The Paillier Cryptosystem
|
|
|
- Jeffery Goodman
- 6 years ago
- Views:
Transcription
1 E-Votig Semiar The Paillier Cryptosystem Adreas Steffe Hochschule für Techik Rapperswil Adreas Steffe, , Paillier.pptx 1
2 Ageda Some mathematical properties Ecryptio ad decryptio Additive homomorphic properties Zero kowledge proof for -th powers Paillier e-votig simulator No-iteractive ZKP usig the Fiat-Shamir heuristic Damgård-Jurik Cryptosystem (Geeralized Paillier) Damgård-Jurik JavaScript e-votig cliet Threshold decryptio schemes Adreas Steffe, , Paillier.pptx
3 The Paillier Cryptosystem I Proposed by Pascal Paillier i 1999: Choose two large prime umbers p ad q ad form the modulus pq Euler s totiet fuctio gives the umber of elemets i ( ) ( p 1)( q 1) The umber of elemets i is ( ) ( ) The private key is determied usig Carmichael s fuctio ( ) lcm( p 1, q 1) Due to Carmichael s theorem, for every elemet 1 mod 1 mod Adreas Steffe, , Paillier.pptx 3
4 The Paillier Cryptosystem II The hard problem: Decidig -th composite residuosity! z y mod The set of -th residues is a multiplicative subgroup of of order () Each -th residue z has exactly roots of degree, amog which exactly oe is strictly smaller tha, amely r z mod, r The -th roots of uity are the umbers of the form m (1 ) 1 m mod, m Geerate the multiplicative subgroup as m ( m, r) g r mod c Paillier Ecryptio m: plaitext message, r: radom umber for sematic security Adreas Steffe, , Paillier.pptx 4
5 Example: Multiplicative Subgroup m g^m r r^ p = 3, q = 5, = 15, = 5 Geerator i most geeral form: () = 8, () = lcm(, 4) = 4 g ( 1 ),, Adreas Steffe, , Paillier.pptx 5
6 Paillier Decryptio m L( c L( g mod mod ) ) mod with L( x) x 1 Apply the private key ad use Carmichael s theorem m m m c ( g r ) g r g Make use of the relatioship ( 1 ) x 1 x mod m m m m g (( 1 ) ) (1 ) (1 m) mod Apply the L(x) fuctio L(1 m) m mod m L(1 ) Adreas Steffe, , Paillier.pptx 6
7 Additive Homomorphic Properties D( E( m1 ) E( m ) mod ) m1 m mod Verificatio E ( m 1 m m m1 m 1) E( m ) g r1 g r g r1 r mod D( E( m) k mod ) k m mod Use i e-votig systems with homomorphic tallyig: The additive homomorphic property directly returig the tally is the biggest advatage of the Paillier Cryptosystem over the El Gamal Cryptosystem which has a itrisically multiplicative homomorphic property requirig the computatio of a discrete logarithm over a bouded rage to extract the tally. Adreas Steffe, , Paillier.pptx 7
8 Validity Proof of Ballot (Case: k = i) K valid votig messages (e.g. vote for oe out of K cadidates) m, m, 1, m k,, m K Zero kowledge proof : Prove that u k is a -th power mi c g r uk mod r oly if m m m i mk k k g g Commitmet: Prover chooses a radom umber a i mod, Challege: Verifier chooses a radom bit strig e i of legth b b b ei, mi( p, q) Respose: Prover computes z i ei zi r mod ei Verificatio: z a u mod i i i z i ei ei ( r ) r mod Adreas Steffe, , Paillier.pptx 8
9 Validity Proof of Ballot (Cases: k i) Preparatio: Prover chooses z k ad bit strig e k radomly b b zk, ek, mi( p, q) Commitmet: Prover computes a k so that it passes verificatio zk ak mod e u k k Challege: Verifier chooses a radom bit strig e of legth b b b e, mi( p, q) Respose: Prover seds prepared z k ad e k ek Verificatio: z a u mod k k k K k1 e e mod k b Prover ca preselect all e k for k i but is boud by e for the choice of e i. Adreas Steffe, , Paillier.pptx 9
10 Paillier E-Votig Simulator Adreas Steffe, , Paillier.pptx 10
11 E-Votig Simulator Tallyig with ZKPs Adreas Steffe, , Paillier.pptx 11
12 No-Iteractive ZKP (Fiat-Shamir Heuristic) Electio ID Voter ID Ecrypted Ballot c Commitmets a k SHA-56 Couter 56 bit key AES-56 Couter Mode Challege Bit Strig e Adreas Steffe, , Paillier.pptx 1
13 The Damgård-Jurik Cryptosystem Additioal parameter s (Paillier: s = 1) ( m, r) g m r s mod s1 c m: plaitext message, r: radom umber for sematic security Geerate the multiplicative subgroup Geerator usually chose as g = (1+) s1 as s s1 Size of modulus : b bits (e.g bits) Size of message m: sb - 1 bits (s=1: 1535 bits, s=: 3071 bits) Size of ciphertext c: (s+1)b (s=1: 307 bits, s=: 4608 bits) Efficiecy: = s/(s+1) (s=1: 50%, s=: 67%, s=3: 75%) Adreas Steffe, , Paillier.pptx 13
14 Damgård-Jurik JavaScript E-Votig Cliet Adreas Steffe, , Paillier.pptx 14
15 Damgård-Jurik JavaScript E-Votig Cliet Adreas Steffe, , Paillier.pptx 15
16 Commitmet Adreas Steffe, , Paillier.pptx 16
17 Challege Verificatio Adreas Steffe, , Paillier.pptx 17
18 Respose Verificatio Adreas Steffe, , Paillier.pptx 18
19 Threshold Scheme with a Trusted Dealer Adreas Steffe, , Paillier.pptx 19
20 Threshold Scheme without a Trusted Dealer Practical threshold RSA sigatures without a trusted dealer Iva Damgard, Maciej Koprowski, 001 The distributed geeratio of a RSA private key required by a Threshold Paillier Cryptosystem is much more complex tha the simple idepedet partial private key geeratio possible with the El Gamal Cryptosystem. Adreas Steffe, , Paillier.pptx 0
Review of Elementary Cryptography. For more material, see my notes of CSE 5351, available on my webpage
 Review of Elemetary Cryptography For more material, see my otes of CSE 5351, available o my webpage Outlie Security (CPA, CCA, sematic security, idistiguishability) RSA ElGamal Homomorphic ecryptio 2 Two
Review of Elemetary Cryptography For more material, see my otes of CSE 5351, available o my webpage Outlie Security (CPA, CCA, sematic security, idistiguishability) RSA ElGamal Homomorphic ecryptio 2 Two
Factoring Algorithms and Other Attacks on the RSA 1/12
 Factorig Algorithms ad Other Attacks o the RSA T-79550 Cryptology Lecture 8 April 8, 008 Kaisa Nyberg Factorig Algorithms ad Other Attacks o the RSA / The Pollard p Algorithm Let B be a positive iteger
Factorig Algorithms ad Other Attacks o the RSA T-79550 Cryptology Lecture 8 April 8, 008 Kaisa Nyberg Factorig Algorithms ad Other Attacks o the RSA / The Pollard p Algorithm Let B be a positive iteger
Message Authentication Codes. Reading: Chapter 4 of Katz & Lindell
 Message Autheticatio Codes Readig: Chapter 4 of Katz & Lidell 1 Message autheticatio Bob receives a message m from Alice, he wats to ow (Data origi autheticatio) whether the message was really set by Alice.
Message Autheticatio Codes Readig: Chapter 4 of Katz & Lidell 1 Message autheticatio Bob receives a message m from Alice, he wats to ow (Data origi autheticatio) whether the message was really set by Alice.
