DTM: A Distributed Traffic Management Algorithm for Sensor Networks
|
|
|
- Poppy Turner
- 5 years ago
- Views:
Transcription
1 8 IJCSNS International Journal of Computer Science Network Security, VOL6 No8A, Augut 6 DM: A Ditributed raffic Management Algorithm for Senor Network Yantao Pan, Xicheng Lu, Peidong Zhu School of Computer, National Unierity of Defene echnology, Changha, P R China Summary Lifetime optimization i a key challenge of enor network Since data tranmiion i the main energy conumer, it i important to make ue of energy efficient routing protocol We regard the lifetime optimization problem a a multi-ource ingle-ink flow problem in a directed graph with capacity power on ertice hen we propoe a ditributed algorithm to ole thi problem he method gie the alue of imum lifetime exactly Key word: Senor Network, raffic Management, Lifetime imization 1 Introduction he deelopment of enor network proide u a new way to interact with phyical enironment It i a key challenge to imize the lifetime of a enor network, which i uually defined a the time from it deployment to it partition when there exit a node that cannot end data to the ink Literature [1-4] inetigate the upper bound the expectation of a enor network imum lifetime Literature [5-8] propoe heuritic algorithm to imize the lifetime approximately Howeer, none of thoe approache proide the imum lifetime exactly In thi paper, we exploit thi problem by flow model propoe a ditributed algorithm to achiee a imum lifetime routing he ret of thi paper i organized a follow In ection, we propoe the formulation of the problem We gie a centralized algorithm in ection 3 then a ditributed algorithm in ection 4 In ection 5, ome concluding remark are made Problem Statement Formulation Conider a group of wirele tatic enor node V romly ditributed in a region Each node V ha a limited battery energy upply which i mainly ued for data communication Aume that each node ha a fixed communication power a fixed tranmiion radiu Let p () be the total quantity of data that ertex can end It i a function of the initial energy upply the communication power Let w () be the data-generating rate at a ource node A enor network can be defined a a directed graph with power on ertice Definition-1 A enor tranportation network (It will be howed a SenorNet for hort in the ret of thi paper) i defined a the form of N = ( V, A, p, X, t), where 1 GV (, A) i a connected imple directed graph, p (): Va i the reiduary tranmiion capacity of ertex, 3 X i the ource et t i the ink Let ( H) = ( u, ) A H, u V \ H} ( H) = (, u) A H, u V \ H} be the et of arc entering leaing a node et H For a function f( a): Aa, we denote f ( H) = ˆ f( a) f ( H) = ˆ f( a) a ( H) a ( H) Definition- f( a): Aa i defined a a flow of N if f () p(), V f () = f (), I Let al( f ) = ˆ f ( X ) f ( X ) be the alue of f Definition-3 Let N be a SenorNet Flow f i defined a a routing of N if there i a uch that f ( x) f ( x) = w( x), p () f = (), V i called the lifetime of N under the routing f If there i no f it correponding o a to >, f i a imum lifetime routing i the imum lifetime For a SenorNet N = ( V, A, p, X, t), we may add a irtual ource to it add a irtual arc from it to each ource Additionally, we et the capacity of a irtual arc to be w() correponding to ertex, where i a alue not more than the imum lifetime hen we can tranfer the imum flow problem from a multi-ource network to a ingle-ource network Manucript receied Augut 5, 6 Manucript reied Augut 5, 6
2 IJCSNS International Journal of Computer Science Network Security, VOL6 No8A, Augut 6 9 Definition-4 Let N = ( V, A, p, X, t) be a SenorNet aume > N = ( V, A, p, c,, t) i defined a the tranformed network of N about, if following 4 condition are atified 1 V = V U } A = AU A, where A = (, x) } 3 p (), V, p () =, otherwie 4 w(), u =, c ( u, ) =, otherwie Lemma-1 Let N be a SenorNet let be it imum lifetime Suppoe N i the tranformed network of N about, f i a imum flow of N hen, al( f ) = w( x) heorem-1 Suppoe N i the tranformed network of N about f i a imum flow of N hen i the imum that atifie al( f ) = w( x) Suppoe i }, i =,1,, i a equence, where = 1 i an upper bound of the imum lifetime he ret element are generated by BS algorithm, where ξ i the gien preciion 1, al( f ) = w( x), θ ( ) =, al( f ) < w( x) BS (, 1 ) 1 low up 1 i while up low > ξ 3 i ( up low ) 4 ifθ ( i ) = 5 up i 6 ele 7 low i 8 i= i 1 9 } 1 return ( ) up low Fig1 BS algorithm From heorem-1 BS algorithm, we obtain lim i } = herefore, we can take a binary i earch between the lower upper bound of the imum lifetime finally achiee a alue exactly enough if only we could find the imum flow of N In order to tranfer the contraint of N from ertice to arc, we diide a ertex into two irtual ertice add a irtual arc between them he capacity of a irtual arc i et to the reidual tranmiion capacity of the correponding ertex For a SenorNet N = ( V, A, p, X, t), we may add a irtual ource to it add a irtual arc from it to each ource Additionally, we et the capacity of a irtual arc to be w() correponding to ertex Definition-5 Let N = ( V, A, p, c,, t) be a tranformed network of N hen N = ( V, A, c,, t) i defined a the VA (Vertex to Arc) network of N, if the following condition are atified 1 V = V U V, uch that V V for each V A = AA U AV, uch that 1) ( u, ) A, (, ) (, ) A c u = c u for ( u, ) A ) (, ) A, (, ) ( ) V c = p for V heorem- Let N = ( V, A, c,, t) be a VA network N = ( V, A, p, c,, t) be a tranformed network of N = ( V, A, p, X, t) Aume f to be a imum flow of N hen f i a imum flow of N, where f ( u, ) = ˆ f ( u, ), ( u, ) A And f i a imum flow of N, ' where f( u, ) = ˆ f( u, ), ( u, ) A Centralized Algorithm In thi ection, we propoe a centralized algorithm baed on preflow-puh method introduced by Golberg-arjan [9] to ole the imum flow problem in N Since there i only N in conideration in thi ection, we denote it a N = ( V, A, c,, t) for hort denote the reidual network of it a N ( f) = ( V, A, c,, t) For a node V, we call ex() f = () f () the exce of It i the difference between the total flow entering leaing node he flow coneration contraint i atified when all node hae zero excee except the ource the ink Definition-6 A function ζ : A a i defined a a preflow if 1 ex( ) for V \, t}, ζ ( a) c( a) for a A A node i actie if it exce i poitie he baic idea i to puh the exce flow to the neighbor that are cloer to the ink o do thi, a height
