Symbolic Dynamical Model of Average Queue Size of Random Early Detection Algorithm
|
|
|
- Gary Dalton
- 5 years ago
- Views:
Transcription
1 Symbolic Dynamical odel of Average Queue Size of Rom Early Detection Algorithm Charlotte Yuk-Fan Ho Telehone: 44 () ext Fax: 44 () School of athematical Sciences Queen ary University of London ile End Road London E 4NS United Kingdom. *Bingo Wing-Kuen Ling Telehone: 44 () Fax: 44 () HTing-kuen.ling@kcl.ac.ukTH Deartment of Electronic Engineering Division of Engineering King s College London Str London WCR LS United Kingdom. Herbert H. C. Iu Telehone: Fax: HTherbert@ee.ua.edu.auTH School of Electrical Electronic Comuter Engineering The University of Western Australia 35 Stirling Highay Craley Perth Western Australia WA69 Australia. ABSTRACT In this aer a symbolic dynamical model of the average ueue size of the rom early detection (RED) algorithm is roosed. The conditions on both the system arameters the initial conditions that the average ueue size of the RED algorithm ould converge to a fixed oint are derived. These results are useful for netork engineers to design both the system arameters the initial conditions so that internet netorks ould achieve a good erformance. Keyords Transmission control rotocol rom early detection algorithm internet congestion roblem symbolic dynamics Lyaunov stability. I. INTRODUCTION There is no doubt that internet netorks lay an imortant role in our daily life. Hoever as
2 the traffic of internet netorks gros raidly congestion roblems become very serious. Poor managements of internet netorks ill result to artly or fully inaccessible netorks hence degrade general erformances of netorking alications []-[6]. To address this issue various aroaches have been roosed. The commonest aroach to address the congestion roblems is via active ueue management (AQ) mechanisms in hich the RED algorithm is a idely deloyed algorithm for AQ mechanisms []-[6]. The goal of the RED algorithm is to detect an early sign of the congestion rovide a feedback by either droing or marking segments of messages so that the congestion can be avoided. Although the RED algorithm is concetually simle the interaction beteen the transmission control rotocol (TCP) the RED algorithm at the router s gateay is actually governed by a first order ieceise nonlinear difference euation in hich comlex behaviors such as limit cycle behaviors chaotic behaviors could be exhibited. For the commonest oeration the average ueue size of the RED algorithm is reuired to converge to a fixed oint these comlex behaviors degrade general erformances of netork alications []-[6]. As these comlex behaviors deend on both the system arameters the initial conditions of the nonlinear difference euation netork engineers reuire to design both the system arameters the initial conditions of the nonlinear difference euation so that the average ueue size of the RED algorithm ould converge to a fixed oint. Nevertheless no result has been reorted on characterizing the conditions on both the system arameters the initial conditions of the nonlinear difference euation that the average ueue size of the RED algorithm ould converge to a fixed oint. This aer is to address this issue. The outline of this aer is as follos. The orking rinciles of the TCP the RED algorithm are revieed in Section II hile nonlinear behaviors of the average ueue size of the RED algorithm are revieed in Section III. In Section IV a symbolic dynamical model is roosed as ell as the conditions on both the system arameters the initial conditions of the nonlinear difference euation that the average ueue size of the RED algorithm ould converge to a fixed
3 oint are derived. Finally a conclusion is dran in Section V. II. REVIEW ON WORKING PRINCIPLES OF TCP AND RED ALGORITH This section describes a brief summary of the orking rinciles of the TCP the RED algorithm. For interested readers lease refer to the details in []-[6]. A. Working rinciles of TCP The transmission rate of a TCP connection is controlled by the size of the congestion indo at the sender end denoted as cnd. The cnd size deteres the number of segments of messages to be sent to the receiver end. The cnd size is adjusted to imize the utilization of the link to avoid the congestion. To adjust the cnd size TCP congestion control algorithms emloy the folloing four hases: the slo start hase the congestion avoidance hase the fast retransmit hase the fast recovery hase. The descrition of the slo start hase is as follos. When a ne connection is first established the cnd size at the sender end is initialized to the size of one segment of messages. Uon a receit of every segment of messages a acket of an acknoledgement (ACK) is sent to the TCP sender by the TCP receiver. Uon a receit of every acket of an ACK at the sender end the TCP sender increases the cnd size by the size of one segment of messages. To segments of messages can no be sent. When both segments of messages are acknoledged the cnd size is increased to the size of four segments of messages. These rocedures are iterated in an exonential manner the TCP sender oens u the indo size exonentially that is 4 8 etc. When the cnd size exceeds a threshold denoted as ssthresh the TCP sender enters the congestion avoidance hase. During the congestion avoidance hase the cnd size is incremented by the size of one segment of messages er a round tri time regardless of the number of the ackets of an ACK has been received. Hence the TCP sender oens u the indo size linearly that is 3 4 etc until it reaches the receiver s advertised indo size denoted as rnd. 3
4 P iteration International Journal of Bifurcation Chaos The descrition of the fast retransmit hase is as follos. A retransmission timer is set every time hen the TCP sender sends a acket of messages. A acket loss is detected by the timeout mechanism if the timer exires before receiving the acket of an ACK. In this case the TCP sender adjusts the ssthresh sitches back to the slo start hase. In the congestion avoidance hase uon receiving an out of order segment of messages the TCP receiver generates a acket of an ACK is immediately folloed by a dulicate acket of an ACK. When three dulicate ackets of an ACK have been received by the TCP sender it is assumed that a segment of messages has been lost. The TCP sender halves the cnd size retransmits the lost segment of messages ithout aiting the exiration of a retransmission timer. The descrition of the fast recovery hase is as follos. Until the retransmitted segment of messages is received the TCP receiver ill continue to receive the out of order segments of messages generate the dulicate ackets of an ACK to the TCP sender. After the fast retransmit hase sends the missing segment of messages the TCP sender increases the cnd size henever each dulicate acket of an ACK is received. Each dulicate acket of an ACK is an indication that one acket of messages has reached the TCP receiver the number of outsting ackets of messages has decreased by one. Therefore the TCP sender is alloed to increment the cnd size. The TCP sender sitches back to the congestion avoidance hase hen the retransmitted segment of messages is received a nondulicate acket of an ACK is sent to the TCP sender. B. Working rinciles of RED algorithm The RED algorithm is a gateay based algorithm for AQ mechanisms. It estimates the congestion level by monitoring udating the average ueue size. In order to maintain a relatively small average ueue size rather than aiting for buffer overflos it dros a acket of messages ith a certain robability to rovide an early sign of the congestion hen the average ueue size exceeds a threshold. Denote the imum ueue threshold the imum ueue threshold the imum acket dro robability the average ueue size the dro robability at the k P th k as 4 resectively. The dro
5 P P iteration P iteration International Journal of Bifurcation Chaos robability deends on the average ueue size it is governed by the folloing euation: H ( ) < < k. Denote the exonential average eight of the RED algorithm as. The average ueue size at the k th is governed by an exonential la it deends on both the average ueue size the dro robability at the k P in hich th k as follos: ( k ) ( ) ( k ) G( ) ( ( )) ( ) G k k k N rnd here the caacity of the link beteen to routers the acket size the number of TCP connections a constant beteen N K d resectively. 8 as ell as the round tri roagation delay are denoted as C 3 It is trivial to see that the dynamical model of the average ueue size can be further reresented by a first order ieceise nonlinear difference euation as follos: ( ) ( ) k ( ) ( ) k k k. ( ) ( ) N rnd k Due to the hysical nature of both the arameters the variables of the RED algorithm it is assumed that all the arameters ( C N K d rnd ) are nonnegative real-valued. Also it is assumed that < <. < ( ) In this model the dynamics of the average ueue size of the RED algorithm at the gateay is considered. The first order ieceise nonlinear dynamical model reflects the TCP congestion 5
6 control mechanism takes into account the slo start hase timeout events. III. NONLINEAR BEHAVIORS OF AVERAGE QUEUE SIZE OF RED ALGORITH It is ell knon that the average ueue size of the RED algorithm could exhibit a bifurcation behavior. Figure shos the bifurcation diagram as varies hen N 3 K 6 C ( ) ( ) d 4 rnd Figure shos the freuency sectrum of the steady state dro robability the steady state hase diagram the steady state dro robability the steady state average ueue size hen. hile Figure 3 Figure 4 Figure 5 sho the corresonding numerical comuter simulation results hen resectively. It can be seen from Figure to Figure 5 that as increases the steady state dro robability the steady state average ueue size exhibit the limit cycle the rom like chaotic behaviors consecutively. When. 7 the steady state dro robability at some time instants is eual to one. Hence it can be seen from Figure 5 that there are to straight lines one located at another one located at hen <. 7 exhibited on the steady state hase diagram. On the other h it can be seen from Figure 3 that there is only one single straight line located at exhibited on the steady state hase diagram. The imortance of observing the above nonlinear henomena is that netork engineers could design both the system arameters the initial conditions so that the average ueue size of the RED algorithm ould not exhibit these nonlinear behaviors. 6
7 Figure. Bifurcation diagram as varies...5 P(ω) Freuency ω (π) 6.6 Average ueue size Probability.6.4 Probability Time index k 7
8 6.6 Average ueue size Figure Time index k. (a) Freuency sectrum of the steady state dro robability. (b) Steady state hase diagram. (c) Steady state dro robability. (d) Steady state average ueue size P(ω) Freuency ω (π) 7 Average ueue size Probability.5. Probability Time index k 8
9 7.5 Average ueue size Time index k Figure (a) Freuency sectrum of the steady state dro robability. (b) Steady state hase diagram. (c) Steady state dro robability. (d) Steady state average ueue size. 4 3 P(ω) Freuency ω (π) Average ueue size Probability Probability Time index k 9
10 9 8.5 Average ueue size Time index k Figure (a) Freuency sectrum of the steady state dro robability. (b) Steady state hase diagram. (c) Steady state dro robability. (d) Steady state average ueue size P(ω) Freuency ω (π) 5 Average ueue size Probability.8 Probability Time index k
11 5 Average ueue size Time index k Figure (a) Freuency sectrum of the steady state dro robability. (b) Steady state hase diagram. (c) Steady state dro robability. (d) Steady state average ueue size. IV. SYBOLIC DYNAICAL ODEL AND CONDITIONS FOR EXHIBITING FIXED A. Symbolic dynamical model POINT BEHAVIORS It is obvious to see that different values of corresonds to different dynamical euations. To analyze the behaviors of the average ueue size of the RED algorithm the set of is artitioned into fifteen different subsets denoted as i reresented by fifteen different symbols denoted as S for i L 5. These subsets are s i for i L 5 k in hich only one symbol is activated in each subset. That is if Si then s i ( k ) j i k. Denote ( ) [ s s ] T k L 5 s j for s k here the suerscrit T denotes the transose oerator. The model of the average ueue size of the RED algorithm can be analyzed via a symbolic dynamical model here symbolic dynamics is a system dynamics in hich some signals in the system are multileveled. The dynamics of the average ueue size of the RED algorithm in each subset is as follos: A. Dynamics of the average ueue size in the first subset N rnd If < ( k ) < N rnd then
12 ( k ) ( ) N rnd ( k ). Denote s j. s j for It is obvious to see that if < then. Hence e have ( k ) ( ) N rnd. As ( k ) N rnd < N rnd e have ( ) N rnd <. This imlies that ( ) have ( k ) k <. Hence e. This comletes the roof. A. Dynamics of the average ueue size in the second subset If < ( k ) N rnd then ( k ) ( ) N rnd ( k ). Denote s j. s j for It is obvious to see that if < then. Hence e have ( k ) ( ) N rnd. As ( k ) N rnd ( ) N rnd. This imlies that ( k ) ( k ) e have. Hence e have. This comletes the roof. A.3 Dynamics of the average ueue size in the third subset N rnd If < > ( k ) ( k ) ( ) Nrnd N rnd then
13 ( ) N rnd. ( k ) Denote s 3 s j for j 3. It is obvious to see that if < then. Hence e have ( k ) ( ) N rnd. As > ( k ) N rnd N rnd e have > ( ) N rnd. This imlies that ( k ) Hence e have ( k ) ( k ) ( ) N rnd >.. This comletes the roof. A.4 Dynamics of the average ueue size in the fourth subset Denote P 4 ( ) ( )( ) k : ( ) 3 ( ) ( ) ( )( ) ( ( )) 3 k ( ) ( ) < Q : P. If < 4 4 Q4 then ( k ) ( ) ( k ) ( k ). Denote 4 ( k ) s j for j 4. s 3
14 It is obvious to see that if < then. Since this imlies that N N K K. Hence e have. ( k ) ( k ) ( ) ( k ) As Q4 e have P4. In other ords e have ( )( ) ( ( )) 3 k ( ) ( ( )) k < This imlies that as ell as Hence e have ( )( ) ( ( )) 3 k ( ) ( ( )) k ( )( ) 4 ( ) < ( )( ) ( ) ( ) <. ( ) k ( ) ( ) <.