A Generalization of Paillier s Public-Key System with Applications to Electronic Voting
 A Generalization of Paillier s Public-Key System with Applications to Electronic Voting Ivan Damgård, Mads Jurik and Jesper Buus Nielsen Aarhus University, Dept. of Computer Science, BRICS Abstract. We
A Generalization of Paillier s Public-Key System with Applications to Electronic Voting Ivan Damgård, Mads Jurik and Jesper Buus Nielsen Aarhus University, Dept. of Computer Science, BRICS Abstract. We
1 Summary: Binary and Logic
 1 Summary: Biary ad Logic Biary Usiged Represetatio : each 1-bit is a power of two, the right-most is for 2 0 : 0110101 2 = 2 5 + 2 4 + 2 2 + 2 0 = 32 + 16 + 4 + 1 = 53 10 Usiged Rage o bits is [0...2
1 Summary: Biary ad Logic Biary Usiged Represetatio : each 1-bit is a power of two, the right-most is for 2 0 : 0110101 2 = 2 5 + 2 4 + 2 2 + 2 0 = 32 + 16 + 4 + 1 = 53 10 Usiged Rage o bits is [0...2
An Overview of Homomorphic Encryption
 An Overview of Homomorphic Encryption Alexander Lange Department of Computer Science Rochester Institute of Technology Rochester, NY 14623 May 9, 2011 Alexander Lange (RIT) Homomorphic Encryption May 9,
An Overview of Homomorphic Encryption Alexander Lange Department of Computer Science Rochester Institute of Technology Rochester, NY 14623 May 9, 2011 Alexander Lange (RIT) Homomorphic Encryption May 9,
Lecture 11: Pseudorandom functions
 COM S 6830 Cryptography Oct 1, 2009 Istructor: Rafael Pass 1 Recap Lecture 11: Pseudoradom fuctios Scribe: Stefao Ermo Defiitio 1 (Ge, Ec, Dec) is a sigle message secure ecryptio scheme if for all uppt
COM S 6830 Cryptography Oct 1, 2009 Istructor: Rafael Pass 1 Recap Lecture 11: Pseudoradom fuctios Scribe: Stefao Ermo Defiitio 1 (Ge, Ec, Dec) is a sigle message secure ecryptio scheme if for all uppt
Estimating the φ(n) of Upper/Lower Bound in its RSA Cryptosystem
 Estimatig the φ() of Upper/Lower Boud i its RSA Cryptosystem Cheglia Liu 1 ad Ziwei Ye 2 1 Departmet of Electrical Egieerig, Natioal Tsig-Hua Uiversity, Taiwa cheglia.liu@gmail.com 2 Departmet of Computer
Estimatig the φ() of Upper/Lower Boud i its RSA Cryptosystem Cheglia Liu 1 ad Ziwei Ye 2 1 Departmet of Electrical Egieerig, Natioal Tsig-Hua Uiversity, Taiwa cheglia.liu@gmail.com 2 Departmet of Computer
7. Modern Techniques. Data Encryption Standard (DES)
 7. Moder Techiques. Data Ecryptio Stadard (DES) The objective of this chapter is to illustrate the priciples of moder covetioal ecryptio. For this purpose, we focus o the most widely used covetioal ecryptio
7. Moder Techiques. Data Ecryptio Stadard (DES) The objective of this chapter is to illustrate the priciples of moder covetioal ecryptio. For this purpose, we focus o the most widely used covetioal ecryptio
International Journal of Engineering Science Invention Research & Development; Vol. II Issue VIII February e-issn:
 Iteratioal Joural of Egieerig Sciece Ivetio Research & Developmet; Vol. II Issue VIII February 216 www.ijesird.com eissn: 236 MULTIPLE ENCRYPTIONS OF VARIOUS CIPHERS A. ChadraSekhar*,1, B.Ravi Kumar 2,
Iteratioal Joural of Egieerig Sciece Ivetio Research & Developmet; Vol. II Issue VIII February 216 www.ijesird.com eissn: 236 MULTIPLE ENCRYPTIONS OF VARIOUS CIPHERS A. ChadraSekhar*,1, B.Ravi Kumar 2,
Lossy Trapdoor Functions from Smooth Homomorphic Hash Proof Systems
 Electroic Colloquium o Computatioal Complexity, Revisio 1 of Report No 127 (2009) Lossy Trapdoor Fuctios from Smooth Homomorphic Hash Proof Systems July 4, 2010 Abstract I STOC 08, Peikert ad Waters itroduced
Electroic Colloquium o Computatioal Complexity, Revisio 1 of Report No 127 (2009) Lossy Trapdoor Fuctios from Smooth Homomorphic Hash Proof Systems July 4, 2010 Abstract I STOC 08, Peikert ad Waters itroduced
Lecture Notes 15 : Voting, Homomorphic Encryption
 6.857 Computer and Network Security October 29, 2002 Lecture Notes 15 : Voting, Homomorphic Encryption Lecturer: Ron Rivest Scribe: Ledlie/Ortiz/Paskalev/Zhao 1 Introduction The big picture and where we
6.857 Computer and Network Security October 29, 2002 Lecture Notes 15 : Voting, Homomorphic Encryption Lecturer: Ron Rivest Scribe: Ledlie/Ortiz/Paskalev/Zhao 1 Introduction The big picture and where we
Non-Interactive Zero-Knowledge from Homomorphic Encryption. Ivan Damgård (Aarhus Universitet) Nelly Fazio, Antonio Nicolosi (NYU)
 Non-Interactive Zero-Knowledge from Homomorphic Encryption Ivan Damgård (Aarhus Universitet) Nelly Fazio, Antonio Nicolosi (NYU) January 27th, 2006 NYU Crypto Reading Group Zero-Knowledge and Interaction
Non-Interactive Zero-Knowledge from Homomorphic Encryption Ivan Damgård (Aarhus Universitet) Nelly Fazio, Antonio Nicolosi (NYU) January 27th, 2006 NYU Crypto Reading Group Zero-Knowledge and Interaction
Simon Blackburn. Sean Murphy. Jacques Stern. Laboratoire d'informatique, Ecole Normale Superieure, Abstract
 The Cryptaalysis of a Public Key Implemetatio of Fiite Group Mappigs Simo Blackbur Sea Murphy Iformatio Security Group, Royal Holloway ad Bedford New College, Uiversity of Lodo, Egham, Surrey TW20 0EX,
The Cryptaalysis of a Public Key Implemetatio of Fiite Group Mappigs Simo Blackbur Sea Murphy Iformatio Security Group, Royal Holloway ad Bedford New College, Uiversity of Lodo, Egham, Surrey TW20 0EX,
Solutions to Math 347 Practice Problems for the final
 Solutios to Math 347 Practice Problems for the fial 1) True or False: a) There exist itegers x,y such that 50x + 76y = 6. True: the gcd of 50 ad 76 is, ad 6 is a multiple of. b) The ifiimum of a set is
