INDIAN INSTITUTE OF TECHNOLOGY KHARAGPUR Design and Analysis of Algorithms Department of Mathematics MA21007/Assignment-2/Due: 18 Aug.
|
|
|
- Theodore York
- 6 years ago
- Views:
Transcription
1 INDIAN INSTITUTE OF TECHNOLOGY KHARAGPUR Design and Analysis of Algorithms Department of Mathematics MA21007/Assignment-2/Due: 18 Aug Problem 1. Computing Fibonacci Numbers The Fibonacci numbers are defined as F 0 = 0, F 1 = 1, F n = F n 1 + F n 2 for n 2. You can show that the nth Fibonacci number is φ n 5 φ n n, F = where φ is the golden ratio and φ is its conjugate. A fellow DAA student comes to you with the following simple recursive algorithm for computing the nth Fibonacci number. FIB(n) 1 if n = 0 2 then return 0 3 elseif n = 1 4 then return 1 5 return FIB(n 1) + FIB(n 2) This algorithm is correct, since it directly implements the definition of the Fibonacci numbers. Let s analyze its running time. Let T (n) be the worst-case running time of FIB(n). 1 (a) Give a recurrence for T (n), and use the substitution method to show that T (n) = O(F n ). (b) Similarly, show that T (n) = Ω(F n ), and hence, that T (n) = Θ(F n ). Professor Grigori Potemkin has recently published an improved algorithm for computing the nth Fibonacci number which uses a cleverly constructed loop to get rid of one of the recursive calls. Professor Potemkin has staked his reputation on this new algorithm, and his tenure committee has asked you to review his algorithm. 1 In this problem, please assume that all operations take unit time. In reality, the time it takes to add two numbers depends on the number of bits in the numbers being added (more precisely, on the number of memory words). However, for the purpose of this problem, the approximation of unit time addition will suffice.
2 FIB (n) 1 if n = 0 2 then return 0 3 elseif n = 1 4 then return 1 5 sum 1 6 for k 1 to n 2 7 do sum sum + FIB (k) 8 return sum 2 Since it is not at all clear that this algorithm actually computes the nth Fibonacci number, let s prove that the algorithm is correct. We ll prove this by induction over n, using a loop invariant in the inductive step of the proof. (c) State the induction hypothesis and the base case of your correctness proof. (d) State a loop invariant for the loop in lines 6-7. Prove, using induction over k, that your invariant is indeed invariant. (e) Use your loop invariant to complete the inductive step of your correctness proof. (f) What is the asymptotic running time, T (n), of FIB (n)? Would you recommend tenure for Professor Potemkin? Problem 2. Polynomial multiplication One can represent a polynomial, in a symbolic variable x, with degree-bound n as an array P [0.. n] of coefficients. Consider two linear polynomials, A(x) = a 1 x + a 0 and B(x) = b 1 x + b 0, where a 1, a 0, b 1, and b 0 are numerical coefficients, which can be represented by the arrays [a 0, a 1 ] and [b 0, b 1 ], respectively. We can multiply A and B using the four coefficient multiplications m 1 = a 1 b 1, m 2 = a 1 b 0, m 3 = a 0 b 1, m 4 = a 0 b 0, as well as one numerical addition, to form the polynomial which can be represented by the array C(x) = m 1 x 2 + (m 2 + m 3 )x + m 4, [c 0, c 1, c 2 ] = [m 4, m 3 + m 2, m 1 ]. (a) Give a divide-and-conquer algorithm for multiplying two polynomials of degree-bound n, represented as coefficient arrays, based on this formula.
3 (b) Give and solve a recurrence for the worst-case running time of your algorithm. 3 (c) Show how to multiply two linear polynomials A(x) = a 1 x + a 0 and B(x) = b 1 x + b 0 using only three coefficient multiplications. (d) Give a divide-and-conquer algorithm for multiplying two polynomials of degree-bound n based on your formula from part (c). (e) Give and solve a recurrence for the worst-case running time of your algorithm. Problem 3 Harry Potter, the child wizard of Hogwarts fame, has once again run into trouble. Professor Snape has sent Harry to detention and assigned him the task of sorting all the old homework assignments from the last 200 years. Being a wizard, Harry waves his wand and says, ordinatus sortitus, and the papers rapidly pile themselves in order. Professor Snape, however, wants to determine whether Harry s spell correctly sorted the papers. Unfortunately, there are a large number n of papers and determining whether they are in perfect order takes Ω(n) time. Professor Snape instead decides to check whether the papers are almost sorted. He wants to know whether 90% of the papers are sorted: is it possible to remove 10% of the papers and have the resulting list be sorted? In this problem, we will help Professor Snape to find an algorithm that takes as input a list A containing n distinct elements, and acts as follows: If the list A is sorted, the algorithm always returns true. If the list A is not 90% sorted, the algorithm returns false with probability at least 2/3. (a) Professor Snape first considers the following algorithm: Repeat k times: 1. Choose a paper i independently and uniformly at random from the open interval (1,n). (That is, 1 <i<n.) 2. Compare paper A[i 1] and A[i]. Output false and halt if they are not sorted correctly. 3. Compare paper A[i] and A[i +1]. Output false and halt if they are not sorted correctly. Output true. Show that for this algorithm to correctly discover whether the list is almost sorted with probability at least 2/3 requires k =Ω(n). Hint: Find a sequence that is not almost sorted, but with only a small number of elements that will cause the algorithm to return false. (b) Imagine you are given a bag of n balls. You are told that at least 10% of the balls are blue, and no more than 90% of the balls are red. Asymptotically (for large n) how many balls do you have to draw from the bag to see a blue ball with probability at least 2/3? (You can assume that the balls are drawn with replacement.)
