Pipeline no Prediction. Branch Delay Slots A. From before branch B. From branch target C. From fall through. Branch Prediction
|
|
|
- Patrick McDowell
- 5 years ago
- Views:
Transcription
1 Pipeline no Prediction Branching completes in 2 cycles We know the target address after the second stage? PC fetch Instruction Memory Decode Check the condition Calculate the branch target address PC+4 1 Cycle delay 39 Branch Delay Slots A. From before branch B. From branch target C. From fall through sub $4,$5,$6 if $1=0 then if $2=0 then delay slot if $1=0 then delay slot delay slot sub $4,$5,$6 becomes becomes becomes if $2=0 then if $1=0 then sub $4,$5,$6 if $1=0 then sub $4,$5,$6 40 Branch Prediction Dynamic scheduling deals with data dependence improving, the limiting factor is the control dependence. Branch prediction is important for processors that maintains a CPI of 1, but it is crucial for processors who tries to issue more than one instruction per cycle (CPI < 1). We have already studied some techniques (delayed branch, predict not taken), but these do not depend on the dynamic behavior of the code. 41
2 Very Simple Predictor not practical Assume we have a for loop for(i=0; i<n; i++) in assemlbly loop_start: loop starts here PC1: beq r1, r2, loop_start 42 Branch History Table A small memory indexed by the lower portion of the address of the branch instruction. The memory contains only 1-bit, to predict taken or untaken If the prediction is incorrect, the prediction bit is inverted. In a loop, it mispredicts twice End of loop case, when it exits instead of looping as before First time through loop on next time through code, when it predicts exit instead of looping 43 1-Bit Predictor 1-Bit bimodal predictor Consider the following example for(i=0;i<10;i++) { } 44
3 ? Consider a loop that is taken 9 times in a row then not taken 45 2-Bit Predictor Uses 2 bits to add some hysteresis to the prediction Compare with 1 bit? 2 bits are as good as N bits (approx.) Predict Taken T Predict Not Taken T NT T NT T NT Other variation, use a saturating counter Predict Taken NT Predict Not Taken 46 2-bit Predictor 4096 entries 2-bit predictor miss rate
4 Correlating Branch Predictors B1 B2 B3 if (aa==2) aa=0; if (bb==2) bb=0; if (aa!==bb){ DSUBUI R3, R1, #2 BNEZ R3, L1 ; b1 (aa!=2) DADD R1, R0, R0 ; aa==0 L1: DSUBUI R3, R1, #2 BNEZ R3, L2 ; b2 (bb!=2) DADD R2, R0, R0 ; bb==0 L2: DSUBUI R3, R1, R2 ; R3=aa-bb BEQZ R3, L3 ; b3 (aa==bb) If the condition is true (B1,B2) branch NOT TAKEN If the condition is true B3 NOT taken If B1 and B2 both NOT TAKEN B3 TAKEN There is a correlation between B3 and both B1 and B2 48 Correlating Branch Predictors Correlating predictors (two-level predictors) use the behavior of other branches to make prediction. Simplest (1-bit) has 2 predictions, one if the last branch is take, the second is when the last branch is not taken The prediction is on the form NT/T 49 Example B1 B2 if (d==0) d=1; if (d==1) { BNEZ R1, L1 ; d == 0? DADD R1, R0, #1 ; YES d==1 L1: DADD R3, R1, #-1 BNEZ R3, L2 ; b2 (bb!=2) L2: If b1 not taken, b2 is taken for sure Initial d d==0? B1 d befoe b2 d==1 b2 0 Y NO 1 Y NO 1 N Taken 1 Y NO 2 N Taken 2 N Taken 50
5 Example Initial d d==0? B1 d befoe b2 d==1 B2 0 Y NO 1 Y NO 1 N Taken 1 Y NO 2 N Taken 2 N Taken d B1 B1 newb1 B2 B2 new B2 Pred action pred pred action pred 2 NT T T NT T T 0 T NT NT T NT NT 2 NT T T NT T T 0 T NT NT T NT NT Miss on every prediction 51 Example Initial d d==0? B1 d befoe b2 d==1 b2 0 Y NO 1 Y NO 1 N Taken 1 Y NO 2 N Taken 2 N Taken d b1 b1 newb1 b2 b2 new b2 Pred action pred pred action pred 2 NT/NT X T T/NT NT/NT X T NT/T 0 T/NT NT T/NT NT/T NT NT/T 2 T/NT T T/NT NT/T T NT/T 0 T /NT NT T/NT NT/T NT NT/T Misprediction on first try only 52 Global Predictor Take for example 10 bits of the branch PC Take 4 bits of global branch history Access 2 14 entry table Or, you could take the 14 bits of PC XORED with 14 bits of branch history (hashing) to access the same table Or any combination 53
6 Local Predictor The recent history of the branch predicts the next one Branch PC 16 K entries each is a 2- bit predictor ?? bits 54 Correlating Predictors The 1-bit predictor is called (1,1) predictor. It uses one bit for history (last branch), to choose among two (2 1 ) 1-bit branch predictors. In general a predictor could me (m,n) predictor. It uses the last m branch to choose among 2 m branch predictors each is n-bit predictor. 55 (2,2) Correlating Predictors (2,2) predictor Behavior of recent branches selects between four predictions of next branch, updating just that prediction Branch address 2-bits per branch predictor 4 Prediction bit global branch history 56
7 Comparison entrirs (2,2) unlimited entries 2 bit 4096 entries 2 bit li eqntott espresso gcc fppp spice doduc tomcatv matrix300 nasa7 57 Branch Prediction Basic 2-bit predictor: For each branch: Predict taken or not taken If the prediction is wrong two consecutive times, change prediction Correlating predictor: Multiple 2-bit predictors for each branch One for each possible combination of outcomes of preceding n branches Local predictor: Multiple 2-bit predictors for each branch One for each possible combination of outcomes for the last n occurrences of this branch Branch Prediction 58 Tournament Predictor Tournament predictor: Combine correlating predictor with local predictor A selector is sued to decide which one of these to use The selector could be similar to a 2-bit predictor A saturating 2-bit binary counter with 2 outcomes P1/P2 Use P1 Use P2 Use P1 Use P2 59
8 Branch Prediction Performance Branch Prediction Branch predictor performance 60 Alpha Branch Predictor Tournament predictor using, 4K 2-bit counters indexed by local branch address. Global predictor 4K entries index by history of last 12 branches (2 12 = 4K) Each entry is a standard 2-bit predictor Local predictor Local history table: bit entries recording last 10 branches, index by branch address The pattern of the last 10 occurrences of that particular branch used to index table of 1K entries with 3-bit saturating counters 61 Branch Target Buffer Prediction tells us if the branch is taken or not. If taken, to where? Target address Branch target buffer tells us where (based on the PC, or parts of the PC). 62
Portland State University ECE 587/687. Branch Prediction
 Portland State University ECE 587/687 Branch Prediction Copyright by Alaa Alameldeen and Haitham Akkary 2015 Branch Penalty Example: Comparing perfect branch prediction to 90%, 95%, 99% prediction accuracy,