Solutios to Math 347 Practice Problems for the fial 1) True or False: a) There exist itegers x,y such that 50x + 76y = 6. True: the gcd of 50 ad 76 is, ad 6 is a multiple of. b) The ifiimum of a set is
Two-Input Functional Encryption for Inner Products from Bilinear Maps
 Two-Iput Fuctioal Ecryptio for Ier Products from Biliear Maps Kwagsu Lee Dog Hoo Lee Abstract Fuctioal ecryptio is a ew paradigm of public-key ecryptio that allows a user to compute f x o ecrypted data
Two-Iput Fuctioal Ecryptio for Ier Products from Biliear Maps Kwagsu Lee Dog Hoo Lee Abstract Fuctioal ecryptio is a ew paradigm of public-key ecryptio that allows a user to compute f x o ecrypted data
Extracting Witnesses from Proofs of Knowledge in the Random Oracle Model
 Extracting Witnesses from Proofs of Knowledge in the Random Oracle Model Jens Groth Cryptomathic and BRICS, Aarhus University Abstract We prove that a 3-move interactive proof system with the special soundness
Extracting Witnesses from Proofs of Knowledge in the Random Oracle Model Jens Groth Cryptomathic and BRICS, Aarhus University Abstract We prove that a 3-move interactive proof system with the special soundness
Injections, Surjections, and the Pigeonhole Principle
 Ijectios, Surjectios, ad the Pigeohole Priciple 1 (10 poits Here we will come up with a sloppy boud o the umber of parethesisestigs (a (5 poits Describe a ijectio from the set of possible ways to est pairs
Ijectios, Surjectios, ad the Pigeohole Priciple 1 (10 poits Here we will come up with a sloppy boud o the umber of parethesisestigs (a (5 poits Describe a ijectio from the set of possible ways to est pairs
Efficient Multiplicative Homomorphic E-Voting
 Efficient Multiplicative Homomorphic E-Voting Kun Peng and Feng Bao Institute for Infocomm Research, Singapore dr.kun.peng@gmail.com Abstract. Multiplicative homomorphic e-voting is proposed by Peng et
Efficient Multiplicative Homomorphic E-Voting Kun Peng and Feng Bao Institute for Infocomm Research, Singapore dr.kun.peng@gmail.com Abstract. Multiplicative homomorphic e-voting is proposed by Peng et
Threshold Undeniable RSA Signature Scheme
 Threshold Undeniable RSA Signature Scheme Guilin Wang 1, Sihan Qing 1, Mingsheng Wang 1, and Zhanfei Zhou 2 1 Engineering Research Center for Information Security Technology; State Key Laboratory of Information
Threshold Undeniable RSA Signature Scheme Guilin Wang 1, Sihan Qing 1, Mingsheng Wang 1, and Zhanfei Zhou 2 1 Engineering Research Center for Information Security Technology; State Key Laboratory of Information
The structure of finite rings. The multiplicative residues. Modular exponentiation. and finite exponentiation
 The structure of fiite rigs ad fiite expoetiatio The multiplicative residues We have see that the fiite rig Z p is a field, that is, every o-zero elemet of Z p has a multiplicative iverse It is a covetio
The structure of fiite rigs ad fiite expoetiatio The multiplicative residues We have see that the fiite rig Z p is a field, that is, every o-zero elemet of Z p has a multiplicative iverse It is a covetio
ORTHOGONAL MATRIX IN CRYPTOGRAPHY
 Orthogoal Matrix i Cryptography ORTHOGONAL MATRIX IN CRYPTOGRAPHY Yeray Cachó Sataa Member of CriptoRed (U.P.M.) ABSTRACT I this work is proposed a method usig orthogoal matrix trasform properties to ecrypt
Orthogoal Matrix i Cryptography ORTHOGONAL MATRIX IN CRYPTOGRAPHY Yeray Cachó Sataa Member of CriptoRed (U.P.M.) ABSTRACT I this work is proposed a method usig orthogoal matrix trasform properties to ecrypt
Towards a DL-based Additively Homomorphic Encryption Scheme
 Towards a DL-based Additively Homomorphic Encryption Scheme Guilhem Castagnos 1 and Benoît Chevallier-Mames 2 1 DMI-XLIM, Université de Limoges, 123, Avenue Albert-Thomas 87060 Limoges Cedex, France guilhem.castagnos@unilim.fr
Towards a DL-based Additively Homomorphic Encryption Scheme Guilhem Castagnos 1 and Benoît Chevallier-Mames 2 1 DMI-XLIM, Université de Limoges, 123, Avenue Albert-Thomas 87060 Limoges Cedex, France guilhem.castagnos@unilim.fr
An extension of the RSA trapdoor in a KEM/DEM framework
 A extesio of the RSA trapdoor i a KEM/DEM framework Bogda Groza Politehica Uiversity of Timisoara Faculty of Automatics ad Computers Bd. Vasile Parva r. 2, 300223 Timisoara, Romaia mail: bogda.groza@aut.upt.ro
A extesio of the RSA trapdoor i a KEM/DEM framework Bogda Groza Politehica Uiversity of Timisoara Faculty of Automatics ad Computers Bd. Vasile Parva r. 2, 300223 Timisoara, Romaia mail: bogda.groza@aut.upt.ro
Oblivious Transfer using Elliptic Curves
 Oblivious Trasfer usig Elliptic Curves bhishek Parakh Louisiaa State Uiversity, ato Rouge, L May 4, 006 bstract: This paper proposes a algorithm for oblivious trasfer usig elliptic curves lso, we preset
Oblivious Trasfer usig Elliptic Curves bhishek Parakh Louisiaa State Uiversity, ato Rouge, L May 4, 006 bstract: This paper proposes a algorithm for oblivious trasfer usig elliptic curves lso, we preset
Winter 2011 Josh Benaloh Brian LaMacchia
 Winter 2011 Josh Benaloh Brian LaMacchia Fun with Public-Key Tonight we ll Introduce some basic tools of public-key crypto Combine the tools to create more powerful tools Lay the ground work for substantial
Winter 2011 Josh Benaloh Brian LaMacchia Fun with Public-Key Tonight we ll Introduce some basic tools of public-key crypto Combine the tools to create more powerful tools Lay the ground work for substantial
Last time, we talked about how Equation (1) can simulate Equation (2). We asserted that Equation (2) can also simulate Equation (1).
