ECEN 655: Advanced Channel Coding Spring Lecture 7 02/04/14. Belief propagation is exact on tree-structured factor graphs.
|
|
|
- Magdalen Robbins
- 5 years ago
- Views:
Transcription
1 ECEN 655: Advaced Chael Codig Sprig 014 Prof. Hery Pfister Lecture 7 0/04/14 Scribe: Megke Lia 1 4-Cycles i Gallager s Esemble What we already kow: Belief propagatio is exact o tree-structured factor graphs. A reasoable assumptio: For a fixed esembles of codes, it is better to have fewer cycles. Gallager s costructio: What is the expected umber of bits ivolved i 4-cycles? Cycles i (, k-ldpc Code Cosider the umber of bits ivolved i 4-cycles. Sice the Gallager esemble is ivariat uder colum permutatio, we have [ ] E I (bit i i 4-cycle = P (bit 1 i 4-cycle i=1 This observatios allows oe to focus o 4-cycles ivolvig the first bit of the code. For ay H from the Gallager esemble, oe ca always permute the colums so that the first /k rows are equal to Q. For example, multiplyig H o the right by P1 T does this because P 1P1 T = I. This holds becaue a permutatio preserves all p-orms ad hece P 1 must be uitary. We ca also permute the rows of the secod Q-block (i.e., rows /k + 1 to /k so that the first row of the d Q-block (i.e., row /k + 1 has a oe i the first positio. Let H = P 0 HP1 T be the parity-check matrix after these permutatios (i.e., P 0 defies the ecessary row permutatio. For a (, k code, the first code bit will be ivolved i a 4-cycle iff row /k + 1 of H has a oe is colum positios, 3,..., k. H = a a k a k+1 a From the above diagram, we observe that row /k + 1 is a biary vector with a oe i the first positio ad k 1 oes distributed uiformly across the other positios. The first bit will be 1
2 ivolved i a 4-cycle iff a l = 1 for l {, 3,..., k}. Whe oe observes a permutatio of a biary vector, there are may permutatios that are idistighuishable. The equivalece classes ca be idetified simply by where the oes are placed i the resultig vector. I this case, there are ( 1 ways to choose the a,..., a values that satisfy the costraits. Of these choices, there are ( k ways that have a = a 3 = = a k = 0. Thus, we fid that P (bit 1 ot i 4-cycle = = # way to choose k 1 oes from k positios # way to choose k 1 oes from 1 positios ( k k ( ( k k i 1 k+i = = 1 i 1 i+1 ( 1 Usig the Taylor expasio, oe ca verify that 1 ax 1 bx = 1 ax + bx + O( x (1 ax(1 bx = 1 ax bx + O ( x. Hece, for a (, k-ldpc code, the probability that bit 1 is ivolved i a 4-cycle is give by P (bit 1 i 4-cycle = 1 P (bit 1 ot i 4-cycle ( k 1 k+i = 1 = 1 k 1 i+1 ( 1 k O( k ( k 1 = + O( = (k 1 + O (. Hece, we fid that the expected umber of bits ivolved i 4-cycles is ( (k 1 P (bit 1 i 4-cycle = + O ( (k 1. Sice the umber coverges to a costat, this gives a hit that a clever choice of permutatios might avoid all 4-cycles Cycles i (j, k-ldpc Code By iductio, we ca compute P (bit 1 i 4-cycle i (j, k-ldpc Code: j 1 P (bit 1 i 4-cycle = 1 P (bit 1 ot i 4-cycle = 1 i=1 ( i( 1 ( 1
3 This is agai based o coutig the equivalece classes of permutatios that avoid 4-cycles for the first bit. Usig the same approach as above, oe ca verify that [ ] ( j lim E I (bit i i 4-cycle = (k 1. i=1 Oe ca see this heuristically by oticig that there are ( j ways to choose two sub-blocks of the parity-check matrix ad form a (, k LDPC code. Each of these will cotribute (k 1 ivolved bits o average. 1.3 Fidig 4-Cycles Let H be the parity-check matrix for LDPC code with its i-th colum h i. The dot(h i, h j = # overlappig oes i h i ad h j If H is a sparse matrix i Matlab, the oe ca compute Z = H * H - diag ( sum(h, [i,j,v] = fid(z>= matrix cotaiig # overlappig oes betwee colums of H gives all pairs of colums that cotai 4-cycles 1.4 Removig 4-Cycles H = Radomly swap bad (sub-colum with ay other (sub-colum i same block to remove 4-cycles. If the block legth is sufficietly large, this will reduce the umber of 4-cycles o average ad evetually remove al 4-cycles. The followig simulatio results for a (3, 6 Gallager code with = 3600 shows that effect of removig 4-cycles is larger i the error floor tha i the waterfall regio. 3
4 Performace of (3, 6 LDPC code ( = BER SNR (db Code with 4-cycles (has error floor Code after removig 4-cycles Note: While the above figure was geerated by a actual experimet, the reader is wared that there ca be sigificat variatio i the performace of radomly chose codes with ad without 4-cycles. 1.5 Matlab Code for Fidig & Removig 4-Cycles fuctio H = samplegallager(j,k, % Sample a radom parity check matrix from Gallager s (j,k regular % esemble % Iput: % j The degree of every variable ode % k The degree of every check ode % The legth of LDPC code % Output: % H The parity check matrix of the code col = zeros(j,1; row = zeros(j,1; for i = 0:j 1 col(( i +1:((i+1 = 1:; row((i +1:((i+1 = i /k + ceil(radperm(/k; H = sparse(row,col,1,j /k,; fuctio H = remove 4Cycle(H % G radom parity check matrix i Gallager s (j,k regular esemble, ad % try to remove all 4 Cycle % Iput: % H The parity check matrix before removig 4 Cycle % Output: 4
5 % H The parity check matrix after removig 4 Cycle = size(h,; k = sum(h(1,:; max iter = 3000; iter = 0; while iter < max iter % Fid 4 Cycles Z = H H diag(sum(h,1; [ col1, col ] = fid(triu(z>=; um cycle = legth(col1; % Check if all 4 Cycles are removed if um cycle == 0 fpritf( All 4 cycles have bee removed after %d iteratio\, iter break; for i = 1:legth(col1 % Fid first same elemet idex = fid(h(:,col1(i. H(:,col(i==1,1, first ; if isempty(idex cotiue; % Fid which level is the elemet i level = ceil(idex/(/k; % Compute row idex of that level rows = ( ( level 1 /k + 1 : ( level /k ; % Radomly choose aother sub colum i that level c = radsample( fid(h(idex,: == 0, 1; % Swap the first sub colum ad the radom oe H(rows,[col1(i c] = H(rows,[c col1(i ]; iter = iter + 1; if iter == max iter [ col1, col ] = fid(triu(h H diag(sum(h,1>=; um cycle = legth(col1; fpritf( There are %d 4 cycles remaiig after %d iteratio\, um cycle, max iter LLR Messages i Decodig The simplest approach is to use uiform quatizatio over some bouded regio. I particular, we ca irestrict rage of LLRs to [ L max, L max ] ad use a quatizatio step size of = Lmax #bits 1. This leads to symmetric 0-cetered quatizatio. While the implemetatio is more complex, o-uiform quatizatio allows oe to achieve very low error rates with oly a few bits of storage. For example, see 5
