Research on Feature Selection in Power User Identification
|
|
|
- Mabel Norman
- 5 years ago
- Views:
Transcription
1 Mathematics and Computer Science 2018; 3(3): doi: /j.mcs ISSN: (Print); ISSN: (Online) Research on Feature Selection in Power User Identification Qiu Yanhao 1, Song Xiaoyu 2, *, Sun Xiangyang 2, Zhao Yang 2 1 College of Engineering, Virginia Polytechnic Institute and State University, Virginia, The United States 2 School of Electronic and Information Engineering, Lanzhou Jiaotong University, Lanzhou, China address: * Corresponding author To cite this article: Qiu Yanhao, Song Xiaoyu, Sun Xiangyang, Zhao Yang. Research on Feature Selection in Power User Identification. Mathematics and Computer Science. Vol. 3, No. 3, 2018, pp doi: /j.mcs Received: April 18, 2018; Accepted: May 7, 2018; Published: June 1, 2018 Abstract: In the previous study of user identification, most of the researchers improved the recognition algorithm. In this paper, we use large data technology to extract electricity feature from different angles and study the impact of different features on recognition. Firstly, the raw data was cleaned. In order to obtain the key information of power theft user identification, the features of the data set are extracted from three aspects: basic attribute feature, statistical feature under different time scale and similarity feature under different time scale. Then we use feature sets of different combinations to carry out experiments under the KNN model, the random forest (RF) model and the XGBoost model. The experimental results show that the experimental results of the BF+SF+PF feature set in the three classifiers are obviously better than the other two feature sets. Therefore, it is concluded that different features have obvious effects on the recognition results. Keywords: Feature Selection, Power User Identification, KNN, Random Forest, XG Boost 1. Introduction The power industry is the basic industry in the national economy, which is related to the national economy and the people's livelihood, and has the nature of public service. The development of electricity is the basic guarantee for social progress and the improvement of the people's lives. To ensure the development of electricity, it is necessary for power grid enterprises to recover electricity in time,and it is also the inevitable choice to protect the state-owned assets and maintain the market order. However, for a variety of reasons, electricity theft is still widespread, and part of the region is even rampant. The loss of electricity stealing to the power grid enterprises is huge [1]. According to incomp - lete statistics, the economic losses caused by electricity theft in the United States are as high as 4 billion dollars a year. Canada has lost 500 million Canadian dollars a year. Israel loses 40 million dollars a year. And the number in China is up to 20 billion yuan. Southeast Asian countries such as India and Philippines are more serious [2]. With the rapid development of power big data, the use of big data technology to monitor and detect the stealing users of power system has become the trend for the power industry [3]. With the help of big data, the monitoring of electricity users' behavior and identification of electricity stealing behavior can reduce the time and cost of abnormal behavior analysis, improve the recognition rate of abnormal behavior and reduce the operation cost of electric power company. Many experts at home and abroad have done research on the recognition of electricity stealing users [4-6]. In 2014, Jian Fujun et al quantized the preprocessed data to form feature vectors. Then, the feature vectors were sent to the One-class SVM classifier to identify the users of the electricity stealing [7]. In 2011, Chen et al. used the clustering method of K-means and suffix tree to identify the electricity stealing behavior with using electricity as the feature value [8]. In 2008, Nizar et al. obtained the feature curve of each user by clustering the power consumption curve, and then, according to the deviation degree of the electricity consumption curve and the feature curve, divided the user into two categories: normal and abnormal [9]. However, in the past research, the feature value of the user is relatively simple, and there is no systematic research on the feature value of the user. In the field of data mining, the character value is closely related to the accuracy of the classification. The original data, due to the huge amount of information, is redundant. Extracting feature can not only reduce redundancy, but also make meaningful variables of data become clearer, which is conducive
2 68 Qiu Yanhao et al.: Research on Feature Selection in Power User Identification to later algorithm recognition. This paper uses large data analysis technology to identify the users of electricity stealing. By comparing experimental results with different feature, it shows that the selection of feature affects the recognition results. Firstly, the original data is preprocessed, including processing the vacancy value and repeated records. The feature are constructed from three aspects: the basic attribute features, the statistical features at different time scales and the similarity features at different time scales. Subsequently, nine groups of experiments are carried out using three different feature sets under the KNN model, the random forest model and the XGBoost model. Finally, the experimental results were analyzed. 2. Pearson Correlation Coefficient The Pearson correlation coefficient, also known as the Pearson product-moment correlation coefficient, is a linear correlation coefficient [10]. The Pearson correlati- on coefficient is used to measure the correlation between the two variables, and the Pearson correlation co- efficient formula is as follows: ρx, Y = corr( X, Y) cov( X, Y) = δ δ X Y E[( X ux )( Y uy )] = δ δ X Y (1) distributed in a two-dimensional space. It is necessary to analyze the correlation between X axis and Y axis of data points in some problems. If the correlation degree between X and Y is small, but the distribution of data is discrete, it will lead to the bigger covariance difference. It is not reasonable to use this value to measure the correlation degree. In order to better measure the correlation degree of two random variables, the Pearson correlation coefficient is introduced. It is easy to get that the Pearson correlation coefficient is a value between -1 and 1. When the linear relationship between the two variables is enhanced, the correlation coefficient tends to 1 or -1. When one variable increases and another variable also increases, it shows that they are positive correlation and the correlation coefficient is greater than 0. If one variable increases, but the other is reduced, it indicates that they are negatively correlated, and the correlation coefficient is less than 0. If the correlation coefficient is equal to 0, it shows that there is no linear correlation between them. 3. Recognition Model 3.1. Data Preprocessing The problems of the original data are missing values and repeated records. These problems affect the efficiency of the Classification results, so data preprocessing is the first step of this study. For repeated records, reprocessing is performed according to the main attribute. The treatment of missing values needs careful consideration. The methods of dealing with the missing value are: ignoring the record, removing the attributes, filling the vacancy manually, using default values, using mean values, inserting values using Lagrange interpolation or Newton interpolation [11]. The Newton interpolation method is used in this paper. Newton interpolation is much simpler. Compared with the Lagrange interpolation, it not only over- comes the shortcoming that the whole calculation work must be restarted when adding a node, but also saves the multiplication and division operation times Feature Extraction Figure 1. Data distribution map. It is known from the formula that the Pearson correlation coefficient is derived from the standard deviation of the covariance divided by two variables. Although covariance can reflect the correlation degree of two random variables (covariance is greater than 0, it indicates a positive correlation between them. When less than 0, it indicates a negative correlation between them), however, the difference of covariance does not well measure the correlation degree of two random variables. As shown in Figure 1, some data are Feature extraction refers to the extraction of key features from the original data as needed. In order to extract more useful information, it is necessary to build new attributes on the basis of existing attributes. In this paper, feature extraction is carried out from the following aspects: (1) Basic attribute features (BF) The statistical features of each user ID are recorded, including maximum, minim- um, mean, variance, median and number of records and so on. The number of records is closely related to the statistical features. These are the basic features of electricity user. (2) Statistical features at different time scales (SF) One is electricity consumption of the user in every 3 days, per month, 3 months and half year. The other is record number of the user in every 3 days, per month, 3 months and half year. The