Portland State University ECE 587/687 Branch Prediction Copyright by Alaa Alameldeen and Haitham Akkary 2015 Branch Penalty Example: Comparing perfect branch prediction to 90%, 95%, 99% prediction accuracy,
Unit 6: Branch Prediction
 CIS 501: Computer Architecture Unit 6: Branch Prediction Slides developed by Joe Devie/, Milo Mar4n & Amir Roth at Upenn with sources that included University of Wisconsin slides by Mark Hill, Guri Sohi,
CIS 501: Computer Architecture Unit 6: Branch Prediction Slides developed by Joe Devie/, Milo Mar4n & Amir Roth at Upenn with sources that included University of Wisconsin slides by Mark Hill, Guri Sohi,
CSE. 1. In following code. addi. r1, skip1 xor in r2. r3, skip2. counter r4, top. taken): PC1: PC2: PC3: TTTTTT TTTTTT
 CSE 560 Practice Problem Set 4 Solution 1. In this question, you will examine several different schemes for branch prediction, using the following code sequence for a simple load store ISA with no branch
CSE 560 Practice Problem Set 4 Solution 1. In this question, you will examine several different schemes for branch prediction, using the following code sequence for a simple load store ISA with no branch
/ : Computer Architecture and Design
 16.482 / 16.561: Computer Architecture and Design Summer 2015 Homework #5 Solution 1. Dynamic scheduling (30 points) Given the loop below: DADDI R3, R0, #4 outer: DADDI R2, R1, #32 inner: L.D F0, 0(R1)
16.482 / 16.561: Computer Architecture and Design Summer 2015 Homework #5 Solution 1. Dynamic scheduling (30 points) Given the loop below: DADDI R3, R0, #4 outer: DADDI R2, R1, #32 inner: L.D F0, 0(R1)
Fall 2011 Prof. Hyesoon Kim
 Fall 2011 Prof. Hyesoon Kim Add: 2 cycles FE_stage add r1, r2, r3 FE L ID L EX L MEM L WB L add add sub r4, r1, r3 sub sub add add mul r5, r2, r3 mul sub sub add add mul sub sub add add mul sub sub add
Fall 2011 Prof. Hyesoon Kim Add: 2 cycles FE_stage add r1, r2, r3 FE L ID L EX L MEM L WB L add add sub r4, r1, r3 sub sub add add mul r5, r2, r3 mul sub sub add add mul sub sub add add mul sub sub add
ICS 233 Computer Architecture & Assembly Language
 ICS 233 Computer Architecture & Assembly Language Assignment 6 Solution 1. Identify all of the RAW data dependencies in the following code. Which dependencies are data hazards that will be resolved by
ICS 233 Computer Architecture & Assembly Language Assignment 6 Solution 1. Identify all of the RAW data dependencies in the following code. Which dependencies are data hazards that will be resolved by
CSCI-564 Advanced Computer Architecture
 CSCI-564 Advanced Computer Architecture Lecture 8: Handling Exceptions and Interrupts / Superscalar Bo Wu Colorado School of Mines Branch Delay Slots (expose control hazard to software) Change the ISA
CSCI-564 Advanced Computer Architecture Lecture 8: Handling Exceptions and Interrupts / Superscalar Bo Wu Colorado School of Mines Branch Delay Slots (expose control hazard to software) Change the ISA
Pattern History Table. Global History Register. Pattern History Table. Branch History Pattern Pattern History Bits
 An Enhanced Two-Level Adaptive Multiple Branch Prediction for Superscalar Processors Jong-bok Lee, Soo-Mook Moon and Wonyong Sung fjblee@mpeg,smoon@altair,wysung@dspg.snu.ac.kr School of Electrical Engineering,
An Enhanced Two-Level Adaptive Multiple Branch Prediction for Superscalar Processors Jong-bok Lee, Soo-Mook Moon and Wonyong Sung fjblee@mpeg,smoon@altair,wysung@dspg.snu.ac.kr School of Electrical Engineering,
ENEE350 Lecture Notes-Weeks 14 and 15
 Pipelining & Amdahl s Law ENEE350 Lecture Notes-Weeks 14 and 15 Pipelining is a method of processing in which a problem is divided into a number of sub problems and solved and the solu8ons of the sub problems
Pipelining & Amdahl s Law ENEE350 Lecture Notes-Weeks 14 and 15 Pipelining is a method of processing in which a problem is divided into a number of sub problems and solved and the solu8ons of the sub problems
Department of Electrical and Computer Engineering University of Wisconsin - Madison. ECE/CS 752 Advanced Computer Architecture I.
 Last (family) name: Solution First (given) name: Student I.D. #: Department of Electrical and Computer Engineering University of Wisconsin - Madison ECE/CS 752 Advanced Computer Architecture I Midterm
Last (family) name: Solution First (given) name: Student I.D. #: Department of Electrical and Computer Engineering University of Wisconsin - Madison ECE/CS 752 Advanced Computer Architecture I Midterm
EXAMPLES 4/12/2018. The MIPS Pipeline. Hazard Summary. Show the pipeline diagram. Show the pipeline diagram. Pipeline Datapath and Control
 The MIPS Pipeline CSCI206 - Computer Organization & Programming Pipeline Datapath and Control zybook: 11.6 Developed and maintained by the Bucknell University Computer Science Department - 2017 Hazard
The MIPS Pipeline CSCI206 - Computer Organization & Programming Pipeline Datapath and Control zybook: 11.6 Developed and maintained by the Bucknell University Computer Science Department - 2017 Hazard
Branch Prediction using Advanced Neural Methods
 Branch Prediction using Advanced Neural Methods Sunghoon Kim Department of Mechanical Engineering University of California, Berkeley shkim@newton.berkeley.edu Abstract Among the hardware techniques, two-level
Branch Prediction using Advanced Neural Methods Sunghoon Kim Department of Mechanical Engineering University of California, Berkeley shkim@newton.berkeley.edu Abstract Among the hardware techniques, two-level
A Novel Meta Predictor Design for Hybrid Branch Prediction
 A Novel Meta Predictor Design for Hybrid Branch Prediction YOUNG JUNG AHN, DAE YON HWANG, YONG SUK LEE, JIN-YOUNG CHOI AND GYUNGHO LEE The Dept. of Computer Science & Engineering Korea University Anam-dong
A Novel Meta Predictor Design for Hybrid Branch Prediction YOUNG JUNG AHN, DAE YON HWANG, YONG SUK LEE, JIN-YOUNG CHOI AND GYUNGHO LEE The Dept. of Computer Science & Engineering Korea University Anam-dong
[2] Predicting the direction of a branch is not enough. What else is necessary?
![[2] Predicting the direction of a branch is not enough. What else is necessary? [2] Predicting the direction of a branch is not enough. What else is necessary?](/thumbs/74/69859984.jpg) [2] When we talk about the number of operands in an instruction (a 1-operand or a 2-operand instruction, for example), what do we mean? [2] What are the two main ways to define performance? [2] Predicting
[2] When we talk about the number of operands in an instruction (a 1-operand or a 2-operand instruction, for example), what do we mean? [2] What are the two main ways to define performance? [2] Predicting
4. (3) What do we mean when we say something is an N-operand machine?
