Location Verification Systems Under Spatially Correlated Shadowing
|
|
|
- August Miles
- 5 years ago
- Views:
Transcription
1 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS Location Verification Systems Under Spatially Correlated Shadowing Shihao Yan, Ido evat, Gareth W. Peters, and Robert Malaney Abstract The verification of the location information utilized in wireless communication networks is a subject of growing importance. In this work we formally analyze, for the first time, the performance of a wireless Location Verification System LVS) under the realistic setting of spatially correlated shadowing. Our analysis illustrates that anticipated levels of correlated shadowing can lead to a dramatic performance improvement of a Received Signal Strength RSS)-based LVS. We also analyze the performance of an LVS that utilizes Differential Received Signal Strength DRSS), formally proving the rather counter-intuitive result that a DRSS-based LVS has identical performance to that of an RSS-based LVS, for all levels of correlated shadowing. Even more surprisingly, the identical performance of RSS and DRSSbased LVSs is found to hold even when the adversary does not optimize his true location. Only in the case where the adversary does not optimize all variables under her control, do we find the performance of an RSS-based LVS to be better than a DRSSbased LVS. The results reported here are important for a wide range of emerging wireless communication applications whose proper functioning depends on the authenticity of the location information reported by a transceiver. Index Terms Location verification, wireless networks, Received Signal Strength RSS), Differential Received Signal Strength DRSS), spatially correlated shadowing. I. ITRODUCTIO As location information becomes of growing importance in wireless networks, procedures to formally authenticate verify) that information have attracted considerable research interest [ 0]. In a wide range of emerging wireless networks, the system may request a device user) to report its location obtained through some independent means e.g., via a Global Positioning System GPS) receiver embedded in the device). Such location information can be used to empower some functionalities or services of wireless networks, such as geographic routing protocols e.g., [ 3]), location-based access control protocols e.g., [4, 5]), and location-based services e.g., location-based key generation [6]). However, the use of location information as an enabler of functionality or services within the wireless network, also provides ample opportunity to attack the system since any reported location information S. Yan was with the School of Electrical Engineering and Telecommunications, The University of ew South Wales, Sydney, SW, Australia. He is currently with the Research School of Engineering, Australia ational University, Canberra, ACT, Australia shihao.yan@anu.edu.au). R. Malaney is with the School of Electrical Engineering and Telecommunications, The University of ew South Wales, Sydney, SW, Australia r.malaney@unsw.edu.au). I. evat is with Institute for Infocomm Research, A STAR, Singapore ido-nevat@i2r.a-star.edu.sg). G. W. Peters is with the Department of Statistical Science, University College London, London, United Kingdom gareth.peters@ucl.ac.uk). Part of this work has been presented in IEEE ICC 204 [7]. can be easily spoofed. Such potential attacks are perhaps most concerning in the context of emerging Intelligent Transport Systems ITS) such as vehicular ad hoc networks VAETs), where spoofed positions may lead to catastrophic results for vehicular collision-avoidance systems [8]. In this work, we focus on a formal analysis of LVSs that attempt to verify a user s claimed location such as a GPS location) based on independent observations received by the wireless communications network itself. The inference in such an LVS is carried out to determine whether the claimed location represents a legitimate user a user who reports/claims to the network a location consistent with his true position) or a malicious user a user who reports to the network a location inconsistent with his true position). A key difference between an LVS and a localization system is that the output of an LVS is a binary decision legitimate/malicious user), whereas in localization system the output is an estimated location e.g., [9 2]). As such, an LVS is provided with some additional a priori but potentially false) location information i.e., a claimed location). Since the RSS measured by wireless network is easily obtained, many location verification algorithms that utilize RSS as input observations have been developed e.g., [3, 5, 6, 9, 0]). In addition, RSS can be readily combined with other location information metrics in order to improve the performance of a localization system [22, 23]. However, shadowing is one of the most influential factors in RSS-based LVSs, and all existing studies in RSS-based LVSs have made a simplified but unrealistic assumption that the shadowing at two different locations is uncorrelated. As per many empirical studies, the shadowing at different locations will be significantly correlated when the locations are close to each other or different locations possess similar terrain configurations e.g., [24 26]). Although some specific studies have investigated the performance of RSS-based localization systems under correlated shadowing [27 29], the impact of spatially correlated shadowing on RSS-based LVSs under realistic threat models has not been previously explored. This leaves an important gap in our understanding on the performance levels of RSS-based LVSs in realistic wireless channel settings and under realistic threat models. The main purpose of this paper is to close this gap. Further to our considerations of RSS-based LVSs, we note that there could be circumstances where the use of Differential Received Signal Strength DRSS) in the LVS context may be beneficial. Indeed it is well known that there are a range of scenarios in which the use of DRSS is more suitable for wireless location acquisition [30]. One example is where users do not have a common transmit power. However, the
2 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS 2 performance of DRSS-based LVSs have not yet been analyzed in the literature. This work also closes this gap, extending our analysis of DRSS-based LVSs to the correlated shadowing regime. This will allow us to provide a detailed performance comparison between RSS-based LVSs and DRSS-based LVSs under correlated shadowing - a comparison that provides for a few surprising results. A summary of the main contributions of this work are as follows. i) Under spatially correlated log-normal shadowing, we analyze the detection performance of an RSS-based LVS in terms of false positive and detection rates. Our analysis demonstrates that the spatial correlation of the shadowing can lead to a significant performance improvement for the RSSbased LVS relative to the case with uncorrelated shadowing a doubling of the detection rate for a given false positive rate for anticipated correlation levels). ii) We analyze the detection performance of a DRSS-based LVS under spatially correlated shadowing, proving that the detection performance of the DRSS-based LVS is identical to that of the RSS-based LVS. As we discuss later, this result is rather surprising. iii) We analyze our systems under a relaxed threat model scenario in which the adversary whose actual location is physically constrained e.g., constrained within a building) and therefore cannot optimize his location for the attack. We show that even in these circumstances the performances of the RSSbased LVS and the DRSS-based LVS remain identical. iv) Finally, we illustrate the case where the RSS-based LVS do have advantages over the DRSS-Based LVS, namely, when the adversary does not or cannot) optimize his boosted transmit power level. The rest of this paper is organized as follows. Section II details our system model. In Section III, the detection performance of the RSS-based LVS is analyzed under spatially correlated shadowing. In Section IV, the detection performance of the DRSS-based LVS is analyzed, and a throughout performance comparison between the RSS-based LVS and the DRSS-based LVS is provided. Section V provides numerical results to verify the accuracy of our analysis. Finally, Section VII draws concluding remarks. A. Assumptions II. SYSTEM MODEL We outline the system model and state the assumptions adopted in this work. ) A single user legitimate or malicious) reports his claimed location, x c = [x c, x 2 c] R 2, to a network with Base Stations BSs) in the communication range of the user, where the publicly known location of the i- th BS is x i = [x i, x2 i ] R2 i =, 2,..., ). Any one of the BSs can be chosen as the Process Center PC), and all other BSs will transmit the measurements collected from the user to the PC. 2) The user legitimate or malicious) can obtain his true position, x t = [x t, x 2 t ], from his localization equipment e.g., GPS), and the localization error is zero. Thus, a legitimate user s claimed location, x c, is exactly the same as his true location. However, a malicious user will falsify spoof) his claimed position in an attempt to fool the LVS. We assume the spoofed claimed location of the malicious user is also x c. 3) We adopt the minimum distance model as our threat model, in which the distance between the malicious user s true location and his claimed location is greater or equal to r, i.e., x c x t r. In this work, we assume the value of r is known to the PC as a priori information. In practice, there are three main methods to assign the value of r. The first method is an assignment based on the network operator s view of how close an attacker can be to his claimed location whilst having no fear of physical apprehension see later discussion in Section VI). A second method could be one dictated by the physical environment. For example, it could be that the threat model is based on a stationary attacker positioned off the highway, and the physical environment e.g., a fence) dictates he must be a minimum distance from the highway [3 33]. A third method is to set the value of r based on the expected localization error e.g., GPS error) of a legitimate user. In this case, r would be set so as to guarantee a low probability that the legitimate user s true location is outside the region determined by x c and r. A combination e.g., weighted value) of all methods could also be used. 4) We denote the null hypothesis where the user is legitimate as H 0, and denote the alternative hypothesis where the user is malicious as H. The a priori knowledge at the LVS can be summarized as { H0 : x c = x t legitimate user), ) H : x c x t r malicious user). B. Observation Model under H 0 Based on the log-normal propagation model, the RSS in db) received by the i-th BS from a legitimate user, y i, is given by where y i = u i + ω i, i =, 2,...,, 2) ) d c u i = p 0γ log i 0, 3) d and p is a reference received power corresponding to a reference distance d, γ is the path loss exponent, ω i is a zero-mean normal random variable with variance σdb 2, and d c i is the Euclidean distance from the i-th BS to the legitimate user s claimed location also his true location) given by d c i = x c x i. We note that d c i = d t i under H 0, where d t i = x t x i. In practice, in order to determine the values of p and d we have to know the transmit power of the legitimate user. We highlight that in this work we assume that the transmit power of the legitimate user is known to the LVS. This is mainly due to the fact that the legitimate user cooperates with the LVS in order to facilitate the location verification. To this end, the legitimate user will set his transmit power to a predetermined value set by the LVS. For fairness, we also assume that the malicious user also knows the transmit
