Computational Complexity - Pseudocode and Recursions
|
|
|
- Beverly Stevens
- 5 years ago
- Views:
Transcription
1 Computational Complexity - Pseudocode and Recursions Nicholas Mainardi 1 Dipartimento di Elettronica e Informazione Politecnico di Milano nicholas.mainardi@polimi.it June 6, Partly Based on Alessandro Barenghi s material, largely enriched with some additional exercises
2 More complexity analysis? Asymptotic complexity assessment In the following slides we will assess the asymptotic complexity of some algorithms using the constant cost criterion This is justified by the fact that all the involved variables are considered to be bounded in size to, at most, a machine word, thus all the atomic operations are effectively O(1) This lesson also tackles the issue of analysing the complexity of algorithms involving recursive function calls
3 Pseudocode Time Complexity - Example 1 P(n) 1 s 0 2 for i 1 to n 3 do j 1 4 while j < n 5 do k 1 6 while k < n 7 do s k 3 k 9 j 2 j The first cycle runs n times The first while loop runs until j < n, and j is doubled each time, that is until 2 h < n h < log 2 (n) The second while loop runs until k < n, and k is triplied each time, that is until 3 h < n h < log 3 (n) Total complexity: n log 2 (n) log 3 (n) = Θ(n log 2 (n))
4 Pseudocode Time Complexity - Example 2 P(n) 1 i 2 2 j 0 3 while i < n 4 do j i i i How many times is the loop executed? i starts from 2 and it is squared at each iteration Th sequence of i values is: 2, 4, 16, 256, The loop body is executed until i < n, that is until 2 2h < n 2 h < log 2 (n) h < log 2 (log 2 (n)) Total time complexity: Θ(log(log(n)))
5 Pseudocode Time Complexity - Example 3 P(n) 1 a 0 2 j 1 3 k 0 4 while j < n 5 do k for i 1 to k 7 do h 2 8 while h < 2 n 9 do a h h h 11 j 2 j The number of iterations of the for loop is dependent on the outer loop it depends on the number of times k is incremented
6 Pseudocode Time Complexity - Example 3 Complexity Estimation in case of Dependent Nested Cycles the outer loop is executed log(n) times, thus k can be incremented up to log(n) At each iteration, the for loop runs k times. Total number of executions of for loop body? log(n) k=1 k = log(n) (log(n)+1) 2 = Θ(log 2 (n)) Each of these executions has another loop This loop is independent from the previous two. How many times does it run? the loop runs until h < 2 n, with h being squared at each iterations, thus it runs until 2 2m < 2 n 2 m < n m < log(n) Total time complexity is Θ(log 3 (n))
7 Pseudocode Time Complexity - Example 4 P(n) 1 sum 0 2 for i 1 to log(n) 3 do j 2 4 while j < 2 n 5 do sum j 2 j The outer loop is executed log(n) times The inner loop is executed until j < 2 n, with j being doubled at each iteration, thus it runs until 2 h < 2 n h < n Total time complexity: Θ(n log(n))
8 Pseudocode Time Complexity - Example 4 Consider this variant: P(n) 1 sum 0 2 for i 1 to log(n) 3 do j 2 4 while j < 2 n 5 do sum sum + f(n) 6 j 2 j where T (f(n)) Θ(log(n)) The number of iterations of the loops are the same as the original version Θ(n log(n)) However, each inner loop body has a logarithmic cost Thus, total time complexity is Θ(n log(n) log(n)) = Θ(n log 2 (n))
9 Pseudocode Time Complexity - Example 4 Another variant: P(n) 1 sum 0 2 for i 1 to log(n) 3 do j 2 4 while j < 2 n 5 do sum sum + f(i) 6 j 2 j where T (f(n)) Θ(log(n)) This time the complexity of the inner loop body is dependent from the outer cycle The total complexity is T (n) = log(n) i=1 n log(i)
10 Pseudocode Time Complexity - Example 4 A bit of math T (n) = log(n) i=1 n log(i) = n log(n) i=1 log(i) = n log( log(n) by applying logarithm properties T (n) = n log( log(n) i=1 i) = n log(log(n)!) Recall the Stirling approximation to get rid fo the factorial: n! = ( n e )n T (n) = n log(log(n)!) = n log(( log(n) e ) log(n) ) i=1 i), Apply logarithm properties: T (n) = n log(( log(n) e ) log(n) ) = n log(n) log( log(n) e ) = n log(n)(log(log(n)) log(e)) = n log(n)(log(log(n)) Θ(1)) = Θ(n log(n) log(log(n)))
11 Computing exponentiations: m n Straightforward implementation We want to compute m n : the following function does so: Exp(n, m) 1 res 1 2 for i 1 to n 3 do res res m 4 return res Complexity? the loop runs exactly n times, thus O(n) Is there a fastest algorithm to compute exponentiation?
12 Way faster exponentiations Another look at the exponent We can rewrite the exponent n as a t = log 2 (n) bit binary number n = (b t 1... b 0 ) Recalling common mathematical properties m n = m (2t 1 b t 1 +2 t 2 b t b 0 ) = m 2t 1 b t 1 m 2t 2 b t 2... m 21 b1 m 20 b 0 We note that m n is actually the product of all the m 2i for which the i-th bit is one All the m 2i values can be obtained by squaring m 2i 1, at the cost of a single multiplication Exploiting this observation we can design an algorithm which computes them and multiplies together only the ones where b i = 1
13 Right-to-Left Square and Multiply Algorithm and Complexity SMExp(n, m) 1 res 1 2 tmp m 3 for i 0 to (t 1) 4 do if n & (1 << i) 0 It is the same as b i = 1 5 then res res tmp 6 tmp tmp tmp 7 return res Complexity? The loop body is run t = log 2 (n) times: O(log(n)), way faster than before!
14 Computing Hamming Weight Straightforward Method HW(n) The Hamming Weight of n is defined as the number of ones in its binary representation 1 tmp n 2 hw 0 3 while tmp > 0 4 do if tmp mod 2 = 1 5 then hw hw tmp tmp 2 7 return hw Complexity? Loop until the result of the repeated integer division by 2 of the input is 0 The loop is run log 2 (n) times, thus O(log(n))
15 Computing HW, Kernighan Style Arithmetic helps Is the previous method the best we can do? No! HWKernighan(n) 1 tmp n 2 hw 0 3 while tmp > 0 4 do hw hw tmp tmp (tmp 1) 6 return hw Line 5 effectively removes only the least significant digit set to 1 of the number in O(k) exploiting the effect of the borrows Thus the loop runs exactly as many times as the Hamming weight of the input, thus Θ(HW (n))
16 Is this a perfect power? Given n, is it a perfect power n = a x, x N \ {0, 1}? Strategy 1: We try all possible bases k, from k = 2 to n How many exponents exp do we need to try? until k exp n exp log k (n) Complexity: n k=2 log k(n) = O( n log(n)) Strategy 2: We try all possible exponents exp, up to log 2 (n) How many bases do we need to try for each exp? until k exp n k exp n At each iteration, we perform an exponentiation O(log(exp)) Complexity: log 2 (n) exp exp=2 n log(exp), which is both O( n log(n) log(log(n))) and Ω( n)
17 Is this a perfect power? A better solution is-n-th-pow(x) 1 for exp 2 to log 2 (n) 2 do k n 2 3 k max n 4 k min 0 5 while k k max 6 do test k exp 7 if test = n 8 then return true 9 if test > n 10 then k max k 11 else k min k 12 k kmax +k min 2 13 return false
18 Is this a perfect power? Complexity The outer for loop runs log 2 (n) 1 times by construction The inner while is slightly more complex to analyze: examine the evolution of the k min and k max variables The viable range for the value of k is cut into a half at each loop body execution, k max retains the upper bound Since the value of k is always an integer (initial value n): log 2 (n) runs are made The main cost of the loop body is the exponentiation: takes log 2 (i) The total complexity is log 2 (n) i=2 log 2 (n) log(i) = log 2 (n) log 2 (n) i=2 log(i) = O(log 2 (n) log(log(n)))
19 Multiple Precision Multiplications The Roman Way Multiplying two n-digit numbers a = (a n 1,..., a 0 ) t, b = (b n 1,..., b 0 ) t represented in base t (think 10, or 2) was a problem in ancient Rome, as they did it like this: Multiply(a, b) 1 res (0 2n 1, 0 2n 2,..., 0 1, 0 0 ) res can be up to 2n digits 2 for i 0 to b 1 3 do res AddWithCarry(res, a) 4 return res The call to AddWithCarry needs to take care of all the possible carries, thus takes O(n). Total complexity? The for loop runs as many times as the size of b: Worst case, b is n-digits in base t, thus b t n : O(nt n )