6 .1 Simple Update Rules Bit ode: ˆL i a = L i + b F (i\a L b i Saturate ˆL to [ L max, L max ] (e.g., a value of L max = 15 is sufficiet i may cases. Check ode: where ˆL a i = h j V (a\i h ( L i a j V (a\i sg (L i a ( ( z h(z = l tah L max, z < h 1 (L max = h(l max h(z = 0, z > L max h(z, otherwise This fuctio is plotted for the case of L max = 3 where h(l max h(z/h(z 1 h(z h(z z Note: While this approach to the check update rule is simple ad ca be made to work well i the waterfall regio, the dyamic rage of the h( fuctio ca be problematic whe tryig to achieve low error floors.. Forward-Backward Approach to Check-Node Rule To use o-uiform quatizatio or improve umerical stability, oe ca use a forward-backward approach to the check-ode update. This approach is based o factorig a degree-d check ode ito a chai of degree-3 check odes. 6
7 f x 1 x 3 f 1 f x 1 x x 3 x 4 x y x 4 o observatio L L 3 L 4 x x 3 x 4 f 1 f f 3 x 1 y 1 y x 4 L L 5 Forward-Backward Approach Usig this approach, oe ca have arbitrary o-uiform quatizatio by usig a lookup table for ( ( a b a b tah (tah 1 tah I the example, oe ca compute the output LLR L 3 associated with the iput LLR L 3 usig L y1 = L 1 L L y = L 4 L 5 L 3 = L y1 L y 7
8 .3 Data Storage x 1 x x 3 x 4 π f 1 f f 3 1 Assume messages from the checks are stored i order by check ad the edge umber (i.e., the 1st edge of the 1st check followed by d edge of 1st check, etc... (a Let c[i] be the i-th edge message i this order (b We will refer this edge orderig as the atural order for the checks (c Iitialize all check messages to 0 (i.e., c[i] = 0, i 1,..., E Assume messages from the bits are stored i order by bit ad the edge umber (i.e., the 1st edge of the 1st bit followed by d edge of 1st bit, etc... (a Let b[i] be the i-th edge message i this order (b Likewise, this edge orderig is called the atural order for the checks 3 Decodig proceeds as follows: (a Reorder check messages ito atural order for bit messages: b[i] = c[π(i], i 1,..., E (b Do bit message updates o b[i] (ote: all operatios are memory local (c Reorder bit messages ito atural order check bit messages: c[π(i] = b[i], i 1,..., E (d Do check message updates o c[i] (ote: all operatios are memory local 4 Other advatages (a For a fixed bit ad check ode degrees, oe ca geerate a radom code simply by choosig π to be a uiform radom permutatio. 8
 1 of 7 7/16/2009 6:06 AM Virtual Laboratories > 6. Radom Samples > 1 2 3 4 5 6 7 6. Order Statistics Defiitios Suppose agai that we have a basic radom experimet, ad that X is a real-valued radom variable
1 of 7 7/16/2009 6:06 AM Virtual Laboratories > 6. Radom Samples > 1 2 3 4 5 6 7 6. Order Statistics Defiitios Suppose agai that we have a basic radom experimet, ad that X is a real-valued radom variable
OPTIMAL ALGORITHMS -- SUPPLEMENTAL NOTES
 OPTIMAL ALGORITHMS -- SUPPLEMENTAL NOTES Peter M. Maurer Why Hashig is θ(). As i biary search, hashig assumes that keys are stored i a array which is idexed by a iteger. However, hashig attempts to bypass
OPTIMAL ALGORITHMS -- SUPPLEMENTAL NOTES Peter M. Maurer Why Hashig is θ(). As i biary search, hashig assumes that keys are stored i a array which is idexed by a iteger. However, hashig attempts to bypass
CS 332: Algorithms. Linear-Time Sorting. Order statistics. Slide credit: David Luebke (Virginia)
 1 CS 332: Algorithms Liear-Time Sortig. Order statistics. Slide credit: David Luebke (Virgiia) Quicksort: Partitio I Words Partitio(A, p, r): Select a elemet to act as the pivot (which?) Grow two regios,
1 CS 332: Algorithms Liear-Time Sortig. Order statistics. Slide credit: David Luebke (Virgiia) Quicksort: Partitio I Words Partitio(A, p, r): Select a elemet to act as the pivot (which?) Grow two regios,
Randomized Algorithms I, Spring 2018, Department of Computer Science, University of Helsinki Homework 1: Solutions (Discussed January 25, 2018)
 Radomized Algorithms I, Sprig 08, Departmet of Computer Sciece, Uiversity of Helsiki Homework : Solutios Discussed Jauary 5, 08). Exercise.: Cosider the followig balls-ad-bi game. We start with oe black
Radomized Algorithms I, Sprig 08, Departmet of Computer Sciece, Uiversity of Helsiki Homework : Solutios Discussed Jauary 5, 08). Exercise.: Cosider the followig balls-ad-bi game. We start with oe black
Lecture 11: Pseudorandom functions
 COM S 6830 Cryptography Oct 1, 2009 Istructor: Rafael Pass 1 Recap Lecture 11: Pseudoradom fuctios Scribe: Stefao Ermo Defiitio 1 (Ge, Ec, Dec) is a sigle message secure ecryptio scheme if for all uppt
COM S 6830 Cryptography Oct 1, 2009 Istructor: Rafael Pass 1 Recap Lecture 11: Pseudoradom fuctios Scribe: Stefao Ermo Defiitio 1 (Ge, Ec, Dec) is a sigle message secure ecryptio scheme if for all uppt
CS / MCS 401 Homework 3 grader solutions
 CS / MCS 401 Homework 3 grader solutios assigmet due July 6, 016 writte by Jāis Lazovskis maximum poits: 33 Some questios from CLRS. Questios marked with a asterisk were ot graded. 1 Use the defiitio of
CS / MCS 401 Homework 3 grader solutios assigmet due July 6, 016 writte by Jāis Lazovskis maximum poits: 33 Some questios from CLRS. Questios marked with a asterisk were ot graded. 1 Use the defiitio of
Lecture 1: Basic problems of coding theory
 Lecture 1: Basic problems of codig theory Error-Correctig Codes (Sprig 016) Rutgers Uiversity Swastik Kopparty Scribes: Abhishek Bhrushudi & Aditya Potukuchi Admiistrivia was discussed at the begiig of
Lecture 1: Basic problems of codig theory Error-Correctig Codes (Sprig 016) Rutgers Uiversity Swastik Kopparty Scribes: Abhishek Bhrushudi & Aditya Potukuchi Admiistrivia was discussed at the begiig of
The Boolean Ring of Intervals
 MATH 532 Lebesgue Measure Dr. Neal, WKU We ow shall apply the results obtaied about outer measure to the legth measure o the real lie. Throughout, our space X will be the set of real umbers R. Whe ecessary,
MATH 532 Lebesgue Measure Dr. Neal, WKU We ow shall apply the results obtaied about outer measure to the legth measure o the real lie. Throughout, our space X will be the set of real umbers R. Whe ecessary,
It is often useful to approximate complicated functions using simpler ones. We consider the task of approximating a function by a polynomial.