4 4 (c) Consider performing a binary search on an unsorted list: BINARY-SEARCH(A, key, left, right) Search for key in A[left..right]. 1 if left = right 2 then return left 3 else mid (left + right)/2 4 if key <A[mid] 5 then return BINARY-SEARCH(A, key, left, mid 1) 6 else return BINARY-SEARCH(A, key, mid, right) Assume that a binary search for key 1 in A (even though A is not sorted) returns slot i. Similarly, a binary search for key 2 in A returns slot j. Explain why the following fact is true: if i<j,thenkey 1 key 2. Draw a picture. Hint: First think about why this is obviously true if list A is sorted. (d) Professor Snape proposes a randomized algorithm to determine whether a list is 90% sorted. The algorithm uses the function RANDOM(1,n) to choose an integer independently and uniformly at random in the closed interval [1,n]. The algorithm is presented below. IS-ALMOST-SORTED(A, n, k) Determine if A[1..n] is almost sorted. 1 for r 1 to k 2 do i RANDOM(1,n) Pick i uniformly and independently. 3 j BINARY-SEARCH(A, A[i], 1,n) 4 if i = j 5 then return false 6 return true Show that the algorithm is correct if k is a sufficiently large constant. That is, with k chosen appropriately, the algorithm always outputs true if a list is correctly sorted and outputs false with probability at least 2/3 if the list is not 90% sorted. (e) Imagine instead that Professor Snape would like to determine whether a list is 1 ɛ sorted for some 0 <ɛ<1. (In the previous parts ɛ =0.10.) For large n, determine the appropriate value of k, asymptotically, and show that the algorithm is correct. What is the overall running time? Problem 4 On his way back from detention, Harry runs into his friend Hermione. He is upset because Professor Snape discovered that his sorting spell failed. Instead of sorting the papers correctly, each paper was within k slots of the proper position. Hermione immediately suggests that insertion sort would have easily fixed theproblem. In this problem, we show that Hermione is correct (as usual). As before, A[1..n] in an array of n distinct elements. (a) First, we define an inversion. If i<jand A[i] >A[j], then the pair (i, j) is called an
5 5 inversion of A. What permutation of the array {1, 2,...,n} has the most inversions? How many does it have? (b) Show that, if every paper is initially within k slots of its proper position, insertion sort runs in time O(nk). (c) Show that sorting a list in which each paper is within k slots of its proper position takes Ω(n lg k) comparisons. (d) Devise an algorithm that matches the lower bound, i.e., sorts a list in which each paper is within k slots of its proper position in Θ(n lg k) time. Problem 5 For n distinct elements x 1,x 2,...,x n with positive weights w 1,w 2,...,w n such that n i=1 w i =1, the weighted (lower) median is the element x k satisfying 1 w i < 2 x i <x k and 1. wi 2 x i >x k (a) Argue that the median of x 1,x 2,...,x n is the weighted median of x 1,x 2,...,x n with weights w i =1/n for i =1, 2,...,n. (b) Show how to compute the weighted median of n elements in O(n lg n) worst-case time using sorting. (c) Show how to compute the weighted median in Θ(n) worst-case time using a lineartime median algorithm such as SELECT. (d) The post-office location problem is defined as follows. We are given n points p 1,p 2,...,p n with associated weights w 1,w 2,...,w n. We wish to find a point p (not necessarily one of the input points) that minimizes the sum n i=1 w i d(p, p i ),whered(a, b) is the dis- tance between points a and b. Argue that the weighted median is a best solution for the one-dimensional post-office location problem, in which points are simply real numbers and the distance between points a and b is d(a, b) = a b. (e) Find the best solution for the two-dimensional post-office location problem, in which the points are (x, y) coordinate pairs and the distance between points a =(x 1,y 1 ) and b =(x 2,y 2 ) is the Manhattan distance given by d(a, b) = x 1 x 2 + y 1 y 2.
Problem Set 1 Solutions
 Introduction to Algorithms September 24, 2004 Massachusetts Institute of Technology 6.046J/18.410J Professors Piotr Indyk and Charles E. Leiserson Handout 7 Problem Set 1 Solutions Exercise 1-1. Do Exercise
Introduction to Algorithms September 24, 2004 Massachusetts Institute of Technology 6.046J/18.410J Professors Piotr Indyk and Charles E. Leiserson Handout 7 Problem Set 1 Solutions Exercise 1-1. Do Exercise
Problem Set 2 Solutions
 Introduction to Algorithms October 1, 2004 Massachusetts Institute of Technology 6.046J/18.410J Professors Piotr Indyk and Charles E. Leiserson Handout 9 Problem Set 2 Solutions Reading: Chapters 5-9,
Introduction to Algorithms October 1, 2004 Massachusetts Institute of Technology 6.046J/18.410J Professors Piotr Indyk and Charles E. Leiserson Handout 9 Problem Set 2 Solutions Reading: Chapters 5-9,
CSCI Honor seminar in algorithms Homework 2 Solution
 CSCI 493.55 Honor seminar in algorithms Homework 2 Solution Saad Mneimneh Visiting Professor Hunter College of CUNY Problem 1: Rabin-Karp string matching Consider a binary string s of length n and another
CSCI 493.55 Honor seminar in algorithms Homework 2 Solution Saad Mneimneh Visiting Professor Hunter College of CUNY Problem 1: Rabin-Karp string matching Consider a binary string s of length n and another
1 Closest Pair of Points on the Plane
 CS 31: Algorithms (Spring 2019): Lecture 5 Date: 4th April, 2019 Topic: Divide and Conquer 3: Closest Pair of Points on a Plane Disclaimer: These notes have not gone through scrutiny and in all probability
CS 31: Algorithms (Spring 2019): Lecture 5 Date: 4th April, 2019 Topic: Divide and Conquer 3: Closest Pair of Points on a Plane Disclaimer: These notes have not gone through scrutiny and in all probability
CS 577 Introduction to Algorithms: Strassen s Algorithm and the Master Theorem
 CS 577 Introduction to Algorithms: Jin-Yi Cai University of Wisconsin Madison In the last class, we described InsertionSort and showed that its worst-case running time is Θ(n 2 ). Check Figure 2.2 for
CS 577 Introduction to Algorithms: Jin-Yi Cai University of Wisconsin Madison In the last class, we described InsertionSort and showed that its worst-case running time is Θ(n 2 ). Check Figure 2.2 for
COL106: Data Structures and Algorithms (IIT Delhi, Semester-II )
 1 Solve the following recurrence relations giving a Θ bound for each of the cases 1 : (a) T (n) = 2T (n/3) + 1; T (1) = 1 (Assume n is a power of 3) (b) T (n) = 5T (n/4) + n; T (1) = 1 (Assume n is a power
1 Solve the following recurrence relations giving a Θ bound for each of the cases 1 : (a) T (n) = 2T (n/3) + 1; T (1) = 1 (Assume n is a power of 3) (b) T (n) = 5T (n/4) + n; T (1) = 1 (Assume n is a power
Central Algorithmic Techniques. Iterative Algorithms
 Central Algorithmic Techniques Iterative Algorithms Code Representation of an Algorithm class InsertionSortAlgorithm extends SortAlgorithm { void sort(int a[]) throws Exception { for (int i = 1; i < a.length;
Central Algorithmic Techniques Iterative Algorithms Code Representation of an Algorithm class InsertionSortAlgorithm extends SortAlgorithm { void sort(int a[]) throws Exception { for (int i = 1; i < a.length;
b + O(n d ) where a 1, b > 1, then O(n d log n) if a = b d d ) if a < b d O(n log b a ) if a > b d
 CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
Algorithm efficiency analysis
 Algorithm efficiency analysis Mădălina Răschip, Cristian Gaţu Faculty of Computer Science Alexandru Ioan Cuza University of Iaşi, Romania DS 2017/2018 Content Algorithm efficiency analysis Recursive function
