY TRANSPORTATION PROBLEMS Yong Joon Ryang Abstract. The optmzaton problems wth quadratc constrants often
APPROXIMATE PRICES OF BASKET AND ASIAN OPTIONS DUPONT OLIVIER. Premia 14
 APPROXIMAE PRICES OF BASKE AND ASIAN OPIONS DUPON OLIVIER Prema 14 Contents Introducton 1 1. Framewor 1 1.1. Baset optons 1.. Asan optons. Computng the prce 3. Lower bound 3.1. Closed formula for the prce
APPROXIMAE PRICES OF BASKE AND ASIAN OPIONS DUPON OLIVIER Prema 14 Contents Introducton 1 1. Framewor 1 1.1. Baset optons 1.. Asan optons. Computng the prce 3. Lower bound 3.1. Closed formula for the prce
NP-Completeness : Proofs
 NP-Completeness : Proofs Proof Methods A method to show a decson problem Π NP-complete s as follows. (1) Show Π NP. (2) Choose an NP-complete problem Π. (3) Show Π Π. A method to show an optmzaton problem
NP-Completeness : Proofs Proof Methods A method to show a decson problem Π NP-complete s as follows. (1) Show Π NP. (2) Choose an NP-complete problem Π. (3) Show Π Π. A method to show an optmzaton problem
The Prncpal Component Transform The Prncpal Component Transform s also called Karhunen-Loeve Transform (KLT, Hotellng Transform, oregenvector Transfor
 Prncpal Component Transform Multvarate Random Sgnals A real tme sgnal x(t can be consdered as a random process and ts samples x m (m =0; ;N, 1 a random vector: The mean vector of X s X =[x0; ;x N,1] T
Prncpal Component Transform Multvarate Random Sgnals A real tme sgnal x(t can be consdered as a random process and ts samples x m (m =0; ;N, 1 a random vector: The mean vector of X s X =[x0; ;x N,1] T
Inner Product. Euclidean Space. Orthonormal Basis. Orthogonal
 Inner Product Defnton 1 () A Eucldean space s a fnte-dmensonal vector space over the reals R, wth an nner product,. Defnton 2 (Inner Product) An nner product, on a real vector space X s a symmetrc, blnear,
Inner Product Defnton 1 () A Eucldean space s a fnte-dmensonal vector space over the reals R, wth an nner product,. Defnton 2 (Inner Product) An nner product, on a real vector space X s a symmetrc, blnear,
Lecture 12: Discrete Laplacian
 Lecture 12: Dscrete Laplacan Scrbe: Tanye Lu Our goal s to come up wth a dscrete verson of Laplacan operator for trangulated surfaces, so that we can use t n practce to solve related problems We are mostly
Lecture 12: Dscrete Laplacan Scrbe: Tanye Lu Our goal s to come up wth a dscrete verson of Laplacan operator for trangulated surfaces, so that we can use t n practce to solve related problems We are mostly
Generalized Linear Methods
 Generalzed Lnear Methods 1 Introducton In the Ensemble Methods the general dea s that usng a combnaton of several weak learner one could make a better learner. More formally, assume that we have a set
Generalzed Lnear Methods 1 Introducton In the Ensemble Methods the general dea s that usng a combnaton of several weak learner one could make a better learner. More formally, assume that we have a set
3.1 Expectation of Functions of Several Random Variables. )' be a k-dimensional discrete or continuous random vector, with joint PMF p (, E X E X1 E X
 Statstcs 1: Probablty Theory II 37 3 EPECTATION OF SEVERAL RANDOM VARIABLES As n Probablty Theory I, the nterest n most stuatons les not on the actual dstrbuton of a random vector, but rather on a number
Statstcs 1: Probablty Theory II 37 3 EPECTATION OF SEVERAL RANDOM VARIABLES As n Probablty Theory I, the nterest n most stuatons les not on the actual dstrbuton of a random vector, but rather on a number
STAT 309: MATHEMATICAL COMPUTATIONS I FALL 2018 LECTURE 16
 STAT 39: MATHEMATICAL COMPUTATIONS I FALL 218 LECTURE 16 1 why teratve methods f we have a lnear system Ax = b where A s very, very large but s ether sparse or structured (eg, banded, Toepltz, banded plus
STAT 39: MATHEMATICAL COMPUTATIONS I FALL 218 LECTURE 16 1 why teratve methods f we have a lnear system Ax = b where A s very, very large but s ether sparse or structured (eg, banded, Toepltz, banded plus
Error Probability for M Signals
 Chapter 3 rror Probablty for M Sgnals In ths chapter we dscuss the error probablty n decdng whch of M sgnals was transmtted over an arbtrary channel. We assume the sgnals are represented by a set of orthonormal
Chapter 3 rror Probablty for M Sgnals In ths chapter we dscuss the error probablty n decdng whch of M sgnals was transmtted over an arbtrary channel. We assume the sgnals are represented by a set of orthonormal
Difference Equations
 Dfference Equatons c Jan Vrbk 1 Bascs Suppose a sequence of numbers, say a 0,a 1,a,a 3,... s defned by a certan general relatonshp between, say, three consecutve values of the sequence, e.g. a + +3a +1
Dfference Equatons c Jan Vrbk 1 Bascs Suppose a sequence of numbers, say a 0,a 1,a,a 3,... s defned by a certan general relatonshp between, say, three consecutve values of the sequence, e.g. a + +3a +1
The Geometry of Logit and Probit
 The Geometry of Logt and Probt Ths short note s meant as a supplement to Chapters and 3 of Spatal Models of Parlamentary Votng and the notaton and reference to fgures n the text below s to those two chapters.