3 Mathematics and Computer Science 2018; 3(3): features of different time scales provide important information for the detection of different types of abnormal user. (3) Similarity features at different time scales (PF) The Pearson Correlation Coefficient is used to measure the correlation between two variables. The Pearson correlation coefficient of power consumption, power starting degree and power termination degree are calculated during per 4 weeks and 5 weeks. 4. Results and Evaluation 4.1. Data Set The sample data comes from the State Grid Gansu Electric Power Company, which contains 6 million 300 thousand electricity consumption records of 9956 power customers of the customers have been identified as stealing users through offline investigation, and the rest are normal users. Each user's data includes the user's daily electricity consumption, the day and yesterday's electricity consumption Evaluation Method Confusion Matrix The confusion matrix is the analysis table that summarizes the classification model prediction results in machine learning [12-13]. In the form of matrix, the records of the data set are collected in accordance with the two criteria, which are the real category and the categories predicted by the classification. The confusion matrix shown in Table 1 shows all possible classification results of the classifier. Each column represents the predicted value, and each row represents the actual category. User identification of electricity stealing is essentially a binary classifier classification problem, and all users are divided into two categories: normal users and stealing users. In this paper, positive and negative correspond to stealing users and normal users respectively. Table 1. The confusion matrix form. Predicted value actual value Positive Negative Positive True positive (TP) False positive (FP) Negative False negative (FN) True negative (TN) FP is the first type of error, and FN is the second type. On the basis of confusion matrix, the evaluation indexes of classifiers can be derived: accuracy (ACC) and the true positive rate (TPR) [14]. Accuracy describes the classification accuracy of the classifier. The true positive rate is also called sensitivity. It describes the sensitivity of classifiers. TP + TN ACC = TP + FP + TN + FN TP TPR = TP + FN ROC Curve and AUC The ROC curve (receiver operating feature curve, the feature curve of the subject) is a graphical method of displaying the compromise between the true rate (TPR) and the false positive rate (FPR) of the classifier [15]. In a two classification model, for the continuous result, it is assumed that a threshold has been determined. For example, 0.6, the instance that is greater than this value is classified as a positive class, and the instance less than that is assigned to the negative class. If the threshold is reduced to 0.5, more classes can be identified. This is to improve the ratio of positive cases to all positive cases, that is TPR, but at the same time, more negative examples are also taken as a positive example, that is, the increase of FPR. In order to visualize this change, the ROC is introduced here, and the ROC curve can be used to accurately evaluate a classifier. The curve closed point (0, 1) shows the best classification effect [16] Experimental Results The software used in this experiment is R on the computer (2) with Intel Corei5-4210, 2.4 Ghz, 8 G, win10x64. Using three different combinations of features, experiments were carried out under KNN classifier, random forest classifier and XGBOOST classifier. There are nine groups of experiments in this paper, the first three groups are carried out using three different feature sets under the KNN model, and the middle three groups are carried out using three different feature sets under the random forest model. The last three groups are carried out using three different feature sets under the XGBoost model. The experiments are conducted 5 times and carried out under different recognition models. KNN classifier takes K=50. In the BP neural network, the hidden layer unit is 8. The training algorithm used Quick Prop. The algorithm parameters are 0.1, 2, , 0.1. The maximum number of iterations is The XGBoost parameters are divided into three kinds: general parameters, booster parameter and learning target parameter [17-18]. In this experiment, the booster parameter shrinkage step size (ETA) is selected 0.01 to prevent overfitting, and the maximum iteration number (nrounds) is selected The minimum sample weight of child nodes (min child weight) is selected 10. The ratio of feature sampling (colsample by tree) is 0.8. In the learning target parameters, the objective function selects binary logistic regression (binary logistic), and the evaluating indicator is the average accuracy (map). The rest parameters keep the default value. The results are as follows. The first group of experiments used features of three different combinations to test under the KNN model. the experimental results are as follows:
4 70 Qiu Yanhao et al.: Research on Feature Selection in Power User Identification Table 2. Results of five experiments under BF--KNN model % 40.29% % 37.77% BF KNN % 35.25% % 38.49% % 35.97% Average 64.39% 37.55% Table 3. Results of five experiments under BF+SF--KNN model % 53.60% % 46.40% BF+SF KNN % 48.92% % 50.36% % 47.84% Average 69.53% 49.42% Table 4. Results of five experiments under BF+SF+PF--KNN model % 54.68% % 52.52% BF+SF+PF KNN % 55.76% % 54.32% % 54.68% Average 74.21% 54.39% From the above table, it can be seen that the average ACC and TPR of the KNN model are 64.39% and 37.55% respectively, when only BF is used. The average ACC and TPR of the KNN model are 69.53% and 49.42% respectively, when BF and SF are used. The average ACC and TPR of the KNN model are 74.21% and 54.39% respectively, when BF, SF and PF are used. Through the above results, it can be seen that, under the KNN model, the difference of ACC and TPR is obvious under different features. Under BF+SF+PF, the recogni- tion results are best, followed by BF+SF, and BF is the worst. Figure 2-4 is the ROC curve of the three experiments. From the ROC curve, it can be seen that under different characteristics, the degree of curve approaching 1 is also different. Among them, BF+SF+PF is the best and BF is the worst. Figure 2. ROC curve of BF--KNN model.
5 Mathematics and Computer Science 2018; 3(3): Figure 3. ROC curve of BF+SF--KNN model. Figure 4. ROC curve of BF+SF+PF--KNN model. The second group of experiments used features of three different combinations to test under the random forest model. The experimental results are as follows. Table 5. Results of five experiments under BF--RF model % 51.08% % 52.52% BF RF % 45.68% % 45.32% % 46.40% Average 69.64% 48.20%
6 72 Qiu Yanhao et al.: Research on Feature Selection in Power User Identification Table 6. Results of five experiments under BF+SF--RF model. BF+SF RF % 52.88% % 52.16% % 51.08% % 50.72% % 55.04% Average 72.45% 52.37% Table 7. Results of five experiments under BF+SF+PF--RF model. BF+SF+PF RF % 75.90% % 74.10% % 76.26% % 74.82% % 78.06% Average 79.60% 75.83% From the above table, it can be seen that the average ACC and TPR of the random forest model are 69.64% and 48.20% respectively, when BF is used. The average ACC and TPR of the random forest model are 72.45% and 52.37% respectively, when BF and SF are used. The average ACC and TPR of the random forest model are 79.60% and 75.83% respectively, when BF, SF and PF are used. when BF, SF and PF are used. Through the above results, it can be seen that, under the random forest model, the difference of ACC and TPR is obvious under different features. Under BF+SF+PF, the recognition results are best, followed by BF+SF, and BF is the worst. Figure 5-7 is the ROC curve of the three experiments. From the ROC curve, it can be seen that under different characteristics, the degree of curve approaching 1 is also different. Among them, BF+SF+PF is the best and BF is the worst. Figure 5. ROC curve of BF--RF model.
7 Mathematics and Computer Science 2018; 3(3): Figure 6. ROC curve of BF+SF--RF model. Figure 7. ROC curve of BF+SF+PF--RF model. The third group of experiments used features of three different combinations to test under the XGBoost model. The experimental results are as follows:
8 74 Qiu Yanhao et al.: Research on Feature Selection in Power User Identification Table 8. Results of five experiments under BF--XGBoost model % 78.42% % 74.10% BF XGBoost % 75.90% % 75.18% % 77.70% Average 77.45% 76.26% Table 9. Results of five experiments under BF+SF--XGBoost model % 76.98% % 77.34% BF+SF XGBoost % 75.18% % 75.54% % 77.34% Average 80.83% 76.47% Table 10. Results of five experiments under BF+SF+PF--XGBoost model % 75.18% % 78.78% BF+SF+PF XGBoost % 78.78% % 77.70% % 78.42% Average 81.51% 77.77% From the above table, it can be seen that the average ACC and TPR of the XGBoost model are 77.45% and 76.26% respectively, when only BF is used. The average ACC and TPR of the XGBoost model are 80.83% and 76.47% respectively, when BF and SF are used. The average ACC and TPR of the XGBoost model are 81.51% and 77.77% respectively, when BF, SF and PF are used. when BF, SF and PF are used. Through the above results, it can be seen that, under the XGBoost model, the difference of ACC and TPR is obvious under different features. Under BF+SF+PF, the recognition results are best, followed by BF+SF, and BF is the worst. Figure 8-10 is the ROC curve of the three experiments. From the ROC curve, it can be seen that under different characteristics, the degree of curve approaching 1 is also different. Among them, BF+SF+PF is the best and BF is the worst. Figure 8. ROC curve of BF--XGBoost model.