15 ( ) < ( k ) < ( k ). Conseuently e have. This comletes the roof. A.5 Dynamics of the average ueue size in the fifth subset Denote ( ) ( )( ) : ( ( )) 3 P ( ) ( ( )) 5 k k k Q : P. If < 5 5 Q5 then ( k ) ( ) ( k ) ( k ). Denote 5 ( k ) s j for j 5. It is obvious to see that if < then s. Since this imlies that N N K K. Hence e have. ( k ) ( k ) ( ) ( k ) 5
16 As Q5 e have P5 This imlies that. In other ords e have ( )( ) ( ( )) 3 k ( ) ( ( )) k ( )( ) ( ) ( ) ( ) ( k ). Hence e have ( k ).. This comletes the roof. A.6 Dynamics of the average ueue size in the sixth subset Denote P 6 ( ) ( )( ) k : ( ) 3 ( ) ( ) ( )( ) ( ( )) 3 k ( ) ( ) < Q : P. If < 6 6 ( k ) Q6 then ( k ) ( k ) ( ) ( k ) 6
17 ( ). ( k ) Denote s 6 s j for j 6. It is obvious to see that if < then. Since this imlies that N N K K. Hence e have As Q6 e have P6 This imlies that as ell as. ( k ) ( k ) ( ) ( k ). In other ords e have ( )( ) ( ( )) 3 k ( ) ( ( )) k ( )( ) ( ( )) 3 k ( ) ( ( )) k < ( )( ) ( )( ) ( ) ( ) <. 7
18 Hence e have ( ) <. ( ) ( ) < < ( ) ( k ) <. Conseuently e have ( k ) comletes the roof. ( ) ( k ) ( k ). This A.7 Dynamics of the average ueue size in the seventh subset If < > < then ( ) k ( k ) ( ) ( k ). Denote s for j 7. It is obvious to see that if < then 7 s j. Since > this imlies that > > 8
19 N N > <. Hence e have ( k ) ( ) ( k ). As K e have ( ) < ( k ) < ( k ) K A.8 Dynamics of the average ueue size in the eighth subset <. This comletes the roof. If < > then ( ) k ( k ) ( ) ( k ). Denote s for j 8. It is obvious to see that if < then 8 s j. Since > this imlies that > > N N > K K <. Hence e have ( k ) ( ) ( k ). As e have ( ) ( k ) ( k ) A.9 Dynamics of the average ueue size in the ninth subset. This comletes the roof. If < > > ( ) k ( k ) ( ) ( k ) s 9 s j for j 9. ( ) It is obvious to see that if < then then. Denote. Since > this imlies that > > N N > K K <. Hence e have ( k ) ( ) ( k ) 9. As
20 > e have > ( ) ( k ) ( k ) ( k ) ( ) >. This comletes the roof. A. Dynamics of the average ueue size in the tenth subset k If ( ) < then ( k ) ( k ) ( ) ( k ) ( k ). Denote s j. that It is obvious to see that if then ( k ). Since N N K As < K ( k ) < ( k ) s j for this imlies.. Hence e have ( k ) ( ) ( k ) e have ( ) <. This comletes the roof. A. Dynamics of the average ueue size in the eleventh subset k If ( ) then ( k ) ( k ) ( ) ( k ) ( k ). Denote s j. that As It is obvious to see that if then ( k ). Since N N K K s j for this imlies.. Hence e have ( k ) ( ) ( k ) e have ( ) ( ) k
21 ( k ). This comletes the roof. A. Dynamics of the average ueue size in the telfth subset k > ( ) ( k ). If ( ) ( k ) ( k ) ( ) ( k ) then Denote s that s j for j. It is obvious to see that if then ( k ). Since N N K As > K > ( k ) ( k ) this imlies.. Hence e have ( k ) ( ) ( k ) e have > ( ) ( k ) ( ). This comletes the roof. A.3 Dynamics of the average ueue size in the thirteenth subset k < If ( ) < then ( k ) ( k ) ( ) ( k ). Denote s 3 s j for j 3. that < this imlies It is obvious to see that if then ( k ). Since N N > K K <. Hence e have ( k ) ( ) ( k ). As
22 < e have ( ) < ( k ) < ( k ) comletes the roof.. This A.4 Dynamics of the average ueue size in the fourteenth subset k < If ( ) then ( k ) ( k ) ( ) ( k ). Denote s 4 s j for j 4. that < this imlies k k. As It is obvious to see that if then ( k ). Since N N > K K <. Hence e have ( ) ( ) ( ) e have ( ) ( k ) ( k ) A.5 Dynamics of the average ueue size in the fifteenth subset k <. This comletes the roof. If ( ) > then ( k ) ( k ) ( ) ( ) ( ) k. Denote s s j for j 5. that 5 < this imlies It is obvious to see that if then ( k ). Since N N > K K <. Hence e have ( k ) ( ) ( k ). As > e have > ( ) ( k ) ( k ) ( k ) ( ) >. This comletes the roof. A could be sitched among these fifteen subsets according to the value of s ( k ) B N rnd [ ] ( ). Denote B [ ]
23 B [ ] B [ ] [ ] 3 4 B 5 ( ) [ B B ( ) B B ] B 3 4 B5 then the dynamics of the averages ueue size of the RED algorithm can be reresented by ( k ) A u here u B ( ) s. This model can be reresented via a closed loo feedback system having a linear time-invariant lant ith the four state sace constants A a ositive nonlinear feedback system ith its inut-outut relationshi governed by u B ( ) s. This roosed symbolic dynamical model is useful for designing both the system arameters the initial conditions so that the average ueue size of the RED algorithm ould converge to a fixed oint. Also the boundedness of the average ueue size of the RED algorithm could be detered easily via the roosed symbolic dynamical model. As < < A is strictly stable. If both the system arameters the initial conditions is designed so that u is bounded then is guaranteed to be bounded. It is orth noting that not all subsets contain a fixed oint. The conditions on both the system arameters the initial conditions that the average ueue size of the RED algorithm ould converge to a fixed oint are derived in Section B as follos. B. Conditions for exhibiting fixed oint behaviors Since the average ueue size of the RED algorithm is reuired to converge to a fixed oint it is imortant to characterize the conditions on both the system arameters the initial conditions so that the average ueue size of the RED algorithm ould converge to a fixed oint. These conditions are summarized in the folloing lemmas: Lemma The fixed oint of the average ueue size of the RED algorithm ould not be located at S S3 U S4 U S5 U S7 U S8 U S9 U S U S U S3 U S4 U S5 U. 3
24 As ( k ) for S U S3 U S4 U S5 U S7 U S8 U S U S U S3 U S5 the fixed oint of the average ueue size of the RED algorithm could not be located at S U S3 U S4 U S5 U S7 U S8 U S U S U S3 U S5 RED algorithm for S4 is governed by ( k ) ( ). As the dynamics of the average ueue size of the if the fixed oint is located at S then the fixed oint has to be located at the origin but it contradicts to ( ) 4 k. Hence the fixed oint of the average ueue size of the RED algorithm could not be located at S 4. Similarly the fixed oint of the average ueue size of the RED algorithm could not be located at S 9. This comleted the roof. U S U S Although the dynamics of the average ueue size for ( ) 6 k S is characterized it is not guaranteed that ( k ) S for S ( k ) S6 for S6 ( k ) S for S. Further conditions are reuired to be imosed the details are discussed in the folloing lemmas. Lemma If k such that i) N rnd < ii) N rnd iii) ( k ) then s i) k k s ii) k k 4
25 iii) N rnd as k. As s ( k ) this imlies that ( ) k < 5. Since N rnd e have ( ) N rnd N rnd ( ) N rnd Nrnd Nrnd. On the other h as N rnd < e have N rnd N rnd < Nrnd ( ) N rnd < N rnd Nrnd N rnd ( k ) Nrnd < N rnd Nrnd Nrnd ( k ) <. As ( k ) < Nrnd. Since ( k ) s e have is a convex combinational of Nrnd Nrnd N rnd e have ( k ) <. This imlies that ( k ) S. Similarly e have S e have k ( k k ) ( ) ( k ) k k. As N rnd N rnd k N rnd as k. This comletes the roof. This lemma characterizes the condition on both the system arameters the initial conditions that the average ueue size of the RED algorithm ould converge to a fixed oint in the first subset. It is orth noting that if the second condition in Lemma is changed to N rnd the same result ould been obtained. Hoever due to the hysical nature of k. Since N rnd as k the hysical nature of is
26 violated. Hence this case has not been considered in Lemma. Lemma 3 If k such that i) ii) ( k ) then s i) ( k ) k k s ii) ( k ) k k iii) as k. As s ( k ) this imlies that ( k ). Since e have ( ). As s ( k ) e have ( k ) ( k ) is a convex combinational of ( ) 6 k. Since e have ( k ). This imlies that ( k ) S. Similarly e have S k. As ( k k ) ( ) ( k ) k k ( k ) k e have as k. This comletes the roof. This lemma characterizes the condition on both the system arameters the initial conditions that the average ueue size of the RED algorithm ould converge to a fixed oint in the