Algorithm efficiency analysis Mădălina Răschip, Cristian Gaţu Faculty of Computer Science Alexandru Ioan Cuza University of Iaşi, Romania DS 2017/2018 Content Algorithm efficiency analysis Recursive function
Advanced Analysis of Algorithms - Midterm (Solutions)
 Advanced Analysis of Algorithms - Midterm (Solutions) K. Subramani LCSEE, West Virginia University, Morgantown, WV {ksmani@csee.wvu.edu} 1 Problems 1. Solve the following recurrence using substitution:
Advanced Analysis of Algorithms - Midterm (Solutions) K. Subramani LCSEE, West Virginia University, Morgantown, WV {ksmani@csee.wvu.edu} 1 Problems 1. Solve the following recurrence using substitution:
CSCI 3110 Assignment 6 Solutions
 CSCI 3110 Assignment 6 Solutions December 5, 2012 2.4 (4 pts) Suppose you are choosing between the following three algorithms: 1. Algorithm A solves problems by dividing them into five subproblems of half
CSCI 3110 Assignment 6 Solutions December 5, 2012 2.4 (4 pts) Suppose you are choosing between the following three algorithms: 1. Algorithm A solves problems by dividing them into five subproblems of half
Algorithms and Data Structures 2016 Week 5 solutions (Tues 9th - Fri 12th February)
 Algorithms and Data Structures 016 Week 5 solutions (Tues 9th - Fri 1th February) 1. Draw the decision tree (under the assumption of all-distinct inputs) Quicksort for n = 3. answer: (of course you should
Algorithms and Data Structures 016 Week 5 solutions (Tues 9th - Fri 1th February) 1. Draw the decision tree (under the assumption of all-distinct inputs) Quicksort for n = 3. answer: (of course you should
Chapter 4 Divide-and-Conquer
 Chapter 4 Divide-and-Conquer 1 About this lecture (1) Recall the divide-and-conquer paradigm, which we used for merge sort: Divide the problem into a number of subproblems that are smaller instances of
Chapter 4 Divide-and-Conquer 1 About this lecture (1) Recall the divide-and-conquer paradigm, which we used for merge sort: Divide the problem into a number of subproblems that are smaller instances of
CS 161 Summer 2009 Homework #2 Sample Solutions
 CS 161 Summer 2009 Homework #2 Sample Solutions Regrade Policy: If you believe an error has been made in the grading of your homework, you may resubmit it for a regrade. If the error consists of more than
CS 161 Summer 2009 Homework #2 Sample Solutions Regrade Policy: If you believe an error has been made in the grading of your homework, you may resubmit it for a regrade. If the error consists of more than
Solutions. Problem 1: Suppose a polynomial in n of degree d has the form
 Assignment 1 1. Problem 3-1 on p. 57 2. Problem 3-2 on p. 58 3. Problem 4-5 on p. 86 4. Problem 6-1 on p. 142 5. Problem 7-4 on p. 162 6. Prove correctness (including halting) of SelectionSort (use loop
Assignment 1 1. Problem 3-1 on p. 57 2. Problem 3-2 on p. 58 3. Problem 4-5 on p. 86 4. Problem 6-1 on p. 142 5. Problem 7-4 on p. 162 6. Prove correctness (including halting) of SelectionSort (use loop
CS483 Design and Analysis of Algorithms
 CS483 Design and Analysis of Algorithms Chapter 2 Divide and Conquer Algorithms Instructor: Fei Li lifei@cs.gmu.edu with subject: CS483 Office hours: Room 5326, Engineering Building, Thursday 4:30pm -
CS483 Design and Analysis of Algorithms Chapter 2 Divide and Conquer Algorithms Instructor: Fei Li lifei@cs.gmu.edu with subject: CS483 Office hours: Room 5326, Engineering Building, Thursday 4:30pm -
CS483 Design and Analysis of Algorithms
 CS483 Design and Analysis of Algorithms Lecture 6-8 Divide and Conquer Algorithms Instructor: Fei Li lifei@cs.gmu.edu with subject: CS483 Office hours: STII, Room 443, Friday 4:00pm - 6:00pm or by appointments
CS483 Design and Analysis of Algorithms Lecture 6-8 Divide and Conquer Algorithms Instructor: Fei Li lifei@cs.gmu.edu with subject: CS483 Office hours: STII, Room 443, Friday 4:00pm - 6:00pm or by appointments
Grade 11/12 Math Circles Fall Nov. 5 Recurrences, Part 2
 1 Faculty of Mathematics Waterloo, Ontario Centre for Education in Mathematics and Computing Grade 11/12 Math Circles Fall 2014 - Nov. 5 Recurrences, Part 2 Running time of algorithms In computer science,
1 Faculty of Mathematics Waterloo, Ontario Centre for Education in Mathematics and Computing Grade 11/12 Math Circles Fall 2014 - Nov. 5 Recurrences, Part 2 Running time of algorithms In computer science,
Analysis of Algorithms I: Asymptotic Notation, Induction, and MergeSort
 Analysis of Algorithms I: Asymptotic Notation, Induction, and MergeSort Xi Chen Columbia University We continue with two more asymptotic notation: o( ) and ω( ). Let f (n) and g(n) are functions that map
Analysis of Algorithms I: Asymptotic Notation, Induction, and MergeSort Xi Chen Columbia University We continue with two more asymptotic notation: o( ) and ω( ). Let f (n) and g(n) are functions that map
COMP 382: Reasoning about algorithms
 Fall 2014 Unit 4: Basics of complexity analysis Correctness and efficiency So far, we have talked about correctness and termination of algorithms What about efficiency? Running time of an algorithm For
Fall 2014 Unit 4: Basics of complexity analysis Correctness and efficiency So far, we have talked about correctness and termination of algorithms What about efficiency? Running time of an algorithm For
Outline. 1 Introduction. 3 Quicksort. 4 Analysis. 5 References. Idea. 1 Choose an element x and reorder the array as follows:
 Outline Computer Science 331 Quicksort Mike Jacobson Department of Computer Science University of Calgary Lecture #28 1 Introduction 2 Randomized 3 Quicksort Deterministic Quicksort Randomized Quicksort
Outline Computer Science 331 Quicksort Mike Jacobson Department of Computer Science University of Calgary Lecture #28 1 Introduction 2 Randomized 3 Quicksort Deterministic Quicksort Randomized Quicksort
1 Quick Sort LECTURE 7. OHSU/OGI (Winter 2009) ANALYSIS AND DESIGN OF ALGORITHMS
 OHSU/OGI (Winter 2009) CS532 ANALYSIS AND DESIGN OF ALGORITHMS LECTURE 7 1 Quick Sort QuickSort 1 is a classic example of divide and conquer. The hard work is to rearrange the elements of the array A[1..n]
OHSU/OGI (Winter 2009) CS532 ANALYSIS AND DESIGN OF ALGORITHMS LECTURE 7 1 Quick Sort QuickSort 1 is a classic example of divide and conquer. The hard work is to rearrange the elements of the array A[1..n]
Introduction to Divide and Conquer
 Introduction to Divide and Conquer Sorting with O(n log n) comparisons and integer multiplication faster than O(n 2 ) Periklis A. Papakonstantinou York University Consider a problem that admits a straightforward
Introduction to Divide and Conquer Sorting with O(n log n) comparisons and integer multiplication faster than O(n 2 ) Periklis A. Papakonstantinou York University Consider a problem that admits a straightforward
Lecture 2. Fundamentals of the Analysis of Algorithm Efficiency
 Lecture 2 Fundamentals of the Analysis of Algorithm Efficiency 1 Lecture Contents 1. Analysis Framework 2. Asymptotic Notations and Basic Efficiency Classes 3. Mathematical Analysis of Nonrecursive Algorithms
Lecture 2 Fundamentals of the Analysis of Algorithm Efficiency 1 Lecture Contents 1. Analysis Framework 2. Asymptotic Notations and Basic Efficiency Classes 3. Mathematical Analysis of Nonrecursive Algorithms
Divide and Conquer. Maximum/minimum. Median finding. CS125 Lecture 4 Fall 2016
 CS125 Lecture 4 Fall 2016 Divide and Conquer We have seen one general paradigm for finding algorithms: the greedy approach. We now consider another general paradigm, known as divide and conquer. We have