9 Mathematics and Computer Science 2018; 3(3): Figure 9. ROC curve of BF+SF--XGBoost model. Figure 10. ROC curve of BF+SF+PF--XGBoost model. In order to compare, tables 11 and 12 are obtained by summarizing the results. The values in the table are the average values of each set of experimental results. Table 11. ACC value of evaluation indicators. ACC KNN RF XGBoost BF 64.39% 69.64% 77.45% BF+SF 69.53% 72.45% 80.83% BF+SF+PF 74.21% 79.60% 81.51% It can be seen from the table 11 that ACC of BF+SF+PF feature set increases by 9.82% and 4.68% compared with BF feature set and BF+SF feature set under KNN classifier. ACC of BF+SF+PF feature set increases by 9.96% and 7.15% compared with BF feature set and BF+SF feature set under random forest classifier. ACC of BF+SF+PF feature set increases by 4.06% and 0.68% compared with BF feature set and BF+SF feature set under XGBoost classifier. BF+SF+PF. Table 12. TPR value of evaluation indicators. TPR KNN RF XGBoost BF 37.55% 48.20% 76.26% BF+SF 49.42% 52.37% 76.47% BF+SF+PF 54.39% 75.83% 77.77%
10 76 Qiu Yanhao et al.: Research on Feature Selection in Power User Identification It can be seen from the above table 12 that TPR of BF+SF+PF feature set increases by 16.84% and 4.97% compared with BF feature set and BF+SF feature set under KNN classifier. TPR of BF+SF+PF feature set increases by 27.63% and 23.46% compared with BF feature set and BF+SF feature set under random forest classifier. TPR of BF+SF+PF feature set increases by 1.51% and 1.3% compared with BF feature set and BF+SF feature set under XGBoost classifier. BF+ SF+ PF. Therefore, through the above results, it can be concluded that the selection of features has a great influence on the recognition results. 5. Conclusion With the continuous improvement of information degree in power system and the rapid growth of electricity consumption data, it is important to study the analysis technology suitable for power big data, which is of great significance for the innovation of power business mode and the development of smart grid. In this paper, the features of three different combinations are constructed under the KNN model, the random forest model and the XGBoost model, nine groups of experiments are carried out to study the effect of feature selection on the identification of electricity stealing user. From the experimental results, it can be seen that the characteristics of different combinations have obvious impact on the experimental results, the more features that can characterize the behavior of users, have better results. From another point of view, it can be found that different classifiers have influence on the recognition results. In further, more effective feature will be obtained to improve the accuracy of recognition. Acknowledgements This work is supported by National Natural Science Foundation of China ( ). References [1] Song Y, Zhou G, Zhu Y. Present Status and Challenges of Big Data Processing in Smart Grid. Power System Technology, 2013, 37(4): [2] Tan Z. Design and implementation of online abnormal electricity utilization and risk monitoring system based on electricity behavior analysis. South China University of Technology, [3] Chen W, Chen Y, Qiu L, et al. Analysis of anti-stealing electric power based on big data technology. Journal of Electronic Measurement & Instrumentation, [4] Zhuang C, Zhang B, Jun H U, et al. Anomaly Detection for Power Consumption Patterns Based on Unsupervised Learning. Proceedings of the Csee, [5] Zhou L, Zhao L, Gao W. Application of Sparse Coding in Detection for Abnormal Electricity Consumption Behaviors. Power System Technology, 2015 [6] Monedero I, Biscarri F, León C, et al. Detection of frauds and other non-technical losses in a power utility using Pearson coefficient, Bayesian networks and decision trees. International Journal of Electrical Power & Energy Systems, 2012, 34(1): [7] Jian F J, Cao M, Wang L, et al. SVM Based Energy Consumption Abnormality Detection in AMI System. Electrical Measurement & Instrumentation, [8] Chen C, Cook D J. Energy Outlier Detection in Smart Environments// Artificial Intelligence and Smarter Living: the Conquest of Complexity, Papers From the 2011 AAAI Workshop, San Francisco, California, Usa, August [9] Nizar A H, Dong Z Y, Wang Y. Power utility nontechnical loss analysis with extreme learning machine method. IEEE Transactions on Power Systems, 2008, 23(3): [10] Geng Y J, Zhang J Y, Yuan X G. A feature relevance measure based on sparse representation coefficient. Pa- ttern Recognition & Artificial Intelli- gence, 2013, 26(1): [11] Zhang Y, Shang C. Combining Newton interpolation and deep learning for image classification. Electronics Letters, 2015, 51(1): [12] Kong Y H, Jing M L. Research of the Classification Method Based on Confu- sion Matrixes and Ensemble Learning. Computer Engineering & Science, 2012, 34(6): [13] Song Y F, Wang X D, Lei L. Evaluating evidence reliability based on confusion matrix. XI Tong Gong Cheng Yu Dian Zi Ji Shu/systems Engineering & Elec- tronics, 2015, 37(4): [14] Huang Y A, You Z H, Gao X, et al. Using Weighted Sparse Representation Model Combined with Discrete Cosine Transformation to Predict Protein-Protein Interactions from Protein Sequence. Biomed Research International, 2015, 2015: [15] Song H L, He J, Huang P X, et al. Application of parametric method and non-parametric method in estimation of area under ROC curve. Academic Journal of Second Military Medical University, 2006, 27(7): [16] Fawcett T. An introduction to ROC analysis. Pattern Recognition Letters, 2006, 27(8): [17] Chen T, Guestrin C. XGBoost:A Scalable Tree Boosting System// ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. ACM, 2016: [18] Zhang L, Zhan C. Machine Learning in Rock Facies Classification: An Applic- ation of XGBoost// International Geophysical Conference, Qingdao, China, April. 2017:
The Abnormal Electricity Consumption Detection System Based on the Outlier Behavior Pattern Recognition
 2017 International Conference on Energy, Power and Environmental Engineering (ICEPEE 2017) ISBN: 978-1-60595-456-1 The Abnormal Electricity Consumption Detection System Based on the Outlier Behavior Pattern
2017 International Conference on Energy, Power and Environmental Engineering (ICEPEE 2017) ISBN: 978-1-60595-456-1 The Abnormal Electricity Consumption Detection System Based on the Outlier Behavior Pattern
Performance Evaluation
 Performance Evaluation David S. Rosenberg Bloomberg ML EDU October 26, 2017 David S. Rosenberg (Bloomberg ML EDU) October 26, 2017 1 / 36 Baseline Models David S. Rosenberg (Bloomberg ML EDU) October 26,
Performance Evaluation David S. Rosenberg Bloomberg ML EDU October 26, 2017 David S. Rosenberg (Bloomberg ML EDU) October 26, 2017 1 / 36 Baseline Models David S. Rosenberg (Bloomberg ML EDU) October 26,
Lecture 4 Discriminant Analysis, k-nearest Neighbors
 Lecture 4 Discriminant Analysis, k-nearest Neighbors Fredrik Lindsten Division of Systems and Control Department of Information Technology Uppsala University. Email: fredrik.lindsten@it.uu.se fredrik.lindsten@it.uu.se
Lecture 4 Discriminant Analysis, k-nearest Neighbors Fredrik Lindsten Division of Systems and Control Department of Information Technology Uppsala University. Email: fredrik.lindsten@it.uu.se fredrik.lindsten@it.uu.se
From statistics to data science. BAE 815 (Fall 2017) Dr. Zifei Liu
 From statistics to data science BAE 815 (Fall 2017) Dr. Zifei Liu Zifeiliu@ksu.edu Why? How? What? How much? How many? Individual facts (quantities, characters, or symbols) The Data-Information-Knowledge-Wisdom
From statistics to data science BAE 815 (Fall 2017) Dr. Zifei Liu Zifeiliu@ksu.edu Why? How? What? How much? How many? Individual facts (quantities, characters, or symbols) The Data-Information-Knowledge-Wisdom
Class 4: Classification. Quaid Morris February 11 th, 2011 ML4Bio
 Class 4: Classification Quaid Morris February 11 th, 211 ML4Bio Overview Basic concepts in classification: overfitting, cross-validation, evaluation. Linear Discriminant Analysis and Quadratic Discriminant
Class 4: Classification Quaid Morris February 11 th, 211 ML4Bio Overview Basic concepts in classification: overfitting, cross-validation, evaluation. Linear Discriminant Analysis and Quadratic Discriminant
Online Advertising is Big Business
 Online Advertising Online Advertising is Big Business Multiple billion dollar industry $43B in 2013 in USA, 17% increase over 2012 [PWC, Internet Advertising Bureau, April 2013] Higher revenue in USA
Online Advertising Online Advertising is Big Business Multiple billion dollar industry $43B in 2013 in USA, 17% increase over 2012 [PWC, Internet Advertising Bureau, April 2013] Higher revenue in USA
Pointwise Exact Bootstrap Distributions of Cost Curves
 Pointwise Exact Bootstrap Distributions of Cost Curves Charles Dugas and David Gadoury University of Montréal 25th ICML Helsinki July 2008 Dugas, Gadoury (U Montréal) Cost curves July 8, 2008 1 / 24 Outline
Pointwise Exact Bootstrap Distributions of Cost Curves Charles Dugas and David Gadoury University of Montréal 25th ICML Helsinki July 2008 Dugas, Gadoury (U Montréal) Cost curves July 8, 2008 1 / 24 Outline
BANA 7046 Data Mining I Lecture 4. Logistic Regression and Classications 1
 BANA 7046 Data Mining I Lecture 4. Logistic Regression and Classications 1 Shaobo Li University of Cincinnati 1 Partially based on Hastie, et al. (2009) ESL, and James, et al. (2013) ISLR Data Mining I
BANA 7046 Data Mining I Lecture 4. Logistic Regression and Classications 1 Shaobo Li University of Cincinnati 1 Partially based on Hastie, et al. (2009) ESL, and James, et al. (2013) ISLR Data Mining I
Anomaly Detection. Jing Gao. SUNY Buffalo
 Anomaly Detection Jing Gao SUNY Buffalo 1 Anomaly Detection Anomalies the set of objects are considerably dissimilar from the remainder of the data occur relatively infrequently when they do occur, their
Anomaly Detection Jing Gao SUNY Buffalo 1 Anomaly Detection Anomalies the set of objects are considerably dissimilar from the remainder of the data occur relatively infrequently when they do occur, their
Machine learning comes from Bayesian decision theory in statistics. There we want to minimize the expected value of the loss function.