27 eleventh subset. Lemma 4 If k such that i) ( k ) s 6 ii) ( ) ( k ) ( k ) > iii) ( ) ( k ) ( k ) ( k ) iv) ( ) ( k ) then ( k ) k k. s 6 As s ( k ) e have ( ) 6 e have ( k ) ( ) ( k ) > k. Since ( k ). As 7
28 ( ) ( k ) ( k ) > ( ) ( k ) ( k ) e have < ( k ). This imlies that < ( k ). This further imlies that < ( k ). Conseuently e have This further imlies that the convex combinational of <. ( k ) ( k ) is larger than or eual to that is ( ) ( ) k. Similarly the convex combinational of ( k ) is smaller than that is ( ) <. ( k ) Since > ( k ) e have ( ) ( k ) < ( k ) ( ) ( k ) ( ) k. In other ords e have 8
29 ( ) ( k ) < ( k ) ( ) ( ) ( ) k < ( k ) k ( ) ( ) ( ) ( k ) ( ) k ( ) ( ) ( ) ( k ) ( ) <. Hence e have ( ) ( )( ( )) 3 ( ) ( ( ) k k ) ( ) ( )( ( )) 3 ( ) ( ( ) k k ) < imlies that ( k ) P6 ( k ) Q6. Similarly e have S6. This further k k. This comletes the roof. Although Lemma 4 characterizes the conditions on S6 k k if ( k ) S6 it does not guarantee the existence of a fixed oint. To guarantee the existence of a fixed oint the folloing lemma is reuired: Lemma 5 Define ( ) such that. ( ) ( ). Then this As ( ) ( ) comletes the roof. Obviously ( ) is a fixed oint based on the dynamics defined in the sixth subset. 9
30 Hoever even though there exists a fixed oint it does not guarantee that this fixed oint ould be located at S 6 satisfy Lemma 4. Further conditions are reuired to be imosed the details are discussed in folloing lemma. Denote the set { ( ) : Lemma 4 is satisfied. } Lemma 6 If Ω k S 6. i) ii) < then Ω. Since < this imlies that < < <. This further imlies that is the fixed oint in Ω. This comletes the roof. 3
31 Although Ω in general it does not guarantee that ( k ) Ω ( ) ould converge k to. Further conditions are reuired to be imosed the details are discussed in folloing lemma. Define a ma Δ V : Ω R such that ΔV define Lemma 7 ( ( k )) ( ) ( k ) ( k ) ( k ) Ω ( ( k )) ΔV ΔV. ( ( k ) ) ( k ) Suose that satisfies the conditions in Lemma 6 ( k ) Ω ΔV < then ( ) ( ). Denote ( ) ( ) V k k. Obviously k k. Since V satisfies the conditions in Lemma 6 Ω. As 3
32 V ( k ) V ( k ) ( k ) ΔV ( ) ( k ) ( ) ( k ) ( ) ( k ) ( ) ( k ) Δ < ( ) ( ( k ) ) ( ( k ) ) ( ( k ) ) ( k ) ( k ) ( k ) ( k ) ( ) ( k ) ( ) ( k ) ( k ) ( ( k )) ( ( k ) ) ( k ) ( k ) ( ) ( ) ( k ) ( k ) V this imlies that V ( k ) V( k ) ( k ) Ω. Since ( ) Ω < of the Lyaunov stability theorem e have ( k ) ( k ) ( ) ( ) k by the rincile. This comletes the roof. Lemma 4 to Lemma 7 characterize the conditions on both the system arameters the initial conditions that the average ueue size of the RED algorithm ould converge to a fixed oint in the sixth subset. As there is no fixed oint in other subsets the state vectors in these other subsets ill not stay in these subsets. V. CONCLUSION This aer rooses a symbolic dynamical model of the average ueue size of the RED algorithm characterizes the conditions on both the system arameters the initial conditions that the average ueue size of the RED algorithm ould converge to a fixed oint. By emloying 3
33 the symbolic dynamical system aroach both the system arameters the initial conditions can be designed so that the average ueue size of the RED algorithm ould converge to a fixed oint behavior. ACKNOWLWDGEENTS The ork obtained in this aer as suorted by an Australian research grant a research grant from the Queen ary University of London. REFERENCES [] Priya Ranjan Eyad H. Abed Richard J. La Nonlinear instabilities in TCP-RED IEEE Transactions on Netorking vol. no [] Priya Ranjan Eyad H. Abed Richard J. La Nonlinear instabilities in TCP-RED The Tenty-First Annual Joint Conference of the IEEE Comuter Communications Societies IEEE INFOCO vol June 3-7. [3] L. Chen X. F. Wang Z. Z. Han Controlling bifurcation chaos in internet congestion control model International Symosium on Circuits Systems ISCAS vol. 3. III3-III35 ay [4] J. H. C. Nga H. H. C. Iu B. W. K. Ling H. K. Lam Analysis control of bifurcation chaos in average ueue length in TCP/RED model International Journal of Bifurcation Chaos vol. 8 no [5] Feng Liu Zhi-Hong Guan Hua O. Wang Imulsive control bifurcation chaos in internet TCP-RED congestion control system The IEEE International Conference on Control Automation ICCA. 4-7 ay 3-June 7. [6] Kirk Chang Gitae Kim Larry Wong Sunil Samtani Aristides Staikos itesh Patel Jeffrey Bocock Netork layer congestion control to ensure uality of service (QOS) in secure battlefield mobile ad hoc netorks The IEEE ilitary Communications Conference 33
34 ILCO. -7 October
DEVELOPMENT AND VALIDATION OF A VERSATILE METHOD FOR THE CALCULATION OF HEAT TRANSFER IN WATER-BASED RADIANT SYSTEMS METHODS
 Eleventh International IBPSA Conference Glasgo, Scotland July 27-30, 2009 DEVELOPMENT AND VALIDATION OF A VERSATILE METHOD FOR THE CALCULATION OF HEAT TRANSFER IN WATER-BASED RADIANT SYSTEMS Massimiliano
Eleventh International IBPSA Conference Glasgo, Scotland July 27-30, 2009 DEVELOPMENT AND VALIDATION OF A VERSATILE METHOD FOR THE CALCULATION OF HEAT TRANSFER IN WATER-BASED RADIANT SYSTEMS Massimiliano
A Study of Active Queue Management for Congestion Control
 A Study of Active Queue Management for Congestion Control Victor Firoiu vfiroiu@nortelnetworks.com Nortel Networks 3 Federal St. illerica, MA 1821 USA Marty orden mborden@tollbridgetech.com Tollridge Technologies
A Study of Active Queue Management for Congestion Control Victor Firoiu vfiroiu@nortelnetworks.com Nortel Networks 3 Federal St. illerica, MA 1821 USA Marty orden mborden@tollbridgetech.com Tollridge Technologies
An Analysis of TCP over Random Access Satellite Links
 An Analysis of over Random Access Satellite Links Chunmei Liu and Eytan Modiano Massachusetts Institute of Technology Cambridge, MA 0239 Email: mayliu, modiano@mit.edu Abstract This aer analyzes the erformance
An Analysis of over Random Access Satellite Links Chunmei Liu and Eytan Modiano Massachusetts Institute of Technology Cambridge, MA 0239 Email: mayliu, modiano@mit.edu Abstract This aer analyzes the erformance
Anytime communication over the Gilbert-Eliot channel with noiseless feedback
 Anytime communication over the Gilbert-Eliot channel with noiseless feedback Anant Sahai, Salman Avestimehr, Paolo Minero Deartment of Electrical Engineering and Comuter Sciences University of California
Anytime communication over the Gilbert-Eliot channel with noiseless feedback Anant Sahai, Salman Avestimehr, Paolo Minero Deartment of Electrical Engineering and Comuter Sciences University of California
Improving AOR Method for a Class of Two-by-Two Linear Systems
 Alied Mathematics 2 2 236-24 doi:4236/am22226 Published Online February 2 (htt://scirporg/journal/am) Imroving AOR Method for a Class of To-by-To Linear Systems Abstract Cuixia Li Shiliang Wu 2 College
Alied Mathematics 2 2 236-24 doi:4236/am22226 Published Online February 2 (htt://scirporg/journal/am) Imroving AOR Method for a Class of To-by-To Linear Systems Abstract Cuixia Li Shiliang Wu 2 College
Finding Shortest Hamiltonian Path is in P. Abstract
 Finding Shortest Hamiltonian Path is in P Dhananay P. Mehendale Sir Parashurambhau College, Tilak Road, Pune, India bstract The roblem of finding shortest Hamiltonian ath in a eighted comlete grah belongs
Finding Shortest Hamiltonian Path is in P Dhananay P. Mehendale Sir Parashurambhau College, Tilak Road, Pune, India bstract The roblem of finding shortest Hamiltonian ath in a eighted comlete grah belongs
Robust Beamforming via Matrix Completion
 Robust Beamforming via Matrix Comletion Shunqiao Sun and Athina P. Petroulu Deartment of Electrical and Comuter Engineering Rutgers, the State University of Ne Jersey Piscataay, Ne Jersey 8854-858 Email:
Robust Beamforming via Matrix Comletion Shunqiao Sun and Athina P. Petroulu Deartment of Electrical and Comuter Engineering Rutgers, the State University of Ne Jersey Piscataay, Ne Jersey 8854-858 Email:
On the Chvatál-Complexity of Knapsack Problems
 R u t c o r Research R e o r t On the Chvatál-Comlexity of Knasack Problems Gergely Kovács a Béla Vizvári b RRR 5-08, October 008 RUTCOR Rutgers Center for Oerations Research Rutgers University 640 Bartholomew
R u t c o r Research R e o r t On the Chvatál-Comlexity of Knasack Problems Gergely Kovács a Béla Vizvári b RRR 5-08, October 008 RUTCOR Rutgers Center for Oerations Research Rutgers University 640 Bartholomew
Group Communication Protocol in Transaction-Oriented Applications
 Grou Communication Protocol in Transaction-Oriented Alications Tomoya Enokido, Takayuki Tachikaa, and Makoto Takizaa Det. of Comuters and Systems Engineering Tokyo Denki University Email feno, tachi, takig@takilab.k.dendai.ac.j
Grou Communication Protocol in Transaction-Oriented Alications Tomoya Enokido, Takayuki Tachikaa, and Makoto Takizaa Det. of Comuters and Systems Engineering Tokyo Denki University Email feno, tachi, takig@takilab.k.dendai.ac.j
Linear diophantine equations for discrete tomography
 Journal of X-Ray Science and Technology 10 001 59 66 59 IOS Press Linear diohantine euations for discrete tomograhy Yangbo Ye a,gewang b and Jiehua Zhu a a Deartment of Mathematics, The University of Iowa,
Journal of X-Ray Science and Technology 10 001 59 66 59 IOS Press Linear diohantine euations for discrete tomograhy Yangbo Ye a,gewang b and Jiehua Zhu a a Deartment of Mathematics, The University of Iowa,
A Simple Throughput Model for TCP Veno
 A Simle Throughut Model for TCP Veno Bin Zhou, Cheng Peng Fu, Dah-Ming Chiu, Chiew Tong Lau, and Lek Heng Ngoh School of Comuter Engineering, Nanyang Technological University, Singaore 639798 Email: {zhou00,
A Simle Throughut Model for TCP Veno Bin Zhou, Cheng Peng Fu, Dah-Ming Chiu, Chiew Tong Lau, and Lek Heng Ngoh School of Comuter Engineering, Nanyang Technological University, Singaore 639798 Email: {zhou00,
Approximating min-max k-clustering
 Aroximating min-max k-clustering Asaf Levin July 24, 2007 Abstract We consider the roblems of set artitioning into k clusters with minimum total cost and minimum of the maximum cost of a cluster. The cost
Aroximating min-max k-clustering Asaf Levin July 24, 2007 Abstract We consider the roblems of set artitioning into k clusters with minimum total cost and minimum of the maximum cost of a cluster. The cost
Factor Analysis of Convective Heat Transfer for a Horizontal Tube in the Turbulent Flow Region Using Artificial Neural Network
 COMPUTATIONAL METHODS IN ENGINEERING AND SCIENCE EPMESC X, Aug. -3, 6, Sanya, Hainan,China 6 Tsinghua University ess & Sringer-Verlag Factor Analysis of Convective Heat Transfer for a Horizontal Tube in
COMPUTATIONAL METHODS IN ENGINEERING AND SCIENCE EPMESC X, Aug. -3, 6, Sanya, Hainan,China 6 Tsinghua University ess & Sringer-Verlag Factor Analysis of Convective Heat Transfer for a Horizontal Tube in
UNDERWATER SOUND RECEIVED FROM SOME DEFENCE ACTIVITIES IN SHALLOW OCEAN REGIONS. Signal and Noise Transmission and Data Processing
 UNDERWATER SOUND RECEIVED FROM SOME DEFENCE ACTIVITIES IN SHALLOW OCEAN REGIONS Adrian D. Jones(1) and Paul A. Clarke() (1) Program Office, DSTO Edinburgh, SA 5111, Australia () Maritime Oerations Division,
UNDERWATER SOUND RECEIVED FROM SOME DEFENCE ACTIVITIES IN SHALLOW OCEAN REGIONS Adrian D. Jones(1) and Paul A. Clarke() (1) Program Office, DSTO Edinburgh, SA 5111, Australia () Maritime Oerations Division,
A ROBUST BEAMFORMER BASED ON WEIGHTED SPARSE CONSTRAINT
 Progress In Electromagnetics Research Letters, Vol. 16, 53 60, 2010 A ROBUST BEAMFORMER BASED ON WEIGHTED SPARSE CONSTRAINT Y. P. Liu and Q. Wan School of Electronic Engineering University of Electronic
Progress In Electromagnetics Research Letters, Vol. 16, 53 60, 2010 A ROBUST BEAMFORMER BASED ON WEIGHTED SPARSE CONSTRAINT Y. P. Liu and Q. Wan School of Electronic Engineering University of Electronic
Improved Capacity Bounds for the Binary Energy Harvesting Channel
 Imroved Caacity Bounds for the Binary Energy Harvesting Channel Kaya Tutuncuoglu 1, Omur Ozel 2, Aylin Yener 1, and Sennur Ulukus 2 1 Deartment of Electrical Engineering, The Pennsylvania State University,
Imroved Caacity Bounds for the Binary Energy Harvesting Channel Kaya Tutuncuoglu 1, Omur Ozel 2, Aylin Yener 1, and Sennur Ulukus 2 1 Deartment of Electrical Engineering, The Pennsylvania State University,
MATHEMATICAL MODELLING OF THE WIRELESS COMMUNICATION NETWORK
 Comuter Modelling and ew Technologies, 5, Vol.9, o., 3-39 Transort and Telecommunication Institute, Lomonosov, LV-9, Riga, Latvia MATHEMATICAL MODELLIG OF THE WIRELESS COMMUICATIO ETWORK M. KOPEETSK Deartment
Comuter Modelling and ew Technologies, 5, Vol.9, o., 3-39 Transort and Telecommunication Institute, Lomonosov, LV-9, Riga, Latvia MATHEMATICAL MODELLIG OF THE WIRELESS COMMUICATIO ETWORK M. KOPEETSK Deartment
Robust Predictive Control of Input Constraints and Interference Suppression for Semi-Trailer System
 Vol.7, No.7 (4),.37-38 htt://dx.doi.org/.457/ica.4.7.7.3 Robust Predictive Control of Inut Constraints and Interference Suression for Semi-Trailer System Zhao, Yang Electronic and Information Technology
Vol.7, No.7 (4),.37-38 htt://dx.doi.org/.457/ica.4.7.7.3 Robust Predictive Control of Inut Constraints and Interference Suression for Semi-Trailer System Zhao, Yang Electronic and Information Technology
On Buffer Limited Congestion Window Dynamics and Packet Loss
 On Buffer Limited Congestion Windo Dynamics and Packet Loss A. Fekete, G. Vattay Communication Netorks Laboratory, Eötvös University Pázmány P. sétány /A, Budapest, Hungary 7 Abstract The central result
On Buffer Limited Congestion Windo Dynamics and Packet Loss A. Fekete, G. Vattay Communication Netorks Laboratory, Eötvös University Pázmány P. sétány /A, Budapest, Hungary 7 Abstract The central result
Roots Blower with Gradually Expanding Outlet Gap: Mathematical Modelling and Performance Simulation Yingjie Cai 1, a, Ligang Yao 2, b
 2nd International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 216) Roots Bloer ith Gradually Exanding Outlet Ga: Mathematical Modelling and Performance Simulation
2nd International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 216) Roots Bloer ith Gradually Exanding Outlet Ga: Mathematical Modelling and Performance Simulation
Convex Optimization methods for Computing Channel Capacity
 Convex Otimization methods for Comuting Channel Caacity Abhishek Sinha Laboratory for Information and Decision Systems (LIDS), MIT sinhaa@mit.edu May 15, 2014 We consider a classical comutational roblem
Convex Otimization methods for Comuting Channel Caacity Abhishek Sinha Laboratory for Information and Decision Systems (LIDS), MIT sinhaa@mit.edu May 15, 2014 We consider a classical comutational roblem
Solved Problems. (a) (b) (c) Figure P4.1 Simple Classification Problems First we draw a line between each set of dark and light data points.
 Solved Problems Solved Problems P Solve the three simle classification roblems shown in Figure P by drawing a decision boundary Find weight and bias values that result in single-neuron ercetrons with the
Solved Problems Solved Problems P Solve the three simle classification roblems shown in Figure P by drawing a decision boundary Find weight and bias values that result in single-neuron ercetrons with the
2-D Analysis for Iterative Learning Controller for Discrete-Time Systems With Variable Initial Conditions Yong FANG 1, and Tommy W. S.