CS125 Lecture 4 Fall 2016 Divide and Conquer We have seen one general paradigm for finding algorithms: the greedy approach. We now consider another general paradigm, known as divide and conquer. We have
CSE 591 Homework 3 Sample Solutions. Problem 1
 CSE 591 Homework 3 Sample Solutions Problem 1 (a) Let p = max{1, k d}, q = min{n, k + d}, it suffices to find the pth and qth largest element of L and output all elements in the range between these two
CSE 591 Homework 3 Sample Solutions Problem 1 (a) Let p = max{1, k d}, q = min{n, k + d}, it suffices to find the pth and qth largest element of L and output all elements in the range between these two
CS383, Algorithms Spring 2009 HW1 Solutions
 Prof. Sergio A. Alvarez http://www.cs.bc.edu/ alvarez/ 21 Campanella Way, room 569 alvarez@cs.bc.edu Computer Science Department voice: (617) 552-4333 Boston College fax: (617) 552-6790 Chestnut Hill,
Prof. Sergio A. Alvarez http://www.cs.bc.edu/ alvarez/ 21 Campanella Way, room 569 alvarez@cs.bc.edu Computer Science Department voice: (617) 552-4333 Boston College fax: (617) 552-6790 Chestnut Hill,
Algorithms and Their Complexity
 CSCE 222 Discrete Structures for Computing David Kebo Houngninou Algorithms and Their Complexity Chapter 3 Algorithm An algorithm is a finite sequence of steps that solves a problem. Computational complexity
CSCE 222 Discrete Structures for Computing David Kebo Houngninou Algorithms and Their Complexity Chapter 3 Algorithm An algorithm is a finite sequence of steps that solves a problem. Computational complexity
Advanced Analysis of Algorithms - Homework I (Solutions)
 Advanced Analysis of Algorithms - Homework I (Solutions) K. Subramani LCSEE, West Virginia University, Morgantown, WV {ksmani@csee.wvu.edu} 1 Problems 1. Given an array A of n integer elements, how would
Advanced Analysis of Algorithms - Homework I (Solutions) K. Subramani LCSEE, West Virginia University, Morgantown, WV {ksmani@csee.wvu.edu} 1 Problems 1. Given an array A of n integer elements, how would
Divide and Conquer CPE 349. Theresa Migler-VonDollen
 Divide and Conquer CPE 349 Theresa Migler-VonDollen Divide and Conquer Divide and Conquer is a strategy that solves a problem by: 1 Breaking the problem into subproblems that are themselves smaller instances
Divide and Conquer CPE 349 Theresa Migler-VonDollen Divide and Conquer Divide and Conquer is a strategy that solves a problem by: 1 Breaking the problem into subproblems that are themselves smaller instances
Growth of Functions (CLRS 2.3,3)
 Growth of Functions (CLRS 2.3,3) 1 Review Last time we discussed running time of algorithms and introduced the RAM model of computation. Best-case running time: the shortest running time for any input
Growth of Functions (CLRS 2.3,3) 1 Review Last time we discussed running time of algorithms and introduced the RAM model of computation. Best-case running time: the shortest running time for any input
Mergesort and Recurrences (CLRS 2.3, 4.4)
 Mergesort and Recurrences (CLRS 2.3, 4.4) We saw a couple of O(n 2 ) algorithms for sorting. Today we ll see a different approach that runs in O(n lg n) and uses one of the most powerful techniques for
Mergesort and Recurrences (CLRS 2.3, 4.4) We saw a couple of O(n 2 ) algorithms for sorting. Today we ll see a different approach that runs in O(n lg n) and uses one of the most powerful techniques for
1 Terminology and setup
 15-451/651: Design & Analysis of Algorithms August 31, 2017 Lecture #2 last changed: August 29, 2017 In this lecture, we will examine some simple, concrete models of computation, each with a precise definition
15-451/651: Design & Analysis of Algorithms August 31, 2017 Lecture #2 last changed: August 29, 2017 In this lecture, we will examine some simple, concrete models of computation, each with a precise definition
CSE101: Design and Analysis of Algorithms. Ragesh Jaiswal, CSE, UCSD
 Greedy s Greedy s Shortest path Claim 2: Let S be a subset of vertices containing s such that we know the shortest path length l(s, u) from s to any vertex in u S. Let e = (u, v) be an edge such that 1
Greedy s Greedy s Shortest path Claim 2: Let S be a subset of vertices containing s such that we know the shortest path length l(s, u) from s to any vertex in u S. Let e = (u, v) be an edge such that 1
CS173 Running Time and Big-O. Tandy Warnow
 CS173 Running Time and Big-O Tandy Warnow CS 173 Running Times and Big-O analysis Tandy Warnow Today s material We will cover: Running time analysis Review of running time analysis of Bubblesort Review
CS173 Running Time and Big-O Tandy Warnow CS 173 Running Times and Big-O analysis Tandy Warnow Today s material We will cover: Running time analysis Review of running time analysis of Bubblesort Review
1. [10 marks] Consider the following two algorithms that find the two largest elements in an array A[1..n], where n >= 2.
![1. [10 marks] Consider the following two algorithms that find the two largest elements in an array A[1..n], where n >= 2. 1. [10 marks] Consider the following two algorithms that find the two largest elements in an array A[1..n], where n >= 2.](/thumbs/73/68822500.jpg) CSC 6 H5S Homework Assignment # 1 Spring 010 Worth: 11% Due: Monday February 1 (at class) For each question, please write up detailed answers carefully. Make sure that you use notation and terminology
CSC 6 H5S Homework Assignment # 1 Spring 010 Worth: 11% Due: Monday February 1 (at class) For each question, please write up detailed answers carefully. Make sure that you use notation and terminology
Fall 2017 November 10, Written Homework 5
 CS1800 Discrete Structures Profs. Aslam, Gold, & Pavlu Fall 2017 November 10, 2017 Assigned: Mon Nov 13 2017 Due: Wed Nov 29 2017 Instructions: Written Homework 5 The assignment has to be uploaded to blackboard
CS1800 Discrete Structures Profs. Aslam, Gold, & Pavlu Fall 2017 November 10, 2017 Assigned: Mon Nov 13 2017 Due: Wed Nov 29 2017 Instructions: Written Homework 5 The assignment has to be uploaded to blackboard
Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts)
![Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts) Quiz 1 Solutions. Problem 2. Asymptotics & Recurrences [20 points] (3 parts)](/thumbs/87/95581149.jpg) Introduction to Algorithms October 13, 2010 Massachusetts Institute of Technology 6.006 Fall 2010 Professors Konstantinos Daskalakis and Patrick Jaillet Quiz 1 Solutions Quiz 1 Solutions Problem 1. We
Introduction to Algorithms October 13, 2010 Massachusetts Institute of Technology 6.006 Fall 2010 Professors Konstantinos Daskalakis and Patrick Jaillet Quiz 1 Solutions Quiz 1 Solutions Problem 1. We
Lecture 1: Asymptotics, Recurrences, Elementary Sorting
 Lecture 1: Asymptotics, Recurrences, Elementary Sorting Instructor: Outline 1 Introduction to Asymptotic Analysis Rate of growth of functions Comparing and bounding functions: O, Θ, Ω Specifying running
Lecture 1: Asymptotics, Recurrences, Elementary Sorting Instructor: Outline 1 Introduction to Asymptotic Analysis Rate of growth of functions Comparing and bounding functions: O, Θ, Ω Specifying running
Computational Complexity - Pseudocode and Recursions
 Computational Complexity - Pseudocode and Recursions Nicholas Mainardi 1 Dipartimento di Elettronica e Informazione Politecnico di Milano nicholas.mainardi@polimi.it June 6, 2018 1 Partly Based on Alessandro
Computational Complexity - Pseudocode and Recursions Nicholas Mainardi 1 Dipartimento di Elettronica e Informazione Politecnico di Milano nicholas.mainardi@polimi.it June 6, 2018 1 Partly Based on Alessandro