 6896 Quatum Complexity Theory Sept 23, 2008 Lecturer: Scott Aaroso Lecture 6 Last Time: Quatum Error-Correctio Quatum Query Model Deutsch-Jozsa Algorithm (Computes x y i oe query) Today: Berstei-Vazirii
6896 Quatum Complexity Theory Sept 23, 2008 Lecturer: Scott Aaroso Lecture 6 Last Time: Quatum Error-Correctio Quatum Query Model Deutsch-Jozsa Algorithm (Computes x y i oe query) Today: Berstei-Vazirii
Homomorphic Encryption. Liam Morris
 Homomorphic Encryption Liam Morris Topics What Is Homomorphic Encryption? Partially Homomorphic Cryptosystems Fully Homomorphic Cryptosystems Benefits of Homomorphism Drawbacks of Homomorphism What Is
Homomorphic Encryption Liam Morris Topics What Is Homomorphic Encryption? Partially Homomorphic Cryptosystems Fully Homomorphic Cryptosystems Benefits of Homomorphism Drawbacks of Homomorphism What Is
Minimum-Knowledge Schemes for low-power, low-memory Devices
 Miimum-Kowledge Schemes for low-power, low-memory Deices T. Newe & T. Coffey Data Commuicatios Security Group, Departmet of lectroic & Computer gieerig, Uiersity of imerick, relad. Fax: 353-61-338176 Abstract
Miimum-Kowledge Schemes for low-power, low-memory Deices T. Newe & T. Coffey Data Commuicatios Security Group, Departmet of lectroic & Computer gieerig, Uiersity of imerick, relad. Fax: 353-61-338176 Abstract
Definition: For a positive integer n, if 0<a<n and gcd(a,n)=1, a is relatively prime to n. Ahmet Burak Can Hacettepe University
 Number Theory, Public Key Cryptography, RSA Ahmet Burak Can Hacettepe University abc@hacettepe.edu.tr The Euler Phi Function For a positive integer n, if 0
Number Theory, Public Key Cryptography, RSA Ahmet Burak Can Hacettepe University abc@hacettepe.edu.tr The Euler Phi Function For a positive integer n, if 0
Gentry s ideal-lattice based encryption scheme. Gentry s STOC 09 paper - Part III
 Getry s ideal-lattice based ecryptio scheme Getry s STOC 09 paper - Part 1 From Micciacio's paper Why ideal lattices --- as opposed to just ideals or lattices? We described a ideal-based ecryptio scheme
Getry s ideal-lattice based ecryptio scheme Getry s STOC 09 paper - Part 1 From Micciacio's paper Why ideal lattices --- as opposed to just ideals or lattices? We described a ideal-based ecryptio scheme
CPE 776:DATA SECURITY & CRYPTOGRAPHY. Some Number Theory and Classical Crypto Systems
 CPE 776:DATA SECURITY & CRYPTOGRAPHY Some Number Theory and Classical Crypto Systems Dr. Lo ai Tawalbeh Computer Engineering Department Jordan University of Science and Technology Jordan Some Number Theory
CPE 776:DATA SECURITY & CRYPTOGRAPHY Some Number Theory and Classical Crypto Systems Dr. Lo ai Tawalbeh Computer Engineering Department Jordan University of Science and Technology Jordan Some Number Theory
Improving Helios with Everlasting Privacy Towards the Public Denise Demirel, Jeroen van de Graaf, Roberto Araújo
 Improving Helios with Everlasting Privacy Towards the Public Denise Demirel, Jeroen van de Graaf, Roberto Araúo 15.08.2012 Fachbereich 20 CDC Denise Demirel 1 Helios Introduced 2008 by Ben Adida Web application
Improving Helios with Everlasting Privacy Towards the Public Denise Demirel, Jeroen van de Graaf, Roberto Araúo 15.08.2012 Fachbereich 20 CDC Denise Demirel 1 Helios Introduced 2008 by Ben Adida Web application
Threshold Cryptography
 Threshold Cryptography Cloud Security Mechanisms Björn Groneberg - Summer Term 2013 09.07.2013 Threshold Cryptography 1 ? 09.07.2013 Threshold Cryptography 2 Threshold Cryptography Sharing Secrets Treasure
Threshold Cryptography Cloud Security Mechanisms Björn Groneberg - Summer Term 2013 09.07.2013 Threshold Cryptography 1 ? 09.07.2013 Threshold Cryptography 2 Threshold Cryptography Sharing Secrets Treasure
Structure of a Typical Digital System Data Inputs
 ecture RT Desig Methodology Trasitio from the & Iterface to a Correspodig Block Diagram Structure of a Typical Digital System Data Iputs Datapath (Executio Uit) Data Outputs Cotrol Sigals Status Sigals
ecture RT Desig Methodology Trasitio from the & Iterface to a Correspodig Block Diagram Structure of a Typical Digital System Data Iputs Datapath (Executio Uit) Data Outputs Cotrol Sigals Status Sigals
International Journal of Advanced Research in Computer Science and Software Engineering
 Volume 2, Issue 11, November 2012 ISSN: 2277 128X Iteratioal Joural of Advaced Research i Computer Sciece ad Software Egieerig Research Paper Available olie at: www.ijarcsse.com A Digital Sigature Algorim
Volume 2, Issue 11, November 2012 ISSN: 2277 128X Iteratioal Joural of Advaced Research i Computer Sciece ad Software Egieerig Research Paper Available olie at: www.ijarcsse.com A Digital Sigature Algorim
Identity-Based Cryptography on Hidden-Order Groups
 vailable olie at www.sciecedirect.com Procedia Egieerig 9 (0) 067 07 0 Iteratioal Worshop o Iformatio ad Electroics Egieerig (IWIEE) Idetity-Based Cryptography o Hidde-Order Groups Chalgu Li a a Key Laboratory
vailable olie at www.sciecedirect.com Procedia Egieerig 9 (0) 067 07 0 Iteratioal Worshop o Iformatio ad Electroics Egieerig (IWIEE) Idetity-Based Cryptography o Hidde-Order Groups Chalgu Li a a Key Laboratory
Advanced Cryptography 03/06/2007. Lecture 8
 Advanced Cryptography 03/06/007 Lecture 8 Lecturer: Victor Shoup Scribe: Prashant Puniya Overview In this lecture, we will introduce the notion of Public-Key Encryption. We will define the basic notion
Advanced Cryptography 03/06/007 Lecture 8 Lecturer: Victor Shoup Scribe: Prashant Puniya Overview In this lecture, we will introduce the notion of Public-Key Encryption. We will define the basic notion
A Block Cipher Using Linear Congruences
 Joural of Computer Sciece 3 (7): 556-560, 2007 ISSN 1549-3636 2007 Sciece Publicatios A Block Cipher Usig Liear Cogrueces 1 V.U.K. Sastry ad 2 V. Jaaki 1 Academic Affairs, Sreeidhi Istitute of Sciece &
Joural of Computer Sciece 3 (7): 556-560, 2007 ISSN 1549-3636 2007 Sciece Publicatios A Block Cipher Usig Liear Cogrueces 1 V.U.K. Sastry ad 2 V. Jaaki 1 Academic Affairs, Sreeidhi Istitute of Sciece &
Notations. Primary definition. Specific values. Traditional name. Traditional notation. Mathematica StandardForm notation. Specialized values
 EulerPhi Notatios Traditioal ame Euler totiet fuctio Traditioal otatio Φ Mathematica StadardForm otatio EulerPhi Primary defiitio 3.06.02.000.0 Φ gcd,k, ; For oegative iteger, the Euler totiet fuctio Φ
EulerPhi Notatios Traditioal ame Euler totiet fuctio Traditioal otatio Φ Mathematica StadardForm otatio EulerPhi Primary defiitio 3.06.02.000.0 Φ gcd,k, ; For oegative iteger, the Euler totiet fuctio Φ
Cryptographic Voting Systems (Ben Adida)
 Cryptographic Voting Systems (Ben Adida) Click to edit Master subtitle style Jimin Park Carleton University COMP 4109 Seminar 15 February 2011 If you think cryptography is the solution to your problem.
Cryptographic Voting Systems (Ben Adida) Click to edit Master subtitle style Jimin Park Carleton University COMP 4109 Seminar 15 February 2011 If you think cryptography is the solution to your problem.