 Bayesian learning: Machine learning comes from Bayesian decision theory in statistics. There we want to minimize the expected value of the loss function. Let y be the true label and y be the predicted
Bayesian learning: Machine learning comes from Bayesian decision theory in statistics. There we want to minimize the expected value of the loss function. Let y be the true label and y be the predicted
Chart types and when to use them
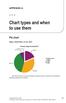 APPENDIX A Chart types and when to use them Pie chart Figure illustration of pie chart 2.3 % 4.5 % Browser Usage for April 2012 18.3 % 38.3 % Internet Explorer Firefox Chrome Safari Opera 35.8 % Pie chart
APPENDIX A Chart types and when to use them Pie chart Figure illustration of pie chart 2.3 % 4.5 % Browser Usage for April 2012 18.3 % 38.3 % Internet Explorer Firefox Chrome Safari Opera 35.8 % Pie chart
Multi-wind Field Output Power Prediction Method based on Energy Internet and DBPSO-LSSVM
 , pp.128-133 http://dx.doi.org/1.14257/astl.16.138.27 Multi-wind Field Output Power Prediction Method based on Energy Internet and DBPSO-LSSVM *Jianlou Lou 1, Hui Cao 1, Bin Song 2, Jizhe Xiao 1 1 School
, pp.128-133 http://dx.doi.org/1.14257/astl.16.138.27 Multi-wind Field Output Power Prediction Method based on Energy Internet and DBPSO-LSSVM *Jianlou Lou 1, Hui Cao 1, Bin Song 2, Jizhe Xiao 1 1 School
An Improved Method of Power System Short Term Load Forecasting Based on Neural Network
 An Improved Method of Power System Short Term Load Forecasting Based on Neural Network Shunzhou Wang School of Electrical and Electronic Engineering Huailin Zhao School of Electrical and Electronic Engineering
An Improved Method of Power System Short Term Load Forecasting Based on Neural Network Shunzhou Wang School of Electrical and Electronic Engineering Huailin Zhao School of Electrical and Electronic Engineering
day month year documentname/initials 1
 ECE471-571 Pattern Recognition Lecture 13 Decision Tree Hairong Qi, Gonzalez Family Professor Electrical Engineering and Computer Science University of Tennessee, Knoxville http://www.eecs.utk.edu/faculty/qi
ECE471-571 Pattern Recognition Lecture 13 Decision Tree Hairong Qi, Gonzalez Family Professor Electrical Engineering and Computer Science University of Tennessee, Knoxville http://www.eecs.utk.edu/faculty/qi
Method for Recognizing Mechanical Status of Container Crane Motor Based on SOM Neural Network
 IOP Conference Series: Materials Science and Engineering PAPER OPEN ACCESS Method for Recognizing Mechanical Status of Container Crane Motor Based on SOM Neural Network To cite this article: X Q Yao et
IOP Conference Series: Materials Science and Engineering PAPER OPEN ACCESS Method for Recognizing Mechanical Status of Container Crane Motor Based on SOM Neural Network To cite this article: X Q Yao et
Computational paradigms for the measurement signals processing. Metodologies for the development of classification algorithms.
 Computational paradigms for the measurement signals processing. Metodologies for the development of classification algorithms. January 5, 25 Outline Methodologies for the development of classification
Computational paradigms for the measurement signals processing. Metodologies for the development of classification algorithms. January 5, 25 Outline Methodologies for the development of classification
Journal of Chemical and Pharmaceutical Research, 2014, 6(5): Research Article
 Available online www.jocpr.com Journal of Chemical and Pharmaceutical Research, 2014, 6(5):266-270 Research Article ISSN : 0975-7384 CODEN(USA) : JCPRC5 Anomaly detection of cigarette sales using ARIMA
Available online www.jocpr.com Journal of Chemical and Pharmaceutical Research, 2014, 6(5):266-270 Research Article ISSN : 0975-7384 CODEN(USA) : JCPRC5 Anomaly detection of cigarette sales using ARIMA
Applying Machine Learning for Gravitational-wave Burst Data Analysis
 Applying Machine Learning for Gravitational-wave Burst Data Analysis Junwei Cao LIGO Scientific Collaboration Research Group Research Institute of Information Technology Tsinghua University June 29, 2016
Applying Machine Learning for Gravitational-wave Burst Data Analysis Junwei Cao LIGO Scientific Collaboration Research Group Research Institute of Information Technology Tsinghua University June 29, 2016
Multi-Plant Photovoltaic Energy Forecasting Challenge with Regression Tree Ensembles and Hourly Average Forecasts
 Multi-Plant Photovoltaic Energy Forecasting Challenge with Regression Tree Ensembles and Hourly Average Forecasts Kathrin Bujna 1 and Martin Wistuba 2 1 Paderborn University 2 IBM Research Ireland Abstract.
Multi-Plant Photovoltaic Energy Forecasting Challenge with Regression Tree Ensembles and Hourly Average Forecasts Kathrin Bujna 1 and Martin Wistuba 2 1 Paderborn University 2 IBM Research Ireland Abstract.
Part I. Linear Discriminant Analysis. Discriminant analysis. Discriminant analysis
 Week 5 Based in part on slides from textbook, slides of Susan Holmes Part I Linear Discriminant Analysis October 29, 2012 1 / 1 2 / 1 Nearest centroid rule Suppose we break down our data matrix as by the
Week 5 Based in part on slides from textbook, slides of Susan Holmes Part I Linear Discriminant Analysis October 29, 2012 1 / 1 2 / 1 Nearest centroid rule Suppose we break down our data matrix as by the
Machine Learning Concepts in Chemoinformatics
 Machine Learning Concepts in Chemoinformatics Martin Vogt B-IT Life Science Informatics Rheinische Friedrich-Wilhelms-Universität Bonn BigChem Winter School 2017 25. October Data Mining in Chemoinformatics
Machine Learning Concepts in Chemoinformatics Martin Vogt B-IT Life Science Informatics Rheinische Friedrich-Wilhelms-Universität Bonn BigChem Winter School 2017 25. October Data Mining in Chemoinformatics
Detection of Unauthorized Electricity Consumption using Machine Learning
 Detection of Unauthorized Electricity Consumption using Machine Learning Bo Tang, Ph.D. Department of Electrical and Computer Engineering Mississippi State University Outline Advanced Metering Infrastructure
Detection of Unauthorized Electricity Consumption using Machine Learning Bo Tang, Ph.D. Department of Electrical and Computer Engineering Mississippi State University Outline Advanced Metering Infrastructure
Q1 (12 points): Chap 4 Exercise 3 (a) to (f) (2 points each)
 Q1 (1 points): Chap 4 Exercise 3 (a) to (f) ( points each) Given a table Table 1 Dataset for Exercise 3 Instance a 1 a a 3 Target Class 1 T T 1.0 + T T 6.0 + 3 T F 5.0-4 F F 4.0 + 5 F T 7.0-6 F T 3.0-7
Q1 (1 points): Chap 4 Exercise 3 (a) to (f) ( points each) Given a table Table 1 Dataset for Exercise 3 Instance a 1 a a 3 Target Class 1 T T 1.0 + T T 6.0 + 3 T F 5.0-4 F F 4.0 + 5 F T 7.0-6 F T 3.0-7
Machine learning for pervasive systems Classification in high-dimensional spaces
 Machine learning for pervasive systems Classification in high-dimensional spaces Department of Communications and Networking Aalto University, School of Electrical Engineering stephan.sigg@aalto.fi Version
Machine learning for pervasive systems Classification in high-dimensional spaces Department of Communications and Networking Aalto University, School of Electrical Engineering stephan.sigg@aalto.fi Version
Classifying Galaxy Morphology using Machine Learning
 Julian Kates-Harbeck, Introduction: Classifying Galaxy Morphology using Machine Learning The goal of this project is to classify galaxy morphologies. Generally, galaxy morphologies fall into one of two
Julian Kates-Harbeck, Introduction: Classifying Galaxy Morphology using Machine Learning The goal of this project is to classify galaxy morphologies. Generally, galaxy morphologies fall into one of two
Predictive Analytics on Accident Data Using Rule Based and Discriminative Classifiers
 Advances in Computational Sciences and Technology ISSN 0973-6107 Volume 10, Number 3 (2017) pp. 461-469 Research India Publications http://www.ripublication.com Predictive Analytics on Accident Data Using
Advances in Computational Sciences and Technology ISSN 0973-6107 Volume 10, Number 3 (2017) pp. 461-469 Research India Publications http://www.ripublication.com Predictive Analytics on Accident Data Using
A METHOD OF FINDING IMAGE SIMILAR PATCHES BASED ON GRADIENT-COVARIANCE SIMILARITY
 IJAMML 3:1 (015) 69-78 September 015 ISSN: 394-58 Available at http://scientificadvances.co.in DOI: http://dx.doi.org/10.1864/ijamml_710011547 A METHOD OF FINDING IMAGE SIMILAR PATCHES BASED ON GRADIENT-COVARIANCE
IJAMML 3:1 (015) 69-78 September 015 ISSN: 394-58 Available at http://scientificadvances.co.in DOI: http://dx.doi.org/10.1864/ijamml_710011547 A METHOD OF FINDING IMAGE SIMILAR PATCHES BASED ON GRADIENT-COVARIANCE