 1. (2) What are the two main ways to define performance? 2. (2) When dealing with control hazards, a prediction is not enough - what else is necessary in order to eliminate stalls? 3. (3) What is an "unbalanced"
1. (2) What are the two main ways to define performance? 2. (2) When dealing with control hazards, a prediction is not enough - what else is necessary in order to eliminate stalls? 3. (3) What is an "unbalanced"
A Detailed Study on Phase Predictors
 A Detailed Study on Phase Predictors Frederik Vandeputte, Lieven Eeckhout, and Koen De Bosschere Ghent University, Electronics and Information Systems Department Sint-Pietersnieuwstraat 41, B-9000 Gent,
A Detailed Study on Phase Predictors Frederik Vandeputte, Lieven Eeckhout, and Koen De Bosschere Ghent University, Electronics and Information Systems Department Sint-Pietersnieuwstraat 41, B-9000 Gent,
CPSC 3300 Spring 2017 Exam 2
 CPSC 3300 Spring 2017 Exam 2 Name: 1. Matching. Write the correct term from the list into each blank. (2 pts. each) structural hazard EPIC forwarding precise exception hardwired load-use data hazard VLIW
CPSC 3300 Spring 2017 Exam 2 Name: 1. Matching. Write the correct term from the list into each blank. (2 pts. each) structural hazard EPIC forwarding precise exception hardwired load-use data hazard VLIW
1. (2 )Clock rates have grown by a factor of 1000 while power consumed has only grown by a factor of 30. How was this accomplished?
 1. (2 )Clock rates have grown by a factor of 1000 while power consumed has only grown by a factor of 30. How was this accomplished? 2. (2 )What are the two main ways to define performance? 3. (2 )What
1. (2 )Clock rates have grown by a factor of 1000 while power consumed has only grown by a factor of 30. How was this accomplished? 2. (2 )What are the two main ways to define performance? 3. (2 )What
Worst-Case Execution Time Analysis. LS 12, TU Dortmund
 Worst-Case Execution Time Analysis Prof. Dr. Jian-Jia Chen LS 12, TU Dortmund 02, 03 May 2016 Prof. Dr. Jian-Jia Chen (LS 12, TU Dortmund) 1 / 53 Most Essential Assumptions for Real-Time Systems Upper
Worst-Case Execution Time Analysis Prof. Dr. Jian-Jia Chen LS 12, TU Dortmund 02, 03 May 2016 Prof. Dr. Jian-Jia Chen (LS 12, TU Dortmund) 1 / 53 Most Essential Assumptions for Real-Time Systems Upper
Implementing the Controller. Harvard-Style Datapath for DLX
 6.823, L6--1 Implementing the Controller Laboratory for Computer Science M.I.T. http://www.csg.lcs.mit.edu/6.823 6.823, L6--2 Harvard-Style Datapath for DLX Src1 ( j / ~j ) Src2 ( R / RInd) RegWrite MemWrite
6.823, L6--1 Implementing the Controller Laboratory for Computer Science M.I.T. http://www.csg.lcs.mit.edu/6.823 6.823, L6--2 Harvard-Style Datapath for DLX Src1 ( j / ~j ) Src2 ( R / RInd) RegWrite MemWrite
Pipelining. Traditional Execution. CS 365 Lecture 12 Prof. Yih Huang. add ld beq CS CS 365 2
 Pipelining CS 365 Lecture 12 Prof. Yih Huang CS 365 1 Traditional Execution 1 2 3 4 1 2 3 4 5 1 2 3 add ld beq CS 365 2 1 Pipelined Execution 1 2 3 4 5 1 2 3 4 5 1 2 3 4 5 1 2 3 4 5 1 2 3 4 5 1 2 3 4 5
Pipelining CS 365 Lecture 12 Prof. Yih Huang CS 365 1 Traditional Execution 1 2 3 4 1 2 3 4 5 1 2 3 add ld beq CS 365 2 1 Pipelined Execution 1 2 3 4 5 1 2 3 4 5 1 2 3 4 5 1 2 3 4 5 1 2 3 4 5 1 2 3 4 5
CMP 334: Seventh Class
 CMP 334: Seventh Class Performance HW 5 solution Averages and weighted averages (review) Amdahl's law Ripple-carry adder circuits Binary addition Half-adder circuits Full-adder circuits Subtraction, negative
CMP 334: Seventh Class Performance HW 5 solution Averages and weighted averages (review) Amdahl's law Ripple-carry adder circuits Binary addition Half-adder circuits Full-adder circuits Subtraction, negative
Computer Engineering Department. CC 311- Computer Architecture. Chapter 4. The Processor: Datapath and Control. Single Cycle
 Computer Engineering Department CC 311- Computer Architecture Chapter 4 The Processor: Datapath and Control Single Cycle Introduction The 5 classic components of a computer Processor Input Control Memory
Computer Engineering Department CC 311- Computer Architecture Chapter 4 The Processor: Datapath and Control Single Cycle Introduction The 5 classic components of a computer Processor Input Control Memory
Issue = Select + Wakeup. Out-of-order Pipeline. Issue. Issue = Select + Wakeup. OOO execution (2-wide) OOO execution (2-wide)
 Out-of-order Pipeline Buffer of instructions Issue = Select + Wakeup Select N oldest, read instructions N=, xor N=, xor and sub Note: ma have execution resource constraints: i.e., load/store/fp Fetch Decode
Out-of-order Pipeline Buffer of instructions Issue = Select + Wakeup Select N oldest, read instructions N=, xor N=, xor and sub Note: ma have execution resource constraints: i.e., load/store/fp Fetch Decode
[2] Predicting the direction of a branch is not enough. What else is necessary?
![[2] Predicting the direction of a branch is not enough. What else is necessary? [2] Predicting the direction of a branch is not enough. What else is necessary?](/thumbs/74/69860001.jpg) [2] What are the two main ways to define performance? [2] Predicting the direction of a branch is not enough. What else is necessary? [2] The power consumed by a chip has increased over time, but the clock
[2] What are the two main ways to define performance? [2] Predicting the direction of a branch is not enough. What else is necessary? [2] The power consumed by a chip has increased over time, but the clock
3. (2) What is the difference between fixed and hybrid instructions?