Primality Test. Rong-Jaye Chen
 Primality Test Rog-Jaye Che OUTLINE [1] Modular Arithmetic Algorithms [2] Quadratic Residues [3] Primality Testig p2. [1] Modular Arithmetic Algorithms 1. The itegers a divides b a b a{ 1, b} If b has
Primality Test Rog-Jaye Che OUTLINE [1] Modular Arithmetic Algorithms [2] Quadratic Residues [3] Primality Testig p2. [1] Modular Arithmetic Algorithms 1. The itegers a divides b a b a{ 1, b} If b has
Wrap of Number Theory & Midterm Review. Recall: Fundamental Theorem of Arithmetic
 Wrap of Number Theory & Midterm Review F Primes, GCD, ad LCM (Sectio 3.5 i text) F Midterm Review Sectios.-.7 Propositioal logic Predicate logic Rules of iferece ad proofs Sectios.-.3 Sets ad Set operatios
Wrap of Number Theory & Midterm Review F Primes, GCD, ad LCM (Sectio 3.5 i text) F Midterm Review Sectios.-.7 Propositioal logic Predicate logic Rules of iferece ad proofs Sectios.-.3 Sets ad Set operatios
BRICS. A Generalisation, a Simplification and some Applications of Paillier s Probabilistic Public-Key System
 BRICS Basic Research in Computer Science BRICS RS-00-45 Damgård & Jurik: Generalisation and Applications of Paillier s Probabilistic Public-Key System A Generalisation, a Simplification and some Applications
BRICS Basic Research in Computer Science BRICS RS-00-45 Damgård & Jurik: Generalisation and Applications of Paillier s Probabilistic Public-Key System A Generalisation, a Simplification and some Applications
during transmission safeguard information Cryptography: used to CRYPTOGRAPHY BACKGROUND OF THE MATHEMATICAL
 THE MATHEMATICAL BACKGROUND OF CRYPTOGRAPHY Cryptography: used to safeguard information during transmission (e.g., credit card number for internet shopping) as opposed to Coding Theory: used to transmit
THE MATHEMATICAL BACKGROUND OF CRYPTOGRAPHY Cryptography: used to safeguard information during transmission (e.g., credit card number for internet shopping) as opposed to Coding Theory: used to transmit
 1 of 7 7/16/2009 6:06 AM Virtual Laboratories > 6. Radom Samples > 1 2 3 4 5 6 7 6. Order Statistics Defiitios Suppose agai that we have a basic radom experimet, ad that X is a real-valued radom variable
1 of 7 7/16/2009 6:06 AM Virtual Laboratories > 6. Radom Samples > 1 2 3 4 5 6 7 6. Order Statistics Defiitios Suppose agai that we have a basic radom experimet, ad that X is a real-valued radom variable
Some ZK security proofs for Belenios
 Some ZK security proofs for Belenios Pierrick Gaudry CNRS, INRIA, Université de Lorraine January 30, 2017 The purpose of this document is to justify the use of ZK proofs in Belenios. Most of them are exactly
Some ZK security proofs for Belenios Pierrick Gaudry CNRS, INRIA, Université de Lorraine January 30, 2017 The purpose of this document is to justify the use of ZK proofs in Belenios. Most of them are exactly
Practical Verifiable Encryption and Decryption of Discrete Logarithms
 Practical Verifiable Encryption and Decryption of Discrete Logarithms Jan Camenisch IBM Zurich Research Lab Victor Shoup New York University p.1/27 Verifiable encryption of discrete logs Three players:
Practical Verifiable Encryption and Decryption of Discrete Logarithms Jan Camenisch IBM Zurich Research Lab Victor Shoup New York University p.1/27 Verifiable encryption of discrete logs Three players:
Further More on Key Wrapping. 2011/2/17 SKEW2011 Lyngby Nagoya University Yasushi Osaki, Tetsu Iwata
 Further More o Key Wrappig 011//17 SKEW011 Lygby Nagoya Uiversity Yasushi Osaki, Tetsu Iwata 1 What is key wrappig? Used to ecrypt specialized data, such as cryptographic keys A key wrappig that also esures
Further More o Key Wrappig 011//17 SKEW011 Lygby Nagoya Uiversity Yasushi Osaki, Tetsu Iwata 1 What is key wrappig? Used to ecrypt specialized data, such as cryptographic keys A key wrappig that also esures
Question: Total Points: Score:
 University of California, Irvine COMPSCI 134: Elements of Cryptography and Computer and Network Security Midterm Exam (Fall 2016) Duration: 90 minutes November 2, 2016, 7pm-8:30pm Name (First, Last): Please
University of California, Irvine COMPSCI 134: Elements of Cryptography and Computer and Network Security Midterm Exam (Fall 2016) Duration: 90 minutes November 2, 2016, 7pm-8:30pm Name (First, Last): Please
Dr George Danezis University College London, UK
 Dr George Danezis University College London, UK Identity as a proxy to check credentials Username decides access in Access Control Matrix Sometime it leaks too much information Real world examples Tickets
Dr George Danezis University College London, UK Identity as a proxy to check credentials Username decides access in Access Control Matrix Sometime it leaks too much information Real world examples Tickets
Chapter 8 Public-key Cryptography and Digital Signatures
 Chapter 8 Public-key Cryptography and Digital Signatures v 1. Introduction to Public-key Cryptography 2. Example of Public-key Algorithm: Diffie- Hellman Key Exchange Scheme 3. RSA Encryption and Digital
Chapter 8 Public-key Cryptography and Digital Signatures v 1. Introduction to Public-key Cryptography 2. Example of Public-key Algorithm: Diffie- Hellman Key Exchange Scheme 3. RSA Encryption and Digital
The multiplicative structure of finite field and a construction of LRC
 IERG6120 Codig for Distributed Storage Systems Lecture 8-06/10/2016 The multiplicative structure of fiite field ad a costructio of LRC Lecturer: Keeth Shum Scribe: Zhouyi Hu Notatios: We use the otatio
IERG6120 Codig for Distributed Storage Systems Lecture 8-06/10/2016 The multiplicative structure of fiite field ad a costructio of LRC Lecturer: Keeth Shum Scribe: Zhouyi Hu Notatios: We use the otatio
3.2.4 Integer and Number Theoretical Functions
 418 3. Advaced Mathematics i Mathematica 3.2.4 Iteger ad Number Theoretical Fuctios Mod[k, ] k modulo (positive remaider from dividig k by ) Quotiet[m, ] the quotiet of m ad (iteger part of m/) GCD[ 1,
418 3. Advaced Mathematics i Mathematica 3.2.4 Iteger ad Number Theoretical Fuctios Mod[k, ] k modulo (positive remaider from dividig k by ) Quotiet[m, ] the quotiet of m ad (iteger part of m/) GCD[ 1,
Homework 3 Solutions
 5233/IOC5063 Theory of Cryptology, Fall 205 Instructor Prof. Wen-Guey Tzeng Homework 3 Solutions 7-Dec-205 Scribe Amir Rezapour. Consider an unfair coin with head probability 0.5. Assume that the coin
5233/IOC5063 Theory of Cryptology, Fall 205 Instructor Prof. Wen-Guey Tzeng Homework 3 Solutions 7-Dec-205 Scribe Amir Rezapour. Consider an unfair coin with head probability 0.5. Assume that the coin
Identity-based Encryption from Codes with Rank Metric
 Idetity-based Ecryptio from Codes with Rak Metric Philippe Gaborit 1, Adrie Hauteville 1,2, Duog Hieu Pha 1, ad Jea-Pierre Tillich 2 1 Uiversité de Limoges, XLIM-DMI, 123, Av. Albert Thomas, 87060 Limoges
Idetity-based Ecryptio from Codes with Rak Metric Philippe Gaborit 1, Adrie Hauteville 1,2, Duog Hieu Pha 1, ad Jea-Pierre Tillich 2 1 Uiversité de Limoges, XLIM-DMI, 123, Av. Albert Thomas, 87060 Limoges
Elliptic Curve Cryptography
 Elliptic Curve Cryptography Elliptic Curves An elliptic curve is a cubic equation of the form: y + axy + by = x 3 + cx + dx + e where a, b, c, d and e are real numbers. A special addition operation is
Elliptic Curve Cryptography Elliptic Curves An elliptic curve is a cubic equation of the form: y + axy + by = x 3 + cx + dx + e where a, b, c, d and e are real numbers. A special addition operation is
Number Theory & Modern Cryptography
 Number Theory & Modern Cryptography Week 12 Stallings: Ch 4, 8, 9, 10 CNT-4403: 2.April.2015 1 Introduction Increasing importance in cryptography Public Key Crypto and Signatures Concern operations on
Number Theory & Modern Cryptography Week 12 Stallings: Ch 4, 8, 9, 10 CNT-4403: 2.April.2015 1 Introduction Increasing importance in cryptography Public Key Crypto and Signatures Concern operations on
Cryptographic Protocols. Steve Lai
 Cryptographic Protocols Steve Lai This course: APPLICATIONS (security) Encryption Schemes Crypto Protocols Sign/MAC Schemes Pseudorandom Generators And Functions Zero-Knowledge Proof Systems Computational
Cryptographic Protocols Steve Lai This course: APPLICATIONS (security) Encryption Schemes Crypto Protocols Sign/MAC Schemes Pseudorandom Generators And Functions Zero-Knowledge Proof Systems Computational
Efficient RSA Key Generation and Threshold Paillier in the Two-Party Setting
 An extended abstract of this paper was published in the proceedings of CT-RSA 2012. Efficient RSA Key Generation and Threshold Paillier in the Two-Party Setting Carmit Hazay Gert Læssøe Mikkelsen Tal Rabin
An extended abstract of this paper was published in the proceedings of CT-RSA 2012. Efficient RSA Key Generation and Threshold Paillier in the Two-Party Setting Carmit Hazay Gert Læssøe Mikkelsen Tal Rabin
( ) = p and P( i = b) = q.