Fault prediction of power system distribution equipment based on support vector machine
 Fault prediction of power system distribution equipment based on support vector machine Zhenqi Wang a, Hongyi Zhang b School of Control and Computer Engineering, North China Electric Power University,
Fault prediction of power system distribution equipment based on support vector machine Zhenqi Wang a, Hongyi Zhang b School of Control and Computer Engineering, North China Electric Power University,
SUPERVISED LEARNING: INTRODUCTION TO CLASSIFICATION
 SUPERVISED LEARNING: INTRODUCTION TO CLASSIFICATION 1 Outline Basic terminology Features Training and validation Model selection Error and loss measures Statistical comparison Evaluation measures 2 Terminology
SUPERVISED LEARNING: INTRODUCTION TO CLASSIFICATION 1 Outline Basic terminology Features Training and validation Model selection Error and loss measures Statistical comparison Evaluation measures 2 Terminology
Two-stage Pedestrian Detection Based on Multiple Features and Machine Learning
 38 3 Vol. 38, No. 3 2012 3 ACTA AUTOMATICA SINICA March, 2012 1 1 1, (Adaboost) (Support vector machine, SVM). (Four direction features, FDF) GAB (Gentle Adaboost) (Entropy-histograms of oriented gradients,
38 3 Vol. 38, No. 3 2012 3 ACTA AUTOMATICA SINICA March, 2012 1 1 1, (Adaboost) (Support vector machine, SVM). (Four direction features, FDF) GAB (Gentle Adaboost) (Entropy-histograms of oriented gradients,
Iterative Laplacian Score for Feature Selection
 Iterative Laplacian Score for Feature Selection Linling Zhu, Linsong Miao, and Daoqiang Zhang College of Computer Science and echnology, Nanjing University of Aeronautics and Astronautics, Nanjing 2006,
Iterative Laplacian Score for Feature Selection Linling Zhu, Linsong Miao, and Daoqiang Zhang College of Computer Science and echnology, Nanjing University of Aeronautics and Astronautics, Nanjing 2006,
Finding Multiple Outliers from Multidimensional Data using Multiple Regression
 Finding Multiple Outliers from Multidimensional Data using Multiple Regression L. Sunitha 1*, Dr M. Bal Raju 2 1* CSE Research Scholar, J N T U Hyderabad, Telangana (India) 2 Professor and principal, K
Finding Multiple Outliers from Multidimensional Data using Multiple Regression L. Sunitha 1*, Dr M. Bal Raju 2 1* CSE Research Scholar, J N T U Hyderabad, Telangana (India) 2 Professor and principal, K
Discovery Through Situational Awareness
 Discovery Through Situational Awareness BRETT AMIDAN JIM FOLLUM NICK BETZSOLD TIM YIN (UNIVERSITY OF WYOMING) SHIKHAR PANDEY (WASHINGTON STATE UNIVERSITY) Pacific Northwest National Laboratory February
Discovery Through Situational Awareness BRETT AMIDAN JIM FOLLUM NICK BETZSOLD TIM YIN (UNIVERSITY OF WYOMING) SHIKHAR PANDEY (WASHINGTON STATE UNIVERSITY) Pacific Northwest National Laboratory February
Optimizing Abstaining Classifiers using ROC Analysis. Tadek Pietraszek / 'tʌ dek pɪe 'trʌ ʃek / ICML 2005 August 9, 2005
 IBM Zurich Research Laboratory, GSAL Optimizing Abstaining Classifiers using ROC Analysis Tadek Pietraszek / 'tʌ dek pɪe 'trʌ ʃek / pie@zurich.ibm.com ICML 2005 August 9, 2005 To classify, or not to classify:
IBM Zurich Research Laboratory, GSAL Optimizing Abstaining Classifiers using ROC Analysis Tadek Pietraszek / 'tʌ dek pɪe 'trʌ ʃek / pie@zurich.ibm.com ICML 2005 August 9, 2005 To classify, or not to classify:
Local Feature Extraction Models from Incomplete Data in Face Recognition Based on Nonnegative Matrix Factorization
 American Journal of Software Engineering and Applications 2015; 4(3): 50-55 Published online May 12, 2015 (http://www.sciencepublishinggroup.com/j/ajsea) doi: 10.11648/j.ajsea.20150403.12 ISSN: 2327-2473
American Journal of Software Engineering and Applications 2015; 4(3): 50-55 Published online May 12, 2015 (http://www.sciencepublishinggroup.com/j/ajsea) doi: 10.11648/j.ajsea.20150403.12 ISSN: 2327-2473
CS570 Data Mining. Anomaly Detection. Li Xiong. Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber.
 CS570 Data Mining Anomaly Detection Li Xiong Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber April 3, 2011 1 Anomaly Detection Anomaly is a pattern in the data that does not conform
CS570 Data Mining Anomaly Detection Li Xiong Slide credits: Tan, Steinbach, Kumar Jiawei Han and Micheline Kamber April 3, 2011 1 Anomaly Detection Anomaly is a pattern in the data that does not conform
Gradient Boosting, Continued
 Gradient Boosting, Continued David Rosenberg New York University December 26, 2016 David Rosenberg (New York University) DS-GA 1003 December 26, 2016 1 / 16 Review: Gradient Boosting Review: Gradient Boosting
Gradient Boosting, Continued David Rosenberg New York University December 26, 2016 David Rosenberg (New York University) DS-GA 1003 December 26, 2016 1 / 16 Review: Gradient Boosting Review: Gradient Boosting
Machine Learning Linear Classification. Prof. Matteo Matteucci
 Machine Learning Linear Classification Prof. Matteo Matteucci Recall from the first lecture 2 X R p Regression Y R Continuous Output X R p Y {Ω 0, Ω 1,, Ω K } Classification Discrete Output X R p Y (X)
Machine Learning Linear Classification Prof. Matteo Matteucci Recall from the first lecture 2 X R p Regression Y R Continuous Output X R p Y {Ω 0, Ω 1,, Ω K } Classification Discrete Output X R p Y (X)
Research Article Dynamic Time Warping Distance Method for Similarity Test of Multipoint Ground Motion Field
 Hindawi Publishing Corporation Mathematical Problems in Engineering Volume 2, Article ID 74957, 2 pages doi:.55/2/74957 Research Article Dynamic Time Warping Distance Method for Similarity Test of Multipoint
Hindawi Publishing Corporation Mathematical Problems in Engineering Volume 2, Article ID 74957, 2 pages doi:.55/2/74957 Research Article Dynamic Time Warping Distance Method for Similarity Test of Multipoint
Online Estimation of Discrete Densities using Classifier Chains
 Online Estimation of Discrete Densities using Classifier Chains Michael Geilke 1 and Eibe Frank 2 and Stefan Kramer 1 1 Johannes Gutenberg-Universtität Mainz, Germany {geilke,kramer}@informatik.uni-mainz.de
Online Estimation of Discrete Densities using Classifier Chains Michael Geilke 1 and Eibe Frank 2 and Stefan Kramer 1 1 Johannes Gutenberg-Universtität Mainz, Germany {geilke,kramer}@informatik.uni-mainz.de
A Wavelet Neural Network Forecasting Model Based On ARIMA
 A Wavelet Neural Network Forecasting Model Based On ARIMA Wang Bin*, Hao Wen-ning, Chen Gang, He Deng-chao, Feng Bo PLA University of Science &Technology Nanjing 210007, China e-mail:lgdwangbin@163.com
A Wavelet Neural Network Forecasting Model Based On ARIMA Wang Bin*, Hao Wen-ning, Chen Gang, He Deng-chao, Feng Bo PLA University of Science &Technology Nanjing 210007, China e-mail:lgdwangbin@163.com
Classification using stochastic ensembles
 July 31, 2014 Topics Introduction Topics Classification Application and classfication Classification and Regression Trees Stochastic ensemble methods Our application: USAID Poverty Assessment Tools Topics
July 31, 2014 Topics Introduction Topics Classification Application and classfication Classification and Regression Trees Stochastic ensemble methods Our application: USAID Poverty Assessment Tools Topics
Linear Discriminant Analysis Based in part on slides from textbook, slides of Susan Holmes. November 9, Statistics 202: Data Mining
 Linear Discriminant Analysis Based in part on slides from textbook, slides of Susan Holmes November 9, 2012 1 / 1 Nearest centroid rule Suppose we break down our data matrix as by the labels yielding (X
Linear Discriminant Analysis Based in part on slides from textbook, slides of Susan Holmes November 9, 2012 1 / 1 Nearest centroid rule Suppose we break down our data matrix as by the labels yielding (X
Anomaly Detection for the CERN Large Hadron Collider injection magnets
 Anomaly Detection for the CERN Large Hadron Collider injection magnets Armin Halilovic KU Leuven - Department of Computer Science In cooperation with CERN 2018-07-27 0 Outline 1 Context 2 Data 3 Preprocessing
Anomaly Detection for the CERN Large Hadron Collider injection magnets Armin Halilovic KU Leuven - Department of Computer Science In cooperation with CERN 2018-07-27 0 Outline 1 Context 2 Data 3 Preprocessing
Performance Evaluation
 Statistical Data Mining and Machine Learning Hilary Term 2016 Dino Sejdinovic Department of Statistics Oxford Slides and other materials available at: http://www.stats.ox.ac.uk/~sejdinov/sdmml Example:
Statistical Data Mining and Machine Learning Hilary Term 2016 Dino Sejdinovic Department of Statistics Oxford Slides and other materials available at: http://www.stats.ox.ac.uk/~sejdinov/sdmml Example:
A Novel Activity Detection Method
 A Novel Activity Detection Method Gismy George P.G. Student, Department of ECE, Ilahia College of,muvattupuzha, Kerala, India ABSTRACT: This paper presents an approach for activity state recognition of
A Novel Activity Detection Method Gismy George P.G. Student, Department of ECE, Ilahia College of,muvattupuzha, Kerala, India ABSTRACT: This paper presents an approach for activity state recognition of
Evaluation & Credibility Issues
 Evaluation & Credibility Issues What measure should we use? accuracy might not be enough. How reliable are the predicted results? How much should we believe in what was learned? Error on the training data
Evaluation & Credibility Issues What measure should we use? accuracy might not be enough. How reliable are the predicted results? How much should we believe in what was learned? Error on the training data
Multi-Plant Photovoltaic Energy Forecasting Challenge: Second place solution
 Multi-Plant Photovoltaic Energy Forecasting Challenge: Second place solution Clément Gautrais 1, Yann Dauxais 1, and Maël Guilleme 2 1 University of Rennes 1/Inria Rennes clement.gautrais@irisa.fr 2 Energiency/University
Multi-Plant Photovoltaic Energy Forecasting Challenge: Second place solution Clément Gautrais 1, Yann Dauxais 1, and Maël Guilleme 2 1 University of Rennes 1/Inria Rennes clement.gautrais@irisa.fr 2 Energiency/University
Neural Networks. Single-layer neural network. CSE 446: Machine Learning Emily Fox University of Washington March 10, /9/17
 3/9/7 Neural Networks Emily Fox University of Washington March 0, 207 Slides adapted from Ali Farhadi (via Carlos Guestrin and Luke Zettlemoyer) Single-layer neural network 3/9/7 Perceptron as a neural
3/9/7 Neural Networks Emily Fox University of Washington March 0, 207 Slides adapted from Ali Farhadi (via Carlos Guestrin and Luke Zettlemoyer) Single-layer neural network 3/9/7 Perceptron as a neural
Unsupervised Anomaly Detection for High Dimensional Data
 Unsupervised Anomaly Detection for High Dimensional Data Department of Mathematics, Rowan University. July 19th, 2013 International Workshop in Sequential Methodologies (IWSM-2013) Outline of Talk Motivation
Unsupervised Anomaly Detection for High Dimensional Data Department of Mathematics, Rowan University. July 19th, 2013 International Workshop in Sequential Methodologies (IWSM-2013) Outline of Talk Motivation
A Little History of Machine Learning
 機器學習現在 過去 未來 A Little History of Machine Learning Chia-Ping Chen National Sun Yat-sen University @NPTU, December 2016 Outline ubiquitous machine intelligence challenge and reaction AI brief deep learning
機器學習現在 過去 未來 A Little History of Machine Learning Chia-Ping Chen National Sun Yat-sen University @NPTU, December 2016 Outline ubiquitous machine intelligence challenge and reaction AI brief deep learning
Multivariate statistical methods and data mining in particle physics Lecture 4 (19 June, 2008)
 Multivariate statistical methods and data mining in particle physics Lecture 4 (19 June, 2008) RHUL Physics www.pp.rhul.ac.uk/~cowan Academic Training Lectures CERN 16 19 June, 2008 1 Outline Statement
Multivariate statistical methods and data mining in particle physics Lecture 4 (19 June, 2008) RHUL Physics www.pp.rhul.ac.uk/~cowan Academic Training Lectures CERN 16 19 June, 2008 1 Outline Statement
A FUZZY NEURAL NETWORK MODEL FOR FORECASTING STOCK PRICE
 A FUZZY NEURAL NETWORK MODEL FOR FORECASTING STOCK PRICE Li Sheng Institute of intelligent information engineering Zheiang University Hangzhou, 3007, P. R. China ABSTRACT In this paper, a neural network-driven
A FUZZY NEURAL NETWORK MODEL FOR FORECASTING STOCK PRICE Li Sheng Institute of intelligent information engineering Zheiang University Hangzhou, 3007, P. R. China ABSTRACT In this paper, a neural network-driven
Text Mining. Dr. Yanjun Li. Associate Professor. Department of Computer and Information Sciences Fordham University
 Text Mining Dr. Yanjun Li Associate Professor Department of Computer and Information Sciences Fordham University Outline Introduction: Data Mining Part One: Text Mining Part Two: Preprocessing Text Data
Text Mining Dr. Yanjun Li Associate Professor Department of Computer and Information Sciences Fordham University Outline Introduction: Data Mining Part One: Text Mining Part Two: Preprocessing Text Data
RaRE: Social Rank Regulated Large-scale Network Embedding
 RaRE: Social Rank Regulated Large-scale Network Embedding Authors: Yupeng Gu 1, Yizhou Sun 1, Yanen Li 2, Yang Yang 3 04/26/2018 The Web Conference, 2018 1 University of California, Los Angeles 2 Snapchat
RaRE: Social Rank Regulated Large-scale Network Embedding Authors: Yupeng Gu 1, Yizhou Sun 1, Yanen Li 2, Yang Yang 3 04/26/2018 The Web Conference, 2018 1 University of California, Los Angeles 2 Snapchat
Multivariate statistical methods and data mining in particle physics
 Multivariate statistical methods and data mining in particle physics RHUL Physics www.pp.rhul.ac.uk/~cowan Academic Training Lectures CERN 16 19 June, 2008 1 Outline Statement of the problem Some general
Multivariate statistical methods and data mining in particle physics RHUL Physics www.pp.rhul.ac.uk/~cowan Academic Training Lectures CERN 16 19 June, 2008 1 Outline Statement of the problem Some general
Gradient Boosting (Continued)
 Gradient Boosting (Continued) David Rosenberg New York University April 4, 2016 David Rosenberg (New York University) DS-GA 1003 April 4, 2016 1 / 31 Boosting Fits an Additive Model Boosting Fits an Additive
Gradient Boosting (Continued) David Rosenberg New York University April 4, 2016 David Rosenberg (New York University) DS-GA 1003 April 4, 2016 1 / 31 Boosting Fits an Additive Model Boosting Fits an Additive
Evaluation Metrics for Intrusion Detection Systems - A Study
 Evaluation Metrics for Intrusion Detection Systems - A Study Gulshan Kumar Assistant Professor, Shaheed Bhagat Singh State Technical Campus, Ferozepur (Punjab)-India 152004 Email: gulshanahuja@gmail.com
Evaluation Metrics for Intrusion Detection Systems - A Study Gulshan Kumar Assistant Professor, Shaheed Bhagat Singh State Technical Campus, Ferozepur (Punjab)-India 152004 Email: gulshanahuja@gmail.com
Lecture 9: Classification, LDA
 Lecture 9: Classification, LDA Reading: Chapter 4 STATS 202: Data mining and analysis October 13, 2017 1 / 21 Review: Main strategy in Chapter 4 Find an estimate ˆP (Y X). Then, given an input x 0, we
Lecture 9: Classification, LDA Reading: Chapter 4 STATS 202: Data mining and analysis October 13, 2017 1 / 21 Review: Main strategy in Chapter 4 Find an estimate ˆP (Y X). Then, given an input x 0, we
Data Mining and Knowledge Discovery: Practice Notes
 Data Mining and Knowledge Discovery: Practice Notes dr. Petra Kralj Novak Petra.Kralj.Novak@ijs.si 7.11.2017 1 Course Prof. Bojan Cestnik Data preparation Prof. Nada Lavrač: Data mining overview Advanced
Data Mining and Knowledge Discovery: Practice Notes dr. Petra Kralj Novak Petra.Kralj.Novak@ijs.si 7.11.2017 1 Course Prof. Bojan Cestnik Data preparation Prof. Nada Lavrač: Data mining overview Advanced
Lecture 9: Classification, LDA
 Lecture 9: Classification, LDA Reading: Chapter 4 STATS 202: Data mining and analysis Jonathan Taylor, 10/12 Slide credits: Sergio Bacallado 1 / 1 Review: Main strategy in Chapter 4 Find an estimate ˆP
Lecture 9: Classification, LDA Reading: Chapter 4 STATS 202: Data mining and analysis Jonathan Taylor, 10/12 Slide credits: Sergio Bacallado 1 / 1 Review: Main strategy in Chapter 4 Find an estimate ˆP
Data Mining: Concepts and Techniques. (3 rd ed.) Chapter 8. Chapter 8. Classification: Basic Concepts
 Data Mining: Concepts and Techniques (3 rd ed.) Chapter 8 1 Chapter 8. Classification: Basic Concepts Classification: Basic Concepts Decision Tree Induction Bayes Classification Methods Rule-Based Classification
Data Mining: Concepts and Techniques (3 rd ed.) Chapter 8 1 Chapter 8. Classification: Basic Concepts Classification: Basic Concepts Decision Tree Induction Bayes Classification Methods Rule-Based Classification
Data Mining algorithms
 Data Mining algorithms 2017-2018 spring 02.07-09.2018 Overview Classification vs. Regression Evaluation I Basics Bálint Daróczy daroczyb@ilab.sztaki.hu Basic reachability: MTA SZTAKI, Lágymányosi str.
Data Mining algorithms 2017-2018 spring 02.07-09.2018 Overview Classification vs. Regression Evaluation I Basics Bálint Daróczy daroczyb@ilab.sztaki.hu Basic reachability: MTA SZTAKI, Lágymányosi str.
