Identification of Destabilizing Attacks in Power Systems
|
|
|
- Katherine Gaines
- 5 years ago
- Views:
Transcription
1 Identification of Destabilizing Attacks in Power Systems Mike Izbicki, Sajjad Amini, Christian R. Shelton, and Hamed Mohsenian-Rad Abstract In a destabilizing attack against a power system, the adversary hacks into generators or load control mechanisms to insert positive feedback into the power system dynamics. The implementation of destabilizing attacks, both on the generation and load sides, have recently been studied. There are also recent advances on how to detect, i.e., realize the presence of, destabilizing attacks in power systems. However, identifying the location(s) of the compromised buses is still an open problem. This is particularly challenging if, as in practice, one does not even know the number of compromised buses. Another challenge is to keep the computational complexity low to allow fast attack identification with high accuracy. To address these various issues, we observe in this paper that destabilizing attacks can be modeled as a reparameterization of the power system s dynamical model. Therefore, we propose an attack detection method that uses the unscented Kalman filter to jointly estimate both the system states and parameters of the attack. We also propose a low-rank modification to the Kalman filter that improves computational efficiency while maintaining the detection accuracy. We show empirically that this method successfully identifies complex attacks involving many buses. I. INTRODUCTION In this paper, we consider attacks against power system stability. Such attacks can be conducted in different ways, either on the generation side [3], [10] or on the load side [1], [7], [8]. Either way they essentially involve inserting positive feedback into various power system control mechanisms. Recent work has made advances on how to detect destabilizing attacks in power systems. Specifically, [2] applies the fast Fourier transform (FFT) to system measurements. It detects frequencies that a destabilizing attack adds that are not present during normal operation. The presence of such new frequencies beyond certain pre-specified magnitude thresholds indicate the presence of a destabilizing attack. In this paper, we move one step ahead and address the open problem of identifying destabilizing attacks against power systems by only monitoring state variables. That is, we devise a method that examines the state-variable data from power system sensors such as phasor measurement units (PMUs), to indicate at which exact power system buses (i.e., nodes) the load and/or generation are compromised. Our proposed method has three main properties: 1) It does not require prior knowledge of the number of buses that are compromised. That is, as in practice, we assume that the grid operator is not initially aware of how many buses are compromised. Nevertheless, our method can identify which buses are compromised. This work was supported in part by the National Science Foundation (NSF) grant ECCS/AFOSR The authors are with the Bourns College of Engineering, University of California, Riverside, CA, USA. s: mike@izbicki.me, saamini@ece.ucr.edu, cshelton@cs.ucr.edu, hamed@ece.ucr.edu. 2) Prior methods, e.g., in [2], often analyze the attack at each individual bus, which would allow attack identification only if the method is applied several times separately on every bus. In contrast, our method naturally identifies attacks on the entire system considered as a whole. This reduces the computation time. 3) It is capable of distinguishing destabilizing attacks, i.e., load or generation control loops that are malicious and based on positive feedback, from the many load and generation control loops that exist in a power system that are benign and based on negative feedback. The main tool that we use in this paper is the unscented Kalman filter (UKF) to perform dual state estimation to estimate an unknown attack matrix. We then identify the attack location(s) through a proper thresholding mechanism applied to the entries of the estimated attack matrix. A. Related work This paper belongs to the family of studies that address destabilizing attacks against power systems. While the focus so far has been mostly on the definition and implementation of such attacks [1], [3], [8], on the methods to protect the power system against such attacks [7], [10], and occasionally on methods to detect such attacks [2], the focus in this paper is on the less explored topic of identifying the attack by finding the location(s) of the compromised buses. In terms of the methodology used in this paper, the UKF has been used before for power system problems, e.g., to estimate the rotor angle and speed in synchronous generators [4]. However, no joint estimation is used, and the system is not under attack. A more recent analysis estimates the parameters of the motor controller and bus loads [5]. Again, the system is not under attack. This paper shows through numerical results that the current power system monitoring systems would require calculation of a large Jacobian matrix if one wants to apply the UKF without modification for the purpose of identifying destabilizing attacks. In this regard, the current study is related also to a thread of work, such as in [11], [14], that similarly have to deal with the computational issues that arise when applying the UKF to power systems. Again, these studies do not address the power system under attack and the details of the analysis are different from those in this paper. II. PROBLEM STATEMENT We consider a power system with g generator buses and l load buses. An example is shown in Figure 1. We model the dynamics of this system using the standard linear power
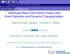
2 attack begins P G P L 7 ω 2 safe operating range 5 P L 6 4 P L P L P G 1 1 Fig. 1. The standard IEEE 9 bus power system under a destabilizing attack. The attacker has added a load to bus 8 that gets positive feedback from generator bus 3. This causes instabilities throughout the power system. The inset shows that generator 2 s rotar angle frequency deviation (ω 2 ). During normal operations, ω 2 remains close to 0 because the system is stable. The attack adds instability to the system, which causes ω 2 to exceed safe operating levels unless corrective action is taken. Our goal is to identify which system buses are compromised so that we can take this corrective action. system state space equation 8 P L 8 ẋ Ax + Bu, (1) where the state variables and inputs are δ [ ] x θ P G, u P ω L. (2) Here, δ is the vector of voltage phase angles at all generator buses, ω is the vector of rotor angular frequency deviations at all generator buses, θ is the vector of voltage phase angles at all load buses, P L is the vector of power consumption at all load buses, and P G is the vector of power generation at all generator buses. Many generators are equipped with Automatic Generation Control (AGC), which is a system for automatically adjusting the power output in response to the load. Entries of P G associated with generators that have AGC are zero. All other entries are nonzero. The system dynamics matrices are 0 0 I A (D L ) -1 H (D L ) -1 H LL 0, M -1 (K I +H GG ) M -1 H GL M -1 (K P +D G ) 0 0 B 0 (D L ) -1, M -1 0 where I is the identity matrix of appropriate dimension, and M, D G, and D L are diagonal matrices with diagonal entries P L P G 3 equal to the inertia, damping coefficients of generators, and damping coefficients of loads, respectively. Matrices H, H GG, H GL, and H LL are the imaginary components of the standard system admittance matrix H bus. Specifically, [ ] H bus H GG H GL. H H LL Matrices K I and K P are diagonal matrices with diagonal entries equal to the integral and proportional coefficients of the generator controllers with AGC capability. Note that the coefficients corresponding to generators without AGC are zero. This system incorporates the swing equations for generators, power flow equations for the transmission network, and the governor and load frequency controller for generators with AGC. The focus in this paper is attacks against power system stability. As shown in Figure 1, an attack in one portion of the power system can cause instability throughout the power system. These destabilizing attacks can affect both generation and load sectors. On the generation side, the attack might compromise the generator governor controller directly or the generator s sensors and communications systems. (See [3], [10] for more details.) On the load side, the attack might compromise the direct or indirect load control mechanisms, e.g., in demand response programs, or their associated sensors, or command signals. (See [1], [7], [8] for more details.) In either case, the attacker s goal is to insert positive feedback into the system. We model a destabilizing attack by decomposing the control input vector u as u u n + u a. (3) Here, the vector u n denotes the control input under normal operation and the vector u a represents the control input added by the attacker. We consider the case where the attacker uses a proportional controller to dynamically determine the value of u a with feedback taken from the demand side. Loads with this feedback are called frequencyresponsive controllable loads, and are widely used in practice [9], [12], [16]. We model the proportional controller input vector as u a A p x + u p, (4) where u p is the constant term for the proportional controller and [ ] A p 0 0 (D L ) 1 K. (5) The entry in row i column j of matrix K contains the proportional gain for load bus i getting feedback from the frequency of generator bus j. If the entry is positive, then bus i is under attack and the system may destabilize. If the entry is negative, then there is a benign frequency-responsive load. These loads will never destabilize the system. If the entry is zero, there are no frequency-responsive loads. Substituting (4) and (3) into (1) gives us our final system dynamics under attack: ẋ (A + BA p )x + B(u n + u p ). (6)