The Geometry of Logt and Probt Ths short note s meant as a supplement to Chapters and 3 of Spatal Models of Parlamentary Votng and the notaton and reference to fgures n the text below s to those two chapters.
Formulas for the Determinant
 page 224 224 CHAPTER 3 Determnants e t te t e 2t 38 A = e t 2te t e 2t e t te t 2e 2t 39 If 123 A = 345, 456 compute the matrx product A adj(a) What can you conclude about det(a)? For Problems 40 43, use
page 224 224 CHAPTER 3 Determnants e t te t e 2t 38 A = e t 2te t e 2t e t te t 2e 2t 39 If 123 A = 345, 456 compute the matrx product A adj(a) What can you conclude about det(a)? For Problems 40 43, use
Week 5: Neural Networks
 Week 5: Neural Networks Instructor: Sergey Levne Neural Networks Summary In the prevous lecture, we saw how we can construct neural networks by extendng logstc regresson. Neural networks consst of multple
Week 5: Neural Networks Instructor: Sergey Levne Neural Networks Summary In the prevous lecture, we saw how we can construct neural networks by extendng logstc regresson. Neural networks consst of multple
Simultaneous Optimization of Berth Allocation, Quay Crane Assignment and Quay Crane Scheduling Problems in Container Terminals
 Smultaneous Optmzaton of Berth Allocaton, Quay Crane Assgnment and Quay Crane Schedulng Problems n Contaner Termnals Necat Aras, Yavuz Türkoğulları, Z. Caner Taşkın, Kuban Altınel Abstract In ths work,
Smultaneous Optmzaton of Berth Allocaton, Quay Crane Assgnment and Quay Crane Schedulng Problems n Contaner Termnals Necat Aras, Yavuz Türkoğulları, Z. Caner Taşkın, Kuban Altınel Abstract In ths work,
Dynamic Programming. Preview. Dynamic Programming. Dynamic Programming. Dynamic Programming (Example: Fibonacci Sequence)
 /24/27 Prevew Fbonacc Sequence Longest Common Subsequence Dynamc programmng s a method for solvng complex problems by breakng them down nto smpler sub-problems. It s applcable to problems exhbtng the propertes
/24/27 Prevew Fbonacc Sequence Longest Common Subsequence Dynamc programmng s a method for solvng complex problems by breakng them down nto smpler sub-problems. It s applcable to problems exhbtng the propertes
Errors for Linear Systems
 Errors for Lnear Systems When we solve a lnear system Ax b we often do not know A and b exactly, but have only approxmatons  and ˆb avalable. Then the best thng we can do s to solve ˆx ˆb exactly whch
Errors for Lnear Systems When we solve a lnear system Ax b we often do not know A and b exactly, but have only approxmatons  and ˆb avalable. Then the best thng we can do s to solve ˆx ˆb exactly whch
The optimal delay of the second test is therefore approximately 210 hours earlier than =2.
 THE IEC 61508 FORMULAS 223 The optmal delay of the second test s therefore approxmately 210 hours earler than =2. 8.4 The IEC 61508 Formulas IEC 61508-6 provdes approxmaton formulas for the PF for smple
THE IEC 61508 FORMULAS 223 The optmal delay of the second test s therefore approxmately 210 hours earler than =2. 8.4 The IEC 61508 Formulas IEC 61508-6 provdes approxmaton formulas for the PF for smple
ANSWERS. Problem 1. and the moment generating function (mgf) by. defined for any real t. Use this to show that E( U) var( U)
 Econ 413 Exam 13 H ANSWERS Settet er nndelt 9 deloppgaver, A,B,C, som alle anbefales å telle lkt for å gøre det ltt lettere å stå. Svar er gtt . Unfortunately, there s a prntng error n the hnt of
Econ 413 Exam 13 H ANSWERS Settet er nndelt 9 deloppgaver, A,B,C, som alle anbefales å telle lkt for å gøre det ltt lettere å stå. Svar er gtt . Unfortunately, there s a prntng error n the hnt of
APPENDIX A Some Linear Algebra
 APPENDIX A Some Lnear Algebra The collecton of m, n matrces A.1 Matrces a 1,1,..., a 1,n A = a m,1,..., a m,n wth real elements a,j s denoted by R m,n. If n = 1 then A s called a column vector. Smlarly,
APPENDIX A Some Lnear Algebra The collecton of m, n matrces A.1 Matrces a 1,1,..., a 1,n A = a m,1,..., a m,n wth real elements a,j s denoted by R m,n. If n = 1 then A s called a column vector. Smlarly,
An Interactive Optimisation Tool for Allocation Problems
 An Interactve Optmsaton ool for Allocaton Problems Fredr Bonäs, Joam Westerlund and apo Westerlund Process Desgn Laboratory, Faculty of echnology, Åbo Aadem Unversty, uru 20500, Fnland hs paper presents
An Interactve Optmsaton ool for Allocaton Problems Fredr Bonäs, Joam Westerlund and apo Westerlund Process Desgn Laboratory, Faculty of echnology, Åbo Aadem Unversty, uru 20500, Fnland hs paper presents
Structure and Drive Paul A. Jensen Copyright July 20, 2003
 Structure and Drve Paul A. Jensen Copyrght July 20, 2003 A system s made up of several operatons wth flow passng between them. The structure of the system descrbes the flow paths from nputs to outputs.