Mobile Internet anomaly traffic detection technology research based on improved wavelet neural network
 Acta Technica 62 No. 2A/2017, 245 254 c 2017 Institute of Thermomechanics CAS, v.v.i. Mobile Internet anomaly traffic detection technology research based on improved wavelet neural network Qingshan Li
Acta Technica 62 No. 2A/2017, 245 254 c 2017 Institute of Thermomechanics CAS, v.v.i. Mobile Internet anomaly traffic detection technology research based on improved wavelet neural network Qingshan Li
Similarity and Dissimilarity
 1//015 Similarity and Dissimilarity COMP 465 Data Mining Similarity of Data Data Preprocessing Slides Adapted From : Jiawei Han, Micheline Kamber & Jian Pei Data Mining: Concepts and Techniques, 3 rd ed.
1//015 Similarity and Dissimilarity COMP 465 Data Mining Similarity of Data Data Preprocessing Slides Adapted From : Jiawei Han, Micheline Kamber & Jian Pei Data Mining: Concepts and Techniques, 3 rd ed.
Classifier performance evaluation
 Classifier performance evaluation Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics 166 36 Prague 6, Jugoslávských partyzánu 1580/3, Czech Republic
Classifier performance evaluation Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics 166 36 Prague 6, Jugoslávských partyzánu 1580/3, Czech Republic
A Comparison among various Classification Algorithms for Travel Mode Detection using Sensors data collected by Smartphones
 CUPUM 2015 175-Paper A Comparison among various Classification Algorithms for Travel Mode Detection using Sensors data collected by Smartphones Muhammad Awais Shafique and Eiji Hato Abstract Nowadays,
CUPUM 2015 175-Paper A Comparison among various Classification Algorithms for Travel Mode Detection using Sensors data collected by Smartphones Muhammad Awais Shafique and Eiji Hato Abstract Nowadays,
An Approach to Classification Based on Fuzzy Association Rules
 An Approach to Classification Based on Fuzzy Association Rules Zuoliang Chen, Guoqing Chen School of Economics and Management, Tsinghua University, Beijing 100084, P. R. China Abstract Classification based
An Approach to Classification Based on Fuzzy Association Rules Zuoliang Chen, Guoqing Chen School of Economics and Management, Tsinghua University, Beijing 100084, P. R. China Abstract Classification based
Comprehensive Evaluation of Social Benefits of Mineral Resources Development in Ordos Basin
 Studies in Sociology of Science Vol. 4, No. 1, 2013, pp. 25-29 DOI:10.3968/j.sss.1923018420130401.2909 ISSN 1923-0176 [Print] ISSN 1923-0184 [Online] www.cscanada.net www.cscanada.org Comprehensive Evaluation
Studies in Sociology of Science Vol. 4, No. 1, 2013, pp. 25-29 DOI:10.3968/j.sss.1923018420130401.2909 ISSN 1923-0176 [Print] ISSN 1923-0184 [Online] www.cscanada.net www.cscanada.org Comprehensive Evaluation
UPDATING AND REFINEMENT OF NATIONAL 1: DEM. National Geomatics Center of China, Beijing
 UPDATING AND REFINEMENT OF NATIONAL 1:500000 DEM Jian-jun LIU a, Dong-hua WANG a, Yao-ling SHANG a, Wen-hao ZHAO a Xi KUAI b a National Geomatics Center of China, Beijing 100830 b School of Resources and
UPDATING AND REFINEMENT OF NATIONAL 1:500000 DEM Jian-jun LIU a, Dong-hua WANG a, Yao-ling SHANG a, Wen-hao ZHAO a Xi KUAI b a National Geomatics Center of China, Beijing 100830 b School of Resources and
Visualize Biological Database for Protein in Homosapiens Using Classification Searching Models
 International Journal of Computational Intelligence Research ISSN 0973-1873 Volume 13, Number 2 (2017), pp. 213-224 Research India Publications http://www.ripublication.com Visualize Biological Database
International Journal of Computational Intelligence Research ISSN 0973-1873 Volume 13, Number 2 (2017), pp. 213-224 Research India Publications http://www.ripublication.com Visualize Biological Database
Model Accuracy Measures
 Model Accuracy Measures Master in Bioinformatics UPF 2017-2018 Eduardo Eyras Computational Genomics Pompeu Fabra University - ICREA Barcelona, Spain Variables What we can measure (attributes) Hypotheses
Model Accuracy Measures Master in Bioinformatics UPF 2017-2018 Eduardo Eyras Computational Genomics Pompeu Fabra University - ICREA Barcelona, Spain Variables What we can measure (attributes) Hypotheses
Statistical Machine Learning from Data
 Samy Bengio Statistical Machine Learning from Data 1 Statistical Machine Learning from Data Ensembles Samy Bengio IDIAP Research Institute, Martigny, Switzerland, and Ecole Polytechnique Fédérale de Lausanne
Samy Bengio Statistical Machine Learning from Data 1 Statistical Machine Learning from Data Ensembles Samy Bengio IDIAP Research Institute, Martigny, Switzerland, and Ecole Polytechnique Fédérale de Lausanne
UNCERTAINTY IN THE POPULATION GEOGRAPHIC INFORMATION SYSTEM
 UNCERTAINTY IN THE POPULATION GEOGRAPHIC INFORMATION SYSTEM 1. 2. LIU De-qin 1, LIU Yu 1,2, MA Wei-jun 1 Chinese Academy of Surveying and Mapping, Beijing 100039, China Shandong University of Science and
UNCERTAINTY IN THE POPULATION GEOGRAPHIC INFORMATION SYSTEM 1. 2. LIU De-qin 1, LIU Yu 1,2, MA Wei-jun 1 Chinese Academy of Surveying and Mapping, Beijing 100039, China Shandong University of Science and
Rare Event Discovery And Event Change Point In Biological Data Stream
 Rare Event Discovery And Event Change Point In Biological Data Stream T. Jagadeeswari 1 M.Tech(CSE) MISTE, B. Mahalakshmi 2 M.Tech(CSE)MISTE, N. Anusha 3 M.Tech(CSE) Department of Computer Science and
Rare Event Discovery And Event Change Point In Biological Data Stream T. Jagadeeswari 1 M.Tech(CSE) MISTE, B. Mahalakshmi 2 M.Tech(CSE)MISTE, N. Anusha 3 M.Tech(CSE) Department of Computer Science and
Lecture 9: Classification, LDA
 Lecture 9: Classification, LDA Reading: Chapter 4 STATS 202: Data mining and analysis October 13, 2017 1 / 21 Review: Main strategy in Chapter 4 Find an estimate ˆP (Y X). Then, given an input x 0, we
Lecture 9: Classification, LDA Reading: Chapter 4 STATS 202: Data mining and analysis October 13, 2017 1 / 21 Review: Main strategy in Chapter 4 Find an estimate ˆP (Y X). Then, given an input x 0, we
Research Article Data-Driven Fault Diagnosis Method for Power Transformers Using Modified Kriging Model
 Hindawi Mathematical Problems in Engineering Volume 2017, Article ID 3068548, 5 pages https://doi.org/10.1155/2017/3068548 Research Article Data-Driven Fault Diagnosis Method for Power Transformers Using
Hindawi Mathematical Problems in Engineering Volume 2017, Article ID 3068548, 5 pages https://doi.org/10.1155/2017/3068548 Research Article Data-Driven Fault Diagnosis Method for Power Transformers Using
Dynamic Time Warping and FFT: A Data Preprocessing Method for Electrical Load Forecasting
 Vol. 9, No., 18 Dynamic Time Warping and FFT: A Data Preprocessing Method for Electrical Load Forecasting Juan Huo School of Electrical and Automation Engineering Zhengzhou University, Henan Province,
Vol. 9, No., 18 Dynamic Time Warping and FFT: A Data Preprocessing Method for Electrical Load Forecasting Juan Huo School of Electrical and Automation Engineering Zhengzhou University, Henan Province,
Switching-state Dynamical Modeling of Daily Behavioral Data
 Switching-state Dynamical Modeling of Daily Behavioral Data Randy Ardywibowo Shuai Huang Cao Xiao Shupeng Gui Yu Cheng Ji Liu Xiaoning Qian Texas A&M University University of Washington IBM T.J. Watson
Switching-state Dynamical Modeling of Daily Behavioral Data Randy Ardywibowo Shuai Huang Cao Xiao Shupeng Gui Yu Cheng Ji Liu Xiaoning Qian Texas A&M University University of Washington IBM T.J. Watson
Data Analytics for Social Science
 Data Analytics for Social Science Johan A. Elkink School of Politics & International Relations University College Dublin 17 October 2017 Outline 1 2 3 4 5 6 Levels of measurement Discreet Continuous Nominal
Data Analytics for Social Science Johan A. Elkink School of Politics & International Relations University College Dublin 17 October 2017 Outline 1 2 3 4 5 6 Levels of measurement Discreet Continuous Nominal
Article from. Predictive Analytics and Futurism. July 2016 Issue 13
 Article from Predictive Analytics and Futurism July 2016 Issue 13 Regression and Classification: A Deeper Look By Jeff Heaton Classification and regression are the two most common forms of models fitted
Article from Predictive Analytics and Futurism July 2016 Issue 13 Regression and Classification: A Deeper Look By Jeff Heaton Classification and regression are the two most common forms of models fitted
Linear Classifiers as Pattern Detectors
 Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2014/2015 Lesson 16 8 April 2015 Contents Linear Classifiers as Pattern Detectors Notation...2 Linear
Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2014/2015 Lesson 16 8 April 2015 Contents Linear Classifiers as Pattern Detectors Notation...2 Linear
Research on fault prediction method of power electronic circuits based on least squares support vector machine
 15 8 2011 8 ELECTRI C MACHINES AND CONTROL Vol. 15 No. 8 Aug. 2011 LS-SVM 1 2 1 1 1 1. 210016 2. 232001 least squares support vector machine LS-SVM Buck LS-SVM LS-SVM 2% TP 206 A 1007-449X 2011 08-0064-
15 8 2011 8 ELECTRI C MACHINES AND CONTROL Vol. 15 No. 8 Aug. 2011 LS-SVM 1 2 1 1 1 1. 210016 2. 232001 least squares support vector machine LS-SVM Buck LS-SVM LS-SVM 2% TP 206 A 1007-449X 2011 08-0064-
A study on new customer satisfaction index model of smart grid
 2nd Annual International Conference on Electronics, Electrical Engineering and Information Science (EEEIS 2016) A study on new index model of smart grid Ze-San Liu 1,a, Zhuo Yu 1,b and Ai-Qiang Dong 1,c
2nd Annual International Conference on Electronics, Electrical Engineering and Information Science (EEEIS 2016) A study on new index model of smart grid Ze-San Liu 1,a, Zhuo Yu 1,b and Ai-Qiang Dong 1,c
Linear Classifiers as Pattern Detectors
 Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2013/2014 Lesson 18 23 April 2014 Contents Linear Classifiers as Pattern Detectors Notation...2 Linear
Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2013/2014 Lesson 18 23 April 2014 Contents Linear Classifiers as Pattern Detectors Notation...2 Linear
Performance Evaluation
 Performance Evaluation Confusion Matrix: Detected Positive Negative Actual Positive A: True Positive B: False Negative Negative C: False Positive D: True Negative Recall or Sensitivity or True Positive
Performance Evaluation Confusion Matrix: Detected Positive Negative Actual Positive A: True Positive B: False Negative Negative C: False Positive D: True Negative Recall or Sensitivity or True Positive
Machine Learning in Action
 Machine Learning in Action Tatyana Goldberg (goldberg@rostlab.org) August 16, 2016 @ Machine Learning in Biology Beijing Genomics Institute in Shenzhen, China June 2014 GenBank 1 173,353,076 DNA sequences
Machine Learning in Action Tatyana Goldberg (goldberg@rostlab.org) August 16, 2016 @ Machine Learning in Biology Beijing Genomics Institute in Shenzhen, China June 2014 GenBank 1 173,353,076 DNA sequences
Review of Lecture 1. Across records. Within records. Classification, Clustering, Outlier detection. Associations
 Review of Lecture 1 This course is about finding novel actionable patterns in data. We can divide data mining algorithms (and the patterns they find) into five groups Across records Classification, Clustering,
Review of Lecture 1 This course is about finding novel actionable patterns in data. We can divide data mining algorithms (and the patterns they find) into five groups Across records Classification, Clustering,
Evaluation requires to define performance measures to be optimized
 Evaluation Basic concepts Evaluation requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain (generalization error) approximation
Evaluation Basic concepts Evaluation requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain (generalization error) approximation
Experimental Research of Optimal Die-forging Technological Schemes Based on Orthogonal Plan
 Experimental Research of Optimal Die-forging Technological Schemes Based on Orthogonal Plan Jianhao Tan (Corresponding author) Electrical and Information Engineering College Hunan University Changsha 410082,
Experimental Research of Optimal Die-forging Technological Schemes Based on Orthogonal Plan Jianhao Tan (Corresponding author) Electrical and Information Engineering College Hunan University Changsha 410082,
EXAM IN STATISTICAL MACHINE LEARNING STATISTISK MASKININLÄRNING
 EXAM IN STATISTICAL MACHINE LEARNING STATISTISK MASKININLÄRNING DATE AND TIME: June 9, 2018, 09.00 14.00 RESPONSIBLE TEACHER: Andreas Svensson NUMBER OF PROBLEMS: 5 AIDING MATERIAL: Calculator, mathematical
EXAM IN STATISTICAL MACHINE LEARNING STATISTISK MASKININLÄRNING DATE AND TIME: June 9, 2018, 09.00 14.00 RESPONSIBLE TEACHER: Andreas Svensson NUMBER OF PROBLEMS: 5 AIDING MATERIAL: Calculator, mathematical
Bayesian Decision Theory
 Introduction to Pattern Recognition [ Part 4 ] Mahdi Vasighi Remarks It is quite common to assume that the data in each class are adequately described by a Gaussian distribution. Bayesian classifier is
Introduction to Pattern Recognition [ Part 4 ] Mahdi Vasighi Remarks It is quite common to assume that the data in each class are adequately described by a Gaussian distribution. Bayesian classifier is
Methods and Criteria for Model Selection. CS57300 Data Mining Fall Instructor: Bruno Ribeiro
 Methods and Criteria for Model Selection CS57300 Data Mining Fall 2016 Instructor: Bruno Ribeiro Goal } Introduce classifier evaluation criteria } Introduce Bias x Variance duality } Model Assessment }
Methods and Criteria for Model Selection CS57300 Data Mining Fall 2016 Instructor: Bruno Ribeiro Goal } Introduce classifier evaluation criteria } Introduce Bias x Variance duality } Model Assessment }
Anomaly Detection and Categorization Using Unsupervised Deep Learning
 Anomaly Detection and Categorization Using Unsupervised S6340 Thursday 7 th April 2016 GPU Technology Conference A. Stephen McGough, Noura Al Moubayed, Jonathan Cumming, Eduardo Cabrera, Peter Matthews,
Anomaly Detection and Categorization Using Unsupervised S6340 Thursday 7 th April 2016 GPU Technology Conference A. Stephen McGough, Noura Al Moubayed, Jonathan Cumming, Eduardo Cabrera, Peter Matthews,
Math 6330: Statistical Consulting Class 5
 Math 6330: Statistical Consulting Class 5 Tony Cox tcoxdenver@aol.com University of Colorado at Denver Course web site: http://cox-associates.com/6330/ What is a predictive model? The probability that
Math 6330: Statistical Consulting Class 5 Tony Cox tcoxdenver@aol.com University of Colorado at Denver Course web site: http://cox-associates.com/6330/ What is a predictive model? The probability that
Analysis on Characteristics of Precipitation Change from 1957 to 2015 in Weishan County
 Journal of Geoscience and Environment Protection, 2017, 5, 125-133 http://www.scirp.org/journal/gep ISSN Online: 2327-4344 ISSN Print: 2327-4336 Analysis on Characteristics of Precipitation Change from
Journal of Geoscience and Environment Protection, 2017, 5, 125-133 http://www.scirp.org/journal/gep ISSN Online: 2327-4344 ISSN Print: 2327-4336 Analysis on Characteristics of Precipitation Change from
International Journal of Research in Computer and Communication Technology, Vol 3, Issue 7, July
 Hybrid SVM Data mining Techniques for Weather Data Analysis of Krishna District of Andhra Region N.Rajasekhar 1, Dr. T. V. Rajini Kanth 2 1 (Assistant Professor, Department of Computer Science & Engineering,
Hybrid SVM Data mining Techniques for Weather Data Analysis of Krishna District of Andhra Region N.Rajasekhar 1, Dr. T. V. Rajini Kanth 2 1 (Assistant Professor, Department of Computer Science & Engineering,
Learning Multiple Tasks with a Sparse Matrix-Normal Penalty
 Learning Multiple Tasks with a Sparse Matrix-Normal Penalty Yi Zhang and Jeff Schneider NIPS 2010 Presented by Esther Salazar Duke University March 25, 2011 E. Salazar (Reading group) March 25, 2011 1
Learning Multiple Tasks with a Sparse Matrix-Normal Penalty Yi Zhang and Jeff Schneider NIPS 2010 Presented by Esther Salazar Duke University March 25, 2011 E. Salazar (Reading group) March 25, 2011 1
Classification Ensemble That Maximizes the Area Under Receiver Operating Characteristic Curve (AUC)
 Classification Ensemble That Maximizes the Area Under Receiver Operating Characteristic Curve (AUC) Eunsik Park 1 and Y-c Ivan Chang 2 1 Chonnam National University, Gwangju, Korea 2 Academia Sinica, Taipei,
Classification Ensemble That Maximizes the Area Under Receiver Operating Characteristic Curve (AUC) Eunsik Park 1 and Y-c Ivan Chang 2 1 Chonnam National University, Gwangju, Korea 2 Academia Sinica, Taipei,
Analysis of Data Mining Techniques for Weather Prediction
 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 Indian Journal of Science and Technology, Vol 9(38), DOI: 10.17485/ijst/2016/v9i38/101962, October 2016 Analysis of Data Mining Techniques for Weather
ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 Indian Journal of Science and Technology, Vol 9(38), DOI: 10.17485/ijst/2016/v9i38/101962, October 2016 Analysis of Data Mining Techniques for Weather