 Taylor Polyomials ad Taylor Series It is ofte useful to approximate complicated fuctios usig simpler oes We cosider the task of approximatig a fuctio by a polyomial If f is at least -times differetiable
Taylor Polyomials ad Taylor Series It is ofte useful to approximate complicated fuctios usig simpler oes We cosider the task of approximatig a fuctio by a polyomial If f is at least -times differetiable
The Maximum-Likelihood Decoding Performance of Error-Correcting Codes
 The Maximum-Lielihood Decodig Performace of Error-Correctig Codes Hery D. Pfister ECE Departmet Texas A&M Uiversity August 27th, 2007 (rev. 0) November 2st, 203 (rev. ) Performace of Codes. Notatio X,
The Maximum-Lielihood Decodig Performace of Error-Correctig Codes Hery D. Pfister ECE Departmet Texas A&M Uiversity August 27th, 2007 (rev. 0) November 2st, 203 (rev. ) Performace of Codes. Notatio X,
CS284A: Representations and Algorithms in Molecular Biology
 CS284A: Represetatios ad Algorithms i Molecular Biology Scribe Notes o Lectures 3 & 4: Motif Discovery via Eumeratio & Motif Represetatio Usig Positio Weight Matrix Joshua Gervi Based o presetatios by
CS284A: Represetatios ad Algorithms i Molecular Biology Scribe Notes o Lectures 3 & 4: Motif Discovery via Eumeratio & Motif Represetatio Usig Positio Weight Matrix Joshua Gervi Based o presetatios by
Ma 530 Introduction to Power Series
 Ma 530 Itroductio to Power Series Please ote that there is material o power series at Visual Calculus. Some of this material was used as part of the presetatio of the topics that follow. What is a Power
Ma 530 Itroductio to Power Series Please ote that there is material o power series at Visual Calculus. Some of this material was used as part of the presetatio of the topics that follow. What is a Power
1 Hash tables. 1.1 Implementation
 Lecture 8 Hash Tables, Uiversal Hash Fuctios, Balls ad Bis Scribes: Luke Johsto, Moses Charikar, G. Valiat Date: Oct 18, 2017 Adapted From Virgiia Williams lecture otes 1 Hash tables A hash table is a
Lecture 8 Hash Tables, Uiversal Hash Fuctios, Balls ad Bis Scribes: Luke Johsto, Moses Charikar, G. Valiat Date: Oct 18, 2017 Adapted From Virgiia Williams lecture otes 1 Hash tables A hash table is a
Hashing and Amortization
 Lecture Hashig ad Amortizatio Supplemetal readig i CLRS: Chapter ; Chapter 7 itro; Sectio 7.. Arrays ad Hashig Arrays are very useful. The items i a array are statically addressed, so that isertig, deletig,
Lecture Hashig ad Amortizatio Supplemetal readig i CLRS: Chapter ; Chapter 7 itro; Sectio 7.. Arrays ad Hashig Arrays are very useful. The items i a array are statically addressed, so that isertig, deletig,
Chapter 2 The Solution of Numerical Algebraic and Transcendental Equations
 Chapter The Solutio of Numerical Algebraic ad Trascedetal Equatios Itroductio I this chapter we shall discuss some umerical methods for solvig algebraic ad trascedetal equatios. The equatio f( is said
Chapter The Solutio of Numerical Algebraic ad Trascedetal Equatios Itroductio I this chapter we shall discuss some umerical methods for solvig algebraic ad trascedetal equatios. The equatio f( is said
Disjoint set (Union-Find)
 CS124 Lecture 7 Fall 2018 Disjoit set (Uio-Fid) For Kruskal s algorithm for the miimum spaig tree problem, we foud that we eeded a data structure for maitaiig a collectio of disjoit sets. That is, we eed
CS124 Lecture 7 Fall 2018 Disjoit set (Uio-Fid) For Kruskal s algorithm for the miimum spaig tree problem, we foud that we eeded a data structure for maitaiig a collectio of disjoit sets. That is, we eed
Sequences I. Chapter Introduction
 Chapter 2 Sequeces I 2. Itroductio A sequece is a list of umbers i a defiite order so that we kow which umber is i the first place, which umber is i the secod place ad, for ay atural umber, we kow which
Chapter 2 Sequeces I 2. Itroductio A sequece is a list of umbers i a defiite order so that we kow which umber is i the first place, which umber is i the secod place ad, for ay atural umber, we kow which
End-of-Year Contest. ERHS Math Club. May 5, 2009
 Ed-of-Year Cotest ERHS Math Club May 5, 009 Problem 1: There are 9 cois. Oe is fake ad weighs a little less tha the others. Fid the fake coi by weighigs. Solutio: Separate the 9 cois ito 3 groups (A, B,
Ed-of-Year Cotest ERHS Math Club May 5, 009 Problem 1: There are 9 cois. Oe is fake ad weighs a little less tha the others. Fid the fake coi by weighigs. Solutio: Separate the 9 cois ito 3 groups (A, B,
Sums, products and sequences
 Sums, products ad sequeces How to write log sums, e.g., 1+2+ (-1)+ cocisely? i=1 Sum otatio ( sum from 1 to ): i 3 = 1 + 2 + + If =3, i=1 i = 1+2+3=6. The ame ii does ot matter. Could use aother letter
Sums, products ad sequeces How to write log sums, e.g., 1+2+ (-1)+ cocisely? i=1 Sum otatio ( sum from 1 to ): i 3 = 1 + 2 + + If =3, i=1 i = 1+2+3=6. The ame ii does ot matter. Could use aother letter
Kinetics of Complex Reactions
 Kietics of Complex Reactios by Flick Colema Departmet of Chemistry Wellesley College Wellesley MA 28 wcolema@wellesley.edu Copyright Flick Colema 996. All rights reserved. You are welcome to use this documet
Kietics of Complex Reactios by Flick Colema Departmet of Chemistry Wellesley College Wellesley MA 28 wcolema@wellesley.edu Copyright Flick Colema 996. All rights reserved. You are welcome to use this documet
Sequences and Series of Functions
 Chapter 6 Sequeces ad Series of Fuctios 6.1. Covergece of a Sequece of Fuctios Poitwise Covergece. Defiitio 6.1. Let, for each N, fuctio f : A R be defied. If, for each x A, the sequece (f (x)) coverges
Chapter 6 Sequeces ad Series of Fuctios 6.1. Covergece of a Sequece of Fuctios Poitwise Covergece. Defiitio 6.1. Let, for each N, fuctio f : A R be defied. If, for each x A, the sequece (f (x)) coverges
Recurrence Relations
 Recurrece Relatios Aalysis of recursive algorithms, such as: it factorial (it ) { if (==0) retur ; else retur ( * factorial(-)); } Let t be the umber of multiplicatios eeded to calculate factorial(). The
Recurrece Relatios Aalysis of recursive algorithms, such as: it factorial (it ) { if (==0) retur ; else retur ( * factorial(-)); } Let t be the umber of multiplicatios eeded to calculate factorial(). The
Lecture 11: Hash Functions and Random Oracle Model
 CS 7810 Foudatios of Cryptography October 16, 017 Lecture 11: Hash Fuctios ad Radom Oracle Model Lecturer: Daiel Wichs Scribe: Akshar Varma 1 Topic Covered Defiitio of Hash Fuctios Merkle-Damgaård Theorem
CS 7810 Foudatios of Cryptography October 16, 017 Lecture 11: Hash Fuctios ad Radom Oracle Model Lecturer: Daiel Wichs Scribe: Akshar Varma 1 Topic Covered Defiitio of Hash Fuctios Merkle-Damgaård Theorem
MATH301 Real Analysis (2008 Fall) Tutorial Note #7. k=1 f k (x) converges pointwise to S(x) on E if and
 MATH01 Real Aalysis (2008 Fall) Tutorial Note #7 Sequece ad Series of fuctio 1: Poitwise Covergece ad Uiform Covergece Part I: Poitwise Covergece Defiitio of poitwise covergece: A sequece of fuctios f
MATH01 Real Aalysis (2008 Fall) Tutorial Note #7 Sequece ad Series of fuctio 1: Poitwise Covergece ad Uiform Covergece Part I: Poitwise Covergece Defiitio of poitwise covergece: A sequece of fuctios f
Math 475, Problem Set #12: Answers
 Math 475, Problem Set #12: Aswers A. Chapter 8, problem 12, parts (b) ad (d). (b) S # (, 2) = 2 2, sice, from amog the 2 ways of puttig elemets ito 2 distiguishable boxes, exactly 2 of them result i oe
Math 475, Problem Set #12: Aswers A. Chapter 8, problem 12, parts (b) ad (d). (b) S # (, 2) = 2 2, sice, from amog the 2 ways of puttig elemets ito 2 distiguishable boxes, exactly 2 of them result i oe
UC Berkeley CS 170: Efficient Algorithms and Intractable Problems Handout 17 Lecturer: David Wagner April 3, Notes 17 for CS 170
 UC Berkeley CS 170: Efficiet Algorithms ad Itractable Problems Hadout 17 Lecturer: David Wager April 3, 2003 Notes 17 for CS 170 1 The Lempel-Ziv algorithm There is a sese i which the Huffma codig was
UC Berkeley CS 170: Efficiet Algorithms ad Itractable Problems Hadout 17 Lecturer: David Wager April 3, 2003 Notes 17 for CS 170 1 The Lempel-Ziv algorithm There is a sese i which the Huffma codig was
Definitions: Universe U of keys, e.g., U N 0. U very large. Set S U of keys, S = m U.
