Theoretical Linear Convergence of Unfolded ISTA and its Practical Weights and Thresholds
|
|
|
- Edward Ross
- 5 years ago
- Views:
Transcription
1 Theoretical Linear Convergence of Unfolded ISTA and its Practical Weights and Thresholds Xiaohan Chen Department of Computer Science and Engineering Texas A&M University College Station, TX 77843, USA Zhangyang Wang Department of Computer Science and Engineering Texas A&M University College Station, TX 77843, USA Jialin Liu Department of Mathematics University of California, Los Angeles Los Angeles, CA 995, USA Wotao Yin Department of Mathematics University of California, Los Angeles Los Angeles, CA 995, USA Abstract In recent years, unfolding iterative algorithms as neural networks has become an empirical success in solving sparse recovery problems. However, its theoretical understanding is still immature, which prevents us from fully utilizing the power of neural networks. In this work, we study unfolded ISTA Iterative Shrinkage Thresholding Algorithm for sparse signal recovery. We introduce a weight structure that is necessary for asymptotic convergence to the true sparse signal. With this structure, unfolded ISTA can attain a linear convergence, which is better than the sublinear convergence of ISTA/FISTA in general cases. Furthermore, we propose to incorporate thresholding in the network to perform support selection, which is easy to implement and able to boost the convergence rate both theoretically and empirically. Extensive simulations, including sparse vector recovery and a compressive sensing experiment on real image data, corroborate our theoretical results and demonstrate their practical usefulness. We have made our codes publicly available Introduction This paper aims to recover a sparse vector x from its noisy linear measurements: b = Ax + ε, 1 where b R m, x R n, A R m n, ε R m is additive Gaussian white noise, and we have m n. 1 is an ill-posed, highly under-determined system. However, it becomes easier to solve if x is assumed to be sparse, i.e. the cardinality of support of x, S = {i x i }, is small compared to n. A popular approach is to model the problem as the LASSO formulation λ is a scalar: 1 minimize x 2 b Ax λ x 1 2 and solve it using iterative algorithms such as the iterative shrinkage thresholding algorithm ISTA [1]: x k+1 = η λ/l x k + 1 L AT b Ax k, k =, 1, 2,... 3 These authors contributed equally and are listed alphabetically nd Conference on Neural Information Processing Systems NIPS 218, Montréal, Canada.
2 where η θ is the soft-thresholding function 3 and L is usually taken as the largest eigenvalue of A T A. In general, ISTA converges sublinearly for any given and fixed dictionary A and sparse code x [2] In [3], inspired by ISTA, the authors proposed a learning-based model named Learned ISTA LISTA. They view ISTA as a recurrent neural network RNN that is illustrated in Figure 1a, where W 1 = 1 L AT, W 2 = I 1 L AT A, θ = 1 Lλ. LISTA, illustrated in Figure 1b, unrolls the RNN and truncates it into K iterations: x k+1 = η θ kw k 1 b + W k 2 x k, k =, 1,, K 1, 4 leading to a K-layer feed-forward neural network with side connections. Different from ISTA where no parameter is learnable except the hyper parameter λ to be tuned, LISTA is treated as a specially structured neural network and trained using stochastic gradient descent SGD, over a given training dataset {x i, b i} N i=1 sampled from some distribution Px, b. All the parameters Θ = {W1 k, W2 k, θ k } K 1 k= are subject to learning. The training is modeled as: minimize E x Θ,b x K Θ, b, x x 2. 5 Many empirical results, e.g., [3 7], show that a trained K-layer LISTA with K usually set to 1 2 or its variants can generalize more than well to unseen samples x, b from the same Px, b and recover x from b to the same accuracy within one or two order-of-magnitude fewer iterations than the original ISTA. Moreover, the accuracies of the outputs {x k } of the layers k = 1,.., K gradually improve. 2 a RNN structure of ISTA. b Unfolded learned ISTA Network. 1.1 Related Works Figure 1: Diagrams of ISTA and LISTA. Many recent works [8, 9, 4, 1, 11] followed the idea of [3] to construct feed-forward networks by unfolding and truncating iterative algorithms, as fast trainable regressors to approximate the solutions of sparse coding models. On the other hand, progress has been slow towards understanding the efficient approximation from a theoretical perspective. The most relevant works are discussed below. [12] attempted to explain the mechanism of LISTA by re-factorizing the Gram matrix of dictionary, which tries to nearly diagonalize the Gram matrix with a basis that produces a small perturbation of the l 1 ball. They re-parameterized LISTA into a new factorized architecture that achieved similar acceleration gain to LISTA. Using an indirect proof, [12] was able to show that LISTA can converge faster than ISTA, but still sublinearly. Lately, [13] tried to relate LISTA to a projected gradient descent descent PGD relying on inaccurate projections, where a trade-off between approximation error and convergence speed was made possible. [14] investigated the convergence property of a sibling architecture to LISTA, proposed in [4], which was obtained by instead unfolding/truncating the iterative hard thresholding IHT algorithm rather than ISTA. The authors argued that they can use data to train a transformation of dictionary that can improve its restricted isometry property RIP constant, when the original dictionary is highly correlated, causing IHT to fail easily. They moreover showed it beneficial to allow the weights to decouple across layers. However, the analysis in [14] cannot be straightforwardly extended to ISTA although IHT is linearly convergent [15] under rather strong assumptions. In [16], a similar learning-based model inspired by another iterative algorithm solve LASSO, approximated message passing AMP, was studied. The idea was advanced in [17] to substituting the AMP 3 Soft-thresholding function is defined in a component-wise way: η θ x = signx max, x θ 2
3 proximal operator soft-thresholding with a learnable Gaussian denoiser. The resulting model, called Learned Denoising AMP L-DAMP, has theoretical guarantees under the asymptotic assumption named state evolution. While the assumption is common in analyzing AMP algorithms, the tool is not directly applicable to ISTA. Moreover, [16] shows L-DAMP is MMSE optimal, but there is no result on its convergence rate. Besides, we also note the empirical effort in [18] that introduces an Onsager correction to LISTA to make it resemble AMP. 1.2 Motivations and Contributions We attempt to answer the following questions, which are not fully addressed in the literature yet: Rather than training LISTA as a conventional black-box network, can we benefit from exploiting certain dependencies among its parameters {W1 k, W2 k, θ k } K 1 k= to simplify the network and improve the recovery results? Obtained with sufficiently many training samples from the target distribution Px, b, LISTA works very well. So, we wonder if there is a theoretical guarantee to ensure that LISTA 4 converges 4 faster and/or produces a better solution than ISTA 3 when its parameters are ideal? If the answer is affirmative, can we quantize the amount of acceleration? Can some of the acceleration techniques such as support detection that were developed for LASSO also be used to improve LISTA? Our Contributions: this paper aims to introduce more theoretical insights for LISTA and to further unleash its power. To our best knowledge, this is the first attempt to establish a theoretical convergence rate upper bound of LISTA directly. We also observe that the weight structure and the thresholds can speedup the convergence of LISTA: We give a result on asymptotic coupling between the weight matrices W k 1 and W k 2. This result leads us to eliminating one of them, thus reducing the number of trainable parameters. This elimination still retains the theoretical and experimental performance of LISTA. ISTA is generally sublinearly convergent before its iterates settle on a support. We prove that, however, there exists a sequence of parameters that makes LISTA converge linearly since its first iteration. Our numerical experiments support this theoretical result. Furthermore, we introduce a thresholding scheme for support selection, which is extremely simple to implement and significantly boosts the practical convergence. The linear convergence results are extended to support detection with an improved rate. Detailed discussions of the above three points will follow after Theorems 1, 2 and 3, respectively. Our proofs do not rely on any indirect resemblance, e.g., to AMP [18] or PGD [13]. The theories are supported by extensive simulation experiments, and substantial performance improvements are observed when applying the weight coupling and support selection schemes. We also evaluated LISTA equipped with those proposed techniques in an image compressive sensing task, obtaining superior performance over several of the state-of-the-arts. 2 Algorithm Description We first establish the necessary condition for LISTA convergence, which implies a partial weight coupling structure for training LISTA. We then describe the support-selection technique. 2.1 Necessary Condition for LISTA Convergence and Partial Weight Coupling Assumption 1 Basic assumptions. The signal x and the observation noise ε are sampled from the following set: { } x, ε X B, s, σ x, ε x i B, i, x s, ε 1 σ. 6 In other words, x is bounded and s-sparse 5 s 2, and ε is bounded. Theorem 1 Necessary Condition. Given {W1 k, W2 k, θ k } k= and x =, let b be observed by 1 and {x k } k=1 be generated layer-wise by LISTA 4. If the following holds uniformly for any 4 The convergence of ISTA/FISTA measures how fast the k-th iterate proceeds; the convergence of LISTA measures how fast the output of the k-th layer proceeds as k increases. 5 A signal is s-sparse if it has no more than s non-zero entries. 3
4 x, ε X B, s, no observation noise: and {W2 k } k=1 are bounded W then {W1 k, W2 k, θ k } k= must satisfy x k {W τ 1, W τ 2, θ τ } k 1 τ=, b, x x, as k k 2 2 B W, k =, 1, 2,, W k 2 I W k 1 A, as k 7 θ k, as k. 8 Proofs of the results throughout this paper can be found in the supplementary. The conclusion 7 demonstrates that the weights {W1 k, W2 k } k= in LISTA asymptotically satisfies the following partial weight coupling structure: W2 k = I W1 k A. 9 We adopt the above partial weight coupling for all layers, letting W k = W1 k T R m n, thus simplifying LISTA 4 to: x k+1 = η θ k x k + W k b Ax k, k =, 1,, K 1, 1 where {W k, θ k } K 1 k= remain as free parameters to train. Empirical results in Fig. 3 illustrate that the structure 9, though having fewer parameters, improves the performance of LISTA. The coupled structure 9 for soft-thresholding based algorithms was empirically studied in [16]. The similar structure was also theoretically studied in Proposition 1 of [14] for IHT algorithms using the fixed-point theory, but they let all layers share the same weights, i.e. W k 2 = W 2, W k 1 = W 1, k. 2.2 LISTA with Support Selection We introduce a special thresholding scheme to LISTA, called support selection, which is inspired by kicking [19] in linearized Bregman iteration. This technique shows advantages on recoverability and convergence. Its impact on improving LISTA convergence rate and reducing recovery errors will be analyzed in Section 3. With support selection, at each LISTA layer before applying soft thresholding, we will select a certain percentage of entries with largest magnitudes, and trust them as true support and won t pass them through thresholding. Those entries that do not go through thresholding will be directly fed into next layer, together with other thresholded entires. Assume we select p k % of entries as the trusted support at layer k. LISTA with support selection can be generally formulated as x k+1 = η ss p k θ k W k 1 b + W k 2 x k, k =, 1,, K 1, 11 where η ss is the thresholding operator with support selection, formally defined as: v i : v i > θ k, i S pk v, v i θ k : v i > θ k, i / S pk v, p η k ss v θ k i = : θ k v i θ k v i + θ k : v i < θ k, i / S pk v, v i : v i < θ k, i S pk v, where S pk v includes the elements { with the largest p k % magnitudes in vector v: } S pk v = i 1, i 2,, i p k v i1 v i2 v v ip k i n. 12 To clarify, in 11, p k is a hyperparameter to be manually tuned, and θ k is a parameter to train. We use an empirical formula to select p k for layer k: p k = minp k, p max, where p is a positive constant and p max is an upper bound of the percentage of the support cardinality. Here p and p max are both hyperparameters to be manually tuned. If we adopt the partial weight coupling in 9, then 11 is modified as x k+1 p = η k ss x k + W k T b Ax k, k =, 1,, K θ k 4