 -D Analysis for Iterative Learning Controller for Discrete-ime Systems With Variable Initial Conditions Yong FANG, and ommy W. S. Chow Abstract In this aer, an iterative learning controller alying to linear
-D Analysis for Iterative Learning Controller for Discrete-ime Systems With Variable Initial Conditions Yong FANG, and ommy W. S. Chow Abstract In this aer, an iterative learning controller alying to linear
A Method of Setting the Penalization Constants in the Suboptimal Linear Quadratic Tracking Method
 XXVI. ASR '21 Seminar, Instruments and Control, Ostrava, Aril 26-27, 21 Paer 57 A Method of Setting the Penalization Constants in the Subotimal Linear Quadratic Tracking Method PERŮTKA, Karel Ing., Deartment
XXVI. ASR '21 Seminar, Instruments and Control, Ostrava, Aril 26-27, 21 Paer 57 A Method of Setting the Penalization Constants in the Subotimal Linear Quadratic Tracking Method PERŮTKA, Karel Ing., Deartment
BOUNDS FOR THE COUPLING TIME IN QUEUEING NETWORKS PERFECT SIMULATION
 BOUNDS FOR THE COUPLING TIME IN QUEUEING NETWORKS PERFECT SIMULATION JANTIEN G. DOPPER, BRUNO GAUJAL AND JEAN-MARC VINCENT Abstract. In this aer, the duration of erfect simulations for Markovian finite
BOUNDS FOR THE COUPLING TIME IN QUEUEING NETWORKS PERFECT SIMULATION JANTIEN G. DOPPER, BRUNO GAUJAL AND JEAN-MARC VINCENT Abstract. In this aer, the duration of erfect simulations for Markovian finite
Research on Evaluation Method of Organization s Performance Based on Comparative Advantage Characteristics
 Vol.1, No.10, Ar 01,.67-7 Research on Evaluation Method of Organization s Performance Based on Comarative Advantage Characteristics WEN Xin 1, JIA Jianfeng and ZHAO Xi nan 3 Abstract It as under the guidance
Vol.1, No.10, Ar 01,.67-7 Research on Evaluation Method of Organization s Performance Based on Comarative Advantage Characteristics WEN Xin 1, JIA Jianfeng and ZHAO Xi nan 3 Abstract It as under the guidance
Analysis of M/M/n/K Queue with Multiple Priorities
 Analysis of M/M/n/K Queue with Multile Priorities Coyright, Sanjay K. Bose For a P-riority system, class P of highest riority Indeendent, Poisson arrival rocesses for each class with i as average arrival
Analysis of M/M/n/K Queue with Multile Priorities Coyright, Sanjay K. Bose For a P-riority system, class P of highest riority Indeendent, Poisson arrival rocesses for each class with i as average arrival
Mobility-Induced Service Migration in Mobile. Micro-Clouds
 arxiv:503054v [csdc] 7 Mar 205 Mobility-Induced Service Migration in Mobile Micro-Clouds Shiiang Wang, Rahul Urgaonkar, Ting He, Murtaza Zafer, Kevin Chan, and Kin K LeungTime Oerating after ossible Deartment
arxiv:503054v [csdc] 7 Mar 205 Mobility-Induced Service Migration in Mobile Micro-Clouds Shiiang Wang, Rahul Urgaonkar, Ting He, Murtaza Zafer, Kevin Chan, and Kin K LeungTime Oerating after ossible Deartment
On the Role of Finite Queues in Cooperative Cognitive Radio Networks with Energy Harvesting
 On the Role of Finite Queues in Cooerative Cognitive Radio Networks with Energy Harvesting Mohamed A. Abd-Elmagid, Tamer Elatt, and Karim G. Seddik Wireless Intelligent Networks Center (WINC), Nile University,
On the Role of Finite Queues in Cooerative Cognitive Radio Networks with Energy Harvesting Mohamed A. Abd-Elmagid, Tamer Elatt, and Karim G. Seddik Wireless Intelligent Networks Center (WINC), Nile University,
4 Scheduling. Outline of the chapter. 4.1 Preliminaries
 4 Scheduling In this section, e consider so-called Scheduling roblems I.e., if there are altogether M machines or resources for each machine, a roduction sequence of all N jobs has to be found as ell as
4 Scheduling In this section, e consider so-called Scheduling roblems I.e., if there are altogether M machines or resources for each machine, a roduction sequence of all N jobs has to be found as ell as
Adaptive Minimum Symbol-Error-Rate CDMA Linear Multiuser Detector for Pulse-Amplitude Modulation
 Adative Minimum Symbol-Error-Rate CDMA inear Multiuser Detector for Pulse-Amlitude Modulation AK Samingan, S Chen and Hanzo Deartment of Electronics and Comuter Science University of Southamton, Southamton
Adative Minimum Symbol-Error-Rate CDMA inear Multiuser Detector for Pulse-Amlitude Modulation AK Samingan, S Chen and Hanzo Deartment of Electronics and Comuter Science University of Southamton, Southamton
On the Relationship Between Packet Size and Router Performance for Heavy-Tailed Traffic 1
 On the Relationshi Between Packet Size and Router Performance for Heavy-Tailed Traffic 1 Imad Antonios antoniosi1@southernct.edu CS Deartment MO117 Southern Connecticut State University 501 Crescent St.
On the Relationshi Between Packet Size and Router Performance for Heavy-Tailed Traffic 1 Imad Antonios antoniosi1@southernct.edu CS Deartment MO117 Southern Connecticut State University 501 Crescent St.
y p 2 p 1 y p Flexible System p 2 y p2 p1 y p u, y 1 -u, y 2 Component Breakdown z 1 w 1 1 y p 1 P 1 P 2 w 2 z 2
 ROBUSTNESS OF FLEXIBLE SYSTEMS WITH COMPONENT-LEVEL UNCERTAINTIES Peiman G. Maghami Λ NASA Langley Research Center, Hamton, VA 368 Robustness of flexible systems in the resence of model uncertainties at
ROBUSTNESS OF FLEXIBLE SYSTEMS WITH COMPONENT-LEVEL UNCERTAINTIES Peiman G. Maghami Λ NASA Langley Research Center, Hamton, VA 368 Robustness of flexible systems in the resence of model uncertainties at
Research Article An Iterative Algorithm for the Reflexive Solution of the General Coupled Matrix Equations
 he Scientific World Journal Volume 013 Article ID 95974 15 ages htt://dxdoiorg/101155/013/95974 Research Article An Iterative Algorithm for the Reflexive Solution of the General Couled Matrix Euations
he Scientific World Journal Volume 013 Article ID 95974 15 ages htt://dxdoiorg/101155/013/95974 Research Article An Iterative Algorithm for the Reflexive Solution of the General Couled Matrix Euations
Heteroclinic Bifurcation of a Predator-Prey System with Hassell-Varley Functional Response and Allee Effect
 International Journal of ngineering Research And Management (IJRM) ISSN: 49-058 Volume-05 Issue-0 October 08 Heteroclinic Bifurcation of a Predator-Prey System with Hassell-Varley Functional Resonse and
International Journal of ngineering Research And Management (IJRM) ISSN: 49-058 Volume-05 Issue-0 October 08 Heteroclinic Bifurcation of a Predator-Prey System with Hassell-Varley Functional Resonse and
On the Energy-Delay Trade-off of a Two-Way Relay Network
 On the Energy-Delay Trade-off of a To-Way Relay Netork Xiang He Aylin Yener Wireless Communications and Netorking Laboratory Electrical Engineering Department The Pennsylvania State University University
On the Energy-Delay Trade-off of a To-Way Relay Netork Xiang He Aylin Yener Wireless Communications and Netorking Laboratory Electrical Engineering Department The Pennsylvania State University University
LINEAR SYSTEMS WITH POLYNOMIAL UNCERTAINTY STRUCTURE: STABILITY MARGINS AND CONTROL
 LINEAR SYSTEMS WITH POLYNOMIAL UNCERTAINTY STRUCTURE: STABILITY MARGINS AND CONTROL Mohammad Bozorg Deatment of Mechanical Engineering University of Yazd P. O. Box 89195-741 Yazd Iran Fax: +98-351-750110
LINEAR SYSTEMS WITH POLYNOMIAL UNCERTAINTY STRUCTURE: STABILITY MARGINS AND CONTROL Mohammad Bozorg Deatment of Mechanical Engineering University of Yazd P. O. Box 89195-741 Yazd Iran Fax: +98-351-750110
MODELING THE RELIABILITY OF C4ISR SYSTEMS HARDWARE/SOFTWARE COMPONENTS USING AN IMPROVED MARKOV MODEL
 Technical Sciences and Alied Mathematics MODELING THE RELIABILITY OF CISR SYSTEMS HARDWARE/SOFTWARE COMPONENTS USING AN IMPROVED MARKOV MODEL Cezar VASILESCU Regional Deartment of Defense Resources Management
Technical Sciences and Alied Mathematics MODELING THE RELIABILITY OF CISR SYSTEMS HARDWARE/SOFTWARE COMPONENTS USING AN IMPROVED MARKOV MODEL Cezar VASILESCU Regional Deartment of Defense Resources Management
Radial Basis Function Networks: Algorithms
 Radial Basis Function Networks: Algorithms Introduction to Neural Networks : Lecture 13 John A. Bullinaria, 2004 1. The RBF Maing 2. The RBF Network Architecture 3. Comutational Power of RBF Networks 4.
Radial Basis Function Networks: Algorithms Introduction to Neural Networks : Lecture 13 John A. Bullinaria, 2004 1. The RBF Maing 2. The RBF Network Architecture 3. Comutational Power of RBF Networks 4.
Positive decomposition of transfer functions with multiple poles
 Positive decomosition of transfer functions with multile oles Béla Nagy 1, Máté Matolcsi 2, and Márta Szilvási 1 Deartment of Analysis, Technical University of Budaest (BME), H-1111, Budaest, Egry J. u.
Positive decomosition of transfer functions with multile oles Béla Nagy 1, Máté Matolcsi 2, and Márta Szilvási 1 Deartment of Analysis, Technical University of Budaest (BME), H-1111, Budaest, Egry J. u.