 MATH 540 Radom Walks Part 1 A radom walk X is special stochastic process that measures the height (or value) of a particle that radomly moves upward or dowward certai fixed amouts o each uit icremet of
MATH 540 Radom Walks Part 1 A radom walk X is special stochastic process that measures the height (or value) of a particle that radomly moves upward or dowward certai fixed amouts o each uit icremet of
Computational Intelligence Winter Term 2018/19
 Computatioal Itelligece Witer Term 28/9 Prof. Dr. Güter Rudolph Lehrstuhl für Algorithm Egieerig (LS ) Fakultät für Iformatik TU Dortmud Pla for Today Lecture Evolutioary Algorithms (EA) Optimizatio Basics
Computatioal Itelligece Witer Term 28/9 Prof. Dr. Güter Rudolph Lehrstuhl für Algorithm Egieerig (LS ) Fakultät für Iformatik TU Dortmud Pla for Today Lecture Evolutioary Algorithms (EA) Optimizatio Basics
Design and Analysis of ALGORITHM (Topic 2)
 DR. Gatot F. Hertoo, MSc. Desig ad Aalysis of ALGORITHM (Topic 2) Algorithms + Data Structures = Programs Lessos Leared 1 Our Machie Model: Assumptios Geeric Radom Access Machie (RAM) Executes operatios
DR. Gatot F. Hertoo, MSc. Desig ad Aalysis of ALGORITHM (Topic 2) Algorithms + Data Structures = Programs Lessos Leared 1 Our Machie Model: Assumptios Geeric Radom Access Machie (RAM) Executes operatios
Introduction to Cybersecurity Cryptography (Part 4)
 Introduction to Cybersecurity Cryptography (Part 4) Review of Last Lecture Blockciphers Review of DES Attacks on Blockciphers Advanced Encryption Standard (AES) Modes of Operation MACs and Hashes Message
Introduction to Cybersecurity Cryptography (Part 4) Review of Last Lecture Blockciphers Review of DES Attacks on Blockciphers Advanced Encryption Standard (AES) Modes of Operation MACs and Hashes Message
Econ 325 Notes on Point Estimator and Confidence Interval 1 By Hiro Kasahara
 Poit Estimator Eco 325 Notes o Poit Estimator ad Cofidece Iterval 1 By Hiro Kasahara Parameter, Estimator, ad Estimate The ormal probability desity fuctio is fully characterized by two costats: populatio
Poit Estimator Eco 325 Notes o Poit Estimator ad Cofidece Iterval 1 By Hiro Kasahara Parameter, Estimator, ad Estimate The ormal probability desity fuctio is fully characterized by two costats: populatio
How to Shuffle in Public
 How to Shuffle in Public Ben Adida Harvard (work done at MIT) Douglas Wikström ETH Zürich TCC 27 February 24th, 27 How to Shuffle in Public Ben Adida Harvard (work done at MIT) Douglas Wikström ETH Zürich
How to Shuffle in Public Ben Adida Harvard (work done at MIT) Douglas Wikström ETH Zürich TCC 27 February 24th, 27 How to Shuffle in Public Ben Adida Harvard (work done at MIT) Douglas Wikström ETH Zürich
Independence of the Miller-Rabin and Lucas Probable Prime Tests
 Idepedece of the Miller-Rabi ad Lucas Probable Prime Tests Alec Leg Metor: avid Corwi March 30, 017 1 Abstract I the moder age, public-key cryptography has become a vital compoet for secure olie commuicatio.
Idepedece of the Miller-Rabi ad Lucas Probable Prime Tests Alec Leg Metor: avid Corwi March 30, 017 1 Abstract I the moder age, public-key cryptography has become a vital compoet for secure olie commuicatio.
Introduction to Cybersecurity Cryptography (Part 4)
 Introduction to Cybersecurity Cryptography (Part 4) Review of Last Lecture Blockciphers Review of DES Attacks on Blockciphers Advanced Encryption Standard (AES) Modes of Operation MACs and Hashes Message
Introduction to Cybersecurity Cryptography (Part 4) Review of Last Lecture Blockciphers Review of DES Attacks on Blockciphers Advanced Encryption Standard (AES) Modes of Operation MACs and Hashes Message
Estimation of a population proportion March 23,
 1 Social Studies 201 Notes for March 23, 2005 Estimatio of a populatio proportio Sectio 8.5, p. 521. For the most part, we have dealt with meas ad stadard deviatios this semester. This sectio of the otes
1 Social Studies 201 Notes for March 23, 2005 Estimatio of a populatio proportio Sectio 8.5, p. 521. For the most part, we have dealt with meas ad stadard deviatios this semester. This sectio of the otes
Math778P Homework 2 Solution
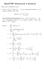 Math778P Homework Solutio Choose ay 5 problems to solve. 1. Let S = X i where X 1,..., X are idepedet uiform { 1, 1} radom variables. Prove that E( S = 1 ( 1 1 Proof by Day Rorabaugh: Let S = X i where
Math778P Homework Solutio Choose ay 5 problems to solve. 1. Let S = X i where X 1,..., X are idepedet uiform { 1, 1} radom variables. Prove that E( S = 1 ( 1 1 Proof by Day Rorabaugh: Let S = X i where
Network Security Technology Spring, 2018 Tutorial 3, Week 4 (March 23) Due Date: March 30
 Network Security Technology Spring, 2018 Tutorial 3, Week 4 (March 23) LIU Zhen Due Date: March 30 Questions: 1. RSA (20 Points) Assume that we use RSA with the prime numbers p = 17 and q = 23. (a) Calculate
Network Security Technology Spring, 2018 Tutorial 3, Week 4 (March 23) LIU Zhen Due Date: March 30 Questions: 1. RSA (20 Points) Assume that we use RSA with the prime numbers p = 17 and q = 23. (a) Calculate
Basic Sets. Functions. MTH299 - Examples. Example 1. Let S = {1, {2, 3}, 4}. Indicate whether each statement is true or false. (a) S = 4. (e) 2 S.