3 The attack will be destabilizing if the matrix (A+BA p ) has an eigenvalue whose absolute value is greater than 1. Detecting the presence of an attack is not difficult. It can be done by monitoring only a few state variables [1]. However, identifying which load bus is compromised is an open problem. In this paper, we propose an identification method that directly estimates the K matrix. Our method automatically determines which load buses are compromised and can distinguish between destabilizing and benign loads. Our method requires access only to synchronized measurements of the state vector x, and does not require access to the control input u. These state measurements are widely available in existing modern power systems through Phasor Measurement Units (PMUs). III. ATTACK IDENTIFICATION METHOD Our attack identification procedure has two steps. First we estimate the K matrix using dual state estimation. This is a standard technique that applies the unscented Kalman filter (UKF) [13] to simultaneously estimate the entries of matrix K and the system states x. Unfortunately, the standard application of this technique does not work well for our problem. It is too slow computationally and has poor accuracy. So we introduce a novel rank-1 approximation which lets us effectively apply dual state estimation to our problem. Finally, once K is estimated, we apply a thresholding procedure to identify the attacked buses. A. Standard dual state estimation and its limitations Dual state estimation is traditionally described using the system s discrete state equations, so we begin our presentation by discretizing (6) as x t+1 (sa + sba p t + I)x t + sb(u n t + u p t ) + ɛ. (7) The subscripts indicate the timestep, s is a scalar that represents the length of a time step, and ɛ N (0, Q ɛ ) is an error term capturing both modeling and observation errors. Now we describe how to estimate the A p t matrix. Recall that in the definition of A p t, the Kt matrix is unknown and determined by the attacker; all other elements are statically known. In dual state estimation, we augment the original dynamical system s state variables to also include the elements of Kt. The resulting augmented system is [ ] [ xt+1 sa + sba p ] [ ] vec Kt+1 t + I 0 x t 0 I vec Kt [ ] [ sb 0 u n + t + u p ] t + 0 I where ɛ N (0, Q ɛ ), ɛ m N u m t [ ɛ ɛ m ], (8) ( 0, Q ɛm) (9) Here we have also introduced a new control input u m t with error ɛ m. It is unobserved and controlled by the attacker. Specifically, the attacker uses u m t to manipulate the entries of Kt, and hence A p t. The notation vec Kt refers to the column vector constructed by stacking the columns of Kt on top of each other. Next we note that the control inputs u n t, u a t, and u m t are unobserved. A standard technique for modeling unobserved inputs is to replace them with random error terms. The true distribution of these random errors is unknown, but for computational convenience we assume they are normally distributed. In particular, we assume the control inputs are zero-mean Gaussians with covariance Q n, Q a, and Q m respectively. Under these assumptions, we can rewrite the dualized system dynamics described in (9) as [ ] [ xt+1 sa + sba p ] [ ] [ ] vec Kt+1 t + I 0 x t ɛ 0 I vec Kt + ɛ KL, (10) where ɛ N (0, B(Q n + Q p ) + Q ɛ ), ɛ KL N (0, Q m ). Observe that the dynamical system described by (10) is nonlinear because the K term appears in the definition of A p t. It is standard to solve systems of this form using the UKF [13]. We defer to the cited paper for details. The UKF encounters two problems when run on (10). The first is that the problem is underspecified. The number of parameters we are trying to estimate (i.e. the number of entries in K ) grows as O(lg), but the size of the observed data (i.e. the size of x) grows at the slower rate of O(l + g). In general, underspecified problems are difficult to solve without introducing additional statistical assumptions. As the size of the power grid increases, the degree of underspecification increases, so we would expect this method to have low accuracy on large grids. The second problem is computational. At each time step, the UKF takes the inverse of a matrix whose dimension depends on the number of state variables. There are O(lg) states in (10), and so the runtime of this inversion is O((lg) 3 ). This poor scaling makes the standard method impractical to run on power systems with more than about 50 buses. These limitations of the standard method motivate our proposed rank-1 method, which we describe next. B. The rank-1 method In this method, we assume that the K matrix has rank 1. We justify this assumption as follows. In a typical destabilizing attack, only a small number of buses are compromised and subject to positive feedback. For each of these compromised buses, there is a corresponding nonzero entry in the Kt matrix. A basic fact of linear algebra is that the rank of a matrix is less than or equal to the number of nonzero entries in the matrix. Specifically, we have Rank{Kt } Non-zero entries in Kt. (11) Therefore, assuming that there are a small number of compromised buses is equivalent to assuming that K has low rank. Specifically, we assume that K t k L t k GT t, (12)
4 where k L t and k G t are column vectors. Under this assumption, we can rewrite the standard method s dynamics from (10) as x t+1 sa + sba p k L t + I 0 0 x t ɛ t+1 0 I 0 k L k G t + ɛ 1, (13) t I k G t ɛ 2 where ɛ N (0, B(Q n + Q p ) + Q ɛ ), ɛ 1 N (0, Q m + Q ɛ1 ), ɛ 2 N (0, Q m + Q ɛ2 ), and the new attack matrix is [ A p t 0 0 (D L ) 1 k LT t k G t This system remains nonlinear and is solved using the UKF. The rank-1 method has improved statistical and computational performance. Statistically, there are only O(l + g) parameters to estimate in the rank-1 method. This matches the size of the state vector x, so the problem is no longer underspecified. We no longer expect statistical performance to degrade as the problem size increases. Computationally, the run time of each iteration of the UKF is only O((l+g) 3 ). This is much faster than the O((lg) 3 ) required for the standard method. C. Thresholding Once the matrix K is estimated, we apply a thresholding procedure to identify the attack. Define the function n f t (i) Kt (i, j) (14) j1 to be the sum of the entries in the ith row of the Kt matrix. This value is the total predicted attack on the ith bus in the power grid. Also define ]. α t arg max f t (i) (15) i to be the bus we predict has the most compromised load and so is under the heaviest attack. If f t (α t ) is greater than some threshold τ, then we declare that the system is under attack at bus α t. At this point, the system operator can take defensive measures such as isolating the bus from the system. IV. CONNECTION TO PREVIOUS METHODS Recall from Section I that destabilizing attacks in power systems can be detected using an FFT-based method applied to the system state variables, as explained in [2]. A destabilizing attack will introduce new frequencies that are not present during normal operation. Whenever these frequencies exceed a pre-specified threshold, we say an attack is happening. One can apply the same type of FFT-based method directly to the input measurements in a power system, i.e., to u t u n t + A p t x t + u p t, to also identify the attack. However, this is not a desirable approach in practice due to several reasons, as we explain next. First, unlike the state variables that are measured using advanced sensors such as PMUs at high resolutions, e.g., at 60 to 120 samples per second, the input signals, i.e., the load and generation levels, are metered at low resolutions, e.g., once every one to 15 minutes. These low resolution measurements do not allow observing the new frequencies that would be present, e.g., at 0.26 Hz [2], under an attack. Second, even if we use the high resolution state variable data from PMUs, combine it with an unknown input observer (UIO) method, and then estimate the input signals at high resolutions, we would still have three problems: (i) the high computational cost of the UIO method; (ii) the high computational cost of applying the FFT method to each entry of the estimated input signal; (iii) the inherent weakness of FFT-based methods in distinguishing destabilizing attacks, i.e., load or generation control loops that are malicious and based on positive feedback, from the many load and generation control loops that exist in a power system that are benign and based on negative feedback, c.f. [2]. One of our contributions in this paper is to observe that the A p t matrix contains all the information we need to determine whether an attack is occurring, so there is no need to perform the subsequent FFT step. In fact, the FFT step necessarily loses some of the information contained within A p t. The FFT method is only able to detect the presence of frequency dependent loads or generators; it cannot identify either the sign or the magnitude of the feedback. Direct inspection of the A p t method, on the other hand, gives us both. V. SIMULATION RESULTS In this section we compare the performance of the proposed method in Section III with a baseline approach that does not apply the rank-1 assumption from Section III-B. We refer to the latter method as the standard method. In this section, we show that compared to the standard method, our proposed method can: 1) significantly lower the computation time; 2) significantly lower the identification error; and 3) better distinguish positive and negative feedback. We begin with a qualitative demonstration of these facts, and then conclude with a quantitative demonstration. A. Test Setup and Qualitative Results All experiments in this section use a single randomly generated power grid with 20 generator and 20 load buses. We test on this relatively small grid size because the standard method that estimates a full rank K matrix cannot scale to larger problems. On this size problem, a single iteration of our rank-1 method takes about 1 second, and a single iteration of the standard method takes about 1 minute. On a problem with 100 generators and 100 loads, a single iteration of our rank-1 method takes about 5 seconds, and a single iteration of the standard method takes over an hour. The computation advantage of our proposed method is evident. We follow the clustersmallworld procedure for generating the power grid [15]. Note that, standard methods for generating random graphs do not exhibit the topological