Structure and Drve Paul A. Jensen Copyrght July 20, 2003 A system s made up of several operatons wth flow passng between them. The structure of the system descrbes the flow paths from nputs to outputs.
Composite Hypotheses testing
 Composte ypotheses testng In many hypothess testng problems there are many possble dstrbutons that can occur under each of the hypotheses. The output of the source s a set of parameters (ponts n a parameter
Composte ypotheses testng In many hypothess testng problems there are many possble dstrbutons that can occur under each of the hypotheses. The output of the source s a set of parameters (ponts n a parameter
COS 521: Advanced Algorithms Game Theory and Linear Programming
 COS 521: Advanced Algorthms Game Theory and Lnear Programmng Moses Charkar February 27, 2013 In these notes, we ntroduce some basc concepts n game theory and lnear programmng (LP). We show a connecton
COS 521: Advanced Algorthms Game Theory and Lnear Programmng Moses Charkar February 27, 2013 In these notes, we ntroduce some basc concepts n game theory and lnear programmng (LP). We show a connecton
Lectures - Week 4 Matrix norms, Conditioning, Vector Spaces, Linear Independence, Spanning sets and Basis, Null space and Range of a Matrix
 Lectures - Week 4 Matrx norms, Condtonng, Vector Spaces, Lnear Independence, Spannng sets and Bass, Null space and Range of a Matrx Matrx Norms Now we turn to assocatng a number to each matrx. We could
Lectures - Week 4 Matrx norms, Condtonng, Vector Spaces, Lnear Independence, Spannng sets and Bass, Null space and Range of a Matrx Matrx Norms Now we turn to assocatng a number to each matrx. We could
Kernel Methods and SVMs Extension
 Kernel Methods and SVMs Extenson The purpose of ths document s to revew materal covered n Machne Learnng 1 Supervsed Learnng regardng support vector machnes (SVMs). Ths document also provdes a general
Kernel Methods and SVMs Extenson The purpose of ths document s to revew materal covered n Machne Learnng 1 Supervsed Learnng regardng support vector machnes (SVMs). Ths document also provdes a general
The Minimum Universal Cost Flow in an Infeasible Flow Network
 Journal of Scences, Islamc Republc of Iran 17(2): 175-180 (2006) Unversty of Tehran, ISSN 1016-1104 http://jscencesutacr The Mnmum Unversal Cost Flow n an Infeasble Flow Network H Saleh Fathabad * M Bagheran
Journal of Scences, Islamc Republc of Iran 17(2): 175-180 (2006) Unversty of Tehran, ISSN 1016-1104 http://jscencesutacr The Mnmum Unversal Cost Flow n an Infeasble Flow Network H Saleh Fathabad * M Bagheran
Outline and Reading. Dynamic Programming. Dynamic Programming revealed. Computing Fibonacci. The General Dynamic Programming Technique
 Outlne and Readng Dynamc Programmng The General Technque ( 5.3.2) -1 Knapsac Problem ( 5.3.3) Matrx Chan-Product ( 5.3.1) Dynamc Programmng verson 1.4 1 Dynamc Programmng verson 1.4 2 Dynamc Programmng
Outlne and Readng Dynamc Programmng The General Technque ( 5.3.2) -1 Knapsac Problem ( 5.3.3) Matrx Chan-Product ( 5.3.1) Dynamc Programmng verson 1.4 1 Dynamc Programmng verson 1.4 2 Dynamc Programmng
Min Cut, Fast Cut, Polynomial Identities
 Randomzed Algorthms, Summer 016 Mn Cut, Fast Cut, Polynomal Identtes Instructor: Thomas Kesselhem and Kurt Mehlhorn 1 Mn Cuts n Graphs Lecture (5 pages) Throughout ths secton, G = (V, E) s a mult-graph.
Randomzed Algorthms, Summer 016 Mn Cut, Fast Cut, Polynomal Identtes Instructor: Thomas Kesselhem and Kurt Mehlhorn 1 Mn Cuts n Graphs Lecture (5 pages) Throughout ths secton, G = (V, E) s a mult-graph.