3 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS 3 power of the legitimate user equivalently, knows the values of p and d), which allows the malicious user to optimally set his transmit power in order to minimize the probability to be detected. Under spatially correlated shadowing, ω i is correlated to ω j j =, 2,..., ), and the covariance matrix of ω = [ω,..., ω ] is denoted as R. Adopting the well-known spatially correlated shadowing model of [7, 24], the i, j)-th element of R is given by R ij = σdb 2 exp d ) ij ln 2, j =, 2,...,, 4) D c where d ij = x i x j is the Euclidean distance from the i-th BS to the j-th BS and D c is a constant in units of distance, at which the correlation coefficient reduces to /2 in this work all distances are in meters). From 4), we can see that the correlation between ω i and ω j decreases as d ij increases R ij = σdb 2 when i = j, and R ij 0 as d ij ). We also note that R ij increases as D c increases for a given d ij. As such, D c is a parameter that indicates the degree of shadowing correlation in some specific environment for a given d ij, a larger D c means that the shadowing is more correlated). Based on 2), we can see that under H 0 the -dimensional observation vector y = [y,..., y ] T follows a multivariate normal distribution, which is f y H 0 ) = u, R), 5) where u = [u, u 2,..., u ] T is the mean vector. C. Observation Model under H In practice, in addition to spoofing the claimed location, the malicious user can also adjust his transmit power to impact the RSS values received by all BSs in order to minimize the probability of being detected. As such, the RSS received by the i-th BS from a malicious user, y i, is given by where y i = p x + v i + ω i, 6) ) d t v i = p 0γ log i 0, 7) d and p x is the additional boosted transmit power. We note that p x is the same for all the BSs since the additional transmit power only effects the value of p and the distance between i-th BS and the malicious user is absorbed by v i. Based on 6), under H the -dimensional observation vector y, conditioned on known p x and x t, also follows a multivariate normal distribution, which is f y p x, x t, H ) = p x + v, R), 8) where is a vector with all elements set to unity and v = [v, v 2,..., v ] T. We note that in practice p x and x t are set by the malicious user. D. Decision Rule of an LVS We adopt the Likelihood Ratio Test LRT) as the decision rule since it is optimal for binary hypothesis testing problem in terms of achieving the highest detection rate for any given false positive rate [34]. Therefore, the LRT can achieve the minimum Bayesain average cost [35] and the maximum mutual information between the input and output of an LVS [0]. Given that no related work on LVSs under correlated shadowing is available in the literature, in this work we focus on analyzing the detection performances of our LVSs rather than comparisons with other works. We note that the deployment of the LRT requires that the likelihood functions under both H 0 and H can be evaluated exactly in analytic forms i.e., there are no nuisance parameters involved in these likelihood functions). In general, the likelihood function under H is dependent on some parameters e.g., p x, x t ) that are unknown to the LVS. In this work we adopt a conservative scenario, in which we assume that the malicious user can optimize all the parameters under his control. We refer to this scenario as the worst-case scenario throughout this work. In practice, if the malicious user cannot optimize all the parameters under his control, our analysis based on the worstcase scenario serves as the lower bound for the detection performance of a practical LVS. The LRT decision rule is given by Λ ψy)) f ψy) H ) f ψy) H 0 ) λ, 9) where Λ ψy)) is the test statistic, ψy) is a predefined transformation of y, f ψy) H ) is the likelihood function probability density function of ψy)) under H, f ψy) H 0 ) is the likelihood function under H 0, λ is the threshold corresponding to Λ ψy)), and are the binary decisions that infer whether the user is legitimate or malicious, respectively. It is worth noting that another definition of the likelihood ratio e.g., composite likelihood ratio) has to be adopted if some parameters under H 0 and H are unknown. In our work, 9) does not involve any unknown parameters based on the worstcase scenario. We clarify that in our RSS-based LVS we have ψy) = y, i.e., no transformation function is utilized in the RSS-based LVS. In our DRSS-based LVS the transformation function ψ ) maps the RSS into DRSS detailed in Section IV-A). Although ψy) in our work is still normal given that y is normal, ψy) is not necessarily normal since the transformation may be not linear. Given the decision rule in 9), the false positive and detection rates of an LVS are functions of λ. The intrinsic core performance metrics of an LVS are false positive and detection rates, other potential performance metrics can be written as functions of these two rates. As such, in this work we adopt the false positive and detection rates as the performance metrics for an LVS. We note that a priori probabilities may be required for some performance metrics adopted by an LVS. For example, the Bayesian average cost is defined as C = P 0 αc 0 + P 0 ) β)c, where P 0 is the a priori probability that H 0 is true, C 0 is the pre-assigned cost of rejecting a legitimate user, and C is the pre-assigned cost of accepting a malicious user [35]. We highlight that in
4 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS 4 order to achieve the overall minimum Bayesian average cost the likelihood ratio i.e., Λ ψy))) should be adopted as the test statistic. III. RSS-BASED LOCATIO VERIFICATIO SYSTEM In this section, we analyze the performance of the RSSbased LVS in terms of the false positive and detection rates, based on which we examine the impact of the spatially correlated shadowing. A. Attack Strategy of the Malicious User We assume that the malicious user optimizes all the parameters under his control. This assumption is adopted in most threat models. The ultimate goal of the malicious user is to minimize the detection rate. To this end, the malicious user is to minimize the KL divergence from f y p x, x t, H ) to f y H 0 ) [36]. This result is mainly due to the fact that the threshold λ and observation y are unknown to the malicious user and the KL divergence from f y p x, x t, H ) to f y H 0 ) is the expected log likelihood ratio when the alternative hypothesis H is true. Based on 5) and 8), the KL divergence from f y p x, x t, H ) to f y H 0 ) is given by [37] ϕp x, x t ) = D KL [f y p x, x t, H ) f y H 0 )] = ln f y p x, x t, H ) f y p x, x t, H ) dy f y H 0 ) = 2 p x + v u) T R p x + v u). 0) Then, the optimal values of p x and x t that minimize ϕp x, x t ) can be obtained through p x, x t ) = argmin ϕp x, x t ). ) p x, x t x c r The closed-form expressions for p x and x t are intractable, but they can be obtained through numerical search. In order to simplify the numerical search, we first derive the optimal value of p x for a given x t, which is presented in the following lemma. Lemma : The optimal value of p x that minimizes ϕp x, x t ) for any given x t is p o xx t ) = u v)t R T R. 2) Proof: The first derivative of ϕp x, x t ) with respect to p x is derived as ϕp x, x t ) = ϕp x, x t ) p x p x ) p x ) p x = p x + v u) T R p x ) p x = p x + v u) T R. 3) Following 3), the second derivative of ϕp x, x t ) with respect to p x is derived as 2 ϕp x, x t ) 2 p x = T R. 4) oting that R given by 4) is a positive-definite matrix, as per 4) we have 2 ϕp x, x t )/ 2 p x > 0, which indicates that ϕp x, x t ) is a convex function of p x. As such, setting ϕp x, x t )/ p x = 0, we obtain the desired result in 2) after some algebraic manipulations. From Lemma, we note that the malicious user optimizes his transmit power, i.e., p x = p o xx t ), to compensate the path-loss difference between his claimed location and his true location. We also note that p o xx t ) is a function of R under spatial correlated shadowing. This is different from the scenario with uncorrelated shadowing, where p o xx t ) is independent of the shadowing noise [0]. Substituting p o xx t ) into 0), we have where ϕp o xx t ), x t ) = 2 w u)t R w u), 5) w = u v)t R T R + v. 6) Since we have shown that ϕp x, x t ) is a convex function of p x in 4), x t can be obtained through x t = argmin ϕp o xx t ), x t ). 7) x t x c r Substituting x t into p o xx t ), we obtain p x = p o xx t ). We note that Lemma is of importance since it reduces a threedimension numerical search in ) into a two-dimension numerical search in 7). On average, the computing time required to search for x t in 7) is around 20 seconds when the grid search method is adopted and 00 points in each dimension are searched based on MATLAB R204b on a DELL desktop with a Core i7 processor). Substituting p x and x t into 6), the RSS received by the i-th BS from a malicious user can be written as where y = w + ω, 8) w = u v ) T R T R + v, 9) v is obtained by substituting x t into v. Based on 8), the likelihood function under H conditioned on p x and x t can be written as f y p x, x t, H ) = w, R). 20) B. Performance of the RSS-based LVS In some practical cases, the malicious user may not have the freedom to optimize his true location, e.g., the malicious user is physically limited to be inside a building. However, the malicious user can still optimize his transmit power as per his true location. As such, without losing generality, we first analyze the performance of the RSS-based LVS for p x = p o xx t ), and then present the performance of the RSS-based LVS for p x = p x and x t = x t as a special case.
5 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS 5 Following 9) and noting ψy) = y, the specific LRT decision rule of the RSS-based LVS for p x = p o xx t ) is given by Λ o y) f y po xx t ), x t, H ) f y H 0 ) λ o R, 2) where Λ o y) is the likelihood ratio of y for p x = p o xx t ), f y p o xx t ), x t, H ) = w, R), and λ o R is a threshold for Λ o y). Then, we obtain Λ o y) in the ln domain as ln Λ o y)= 2 y u)t R y u) 2 y w)t R y w) = w u) T R y 2 w u)t R w+u). As such, for the theorem to follow, we can rewrite the decision rule in 2) as the following format Ty) where Ty) is the test statistic given by Γ R, 22) Ty) w u) T R y, 23) and Γ R is the threshold for Ty) given by Γ R ln λ o R + 2 w u)t R w + u). 24) We note that 22) is the explicit binary decision rule at the PC for the RSS-based LVS. In 22) only the test statistic Ty) is a function of the observations. The threshold Γ R can be determined by setting an acceptable false positive rate, minimizing the Bayesian average cost, or maximizing the mutual information between the input and output of the RSSbased LVS. To this end, we have to derive the false positive rate, αr o, and detection rate, βo R, of the RSS-based LVS, which are provided in the following theorem. Theorem : For p x = p o xx t ), the false positive and detection rates of the RSS-based LVS are αrx o t ) = Q Γ R w u) T R u w u) T R w u) = Q ln λo R + 2 w u)t R w u), 25) w u) T R w u) βrx o t ) = Q Γ R w u) T R w w u) T R w u) = Q ln λo R 2 w u)t R w u), 26) w u) T R w u) where Q[x] = 2π x exp t2 /2)dt. Proof: Using 23), the distributions of Ty) under H 0 and H are derived as follows ) Ty) H 0 w u) T R u, w u) T R w u), 27) ) Ty) H w u) T R w, w u) T R w u). 28) As per the decision rule in 22), the false positive and detection rates are given by α o Rx t ) Pr Ty) Γ R H 0 ), 29) β o Rx t ) Pr Ty) Γ R H ). 30) Substituting 27) and 28) into 29) and 30), respectively, we obtain the results in 25) and 26) after some algebraic manipulations. For p x = p x and x t = x t, the LRT decision rule of the RSS-based LVS is given by Λ y) f y p x, x t, H ) f y H 0 ) λ R, 3) where Λ y) is the likelihood ratio of y for p x = p x and x t = x t, and λ R is a threshold for Λ y). Following Theorem, the false positive and detection rates of the RSS-based LVS for p x = p x and x t = x t are given by αr = Q ln λ R + 2 w u) T R w u), 32) w u) T R w u) βr = Q ln λ R 2 w u) T R w u). 33) w u) T R w u) We note that the results provided in 25) and 26) are based on an arbitrary true location x t of the malicious user, which are more general than that provided in 32) and 33). That is, αr = αo R x t ) and βr = βo R x t ). By using 25) and 26), we can compare the performance of the RSS-based LVS with that of the DRSS-based LVS in a general scenario. We also note that based on 32) and 33) we can examine the impact of shadowing correlation on the detection performance of the RSS-based LVS. Considering the properties of the Q-function, we have the following corollary. Corollary : The detection performance of the RSS-based LVS increases as κ w u) T R w u) increases, i.e., βr increases for any fixed α R as κ increases or α R decreases for any fixed βr as κ increases). Proof: Let us suppose we have two LVSs, LVS- and LVS-2. We assume that the false positive rate and detection rate of LVS-k k {, 2}) are given by, respectively, α k = Q [ ln λk + 2 κ k κk ] = Q [ ln λk κk + [ ln λk 2 β k = Q κ ] [ k ln λk = Q κk κk κk 2 κk 2 ], 34) ]. 35) We note that Q[x] is a monotonic decreasing function of x. Then, following 34) and setting α = α 2, we have ln λ κ + = ln λ 2 κ2 + κ 2 κ ) Suppose κ κ 2, by subtracting κ and κ 2 from the left side and right side of 36), respectively, we have ln λ κ > ln λ 2 κ2 κ 2 κ )