3 1 IJCSNS International Journal of Computer Science Network Security, VOL6 No8A, Augut 6 function h: V a i aigned to each node A alid height function atify: ht () = hu ( ) h ( ) 1 for ( u, ) A We only puh flow from a higher node to a lower node Definition-7 A reidual arc ( u, ) A, u i admiible if hu ( ) = h ( ) 1 Let u be an actie node uppoe ( u, ) i admiible We puh Δ unit flow from u to through ( u, ), Δ= min ex, c ( u, ) hen ex = ex Δ where } ex() = ex() Δ If no more admiible arc exit, we perform lift proce to create admiible arc In thi tage, a node that ha no admiible outward arc et it height to min h ( ) 1 ( u, ) A } he algorithm end when there i no actie node At that tage the flow i feaible for the firt time alo imized CA( N ) 1 h ( ) V ht () Compute h ( ) for other node 3 ex( ), V ζ ( a), a A 4 for u Adj ( ) = ˆ u (, u) A } 5 ζ ( u, ) cu (, ), exu ( ) cu (, ) 6 while there exit actie node 7 elect an actie node u 8 if there i admiible arc 9 elect an admiible arc (, u ) 1 Δ min ex, c ( u, )} 11 ex ex( u ) Δ 1 ex( ) ex( ) Δ 13 ζ(, u) ζ(, u ) Δ 14 c (, u ) c (, u ) Δ 15 c (, u) c (, u ) Δ 16 }ele 17 hu ( ) min h ( ) 1( u, ) A } 18 }//while 19 return ζ Fig CA algorithm Lemma- Let h be a alid height function hen hu ( ) i a lower bound on the ditance from u to t in N ( ζ ) heorem-3he CA algorithm i finite terminate with the imum -t flow Proof he algorithm i finite becaue the height alue can increae at mot V time each he algorithm end with a flow f = ζ becaue if there were any actie node, the algorithm would not end At the end, h () = V Since h () i a lower bound on the hortet t path in N ( f ), there i no tpath in N( f ) hen there i no t admiible path in N ( f) the flow i imized 3 heorem-4he time complexity of CA i OV ( ) for N = ( V, A, p, X, t) 4 Ditributed Algorithm In thi ection, we propoe an aynchronouly ditributed algorithm DA baed on CA he baic idea i introduced by [1] he difference i that our approach can ole the imum flow problem in multi-ource network with capacity contraint on ertice We aume that each node in the network execute a ditributed program aynchronouly Each link i bidirectional All procee are eent-drien work on local data Communication are meage baed We aume that any ource node know the number of ource X he execution of algorithm alo proceed in two phae he firt phae et height of all node he econd phae etablihe the imum flow Different from the centralized algorithm preented in ection 3, a reidual arc ( u, ) i admiible for node u if hu ( ) h ( ) 1 Additionally, in lift proce, we increae a node height to a alue which i jut enough for it to puh all it exce out Conider a SenorNet N = ( V, A, p, X, t) We regard a node V a two irtual node i called In-node i called Out-node hey are connected to the neighbor of node by incoming arc outgoing arc repectiely At each node, the program maintain the following information 1 Adj () = Adj ( ) U Adj ( ) i the neighbor et, Adj( ) = u ( u, ) A where } Adj( ) = u (, u) A} h± ( ) i the height of ± 3 ex( ± ) i the exce of ± 4 h ± i u height from the point of iew of ± 5 ty() i the node type 6 c± i the reidual capacity of arc (, u ) or (, u ) Epecially c () = p() at the beginning If i a ource, it ha to maintain following information about the irtual ource 1 InitOk denote if all ource are initialized already
4 IJCSNS International Journal of Computer Science Network Security, VOL6 No8A, Augut 6 11 h () c () for 3 ex( ) h ( ) 4 h c for all u V he algorithm terminate at any of two ituation he firt i when all node are inactie hi mean there are no more meage will be exchanged he econd i when a ource puhe it exce back to the irtual ource hi mean the ource cannot tranmit wdata to the ink A to BS algorithm, i larger than the imum flow more computation i uele herefore, we terminate the algorithm he detail of DA are decribed a follow MainOnNode( ) 1 Initialization( ) while (1) 3 wait for incoming mg 4 proce mg 5 }//while Fig3 MainOnNode Initialization( ) 1 ex( ) ex( ) h ( ), h ( ) h ( ), h ( ) 3 for all u Adj( ) 4 c M 1 5 for all u Adj( ) 6 c ( u ) 7 c ( ) p( ) c ( ) 8 h ( u ), h for allu V 9 if ty( )= Source 1 InitOk 11 Adj( ) Adj( ) U } 1 h ( ) c ( ) 13 ex( ) h ( ) 14 h ( u ), c for allu V 15 }//if 16 if ty( )= Sink 17 h ( ) 18 InitHight( ) 19 }//if Fig4 Initialization InitHight( ) 1 for all u Adj( ) Send(NEW-HEIGH, h ( )) to u 3 for all u Adj( ) 4 Send(INI-HEIGH, h ( ) ) to u 5 if ty( )= Source 6 ex( ) w ( ) 7 c ( ) w( ) 1 M i a poitie real number that i large enough 8 Broadcat(ADD-SOURCE, h ( ) )to all 9 ReAS( h, ( ), ) 1 }//if Fig5 InitHight //when receie(new-heigh, h )fromw ReNH( hw),, 1 if w Adj( ) h ( w) h 3 if w Adj( ) 4 h ( w) h Fig6 ReNH //when receie(ini-heigh, h )fromw ReIH( hw),, 1 ReNH( hw),, if ( h ( ) = h ( ) > h 1) 3 h ( ), h ( ) h 1 h ( ), h ( ) h 4 InitHight( ) Fig7 ReIH //when receie(add-source, h )fromw ReAS( hw),, 1 if ty( )= Source InitOk InitOk 1 3 h ( w) h 4 if InitOk = X 5 h ( ) V 6 h ( ) V 7 PuhLiftIn(,,) 8 }//if 9 }//if Fig8 ReAS PuhLiftIn(,w, Δ ) 1 c ( w) c ( w ) Δ ex( ) ex( ) Δ while ( u t c > h( ) > h ( u )) ex( ) > 3 min ( ), ( )} Δ ex c u 4 ex( ) ex( ) Δ c c( u ) Δ 5 if u= 6 PuhLiftOut(,, Δ ) 7 ele 8 Send(PUSH-REQUES, Δ )tou 9 }//while 1 if ex( ) > 11 min ( ) ( ) uc ( ) ( ) } u > h u < h h h c u ex 1 h ( ), h ( ) h
5 1 IJCSNS International Journal of Computer Science Network Security, VOL6 No8A, Augut 6 13 if( ty( ) = Source h( ) > h ( )) 14 terminate 15 for all u Adj( ) 16 Send(NEW-HEIGH, h ( ) ) to u 17 }//for 18 PuhLiftIn(,,) 19 }//if Fig9 PuhLiftIn PuhLiftOut(,w, Δ ) 1 c ( w) c ( w ) Δ ex( ) ex( ) Δ while ( u t c > h( ) > h ( u )) ex( ) > 3 min ( ), ( )} Δ ex c u 4 ex( ) ex( ) Δ c c ( u ) Δ 5 if u= 6 PuhLiftIn(,, Δ ) 7 ele 8 Send(PUSH-REQUES, Δ )tou 9 }//while 1 if ex( ) > 11 min ( ( ) ( ) uc ( ) ( ) ) u > h u < h h h c u ex 1 h ( ), h ( ) h 13 for all u Adj( ) 14 Send(NEW-HEIGH, h ( ))to u 15 PuhLiftOut(,,) 16 }//if Fig1 PuhLiftOut //when receie(push-reques, Δ )fromw RePR(, Δ, w ) 1 if w Adj( ) h ( w ) > h( ) if ty( ) Sink 3 PuhLiftIn(,w, Δ ) 4 ele 5 c( w) c( w ) Δ 6 ex( ) ex( ) Δ 7 }//ele 8 }ele if w Adj( ) h ( w ) > h( ) 9 PuhLiftOut(,w, Δ ) 1 ele 11 Send(PUSH-DENY, Δ )to w Fig11 RePR //when receie(push-deny, Δ )fromw RePD(, Δ, w ) 1 if w Adj( ) c( w) c( w ) Δ 3 ex( ) ex( ) Δ 4 PuhLiftIn(,,) 5 }ele 6 c ( w) c ( w ) Δ 7 ex( ) ex( ) Δ 8 PuhLiftOut(,,) 9 }//ele Fig1 RePD he time complexity of DA i OV ( ) he meage complexity of DA i OV ( A) 5 Concluion In thi paper, we formulate the lifetime imization problem of enor network a a flow problem on a tranportation network with power on