5 1 compromised bus 3 compromised buses 5 compromised buses fi(t) attack initiated compromised buses uncompromised buses standard method proposed rank-1 method simulation time (sec) Fig. 2. Each line in the figures above represents the predicted positive feedback of a particular load bus. Compromised buses are drawn in bold red, and uncompromised buses are drawn in thin green. For all times t before the attack begins, each bus i has f i (t) near zero. After the attack begins, the f i (t) deviate from zero. Our method is correctly identifying the attacked buses whenever the red lines are above the green lines. In the top row, we see that our rank-1 approximation of K provides relatively accurate predictions even when the number of attacks increases and the rank-1 approximation is no longer true. In the bottom row, we see that the standard method has poor accuracy. and electrical properties of real world power grids [6], but clustersmallworld was designed specifically for modeling real world power grids. An outline of the procedure is: First generate a random number of ring shaped grids with fewer than 10 buses each; Then randomly add connections between the buses until the average degree of each node is 4. To ensure the stability of the resulting system, scale matrix A so that its maximum eigenvalue is no greater than This model generates realistically shaped power grids up to about 300 buses. Once the power grid has been generated, a load input vector, i.e., u t, is sampled from a Gaussian process truncated so that values are always non-negative. The first experiment has 6 separate scenarios that test how the proposed method and the standard method perform in identifying 1, 3, and 5 compromised buses. In each case, the attack begins at time 0.1 seconds. Matrix A p t is selected such that (A+BA p t ) has maximum eigenvalue 1.05, ensuring that the attack destabilizes the system. Figure 2 shows the results. The proposed method clearly has better qualitative performance on this particular problem. Specifically, it identifies the compromised buses faster and more accurately. To look carefully into how our proposed method can differentiate between benign and malicious loads, next we randomly selected a load i and generator j, then set the ith row and jth column of K to 10. Recall that negative values of the K matrix correspond to benign loads. The results are shown in Figure 3. Negative feedback does not destabilize the system, yet we are able to detect the feedback. The standard method (not shown) has difficulty with this fi(t) buses with normal loads responsive load added bus with responsive load simulation time (sec) Fig. 3. In this simulation, we added a benign frequency responsive load. Our rank-1 method is able to quickly identify the load with the responsive feedback. The corresponding value of f i (t) is negative because the feedback is negative. Previous work cannot distinguish these benign frequency responsive loads from malicious loads, whereas ours can. problem as it takes much longer for the standard method to converge. B. Quantitative Results We now explore the quantitative performance of our methods by measuring its performance on several power systems. We generated two sets of power grids, one with 20 generators and 20 loads (as in the previous section), and the other one with 100 generators and 100 loads. The standard method was run only on the smaller grid, again because it is computationally infeasible to run it on the larger one, and
6 accuracy of αt rank-1 K 1 compromised bus attack initiated simulation time (sec) rank-1 K 5 compromised buses full K 5 compromised buses full K 1 compromised bus Fig. 4. It takes only about a quarter of a second for our rank-1 method to detect a single attack with 99% accuracy. As the number of attacks increases, our rank-1 method takes longer to achieve high accuracy. With 5 compromised buses, the attack is detected with 95% accuracy by two seconds. This is fast enough to implement corrective actions. The full K method has much worse accuracy no matter how many buses are compromised. the proposed method was run only on both grids. A major strength of both methods is that they experienced no false positives. We define a false positive to be the detection of an attack when no attack occurred. It does not matter if the value of α t is correct. When no attack is underway, the largest entries of the estimated Kt are typically less than When an attack is underway, the largest values of the estimated K skyrocket to well above Therefore, it is easy to set the threshold τ to avoid false positives. Finally, we evaluate the method s accuracy of identification. We define the accuracy at time point t to be the fraction of α t values that correctly predict the attacked bus. Figure 4 shows that the longer we wait to declare an attack occurs (i.e. the larger we set τ), the higher our accuracy is. In the case of the rank-1 method detecting a single attack, we observed 99% accuracy in under one second. The rank-1 method operating on the 200 bus system has much higher accuracy than the standard method operating on the significantly easier 40 bus system. The standard method s accuracy is little better than random guessing after two seconds. VI. CONCLUSIONS In this paper we addressed the open problem of detecting a destabilizing attack against the power system, i.e., identifying which buses are compromised through a possible positive feedback. Our method does not require prior knowledge on the number of buses that are compromised. It also does not require conducting a separate analysis at each bus. Instead, it naturally identifies attacks on the entire system considered as a whole. Therefore, it has low computational complexity. Furthermore, it is capable of distinguishing destabilizing attacks, i.e., load or generation control loops that are malicious and based on positive feedback, from the many load and generation control loops that exist in a power system that are benign and based on negative feedback. Numerical results show that this method successfully identifies complex attacks involving many buses. The detection is accurate and fast. REFERENCES [1] Sajjad Amini, Hamed Mohsenian-Rad, and Fabio Pasqualetti. Dynamic load altering attacks in smart grid. In Innovative Smart Grid Technologies Conference (ISGT), 2015 IEEE Power & Energy Society, pages 1 5. IEEE, [2] Sajjad Amini, Fabio Pasqualetti, and Hamed Mohsenian-Rad. Detecting dynamic load altering attacks: A data-driven time-frequency analysis. In 2015 IEEE International Conference on Smart Grid Communications (SmartGridComm), pages IEEE, [3] Christopher L. DeMarco, J.V. Sariashkar, and Fernando Alvarado. The potential for malicious control in a competitive power systems environment. In Control Applications, 1996., Proceedings of the 1996 IEEE International Conference on, pages IEEE, [4] Esmaeil Ghahremani and Innocent Kamwa. Online state estimation of a synchronous generator using unscented Kalman filter from phasor measurements units. IEEE Transactions on Energy Conversion, 26(4): , [5] Esmaeil Ghahremani and Innocent Kamwa. Local and wide-area pmubased decentralized dynamic state estimation in multi-machine power systems. IEEE Transactions on Power Systems, 31(1): , [6] Paul Hines, Seth Blumsack, E Cotilla Sanchez, and Clayton Barrows. The topological and electrical structure of power grids. In System Sciences (HICSS), rd Hawaii International Conference on, pages IEEE, [7] Angelos K. Marnerides, Paul Smith, Alberto Schaeffer-Filho, and Andreas Mauthe. Power consumption profiling using energy timefrequency distributions in smart grids. IEEE Communications Letters, 19(1):46 49, [8] Amir-Hamed Mohsenian-Rad and Alberto Leon-Garcia. Distributed internet-based load altering attacks against smart power grids. IEEE Transactions on Smart Grid, 2(4): , [9] Angel Molina-Garcia, Franois Bouffard, and Daniel S. Kirschen. Decentralized demand-side contribution to primary frequency control. IEEE Trans. on Power Systems, 26(1): , February [10] Fabio Pasqualetti, Florian Dörfler, and Francesco Bullo. Cyberphysical security via geometric control: Distributed monitoring and malicious attacks. In 2012 IEEE 51st IEEE Conference on Decision and Control (CDC), pages IEEE, [11] Xiangyun Qing, Hamid Reza Karimi, Yugang Niu, and Xingyu Wang. Decentralized unscented Kalman filter based on a consensus algorithm for multi-area dynamic state estimation in power systems. International Journal of Electrical Power & Energy Systems, 65:26 33, [12] Joe Short, David Infield, and Leon L. Freris. Stabilization of grid frequency through dynamic demand control. IEEE Trans. on Power Systems, 22(3): , August [13] Eric A Wan and Rudolph Van Der Merwe. The unscented Kalman filter for nonlinear estimation. In Adaptive Systems for Signal Processing, Communications, and Control Symposium AS-SPCC. The IEEE 2000, pages Ieee, [14] Shaobu Wang, Wenzhong Gao, and A.P. Sakis Meliopoulos. An alternative method for power system dynamic state estimation based on unscented transform. IEEE Transactions on Power Systems, 27(2): , [15] Zhifang Wang, Anna Scaglione, and Robert J Thomas. Generating statistically correct random topologies for testing smart grid communication and control networks. IEEE transactions on Smart Grid, 1(1):28 39, [16] Changhong Zhao, Ufuk Topcu, and Steven H. Low. Optimal load control via frequency measurement and neighborhood area communication. IEEE Trans. on Power Systems, 28(4): , November 2013.