 1. (2 pts) What is a "balanced" pipeline? 2. (2 pts) What are the two main ways to define performance? 3. (2) What is the difference between fixed and hybrid instructions? 4. (2 pts) Clock rates have grown
1. (2 pts) What is a "balanced" pipeline? 2. (2 pts) What are the two main ways to define performance? 3. (2) What is the difference between fixed and hybrid instructions? 4. (2 pts) Clock rates have grown
Lecture 9: Control Hazard and Resolution. James C. Hoe Department of ECE Carnegie Mellon University
 18 447 Lectre 9: Control Hazard and Resoltion James C. Hoe Department of ECE Carnegie ellon University 18 447 S18 L09 S1, James C. Hoe, CU/ECE/CALC, 2018 Yor goal today Hosekeeping simple control flow
18 447 Lectre 9: Control Hazard and Resoltion James C. Hoe Department of ECE Carnegie ellon University 18 447 S18 L09 S1, James C. Hoe, CU/ECE/CALC, 2018 Yor goal today Hosekeeping simple control flow
NCU EE -- DSP VLSI Design. Tsung-Han Tsai 1
 NCU EE -- DSP VLSI Design. Tsung-Han Tsai 1 Multi-processor vs. Multi-computer architecture µp vs. DSP RISC vs. DSP RISC Reduced-instruction-set Register-to-register operation Higher throughput by using
NCU EE -- DSP VLSI Design. Tsung-Han Tsai 1 Multi-processor vs. Multi-computer architecture µp vs. DSP RISC vs. DSP RISC Reduced-instruction-set Register-to-register operation Higher throughput by using
Worst-Case Execution Time Analysis. LS 12, TU Dortmund
 Worst-Case Execution Time Analysis Prof. Dr. Jian-Jia Chen LS 12, TU Dortmund 09/10, Jan., 2018 Prof. Dr. Jian-Jia Chen (LS 12, TU Dortmund) 1 / 43 Most Essential Assumptions for Real-Time Systems Upper
Worst-Case Execution Time Analysis Prof. Dr. Jian-Jia Chen LS 12, TU Dortmund 09/10, Jan., 2018 Prof. Dr. Jian-Jia Chen (LS 12, TU Dortmund) 1 / 43 Most Essential Assumptions for Real-Time Systems Upper
INF 4140: Models of Concurrency Series 3
 Universitetet i Oslo Institutt for Informatikk PMA Olaf Owe, Martin Steffen, Toktam Ramezani INF 4140: Models of Concurrency Høst 2016 Series 3 14. 9. 2016 Topic: Semaphores (Exercises with hints for solution)
Universitetet i Oslo Institutt for Informatikk PMA Olaf Owe, Martin Steffen, Toktam Ramezani INF 4140: Models of Concurrency Høst 2016 Series 3 14. 9. 2016 Topic: Semaphores (Exercises with hints for solution)
Branch Prediction based attacks using Hardware performance Counters IIT Kharagpur
 Branch Prediction based attacks using Hardware performance Counters IIT Kharagpur March 19, 2018 Modular Exponentiation Public key Cryptography March 19, 2018 Branch Prediction Attacks 2 / 54 Modular Exponentiation
Branch Prediction based attacks using Hardware performance Counters IIT Kharagpur March 19, 2018 Modular Exponentiation Public key Cryptography March 19, 2018 Branch Prediction Attacks 2 / 54 Modular Exponentiation
COVER SHEET: Problem#: Points
 EEL 4712 Midterm 3 Spring 2017 VERSION 1 Name: UFID: Sign here to give permission for your test to be returned in class, where others might see your score: IMPORTANT: Please be neat and write (or draw)
EEL 4712 Midterm 3 Spring 2017 VERSION 1 Name: UFID: Sign here to give permission for your test to be returned in class, where others might see your score: IMPORTANT: Please be neat and write (or draw)
Computer Architecture ELEC2401 & ELEC3441
 Last Time Pipeline Hazard Computer Architecture ELEC2401 & ELEC3441 Lecture 8 Pipelining (3) Dr. Hayden Kwok-Hay So Department of Electrical and Electronic Engineering Structural Hazard Hazard Control
Last Time Pipeline Hazard Computer Architecture ELEC2401 & ELEC3441 Lecture 8 Pipelining (3) Dr. Hayden Kwok-Hay So Department of Electrical and Electronic Engineering Structural Hazard Hazard Control
Enrico Nardelli Logic Circuits and Computer Architecture
 Enrico Nardelli Logic Circuits and Computer Architecture Appendix B The design of VS0: a very simple CPU Rev. 1.4 (2009-10) by Enrico Nardelli B - 1 Instruction set Just 4 instructions LOAD M - Copy into
Enrico Nardelli Logic Circuits and Computer Architecture Appendix B The design of VS0: a very simple CPU Rev. 1.4 (2009-10) by Enrico Nardelli B - 1 Instruction set Just 4 instructions LOAD M - Copy into
1.10 (a) Function of AND, OR, NOT, NAND & NOR Logic gates and their input/output.
 Chapter 1.10 Logic Gates 1.10 (a) Function of AND, OR, NOT, NAND & NOR Logic gates and their input/output. Microprocessors are the central hardware that runs computers. There are several components that
Chapter 1.10 Logic Gates 1.10 (a) Function of AND, OR, NOT, NAND & NOR Logic gates and their input/output. Microprocessors are the central hardware that runs computers. There are several components that
Lecture 13: Sequential Circuits, FSM
 Lecture 13: Sequential Circuits, FSM Today s topics: Sequential circuits Finite state machines 1 Clocks A microprocessor is composed of many different circuits that are operating simultaneously if each
Lecture 13: Sequential Circuits, FSM Today s topics: Sequential circuits Finite state machines 1 Clocks A microprocessor is composed of many different circuits that are operating simultaneously if each
Fast Path-Based Neural Branch Prediction
 Fast Path-Based Neral Branch Prediction Daniel A. Jiménez http://camino.rtgers.ed Department of Compter Science Rtgers, The State University of New Jersey Overview The context: microarchitectre Branch
Fast Path-Based Neral Branch Prediction Daniel A. Jiménez http://camino.rtgers.ed Department of Compter Science Rtgers, The State University of New Jersey Overview The context: microarchitectre Branch
EE 660: Computer Architecture Out-of-Order Processors
 EE 660: Computer Architecture Out-of-Order Processors Yao Zheng Department of Electrical Engineering University of Hawaiʻi at Mānoa Based on the slides of Prof. David entzlaff Agenda I4 Processors I2O2
EE 660: Computer Architecture Out-of-Order Processors Yao Zheng Department of Electrical Engineering University of Hawaiʻi at Mānoa Based on the slides of Prof. David entzlaff Agenda I4 Processors I2O2
Rainbow Tables ENEE 457/CMSC 498E
 Rainbow Tables ENEE 457/CMSC 498E How are Passwords Stored? Option 1: Store all passwords in a table in the clear. Problem: If Server is compromised then all passwords are leaked. Option 2: Store only
Rainbow Tables ENEE 457/CMSC 498E How are Passwords Stored? Option 1: Store all passwords in a table in the clear. Problem: If Server is compromised then all passwords are leaked. Option 2: Store only
Fall 2008 CSE Qualifying Exam. September 13, 2008
 Fall 2008 CSE Qualifying Exam September 13, 2008 1 Architecture 1. (Quan, Fall 2008) Your company has just bought a new dual Pentium processor, and you have been tasked with optimizing your software for
Fall 2008 CSE Qualifying Exam September 13, 2008 1 Architecture 1. (Quan, Fall 2008) Your company has just bought a new dual Pentium processor, and you have been tasked with optimizing your software for
Limits to Branch Prediction
 This document was created with FrameMaker 4.0.4 Limits to Branch Prediction Trevor N. Mudge*, I-Cheng K. Chen, and John T. Coffey Electrical Engineering and Computer Science Department The University of
This document was created with FrameMaker 4.0.4 Limits to Branch Prediction Trevor N. Mudge*, I-Cheng K. Chen, and John T. Coffey Electrical Engineering and Computer Science Department The University of
Elementary maths for GMT
 Elementary maths for GMT Linear Algebra Part 2: Matrices, Elimination and Determinant m n matrices The system of m linear equations in n variables x 1, x 2,, x n a 11 x 1 + a 12 x 2 + + a 1n x n = b 1
Elementary maths for GMT Linear Algebra Part 2: Matrices, Elimination and Determinant m n matrices The system of m linear equations in n variables x 1, x 2,, x n a 11 x 1 + a 12 x 2 + + a 1n x n = b 1
CSC 5170: Theory of Computational Complexity Lecture 4 The Chinese University of Hong Kong 1 February 2010
 CSC 5170: Theory of Computational Complexity Lecture 4 The Chinese University of Hong Kong 1 February 2010 Computational complexity studies the amount of resources necessary to perform given computations.