ertice arc With BS algorithm, we can achiee imum lifetime routing of a enor network in any preciion if only we can find the flow on uch a tranportation network After propoe a centralized algorithm with time complexity 3 of OV ( ), we propoe an aynchronouly ditributed algorithm with time complexity of OV ( ) meage complexity of DA i OV ( A) Reference [1] M Bhardwaj, A Chrakaan, Garnett, Upper Bound on the Lifetime of Senor Network, IEEE International Conference on Communication, Helinki, Finl, June 1 [] M Bhardwaj, A Chrakaan, Bounding the Lifetime of Senor Network Via Optimal Role Aignment, IEEE INFOCOM [3] E J Duarte-Melo, M Liu, A Mira, A Modeling Framework for Computing Lifetime Information Capacity in Wirele Senor Network, Modeling Optimization in Mobile, Ad Hoc Wirele Network, Cambridge, UK, March 4 [4] Viek Rai, Rabi N Mahapatra, Lifetime Modeling of a Senor Network, Deign, Automation et in Europe, Munich, Germany, March 5 [5] J H Chang, L aiula, Energy conering routing in wirele ad-hoc network, IEEE INFOCOM [6] K Dagupta, K Kalpaki, P Namjohi, Efficient Algorithm for Maximum Lifetime Data Gathering Aggregation in Wirele Senor Network, Computer Network, ol 4, 3 [7] Sankar, Z Liu, Maximum Lifetime Routing in Wirele Ad-hoc Network, INFOCOM 4 [8] R Madan, S Lall, Ditributed Algorithm for Maximum Lifetime Routing in Wirele Senor Net-work, Global elecommunication Conference, IEEE, olume, No 4 [9] Andrew V Goldberg Robert E arjan, A New Approach to the Maximum Flow Problem, Journal of ACM, 35(4):91-94, 1988 [1] L Pham, M Bui, I Laallae, S H Do, A Ditributed Preflow-Puh for the Maximum Flow Problem, Innoatie Internet Community Sytem, 5th International Workhop, IICS 5, Pari, France, June, 5
A Full-Newton Step Primal-Dual Interior Point Algorithm for Linear Complementarity Problems *
 ISSN 76-7659, England, UK Journal of Information and Computing Science Vol 5, No,, pp 35-33 A Full-Newton Step Primal-Dual Interior Point Algorithm for Linear Complementarity Problem * Lipu Zhang and Yinghong
ISSN 76-7659, England, UK Journal of Information and Computing Science Vol 5, No,, pp 35-33 A Full-Newton Step Primal-Dual Interior Point Algorithm for Linear Complementarity Problem * Lipu Zhang and Yinghong
Chapter 7. Network Flow. CS 350: Winter 2018
 Chapter 7 Network Flow CS 3: Winter 1 1 Soviet Rail Network, Reference: On the hitory of the tranportation and maximum flow problem. Alexander Schrijver in Math Programming, 1: 3,. Maximum Flow and Minimum
Chapter 7 Network Flow CS 3: Winter 1 1 Soviet Rail Network, Reference: On the hitory of the tranportation and maximum flow problem. Alexander Schrijver in Math Programming, 1: 3,. Maximum Flow and Minimum
Clustering Methods without Given Number of Clusters
 Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Zbigniew Dziong Department of Electrical Engineering, Ecole de Technologie Superieure 1100 Notre-Dame Street West, Montreal, Quebec, Canada H3C 1k3
 Capacity Allocation in Serice Oerlay Network - Maximum Profit Minimum Cot Formulation Ngok Lam Department of Electrical and Computer Engineering, McGill Unierity 3480 Unierity Street, Montreal, Quebec,
Capacity Allocation in Serice Oerlay Network - Maximum Profit Minimum Cot Formulation Ngok Lam Department of Electrical and Computer Engineering, McGill Unierity 3480 Unierity Street, Montreal, Quebec,
Problem Set 8 Solutions
 Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
3.1 The Revised Simplex Algorithm. 3 Computational considerations. Thus, we work with the following tableau. Basic observations = CARRY. ... m.
 3 Computational conideration In what follow, we analyze the complexity of the Simplex algorithm more in detail For thi purpoe, we focu on the update proce in each iteration of thi procedure Clearly, ince,
3 Computational conideration In what follow, we analyze the complexity of the Simplex algorithm more in detail For thi purpoe, we focu on the update proce in each iteration of thi procedure Clearly, ince,
SOME RESULTS ON INFINITE POWER TOWERS
 NNTDM 16 2010) 3, 18-24 SOME RESULTS ON INFINITE POWER TOWERS Mladen Vailev - Miana 5, V. Hugo Str., Sofia 1124, Bulgaria E-mail:miana@abv.bg Abtract To my friend Kratyu Gumnerov In the paper the infinite
NNTDM 16 2010) 3, 18-24 SOME RESULTS ON INFINITE POWER TOWERS Mladen Vailev - Miana 5, V. Hugo Str., Sofia 1124, Bulgaria E-mail:miana@abv.bg Abtract To my friend Kratyu Gumnerov In the paper the infinite
Algorithm Design and Analysis
 Algorithm Deign and Analyi LECTURES 1-1 Network Flow Flow, cut Ford-Fulkeron Min-cut/max-flow theorem Adam Smith // A. Smith; baed on lide by E. Demaine, C. Leieron, S. Rakhodnikova, K. Wayne Detecting
Algorithm Deign and Analyi LECTURES 1-1 Network Flow Flow, cut Ford-Fulkeron Min-cut/max-flow theorem Adam Smith // A. Smith; baed on lide by E. Demaine, C. Leieron, S. Rakhodnikova, K. Wayne Detecting
Speaker. Low- Pass Filter. D/A Converter. Power Amp. Counter. Memory. Clock
 Maachuett Intitute of Technology Department of Electrical Engineering and Computer Science 6.00 { Electronic Circuit Homework # Solution Handout F9806 Iued /0/98 { Due /4/98 Introduction Thi homework aignment
Maachuett Intitute of Technology Department of Electrical Engineering and Computer Science 6.00 { Electronic Circuit Homework # Solution Handout F9806 Iued /0/98 { Due /4/98 Introduction Thi homework aignment
Main Reference: Sections in CLRS.
 Maximum Flow Reied 09/09/200 Main Reference: Secion 26.-26. in CLRS. Inroducion Definiion Muli-Source Muli-Sink The Ford-Fulkeron Mehod Reidual Nework Augmening Pah The Max-Flow Min-Cu Theorem The Edmond-Karp
Maximum Flow Reied 09/09/200 Main Reference: Secion 26.-26. in CLRS. Inroducion Definiion Muli-Source Muli-Sink The Ford-Fulkeron Mehod Reidual Nework Augmening Pah The Max-Flow Min-Cu Theorem The Edmond-Karp
Optimal Coordination of Samples in Business Surveys
 Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Service Overlay Network Design with Reliability Constraints
 Serice Oerlay etwork Deign with Reliability Contraint gok Lam, Lorne G. Maon Department of Electrical and Computer Engineering, McGill Unierity, Montreal, Canada {ngok.lam, lorne.maon}@mcgill.ca Zbigniew
Serice Oerlay etwork Deign with Reliability Contraint gok Lam, Lorne G. Maon Department of Electrical and Computer Engineering, McGill Unierity, Montreal, Canada {ngok.lam, lorne.maon}@mcgill.ca Zbigniew
Problem Set If all directed edges in a network have distinct capacities, then there is a unique maximum flow.