On the Multicriteria Integer Network Flow Problem
 BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 5, No 2 Sofa 2005 On the Multcrtera Integer Network Flow Problem Vassl Vasslev, Marana Nkolova, Maryana Vassleva Insttute of
BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 5, No 2 Sofa 2005 On the Multcrtera Integer Network Flow Problem Vassl Vasslev, Marana Nkolova, Maryana Vassleva Insttute of
U.C. Berkeley CS294: Beyond Worst-Case Analysis Luca Trevisan September 5, 2017
 U.C. Berkeley CS94: Beyond Worst-Case Analyss Handout 4s Luca Trevsan September 5, 07 Summary of Lecture 4 In whch we ntroduce semdefnte programmng and apply t to Max Cut. Semdefnte Programmng Recall that
U.C. Berkeley CS94: Beyond Worst-Case Analyss Handout 4s Luca Trevsan September 5, 07 Summary of Lecture 4 In whch we ntroduce semdefnte programmng and apply t to Max Cut. Semdefnte Programmng Recall that
P R. Lecture 4. Theory and Applications of Pattern Recognition. Dept. of Electrical and Computer Engineering /
 Theory and Applcatons of Pattern Recognton 003, Rob Polkar, Rowan Unversty, Glassboro, NJ Lecture 4 Bayes Classfcaton Rule Dept. of Electrcal and Computer Engneerng 0909.40.0 / 0909.504.04 Theory & Applcatons
Theory and Applcatons of Pattern Recognton 003, Rob Polkar, Rowan Unversty, Glassboro, NJ Lecture 4 Bayes Classfcaton Rule Dept. of Electrcal and Computer Engneerng 0909.40.0 / 0909.504.04 Theory & Applcatons
CS 331 DESIGN AND ANALYSIS OF ALGORITHMS DYNAMIC PROGRAMMING. Dr. Daisy Tang
 CS DESIGN ND NLYSIS OF LGORITHMS DYNMIC PROGRMMING Dr. Dasy Tang Dynamc Programmng Idea: Problems can be dvded nto stages Soluton s a sequence o decsons and the decson at the current stage s based on the
CS DESIGN ND NLYSIS OF LGORITHMS DYNMIC PROGRMMING Dr. Dasy Tang Dynamc Programmng Idea: Problems can be dvded nto stages Soluton s a sequence o decsons and the decson at the current stage s based on the
On an Extension of Stochastic Approximation EM Algorithm for Incomplete Data Problems. Vahid Tadayon 1
 On an Extenson of Stochastc Approxmaton EM Algorthm for Incomplete Data Problems Vahd Tadayon Abstract: The Stochastc Approxmaton EM (SAEM algorthm, a varant stochastc approxmaton of EM, s a versatle tool
On an Extenson of Stochastc Approxmaton EM Algorthm for Incomplete Data Problems Vahd Tadayon Abstract: The Stochastc Approxmaton EM (SAEM algorthm, a varant stochastc approxmaton of EM, s a versatle tool
Tracking with Kalman Filter
 Trackng wth Kalman Flter Scott T. Acton Vrgna Image and Vdeo Analyss (VIVA), Charles L. Brown Department of Electrcal and Computer Engneerng Department of Bomedcal Engneerng Unversty of Vrgna, Charlottesvlle,
Trackng wth Kalman Flter Scott T. Acton Vrgna Image and Vdeo Analyss (VIVA), Charles L. Brown Department of Electrcal and Computer Engneerng Department of Bomedcal Engneerng Unversty of Vrgna, Charlottesvlle,
O-line Temporary Tasks Assignment. Abstract. In this paper we consider the temporary tasks assignment
 O-lne Temporary Tasks Assgnment Yoss Azar and Oded Regev Dept. of Computer Scence, Tel-Avv Unversty, Tel-Avv, 69978, Israel. azar@math.tau.ac.l??? Dept. of Computer Scence, Tel-Avv Unversty, Tel-Avv, 69978,
O-lne Temporary Tasks Assgnment Yoss Azar and Oded Regev Dept. of Computer Scence, Tel-Avv Unversty, Tel-Avv, 69978, Israel. azar@math.tau.ac.l??? Dept. of Computer Scence, Tel-Avv Unversty, Tel-Avv, 69978,
Lecture Space-Bounded Derandomization
 Notes on Complexty Theory Last updated: October, 2008 Jonathan Katz Lecture Space-Bounded Derandomzaton 1 Space-Bounded Derandomzaton We now dscuss derandomzaton of space-bounded algorthms. Here non-trval
Notes on Complexty Theory Last updated: October, 2008 Jonathan Katz Lecture Space-Bounded Derandomzaton 1 Space-Bounded Derandomzaton We now dscuss derandomzaton of space-bounded algorthms. Here non-trval
Lecture 4: November 17, Part 1 Single Buffer Management
 Lecturer: Ad Rosén Algorthms for the anagement of Networs Fall 2003-2004 Lecture 4: November 7, 2003 Scrbe: Guy Grebla Part Sngle Buffer anagement In the prevous lecture we taled about the Combned Input
Lecturer: Ad Rosén Algorthms for the anagement of Networs Fall 2003-2004 Lecture 4: November 7, 2003 Scrbe: Guy Grebla Part Sngle Buffer anagement In the prevous lecture we taled about the Combned Input
Solutions HW #2. minimize. Ax = b. Give the dual problem, and make the implicit equality constraints explicit. Solution.