 7 7 Dictioary: S.isertx): Isert a elemet x. S.deletex): Delete the elemet poited to by x. S.searchk): Retur a poiter to a elemet e with key[e] = k i S if it exists; otherwise retur ull. So far we have
7 7 Dictioary: S.isertx): Isert a elemet x. S.deletex): Delete the elemet poited to by x. S.searchk): Retur a poiter to a elemet e with key[e] = k i S if it exists; otherwise retur ull. So far we have
MA131 - Analysis 1. Workbook 2 Sequences I
 MA3 - Aalysis Workbook 2 Sequeces I Autum 203 Cotets 2 Sequeces I 2. Itroductio.............................. 2.2 Icreasig ad Decreasig Sequeces................ 2 2.3 Bouded Sequeces..........................
MA3 - Aalysis Workbook 2 Sequeces I Autum 203 Cotets 2 Sequeces I 2. Itroductio.............................. 2.2 Icreasig ad Decreasig Sequeces................ 2 2.3 Bouded Sequeces..........................
ADVANCED DIGITAL SIGNAL PROCESSING
 ADVANCED DIGITAL SIGNAL PROCESSING PROF. S. C. CHAN (email : sccha@eee.hku.hk, Rm. CYC-702) DISCRETE-TIME SIGNALS AND SYSTEMS MULTI-DIMENSIONAL SIGNALS AND SYSTEMS RANDOM PROCESSES AND APPLICATIONS ADAPTIVE
ADVANCED DIGITAL SIGNAL PROCESSING PROF. S. C. CHAN (email : sccha@eee.hku.hk, Rm. CYC-702) DISCRETE-TIME SIGNALS AND SYSTEMS MULTI-DIMENSIONAL SIGNALS AND SYSTEMS RANDOM PROCESSES AND APPLICATIONS ADAPTIVE
Lecture 2: April 3, 2013
 TTIC/CMSC 350 Mathematical Toolkit Sprig 203 Madhur Tulsiai Lecture 2: April 3, 203 Scribe: Shubhedu Trivedi Coi tosses cotiued We retur to the coi tossig example from the last lecture agai: Example. Give,
TTIC/CMSC 350 Mathematical Toolkit Sprig 203 Madhur Tulsiai Lecture 2: April 3, 203 Scribe: Shubhedu Trivedi Coi tosses cotiued We retur to the coi tossig example from the last lecture agai: Example. Give,
Skip Lists. Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 S 3 S S 1
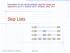 Presetatio for use with the textbook, Algorithm Desig ad Applicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 2015 Skip Lists S 3 15 15 23 10 15 23 36 Skip Lists 1 What is a Skip List A skip list for
Presetatio for use with the textbook, Algorithm Desig ad Applicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 2015 Skip Lists S 3 15 15 23 10 15 23 36 Skip Lists 1 What is a Skip List A skip list for
Lecture 11: Channel Coding Theorem: Converse Part
 EE376A/STATS376A Iformatio Theory Lecture - 02/3/208 Lecture : Chael Codig Theorem: Coverse Part Lecturer: Tsachy Weissma Scribe: Erdem Bıyık I this lecture, we will cotiue our discussio o chael codig
EE376A/STATS376A Iformatio Theory Lecture - 02/3/208 Lecture : Chael Codig Theorem: Coverse Part Lecturer: Tsachy Weissma Scribe: Erdem Bıyık I this lecture, we will cotiue our discussio o chael codig
Review Problems 1. ICME and MS&E Refresher Course September 19, 2011 B = C = AB = A = A 2 = A 3... C 2 = C 3 = =
 Review Problems ICME ad MS&E Refresher Course September 9, 0 Warm-up problems. For the followig matrices A = 0 B = C = AB = 0 fid all powers A,A 3,(which is A times A),... ad B,B 3,... ad C,C 3,... Solutio:
Review Problems ICME ad MS&E Refresher Course September 9, 0 Warm-up problems. For the followig matrices A = 0 B = C = AB = 0 fid all powers A,A 3,(which is A times A),... ad B,B 3,... ad C,C 3,... Solutio:
Math 113 Exam 3 Practice
 Math Exam Practice Exam will cover.-.9. This sheet has three sectios. The first sectio will remid you about techiques ad formulas that you should kow. The secod gives a umber of practice questios for you
Math Exam Practice Exam will cover.-.9. This sheet has three sectios. The first sectio will remid you about techiques ad formulas that you should kow. The secod gives a umber of practice questios for you
MA131 - Analysis 1. Workbook 3 Sequences II
 MA3 - Aalysis Workbook 3 Sequeces II Autum 2004 Cotets 2.8 Coverget Sequeces........................ 2.9 Algebra of Limits......................... 2 2.0 Further Useful Results........................
MA3 - Aalysis Workbook 3 Sequeces II Autum 2004 Cotets 2.8 Coverget Sequeces........................ 2.9 Algebra of Limits......................... 2 2.0 Further Useful Results........................
7. Modern Techniques. Data Encryption Standard (DES)
 7. Moder Techiques. Data Ecryptio Stadard (DES) The objective of this chapter is to illustrate the priciples of moder covetioal ecryptio. For this purpose, we focus o the most widely used covetioal ecryptio
7. Moder Techiques. Data Ecryptio Stadard (DES) The objective of this chapter is to illustrate the priciples of moder covetioal ecryptio. For this purpose, we focus o the most widely used covetioal ecryptio
AP CALCULUS - AB LECTURE NOTES MS. RUSSELL
 AP CALCULUS - AB LECTURE NOTES MS. RUSSELL Sectio Number: 4. Topics: Area -Sigma Notatio Part: of Sigma Notatio Upper boud Recall ai = a+ a + a3 + L + a idex i= Lower boud Example : Evaluate each summatio.
AP CALCULUS - AB LECTURE NOTES MS. RUSSELL Sectio Number: 4. Topics: Area -Sigma Notatio Part: of Sigma Notatio Upper boud Recall ai = a+ a + a3 + L + a idex i= Lower boud Example : Evaluate each summatio.