CSC 5170: Theory of Computational Complexity Lecture 4 The Chinese University of Hong Kong 1 February 2010 Computational complexity studies the amount of resources necessary to perform given computations.
Hardware Design I Chap. 4 Representative combinational logic
 Hardware Design I Chap. 4 Representative combinational logic E-mail: shimada@is.naist.jp Already optimized circuits There are many optimized circuits which are well used You can reduce your design workload
Hardware Design I Chap. 4 Representative combinational logic E-mail: shimada@is.naist.jp Already optimized circuits There are many optimized circuits which are well used You can reduce your design workload
ECE 172 Digital Systems. Chapter 12 Instruction Pipelining. Herbert G. Mayer, PSU Status 7/20/2018
 ECE 172 Digital Systems Chapter 12 Instruction Pipelining Herbert G. Mayer, PSU Status 7/20/2018 1 Syllabus l Scheduling on Pipelined Architecture l Idealized Pipeline l Goal of Scheduling l Causes for
ECE 172 Digital Systems Chapter 12 Instruction Pipelining Herbert G. Mayer, PSU Status 7/20/2018 1 Syllabus l Scheduling on Pipelined Architecture l Idealized Pipeline l Goal of Scheduling l Causes for
Looking at a two binary digit sum shows what we need to extend addition to multiple binary digits.
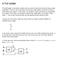 A Full Adder The half-adder is extremely useful until you want to add more that one binary digit quantities. The slow way to develop a two binary digit adders would be to make a truth table and reduce
A Full Adder The half-adder is extremely useful until you want to add more that one binary digit quantities. The slow way to develop a two binary digit adders would be to make a truth table and reduce
ECE290 Fall 2012 Lecture 22. Dr. Zbigniew Kalbarczyk
 ECE290 Fall 2012 Lecture 22 Dr. Zbigniew Kalbarczyk Today LC-3 Micro-sequencer (the control store) LC-3 Micro-programmed control memory LC-3 Micro-instruction format LC -3 Micro-sequencer (the circuitry)
ECE290 Fall 2012 Lecture 22 Dr. Zbigniew Kalbarczyk Today LC-3 Micro-sequencer (the control store) LC-3 Micro-programmed control memory LC-3 Micro-instruction format LC -3 Micro-sequencer (the circuitry)
Read this before starting!
 Points missed: Student's Name: Total score: / points East Tennessee State University Department of Computer and Information Sciences CSCI 25 (Tarnoff) Computer Organization TEST 2 for Spring Semester,
Points missed: Student's Name: Total score: / points East Tennessee State University Department of Computer and Information Sciences CSCI 25 (Tarnoff) Computer Organization TEST 2 for Spring Semester,
This Unit: Scheduling (Static + Dynamic) CIS 501 Computer Architecture. Readings. Review Example
 This Unit: Scheduling (Static + Dnamic) CIS 50 Computer Architecture Unit 8: Static and Dnamic Scheduling Application OS Compiler Firmware CPU I/O Memor Digital Circuits Gates & Transistors! Previousl:!
This Unit: Scheduling (Static + Dnamic) CIS 50 Computer Architecture Unit 8: Static and Dnamic Scheduling Application OS Compiler Firmware CPU I/O Memor Digital Circuits Gates & Transistors! Previousl:!
Synchronous Sequential Logic
 1 IT 201 DIGITAL SYSTEMS DESIGN MODULE4 NOTES Synchronous Sequential Logic Sequential Circuits - A sequential circuit consists of a combinational circuit and a feedback through the storage elements in
1 IT 201 DIGITAL SYSTEMS DESIGN MODULE4 NOTES Synchronous Sequential Logic Sequential Circuits - A sequential circuit consists of a combinational circuit and a feedback through the storage elements in
Formal Fault Analysis of Branch Predictors: Attacking countermeasures of Asymmetric key ciphers
 Formal Fault Analysis of Branch Predictors: Attacking countermeasures of Asymmetric key ciphers Sarani Bhattacharya and Debdeep Mukhopadhyay Indian Institute of Technology Kharagpur PROOFS 2016 August
Formal Fault Analysis of Branch Predictors: Attacking countermeasures of Asymmetric key ciphers Sarani Bhattacharya and Debdeep Mukhopadhyay Indian Institute of Technology Kharagpur PROOFS 2016 August
Processor Design & ALU Design
 3/8/2 Processor Design A. Sahu CSE, IIT Guwahati Please be updated with http://jatinga.iitg.ernet.in/~asahu/c22/ Outline Components of CPU Register, Multiplexor, Decoder, / Adder, substractor, Varity of
3/8/2 Processor Design A. Sahu CSE, IIT Guwahati Please be updated with http://jatinga.iitg.ernet.in/~asahu/c22/ Outline Components of CPU Register, Multiplexor, Decoder, / Adder, substractor, Varity of
Project Two RISC Processor Implementation ECE 485
 Project Two RISC Processor Implementation ECE 485 Chenqi Bao Peter Chinetti November 6, 2013 Instructor: Professor Borkar 1 Statement of Problem This project requires the design and test of a RISC processor
Project Two RISC Processor Implementation ECE 485 Chenqi Bao Peter Chinetti November 6, 2013 Instructor: Professor Borkar 1 Statement of Problem This project requires the design and test of a RISC processor
CPU DESIGN The Single-Cycle Implementation
 CSE 202 Computer Organization CPU DESIGN The Single-Cycle Implementation Shakil M. Khan (adapted from Prof. H. Roumani) Dept of CS & Eng, York University Sequential vs. Combinational Circuits Digital circuits
CSE 202 Computer Organization CPU DESIGN The Single-Cycle Implementation Shakil M. Khan (adapted from Prof. H. Roumani) Dept of CS & Eng, York University Sequential vs. Combinational Circuits Digital circuits
UNIT II COMBINATIONAL CIRCUITS:
 UNIT II COMBINATIONAL CIRCUITS: INTRODUCTION: The digital system consists of two types of circuits, namely (i) (ii) Combinational circuits Sequential circuits Combinational circuit consists of logic gates
UNIT II COMBINATIONAL CIRCUITS: INTRODUCTION: The digital system consists of two types of circuits, namely (i) (ii) Combinational circuits Sequential circuits Combinational circuit consists of logic gates
Computer organization
 Computer organization Levels of abstraction Assembler Simulator Applications C C++ Java High-level language SOFTWARE add lw ori Assembly language Goal 0000 0001 0000 1001 0101 Machine instructions/data
Computer organization Levels of abstraction Assembler Simulator Applications C C++ Java High-level language SOFTWARE add lw ori Assembly language Goal 0000 0001 0000 1001 0101 Machine instructions/data
BETTER BRANCH PREDICTION THROUGH PROPHET/CRITIC HYBRIDS
 BETTER BRANCH PREDICTION THROUGH PROPHET/CRITIC HYBRIDS THE PROPHET/CRITIC HYBRID CONDITIONAL BRANCH PREDICTOR HAS TWO COMPONENT PREDICTORS. THE PROPHET USES A BRANCH S HISTORY TO PREDICT ITS DIRECTION.
BETTER BRANCH PREDICTION THROUGH PROPHET/CRITIC HYBRIDS THE PROPHET/CRITIC HYBRID CONDITIONAL BRANCH PREDICTOR HAS TWO COMPONENT PREDICTORS. THE PROPHET USES A BRANCH S HISTORY TO PREDICT ITS DIRECTION.