 Solutons HW #2 Dual of general LP. Fnd the dual functon of the LP mnmze subject to c T x Gx h Ax = b. Gve the dual problem, and make the mplct equalty constrants explct. Soluton. 1. The Lagrangan s L(x,
Solutons HW #2 Dual of general LP. Fnd the dual functon of the LP mnmze subject to c T x Gx h Ax = b. Gve the dual problem, and make the mplct equalty constrants explct. Soluton. 1. The Lagrangan s L(x,
U.C. Berkeley CS294: Spectral Methods and Expanders Handout 8 Luca Trevisan February 17, 2016
 U.C. Berkeley CS94: Spectral Methods and Expanders Handout 8 Luca Trevsan February 7, 06 Lecture 8: Spectral Algorthms Wrap-up In whch we talk about even more generalzatons of Cheeger s nequaltes, and
U.C. Berkeley CS94: Spectral Methods and Expanders Handout 8 Luca Trevsan February 7, 06 Lecture 8: Spectral Algorthms Wrap-up In whch we talk about even more generalzatons of Cheeger s nequaltes, and
Stanford University CS359G: Graph Partitioning and Expanders Handout 4 Luca Trevisan January 13, 2011
 Stanford Unversty CS359G: Graph Parttonng and Expanders Handout 4 Luca Trevsan January 3, 0 Lecture 4 In whch we prove the dffcult drecton of Cheeger s nequalty. As n the past lectures, consder an undrected
Stanford Unversty CS359G: Graph Parttonng and Expanders Handout 4 Luca Trevsan January 3, 0 Lecture 4 In whch we prove the dffcult drecton of Cheeger s nequalty. As n the past lectures, consder an undrected
Hidden Markov Models & The Multivariate Gaussian (10/26/04)
 CS281A/Stat241A: Statstcal Learnng Theory Hdden Markov Models & The Multvarate Gaussan (10/26/04) Lecturer: Mchael I. Jordan Scrbes: Jonathan W. Hu 1 Hdden Markov Models As a bref revew, hdden Markov models
CS281A/Stat241A: Statstcal Learnng Theory Hdden Markov Models & The Multvarate Gaussan (10/26/04) Lecturer: Mchael I. Jordan Scrbes: Jonathan W. Hu 1 Hdden Markov Models As a bref revew, hdden Markov models
5 The Rational Canonical Form
 5 The Ratonal Canoncal Form Here p s a monc rreducble factor of the mnmum polynomal m T and s not necessarly of degree one Let F p denote the feld constructed earler n the course, consstng of all matrces
5 The Ratonal Canoncal Form Here p s a monc rreducble factor of the mnmum polynomal m T and s not necessarly of degree one Let F p denote the feld constructed earler n the course, consstng of all matrces
Module 3 LOSSY IMAGE COMPRESSION SYSTEMS. Version 2 ECE IIT, Kharagpur
 Module 3 LOSSY IMAGE COMPRESSION SYSTEMS Verson ECE IIT, Kharagpur Lesson 6 Theory of Quantzaton Verson ECE IIT, Kharagpur Instructonal Objectves At the end of ths lesson, the students should be able to:
Module 3 LOSSY IMAGE COMPRESSION SYSTEMS Verson ECE IIT, Kharagpur Lesson 6 Theory of Quantzaton Verson ECE IIT, Kharagpur Instructonal Objectves At the end of ths lesson, the students should be able to:
Module 9. Lecture 6. Duality in Assignment Problems
 Module 9 1 Lecture 6 Dualty n Assgnment Problems In ths lecture we attempt to answer few other mportant questons posed n earler lecture for (AP) and see how some of them can be explaned through the concept
Module 9 1 Lecture 6 Dualty n Assgnment Problems In ths lecture we attempt to answer few other mportant questons posed n earler lecture for (AP) and see how some of them can be explaned through the concept
THE SUMMATION NOTATION Ʃ
 Sngle Subscrpt otaton THE SUMMATIO OTATIO Ʃ Most of the calculatons we perform n statstcs are repettve operatons on lsts of numbers. For example, we compute the sum of a set of numbers, or the sum of the
Sngle Subscrpt otaton THE SUMMATIO OTATIO Ʃ Most of the calculatons we perform n statstcs are repettve operatons on lsts of numbers. For example, we compute the sum of a set of numbers, or the sum of the
The lower and upper bounds on Perron root of nonnegative irreducible matrices
 Journal of Computatonal Appled Mathematcs 217 (2008) 259 267 wwwelsevercom/locate/cam The lower upper bounds on Perron root of nonnegatve rreducble matrces Guang-Xn Huang a,, Feng Yn b,keguo a a College
Journal of Computatonal Appled Mathematcs 217 (2008) 259 267 wwwelsevercom/locate/cam The lower upper bounds on Perron root of nonnegatve rreducble matrces Guang-Xn Huang a,, Feng Yn b,keguo a a College
Communication with AWGN Interference
 Communcaton wth AWG Interference m {m } {p(m } Modulator s {s } r=s+n Recever ˆm AWG n m s a dscrete random varable(rv whch takes m wth probablty p(m. Modulator maps each m nto a waveform sgnal s m=m
Communcaton wth AWG Interference m {m } {p(m } Modulator s {s } r=s+n Recever ˆm AWG n m s a dscrete random varable(rv whch takes m wth probablty p(m. Modulator maps each m nto a waveform sgnal s m=m
Assortment Optimization under MNL
 Assortment Optmzaton under MNL Haotan Song Aprl 30, 2017 1 Introducton The assortment optmzaton problem ams to fnd the revenue-maxmzng assortment of products to offer when the prces of products are fxed.
Assortment Optmzaton under MNL Haotan Song Aprl 30, 2017 1 Introducton The assortment optmzaton problem ams to fnd the revenue-maxmzng assortment of products to offer when the prces of products are fxed.
Feature Selection: Part 1
 CSE 546: Machne Learnng Lecture 5 Feature Selecton: Part 1 Instructor: Sham Kakade 1 Regresson n the hgh dmensonal settng How do we learn when the number of features d s greater than the sample sze n?
CSE 546: Machne Learnng Lecture 5 Feature Selecton: Part 1 Instructor: Sham Kakade 1 Regresson n the hgh dmensonal settng How do we learn when the number of features d s greater than the sample sze n?