20 Back to first grade school Multiple Digits Multiplications We were taught to go faster than ancient Romans in first grade school, namely we do : Multiply(a, b) 1 res (0 2n 1, 0 2n 2,..., 0 1, 0 0 ) 2 for i 0 to n 1 3 do intermediate = 0 4 for j 0 to n 1 5 do tmp a j b i 6 intermediate intermediate + (tmp t i+j ) 7 res AddWithCarry(res, intermediate) 8 return res
21 Back to first grade school Time Complexity for Schoolbook Multiplication Note: t i+j can be computed through shifting, the addition in line 6 is at most 2 digits one (takes O(k)). Total complexity? The inner loop runs n times, the loop body is O(k), thus O(n k) = O(n) Each iteration of the outer loop requires O(n) for the inner loop and O(n) for AddWithCarry O(n)complexity The outer loop runs n times each, the loop body is O(n), thus O(n n) = O(n 2 ) Better! Multiple Digits Divisions Similarly: Division with repeated subtractions is O(nt n ). Schoolbook division is O(n 2 )
22 Improving Multiplication Karatsuba s algorithm Karatsubamult(a, b, t) 1 a, b and all operations are in base t 2 if a < t b < t 3 then return a b 4 digit = max(log t (a), log t (b)) 5 m = digit 2 6 high a = a >> m 7 low a = a (high a << m) 8 high b = b >> m 9 low b = b (high b << m) 10 z 0 karatsubamult(low a, low b, t) 11 z 1 karatsubamult(high a + low a, high b + low b, t) 12 z 2 karatsubamult(high a, high b, t) 13 return z 2 << 2m + (z 1 z 2 z 0 ) << m + z 0
23 Improving Multiplication Why Does It Work? a = high a t m + low a and b = high b t m + low b a b = high a t m high b t m + low a high b t m + high a low b t m +low a low b = z 2 t 2m +t m (low a high b +high a low b )+z 0 Now, we show that high a low b + low a high b = z 1 z 2 z 0 : z 1 = (high a +low a ) (high b +low b ) = high a high b +high a low b + low a high b + low a low b = z 2 + high a low b + low a high b + z 0 a b = z 2 t 2m + t m (low a high b + high a low b ) + z 0 = z 2 t 2m + t m (z 1 z 2 z 0 ) + z 0 We can perform the multiplication with 3 multiplications on half digits numbers, plus some shift/additions, until we get a single digit multiplication, which stops the recursion Basically, only single digit multiplications are performed and the results are composed using the equation in line 13
24 Improving Multiplication Complexity Wait: the algorithm is recursive! Recursion always involve sub-problems, which has the same complexity function of the main problem Thus, we can formulate the time complexity as a function of the costs of the sub-problems, defining the so-called recurrence equation How many sub-problems? 3 What size of these sub-problems? n 2 What is the cost of the function without considering the sub-problems? Θ(n), since only shifts and additions are performed Thus, T (n) = 3T ( n 2 ) + Θ(n)
25 Analyzing recursions How to solve recursions? The previous time complexity is also stated in a recurrent fashion: we need to solve the issue There are two main ways to do so: Master s theorem: provided the recurrence fits certain conditions, easy, closed form solutions are available Hypothesize and prove by induction: we obtain an educated guess on the total complexity through partially unrolling the recursion, and subsequently prove that our conjecture is correct by means of mathematical induction
26 Master s Theorem A smart toolbox The master s theorem provides a ready-made toolbox for the complexity analysis of recursions. The recursion complexity must be expressible in this form : T (n) = at ( n b ) + f (n) with a 1, b > 1 Key idea: compare the complexities of n logb(a) (the effect of the recursive calls) and f (n) (the cost of running the function) Hypotheses for the Master s theorem: a must be constant, and greater or equal to one (at least one sub-problem per recursion) f (n) must be added, not subtracted or anything else to at ( n b ) The difference between n log b (a) and f (n) should be polynomial The solutions provided by the MT are split into three cases
27 Master s Theorem Case 1 Case 1 : f (n) = O(n log b(a) ɛ ) for some ɛ > 0 Result : T (n) = Θ(n log b(a) ) Key idea : the recursion dominates the complexity Example : T (n) = 32T ( n 4 ) + n log(n) Compare : O(n log 4 (32) ɛ ) = n log(n) O(n 5 2 ɛ ) = n log(n) ɛ = 1 2 The complexity of the example is Θ(n log 4 (32) ) = Θ(n 5 2 )
28 Master s Theorem Case 2 Case 2 : f (n) = Θ(n log b (a) ) Result : T (n) = Θ(n log b (a) log(n)) Key idea : the weights of the two parts of the sum are the same up to a polynomial term Example: T (n) = T ( n 3 ) + Θ(1) Compare: Θ(1) = Θ(n log 3 (1) )? Yes : Θ(1) = Θ(n 0 ) The complexity of the example is Θ(n log 3(1) log(n)) = Θ(log(n))
29 Master s Theorem Case 3 Case 3 : f (n) = Ω(n log b(a)+ɛ ), ɛ > 0 In this case, for the theorem to hold, we need also to check that : af ( n b ) < cf (n) for some c < 1 Result : T (n) = Θ(f (n)) Key idea : the function call at each recursion step outweights the rest Example T (n) = 2T ( n 4 ) + n log(n) Compare n log(n) = Ω(n log 4 (2)+ɛ ) n log(n) = Ω(n 1 2 +ɛ ) ɛ = 1 2 > 0 Check 2f ( n 4 ) = 2 n 4 log( n 4 ) < cn log(n) for c < 1? 2 n 4 log( n 4 ) = n 2 log(n) n 2 log(4) < n 2 log(n) < cn log(n) for c ( 1 2 ; 1) The complexity of the example is Θ(n log(n))
30 Improving Multiplication Karatsuba Algorithm Let s go back to Karatsuba s recurrence: T (n) = 3T ( n 2 ) + Θ(n) Can we solve it through master theorem? Yes! a = 3, b = 2 and f (n) = Θ(n) Which case? n log b (a) = n log 2 (3). n log 2 (3) ɛ = n log 2 (3) ɛ = 1 ɛ = log 2 (3) 1 > 0, thus it is case 1 of the theorem Therefore, T (n) = Θ(n log b (a) ) = Θ(n log 2 (3) ) = Θ(n )
31 When being a Master is not enough... Alternatives to Master s Theorem Some cases where the MT is not applicable are: 1 T (n) = 2T (n 3) + Θ(log(n)) b 1, the MT needs b > 1 2 T (n) = 3T (log(n)) + 2 n The recursion argument is not polynomial (so, for sure b 1) 3 T (n) = nt (n 2) + Θ(1) a is not constant (a = n in this case) We will now solve them via inductive proofs
32 Solutions Example 1 - Conjecture Let s try expanding a step of the recursion T (n) = 2T (n 3) + Θ(log(n)) T (n) = 2(2T (n 6) + Θ(log(n 3))) + Θ(log(n)) Each recursion step adds a term which is 2 i log(n 3i)) The number of recursive calls is n 3 (remember division by iterated subtraction?) The expanded equation is O( n 3 i=0 2 i log(n 3i)) We thus conjecture that T (n) is O(2 n 3 log(n))
33 Solutions Example 1 - Proof We want to prove that T (n) is O(2 n 3 log(n)), i.e. T (n) c2 n 3 log(n) By induction, assume T (n 3) c2 n 3 3 log(n 3) (this is a reasonable induction hp, as clearly (n 3) < n) Substitute the previous one in the original recurrence equation T (n) = 2T (n 3) + d log(n), yielding T (n) = 2T (n 3) + d log(n) c2 2 n 3 3 log(n 3) + d log(n) Manipulating : T (n) c n 3 log(n 3) + d log(n) As clearly log(n 3) < log(n), we get to: T (n) c2 n 3 log(n) + d log(n) Can we drop d log(n)?
34 Solutions Example 1 - Proof (Continued) We can drop log(n) with a trick: Let s change our thesis to be proven to: T (n) c2 n 3 log(n) bn a O(2 n 3 log(n)) Induction hypothesis becomes: T (n 3) c2 n 3 3 log(n 3) b(n 3) a T (n) = 2T (n 3)+d log(n) 2c2 n 3 3 log(n 3) 2b(n 3) 2a+d log(n) = c2 n 3 log(n 3) 2bn+6b 2a+d log(n) c2 n 3 log(n) 2bn + 6b 2a + dn Now, if d 2b b and 6b 2a a, we get: c2 n 3 log(n) 2bn + dn + 6b 2a c2 n 3 log(n) bn a As a conclusion, T (n) c2 n 3 log(n) bn a, if d 2b b b d and 6b 2a a a 6b
35 Solution Example 1 - Smaller Upper Bound? Let s look at the proof: Do we really exploit the log(n) term multiplied to 2 n 3? Maybe T (n) O(2 n 3 ). Let s try to prove it! Thesis: T (n) c2 n 3 bn a O(2 n 3 ) Induction hypothesis: T (n 3) c2 n 3 3 b(n 3) a T (n) = 2T (n 3) + d log(n) 2c2 n 3 3 2b(n 3) 2a + d log(n) = c2 n 3 2bn+6b 2a+d log(n) c2 n 3 2bn+6b 2a+dn As in the previous proof, eventually: T (n) c2 n 3 2bn + 6b 2a + dn c2 n 3 bn a, if d 2b b b d and 6b 2a a a 6b T (n) O(2 n 3 )!