6 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS 6 As such, following 35) and 37) we have β β 2. Therefore, we have proved that β β 2 for α = α 2 if κ κ 2. Similarly, we can prove that α > α 2 for β = β 2 if κ κ 2. Comparing 32) and 33) with 34) and 35), respectively, the proof follows. Corollary is consistent with our previous conclusion that the malicious user will minimize the KL-divergence given in 0) in order to minimize the detection performance of an LVS, because 2 w u) T R w u) is the minimum value of the KL-divergence given in 5). Therefore, in order to examine the impact of the shadowing correlation we only have to check whether an increased correlation e.g., increased D c ) leads to an increased or decreased value of 2 w u) T R w u). Due to the fact that x t cannot be obtained analytically, it is impossible to theoretically analyze the impact of shadowing correlation on the detection performance of the RSS-based LVS. In this regard, we will examine this impact numerically. As we will show in Section V the correlation of the shadowing leads to performance improvements in practical scenarios. Intuitively, this is due to the fact that the shadowing correlation reduces the uncertainty of the observations caused by shadowing noise, and consequently it becomes harder for the malicious user to mimic these observations. Following Corollary, we have the following corollary with regard to how the values of σdb 2 effect the performance of the RSSbased LVS. Corollary 2: The detection rate of the RSS-based LVS decreases as σdb 2 increases for any arbitrary fixed false positive rate or the false positive rate of the RSS-based LVS increases as σdb 2 increases for any arbitrary fixed detection rate). Following Corollary, we can prove Corollary 2 by noting that κ decreases as σdb 2 increases due to 4). IV. DRSS-BASED LOCATIO VERIFICATIO SYSTEM In this section, we analyze the detection performance of the DRSS-based LVS under spatially correlated shadowing. We also provide an analytical comparison between the RSS-based LVS and the DRSS-based LVS. A. DRSS Observations We obtain ) basic DRSS observations from RSS observations by subtracting the -th RSS observation from all other ) RSS observations. As such, the m-th DRSS value under H 0 is given by y m = u m + ω m, m =, 2,...,, 38) where u m = u m u and ω m = ω m ω. We note that ω m is Gaussian with zero mean and variance 2σ 2 db R m). We denote the ) ) covariance matrix of the )-dimensional DRSS vector y = [ y,..., y ] T as D, whose m, n)-th element is given by n =, 2,..., ) D mn = R + R mn R m R n. 39) As such, y under H 0 follows a multivariate normal distribution, which is given by f y H 0 ) = u, D), 40) where u = [ u,..., u ] T is the mean vector. Likewise, the m-th DRSS value under H is y m = v m + ω m, 4) where v m = v m v. oting v = [ v,..., v ] T, y under H follows another multivariate normal distribution, which is given by f y x t, H ) = v, D). 42) B. Attack Strategy of the Malicious User As per 3) and 7), we know that both p and d are constant at all elements of u and v. As such, based on 38) and 4) we can see that y under both H 0 and H is independent of p and d, and therefore both f y H 0 ) and f y x t, H ) are independent of p and d. As such, in the DRSS-based LVS the malicious user does not need to adjust his transmit power in order to minimize the detection rate. In the DRSS-based LVS, the malicious user only has to optimize his true location through minimizing the KL-divergence from f y x t, H ) to f y H 0 ), which is given by φx t ) = D KL [f y x t, H ) f y H 0 )] = ln f y x t, H ) f y x t, H ) d y f y H 0 ) = 2 v u)t D v u). 43) Then, the optimal value of x t for the malicious user in the DRSS-based LVS can be obtained through x t = argmin φx t ). 44) x t x c r The likelihood function under H for x t = x t is given by ) f y x t, H = v, D), 45) where v m = v m v and v is obtained by substituting x t into v. C. Performance of the DRSS-based LVS In this subsection, we again consider the case where the true location of the malicious user is physically constrained. Specifically, we first analyze the performance of the DRSSbased LVS for an arbitrary x t, and then present the performance of the DRSS-based LVS for x t = x t as a special case in this subsection. Following 9), the specific LRT decision rule of the DRSSbased LVS for any x t is given by Λ y) f y x t, H ) f y H 0 ) λ D, 46) where Λ y) is the likelihood ratio of y and λ D is a threshold for Λ y). Substituting 40) and 45) into 46),
7 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS 7 we obtain Λ y) in ln domain as ln Λ y) = 2 y u)t D y u) 2 y v)t D y v) = v u) T D y 2 v u)t D v + u). Then, we can rewrite the decision rule given in 46) as T y) where T y) is the test statistic given by Γ D, 47) T y) v u) T D y, 48) and Γ D is the threshold for T y) given by Γ D ln λ D + 2 v u)t D v + u). 49) We would like to highlight that 47) is the explicit binary decision rule at the PC for the DRSS-based LVS. In 47) only the test statistic T y) depends on the DRSS observations y. The threshold Γ D can be determined by setting an acceptable false positive rate, minimizing the Bayesian average cost, or maximizing the mutual information between the input and output of the DRSS-based LVS. In this regard, the false positive rate, α D x t ), and the detection rate, β D x t ), of the DRSS-based LVS have to be derived, which are present in the following theorem. Theorem 2: The false positive and detection rates of the DRSS-based LVS for any x t are given by α D x t ) = Q Γ D v u) T D u v u) T D v u) = Q ln λ D + 2 v u)t D v u), v u) T D v u) 50) β D x t ) = Q Γ D v u) T D v v u) T D v u) = Q ln λ D 2 v u)t D v u). v u) T D v u) 5) The proof of Theorem 2 is similar to that of Theorem and omitted here due to page limits. For x t = x t, the LRT decision rule of the DRSS-based LVS is given by Λ y) f y x t, H ) f y H 0 ) λ D, 52) where Λ y) is the likelihood ratio of y for x t = x t and λ D is a threshold for Λ y). Following Theorem 2, the false positive and detection rates of the DRSS-based LVS for x t = x t are given by T ) ln λ αd D = Q + 2 v u) D v u ) T ), v u D v u ln λ βd D = Q 2 T v u) D v u ) T ) v u D v u 53) ). 54) Again, note that the results provided in 50) and 5) are for any x t, which are more general than that provided in 53) and 54). That is, α D = α Dx t) and β D = β Dx t). By using 50) and 5), we can compare the performance of the DRSS-based LVS with that of the RSS-based LVS in a general scenario. D. Comparison between the RSS-based LVS and the DRSSbased LVS We now present the following theorem with regard to the comparison between the RSS-based LVS and the DRSS-based LVS. Theorem 3: For any x t, we have αr o x t) = α D x t ) and βr o x t) = β D x t ) for λ R = λ D. That is, for any x t the performance of the RSS-based LVS with p x = p o xx t ) is identical to the performance of the DRSS-based LVS. Proof: Based on 25), 26), 50), and 5), we can see that αr o x t), βr o x t), α D x t ), and β D x t ) are all in the form of a Q function. We denote αr o x t) = QζR o ), βo R x t) = QηR o ), α D x t ) = Qζ D ), and β D x t ) = Qη D ). In order to prove αr o x t) = α D x t ) and βr o x t) = β D x t ) for λ R = λ D, we only need to prove ζr o ηo R = ζ D η D. As per 25), 26), 50), and 5), in order to prove ζr o ηo R = ζ D η D such as to prove Theorem 3) we have to prove the following equation w u) T R w u) = v u) T D v u). 55) Based on the singular value decomposition SVD) of R, we can transform the RSS observation vector y into another observation vector y by rotating and scaling. We can then obtain the DRSS observations from y instead of y. The transformation from y to y is unique since the singular values of R are unique. In addition, y follows a multivariate normal distribution. As such, the transformation from y to y keeps all the properties of y in y, which means the performance of an LVS based on y is identical to the performance of an LVS based on y [38, 39]. Therefore, in order to prove Theorem 3 we only have to prove 55) for R = I. Denoting g = v u, we have v m u m = g m g. Substituting R = I into w given in 6), we obtain w u = g gt R T = g R g j. The covariance matrix R is a real positive-definite symmetric matrix, and thus the SVD of R can be written as R = SR S T. As such, y is given by y = R 2 Sy and the covariance matrix of y will be I.
8 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS 8 With regard to the left side of 55), for R = I we have 2 w u) T R w u) = g i g j 2 = gi 2 2 g i g j + 2 g j = gi 2 2 ) g i g j + g j 2 = gi 2 ) 2 g i. 56) As per the definition of D given in 39), for R = I we have D = I + ) ), 57) where ) ) ) is the ) ) matrix with all elements set to unity. Then, based on the Sherman-Morrison formula [40], we have [ ] D = I + ) T ) [ ] = = I I ) )I + T ) [ I I ) ) ) ]. 58) Substituting 58) into the right side of 55), we have v u) T D v u) [ = v u) T I ] ) ) v u) = v u) T I v u) v u)t ) T ) v u) [ = g i g ) 2 ] 2 g i g ) [ = g i g ) 2 ] 2 g i g ) = g i g ) 2 g i g ) g j g ) = gi 2 ) 2 g i. 59) Comparing 56) with 59), we can see that we have proved 55) for R = I. This completes the proof of Theorem 3. We note that the result provided in Theorem 3 is valid for any R, i.e., for any kind of shadowing correlated or uncorrelated). We also note that in Theorem 3 the condition to guarantee the RSS-based LVS being identical to the DRSSbased LVS is that p x = p o xx t ). This condition forces the malicious user to optimize his transmit power based on the given x t in the RSS-based LVS, but not in the DRSS-based LVS. Without this condition, the comparison result between the RSS-based LVS and the DRSS-based LVS is present in the following corollary. Two intuitive explanations for Theorem 3 are as follows. i) Knowing the transmit power of the legitimate user by the LVS enables the RSS-based LVS to gain an advantage over the DRSS-based LVS. This is due to the fact that p together with d provide useful information on RSS observations while DRSS observations are not functions of p and d. ii) The malicious user s knowledge on p and d allows him to optimally set his transmit power equivalently, to optimize p x ) in the RSS-based LVS. This nullifies the advantage of the RSS-based LVS over the DRSS-based LVS. Following Theorem 3, we further have the following four corollaries with regard to the performances of the RSS-based and DRSS-based LVSs. Corollary 3: For any + > 2 the detection performances of the RSS-based and DRSS-based LVSs will at be at least as good as the performances for. The proof of Corollary 3 follows from the fact that the RHS of 56) and 59)) for + > 2 is equal or larger than that for. We note that the equality can only occur in the most unusual of circumstances such as the malicious user reporting his true location). As such, in practice increases in will effectively always lead to an improvement in detection performance. Corollary 4: In the DRSS-based LVS, any of the BSs can be selected as the reference BS, and this selection does not effect the performance of the DRSS-based LVS. The proof of Corollary 4 follows from the fact that 59) does not depend on the selection of the reference BS. Corollary 5: For any x t, the performance of the RSS-based LVS with p x p o xx t ) is better than the performance of the DRSS-based LVS. The proof of Corollary 5 follows from Corollary and the proof of Theorem 3. Corollary 6: We have α R = α D and β R = β D for λ R = λ D. That is, the performance of the RSS-based LVS for p x = p x and x t = x t is identical to the performance of the DRSSbased LVS for x t = x t. Proof: Based on Theorem 3, in order to prove Corollary 6 we only have to prove x t = x t. We note that x t and x t are obtained through minimizing ϕp o xx t ), x t ) and φx t ), respectively. As such, in order to prove x t = x t, it suffices to prove ϕp o xx t ), x t ) = φx t ). As per 5) and 43), we can see that we have proved ϕp o xx t ), x t ) = φx t ) in 55). We note that Corollary 6 presents a comparison between the performance limits of the RSS-based LVS and the DRSSbased LVS. In the proof of Corollary 6, we also prove that the malicious user s optimal true location for the RSS-based LVS is the same as that for the DRSS-based LVS. We also note that the analysis and results reported in this work are not directly applicable to the colluding threat scenario where multiple colluding adversaries attack the LVS). Future studies may wish to explore these more sophisticated attacks, in the context of correlated shadowing. However, although such sophisticated attacks will obviously lead to poorer LVS performance, a