Power Grid State Estimation after a Cyber-Physical Attack under the AC Power Flow Model
 Power Grid State Estimation after a Cyber-Physical Attack under the AC Power Flow Model Saleh Soltan, Gil Zussman Department of Electrical Engineering Columbia University, New York, NY Email: {saleh,gil}@ee.columbia.edu
Power Grid State Estimation after a Cyber-Physical Attack under the AC Power Flow Model Saleh Soltan, Gil Zussman Department of Electrical Engineering Columbia University, New York, NY Email: {saleh,gil}@ee.columbia.edu
False Data Injection Attacks Against Nonlinear State Estimation in Smart Power Grids
 1 False Data Injection Attacks Against Nonlinear State Estimation in Smart Power rids Md. Ashfaqur Rahman and Hamed Mohsenian-Rad Department of Electrical and Computer Engineering, Texas Tech University,
1 False Data Injection Attacks Against Nonlinear State Estimation in Smart Power rids Md. Ashfaqur Rahman and Hamed Mohsenian-Rad Department of Electrical and Computer Engineering, Texas Tech University,
Cyber Attacks, Detection and Protection in Smart Grid State Estimation
 1 Cyber Attacks, Detection and Protection in Smart Grid State Estimation Yi Zhou, Student Member, IEEE Zhixin Miao, Senior Member, IEEE Abstract This paper reviews the types of cyber attacks in state estimation
1 Cyber Attacks, Detection and Protection in Smart Grid State Estimation Yi Zhou, Student Member, IEEE Zhixin Miao, Senior Member, IEEE Abstract This paper reviews the types of cyber attacks in state estimation
On the Failure of Power System Automatic Generation Control due to Measurement Noise
 1 On the Failure of Power System Automatic Generation Control due to Measurement Noise Jiangmeng Zhang and Alejandro. D. Domínguez-García University of Illinois at Urbana-Champaign Urbana, Illinois 6181
1 On the Failure of Power System Automatic Generation Control due to Measurement Noise Jiangmeng Zhang and Alejandro. D. Domínguez-García University of Illinois at Urbana-Champaign Urbana, Illinois 6181
Distributed Detection of Cyber Attacks and Faults for Power Systems
 Preprints of the 19th World Congress The International Federation of Automatic Control Cape Town, South Africa. August 24-29, 214 Distributed Detection of Cyber Attacks and Faults for Power Systems Hiroaki
Preprints of the 19th World Congress The International Federation of Automatic Control Cape Town, South Africa. August 24-29, 214 Distributed Detection of Cyber Attacks and Faults for Power Systems Hiroaki
Power Grid Partitioning: Static and Dynamic Approaches
 Power Grid Partitioning: Static and Dynamic Approaches Miao Zhang, Zhixin Miao, Lingling Fan Department of Electrical Engineering University of South Florida Tampa FL 3320 miaozhang@mail.usf.edu zmiao,
Power Grid Partitioning: Static and Dynamic Approaches Miao Zhang, Zhixin Miao, Lingling Fan Department of Electrical Engineering University of South Florida Tampa FL 3320 miaozhang@mail.usf.edu zmiao,
Performance of Flocking-Based Control Schemes in Smart Grid Applications
 Performance of Flocking-Based Control Schemes in Smart Grid Applications Abdallah K. Farraj Eman M. Hammad Jin Wei Deepa Kundur Karen L. Butler-Purry Department of Electrical and Computer Engineering,
Performance of Flocking-Based Control Schemes in Smart Grid Applications Abdallah K. Farraj Eman M. Hammad Jin Wei Deepa Kundur Karen L. Butler-Purry Department of Electrical and Computer Engineering,
Dynamic Attacks on Power Systems Economic Dispatch
 Dynamic Attacks on Power Systems Economic Dispatch Jinsub Kim School of Electrical Engineering and Computer Science Oregon State University, Corvallis, OR 9733 Email: {insub.kim}@oregonstate.edu Lang Tong
Dynamic Attacks on Power Systems Economic Dispatch Jinsub Kim School of Electrical Engineering and Computer Science Oregon State University, Corvallis, OR 9733 Email: {insub.kim}@oregonstate.edu Lang Tong
Dynamic Decomposition for Monitoring and Decision Making in Electric Power Systems
 Dynamic Decomposition for Monitoring and Decision Making in Electric Power Systems Contributed Talk at NetSci 2007 May 20, 2007 Le Xie (lx@ece.cmu.edu) Advisor: Marija Ilic Outline Motivation Problem Statement
Dynamic Decomposition for Monitoring and Decision Making in Electric Power Systems Contributed Talk at NetSci 2007 May 20, 2007 Le Xie (lx@ece.cmu.edu) Advisor: Marija Ilic Outline Motivation Problem Statement
Analysis of Coupling Dynamics for Power Systems with Iterative Discrete Decision Making Architectures
 Analysis of Coupling Dynamics for Power Systems with Iterative Discrete Decision Making Architectures Zhixin Miao Department of Electrical Engineering, University of South Florida, Tampa FL USA 3362. Email:
Analysis of Coupling Dynamics for Power Systems with Iterative Discrete Decision Making Architectures Zhixin Miao Department of Electrical Engineering, University of South Florida, Tampa FL USA 3362. Email:
DESIGN AND IMPLEMENTATION OF SENSORLESS SPEED CONTROL FOR INDUCTION MOTOR DRIVE USING AN OPTIMIZED EXTENDED KALMAN FILTER
 INTERNATIONAL JOURNAL OF ELECTRONICS AND COMMUNICATION ENGINEERING & TECHNOLOGY (IJECET) International Journal of Electronics and Communication Engineering & Technology (IJECET), ISSN 0976 ISSN 0976 6464(Print)
INTERNATIONAL JOURNAL OF ELECTRONICS AND COMMUNICATION ENGINEERING & TECHNOLOGY (IJECET) International Journal of Electronics and Communication Engineering & Technology (IJECET), ISSN 0976 ISSN 0976 6464(Print)
An Abrupt Change Detection Heuristic with Applications to Cyber Data Attacks on Power Systems π
 An Abrupt Change Detection Heuristic with Applications to Cyber Data Attacks on Power Systems π Borhan M. Sanandaji Eilyan Bitar Kameshwar Poolla and Tyrone L. Vincent Abstract We present an analysis of
An Abrupt Change Detection Heuristic with Applications to Cyber Data Attacks on Power Systems π Borhan M. Sanandaji Eilyan Bitar Kameshwar Poolla and Tyrone L. Vincent Abstract We present an analysis of
Joint Frequency Regulation and Economic Dispatch Using Limited Communication
 Joint Frequency Regulation and Economic Dispatch Using Limited Communication Jianan Zhang, and Eytan Modiano Massachusetts Institute of Technology, Cambridge, MA, USA Abstract We study the performance
Joint Frequency Regulation and Economic Dispatch Using Limited Communication Jianan Zhang, and Eytan Modiano Massachusetts Institute of Technology, Cambridge, MA, USA Abstract We study the performance
Fine Tuning Of State Estimator Using Phasor Values From Pmu s
 National conference on Engineering Innovations and Solutions (NCEIS 2018) International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2018 IJSRCSEIT Volume
National conference on Engineering Innovations and Solutions (NCEIS 2018) International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2018 IJSRCSEIT Volume
= V I = Bus Admittance Matrix. Chapter 6: Power Flow. Constructing Ybus. Example. Network Solution. Triangular factorization. Let
 Chapter 6: Power Flow Network Matrices Network Solutions Newton-Raphson Method Fast Decoupled Method Bus Admittance Matri Let I = vector of currents injected into nodes V = vector of node voltages Y bus
Chapter 6: Power Flow Network Matrices Network Solutions Newton-Raphson Method Fast Decoupled Method Bus Admittance Matri Let I = vector of currents injected into nodes V = vector of node voltages Y bus
A graph-theoretical characterization of power network vulnerabilities
 A graph-theoretical characterization of power network vulnerabilities Fabio Pasqualetti, Antonio Bicchi, and Francesco Bullo Abstract This work is concerned with the security of a power network against
A graph-theoretical characterization of power network vulnerabilities Fabio Pasqualetti, Antonio Bicchi, and Francesco Bullo Abstract This work is concerned with the security of a power network against
Multi-Robotic Systems
 CHAPTER 9 Multi-Robotic Systems The topic of multi-robotic systems is quite popular now. It is believed that such systems can have the following benefits: Improved performance ( winning by numbers ) Distributed
CHAPTER 9 Multi-Robotic Systems The topic of multi-robotic systems is quite popular now. It is believed that such systems can have the following benefits: Improved performance ( winning by numbers ) Distributed
The N k Problem using AC Power Flows
 The N k Problem using AC Power Flows Sean Harnett 5-19-2011 Outline Introduction AC power flow model The optimization problem Some results Goal: find a small set of lines whose removal will cause the power
The N k Problem using AC Power Flows Sean Harnett 5-19-2011 Outline Introduction AC power flow model The optimization problem Some results Goal: find a small set of lines whose removal will cause the power
Power system modelling under the phasor approximation
 ELEC0047 - Power system dynamics, control and stability Thierry Van Cutsem t.vancutsem@ulg.ac.be www.montefiore.ulg.ac.be/~vct October 2018 1 / 16 Electromagnetic transient vs. phasor-mode simulations
ELEC0047 - Power system dynamics, control and stability Thierry Van Cutsem t.vancutsem@ulg.ac.be www.montefiore.ulg.ac.be/~vct October 2018 1 / 16 Electromagnetic transient vs. phasor-mode simulations
Sparsity-promoting wide-area control of power systems. F. Dörfler, Mihailo Jovanović, M. Chertkov, and F. Bullo American Control Conference
 Sparsity-promoting wide-area control of power systems F. Dörfler, Mihailo Jovanović, M. Chertkov, and F. Bullo 203 American Control Conference Electro-mechanical oscillations in power systems Local oscillations
Sparsity-promoting wide-area control of power systems F. Dörfler, Mihailo Jovanović, M. Chertkov, and F. Bullo 203 American Control Conference Electro-mechanical oscillations in power systems Local oscillations
PMU-Based Power System Real-Time Stability Monitoring. Chen-Ching Liu Boeing Distinguished Professor Director, ESI Center
 PMU-Based Power System Real-Time Stability Monitoring Chen-Ching Liu Boeing Distinguished Professor Director, ESI Center Dec. 2015 Real-Time Monitoring of System Dynamics EMS Real-Time Data Server Ethernet