5 Algorithm abbreviations For simplicity, hereinafter we will use the abbreviation CP for the partial weight coupling in 9, and SS for the support selection technique. LISTA-CP denotes the LISTA model with weights coupling 1. LISTA-SS denotes the LISTA model with support selection 11. Similarly, LISTA-CPSS stands for a model using both techniques 13, which has the best performance. Unless otherwise specified, LISTA refers to the baseline LISTA 4. 3 Convergence Analysis In this section, we formally establish the impacts of 1 and 13 on LISTA s convergence. The output of the k th layer x k depends on the parameters {W τ, θ τ } k 1 τ=, the observed measurement b and the initial point x. Strictly speaking, x k should be written as x k {W τ, θ τ } k 1 τ=., b, x By the observation model b = Ax + ε, since A is given and x can be taken as, x k therefore depends on {W τ, θ τ } k τ=, x and ε. So, we can write x k {W τ, θ τ } k 1 τ=, x, ε. For simplicity, we instead just write x k x, ε. Theorem 2 Convergence of LISTA-CP. Given {W k, θ k } k= and x =, let {x k } k=1 be generated by 1. If Assumption 1 holds and s is sufficiently small, then there exists a sequence of parameters {W k, θ k } such that, for all x, ε X B, s, σ, we have the error bound: x k x, ε x 2 sb exp ck + Cσ, k = 1, 2,, 14 where c >, C > are constants that depend only on A and s. Recall s sparsity of the signals and σ noise-level are defined in 6. If σ = noiseless case, 14 reduces to x k x, x 2 sb exp ck. 15 The recovery error converges to at a linear rate as the number of layers goes to infinity. Combined with Theorem 1, we see that the partial weight coupling structure 1 is both necessary and sufficient to guarantee convergence in the noiseless case. Fig. 3 validates 14 and 15 directly. Discussion: The bound 15 also explains why LISTA or its variants can converge faster than ISTA and fast ISTA FISTA [2]. With a proper λ see 2, ISTA converges at an O1/k rate and FISTA converges at an O1/k 2 rate [2]. With a large enough λ, ISTA achieves a linear rate [2, 21]. With xλ being the solution of LASSO noiseless case, these results can be summarized as: before the iterates x k settle on a support 6, x k xλ sublinearly, xλ x = Oλ, λ > x k xλ linearly, xλ x = Oλ, λ large enough. Based on the choice of λ in LASSO, the above observation reflects an inherent trade-off between convergence rate and approximation accuracy in solving the problem 1, see a similar conclusion in [13]: a larger λ leads to faster convergence but a less accurate solution, and vice versa. However, if λ is not constant throughout all iterations/layers, but instead chosen adaptively for each step, more promising trade-off can arise 7. LISTA and LISTA-CP, with the thresholds {θ k } K 1 k= free to train, actually adopt this idea because {θ k } K 1 k= corresponds to a path of LASSO parameters {λk } K 1 k=. With extra free trainable parameters, {W k } K 1 k= LISTA-CP or {W 1 k, W2 k } K 1 k= LISTA, learning based algorithms are able to converge to an accurate solution at a fast convergence rate. Theorem 2 demonstrates the existence of such sequence {W k, θ k } k in LISTA-CP 1. The experiment results in Fig. 4 show that such {W k, θ k } k can be obtained by training. Assumption 2. Signal x and observation noise ε are sampled from the following set: x, ε X { } B, B, s, σ x, ε x i B, i, x 1 B, x s, ε 1 σ After x k settles on a support, i.e. as k large enough such that supportx k is fixed, even with small λ, ISTA reduces to a linear iteration, which has a linear convergence rate [22]. 7 This point was studied in [23, 24] with classical compressive sensing settings, while our learning settings can learn a good path of parameters without a complicated thresholding rule or any manual tuning. 5
6 Theorem 3 Convergence of LISTA-CPSS. Given {W k, θ k } k= and x =, let {x k } k=1 be generated by 13. With the same assumption and parameters as in Theorem 2, the approximation error can be bounded for all x, ε X B, s, σ: k 1 x k x, ε x 2 sb exp + C ss σ, k = 1, 2,, 17 where c k ss c for all k and C ss C. If Assumption 2 holds, s is small enough, and B 2Cσ SNR is not too small, then there exists another sequence of parameters { W k, θ k } that yields the following improved error bound: for all x, ε X B, B, s, σ, x k x, ε x 2 sb exp k 1 where c k ss c for all k, c k ss > c for large enough k, and C ss < C. c t ss c t ss + C ss σ, k = 1, 2,, 18 The bound in 17 ensures that, with the same assumptions and parameters, LISTA-CPSS is at least no worse than LISTA-CP. The bound in 18 shows that, under stronger assumptions, LISTA-CPSS can be strictly better than LISTA-CP in both folds: c k ss > c is the better convergence rate of LISTA-CPSS; C ss < C means that the LISTA-CPSS can achieve smaller approximation error than the minimum error that LISTA can achieve. 4 Numerical Results For all the models reported in this section, including the baseline LISTA and LAMP models, we adopt a stage-wise training strategy with learning rate decaying to stabilize the training and to get better performance, which is discussed in the supplementary. 4.1 Simulation Experiments Experiments Setting. We choose m = 25, n = 5. We sample the entries of A i.i.d. from the standard Gaussian distribution, A ij N, 1/m and then normalize its columns to have the unit l 2 norm. We fix a matrix A in each setting where different networks are compared. To generate sparse vectors x, we decide each of its entry to be non-zero following the Bernoulli distribution with p b =.1. The values of the non-zero entries are sampled from the standard Gaussian distribution. A test set of 1 samples generated in the above manner is fixed for all tests in our simulations. All the networks have K = 16 layers. In LISTA models with support selection, we add p% of entries into support and maximally select p max % in each layer. We manually tune the value of p and p max for the best final performance. With p b =.1 and K = 16, we choose p = 1.2 for all models in simulation experiments and p max = 12 for LISTA-SS but p max = 13 for LISTA-CPSS. The recovery performance is evaluated by NMSE in db: E ˆx x NMSEˆx, x 2 = 1 log 1 E x 2, where x is the ground truth and ˆx is the estimate obtained by the recovery algorithms ISTA, FISTA, LISTA, etc.. Validation of Theorem 1. In Fig 2, we report two values, W k 2 I W k 1 A 2 and θ k, obtained by the baseline LISTA model 4 trained under the noiseless setting. The plot clearly demonstrates that W k 2 I W k 1 A, and θ k, as k. Theorem 1 is directly validated. Validation of Theorem 2. We report the test-set NMSE of LISTA-CP 1 in Fig. 3. Although 1 fixes the structure between W1 k and W2 k, the final performance remains the same with the baseline LISTA 4, and outperforms AMP, in both noiseless and noisy cases. Moreover, the output of interior layers in LISTA-CP are even better than the baseline LISTA. In the noiseless case, NMSE converges exponentially to ; in the noisy case, NMSE converges to a stationary level related with the noise-level. This supports Theorem 2: there indeed exist a sequence of parameters {W k, θ k } K 1 k= leading to linear convergence for LISTA-CP, and they can be obtained by data-driven learning. 6
7 a Weight W k 2 I W k 1 A as k b The threshold θ k. Figure 2: Validation of Theorem ISTA FISTA AMP LISTA LISTA-CP -4 ISTA FISTA AMP LISTA LISTA-CP a SNR = b SNR = 3 Figure 3: Validation of Theorem 2. Validation of Discussion after Theorem 2. In Fig 4, We compare LISTA-CP and ISTA with different λs see the LASSO problem 2 as well as an adaptive threshold rule similar to one in [23], which is described in the supplementary. As we have discussed after Theorem 2, LASSO has an inherent tradeoff based on the choice of λ. A smaller λ leads to a more accurate solution but slower convergence. The adaptive thresholding rule fixes this issue: it uses large λ k for NMSE db ISTA =.1 ISTA =.5 ISTA =.25 LISTA-CP ISTA adaptive Figure 4: Validating Discussion after Theorem 2 SNR =. small k, and gradually reduces it as k increases to improve the accuracy [23]. Except for adaptive thresholds {θ k } k θ k corresponds to λ k in LASSO, LISTA-CP has adaptive weights {W k } k, which further greatly accelerate the convergence. Note that we only ran ISTA and FISTA for 16 iterations, just enough and fair to compare them with the learned models. The number of iterations is so small that the difference between ISTA and FISTA is not quite observable. Validation of Theorem 3. We compare the recovery NMSEs of LISTA-CP 1 and LISTA-CPSS 13 in Fig. 5. The result of the noiseless case Fig. 5a shows that the recovery error of LISTA-SS converges to at a faster rate than that of LISTA-CP. The difference is significant with the number of layers k 1, which supports our theoretical result: c k ss > c as k large enough in Theorem 3. The result of the noisy case Fig. 5b shows that LISTA-CPSS has better recovery error than LISTA-CP. This point supports C ss < C in Theorem 3. Notably, LISTA-CPSS also outperforms LAMP [16], when k > 1 in the noiseless case, and even earlier as SNR becomes lower. Performance with Ill-Conditioned Matrix. We train LISTA, LAMP, LISTA-CPSS with illconditioned matrices A of condition numbers κ = 5, 3, 5. As is shown in Fig. 6, as κ increases, the performance of LISTA remains stable while LAMP becomes worse, and eventually inferior to LISTA when κ = 5. Although our LISTA-CPSS also suffers from ill-conditioning, its performance always stays much better than LISTA and LAMP. k 7