ANALYTICAL MODEL FOR THE BYPASS VALVE IN A LOOP HEAT PIPE
 ANALYTICAL MODEL FOR THE BYPASS ALE IN A LOOP HEAT PIPE Michel Seetjens & Camilo Rindt Laboratory for Energy Technology Mechanical Engineering Deartment Eindhoven University of Technology The Netherlands
ANALYTICAL MODEL FOR THE BYPASS ALE IN A LOOP HEAT PIPE Michel Seetjens & Camilo Rindt Laboratory for Energy Technology Mechanical Engineering Deartment Eindhoven University of Technology The Netherlands
Optimal Random Access and Random Spectrum Sensing for an Energy Harvesting Cognitive Radio with and without Primary Feedback Leveraging
 1 Otimal Random Access and Random Sectrum Sensing for an Energy Harvesting Cognitive Radio with and without Primary Feedback Leveraging Ahmed El Shafie, Member, IEEE, arxiv:1401.0340v3 [cs.it] 27 Ar 2014
1 Otimal Random Access and Random Sectrum Sensing for an Energy Harvesting Cognitive Radio with and without Primary Feedback Leveraging Ahmed El Shafie, Member, IEEE, arxiv:1401.0340v3 [cs.it] 27 Ar 2014
CONTROL SYSTEMS, ROBOTICS, AND AUTOMATION Vol. III Stability Theory - Peter C. Müller
 STABILITY THEORY Peter C. Müller University of Wuertal, Germany Keywords: Asymtotic stability, Eonential stability, Linearization, Linear systems, Lyaunov equation, Lyaunov function, Lyaunov stability,
STABILITY THEORY Peter C. Müller University of Wuertal, Germany Keywords: Asymtotic stability, Eonential stability, Linearization, Linear systems, Lyaunov equation, Lyaunov function, Lyaunov stability,
Optimal Random Access and Random Spectrum Sensing for an Energy Harvesting Cognitive Radio with and without Primary Feedback Leveraging
 Otimal Random Access and Random Sectrum Sensing for an Energy Harvesting Cognitive Radio with and without Primary Feedback Leveraging Ahmed El Shafie Wireless Intelligent Networks Center WINC, Nile University,
Otimal Random Access and Random Sectrum Sensing for an Energy Harvesting Cognitive Radio with and without Primary Feedback Leveraging Ahmed El Shafie Wireless Intelligent Networks Center WINC, Nile University,
Shadow Computing: An Energy-Aware Fault Tolerant Computing Model
 Shadow Comuting: An Energy-Aware Fault Tolerant Comuting Model Bryan Mills, Taieb Znati, Rami Melhem Deartment of Comuter Science University of Pittsburgh (bmills, znati, melhem)@cs.itt.edu Index Terms
Shadow Comuting: An Energy-Aware Fault Tolerant Comuting Model Bryan Mills, Taieb Znati, Rami Melhem Deartment of Comuter Science University of Pittsburgh (bmills, znati, melhem)@cs.itt.edu Index Terms
arxiv: v1 [math.fa] 22 Jun 2018
![arxiv: v1 [math.fa] 22 Jun 2018 arxiv: v1 [math.fa] 22 Jun 2018](/thumbs/95/125092124.jpg) MODULATION SPACES WITH SCALING SYMMETRY ÁRPÁD BÉNYI AND TADAHIRO OH arxiv:1806.08587v1 [math.fa] 22 Jun 2018 Abstract. We indicate ho to construct a family of modulation function saces that have a scaling
MODULATION SPACES WITH SCALING SYMMETRY ÁRPÁD BÉNYI AND TADAHIRO OH arxiv:1806.08587v1 [math.fa] 22 Jun 2018 Abstract. We indicate ho to construct a family of modulation function saces that have a scaling
Hölder Inequality with Variable Index
 Theoretical Mathematics & Alications, vol.4, no.3, 204, 9-23 ISSN: 792-9687 (rint), 792-9709 (online) Scienress Ltd, 204 Hölder Ineuality with Variable Index Richeng Liu Abstract By using the Young ineuality,
Theoretical Mathematics & Alications, vol.4, no.3, 204, 9-23 ISSN: 792-9687 (rint), 792-9709 (online) Scienress Ltd, 204 Hölder Ineuality with Variable Index Richeng Liu Abstract By using the Young ineuality,
Analysis of Multi-Hop Emergency Message Propagation in Vehicular Ad Hoc Networks
 Analysis of Multi-Ho Emergency Message Proagation in Vehicular Ad Hoc Networks ABSTRACT Vehicular Ad Hoc Networks (VANETs) are attracting the attention of researchers, industry, and governments for their
Analysis of Multi-Ho Emergency Message Proagation in Vehicular Ad Hoc Networks ABSTRACT Vehicular Ad Hoc Networks (VANETs) are attracting the attention of researchers, industry, and governments for their
ASPECTS OF POLE PLACEMENT TECHNIQUE IN SYMMETRICAL OPTIMUM METHOD FOR PID CONTROLLER DESIGN
 ASES OF OLE LAEMEN EHNIQUE IN SYMMERIAL OIMUM MEHOD FOR ID ONROLLER DESIGN Viorel Nicolau *, onstantin Miholca *, Dorel Aiordachioaie *, Emil eanga ** * Deartment of Electronics and elecommunications,
ASES OF OLE LAEMEN EHNIQUE IN SYMMERIAL OIMUM MEHOD FOR ID ONROLLER DESIGN Viorel Nicolau *, onstantin Miholca *, Dorel Aiordachioaie *, Emil eanga ** * Deartment of Electronics and elecommunications,
Multi-Operation Multi-Machine Scheduling
 Multi-Oeration Multi-Machine Scheduling Weizhen Mao he College of William and Mary, Williamsburg VA 3185, USA Abstract. In the multi-oeration scheduling that arises in industrial engineering, each job
Multi-Oeration Multi-Machine Scheduling Weizhen Mao he College of William and Mary, Williamsburg VA 3185, USA Abstract. In the multi-oeration scheduling that arises in industrial engineering, each job
Robust Performance Design of PID Controllers with Inverse Multiplicative Uncertainty
 American Control Conference on O'Farrell Street San Francisco CA USA June 9 - July Robust Performance Design of PID Controllers with Inverse Multilicative Uncertainty Tooran Emami John M Watkins Senior
American Control Conference on O'Farrell Street San Francisco CA USA June 9 - July Robust Performance Design of PID Controllers with Inverse Multilicative Uncertainty Tooran Emami John M Watkins Senior
Research Article An iterative Algorithm for Hemicontractive Mappings in Banach Spaces
 Abstract and Alied Analysis Volume 2012, Article ID 264103, 11 ages doi:10.1155/2012/264103 Research Article An iterative Algorithm for Hemicontractive Maings in Banach Saces Youli Yu, 1 Zhitao Wu, 2 and
Abstract and Alied Analysis Volume 2012, Article ID 264103, 11 ages doi:10.1155/2012/264103 Research Article An iterative Algorithm for Hemicontractive Maings in Banach Saces Youli Yu, 1 Zhitao Wu, 2 and
Probability Estimates for Multi-class Classification by Pairwise Coupling
 Probability Estimates for Multi-class Classification by Pairwise Couling Ting-Fan Wu Chih-Jen Lin Deartment of Comuter Science National Taiwan University Taiei 06, Taiwan Ruby C. Weng Deartment of Statistics
Probability Estimates for Multi-class Classification by Pairwise Couling Ting-Fan Wu Chih-Jen Lin Deartment of Comuter Science National Taiwan University Taiei 06, Taiwan Ruby C. Weng Deartment of Statistics
Introduction to MVC. least common denominator of all non-identical-zero minors of all order of G(s). Example: The minor of order 2: 1 2 ( s 1)
 Introduction to MVC Definition---Proerness and strictly roerness A system G(s) is roer if all its elements { gij ( s)} are roer, and strictly roer if all its elements are strictly roer. Definition---Causal
Introduction to MVC Definition---Proerness and strictly roerness A system G(s) is roer if all its elements { gij ( s)} are roer, and strictly roer if all its elements are strictly roer. Definition---Causal
Minimax Design of Nonnegative Finite Impulse Response Filters
 Minimax Design of Nonnegative Finite Imulse Resonse Filters Xiaoing Lai, Anke Xue Institute of Information and Control Hangzhou Dianzi University Hangzhou, 3118 China e-mail: laix@hdu.edu.cn; akxue@hdu.edu.cn
Minimax Design of Nonnegative Finite Imulse Resonse Filters Xiaoing Lai, Anke Xue Institute of Information and Control Hangzhou Dianzi University Hangzhou, 3118 China e-mail: laix@hdu.edu.cn; akxue@hdu.edu.cn
Some Unitary Space Time Codes From Sphere Packing Theory With Optimal Diversity Product of Code Size
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 5, NO., DECEMBER 4 336 Some Unitary Sace Time Codes From Shere Packing Theory With Otimal Diversity Product of Code Size Haiquan Wang, Genyuan Wang, and Xiang-Gen
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 5, NO., DECEMBER 4 336 Some Unitary Sace Time Codes From Shere Packing Theory With Otimal Diversity Product of Code Size Haiquan Wang, Genyuan Wang, and Xiang-Gen
NUMERICAL AND THEORETICAL INVESTIGATIONS ON DETONATION- INERT CONFINEMENT INTERACTIONS
 NUMERICAL AND THEORETICAL INVESTIGATIONS ON DETONATION- INERT CONFINEMENT INTERACTIONS Tariq D. Aslam and John B. Bdzil Los Alamos National Laboratory Los Alamos, NM 87545 hone: 1-55-667-1367, fax: 1-55-667-6372
NUMERICAL AND THEORETICAL INVESTIGATIONS ON DETONATION- INERT CONFINEMENT INTERACTIONS Tariq D. Aslam and John B. Bdzil Los Alamos National Laboratory Los Alamos, NM 87545 hone: 1-55-667-1367, fax: 1-55-667-6372
Feedback-Based Iterative Learning Control for MIMO LTI Systems
 International Journal of Control, Feedback-Based Automation, Iterative and Systems, Learning vol. Control 6, no., for. MIMO 69-77, LTI Systems Aril 8 69 Feedback-Based Iterative Learning Control for MIMO
International Journal of Control, Feedback-Based Automation, Iterative and Systems, Learning vol. Control 6, no., for. MIMO 69-77, LTI Systems Aril 8 69 Feedback-Based Iterative Learning Control for MIMO
Infinite Number of Chaotic Generalized Sub-shifts of Cellular Automaton Rule 180
 Infinite Number of Chaotic Generalized Sub-shifts of Cellular Automaton Rule 180 Wei Chen, Fangyue Chen, Yunfeng Bian, Jing Chen School of Science, Hangzhou Dianzi University, Hangzhou, Zhejiang, P. R.
Infinite Number of Chaotic Generalized Sub-shifts of Cellular Automaton Rule 180 Wei Chen, Fangyue Chen, Yunfeng Bian, Jing Chen School of Science, Hangzhou Dianzi University, Hangzhou, Zhejiang, P. R.