Section 8.3 Polar Form of Complex Numbers
 80 Chapter 8 Secton 8 Polar Form of Complex Numbers From prevous classes, you may have encountered magnary numbers the square roots of negatve numbers and, more generally, complex numbers whch are the
80 Chapter 8 Secton 8 Polar Form of Complex Numbers From prevous classes, you may have encountered magnary numbers the square roots of negatve numbers and, more generally, complex numbers whch are the
Outline. Communication. Bellman Ford Algorithm. Bellman Ford Example. Bellman Ford Shortest Path [1]
![Outline. Communication. Bellman Ford Algorithm. Bellman Ford Example. Bellman Ford Shortest Path [1] Outline. Communication. Bellman Ford Algorithm. Bellman Ford Example. Bellman Ford Shortest Path [1]](/thumbs/81/84170417.jpg) DYNAMIC SHORTEST PATH SEARCH AND SYNCHRONIZED TASK SWITCHING Jay Wagenpfel, Adran Trachte 2 Outlne Shortest Communcaton Path Searchng Bellmann Ford algorthm Algorthm for dynamc case Modfcatons to our algorthm
DYNAMIC SHORTEST PATH SEARCH AND SYNCHRONIZED TASK SWITCHING Jay Wagenpfel, Adran Trachte 2 Outlne Shortest Communcaton Path Searchng Bellmann Ford algorthm Algorthm for dynamc case Modfcatons to our algorthm
Case A. P k = Ni ( 2L i k 1 ) + (# big cells) 10d 2 P k.
 THE CELLULAR METHOD In ths lecture, we ntroduce the cellular method as an approach to ncdence geometry theorems lke the Szemeréd-Trotter theorem. The method was ntroduced n the paper Combnatoral complexty
THE CELLULAR METHOD In ths lecture, we ntroduce the cellular method as an approach to ncdence geometry theorems lke the Szemeréd-Trotter theorem. The method was ntroduced n the paper Combnatoral complexty
LINEAR REGRESSION ANALYSIS. MODULE IX Lecture Multicollinearity
 LINEAR REGRESSION ANALYSIS MODULE IX Lecture - 30 Multcollnearty Dr. Shalabh Department of Mathematcs and Statstcs Indan Insttute of Technology Kanpur 2 Remedes for multcollnearty Varous technques have
LINEAR REGRESSION ANALYSIS MODULE IX Lecture - 30 Multcollnearty Dr. Shalabh Department of Mathematcs and Statstcs Indan Insttute of Technology Kanpur 2 Remedes for multcollnearty Varous technques have
1 GSW Iterative Techniques for y = Ax
 1 for y = A I m gong to cheat here. here are a lot of teratve technques that can be used to solve the general case of a set of smultaneous equatons (wrtten n the matr form as y = A), but ths chapter sn
1 for y = A I m gong to cheat here. here are a lot of teratve technques that can be used to solve the general case of a set of smultaneous equatons (wrtten n the matr form as y = A), but ths chapter sn
Finding Dense Subgraphs in G(n, 1/2)
 Fndng Dense Subgraphs n Gn, 1/ Atsh Das Sarma 1, Amt Deshpande, and Rav Kannan 1 Georga Insttute of Technology,atsh@cc.gatech.edu Mcrosoft Research-Bangalore,amtdesh,annan@mcrosoft.com Abstract. Fndng
Fndng Dense Subgraphs n Gn, 1/ Atsh Das Sarma 1, Amt Deshpande, and Rav Kannan 1 Georga Insttute of Technology,atsh@cc.gatech.edu Mcrosoft Research-Bangalore,amtdesh,annan@mcrosoft.com Abstract. Fndng
Hopfield Training Rules 1 N
 Hopfeld Tranng Rules To memorse a sngle pattern Suppose e set the eghts thus - = p p here, s the eght beteen nodes & s the number of nodes n the netor p s the value requred for the -th node What ll the
Hopfeld Tranng Rules To memorse a sngle pattern Suppose e set the eghts thus - = p p here, s the eght beteen nodes & s the number of nodes n the netor p s the value requred for the -th node What ll the
COS 511: Theoretical Machine Learning. Lecturer: Rob Schapire Lecture # 15 Scribe: Jieming Mao April 1, 2013
 COS 511: heoretcal Machne Learnng Lecturer: Rob Schapre Lecture # 15 Scrbe: Jemng Mao Aprl 1, 013 1 Bref revew 1.1 Learnng wth expert advce Last tme, we started to talk about learnng wth expert advce.
COS 511: heoretcal Machne Learnng Lecturer: Rob Schapre Lecture # 15 Scrbe: Jemng Mao Aprl 1, 013 1 Bref revew 1.1 Learnng wth expert advce Last tme, we started to talk about learnng wth expert advce.
The Expectation-Maximization Algorithm
 The Expectaton-Maxmaton Algorthm Charles Elan elan@cs.ucsd.edu November 16, 2007 Ths chapter explans the EM algorthm at multple levels of generalty. Secton 1 gves the standard hgh-level verson of the algorthm.
The Expectaton-Maxmaton Algorthm Charles Elan elan@cs.ucsd.edu November 16, 2007 Ths chapter explans the EM algorthm at multple levels of generalty. Secton 1 gves the standard hgh-level verson of the algorthm.