36 Solutions Example 2 - Conjecture Start by expand a step of T (n) = 3T (log(n)) + 2 n T (n) = 3(3T (log(log(n))) + 2 log(n) ) + 2 n At each recursion step, the added contribution is a term of lower order w.r.t. the ones already present This time we can already stop the analysis now and say that T (n) = O(2 n ) as all other added terms are negligible w.r.t. 2 n Willing to be picky, the number of steps performed by the recursion is the iterated logarithm of n, log (n) We can thus write the Θ( log (n) i=0 2 log i (n) )
37 Solutions Example 2 - Proof Thesis: T (n) c2 n O(2 n ) Induction Hypothesis: T (log(n)) c2 log(n) = cn log(2) cn T (n) = 3T (log(n)) + 2 n 3cn + 2 n 3c2 n + 2 n If 3c + 1 c, we can get to our desired result But 3c + 1 c c 1 2, but c > 0 Let s try another transformation: T (n) 3cn + 2 n c 2 2n + 2 n This is legitimate since there always exists n 0 such that n n 0 ( c 2 2n 3cn) Now, c c c 2, which is ok Hence, we can do: T (n) c 2 2n + 2 n c2 n
38 Solutions Example 3 - Conjecture Again, expand a step of T (n) = nt (n 2) + Θ(1) T (n) = n((n 2)T (n 4) + Θ(1)) + Θ(1) = (n 2 2n)T (n 4) + Θ(n) + Θ(1) = (n 2 2n)((n 4)T (n 6) + Θ(1)) + Θ(n) + Θ(1) = (n 3 6n 2 + 8n)T (n 6) + Θ(n 2 ) + Θ(n) + Θ(1) At every recursion step, a term polynomially greater than the previous is added. The recursion is n 2 steps deep The dominating complexity is the one added at the last step As each step raises the polynomial complexity by one, the final complexity is O(n n 2 )
39 Solutions Example 3 - Proof Again, proof by induction, assume T (n 2) c(n 2) (n 2) 2 Substitute and obtain T (n) = nt (n 2) + Θ(1) n(c(n 2) (n 2) 2 ) + d Manipulate a bit and get T (n) cn(n 2) (n 2) 2 + d Note that cn(n 2) (n 2) 2 < cnn (n 2) 2 = cn n 2 Plug it in the previous inequality and obtain, T (n) cn n 2 + d Change the thesis to get rid of d: T (n) cn n 2 b T (n) cn(n 2) n 2 2 bn + d cn n 2 bn + d cn n 2 2b + d, since bn 2b for n n 0 = 2 If 2b + d b b d, then T (n) cn n 2 2b + d cn n 2 b
40 Naive Sorting Simple idea for a sorting algorithm: Compute the minimum of the array, swap it with the first element of the array, then do the same on the sub-array starting from the second element: Naive Sorting Algorithm SelectionSort(a, start) 1 min a[start] 2 i min start 3 for j start + 1 to Length(a) 4 do if a[j] < min 5 then min a[j] 6 i min j 7 a[i min ] a[start] 8 a[start] min 9 if start < Length(a) 10 then SelectionSort(start + 1)
41 Naive Sorting Complexity: Recurrence Equation The algorithm is recursive Each time a sub-array of size n 1 is considered T (n 1) 1 recursive call Each recursion step scan the sub-array Θ(n) Thus, recurrence equation is T (n) = T (n 1) + Θ(n) Complexity: Determining T (n) Can we employ master theorem? No, since b = 0 Let s make a guess on T (n) How many recursive calls? n Each of them adds to the time complexity n i Thus, T (n) = n 1 i=0 n i = n(n 1) 2 = O(n 2 )
42 Naive Sorting Proof Again, our thesis is T (n) cn 2 Induction hypothesis: T (n 1) c(n 1) 2 T (n) = T (n 1) + kn c(n 1) 2 + kn = cn 2 + c 2cn + kn cn 2 + cn 2cn + kn = cn 2 cn + kn If k c 0 c k, then we got: T (n) cn 2 cn + kn cn 2 Is T (n) O(n log(n))? Now, our thesis is T (n) cn log(n) Induction hypothesis: T (n 1) c(n 1) log(n 1) T (n) c(n 1) log(n 1) + kn cn log(n) + kn Can we get rid of kn?
43 Naive Sorting Let s try the usual trick: T (n) cn log(n) bn Induction hp: T (n 1) c(n 1) log(n 1) b(n 1) T (n) c(n 1) log(n 1) bn+b+kn cn log(n) bn+b+kn To get bn, we need to have k b < b, which holds for k < 0, but k > 0 impossible Idea: we may try to introduce a new linear term hn: T (n) cn log(n) bn + hn + kn + b, for some h > 0. To get bn, we need to have k b + h < b k + h < 0, which has no solution since k, h > 0 Can we avoid getting rid of n 1 and using the term c log(n) to get another linear term? 1 c log(n) cn does not hold for c > 0 2 c log(n) cn is ok, but we would get c + k < 0, which has still no solution
44 Differences on Proofs Consider the following recurrence equations: T (n) = 2T ( n 2 ) + n T (n) = T ( n 2 ) + n Are they O(n)? Equation 1 T (n) 2c n 2 + n cn + n We cannot get rid of n, since c + 1 > c c Indeed, this is the merge sort recurrence, which is Ω(n log(n)) Equation 2 T (n) c n 2 + n = c 2 n + n Now, if we impose c c c 2, we can state n + n cn, thus T (n) cn c 2
45 Induction Proofs: Summing Up Recap of all the Tricks in Proofs Change the thesis to try to get rid of lower order terms T (n) cn becomes T (n) cn b Play with constants Suppose our thesis is T (n) cn, and we got to T (n) c 2 n. We can get to thesis since c 2 c If a term is added, you can replace it with an higher order term and an arbitrary constant (usually we want to decrease the constant factor) T (n) cn + 2 n c 2 2n + 2 n c2 n, for c 2 If a term is subtracted, you can replace it with a lower order term and an arbitrary constant (usually we want to increase the constant factor) T (n) cn 2 bn cn 2 2b
46 Greatest Common Divisor Compute the greatest common divisor between 2 integers a, b Suppose, as a precondition, a b Naive idea: Try all possible integers starting from b to 1 The Algorithm GCD(a, b) 1 for ı b downto 1 2 do if a mod i = 0 b mod i = 0 3 then return i Complexity: the loop runs at most b times, one for each candidate divisor O(b)
47 Greatest Common Divisor A clever solution: Euclidean algorithm! Main idea: gcd(a, b) = gcd(b, a mod b). Since a mod b is less than b, we reduce the size of the numbers, eventually getting to multiples. Euclidean Algorithm EuclideanGCD(a, b) 1 r a mod b 2 n b 3 d b 4 while r 0 5 do d r 6 r n mod d 7 n d 8 return d
48 Greatest Common Divisor Complexity The time complexity is surely dominated by the loop How many times does it run? Different cases: If gcd(a, b) = b, the algorithm does not even get into the loop There may be two steps even if gcd(a, b) is 1 (e.g. gcd(32, 15)) There may be a lot of steps: gcd(21, 13) Let s try to identify the worst case The maximum number of iterations is achieved if the remainder is close to d Turns out that such worst case is when we want to compute gcd(f n+1, f n ), where f n is the n th element of Fibonacci s sequence!
49 Greatest Common Divisor Worst Case Complexity Indeed, f n+1 < 2f n, thus r = f n+1 f n, which is f n 1, that is a Fibonacci number itself, which is quite big Most importantly, the next step of the algorithm will compute gcd(f n, f n 1 ), which still exhibit the same behavior Therefore, we have a sequence of r values, which are the Fibonacci s sums, starting from f n 1 = a b to f 1 = 1 Thus, we have O(n) iterations, but what is n? hint: f n φ n, where φ = , the golden ratio! Indeed, it is easy to prove it by induction: f n = f n 1 + f n 2... Since, b = f n, then n = log φ (b) In conclusion, worst case complexity is O(n) = O(log(b))
Algorithm efficiency analysis
 Algorithm efficiency analysis Mădălina Răschip, Cristian Gaţu Faculty of Computer Science Alexandru Ioan Cuza University of Iaşi, Romania DS 2017/2018 Content Algorithm efficiency analysis Recursive function
Algorithm efficiency analysis Mădălina Răschip, Cristian Gaţu Faculty of Computer Science Alexandru Ioan Cuza University of Iaşi, Romania DS 2017/2018 Content Algorithm efficiency analysis Recursive function
Solving recurrences. Frequently showing up when analysing divide&conquer algorithms or, more generally, recursive algorithms.
 Solving recurrences Frequently showing up when analysing divide&conquer algorithms or, more generally, recursive algorithms Example: Merge-Sort(A, p, r) 1: if p < r then 2: q (p + r)/2 3: Merge-Sort(A,
Solving recurrences Frequently showing up when analysing divide&conquer algorithms or, more generally, recursive algorithms Example: Merge-Sort(A, p, r) 1: if p < r then 2: q (p + r)/2 3: Merge-Sort(A,
CS 161 Summer 2009 Homework #2 Sample Solutions
 CS 161 Summer 2009 Homework #2 Sample Solutions Regrade Policy: If you believe an error has been made in the grading of your homework, you may resubmit it for a regrade. If the error consists of more than
CS 161 Summer 2009 Homework #2 Sample Solutions Regrade Policy: If you believe an error has been made in the grading of your homework, you may resubmit it for a regrade. If the error consists of more than
CS 4104 Data and Algorithm Analysis. Recurrence Relations. Modeling Recursive Function Cost. Solving Recurrences. Clifford A. Shaffer.
 Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2010,2017 by Clifford A. Shaffer Data and Algorithm Analysis Title page Data and Algorithm Analysis Clifford A. Shaffer Spring
Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2010,2017 by Clifford A. Shaffer Data and Algorithm Analysis Title page Data and Algorithm Analysis Clifford A. Shaffer Spring
Algorithms and Their Complexity
 CSCE 222 Discrete Structures for Computing David Kebo Houngninou Algorithms and Their Complexity Chapter 3 Algorithm An algorithm is a finite sequence of steps that solves a problem. Computational complexity
CSCE 222 Discrete Structures for Computing David Kebo Houngninou Algorithms and Their Complexity Chapter 3 Algorithm An algorithm is a finite sequence of steps that solves a problem. Computational complexity
Divide and Conquer. Arash Rafiey. 27 October, 2016
 27 October, 2016 Divide the problem into a number of subproblems Divide the problem into a number of subproblems Conquer the subproblems by solving them recursively or if they are small, there must be
27 October, 2016 Divide the problem into a number of subproblems Divide the problem into a number of subproblems Conquer the subproblems by solving them recursively or if they are small, there must be
CSCI 3110 Assignment 6 Solutions
 CSCI 3110 Assignment 6 Solutions December 5, 2012 2.4 (4 pts) Suppose you are choosing between the following three algorithms: 1. Algorithm A solves problems by dividing them into five subproblems of half
CSCI 3110 Assignment 6 Solutions December 5, 2012 2.4 (4 pts) Suppose you are choosing between the following three algorithms: 1. Algorithm A solves problems by dividing them into five subproblems of half
Introduction to Divide and Conquer
 Introduction to Divide and Conquer Sorting with O(n log n) comparisons and integer multiplication faster than O(n 2 ) Periklis A. Papakonstantinou York University Consider a problem that admits a straightforward
Introduction to Divide and Conquer Sorting with O(n log n) comparisons and integer multiplication faster than O(n 2 ) Periklis A. Papakonstantinou York University Consider a problem that admits a straightforward
Input Decidable Language -- Program Halts on all Input Encoding of Input -- Natural Numbers Encoded in Binary or Decimal, Not Unary
 Complexity Analysis Complexity Theory Input Decidable Language -- Program Halts on all Input Encoding of Input -- Natural Numbers Encoded in Binary or Decimal, Not Unary Output TRUE or FALSE Time and Space
Complexity Analysis Complexity Theory Input Decidable Language -- Program Halts on all Input Encoding of Input -- Natural Numbers Encoded in Binary or Decimal, Not Unary Output TRUE or FALSE Time and Space
CSCI Honor seminar in algorithms Homework 2 Solution
 CSCI 493.55 Honor seminar in algorithms Homework 2 Solution Saad Mneimneh Visiting Professor Hunter College of CUNY Problem 1: Rabin-Karp string matching Consider a binary string s of length n and another
CSCI 493.55 Honor seminar in algorithms Homework 2 Solution Saad Mneimneh Visiting Professor Hunter College of CUNY Problem 1: Rabin-Karp string matching Consider a binary string s of length n and another
CS 577 Introduction to Algorithms: Strassen s Algorithm and the Master Theorem
 CS 577 Introduction to Algorithms: Jin-Yi Cai University of Wisconsin Madison In the last class, we described InsertionSort and showed that its worst-case running time is Θ(n 2 ). Check Figure 2.2 for
CS 577 Introduction to Algorithms: Jin-Yi Cai University of Wisconsin Madison In the last class, we described InsertionSort and showed that its worst-case running time is Θ(n 2 ). Check Figure 2.2 for
Data structures Exercise 1 solution. Question 1. Let s start by writing all the functions in big O notation:
 Data structures Exercise 1 solution Question 1 Let s start by writing all the functions in big O notation: f 1 (n) = 2017 = O(1), f 2 (n) = 2 log 2 n = O(n 2 ), f 3 (n) = 2 n = O(2 n ), f 4 (n) = 1 = O
Data structures Exercise 1 solution Question 1 Let s start by writing all the functions in big O notation: f 1 (n) = 2017 = O(1), f 2 (n) = 2 log 2 n = O(n 2 ), f 3 (n) = 2 n = O(2 n ), f 4 (n) = 1 = O
The maximum-subarray problem. Given an array of integers, find a contiguous subarray with the maximum sum. Very naïve algorithm:
 The maximum-subarray problem Given an array of integers, find a contiguous subarray with the maximum sum. Very naïve algorithm: Brute force algorithm: At best, θ(n 2 ) time complexity 129 Can we do divide
The maximum-subarray problem Given an array of integers, find a contiguous subarray with the maximum sum. Very naïve algorithm: Brute force algorithm: At best, θ(n 2 ) time complexity 129 Can we do divide
CDM. Recurrences and Fibonacci. 20-fibonacci 2017/12/15 23:16. Terminology 4. Recurrence Equations 3. Solution and Asymptotics 6.
 CDM Recurrences and Fibonacci 1 Recurrence Equations Klaus Sutner Carnegie Mellon University Second Order 20-fibonacci 2017/12/15 23:16 The Fibonacci Monoid Recurrence Equations 3 Terminology 4 We can
CDM Recurrences and Fibonacci 1 Recurrence Equations Klaus Sutner Carnegie Mellon University Second Order 20-fibonacci 2017/12/15 23:16 The Fibonacci Monoid Recurrence Equations 3 Terminology 4 We can
COMP Analysis of Algorithms & Data Structures
 COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 4 - Jan. 10, 2018 CLRS 1.1, 1.2, 2.2, 3.1, 4.3, 4.5 University of Manitoba Picture is from the cover of the textbook CLRS. 1 /
COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 4 - Jan. 10, 2018 CLRS 1.1, 1.2, 2.2, 3.1, 4.3, 4.5 University of Manitoba Picture is from the cover of the textbook CLRS. 1 /
CSC236 Week 4. Larry Zhang
 CSC236 Week 4 Larry Zhang 1 Announcements PS2 due on Friday This week s tutorial: Exercises with big-oh PS1 feedback People generally did well Writing style need to be improved. This time the TAs are lenient,
CSC236 Week 4 Larry Zhang 1 Announcements PS2 due on Friday This week s tutorial: Exercises with big-oh PS1 feedback People generally did well Writing style need to be improved. This time the TAs are lenient,
Solutions. Problem 1: Suppose a polynomial in n of degree d has the form
 Assignment 1 1. Problem 3-1 on p. 57 2. Problem 3-2 on p. 58 3. Problem 4-5 on p. 86 4. Problem 6-1 on p. 142 5. Problem 7-4 on p. 162 6. Prove correctness (including halting) of SelectionSort (use loop
Assignment 1 1. Problem 3-1 on p. 57 2. Problem 3-2 on p. 58 3. Problem 4-5 on p. 86 4. Problem 6-1 on p. 142 5. Problem 7-4 on p. 162 6. Prove correctness (including halting) of SelectionSort (use loop
5 + 9(10) + 3(100) + 0(1000) + 2(10000) =
 Chapter 5 Analyzing Algorithms So far we have been proving statements about databases, mathematics and arithmetic, or sequences of numbers. Though these types of statements are common in computer science,
Chapter 5 Analyzing Algorithms So far we have been proving statements about databases, mathematics and arithmetic, or sequences of numbers. Though these types of statements are common in computer science,