8 ISTA FISTA AMP LISTA LAMP LISTA-CP LISTA-SS LISTA-CPSS -4-5 ISTA FISTA AMP LISTA LAMP LISTA-CP LISTA-SS LISTA-CPSS a Noiseless Case b Noisy Case: SNR=4dB ISTA FISTA AMP LISTA LAMP LISTA-CP LISTA-SS LISTA-CPSS -2 ISTA FISTA AMP LISTA LAMP LISTA-CP LISTA-SS LISTA-CPSS c Noisy Case: SNR=3dB d Noisy Case: SNR=2dB Figure 5: Validation of Theorem LISTA LAMP LISTA-CPSS -5-6 LISTA LAMP LISTA-CPSS -5-6 LISTA LAMP LISTA-CPSS a κ = b κ = c κ = 5 Figure 6: Performance in ill-conditioned situations SNR =. 4.2 Natural Image Compressive Sensing Experiments Setting. We perform a compressive sensing CS experiment on natural images patches. We divide the BSD5 [25] set into a training set of 4 images, a validation set of 5 images, and a test set of 5 images. For training, we extract 1, patches f R at random positions of each image, with all means removed. We then learn a dictionary D R from them, using a block proximal gradient method [26]. For each testing image, we divide it into non-overlapping patches. A Gaussian sensing matrices Φ R m 256 is created in the same manner as in Sec. 4.1, where m 256 is the CS ratio. Since f is typically not exactly sparse under the dictionary D, Assumptions 1 and 2 no longer strictly hold. The primary goal of this experiment is thus to show that our proposed techniques remain robust and practically useful in non-ideal conditions, rather than beating all CS state-of-the-arts. Network Extension. In the real data case, we have no ground-truth sparse code available as the regression target for the loss function 5. In order to bypass pre-computing sparse codes f over D on the training set, we are inspired by [11]: first using layer-wise pre-training with a reconstruction loss w.r.t. dictionary D plus an l 1 loss, shown in 19, where k is the layer index and Θ k denotes all parameters in the k-th and previous layers; then appending another learnable fully-connected layer initialized by D to LISTA-CPSS and perform an end-to-end training with the cost function 2. L k Θ k = LΘ, W D = N f i D x k i Θ k λ x k i Θ k 1 19 i=1 N f i W D x K i Θ λ x K i Θ 1 2 i=1 8
9 Table 1: The Average PSRN db for Set 11 test images with CS ratio ranging from.2 to.6 Algorithm 2% 3% 4% 5% 6% TVAL Recon-Net LIHT LISTA LISTA-CPSS Results. The results are reported in Table 1. We build CS models at the sample rates of 2%, 3%, 4%, 5%, 6% and test on the standard Set 11 images as in [27]. We compare our results with three baselines: the classical iterative CS solver, TVAL3 [28]; the black-box deep learning CS solver, Recon-Net [27];a l -based network unfolded from IHT algorithm [15], noted as LIHT; and the baseline LISTA network, in terms of PSNR db 8. We build 16-layer LIHT, LISTA and LISTA-CPSS networks and set λ =.2. For LISTA-CPSS, we set p% =.4% more entries into the support in each layer for support selection. We also select support w.r.t. a percentage of the largest magnitudes within the whole batch rather than within a single sample as we do in theorems and simulated experiments, which we emprically find is beneficial to the recovery performance. Table 1 confirms LISTA-CPSS as the best performer among all. The advantage of LISTA-CPSS and LISTA over Recon-Net also endorses the incorporation of the unrolled sparse solver structure into deep networks. 5 Conclusions In this paper, we have introduced a partial weight coupling structure to LISTA, which reduces the number of trainable parameters but does not hurt the performance. With this structure, unfolded ISTA can attain a linear convergence rate. We have further proposed support selection, which improves the convergence rate both theoretically and empirically. Our theories are endorsed by extensive simulations and a real-data experiment. We believe that the methodology in this paper can be extended to analyzing and enhancing other unfolded iterative algorithms. Acknowledgments The work by X. Chen and Z. Wang is supported in part by NSF RI The work by J. Liu and W. Yin is supported in part by NSF DMS and ONR N We would also like to thank all anonymous reviewers for their tremendously useful comments to help improve our work. References [1] Thomas Blumensath and Mike E Davies. Iterative thresholding for sparse approximations. Journal of Fourier analysis and Applications, 145-6: , 28. [2] Amir Beck and Marc Teboulle. A fast iterative shrinkage-thresholding algorithm for linear inverse problems. SIAM journal on imaging sciences, 21:183 22, 29. [3] Karol Gregor and Yann LeCun. Learning fast approximations of sparse coding. In Proceedings of the 27th International Conference on International Conference on Machine Learning, pages Omnipress, 21. [4] Zhangyang Wang, Qing Ling, and Thomas Huang. Learning deep l encoders. In AAAI Conference on Artificial Intelligence, pages , 216. [5] Zhangyang Wang, Ding Liu, Shiyu Chang, Qing Ling, Yingzhen Yang, and Thomas S Huang. D3: Deep dual-domain based fast restoration of jpeg-compressed images. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages , 216. [6] Zhangyang Wang, Shiyu Chang, Jiayu Zhou, Meng Wang, and Thomas S Huang. Learning a task-specific deep architecture for clustering. In Proceedings of the 216 SIAM International Conference on Data Mining, pages SIAM, We applied TVAL3, LISTA and LISTA-CPSS on patches to be fair. For Recon-Net, we used their default setting working on patches, which was verified to perform better than using smaller patches. 9
10 [7] Zhangyang Wang, Yingzhen Yang, Shiyu Chang, Qing Ling, and Thomas S Huang. Learning a deep l encoder for hashing. pages , 216. [8] Pablo Sprechmann, Alexander M Bronstein, and Guillermo Sapiro. Learning efficient sparse and low rank models. IEEE transactions on pattern analysis and machine intelligence, 215. [9] Zhaowen Wang, Jianchao Yang, Haichao Zhang, Zhangyang Wang, Yingzhen Yang, Ding Liu, and Thomas S Huang. Sparse Coding and its Applications in Computer Vision. World Scientific. [1] Jian Zhang and Bernard Ghanem. ISTA-Net: Interpretable optimization-inspired deep network for image compressive sensing. In IEEE CVPR, 218. [11] Joey Tianyi Zhou, Kai Di, Jiawei Du, Xi Peng, Hao Yang, Sinno Jialin Pan, Ivor W Tsang, Yong Liu, Zheng Qin, and Rick Siow Mong Goh. SC2Net: Sparse LSTMs for sparse coding. In AAAI Conference on Artificial Intelligence, 218. [12] Thomas Moreau and Joan Bruna. Understanding trainable sparse coding with matrix factorization. In ICLR, 217. [13] Raja Giryes, Yonina C Eldar, Alex Bronstein, and Guillermo Sapiro. Tradeoffs between convergence speed and reconstruction accuracy in inverse problems. IEEE Transactions on Signal Processing, 218. [14] Bo Xin, Yizhou Wang, Wen Gao, David Wipf, and Baoyuan Wang. Maximal sparsity with deep networks? In Advances in Neural Information Processing Systems, pages , 216. [15] Thomas Blumensath and Mike E Davies. Iterative hard thresholding for compressed sensing. Applied and computational harmonic analysis, 273: , 29. [16] Mark Borgerding, Philip Schniter, and Sundeep Rangan. AMP-inspired deep networks for sparse linear inverse problems. IEEE Transactions on Signal Processing, 217. [17] Christopher A Metzler, Ali Mousavi, and Richard G Baraniuk. Learned D-AMP: Principled neural network based compressive image recovery. In Advances in Neural Information Processing Systems, pages , 217. [18] Mark Borgerding and Philip Schniter. Onsager-corrected deep learning for sparse linear inverse problems. In 216 IEEE Global Conference on Signal and Information Processing GlobalSIP. [19] Stanley Osher, Yu Mao, Bin Dong, and Wotao Yin. Fast linearized bregman iteration for compressive sensing and sparse denoising. Communications in Mathematical Sciences, 21. [2] Kristian Bredies and Dirk A Lorenz. Linear convergence of iterative soft-thresholding. Journal of Fourier Analysis and Applications, 145-6: , 28. [21] Lufang Zhang, Yaohua Hu, Chong Li, and Jen-Chih Yao. A new linear convergence result for the iterative soft thresholding algorithm. Optimization, 667: , 217. [22] Shaozhe Tao, Daniel Boley, and Shuzhong Zhang. Local linear convergence of ista and fista on the lasso problem. SIAM Journal on Optimization, 261: , 216. [23] Elaine T. Hale, Wotao Yin, and Yin Zhang. Fixed-point continuation for l 1 -minimization: methodology and convergence. SIAM Journal on Optimization, 193: , 28. [24] Lin Xiao and Tong Zhang. A proximal-gradient homotopy method for the sparse least-squares problem. SIAM Journal on Optimization, 232: , 213. [25] David Martin, Charless Fowlkes, Doron Tal, and Jitendra Malik. A database of human segmented natural images and its application to evaluating segmentation algorithms and measuring ecological statistics. In Proceedings of the International Conference on Computer Vision, volume 2, pages , 21. [26] Yangyang Xu and Wotao Yin. A block coordinate descent method for regularized multiconvex optimization with applications to nonnegative tensor factorization and completion. SIAM Journal on imaging sciences, 63: ,
11 [27] Kuldeep Kulkarni, Suhas Lohit, Pavan Turaga, Ronan Kerviche, and Amit Ashok. Recon- Net: Non-iterative reconstruction of images from compressively sensed measurements. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, 216. [28] Chengbo Li, Wotao Yin, Hong Jiang, and Yin Zhang. An efficient augmented lagrangian method with applications to total variation minimization. Computational Optimization and Applications, 563:57 53, 213. [29] Dimitris Bertsimas and John N Tsitsiklis. Introduction to linear optimization. Athena Scientific Belmont, MA,
12 Theoretical Linear Convergence of Unfolded ISTA and Its Practical Weights and Thresholds Supplementary Material Some notation For any n-dimensional vector x R n, subscript x S means the part of x that is supported on the index set S: x S [x i1, x i2,, x i S ] T, i 1,, i S S, i 1 i 2 i S, where S is the size of set S. For any matrix W R m n, W i 1, i 1, W i 1, i 2,, W i 1, i S W i W S, S 2, i 1, W i 2, i 2,, W i 2, i S, i 1,, i S S, i 1 i 2 i S, W i S, i 1, W i S, i 2,, W i S, i S W S, : W i 1, 1, W i 1, 2,, W i 1, n W i 2, 1, W i 2, 2,, W i 2, n W i S, 1, W i S, 2,, W i S, n, i 1,, i S S, i 1 i 2 i S, W 1, i 1, W 1, i 2,, W 1, i S W 2, i W :, S 1, W 2, i 2,, W 2, i S, i 1,, i S S, i 1 i 2 i S. W n, i 1, W n, i 2,, W n, i S A Proof of Theorem 1 Proof. By LISTA model 4, the output of the k-th layer x k depends on parameters, observed signal b and initial point x : x k {W1 τ, W2 τ, θ τ } k 1 τ=., b, x Since we assume x, ε X B, s,, the noise ε =. Moreover, A is fixed and x is taken as. Thus, x k therefore depends on parameters and x : x k {W τ 1, W τ 2, θ τ } k 1 τ=, x In this proof, for simplicity, we use x k denote x k {W τ 1, W τ 2, θ τ } k 1 τ=, x. Step 1 Firstly, we prove θ k as k. We define a subset of X B, s, given < B B: X B, B, { s, x, ε B } x i B, i, x s, ε = X B, s,. Since x k x uniformly for all x, X B, s,, so does for all x, X B, B/1, s,. Then there exists a uniform K 1 > for all x, X B, B/1, s,, such that x k i x i < B/1 for all i = 1, 2,, n and k K 1, which implies The relationship between x k and x k+1 is signx k = signx, k K x k+1 = η θ k W2 k x k + W1 k b. Let S = supportx. Then, 21 implies that, for any k K 1 and x, X B, B/1, s,, we have = η θ k W2 k S, Sx k S + W1 k S, :b. x k+1 S The fact 21 means x k+1 i, i S. By the definition η θ x = signx max, x θ, as long as η θ x i, we have η θ x i = x i θ signx i. Thus, x k+1 S = W k 2 S, Sx k S + W k 1 S, :b θ k signx S. 1