Efficient Approximations for Call Admission Control Performance Evaluations in Multi-Service Networks
 Efficient Aroximations for Call Admission Control Performance Evaluations in Multi-Service Networks Emre A. Yavuz, and Victor C. M. Leung Deartment of Electrical and Comuter Engineering The University
Efficient Aroximations for Call Admission Control Performance Evaluations in Multi-Service Networks Emre A. Yavuz, and Victor C. M. Leung Deartment of Electrical and Comuter Engineering The University
Evaluating Circuit Reliability Under Probabilistic Gate-Level Fault Models
 Evaluating Circuit Reliability Under Probabilistic Gate-Level Fault Models Ketan N. Patel, Igor L. Markov and John P. Hayes University of Michigan, Ann Arbor 48109-2122 {knatel,imarkov,jhayes}@eecs.umich.edu
Evaluating Circuit Reliability Under Probabilistic Gate-Level Fault Models Ketan N. Patel, Igor L. Markov and John P. Hayes University of Michigan, Ann Arbor 48109-2122 {knatel,imarkov,jhayes}@eecs.umich.edu
Topic: Lower Bounds on Randomized Algorithms Date: September 22, 2004 Scribe: Srinath Sridhar
 15-859(M): Randomized Algorithms Lecturer: Anuam Guta Toic: Lower Bounds on Randomized Algorithms Date: Setember 22, 2004 Scribe: Srinath Sridhar 4.1 Introduction In this lecture, we will first consider
15-859(M): Randomized Algorithms Lecturer: Anuam Guta Toic: Lower Bounds on Randomized Algorithms Date: Setember 22, 2004 Scribe: Srinath Sridhar 4.1 Introduction In this lecture, we will first consider
Global Behavior of a Higher Order Rational Difference Equation
 International Journal of Difference Euations ISSN 0973-6069, Volume 10, Number 1,. 1 11 (2015) htt://camus.mst.edu/ijde Global Behavior of a Higher Order Rational Difference Euation Raafat Abo-Zeid The
International Journal of Difference Euations ISSN 0973-6069, Volume 10, Number 1,. 1 11 (2015) htt://camus.mst.edu/ijde Global Behavior of a Higher Order Rational Difference Euation Raafat Abo-Zeid The
On the capacity of the general trapdoor channel with feedback
 On the caacity of the general tradoor channel with feedback Jui Wu and Achilleas Anastasooulos Electrical Engineering and Comuter Science Deartment University of Michigan Ann Arbor, MI, 48109-1 email:
On the caacity of the general tradoor channel with feedback Jui Wu and Achilleas Anastasooulos Electrical Engineering and Comuter Science Deartment University of Michigan Ann Arbor, MI, 48109-1 email:
Position Control of Induction Motors by Exact Feedback Linearization *
 BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 8 No Sofia 008 Position Control of Induction Motors by Exact Feedback Linearization * Kostadin Kostov Stanislav Enev Farhat
BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 8 No Sofia 008 Position Control of Induction Motors by Exact Feedback Linearization * Kostadin Kostov Stanislav Enev Farhat
Lecture 7: Linear Classification Methods
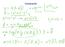 Homeork Homeork Lecture 7: Linear lassification Methods Final rojects? Grous oics Proosal eek 5 Lecture is oster session, Jacobs Hall Lobby, snacks Final reort 5 June. What is linear classification? lassification
Homeork Homeork Lecture 7: Linear lassification Methods Final rojects? Grous oics Proosal eek 5 Lecture is oster session, Jacobs Hall Lobby, snacks Final reort 5 June. What is linear classification? lassification
For q 0; 1; : : : ; `? 1, we have m 0; 1; : : : ; q? 1. The set fh j(x) : j 0; 1; ; : : : ; `? 1g forms a basis for the tness functions dened on the i
 Comuting with Haar Functions Sami Khuri Deartment of Mathematics and Comuter Science San Jose State University One Washington Square San Jose, CA 9519-0103, USA khuri@juiter.sjsu.edu Fax: (40)94-500 Keywords:
Comuting with Haar Functions Sami Khuri Deartment of Mathematics and Comuter Science San Jose State University One Washington Square San Jose, CA 9519-0103, USA khuri@juiter.sjsu.edu Fax: (40)94-500 Keywords:
Power System Reactive Power Optimization Based on Fuzzy Formulation and Interior Point Filter Algorithm
 Energy and Power Engineering, 203, 5, 693-697 doi:0.4236/ee.203.54b34 Published Online July 203 (htt://www.scir.org/journal/ee Power System Reactive Power Otimization Based on Fuzzy Formulation and Interior
Energy and Power Engineering, 203, 5, 693-697 doi:0.4236/ee.203.54b34 Published Online July 203 (htt://www.scir.org/journal/ee Power System Reactive Power Otimization Based on Fuzzy Formulation and Interior
The Recursive Fitting of Multivariate. Complex Subset ARX Models
 lied Mathematical Sciences, Vol. 1, 2007, no. 23, 1129-1143 The Recursive Fitting of Multivariate Comlex Subset RX Models Jack Penm School of Finance and lied Statistics NU College of Business & conomics
lied Mathematical Sciences, Vol. 1, 2007, no. 23, 1129-1143 The Recursive Fitting of Multivariate Comlex Subset RX Models Jack Penm School of Finance and lied Statistics NU College of Business & conomics
A Recursive Block Incomplete Factorization. Preconditioner for Adaptive Filtering Problem
 Alied Mathematical Sciences, Vol. 7, 03, no. 63, 3-3 HIKARI Ltd, www.m-hiari.com A Recursive Bloc Incomlete Factorization Preconditioner for Adative Filtering Problem Shazia Javed School of Mathematical
Alied Mathematical Sciences, Vol. 7, 03, no. 63, 3-3 HIKARI Ltd, www.m-hiari.com A Recursive Bloc Incomlete Factorization Preconditioner for Adative Filtering Problem Shazia Javed School of Mathematical
DEPARTMENT OF ECONOMICS ISSN DISCUSSION PAPER 20/07 TWO NEW EXPONENTIAL FAMILIES OF LORENZ CURVES
 DEPARTMENT OF ECONOMICS ISSN 1441-549 DISCUSSION PAPER /7 TWO NEW EXPONENTIAL FAMILIES OF LORENZ CURVES ZuXiang Wang * & Russell Smyth ABSTRACT We resent two new Lorenz curve families by using the basic
DEPARTMENT OF ECONOMICS ISSN 1441-549 DISCUSSION PAPER /7 TWO NEW EXPONENTIAL FAMILIES OF LORENZ CURVES ZuXiang Wang * & Russell Smyth ABSTRACT We resent two new Lorenz curve families by using the basic
An Investigation on the Numerical Ill-conditioning of Hybrid State Estimators
 An Investigation on the Numerical Ill-conditioning of Hybrid State Estimators S. K. Mallik, Student Member, IEEE, S. Chakrabarti, Senior Member, IEEE, S. N. Singh, Senior Member, IEEE Deartment of Electrical
An Investigation on the Numerical Ill-conditioning of Hybrid State Estimators S. K. Mallik, Student Member, IEEE, S. Chakrabarti, Senior Member, IEEE, S. N. Singh, Senior Member, IEEE Deartment of Electrical
Large inelastic deformation resistance of stiffened panels subjected to lateral loading
 Large inelastic deformation resistance of stiffened anels subjected to lateral loading Zhaolong Yu a, b, Jørgen Amdahl a, b, Yanyan Sha a. Deartment of Marine Technology, oregian University of Science
Large inelastic deformation resistance of stiffened anels subjected to lateral loading Zhaolong Yu a, b, Jørgen Amdahl a, b, Yanyan Sha a. Deartment of Marine Technology, oregian University of Science
Recursive Estimation of the Preisach Density function for a Smart Actuator
 Recursive Estimation of the Preisach Density function for a Smart Actuator Ram V. Iyer Deartment of Mathematics and Statistics, Texas Tech University, Lubbock, TX 7949-142. ABSTRACT The Preisach oerator
Recursive Estimation of the Preisach Density function for a Smart Actuator Ram V. Iyer Deartment of Mathematics and Statistics, Texas Tech University, Lubbock, TX 7949-142. ABSTRACT The Preisach oerator
4. Score normalization technical details We now discuss the technical details of the score normalization method.
 SMT SCORING SYSTEM This document describes the scoring system for the Stanford Math Tournament We begin by giving an overview of the changes to scoring and a non-technical descrition of the scoring rules
SMT SCORING SYSTEM This document describes the scoring system for the Stanford Math Tournament We begin by giving an overview of the changes to scoring and a non-technical descrition of the scoring rules
Feedback-error control
 Chater 4 Feedback-error control 4.1 Introduction This chater exlains the feedback-error (FBE) control scheme originally described by Kawato [, 87, 8]. FBE is a widely used neural network based controller
Chater 4 Feedback-error control 4.1 Introduction This chater exlains the feedback-error (FBE) control scheme originally described by Kawato [, 87, 8]. FBE is a widely used neural network based controller
Supplementary Materials for Robust Estimation of the False Discovery Rate
 Sulementary Materials for Robust Estimation of the False Discovery Rate Stan Pounds and Cheng Cheng This sulemental contains roofs regarding theoretical roerties of the roosed method (Section S1), rovides
Sulementary Materials for Robust Estimation of the False Discovery Rate Stan Pounds and Cheng Cheng This sulemental contains roofs regarding theoretical roerties of the roosed method (Section S1), rovides
Uncorrelated Multilinear Principal Component Analysis for Unsupervised Multilinear Subspace Learning
 TNN-2009-P-1186.R2 1 Uncorrelated Multilinear Princial Comonent Analysis for Unsuervised Multilinear Subsace Learning Haiing Lu, K. N. Plataniotis and A. N. Venetsanooulos The Edward S. Rogers Sr. Deartment
TNN-2009-P-1186.R2 1 Uncorrelated Multilinear Princial Comonent Analysis for Unsuervised Multilinear Subsace Learning Haiing Lu, K. N. Plataniotis and A. N. Venetsanooulos The Edward S. Rogers Sr. Deartment
Modeling Residual-Geometric Flow Sampling
 1 Modeling Residual-Geometric Flow Samling Xiaoming Wang, Xiaoyong Li, and Dmitri Loguinov Abstract Traffic monitoring and estimation of flow arameters in high seed routers have recently become challenging
1 Modeling Residual-Geometric Flow Samling Xiaoming Wang, Xiaoyong Li, and Dmitri Loguinov Abstract Traffic monitoring and estimation of flow arameters in high seed routers have recently become challenging
Bayesian System for Differential Cryptanalysis of DES
 Available online at www.sciencedirect.com ScienceDirect IERI Procedia 7 (014 ) 15 0 013 International Conference on Alied Comuting, Comuter Science, and Comuter Engineering Bayesian System for Differential
Available online at www.sciencedirect.com ScienceDirect IERI Procedia 7 (014 ) 15 0 013 International Conference on Alied Comuting, Comuter Science, and Comuter Engineering Bayesian System for Differential
Optimal Design of Truss Structures Using a Neutrosophic Number Optimization Model under an Indeterminate Environment
 Neutrosohic Sets and Systems Vol 14 016 93 University of New Mexico Otimal Design of Truss Structures Using a Neutrosohic Number Otimization Model under an Indeterminate Environment Wenzhong Jiang & Jun
Neutrosohic Sets and Systems Vol 14 016 93 University of New Mexico Otimal Design of Truss Structures Using a Neutrosohic Number Otimization Model under an Indeterminate Environment Wenzhong Jiang & Jun
CSE 599d - Quantum Computing When Quantum Computers Fall Apart
 CSE 599d - Quantum Comuting When Quantum Comuters Fall Aart Dave Bacon Deartment of Comuter Science & Engineering, University of Washington In this lecture we are going to begin discussing what haens to
CSE 599d - Quantum Comuting When Quantum Comuters Fall Aart Dave Bacon Deartment of Comuter Science & Engineering, University of Washington In this lecture we are going to begin discussing what haens to
Symbolic Dynamics of Digital Signal Processing Systems
 Symbolic Dynamics of Digital Signal Processing Systems Dr. Bingo Wing-Kuen Ling School of Engineering, University of Lincoln. Brayford Pool, Lincoln, Lincolnshire, LN6 7TS, United Kingdom. Email: wling@lincoln.ac.uk
Symbolic Dynamics of Digital Signal Processing Systems Dr. Bingo Wing-Kuen Ling School of Engineering, University of Lincoln. Brayford Pool, Lincoln, Lincolnshire, LN6 7TS, United Kingdom. Email: wling@lincoln.ac.uk
This document is downloaded from DR-NTU, Nanyang Technological University Library, Singapore.