3. Algorithms. What matters? How fast do we solve the problem? How much computer resource do we need?
 3. Algorithms We will study algorithms to solve many different types of problems such as finding the largest of a sequence of numbers sorting a sequence of numbers finding the shortest path between two
3. Algorithms We will study algorithms to solve many different types of problems such as finding the largest of a sequence of numbers sorting a sequence of numbers finding the shortest path between two
Chapter Summary. Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms
 1 Chapter Summary Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms 2 Section 5.1 3 Section Summary Mathematical Induction Examples of
1 Chapter Summary Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms 2 Section 5.1 3 Section Summary Mathematical Induction Examples of
Data Structures and Algorithms Chapter 2
 1 Data Structures and Algorithms Chapter 2 Werner Nutt 2 Acknowledgments The course follows the book Introduction to Algorithms, by Cormen, Leiserson, Rivest and Stein, MIT Press [CLRST]. Many examples
1 Data Structures and Algorithms Chapter 2 Werner Nutt 2 Acknowledgments The course follows the book Introduction to Algorithms, by Cormen, Leiserson, Rivest and Stein, MIT Press [CLRST]. Many examples
COMP Analysis of Algorithms & Data Structures
 COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 4 - Jan. 14, 2019 CLRS 1.1, 1.2, 2.2, 3.1, 4.3, 4.5 University of Manitoba Picture is from the cover of the textbook CLRS. COMP
COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 4 - Jan. 14, 2019 CLRS 1.1, 1.2, 2.2, 3.1, 4.3, 4.5 University of Manitoba Picture is from the cover of the textbook CLRS. COMP
CDM. Recurrences and Fibonacci
 CDM Recurrences and Fibonacci Klaus Sutner Carnegie Mellon University 20-fibonacci 2017/12/15 23:16 1 Recurrence Equations Second Order The Fibonacci Monoid Recurrence Equations 3 We can define a sequence
CDM Recurrences and Fibonacci Klaus Sutner Carnegie Mellon University 20-fibonacci 2017/12/15 23:16 1 Recurrence Equations Second Order The Fibonacci Monoid Recurrence Equations 3 We can define a sequence
Objective. - mathematical induction, recursive definitions - arithmetic manipulations, series, products
 Recurrences Objective running time as recursive function solve recurrence for order of growth method: substitution method: iteration/recursion tree method: MASTER method prerequisite: - mathematical induction,
Recurrences Objective running time as recursive function solve recurrence for order of growth method: substitution method: iteration/recursion tree method: MASTER method prerequisite: - mathematical induction,
Analysis of Algorithms - Using Asymptotic Bounds -
 Analysis of Algorithms - Using Asymptotic Bounds - Andreas Ermedahl MRTC (Mälardalens Real-Time Research Center) andreas.ermedahl@mdh.se Autumn 004 Rehersal: Asymptotic bounds Gives running time bounds
Analysis of Algorithms - Using Asymptotic Bounds - Andreas Ermedahl MRTC (Mälardalens Real-Time Research Center) andreas.ermedahl@mdh.se Autumn 004 Rehersal: Asymptotic bounds Gives running time bounds
Divide and Conquer. Andreas Klappenecker. [based on slides by Prof. Welch]
![Divide and Conquer. Andreas Klappenecker. [based on slides by Prof. Welch] Divide and Conquer. Andreas Klappenecker. [based on slides by Prof. Welch]](/thumbs/84/89083836.jpg) Divide and Conquer Andreas Klappenecker [based on slides by Prof. Welch] Divide and Conquer Paradigm An important general technique for designing algorithms: divide problem into subproblems recursively
Divide and Conquer Andreas Klappenecker [based on slides by Prof. Welch] Divide and Conquer Paradigm An important general technique for designing algorithms: divide problem into subproblems recursively
CS 310 Advanced Data Structures and Algorithms
 CS 310 Advanced Data Structures and Algorithms Runtime Analysis May 31, 2017 Tong Wang UMass Boston CS 310 May 31, 2017 1 / 37 Topics Weiss chapter 5 What is algorithm analysis Big O, big, big notations
CS 310 Advanced Data Structures and Algorithms Runtime Analysis May 31, 2017 Tong Wang UMass Boston CS 310 May 31, 2017 1 / 37 Topics Weiss chapter 5 What is algorithm analysis Big O, big, big notations
A design paradigm. Divide and conquer: (When) does decomposing a problem into smaller parts help? 09/09/ EECS 3101
 A design paradigm Divide and conquer: (When) does decomposing a problem into smaller parts help? 09/09/17 112 Multiplying complex numbers (from Jeff Edmonds slides) INPUT: Two pairs of integers, (a,b),
A design paradigm Divide and conquer: (When) does decomposing a problem into smaller parts help? 09/09/17 112 Multiplying complex numbers (from Jeff Edmonds slides) INPUT: Two pairs of integers, (a,b),
Induction and Recursion
 . All rights reserved. Authorized only for instructor use in the classroom. No reproduction or further distribution permitted without the prior written consent of McGraw-Hill Education. Induction and Recursion
. All rights reserved. Authorized only for instructor use in the classroom. No reproduction or further distribution permitted without the prior written consent of McGraw-Hill Education. Induction and Recursion
CS383, Algorithms Spring 2009 HW1 Solutions
 Prof. Sergio A. Alvarez http://www.cs.bc.edu/ alvarez/ 21 Campanella Way, room 569 alvarez@cs.bc.edu Computer Science Department voice: (617) 552-4333 Boston College fax: (617) 552-6790 Chestnut Hill,
Prof. Sergio A. Alvarez http://www.cs.bc.edu/ alvarez/ 21 Campanella Way, room 569 alvarez@cs.bc.edu Computer Science Department voice: (617) 552-4333 Boston College fax: (617) 552-6790 Chestnut Hill,
Algorithm Analysis Recurrence Relation. Chung-Ang University, Jaesung Lee
 Algorithm Analysis Recurrence Relation Chung-Ang University, Jaesung Lee Recursion 2 Recursion 3 Recursion in Real-world Fibonacci sequence = + Initial conditions: = 0 and = 1. = + = + = + 0, 1, 1, 2,
Algorithm Analysis Recurrence Relation Chung-Ang University, Jaesung Lee Recursion 2 Recursion 3 Recursion in Real-world Fibonacci sequence = + Initial conditions: = 0 and = 1. = + = + = + 0, 1, 1, 2,
Lecture 2. Fundamentals of the Analysis of Algorithm Efficiency
 Lecture 2 Fundamentals of the Analysis of Algorithm Efficiency 1 Lecture Contents 1. Analysis Framework 2. Asymptotic Notations and Basic Efficiency Classes 3. Mathematical Analysis of Nonrecursive Algorithms
Lecture 2 Fundamentals of the Analysis of Algorithm Efficiency 1 Lecture Contents 1. Analysis Framework 2. Asymptotic Notations and Basic Efficiency Classes 3. Mathematical Analysis of Nonrecursive Algorithms
Ch01. Analysis of Algorithms
 Ch01. Analysis of Algorithms Input Algorithm Output Acknowledgement: Parts of slides in this presentation come from the materials accompanying the textbook Algorithm Design and Applications, by M. T. Goodrich
Ch01. Analysis of Algorithms Input Algorithm Output Acknowledgement: Parts of slides in this presentation come from the materials accompanying the textbook Algorithm Design and Applications, by M. T. Goodrich
When we use asymptotic notation within an expression, the asymptotic notation is shorthand for an unspecified function satisfying the relation:
 CS 124 Section #1 Big-Oh, the Master Theorem, and MergeSort 1/29/2018 1 Big-Oh Notation 1.1 Definition Big-Oh notation is a way to describe the rate of growth of functions. In CS, we use it to describe
CS 124 Section #1 Big-Oh, the Master Theorem, and MergeSort 1/29/2018 1 Big-Oh Notation 1.1 Definition Big-Oh notation is a way to describe the rate of growth of functions. In CS, we use it to describe
Grade 11/12 Math Circles Fall Nov. 5 Recurrences, Part 2
 1 Faculty of Mathematics Waterloo, Ontario Centre for Education in Mathematics and Computing Grade 11/12 Math Circles Fall 2014 - Nov. 5 Recurrences, Part 2 Running time of algorithms In computer science,
1 Faculty of Mathematics Waterloo, Ontario Centre for Education in Mathematics and Computing Grade 11/12 Math Circles Fall 2014 - Nov. 5 Recurrences, Part 2 Running time of algorithms In computer science,
Data Structures and Algorithms. Asymptotic notation
 Data Structures and Algorithms Asymptotic notation Estimating Running Time Algorithm arraymax executes 7n 1 primitive operations in the worst case. Define: a = Time taken by the fastest primitive operation
Data Structures and Algorithms Asymptotic notation Estimating Running Time Algorithm arraymax executes 7n 1 primitive operations in the worst case. Define: a = Time taken by the fastest primitive operation
Module 1: Analyzing the Efficiency of Algorithms
 Module 1: Analyzing the Efficiency of Algorithms Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu What is an Algorithm?
Module 1: Analyzing the Efficiency of Algorithms Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu What is an Algorithm?
Ch 01. Analysis of Algorithms
 Ch 01. Analysis of Algorithms Input Algorithm Output Acknowledgement: Parts of slides in this presentation come from the materials accompanying the textbook Algorithm Design and Applications, by M. T.
Ch 01. Analysis of Algorithms Input Algorithm Output Acknowledgement: Parts of slides in this presentation come from the materials accompanying the textbook Algorithm Design and Applications, by M. T.