Inf 2B: Sorting, MergeSort and Divide-and-Conquer
 Inf 2B: Sorting, MergeSort and Divide-and-Conquer Lecture 7 of ADS thread Kyriakos Kalorkoti School of Informatics University of Edinburgh The Sorting Problem Input: Task: Array A of items with comparable
Inf 2B: Sorting, MergeSort and Divide-and-Conquer Lecture 7 of ADS thread Kyriakos Kalorkoti School of Informatics University of Edinburgh The Sorting Problem Input: Task: Array A of items with comparable
Mid-term Exam Answers and Final Exam Study Guide CIS 675 Summer 2010
 Mid-term Exam Answers and Final Exam Study Guide CIS 675 Summer 2010 Midterm Problem 1: Recall that for two functions g : N N + and h : N N +, h = Θ(g) iff for some positive integer N and positive real
Mid-term Exam Answers and Final Exam Study Guide CIS 675 Summer 2010 Midterm Problem 1: Recall that for two functions g : N N + and h : N N +, h = Θ(g) iff for some positive integer N and positive real
Topic 17. Analysis of Algorithms
 Topic 17 Analysis of Algorithms Analysis of Algorithms- Review Efficiency of an algorithm can be measured in terms of : Time complexity: a measure of the amount of time required to execute an algorithm
Topic 17 Analysis of Algorithms Analysis of Algorithms- Review Efficiency of an algorithm can be measured in terms of : Time complexity: a measure of the amount of time required to execute an algorithm
Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018
 CS17 Integrated Introduction to Computer Science Klein Contents Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018 1 Tree definitions 1 2 Analysis of mergesort using a binary tree 1 3 Analysis of
CS17 Integrated Introduction to Computer Science Klein Contents Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018 1 Tree definitions 1 2 Analysis of mergesort using a binary tree 1 3 Analysis of
1 Divide and Conquer (September 3)
 The control of a large force is the same principle as the control of a few men: it is merely a question of dividing up their numbers. Sun Zi, The Art of War (c. 400 C.E.), translated by Lionel Giles (1910)
The control of a large force is the same principle as the control of a few men: it is merely a question of dividing up their numbers. Sun Zi, The Art of War (c. 400 C.E.), translated by Lionel Giles (1910)
Analysis of Algorithms - Midterm (Solutions)
 Analysis of Algorithms - Midterm (Solutions) K Subramani LCSEE, West Virginia University, Morgantown, WV {ksmani@cseewvuedu} 1 Problems 1 Recurrences: Solve the following recurrences exactly or asymototically
Analysis of Algorithms - Midterm (Solutions) K Subramani LCSEE, West Virginia University, Morgantown, WV {ksmani@cseewvuedu} 1 Problems 1 Recurrences: Solve the following recurrences exactly or asymototically
Lecture 4. Quicksort
 Lecture 4. Quicksort T. H. Cormen, C. E. Leiserson and R. L. Rivest Introduction to Algorithms, 3rd Edition, MIT Press, 2009 Sungkyunkwan University Hyunseung Choo choo@skku.edu Copyright 2000-2018 Networking
Lecture 4. Quicksort T. H. Cormen, C. E. Leiserson and R. L. Rivest Introduction to Algorithms, 3rd Edition, MIT Press, 2009 Sungkyunkwan University Hyunseung Choo choo@skku.edu Copyright 2000-2018 Networking
COM S 330 Homework 08 Solutions. Type your answers to the following questions and submit a PDF file to Blackboard. One page per problem.
 COM S 0 Homework 08 Solutions Type your answers to the following questions and submit a PDF file to Blackboard. One page per problem. Problem 1. [10pts] Let M = (S, T, s 0 ) be the state machine where
COM S 0 Homework 08 Solutions Type your answers to the following questions and submit a PDF file to Blackboard. One page per problem. Problem 1. [10pts] Let M = (S, T, s 0 ) be the state machine where
Sorting and Searching. Tony Wong
 Tony Wong 2017-03-04 Sorting Sorting is the reordering of array elements into a specific order (usually ascending) For example, array a[0..8] consists of the final exam scores of the n = 9 students in
Tony Wong 2017-03-04 Sorting Sorting is the reordering of array elements into a specific order (usually ascending) For example, array a[0..8] consists of the final exam scores of the n = 9 students in
Loop Invariants and Binary Search. Chapter 4.4, 5.1
 Loop Invariants and Binary Search Chapter 4.4, 5.1 Outline Iterative Algorithms, Assertions and Proofs of Correctness Binary Search: A Case Study Outline Iterative Algorithms, Assertions and Proofs of
Loop Invariants and Binary Search Chapter 4.4, 5.1 Outline Iterative Algorithms, Assertions and Proofs of Correctness Binary Search: A Case Study Outline Iterative Algorithms, Assertions and Proofs of
CS 170 Algorithms Fall 2014 David Wagner MT2
 CS 170 Algorithms Fall 2014 David Wagner MT2 PRINT your name:, (last) SIGN your name: (first) Your Student ID number: Your Unix account login: cs170- The room you are sitting in right now: Name of the
CS 170 Algorithms Fall 2014 David Wagner MT2 PRINT your name:, (last) SIGN your name: (first) Your Student ID number: Your Unix account login: cs170- The room you are sitting in right now: Name of the
Algorithms and Data Structures 2014 Exercises week 5
 Algorithms and Data Structures 014 Exercises week 5 October, 014 Exercises marked by ( ) are hard, but they might show up on the exam. Exercises marked by ( ) are even harder, but they will not be on the
Algorithms and Data Structures 014 Exercises week 5 October, 014 Exercises marked by ( ) are hard, but they might show up on the exam. Exercises marked by ( ) are even harder, but they will not be on the
Solving Recurrences. Lecture 23 CS2110 Fall 2011
 Solving Recurrences Lecture 23 CS2110 Fall 2011 1 Announcements Makeup Prelim 2 Monday 11/21 7:30-9pm Upson 5130 Please do not discuss the prelim with your classmates! Quiz 4 next Tuesday in class Topics:
Solving Recurrences Lecture 23 CS2110 Fall 2011 1 Announcements Makeup Prelim 2 Monday 11/21 7:30-9pm Upson 5130 Please do not discuss the prelim with your classmates! Quiz 4 next Tuesday in class Topics:
Week 5: Quicksort, Lower bound, Greedy
 Week 5: Quicksort, Lower bound, Greedy Agenda: Quicksort: Average case Lower bound for sorting Greedy method 1 Week 5: Quicksort Recall Quicksort: The ideas: Pick one key Compare to others: partition into
Week 5: Quicksort, Lower bound, Greedy Agenda: Quicksort: Average case Lower bound for sorting Greedy method 1 Week 5: Quicksort Recall Quicksort: The ideas: Pick one key Compare to others: partition into
CSE 312, Winter 2011, W.L.Ruzzo. 8. Average-Case Analysis of Algorithms + Randomized Algorithms
 CSE 312, Winter 2011, W.L.Ruzzo 8. Average-Case Analysis of Algorithms + Randomized Algorithms 1 insertion sort Array A[1]..A[n] for i = 1..n-1 { T = A[i] Sorted j swap j = i-1 compare while j >= 0 &&
CSE 312, Winter 2011, W.L.Ruzzo 8. Average-Case Analysis of Algorithms + Randomized Algorithms 1 insertion sort Array A[1]..A[n] for i = 1..n-1 { T = A[i] Sorted j swap j = i-1 compare while j >= 0 &&
CS Non-recursive and Recursive Algorithm Analysis
 CS483-04 Non-recursive and Recursive Algorithm Analysis Instructor: Fei Li Room 443 ST II Office hours: Tue. & Thur. 4:30pm - 5:30pm or by appointments lifei@cs.gmu.edu with subject: CS483 http://www.cs.gmu.edu/
CS483-04 Non-recursive and Recursive Algorithm Analysis Instructor: Fei Li Room 443 ST II Office hours: Tue. & Thur. 4:30pm - 5:30pm or by appointments lifei@cs.gmu.edu with subject: CS483 http://www.cs.gmu.edu/
Solving recurrences. Frequently showing up when analysing divide&conquer algorithms or, more generally, recursive algorithms.