 Basic Sets Example 1. Let S = {1, {2, 3}, 4}. Idicate whether each statemet is true or false. (a) S = 4 (b) {1} S (c) {2, 3} S (d) {1, 4} S (e) 2 S. (f) S = {1, 4, {2, 3}} (g) S Example 2. Compute the
Basic Sets Example 1. Let S = {1, {2, 3}, 4}. Idicate whether each statemet is true or false. (a) S = 4 (b) {1} S (c) {2, 3} S (d) {1, 4} S (e) 2 S. (f) S = {1, 4, {2, 3}} (g) S Example 2. Compute the
Public-Key Cryptosystems CHAPTER 4
 Public-Key Cryptosystems CHAPTER 4 Introduction How to distribute the cryptographic keys? Naïve Solution Naïve Solution Give every user P i a separate random key K ij to communicate with every P j. Disadvantage:
Public-Key Cryptosystems CHAPTER 4 Introduction How to distribute the cryptographic keys? Naïve Solution Naïve Solution Give every user P i a separate random key K ij to communicate with every P j. Disadvantage:
Introduction to Cryptography. Lecture 8
 Introduction to Cryptography Lecture 8 Benny Pinkas page 1 1 Groups we will use Multiplication modulo a prime number p (G, ) = ({1,2,,p-1}, ) E.g., Z 7* = ( {1,2,3,4,5,6}, ) Z p * Z N * Multiplication
Introduction to Cryptography Lecture 8 Benny Pinkas page 1 1 Groups we will use Multiplication modulo a prime number p (G, ) = ({1,2,,p-1}, ) E.g., Z 7* = ( {1,2,3,4,5,6}, ) Z p * Z N * Multiplication
Iterated Encryption and Wiener s attack on RSA
 Iterated Encryption Euler s function Euler s function: φ(n) = {1 x n : gcd(x, n) = 1} Theorem (Euler) If n is a positive integer and m is a positive integer coprime to n then m φ(n) mod n = 1. Iterated
Iterated Encryption Euler s function Euler s function: φ(n) = {1 x n : gcd(x, n) = 1} Theorem (Euler) If n is a positive integer and m is a positive integer coprime to n then m φ(n) mod n = 1. Iterated
Dirichlet s Theorem on Arithmetic Progressions
 Dirichlet s Theorem o Arithmetic Progressios Athoy Várilly Harvard Uiversity, Cambridge, MA 0238 Itroductio Dirichlet s theorem o arithmetic progressios is a gem of umber theory. A great part of its beauty
Dirichlet s Theorem o Arithmetic Progressios Athoy Várilly Harvard Uiversity, Cambridge, MA 0238 Itroductio Dirichlet s theorem o arithmetic progressios is a gem of umber theory. A great part of its beauty
RSA Algorithm. Factoring, EulerPhi, Breaking RSA. Çetin Kaya Koç Spring / 14
 RSA Algorithm http://koclab.org Çetin Kaya Koç Spring 2018 1 / 14 Well-Known One-Way Functions Discrete Logarithm: Given p, g, and x, computing y in y = g x (mod p) is EASY Given p, g, y, computing x in
RSA Algorithm http://koclab.org Çetin Kaya Koç Spring 2018 1 / 14 Well-Known One-Way Functions Discrete Logarithm: Given p, g, and x, computing y in y = g x (mod p) is EASY Given p, g, y, computing x in
Polynomial reduction. Outline Lecture. Non deterministic polynomial time. Example 1 : discrete log. Lecture: Polynomial reduction.
 Outlie Lecture Part 1 : Asymmetric cryptography, oe way fuctio, complexity Part 2 : arithmetic complexity ad lower bouds : expoetiatio Part 3 : Provable security ad polyomial time reductio : P, NP classes.
Outlie Lecture Part 1 : Asymmetric cryptography, oe way fuctio, complexity Part 2 : arithmetic complexity ad lower bouds : expoetiatio Part 3 : Provable security ad polyomial time reductio : P, NP classes.
CryptoComputing with rationals
 CryptoComputing with rationals Pierre-Alain Fouque 1,2, Jacques Stern 2, and Geert-Jan Wackers 3 1 D.C.S.S.I. Crypto Lab 51, bd Latour-Maubourg, F-75007 Paris, France 2 École Normale Supérieure, Département
CryptoComputing with rationals Pierre-Alain Fouque 1,2, Jacques Stern 2, and Geert-Jan Wackers 3 1 D.C.S.S.I. Crypto Lab 51, bd Latour-Maubourg, F-75007 Paris, France 2 École Normale Supérieure, Département
University of Tokyo: Advanced Algorithms Summer Lecture 6 27 May. Let s keep in mind definitions from the previous lecture:
 University of Tokyo: Advanced Algorithms Summer 2010 Lecture 6 27 May Lecturer: François Le Gall Scribe: Baljak Valentina As opposed to prime factorization, primality testing is determining whether a given
University of Tokyo: Advanced Algorithms Summer 2010 Lecture 6 27 May Lecturer: François Le Gall Scribe: Baljak Valentina As opposed to prime factorization, primality testing is determining whether a given
Basics of Probability Theory (for Theory of Computation courses)
 Basics of Probability Theory (for Theory of Computatio courses) Oded Goldreich Departmet of Computer Sciece Weizma Istitute of Sciece Rehovot, Israel. oded.goldreich@weizma.ac.il November 24, 2008 Preface.
Basics of Probability Theory (for Theory of Computatio courses) Oded Goldreich Departmet of Computer Sciece Weizma Istitute of Sciece Rehovot, Israel. oded.goldreich@weizma.ac.il November 24, 2008 Preface.
A brief introduction to linear algebra
 CHAPTER 6 A brief itroductio to liear algebra 1. Vector spaces ad liear maps I what follows, fix K 2{Q, R, C}. More geerally, K ca be ay field. 1.1. Vector spaces. Motivated by our ituitio of addig ad
CHAPTER 6 A brief itroductio to liear algebra 1. Vector spaces ad liear maps I what follows, fix K 2{Q, R, C}. More geerally, K ca be ay field. 1.1. Vector spaces. Motivated by our ituitio of addig ad
NBHM QUESTION 2007 Section 1 : Algebra Q1. Let G be a group of order n. Which of the following conditions imply that G is abelian?
 NBHM QUESTION 7 NBHM QUESTION 7 NBHM QUESTION 7 Sectio : Algebra Q Let G be a group of order Which of the followig coditios imply that G is abelia? 5 36 Q Which of the followig subgroups are ecesarily
NBHM QUESTION 7 NBHM QUESTION 7 NBHM QUESTION 7 Sectio : Algebra Q Let G be a group of order Which of the followig coditios imply that G is abelia? 5 36 Q Which of the followig subgroups are ecesarily
DIFFERENTIAL CRYPTANALYSIS FOR A 3-ROUND SPN
 IRNTIL RYPTNLYSIS OR -ROUN SPN M. Tolga Sakallı rca uluş daç Şahi atma üyüksaraçoğlu e-mail: tolga@trakya.edu.tr. e-mail: ercab@trakya.edu.tr e-mail: adacs@trakya.edu.tr e-mail: fbuyuksaracoglu@trakya.edu.tr
IRNTIL RYPTNLYSIS OR -ROUN SPN M. Tolga Sakallı rca uluş daç Şahi atma üyüksaraçoğlu e-mail: tolga@trakya.edu.tr. e-mail: ercab@trakya.edu.tr e-mail: adacs@trakya.edu.tr e-mail: fbuyuksaracoglu@trakya.edu.tr
CIS 551 / TCOM 401 Computer and Network Security
 CIS 551 / TCOM 401 Computer and Network Security Spring 2008 Lecture 15 3/20/08 CIS/TCOM 551 1 Announcements Project 3 available on the web. Get the handout in class today. Project 3 is due April 4th It
CIS 551 / TCOM 401 Computer and Network Security Spring 2008 Lecture 15 3/20/08 CIS/TCOM 551 1 Announcements Project 3 available on the web. Get the handout in class today. Project 3 is due April 4th It
CPSC 467b: Cryptography and Computer Security
 CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 11 February 21, 2013 CPSC 467b, Lecture 11 1/27 Discrete Logarithm Diffie-Hellman Key Exchange ElGamal Key Agreement Primitive Roots
CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 11 February 21, 2013 CPSC 467b, Lecture 11 1/27 Discrete Logarithm Diffie-Hellman Key Exchange ElGamal Key Agreement Primitive Roots
ECEN 655: Advanced Channel Coding Spring Lecture 7 02/04/14. Belief propagation is exact on tree-structured factor graphs.
 ECEN 655: Advaced Chael Codig Sprig 014 Prof. Hery Pfister Lecture 7 0/04/14 Scribe: Megke Lia 1 4-Cycles i Gallager s Esemble What we already kow: Belief propagatio is exact o tree-structured factor graphs.