 CSE 202: Deign and Analyi of Algorihm Winer 2013 Problem Se 3 Inrucor: Kamalika Chaudhuri Due on: Tue. Feb 26, 2013 Inrucion For your proof, you may ue any lower bound, algorihm or daa rucure from he ex
CSE 202: Deign and Analyi of Algorihm Winer 2013 Problem Se 3 Inrucor: Kamalika Chaudhuri Due on: Tue. Feb 26, 2013 Inrucion For your proof, you may ue any lower bound, algorihm or daa rucure from he ex
Codes Correcting Two Deletions
 1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
CHAPTER 4 DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL
 98 CHAPTER DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL INTRODUCTION The deign of ytem uing tate pace model for the deign i called a modern control deign and it i
98 CHAPTER DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL INTRODUCTION The deign of ytem uing tate pace model for the deign i called a modern control deign and it i
STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND
 OPERATIONS RESEARCH AND DECISIONS No. 4 203 DOI: 0.5277/ord30402 Marcin ANHOLCER STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND The generalized tranportation problem
OPERATIONS RESEARCH AND DECISIONS No. 4 203 DOI: 0.5277/ord30402 Marcin ANHOLCER STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND The generalized tranportation problem
Dyadic Green s Function
 EECS 730 Winter 2009 c K. Sarabandi Dyadic Green Function A mentioned earlier the application of dyadic analyi facilitate imple manipulation of field ector calculation. The ource of electromagnetic field
EECS 730 Winter 2009 c K. Sarabandi Dyadic Green Function A mentioned earlier the application of dyadic analyi facilitate imple manipulation of field ector calculation. The ource of electromagnetic field
Connectivity in large mobile ad-hoc networks
 Weiertraß-Intitut für Angewandte Analyi und Stochatik Connectivity in large mobile ad-hoc network WOLFGANG KÖNIG (WIAS und U Berlin) joint work with HANNA DÖRING (Onabrück) and GABRIEL FARAUD (Pari) Mohrentraße
Weiertraß-Intitut für Angewandte Analyi und Stochatik Connectivity in large mobile ad-hoc network WOLFGANG KÖNIG (WIAS und U Berlin) joint work with HANNA DÖRING (Onabrück) and GABRIEL FARAUD (Pari) Mohrentraße
Lecture 21. The Lovasz splitting-off lemma Topics in Combinatorial Optimization April 29th, 2004
 18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
Multi-dimensional Fuzzy Euler Approximation
 Mathematica Aeterna, Vol 7, 2017, no 2, 163-176 Multi-dimenional Fuzzy Euler Approximation Yangyang Hao College of Mathematic and Information Science Hebei Univerity, Baoding 071002, China hdhyywa@163com
Mathematica Aeterna, Vol 7, 2017, no 2, 163-176 Multi-dimenional Fuzzy Euler Approximation Yangyang Hao College of Mathematic and Information Science Hebei Univerity, Baoding 071002, China hdhyywa@163com
To describe a queuing system, an input process and an output process has to be specified.
 5. Queue (aiting Line) Queuing terminology Input Service Output To decribe a ueuing ytem, an input proce and an output proce ha to be pecified. For example ituation input proce output proce Bank Cutomer
5. Queue (aiting Line) Queuing terminology Input Service Output To decribe a ueuing ytem, an input proce and an output proce ha to be pecified. For example ituation input proce output proce Bank Cutomer
Unavoidable Cycles in Polynomial-Based Time-Invariant LDPC Convolutional Codes
 European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
Beyond Cut-Set Bounds - The Approximate Capacity of D2D Networks
 Beyond Cut-Set Bound - The Approximate Capacity of DD Network Avik Sengupta Hume Center for National Security and Technology Department of Electrical and Computer Engineering Virginia Tech, Blackburg,
Beyond Cut-Set Bound - The Approximate Capacity of DD Network Avik Sengupta Hume Center for National Security and Technology Department of Electrical and Computer Engineering Virginia Tech, Blackburg,
Today. Flow review. Augmenting paths. Ford-Fulkerson Algorithm. Intro to cuts (reason: prove correctness)
 Today Flow review Augmenting path Ford-Fulkeron Algorithm Intro to cut (reaon: prove correctne) Flow Network = ource, t = ink. c(e) = capacity of edge e Capacity condition: f(e) c(e) Conervation condition:
Today Flow review Augmenting path Ford-Fulkeron Algorithm Intro to cut (reaon: prove correctne) Flow Network = ource, t = ink. c(e) = capacity of edge e Capacity condition: f(e) c(e) Conervation condition:
Pacific Journal of Mathematics
 Pacific Journal of Mathematic OSCILLAION AND NONOSCILLAION OF FORCED SECOND ORDER DYNAMIC EQUAIONS MARIN BOHNER AND CHRISOPHER C. ISDELL Volume 230 No. March 2007 PACIFIC JOURNAL OF MAHEMAICS Vol. 230,
Pacific Journal of Mathematic OSCILLAION AND NONOSCILLAION OF FORCED SECOND ORDER DYNAMIC EQUAIONS MARIN BOHNER AND CHRISOPHER C. ISDELL Volume 230 No. March 2007 PACIFIC JOURNAL OF MAHEMAICS Vol. 230,
Theoretical Computer Science. Optimal algorithms for online scheduling with bounded rearrangement at the end
 Theoretical Computer Science 4 (0) 669 678 Content lit available at SciVere ScienceDirect Theoretical Computer Science journal homepage: www.elevier.com/locate/tc Optimal algorithm for online cheduling
Theoretical Computer Science 4 (0) 669 678 Content lit available at SciVere ScienceDirect Theoretical Computer Science journal homepage: www.elevier.com/locate/tc Optimal algorithm for online cheduling
Chapter 7. Network Flow. Slides by Kevin Wayne. Copyright 2005 Pearson-Addison Wesley. All rights reserved.
 Chapter 7 Network Flow Slide by Kevin Wayne. Copyright 5 Pearon-Addion Weley. All right reerved. Soviet Rail Network, 55 Reference: On the hitory of the tranportation and maximum flow problem. Alexander
Chapter 7 Network Flow Slide by Kevin Wayne. Copyright 5 Pearon-Addion Weley. All right reerved. Soviet Rail Network, 55 Reference: On the hitory of the tranportation and maximum flow problem. Alexander
Optimization model in Input output analysis and computable general. equilibrium by using multiple criteria non-linear programming.
 Optimization model in Input output analyi and computable general equilibrium by uing multiple criteria non-linear programming Jing He * Intitute of ytem cience, cademy of Mathematic and ytem cience Chinee
Optimization model in Input output analyi and computable general equilibrium by uing multiple criteria non-linear programming Jing He * Intitute of ytem cience, cademy of Mathematic and ytem cience Chinee
4. Connectivity Connectivity Connectivity. Whitney's s connectivity theorem: (G) (G) (G) for special
 4. Connectivity 4.. Connectivity Vertex-cut and vertex-connectivity Edge-cut and edge-connectivty Whitney' connectivity theorem: Further theorem for the relation of and graph 4.. The Menger Theorem and
4. Connectivity 4.. Connectivity Vertex-cut and vertex-connectivity Edge-cut and edge-connectivty Whitney' connectivity theorem: Further theorem for the relation of and graph 4.. The Menger Theorem and
Jul 4, 2005 turbo_code_primer Revision 0.0. Turbo Code Primer
 Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Lecture 13. Thermodynamic Potentials (Ch. 5)
 Lecture 13. hermodynamic Potential (Ch. 5) So far we have been uing the total internal energy U and ometime the enthalpy H to characterize variou macrocopic ytem. hee function are called the thermodynamic