9 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS Detection rate Theoretic results for x t = [ 500, 0] Simulated results for x t = [ 500, 0] Theoretic results for x t = [500, 250] Simulated results for x t = [500, 250] Theoretic results for x t = x t = [09.9, 49.4] Detection rate Theoretic results for x t = [ 500, 0] Simulated results for x t = [ 500, 0] Theoretic results for x t = [500, 250] Simulated results for x t = [500, 250] Theoretic results for x t = x t = [09.9, 49.4] 0. Simulated results for x t = x t = [09.9, 49.4] 0. Simulated results for x t = x t = [09.9, 49.4] False positive rate Fig.. ROC curves of the RSS-based LVS for σ db = 7.5, D c = 50m, r = 500m, p x = p o xx t ), and = 3 x = [ 250, 0], x 2 = [0, 0], and x 3 = [250, 0] ) False positive rate Fig. 2. ROC curves of the DRSS-based LVS for σ db = 0, D c = 50m, r = 500m, and = 3 x = [ 250, 0], x 2 = [0, 0], and x 3 = [250, 0] ). conjecture is that the trends discovered here with regard to the impact of correlated shadowing on LVS performance will persist. V. UMERICAL RESULTS We now present numerical results to verify the accuracy of our provided analysis. We also provide some insights on the impact of the spatially correlated shadowing on the performance of the RSS-based LVS and the DRSS-based LVS. Although we have simulated a wide range of system settings, the associated settings for the results shown in this work unless otherwise stated) are as follows. In the simulations presented here, the BSs and the claimed locations are deployed in a 500m-by-20m rectangular area and a 200m-by-200m square area. The 500m-by-20m rectangular area mimics a stretch of a road e.g., a highway) in which emerging ITS will be applicable and LVSs will be of significant importance. The simulations for the 200m-by-200m square area investigates LVSs in the context of wireless sensor networks, in which senors provide observation of various physical phenomena e.g., temperature, humidity) together with their location information to the BSs. The origin is set at the center of the rectangular area, with the x-coordinate taken along the length, and the y-coordinate taken along the width. The claimed location of a user legitimate or malicious) is set as x c = [50, 5], which is also the true location of the legitimate user. The locations of all BSs are provided in the caption of each figure, and all BSs collect measurements from the legitimate and malicious users. The path loss exponent is set to γ = 3, and the reference power is set to p = 0 db at d = m. In Fig., we present the Receiver Operating Characteristic ROC) curves of the RSS-based LVS. In order to obtain this figure, we have set the BSs at regular intervals 250m) on each side of the rectangular area. In this figure, we first observe that the Monte Carlo simulations precisely match the theoretic results, confirming our analysis in Theorem. We also observe that the ROC curves for x t x t dominate the ROC curve for x t = x t. This observation indicates that if the malicious user does not optimize his true location, it will be easier for the RSS-based LVS to detect the malicious user. In summary, the ROC curve for x t = x t provides a lower bound for the performance of the RSS-based LVS. In Fig. 2, we present the ROC curves of the DRSS-based LVS. In order to obtain this figure, we have adopted the same locations of the BSs. We note that a different value of σ db is adopted to produce Fig. 2 in order to avoid the identical between Fig. and Fig. 2. In this figure, we first observe that the Monte Carlo simulations precisely match the theoretic results, confirming our analysis in Theorem 2. We also observe that the ROC curves for x t x t dominate the ROC curve for x t = x t. Again, this observation demonstrates the importance of optimally choosing the true location for the malicious user. To conclude, the ROC curve for x t = x t provides a lower bound for the performance of the DRSS-based LVS. In Fig. 3, we present the ROC curves of the RSS-based LVS and the DRSS-based LVS. In order to obtain this figure, we have set one of the BSs at one side of the rectangular area and deployed the other two BSs randomly inside the rectangular area. This mimics the scenario in which only one fixed BS is available and we have to conduct location verification with the help of two already-authorized vehicles. In this figure, we first observe that the RSS-based LVS for p x = p o xx t ) and the DRSS-based LVS achieve identical performance identical ROC curves). This demonstrates that as long as the malicious user optimizes his transmit power as per his true location) the RSS-based LVS is identical to the DRSS-based LVS, which confirms the analytical comparison between the RSS-based LVS and the DRSS-based LVS presented in Theorem 3. We also observe that the ROC curves of the RSS-based LVS for
10 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS p x = p x + 3dB 0.8 Detection rate D c = 0m x t = x t = x t = [ 450,4.7] D c = 50m x t = x t = x t = [ 399, 25] RSS-based LVS for p x p x p x = p x 5dB RSS-based LVS for p x = p x Detection rate r = 000m, x t = x t = [ 926.9, 208.7] r = 250m, x t = x t = [9.9, 78.4] r = 00m, x t = x t = [4.2, 83.9] r = 70m, x t = x t = [9.9, 58.2] 0. DRSS-based LVS 0. r = 50m, x t = x t = [29.7, 40.7] False positive rate Fig. 3. ROC curves of the RSS-based LVS and the DRSS-based LVS for σ db = 5, r = 500m, and = 3 x = [0, 0], x 2 = [3.4, 9.3], and x 3 = [20.6, 0.9] ) False positive rate Fig. 5. ROC curves of the RSS-based LVS p x = p x ) and the DRSS-based LVS for σ db = 5, D c = 50m, x t = x t = x t, and = 3 x = [0, 0], x 2 = [3.4, 9.3], and x 3 = [20.6, 0.9] ). Detection rate D c = 400m, p x = 3.67dB, x t = [77.0, 494.3] D c = 200m, p x = 5.03dB, x t = [78.3, 494.2] D c = 00m, p x = 6.27dB, x t = [94.7, 493.0] D c = 0m, p x = 7.04dB, x t = [09.9, 49.4] False positive rate Fig. 4. ROC curves of the RSS-based LVS for σ db = 7.5, r = 500m, p x = p x, x t = x t, and = 3 x = [ 250, 0], x 2 = [0, 0], and x 3 = [250, 0] ). p x p o xx t ) dominate the ROC curves of the DRSS-based LVS. This observation confirms that if the malicious user does not optimize his transmit power, the RSS-based LVS achieves a better performance than the DRSS-based LVS, which is provided in Corollary 5. This indicates that the RSS-based LVS is subjectively better than the DRSS-based LVS since the performance of the DRSS-based LVS is independent of the malicious user s transmit power and the determination of the optimal transmit power for the malicious user is no longer required in the DRSS-based LVS. In Fig. 4, we investigate the impact of the spatial correlation of the shadowing on the performance of the RSS-based LVS and the DRSS-based LVS, where D c = 0m corresponds to the case with uncorrelated shadowing. In Fig. 4, we set p x = p x and x t = x t for the RSS-based LVS. From 2) and 7), we can see that both p x and x t are dependent on the spatial correlation of the shadowing they are both functions of D c ), and the exact values of p x and x t corresponding to each D c are also provided in Fig. 4. In this figure, we first observe the ROC curve moves toward the upper left corner i.e., the area under the ROC curve increases) as D c increases, which shows that the performance of the RSS-based LVS becomes better as D c increases. This observation demonstrates that the spatial correlation of the shadowing improves the detection performance of the RSS-based LVS. Intuitively, this improvement is due to the fact that the increased D c reduces the randomness embedded in the RSS observations, and thus it is more difficult for the malicious user to mimic the legitimate observations for the increased D c i.e., the KL divergence presented in 0) increases as D c increases under the system settings of Fig. 4). We note that the above performance improvement due to the spatial correlation of the shadowing is only achieved under the condition p x = p x and x t = x t. If the malicious user is physically limited at some specific location x t and he optimizes his transmit power as per x t, i.e., p x = p o xx t ), the spatial correlation of the shadowing does not have a monotonic impact on the performance of the RSS-based LVS. As per Theorem 3 and Corollary 6, the ROC curves provided in Fig. 4 are also valid for the DRSS-based LVS, in which we have to set x t = x t. As such, we can conclude that the spatial correlation of the shadowing also improves the detection performance of the DRSS-based LVS. Also, for a determined x t the spatial correlation does not have a monotonic impact on the performance of the DRSS-based LVS.
11 SUBMITTED TO IEEE TRASACTIOS O WIRELESS COMMUICATIOS In Fig. 5, we examine the impact of the parameter r on the performance of both the RSS-based LVS and the DRSSbased LVS. We note that r is the minimum distance between the claimed location and the malicious user s true location. As such, the disc determined by x c and r can be interpreted as the area protected by some physical boundaries. In Fig. 5, we observe that the ROC curve moves toward the upper left corner as r increases, which indicates that the malicious user will be easier to detect if he is further away from his claimed location. We also observe that the performance improvement due to increasing r is not significant when r is larger than some specific value e.g., r > 250m). Detection rate o uncertainty on x t Localization error on x t Exhaustive decision space on x t VI. DISCUSSIOS We would like to clarify that the a priori knowledge model given in ) does not represent an exhaustive decision space and also does not involve localization errors e.g., GPS errors) on the true location of the legitimate user. However, we can adopt a generalized a priori knowledge model to address these two effects, which is given by { H0 : x t = x c + x e legitimate user), 60) H : x c x t r malicious user), where x e is the a priori uncertainty of x t at the legitimate user and the a priori distribution of x e is denoted as fx e ). We can specify different a priori knowledge on x e in order to consider the exhaustive decision space or the localization error. Specifically, we can assume x e r for the exhaustive decision space in order to avoid any overlap between the possible spaces under H 0 and H. We would like to clarify that x e r means that x e is randomly distributed inside a disk with the origin at the center and r as the radius. In practice, this disk can be approximated as an area with some physical boundaries e.g., fences). We note that the assumption, x e r, is normally adopted in the in-region location verification systems [4, 42], which were mainly investigated via new protocol designs rather than via statistical analysis. From a statistical point of view, we have to adopt some specific a priori distribution for x e under the constraint x e r in order to conduct further analysis. With regard to the impact of the localization error on the true location of the legitimate user, it is reasonable to assume that x e follows a zero-mean normal distribution with a covariance matrix determined by the localization error i.e., fx e ) = 0, Σ), where Σ is the covariance matrix associated with the localization error). We note that the assumption of normal distribution does not ensure x e r. We have checked numerically that this assumption does not significantly impact the results compared to the scenarios where x e r is actually imposed as an additional constraint. The main variation on our RSS-based and DRSS-based LVSs caused by the adoption of the generalized a priori knowledge model given in 60) involves the determination of the likelihood functions under H 0. Different from 5), in the RSS-based LVS the new likelihood function under H 0 based on 60) is given by f g y H 0 ) = f y x e, H 0 ) fx e )dx e, 6) x e x t = x c x t = x c +x e with normal x e x t = x c +x e with uniform x e False positive rate Fig. 6. ROC curves of the RSS-based LVS for σ db = 5, r = 00m, x t = [4.2, 83.9], D c = 50, Σ = diag{σ 2, σ2 2 }, σ = σ 2 = 20, and = 3 x = [0, 0], x 2 = [3.4, 9.3], and x 3 = [20.6, 0.9] ) where f y x e, H 0 ) can be obtained by replacing x c with x t in 5). Likewise, in the DRSS-based LVS the new likelihood function under H 0 based on 60) is given by f g y H 0 ) = f y x e, H 0 ) fx e )dx e, 62) x e where f y x e, H 0 ) can be obtained by replacing x c with x t in 40). Closed-from expressions for f g y H 0 ) and f g y H 0 ) are generally hard, if not impossible, to achieve. Therefore, we numerically calculate f g y H 0 ) and f g y H 0 ), and then evaluate the performances of the resultant RSS-based and DRSS-based LVSs by utilizing our previous theoretic analysis as the benchmark. The results of our numerical studies are provided in Fig. 6, where we adopt the RSS-based LVS as an example following Theorem 3 the results are valid for the DRSS-based LVS as well). We note that the curve for x t = x c is for the a priori model given in ), which is obtained from our previous analysis i.e., 32) and 33)). The curve for x t = x c + x e with normal x e is obtained by numerically calculating f g y H 0 ) given in 6) with fx e ) = 0, Σ), and the curve for x t = x c + x e with uniform x e is achieved through numerically evaluating f g y H 0 ) by assuming x e is uniformly distributed within the region determined by r. We refer to former case as the localization error and the latter as the exhaustive decision space. As expected, we observe that both the localization error and the exhaustive decision space reduce the detection performance of the RSS-based LVS. We also observe that the impact of the localization error is relatively weak even when the localization error is up to tens of meters i.e., σ = σ 2 = 20). Meanwhile, the effect of the exhaustive decision space is significant as a consequence of the adopted uniform distribution for x e. This is due to the fact that the possible true locations of the legitimate user are more
Location Verification Systems Under Spatially Correlated Shadowing
 Location Verification Systems Under Spatially Correlated Shadowing Shihao Yan, Ido evat, Gareth W. Peters, and Robert Malaney arxiv:4499v cs.it] 2 Oct 24 Abstract The verification of the location information
Location Verification Systems Under Spatially Correlated Shadowing Shihao Yan, Ido evat, Gareth W. Peters, and Robert Malaney arxiv:4499v cs.it] 2 Oct 24 Abstract The verification of the location information
SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM. Neal Patwari and Alfred O.
 SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM Neal Patwari and Alfred O. Hero III Department of Electrical Engineering & Computer Science University of
SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM Neal Patwari and Alfred O. Hero III Department of Electrical Engineering & Computer Science University of
Analysis of Random Radar Networks
 Analysis of Random Radar Networks Rani Daher, Ravira Adve Department of Electrical and Computer Engineering, University of Toronto 1 King s College Road, Toronto, ON M5S3G4 Email: rani.daher@utoronto.ca,
Analysis of Random Radar Networks Rani Daher, Ravira Adve Department of Electrical and Computer Engineering, University of Toronto 1 King s College Road, Toronto, ON M5S3G4 Email: rani.daher@utoronto.ca,
SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM. Neal Patwari and Alfred O.
 SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM Neal Patwari and Alfred O. Hero III Department of Electrical Engineering & Computer Science University of
SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM Neal Patwari and Alfred O. Hero III Department of Electrical Engineering & Computer Science University of
Novel spectrum sensing schemes for Cognitive Radio Networks
 Novel spectrum sensing schemes for Cognitive Radio Networks Cantabria University Santander, May, 2015 Supélec, SCEE Rennes, France 1 The Advanced Signal Processing Group http://gtas.unican.es The Advanced
Novel spectrum sensing schemes for Cognitive Radio Networks Cantabria University Santander, May, 2015 Supélec, SCEE Rennes, France 1 The Advanced Signal Processing Group http://gtas.unican.es The Advanced
INFORMATION PROCESSING ABILITY OF BINARY DETECTORS AND BLOCK DECODERS. Michael A. Lexa and Don H. Johnson
 INFORMATION PROCESSING ABILITY OF BINARY DETECTORS AND BLOCK DECODERS Michael A. Lexa and Don H. Johnson Rice University Department of Electrical and Computer Engineering Houston, TX 775-892 amlexa@rice.edu,
INFORMATION PROCESSING ABILITY OF BINARY DETECTORS AND BLOCK DECODERS Michael A. Lexa and Don H. Johnson Rice University Department of Electrical and Computer Engineering Houston, TX 775-892 amlexa@rice.edu,
False Discovery Rate Based Distributed Detection in the Presence of Byzantines
 IEEE TRANSACTIONS ON AEROSPACE AND ELECTRONIC SYSTEMS () 1 False Discovery Rate Based Distributed Detection in the Presence of Byzantines Aditya Vempaty*, Student Member, IEEE, Priyadip Ray, Member, IEEE,
IEEE TRANSACTIONS ON AEROSPACE AND ELECTRONIC SYSTEMS () 1 False Discovery Rate Based Distributed Detection in the Presence of Byzantines Aditya Vempaty*, Student Member, IEEE, Priyadip Ray, Member, IEEE,
UNIFORMLY MOST POWERFUL CYCLIC PERMUTATION INVARIANT DETECTION FOR DISCRETE-TIME SIGNALS
 UNIFORMLY MOST POWERFUL CYCLIC PERMUTATION INVARIANT DETECTION FOR DISCRETE-TIME SIGNALS F. C. Nicolls and G. de Jager Department of Electrical Engineering, University of Cape Town Rondebosch 77, South
UNIFORMLY MOST POWERFUL CYCLIC PERMUTATION INVARIANT DETECTION FOR DISCRETE-TIME SIGNALS F. C. Nicolls and G. de Jager Department of Electrical Engineering, University of Cape Town Rondebosch 77, South
User Association with Unequal User Priorities in Heterogeneous Cellular Networks
 User Association with Unequal User Priorities in Heterogeneous Cellular Networks Youjia Chen, Jun Li, Member, IEEE, Zihuai Lin, Senior Member, IEEE, Guoqiang Mao, Senior Member, IEEE, and Branka Vucetic,
User Association with Unequal User Priorities in Heterogeneous Cellular Networks Youjia Chen, Jun Li, Member, IEEE, Zihuai Lin, Senior Member, IEEE, Guoqiang Mao, Senior Member, IEEE, and Branka Vucetic,
Binary Compressive Sensing via Analog. Fountain Coding
 Binary Compressive Sensing via Analog 1 Fountain Coding Mahyar Shirvanimoghaddam, Member, IEEE, Yonghui Li, Senior Member, IEEE, Branka Vucetic, Fellow, IEEE, and Jinhong Yuan, Senior Member, IEEE, arxiv:1508.03401v1
Binary Compressive Sensing via Analog 1 Fountain Coding Mahyar Shirvanimoghaddam, Member, IEEE, Yonghui Li, Senior Member, IEEE, Branka Vucetic, Fellow, IEEE, and Jinhong Yuan, Senior Member, IEEE, arxiv:1508.03401v1
Composite Hypotheses and Generalized Likelihood Ratio Tests
 Composite Hypotheses and Generalized Likelihood Ratio Tests Rebecca Willett, 06 In many real world problems, it is difficult to precisely specify probability distributions. Our models for data may involve
Composite Hypotheses and Generalized Likelihood Ratio Tests Rebecca Willett, 06 In many real world problems, it is difficult to precisely specify probability distributions. Our models for data may involve
2. What are the tradeoffs among different measures of error (e.g. probability of false alarm, probability of miss, etc.)?
 ECE 830 / CS 76 Spring 06 Instructors: R. Willett & R. Nowak Lecture 3: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we
ECE 830 / CS 76 Spring 06 Instructors: R. Willett & R. Nowak Lecture 3: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we
Transmission Schemes for Lifetime Maximization in Wireless Sensor Networks: Uncorrelated Source Observations
 Transmission Schemes for Lifetime Maximization in Wireless Sensor Networks: Uncorrelated Source Observations Xiaolu Zhang, Meixia Tao and Chun Sum Ng Department of Electrical and Computer Engineering National
Transmission Schemes for Lifetime Maximization in Wireless Sensor Networks: Uncorrelated Source Observations Xiaolu Zhang, Meixia Tao and Chun Sum Ng Department of Electrical and Computer Engineering National
A Note on Auxiliary Particle Filters
 A Note on Auxiliary Particle Filters Adam M. Johansen a,, Arnaud Doucet b a Department of Mathematics, University of Bristol, UK b Departments of Statistics & Computer Science, University of British Columbia,
A Note on Auxiliary Particle Filters Adam M. Johansen a,, Arnaud Doucet b a Department of Mathematics, University of Bristol, UK b Departments of Statistics & Computer Science, University of British Columbia,
PATTERN RECOGNITION AND MACHINE LEARNING
 PATTERN RECOGNITION AND MACHINE LEARNING Chapter 1. Introduction Shuai Huang April 21, 2014 Outline 1 What is Machine Learning? 2 Curve Fitting 3 Probability Theory 4 Model Selection 5 The curse of dimensionality
PATTERN RECOGNITION AND MACHINE LEARNING Chapter 1. Introduction Shuai Huang April 21, 2014 Outline 1 What is Machine Learning? 2 Curve Fitting 3 Probability Theory 4 Model Selection 5 The curse of dimensionality
ADAPTIVE CLUSTERING ALGORITHM FOR COOPERATIVE SPECTRUM SENSING IN MOBILE ENVIRONMENTS. Jesus Perez and Ignacio Santamaria
 ADAPTIVE CLUSTERING ALGORITHM FOR COOPERATIVE SPECTRUM SENSING IN MOBILE ENVIRONMENTS Jesus Perez and Ignacio Santamaria Advanced Signal Processing Group, University of Cantabria, Spain, https://gtas.unican.es/
ADAPTIVE CLUSTERING ALGORITHM FOR COOPERATIVE SPECTRUM SENSING IN MOBILE ENVIRONMENTS Jesus Perez and Ignacio Santamaria Advanced Signal Processing Group, University of Cantabria, Spain, https://gtas.unican.es/
Novel Distributed Spectrum Sensing Techniques for Cognitive Radio Networks
 28 IEEE Wireless Communications and Networking Conference (WCNC) Novel Distributed Spectrum Sensing Techniques for Cognitive Radio Networks Peter J. Smith, Rajitha Senanayake, Pawel A. Dmochowski and Jamie
28 IEEE Wireless Communications and Networking Conference (WCNC) Novel Distributed Spectrum Sensing Techniques for Cognitive Radio Networks Peter J. Smith, Rajitha Senanayake, Pawel A. Dmochowski and Jamie
Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics. 1 Executive summary
 ECE 830 Spring 207 Instructor: R. Willett Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we saw that the likelihood
ECE 830 Spring 207 Instructor: R. Willett Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we saw that the likelihood
Introduction. Chapter 1
 Chapter 1 Introduction In this book we will be concerned with supervised learning, which is the problem of learning input-output mappings from empirical data (the training dataset). Depending on the characteristics
Chapter 1 Introduction In this book we will be concerned with supervised learning, which is the problem of learning input-output mappings from empirical data (the training dataset). Depending on the characteristics
Diversity Performance of a Practical Non-Coherent Detect-and-Forward Receiver
 Diversity Performance of a Practical Non-Coherent Detect-and-Forward Receiver Michael R. Souryal and Huiqing You National Institute of Standards and Technology Advanced Network Technologies Division Gaithersburg,
Diversity Performance of a Practical Non-Coherent Detect-and-Forward Receiver Michael R. Souryal and Huiqing You National Institute of Standards and Technology Advanced Network Technologies Division Gaithersburg,
Chapter 2 Signal Processing at Receivers: Detection Theory
 Chapter Signal Processing at Receivers: Detection Theory As an application of the statistical hypothesis testing, signal detection plays a key role in signal processing at receivers of wireless communication
Chapter Signal Processing at Receivers: Detection Theory As an application of the statistical hypothesis testing, signal detection plays a key role in signal processing at receivers of wireless communication
Cell throughput analysis of the Proportional Fair scheduler in the single cell environment
 Cell throughput analysis of the Proportional Fair scheduler in the single cell environment Jin-Ghoo Choi and Seawoong Bahk IEEE Trans on Vehicular Tech, Mar 2007 *** Presented by: Anh H. Nguyen February
Cell throughput analysis of the Proportional Fair scheduler in the single cell environment Jin-Ghoo Choi and Seawoong Bahk IEEE Trans on Vehicular Tech, Mar 2007 *** Presented by: Anh H. Nguyen February
Distributed Detection of Binary Decisions with Collisions in a Large, Random Network
 Distributed Detection of Binary Decisions with Collisions in a Large, Random Network Gene T Whipps, Emre Ertin, and Randolph L Moses US Army Research Laboratory, Adelphi, MD 2783 Department of Electrical
Distributed Detection of Binary Decisions with Collisions in a Large, Random Network Gene T Whipps, Emre Ertin, and Randolph L Moses US Army Research Laboratory, Adelphi, MD 2783 Department of Electrical
Chapter 2. Binary and M-ary Hypothesis Testing 2.1 Introduction (Levy 2.1)
 Chapter 2. Binary and M-ary Hypothesis Testing 2.1 Introduction (Levy 2.1) Detection problems can usually be casted as binary or M-ary hypothesis testing problems. Applications: This chapter: Simple hypothesis
Chapter 2. Binary and M-ary Hypothesis Testing 2.1 Introduction (Levy 2.1) Detection problems can usually be casted as binary or M-ary hypothesis testing problems. Applications: This chapter: Simple hypothesis
Distributed Detection and Estimation in Wireless Sensor Networks: Resource Allocation, Fusion Rules, and Network Security
 Distributed Detection and Estimation in Wireless Sensor Networks: Resource Allocation, Fusion Rules, and Network Security Edmond Nurellari The University of Leeds, UK School of Electronic and Electrical
Distributed Detection and Estimation in Wireless Sensor Networks: Resource Allocation, Fusion Rules, and Network Security Edmond Nurellari The University of Leeds, UK School of Electronic and Electrical
Target Tracking and Classification using Collaborative Sensor Networks
 Target Tracking and Classification using Collaborative Sensor Networks Xiaodong Wang Department of Electrical Engineering Columbia University p.1/3 Talk Outline Background on distributed wireless sensor
Target Tracking and Classification using Collaborative Sensor Networks Xiaodong Wang Department of Electrical Engineering Columbia University p.1/3 Talk Outline Background on distributed wireless sensor
EUSIPCO
 EUSIPCO 3 569736677 FULLY ISTRIBUTE SIGNAL ETECTION: APPLICATION TO COGNITIVE RAIO Franc Iutzeler Philippe Ciblat Telecom ParisTech, 46 rue Barrault 753 Paris, France email: firstnamelastname@telecom-paristechfr
EUSIPCO 3 569736677 FULLY ISTRIBUTE SIGNAL ETECTION: APPLICATION TO COGNITIVE RAIO Franc Iutzeler Philippe Ciblat Telecom ParisTech, 46 rue Barrault 753 Paris, France email: firstnamelastname@telecom-paristechfr
Power Allocation and Coverage for a Relay-Assisted Downlink with Voice Users
 Power Allocation and Coverage for a Relay-Assisted Downlink with Voice Users Junjik Bae, Randall Berry, and Michael L. Honig Department of Electrical Engineering and Computer Science Northwestern University,
Power Allocation and Coverage for a Relay-Assisted Downlink with Voice Users Junjik Bae, Randall Berry, and Michael L. Honig Department of Electrical Engineering and Computer Science Northwestern University,
Diffusion based Projection Method for Distributed Source Localization in Wireless Sensor Networks
 The Third International Workshop on Wireless Sensor, Actuator and Robot Networks Diffusion based Projection Method for Distributed Source Localization in Wireless Sensor Networks Wei Meng 1, Wendong Xiao,
The Third International Workshop on Wireless Sensor, Actuator and Robot Networks Diffusion based Projection Method for Distributed Source Localization in Wireless Sensor Networks Wei Meng 1, Wendong Xiao,
Collaborative Localization Using Weighted Centroid Localization (WCL) Algorithm in CR Networks
 Collaborative Localization Using Weighted Centroid Localization (WCL) Algorithm in CR Networks Simulation and Theoretical Results Jun Wang Paulo Urriza Prof. Danijela Čabrić UCLA CORES Lab March 12, 2010