Lecture 5. Logical Effort Using LE on a Decoder
 Lecture 5 Logical Effort Using LE on a Decoder Mark Horowitz Computer Systems Laboratory Stanford University horowitz@stanford.edu Copyright 00 by Mark Horowitz Overview Reading Harris, Logical Effort
Lecture 5 Logical Effort Using LE on a Decoder Mark Horowitz Computer Systems Laboratory Stanford University horowitz@stanford.edu Copyright 00 by Mark Horowitz Overview Reading Harris, Logical Effort
Performance Prediction Models
 Performance Prediction Models Shruti Padmanabha, Andrew Lukefahr, Reetuparna Das, Scott Mahlke {shrupad,lukefahr,reetudas,mahlke}@umich.edu Gem5 workshop Micro 2012 December 2, 2012 Composite Cores Pushing
Performance Prediction Models Shruti Padmanabha, Andrew Lukefahr, Reetuparna Das, Scott Mahlke {shrupad,lukefahr,reetudas,mahlke}@umich.edu Gem5 workshop Micro 2012 December 2, 2012 Composite Cores Pushing
HW Solution 3 Due: July 15
 ECS 315: Probability and Random Processes 2010/1 HW Solution 3 Due: July 15 Lecturer: Prapun Suksompong, Ph.D. Instructions (a) A part of ONE question will be graded. Of course, you do not know which problem
ECS 315: Probability and Random Processes 2010/1 HW Solution 3 Due: July 15 Lecturer: Prapun Suksompong, Ph.D. Instructions (a) A part of ONE question will be graded. Of course, you do not know which problem
Figure 4.9 MARIE s Datapath
 Term Control Word Microoperation Hardwired Control Microprogrammed Control Discussion A set of signals that executes a microoperation. A register transfer or other operation that the CPU can execute in
Term Control Word Microoperation Hardwired Control Microprogrammed Control Discussion A set of signals that executes a microoperation. A register transfer or other operation that the CPU can execute in
Potentials of Branch Predictors from Entropy Viewpoints
 Potentials of Branch Predictors from Entropy Viewpoints Takashi Yokota,KanemitsuOotsu, and Takanobu Baba Department of Information Science, Utsunomiya University, 7 2 Yoto, Utsunomiya-shi, Tochigi, 32
Potentials of Branch Predictors from Entropy Viewpoints Takashi Yokota,KanemitsuOotsu, and Takanobu Baba Department of Information Science, Utsunomiya University, 7 2 Yoto, Utsunomiya-shi, Tochigi, 32
Caches in WCET Analysis
 Caches in WCET Analysis Jan Reineke Department of Computer Science Saarland University Saarbrücken, Germany ARTIST Summer School in Europe 2009 Autrans, France September 7-11, 2009 Jan Reineke Caches in
Caches in WCET Analysis Jan Reineke Department of Computer Science Saarland University Saarbrücken, Germany ARTIST Summer School in Europe 2009 Autrans, France September 7-11, 2009 Jan Reineke Caches in
Department of Electrical and Computer Engineering The University of Texas at Austin
 Department of Electrical and Computer Engineering The University of Texas at Austin EE 360N, Fall 2004 Yale Patt, Instructor Aater Suleman, Huzefa Sanjeliwala, Dam Sunwoo, TAs Exam 1, October 6, 2004 Name:
Department of Electrical and Computer Engineering The University of Texas at Austin EE 360N, Fall 2004 Yale Patt, Instructor Aater Suleman, Huzefa Sanjeliwala, Dam Sunwoo, TAs Exam 1, October 6, 2004 Name:
CMP N 301 Computer Architecture. Appendix C
 CMP N 301 Computer Architecture Appendix C Outline Introduction Pipelining Hazards Pipelining Implementation Exception Handling Advanced Issues (Dynamic Scheduling, Out of order Issue, Superscalar, etc)
CMP N 301 Computer Architecture Appendix C Outline Introduction Pipelining Hazards Pipelining Implementation Exception Handling Advanced Issues (Dynamic Scheduling, Out of order Issue, Superscalar, etc)
Exploiting Bias in the Hysteresis Bit of 2-bit Saturating Counters in Branch Predictors
 Journal of Instruction-Level Parallelism 5(23) -32 Submitted 2/2; published 6/3 Exploiting Bias in the Hysteresis Bit of 2-bit Saturating Counters in Branch Predictors Gabriel H. Loh Dana S. Henry Arvind
Journal of Instruction-Level Parallelism 5(23) -32 Submitted 2/2; published 6/3 Exploiting Bias in the Hysteresis Bit of 2-bit Saturating Counters in Branch Predictors Gabriel H. Loh Dana S. Henry Arvind
Digital Logic. CS211 Computer Architecture. l Topics. l Transistors (Design & Types) l Logic Gates. l Combinational Circuits.
 CS211 Computer Architecture Digital Logic l Topics l Transistors (Design & Types) l Logic Gates l Combinational Circuits l K-Maps Figures & Tables borrowed from:! http://www.allaboutcircuits.com/vol_4/index.html!
CS211 Computer Architecture Digital Logic l Topics l Transistors (Design & Types) l Logic Gates l Combinational Circuits l K-Maps Figures & Tables borrowed from:! http://www.allaboutcircuits.com/vol_4/index.html!