13 Furthermore, the uniform convergence of x k tells us, for any ɛ > and x, X B, B/1, s,, there exists a large enough constant K 2 > and ξ 1, ξ 2 R S such that x k S = x S + ξ 1, x k+1 S = x S + ξ 2 and ξ 1 2 ɛ, ξ 2 2 ɛ. Then x S + ξ 2 = W k 2 S, Sx S + ξ 1 + W k 1 S, :b θ k signx S. Since the noise is supposed to be zero ε =, b = Ax. Substituting b with Ax in the above equality, we obtain x S = W k 2 S, Sx S + W k 1 S, :A:, Sx S θ k signx S + ξ, where ξ 2 = W2 k S, Sξ 1 ξ B W ɛ, B W is defined in Theorem 1. Equivalently, I W2 k S, S W1 k AS, S x S = θ k signx S ξ. 22 For any x, X B/2, B/1, s,, 2x, X B, B/1, s, holds. Thus, the above argument holds for all 2x if x, X B/2, B/1, s,. Substituting x with 2x in 22, we get I W2 k S, S W1 k AS, S 2x S = θ k sign2x S ξ = θ k signx S ξ, 23 where ξ B W ɛ. Taking the difference between 22 and 23, we have I W2 k S, S W1 k AS, S x S = ξ + ξ. 24 Equations 22 and 24 imply Then θ k can be bounded with θ k signx S ξ = ξ + ξ. θ k 31 + B W S ɛ, k maxk 1, K The above conclusion holds for all S 1. Moreover, as a threshold in η θ, θ k. Thus, θ k 31 + B W ɛ for any ɛ > as long as k large enough. In another word, θ k as k. Step 2 We prove that I W k 2 W k 1 A as k. LISTA model 4 and b = Ax gives x k+1 S =η θ k W2 k S, :x k + W1 k S, :b =η θ k W2 k S, :x k + W1 k S, :A:, Sx S W k 2 S, :x k + W k 1 S, :A:, Sx S θ k l 1 x k+1 S, where l 1 x is the sub-gradient of x 1. It is a set defined component-wisely: l 1 x i = { {signxi } if x i, [ 1, 1] if x i =. 26 The uniform convergence of x k implies, for any ɛ > and x, X B, s,, there exists a large enough constant K 3 > and ξ 1, ξ 2 R n such that x k = x + ξ 3, x k+1 = x + ξ 4 and ξ 3 2 ɛ, ξ 4 2 ɛ. Thus, x S + ξ 4 S W2 k S, Sx S + W2 k S, :ξ 3 + W1 k AS, Sx S θ k l 1 x k+1 I W2 k S, S W1 k AS, S x S W2 k S, :ξ 3 ξ 4 S θ k l 1 x k+1 By the definition 26 of l 1, every element in l 1 x, x R has a magnitude less than or equal to 1. Thus, for any ξ l 1 x k+1 S, we have ξ 2 S, which implies I W2 k S, S W1 k AS, S W2 k 2 ɛ + ɛ + θ k S. 2 x S S S 2
14 Combined with 25, we obtain the following inequality for all k maxk 1, K 2, K 3 : I W2 k S, S W1 k AS, S W2 k 2 ɛ + ɛ B W ɛ = 41 + B W ɛ. 2 x S The above inequality holds for all x, X B, s,, which implies, for all k maxk 1, K 2, K 3, { I W σ max I W2 k S, S W1 k k AS, S = sup 2 S, S W1 k AS, Sx S } 2 supportx =S B x i 2=B sup { I W k 2 S, S W1 k AS, Sx S } 2 B x, X B,s, 41 + B W ɛ. B Since s 2, I W2 k S, S W1 k AS, S uniformly for all S with 2 S s. Then, I W2 k W1 k A as k. B Proof of Theorem 2 Before proving Theorem 2, we introduce some definitions and a lemma. Definition 1. Mutual coherence µ of A R m n each column of A is normalized is defined as: µa = where A i refers to the i th column of matrix A. inf W R m n W i T A i=1,1 i n max i j A i A j, 27 1 i,j n Generalized mutual coherence µ of A R m n each column of A is normalized is defined as: { } µa = max i j W i A j i,j n The following lemma tells us the generalized mutual coherence is attached at some W R m n. Lemma 1. There exists a matrix W R m n that attaches the infimum given in 28: W i T A i = 1, 1 i n, max W i A j = µ i j 1 i,j n Proof. Optimization problem given in 28 is a linear programming because it minimizing a piecewise linear function with linear constraints. Since each column of A is normalized, there is at least one matrix in the feasible set: A {W R m n : W i T A i = 1, 1 i n}. In another word, optimization problem 28 is feasible. Moreover, by the definition of infimum bound 28, we have µa max A i A j = µa. i j 1 i,j n Thus, µ is bounded. According to Corollary 2.3 in [29], a feasible and bounded linear programming problem has an optimal solution. Based on Lemma 1, we define a set of good weights which W k s are chosen from: Definition 2. Given A R m n, a weight matrix is good if it belongs to { X W A = arg min W R m n max W i,j : W i T A i = 1, 1 i n, 1 i,j n Let C W = max 1 i,j n W i,j, if W X W A. max i j 1 i,j n } W i A j = µ. 29 3
15 With definitions 28 and 29, we propose a choice of parameters: W k X W A, θ k = sup { µ x k x, ε x 1 } + C W σ, 3 X B,s,σ which are uniform for all x, ε X B, s, σ. In the following proof line, we prove that 3 leads to the conclusion 14 in Theorem 2. Proof of Theorem 2 Proof. In this proof, we use the notation x k to replace x k x, ε for simplicity. Step 1: no false positives. Firstly, we take x, ε X B, s, σ. Let S = supportx. We want to prove by induction that, as long as 3 holds, x k i =, i / S, k no false positives. When k =, it is satisfied since x =. Fixing k, and assuming x k i =, i / S, we have =η θ k x k i i j SW k T Ax k b x k+1 i =η θ k i j SW k T A j x k j x j + Wi k T ε, i / S. Since θ k = µ sup x,ε{ x k x 1 } + C W σ and W k X W A, θ k µ x k x 1 + C W ε 1 i j SW k T A j x k j x j + Wi k T ε, i / S, which implies x k+1 i =, i / S by the definition of η θ k. By induction, we have x k i =, i / S, k. 31 In another word, threshold rule in 3 ensures no false positives 9 for all x k, k = 1, 2, Step 2: error bound for one x, ε. Next, let s consider the components on S. For all i S, = η θ k x k i Wi k T A S x k S x S + Wi k T ε x k+1 i x k i W k i T A S x k S x S + W k i T ε θ k l 1 x k+1 i, where l 1 x is defined in 26. Since Wi kt A i = 1, we have x k i Wi k T A S x k S x S =x k i Wi k T A j x k j x j x k i x i Then, x k+1 i x i j S,j i j S,j i =x i j S,j i W k i T A j x k j x j. Wi k T A j x k j x j + Wi k T ε θ k l 1 x k+1 i, i S. By the definition 26 of l 1, every element in l 1 x, x R has a magnitude less than or equal to 1. Thus, for all i S, x k+1 i x i Wi k T x k A j j x j + θ k + Wi k T ε µ j S,j i j S,j i x k j x j + θ k + C W ε 1 9 In practice, if we obtain θ k by training, but not 3, the learned θ k may not guarantee no false positives for all layers. However, the magnitudes on the false positives are actually small compared to those on true positives. Our proof sketch are qualitatively describing the learning-based ISTA. 4
16 Equation 31 implies x k x 1 = x k S x S 1 for all k. Then x k+1 x 1 = x k+1 i x i µ x k j x j + θ k + C W σ i S i S j S,j i = µ S 1 i S x k i x i + θ k S + S C W σ µ S 1 x k x 1 + θ k S + S C W σ Step 3: error bound for the whole data set. Finally, we take supremum over x, ε X B, x, σ, by S s, sup{ x k+1 x 1 } µs 1 sup{ x k x 1 } + sθ k + sc W σ. By θ k = sup { µ x k x 1 } + C W σ, we have sup{ x k+1 x 1 } 2 µs µ sup{ x k x 1 } + 2sC W σ. By induction, with c = log2 µs µ, C = 2sC W 1+ µ 2 µs, we obtain sup{ x k+1 x 1 } 2 µs µ k+1 sup{ x x 1 } + 2sC W σ 2 µs µ k sb + Cσ = sb exp ck + Cσ. k+1 Since x 2 x 1 for any x R n, we can get the upper bound for l 2 norm: 2 µs µ τ τ= sup{ x k+1 x 2 } sup{ x k+1 x 1 } sb exp ck + Cσ. As long as s < 1 + 1/ µ/2, c = log2 µs µ >, then the error bound 14 holds uniformly for all x, ε X B, s, σ. C Proof of Theorem 3 Proof. In this proof, we use the notation x k to replace x k x, ε for simplicity. Step 1: proving 17. Firstly, we assume Assumption 1 holds. Take x, ε X B, s, σ. Let S = supportx p. By the definition of selecting-support operator η k ss, using the same argument θ k with the proof of Theorem 2, we have LISTA-CPSS also satisfies x k i =, i / S, k no false positive with the same parameters as 3. For all i S, by the definition of η ss p k where ξ k i x k+1 i The set S pk is defined in 12. Let, there exists ξ k R n such that θ k p =η k ss x k θ k i Wi k T A S x k S x S + Wi k T ε =x k i W k i T A S x k S x S + W k i T ε θ k ξ k i, = if i / S [ 1, 1] if i S, x k+1 i = = signx k+1 i if i S, x k+1 i, i / S pk x k+1, = if i S, x k+1 i, i S pk x k+1. S k x, ε = {i i S, x k+1 i, i S pk x k+1 }, where S k depends on x and ε because x k+1 depends on x and ε. Then, using the same argument with that of LISTA-CP Theorem 2, we have x k+1 S x S 1 µ S 1 x k S x S 1 + θ k S S k x, ε + S C W ε 1. 5
17 Since x k i =, i / S, x k x 2 = x k S x S 2 for all k. Taking supremum over x, ε X B, s, σ, we have sup x k+1 x 1 µs 1 sup x k x 1 + θ k s inf Sk x, ε + sc W σ. By θ k = sup x,ε{ µ x k x 1 } + C W σ, we have Let Then, sup{ x k+1 x 1 } sup{ x k x 1 } k 1 sb k 1 2 µs µ µ inf Sk x, ε c k ss = log 2 µs µ µ inf Sk x, ε C ss =2sC W k= k exp c t ss. sup{ x k x 1 } + 2sC W σ. exp c t ss sup x,ε{ x x 1 } + 2sC W exp c t ss + + With x 2 x 1, we have exp c t ss + C ss σ B exp k 1 c t ss sup{ x k x 2 } sup{ x k x 1 } sb + C ss σ. k 1 k 1 exp c t ss + C ss σ. exp c t ss σ Since S k means the number of elements in S k, S k. Thus, c k ss c for all k. Consequently, C ss 2sC W exp ck = 2sC W 2 µs µ k 2sC W = 1 + µ 2 µs = C. k= Step 2: proving 18. Secondly, we assume Assumption 2 holds. Take x, ε X B, B, s, σ. The parameters are taken as W k X W A, θ k = sup { µ x k x, ε x 1 } + C W σ. X B,B,s,σ With the same argument as before, we get where k= sup { x k x 2 } sb exp X B,B,s,σ c k ss = log 2 µs µ µ C ss =2sC W k= inf X B,B,s,σ k exp c t ss C. k 1 c t ss + C ss σ, S k x, ε c Now we consider S k in a more precise way. The definition of S k implies S k x, ε = min p k, # of non-zero elements of x k By Assumption 2, it holds that x 1 B 2Cσ. Consequently, if k > 1/clogsB/Cσ, then sb exp ck + Cσ < 2Cσ x 1, 6
18 which implies k x k+1 x 1 sb exp c t ss + C ss σ sb exp ck + Cσ < x 1. Then # of non-zero elements of x k+1 1. Otherwise, x k+1 x 1 = x 1, which contradicts. Moreover, p k = minpk, s for some constant p >. Thus, as long as k 1/p, we have p k 1. By 32, we obtain 1 S k x, ε >, k > max p, 1 sb c log, x, ε Cσ X B, B, s, σ. Then, we have c k ss > c for large enough k, consequently, C ss < C. D The adaptive threshold rule used to produce Fig. 4 Algorithm 1: A thresholding rule for LASSO Similar to that in [23] Input :Maximum iteration K, initial λ, ɛ. Initialization :Let x =, λ 1 = λ, ɛ 1 = ɛ. 1 for k = 1, 2,, K do 2 Conduct ISTA: x k = η λk /L x k 1 1 L AT Ax k 1 b. 3 if x k x k 1 < ɛ k then 4 Let λ k+1.5λ k, ɛ k+1.5ɛ k. 5 else 6 Let λ k+1 λ k, ɛ k+1 ɛ k. 7 end 8 end Output: x K We take λ =.2, ɛ =.5 in our experiments. E Training Strategy In this section we have a detailed discussion on the stage-wise training strategy in empirical experiments. Denote Θ = {W1 k, W2 k, θ k } K 1 k= as all the weights in the network. Note that W 1 k, W2 k can be coupled as in 7. Denote Θ τ = {W1 k, W2 k, θ k } τ k= all the weights in the τ-th and all the previous layers. We assign a learning multiplier c, which is initialized as 1, to each weight in the network. Define an initial learning rate α and two decayed learning rates α 1, α 2. In real training, we have α 1 =.2α, α 2 =.2α. Our training strategy is described as below: Train the network layer by layer. Training in each layer consists of 3 stages. In layer τ, Θ τ 1 is pre-trained. Initialize cw τ 1, cw τ 2, cθ τ = 1. The actual learning rates of all weights in the following are multiplied by their learning multipliers. Train W τ 1, W τ 2, θ τ the initial learning rate α. Train Θ τ = Θ τ 1 W τ 1, W τ 2, θ τ with the learning rates α 1 and α 2. Multiply a decaying rate γ set to.3 in experiments to each weight in Θ τ. Proceed training to the next layer. The layer-wise training is widely adopted in previous LISTA-type networks. We add the learning rate decaying that is able to stabilize the training process. It will make the previous layers change very slowly when the training proceeds to deeper layers because learning rates of first several layers will exponentially decay and quickly go to near zero when the training process progresses to deeper layers, which can prevent them varying too far from pre-trained positions. It works well especially 7
19 when the unfolding goes deep to K > 1. All models trained and reported in experiments section are trained using the above strategy. Remark While adopting the above stage-wise training strategy, we first finish a complete training pass, calculate the intermediate results and final outputs, and then draw curves and evaluate the performance based on these results, instead of logging how the best performance changes when the training process goes deeper. This manner possibly accounts for the reason why some curves plotted in Section 4.1 display some unexpected fluctuations. 8
Distributed Inexact Newton-type Pursuit for Non-convex Sparse Learning
 Distributed Inexact Newton-type Pursuit for Non-convex Sparse Learning Bo Liu Department of Computer Science, Rutgers Univeristy Xiao-Tong Yuan BDAT Lab, Nanjing University of Information Science and Technology