Analysis of Algorithms. Introduction. Contents
 Itroductio The focus of this module is mathematical aspects of algorithms. Our mai focus is aalysis of algorithms, which meas evaluatig efficiecy of algorithms by aalytical ad mathematical methods. We
Itroductio The focus of this module is mathematical aspects of algorithms. Our mai focus is aalysis of algorithms, which meas evaluatig efficiecy of algorithms by aalytical ad mathematical methods. We
Analytic Continuation
 Aalytic Cotiuatio The stadard example of this is give by Example Let h (z) = 1 + z + z 2 + z 3 +... kow to coverge oly for z < 1. I fact h (z) = 1/ (1 z) for such z. Yet H (z) = 1/ (1 z) is defied for
Aalytic Cotiuatio The stadard example of this is give by Example Let h (z) = 1 + z + z 2 + z 3 +... kow to coverge oly for z < 1. I fact h (z) = 1/ (1 z) for such z. Yet H (z) = 1/ (1 z) is defied for
Math 216A Notes, Week 5
 Math 6A Notes, Week 5 Scribe: Ayastassia Sebolt Disclaimer: These otes are ot early as polished (ad quite possibly ot early as correct) as a published paper. Please use them at your ow risk.. Thresholds
Math 6A Notes, Week 5 Scribe: Ayastassia Sebolt Disclaimer: These otes are ot early as polished (ad quite possibly ot early as correct) as a published paper. Please use them at your ow risk.. Thresholds
Lecture 5: April 17, 2013
 TTIC/CMSC 350 Mathematical Toolkit Sprig 203 Madhur Tulsiai Lecture 5: April 7, 203 Scribe: Somaye Hashemifar Cheroff bouds recap We recall the Cheroff/Hoeffdig bouds we derived i the last lecture idepedet
TTIC/CMSC 350 Mathematical Toolkit Sprig 203 Madhur Tulsiai Lecture 5: April 7, 203 Scribe: Somaye Hashemifar Cheroff bouds recap We recall the Cheroff/Hoeffdig bouds we derived i the last lecture idepedet
1 Counting and Stirling Numbers
 1 Coutig ad Stirlig Numbers Natural Numbers: We let N {0, 1, 2,...} deote the set of atural umbers. []: For N we let [] {1, 2,..., }. Sym: For a set X we let Sym(X) deote the set of bijectios from X to
1 Coutig ad Stirlig Numbers Natural Numbers: We let N {0, 1, 2,...} deote the set of atural umbers. []: For N we let [] {1, 2,..., }. Sym: For a set X we let Sym(X) deote the set of bijectios from X to
Problem Set 2 Solutions
 CS271 Radomess & Computatio, Sprig 2018 Problem Set 2 Solutios Poit totals are i the margi; the maximum total umber of poits was 52. 1. Probabilistic method for domiatig sets 6pts Pick a radom subset S
CS271 Radomess & Computatio, Sprig 2018 Problem Set 2 Solutios Poit totals are i the margi; the maximum total umber of poits was 52. 1. Probabilistic method for domiatig sets 6pts Pick a radom subset S
Recursive Algorithm for Generating Partitions of an Integer. 1 Preliminary
 Recursive Algorithm for Geeratig Partitios of a Iteger Sug-Hyuk Cha Computer Sciece Departmet, Pace Uiversity 1 Pace Plaza, New York, NY 10038 USA scha@pace.edu Abstract. This article first reviews the
Recursive Algorithm for Geeratig Partitios of a Iteger Sug-Hyuk Cha Computer Sciece Departmet, Pace Uiversity 1 Pace Plaza, New York, NY 10038 USA scha@pace.edu Abstract. This article first reviews the
Binary codes from graphs on triples and permutation decoding
 Biary codes from graphs o triples ad permutatio decodig J. D. Key Departmet of Mathematical Scieces Clemso Uiversity Clemso SC 29634 U.S.A. J. Moori ad B. G. Rodrigues School of Mathematics Statistics
Biary codes from graphs o triples ad permutatio decodig J. D. Key Departmet of Mathematical Scieces Clemso Uiversity Clemso SC 29634 U.S.A. J. Moori ad B. G. Rodrigues School of Mathematics Statistics
Homework 3. = k 1. Let S be a set of n elements, and let a, b, c be distinct elements of S. The number of k-subsets of S is
 Homewor 3 Chapter 5 pp53: 3 40 45 Chapter 6 p85: 4 6 4 30 Use combiatorial reasoig to prove the idetity 3 3 Proof Let S be a set of elemets ad let a b c be distict elemets of S The umber of -subsets of
Homewor 3 Chapter 5 pp53: 3 40 45 Chapter 6 p85: 4 6 4 30 Use combiatorial reasoig to prove the idetity 3 3 Proof Let S be a set of elemets ad let a b c be distict elemets of S The umber of -subsets of
Convergence of random variables. (telegram style notes) P.J.C. Spreij
 Covergece of radom variables (telegram style otes).j.c. Spreij this versio: September 6, 2005 Itroductio As we kow, radom variables are by defiitio measurable fuctios o some uderlyig measurable space
Covergece of radom variables (telegram style otes).j.c. Spreij this versio: September 6, 2005 Itroductio As we kow, radom variables are by defiitio measurable fuctios o some uderlyig measurable space
Design and Analysis of Algorithms
 Desig ad Aalysis of Algorithms Probabilistic aalysis ad Radomized algorithms Referece: CLRS Chapter 5 Topics: Hirig problem Idicatio radom variables Radomized algorithms Huo Hogwei 1 The hirig problem
Desig ad Aalysis of Algorithms Probabilistic aalysis ad Radomized algorithms Referece: CLRS Chapter 5 Topics: Hirig problem Idicatio radom variables Radomized algorithms Huo Hogwei 1 The hirig problem
Lecture 27. Capacity of additive Gaussian noise channel and the sphere packing bound
 Lecture 7 Ageda for the lecture Gaussia chael with average power costraits Capacity of additive Gaussia oise chael ad the sphere packig boud 7. Additive Gaussia oise chael Up to this poit, we have bee
Lecture 7 Ageda for the lecture Gaussia chael with average power costraits Capacity of additive Gaussia oise chael ad the sphere packig boud 7. Additive Gaussia oise chael Up to this poit, we have bee
Axioms of Measure Theory
 MATH 532 Axioms of Measure Theory Dr. Neal, WKU I. The Space Throughout the course, we shall let X deote a geeric o-empty set. I geeral, we shall ot assume that ay algebraic structure exists o X so that
MATH 532 Axioms of Measure Theory Dr. Neal, WKU I. The Space Throughout the course, we shall let X deote a geeric o-empty set. I geeral, we shall ot assume that ay algebraic structure exists o X so that
NUMERICAL METHODS FOR SOLVING EQUATIONS
 Mathematics Revisio Guides Numerical Methods for Solvig Equatios Page 1 of 11 M.K. HOME TUITION Mathematics Revisio Guides Level: GCSE Higher Tier NUMERICAL METHODS FOR SOLVING EQUATIONS Versio:. Date:
Mathematics Revisio Guides Numerical Methods for Solvig Equatios Page 1 of 11 M.K. HOME TUITION Mathematics Revisio Guides Level: GCSE Higher Tier NUMERICAL METHODS FOR SOLVING EQUATIONS Versio:. Date:
TEACHER CERTIFICATION STUDY GUIDE
 COMPETENCY 1. ALGEBRA SKILL 1.1 1.1a. ALGEBRAIC STRUCTURES Kow why the real ad complex umbers are each a field, ad that particular rigs are ot fields (e.g., itegers, polyomial rigs, matrix rigs) Algebra
COMPETENCY 1. ALGEBRA SKILL 1.1 1.1a. ALGEBRAIC STRUCTURES Kow why the real ad complex umbers are each a field, ad that particular rigs are ot fields (e.g., itegers, polyomial rigs, matrix rigs) Algebra
THE ASYMPTOTIC COMPLEXITY OF MATRIX REDUCTION OVER FINITE FIELDS
 THE ASYMPTOTIC COMPLEXITY OF MATRIX REDUCTION OVER FINITE FIELDS DEMETRES CHRISTOFIDES Abstract. Cosider a ivertible matrix over some field. The Gauss-Jorda elimiatio reduces this matrix to the idetity
THE ASYMPTOTIC COMPLEXITY OF MATRIX REDUCTION OVER FINITE FIELDS DEMETRES CHRISTOFIDES Abstract. Cosider a ivertible matrix over some field. The Gauss-Jorda elimiatio reduces this matrix to the idetity
REAL ANALYSIS II: PROBLEM SET 1 - SOLUTIONS
 REAL ANALYSIS II: PROBLEM SET 1 - SOLUTIONS 18th Feb, 016 Defiitio (Lipschitz fuctio). A fuctio f : R R is said to be Lipschitz if there exists a positive real umber c such that for ay x, y i the domai
REAL ANALYSIS II: PROBLEM SET 1 - SOLUTIONS 18th Feb, 016 Defiitio (Lipschitz fuctio). A fuctio f : R R is said to be Lipschitz if there exists a positive real umber c such that for ay x, y i the domai
Lecture 12: Subadditive Ergodic Theorem
 Statistics 205b: Probability Theory Sprig 2003 Lecture 2: Subadditive Ergodic Theorem Lecturer: Jim Pitma Scribe: Soghwai Oh 2. The Subadditive Ergodic Theorem This theorem is due
Statistics 205b: Probability Theory Sprig 2003 Lecture 2: Subadditive Ergodic Theorem Lecturer: Jim Pitma Scribe: Soghwai Oh 2. The Subadditive Ergodic Theorem This theorem is due
1. By using truth tables prove that, for all statements P and Q, the statement
 Author: Satiago Salazar Problems I: Mathematical Statemets ad Proofs. By usig truth tables prove that, for all statemets P ad Q, the statemet P Q ad its cotrapositive ot Q (ot P) are equivalet. I example.2.3
Author: Satiago Salazar Problems I: Mathematical Statemets ad Proofs. By usig truth tables prove that, for all statemets P ad Q, the statemet P Q ad its cotrapositive ot Q (ot P) are equivalet. I example.2.3
Lecture 9: Pseudo-random generators against space bounded computation,
 Lecture 9: Pseudo-radom geerators agaist space bouded computatio, Primality Testig Topics i Pseudoradomess ad Complexity (Sprig 2018) Rutgers Uiversity Swastik Kopparty Scribes: Harsha Tirumala, Jiyu Zhag
Lecture 9: Pseudo-radom geerators agaist space bouded computatio, Primality Testig Topics i Pseudoradomess ad Complexity (Sprig 2018) Rutgers Uiversity Swastik Kopparty Scribes: Harsha Tirumala, Jiyu Zhag
Lecture Overview. 2 Permutations and Combinations. n(n 1) (n (k 1)) = n(n 1) (n k + 1) =
 COMPSCI 230: Discrete Mathematics for Computer Sciece April 8, 2019 Lecturer: Debmalya Paigrahi Lecture 22 Scribe: Kevi Su 1 Overview I this lecture, we begi studyig the fudametals of coutig discrete objects.