CS Non-recursive and Recursive Algorithm Analysis
 CS483-04 Non-recursive and Recursive Algorithm Analysis Instructor: Fei Li Room 443 ST II Office hours: Tue. & Thur. 4:30pm - 5:30pm or by appointments lifei@cs.gmu.edu with subject: CS483 http://www.cs.gmu.edu/
CS483-04 Non-recursive and Recursive Algorithm Analysis Instructor: Fei Li Room 443 ST II Office hours: Tue. & Thur. 4:30pm - 5:30pm or by appointments lifei@cs.gmu.edu with subject: CS483 http://www.cs.gmu.edu/
Divide and Conquer. CSE21 Winter 2017, Day 9 (B00), Day 6 (A00) January 30,
 Divide and Conquer CSE21 Winter 2017, Day 9 (B00), Day 6 (A00) January 30, 2017 http://vlsicad.ucsd.edu/courses/cse21-w17 Merging sorted lists: WHAT Given two sorted lists a 1 a 2 a 3 a k b 1 b 2 b 3 b
Divide and Conquer CSE21 Winter 2017, Day 9 (B00), Day 6 (A00) January 30, 2017 http://vlsicad.ucsd.edu/courses/cse21-w17 Merging sorted lists: WHAT Given two sorted lists a 1 a 2 a 3 a k b 1 b 2 b 3 b
Induction and recursion. Chapter 5
 Induction and recursion Chapter 5 Chapter Summary Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms Mathematical Induction Section 5.1
Induction and recursion Chapter 5 Chapter Summary Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms Mathematical Induction Section 5.1
Asymptotic Analysis and Recurrences
 Appendix A Asymptotic Analysis and Recurrences A.1 Overview We discuss the notion of asymptotic analysis and introduce O, Ω, Θ, and o notation. We then turn to the topic of recurrences, discussing several
Appendix A Asymptotic Analysis and Recurrences A.1 Overview We discuss the notion of asymptotic analysis and introduce O, Ω, Θ, and o notation. We then turn to the topic of recurrences, discussing several
Math 2602 Finite and Linear Math Fall 14. Homework 8: Core solutions
 Math 2602 Finite and Linear Math Fall 14 Homework 8: Core solutions Review exercises for Chapter 5 page 183 problems 25, 26a-26b, 29. Section 8.1 on page 252 problems 8, 9, 10, 13. Section 8.2 on page
Math 2602 Finite and Linear Math Fall 14 Homework 8: Core solutions Review exercises for Chapter 5 page 183 problems 25, 26a-26b, 29. Section 8.1 on page 252 problems 8, 9, 10, 13. Section 8.2 on page
Lecture 1: Asymptotics, Recurrences, Elementary Sorting
 Lecture 1: Asymptotics, Recurrences, Elementary Sorting Instructor: Outline 1 Introduction to Asymptotic Analysis Rate of growth of functions Comparing and bounding functions: O, Θ, Ω Specifying running
Lecture 1: Asymptotics, Recurrences, Elementary Sorting Instructor: Outline 1 Introduction to Asymptotic Analysis Rate of growth of functions Comparing and bounding functions: O, Θ, Ω Specifying running
Algorithms Design & Analysis. Analysis of Algorithm
 Algorithms Design & Analysis Analysis of Algorithm Review Internship Stable Matching Algorithm 2 Outline Time complexity Computation model Asymptotic notions Recurrence Master theorem 3 The problem of
Algorithms Design & Analysis Analysis of Algorithm Review Internship Stable Matching Algorithm 2 Outline Time complexity Computation model Asymptotic notions Recurrence Master theorem 3 The problem of
Chapter 2. Recurrence Relations. Divide and Conquer. Divide and Conquer Strategy. Another Example: Merge Sort. Merge Sort Example. Merge Sort Example
 Recurrence Relations Chapter 2 Divide and Conquer Equation or an inequality that describes a function by its values on smaller inputs. Recurrence relations arise when we analyze the running time of iterative
Recurrence Relations Chapter 2 Divide and Conquer Equation or an inequality that describes a function by its values on smaller inputs. Recurrence relations arise when we analyze the running time of iterative
The Time Complexity of an Algorithm
 Analysis of Algorithms The Time Complexity of an Algorithm Specifies how the running time depends on the size of the input. Purpose To estimate how long a program will run. To estimate the largest input
Analysis of Algorithms The Time Complexity of an Algorithm Specifies how the running time depends on the size of the input. Purpose To estimate how long a program will run. To estimate the largest input
Topic 17. Analysis of Algorithms
 Topic 17 Analysis of Algorithms Analysis of Algorithms- Review Efficiency of an algorithm can be measured in terms of : Time complexity: a measure of the amount of time required to execute an algorithm
Topic 17 Analysis of Algorithms Analysis of Algorithms- Review Efficiency of an algorithm can be measured in terms of : Time complexity: a measure of the amount of time required to execute an algorithm
CS173 Running Time and Big-O. Tandy Warnow
 CS173 Running Time and Big-O Tandy Warnow CS 173 Running Times and Big-O analysis Tandy Warnow Today s material We will cover: Running time analysis Review of running time analysis of Bubblesort Review
CS173 Running Time and Big-O Tandy Warnow CS 173 Running Times and Big-O analysis Tandy Warnow Today s material We will cover: Running time analysis Review of running time analysis of Bubblesort Review
Computational Complexity. This lecture. Notes. Lecture 02 - Basic Complexity Analysis. Tom Kelsey & Susmit Sarkar. Notes
 Computational Complexity Lecture 02 - Basic Complexity Analysis Tom Kelsey & Susmit Sarkar School of Computer Science University of St Andrews http://www.cs.st-andrews.ac.uk/~tom/ twk@st-andrews.ac.uk
Computational Complexity Lecture 02 - Basic Complexity Analysis Tom Kelsey & Susmit Sarkar School of Computer Science University of St Andrews http://www.cs.st-andrews.ac.uk/~tom/ twk@st-andrews.ac.uk
COL106: Data Structures and Algorithms (IIT Delhi, Semester-II )
 1 Solve the following recurrence relations giving a Θ bound for each of the cases 1 : (a) T (n) = 2T (n/3) + 1; T (1) = 1 (Assume n is a power of 3) (b) T (n) = 5T (n/4) + n; T (1) = 1 (Assume n is a power
1 Solve the following recurrence relations giving a Θ bound for each of the cases 1 : (a) T (n) = 2T (n/3) + 1; T (1) = 1 (Assume n is a power of 3) (b) T (n) = 5T (n/4) + n; T (1) = 1 (Assume n is a power
Divide and Conquer. Andreas Klappenecker
 Divide and Conquer Andreas Klappenecker The Divide and Conquer Paradigm The divide and conquer paradigm is important general technique for designing algorithms. In general, it follows the steps: - divide
Divide and Conquer Andreas Klappenecker The Divide and Conquer Paradigm The divide and conquer paradigm is important general technique for designing algorithms. In general, it follows the steps: - divide
Arithmetic Algorithms, Part 1
 Arithmetic Algorithms, Part 1 DPV Chapter 1 Jim Royer EECS January 18, 2019 Royer Arithmetic Algorithms, Part 1 1/ 15 Multiplication à la Français function multiply(a, b) // input: two n-bit integers a
Arithmetic Algorithms, Part 1 DPV Chapter 1 Jim Royer EECS January 18, 2019 Royer Arithmetic Algorithms, Part 1 1/ 15 Multiplication à la Français function multiply(a, b) // input: two n-bit integers a
Asymptotic Analysis Cont'd
 Cont'd Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Announcements We have class this Wednesday, Jan 18 at 12:30 That is, we have two sessions this Wednesday: at
Cont'd Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Announcements We have class this Wednesday, Jan 18 at 12:30 That is, we have two sessions this Wednesday: at
Discrete Mathematics and Probability Theory Summer 2014 James Cook Note 5
 CS 70 Discrete Mathematics and Probability Theory Summer 2014 James Cook Note 5 Modular Arithmetic In several settings, such as error-correcting codes and cryptography, we sometimes wish to work over a
CS 70 Discrete Mathematics and Probability Theory Summer 2014 James Cook Note 5 Modular Arithmetic In several settings, such as error-correcting codes and cryptography, we sometimes wish to work over a
Growth of Functions (CLRS 2.3,3)
 Growth of Functions (CLRS 2.3,3) 1 Review Last time we discussed running time of algorithms and introduced the RAM model of computation. Best-case running time: the shortest running time for any input
Growth of Functions (CLRS 2.3,3) 1 Review Last time we discussed running time of algorithms and introduced the RAM model of computation. Best-case running time: the shortest running time for any input
The Time Complexity of an Algorithm
 CSE 3101Z Design and Analysis of Algorithms The Time Complexity of an Algorithm Specifies how the running time depends on the size of the input. Purpose To estimate how long a program will run. To estimate
CSE 3101Z Design and Analysis of Algorithms The Time Complexity of an Algorithm Specifies how the running time depends on the size of the input. Purpose To estimate how long a program will run. To estimate
Exercise Sheet #1 Solutions, Computer Science, A M. Hallett, K. Smith a k n b k = n b + k. a k n b k c 1 n b k. a k n b.