Distributed Inexact Newton-type Pursuit for Non-convex Sparse Learning Bo Liu Department of Computer Science, Rutgers Univeristy Xiao-Tong Yuan BDAT Lab, Nanjing University of Information Science and Technology
arxiv: v1 [cs.it] 21 Feb 2013
![arxiv: v1 [cs.it] 21 Feb 2013 arxiv: v1 [cs.it] 21 Feb 2013](/thumbs/88/115041122.jpg) q-ary Compressive Sensing arxiv:30.568v [cs.it] Feb 03 Youssef Mroueh,, Lorenzo Rosasco, CBCL, CSAIL, Massachusetts Institute of Technology LCSL, Istituto Italiano di Tecnologia and IIT@MIT lab, Istituto
q-ary Compressive Sensing arxiv:30.568v [cs.it] Feb 03 Youssef Mroueh,, Lorenzo Rosasco, CBCL, CSAIL, Massachusetts Institute of Technology LCSL, Istituto Italiano di Tecnologia and IIT@MIT lab, Istituto
Phil Schniter. Supported in part by NSF grants IIP , CCF , and CCF
 AMP-inspired Deep Networks, with Comms Applications Phil Schniter Collaborators: Sundeep Rangan (NYU), Alyson Fletcher (UCLA), Mark Borgerding (OSU) Supported in part by NSF grants IIP-1539960, CCF-1527162,
AMP-inspired Deep Networks, with Comms Applications Phil Schniter Collaborators: Sundeep Rangan (NYU), Alyson Fletcher (UCLA), Mark Borgerding (OSU) Supported in part by NSF grants IIP-1539960, CCF-1527162,
TRADEOFFS BETWEEN SPEED AND ACCURACY IN INVERSE PROBLEMS RAJA GIRYES TEL AVIV UNIVERSITY
 TRADEOFFS BETWEEN SPEED AND ACCURACY IN INVERSE PROBLEMS RAJA GIRYES TEL AVIV UNIVERSITY Deep Learning TCE Conference June 14, 2018 DEEP LEARNING IMPACT Today we get 3.5% by 152 layers Imagenet dataset
TRADEOFFS BETWEEN SPEED AND ACCURACY IN INVERSE PROBLEMS RAJA GIRYES TEL AVIV UNIVERSITY Deep Learning TCE Conference June 14, 2018 DEEP LEARNING IMPACT Today we get 3.5% by 152 layers Imagenet dataset
Optimization for Compressed Sensing
 Optimization for Compressed Sensing Robert J. Vanderbei 2014 March 21 Dept. of Industrial & Systems Engineering University of Florida http://www.princeton.edu/ rvdb Lasso Regression The problem is to solve
Optimization for Compressed Sensing Robert J. Vanderbei 2014 March 21 Dept. of Industrial & Systems Engineering University of Florida http://www.princeton.edu/ rvdb Lasso Regression The problem is to solve
STAT 200C: High-dimensional Statistics
 STAT 200C: High-dimensional Statistics Arash A. Amini May 30, 2018 1 / 57 Table of Contents 1 Sparse linear models Basis Pursuit and restricted null space property Sufficient conditions for RNS 2 / 57
STAT 200C: High-dimensional Statistics Arash A. Amini May 30, 2018 1 / 57 Table of Contents 1 Sparse linear models Basis Pursuit and restricted null space property Sufficient conditions for RNS 2 / 57
Large-Scale L1-Related Minimization in Compressive Sensing and Beyond
 Large-Scale L1-Related Minimization in Compressive Sensing and Beyond Yin Zhang Department of Computational and Applied Mathematics Rice University, Houston, Texas, U.S.A. Arizona State University March
Large-Scale L1-Related Minimization in Compressive Sensing and Beyond Yin Zhang Department of Computational and Applied Mathematics Rice University, Houston, Texas, U.S.A. Arizona State University March
Optimization methods
 Lecture notes 3 February 8, 016 1 Introduction Optimization methods In these notes we provide an overview of a selection of optimization methods. We focus on methods which rely on first-order information,
Lecture notes 3 February 8, 016 1 Introduction Optimization methods In these notes we provide an overview of a selection of optimization methods. We focus on methods which rely on first-order information,
sparse and low-rank tensor recovery Cubic-Sketching
 Sparse and Low-Ran Tensor Recovery via Cubic-Setching Guang Cheng Department of Statistics Purdue University www.science.purdue.edu/bigdata CCAM@Purdue Math Oct. 27, 2017 Joint wor with Botao Hao and Anru
Sparse and Low-Ran Tensor Recovery via Cubic-Setching Guang Cheng Department of Statistics Purdue University www.science.purdue.edu/bigdata CCAM@Purdue Math Oct. 27, 2017 Joint wor with Botao Hao and Anru
Compressed Sensing and Sparse Recovery
 ELE 538B: Sparsity, Structure and Inference Compressed Sensing and Sparse Recovery Yuxin Chen Princeton University, Spring 217 Outline Restricted isometry property (RIP) A RIPless theory Compressed sensing
ELE 538B: Sparsity, Structure and Inference Compressed Sensing and Sparse Recovery Yuxin Chen Princeton University, Spring 217 Outline Restricted isometry property (RIP) A RIPless theory Compressed sensing
Compressibility of Infinite Sequences and its Interplay with Compressed Sensing Recovery
 Compressibility of Infinite Sequences and its Interplay with Compressed Sensing Recovery Jorge F. Silva and Eduardo Pavez Department of Electrical Engineering Information and Decision Systems Group Universidad
Compressibility of Infinite Sequences and its Interplay with Compressed Sensing Recovery Jorge F. Silva and Eduardo Pavez Department of Electrical Engineering Information and Decision Systems Group Universidad
Enhanced Compressive Sensing and More
 Enhanced Compressive Sensing and More Yin Zhang Department of Computational and Applied Mathematics Rice University, Houston, Texas, U.S.A. Nonlinear Approximation Techniques Using L1 Texas A & M University
Enhanced Compressive Sensing and More Yin Zhang Department of Computational and Applied Mathematics Rice University, Houston, Texas, U.S.A. Nonlinear Approximation Techniques Using L1 Texas A & M University
Bias-free Sparse Regression with Guaranteed Consistency
 Bias-free Sparse Regression with Guaranteed Consistency Wotao Yin (UCLA Math) joint with: Stanley Osher, Ming Yan (UCLA) Feng Ruan, Jiechao Xiong, Yuan Yao (Peking U) UC Riverside, STATS Department March
Bias-free Sparse Regression with Guaranteed Consistency Wotao Yin (UCLA Math) joint with: Stanley Osher, Ming Yan (UCLA) Feng Ruan, Jiechao Xiong, Yuan Yao (Peking U) UC Riverside, STATS Department March
Strengthened Sobolev inequalities for a random subspace of functions
 Strengthened Sobolev inequalities for a random subspace of functions Rachel Ward University of Texas at Austin April 2013 2 Discrete Sobolev inequalities Proposition (Sobolev inequality for discrete images)
Strengthened Sobolev inequalities for a random subspace of functions Rachel Ward University of Texas at Austin April 2013 2 Discrete Sobolev inequalities Proposition (Sobolev inequality for discrete images)
A Multilevel Proximal Algorithm for Large Scale Composite Convex Optimization
 A Multilevel Proximal Algorithm for Large Scale Composite Convex Optimization Panos Parpas Department of Computing Imperial College London www.doc.ic.ac.uk/ pp500 p.parpas@imperial.ac.uk jointly with D.V.
A Multilevel Proximal Algorithm for Large Scale Composite Convex Optimization Panos Parpas Department of Computing Imperial College London www.doc.ic.ac.uk/ pp500 p.parpas@imperial.ac.uk jointly with D.V.
Learning MMSE Optimal Thresholds for FISTA
 MITSUBISHI ELECTRIC RESEARCH LABORATORIES http://www.merl.com Learning MMSE Optimal Thresholds for FISTA Kamilov, U.; Mansour, H. TR2016-111 August 2016 Abstract Fast iterative shrinkage/thresholding algorithm
MITSUBISHI ELECTRIC RESEARCH LABORATORIES http://www.merl.com Learning MMSE Optimal Thresholds for FISTA Kamilov, U.; Mansour, H. TR2016-111 August 2016 Abstract Fast iterative shrinkage/thresholding algorithm
ALISTA: ANALYTIC WEIGHTS ARE AS GOOD AS LEARNED WEIGHTS IN LISTA
 ALITA: ANALYTIC WEIGHT ARE A GOOD A LEARNED WEIGHT IN LITA Anonymous authors Paper under double-blind review ABTRACT Deep neural networks based on unfolding an iterative algorithm, for example, LITA learned
ALITA: ANALYTIC WEIGHT ARE A GOOD A LEARNED WEIGHT IN LITA Anonymous authors Paper under double-blind review ABTRACT Deep neural networks based on unfolding an iterative algorithm, for example, LITA learned
Approximate Message Passing Algorithms
 November 4, 2017 Outline AMP (Donoho et al., 2009, 2010a) Motivations Derivations from a message-passing perspective Limitations Extensions Generalized Approximate Message Passing (GAMP) (Rangan, 2011)
November 4, 2017 Outline AMP (Donoho et al., 2009, 2010a) Motivations Derivations from a message-passing perspective Limitations Extensions Generalized Approximate Message Passing (GAMP) (Rangan, 2011)
Lecture: Introduction to Compressed Sensing Sparse Recovery Guarantees
 Lecture: Introduction to Compressed Sensing Sparse Recovery Guarantees http://bicmr.pku.edu.cn/~wenzw/bigdata2018.html Acknowledgement: this slides is based on Prof. Emmanuel Candes and Prof. Wotao Yin
Lecture: Introduction to Compressed Sensing Sparse Recovery Guarantees http://bicmr.pku.edu.cn/~wenzw/bigdata2018.html Acknowledgement: this slides is based on Prof. Emmanuel Candes and Prof. Wotao Yin
Reconstruction from Anisotropic Random Measurements
 Reconstruction from Anisotropic Random Measurements Mark Rudelson and Shuheng Zhou The University of Michigan, Ann Arbor Coding, Complexity, and Sparsity Workshop, 013 Ann Arbor, Michigan August 7, 013
Reconstruction from Anisotropic Random Measurements Mark Rudelson and Shuheng Zhou The University of Michigan, Ann Arbor Coding, Complexity, and Sparsity Workshop, 013 Ann Arbor, Michigan August 7, 013
Fast Nonnegative Matrix Factorization with Rank-one ADMM
 Fast Nonnegative Matrix Factorization with Rank-one Dongjin Song, David A. Meyer, Martin Renqiang Min, Department of ECE, UCSD, La Jolla, CA, 9093-0409 dosong@ucsd.edu Department of Mathematics, UCSD,
Fast Nonnegative Matrix Factorization with Rank-one Dongjin Song, David A. Meyer, Martin Renqiang Min, Department of ECE, UCSD, La Jolla, CA, 9093-0409 dosong@ucsd.edu Department of Mathematics, UCSD,
SPARSE signal representations have gained popularity in recent
 6958 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 10, OCTOBER 2011 Blind Compressed Sensing Sivan Gleichman and Yonina C. Eldar, Senior Member, IEEE Abstract The fundamental principle underlying
6958 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 10, OCTOBER 2011 Blind Compressed Sensing Sivan Gleichman and Yonina C. Eldar, Senior Member, IEEE Abstract The fundamental principle underlying
Data Sparse Matrix Computation - Lecture 20
 Data Sparse Matrix Computation - Lecture 20 Yao Cheng, Dongping Qi, Tianyi Shi November 9, 207 Contents Introduction 2 Theorems on Sparsity 2. Example: A = [Φ Ψ]......................... 2.2 General Matrix
Data Sparse Matrix Computation - Lecture 20 Yao Cheng, Dongping Qi, Tianyi Shi November 9, 207 Contents Introduction 2 Theorems on Sparsity 2. Example: A = [Φ Ψ]......................... 2.2 General Matrix
Minimizing the Difference of L 1 and L 2 Norms with Applications
 1/36 Minimizing the Difference of L 1 and L 2 Norms with Department of Mathematical Sciences University of Texas Dallas May 31, 2017 Partially supported by NSF DMS 1522786 2/36 Outline 1 A nonconvex approach:
1/36 Minimizing the Difference of L 1 and L 2 Norms with Department of Mathematical Sciences University of Texas Dallas May 31, 2017 Partially supported by NSF DMS 1522786 2/36 Outline 1 A nonconvex approach:
On the Sub-Optimality of Proximal Gradient Descent for l 0 Sparse Approximation
 On the Sub-Optimality of Proximal Gradient Descent for l 0 Sparse Approximation Yingzhen Yang YYANG58@ILLINOIS.EDU Jianchao Yang JIANCHAO.YANG@SNAPCHAT.COM Snapchat, Venice, CA 90291 Wei Han WEIHAN3@ILLINOIS.EDU
On the Sub-Optimality of Proximal Gradient Descent for l 0 Sparse Approximation Yingzhen Yang YYANG58@ILLINOIS.EDU Jianchao Yang JIANCHAO.YANG@SNAPCHAT.COM Snapchat, Venice, CA 90291 Wei Han WEIHAN3@ILLINOIS.EDU
Does l p -minimization outperform l 1 -minimization?