 Solving recurrences Frequently showing up when analysing divide&conquer algorithms or, more generally, recursive algorithms Example: Merge-Sort(A, p, r) 1: if p < r then 2: q (p + r)/2 3: Merge-Sort(A,
Solving recurrences Frequently showing up when analysing divide&conquer algorithms or, more generally, recursive algorithms Example: Merge-Sort(A, p, r) 1: if p < r then 2: q (p + r)/2 3: Merge-Sort(A,
Asymptotic Analysis and Recurrences
 Appendix A Asymptotic Analysis and Recurrences A.1 Overview We discuss the notion of asymptotic analysis and introduce O, Ω, Θ, and o notation. We then turn to the topic of recurrences, discussing several
Appendix A Asymptotic Analysis and Recurrences A.1 Overview We discuss the notion of asymptotic analysis and introduce O, Ω, Θ, and o notation. We then turn to the topic of recurrences, discussing several
Discrete Math, Spring Solutions to Problems V
 Discrete Math, Spring 202 - Solutions to Problems V Suppose we have statements P, P 2, P 3,, one for each natural number In other words, we have the collection or set of statements {P n n N} a Suppose
Discrete Math, Spring 202 - Solutions to Problems V Suppose we have statements P, P 2, P 3,, one for each natural number In other words, we have the collection or set of statements {P n n N} a Suppose
Review Of Topics. Review: Induction
 Review Of Topics Asymptotic notation Solving recurrences Sorting algorithms Insertion sort Merge sort Heap sort Quick sort Counting sort Radix sort Medians/order statistics Randomized algorithm Worst-case
Review Of Topics Asymptotic notation Solving recurrences Sorting algorithms Insertion sort Merge sort Heap sort Quick sort Counting sort Radix sort Medians/order statistics Randomized algorithm Worst-case
Divide and Conquer. Chapter Overview. 1.2 Divide and Conquer
 Chapter 1 Divide and Conquer 1.1 Overview This chapter introduces Divide and Conquer, which is a technique for designing recursive algorithms that are (sometimes) asymptotically efficient. It also presents
Chapter 1 Divide and Conquer 1.1 Overview This chapter introduces Divide and Conquer, which is a technique for designing recursive algorithms that are (sometimes) asymptotically efficient. It also presents
Algorithms. Quicksort. Slide credit: David Luebke (Virginia)
 1 Algorithms Quicksort Slide credit: David Luebke (Virginia) Sorting revisited We have seen algorithms for sorting: INSERTION-SORT, MERGESORT More generally: given a sequence of items Each item has a characteristic
1 Algorithms Quicksort Slide credit: David Luebke (Virginia) Sorting revisited We have seen algorithms for sorting: INSERTION-SORT, MERGESORT More generally: given a sequence of items Each item has a characteristic
CS2223 Algorithms D Term 2009 Exam 3 Solutions
 CS2223 Algorithms D Term 2009 Exam 3 Solutions May 4, 2009 By Prof. Carolina Ruiz Dept. of Computer Science WPI PROBLEM 1: Asymptoptic Growth Rates (10 points) Let A and B be two algorithms with runtimes
CS2223 Algorithms D Term 2009 Exam 3 Solutions May 4, 2009 By Prof. Carolina Ruiz Dept. of Computer Science WPI PROBLEM 1: Asymptoptic Growth Rates (10 points) Let A and B be two algorithms with runtimes
Divide and Conquer Strategy
 Divide and Conquer Strategy Algorithm design is more an art, less so a science. There are a few useful strategies, but no guarantee to succeed. We will discuss: Divide and Conquer, Greedy, Dynamic Programming.
Divide and Conquer Strategy Algorithm design is more an art, less so a science. There are a few useful strategies, but no guarantee to succeed. We will discuss: Divide and Conquer, Greedy, Dynamic Programming.
Big O 2/14/13. Administrative. Does it terminate? David Kauchak cs302 Spring 2013
 /4/3 Administrative Big O David Kauchak cs3 Spring 3 l Assignment : how d it go? l Assignment : out soon l CLRS code? l Videos Insertion-sort Insertion-sort Does it terminate? /4/3 Insertion-sort Loop
/4/3 Administrative Big O David Kauchak cs3 Spring 3 l Assignment : how d it go? l Assignment : out soon l CLRS code? l Videos Insertion-sort Insertion-sort Does it terminate? /4/3 Insertion-sort Loop
Algorithm Design CS 515 Fall 2015 Sample Final Exam Solutions
 Algorithm Design CS 515 Fall 2015 Sample Final Exam Solutions Copyright c 2015 Andrew Klapper. All rights reserved. 1. For the functions satisfying the following three recurrences, determine which is the
Algorithm Design CS 515 Fall 2015 Sample Final Exam Solutions Copyright c 2015 Andrew Klapper. All rights reserved. 1. For the functions satisfying the following three recurrences, determine which is the
Homework 1 Submission
 Homework Submission Sample Solution; Due Date: Thursday, May 4, :59 pm Directions: Your solutions should be typed and submitted as a single pdf on Gradescope by the due date. L A TEX is preferred but not
Homework Submission Sample Solution; Due Date: Thursday, May 4, :59 pm Directions: Your solutions should be typed and submitted as a single pdf on Gradescope by the due date. L A TEX is preferred but not
Input Decidable Language -- Program Halts on all Input Encoding of Input -- Natural Numbers Encoded in Binary or Decimal, Not Unary
 Complexity Analysis Complexity Theory Input Decidable Language -- Program Halts on all Input Encoding of Input -- Natural Numbers Encoded in Binary or Decimal, Not Unary Output TRUE or FALSE Time and Space
Complexity Analysis Complexity Theory Input Decidable Language -- Program Halts on all Input Encoding of Input -- Natural Numbers Encoded in Binary or Decimal, Not Unary Output TRUE or FALSE Time and Space
Data Structures and Algorithms Chapter 2
 1 Data Structures and Algorithms Chapter 2 Werner Nutt 2 Acknowledgments The course follows the book Introduction to Algorithms, by Cormen, Leiserson, Rivest and Stein, MIT Press [CLRST]. Many examples
1 Data Structures and Algorithms Chapter 2 Werner Nutt 2 Acknowledgments The course follows the book Introduction to Algorithms, by Cormen, Leiserson, Rivest and Stein, MIT Press [CLRST]. Many examples
Concrete models and tight upper/lower bounds
 Lecture 3 Concrete models and tight upper/lower bounds 3.1 Overview In this lecture, we will examine some simple, concrete models of computation, each with a precise definition of what counts as a step,
Lecture 3 Concrete models and tight upper/lower bounds 3.1 Overview In this lecture, we will examine some simple, concrete models of computation, each with a precise definition of what counts as a step,
COMP Analysis of Algorithms & Data Structures
 COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Computational Complexity CLRS 34.1-34.4 University of Manitoba COMP 3170 - Analysis of Algorithms & Data Structures 1 / 50 Polynomial
COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Computational Complexity CLRS 34.1-34.4 University of Manitoba COMP 3170 - Analysis of Algorithms & Data Structures 1 / 50 Polynomial
Randomized Sorting Algorithms Quick sort can be converted to a randomized algorithm by picking the pivot element randomly. In this case we can show th
 CSE 3500 Algorithms and Complexity Fall 2016 Lecture 10: September 29, 2016 Quick sort: Average Run Time In the last lecture we started analyzing the expected run time of quick sort. Let X = k 1, k 2,...,
CSE 3500 Algorithms and Complexity Fall 2016 Lecture 10: September 29, 2016 Quick sort: Average Run Time In the last lecture we started analyzing the expected run time of quick sort. Let X = k 1, k 2,...,
NAME (1 pt): SID (1 pt): TA (1 pt): Name of Neighbor to your left (1 pt): Name of Neighbor to your right (1 pt):
 CS 170 First Midterm 26 Feb 2010 NAME (1 pt): SID (1 pt): TA (1 pt): Name of Neighbor to your left (1 pt): Name of Neighbor to your right (1 pt): Instructions: This is a closed book, closed calculator,
CS 170 First Midterm 26 Feb 2010 NAME (1 pt): SID (1 pt): TA (1 pt): Name of Neighbor to your left (1 pt): Name of Neighbor to your right (1 pt): Instructions: This is a closed book, closed calculator,
Lecture 22: Multithreaded Algorithms CSCI Algorithms I. Andrew Rosenberg
 Lecture 22: Multithreaded Algorithms CSCI 700 - Algorithms I Andrew Rosenberg Last Time Open Addressing Hashing Today Multithreading Two Styles of Threading Shared Memory Every thread can access the same
Lecture 22: Multithreaded Algorithms CSCI 700 - Algorithms I Andrew Rosenberg Last Time Open Addressing Hashing Today Multithreading Two Styles of Threading Shared Memory Every thread can access the same
Module 1: Analyzing the Efficiency of Algorithms
 Module 1: Analyzing the Efficiency of Algorithms Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu What is an Algorithm?
Module 1: Analyzing the Efficiency of Algorithms Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu What is an Algorithm?
Divide-and-conquer: Order Statistics. Curs: Fall 2017
 Divide-and-conquer: Order Statistics Curs: Fall 2017 The divide-and-conquer strategy. 1. Break the problem into smaller subproblems, 2. recursively solve each problem, 3. appropriately combine their answers.
Divide-and-conquer: Order Statistics Curs: Fall 2017 The divide-and-conquer strategy. 1. Break the problem into smaller subproblems, 2. recursively solve each problem, 3. appropriately combine their answers.
Recommended readings: Description of Quicksort in my notes, Ch7 of your CLRS text.
 Chapter 1 Quicksort 1.1 Prerequisites You need to be familiar with the divide-and-conquer paradigm, standard notations for expressing the time-complexity of an algorithm, like the big-oh, big-omega notations.
Chapter 1 Quicksort 1.1 Prerequisites You need to be familiar with the divide-and-conquer paradigm, standard notations for expressing the time-complexity of an algorithm, like the big-oh, big-omega notations.
CSE 421, Spring 2017, W.L.Ruzzo. 8. Average-Case Analysis of Algorithms + Randomized Algorithms
 CSE 421, Spring 2017, W.L.Ruzzo 8. Average-Case Analysis of Algorithms + Randomized Algorithms 1 outline and goals 1) Probability tools you've seen allow formal definition of "average case" running time
CSE 421, Spring 2017, W.L.Ruzzo 8. Average-Case Analysis of Algorithms + Randomized Algorithms 1 outline and goals 1) Probability tools you've seen allow formal definition of "average case" running time
Divide and Conquer. Arash Rafiey. 27 October, 2016
 27 October, 2016 Divide the problem into a number of subproblems Divide the problem into a number of subproblems Conquer the subproblems by solving them recursively or if they are small, there must be
27 October, 2016 Divide the problem into a number of subproblems Divide the problem into a number of subproblems Conquer the subproblems by solving them recursively or if they are small, there must be
4. What is the probability that the two values differ by 4 or more in absolute value? There are only six
 1. Short Questions: 2/2/2/2/2 Provide a clear and concise justification of your answer. In this problem, you roll two balanced six-sided dice. Hint: Draw a picture. 1. What is the probability that the
1. Short Questions: 2/2/2/2/2 Provide a clear and concise justification of your answer. In this problem, you roll two balanced six-sided dice. Hint: Draw a picture. 1. What is the probability that the
CPSC 320 (Intermediate Algorithm Design and Analysis). Summer Instructor: Dr. Lior Malka Final Examination, July 24th, 2009
 CPSC 320 (Intermediate Algorithm Design and Analysis). Summer 2009. Instructor: Dr. Lior Malka Final Examination, July 24th, 2009 Student ID: INSTRUCTIONS: There are 6 questions printed on pages 1 7. Exam
CPSC 320 (Intermediate Algorithm Design and Analysis). Summer 2009. Instructor: Dr. Lior Malka Final Examination, July 24th, 2009 Student ID: INSTRUCTIONS: There are 6 questions printed on pages 1 7. Exam
Lecture 5: Loop Invariants and Insertion-sort
 Lecture 5: Loop Invariants and Insertion-sort COMS10007 - Algorithms Dr. Christian Konrad 11.01.2019 Dr. Christian Konrad Lecture 5: Loop Invariants and Insertion-sort 1 / 12 Proofs by Induction Structure
Lecture 5: Loop Invariants and Insertion-sort COMS10007 - Algorithms Dr. Christian Konrad 11.01.2019 Dr. Christian Konrad Lecture 5: Loop Invariants and Insertion-sort 1 / 12 Proofs by Induction Structure
Computational Complexity. This lecture. Notes. Lecture 02 - Basic Complexity Analysis. Tom Kelsey & Susmit Sarkar. Notes
 Computational Complexity Lecture 02 - Basic Complexity Analysis Tom Kelsey & Susmit Sarkar School of Computer Science University of St Andrews http://www.cs.st-andrews.ac.uk/~tom/ twk@st-andrews.ac.uk
Computational Complexity Lecture 02 - Basic Complexity Analysis Tom Kelsey & Susmit Sarkar School of Computer Science University of St Andrews http://www.cs.st-andrews.ac.uk/~tom/ twk@st-andrews.ac.uk
Data Structures and Algorithms
 Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
Asymptotic Algorithm Analysis & Sorting
 Asymptotic Algorithm Analysis & Sorting (Version of 5th March 2010) (Based on original slides by John Hamer and Yves Deville) We can analyse an algorithm without needing to run it, and in so doing we can
Asymptotic Algorithm Analysis & Sorting (Version of 5th March 2010) (Based on original slides by John Hamer and Yves Deville) We can analyse an algorithm without needing to run it, and in so doing we can
Fundamental Algorithms