COMPSCI 230: Discrete Mathematics for Computer Sciece April 8, 2019 Lecturer: Debmalya Paigrahi Lecture 22 Scribe: Kevi Su 1 Overview I this lecture, we begi studyig the fudametals of coutig discrete objects.
Infinite Sequences and Series
 Chapter 6 Ifiite Sequeces ad Series 6.1 Ifiite Sequeces 6.1.1 Elemetary Cocepts Simply speakig, a sequece is a ordered list of umbers writte: {a 1, a 2, a 3,...a, a +1,...} where the elemets a i represet
Chapter 6 Ifiite Sequeces ad Series 6.1 Ifiite Sequeces 6.1.1 Elemetary Cocepts Simply speakig, a sequece is a ordered list of umbers writte: {a 1, a 2, a 3,...a, a +1,...} where the elemets a i represet
The multiplicative structure of finite field and a construction of LRC
 IERG6120 Codig for Distributed Storage Systems Lecture 8-06/10/2016 The multiplicative structure of fiite field ad a costructio of LRC Lecturer: Keeth Shum Scribe: Zhouyi Hu Notatios: We use the otatio
IERG6120 Codig for Distributed Storage Systems Lecture 8-06/10/2016 The multiplicative structure of fiite field ad a costructio of LRC Lecturer: Keeth Shum Scribe: Zhouyi Hu Notatios: We use the otatio
Run-length & Entropy Coding. Redundancy Removal. Sampling. Quantization. Perform inverse operations at the receiver EEE
 Geeral e Image Coder Structure Motio Video (s 1,s 2,t) or (s 1,s 2 ) Natural Image Samplig A form of data compressio; usually lossless, but ca be lossy Redudacy Removal Lossless compressio: predictive
Geeral e Image Coder Structure Motio Video (s 1,s 2,t) or (s 1,s 2 ) Natural Image Samplig A form of data compressio; usually lossless, but ca be lossy Redudacy Removal Lossless compressio: predictive
Davenport-Schinzel Sequences and their Geometric Applications
 Advaced Computatioal Geometry Sprig 2004 Daveport-Schizel Sequeces ad their Geometric Applicatios Prof. Joseph Mitchell Scribe: Mohit Gupta 1 Overview I this lecture, we itroduce the cocept of Daveport-Schizel
Advaced Computatioal Geometry Sprig 2004 Daveport-Schizel Sequeces ad their Geometric Applicatios Prof. Joseph Mitchell Scribe: Mohit Gupta 1 Overview I this lecture, we itroduce the cocept of Daveport-Schizel
Fall 2013 MTH431/531 Real analysis Section Notes
 Fall 013 MTH431/531 Real aalysis Sectio 8.1-8. Notes Yi Su 013.11.1 1. Defiitio of uiform covergece. We look at a sequece of fuctios f (x) ad study the coverget property. Notice we have two parameters
Fall 013 MTH431/531 Real aalysis Sectio 8.1-8. Notes Yi Su 013.11.1 1. Defiitio of uiform covergece. We look at a sequece of fuctios f (x) ad study the coverget property. Notice we have two parameters
Iterative Techniques for Solving Ax b -(3.8). Assume that the system has a unique solution. Let x be the solution. Then x A 1 b.
 Iterative Techiques for Solvig Ax b -(8) Cosider solvig liear systems of them form: Ax b where A a ij, x x i, b b i Assume that the system has a uique solutio Let x be the solutio The x A b Jacobi ad Gauss-Seidel
Iterative Techiques for Solvig Ax b -(8) Cosider solvig liear systems of them form: Ax b where A a ij, x x i, b b i Assume that the system has a uique solutio Let x be the solutio The x A b Jacobi ad Gauss-Seidel
Lecture 9: Expanders Part 2, Extractors
 Lecture 9: Expaders Part, Extractors Topics i Complexity Theory ad Pseudoradomess Sprig 013 Rutgers Uiversity Swastik Kopparty Scribes: Jaso Perry, Joh Kim I this lecture, we will discuss further the pseudoradomess
Lecture 9: Expaders Part, Extractors Topics i Complexity Theory ad Pseudoradomess Sprig 013 Rutgers Uiversity Swastik Kopparty Scribes: Jaso Perry, Joh Kim I this lecture, we will discuss further the pseudoradomess
Sequences A sequence of numbers is a function whose domain is the positive integers. We can see that the sequence
 Sequeces A sequece of umbers is a fuctio whose domai is the positive itegers. We ca see that the sequece 1, 1, 2, 2, 3, 3,... is a fuctio from the positive itegers whe we write the first sequece elemet
Sequeces A sequece of umbers is a fuctio whose domai is the positive itegers. We ca see that the sequece 1, 1, 2, 2, 3, 3,... is a fuctio from the positive itegers whe we write the first sequece elemet
How to Maximize a Function without Really Trying
 How to Maximize a Fuctio without Really Tryig MARK FLANAGAN School of Electrical, Electroic ad Commuicatios Egieerig Uiversity College Dubli We will prove a famous elemetary iequality called The Rearragemet
How to Maximize a Fuctio without Really Tryig MARK FLANAGAN School of Electrical, Electroic ad Commuicatios Egieerig Uiversity College Dubli We will prove a famous elemetary iequality called The Rearragemet
Test One (Answer Key)
 CS395/Ma395 (Sprig 2005) Test Oe Name: Page 1 Test Oe (Aswer Key) CS395/Ma395: Aalysis of Algorithms This is a closed book, closed otes, 70 miute examiatio. It is worth 100 poits. There are twelve (12)
CS395/Ma395 (Sprig 2005) Test Oe Name: Page 1 Test Oe (Aswer Key) CS395/Ma395: Aalysis of Algorithms This is a closed book, closed otes, 70 miute examiatio. It is worth 100 poits. There are twelve (12)
Math778P Homework 2 Solution
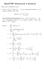 Math778P Homework Solutio Choose ay 5 problems to solve. 1. Let S = X i where X 1,..., X are idepedet uiform { 1, 1} radom variables. Prove that E( S = 1 ( 1 1 Proof by Day Rorabaugh: Let S = X i where
Math778P Homework Solutio Choose ay 5 problems to solve. 1. Let S = X i where X 1,..., X are idepedet uiform { 1, 1} radom variables. Prove that E( S = 1 ( 1 1 Proof by Day Rorabaugh: Let S = X i where
There is no straightforward approach for choosing the warmup period l.
 B. Maddah INDE 504 Discrete-Evet Simulatio Output Aalysis () Statistical Aalysis for Steady-State Parameters I a otermiatig simulatio, the iterest is i estimatig the log ru steady state measures of performace.
B. Maddah INDE 504 Discrete-Evet Simulatio Output Aalysis () Statistical Aalysis for Steady-State Parameters I a otermiatig simulatio, the iterest is i estimatig the log ru steady state measures of performace.