 Does l p -minimization outperform l -minimization? Le Zheng, Arian Maleki, Haolei Weng, Xiaodong Wang 3, Teng Long Abstract arxiv:50.03704v [cs.it] 0 Jun 06 In many application areas ranging from bioinformatics
Does l p -minimization outperform l -minimization? Le Zheng, Arian Maleki, Haolei Weng, Xiaodong Wang 3, Teng Long Abstract arxiv:50.03704v [cs.it] 0 Jun 06 In many application areas ranging from bioinformatics
Machine Learning and Computational Statistics, Spring 2017 Homework 2: Lasso Regression
 Machine Learning and Computational Statistics, Spring 2017 Homework 2: Lasso Regression Due: Monday, February 13, 2017, at 10pm (Submit via Gradescope) Instructions: Your answers to the questions below,
Machine Learning and Computational Statistics, Spring 2017 Homework 2: Lasso Regression Due: Monday, February 13, 2017, at 10pm (Submit via Gradescope) Instructions: Your answers to the questions below,
SVRG++ with Non-uniform Sampling
 SVRG++ with Non-uniform Sampling Tamás Kern András György Department of Electrical and Electronic Engineering Imperial College London, London, UK, SW7 2BT {tamas.kern15,a.gyorgy}@imperial.ac.uk Abstract
SVRG++ with Non-uniform Sampling Tamás Kern András György Department of Electrical and Electronic Engineering Imperial College London, London, UK, SW7 2BT {tamas.kern15,a.gyorgy}@imperial.ac.uk Abstract
New Coherence and RIP Analysis for Weak. Orthogonal Matching Pursuit
 New Coherence and RIP Analysis for Wea 1 Orthogonal Matching Pursuit Mingrui Yang, Member, IEEE, and Fran de Hoog arxiv:1405.3354v1 [cs.it] 14 May 2014 Abstract In this paper we define a new coherence
New Coherence and RIP Analysis for Wea 1 Orthogonal Matching Pursuit Mingrui Yang, Member, IEEE, and Fran de Hoog arxiv:1405.3354v1 [cs.it] 14 May 2014 Abstract In this paper we define a new coherence
2.3. Clustering or vector quantization 57
 Multivariate Statistics non-negative matrix factorisation and sparse dictionary learning The PCA decomposition is by construction optimal solution to argmin A R n q,h R q p X AH 2 2 under constraint :
Multivariate Statistics non-negative matrix factorisation and sparse dictionary learning The PCA decomposition is by construction optimal solution to argmin A R n q,h R q p X AH 2 2 under constraint :
Comparison of Modern Stochastic Optimization Algorithms
 Comparison of Modern Stochastic Optimization Algorithms George Papamakarios December 214 Abstract Gradient-based optimization methods are popular in machine learning applications. In large-scale problems,
Comparison of Modern Stochastic Optimization Algorithms George Papamakarios December 214 Abstract Gradient-based optimization methods are popular in machine learning applications. In large-scale problems,
DNNs for Sparse Coding and Dictionary Learning
 DNNs for Sparse Coding and Dictionary Learning Subhadip Mukherjee, Debabrata Mahapatra, and Chandra Sekhar Seelamantula Department of Electrical Engineering, Indian Institute of Science, Bangalore 5612,
DNNs for Sparse Coding and Dictionary Learning Subhadip Mukherjee, Debabrata Mahapatra, and Chandra Sekhar Seelamantula Department of Electrical Engineering, Indian Institute of Science, Bangalore 5612,
A New Combined Approach for Inference in High-Dimensional Regression Models with Correlated Variables
 A New Combined Approach for Inference in High-Dimensional Regression Models with Correlated Variables Niharika Gauraha and Swapan Parui Indian Statistical Institute Abstract. We consider the problem of
A New Combined Approach for Inference in High-Dimensional Regression Models with Correlated Variables Niharika Gauraha and Swapan Parui Indian Statistical Institute Abstract. We consider the problem of
OWL to the rescue of LASSO
 OWL to the rescue of LASSO IISc IBM day 2018 Joint Work R. Sankaran and Francis Bach AISTATS 17 Chiranjib Bhattacharyya Professor, Department of Computer Science and Automation Indian Institute of Science,
OWL to the rescue of LASSO IISc IBM day 2018 Joint Work R. Sankaran and Francis Bach AISTATS 17 Chiranjib Bhattacharyya Professor, Department of Computer Science and Automation Indian Institute of Science,
Master 2 MathBigData. 3 novembre CMAP - Ecole Polytechnique
 Master 2 MathBigData S. Gaïffas 1 3 novembre 2014 1 CMAP - Ecole Polytechnique 1 Supervised learning recap Introduction Loss functions, linearity 2 Penalization Introduction Ridge Sparsity Lasso 3 Some
Master 2 MathBigData S. Gaïffas 1 3 novembre 2014 1 CMAP - Ecole Polytechnique 1 Supervised learning recap Introduction Loss functions, linearity 2 Penalization Introduction Ridge Sparsity Lasso 3 Some
Analysis of Greedy Algorithms
 Analysis of Greedy Algorithms Jiahui Shen Florida State University Oct.26th Outline Introduction Regularity condition Analysis on orthogonal matching pursuit Analysis on forward-backward greedy algorithm
Analysis of Greedy Algorithms Jiahui Shen Florida State University Oct.26th Outline Introduction Regularity condition Analysis on orthogonal matching pursuit Analysis on forward-backward greedy algorithm
ECE G: Special Topics in Signal Processing: Sparsity, Structure, and Inference
 ECE 18-898G: Special Topics in Signal Processing: Sparsity, Structure, and Inference Sparse Recovery using L1 minimization - algorithms Yuejie Chi Department of Electrical and Computer Engineering Spring
ECE 18-898G: Special Topics in Signal Processing: Sparsity, Structure, and Inference Sparse Recovery using L1 minimization - algorithms Yuejie Chi Department of Electrical and Computer Engineering Spring
Self-Calibration and Biconvex Compressive Sensing
 Self-Calibration and Biconvex Compressive Sensing Shuyang Ling Department of Mathematics, UC Davis July 12, 2017 Shuyang Ling (UC Davis) SIAM Annual Meeting, 2017, Pittsburgh July 12, 2017 1 / 22 Acknowledgements
Self-Calibration and Biconvex Compressive Sensing Shuyang Ling Department of Mathematics, UC Davis July 12, 2017 Shuyang Ling (UC Davis) SIAM Annual Meeting, 2017, Pittsburgh July 12, 2017 1 / 22 Acknowledgements
(Part 1) High-dimensional statistics May / 41
 Theory for the Lasso Recall the linear model Y i = p j=1 β j X (j) i + ɛ i, i = 1,..., n, or, in matrix notation, Y = Xβ + ɛ, To simplify, we assume that the design X is fixed, and that ɛ is N (0, σ 2
Theory for the Lasso Recall the linear model Y i = p j=1 β j X (j) i + ɛ i, i = 1,..., n, or, in matrix notation, Y = Xβ + ɛ, To simplify, we assume that the design X is fixed, and that ɛ is N (0, σ 2
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 11, NOVEMBER On the Performance of Sparse Recovery
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 11, NOVEMBER 2011 7255 On the Performance of Sparse Recovery Via `p-minimization (0 p 1) Meng Wang, Student Member, IEEE, Weiyu Xu, and Ao Tang, Senior
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 11, NOVEMBER 2011 7255 On the Performance of Sparse Recovery Via `p-minimization (0 p 1) Meng Wang, Student Member, IEEE, Weiyu Xu, and Ao Tang, Senior
Sparse regression. Optimization-Based Data Analysis. Carlos Fernandez-Granda
 Sparse regression Optimization-Based Data Analysis http://www.cims.nyu.edu/~cfgranda/pages/obda_spring16 Carlos Fernandez-Granda 3/28/2016 Regression Least-squares regression Example: Global warming Logistic
Sparse regression Optimization-Based Data Analysis http://www.cims.nyu.edu/~cfgranda/pages/obda_spring16 Carlos Fernandez-Granda 3/28/2016 Regression Least-squares regression Example: Global warming Logistic
Sparse Algorithms are not Stable: A No-free-lunch Theorem
 Sparse Algorithms are not Stable: A No-free-lunch Theorem Huan Xu Shie Mannor Constantine Caramanis Abstract We consider two widely used notions in machine learning, namely: sparsity algorithmic stability.
Sparse Algorithms are not Stable: A No-free-lunch Theorem Huan Xu Shie Mannor Constantine Caramanis Abstract We consider two widely used notions in machine learning, namely: sparsity algorithmic stability.
A tutorial on sparse modeling. Outline:
 A tutorial on sparse modeling. Outline: 1. Why? 2. What? 3. How. 4. no really, why? Sparse modeling is a component in many state of the art signal processing and machine learning tasks. image processing
A tutorial on sparse modeling. Outline: 1. Why? 2. What? 3. How. 4. no really, why? Sparse modeling is a component in many state of the art signal processing and machine learning tasks. image processing
Introduction to Compressed Sensing
 Introduction to Compressed Sensing Alejandro Parada, Gonzalo Arce University of Delaware August 25, 2016 Motivation: Classical Sampling 1 Motivation: Classical Sampling Issues Some applications Radar Spectral
Introduction to Compressed Sensing Alejandro Parada, Gonzalo Arce University of Delaware August 25, 2016 Motivation: Classical Sampling 1 Motivation: Classical Sampling Issues Some applications Radar Spectral
Learning Bound for Parameter Transfer Learning
 Learning Bound for Parameter Transfer Learning Wataru Kumagai Faculty of Engineering Kanagawa University kumagai@kanagawa-u.ac.jp Abstract We consider a transfer-learning problem by using the parameter
Learning Bound for Parameter Transfer Learning Wataru Kumagai Faculty of Engineering Kanagawa University kumagai@kanagawa-u.ac.jp Abstract We consider a transfer-learning problem by using the parameter
CSC 576: Variants of Sparse Learning
 CSC 576: Variants of Sparse Learning Ji Liu Department of Computer Science, University of Rochester October 27, 205 Introduction Our previous note basically suggests using l norm to enforce sparsity in
CSC 576: Variants of Sparse Learning Ji Liu Department of Computer Science, University of Rochester October 27, 205 Introduction Our previous note basically suggests using l norm to enforce sparsity in
Orthogonal Matching Pursuit for Sparse Signal Recovery With Noise
 Orthogonal Matching Pursuit for Sparse Signal Recovery With Noise The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation As Published
Orthogonal Matching Pursuit for Sparse Signal Recovery With Noise The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation As Published
Optimization methods
 Optimization methods Optimization-Based Data Analysis http://www.cims.nyu.edu/~cfgranda/pages/obda_spring16 Carlos Fernandez-Granda /8/016 Introduction Aim: Overview of optimization methods that Tend to
Optimization methods Optimization-Based Data Analysis http://www.cims.nyu.edu/~cfgranda/pages/obda_spring16 Carlos Fernandez-Granda /8/016 Introduction Aim: Overview of optimization methods that Tend to
Adaptive Corrected Procedure for TVL1 Image Deblurring under Impulsive Noise
 Adaptive Corrected Procedure for TVL1 Image Deblurring under Impulsive Noise Minru Bai(x T) College of Mathematics and Econometrics Hunan University Joint work with Xiongjun Zhang, Qianqian Shao June 30,
Adaptive Corrected Procedure for TVL1 Image Deblurring under Impulsive Noise Minru Bai(x T) College of Mathematics and Econometrics Hunan University Joint work with Xiongjun Zhang, Qianqian Shao June 30,
Differentiable Fine-grained Quantization for Deep Neural Network Compression
 Differentiable Fine-grained Quantization for Deep Neural Network Compression Hsin-Pai Cheng hc218@duke.edu Yuanjun Huang University of Science and Technology of China Anhui, China yjhuang@mail.ustc.edu.cn
Differentiable Fine-grained Quantization for Deep Neural Network Compression Hsin-Pai Cheng hc218@duke.edu Yuanjun Huang University of Science and Technology of China Anhui, China yjhuang@mail.ustc.edu.cn
ACCORDING to Shannon s sampling theorem, an analog
 554 IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL 59, NO 2, FEBRUARY 2011 Segmented Compressed Sampling for Analog-to-Information Conversion: Method and Performance Analysis Omid Taheri, Student Member,
554 IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL 59, NO 2, FEBRUARY 2011 Segmented Compressed Sampling for Analog-to-Information Conversion: Method and Performance Analysis Omid Taheri, Student Member,
Truncation Strategy of Tensor Compressive Sensing for Noisy Video Sequences
 Journal of Information Hiding and Multimedia Signal Processing c 2016 ISSN 207-4212 Ubiquitous International Volume 7, Number 5, September 2016 Truncation Strategy of Tensor Compressive Sensing for Noisy
Journal of Information Hiding and Multimedia Signal Processing c 2016 ISSN 207-4212 Ubiquitous International Volume 7, Number 5, September 2016 Truncation Strategy of Tensor Compressive Sensing for Noisy
Rigorous Dynamics and Consistent Estimation in Arbitrarily Conditioned Linear Systems
 1 Rigorous Dynamics and Consistent Estimation in Arbitrarily Conditioned Linear Systems Alyson K. Fletcher, Mojtaba Sahraee-Ardakan, Philip Schniter, and Sundeep Rangan Abstract arxiv:1706.06054v1 cs.it
1 Rigorous Dynamics and Consistent Estimation in Arbitrarily Conditioned Linear Systems Alyson K. Fletcher, Mojtaba Sahraee-Ardakan, Philip Schniter, and Sundeep Rangan Abstract arxiv:1706.06054v1 cs.it
GROUP-SPARSE SUBSPACE CLUSTERING WITH MISSING DATA
 GROUP-SPARSE SUBSPACE CLUSTERING WITH MISSING DATA D Pimentel-Alarcón 1, L Balzano 2, R Marcia 3, R Nowak 1, R Willett 1 1 University of Wisconsin - Madison, 2 University of Michigan - Ann Arbor, 3 University
GROUP-SPARSE SUBSPACE CLUSTERING WITH MISSING DATA D Pimentel-Alarcón 1, L Balzano 2, R Marcia 3, R Nowak 1, R Willett 1 1 University of Wisconsin - Madison, 2 University of Michigan - Ann Arbor, 3 University
INDUSTRIAL MATHEMATICS INSTITUTE. B.S. Kashin and V.N. Temlyakov. IMI Preprint Series. Department of Mathematics University of South Carolina
 INDUSTRIAL MATHEMATICS INSTITUTE 2007:08 A remark on compressed sensing B.S. Kashin and V.N. Temlyakov IMI Preprint Series Department of Mathematics University of South Carolina A remark on compressed
INDUSTRIAL MATHEMATICS INSTITUTE 2007:08 A remark on compressed sensing B.S. Kashin and V.N. Temlyakov IMI Preprint Series Department of Mathematics University of South Carolina A remark on compressed
Sparsity Regularization
 Sparsity Regularization Bangti Jin Course Inverse Problems & Imaging 1 / 41 Outline 1 Motivation: sparsity? 2 Mathematical preliminaries 3 l 1 solvers 2 / 41 problem setup finite-dimensional formulation
Sparsity Regularization Bangti Jin Course Inverse Problems & Imaging 1 / 41 Outline 1 Motivation: sparsity? 2 Mathematical preliminaries 3 l 1 solvers 2 / 41 problem setup finite-dimensional formulation
Adaptive Primal Dual Optimization for Image Processing and Learning
 Adaptive Primal Dual Optimization for Image Processing and Learning Tom Goldstein Rice University tag7@rice.edu Ernie Esser University of British Columbia eesser@eos.ubc.ca Richard Baraniuk Rice University
Adaptive Primal Dual Optimization for Image Processing and Learning Tom Goldstein Rice University tag7@rice.edu Ernie Esser University of British Columbia eesser@eos.ubc.ca Richard Baraniuk Rice University
SPARSE SIGNAL RESTORATION. 1. Introduction
 SPARSE SIGNAL RESTORATION IVAN W. SELESNICK 1. Introduction These notes describe an approach for the restoration of degraded signals using sparsity. This approach, which has become quite popular, is useful
SPARSE SIGNAL RESTORATION IVAN W. SELESNICK 1. Introduction These notes describe an approach for the restoration of degraded signals using sparsity. This approach, which has become quite popular, is useful
Big Data Analytics: Optimization and Randomization
 Big Data Analytics: Optimization and Randomization Tianbao Yang Tutorial@ACML 2015 Hong Kong Department of Computer Science, The University of Iowa, IA, USA Nov. 20, 2015 Yang Tutorial for ACML 15 Nov.