COSC 243. Introduction to Logic And Combinatorial Logic. Lecture 4 - Introduction to Logic and Combinatorial Logic. COSC 243 (Computer Architecture)
 COSC 243 Introduction to Logic And Combinatorial Logic 1 Overview This Lecture Introduction to Digital Logic Gates Boolean algebra Combinatorial Logic Source: Chapter 11 (10 th edition) Source: J.R. Gregg,
COSC 243 Introduction to Logic And Combinatorial Logic 1 Overview This Lecture Introduction to Digital Logic Gates Boolean algebra Combinatorial Logic Source: Chapter 11 (10 th edition) Source: J.R. Gregg,
0-1 Knapsack Problem in parallel Progetto del corso di Calcolo Parallelo AA
 0-1 Knapsack Problem in parallel Progetto del corso di Calcolo Parallelo AA 2008-09 Salvatore Orlando 1 0-1 Knapsack problem N objects, j=1,..,n Each kind of item j has a value p j and a weight w j (single
0-1 Knapsack Problem in parallel Progetto del corso di Calcolo Parallelo AA 2008-09 Salvatore Orlando 1 0-1 Knapsack problem N objects, j=1,..,n Each kind of item j has a value p j and a weight w j (single
CMP 338: Third Class
 CMP 338: Third Class HW 2 solution Conversion between bases The TINY processor Abstraction and separation of concerns Circuit design big picture Moore s law and chip fabrication cost Performance What does
CMP 338: Third Class HW 2 solution Conversion between bases The TINY processor Abstraction and separation of concerns Circuit design big picture Moore s law and chip fabrication cost Performance What does
Boolean Algebra and Digital Logic 2009, University of Colombo School of Computing
 IT 204 Section 3.0 Boolean Algebra and Digital Logic Boolean Algebra 2 Logic Equations to Truth Tables X = A. B + A. B + AB A B X 0 0 0 0 3 Sum of Products The OR operation performed on the products of
IT 204 Section 3.0 Boolean Algebra and Digital Logic Boolean Algebra 2 Logic Equations to Truth Tables X = A. B + A. B + AB A B X 0 0 0 0 3 Sum of Products The OR operation performed on the products of
The Design Procedure. Output Equation Determination - Derive output equations from the state table
 The Design Procedure Specification Formulation - Obtain a state diagram or state table State Assignment - Assign binary codes to the states Flip-Flop Input Equation Determination - Select flipflop types
The Design Procedure Specification Formulation - Obtain a state diagram or state table State Assignment - Assign binary codes to the states Flip-Flop Input Equation Determination - Select flipflop types
INF2270 Spring Philipp Häfliger. Lecture 8: Superscalar CPUs, Course Summary/Repetition (1/2)
 INF2270 Spring 2010 Philipp Häfliger Summary/Repetition (1/2) content From Scalar to Superscalar Lecture Summary and Brief Repetition Binary numbers Boolean Algebra Combinational Logic Circuits Encoder/Decoder
INF2270 Spring 2010 Philipp Häfliger Summary/Repetition (1/2) content From Scalar to Superscalar Lecture Summary and Brief Repetition Binary numbers Boolean Algebra Combinational Logic Circuits Encoder/Decoder
Lecture 12: Pipelined Implementations: Control Hazards and Resolutions
 18-447 Lectre 12: Pipelined Implementations: Control Hazards and Resoltions S 09 L12-1 James C. Hoe Dept of ECE, CU arch 2, 2009 Annoncements: Spring break net week!! Project 2 de the week after spring
18-447 Lectre 12: Pipelined Implementations: Control Hazards and Resoltions S 09 L12-1 James C. Hoe Dept of ECE, CU arch 2, 2009 Annoncements: Spring break net week!! Project 2 de the week after spring
Module 2 LOSSLESS IMAGE COMPRESSION SYSTEMS. Version 2 ECE IIT, Kharagpur
 Module 2 LOSSLESS IMAGE COMPRESSION SYSTEMS Lesson 5 Other Coding Techniques Instructional Objectives At the end of this lesson, the students should be able to:. Convert a gray-scale image into bit-plane
Module 2 LOSSLESS IMAGE COMPRESSION SYSTEMS Lesson 5 Other Coding Techniques Instructional Objectives At the end of this lesson, the students should be able to:. Convert a gray-scale image into bit-plane
Counters. We ll look at different kinds of counters and discuss how to build them
 Counters We ll look at different kinds of counters and discuss how to build them These are not only examples of sequential analysis and design, but also real devices used in larger circuits 1 Introducing
Counters We ll look at different kinds of counters and discuss how to build them These are not only examples of sequential analysis and design, but also real devices used in larger circuits 1 Introducing
Pipelined Datapath. Reading. Sections Practice Problems: 1, 3, 8, 12 (2) Lecture notes from MKP, H. H. Lee and S.
 Pipelined Datapath Lectre notes from KP, H. H. Lee and S. Yalamanchili Sections 4.5 4. Practice Problems:, 3, 8, 2 Reading (2) Pipeline Performance Assme time for stages is v ps for register read or write
Pipelined Datapath Lectre notes from KP, H. H. Lee and S. Yalamanchili Sections 4.5 4. Practice Problems:, 3, 8, 2 Reading (2) Pipeline Performance Assme time for stages is v ps for register read or write
DEPARTMENT OF EECS MASSACHUSETTS INSTITUTE OF TECHNOLOGY. 6.02: Digital Communication Systems, Fall Quiz I. October 11, 2012
 6.02 Fall 2012, Quiz 2 Page 1 of 12 Name: DEPARTMENT OF EECS MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.02: Digital Communication Systems, Fall 2012 Quiz I October 11, 2012 your section Section Time Recitation
6.02 Fall 2012, Quiz 2 Page 1 of 12 Name: DEPARTMENT OF EECS MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.02: Digital Communication Systems, Fall 2012 Quiz I October 11, 2012 your section Section Time Recitation
Examples of Groups
 Examples of Groups 8-23-2016 In this section, I ll look at some additional examples of groups. Some of these will be discussed in more detail later on. In many of these examples, I ll assume familiar things
Examples of Groups 8-23-2016 In this section, I ll look at some additional examples of groups. Some of these will be discussed in more detail later on. In many of these examples, I ll assume familiar things
18.06 Problem Set 3 Solution Due Wednesday, 25 February 2009 at 4 pm in Total: 160 points.
 8.6 Problem Set 3 Solution Due Wednesday, 25 February 29 at 4 pm in 2-6. Total: 6 points. Problem : Consider the matrix A = 2 4 2 6 3 4 2 7 (a) Reduce A to echelon form U, find a special solution for each
8.6 Problem Set 3 Solution Due Wednesday, 25 February 29 at 4 pm in 2-6. Total: 6 points. Problem : Consider the matrix A = 2 4 2 6 3 4 2 7 (a) Reduce A to echelon form U, find a special solution for each
Logic and Computer Design Fundamentals. Chapter 8 Sequencing and Control
 Logic and Computer Design Fundamentals Chapter 8 Sequencing and Control Datapath and Control Datapath - performs data transfer and processing operations Control Unit - Determines enabling and sequencing
Logic and Computer Design Fundamentals Chapter 8 Sequencing and Control Datapath and Control Datapath - performs data transfer and processing operations Control Unit - Determines enabling and sequencing
Cache-Oblivious Algorithms
 Cache-Oblivious Algorithms 1 Cache-Oblivious Model 2 The Unknown Machine Algorithm C program gcc Object code linux Execution Can be executed on machines with a specific class of CPUs Algorithm Java program
Cache-Oblivious Algorithms 1 Cache-Oblivious Model 2 The Unknown Machine Algorithm C program gcc Object code linux Execution Can be executed on machines with a specific class of CPUs Algorithm Java program
Simple Instruction-Pipelining. Pipelined Harvard Datapath
 6.823, L8--1 Simple ruction-pipelining Laboratory for Computer Science M.I.T. http://www.csg.lcs.mit.edu/6.823 Pipelined Harvard path 6.823, L8--2. I fetch decode & eg-fetch execute memory Clock period
6.823, L8--1 Simple ruction-pipelining Laboratory for Computer Science M.I.T. http://www.csg.lcs.mit.edu/6.823 Pipelined Harvard path 6.823, L8--2. I fetch decode & eg-fetch execute memory Clock period
Cache-Oblivious Algorithms
 Cache-Oblivious Algorithms 1 Cache-Oblivious Model 2 The Unknown Machine Algorithm C program gcc Object code linux Execution Can be executed on machines with a specific class of CPUs Algorithm Java program
Cache-Oblivious Algorithms 1 Cache-Oblivious Model 2 The Unknown Machine Algorithm C program gcc Object code linux Execution Can be executed on machines with a specific class of CPUs Algorithm Java program
ECS 120 Lesson 23 The Class P
 ECS 120 Lesson 23 The Class P Oliver Kreylos Wednesday, May 23th, 2001 We saw last time how to analyze the time complexity of Turing Machines, and how to classify languages into complexity classes. We
ECS 120 Lesson 23 The Class P Oliver Kreylos Wednesday, May 23th, 2001 We saw last time how to analyze the time complexity of Turing Machines, and how to classify languages into complexity classes. We
Simple Instruction-Pipelining (cont.) Pipelining Jumps
 6.823, L9--1 Simple ruction-pipelining (cont.) + Interrupts Updated March 6, 2000 Laboratory for Computer Science M.I.T. http://www.csg.lcs.mit.edu/6.823 Src1 ( j / ~j ) Src2 ( / Ind) Pipelining Jumps
6.823, L9--1 Simple ruction-pipelining (cont.) + Interrupts Updated March 6, 2000 Laboratory for Computer Science M.I.T. http://www.csg.lcs.mit.edu/6.823 Src1 ( j / ~j ) Src2 ( / Ind) Pipelining Jumps
Sequential Circuit Design
 Sequential Circuit esign esign Procedure. Specification 2. Formulation Obtain a state diagram or state table 3. State Assignment Assign binary codes to the states 4. Flip-Flop Input Equation etermination
Sequential Circuit esign esign Procedure. Specification 2. Formulation Obtain a state diagram or state table 3. State Assignment Assign binary codes to the states 4. Flip-Flop Input Equation etermination
CSE 140 Spring 2017: Final Solutions (Total 50 Points)
 CSE 140 Spring 2017: Final Solutions (Total 50 Points) 1. (Boolean Algebra) Prove the following Boolean theorem using Boolean laws only, i.e. no theorem is allowed for the proof. State the name of the
CSE 140 Spring 2017: Final Solutions (Total 50 Points) 1. (Boolean Algebra) Prove the following Boolean theorem using Boolean laws only, i.e. no theorem is allowed for the proof. State the name of the
Floating Point Representation and Digital Logic. Lecture 11 CS301
 Floating Point Representation and Digital Logic Lecture 11 CS301 Administrative Daily Review of today s lecture w Due tomorrow (10/4) at 8am Lab #3 due Friday (9/7) 1:29pm HW #5 assigned w Due Monday 10/8
Floating Point Representation and Digital Logic Lecture 11 CS301 Administrative Daily Review of today s lecture w Due tomorrow (10/4) at 8am Lab #3 due Friday (9/7) 1:29pm HW #5 assigned w Due Monday 10/8
So far we discussed random number generators that need to have the maximum length period.