PMU-Based Power System Real-Time Stability Monitoring Chen-Ching Liu Boeing Distinguished Professor Director, ESI Center Dec. 2015 Real-Time Monitoring of System Dynamics EMS Real-Time Data Server Ethernet
Minimum Sparsity of Unobservable. Power Network Attacks
 Minimum Sparsity of Unobservable 1 Power Network Attacks Yue Zhao, Andrea Goldsmith, H. Vincent Poor Abstract Physical security of power networks under power injection attacks that alter generation and
Minimum Sparsity of Unobservable 1 Power Network Attacks Yue Zhao, Andrea Goldsmith, H. Vincent Poor Abstract Physical security of power networks under power injection attacks that alter generation and
Oscillation energy based sensitivity analysis and control for multi-mode oscillation systems
 Oscillation energy based sensitivity analysis and control for multi-mode oscillation systems Horacio Silva-Saravia, Yajun Wang, Héctor Pulgar-Painemal, Kevin Tomsovic Department of Electrical Engineering
Oscillation energy based sensitivity analysis and control for multi-mode oscillation systems Horacio Silva-Saravia, Yajun Wang, Héctor Pulgar-Painemal, Kevin Tomsovic Department of Electrical Engineering
Coordinated Variable Structure Switching in Smart Power Systems: Attacks and Mitigation
 Coordinated Variable Structure Switching in Smart Power Systems: Attacks and Mitigation Shan Liu, Deepa Kundur, Takis Zourntos and Karen Butler-Purry Department of Electrical and Computer Engineering Texas
Coordinated Variable Structure Switching in Smart Power Systems: Attacks and Mitigation Shan Liu, Deepa Kundur, Takis Zourntos and Karen Butler-Purry Department of Electrical and Computer Engineering Texas
ECE 422/522 Power System Operations & Planning/Power Systems Analysis II : 7 - Transient Stability
 ECE 4/5 Power System Operations & Planning/Power Systems Analysis II : 7 - Transient Stability Spring 014 Instructor: Kai Sun 1 Transient Stability The ability of the power system to maintain synchronism
ECE 4/5 Power System Operations & Planning/Power Systems Analysis II : 7 - Transient Stability Spring 014 Instructor: Kai Sun 1 Transient Stability The ability of the power system to maintain synchronism
Automatic Generation Control. Meth Bandara and Hassan Oukacha
 Automatic Generation Control Meth Bandara and Hassan Oukacha EE194 Advanced Controls Theory February 25, 2013 Outline Introduction System Modeling Single Generator AGC Going Forward Conclusion Introduction
Automatic Generation Control Meth Bandara and Hassan Oukacha EE194 Advanced Controls Theory February 25, 2013 Outline Introduction System Modeling Single Generator AGC Going Forward Conclusion Introduction
Generalized Injection Shift Factors and Application to Estimation of Power Flow Transients
 Generalized Injection Shift Factors and Application to Estimation of Power Flow Transients Yu Christine Chen, Alejandro D. Domínguez-García, and Peter W. Sauer Department of Electrical and Computer Engineering
Generalized Injection Shift Factors and Application to Estimation of Power Flow Transients Yu Christine Chen, Alejandro D. Domínguez-García, and Peter W. Sauer Department of Electrical and Computer Engineering
Identification of Synchronous Generator Parameters Using Continuous ARX Model and Least Square Estimation
 Identification of Synchronous Generator Parameters Using Continuous ARX Model and Least Square Estimation Yangkun Xu, Student Member, IEEE, Zhixin Miao, Senior Member, IEEE, Yin Li, Student Member, IEEE
Identification of Synchronous Generator Parameters Using Continuous ARX Model and Least Square Estimation Yangkun Xu, Student Member, IEEE, Zhixin Miao, Senior Member, IEEE, Yin Li, Student Member, IEEE
Accurate Joule Loss Estimation for Rotating Machines: An Engineering Approach
 Accurate Joule Loss Estimation for Rotating Machines: An Engineering Approach Adeeb Ahmed Department of Electrical and Computer Engineering North Carolina State University Raleigh, NC, USA aahmed4@ncsu.edu
Accurate Joule Loss Estimation for Rotating Machines: An Engineering Approach Adeeb Ahmed Department of Electrical and Computer Engineering North Carolina State University Raleigh, NC, USA aahmed4@ncsu.edu
Self-Tuning Control for Synchronous Machine Stabilization
 http://dx.doi.org/.5755/j.eee.2.4.2773 ELEKTRONIKA IR ELEKTROTECHNIKA, ISSN 392-25, VOL. 2, NO. 4, 25 Self-Tuning Control for Synchronous Machine Stabilization Jozef Ritonja Faculty of Electrical Engineering
http://dx.doi.org/.5755/j.eee.2.4.2773 ELEKTRONIKA IR ELEKTROTECHNIKA, ISSN 392-25, VOL. 2, NO. 4, 25 Self-Tuning Control for Synchronous Machine Stabilization Jozef Ritonja Faculty of Electrical Engineering
EL 625 Lecture 10. Pole Placement and Observer Design. ẋ = Ax (1)
 EL 625 Lecture 0 EL 625 Lecture 0 Pole Placement and Observer Design Pole Placement Consider the system ẋ Ax () The solution to this system is x(t) e At x(0) (2) If the eigenvalues of A all lie in the
EL 625 Lecture 0 EL 625 Lecture 0 Pole Placement and Observer Design Pole Placement Consider the system ẋ Ax () The solution to this system is x(t) e At x(0) (2) If the eigenvalues of A all lie in the
Various Techniques for Nonlinear Energy-Related Optimizations. Javad Lavaei. Department of Electrical Engineering Columbia University
 Various Techniques for Nonlinear Energy-Related Optimizations Javad Lavaei Department of Electrical Engineering Columbia University Acknowledgements Caltech: Steven Low, Somayeh Sojoudi Columbia University:
Various Techniques for Nonlinear Energy-Related Optimizations Javad Lavaei Department of Electrical Engineering Columbia University Acknowledgements Caltech: Steven Low, Somayeh Sojoudi Columbia University:
STATE ESTIMATION IN DISTRIBUTION SYSTEMS
 SAE ESIMAION IN DISRIBUION SYSEMS 2015 CIGRE Grid of the Future Symposium Chicago (IL), October 13, 2015 L. Garcia-Garcia, D. Apostolopoulou Laura.GarciaGarcia@ComEd.com Dimitra.Apostolopoulou@ComEd.com
SAE ESIMAION IN DISRIBUION SYSEMS 2015 CIGRE Grid of the Future Symposium Chicago (IL), October 13, 2015 L. Garcia-Garcia, D. Apostolopoulou Laura.GarciaGarcia@ComEd.com Dimitra.Apostolopoulou@ComEd.com
Optimal PMU Placement
 Optimal PMU Placement S. A. Soman Department of Electrical Engineering Indian Institute of Technology Bombay Dec 2, 2011 PMU Numerical relays as PMU System Observability Control Center Architecture WAMS
Optimal PMU Placement S. A. Soman Department of Electrical Engineering Indian Institute of Technology Bombay Dec 2, 2011 PMU Numerical relays as PMU System Observability Control Center Architecture WAMS
SUPPLEMENTARY INFORMATION
 DOI: 1.138/NPHYS535 Spontaneous synchrony in power-grid networks Adilson E. Motter, Seth A. Myers, Marian Anghel and Takashi Nishikawa Supplementary Sections S1. Power-grid data. The data required for
DOI: 1.138/NPHYS535 Spontaneous synchrony in power-grid networks Adilson E. Motter, Seth A. Myers, Marian Anghel and Takashi Nishikawa Supplementary Sections S1. Power-grid data. The data required for
Designing Information Devices and Systems I Fall 2018 Lecture Notes Note Introduction to Linear Algebra the EECS Way
 EECS 16A Designing Information Devices and Systems I Fall 018 Lecture Notes Note 1 1.1 Introduction to Linear Algebra the EECS Way In this note, we will teach the basics of linear algebra and relate it
EECS 16A Designing Information Devices and Systems I Fall 018 Lecture Notes Note 1 1.1 Introduction to Linear Algebra the EECS Way In this note, we will teach the basics of linear algebra and relate it
WIDE AREA CONTROL THROUGH AGGREGATION OF POWER SYSTEMS
 WIDE AREA CONTROL THROUGH AGGREGATION OF POWER SYSTEMS Arash Vahidnia B.Sc, M.Sc in Electrical Engineering A Thesis submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy
WIDE AREA CONTROL THROUGH AGGREGATION OF POWER SYSTEMS Arash Vahidnia B.Sc, M.Sc in Electrical Engineering A Thesis submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy
A Robust Event-Triggered Consensus Strategy for Linear Multi-Agent Systems with Uncertain Network Topology
 A Robust Event-Triggered Consensus Strategy for Linear Multi-Agent Systems with Uncertain Network Topology Amir Amini, Amir Asif, Arash Mohammadi Electrical and Computer Engineering,, Montreal, Canada.
A Robust Event-Triggered Consensus Strategy for Linear Multi-Agent Systems with Uncertain Network Topology Amir Amini, Amir Asif, Arash Mohammadi Electrical and Computer Engineering,, Montreal, Canada.
Designing Information Devices and Systems I Spring 2018 Lecture Notes Note Introduction to Linear Algebra the EECS Way
 EECS 16A Designing Information Devices and Systems I Spring 018 Lecture Notes Note 1 1.1 Introduction to Linear Algebra the EECS Way In this note, we will teach the basics of linear algebra and relate
EECS 16A Designing Information Devices and Systems I Spring 018 Lecture Notes Note 1 1.1 Introduction to Linear Algebra the EECS Way In this note, we will teach the basics of linear algebra and relate
CURENT Course Power System Coherency and Model Reduction
 CURENT Course Power System Coherency and Model Reduction Prof. Joe H. Chow Rensselaer Polytechnic Institute ECSE Department November 1, 2017 Slow Coherency A large power system usually consists of tightly
CURENT Course Power System Coherency and Model Reduction Prof. Joe H. Chow Rensselaer Polytechnic Institute ECSE Department November 1, 2017 Slow Coherency A large power system usually consists of tightly
COMPARISON OF STATISTICAL ALGORITHMS FOR POWER SYSTEM LINE OUTAGE DETECTION
 COMPARISON OF STATISTICAL ALGORITHMS FOR POWER SYSTEM LINE OUTAGE DETECTION Georgios Rovatsos*, Xichen Jiang*, Alejandro D. Domínguez-García, and Venugopal V. Veeravalli Department of Electrical and Computer
COMPARISON OF STATISTICAL ALGORITHMS FOR POWER SYSTEM LINE OUTAGE DETECTION Georgios Rovatsos*, Xichen Jiang*, Alejandro D. Domínguez-García, and Venugopal V. Veeravalli Department of Electrical and Computer
Linear Algebra. The analysis of many models in the social sciences reduces to the study of systems of equations.