Lecture 13. hermodynamic Potential (Ch. 5) So far we have been uing the total internal energy U and ometime the enthalpy H to characterize variou macrocopic ytem. hee function are called the thermodynamic
FUNDAMENTALS OF POWER SYSTEMS
 1 FUNDAMENTALS OF POWER SYSTEMS 1 Chapter FUNDAMENTALS OF POWER SYSTEMS INTRODUCTION The three baic element of electrical engineering are reitor, inductor and capacitor. The reitor conume ohmic or diipative
1 FUNDAMENTALS OF POWER SYSTEMS 1 Chapter FUNDAMENTALS OF POWER SYSTEMS INTRODUCTION The three baic element of electrical engineering are reitor, inductor and capacitor. The reitor conume ohmic or diipative
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD
 SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
Lecture 10 Filtering: Applied Concepts
 Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
List Coloring Graphs
 Lit Coloring Graph February 6, 004 LIST COLORINGS AND CHOICE NUMBER Thomaen Long Grotzch girth 5 verion Thomaen Long Let G be a connected planar graph of girth at leat 5. Let A be a et of vertice in G
Lit Coloring Graph February 6, 004 LIST COLORINGS AND CHOICE NUMBER Thomaen Long Grotzch girth 5 verion Thomaen Long Let G be a connected planar graph of girth at leat 5. Let A be a et of vertice in G
Assessment of Performance for Single Loop Control Systems
 Aement of Performance for Single Loop Control Sytem Hiao-Ping Huang and Jyh-Cheng Jeng Department of Chemical Engineering National Taiwan Univerity Taipei 1617, Taiwan Abtract Aement of performance in
Aement of Performance for Single Loop Control Sytem Hiao-Ping Huang and Jyh-Cheng Jeng Department of Chemical Engineering National Taiwan Univerity Taipei 1617, Taiwan Abtract Aement of performance in
The Impact of Imperfect Scheduling on Cross-Layer Rate. Control in Multihop Wireless Networks
 The mpact of mperfect Scheduling on Cro-Layer Rate Control in Multihop Wirele Network Xiaojun Lin and Ne B. Shroff Center for Wirele Sytem and Application (CWSA) School of Electrical and Computer Engineering,
The mpact of mperfect Scheduling on Cro-Layer Rate Control in Multihop Wirele Network Xiaojun Lin and Ne B. Shroff Center for Wirele Sytem and Application (CWSA) School of Electrical and Computer Engineering,
Linearteam tech paper. The analysis of fourth-order state variable filter and it s application to Linkwitz- Riley filters
 Linearteam tech paper The analyi of fourth-order tate variable filter and it application to Linkwitz- iley filter Janne honen 5.. TBLE OF CONTENTS. NTOCTON.... FOTH-OE LNWTZ-LEY (L TNSFE FNCTON.... TNSFE
Linearteam tech paper The analyi of fourth-order tate variable filter and it application to Linkwitz- iley filter Janne honen 5.. TBLE OF CONTENTS. NTOCTON.... FOTH-OE LNWTZ-LEY (L TNSFE FNCTON.... TNSFE
Lecture 9: Shor s Algorithm
 Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Simulation Study on the Shock Properties of the Double-Degree-of-Freedom Cushioning Packaging System
 Proceeding of the 7th IAPRI World Conference on Packaging Simulation Study on the Shock Propertie of the Double-Degree-of-Freedom Cuhioning Packaging Sytem Xia Zhu, Qiaoqiao Yan, Xiaoling Yao, Junbin Chen,
Proceeding of the 7th IAPRI World Conference on Packaging Simulation Study on the Shock Propertie of the Double-Degree-of-Freedom Cuhioning Packaging Sytem Xia Zhu, Qiaoqiao Yan, Xiaoling Yao, Junbin Chen,
Balanced Network Flows
 revied, June, 1992 Thi paper appeared in Bulletin of the Intitute of Combinatoric and it Application 7 (1993), 17-32. Balanced Network Flow William Kocay* and Dougla tone Department of Computer cience
revied, June, 1992 Thi paper appeared in Bulletin of the Intitute of Combinatoric and it Application 7 (1993), 17-32. Balanced Network Flow William Kocay* and Dougla tone Department of Computer cience
Bogoliubov Transformation in Classical Mechanics
 Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Digital Control System
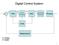 Digital Control Sytem - A D D A Micro ADC DAC Proceor Correction Element Proce Clock Meaurement A: Analog D: Digital Continuou Controller and Digital Control Rt - c Plant yt Continuou Controller Digital
Digital Control Sytem - A D D A Micro ADC DAC Proceor Correction Element Proce Clock Meaurement A: Analog D: Digital Continuou Controller and Digital Control Rt - c Plant yt Continuou Controller Digital
Chapter 2 Homework Solution P2.2-1, 2, 5 P2.4-1, 3, 5, 6, 7 P2.5-1, 3, 5 P2.6-2, 5 P2.7-1, 4 P2.8-1 P2.9-1
 Chapter Homework Solution P.-1,, 5 P.4-1, 3, 5, 6, 7 P.5-1, 3, 5 P.6-, 5 P.7-1, 4 P.8-1 P.9-1 P.-1 An element ha oltage and current i a hown in Figure P.-1a. Value of the current i and correponding oltage
Chapter Homework Solution P.-1,, 5 P.4-1, 3, 5, 6, 7 P.5-1, 3, 5 P.6-, 5 P.7-1, 4 P.8-1 P.9-1 P.-1 An element ha oltage and current i a hown in Figure P.-1a. Value of the current i and correponding oltage
Myriad of applications
 Shortet Path Myriad of application Finding hortet ditance between location (Google map, etc.) Internet router protocol: OSPF (Open Shortet Path Firt) i ued to find the hortet path to interchange package
Shortet Path Myriad of application Finding hortet ditance between location (Google map, etc.) Internet router protocol: OSPF (Open Shortet Path Firt) i ued to find the hortet path to interchange package
Highway Capacity Manual 2010
 RR = minimum number of lane change that mut be made by one ramp-toramp ehicle to execute the deired maneuer uccefully. MIN for two-ided weaing egment i gien by Equation 12-3: MIN RR For two-ided weaing
RR = minimum number of lane change that mut be made by one ramp-toramp ehicle to execute the deired maneuer uccefully. MIN for two-ided weaing egment i gien by Equation 12-3: MIN RR For two-ided weaing
Entropy Minimization in Design of Extractive Distillation System with Internal Heat Exchangers
 Entropy Minimization in Deign of Extractive Ditillation Sytem with Internal Heat Exchanger Diego F. Mendoza, Carlo.M. Riaco * Group of Proce Sytem Engineering, Department of Chemical and Environmental
Entropy Minimization in Deign of Extractive Ditillation Sytem with Internal Heat Exchanger Diego F. Mendoza, Carlo.M. Riaco * Group of Proce Sytem Engineering, Department of Chemical and Environmental
PI control system design for Electromagnetic Molding Machine based on Linear Programing
 PI control ytem deign for Electromagnetic Molding Machine baed on Linear Programing Takayuki Ihizaki, Kenji Kahima, Jun-ichi Imura*, Atuhi Katoh and Hirohi Morita** Abtract In thi paper, we deign a PI
PI control ytem deign for Electromagnetic Molding Machine baed on Linear Programing Takayuki Ihizaki, Kenji Kahima, Jun-ichi Imura*, Atuhi Katoh and Hirohi Morita** Abtract In thi paper, we deign a PI
Chapter 13. Root Locus Introduction
 Chapter 13 Root Locu 13.1 Introduction In the previou chapter we had a glimpe of controller deign iue through ome imple example. Obviouly when we have higher order ytem, uch imple deign technique will
Chapter 13 Root Locu 13.1 Introduction In the previou chapter we had a glimpe of controller deign iue through ome imple example. Obviouly when we have higher order ytem, uch imple deign technique will
Bahram Noshad Department of Electrical Engineering, Bandar Deylam Branch, Islamic Azad University, Bandar Deylam, Iran.