 So far we discussed random number generators that need to have the maximum length period. Even the increment series has the maximum length period yet it is by no means random How do we decide if a generator
So far we discussed random number generators that need to have the maximum length period. Even the increment series has the maximum length period yet it is by no means random How do we decide if a generator
Lecture 13: Sequential Circuits, FSM
 Lecture 13: Sequential Circuits, FSM Today s topics: Sequential circuits Finite state machines Reminder: midterm on Tue 2/28 will cover Chapters 1-3, App A, B if you understand all slides, assignments,
Lecture 13: Sequential Circuits, FSM Today s topics: Sequential circuits Finite state machines Reminder: midterm on Tue 2/28 will cover Chapters 1-3, App A, B if you understand all slides, assignments,
Read this before starting!
 Points missed: Student's Name: Total score: / points East Tennessee State University epartment of omputer and Information Sciences SI 25 (Tarnoff) omputer Organization TEST 2 for Fall Semester, 28 Read
Points missed: Student's Name: Total score: / points East Tennessee State University epartment of omputer and Information Sciences SI 25 (Tarnoff) omputer Organization TEST 2 for Fall Semester, 28 Read
Collision. Kuan-Yu Chen ( 陳冠宇 ) TR-212, NTUST
 Collision Kuan-Yu Chen ( 陳冠宇 ) 2018/12/17 @ TR-212, NTUST Review Hash table is a data structure in which keys are mapped to array positions by a hash function When two or more keys map to the same memory
Collision Kuan-Yu Chen ( 陳冠宇 ) 2018/12/17 @ TR-212, NTUST Review Hash table is a data structure in which keys are mapped to array positions by a hash function When two or more keys map to the same memory
Combinational Logic. Mantıksal Tasarım BBM231. section instructor: Ufuk Çelikcan
 Combinational Logic Mantıksal Tasarım BBM23 section instructor: Ufuk Çelikcan Classification. Combinational no memory outputs depends on only the present inputs expressed by Boolean functions 2. Sequential
Combinational Logic Mantıksal Tasarım BBM23 section instructor: Ufuk Çelikcan Classification. Combinational no memory outputs depends on only the present inputs expressed by Boolean functions 2. Sequential
ECE/CS 250: Computer Architecture. Basics of Logic Design: Boolean Algebra, Logic Gates. Benjamin Lee
 ECE/CS 250: Computer Architecture Basics of Logic Design: Boolean Algebra, Logic Gates Benjamin Lee Slides based on those from Alvin Lebeck, Daniel Sorin, Andrew Hilton, Amir Roth, Gershon Kedem Admin
ECE/CS 250: Computer Architecture Basics of Logic Design: Boolean Algebra, Logic Gates Benjamin Lee Slides based on those from Alvin Lebeck, Daniel Sorin, Andrew Hilton, Amir Roth, Gershon Kedem Admin
Boolean Logic Continued Prof. James L. Frankel Harvard University
 Boolean Logic Continued Prof. James L. Frankel Harvard University Version of 10:18 PM 5-Sep-2017 Copyright 2017, 2016 James L. Frankel. All rights reserved. D Latch D R S Clk D Clk R S X 0 ~S 0 = R 0 ~R
Boolean Logic Continued Prof. James L. Frankel Harvard University Version of 10:18 PM 5-Sep-2017 Copyright 2017, 2016 James L. Frankel. All rights reserved. D Latch D R S Clk D Clk R S X 0 ~S 0 = R 0 ~R
What s the Deal? MULTIPLICATION. Time to multiply
 What s the Deal? MULTIPLICATION Time to multiply Multiplying two numbers requires a multiply Luckily, in binary that s just an AND gate! 0*0=0, 0*1=0, 1*0=0, 1*1=1 Generate a bunch of partial products
What s the Deal? MULTIPLICATION Time to multiply Multiplying two numbers requires a multiply Luckily, in binary that s just an AND gate! 0*0=0, 0*1=0, 1*0=0, 1*1=1 Generate a bunch of partial products
Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay
 Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 13 Competitive Optimality of the Shannon Code So, far we have studied
Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 13 Competitive Optimality of the Shannon Code So, far we have studied
Summary of Last Lectures
 Lossless Coding IV a k p k b k a 0.16 111 b 0.04 0001 c 0.04 0000 d 0.16 110 e 0.23 01 f 0.07 1001 g 0.06 1000 h 0.09 001 i 0.15 101 100 root 1 60 1 0 0 1 40 0 32 28 23 e 17 1 0 1 0 1 0 16 a 16 d 15 i
Lossless Coding IV a k p k b k a 0.16 111 b 0.04 0001 c 0.04 0000 d 0.16 110 e 0.23 01 f 0.07 1001 g 0.06 1000 h 0.09 001 i 0.15 101 100 root 1 60 1 0 0 1 40 0 32 28 23 e 17 1 0 1 0 1 0 16 a 16 d 15 i
(a) Definition of TMs. First Problem of URMs
 Sec. 4: Turing Machines First Problem of URMs (a) Definition of the Turing Machine. (b) URM computable functions are Turing computable. (c) Undecidability of the Turing Halting Problem That incrementing
Sec. 4: Turing Machines First Problem of URMs (a) Definition of the Turing Machine. (b) URM computable functions are Turing computable. (c) Undecidability of the Turing Halting Problem That incrementing