 Chapter 2: Sorting, Winter 2018/19 1 Fundamental Algorithms Chapter 2: Sorting Jan Křetínský Winter 2018/19 Chapter 2: Sorting, Winter 2018/19 2 Part I Simple Sorts Chapter 2: Sorting, Winter 2018/19 3
Chapter 2: Sorting, Winter 2018/19 1 Fundamental Algorithms Chapter 2: Sorting Jan Křetínský Winter 2018/19 Chapter 2: Sorting, Winter 2018/19 2 Part I Simple Sorts Chapter 2: Sorting, Winter 2018/19 3
CPSC 320 Sample Final Examination December 2013
 CPSC 320 Sample Final Examination December 2013 [10] 1. Answer each of the following questions with true or false. Give a short justification for each of your answers. [5] a. 6 n O(5 n ) lim n + This is
CPSC 320 Sample Final Examination December 2013 [10] 1. Answer each of the following questions with true or false. Give a short justification for each of your answers. [5] a. 6 n O(5 n ) lim n + This is
CS483 Design and Analysis of Algorithms
 CS483 Design and Analysis of Algorithms Lecture 1 Introduction and Prologue Instructor: Fei Li lifei@cs.gmu.edu with subject: CS483 Office hours: Room 5326, Engineering Building, Thursday 4:30pm - 6:30pm
CS483 Design and Analysis of Algorithms Lecture 1 Introduction and Prologue Instructor: Fei Li lifei@cs.gmu.edu with subject: CS483 Office hours: Room 5326, Engineering Building, Thursday 4:30pm - 6:30pm
Fundamental Algorithms
 Fundamental Algorithms Chapter 2: Sorting Harald Räcke Winter 2015/16 Chapter 2: Sorting, Winter 2015/16 1 Part I Simple Sorts Chapter 2: Sorting, Winter 2015/16 2 The Sorting Problem Definition Sorting
Fundamental Algorithms Chapter 2: Sorting Harald Räcke Winter 2015/16 Chapter 2: Sorting, Winter 2015/16 1 Part I Simple Sorts Chapter 2: Sorting, Winter 2015/16 2 The Sorting Problem Definition Sorting
Reductions, Recursion and Divide and Conquer
 CS/ECE 374: Algorithms & Models of Computation, Fall 2018 Reductions, Recursion and Divide and Conquer Lecture 10 October 2, 2018 Chandra Chekuri (UIUC) CS/ECE 374 1 Fall 2018 1 / 56 Part I Brief Intro
CS/ECE 374: Algorithms & Models of Computation, Fall 2018 Reductions, Recursion and Divide and Conquer Lecture 10 October 2, 2018 Chandra Chekuri (UIUC) CS/ECE 374 1 Fall 2018 1 / 56 Part I Brief Intro
CS 4407 Algorithms Lecture 2: Iterative and Divide and Conquer Algorithms
 CS 4407 Algorithms Lecture 2: Iterative and Divide and Conquer Algorithms Prof. Gregory Provan Department of Computer Science University College Cork 1 Lecture Outline CS 4407, Algorithms Growth Functions
CS 4407 Algorithms Lecture 2: Iterative and Divide and Conquer Algorithms Prof. Gregory Provan Department of Computer Science University College Cork 1 Lecture Outline CS 4407, Algorithms Growth Functions
Divide and conquer. Philip II of Macedon
 Divide and conquer Philip II of Macedon Divide and conquer 1) Divide your problem into subproblems 2) Solve the subproblems recursively, that is, run the same algorithm on the subproblems (when the subproblems
Divide and conquer Philip II of Macedon Divide and conquer 1) Divide your problem into subproblems 2) Solve the subproblems recursively, that is, run the same algorithm on the subproblems (when the subproblems
Chapter 2. Recurrence Relations. Divide and Conquer. Divide and Conquer Strategy. Another Example: Merge Sort. Merge Sort Example. Merge Sort Example
 Recurrence Relations Chapter 2 Divide and Conquer Equation or an inequality that describes a function by its values on smaller inputs. Recurrence relations arise when we analyze the running time of iterative
Recurrence Relations Chapter 2 Divide and Conquer Equation or an inequality that describes a function by its values on smaller inputs. Recurrence relations arise when we analyze the running time of iterative
CS325: Analysis of Algorithms, Fall Midterm
 CS325: Analysis of Algorithms, Fall 2017 Midterm I don t know policy: you may write I don t know and nothing else to answer a question and receive 25 percent of the total points for that problem whereas
CS325: Analysis of Algorithms, Fall 2017 Midterm I don t know policy: you may write I don t know and nothing else to answer a question and receive 25 percent of the total points for that problem whereas
Fast Convolution; Strassen s Method
 Fast Convolution; Strassen s Method 1 Fast Convolution reduction to subquadratic time polynomial evaluation at complex roots of unity interpolation via evaluation at complex roots of unity 2 The Master
Fast Convolution; Strassen s Method 1 Fast Convolution reduction to subquadratic time polynomial evaluation at complex roots of unity interpolation via evaluation at complex roots of unity 2 The Master
Exercise Sheet #1 Solutions, Computer Science, A M. Hallett, K. Smith a k n b k = n b + k. a k n b k c 1 n b k. a k n b.
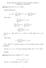 Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Algorithm Analysis Recurrence Relation. Chung-Ang University, Jaesung Lee
 Algorithm Analysis Recurrence Relation Chung-Ang University, Jaesung Lee Recursion 2 Recursion 3 Recursion in Real-world Fibonacci sequence = + Initial conditions: = 0 and = 1. = + = + = + 0, 1, 1, 2,
Algorithm Analysis Recurrence Relation Chung-Ang University, Jaesung Lee Recursion 2 Recursion 3 Recursion in Real-world Fibonacci sequence = + Initial conditions: = 0 and = 1. = + = + = + 0, 1, 1, 2,
CSE 21 Practice Exam for Midterm 2 Fall 2017
 CSE 1 Practice Exam for Midterm Fall 017 These practice problems should help prepare you for the second midterm, which is on monday, November 11 This is longer than the actual exam will be, but good practice
CSE 1 Practice Exam for Midterm Fall 017 These practice problems should help prepare you for the second midterm, which is on monday, November 11 This is longer than the actual exam will be, but good practice
Problem 5. Use mathematical induction to show that when n is an exact power of two, the solution of the recurrence
 A. V. Gerbessiotis CS 610-102 Spring 2014 PS 1 Jan 27, 2014 No points For the remainder of the course Give an algorithm means: describe an algorithm, show that it works as claimed, analyze its worst-case
A. V. Gerbessiotis CS 610-102 Spring 2014 PS 1 Jan 27, 2014 No points For the remainder of the course Give an algorithm means: describe an algorithm, show that it works as claimed, analyze its worst-case
CS 4104 Data and Algorithm Analysis. Recurrence Relations. Modeling Recursive Function Cost. Solving Recurrences. Clifford A. Shaffer.
 Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2010,2017 by Clifford A. Shaffer Data and Algorithm Analysis Title page Data and Algorithm Analysis Clifford A. Shaffer Spring
Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2010,2017 by Clifford A. Shaffer Data and Algorithm Analysis Title page Data and Algorithm Analysis Clifford A. Shaffer Spring