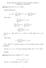 Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
1 Substitution method
 Recurrence Relations we have discussed asymptotic analysis of algorithms and various properties associated with asymptotic notation. As many algorithms are recursive in nature, it is natural to analyze
Recurrence Relations we have discussed asymptotic analysis of algorithms and various properties associated with asymptotic notation. As many algorithms are recursive in nature, it is natural to analyze
CIS 121. Analysis of Algorithms & Computational Complexity. Slides based on materials provided by Mary Wootters (Stanford University)
 CIS 121 Analysis of Algorithms & Computational Complexity Slides based on materials provided by Mary Wootters (Stanford University) Today Sorting: InsertionSort vs MergeSort Analyzing the correctness of
CIS 121 Analysis of Algorithms & Computational Complexity Slides based on materials provided by Mary Wootters (Stanford University) Today Sorting: InsertionSort vs MergeSort Analyzing the correctness of
Notes on arithmetic. 1. Representation in base B
 Notes on arithmetic The Babylonians that is to say, the people that inhabited what is now southern Iraq for reasons not entirely clear to us, ued base 60 in scientific calculation. This offers us an excuse
Notes on arithmetic The Babylonians that is to say, the people that inhabited what is now southern Iraq for reasons not entirely clear to us, ued base 60 in scientific calculation. This offers us an excuse
8 Primes and Modular Arithmetic
 8 Primes and Modular Arithmetic 8.1 Primes and Factors Over two millennia ago already, people all over the world were considering the properties of numbers. One of the simplest concepts is prime numbers.
8 Primes and Modular Arithmetic 8.1 Primes and Factors Over two millennia ago already, people all over the world were considering the properties of numbers. One of the simplest concepts is prime numbers.
Practical Session #3 - Recursions
 Practical Session #3 - Recursions Substitution method Guess the form of the solution and prove it by induction Iteration Method Convert the recurrence into a summation and solve it Tightly bound a recurrence
Practical Session #3 - Recursions Substitution method Guess the form of the solution and prove it by induction Iteration Method Convert the recurrence into a summation and solve it Tightly bound a recurrence
CSE373: Data Structures and Algorithms Lecture 3: Math Review; Algorithm Analysis. Catie Baker Spring 2015
 CSE373: Data Structures and Algorithms Lecture 3: Math Review; Algorithm Analysis Catie Baker Spring 2015 Today Registration should be done. Homework 1 due 11:59pm next Wednesday, April 8 th. Review math
CSE373: Data Structures and Algorithms Lecture 3: Math Review; Algorithm Analysis Catie Baker Spring 2015 Today Registration should be done. Homework 1 due 11:59pm next Wednesday, April 8 th. Review math
b + O(n d ) where a 1, b > 1, then O(n d log n) if a = b d d ) if a < b d O(n log b a ) if a > b d
 CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
CSE 417: Algorithms and Computational Complexity
 CSE 417: Algorithms and Computational Complexity Lecture 2: Analysis Larry Ruzzo 1 Why big-o: measuring algorithm efficiency outline What s big-o: definition and related concepts Reasoning with big-o:
CSE 417: Algorithms and Computational Complexity Lecture 2: Analysis Larry Ruzzo 1 Why big-o: measuring algorithm efficiency outline What s big-o: definition and related concepts Reasoning with big-o:
A SUMMARY OF RECURSION SOLVING TECHNIQUES
 A SUMMARY OF RECURSION SOLVING TECHNIQUES KIMMO ERIKSSON, KTH These notes are meant to be a complement to the material on recursion solving techniques in the textbook Discrete Mathematics by Biggs. In
A SUMMARY OF RECURSION SOLVING TECHNIQUES KIMMO ERIKSSON, KTH These notes are meant to be a complement to the material on recursion solving techniques in the textbook Discrete Mathematics by Biggs. In
What is Performance Analysis?
 1.2 Basic Concepts What is Performance Analysis? Performance Analysis Space Complexity: - the amount of memory space used by the algorithm Time Complexity - the amount of computing time used by the algorithm
1.2 Basic Concepts What is Performance Analysis? Performance Analysis Space Complexity: - the amount of memory space used by the algorithm Time Complexity - the amount of computing time used by the algorithm
Intermediate Math Circles February 29, 2012 Linear Diophantine Equations I
 Intermediate Math Circles February 29, 2012 Linear Diophantine Equations I Diophantine equations are equations intended to be solved in the integers. We re going to focus on Linear Diophantine Equations.
Intermediate Math Circles February 29, 2012 Linear Diophantine Equations I Diophantine equations are equations intended to be solved in the integers. We re going to focus on Linear Diophantine Equations.
Design and Analysis of Algorithms
 CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 4: Divide and Conquer (I) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ Divide and Conquer ( DQ ) First paradigm or framework DQ(S)
CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 4: Divide and Conquer (I) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ Divide and Conquer ( DQ ) First paradigm or framework DQ(S)
Asymptotic Analysis 1
 Asymptotic Analysis 1 Last week, we discussed how to present algorithms using pseudocode. For example, we looked at an algorithm for singing the annoying song 99 Bottles of Beer on the Wall for arbitrary
Asymptotic Analysis 1 Last week, we discussed how to present algorithms using pseudocode. For example, we looked at an algorithm for singing the annoying song 99 Bottles of Beer on the Wall for arbitrary
Big , and Definition Definition
 Big O, Ω, and Θ Big-O gives us only a one-way comparison; if f is O(g) then g eventually is bigger than f from that point on, but in fact f could be very small in comparison. Example; 3n is O(2 2n ). We
Big O, Ω, and Θ Big-O gives us only a one-way comparison; if f is O(g) then g eventually is bigger than f from that point on, but in fact f could be very small in comparison. Example; 3n is O(2 2n ). We
Intermediate Math Circles February 26, 2014 Diophantine Equations I
 Intermediate Math Circles February 26, 2014 Diophantine Equations I 1. An introduction to Diophantine equations A Diophantine equation is a polynomial equation that is intended to be solved over the integers.
Intermediate Math Circles February 26, 2014 Diophantine Equations I 1. An introduction to Diophantine equations A Diophantine equation is a polynomial equation that is intended to be solved over the integers.
Copyright 2000, Kevin Wayne 1
 Algorithm runtime analysis and computational tractability Time Complexity of an Algorithm How do we measure the complexity (time, space requirements) of an algorithm. 1 microsecond? Units of time As soon
Algorithm runtime analysis and computational tractability Time Complexity of an Algorithm How do we measure the complexity (time, space requirements) of an algorithm. 1 microsecond? Units of time As soon
Introduction to Algorithms 6.046J/18.401J/SMA5503
 Introduction to Algorithms 6.046J/8.40J/SMA5503 Lecture 3 Prof. Piotr Indyk The divide-and-conquer design paradigm. Divide the problem (instance) into subproblems. 2. Conquer the subproblems by solving
Introduction to Algorithms 6.046J/8.40J/SMA5503 Lecture 3 Prof. Piotr Indyk The divide-and-conquer design paradigm. Divide the problem (instance) into subproblems. 2. Conquer the subproblems by solving
Math 391: Midterm 1.0 Spring 2016
 Math 391: Midterm 1.0 Spring 2016 James Skon skonjp@kenyon.edu Test date: October 5 Submission Instructions: Give all your assumptions. Show all your work. Be as complete as possible. Grading Problem 1
Math 391: Midterm 1.0 Spring 2016 James Skon skonjp@kenyon.edu Test date: October 5 Submission Instructions: Give all your assumptions. Show all your work. Be as complete as possible. Grading Problem 1
Data Structures and Algorithms Chapter 3
 1 Data Structures and Algorithms Chapter 3 Werner Nutt 2 Acknowledgments The course follows the book Introduction to Algorithms, by Cormen, Leiserson, Rivest and Stein, MIT Press [CLRST]. Many examples
1 Data Structures and Algorithms Chapter 3 Werner Nutt 2 Acknowledgments The course follows the book Introduction to Algorithms, by Cormen, Leiserson, Rivest and Stein, MIT Press [CLRST]. Many examples
Remainders. We learned how to multiply and divide in elementary
 Remainders We learned how to multiply and divide in elementary school. As adults we perform division mostly by pressing the key on a calculator. This key supplies the quotient. In numerical analysis and
Remainders We learned how to multiply and divide in elementary school. As adults we perform division mostly by pressing the key on a calculator. This key supplies the quotient. In numerical analysis and
PUTNAM TRAINING NUMBER THEORY. Exercises 1. Show that the sum of two consecutive primes is never twice a prime.
 PUTNAM TRAINING NUMBER THEORY (Last updated: December 11, 2017) Remark. This is a list of exercises on Number Theory. Miguel A. Lerma Exercises 1. Show that the sum of two consecutive primes is never twice
PUTNAM TRAINING NUMBER THEORY (Last updated: December 11, 2017) Remark. This is a list of exercises on Number Theory. Miguel A. Lerma Exercises 1. Show that the sum of two consecutive primes is never twice
Methods for solving recurrences
 Methods for solving recurrences Analyzing the complexity of mergesort The merge function Consider the following implementation: 1 int merge ( int v1, int n1, int v, int n ) { 3 int r = malloc ( ( n1+n
Methods for solving recurrences Analyzing the complexity of mergesort The merge function Consider the following implementation: 1 int merge ( int v1, int n1, int v, int n ) { 3 int r = malloc ( ( n1+n
Algorithm Design CS 515 Fall 2015 Sample Final Exam Solutions
 Algorithm Design CS 515 Fall 2015 Sample Final Exam Solutions Copyright c 2015 Andrew Klapper. All rights reserved. 1. For the functions satisfying the following three recurrences, determine which is the
Algorithm Design CS 515 Fall 2015 Sample Final Exam Solutions Copyright c 2015 Andrew Klapper. All rights reserved. 1. For the functions satisfying the following three recurrences, determine which is the
Lecture 3. Big-O notation, more recurrences!!