 This document is donloaded from DR-NTU, Nanyang Technological University Library, Singapore. Title Amplify-and-forard based to-ay relay ARQ system ith relay combination Author(s) Luo, Sheng; Teh, Kah Chan
This document is donloaded from DR-NTU, Nanyang Technological University Library, Singapore. Title Amplify-and-forard based to-ay relay ARQ system ith relay combination Author(s) Luo, Sheng; Teh, Kah Chan
The non-stochastic multi-armed bandit problem
 Submitted for journal ublication. The non-stochastic multi-armed bandit roblem Peter Auer Institute for Theoretical Comuter Science Graz University of Technology A-8010 Graz (Austria) auer@igi.tu-graz.ac.at
Submitted for journal ublication. The non-stochastic multi-armed bandit roblem Peter Auer Institute for Theoretical Comuter Science Graz University of Technology A-8010 Graz (Austria) auer@igi.tu-graz.ac.at
Towards understanding the Lorenz curve using the Uniform distribution. Chris J. Stephens. Newcastle City Council, Newcastle upon Tyne, UK
 Towards understanding the Lorenz curve using the Uniform distribution Chris J. Stehens Newcastle City Council, Newcastle uon Tyne, UK (For the Gini-Lorenz Conference, University of Siena, Italy, May 2005)
Towards understanding the Lorenz curve using the Uniform distribution Chris J. Stehens Newcastle City Council, Newcastle uon Tyne, UK (For the Gini-Lorenz Conference, University of Siena, Italy, May 2005)
A Note on Guaranteed Sparse Recovery via l 1 -Minimization
 A Note on Guaranteed Sarse Recovery via l -Minimization Simon Foucart, Université Pierre et Marie Curie Abstract It is roved that every s-sarse vector x C N can be recovered from the measurement vector
A Note on Guaranteed Sarse Recovery via l -Minimization Simon Foucart, Université Pierre et Marie Curie Abstract It is roved that every s-sarse vector x C N can be recovered from the measurement vector
Paper C Exact Volume Balance Versus Exact Mass Balance in Compositional Reservoir Simulation
 Paer C Exact Volume Balance Versus Exact Mass Balance in Comositional Reservoir Simulation Submitted to Comutational Geosciences, December 2005. Exact Volume Balance Versus Exact Mass Balance in Comositional
Paer C Exact Volume Balance Versus Exact Mass Balance in Comositional Reservoir Simulation Submitted to Comutational Geosciences, December 2005. Exact Volume Balance Versus Exact Mass Balance in Comositional
Time Domain Calculation of Vortex Induced Vibration of Long-Span Bridges by Using a Reduced-order Modeling Technique
 2017 2nd International Conference on Industrial Aerodynamics (ICIA 2017) ISBN: 978-1-60595-481-3 Time Domain Calculation of Vortex Induced Vibration of Long-San Bridges by Using a Reduced-order Modeling
2017 2nd International Conference on Industrial Aerodynamics (ICIA 2017) ISBN: 978-1-60595-481-3 Time Domain Calculation of Vortex Induced Vibration of Long-San Bridges by Using a Reduced-order Modeling
A Performance Evaluation of KANBAN, CONWIP and Base-stock
 Deartment of Social Systems and Management Discussion Paer Series No.0 A Performance Evaluation of KANBAN, ONWIP and Base-stock in Serial Production Lines y Yaghou Khojasteh-Ghamari, Ryo Sato Aril 008
Deartment of Social Systems and Management Discussion Paer Series No.0 A Performance Evaluation of KANBAN, ONWIP and Base-stock in Serial Production Lines y Yaghou Khojasteh-Ghamari, Ryo Sato Aril 008
Nonlinear Parameter Estimation Based on History Matching of Temperature Measurements for Single-Phase Liquid-Water Geothermal Reservoirs
 Proceedings World Geothermal Congress 015 Melbourne, Australia, 19-5 Aril 015 Nonlinear Parameter Estimation Based on History Matching of Temerature Measurements for Single-Phase Liquid-Water Geothermal
Proceedings World Geothermal Congress 015 Melbourne, Australia, 19-5 Aril 015 Nonlinear Parameter Estimation Based on History Matching of Temerature Measurements for Single-Phase Liquid-Water Geothermal
Eigenanalysis of Finite Element 3D Flow Models by Parallel Jacobi Davidson
 Eigenanalysis of Finite Element 3D Flow Models by Parallel Jacobi Davidson Luca Bergamaschi 1, Angeles Martinez 1, Giorgio Pini 1, and Flavio Sartoretto 2 1 Diartimento di Metodi e Modelli Matematici er
Eigenanalysis of Finite Element 3D Flow Models by Parallel Jacobi Davidson Luca Bergamaschi 1, Angeles Martinez 1, Giorgio Pini 1, and Flavio Sartoretto 2 1 Diartimento di Metodi e Modelli Matematici er
Multiplicity of weak solutions for a class of nonuniformly elliptic equations of p-laplacian type
 Nonlinear Analysis 7 29 536 546 www.elsevier.com/locate/na Multilicity of weak solutions for a class of nonuniformly ellitic equations of -Lalacian tye Hoang Quoc Toan, Quô c-anh Ngô Deartment of Mathematics,
Nonlinear Analysis 7 29 536 546 www.elsevier.com/locate/na Multilicity of weak solutions for a class of nonuniformly ellitic equations of -Lalacian tye Hoang Quoc Toan, Quô c-anh Ngô Deartment of Mathematics,
Mean Square Stability Analysis of Sampled-Data Supervisory Control Systems
 17th IEEE International Conference on Control Alications Part of 28 IEEE Multi-conference on Systems and Control San Antonio, Texas, USA, Setember 3-5, 28 WeA21 Mean Square Stability Analysis of Samled-Data
17th IEEE International Conference on Control Alications Part of 28 IEEE Multi-conference on Systems and Control San Antonio, Texas, USA, Setember 3-5, 28 WeA21 Mean Square Stability Analysis of Samled-Data
Cost and benefit including value of life and limb measured in time units
 Secial Worksho on Risk Accetance and Risk Communication March 26-27, 2007, Stanford University Cost and benefit including value of life and limb measured in time units Ove Ditlevsen and Peter Friis-Hansen
Secial Worksho on Risk Accetance and Risk Communication March 26-27, 2007, Stanford University Cost and benefit including value of life and limb measured in time units Ove Ditlevsen and Peter Friis-Hansen
Existence and nonexistence of positive solutions for quasilinear elliptic systems
 ISSN 1746-7233, England, UK World Journal of Modelling and Simulation Vol. 4 (2008) No. 1,. 44-48 Existence and nonexistence of ositive solutions for uasilinear ellitic systems G. A. Afrouzi, H. Ghorbani
ISSN 1746-7233, England, UK World Journal of Modelling and Simulation Vol. 4 (2008) No. 1,. 44-48 Existence and nonexistence of ositive solutions for uasilinear ellitic systems G. A. Afrouzi, H. Ghorbani
On Wald-Type Optimal Stopping for Brownian Motion
 J Al Probab Vol 34, No 1, 1997, (66-73) Prerint Ser No 1, 1994, Math Inst Aarhus On Wald-Tye Otimal Stoing for Brownian Motion S RAVRSN and PSKIR The solution is resented to all otimal stoing roblems of
J Al Probab Vol 34, No 1, 1997, (66-73) Prerint Ser No 1, 1994, Math Inst Aarhus On Wald-Tye Otimal Stoing for Brownian Motion S RAVRSN and PSKIR The solution is resented to all otimal stoing roblems of
arxiv: v1 [quant-ph] 20 Jun 2017
![arxiv: v1 [quant-ph] 20 Jun 2017 arxiv: v1 [quant-ph] 20 Jun 2017](/thumbs/74/71431394.jpg) A Direct Couling Coherent Quantum Observer for an Oscillatory Quantum Plant Ian R Petersen arxiv:76648v quant-h Jun 7 Abstract A direct couling coherent observer is constructed for a linear quantum lant
A Direct Couling Coherent Quantum Observer for an Oscillatory Quantum Plant Ian R Petersen arxiv:76648v quant-h Jun 7 Abstract A direct couling coherent observer is constructed for a linear quantum lant
Modeling Pointing Tasks in Mouse-Based Human-Computer Interactions
 Modeling Pointing Tasks in Mouse-Based Human-Comuter Interactions Stanislav Aranovskiy, Rosane Ushirobira, Denis Efimov, Géry Casiez To cite this version: Stanislav Aranovskiy, Rosane Ushirobira, Denis
Modeling Pointing Tasks in Mouse-Based Human-Comuter Interactions Stanislav Aranovskiy, Rosane Ushirobira, Denis Efimov, Géry Casiez To cite this version: Stanislav Aranovskiy, Rosane Ushirobira, Denis
Combining Logistic Regression with Kriging for Mapping the Risk of Occurrence of Unexploded Ordnance (UXO)
 Combining Logistic Regression with Kriging for Maing the Risk of Occurrence of Unexloded Ordnance (UXO) H. Saito (), P. Goovaerts (), S. A. McKenna (2) Environmental and Water Resources Engineering, Deartment
Combining Logistic Regression with Kriging for Maing the Risk of Occurrence of Unexloded Ordnance (UXO) H. Saito (), P. Goovaerts (), S. A. McKenna (2) Environmental and Water Resources Engineering, Deartment