Collaborative Localization Using Weighted Centroid Localization (WCL) Algorithm in CR Networks Simulation and Theoretical Results Jun Wang Paulo Urriza Prof. Danijela Čabrić UCLA CORES Lab March 12, 2010
Lecture 12 November 3
 STATS 300A: Theory of Statistics Fall 2015 Lecture 12 November 3 Lecturer: Lester Mackey Scribe: Jae Hyuck Park, Christian Fong Warning: These notes may contain factual and/or typographic errors. 12.1
STATS 300A: Theory of Statistics Fall 2015 Lecture 12 November 3 Lecturer: Lester Mackey Scribe: Jae Hyuck Park, Christian Fong Warning: These notes may contain factual and/or typographic errors. 12.1
Applications of Robust Optimization in Signal Processing: Beamforming and Power Control Fall 2012
 Applications of Robust Optimization in Signal Processing: Beamforg and Power Control Fall 2012 Instructor: Farid Alizadeh Scribe: Shunqiao Sun 12/09/2012 1 Overview In this presentation, we study the applications
Applications of Robust Optimization in Signal Processing: Beamforg and Power Control Fall 2012 Instructor: Farid Alizadeh Scribe: Shunqiao Sun 12/09/2012 1 Overview In this presentation, we study the applications
Lecture 7. Union bound for reducing M-ary to binary hypothesis testing
 Lecture 7 Agenda for the lecture M-ary hypothesis testing and the MAP rule Union bound for reducing M-ary to binary hypothesis testing Introduction of the channel coding problem 7.1 M-ary hypothesis testing
Lecture 7 Agenda for the lecture M-ary hypothesis testing and the MAP rule Union bound for reducing M-ary to binary hypothesis testing Introduction of the channel coding problem 7.1 M-ary hypothesis testing
Transmitter-Receiver Cooperative Sensing in MIMO Cognitive Network with Limited Feedback
 IEEE INFOCOM Workshop On Cognitive & Cooperative Networks Transmitter-Receiver Cooperative Sensing in MIMO Cognitive Network with Limited Feedback Chao Wang, Zhaoyang Zhang, Xiaoming Chen, Yuen Chau. Dept.of
IEEE INFOCOM Workshop On Cognitive & Cooperative Networks Transmitter-Receiver Cooperative Sensing in MIMO Cognitive Network with Limited Feedback Chao Wang, Zhaoyang Zhang, Xiaoming Chen, Yuen Chau. Dept.of
STONY BROOK UNIVERSITY. CEAS Technical Report 829
 1 STONY BROOK UNIVERSITY CEAS Technical Report 829 Variable and Multiple Target Tracking by Particle Filtering and Maximum Likelihood Monte Carlo Method Jaechan Lim January 4, 2006 2 Abstract In most applications
1 STONY BROOK UNIVERSITY CEAS Technical Report 829 Variable and Multiple Target Tracking by Particle Filtering and Maximum Likelihood Monte Carlo Method Jaechan Lim January 4, 2006 2 Abstract In most applications
On the errors introduced by the naive Bayes independence assumption
 On the errors introduced by the naive Bayes independence assumption Author Matthijs de Wachter 3671100 Utrecht University Master Thesis Artificial Intelligence Supervisor Dr. Silja Renooij Department of
On the errors introduced by the naive Bayes independence assumption Author Matthijs de Wachter 3671100 Utrecht University Master Thesis Artificial Intelligence Supervisor Dr. Silja Renooij Department of
Spectrum Sensing under Spectrum Misuse Behaviors: A Multi-Hypothesis Test Perspective
 ............ Spectrum Sensing under Spectrum Misuse Behaviors: A Multi-Hypothesis Test Perspective Linyuan Zhang, Guoru Ding, Senior Member, IEEE, Qihui Wu, Senior Member, IEEE, and Zhu Han, Fellow, IEEE
............ Spectrum Sensing under Spectrum Misuse Behaviors: A Multi-Hypothesis Test Perspective Linyuan Zhang, Guoru Ding, Senior Member, IEEE, Qihui Wu, Senior Member, IEEE, and Zhu Han, Fellow, IEEE
Regression. Oscar García
 Regression Oscar García Regression methods are fundamental in Forest Mensuration For a more concise and general presentation, we shall first review some matrix concepts 1 Matrices An order n m matrix is
Regression Oscar García Regression methods are fundamental in Forest Mensuration For a more concise and general presentation, we shall first review some matrix concepts 1 Matrices An order n m matrix is
Data Gathering and Personalized Broadcasting in Radio Grids with Interferences
 Data Gathering and Personalized Broadcasting in Radio Grids with Interferences Jean-Claude Bermond a,, Bi Li a,b, Nicolas Nisse a, Hervé Rivano c, Min-Li Yu d a Coati Project, INRIA I3S(CNRS/UNSA), Sophia
Data Gathering and Personalized Broadcasting in Radio Grids with Interferences Jean-Claude Bermond a,, Bi Li a,b, Nicolas Nisse a, Hervé Rivano c, Min-Li Yu d a Coati Project, INRIA I3S(CNRS/UNSA), Sophia
A Signal-Space Analysis of Spatial Self-Interference Isolation for Full-Duplex Wireless
 A Signal-Space Analysis of Spatial Self-Interference Isolation for Full-Duplex Wireless Evan Everett Rice University Ashutosh Sabharwal Rice University Abstract The challenge to in-band full-duplex wireless
A Signal-Space Analysis of Spatial Self-Interference Isolation for Full-Duplex Wireless Evan Everett Rice University Ashutosh Sabharwal Rice University Abstract The challenge to in-band full-duplex wireless
Distributed Spectrum Sensing for Cognitive Radio Networks Based on the Sphericity Test
 This article h been accepted for publication in a future issue of this journal, but h not been fully edited. Content may change prior to final publication. Citation information: DOI 0.09/TCOMM.208.2880902,
This article h been accepted for publication in a future issue of this journal, but h not been fully edited. Content may change prior to final publication. Citation information: DOI 0.09/TCOMM.208.2880902,
Achieving Covert Wireless Communications Using a Full-Duplex Receiver
 IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS 1 Achieving Covert Wireless Communications Using a Full-Duplex Receiver Khurram Shahzad, Student Member, IEEE, Xiangyun Zhou, Senior Member, IEEE, Shihao Yan,
IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS 1 Achieving Covert Wireless Communications Using a Full-Duplex Receiver Khurram Shahzad, Student Member, IEEE, Xiangyun Zhou, Senior Member, IEEE, Shihao Yan,
PERFECTLY secure key agreement has been studied recently
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 45, NO. 2, MARCH 1999 499 Unconditionally Secure Key Agreement the Intrinsic Conditional Information Ueli M. Maurer, Senior Member, IEEE, Stefan Wolf Abstract
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 45, NO. 2, MARCH 1999 499 Unconditionally Secure Key Agreement the Intrinsic Conditional Information Ueli M. Maurer, Senior Member, IEEE, Stefan Wolf Abstract
A Framework for Optimizing Nonlinear Collusion Attacks on Fingerprinting Systems
 A Framework for Optimizing onlinear Collusion Attacks on Fingerprinting Systems egar iyavash Department of Electrical and Computer Engineering University of Illinois at Urbana-Champaign Coordinated Science
A Framework for Optimizing onlinear Collusion Attacks on Fingerprinting Systems egar iyavash Department of Electrical and Computer Engineering University of Illinois at Urbana-Champaign Coordinated Science
Mathematical Statistics
 Mathematical Statistics MAS 713 Chapter 8 Previous lecture: 1 Bayesian Inference 2 Decision theory 3 Bayesian Vs. Frequentist 4 Loss functions 5 Conjugate priors Any questions? Mathematical Statistics
Mathematical Statistics MAS 713 Chapter 8 Previous lecture: 1 Bayesian Inference 2 Decision theory 3 Bayesian Vs. Frequentist 4 Loss functions 5 Conjugate priors Any questions? Mathematical Statistics
Distributed power allocation for D2D communications underlaying/overlaying OFDMA cellular networks
 Distributed power allocation for D2D communications underlaying/overlaying OFDMA cellular networks Marco Moretti, Andrea Abrardo Dipartimento di Ingegneria dell Informazione, University of Pisa, Italy
Distributed power allocation for D2D communications underlaying/overlaying OFDMA cellular networks Marco Moretti, Andrea Abrardo Dipartimento di Ingegneria dell Informazione, University of Pisa, Italy
Degrees-of-Freedom for the 4-User SISO Interference Channel with Improper Signaling
 Degrees-of-Freedom for the -User SISO Interference Channel with Improper Signaling C Lameiro and I Santamaría Dept of Communications Engineering University of Cantabria 9005 Santander Cantabria Spain Email:
Degrees-of-Freedom for the -User SISO Interference Channel with Improper Signaling C Lameiro and I Santamaría Dept of Communications Engineering University of Cantabria 9005 Santander Cantabria Spain Email:
10. Composite Hypothesis Testing. ECE 830, Spring 2014
 10. Composite Hypothesis Testing ECE 830, Spring 2014 1 / 25 In many real world problems, it is difficult to precisely specify probability distributions. Our models for data may involve unknown parameters
10. Composite Hypothesis Testing ECE 830, Spring 2014 1 / 25 In many real world problems, it is difficult to precisely specify probability distributions. Our models for data may involve unknown parameters
EECS564 Estimation, Filtering, and Detection Exam 2 Week of April 20, 2015
 EECS564 Estimation, Filtering, and Detection Exam Week of April 0, 015 This is an open book takehome exam. You have 48 hours to complete the exam. All work on the exam should be your own. problems have
EECS564 Estimation, Filtering, and Detection Exam Week of April 0, 015 This is an open book takehome exam. You have 48 hours to complete the exam. All work on the exam should be your own. problems have
Statistics for the LHC Lecture 1: Introduction
 Statistics for the LHC Lecture 1: Introduction Academic Training Lectures CERN, 14 17 June, 2010 indico.cern.ch/conferencedisplay.py?confid=77830 Glen Cowan Physics Department Royal Holloway, University
Statistics for the LHC Lecture 1: Introduction Academic Training Lectures CERN, 14 17 June, 2010 indico.cern.ch/conferencedisplay.py?confid=77830 Glen Cowan Physics Department Royal Holloway, University
Performance Analysis of a Threshold-Based Relay Selection Algorithm in Wireless Networks
 Communications and Networ, 2010, 2, 87-92 doi:10.4236/cn.2010.22014 Published Online May 2010 (http://www.scirp.org/journal/cn Performance Analysis of a Threshold-Based Relay Selection Algorithm in Wireless
Communications and Networ, 2010, 2, 87-92 doi:10.4236/cn.2010.22014 Published Online May 2010 (http://www.scirp.org/journal/cn Performance Analysis of a Threshold-Based Relay Selection Algorithm in Wireless
Statistical Modeling of Co-Channel Interference
 Statistical Modeling of Co-Channel Interference Kapil Gulati, Aditya Chopra, Brian L. Evans and Keith R. Tinsley The University of Texas at Austin, Austin, Texas 7871 Email: gulati,chopra,bevans}@ece.utexas.edu
Statistical Modeling of Co-Channel Interference Kapil Gulati, Aditya Chopra, Brian L. Evans and Keith R. Tinsley The University of Texas at Austin, Austin, Texas 7871 Email: gulati,chopra,bevans}@ece.utexas.edu
A Statistical Kirchhoff Model for EM Scattering from Gaussian Rough Surface
 Progress In Electromagnetics Research Symposium 2005, Hangzhou, China, August 22-26 187 A Statistical Kirchhoff Model for EM Scattering from Gaussian Rough Surface Yang Du 1, Tao Xu 1, Yingliang Luo 1,
Progress In Electromagnetics Research Symposium 2005, Hangzhou, China, August 22-26 187 A Statistical Kirchhoff Model for EM Scattering from Gaussian Rough Surface Yang Du 1, Tao Xu 1, Yingliang Luo 1,
Scalable robust hypothesis tests using graphical models
 Scalable robust hypothesis tests using graphical models Umamahesh Srinivas ipal Group Meeting October 22, 2010 Binary hypothesis testing problem Random vector x = (x 1,...,x n ) R n generated from either
Scalable robust hypothesis tests using graphical models Umamahesh Srinivas ipal Group Meeting October 22, 2010 Binary hypothesis testing problem Random vector x = (x 1,...,x n ) R n generated from either
Optimal Geographical Caching in Heterogeneous Cellular Networks
 1 Optimal Geographical Caching in Heterogeneous Cellular Networks Berksan Serbetci, and Jasper Goseling arxiv:1710.09626v2 [cs.ni] 22 Nov 2018 Abstract We investigate optimal geographical caching in heterogeneous
1 Optimal Geographical Caching in Heterogeneous Cellular Networks Berksan Serbetci, and Jasper Goseling arxiv:1710.09626v2 [cs.ni] 22 Nov 2018 Abstract We investigate optimal geographical caching in heterogeneous
Introduction to Machine Learning CMU-10701
 Introduction to Machine Learning CMU-10701 Markov Chain Monte Carlo Methods Barnabás Póczos & Aarti Singh Contents Markov Chain Monte Carlo Methods Goal & Motivation Sampling Rejection Importance Markov