18.1 Introduction and Recap
 CS787: Advanced Algorthms Scrbe: Pryananda Shenoy and Shjn Kong Lecturer: Shuch Chawla Topc: Streamng Algorthmscontnued) Date: 0/26/2007 We contnue talng about streamng algorthms n ths lecture, ncludng
CS787: Advanced Algorthms Scrbe: Pryananda Shenoy and Shjn Kong Lecturer: Shuch Chawla Topc: Streamng Algorthmscontnued) Date: 0/26/2007 We contnue talng about streamng algorthms n ths lecture, ncludng
Valuated Binary Tree: A New Approach in Study of Integers
 Internatonal Journal of Scentfc Innovatve Mathematcal Research (IJSIMR) Volume 4, Issue 3, March 6, PP 63-67 ISS 347-37X (Prnt) & ISS 347-34 (Onlne) wwwarcournalsorg Valuated Bnary Tree: A ew Approach
Internatonal Journal of Scentfc Innovatve Mathematcal Research (IJSIMR) Volume 4, Issue 3, March 6, PP 63-67 ISS 347-37X (Prnt) & ISS 347-34 (Onlne) wwwarcournalsorg Valuated Bnary Tree: A ew Approach
Durban Watson for Testing the Lack-of-Fit of Polynomial Regression Models without Replications
 Durban Watson for Testng the Lack-of-Ft of Polynomal Regresson Models wthout Replcatons Ruba A. Alyaf, Maha A. Omar, Abdullah A. Al-Shha ralyaf@ksu.edu.sa, maomar@ksu.edu.sa, aalshha@ksu.edu.sa Department
Durban Watson for Testng the Lack-of-Ft of Polynomal Regresson Models wthout Replcatons Ruba A. Alyaf, Maha A. Omar, Abdullah A. Al-Shha ralyaf@ksu.edu.sa, maomar@ksu.edu.sa, aalshha@ksu.edu.sa Department
ISSN: ISO 9001:2008 Certified International Journal of Engineering and Innovative Technology (IJEIT) Volume 3, Issue 1, July 2013
 ISSN: 2277-375 Constructon of Trend Free Run Orders for Orthogonal rrays Usng Codes bstract: Sometmes when the expermental runs are carred out n a tme order sequence, the response can depend on the run
ISSN: 2277-375 Constructon of Trend Free Run Orders for Orthogonal rrays Usng Codes bstract: Sometmes when the expermental runs are carred out n a tme order sequence, the response can depend on the run
Appendix for Causal Interaction in Factorial Experiments: Application to Conjoint Analysis
 A Appendx for Causal Interacton n Factoral Experments: Applcaton to Conjont Analyss Mathematcal Appendx: Proofs of Theorems A. Lemmas Below, we descrbe all the lemmas, whch are used to prove the man theorems
A Appendx for Causal Interacton n Factoral Experments: Applcaton to Conjont Analyss Mathematcal Appendx: Proofs of Theorems A. Lemmas Below, we descrbe all the lemmas, whch are used to prove the man theorems
Appendix B: Resampling Algorithms
 407 Appendx B: Resamplng Algorthms A common problem of all partcle flters s the degeneracy of weghts, whch conssts of the unbounded ncrease of the varance of the mportance weghts ω [ ] of the partcles
407 Appendx B: Resamplng Algorthms A common problem of all partcle flters s the degeneracy of weghts, whch conssts of the unbounded ncrease of the varance of the mportance weghts ω [ ] of the partcles
Single-Facility Scheduling over Long Time Horizons by Logic-based Benders Decomposition
 Sngle-Faclty Schedulng over Long Tme Horzons by Logc-based Benders Decomposton Elvn Coban and J. N. Hooker Tepper School of Busness, Carnege Mellon Unversty ecoban@andrew.cmu.edu, john@hooker.tepper.cmu.edu
Sngle-Faclty Schedulng over Long Tme Horzons by Logc-based Benders Decomposton Elvn Coban and J. N. Hooker Tepper School of Busness, Carnege Mellon Unversty ecoban@andrew.cmu.edu, john@hooker.tepper.cmu.edu
Comparison of Regression Lines
 STATGRAPHICS Rev. 9/13/2013 Comparson of Regresson Lnes Summary... 1 Data Input... 3 Analyss Summary... 4 Plot of Ftted Model... 6 Condtonal Sums of Squares... 6 Analyss Optons... 7 Forecasts... 8 Confdence
STATGRAPHICS Rev. 9/13/2013 Comparson of Regresson Lnes Summary... 1 Data Input... 3 Analyss Summary... 4 Plot of Ftted Model... 6 Condtonal Sums of Squares... 6 Analyss Optons... 7 Forecasts... 8 Confdence
The L(2, 1)-Labeling on -Product of Graphs
 Annals of Pure and Appled Mathematcs Vol 0, No, 05, 9-39 ISSN: 79-087X (P, 79-0888(onlne Publshed on 7 Aprl 05 wwwresearchmathscorg Annals of The L(, -Labelng on -Product of Graphs P Pradhan and Kamesh
Annals of Pure and Appled Mathematcs Vol 0, No, 05, 9-39 ISSN: 79-087X (P, 79-0888(onlne Publshed on 7 Aprl 05 wwwresearchmathscorg Annals of The L(, -Labelng on -Product of Graphs P Pradhan and Kamesh
Calculation of time complexity (3%)
 Problem 1. (30%) Calculaton of tme complexty (3%) Gven n ctes, usng exhaust search to see every result takes O(n!). Calculaton of tme needed to solve the problem (2%) 40 ctes:40! dfferent tours 40 add
Problem 1. (30%) Calculaton of tme complexty (3%) Gven n ctes, usng exhaust search to see every result takes O(n!). Calculaton of tme needed to solve the problem (2%) 40 ctes:40! dfferent tours 40 add
MEM 255 Introduction to Control Systems Review: Basics of Linear Algebra
 MEM 255 Introducton to Control Systems Revew: Bascs of Lnear Algebra Harry G. Kwatny Department of Mechancal Engneerng & Mechancs Drexel Unversty Outlne Vectors Matrces MATLAB Advanced Topcs Vectors A