 POLI 7 - Mathematical and Statistical Foundations Prof S Saiegh Fall Lecture Notes - Class 4 October 4, Linear Algebra The analysis of many models in the social sciences reduces to the study of systems
POLI 7 - Mathematical and Statistical Foundations Prof S Saiegh Fall Lecture Notes - Class 4 October 4, Linear Algebra The analysis of many models in the social sciences reduces to the study of systems
ON SEPARATION PRINCIPLE FOR THE DISTRIBUTED ESTIMATION AND CONTROL OF FORMATION FLYING SPACECRAFT
 ON SEPARATION PRINCIPLE FOR THE DISTRIBUTED ESTIMATION AND CONTROL OF FORMATION FLYING SPACECRAFT Amir Rahmani (), Olivia Ching (2), and Luis A Rodriguez (3) ()(2)(3) University of Miami, Coral Gables,
ON SEPARATION PRINCIPLE FOR THE DISTRIBUTED ESTIMATION AND CONTROL OF FORMATION FLYING SPACECRAFT Amir Rahmani (), Olivia Ching (2), and Luis A Rodriguez (3) ()(2)(3) University of Miami, Coral Gables,
Stability Analysis Through the Direct Method of Lyapunov in the Oscillation of a Synchronous Machine
 Modern Applied Science; Vol. 12, No. 7; 2018 ISSN 1913-1844 E-ISSN 1913-1852 Published by Canadian Center of Science and Education Stability Analysis Through the Direct Method of Lyapunov in the Oscillation
Modern Applied Science; Vol. 12, No. 7; 2018 ISSN 1913-1844 E-ISSN 1913-1852 Published by Canadian Center of Science and Education Stability Analysis Through the Direct Method of Lyapunov in the Oscillation
Discrete-time Consensus Filters on Directed Switching Graphs
 214 11th IEEE International Conference on Control & Automation (ICCA) June 18-2, 214. Taichung, Taiwan Discrete-time Consensus Filters on Directed Switching Graphs Shuai Li and Yi Guo Abstract We consider
214 11th IEEE International Conference on Control & Automation (ICCA) June 18-2, 214. Taichung, Taiwan Discrete-time Consensus Filters on Directed Switching Graphs Shuai Li and Yi Guo Abstract We consider
Resilient Distributed Optimization Algorithm against Adversary Attacks
 207 3th IEEE International Conference on Control & Automation (ICCA) July 3-6, 207. Ohrid, Macedonia Resilient Distributed Optimization Algorithm against Adversary Attacks Chengcheng Zhao, Jianping He
207 3th IEEE International Conference on Control & Automation (ICCA) July 3-6, 207. Ohrid, Macedonia Resilient Distributed Optimization Algorithm against Adversary Attacks Chengcheng Zhao, Jianping He
Unsupervised Learning with Permuted Data
 Unsupervised Learning with Permuted Data Sergey Kirshner skirshne@ics.uci.edu Sridevi Parise sparise@ics.uci.edu Padhraic Smyth smyth@ics.uci.edu School of Information and Computer Science, University
Unsupervised Learning with Permuted Data Sergey Kirshner skirshne@ics.uci.edu Sridevi Parise sparise@ics.uci.edu Padhraic Smyth smyth@ics.uci.edu School of Information and Computer Science, University
Online Neuro-Adaptive Learning For Power System Dynamic State Estimation
 University of Central Florida Electronic Theses and Dissertations Masters Thesis (Open Access) Online Neuro-Adaptive Learning For Power System Dynamic State Estimation 2017 Rahul Birari University of Central
University of Central Florida Electronic Theses and Dissertations Masters Thesis (Open Access) Online Neuro-Adaptive Learning For Power System Dynamic State Estimation 2017 Rahul Birari University of Central
Role of Synchronized Measurements In Operation of Smart Grids
 Role of Synchronized Measurements In Operation of Smart Grids Ali Abur Electrical and Computer Engineering Department Northeastern University Boston, Massachusetts Boston University CISE Seminar November
Role of Synchronized Measurements In Operation of Smart Grids Ali Abur Electrical and Computer Engineering Department Northeastern University Boston, Massachusetts Boston University CISE Seminar November
Iterative Methods for Solving A x = b
 Iterative Methods for Solving A x = b A good (free) online source for iterative methods for solving A x = b is given in the description of a set of iterative solvers called templates found at netlib: http
Iterative Methods for Solving A x = b A good (free) online source for iterative methods for solving A x = b is given in the description of a set of iterative solvers called templates found at netlib: http
Displacement at very low frequencies produces very low accelerations since:
 SEISMOLOGY The ability to do earthquake location and calculate magnitude immediately brings us into two basic requirement of instrumentation: Keeping accurate time and determining the frequency dependent
SEISMOLOGY The ability to do earthquake location and calculate magnitude immediately brings us into two basic requirement of instrumentation: Keeping accurate time and determining the frequency dependent
Smart Grid State Estimation by Weighted Least Square Estimation
 International Journal of Engineering and Advanced Technology (IJEAT) ISSN: 2249 8958, Volume-5, Issue-6, August 2016 Smart Grid State Estimation by Weighted Least Square Estimation Nithin V G, Libish T
International Journal of Engineering and Advanced Technology (IJEAT) ISSN: 2249 8958, Volume-5, Issue-6, August 2016 Smart Grid State Estimation by Weighted Least Square Estimation Nithin V G, Libish T
Distributed Real-Time Electric Power Grid Event Detection and Dynamic Characterization
 Distributed Real-Time Electric Power Grid Event Detection and Dynamic Characterization Raymond de Callafon, Charles H. Wells University of California, San Diego & OSIsoft CIGRE Grid of the Future Symposium,
Distributed Real-Time Electric Power Grid Event Detection and Dynamic Characterization Raymond de Callafon, Charles H. Wells University of California, San Diego & OSIsoft CIGRE Grid of the Future Symposium,
11.1 Power System Stability Overview
 11.1 Power System Stability Overview This introductory section provides a general description of the power system stability phenomena including fundamental concepts, classification, and definition of associated
11.1 Power System Stability Overview This introductory section provides a general description of the power system stability phenomena including fundamental concepts, classification, and definition of associated
Introduction to Unscented Kalman Filter
 Introduction to Unscented Kalman Filter 1 Introdution In many scientific fields, we use certain models to describe the dynamics of system, such as mobile robot, vision tracking and so on. The word dynamics
Introduction to Unscented Kalman Filter 1 Introdution In many scientific fields, we use certain models to describe the dynamics of system, such as mobile robot, vision tracking and so on. The word dynamics
A Decomposition Based Approach for Solving a General Bilevel Linear Programming
 A Decomposition Based Approach for Solving a General Bilevel Linear Programming Xuan Liu, Member, IEEE, Zuyi Li, Senior Member, IEEE Abstract Bilevel optimization has been widely used in decisionmaking
A Decomposition Based Approach for Solving a General Bilevel Linear Programming Xuan Liu, Member, IEEE, Zuyi Li, Senior Member, IEEE Abstract Bilevel optimization has been widely used in decisionmaking
Slow Coherency & Sparsity-Promoting Optimal Wide-Area Control
 Slow Coherency & Sparsity-Promoting Optimal Wide-Area Control Trends, Advances, & Tomorrow s Power Grid increasing renewables & deregulation growing demand & operation at capacity Florian Dörfler, Mihailo
Slow Coherency & Sparsity-Promoting Optimal Wide-Area Control Trends, Advances, & Tomorrow s Power Grid increasing renewables & deregulation growing demand & operation at capacity Florian Dörfler, Mihailo
Dynamic state based on autoregressive model for outgoing line of high voltage stations
 5th International Conference on Advanced Engineering Materials and Technology (AEMT 015) Dynamic state based on autoregressive model for outgoing line of high voltage stations Yanhong Wang1, a * Tao Xin,b
5th International Conference on Advanced Engineering Materials and Technology (AEMT 015) Dynamic state based on autoregressive model for outgoing line of high voltage stations Yanhong Wang1, a * Tao Xin,b
Topology-Driven Performance Analysis of Power Grids
 Topology-Driven Performance Analysis of Power Grids Hale Çetinay, Yakup Koç, Fernando A. Kuipers, Piet Van Mieghem Abstract Direct connections between nodes usually result in efficient transmission in
Topology-Driven Performance Analysis of Power Grids Hale Çetinay, Yakup Koç, Fernando A. Kuipers, Piet Van Mieghem Abstract Direct connections between nodes usually result in efficient transmission in
A STATIC AND DYNAMIC TECHNIQUE CONTINGENCY RANKING ANALYSIS IN VOLTAGE STABILITY ASSESSMENT
 A STATIC AND DYNAMIC TECHNIQUE CONTINGENCY RANKING ANALYSIS IN VOLTAGE STABILITY ASSESSMENT Muhammad Nizam Engineering Faculty Sebelas Maret University (Ph.D Student of Electrical, Electronic and System
A STATIC AND DYNAMIC TECHNIQUE CONTINGENCY RANKING ANALYSIS IN VOLTAGE STABILITY ASSESSMENT Muhammad Nizam Engineering Faculty Sebelas Maret University (Ph.D Student of Electrical, Electronic and System
A Novel Technique to Improve the Online Calculation Performance of Nonlinear Problems in DC Power Systems
 electronics Article A Novel Technique to Improve the Online Calculation Performance of Nonlinear Problems in DC Power Systems Qingshan Xu 1, Yuqi Wang 1, * ID, Minjian Cao 1 and Jiaqi Zheng 2 1 School
electronics Article A Novel Technique to Improve the Online Calculation Performance of Nonlinear Problems in DC Power Systems Qingshan Xu 1, Yuqi Wang 1, * ID, Minjian Cao 1 and Jiaqi Zheng 2 1 School