 Journal of Advance in Computer Reearch Quarterly pissn: 345-66x eissn: 345-678 Sari Branch, Ilamic Azad Univerity, Sari, I.R.Iran (Vol. 9, No. 3, Augut 8), Page: - www.jacr.iauari.ac.ir A New Model for
Journal of Advance in Computer Reearch Quarterly pissn: 345-66x eissn: 345-678 Sari Branch, Ilamic Azad Univerity, Sari, I.R.Iran (Vol. 9, No. 3, Augut 8), Page: - www.jacr.iauari.ac.ir A New Model for
If Y is normally Distributed, then and 2 Y Y 10. σ σ
 ull Hypothei Significance Teting V. APS 50 Lecture ote. B. Dudek. ot for General Ditribution. Cla Member Uage Only. Chi-Square and F-Ditribution, and Diperion Tet Recall from Chapter 4 material on: ( )
ull Hypothei Significance Teting V. APS 50 Lecture ote. B. Dudek. ot for General Ditribution. Cla Member Uage Only. Chi-Square and F-Ditribution, and Diperion Tet Recall from Chapter 4 material on: ( )
APPLICATION OF THE SINGLE IMPACT MICROINDENTATION FOR NON- DESTRUCTIVE TESTING OF THE FRACTURE TOUGHNESS OF NONMETALLIC AND POLYMERIC MATERIALS
 APPLICATION OF THE SINGLE IMPACT MICROINDENTATION FOR NON- DESTRUCTIVE TESTING OF THE FRACTURE TOUGHNESS OF NONMETALLIC AND POLYMERIC MATERIALS REN A. P. INSTITUTE OF APPLIED PHYSICS OF THE NATIONAL ACADEMY
APPLICATION OF THE SINGLE IMPACT MICROINDENTATION FOR NON- DESTRUCTIVE TESTING OF THE FRACTURE TOUGHNESS OF NONMETALLIC AND POLYMERIC MATERIALS REN A. P. INSTITUTE OF APPLIED PHYSICS OF THE NATIONAL ACADEMY
Design By Emulation (Indirect Method)
 Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
Molecular Dynamics Simulations of Nonequilibrium Effects Associated with Thermally Activated Exothermic Reactions
 Original Paper orma, 5, 9 7, Molecular Dynamic Simulation of Nonequilibrium Effect ociated with Thermally ctivated Exothermic Reaction Jerzy GORECKI and Joanna Natalia GORECK Intitute of Phyical Chemitry,
Original Paper orma, 5, 9 7, Molecular Dynamic Simulation of Nonequilibrium Effect ociated with Thermally ctivated Exothermic Reaction Jerzy GORECKI and Joanna Natalia GORECK Intitute of Phyical Chemitry,
Optimizing Cost-sensitive Trust-negotiation Protocols
 Optimizing Cot-enitive Trut-negotiation Protocol Weifeng Chen, Lori Clarke, Jim Kuroe, Don Towley Department of Computer Science Univerity of Maachuett, Amhert {chenwf, clarke, kuroe, towley}@c.uma.edu
Optimizing Cot-enitive Trut-negotiation Protocol Weifeng Chen, Lori Clarke, Jim Kuroe, Don Towley Department of Computer Science Univerity of Maachuett, Amhert {chenwf, clarke, kuroe, towley}@c.uma.edu
TP A.30 The effect of cue tip offset, cue weight, and cue speed on cue ball speed and spin
 technical proof TP A.30 The effect of cue tip offet, cue weight, and cue peed on cue all peed and pin technical proof upporting: The Illutrated Principle of Pool and Billiard http://illiard.colotate.edu
technical proof TP A.30 The effect of cue tip offet, cue weight, and cue peed on cue all peed and pin technical proof upporting: The Illutrated Principle of Pool and Billiard http://illiard.colotate.edu
Network Flow. Data Structures and Algorithms Andrei Bulatov
 Nework Flow Daa Srucure and Algorihm Andrei Bulao Algorihm Nework Flow 24-2 Flow Nework Think of a graph a yem of pipe We ue hi yem o pump waer from he ource o ink Eery pipe/edge ha limied capaciy Flow
Nework Flow Daa Srucure and Algorihm Andrei Bulao Algorihm Nework Flow 24-2 Flow Nework Think of a graph a yem of pipe We ue hi yem o pump waer from he ource o ink Eery pipe/edge ha limied capaciy Flow
THE Z-TRANSFORM APPLIED TO BIRTH-DEATH MARKOV PROCESSES
 he Zranform applied to birthdeath arov procee HE ZRASOR ALIED O BIRHDEAH ARKO ROCESSES H Department of Electronic and Communication niverity of DareSalaam O Box 3594 DareSalaam anania ABSRAC Birthdeath
he Zranform applied to birthdeath arov procee HE ZRASOR ALIED O BIRHDEAH ARKO ROCESSES H Department of Electronic and Communication niverity of DareSalaam O Box 3594 DareSalaam anania ABSRAC Birthdeath
1. Intensity of Periodic Sound Waves 2. The Doppler Effect
 1. Intenity o Periodic Sound Wae. The Doppler Eect 1-4-018 1 Objectie: The tudent will be able to Deine the intenity o the ound wae. Deine the Doppler Eect. Undertand ome application on ound 1-4-018 3.3
1. Intenity o Periodic Sound Wae. The Doppler Eect 1-4-018 1 Objectie: The tudent will be able to Deine the intenity o the ound wae. Deine the Doppler Eect. Undertand ome application on ound 1-4-018 3.3
Root Locus Diagram. Root loci: The portion of root locus when k assume positive values: that is 0
 Objective Root Locu Diagram Upon completion of thi chapter you will be able to: Plot the Root Locu for a given Tranfer Function by varying gain of the ytem, Analye the tability of the ytem from the root
Objective Root Locu Diagram Upon completion of thi chapter you will be able to: Plot the Root Locu for a given Tranfer Function by varying gain of the ytem, Analye the tability of the ytem from the root
Preemptive scheduling on a small number of hierarchical machines
 Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Algorithms and Data Structures 2011/12 Week 9 Solutions (Tues 15th - Fri 18th Nov)
 Algorihm and Daa Srucure 2011/ Week Soluion (Tue 15h - Fri 18h No) 1. Queion: e are gien 11/16 / 15/20 8/13 0/ 1/ / 11/1 / / To queion: (a) Find a pair of ube X, Y V uch ha f(x, Y) = f(v X, Y). (b) Find
Algorihm and Daa Srucure 2011/ Week Soluion (Tue 15h - Fri 18h No) 1. Queion: e are gien 11/16 / 15/20 8/13 0/ 1/ / 11/1 / / To queion: (a) Find a pair of ube X, Y V uch ha f(x, Y) = f(v X, Y). (b) Find
Lecture 8. PID control. Industrial process control ( today) PID control. Insights about PID actions
 Lecture 8. PID control. The role of P, I, and D action 2. PID tuning Indutrial proce control (92... today) Feedback control i ued to improve the proce performance: tatic performance: for contant reference,
Lecture 8. PID control. The role of P, I, and D action 2. PID tuning Indutrial proce control (92... today) Feedback control i ued to improve the proce performance: tatic performance: for contant reference,
Social Studies 201 Notes for March 18, 2005
 1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
Minimum Cost Noncrossing Flow Problem on Layered Networks
 Minimum Cot Noncroing Flow Problem on Layered Network İ. Kuban Altınel*, Necati Ara, Zeynep Şuvak, Z. Caner Taşkın Department of Indutrial Engineering, Boğaziçi Univerity, 44, Bebek, İtanbul, Turkey Abtract
Minimum Cot Noncroing Flow Problem on Layered Network İ. Kuban Altınel*, Necati Ara, Zeynep Şuvak, Z. Caner Taşkın Department of Indutrial Engineering, Boğaziçi Univerity, 44, Bebek, İtanbul, Turkey Abtract
A Study on Simulating Convolutional Codes and Turbo Codes
 A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
A Study on Simulating Convolutional Code and Turbo Code Final Report By Daniel Chang July 27, 2001 Advior: Dr. P. Kinman Executive Summary Thi project include the deign of imulation of everal convolutional
5.5 Application of Frequency Response: Signal Filters
 44 Dynamic Sytem Second order lowpa filter having tranfer function H()=H ()H () u H () H () y Firt order lowpa filter Figure 5.5: Contruction of a econd order low-pa filter by combining two firt order