MEM 255 Introducton to Control Systems Revew: Bascs of Lnear Algebra Harry G. Kwatny Department of Mechancal Engneerng & Mechancs Drexel Unversty Outlne Vectors Matrces MATLAB Advanced Topcs Vectors A
LECTURE 9 CANONICAL CORRELATION ANALYSIS
 LECURE 9 CANONICAL CORRELAION ANALYSIS Introducton he concept of canoncal correlaton arses when we want to quantfy the assocatons between two sets of varables. For example, suppose that the frst set of
LECURE 9 CANONICAL CORRELAION ANALYSIS Introducton he concept of canoncal correlaton arses when we want to quantfy the assocatons between two sets of varables. For example, suppose that the frst set of
The KMO Method for Solving Non-homogenous, m th Order Differential Equations
 The KMO Method for Solvng Non-homogenous, m th Order Dfferental Equatons Davd Krohn Danel Marño-Johnson John Paul Ouyang March 14, 2013 Abstract Ths paper shows a smple tabular procedure for fndng the
The KMO Method for Solvng Non-homogenous, m th Order Dfferental Equatons Davd Krohn Danel Marño-Johnson John Paul Ouyang March 14, 2013 Abstract Ths paper shows a smple tabular procedure for fndng the
Graph Reconstruction by Permutations
 Graph Reconstructon by Permutatons Perre Ille and Wllam Kocay* Insttut de Mathémathques de Lumny CNRS UMR 6206 163 avenue de Lumny, Case 907 13288 Marselle Cedex 9, France e-mal: lle@ml.unv-mrs.fr Computer
Graph Reconstructon by Permutatons Perre Ille and Wllam Kocay* Insttut de Mathémathques de Lumny CNRS UMR 6206 163 avenue de Lumny, Case 907 13288 Marselle Cedex 9, France e-mal: lle@ml.unv-mrs.fr Computer
Refined Coding Bounds for Network Error Correction
 Refned Codng Bounds for Network Error Correcton Shenghao Yang Department of Informaton Engneerng The Chnese Unversty of Hong Kong Shatn, N.T., Hong Kong shyang5@e.cuhk.edu.hk Raymond W. Yeung Department
Refned Codng Bounds for Network Error Correcton Shenghao Yang Department of Informaton Engneerng The Chnese Unversty of Hong Kong Shatn, N.T., Hong Kong shyang5@e.cuhk.edu.hk Raymond W. Yeung Department
EEE 241: Linear Systems
 EEE : Lnear Systems Summary #: Backpropagaton BACKPROPAGATION The perceptron rule as well as the Wdrow Hoff learnng were desgned to tran sngle layer networks. They suffer from the same dsadvantage: they
EEE : Lnear Systems Summary #: Backpropagaton BACKPROPAGATION The perceptron rule as well as the Wdrow Hoff learnng were desgned to tran sngle layer networks. They suffer from the same dsadvantage: they
THE CHINESE REMAINDER THEOREM. We should thank the Chinese for their wonderful remainder theorem. Glenn Stevens
 THE CHINESE REMAINDER THEOREM KEITH CONRAD We should thank the Chnese for ther wonderful remander theorem. Glenn Stevens 1. Introducton The Chnese remander theorem says we can unquely solve any par of
THE CHINESE REMAINDER THEOREM KEITH CONRAD We should thank the Chnese for ther wonderful remander theorem. Glenn Stevens 1. Introducton The Chnese remander theorem says we can unquely solve any par of
CHAPTER III Neural Networks as Associative Memory
 CHAPTER III Neural Networs as Assocatve Memory Introducton One of the prmary functons of the bran s assocatve memory. We assocate the faces wth names, letters wth sounds, or we can recognze the people
CHAPTER III Neural Networs as Assocatve Memory Introducton One of the prmary functons of the bran s assocatve memory. We assocate the faces wth names, letters wth sounds, or we can recognze the people
Speeding up Computation of Scalar Multiplication in Elliptic Curve Cryptosystem
 H.K. Pathak et. al. / (IJCSE) Internatonal Journal on Computer Scence and Engneerng Speedng up Computaton of Scalar Multplcaton n Ellptc Curve Cryptosystem H. K. Pathak Manju Sangh S.o.S n Computer scence
H.K. Pathak et. al. / (IJCSE) Internatonal Journal on Computer Scence and Engneerng Speedng up Computaton of Scalar Multplcaton n Ellptc Curve Cryptosystem H. K. Pathak Manju Sangh S.o.S n Computer scence
A PROBABILITY-DRIVEN SEARCH ALGORITHM FOR SOLVING MULTI-OBJECTIVE OPTIMIZATION PROBLEMS
 HCMC Unversty of Pedagogy Thong Nguyen Huu et al. A PROBABILITY-DRIVEN SEARCH ALGORITHM FOR SOLVING MULTI-OBJECTIVE OPTIMIZATION PROBLEMS Thong Nguyen Huu and Hao Tran Van Department of mathematcs-nformaton,
HCMC Unversty of Pedagogy Thong Nguyen Huu et al. A PROBABILITY-DRIVEN SEARCH ALGORITHM FOR SOLVING MULTI-OBJECTIVE OPTIMIZATION PROBLEMS Thong Nguyen Huu and Hao Tran Van Department of mathematcs-nformaton,
8.6 The Complex Number System
 8.6 The Complex Number System Earler n the chapter, we mentoned that we cannot have a negatve under a square root, snce the square of any postve or negatve number s always postve. In ths secton we want
8.6 The Complex Number System Earler n the chapter, we mentoned that we cannot have a negatve under a square root, snce the square of any postve or negatve number s always postve. In ths secton we want