Big Data Analytics: Optimization and Randomization Tianbao Yang Tutorial@ACML 2015 Hong Kong Department of Computer Science, The University of Iowa, IA, USA Nov. 20, 2015 Yang Tutorial for ACML 15 Nov.
Linear Convergence of Adaptively Iterative Thresholding Algorithms for Compressed Sensing
 Linear Convergence of Adaptively Iterative Thresholding Algorithms for Compressed Sensing Yu Wang, Jinshan Zeng, Zhimin Peng, Xiangyu Chang, and Zongben Xu arxiv:48.689v3 [math.oc] 6 Dec 5 Abstract This
Linear Convergence of Adaptively Iterative Thresholding Algorithms for Compressed Sensing Yu Wang, Jinshan Zeng, Zhimin Peng, Xiangyu Chang, and Zongben Xu arxiv:48.689v3 [math.oc] 6 Dec 5 Abstract This
Deep Feedforward Networks
 Deep Feedforward Networks Liu Yang March 30, 2017 Liu Yang Short title March 30, 2017 1 / 24 Overview 1 Background A general introduction Example 2 Gradient based learning Cost functions Output Units 3
Deep Feedforward Networks Liu Yang March 30, 2017 Liu Yang Short title March 30, 2017 1 / 24 Overview 1 Background A general introduction Example 2 Gradient based learning Cost functions Output Units 3
Sparse Optimization Lecture: Sparse Recovery Guarantees
 Those who complete this lecture will know Sparse Optimization Lecture: Sparse Recovery Guarantees Sparse Optimization Lecture: Sparse Recovery Guarantees Instructor: Wotao Yin Department of Mathematics,
Those who complete this lecture will know Sparse Optimization Lecture: Sparse Recovery Guarantees Sparse Optimization Lecture: Sparse Recovery Guarantees Instructor: Wotao Yin Department of Mathematics,
Compressed sensing. Or: the equation Ax = b, revisited. Terence Tao. Mahler Lecture Series. University of California, Los Angeles
 Or: the equation Ax = b, revisited University of California, Los Angeles Mahler Lecture Series Acquiring signals Many types of real-world signals (e.g. sound, images, video) can be viewed as an n-dimensional
Or: the equation Ax = b, revisited University of California, Los Angeles Mahler Lecture Series Acquiring signals Many types of real-world signals (e.g. sound, images, video) can be viewed as an n-dimensional
Nonlinear Optimization Methods for Machine Learning
 Nonlinear Optimization Methods for Machine Learning Jorge Nocedal Northwestern University University of California, Davis, Sept 2018 1 Introduction We don t really know, do we? a) Deep neural networks
Nonlinear Optimization Methods for Machine Learning Jorge Nocedal Northwestern University University of California, Davis, Sept 2018 1 Introduction We don t really know, do we? a) Deep neural networks
Stability and Robustness of Weak Orthogonal Matching Pursuits
 Stability and Robustness of Weak Orthogonal Matching Pursuits Simon Foucart, Drexel University Abstract A recent result establishing, under restricted isometry conditions, the success of sparse recovery
Stability and Robustness of Weak Orthogonal Matching Pursuits Simon Foucart, Drexel University Abstract A recent result establishing, under restricted isometry conditions, the success of sparse recovery
The Deep Ritz method: A deep learning-based numerical algorithm for solving variational problems
 The Deep Ritz method: A deep learning-based numerical algorithm for solving variational problems Weinan E 1 and Bing Yu 2 arxiv:1710.00211v1 [cs.lg] 30 Sep 2017 1 The Beijing Institute of Big Data Research,
The Deep Ritz method: A deep learning-based numerical algorithm for solving variational problems Weinan E 1 and Bing Yu 2 arxiv:1710.00211v1 [cs.lg] 30 Sep 2017 1 The Beijing Institute of Big Data Research,
A Bregman alternating direction method of multipliers for sparse probabilistic Boolean network problem
 A Bregman alternating direction method of multipliers for sparse probabilistic Boolean network problem Kangkang Deng, Zheng Peng Abstract: The main task of genetic regulatory networks is to construct a
A Bregman alternating direction method of multipliers for sparse probabilistic Boolean network problem Kangkang Deng, Zheng Peng Abstract: The main task of genetic regulatory networks is to construct a
Rapid, Robust, and Reliable Blind Deconvolution via Nonconvex Optimization
 Rapid, Robust, and Reliable Blind Deconvolution via Nonconvex Optimization Shuyang Ling Department of Mathematics, UC Davis Oct.18th, 2016 Shuyang Ling (UC Davis) 16w5136, Oaxaca, Mexico Oct.18th, 2016
Rapid, Robust, and Reliable Blind Deconvolution via Nonconvex Optimization Shuyang Ling Department of Mathematics, UC Davis Oct.18th, 2016 Shuyang Ling (UC Davis) 16w5136, Oaxaca, Mexico Oct.18th, 2016
Noisy Signal Recovery via Iterative Reweighted L1-Minimization
 Noisy Signal Recovery via Iterative Reweighted L1-Minimization Deanna Needell UC Davis / Stanford University Asilomar SSC, November 2009 Problem Background Setup 1 Suppose x is an unknown signal in R d.
Noisy Signal Recovery via Iterative Reweighted L1-Minimization Deanna Needell UC Davis / Stanford University Asilomar SSC, November 2009 Problem Background Setup 1 Suppose x is an unknown signal in R d.
Compressive Sensing under Matrix Uncertainties: An Approximate Message Passing Approach
 Compressive Sensing under Matrix Uncertainties: An Approximate Message Passing Approach Asilomar 2011 Jason T. Parker (AFRL/RYAP) Philip Schniter (OSU) Volkan Cevher (EPFL) Problem Statement Traditional
Compressive Sensing under Matrix Uncertainties: An Approximate Message Passing Approach Asilomar 2011 Jason T. Parker (AFRL/RYAP) Philip Schniter (OSU) Volkan Cevher (EPFL) Problem Statement Traditional
1 Lyapunov theory of stability
 M.Kawski, APM 581 Diff Equns Intro to Lyapunov theory. November 15, 29 1 1 Lyapunov theory of stability Introduction. Lyapunov s second (or direct) method provides tools for studying (asymptotic) stability
M.Kawski, APM 581 Diff Equns Intro to Lyapunov theory. November 15, 29 1 1 Lyapunov theory of stability Introduction. Lyapunov s second (or direct) method provides tools for studying (asymptotic) stability
A Multi-task Learning Strategy for Unsupervised Clustering via Explicitly Separating the Commonality
 A Multi-task Learning Strategy for Unsupervised Clustering via Explicitly Separating the Commonality Shu Kong, Donghui Wang Dept. of Computer Science and Technology, Zhejiang University, Hangzhou 317,
A Multi-task Learning Strategy for Unsupervised Clustering via Explicitly Separating the Commonality Shu Kong, Donghui Wang Dept. of Computer Science and Technology, Zhejiang University, Hangzhou 317,
Accelerated Dual Gradient-Based Methods for Total Variation Image Denoising/Deblurring Problems (and other Inverse Problems)
 Accelerated Dual Gradient-Based Methods for Total Variation Image Denoising/Deblurring Problems (and other Inverse Problems) Donghwan Kim and Jeffrey A. Fessler EECS Department, University of Michigan
Accelerated Dual Gradient-Based Methods for Total Variation Image Denoising/Deblurring Problems (and other Inverse Problems) Donghwan Kim and Jeffrey A. Fessler EECS Department, University of Michigan
Stochastic Optimization with Inequality Constraints Using Simultaneous Perturbations and Penalty Functions
 International Journal of Control Vol. 00, No. 00, January 2007, 1 10 Stochastic Optimization with Inequality Constraints Using Simultaneous Perturbations and Penalty Functions I-JENG WANG and JAMES C.
International Journal of Control Vol. 00, No. 00, January 2007, 1 10 Stochastic Optimization with Inequality Constraints Using Simultaneous Perturbations and Penalty Functions I-JENG WANG and JAMES C.