Dynamic Attack Detection in Cyber-Physical. Systems with Side Initial State Information
 Dynamic Attack Detection in Cyber-Physical 1 Systems with Side Initial State Information Yuan Chen, Soummya Kar, and José M. F. Moura arxiv:1503.07125v1 math.oc] 24 Mar 2015 Abstract This paper studies
Dynamic Attack Detection in Cyber-Physical 1 Systems with Side Initial State Information Yuan Chen, Soummya Kar, and José M. F. Moura arxiv:1503.07125v1 math.oc] 24 Mar 2015 Abstract This paper studies
Reliability of Bulk Power Systems (cont d)
 Reliability of Bulk Power Systems (cont d) Important requirements of a reliable electric power service Voltage and frequency must be held within close tolerances Synchronous generators must be kept running
Reliability of Bulk Power Systems (cont d) Important requirements of a reliable electric power service Voltage and frequency must be held within close tolerances Synchronous generators must be kept running
MATRICES. a m,1 a m,n A =
 MATRICES Matrices are rectangular arrays of real or complex numbers With them, we define arithmetic operations that are generalizations of those for real and complex numbers The general form a matrix of
MATRICES Matrices are rectangular arrays of real or complex numbers With them, we define arithmetic operations that are generalizations of those for real and complex numbers The general form a matrix of
Power Sharing Correction in Angle Droop Controlled Inverter Interfaced Microgrids
 Power Sharing Correction in Angle Droop Controlled Inverter Interfaced Microgrids Ramachandra Rao Kolluri, Iven Mareels Tansu Alpcan and Marcus Brazil Department of Electrical and Electronic Engineering
Power Sharing Correction in Angle Droop Controlled Inverter Interfaced Microgrids Ramachandra Rao Kolluri, Iven Mareels Tansu Alpcan and Marcus Brazil Department of Electrical and Electronic Engineering
Distributed Frequency Control in Power Grids Under Limited Communication
 Distributed Frequency Control in Power Grids Under Limited Communication Marzieh Parandehgheibi, Konstantin Turitsyn and Eytan Modiano Laboratory for Information and Decision Systems, Massachusetts Institute
Distributed Frequency Control in Power Grids Under Limited Communication Marzieh Parandehgheibi, Konstantin Turitsyn and Eytan Modiano Laboratory for Information and Decision Systems, Massachusetts Institute
MODELLING ANALYSIS & DESIGN OF DSP BASED NOVEL SPEED SENSORLESS VECTOR CONTROLLER FOR INDUCTION MOTOR DRIVE
 International Journal of Advanced Research in Engineering and Technology (IJARET) Volume 6, Issue 3, March, 2015, pp. 70-81, Article ID: IJARET_06_03_008 Available online at http://www.iaeme.com/ijaret/issues.asp?jtypeijaret&vtype=6&itype=3
International Journal of Advanced Research in Engineering and Technology (IJARET) Volume 6, Issue 3, March, 2015, pp. 70-81, Article ID: IJARET_06_03_008 Available online at http://www.iaeme.com/ijaret/issues.asp?jtypeijaret&vtype=6&itype=3
Power System Stability and Control. Dr. B. Kalyan Kumar, Department of Electrical Engineering, Indian Institute of Technology Madras, Chennai, India
 Power System Stability and Control Dr. B. Kalyan Kumar, Department of Electrical Engineering, Indian Institute of Technology Madras, Chennai, India Contents Chapter 1 Introduction to Power System Stability
Power System Stability and Control Dr. B. Kalyan Kumar, Department of Electrical Engineering, Indian Institute of Technology Madras, Chennai, India Contents Chapter 1 Introduction to Power System Stability
Introduction to Control (034040) lecture no. 2
 Introduction to Control (034040) lecture no. 2 Leonid Mirkin Faculty of Mechanical Engineering Technion IIT Setup: Abstract control problem to begin with y P(s) u where P is a plant u is a control signal
Introduction to Control (034040) lecture no. 2 Leonid Mirkin Faculty of Mechanical Engineering Technion IIT Setup: Abstract control problem to begin with y P(s) u where P is a plant u is a control signal
HPC and High-end Data Science
 HPC and High-end Data Science for the Power Grid Alex Pothen August 3, 2018 Outline High-end Data Science 1 3 Data Anonymization Contingency Analysis 2 4 Parallel Oscillation Monitoring 2 / 22 PMUs in
HPC and High-end Data Science for the Power Grid Alex Pothen August 3, 2018 Outline High-end Data Science 1 3 Data Anonymization Contingency Analysis 2 4 Parallel Oscillation Monitoring 2 / 22 PMUs in
Research Article Extended and Unscented Kalman Filtering Applied to a Flexible-Joint Robot with Jerk Estimation
 Hindawi Publishing Corporation Discrete Dynamics in Nature and Society Volume 21, Article ID 482972, 14 pages doi:1.1155/21/482972 Research Article Extended and Unscented Kalman Filtering Applied to a
Hindawi Publishing Corporation Discrete Dynamics in Nature and Society Volume 21, Article ID 482972, 14 pages doi:1.1155/21/482972 Research Article Extended and Unscented Kalman Filtering Applied to a
Mixed Integer Linear Programming and Nonlinear Programming for Optimal PMU Placement
 Mied Integer Linear Programg and Nonlinear Programg for Optimal PMU Placement Anas Almunif Department of Electrical Engineering University of South Florida, Tampa, FL 33620, USA Majmaah University, Al
Mied Integer Linear Programg and Nonlinear Programg for Optimal PMU Placement Anas Almunif Department of Electrical Engineering University of South Florida, Tampa, FL 33620, USA Majmaah University, Al
Data-Driven Joint Topology and Line Parameter Estimation for Renewable Integration
 Data-Driven Joint Topology and Line Parameter Estimation for Renewable Integration Jiafan Yu Dept. of Electrical Engineering Email: jfy@stanford.edu Yang Weng Stanford Sustainable Systems Lab Email: yangweng@stanford.edu
Data-Driven Joint Topology and Line Parameter Estimation for Renewable Integration Jiafan Yu Dept. of Electrical Engineering Email: jfy@stanford.edu Yang Weng Stanford Sustainable Systems Lab Email: yangweng@stanford.edu
Module 3 : Sequence Components and Fault Analysis
 Module 3 : Sequence Components and Fault Analysis Lecture 12 : Sequence Modeling of Power Apparatus Objectives In this lecture we will discuss Per unit calculation and its advantages. Modeling aspects
Module 3 : Sequence Components and Fault Analysis Lecture 12 : Sequence Modeling of Power Apparatus Objectives In this lecture we will discuss Per unit calculation and its advantages. Modeling aspects
Pathwise Observability Through Arithmetic Progressions and Non-Pathological Sampling
 Pathwise Observability Through Arithmetic Progressions and Non-Pathological Sampling Mohamed Babaali and Magnus Egerstedt School of Electrical and Computer Engineering Georgia Institute of Technology Atlanta,
Pathwise Observability Through Arithmetic Progressions and Non-Pathological Sampling Mohamed Babaali and Magnus Egerstedt School of Electrical and Computer Engineering Georgia Institute of Technology Atlanta,
Robust transient stability assessment of renewable power grids
 16 IEEE International Conference on Sustainable Energy Technologies (ICSET) 7 Robust transient stability assessment of renewable power grids Thanh Long Vu, Member, IEEE, and Konstantin Turitsyn, Member,
16 IEEE International Conference on Sustainable Energy Technologies (ICSET) 7 Robust transient stability assessment of renewable power grids Thanh Long Vu, Member, IEEE, and Konstantin Turitsyn, Member,
MATH 1553-C MIDTERM EXAMINATION 3
 MATH 553-C MIDTERM EXAMINATION 3 Name GT Email @gatech.edu Please read all instructions carefully before beginning. Please leave your GT ID card on your desk until your TA scans your exam. Each problem
MATH 553-C MIDTERM EXAMINATION 3 Name GT Email @gatech.edu Please read all instructions carefully before beginning. Please leave your GT ID card on your desk until your TA scans your exam. Each problem
The Important State Coordinates of a Nonlinear System
 The Important State Coordinates of a Nonlinear System Arthur J. Krener 1 University of California, Davis, CA and Naval Postgraduate School, Monterey, CA ajkrener@ucdavis.edu Summary. We offer an alternative
The Important State Coordinates of a Nonlinear System Arthur J. Krener 1 University of California, Davis, CA and Naval Postgraduate School, Monterey, CA ajkrener@ucdavis.edu Summary. We offer an alternative
MTH Linear Algebra. Study Guide. Dr. Tony Yee Department of Mathematics and Information Technology The Hong Kong Institute of Education
 MTH 3 Linear Algebra Study Guide Dr. Tony Yee Department of Mathematics and Information Technology The Hong Kong Institute of Education June 3, ii Contents Table of Contents iii Matrix Algebra. Real Life
MTH 3 Linear Algebra Study Guide Dr. Tony Yee Department of Mathematics and Information Technology The Hong Kong Institute of Education June 3, ii Contents Table of Contents iii Matrix Algebra. Real Life
Synchronization and Kron Reduction in Power Networks
 Synchronization and Kron Reduction in Power Networks Florian Dörfler and Francesco Bullo Center for Control, Dynamical Systems & Computation University of California at Santa Barbara IFAC Workshop on Distributed
Synchronization and Kron Reduction in Power Networks Florian Dörfler and Francesco Bullo Center for Control, Dynamical Systems & Computation University of California at Santa Barbara IFAC Workshop on Distributed
sc Control Systems Design Q.1, Sem.1, Ac. Yr. 2010/11