Introduction to Machine Learning CMU-10701 Markov Chain Monte Carlo Methods Barnabás Póczos & Aarti Singh Contents Markov Chain Monte Carlo Methods Goal & Motivation Sampling Rejection Importance Markov
Selective Hybrid RSS/AOA Approximate Maximum Likelihood Mobile intra cell Localization
 Selective Hybrid RSS/AOA Approximate Maximum Likelihood Mobile intra cell Localization Leila Gazzah Leila Najjar and Hichem Besbes Carthage University Lab. COSIM Higher School of Communication of Tunis
Selective Hybrid RSS/AOA Approximate Maximum Likelihood Mobile intra cell Localization Leila Gazzah Leila Najjar and Hichem Besbes Carthage University Lab. COSIM Higher School of Communication of Tunis
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 2, FEBRUARY Uplink Downlink Duality Via Minimax Duality. Wei Yu, Member, IEEE (1) (2)
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 2, FEBRUARY 2006 361 Uplink Downlink Duality Via Minimax Duality Wei Yu, Member, IEEE Abstract The sum capacity of a Gaussian vector broadcast channel
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 2, FEBRUARY 2006 361 Uplink Downlink Duality Via Minimax Duality Wei Yu, Member, IEEE Abstract The sum capacity of a Gaussian vector broadcast channel
Effective Rate Analysis of MISO Systems over α-µ Fading Channels
 Effective Rate Analysis of MISO Systems over α-µ Fading Channels Jiayi Zhang 1,2, Linglong Dai 1, Zhaocheng Wang 1 Derrick Wing Kwan Ng 2,3 and Wolfgang H. Gerstacker 2 1 Tsinghua National Laboratory for
Effective Rate Analysis of MISO Systems over α-µ Fading Channels Jiayi Zhang 1,2, Linglong Dai 1, Zhaocheng Wang 1 Derrick Wing Kwan Ng 2,3 and Wolfgang H. Gerstacker 2 1 Tsinghua National Laboratory for
Optimal Power Allocation for Cognitive Radio under Primary User s Outage Loss Constraint
 This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE ICC 29 proceedings Optimal Power Allocation for Cognitive Radio
This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE ICC 29 proceedings Optimal Power Allocation for Cognitive Radio
certain class of distributions, any SFQ can be expressed as a set of thresholds on the sufficient statistic. For distributions
 Score-Function Quantization for Distributed Estimation Parvathinathan Venkitasubramaniam and Lang Tong School of Electrical and Computer Engineering Cornell University Ithaca, NY 4853 Email: {pv45, lt35}@cornell.edu
Score-Function Quantization for Distributed Estimation Parvathinathan Venkitasubramaniam and Lang Tong School of Electrical and Computer Engineering Cornell University Ithaca, NY 4853 Email: {pv45, lt35}@cornell.edu
Cheng Soon Ong & Christian Walder. Canberra February June 2018
 Cheng Soon Ong & Christian Walder Research Group and College of Engineering and Computer Science Canberra February June 2018 (Many figures from C. M. Bishop, "Pattern Recognition and ") 1of 89 Part II
Cheng Soon Ong & Christian Walder Research Group and College of Engineering and Computer Science Canberra February June 2018 (Many figures from C. M. Bishop, "Pattern Recognition and ") 1of 89 Part II
Stochastic Spectral Approaches to Bayesian Inference
 Stochastic Spectral Approaches to Bayesian Inference Prof. Nathan L. Gibson Department of Mathematics Applied Mathematics and Computation Seminar March 4, 2011 Prof. Gibson (OSU) Spectral Approaches to
Stochastic Spectral Approaches to Bayesian Inference Prof. Nathan L. Gibson Department of Mathematics Applied Mathematics and Computation Seminar March 4, 2011 Prof. Gibson (OSU) Spectral Approaches to
Digital Transmission Methods S
 Digital ransmission ethods S-7.5 Second Exercise Session Hypothesis esting Decision aking Gram-Schmidt method Detection.K.K. Communication Laboratory 5//6 Konstantinos.koufos@tkk.fi Exercise We assume
Digital ransmission ethods S-7.5 Second Exercise Session Hypothesis esting Decision aking Gram-Schmidt method Detection.K.K. Communication Laboratory 5//6 Konstantinos.koufos@tkk.fi Exercise We assume
Propagation of Errors in Spatial Analysis
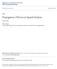 Stephen F. Austin State University SFA ScholarWorks Faculty Presentations Spatial Science 2001 Propagation of Errors in Spatial Analysis Peter P. Siska I-Kuai Hung Arthur Temple College of Forestry and
Stephen F. Austin State University SFA ScholarWorks Faculty Presentations Spatial Science 2001 Propagation of Errors in Spatial Analysis Peter P. Siska I-Kuai Hung Arthur Temple College of Forestry and
Series 7, May 22, 2018 (EM Convergence)
 Exercises Introduction to Machine Learning SS 2018 Series 7, May 22, 2018 (EM Convergence) Institute for Machine Learning Dept. of Computer Science, ETH Zürich Prof. Dr. Andreas Krause Web: https://las.inf.ethz.ch/teaching/introml-s18
Exercises Introduction to Machine Learning SS 2018 Series 7, May 22, 2018 (EM Convergence) Institute for Machine Learning Dept. of Computer Science, ETH Zürich Prof. Dr. Andreas Krause Web: https://las.inf.ethz.ch/teaching/introml-s18
Sensor Tasking and Control
 Sensor Tasking and Control Sensing Networking Leonidas Guibas Stanford University Computation CS428 Sensor systems are about sensing, after all... System State Continuous and Discrete Variables The quantities
Sensor Tasking and Control Sensing Networking Leonidas Guibas Stanford University Computation CS428 Sensor systems are about sensing, after all... System State Continuous and Discrete Variables The quantities
Economics 520. Lecture Note 19: Hypothesis Testing via the Neyman-Pearson Lemma CB 8.1,
 Economics 520 Lecture Note 9: Hypothesis Testing via the Neyman-Pearson Lemma CB 8., 8.3.-8.3.3 Uniformly Most Powerful Tests and the Neyman-Pearson Lemma Let s return to the hypothesis testing problem
Economics 520 Lecture Note 9: Hypothesis Testing via the Neyman-Pearson Lemma CB 8., 8.3.-8.3.3 Uniformly Most Powerful Tests and the Neyman-Pearson Lemma Let s return to the hypothesis testing problem
Detection and Estimation Final Project Report: Modeling and the K-Sigma Algorithm for Radiation Detection
 Detection and Estimation Final Project Report: Modeling and the K-Sigma Algorithm for Radiation Detection Sijie Xiong, 151004243 Department of Electrical and Computer Engineering Rutgers, the State University
Detection and Estimation Final Project Report: Modeling and the K-Sigma Algorithm for Radiation Detection Sijie Xiong, 151004243 Department of Electrical and Computer Engineering Rutgers, the State University
Problem Set 7 Due March, 22
 EE16: Probability and Random Processes SP 07 Problem Set 7 Due March, Lecturer: Jean C. Walrand GSI: Daniel Preda, Assane Gueye Problem 7.1. Let u and v be independent, standard normal random variables
EE16: Probability and Random Processes SP 07 Problem Set 7 Due March, Lecturer: Jean C. Walrand GSI: Daniel Preda, Assane Gueye Problem 7.1. Let u and v be independent, standard normal random variables
Game Theoretic Approach to Power Control in Cellular CDMA
 Game Theoretic Approach to Power Control in Cellular CDMA Sarma Gunturi Texas Instruments(India) Bangalore - 56 7, INDIA Email : gssarma@ticom Fernando Paganini Electrical Engineering Department University
Game Theoretic Approach to Power Control in Cellular CDMA Sarma Gunturi Texas Instruments(India) Bangalore - 56 7, INDIA Email : gssarma@ticom Fernando Paganini Electrical Engineering Department University
ROBUST BLIND CALIBRATION VIA TOTAL LEAST SQUARES
 ROBUST BLIND CALIBRATION VIA TOTAL LEAST SQUARES John Lipor Laura Balzano University of Michigan, Ann Arbor Department of Electrical and Computer Engineering {lipor,girasole}@umich.edu ABSTRACT This paper
ROBUST BLIND CALIBRATION VIA TOTAL LEAST SQUARES John Lipor Laura Balzano University of Michigan, Ann Arbor Department of Electrical and Computer Engineering {lipor,girasole}@umich.edu ABSTRACT This paper
Improved High-Order Conversion From Boolean to Arithmetic Masking
 Improved High-Order Conversion From Boolean to Arithmetic Masking Luk Bettale 1, Jean-Sébastien Coron 2, and Rina Zeitoun 1 1 IDEMIA, France luk.bettale@idemia.com, rina.zeitoun@idemia.com 2 University
Improved High-Order Conversion From Boolean to Arithmetic Masking Luk Bettale 1, Jean-Sébastien Coron 2, and Rina Zeitoun 1 1 IDEMIA, France luk.bettale@idemia.com, rina.zeitoun@idemia.com 2 University
PCA with random noise. Van Ha Vu. Department of Mathematics Yale University
 PCA with random noise Van Ha Vu Department of Mathematics Yale University An important problem that appears in various areas of applied mathematics (in particular statistics, computer science and numerical
PCA with random noise Van Ha Vu Department of Mathematics Yale University An important problem that appears in various areas of applied mathematics (in particular statistics, computer science and numerical
Data Gathering and Personalized Broadcasting in Radio Grids with Interferences
 Data Gathering and Personalized Broadcasting in Radio Grids with Interferences Jean-Claude Bermond a,b,, Bi Li b,a,c, Nicolas Nisse b,a, Hervé Rivano d, Min-Li Yu e a Univ. Nice Sophia Antipolis, CNRS,
Data Gathering and Personalized Broadcasting in Radio Grids with Interferences Jean-Claude Bermond a,b,, Bi Li b,a,c, Nicolas Nisse b,a, Hervé Rivano d, Min-Li Yu e a Univ. Nice Sophia Antipolis, CNRS,
Wideband Fading Channel Capacity with Training and Partial Feedback
 Wideband Fading Channel Capacity with Training and Partial Feedback Manish Agarwal, Michael L. Honig ECE Department, Northwestern University 145 Sheridan Road, Evanston, IL 6008 USA {m-agarwal,mh}@northwestern.edu
Wideband Fading Channel Capacity with Training and Partial Feedback Manish Agarwal, Michael L. Honig ECE Department, Northwestern University 145 Sheridan Road, Evanston, IL 6008 USA {m-agarwal,mh}@northwestern.edu
Physics 403. Segev BenZvi. Choosing Priors and the Principle of Maximum Entropy. Department of Physics and Astronomy University of Rochester
 Physics 403 Choosing Priors and the Principle of Maximum Entropy Segev BenZvi Department of Physics and Astronomy University of Rochester Table of Contents 1 Review of Last Class Odds Ratio Occam Factors
Physics 403 Choosing Priors and the Principle of Maximum Entropy Segev BenZvi Department of Physics and Astronomy University of Rochester Table of Contents 1 Review of Last Class Odds Ratio Occam Factors
An Algorithmist s Toolkit Nov. 10, Lecture 17
 8.409 An Algorithmist s Toolkit Nov. 0, 009 Lecturer: Jonathan Kelner Lecture 7 Johnson-Lindenstrauss Theorem. Recap We first recap a theorem (isoperimetric inequality) and a lemma (concentration) from
8.409 An Algorithmist s Toolkit Nov. 0, 009 Lecturer: Jonathan Kelner Lecture 7 Johnson-Lindenstrauss Theorem. Recap We first recap a theorem (isoperimetric inequality) and a lemma (concentration) from
Wireless Network Security Spring 2016
 Wireless Network Security Spring 2016 Patrick Tague Class #19 Vehicular Network Security & Privacy 2016 Patrick Tague 1 Class #19 Review of some vehicular network stuff How wireless attacks affect vehicle
Wireless Network Security Spring 2016 Patrick Tague Class #19 Vehicular Network Security & Privacy 2016 Patrick Tague 1 Class #19 Review of some vehicular network stuff How wireless attacks affect vehicle
Aerial Anchors Positioning for Reliable RSS-Based Outdoor Localization in Urban Environments
 1 Aerial Anchors Positioning for Reliable RSS-Based Outdoor Localization in Urban Environments Hazem Sallouha, Mohammad Mahdi Azari, Alessandro Chiumento, Sofie Pollin arxiv:1711.06014v2 [cs.ni] 5 Dec
1 Aerial Anchors Positioning for Reliable RSS-Based Outdoor Localization in Urban Environments Hazem Sallouha, Mohammad Mahdi Azari, Alessandro Chiumento, Sofie Pollin arxiv:1711.06014v2 [cs.ni] 5 Dec
Cooperative Spectrum Sensing for Cognitive Radios under Bandwidth Constraints
 Cooperative Spectrum Sensing for Cognitive Radios under Bandwidth Constraints Chunhua Sun, Wei Zhang, and haled Ben Letaief, Fellow, IEEE Department of Electronic and Computer Engineering The Hong ong
Cooperative Spectrum Sensing for Cognitive Radios under Bandwidth Constraints Chunhua Sun, Wei Zhang, and haled Ben Letaief, Fellow, IEEE Department of Electronic and Computer Engineering The Hong ong
Learning with Rejection
 Learning with Rejection Corinna Cortes 1, Giulia DeSalvo 2, and Mehryar Mohri 2,1 1 Google Research, 111 8th Avenue, New York, NY 2 Courant Institute of Mathematical Sciences, 251 Mercer Street, New York,
Learning with Rejection Corinna Cortes 1, Giulia DeSalvo 2, and Mehryar Mohri 2,1 1 Google Research, 111 8th Avenue, New York, NY 2 Courant Institute of Mathematical Sciences, 251 Mercer Street, New York,
How long before I regain my signal?