 Lecture 3 Big-O notation, more recurrences!! Announcements! HW1 is posted! (Due Friday) See Piazza for a list of HW clarifications First recitation section was this morning, there s another tomorrow (same
Lecture 3 Big-O notation, more recurrences!! Announcements! HW1 is posted! (Due Friday) See Piazza for a list of HW clarifications First recitation section was this morning, there s another tomorrow (same
Announcements. CSE332: Data Abstractions Lecture 2: Math Review; Algorithm Analysis. Today. Mathematical induction. Dan Grossman Spring 2010
 Announcements CSE332: Data Abstractions Lecture 2: Math Review; Algorithm Analysis Dan Grossman Spring 2010 Project 1 posted Section materials on using Eclipse will be very useful if you have never used
Announcements CSE332: Data Abstractions Lecture 2: Math Review; Algorithm Analysis Dan Grossman Spring 2010 Project 1 posted Section materials on using Eclipse will be very useful if you have never used
CSE 421 Algorithms: Divide and Conquer
 CSE 42 Algorithms: Divide and Conquer Larry Ruzzo Thanks to Richard Anderson, Paul Beame, Kevin Wayne for some slides Outline: General Idea algorithm design paradigms: divide and conquer Review of Merge
CSE 42 Algorithms: Divide and Conquer Larry Ruzzo Thanks to Richard Anderson, Paul Beame, Kevin Wayne for some slides Outline: General Idea algorithm design paradigms: divide and conquer Review of Merge
Asymptotic Notation. such that t(n) cf(n) for all n n 0. for some positive real constant c and integer threshold n 0
 Asymptotic Notation Asymptotic notation deals with the behaviour of a function in the limit, that is, for sufficiently large values of its parameter. Often, when analysing the run time of an algorithm,
Asymptotic Notation Asymptotic notation deals with the behaviour of a function in the limit, that is, for sufficiently large values of its parameter. Often, when analysing the run time of an algorithm,
Module 1: Analyzing the Efficiency of Algorithms
 Module 1: Analyzing the Efficiency of Algorithms Dr. Natarajan Meghanathan Associate Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Based
Module 1: Analyzing the Efficiency of Algorithms Dr. Natarajan Meghanathan Associate Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Based
Algorithms CMSC Homework set #1 due January 14, 2015
 Algorithms CMSC-27200 http://alg15.cs.uchicago.edu Homework set #1 due January 14, 2015 Read the homework instructions on the website. The instructions that follow here are only an incomplete summary.
Algorithms CMSC-27200 http://alg15.cs.uchicago.edu Homework set #1 due January 14, 2015 Read the homework instructions on the website. The instructions that follow here are only an incomplete summary.
Asymptotic Algorithm Analysis & Sorting
 Asymptotic Algorithm Analysis & Sorting (Version of 5th March 2010) (Based on original slides by John Hamer and Yves Deville) We can analyse an algorithm without needing to run it, and in so doing we can
Asymptotic Algorithm Analysis & Sorting (Version of 5th March 2010) (Based on original slides by John Hamer and Yves Deville) We can analyse an algorithm without needing to run it, and in so doing we can
2WF15 - Discrete Mathematics 2 - Part 1. Algorithmic Number Theory
 1 2WF15 - Discrete Mathematics 2 - Part 1 Algorithmic Number Theory Benne de Weger version 0.54, March 6, 2012 version 0.54, March 6, 2012 2WF15 - Discrete Mathematics 2 - Part 1 2 2WF15 - Discrete Mathematics
1 2WF15 - Discrete Mathematics 2 - Part 1 Algorithmic Number Theory Benne de Weger version 0.54, March 6, 2012 version 0.54, March 6, 2012 2WF15 - Discrete Mathematics 2 - Part 1 2 2WF15 - Discrete Mathematics
Data Structures and Algorithms Chapter 3
 Data Structures and Algorithms Chapter 3 1. Divide and conquer 2. Merge sort, repeated substitutions 3. Tiling 4. Recurrences Recurrences Running times of algorithms with recursive calls can be described
Data Structures and Algorithms Chapter 3 1. Divide and conquer 2. Merge sort, repeated substitutions 3. Tiling 4. Recurrences Recurrences Running times of algorithms with recursive calls can be described
This is a recursive algorithm. The procedure is guaranteed to terminate, since the second argument decreases each time.
 8 Modular Arithmetic We introduce an operator mod. Let d be a positive integer. For c a nonnegative integer, the value c mod d is the remainder when c is divided by d. For example, c mod d = 0 if and only
8 Modular Arithmetic We introduce an operator mod. Let d be a positive integer. For c a nonnegative integer, the value c mod d is the remainder when c is divided by d. For example, c mod d = 0 if and only
Discrete Mathematics and Probability Theory Fall 2018 Alistair Sinclair and Yun Song Note 6
 CS 70 Discrete Mathematics and Probability Theory Fall 2018 Alistair Sinclair and Yun Song Note 6 1 Modular Arithmetic In several settings, such as error-correcting codes and cryptography, we sometimes
CS 70 Discrete Mathematics and Probability Theory Fall 2018 Alistair Sinclair and Yun Song Note 6 1 Modular Arithmetic In several settings, such as error-correcting codes and cryptography, we sometimes
MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 2
 MA008 p.1/36 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 2 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/36 Content of lecture 2 Examples Review data structures Data types vs. data
MA008 p.1/36 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 2 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/36 Content of lecture 2 Examples Review data structures Data types vs. data
1 Divide and Conquer (September 3)
 The control of a large force is the same principle as the control of a few men: it is merely a question of dividing up their numbers. Sun Zi, The Art of War (c. 400 C.E.), translated by Lionel Giles (1910)
The control of a large force is the same principle as the control of a few men: it is merely a question of dividing up their numbers. Sun Zi, The Art of War (c. 400 C.E.), translated by Lionel Giles (1910)
i=1 i B[i] B[i] + A[i, j]; c n for j n downto i + 1 do c n i=1 (n i) C[i] C[i] + A[i, j]; c n
![i=1 i B[i] B[i] + A[i, j]; c n for j n downto i + 1 do c n i=1 (n i) C[i] C[i] + A[i, j]; c n i=1 i B[i] B[i] + A[i, j]; c n for j n downto i + 1 do c n i=1 (n i) C[i] C[i] + A[i, j]; c n](/thumbs/76/73723628.jpg) Fundamental Algorithms Homework #1 Set on June 25, 2009 Due on July 2, 2009 Problem 1. [15 pts] Analyze the worst-case time complexity of the following algorithms,and give tight bounds using the Theta
Fundamental Algorithms Homework #1 Set on June 25, 2009 Due on July 2, 2009 Problem 1. [15 pts] Analyze the worst-case time complexity of the following algorithms,and give tight bounds using the Theta
MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3
 MA008 p.1/37 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/37 Exercise 1 (from LN 2) Asymptotic Notation When constants appear in exponents
MA008 p.1/37 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/37 Exercise 1 (from LN 2) Asymptotic Notation When constants appear in exponents
CS 4407 Algorithms Lecture 2: Iterative and Divide and Conquer Algorithms
 CS 4407 Algorithms Lecture 2: Iterative and Divide and Conquer Algorithms Prof. Gregory Provan Department of Computer Science University College Cork 1 Lecture Outline CS 4407, Algorithms Growth Functions
CS 4407 Algorithms Lecture 2: Iterative and Divide and Conquer Algorithms Prof. Gregory Provan Department of Computer Science University College Cork 1 Lecture Outline CS 4407, Algorithms Growth Functions
Tricks of the Trade in Combinatorics and Arithmetic
 Tricks of the Trade in Combinatorics and Arithmetic Zachary Friggstad Programming Club Meeting Fast Exponentiation Given integers a, b with b 0, compute a b exactly. Fast Exponentiation Given integers
Tricks of the Trade in Combinatorics and Arithmetic Zachary Friggstad Programming Club Meeting Fast Exponentiation Given integers a, b with b 0, compute a b exactly. Fast Exponentiation Given integers
data structures and algorithms lecture 2
 data structures and algorithms 2018 09 06 lecture 2 recall: insertion sort Algorithm insertionsort(a, n): for j := 2 to n do key := A[j] i := j 1 while i 1 and A[i] > key do A[i + 1] := A[i] i := i 1 A[i
data structures and algorithms 2018 09 06 lecture 2 recall: insertion sort Algorithm insertionsort(a, n): for j := 2 to n do key := A[j] i := j 1 while i 1 and A[i] > key do A[i + 1] := A[i] i := i 1 A[i
Lecture 2. More Algorithm Analysis, Math and MCSS By: Sarah Buchanan
 Lecture 2 More Algorithm Analysis, Math and MCSS By: Sarah Buchanan Announcements Assignment #1 is posted online It is directly related to MCSS which we will be talking about today or Monday. There are
Lecture 2 More Algorithm Analysis, Math and MCSS By: Sarah Buchanan Announcements Assignment #1 is posted online It is directly related to MCSS which we will be talking about today or Monday. There are