Solving Corrupted Quadratic Equations, Provably
 Solving Corrupted Quadratic Equations, Provably Yuejie Chi London Workshop on Sparse Signal Processing September 206 Acknowledgement Joint work with Yuanxin Li (OSU), Huishuai Zhuang (Syracuse) and Yingbin
Solving Corrupted Quadratic Equations, Provably Yuejie Chi London Workshop on Sparse Signal Processing September 206 Acknowledgement Joint work with Yuanxin Li (OSU), Huishuai Zhuang (Syracuse) and Yingbin
Constructing Explicit RIP Matrices and the Square-Root Bottleneck
 Constructing Explicit RIP Matrices and the Square-Root Bottleneck Ryan Cinoman July 18, 2018 Ryan Cinoman Constructing Explicit RIP Matrices July 18, 2018 1 / 36 Outline 1 Introduction 2 Restricted Isometry
Constructing Explicit RIP Matrices and the Square-Root Bottleneck Ryan Cinoman July 18, 2018 Ryan Cinoman Constructing Explicit RIP Matrices July 18, 2018 1 / 36 Outline 1 Introduction 2 Restricted Isometry
Overview of gradient descent optimization algorithms. HYUNG IL KOO Based on
 Overview of gradient descent optimization algorithms HYUNG IL KOO Based on http://sebastianruder.com/optimizing-gradient-descent/ Problem Statement Machine Learning Optimization Problem Training samples:
Overview of gradient descent optimization algorithms HYUNG IL KOO Based on http://sebastianruder.com/optimizing-gradient-descent/ Problem Statement Machine Learning Optimization Problem Training samples:
Lecture Notes 9: Constrained Optimization
 Optimization-based data analysis Fall 017 Lecture Notes 9: Constrained Optimization 1 Compressed sensing 1.1 Underdetermined linear inverse problems Linear inverse problems model measurements of the form
Optimization-based data analysis Fall 017 Lecture Notes 9: Constrained Optimization 1 Compressed sensing 1.1 Underdetermined linear inverse problems Linear inverse problems model measurements of the form
Homotopy methods based on l 0 norm for the compressed sensing problem
 Homotopy methods based on l 0 norm for the compressed sensing problem Wenxing Zhu, Zhengshan Dong Center for Discrete Mathematics and Theoretical Computer Science, Fuzhou University, Fuzhou 350108, China
Homotopy methods based on l 0 norm for the compressed sensing problem Wenxing Zhu, Zhengshan Dong Center for Discrete Mathematics and Theoretical Computer Science, Fuzhou University, Fuzhou 350108, China
Stochastic Optimization Methods for Machine Learning. Jorge Nocedal
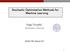 Stochastic Optimization Methods for Machine Learning Jorge Nocedal Northwestern University SIAM CSE, March 2017 1 Collaborators Richard Byrd R. Bollagragada N. Keskar University of Colorado Northwestern
Stochastic Optimization Methods for Machine Learning Jorge Nocedal Northwestern University SIAM CSE, March 2017 1 Collaborators Richard Byrd R. Bollagragada N. Keskar University of Colorado Northwestern
Parallel and Distributed Stochastic Learning -Towards Scalable Learning for Big Data Intelligence
 Parallel and Distributed Stochastic Learning -Towards Scalable Learning for Big Data Intelligence oé LAMDA Group H ŒÆOŽÅ Æ EâX ^ #EâI[ : liwujun@nju.edu.cn Dec 10, 2016 Wu-Jun Li (http://cs.nju.edu.cn/lwj)
Parallel and Distributed Stochastic Learning -Towards Scalable Learning for Big Data Intelligence oé LAMDA Group H ŒÆOŽÅ Æ EâX ^ #EâI[ : liwujun@nju.edu.cn Dec 10, 2016 Wu-Jun Li (http://cs.nju.edu.cn/lwj)
arxiv: v1 [cs.it] 26 Oct 2018
![arxiv: v1 [cs.it] 26 Oct 2018 arxiv: v1 [cs.it] 26 Oct 2018](/thumbs/89/99964659.jpg) Outlier Detection using Generative Models with Theoretical Performance Guarantees arxiv:1810.11335v1 [cs.it] 6 Oct 018 Jirong Yi Anh Duc Le Tianming Wang Xiaodong Wu Weiyu Xu October 9, 018 Abstract This
Outlier Detection using Generative Models with Theoretical Performance Guarantees arxiv:1810.11335v1 [cs.it] 6 Oct 018 Jirong Yi Anh Duc Le Tianming Wang Xiaodong Wu Weiyu Xu October 9, 018 Abstract This
Vector Approximate Message Passing. Phil Schniter
 Vector Approximate Message Passing Phil Schniter Collaborators: Sundeep Rangan (NYU), Alyson Fletcher (UCLA) Supported in part by NSF grant CCF-1527162. itwist @ Aalborg University Aug 24, 2016 Standard
Vector Approximate Message Passing Phil Schniter Collaborators: Sundeep Rangan (NYU), Alyson Fletcher (UCLA) Supported in part by NSF grant CCF-1527162. itwist @ Aalborg University Aug 24, 2016 Standard
arxiv: v1 [stat.ml] 22 Nov 2016
![arxiv: v1 [stat.ml] 22 Nov 2016 arxiv: v1 [stat.ml] 22 Nov 2016](/thumbs/74/70563816.jpg) Interpretable Recurrent Neural Networks Using Sequential Sparse Recovery arxiv:1611.07252v1 [stat.ml] 22 Nov 2016 Scott Wisdom 1, Thomas Powers 1, James Pitton 1,2, and Les Atlas 1 1 Department of Electrical
Interpretable Recurrent Neural Networks Using Sequential Sparse Recovery arxiv:1611.07252v1 [stat.ml] 22 Nov 2016 Scott Wisdom 1, Thomas Powers 1, James Pitton 1,2, and Les Atlas 1 1 Department of Electrical
TTIC 31230, Fundamentals of Deep Learning David McAllester, Winter Generalization and Regularization
 TTIC 31230, Fundamentals of Deep Learning David McAllester, Winter 2019 Generalization and Regularization 1 Chomsky vs. Kolmogorov and Hinton Noam Chomsky: Natural language grammar cannot be learned by
TTIC 31230, Fundamentals of Deep Learning David McAllester, Winter 2019 Generalization and Regularization 1 Chomsky vs. Kolmogorov and Hinton Noam Chomsky: Natural language grammar cannot be learned by
Accelerated primal-dual methods for linearly constrained convex problems
 Accelerated primal-dual methods for linearly constrained convex problems Yangyang Xu SIAM Conference on Optimization May 24, 2017 1 / 23 Accelerated proximal gradient For convex composite problem: minimize
Accelerated primal-dual methods for linearly constrained convex problems Yangyang Xu SIAM Conference on Optimization May 24, 2017 1 / 23 Accelerated proximal gradient For convex composite problem: minimize
CS 229 Project Final Report: Reinforcement Learning for Neural Network Architecture Category : Theory & Reinforcement Learning
 CS 229 Project Final Report: Reinforcement Learning for Neural Network Architecture Category : Theory & Reinforcement Learning Lei Lei Ruoxuan Xiong December 16, 2017 1 Introduction Deep Neural Network
CS 229 Project Final Report: Reinforcement Learning for Neural Network Architecture Category : Theory & Reinforcement Learning Lei Lei Ruoxuan Xiong December 16, 2017 1 Introduction Deep Neural Network
Learning with stochastic proximal gradient
 Learning with stochastic proximal gradient Lorenzo Rosasco DIBRIS, Università di Genova Via Dodecaneso, 35 16146 Genova, Italy lrosasco@mit.edu Silvia Villa, Băng Công Vũ Laboratory for Computational and
Learning with stochastic proximal gradient Lorenzo Rosasco DIBRIS, Università di Genova Via Dodecaneso, 35 16146 Genova, Italy lrosasco@mit.edu Silvia Villa, Băng Công Vũ Laboratory for Computational and
Sparse Approximation and Variable Selection
 Sparse Approximation and Variable Selection Lorenzo Rosasco 9.520 Class 07 February 26, 2007 About this class Goal To introduce the problem of variable selection, discuss its connection to sparse approximation
Sparse Approximation and Variable Selection Lorenzo Rosasco 9.520 Class 07 February 26, 2007 About this class Goal To introduce the problem of variable selection, discuss its connection to sparse approximation
WHY ARE DEEP NETS REVERSIBLE: A SIMPLE THEORY,
 WHY ARE DEEP NETS REVERSIBLE: A SIMPLE THEORY, WITH IMPLICATIONS FOR TRAINING Sanjeev Arora, Yingyu Liang & Tengyu Ma Department of Computer Science Princeton University Princeton, NJ 08540, USA {arora,yingyul,tengyu}@cs.princeton.edu
WHY ARE DEEP NETS REVERSIBLE: A SIMPLE THEORY, WITH IMPLICATIONS FOR TRAINING Sanjeev Arora, Yingyu Liang & Tengyu Ma Department of Computer Science Princeton University Princeton, NJ 08540, USA {arora,yingyul,tengyu}@cs.princeton.edu
Proximal Minimization by Incremental Surrogate Optimization (MISO)
 Proximal Minimization by Incremental Surrogate Optimization (MISO) (and a few variants) Julien Mairal Inria, Grenoble ICCOPT, Tokyo, 2016 Julien Mairal, Inria MISO 1/26 Motivation: large-scale machine
Proximal Minimization by Incremental Surrogate Optimization (MISO) (and a few variants) Julien Mairal Inria, Grenoble ICCOPT, Tokyo, 2016 Julien Mairal, Inria MISO 1/26 Motivation: large-scale machine
Sparse Solutions of an Undetermined Linear System
 1 Sparse Solutions of an Undetermined Linear System Maddullah Almerdasy New York University Tandon School of Engineering arxiv:1702.07096v1 [math.oc] 23 Feb 2017 Abstract This work proposes a research
1 Sparse Solutions of an Undetermined Linear System Maddullah Almerdasy New York University Tandon School of Engineering arxiv:1702.07096v1 [math.oc] 23 Feb 2017 Abstract This work proposes a research
SCRIBERS: SOROOSH SHAFIEEZADEH-ABADEH, MICHAËL DEFFERRARD
 EE-731: ADVANCED TOPICS IN DATA SCIENCES LABORATORY FOR INFORMATION AND INFERENCE SYSTEMS SPRING 2016 INSTRUCTOR: VOLKAN CEVHER SCRIBERS: SOROOSH SHAFIEEZADEH-ABADEH, MICHAËL DEFFERRARD STRUCTURED SPARSITY
EE-731: ADVANCED TOPICS IN DATA SCIENCES LABORATORY FOR INFORMATION AND INFERENCE SYSTEMS SPRING 2016 INSTRUCTOR: VOLKAN CEVHER SCRIBERS: SOROOSH SHAFIEEZADEH-ABADEH, MICHAËL DEFFERRARD STRUCTURED SPARSITY
EUSIPCO
 EUSIPCO 013 1569746769 SUBSET PURSUIT FOR ANALYSIS DICTIONARY LEARNING Ye Zhang 1,, Haolong Wang 1, Tenglong Yu 1, Wenwu Wang 1 Department of Electronic and Information Engineering, Nanchang University,
EUSIPCO 013 1569746769 SUBSET PURSUIT FOR ANALYSIS DICTIONARY LEARNING Ye Zhang 1,, Haolong Wang 1, Tenglong Yu 1, Wenwu Wang 1 Department of Electronic and Information Engineering, Nanchang University,
MLCC 2018 Variable Selection and Sparsity. Lorenzo Rosasco UNIGE-MIT-IIT
 MLCC 2018 Variable Selection and Sparsity Lorenzo Rosasco UNIGE-MIT-IIT Outline Variable Selection Subset Selection Greedy Methods: (Orthogonal) Matching Pursuit Convex Relaxation: LASSO & Elastic Net
MLCC 2018 Variable Selection and Sparsity Lorenzo Rosasco UNIGE-MIT-IIT Outline Variable Selection Subset Selection Greedy Methods: (Orthogonal) Matching Pursuit Convex Relaxation: LASSO & Elastic Net
Cheng Soon Ong & Christian Walder. Canberra February June 2018
 Cheng Soon Ong & Christian Walder Research Group and College of Engineering and Computer Science Canberra February June 2018 Outlines Overview Introduction Linear Algebra Probability Linear Regression
Cheng Soon Ong & Christian Walder Research Group and College of Engineering and Computer Science Canberra February June 2018 Outlines Overview Introduction Linear Algebra Probability Linear Regression
Uniqueness Conditions for A Class of l 0 -Minimization Problems
 Uniqueness Conditions for A Class of l 0 -Minimization Problems Chunlei Xu and Yun-Bin Zhao October, 03, Revised January 04 Abstract. We consider a class of l 0 -minimization problems, which is to search
Uniqueness Conditions for A Class of l 0 -Minimization Problems Chunlei Xu and Yun-Bin Zhao October, 03, Revised January 04 Abstract. We consider a class of l 0 -minimization problems, which is to search
Block stochastic gradient update method
 Block stochastic gradient update method Yangyang Xu and Wotao Yin IMA, University of Minnesota Department of Mathematics, UCLA November 1, 2015 This work was done while in Rice University 1 / 26 Stochastic
Block stochastic gradient update method Yangyang Xu and Wotao Yin IMA, University of Minnesota Department of Mathematics, UCLA November 1, 2015 This work was done while in Rice University 1 / 26 Stochastic
Artificial Neural Networks D B M G. Data Base and Data Mining Group of Politecnico di Torino. Elena Baralis. Politecnico di Torino
 Artificial Neural Networks Data Base and Data Mining Group of Politecnico di Torino Elena Baralis Politecnico di Torino Artificial Neural Networks Inspired to the structure of the human brain Neurons as
Artificial Neural Networks Data Base and Data Mining Group of Politecnico di Torino Elena Baralis Politecnico di Torino Artificial Neural Networks Inspired to the structure of the human brain Neurons as
The uniform uncertainty principle and compressed sensing Harmonic analysis and related topics, Seville December 5, 2008
 The uniform uncertainty principle and compressed sensing Harmonic analysis and related topics, Seville December 5, 2008 Emmanuel Candés (Caltech), Terence Tao (UCLA) 1 Uncertainty principles A basic principle
The uniform uncertainty principle and compressed sensing Harmonic analysis and related topics, Seville December 5, 2008 Emmanuel Candés (Caltech), Terence Tao (UCLA) 1 Uncertainty principles A basic principle