 sc46 - Control Systems Design Q Sem Ac Yr / Mock Exam originally given November 5 9 Notes: Please be reminded that only an A4 paper with formulas may be used during the exam no other material is to be
sc46 - Control Systems Design Q Sem Ac Yr / Mock Exam originally given November 5 9 Notes: Please be reminded that only an A4 paper with formulas may be used during the exam no other material is to be
POWER SYSTEM DYNAMIC STATE ESTIMATION and LOAD MODELING. Cem Bila
 POWER SYSTEM DYNAMIC STATE ESTIMATION and LOAD MODELING A Thesis Presented by Cem Bila to The Department of Electrical and Computer Engineering in partial fulfillment of the requirements for the degree
POWER SYSTEM DYNAMIC STATE ESTIMATION and LOAD MODELING A Thesis Presented by Cem Bila to The Department of Electrical and Computer Engineering in partial fulfillment of the requirements for the degree
TOPIC 2 Computer application for manipulating matrix using MATLAB
 YOGYAKARTA STATE UNIVERSITY MATHEMATICS AND NATURAL SCIENCES FACULTY MATHEMATICS EDUCATION STUDY PROGRAM TOPIC 2 Computer application for manipulating matrix using MATLAB Definition of Matrices in MATLAB
YOGYAKARTA STATE UNIVERSITY MATHEMATICS AND NATURAL SCIENCES FACULTY MATHEMATICS EDUCATION STUDY PROGRAM TOPIC 2 Computer application for manipulating matrix using MATLAB Definition of Matrices in MATLAB
Linear Algebra Tutorial for Math3315/CSE3365 Daniel R. Reynolds
 Linear Algebra Tutorial for Math3315/CSE3365 Daniel R. Reynolds These notes are meant to provide a brief introduction to the topics from Linear Algebra that will be useful in Math3315/CSE3365, Introduction
Linear Algebra Tutorial for Math3315/CSE3365 Daniel R. Reynolds These notes are meant to provide a brief introduction to the topics from Linear Algebra that will be useful in Math3315/CSE3365, Introduction
arxiv: v1 [cs.sy] 24 Mar 2016
![arxiv: v1 [cs.sy] 24 Mar 2016 arxiv: v1 [cs.sy] 24 Mar 2016](/thumbs/88/114536445.jpg) Nonlinear Analysis of an Improved Swing Equation Pooya Monshizadeh, Claudio De Persis, Nima Monshizadeh, and Arjan van der Schaft arxiv:603.07440v [cs.sy] 4 Mar 06 Abstract In this paper, we investigate
Nonlinear Analysis of an Improved Swing Equation Pooya Monshizadeh, Claudio De Persis, Nima Monshizadeh, and Arjan van der Schaft arxiv:603.07440v [cs.sy] 4 Mar 06 Abstract In this paper, we investigate
Quantifying Cyber Security for Networked Control Systems
 Quantifying Cyber Security for Networked Control Systems Henrik Sandberg ACCESS Linnaeus Centre, KTH Royal Institute of Technology Joint work with: André Teixeira, György Dán, Karl H. Johansson (KTH) Kin
Quantifying Cyber Security for Networked Control Systems Henrik Sandberg ACCESS Linnaeus Centre, KTH Royal Institute of Technology Joint work with: André Teixeira, György Dán, Karl H. Johansson (KTH) Kin
Kalman Filter. Predict: Update: x k k 1 = F k x k 1 k 1 + B k u k P k k 1 = F k P k 1 k 1 F T k + Q
 Kalman Filter Kalman Filter Predict: x k k 1 = F k x k 1 k 1 + B k u k P k k 1 = F k P k 1 k 1 F T k + Q Update: K = P k k 1 Hk T (H k P k k 1 Hk T + R) 1 x k k = x k k 1 + K(z k H k x k k 1 ) P k k =(I
Kalman Filter Kalman Filter Predict: x k k 1 = F k x k 1 k 1 + B k u k P k k 1 = F k P k 1 k 1 F T k + Q Update: K = P k k 1 Hk T (H k P k k 1 Hk T + R) 1 x k k = x k k 1 + K(z k H k x k k 1 ) P k k =(I
GRAPH SIGNAL PROCESSING: A STATISTICAL VIEWPOINT
 GRAPH SIGNAL PROCESSING: A STATISTICAL VIEWPOINT Cha Zhang Joint work with Dinei Florêncio and Philip A. Chou Microsoft Research Outline Gaussian Markov Random Field Graph construction Graph transform
GRAPH SIGNAL PROCESSING: A STATISTICAL VIEWPOINT Cha Zhang Joint work with Dinei Florêncio and Philip A. Chou Microsoft Research Outline Gaussian Markov Random Field Graph construction Graph transform
Zero controllability in discrete-time structured systems
 1 Zero controllability in discrete-time structured systems Jacob van der Woude arxiv:173.8394v1 [math.oc] 24 Mar 217 Abstract In this paper we consider complex dynamical networks modeled by means of state
1 Zero controllability in discrete-time structured systems Jacob van der Woude arxiv:173.8394v1 [math.oc] 24 Mar 217 Abstract In this paper we consider complex dynamical networks modeled by means of state
Power System Security. S. Chakrabarti
 Power System Security S. Chakrabarti Outline Introduction Major components of security assessment On-line security assessment Tools for contingency analysis DC power flow Linear sensitivity factors Line
Power System Security S. Chakrabarti Outline Introduction Major components of security assessment On-line security assessment Tools for contingency analysis DC power flow Linear sensitivity factors Line
An Equivalent Circuit Formulation of the Power Flow Problem with Current and Voltage State Variables
 An Equivalent Circuit Formulation of the Power Flow Problem with Current and Voltage State Variables David M. Bromberg, Marko Jereminov, Xin Li, Gabriela Hug, Larry Pileggi Dept. of Electrical and Computer
An Equivalent Circuit Formulation of the Power Flow Problem with Current and Voltage State Variables David M. Bromberg, Marko Jereminov, Xin Li, Gabriela Hug, Larry Pileggi Dept. of Electrical and Computer
URTDSM Initiative in India and Controlled Islanding using PMU Measurements
 URTDSM Initiative in India and Controlled Islanding using PMU Measurements Akhil Raj Gopal Gajjar Meenal Chougule Narayanan Rajagopal Prashant Navalkar Rajeev Gajbhiye S. A. Soman PowerAnser Labs, IIT
URTDSM Initiative in India and Controlled Islanding using PMU Measurements Akhil Raj Gopal Gajjar Meenal Chougule Narayanan Rajagopal Prashant Navalkar Rajeev Gajbhiye S. A. Soman PowerAnser Labs, IIT
POWER SYSTEM DYNAMIC SECURITY ASSESSMENT CLASSICAL TO MODERN APPROACH
 Abstract POWER SYSTEM DYNAMIC SECURITY ASSESSMENT CLASSICAL TO MODERN APPROACH A.H.M.A.Rahim S.K.Chakravarthy Department of Electrical Engineering K.F. University of Petroleum and Minerals Dhahran. Dynamic
Abstract POWER SYSTEM DYNAMIC SECURITY ASSESSMENT CLASSICAL TO MODERN APPROACH A.H.M.A.Rahim S.K.Chakravarthy Department of Electrical Engineering K.F. University of Petroleum and Minerals Dhahran. Dynamic
EE C128 / ME C134 Feedback Control Systems
 EE C128 / ME C134 Feedback Control Systems Lecture Additional Material Introduction to Model Predictive Control Maximilian Balandat Department of Electrical Engineering & Computer Science University of
EE C128 / ME C134 Feedback Control Systems Lecture Additional Material Introduction to Model Predictive Control Maximilian Balandat Department of Electrical Engineering & Computer Science University of
21 Linear State-Space Representations
 ME 132, Spring 25, UC Berkeley, A Packard 187 21 Linear State-Space Representations First, let s describe the most general type of dynamic system that we will consider/encounter in this class Systems may
ME 132, Spring 25, UC Berkeley, A Packard 187 21 Linear State-Space Representations First, let s describe the most general type of dynamic system that we will consider/encounter in this class Systems may
Two-Layer Network Equivalent for Electromagnetic Transients
 1328 IEEE TRANSACTIONS ON POWER DELIVERY, VOL. 18, NO. 4, OCTOBER 2003 Two-Layer Network Equivalent for Electromagnetic Transients Mohamed Abdel-Rahman, Member, IEEE, Adam Semlyen, Life Fellow, IEEE, and
1328 IEEE TRANSACTIONS ON POWER DELIVERY, VOL. 18, NO. 4, OCTOBER 2003 Two-Layer Network Equivalent for Electromagnetic Transients Mohamed Abdel-Rahman, Member, IEEE, Adam Semlyen, Life Fellow, IEEE, and
Distributed Optimization over Networks Gossip-Based Algorithms
 Distributed Optimization over Networks Gossip-Based Algorithms Angelia Nedić angelia@illinois.edu ISE Department and Coordinated Science Laboratory University of Illinois at Urbana-Champaign Outline Random
Distributed Optimization over Networks Gossip-Based Algorithms Angelia Nedić angelia@illinois.edu ISE Department and Coordinated Science Laboratory University of Illinois at Urbana-Champaign Outline Random
Nonlinear Identification of Backlash in Robot Transmissions
 Nonlinear Identification of Backlash in Robot Transmissions G. Hovland, S. Hanssen, S. Moberg, T. Brogårdh, S. Gunnarsson, M. Isaksson ABB Corporate Research, Control Systems Group, Switzerland ABB Automation
Nonlinear Identification of Backlash in Robot Transmissions G. Hovland, S. Hanssen, S. Moberg, T. Brogårdh, S. Gunnarsson, M. Isaksson ABB Corporate Research, Control Systems Group, Switzerland ABB Automation
SYSTEMTEORI - KALMAN FILTER VS LQ CONTROL
 SYSTEMTEORI - KALMAN FILTER VS LQ CONTROL 1. Optimal regulator with noisy measurement Consider the following system: ẋ = Ax + Bu + w, x(0) = x 0 where w(t) is white noise with Ew(t) = 0, and x 0 is a stochastic
SYSTEMTEORI - KALMAN FILTER VS LQ CONTROL 1. Optimal regulator with noisy measurement Consider the following system: ẋ = Ax + Bu + w, x(0) = x 0 where w(t) is white noise with Ew(t) = 0, and x 0 is a stochastic
2nd Symposium on System, Structure and Control, Oaxaca, 2004
 263 2nd Symposium on System, Structure and Control, Oaxaca, 2004 A PROJECTIVE ALGORITHM FOR STATIC OUTPUT FEEDBACK STABILIZATION Kaiyang Yang, Robert Orsi and John B. Moore Department of Systems Engineering,
263 2nd Symposium on System, Structure and Control, Oaxaca, 2004 A PROJECTIVE ALGORITHM FOR STATIC OUTPUT FEEDBACK STABILIZATION Kaiyang Yang, Robert Orsi and John B. Moore Department of Systems Engineering,