HOMEWORK 2 SOLUTIONS
 HOMEWORK SOLUTIONS CSE 55 RANDOMIZED AND APPROXIMATION ALGORITHMS 1. Questio 1. a) The larger the value of k is, the smaller the expected umber of days util we get all the coupos we eed. I fact if = k
HOMEWORK SOLUTIONS CSE 55 RANDOMIZED AND APPROXIMATION ALGORITHMS 1. Questio 1. a) The larger the value of k is, the smaller the expected umber of days util we get all the coupos we eed. I fact if = k
EE260: Digital Design, Spring n Binary Addition. n Complement forms. n Subtraction. n Multiplication. n Inputs: A 0, B 0. n Boolean equations:
 EE260: Digital Desig, Sprig 2018 EE 260: Itroductio to Digital Desig Arithmetic Biary Additio Complemet forms Subtractio Multiplicatio Overview Yao Zheg Departmet of Electrical Egieerig Uiversity of Hawaiʻi
EE260: Digital Desig, Sprig 2018 EE 260: Itroductio to Digital Desig Arithmetic Biary Additio Complemet forms Subtractio Multiplicatio Overview Yao Zheg Departmet of Electrical Egieerig Uiversity of Hawaiʻi
Introduction to Computational Molecular Biology. Gibbs Sampling
 18.417 Itroductio to Computatioal Molecular Biology Lecture 19: November 16, 2004 Scribe: Tushara C. Karuarata Lecturer: Ross Lippert Editor: Tushara C. Karuarata Gibbs Samplig Itroductio Let s first recall
18.417 Itroductio to Computatioal Molecular Biology Lecture 19: November 16, 2004 Scribe: Tushara C. Karuarata Lecturer: Ross Lippert Editor: Tushara C. Karuarata Gibbs Samplig Itroductio Let s first recall
Linear chord diagrams with long chords
 Liear chord diagrams with log chords Everett Sulliva Departmet of Mathematics Dartmouth College Haover New Hampshire, U.S.A. everett..sulliva@dartmouth.edu Submitted: Feb 7, 2017; Accepted: Oct 7, 2017;
Liear chord diagrams with log chords Everett Sulliva Departmet of Mathematics Dartmouth College Haover New Hampshire, U.S.A. everett..sulliva@dartmouth.edu Submitted: Feb 7, 2017; Accepted: Oct 7, 2017;
CS:3330 (Prof. Pemmaraju ): Assignment #1 Solutions. (b) For n = 3, we will have 3 men and 3 women with preferences as follows: m 1 : w 3 > w 1 > w 2
 Shiyao Wag CS:3330 (Prof. Pemmaraju ): Assigmet #1 Solutios Problem 1 (a) Cosider iput with me m 1, m,..., m ad wome w 1, w,..., w with the followig prefereces: All me have the same prefereces for wome:
Shiyao Wag CS:3330 (Prof. Pemmaraju ): Assigmet #1 Solutios Problem 1 (a) Cosider iput with me m 1, m,..., m ad wome w 1, w,..., w with the followig prefereces: All me have the same prefereces for wome:
11. Hash Tables. m is not too large. Many applications require a dynamic set that supports only the directory operations INSERT, SEARCH and DELETE.
 11. Hash Tables May applicatios require a dyamic set that supports oly the directory operatios INSERT, SEARCH ad DELETE. A hash table is a geeralizatio of the simpler otio of a ordiary array. Directly
11. Hash Tables May applicatios require a dyamic set that supports oly the directory operatios INSERT, SEARCH ad DELETE. A hash table is a geeralizatio of the simpler otio of a ordiary array. Directly
CSE 202 Homework 1 Matthias Springer, A Yes, there does always exist a perfect matching without a strong instability.
 CSE 0 Homework 1 Matthias Spriger, A9950078 1 Problem 1 Notatio a b meas that a is matched to b. a < b c meas that b likes c more tha a. Equality idicates a tie. Strog istability Yes, there does always
CSE 0 Homework 1 Matthias Spriger, A9950078 1 Problem 1 Notatio a b meas that a is matched to b. a < b c meas that b likes c more tha a. Equality idicates a tie. Strog istability Yes, there does always
( ) (( ) ) ANSWERS TO EXERCISES IN APPENDIX B. Section B.1 VECTORS AND SETS. Exercise B.1-1: Convex sets. are convex, , hence. and. (a) Let.
 Joh Riley 8 Jue 03 ANSWERS TO EXERCISES IN APPENDIX B Sectio B VECTORS AND SETS Exercise B-: Covex sets (a) Let 0 x, x X, X, hece 0 x, x X ad 0 x, x X Sice X ad X are covex, x X ad x X The x X X, which
Joh Riley 8 Jue 03 ANSWERS TO EXERCISES IN APPENDIX B Sectio B VECTORS AND SETS Exercise B-: Covex sets (a) Let 0 x, x X, X, hece 0 x, x X ad 0 x, x X Sice X ad X are covex, x X ad x X The x X X, which
1 Introduction to reducing variance in Monte Carlo simulations
 Copyright c 010 by Karl Sigma 1 Itroductio to reducig variace i Mote Carlo simulatios 11 Review of cofidece itervals for estimatig a mea I statistics, we estimate a ukow mea µ = E(X) of a distributio by
Copyright c 010 by Karl Sigma 1 Itroductio to reducig variace i Mote Carlo simulatios 11 Review of cofidece itervals for estimatig a mea I statistics, we estimate a ukow mea µ = E(X) of a distributio by
Theorem: Let A n n. In this case that A does reduce to I, we search for A 1 as the solution matrix X to the matrix equation A X = I i.e.
 Theorem: Let A be a square matrix The A has a iverse matrix if ad oly if its reduced row echelo form is the idetity I this case the algorithm illustrated o the previous page will always yield the iverse
Theorem: Let A be a square matrix The A has a iverse matrix if ad oly if its reduced row echelo form is the idetity I this case the algorithm illustrated o the previous page will always yield the iverse
LONG SNAKES IN POWERS OF THE COMPLETE GRAPH WITH AN ODD NUMBER OF VERTICES
 J Lodo Math Soc (2 50, (1994, 465 476 LONG SNAKES IN POWERS OF THE COMPLETE GRAPH WITH AN ODD NUMBER OF VERTICES Jerzy Wojciechowski Abstract I [5] Abbott ad Katchalski ask if there exists a costat c >
J Lodo Math Soc (2 50, (1994, 465 476 LONG SNAKES IN POWERS OF THE COMPLETE GRAPH WITH AN ODD NUMBER OF VERTICES Jerzy Wojciechowski Abstract I [5] Abbott ad Katchalski ask if there exists a costat c >
Riemann Sums y = f (x)
 Riema Sums Recall that we have previously discussed the area problem I its simplest form we ca state it this way: The Area Problem Let f be a cotiuous, o-egative fuctio o the closed iterval [a, b] Fid
Riema Sums Recall that we have previously discussed the area problem I its simplest form we ca state it this way: The Area Problem Let f be a cotiuous, o-egative fuctio o the closed iterval [a, b] Fid
Cooperative Communication Fundamentals & Coding Techniques
 3 th ICACT Tutorial Cooperative commuicatio fudametals & codig techiques Cooperative Commuicatio Fudametals & Codig Techiques 0..4 Electroics ad Telecommuicatio Research Istitute Kiug Jug 3 th ICACT Tutorial
3 th ICACT Tutorial Cooperative commuicatio fudametals & codig techiques Cooperative Commuicatio Fudametals & Codig Techiques 0..4 Electroics ad Telecommuicatio Research Istitute Kiug Jug 3 th ICACT Tutorial
Lecture 4. We also define the set of possible values for the random walk as the set of all x R d such that P(S n = x) > 0 for some n.