 How long before I regain my signal? Tingting Lu, Pei Liu and Shivendra S. Panwar Polytechnic School of Engineering New York University Brooklyn, New York Email: tl984@nyu.edu, peiliu@gmail.com, panwar@catt.poly.edu
How long before I regain my signal? Tingting Lu, Pei Liu and Shivendra S. Panwar Polytechnic School of Engineering New York University Brooklyn, New York Email: tl984@nyu.edu, peiliu@gmail.com, panwar@catt.poly.edu
PERFORMANCE COMPARISON OF DATA-SHARING AND COMPRESSION STRATEGIES FOR CLOUD RADIO ACCESS NETWORKS. Pratik Patil, Binbin Dai, and Wei Yu
 PERFORMANCE COMPARISON OF DATA-SHARING AND COMPRESSION STRATEGIES FOR CLOUD RADIO ACCESS NETWORKS Pratik Patil, Binbin Dai, and Wei Yu Department of Electrical and Computer Engineering University of Toronto,
PERFORMANCE COMPARISON OF DATA-SHARING AND COMPRESSION STRATEGIES FOR CLOUD RADIO ACCESS NETWORKS Pratik Patil, Binbin Dai, and Wei Yu Department of Electrical and Computer Engineering University of Toronto,
The All Versus All Low Earth Orbit Conjunction Problem 1 Arthur Lue MIT Lincoln Laboratory ABSTRACT
 The All Versus All Low Earth Orbit Conjunction Problem 1 Arthur Lue MIT Lincoln Laboratory ABSTRACT A critical problem is emerging in the space environment. For the foreseeable future, we expect there
The All Versus All Low Earth Orbit Conjunction Problem 1 Arthur Lue MIT Lincoln Laboratory ABSTRACT A critical problem is emerging in the space environment. For the foreseeable future, we expect there
Probability Map Building of Uncertain Dynamic Environments with Indistinguishable Obstacles
 Probability Map Building of Uncertain Dynamic Environments with Indistinguishable Obstacles Myungsoo Jun and Raffaello D Andrea Sibley School of Mechanical and Aerospace Engineering Cornell University
Probability Map Building of Uncertain Dynamic Environments with Indistinguishable Obstacles Myungsoo Jun and Raffaello D Andrea Sibley School of Mechanical and Aerospace Engineering Cornell University
Gaussian Process Approximations of Stochastic Differential Equations
 Gaussian Process Approximations of Stochastic Differential Equations Cédric Archambeau Dan Cawford Manfred Opper John Shawe-Taylor May, 2006 1 Introduction Some of the most complex models routinely run
Gaussian Process Approximations of Stochastic Differential Equations Cédric Archambeau Dan Cawford Manfred Opper John Shawe-Taylor May, 2006 1 Introduction Some of the most complex models routinely run
Minimal basis for connected Markov chain over 3 3 K contingency tables with fixed two-dimensional marginals. Satoshi AOKI and Akimichi TAKEMURA
 Minimal basis for connected Markov chain over 3 3 K contingency tables with fixed two-dimensional marginals Satoshi AOKI and Akimichi TAKEMURA Graduate School of Information Science and Technology University
Minimal basis for connected Markov chain over 3 3 K contingency tables with fixed two-dimensional marginals Satoshi AOKI and Akimichi TAKEMURA Graduate School of Information Science and Technology University
Using Belief Propagation to Counter Correlated Reports in Cooperative Spectrum Sensing
 Using Belief Propagation to Counter Correlated Reports in Cooperative Spectrum Sensing Mihir Laghate and Danijela Cabric Department of Electrical Engineering, University of California, Los Angeles Emails:
Using Belief Propagation to Counter Correlated Reports in Cooperative Spectrum Sensing Mihir Laghate and Danijela Cabric Department of Electrical Engineering, University of California, Los Angeles Emails:
Independent Component Analysis and Unsupervised Learning. Jen-Tzung Chien
 Independent Component Analysis and Unsupervised Learning Jen-Tzung Chien TABLE OF CONTENTS 1. Independent Component Analysis 2. Case Study I: Speech Recognition Independent voices Nonparametric likelihood
Independent Component Analysis and Unsupervised Learning Jen-Tzung Chien TABLE OF CONTENTS 1. Independent Component Analysis 2. Case Study I: Speech Recognition Independent voices Nonparametric likelihood
Lecture : Probabilistic Machine Learning
 Lecture : Probabilistic Machine Learning Riashat Islam Reasoning and Learning Lab McGill University September 11, 2018 ML : Many Methods with Many Links Modelling Views of Machine Learning Machine Learning
Lecture : Probabilistic Machine Learning Riashat Islam Reasoning and Learning Lab McGill University September 11, 2018 ML : Many Methods with Many Links Modelling Views of Machine Learning Machine Learning
Information Theory Meets Game Theory on The Interference Channel
 Information Theory Meets Game Theory on The Interference Channel Randall A. Berry Dept. of EECS Northwestern University e-mail: rberry@eecs.northwestern.edu David N. C. Tse Wireless Foundations University
Information Theory Meets Game Theory on The Interference Channel Randall A. Berry Dept. of EECS Northwestern University e-mail: rberry@eecs.northwestern.edu David N. C. Tse Wireless Foundations University
Tight Lower Bounds on the Ergodic Capacity of Rayleigh Fading MIMO Channels
 Tight Lower Bounds on the Ergodic Capacity of Rayleigh Fading MIMO Channels Özgür Oyman ), Rohit U. Nabar ), Helmut Bölcskei 2), and Arogyaswami J. Paulraj ) ) Information Systems Laboratory, Stanford
Tight Lower Bounds on the Ergodic Capacity of Rayleigh Fading MIMO Channels Özgür Oyman ), Rohit U. Nabar ), Helmut Bölcskei 2), and Arogyaswami J. Paulraj ) ) Information Systems Laboratory, Stanford
Blind Attacks on Machine Learners
 Blind Attacks on Machine Learners Alex Beatson 1 Zhaoran Wang 1 Han Liu 1 1 Princeton University NIPS, 2016/ Presenter: Anant Kharkar NIPS, 2016/ Presenter: Anant Kharkar 1 Outline 1 Introduction Motivation
Blind Attacks on Machine Learners Alex Beatson 1 Zhaoran Wang 1 Han Liu 1 1 Princeton University NIPS, 2016/ Presenter: Anant Kharkar NIPS, 2016/ Presenter: Anant Kharkar 1 Outline 1 Introduction Motivation
Information Theory and Hypothesis Testing
 Summer School on Game Theory and Telecommunications Campione, 7-12 September, 2014 Information Theory and Hypothesis Testing Mauro Barni University of Siena September 8 Review of some basic results linking
Summer School on Game Theory and Telecommunications Campione, 7-12 September, 2014 Information Theory and Hypothesis Testing Mauro Barni University of Siena September 8 Review of some basic results linking
On the occurrence times of componentwise maxima and bias in likelihood inference for multivariate max-stable distributions
 On the occurrence times of componentwise maxima and bias in likelihood inference for multivariate max-stable distributions J. L. Wadsworth Department of Mathematics and Statistics, Fylde College, Lancaster
On the occurrence times of componentwise maxima and bias in likelihood inference for multivariate max-stable distributions J. L. Wadsworth Department of Mathematics and Statistics, Fylde College, Lancaster
Covariance function estimation in Gaussian process regression
 Covariance function estimation in Gaussian process regression François Bachoc Department of Statistics and Operations Research, University of Vienna WU Research Seminar - May 2015 François Bachoc Gaussian
Covariance function estimation in Gaussian process regression François Bachoc Department of Statistics and Operations Research, University of Vienna WU Research Seminar - May 2015 François Bachoc Gaussian
Detecting Wormhole Attacks in Wireless Networks Using Local Neighborhood Information
 Detecting Wormhole Attacks in Wireless Networks Using Local Neighborhood Information W. Znaidi M. Minier and JP. Babau Centre d'innovations en Télécommunication & Intégration de services wassim.znaidi@insa-lyon.fr
Detecting Wormhole Attacks in Wireless Networks Using Local Neighborhood Information W. Znaidi M. Minier and JP. Babau Centre d'innovations en Télécommunication & Intégration de services wassim.znaidi@insa-lyon.fr
Lecture Notes 1 Probability and Random Variables. Conditional Probability and Independence. Functions of a Random Variable
 Lecture Notes 1 Probability and Random Variables Probability Spaces Conditional Probability and Independence Random Variables Functions of a Random Variable Generation of a Random Variable Jointly Distributed
Lecture Notes 1 Probability and Random Variables Probability Spaces Conditional Probability and Independence Random Variables Functions of a Random Variable Generation of a Random Variable Jointly Distributed
Lecture 11: Probability, Order Statistics and Sampling
 5-75: Graduate Algorithms February, 7 Lecture : Probability, Order tatistics and ampling Lecturer: David Whitmer cribes: Ilai Deutel, C.J. Argue Exponential Distributions Definition.. Given sample space
5-75: Graduate Algorithms February, 7 Lecture : Probability, Order tatistics and ampling Lecturer: David Whitmer cribes: Ilai Deutel, C.J. Argue Exponential Distributions Definition.. Given sample space