ECEN 655: Advaced Chael Codig Sprig 014 Prof. Hery Pfister Lecture 7 0/04/14 Scribe: Megke Lia 1 4-Cycles i Gallager s Esemble What we already kow: Belief propagatio is exact o tree-structured factor graphs.
Optimal Design of Accelerated Life Tests with Multiple Stresses
 Optimal Desig of Accelerated Life Tests with Multiple Stresses Y. Zhu ad E. A. Elsayed Departmet of Idustrial ad Systems Egieerig Rutgers Uiversity 2009 Quality & Productivity Research Coferece IBM T.
Optimal Desig of Accelerated Life Tests with Multiple Stresses Y. Zhu ad E. A. Elsayed Departmet of Idustrial ad Systems Egieerig Rutgers Uiversity 2009 Quality & Productivity Research Coferece IBM T.
Efficient RSA Key Generation and Threshold Paillier in the Two-Party Setting
 Efficient RSA Key Generation and Threshold Paillier in the Two-Party Setting Carmit Hazay Gert Læssøe Mikkelsen Tal Rabin Tomas Toft Abstract The problem of generating an RSA composite in a distributed
Efficient RSA Key Generation and Threshold Paillier in the Two-Party Setting Carmit Hazay Gert Læssøe Mikkelsen Tal Rabin Tomas Toft Abstract The problem of generating an RSA composite in a distributed
End-of-Year Contest. ERHS Math Club. May 5, 2009
 Ed-of-Year Cotest ERHS Math Club May 5, 009 Problem 1: There are 9 cois. Oe is fake ad weighs a little less tha the others. Fid the fake coi by weighigs. Solutio: Separate the 9 cois ito 3 groups (A, B,
Ed-of-Year Cotest ERHS Math Club May 5, 009 Problem 1: There are 9 cois. Oe is fake ad weighs a little less tha the others. Fid the fake coi by weighigs. Solutio: Separate the 9 cois ito 3 groups (A, B,
Information Theory and Coding
 Sol. Iformatio Theory ad Codig. The capacity of a bad-limited additive white Gaussia (AWGN) chael is give by C = Wlog 2 ( + σ 2 W ) bits per secod(bps), where W is the chael badwidth, is the average power
Sol. Iformatio Theory ad Codig. The capacity of a bad-limited additive white Gaussia (AWGN) chael is give by C = Wlog 2 ( + σ 2 W ) bits per secod(bps), where W is the chael badwidth, is the average power
Merkle-Hellman Knapsack Cryptosystem in Undergraduate Computer Science Curriculum
 Merkle-Hellma Kapsack Cryptosystem i Udergraduate Computer Sciece Curriculum Y. Kortsarts, Y. Kemper 2 Computer Sciece Departmet, Wideer Uiversity, Chester, PA, USA 2 Computer Sciece Departmet, Holo Istitute
Merkle-Hellma Kapsack Cryptosystem i Udergraduate Computer Sciece Curriculum Y. Kortsarts, Y. Kemper 2 Computer Sciece Departmet, Wideer Uiversity, Chester, PA, USA 2 Computer Sciece Departmet, Holo Istitute
Randomized Algorithms I, Spring 2018, Department of Computer Science, University of Helsinki Homework 1: Solutions (Discussed January 25, 2018)
 Radomized Algorithms I, Sprig 08, Departmet of Computer Sciece, Uiversity of Helsiki Homework : Solutios Discussed Jauary 5, 08). Exercise.: Cosider the followig balls-ad-bi game. We start with oe black
Radomized Algorithms I, Sprig 08, Departmet of Computer Sciece, Uiversity of Helsiki Homework : Solutios Discussed Jauary 5, 08). Exercise.: Cosider the followig balls-ad-bi game. We start with oe black
1 Hash tables. 1.1 Implementation
 Lecture 8 Hash Tables, Uiversal Hash Fuctios, Balls ad Bis Scribes: Luke Johsto, Moses Charikar, G. Valiat Date: Oct 18, 2017 Adapted From Virgiia Williams lecture otes 1 Hash tables A hash table is a
Lecture 8 Hash Tables, Uiversal Hash Fuctios, Balls ad Bis Scribes: Luke Johsto, Moses Charikar, G. Valiat Date: Oct 18, 2017 Adapted From Virgiia Williams lecture otes 1 Hash tables A hash table is a
Chapter 6: Mining Frequent Patterns, Association and Correlations
 Chapter 6: Miig Frequet Patters, Associatio ad Correlatios Basic cocepts Frequet itemset miig methods Costrait-based frequet patter miig (ch7) Associatio rules 1 What Is Frequet Patter Aalysis? Frequet
Chapter 6: Miig Frequet Patters, Associatio ad Correlatios Basic cocepts Frequet itemset miig methods Costrait-based frequet patter miig (ch7) Associatio rules 1 What Is Frequet Patter Aalysis? Frequet
Report on Private Information Retrieval over Unsynchronized Databases
 Report o Private Iformatio Retrieval over Usychroized Databases Lembit Valgma Supervised by Vitaly Skachek May 25, 217 1 Problem Statemet There are may challeges cocerig olie privacy. Private iformatio
Report o Private Iformatio Retrieval over Usychroized Databases Lembit Valgma Supervised by Vitaly Skachek May 25, 217 1 Problem Statemet There are may challeges cocerig olie privacy. Private iformatio
Resampling Methods. X (1/2), i.e., Pr (X i m) = 1/2. We order the data: X (1) X (2) X (n). Define the sample median: ( n.
 Jauary 1, 2019 Resamplig Methods Motivatio We have so may estimators with the property θ θ d N 0, σ 2 We ca also write θ a N θ, σ 2 /, where a meas approximately distributed as Oce we have a cosistet estimator
Jauary 1, 2019 Resamplig Methods Motivatio We have so may estimators with the property θ θ d N 0, σ 2 We ca also write θ a N θ, σ 2 /, where a meas approximately distributed as Oce we have a cosistet estimator
MTAT Cryptology II. Zero-knowledge Proofs. Sven Laur University of Tartu
 MTAT.07.003 Cryptology II Zero-knowledge Proofs Sven Laur University of Tartu Formal Syntax Zero-knowledge proofs pk (pk, sk) Gen α 1 β 1 β i V pk (α 1,...,α i 1 ) α i P sk (β 1,...,β i 1 ) (pk,sk)? R
MTAT.07.003 Cryptology II Zero-knowledge Proofs Sven Laur University of Tartu Formal Syntax Zero-knowledge proofs pk (pk, sk) Gen α 1 β 1 β i V pk (α 1,...,α i 1 ) α i P sk (β 1,...,β i 1 ) (pk,sk)? R
Algorithm Analysis. Algorithms that are equally correct can vary in their utilization of computational resources
 Algorithm Aalysis Algorithms that are equally correct ca vary i their utilizatio of computatioal resources time ad memory a slow program it is likely ot to be used a program that demads too much memory
Algorithm Aalysis Algorithms that are equally correct ca vary i their utilizatio of computatioal resources time ad memory a slow program it is likely ot to be used a program that demads too much memory
YALE UNIVERSITY DEPARTMENT OF COMPUTER SCIENCE
 YALE UNIVERSITY DEPARTMENT OF COMPUTER SCIENCE CPSC 467a: Crytograhy ad Comuter Security Notes 16 (rev. 1 Professor M. J. Fischer November 3, 2008 68 Legedre Symbol Lecture Notes 16 ( Let be a odd rime,
YALE UNIVERSITY DEPARTMENT OF COMPUTER SCIENCE CPSC 467a: Crytograhy ad Comuter Security Notes 16 (rev. 1 Professor M. J. Fischer November 3, 2008 68 Legedre Symbol Lecture Notes 16 ( Let be a odd rime,