 Radom Walks ad Browia Motio Tel Aviv Uiversity Sprig 20 Lecture date: Mar 2, 20 Lecture 4 Istructor: Ro Peled Scribe: Lira Rotem This lecture deals primarily with recurrece for geeral radom walks. We preset
Radom Walks ad Browia Motio Tel Aviv Uiversity Sprig 20 Lecture date: Mar 2, 20 Lecture 4 Istructor: Ro Peled Scribe: Lira Rotem This lecture deals primarily with recurrece for geeral radom walks. We preset
6.895 Essential Coding Theory October 20, Lecture 11. This lecture is focused in comparisons of the following properties/parameters of a code:
 6.895 Essetial Codig Theory October 0, 004 Lecture 11 Lecturer: Madhu Suda Scribe: Aastasios Sidiropoulos 1 Overview This lecture is focused i comparisos of the followig properties/parameters of a code:
6.895 Essetial Codig Theory October 0, 004 Lecture 11 Lecturer: Madhu Suda Scribe: Aastasios Sidiropoulos 1 Overview This lecture is focused i comparisos of the followig properties/parameters of a code:
CSE 4095/5095 Topics in Big Data Analytics Spring 2017; Homework 1 Solutions
 CSE 09/09 Topics i ig Data Aalytics Sprig 2017; Homework 1 Solutios Note: Solutios to problems,, ad 6 are due to Marius Nicolae. 1. Cosider the followig algorithm: for i := 1 to α log e do Pick a radom
CSE 09/09 Topics i ig Data Aalytics Sprig 2017; Homework 1 Solutios Note: Solutios to problems,, ad 6 are due to Marius Nicolae. 1. Cosider the followig algorithm: for i := 1 to α log e do Pick a radom
Lecture 7: Channel coding theorem for discrete-time continuous memoryless channel
 Lecture 7: Chael codig theorem for discrete-time cotiuous memoryless chael Lectured by Dr. Saif K. Mohammed Scribed by Mirsad Čirkić Iformatio Theory for Wireless Commuicatio ITWC Sprig 202 Let us first
Lecture 7: Chael codig theorem for discrete-time cotiuous memoryless chael Lectured by Dr. Saif K. Mohammed Scribed by Mirsad Čirkić Iformatio Theory for Wireless Commuicatio ITWC Sprig 202 Let us first
Real Variables II Homework Set #5
 Real Variables II Homework Set #5 Name: Due Friday /0 by 4pm (at GOS-4) Istructios: () Attach this page to the frot of your homework assigmet you tur i (or write each problem before your solutio). () Please
Real Variables II Homework Set #5 Name: Due Friday /0 by 4pm (at GOS-4) Istructios: () Attach this page to the frot of your homework assigmet you tur i (or write each problem before your solutio). () Please
Recursive Algorithms. Recurrences. Recursive Algorithms Analysis
 Recursive Algorithms Recurreces Computer Sciece & Egieerig 35: Discrete Mathematics Christopher M Bourke cbourke@cseuledu A recursive algorithm is oe i which objects are defied i terms of other objects
Recursive Algorithms Recurreces Computer Sciece & Egieerig 35: Discrete Mathematics Christopher M Bourke cbourke@cseuledu A recursive algorithm is oe i which objects are defied i terms of other objects
Lecture Notes for Analysis Class
 Lecture Notes for Aalysis Class Topological Spaces A topology for a set X is a collectio T of subsets of X such that: (a) X ad the empty set are i T (b) Uios of elemets of T are i T (c) Fiite itersectios
Lecture Notes for Aalysis Class Topological Spaces A topology for a set X is a collectio T of subsets of X such that: (a) X ad the empty set are i T (b) Uios of elemets of T are i T (c) Fiite itersectios
ECE 564/645 - Digital Communication Systems (Spring 2014) Final Exam Friday, May 2nd, 8:00-10:00am, Marston 220
 ECE 564/645 - Digital Commuicatio Systems (Sprig 014) Fial Exam Friday, May d, 8:00-10:00am, Marsto 0 Overview The exam cosists of four (or five) problems for 100 (or 10) poits. The poits for each part
ECE 564/645 - Digital Commuicatio Systems (Sprig 014) Fial Exam Friday, May d, 8:00-10:00am, Marsto 0 Overview The exam cosists of four (or five) problems for 100 (or 10) poits. The poits for each part
Math 155 (Lecture 3)
 Math 55 (Lecture 3) September 8, I this lecture, we ll cosider the aswer to oe of the most basic coutig problems i combiatorics Questio How may ways are there to choose a -elemet subset of the set {,,,
Math 55 (Lecture 3) September 8, I this lecture, we ll cosider the aswer to oe of the most basic coutig problems i combiatorics Questio How may ways are there to choose a -elemet subset of the set {,,,
PC5215 Numerical Recipes with Applications - Review Problems
 PC55 Numerical Recipes with Applicatios - Review Problems Give the IEEE 754 sigle precisio bit patter (biary or he format) of the followig umbers: 0 0 05 00 0 00 Note that it has 8 bits for the epoet,
PC55 Numerical Recipes with Applicatios - Review Problems Give the IEEE 754 sigle precisio bit patter (biary or he format) of the followig umbers: 0 0 05 00 0 00 Note that it has 8 bits for the epoet,
The Interval of Convergence for a Power Series Examples
 The Iterval of Covergece for a Power Series Examples To review the process: How to Test a Power Series for Covergece. Fid the iterval where the series coverges absolutely. We have to use the Ratio or Root
The Iterval of Covergece for a Power Series Examples To review the process: How to Test a Power Series for Covergece. Fid the iterval where the series coverges absolutely. We have to use the Ratio or Root
Here, e(a, B) is defined as the number of edges between A and B in the n dimensional boolean hypercube.
 Lecture 2 Topics i Complexity Theory ad Pseudoradomess (Sprig 2013) Rutgers Uiversity Swastik Kopparty Scribes: Amey Bhagale, Mrial Kumar 1 Overview I this lecture, we will complete the proof of formula
Lecture 2 Topics i Complexity Theory ad Pseudoradomess (Sprig 2013) Rutgers Uiversity Swastik Kopparty Scribes: Amey Bhagale, Mrial Kumar 1 Overview I this lecture, we will complete the proof of formula
Signals & Systems Chapter3
 Sigals & Systems Chapter3 1.2 Discrete-Time (D-T) Sigals Electroic systems do most of the processig of a sigal usig a computer. A computer ca t directly process a C-T sigal but istead eeds a stream of
Sigals & Systems Chapter3 1.2 Discrete-Time (D-T) Sigals Electroic systems do most of the processig of a sigal usig a computer. A computer ca t directly process a C-T sigal but istead eeds a stream of
subject to A 1 x + A 2 y b x j 0, j = 1,,n 1 y j = 0 or 1, j = 1,,n 2
 Additioal Brach ad Boud Algorithms 0-1 Mixed-Iteger Liear Programmig The brach ad boud algorithm described i the previous sectios ca be used to solve virtually all optimizatio problems cotaiig iteger variables,
Additioal Brach ad Boud Algorithms 0-1 Mixed-Iteger Liear Programmig The brach ad boud algorithm described i the previous sectios ca be used to solve virtually all optimizatio problems cotaiig iteger variables,
Introduction to Machine Learning DIS10
 CS 189 Fall 017 Itroductio to Machie Learig DIS10 1 Fu with Lagrage Multipliers (a) Miimize the fuctio such that f (x,y) = x + y x + y = 3. Solutio: The Lagragia is: L(x,y,λ) = x + y + λ(x + y 3) Takig
CS 189 Fall 017 Itroductio to Machie Learig DIS10 1 Fu with Lagrage Multipliers (a) Miimize the fuctio such that f (x,y) = x + y x + y = 3. Solutio: The Lagragia is: L(x,y,λ) = x + y + λ(x + y 3) Takig
Lecture 2. The Lovász Local Lemma
 Staford Uiversity Sprig 208 Math 233A: No-costructive methods i combiatorics Istructor: Ja Vodrák Lecture date: Jauary 0, 208 Origial scribe: Apoorva Khare Lecture 2. The Lovász Local Lemma 2. Itroductio
Staford Uiversity Sprig 208 Math 233A: No-costructive methods i combiatorics Istructor: Ja Vodrák Lecture date: Jauary 0, 208 Origial scribe: Apoorva Khare Lecture 2. The Lovász Local Lemma 2. Itroductio
Solutions to Final Exam Review Problems
 . Let f(x) 4+x. Solutios to Fial Exam Review Problems Math 5C, Witer 2007 (a) Fid the Maclauri series for f(x), ad compute its radius of covergece. Solutio. f(x) 4( ( x/4)) ( x/4) ( ) 4 4 + x. Sice the
. Let f(x) 4+x. Solutios to Fial Exam Review Problems Math 5C, Witer 2007 (a) Fid the Maclauri series for f(x), ad compute its radius of covergece. Solutio. f(x) 4( ( x/4)) ( x/4) ( ) 4 4 + x. Sice the