44 Dynamic Sytem Second order lowpa filter having tranfer function H()=H ()H () u H () H () y Firt order lowpa filter Figure 5.5: Contruction of a econd order low-pa filter by combining two firt order
SOME PROPERTIES OF CAYLEY GRAPHS OF CANCELLATIVE SEMIGROUPS
 THE PUBLISHING HOUSE PROEEDINGS OF THE ROMANIAN AADEMY, Serie A, OF THE ROMANIAN AADEMY Volume 7, Number /06, pp 0 MATHEMATIS SOME PROPERTIES OF AYLEY GRAPHS OF ANELLATIVE SEMIGROUPS Bahman KHOSRAVI Qom
THE PUBLISHING HOUSE PROEEDINGS OF THE ROMANIAN AADEMY, Serie A, OF THE ROMANIAN AADEMY Volume 7, Number /06, pp 0 MATHEMATIS SOME PROPERTIES OF AYLEY GRAPHS OF ANELLATIVE SEMIGROUPS Bahman KHOSRAVI Qom
Utility Proportional Fair Bandwidth Allocation: An Optimization Oriented Approach
 Utility Proportional Fair Bandwidth Allocation: An Optimization Oriented Approach 61 Tobia Hark Konrad-Zue-Zentrum für Informationtechnik Berlin (ZIB), Department Optimization, Takutr. 7, 14195 Berlin,
Utility Proportional Fair Bandwidth Allocation: An Optimization Oriented Approach 61 Tobia Hark Konrad-Zue-Zentrum für Informationtechnik Berlin (ZIB), Department Optimization, Takutr. 7, 14195 Berlin,
SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lectures 41-48)
 Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
An estimation approach for autotuning of event-based PI control systems
 Acta de la XXXIX Jornada de Automática, Badajoz, 5-7 de Septiembre de 08 An etimation approach for autotuning of event-baed PI control ytem Joé Sánchez Moreno, María Guinaldo Loada, Sebatián Dormido Departamento
Acta de la XXXIX Jornada de Automática, Badajoz, 5-7 de Septiembre de 08 An etimation approach for autotuning of event-baed PI control ytem Joé Sánchez Moreno, María Guinaldo Loada, Sebatián Dormido Departamento
On the Isomorphism of Fractional Factorial Designs 1
 journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
Topic 6. Digital Signatures and Identity Based Encryption
 Topic 6. Digital Signature and Identity Baed Encryption. Security of Public-key Cryptography 2. Example of Public-key Algorithm: Diffie- Hellman Key Exchange Scheme 3. RSA Encryption and Digital Signature
Topic 6. Digital Signature and Identity Baed Encryption. Security of Public-key Cryptography 2. Example of Public-key Algorithm: Diffie- Hellman Key Exchange Scheme 3. RSA Encryption and Digital Signature
IEOR 3106: Fall 2013, Professor Whitt Topics for Discussion: Tuesday, November 19 Alternating Renewal Processes and The Renewal Equation
 IEOR 316: Fall 213, Profeor Whitt Topic for Dicuion: Tueday, November 19 Alternating Renewal Procee and The Renewal Equation 1 Alternating Renewal Procee An alternating renewal proce alternate between
IEOR 316: Fall 213, Profeor Whitt Topic for Dicuion: Tueday, November 19 Alternating Renewal Procee and The Renewal Equation 1 Alternating Renewal Procee An alternating renewal proce alternate between
C up (E) C low (E) E 2 E 1 E 0
 Spreading in lock-fading hannel. Muriel Médard David N.. Te medardmit.edu Maachuett Intitute of Technoy dteeec.berkeley.edu Univerity of alifornia at erkeley btract We conider wideband fading channel which
Spreading in lock-fading hannel. Muriel Médard David N.. Te medardmit.edu Maachuett Intitute of Technoy dteeec.berkeley.edu Univerity of alifornia at erkeley btract We conider wideband fading channel which
Math 273 Solutions to Review Problems for Exam 1
 Math 7 Solution to Review Problem for Exam True or Fale? Circle ONE anwer for each Hint: For effective tudy, explain why if true and give a counterexample if fale (a) T or F : If a b and b c, then a c
Math 7 Solution to Review Problem for Exam True or Fale? Circle ONE anwer for each Hint: For effective tudy, explain why if true and give a counterexample if fale (a) T or F : If a b and b c, then a c
Chapter 4: Applications of Fourier Representations. Chih-Wei Liu
 Chapter 4: Application of Fourier Repreentation Chih-Wei Liu Outline Introduction Fourier ranform of Periodic Signal Convolution/Multiplication with Non-Periodic Signal Fourier ranform of Dicrete-ime Signal
Chapter 4: Application of Fourier Repreentation Chih-Wei Liu Outline Introduction Fourier ranform of Periodic Signal Convolution/Multiplication with Non-Periodic Signal Fourier ranform of Dicrete-ime Signal
Finite Element Analysis of a Fiber Bragg Grating Accelerometer for Performance Optimization
 Finite Element Analyi of a Fiber Bragg Grating Accelerometer for Performance Optimization N. Baumallick*, P. Biwa, K. Dagupta and S. Bandyopadhyay Fiber Optic Laboratory, Central Gla and Ceramic Reearch
Finite Element Analyi of a Fiber Bragg Grating Accelerometer for Performance Optimization N. Baumallick*, P. Biwa, K. Dagupta and S. Bandyopadhyay Fiber Optic Laboratory, Central Gla and Ceramic Reearch
Chapter Landscape of an Optimization Problem. Local Search. Coping With NP-Hardness. Gradient Descent: Vertex Cover
 Coping With NP-Hardne Chapter 12 Local Search Q Suppoe I need to olve an NP-hard problem What hould I do? A Theory ay you're unlikely to find poly-time algorithm Mut acrifice one of three deired feature
Coping With NP-Hardne Chapter 12 Local Search Q Suppoe I need to olve an NP-hard problem What hould I do? A Theory ay you're unlikely to find poly-time algorithm Mut acrifice one of three deired feature
Lecture 17: Frequency Response of Amplifiers
 ecture 7: Frequency epone of Aplifier Gu-Yeon Wei Diiion of Engineering and Applied Science Harard Unierity guyeon@eec.harard.edu Wei Oeriew eading S&S: Chapter 7 Ski ection ince otly decribed uing BJT
ecture 7: Frequency epone of Aplifier Gu-Yeon Wei Diiion of Engineering and Applied Science Harard Unierity guyeon@eec.harard.edu Wei Oeriew eading S&S: Chapter 7 Ski ection ince otly decribed uing BJT
IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 65, NO. 10, OCTOBER Wenguang Mao, Xudong Wang, Senior Member, IEEE, and Shanshan Wu
 IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 65, NO. 10, OCTOBER 2016 8511 Ditributed Opportunitic Scheduling With QoS Contraint for Wirele Network With Hybrid Link Wenguang Mao, Xudong Wang, Senior
IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 65, NO. 10, OCTOBER 2016 8511 Ditributed Opportunitic Scheduling With QoS Contraint for Wirele Network With Hybrid Link Wenguang Mao, Xudong Wang, Senior
Question 1 Equivalent Circuits
 MAE 40 inear ircuit Fall 2007 Final Intruction ) Thi exam i open book You may ue whatever written material you chooe, including your cla note and textbook You may ue a hand calculator with no communication
MAE 40 inear ircuit Fall 2007 Final Intruction ) Thi exam i open book You may ue whatever written material you chooe, including your cla note and textbook You may ue a hand calculator with no communication
AC Analysis of Idealized Switched-Capacitor Circuits in Spice-Compatible Programs
 A Analyi of Idealized Switched-apacitor ircuit in Spice-ompatible Program DALIBOR BIOLEK, VIERA BIOLKOVA, ZDENEK KOLKA Dept. of Microelectronic and Radioelectronic, Brno Unierity of echnology Dept. of
A Analyi of Idealized Switched-apacitor ircuit in Spice-ompatible Program DALIBOR BIOLEK, VIERA BIOLKOVA, ZDENEK KOLKA Dept. of Microelectronic and Radioelectronic, Brno Unierity of echnology Dept. of
0 of the same magnitude. If we don t use an OA and ignore any damping, the CTF is
 1 4. Image Simulation Influence of C Spherical aberration break the ymmetry that would otherwie exit between overfocu and underfocu. One reult i that the fringe in the FT of the CTF are generally farther
1 4. Image Simulation Influence of C Spherical aberration break the ymmetry that would otherwie exit between overfocu and underfocu. One reult i that the fringe in the FT of the CTF are generally farther
CS4445/9544 Analysis of Algorithms II Solution for Assignment 1
 Conider he following flow nework CS444/944 Analyi of Algorihm II Soluion for Aignmen (0 mark) In he following nework a minimum cu ha capaciy 0 Eiher prove ha hi aemen i rue, or how ha i i fale Uing he
Conider he following flow nework CS444/944 Analyi of Algorihm II Soluion for Aignmen (0 mark) In he following nework a minimum cu ha capaciy 0 Eiher prove ha hi aemen i rue, or how ha i i fale Uing he
USPAS Course on Recirculated and Energy Recovered Linear Accelerators
 USPAS Coure on Recirculated and Energy Recovered Linear Accelerator G. A. Krafft and L. Merminga Jefferon Lab I. Bazarov Cornell Lecture 6 7 March 005 Lecture Outline. Invariant Ellipe Generated by a Unimodular
USPAS Coure on Recirculated and Energy Recovered Linear Accelerator G. A. Krafft and L. Merminga Jefferon Lab I. Bazarov Cornell Lecture 6 7 March 005 Lecture Outline. Invariant Ellipe Generated by a Unimodular
Chapter 4. The Laplace Transform Method
 Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
Kalman Filter. Wim van Drongelen, Introduction
 alman Filter Wim an Drongelen alman Filter Wim an Drongelen, 03. Introduction Getting to undertand a ytem can be quite a challenge. One approach i to create a model, an abtraction of the ytem. The idea
alman Filter Wim an Drongelen alman Filter Wim an Drongelen, 03. Introduction Getting to undertand a ytem can be quite a challenge. One approach i to create a model, an abtraction of the ytem. The idea
Convex Hulls of Curves Sam Burton
 Convex Hull of Curve Sam Burton 1 Introduction Thi paper will primarily be concerned with determining the face of convex hull of curve of the form C = {(t, t a, t b ) t [ 1, 1]}, a < b N in R 3. We hall
Convex Hull of Curve Sam Burton 1 Introduction Thi paper will primarily be concerned with determining the face of convex hull of curve of the form C = {(t, t a, t b ) t [ 1, 1]}, a < b N in R 3. We hall
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS
 CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
Chip-firing game and a partial Tutte polynomial for Eulerian digraphs
 Chip-firing game and a partial Tutte polynomial for Eulerian digraph Kévin Perrot Aix Mareille Univerité, CNRS, LIF UMR 7279 3288 Mareille cedex 9, France. kevin.perrot@lif.univ-mr.fr Trung Van Pham Intitut
Chip-firing game and a partial Tutte polynomial for Eulerian digraph Kévin Perrot Aix Mareille Univerité, CNRS, LIF UMR 7279 3288 Mareille cedex 9, France. kevin.perrot@lif.univ-mr.fr Trung Van Pham Intitut
SIMPLIFIED MODEL FOR EPICYCLIC GEAR INERTIAL CHARACTERISTICS
 UNIVERSITY OF PITESTI SCIENTIFIC BULLETIN FACULTY OF ECHANICS AND TECHNOLOGY AUTOOTIVE erie, year XVII, no. ( 3 ) SIPLIFIED ODEL FOR EPICYCLIC GEAR INERTIAL CHARACTERISTICS Ciobotaru, Ticuşor *, Feraru,
UNIVERSITY OF PITESTI SCIENTIFIC BULLETIN FACULTY OF ECHANICS AND TECHNOLOGY AUTOOTIVE erie, year XVII, no. ( 3 ) SIPLIFIED ODEL FOR EPICYCLIC GEAR INERTIAL CHARACTERISTICS Ciobotaru, Ticuşor *, Feraru,
Multicast Network Coding and Field Sizes
 Multicat Network Coding and Field Size Qifu (Tyler) Sun, Xunrui Yin, Zongpeng Li, and Keping Long Intitute of Advanced Networking Technology and New Service, Univerity of Science and Technology Beijing,
Multicat Network Coding and Field Size Qifu (Tyler) Sun, Xunrui Yin, Zongpeng Li, and Keping Long Intitute of Advanced Networking Technology and New Service, Univerity of Science and Technology Beijing,
Dynamic Behaviour of Timber Footbridges
 Contança RIGUEIRO MSc PhD Student EST-IPCB contança@et.ipcb.pt Dynamic Behaviour of Timber Footbridge Graduated in Civil Engineering in Univ. of Coimbra (1992). MSc, Univ. of Coimbra (1997). João NEGRÃO
Contança RIGUEIRO MSc PhD Student EST-IPCB contança@et.ipcb.pt Dynamic Behaviour of Timber Footbridge Graduated in Civil Engineering in Univ. of Coimbra (1992). MSc, Univ. of Coimbra (1997). João NEGRÃO
The Hassenpflug Matrix Tensor Notation
 The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
A Provably Secure Scheme for Remote User Authentication
 A Provably Secure Scheme for Remote Uer Authentication Fuw-Yi Yang 1, Su-Hui Chiu 2 1 Department of Computer Science and Information Engineering, Chaoyang Univerity of Technology Taichung County 41349,
A Provably Secure Scheme for Remote Uer Authentication Fuw-Yi Yang 1, Su-Hui Chiu 2 1 Department of Computer Science and Information Engineering, Chaoyang Univerity of Technology Taichung County 41349,
Estimation of Temperature Rise in Stator Winding and Rotor Magnet of PMSM Based on EKF
 2010 3rd International Conference on Computer and Electrical Engineering (ICCEE 2010) IPCSIT vol. 53 (2012) (2012) IACSIT Pre, Singapore DOI: 10.7763/IPCSIT.2012.V53.No.2.37 Etimation of Temperature Rie
2010 3rd International Conference on Computer and Electrical Engineering (ICCEE 2010) IPCSIT vol. 53 (2012) (2012) IACSIT Pre, Singapore DOI: 10.7763/IPCSIT.2012.V53.No.2.37 Etimation of Temperature Rie
A Simplified Methodology for the Synthesis of Adaptive Flight Control Systems
 A Simplified Methodology for the Synthei of Adaptive Flight Control Sytem J.ROUSHANIAN, F.NADJAFI Department of Mechanical Engineering KNT Univerity of Technology 3Mirdamad St. Tehran IRAN Abtract- A implified
A Simplified Methodology for the Synthei of Adaptive Flight Control Sytem J.ROUSHANIAN, F.NADJAFI Department of Mechanical Engineering KNT Univerity of Technology 3Mirdamad St. Tehran IRAN Abtract- A implified
UNIVERSITY OF TRENTO. G. Franceschini, M. Donelli, D. Franceschini, M. Benedetti, P. Rocca, and A. Massa. January Technical Report # DISI
 UNIRSITY OF TRNTO DIPARTINTO DI INGGNRIA SCINZA DLL INFORAZION 3813 Poo Trento (Italy), ia Sommarie 14 http://www.dii.unitn.it RCONSTRUCTION OF DILCTRIC OBJCTS FRO APLITUD-ONLY DATA ADANTAGS AND OPN PROBLS
UNIRSITY OF TRNTO DIPARTINTO DI INGGNRIA SCINZA DLL INFORAZION 3813 Poo Trento (Italy), ia Sommarie 14 http://www.dii.unitn.it RCONSTRUCTION OF DILCTRIC OBJCTS FRO APLITUD-ONLY DATA ADANTAGS AND OPN PROBLS
Graphs III - Network Flow
 Graph III - Nework Flow Flow nework eup graph G=(V,E) edge capaciy w(u,v) 0 - if edge doe no exi, hen w(u,v)=0 pecial verice: ource verex ; ink verex - no edge ino and no edge ou of Aume every verex v
Graph III - Nework Flow Flow nework eup graph G=(V,E) edge capaciy w(u,v) 0 - if edge doe no exi, hen w(u,v)=0 pecial verice: ource verex ; ink verex - no edge ino and no edge ou of Aume every verex v
