New cardinality estimation algorithms for HyperLogLog sketches
|
|
|
- Lauren Lloyd
- 5 years ago
- Views:
Transcription
1 New cardinality estimation algorithms for HyperLogLog sketches Otmar Ertl April 3, 2017 This paper presents new methods to estimate the cardinalities of data sets recorded by HyperLogLog sketches. A theoretically motivated extension to the original estimator is presented that eliminates the bias for small and large cardinalities. Based on the maximum likelihood principle a second unbiased method is derived together with a robust and efficient numerical algorithm to calculate the estimate. The maximum likelihood approach can also be applied to more than a single HyperLogLog sketch. In particular, it is shown that it gives more precise cardinality estimates for union, intersection, or relative complements of two sets that are both represented by HyperLogLog sketches compared to the conventional technique using the inclusion-exclusion principle. All the new methods are demonstrated and verified by extensive simulations. 1. Introduction Counting the number of distinct elements in a data stream or large datasets is a common problem in big data processing. In principle, finding the number of distinct elements n with a maximum relative error ε in a data stream requires On) space [1]. However, probabilistic algorithms that achieve the requested accuracy only with high probability are able to drastically reduce space requirements. Many different probabilistic algorithms have been developed over the past two decades [2, 3] until a theoretically optimal algorithm was finally found [4]. Although this algorithm achieves the optimal space complexity of Oε 2 + log n) [1, 5], it is not very efficient in practice [3]. More practicable and already widely used in many applications is the HyperLogLog algorithm [6] with a near-optimal space complexity Oε 2 log log n + log n). It has the This paper together with source code for all presented algorithms and simulations is available at A first version of this paper was published there on April 17,
2 nice property that partial results can be easily merged, which is a necessity for distributed environments. Unfortunately, the originally proposed estimation method has some problems to guarantee the same accuracy over the full cardinality range. Therefore, a couple of variants have been developed to correct the original estimate by empirical means [7, 8, 9]. A more theoretically profound estimator for HyperLogLog sketches that does not depend on empirical data and significantly improves the estimation error is the historic inverse probability estimator [3, 10]. It trades memory efficiency for mergeability. The estimator needs to be continuously updated while inserting elements and the estimate depends on the element insertion order. Moreover, the estimator cannot be further used after merging two sketches, which limits its application to single data streams. If this restriction is acceptable, the self-learning bitmap [11] could also be used, which provides a similar trade-off and also needs less space than the original HyperLogLog method to achieve the same precision. Sometimes not only the number of distinct elements but also a sample of them is needed in order to allow later filtering according to some predicate and estimating the cardinalities of corresponding subsets. In this case the k-minimum values algorithm [12] is the method of choice which also allows set manipulations like the construction of intersections, relative complements, or unions [13]. The latter operation is the only one that is natively supported by HyperLogLog sketches. A sketch that represents the set operation result is not always needed. One approach to estimate the corresponding result cardinality directly is based on the inclusion-exclusion principle, which however can become quite inaccurate, especially for small Jaccard indices of the input sets [13]. Alternatively, the HyperLogLog sketches can be combined with some additional data structure that allows estimating the Jaccard index. Together with the HyperLogLog cardinality estimates the error of the intersection size estimate can be reduced [14, 15], however, at the expense of a significantly larger memory footprint due to the additional data structure Outline This paper presents new algorithms to extract cardinality information from Hyper- LogLog sketches. In Section 2 we start with an introduction to HyperLogLog sketches and the corresponding update algorithm. We also discuss how the resulting state can be statistically described and approximated by a Poisson model. In Section 3 we describe the original cardinality estimation algorithm, its shortcomings at low and large cardinalities, and previous approaches to overcome them. We present a simple derivation of the original raw estimator and analyze the root cause for its limited operating range. We derive an improved version of the raw estimator, which leads to a new fast cardinality estimation algorithm that works over the full cardinality range as demonstrated by extensive simulations. In Section 4 we derive a second even more precise cardinality estimation algorithm based on the maximum likelihood principle which is again verified by simulations. As presented in Section 5 the same approach can be generalized to two HyperLogLog sketches, which allows result cardinality estimation of set operations like 2
3 intersections or complements. The simulation results show that the estimates are significantly better than those of the conventional approach using the inclusion-exclusion principle. Finally, in Section 6 we discuss open problems and ideas for future work including HyperLogLog s potential application as locality-sensitive hashing algorithm before we conclude in Section HyperLogLog data structure The HyperLogLog algorithm collects information of incoming elements into a very compact sketching data structure, that finally allows the estimation of the number of distinct elements. The data structure consists of m = 2 p registers whose number is chosen to be a power of two for performance reasons. p is the precision parameter that directly controls the relative estimation error which scales like 1/ m [6]. All registers start with zero initial value. Each element insertion potentially increases the value of one of these registers. The maximum value a register can reach is a natural bound given either by the output size of the used hash algorithm or the space that is reserved for a single register. Common implementations allocate up to 8 bits per register Data element insertion The insertion of a data element into a HyperLogLog data structure requires the calculation of a p + q)-bit hash value. The leading p bits of the hash value are used to select one of the 2 p registers. Among the next following q bits, the position of the first 1-bit is determined which is a value in the range [1, q +1]. The value q +1 is used, if all q bits are zeros. If the position of the first 1-bit exceeds the current value of the selected register, the register value is replaced. Algorithm 1 shows the update procedure for inserting a data element into the HyperLogLog sketch. Algorithm 1 Insertion of a data element D into a HyperLogLog data structure that consists of m = 2 p registers. All registers K = K 1,..., K m ) start from zero denotes the binary representation of an integer. procedure InsertElementD) a 1,..., a p, b 1,..., b q 2 p + q)-bit hash value of D a i, b i {0, 1} k min{s b s = 1} {q + 1}) k {1, 2,..., q + 1} i 1 + a 1,..., a p 2 i {1, 2,..., m} if k > K i then K i k end if end procedure The described element insertion algorithm makes use of what is known as stochastic averaging [16]. Instead of updating each of all m registers using m independent hash values, which would be an Om) operation, only one register is selected and updated, which requires only a single hash function and reduces the complexity to O1). 3
4 A HyperLogLog sketch can be characterized by a parameter pair p, q). The precision parameter p controls the relative error while the second parameter defines the possible value range of a register. A register can take all values starting from 0 to q+1, inclusively. The sum p + q corresponds to the number of consumed hash value bits and defines the maximum cardinality that can be tracked. Obviously, if the cardinality reaches values in the order of 2 p+q, hash collisions will become more apparent and the estimation error will increase drastically. Algorithm 1 has some properties which are especially useful for distributed data streams. First, the insertion order of elements has no influence on the final HyperLogLog sketch. Furthermore, any two HyperLogLog sketches with same parameters p, q) representing two different sets can be easily merged. The HyperLogLog sketch that represents the union of both sets can be easily constructed by taking the register-wise maximum values as demonstrated by Algorithm 2. Algorithm 2 Merge operation for two HyperLogLog sketches with register values K 1 = K 11,..., K 1m ) and K 2 = K 21,..., K 2m ) representing sets S 1 and S 2, respectively, to obtain the register values K = K 1,..., K m) of a HyperLogLog sketch representing S 1 S 2. function MergeK 1,K 2 ) allocate K = K 1,..., K m) for i 1, m do K i maxk 1i, K 2i ) end for return K end function K 1, K 2 {0, 1,..., q + 1} m K {0, 1,..., q + 1} m At any time a p, q)-hyperloglog sketch can be reduced to a p, q )-HyperLogLog data structure, if p p and p + q p + q is satisfied see Algorithm 3). This transformation is lossless in a sense that the resulting HyperLogLog sketch is the same as if all elements would have been recorded by a p, q )-HyperLogLog sketch right from the beginning. A p, 0)-HyperLogLog sketch corresponds to a bit array as used by linear counting [17]. Each register value can be stored by a single bit in this case. Hence, linear counting can be regarded as a special case of the HyperLogLog algorithm for which q = Joint probability distribution of register values Under the assumption of a uniform hash function, the probability that the register values K = K 1,..., K m ) of a HyperLogLog sketch with parameters p and q are equal to k = k 1,..., k m ) is given by the corresponding probability mass function ρk n) = n n m=n n n 1,..., n m ) 1 m n i=1 m γk i n i ) 1) 4
5 Algorithm 3 Compression of a p, q)-hyperloglog sketch with register values K = K 1,..., K m ) into a p, q )-HyperLogLog sketch with p p and p + q p + q. function CompressK) K {0, 1,..., q + 1} m, m = 2 p allocate K = K 1,..., K ) 2 p K {0, 1,..., q + 1} m, m = 2 p for i 1, 2 p do b i 1) 2 p p j 1 while j 2 p p K b+j = 0 do j j + 1 end while if j = 1 then K i mink b+j + p p, q + 1) else if j 2 p p then a 1,..., a p p 2 j 1 K i min{s a s = 1} {q + 1}) else K i 0 end if end for return K end function where n is the cardinality. The n distinct elements are distributed over all m registers according to a multinomial distribution with equal probabilities. γk n) is the probability that the value of a register is equal to k, after it was selected n times by the insertion algorithm 1 n = 0 k = 0 0 n = 0 1 k q + 1 γk n) := 0 n 1 k = 0 ) 1 1 n ) n n 1 1 k q k 2 k ) n 2 n 1 k = q + 1. q The order of register values K 1,..., K m is not important for the estimation of the cardinality. More formally, the multiset {K 1,..., K m } is a sufficient statistic for n. Since the values of the multiset are all in the range [0, q + 1] the multiset can also be represented as {K 1,..., K m } = 0 C 0 1 C1 q Cq q + 1) C q+1 where C k is the multiplicity of value k. As a consequence, the multiplicity vector C := C 0,..., C q+1 ) is also a sufficient statistic for the cardinality. In addition, this vector contains all the information about the HyperLogLog sketch that is required for cardinality estimation. The two HyperLogLog parameters can be obtained by p = log 2 q+1 k=0 C k) and q = dim C 2, respectively. Algorithm 4 shows the calculation of the multiplicity vector C for a given HyperLogLog sketch with register values K. 2) 5
6 Algorithm 4 Multiplicity vector extraction from a p, q)-hyperloglog sketch with m = 2 p registers having values K = K 1,..., K m ). function ExtractCountsK) allocate C = C 0,..., C q+1 ) C 0, 0,..., 0) for i 1, m do C Ki C Ki + 1 end for return C end function K {0, 1,..., q + 1} m 2.3. Poisson approximation Due to the statistical dependence of the register values, the probability mass function 1) makes further analysis difficult. Therefore, a Poisson model can be used [6], which assumes that the cardinality itself is distributed according to a Poisson distribution n Poissonλ). 3) Under the Poisson model the distribution of the register values is ρk λ) = = = = λ λn ρk n)e n! m γk i n i )e λ m n=0 n 1 =0 m i=1 n=0 q+1 k=0 n m=0 i=1 γk i n)e λ m γk n)e λ m n=0 k=1 λ n n!m n λ n n!m n ) ck λ n i n i!m n i q ) )) = e c 0 λ m e λ m2 k 1 e λ ck ) m2 k 1 e λ cq+1 m2 q. 5) Here c k denotes the multiplicity of value k in the multiset {k 1,..., k m }. The final factorization shows that the register values K 1,..., K m are independent and identically distributed under the Poisson model. The probability that a register has a value less than or equal to k for a given rate λ is given by 0 k < 0 P K k λ) = e λ m2 k 0 k q 1 k > q. 4) 6) 6
7 2.4. Depoissonization Due to the simpler probability mass function 5), it is easier to find an estimator ˆλ = ˆλK) for the Poisson rate λ than for the cardinality n under the fixed-size model 1). Depoissonization [18] finally allows to translate the estimates back to the fixed-size model. Assume we have found an unbiased estimator for the Poisson rate We know from 4) and therefore Eˆλ λ) = λ for all λ 0. 7) Eˆλ λ) = n=0 n=0 λ λn Eˆλ n)e n! 8) λ λn Eˆλ n)e n! = λ 9) holds for all λ 0. The unique solution of this equation is given by Eˆλ n) = n. 10) Hence, the unbiased estimator ˆλ conditioned on n is also an unbiased estimator for n, which motivates us to use ˆλ directly as estimator for the cardinality ˆn := ˆλ. As simulation results will show later, the Poisson approximation works well over the entire cardinality range, even for estimators that are not exactly unbiased. 3. Original cardinality estimation method The original cardinality estimator [6] is based on the idea that the number of distinct element insertions a register needs to reach the value k is proportional to m2 k. Given that, a rough cardinality estimate can be obtained by averaging the values {m2 K 1,..., m2 Km }. In the history of the HyperLogLog algorithm different averaging techniques have been proposed. First, there was the LogLog algorithm using the geometric mean and the SuperLogLog algorithm that enhanced the estimate by truncating the largest register values before applying the geometric mean [19]. Finally, the harmonic mean was found to give even better estimates as it is inherently less sensitive to outliers. The result is the so-called raw estimator which is given by m ˆn raw = α m 1 m = αmm2 m = α m m 2 K 1 m2 Km i=1 2 K i q+1 k=0 C. 11) k k2 Here α m is a bias correction factor which was derived for a given number of registers m as [6] )) 2 + x m ) 1 α m := m log 2 dx. 12) 1 + x 0 7
8 Numerical approximations of α m for various values of m have been listed in [6]. These approximations are used in many HyperLogLog implementations. However, since the published constants have been rounded to 4 significant digits, these approximations even introduce some bias for very high precisions p. For HyperLogLog sketches that are used in practice with 256 or more registers p 8), it is completely sufficient to use α := lim α m = 1 = ) m 2 log 2 as approximation for α m in 11), because the additional bias is negligible compared to the overall estimation error. Fig. 1 shows the distribution of the relative error for the raw estimator as function of the cardinality. The chart is based on randomly generated HyperLogLog sketches. More details of the experimental setup will be explained later in Section 3.5. Obviously, the raw estimator is biased for small and large cardinalities where it fails to return accurate estimates. In order to cover the entire cardinality range, corrections for small and large cardinalities have been proposed. As mentioned in Section 2.1, a HyperLogLog sketch with parameters p, q) can be mapped to a p, 0)-HyperLogLog sketch. Since q = 0 corresponds to linear counting and the reduced HyperLogLog sketch corresponds to a bitset with C 0 zeros, the linear counting cardinality estimator [17] can be used ˆn small = m logm/c 0 ). 14) The corresponding relative estimation error as depicted in Fig. 2 shows that this estimator is convenient for small cardinalities. It was proposed to use this estimator for small cardinalities as long as ˆn raw 5 2 m where the factor 5 2 was empirically determined [6]. For large cardinalities in the order of 2 p+q, for which a lot of registers are already in a saturated state, meaning that they have reached the maximum possible value q + 1, the raw estimator underestimates the cardinalities. For the 32-bit hash value case p + q = 32), which was considered in [6], following correction formula was proposed to take these saturated registers into account ˆn large = 2 32 log 1 ˆn raw /2 32). 15) The original estimation algorithm as presented in [6] including corrections for small and large cardinalities is summarized by Algorithm 5. The relative estimation error for the original method is shown in Fig. 3. Unfortunately, as can be clearly seen, the ranges where the estimation error is small for ˆn raw and ˆn small do not overlap. Therefore, the estimation error is much larger near the transition region. To reduce the estimation error for cardinalities close to this region, it was proposed to correct ˆn raw for bias. Empirically collected bias correction data is either stored as set of interpolation points [7], as lookup table [8], or as best-fitting polynomial [9]. However, all these empirical approaches treat the symptom and not the cause. The large range correction formula 15) is not satisfying either as it does not reduce the estimation error. Quite the contrary, it even makes the bias worse. However, instead 8
9 Algorithm 5 Original cardinality estimation algorithm for HyperLogLog sketches that use 32-bit hash values p + q = 32) for insertion of data items [6]. function EstimateCardinalityK) K {0, 1,..., q + 1} m, m = 2 p ˆn raw α m m 2 m i) 1 i=1 2 K raw estimate 11) if ˆn raw 5 2 m then C 0 {i K i = 0} if C 0 0 then return m logm/c 0 ) small range correction 14) else return ˆn raw end if else if ˆn raw then return ˆn raw else return 2 32 log1 ˆn raw /2 32 ) large range correction 15) end if end function Figure 1: The distribution of the relative estimation error over the cardinality for the raw estimator after evaluation of randomly generated HyperLogLog data structures with parameters p = 12 and q = 20. 9
10 Figure 2: The distribution of the relative estimation error for the linear counting estimator after evaluation of randomly generated bitmaps of size 2 12 which correspond to HyperLogLog sketches with parameters p = 12 and q = 0. Figure 3: The distribution of the relative estimation error over the cardinality for the original estimation algorithm after evaluation of randomly generated HyperLogLog data structures with parameters p = 12 and q =
11 of underestimating the cardinalities, they are now overestimated. Another indication for the incorrectness of the proposed large range correction is the fact that it is not even defined for all possible states. For instance, consider a p, q)-hyperloglog sketch with p+q = 32 for which all registers are equal to the maximum possible value q +1. The raw estimate would be ˆn raw = α m 2 33, which is greater than 2 32 and outside of the domain of the large range correction formula. A simple approach to avoid the need of any large range correction is to extend the operating range of the raw estimator to larger cardinalities. This can be easily accomplished by increasing p + q, which corresponds to using hash values with more bits. Each additional bit doubles the operating range which scales like 2 p+q. However, in case q 31 the number of possible register values, which are {0, 1,..., q + 1}, is greater than 32 which is no longer representable by 5-bit registers. Therefore, it was proposed to use 6 bits per register in combination with 64-bit hash values [7]. Even larger hash values are needless in practice, because it is unrealistic to encounter cardinalities of order Derivation of the raw estimator In order to better understand why the raw estimator fails for small and large cardinalities, we start with a brief and simple derivation without the restriction to large cardinalities n ) and without using complex analysis as in [6]. Let us assume that the register values have following cumulative distribution function λ P K k λ) = e m2 k. 16) For now we ignore that this distribution has infinite support and differs from the register value distribution under the Poisson model 6), whose support is limited to the range [0, q + 1]. For a random variable K obeying 16) the expectation of 2 K is given by E2 K ) = k= where the function 2 k e λ m2 k e λ m2 k 1 ) = 1 2 ξx) := log2) k= k= 2 k e λ m 2k = α m ξlog 2 λ/m)), 17) λ 2 k+x e 2k+x 18) is a smooth periodic function with period 1. Numerical evaluations indicate that this function can be bounded by 1 ε ξ ξx) 1 + ε ξ with ε ξ := see Fig. 4). This value can also be found using Fourier analysis as shown in Appendix A. Let K 1,..., K m be a sample distributed according to 16). For large sample sizes m we have asymptotically ) 1 E 2 K K m = m 1 E2 K K m) = 1 me2 K ). 19) 11
12 Figure 4: The deviation of ξx) from 1. Together with 17) we obtain α m 2 ) ξlog λ = E 2 λ/m)) 2 K K m for m. 20) Therefore, the asymptotic relative bias of ˆλ = α m 2 2 K K m 21) is bounded by ε ξ, which makes this statistic a good estimator for the Poisson parameter. It also corresponds to the raw estimator 11), if the Poisson parameter estimate is used as cardinality estimate see Section 2.4) Limitations of the raw estimator The raw estimator is based on two prerequisites. First, the number of registers needs to be sufficiently large m ). And second, the distribution of register values can be described by 16). However, the latter is not true for small and large cardinalities, which is finally the reason for the bias of the raw estimator. A random variable K with cumulative distribution function 16) can be transformed into a random variable K with cumulative distribution function 6) using K = min max K, 0 ), q + 1 ). 22) Therefore, register values K 1,..., K m can be seen as the result after applying this transformation to a sample K 1,..., K m of the distribution described by 16). If all registers values fall into the range [1, q], they must be identical to the values K 1,..., K m. In other words, the observed register values are also a plausible sample of the assumed distribution described by 16) in this case. Hence, as long as all or at least most register values are in the range [1, q], which is the case if 2 p λ 2 p+q, the approximation of 12
13 6) by 16) is valid. This explains why the raw estimator works best for intermediate cardinalities. However, for small and large cardinalities many register values are equal to 0 or q + 1, respectively, which cannot be described by 16) and finally leads to the observed bias Corrections to the raw estimator If we knew the values K 1,..., K m for which transformation 22) led to the observed register values K 1,..., K m, we would be able to estimate λ using ˆλ = α m 2. 23) 2 K K m As we have already shown, this estimator is approximately unbiased, because all K i follow the assumed distribution. It would be even sufficient, if we knew the multiplicity C k of each k Z in {K 1,..., K m}, C k := {i k = K i }, because the raw estimator can be also written as α m ˆλ 2 =. 24) k= C k2 k Due to 22), the multiplicities C k and the multiplicities C k for the observed register values have following relationships C 0 = 0 k= C k, C k = C k, 1 k q, C q+1 = 25) k=q+1 C k. The idea is now to find estimates ĉ k for all k Z and use them as replacements for C k in 24). For k [1, q] where C k = C k we can use the trivial estimators ĉ k := C k, 1 k q. 26) To get estimators for k 0 and k q + 1, we consider the expectation of C k EC k ) = m P K k λ) P K k 1 λ) ) = me λ m2 k 1 e λ m2 k ). 27) From 6) we know that EC 0 /m) = e λ m and E1 C q+1 /m) = e λ m2 q, and therefore, we can also write EC k ) = m EC 0/m)) 2 k 1 EC 0 /m)) 2 k) 28) and EC k ) = m E1 C q+1/m)) 2q k 1 E1 C q+1 /m)) 2q k), 29) which motivates us to use ĉ k = m C 0/m) 2 k 1 C 0 /m) 2 k) 30) 13
14 as estimator for k 0 and ĉ k = m 1 C q+1/m) 2q k 1 1 C q+1 /m) 2q k) 31) as estimator for k q + 1, respectively. This choice of estimators also conserves the mass of zero-valued and saturated registers, because 25) is satisfied, if C k is replaced by ĉ k. Plugging all these estimators into 24) as replacements for C k finally gives ˆλ = α m 2 = α m 2 k= ĉ k 2 k m σc 0 /m) + q k=1 C k2 k + m τ1 C q+1 /m)2 q 32) which we call the improved raw estimator. Here m σc 0 /m) and 2m τ1 C q+1 /m) are replacements for C 0 and C q+1 in the raw estimator 11), respectively. The functions σ and τ are defined as σx) := x + x 2k 2 k 1 33) and τx) := 1 2 x + k=1 ) x 2 k 2 k. 34) We can cross-check the new estimator for the linear counting case with q = 0. Using the identity σx) + τx) = α ξlog 2 log1/x)))/ log1/x), 35) we get ˆλ = k=1 α m σc 0 /m) + τc 0 /m) = m logm/c 0 ) ξlog 2 logm/c 0 ))) which is as expected almost identical to the linear counting estimator 14), because ξx) 1 see Section 3.1) Improved raw estimation algorithm The improved raw estimator 32) can be directly translated into a new cardinality estimation algorithm for HyperLogLog sketches as shown in Algorithm 6. Since the series 33) converges quadratically for all x [0, 1) and its terms can be recursively calculated using elementary operations, the function σ can be quickly calculated to machine precision. The case x = 1 must be handled separately, because the series diverges and causes an infinite denominator in 32) and therefore a vanishing cardinality estimate. As this case only occurs if all register values are zero C 0 = m), this is exactly what is expected. Among the remaining possible arguments {0, 1 m, 2 m,..., m 1 m } we have slowest convergence for x = m 1 m. However, even in this case we have a manageable amount of iteration cycles. For example, if double-precision floating-point arithmetic is used, the routine for calculating σ converges after 18 and 26 iteration cycles for p = 12 and p = 20, respectively. 36) 14
15 The calculation of τ is more expensive, because it involves square root evaluations. τ can also be written in a numerically more favorable way as ) τx) := 1 1 x 1 x 2 k) 2 2 k. 37) 3 k=1 This representation shows faster convergence for x > 0, because 1 x 2 k logx)2 k. Therefore, the convergence speed is comparable to a geometric series with ratio 1/8. Disregarding the trivial case τ0) = 0, x = 1 m shows slowest convergence speed among all other possible parameters. For this case and if double-precision floating-point numbers are used, the function τ presented in Algorithm 6 converges after 21 and 22 iteration cycles for considered precisions p = 12 and p = 20, respectively. If performance matters σ and τ can also be precalculated for all possible values of C 0 and C q+1. As their value range is {0, 1,..., m}, the function values can be kept in lookup tables of size m + 1. In this way a complete branch-free cardinality estimation can be realized. It is also thinkable to calculate τ using the approximation τx) α / log1/x) σx) which can be obtained from 35). The advantage is that the calculation of σ and the additional logarithm is slightly faster than the calculation of τ. However, for arguments close to 1, where α / log1/x) and σx) are both very large while their difference is very small, special care is needed to avoid numerical cancellation. The new estimation algorithm is very elegant, because it does neither contain magic numbers nor special cases as the original algorithm. Moreover, the algorithm guarantees monotonicity of the cardinality estimate. The estimate will never become smaller when adding new elements. Although this sounds self-evident, previous approaches that combine estimators for different cardinality ranges or make use of empirical collected data have problems to satisfy this property throughout all cardinalities Experimental setup To verify the new estimation algorithm, we generated different HyperLogLog sketches and filled each of them with 50 billion unique elements. During element insertion, we took snapshots of the sketch state by storing the multiplicity vector at predefined cardinality values, which were roughly chosen according to a geometric series with ratio In order to achieve that in reasonable time for all the different HyperLogLog parameter combinations p, q) we have been interested in, we applied a couple of optimizations. First, we assumed a uniform hash function. This allows us to simply generate random numbers instead of creating unique elements and calculating their hash values. We used the Mersenne Twister random number generator with a state size of bits from the C++ standard library. Second, we used Algorithm 7 for insertions, which does basically the same as Algorithm 1, but additionally keeps track of the multiplicity vector and the minimum register value. In this way the expensive register scan needed to obtain the multiplicity vector as described by Algorithm 4 can be avoided. Furthermore, the knowledge of the minimum register value can be used to abort the insertion procedure 15
16 Algorithm 6 Cardinality estimation based on the improved raw estimator. The input is the multiplicity vector C = C 0,..., C q+1 ) as obtained by Algorithm 4. function EstimateCardinalityC) q+1 k=0 C k = m z m τ1 C q+1 /m) for k q, 1 do z 0.5 z + C k ) end for z z + m σc 0 /m) return α m 2 /z end function function σx) x [0, 1] if x = 1 then return end if y 1 z x repeat x x x z z z z + x y y 2 y until z = z return z end function function τx) x [0, 1] if x = 0 x = 1 then return 0 end if y 1 z 1 x repeat x x z z y 0.5 y z z 1 x) 2 y until z = z return z/3 end function alternatively, take m τ1 C q+1 /m) from precalculated lookup table alternatively, take m σc 0 /m) from precalculated lookup table α := 1/2 log2)) 16
17 early, if the hash value is not able to increment any register value. Especially at large cardinalities this saves a great number of register accesses and also reduces the number of cache misses. For example, if K min = 1 only half of all insertions will access a register. If K min = 2 it is already just a quarter, and so forth. Finally, instead of repeating the simulation for different HyperLogLog parameters, we did that only once using the quite accurate setting p = 22 and q = 42. Whenever taking a snapshot, we reduced the sketch state exploiting Algorithm 3 for desired parameters before calculating the multiplicity vector using Algorithm 4. After all, we got the multiplicity vectors at predefined cardinalities of different simulation runs for various HyperLogLog parameter settings. All this data constitutes the basis of the presented results that follow. The generated data allows a quick and simple evaluation of cardinality estimation algorithms by just loading the persisted multiplicity vectors from hard disk and passing them as input to the algorithm. Algorithm 7 Extension of Algorithm 1 that keeps track of the multiplicity vector C = C 0,..., C q+1 ) and the minimum register value K min during insertion. Initially, K min = 0 and C = m, 0, 0,..., 0). procedure InsertElementD) a 1,..., a p, b 1,..., b q 2 p + q)-bit hash value of D a i, b i {0, 1} k min{s b s = 1} {q + 1}) k {1, 2,..., q + 1} if k > K min then i 1 + a 1,..., a p 2 i {1, 2,..., m} if k > K i then C Ki C Ki 1 C k C k + 1 if K i = K min then while C Kmin = 0 do K min K min + 1 end while end if K i k end if end if end procedure 3.6. Estimation error Fig. 5 shows the distribution of the relative error of the estimated cardinality using Algorithm 6 compared to the true cardinality for p = 12 and q = 20. As the mean shows, the error is unbiased over the entire cardinality range. The new approach is able to accurately estimate cardinalities up to 4 billions 2 p+q ) which is about an order of magnitude larger than the operating range upper bound of the raw estimator Fig. 1). 17
18 Figure 5: Relative error of the improved raw estimator as a function of the true cardinality for a HyperLogLog sketch with parameters p = 12 and q = 20. The improved raw estimator beats the precision of methods that apply bias correction on the raw estimator [7, 8, 9]. Based on the simulated data we have empirically determined the bias correction function w corr for the raw estimator 11) that satisfies n = Ew corr ˆn raw ) n) for all cardinalities. By definition, the estimator ˆn raw := w corr ˆn raw ) is unbiased and a function of the raw estimator. Its standard deviation can be compared with that of the improved raw estimator in Fig. 6. For cardinalities smaller than the empirical bias correction approach is not very precise. This is the reason why all previous approaches had to switch over to the linear counting estimator at some point. The standard deviation of the linear counting estimator is also shown in Fig. 6. Obviously, the previous approaches cannot do better than given by the minimum of both curves for linear counting and raw estimator. In practice, the standard deviation is even larger, because the choice between both estimators must be made based on an estimate and not on the true cardinality, for which the intersection point of both curves represents the ideal transition point. In contrast, the improved raw estimator performs well over the entire cardinality range. The new estimation algorithm also works well for other HyperLogLog configurations. First we considered configurations using a 32-bit hash function p + q = 32). The relative estimation error for precisions p = 8, p = 16, and p = 22 are shown in Figs. 7 to 9, respectively. As expected, since p + q = 32 is kept constant, the operating range remains more or less the same, while the relative error decreases with increasing precision parameter p. Again, the new algorithm gives essentially unbiased estimates. Only for very high precisions, an oscillating bias becomes apparent compare Fig. 9), that is caused by approximating the periodic function ξ by a constant see Section 3.1). As proposed in [7], the operating range can be extended by replacing the 32-bit hash 18
19 Figure 6: Standard deviations of the relative error of different cardinality estimators over the true cardinality for a HyperLogLog sketch with parameters p = 12 and q = 20. Figure 7: Relative error of the improved raw estimator as a function of the true cardinality for a HyperLogLog sketch with parameters p = 8 and q =
20 Figure 8: Relative error of the improved raw estimator as a function of the true cardinality for a HyperLogLog sketch with parameters p = 16 and q = 16. Figure 9: Relative error of the improved raw estimator as a function of the true cardinality for a HyperLogLog sketch with parameters p = 22 and q =
21 Figure 10: Relative error of the improved raw estimator as a function of the true cardinality for a HyperLogLog sketch with parameters p = 12 and q = 52. function by a 64-bit hash function. Fig. 10 shows the relative error for such a Hyper- LogLog configuration with parameters p = 12 and q = 52. The doubled hash value size shifts the maximum trackable cardinality value towards As Fig. 10 shows, when compared to the 32-bit hash value case given in Fig. 5, the estimation error remains constant over the entire simulated cardinality range up to 50 billions. We also evaluated the case p = 12 and q = 14, which is interesting, because the register values are limited to the range [0, 15]. As a consequence, 4 bits are sufficient for representing a single register value. This allows two registers to share a single byte, which is beneficial from a performance perspective. Nevertheless, this configuration still allows the estimation of cardinalities up to 100 millions as shown in Fig. 11, which could be enough for many applications Performance To evaluate the performance of the improved raw estimation algorithm, we investigated the average computation time to obtain the cardinality from a given multiplicity vector. For different cardinality values we loaded the precalculated multiplicity vectors see Section 3.5) of 1000 randomly generated HyperLogLog sketches into main memory. The average computation time was determined by cycling over these multiplicity vectors and passing them as input to the algorithm. For each evaluated cardinality value the average execution time was calculated after 100 cycles which corresponds to algorithm executions for each cardinality value. The results for HyperLogLog configurations p = 12, q = 20 and p = 12, q = 52 are shown in Fig. 12. Two variants of Algorithm 6 have been evaluated for which the functions σ and τ have been either calculated on demand 21
22 Figure 11: Relative error of the improved raw estimator as a function of the true cardinality for a HyperLogLog sketch with parameters p = 12 and q = 14. or taken from a lookup table. All these benchmarks where carried out on an Intel Core i5-2500k clocking at 3.3 GHz. The results show that the execution times are nearly constant for q = 52. Using a lookup table makes not much difference, because the on-demand calculation for σ is very fast and the calculation of τ is rarely needed due to the small probability of saturated registers, C 53 = 0 usually holds for realistic cardinalities. If lookup tables are used, the computation time is as expected independent of the cardinality also for the case q = 20. The faster computation times for q = 20 compared to the q = 52 case can be explained by the much smaller dimension of the multiplicity vector which is equal to q + 2. In contrast, if functions σ and τ are calculated on demand, executions take significantly more time for larger cardinalities. The reason is that beginning at cardinality values in the order of the probability of saturated registers increases. This makes the calculation of τ necessary, which is much more expensive than that of σ, because it requires more iterations and involves square root evaluations. However, the calculation of τ could be avoided at all, if the HyperLogLog parameters are appropriately chosen. If 2 p+q is much larger than the maximum expected cardinality value, the number of saturated registers will be negligible, C q+1 m. The calculation of τ could be omitted in this case, because τ1 C q+1 /m) 0. The numbers presented in Fig. 12 do not include the processing time to extract the multiplicity vector out of the HyperLogLog sketch, which requires a complete scan over all registers and counting the different register values into an array as demonstrated by Algorithm 4. A theoretical lower bound for this processing time can be derived using the maximum memory bandwidth of the CPU, which is 21 GB/s for an Intel Core i5-2500k. If we consider a HyperLogLog sketch with precision p = 12 which uses 5 bits per register, 22
23 Figure 12: Average computation time as a function of the true cardinality with an Intel Core i5-2500k clocking at 3.3 GHz when estimating the cardinality from HyperLogLog sketches with parameters p = 12, q = 20 and p = 12, q = 52, respectively. Both cases, σ and τ precalculated and calculated on demand have been considered. the total data size of the HyperLogLog sketch is 2.5 kb minimum. Consequently, the transfer time from main memory to CPU will be at least 120 ns. Having this value in mind, the presented numbers for estimating the cardinality from the multiplicity vector are quite satisfying. 4. Maximum likelihood estimation We know from Section 2.4 that any unbiased estimator for the Poisson parameter is also an unbiased estimator for the cardinality. Moreover, we know that under suitable regularity conditions of the probability mass function the maximum likelihood estimator is asymptotically efficient [20]. This means, if the number of registers m is large enough, the maximum likelihood method should give us an unbiased estimator for the cardinality. For HyperLogLog sketches that have been obtained without stochastic averaging see Section 2.1) the maximum likelihood method was already previously considered [21]. The register values are statistically independent by nature in this case, which allows factorization of the joint probability mass function and a straightforward calculation of the maximum likelihood estimate. The practically more relevant case which uses stochastic averaging and which is considered in this paper, would lead to a more complicated likelihood function compare 1)). However, the Poisson approximation makes the maximum likelihood method feasible again and we are finally able to derive another new robust and efficient cardinality estimation algorithm. Furthermore, in the course of the 23
24 derivation we will demonstrate that consequent application of the maximum likelihood method reveals that the cardinality estimate needs to be roughly proportional to the harmonic mean for intermediate cardinality values. The history of the HyperLogLog algorithm shows that the raw estimator 11) was first found after several attempts using the geometric mean [6, 19] Log-likelihood function Using the probability mass function of the Poisson model 5) the log-likelihood and its derivative are given by log Lλ K) = λ m q C k q ) ) 2 k + C k log 1 e λ m2 k + C q+1 log 1 e λ m2 q k=0 k=1 38) and d dλ log Lλ K) = 1 λ λ m q C k q 2 k + k=0 k=1 C k λ m2 k + C 1 e λ q+1 m2 k λ m2 q 1 e λ m2 q ). 39) As a consequence, the maximum likelihood estimate for the Poisson parameter is given by ˆλ = mˆx, 40) if ˆx denotes the root of the function fx) := x q C k q 2 k + k=0 This function can also be written as fx) := x k=0 k=1 where the function hx) is defined as k=1 C k x 2 k x 2 q + C 1 e x q+1 2 k 1 e. 41) x 2 q q C k q x ) x ) 2 k + C k h 2 k + C q+1 h 2 q m C 0 ), 42) hx) := 1 x e x 1. 43) hx) is strictly increasing and concave as can be seen in Fig. 13. For nonnegative values this function ranges from h0) = 0 to hx ) = 1. Since the function fx) is also strictly increasing, it is obvious that there exists a unique root ˆx for which fˆx) = 0. The function is nonpositive at 0 since f0) = C 0 m 0 and, in case C q+1 < m which implies q C k k=0 > 0, the function is at least linearly increasing. C 2 k q+1 = m corresponds to the case with all registers equal to the maximum value q + 1, for which the maximum likelihood estimate would be positive infinite. It is easy to see that the estimate ˆλ remains equal or becomes larger, when inserting an element into the HyperLogLog sketch following Algorithm 1. An update potentially 24
25 Figure 13: The function hx). changes the multiplicity vector C 0,..., C q+1 ) to C 0,..., C i 1,..., C j + 1,..., C q+1 ) where i < j. Writing 42) as x ) fx) := C 0 x + C 1 h x ) x ) C 2 h x ) x ) + C q h 2 q + x ) 2 q 1 + C q+1 h x 2 q ) ) 1. 44) shows that the coefficient of C i is larger than the coefficient of C j in case i < j. Keeping x fixed during an update decreases fx). As a consequence, since fx) is increasing, the new root and hence the estimate must be larger than prior the update. For the special case q = 0, which corresponds to the already mentioned linear counting algorithm, 41) can be solved analytically. In this case, the maximum likelihood method under the Poisson model leads directly to the linear counting estimator 14). Due to this fact we could expect that maximum likelihood estimation under the Poisson model also works well for the more general HyperLogLog case Inequalities for the maximum likelihood estimate In the following we derive lower and upper bounds for ˆx. Applying Jensen s inequality on h in 42) gives an upper bound for fx): fx) x q k=0 C k 2 k + m C 0) h x q k=1 C k + C q+1 2 k 2 q m C 0 ) m C 0 ). 45) The left-hand side is zero, if ˆx is inserted. Resolution for ˆx finally gives the lower bound q C m C k 0 k=1 + C ) q+1 2 ˆx q C k k=1 + C log 1 + k 2 q q+1 q. 46) C k 2 k 2 q k=0 2 k 25
26 This bound can be weakened using log1 + x) 2x x+2 Using the monotonicity of h, the lower bound fx) x k=0 for x 0 which results in m C 0 ˆx C q C k 2 k=1 + C. 47) q+1 2 k 2 q+1 q C k q x ) x ) 2 k + C k h + C q+1 h m C 0 ) 48) 2 K max 2 K max k=1 can be found, where K max := mink max, q) and K max := max{k C k > 0}). inserting ˆx and transformation gives ) m C ˆx 2 K max 0 log q K max k=0 as upper bound which can be weakened using log1 + x) x for x 0 C k 2 k Again, 49) ˆx m C 0 q C k k=0 2 k. 50) If the HyperLogLog sketch is in the intermediate range, where C 0 = C q+1 = 0 the bounds 47) and 50) differ only by a constant factor and both are proportional to the harmonic mean of 2 K 1,..., 2 Km. Hence, consequent application of the maximum likelihood method would have directly suggested to use a cardinality estimator that is proportional to the harmonic mean without knowing the raw estimator 11) in advance Computation of the maximum likelihood estimate Since f is concave and increasing, both, Newton-Raphson iteration and the secant method, will converge to the root, provided that the function is negative for the chosen starting points. We will use the secant method to derive the new cardinality estimation algorithm. Even though the secant method has the disadvantage of slower convergence, a single iteration is simpler to calculate as it does not require the evaluation of the first derivative. An iteration step of the secant method can be written as x i = x i 1 x i 1 x i 2 ) fx i 1 ) fx i 1 ) fx i 2 ). 51) If we set x 0 equal to 0, for which fx 0 ) = m C 0 ), and x 1 equal to one of the derived lower bounds 46) or 47), the sequence x 0, x 1, x 2,...) is monotone increasing. Using the definitions x i := x i x i 1 52) and gx) := fx) + m C 0 ) = x q C k q x ) x ) 2 k + C k h 2 k + C q+1 h 2 q k=0 k=1 53) 26
27 the iteration scheme can also be written as x i = x i 1 m C 0 ) gx i 1 ) gx i 1 ) gx i 2 ), 54) x i = x i 1 + x i. 55) The iteration can be stopped, if x i δ x i. Since the expected statistical error for the HyperLogLog data structure scales according to 1 m [6], it makes sense to choose δ = ε m with some constant ε. For all results presented later in Section 4.5 we used ε = Maximum likelihood estimation algorithm To get a fast cardinality estimation algorithm, it is crucial to minimize evaluation costs for 53). A couple of optimizations allow significant reduction of computational effort: Only a fraction of all count values C k is nonzero. If we denote K min := min{k C k > 0}) and K max := max{k C k > 0}), it is sufficient to loop over all indices in the range [K min, K max ]. C k 2 k in 53) can be precalculated and reused for all function evalu- The sum q ations. k=0 Many programming languages allow the efficient multiplication and division by any integral power of two using special functions, such as ldexp in C/C++ or scalb in Java. { The function hx) only needs to be evaluated at points x, x,..., x 2 K max 2 K max 1 2 K min where K max := mink max, q). This series corresponds to a geometric series with ratio two. A straightforward calculation using 43) is ) very expensive because of the exponential function. However, if we know h x all other required function 2 K max values can be easily obtained using the identity h4x) = x + h2x) 1 h2x)). 56) x + 1 h2x)) This recursive formula is stable in a sense that the relative error of h4x) is smaller than that of h2x) as shown in Appendix B. If x is smaller than 0.5, the function hx) can be well approximated by a Taylor series around x = 0 hx) = x 2 x x4 720 x Ox8 ), 57) which can be optimized for numerical evaluation using Estrin s scheme and x := x 2 and x := x x hx) = x x /3 + x x ) 1/45 x /472.5 ) + Ox 8 ). 58) } 27
28 x The smallest argument for which h needs to be evaluated is. If C 2 K q+1 = 0, max we can find an upper bound for the smallest argument using 49) x ˆx K max k=0 log 1 + C ) k 2 K max 2 K max K 2 K log ) max max C k k=0 2 k x 2 K max In practice, 0.5 is satisfied most of the time as long as only a few registers x are saturated, that is C q+1 m. In case > 0.5, h ) x 2 K max 2 is calculated instead κ x with κ = 2+ log 2 x). By ) definition, which allows using the Taylor series κ approximation. h x is finally obtained after κ K max iterations using 56). 2 K max As shown in Appendix C, a small approximation error of h does not have much impact on the error of the maximum likelihood estimate as long as most registers are not saturated. Putting all these optimizations together finally gives the new cardinality estimation algorithm presented as Algorithm 8. The algorithm requires mainly only elementary operations. For very large cardinalities it makes sense to use the strong 46) instead of the weak lower bound 47) as second starting point for the secant method. The stronger bound is a much better approximation especially for large cardinalities, where the extra logarithm evaluation is amortized by savings in the number of iteration cycles. Therefore, the presented algorithm switches over to the stronger bound, if q C k k=1 + C q+1 2 k 2 q q k=0 > ) C k 2 k is satisfied. The threshold value of 1.5 was found to be a reasonable choice in order to reduce the computation time for large cardinalities significantly Estimation error We have investigated the estimation error of the maximum likelihood estimation algorithm for the same HyperLogLog configurations as for the improved raw estimation algorithm in Section 3.6. Figs. 14 to 19 show very similar results for same HyperLogLog parameters. What is different for the maximum likelihood estimation approach is a somewhat smaller median bias with less oscillations around zero for small cardinalities. The standard deviation of the relative error is also slightly better for the maximum likelihood estimator than for the improved raw estimator as shown in Fig. 6. Furthermore, contrary to the improved raw estimator which reveals a small oscillating bias for the mean see Fig. 9), the maximum likelihood estimator seems to be completely unbiased see Fig. 17) Performance We also measured the performance of Algorithm 8 using the same test setup as described in Section 3.7. The results for HyperLogLog configurations p = 12, q = 20 and p = 28
29 Algorithm 8 Cardinality estimation based on the maximum likelihood principle. The input is the multiplicity vector C = C 0,..., C q+1 ) as obtained by Algorithm 4. function EstimateCardinalityC) q+1 k=0 C k = m if C q+1 = m then return end if K min min{k C k > 0}) K min maxk min, 1) K max max{k C k > 0}) K max mink max, q) z 0 for k K max, K min do z 0.5 z + C k end for z z 2 K min c C q+1 if q 1 then c c + C K max end if g prev 0 a z + C 0 b z + C q+1 2 q here z = q C k k=1 2 k a = q C k k=0 2 k b = q k=1 C k + C q+1 2 k 2 q m m C 0 if b 1.5 a then x m /0.5 b + a) weak lower bound 47) else x m /b log1 + b/a) strong lower bound 46) end if 29
30 Algorithm 8 continued) x x while x > x δ do secant method iteration δ = ε/ m, ε = 10 2 κ 2 + log 2 x) x x 2 maxk max,κ) 1 x [0, 0.25] x x x h x x /3 + x x ) 1/45 x /472.5) Taylor approximation 58) for k κ 1), K max do h x +h 1 h) x +1 h) calculate h ) x 2, see 56), k at this point x = x 2x end for g c h compare 53) for k K max 1), K min do h x +h 1 h) x +1 h) calculate h x g g + C k h x 2x end for g g + x a if g > g prev m g then x x else x 0 end if x x + x g prev g end while return m x end function m g g g prev see 54) x 2 k+2 ) 2, see 56), k at this point x = x 2 k+2 30
31 Figure 14: Relative error of the maximum likelihood estimates as a function of the true cardinality for a HyperLogLog sketch with parameters p = 12 and q = 20. Figure 15: Relative error of the maximum likelihood estimates as a function of the true cardinality for a HyperLogLog sketch with parameters p = 8 and q =
How Philippe Flipped Coins to Count Data
 1/18 How Philippe Flipped Coins to Count Data Jérémie Lumbroso LIP6 / INRIA Rocquencourt December 16th, 2011 0. DATA STREAMING ALGORITHMS Stream: a (very large) sequence S over (also very large) domain
1/18 How Philippe Flipped Coins to Count Data Jérémie Lumbroso LIP6 / INRIA Rocquencourt December 16th, 2011 0. DATA STREAMING ALGORITHMS Stream: a (very large) sequence S over (also very large) domain
INTRODUCTION TO COMPUTATIONAL MATHEMATICS
 INTRODUCTION TO COMPUTATIONAL MATHEMATICS Course Notes for CM 271 / AMATH 341 / CS 371 Fall 2007 Instructor: Prof. Justin Wan School of Computer Science University of Waterloo Course notes by Prof. Hans
INTRODUCTION TO COMPUTATIONAL MATHEMATICS Course Notes for CM 271 / AMATH 341 / CS 371 Fall 2007 Instructor: Prof. Justin Wan School of Computer Science University of Waterloo Course notes by Prof. Hans
CSE332: Data Structures & Parallelism Lecture 2: Algorithm Analysis. Ruth Anderson Winter 2019
 CSE332: Data Structures & Parallelism Lecture 2: Algorithm Analysis Ruth Anderson Winter 2019 Today Algorithm Analysis What do we care about? How to compare two algorithms Analyzing Code Asymptotic Analysis
CSE332: Data Structures & Parallelism Lecture 2: Algorithm Analysis Ruth Anderson Winter 2019 Today Algorithm Analysis What do we care about? How to compare two algorithms Analyzing Code Asymptotic Analysis
Chapter 3: Root Finding. September 26, 2005
 Chapter 3: Root Finding September 26, 2005 Outline 1 Root Finding 2 3.1 The Bisection Method 3 3.2 Newton s Method: Derivation and Examples 4 3.3 How To Stop Newton s Method 5 3.4 Application: Division
Chapter 3: Root Finding September 26, 2005 Outline 1 Root Finding 2 3.1 The Bisection Method 3 3.2 Newton s Method: Derivation and Examples 4 3.3 How To Stop Newton s Method 5 3.4 Application: Division
The Growth of Functions. A Practical Introduction with as Little Theory as possible
 The Growth of Functions A Practical Introduction with as Little Theory as possible Complexity of Algorithms (1) Before we talk about the growth of functions and the concept of order, let s discuss why
The Growth of Functions A Practical Introduction with as Little Theory as possible Complexity of Algorithms (1) Before we talk about the growth of functions and the concept of order, let s discuss why
15-451/651: Design & Analysis of Algorithms September 13, 2018 Lecture #6: Streaming Algorithms last changed: August 30, 2018
 15-451/651: Design & Analysis of Algorithms September 13, 2018 Lecture #6: Streaming Algorithms last changed: August 30, 2018 Today we ll talk about a topic that is both very old (as far as computer science
15-451/651: Design & Analysis of Algorithms September 13, 2018 Lecture #6: Streaming Algorithms last changed: August 30, 2018 Today we ll talk about a topic that is both very old (as far as computer science
CSE332: Data Structures & Parallelism Lecture 2: Algorithm Analysis. Ruth Anderson Winter 2018
 CSE332: Data Structures & Parallelism Lecture 2: Algorithm Analysis Ruth Anderson Winter 2018 Today Algorithm Analysis What do we care about? How to compare two algorithms Analyzing Code Asymptotic Analysis
CSE332: Data Structures & Parallelism Lecture 2: Algorithm Analysis Ruth Anderson Winter 2018 Today Algorithm Analysis What do we care about? How to compare two algorithms Analyzing Code Asymptotic Analysis
This ensures that we walk downhill. For fixed λ not even this may be the case.
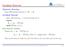 Gradient Descent Objective Function Some differentiable function f : R n R. Gradient Descent Start with some x 0, i = 0 and learning rate λ repeat x i+1 = x i λ f(x i ) until f(x i+1 ) ɛ Line Search Variant
Gradient Descent Objective Function Some differentiable function f : R n R. Gradient Descent Start with some x 0, i = 0 and learning rate λ repeat x i+1 = x i λ f(x i ) until f(x i+1 ) ɛ Line Search Variant
Chapter 1. Root Finding Methods. 1.1 Bisection method
 Chapter 1 Root Finding Methods We begin by considering numerical solutions to the problem f(x) = 0 (1.1) Although the problem above is simple to state it is not always easy to solve analytically. This
Chapter 1 Root Finding Methods We begin by considering numerical solutions to the problem f(x) = 0 (1.1) Although the problem above is simple to state it is not always easy to solve analytically. This
CSE332: Data Structures & Parallelism Lecture 2: Algorithm Analysis. Ruth Anderson Winter 2018
 CSE332: Data Structures & Parallelism Lecture 2: Algorithm Analysis Ruth Anderson Winter 2018 Today Algorithm Analysis What do we care about? How to compare two algorithms Analyzing Code Asymptotic Analysis
CSE332: Data Structures & Parallelism Lecture 2: Algorithm Analysis Ruth Anderson Winter 2018 Today Algorithm Analysis What do we care about? How to compare two algorithms Analyzing Code Asymptotic Analysis
2.6 Complexity Theory for Map-Reduce. Star Joins 2.6. COMPLEXITY THEORY FOR MAP-REDUCE 51
 2.6. COMPLEXITY THEORY FOR MAP-REDUCE 51 Star Joins A common structure for data mining of commercial data is the star join. For example, a chain store like Walmart keeps a fact table whose tuples each
2.6. COMPLEXITY THEORY FOR MAP-REDUCE 51 Star Joins A common structure for data mining of commercial data is the star join. For example, a chain store like Walmart keeps a fact table whose tuples each
Lecture 7: Numerical Tools
 Lecture 7: Numerical Tools Fatih Guvenen January 10, 2016 Fatih Guvenen Lecture 7: Numerical Tools January 10, 2016 1 / 18 Overview Three Steps: V (k, z) =max c,k 0 apple u(c)+ Z c + k 0 =(1 + r)k + z
Lecture 7: Numerical Tools Fatih Guvenen January 10, 2016 Fatih Guvenen Lecture 7: Numerical Tools January 10, 2016 1 / 18 Overview Three Steps: V (k, z) =max c,k 0 apple u(c)+ Z c + k 0 =(1 + r)k + z
Asymptotic Notation. such that t(n) cf(n) for all n n 0. for some positive real constant c and integer threshold n 0
 Asymptotic Notation Asymptotic notation deals with the behaviour of a function in the limit, that is, for sufficiently large values of its parameter. Often, when analysing the run time of an algorithm,
Asymptotic Notation Asymptotic notation deals with the behaviour of a function in the limit, that is, for sufficiently large values of its parameter. Often, when analysing the run time of an algorithm,
14 Random Variables and Simulation
 14 Random Variables and Simulation In this lecture note we consider the relationship between random variables and simulation models. Random variables play two important roles in simulation models. We assume
14 Random Variables and Simulation In this lecture note we consider the relationship between random variables and simulation models. Random variables play two important roles in simulation models. We assume
Shannon-Fano-Elias coding
 Shannon-Fano-Elias coding Suppose that we have a memoryless source X t taking values in the alphabet {1, 2,..., L}. Suppose that the probabilities for all symbols are strictly positive: p(i) > 0, i. The
Shannon-Fano-Elias coding Suppose that we have a memoryless source X t taking values in the alphabet {1, 2,..., L}. Suppose that the probabilities for all symbols are strictly positive: p(i) > 0, i. The
Some Background Material
 Chapter 1 Some Background Material In the first chapter, we present a quick review of elementary - but important - material as a way of dipping our toes in the water. This chapter also introduces important
Chapter 1 Some Background Material In the first chapter, we present a quick review of elementary - but important - material as a way of dipping our toes in the water. This chapter also introduces important
We are going to discuss what it means for a sequence to converge in three stages: First, we define what it means for a sequence to converge to zero
 Chapter Limits of Sequences Calculus Student: lim s n = 0 means the s n are getting closer and closer to zero but never gets there. Instructor: ARGHHHHH! Exercise. Think of a better response for the instructor.
Chapter Limits of Sequences Calculus Student: lim s n = 0 means the s n are getting closer and closer to zero but never gets there. Instructor: ARGHHHHH! Exercise. Think of a better response for the instructor.
Scientific Computing: An Introductory Survey
 Scientific Computing: An Introductory Survey Chapter 5 Nonlinear Equations Prof. Michael T. Heath Department of Computer Science University of Illinois at Urbana-Champaign Copyright c 2002. Reproduction
Scientific Computing: An Introductory Survey Chapter 5 Nonlinear Equations Prof. Michael T. Heath Department of Computer Science University of Illinois at Urbana-Champaign Copyright c 2002. Reproduction
Algorithms and Their Complexity
 CSCE 222 Discrete Structures for Computing David Kebo Houngninou Algorithms and Their Complexity Chapter 3 Algorithm An algorithm is a finite sequence of steps that solves a problem. Computational complexity
CSCE 222 Discrete Structures for Computing David Kebo Houngninou Algorithms and Their Complexity Chapter 3 Algorithm An algorithm is a finite sequence of steps that solves a problem. Computational complexity
Outline. Math Numerical Analysis. Intermediate Value Theorem. Lecture Notes Zeros and Roots. Joseph M. Mahaffy,
 Outline Math 541 - Numerical Analysis Lecture Notes Zeros and Roots Joseph M. Mahaffy, jmahaffy@mail.sdsu.edu Department of Mathematics and Statistics Dynamical Systems Group Computational Sciences Research
Outline Math 541 - Numerical Analysis Lecture Notes Zeros and Roots Joseph M. Mahaffy, jmahaffy@mail.sdsu.edu Department of Mathematics and Statistics Dynamical Systems Group Computational Sciences Research
Math Numerical Analysis
 Math 541 - Numerical Analysis Lecture Notes Zeros and Roots Joseph M. Mahaffy, jmahaffy@mail.sdsu.edu Department of Mathematics and Statistics Dynamical Systems Group Computational Sciences Research Center
Math 541 - Numerical Analysis Lecture Notes Zeros and Roots Joseph M. Mahaffy, jmahaffy@mail.sdsu.edu Department of Mathematics and Statistics Dynamical Systems Group Computational Sciences Research Center
Numerical Methods in Informatics
 Numerical Methods in Informatics Lecture 2, 30.09.2016: Nonlinear Equations in One Variable http://www.math.uzh.ch/binf4232 Tulin Kaman Institute of Mathematics, University of Zurich E-mail: tulin.kaman@math.uzh.ch
Numerical Methods in Informatics Lecture 2, 30.09.2016: Nonlinear Equations in One Variable http://www.math.uzh.ch/binf4232 Tulin Kaman Institute of Mathematics, University of Zurich E-mail: tulin.kaman@math.uzh.ch
Outline. Scientific Computing: An Introductory Survey. Nonlinear Equations. Nonlinear Equations. Examples: Nonlinear Equations
 Methods for Systems of Methods for Systems of Outline Scientific Computing: An Introductory Survey Chapter 5 1 Prof. Michael T. Heath Department of Computer Science University of Illinois at Urbana-Champaign
Methods for Systems of Methods for Systems of Outline Scientific Computing: An Introductory Survey Chapter 5 1 Prof. Michael T. Heath Department of Computer Science University of Illinois at Urbana-Champaign
An Optimal Algorithm for l 1 -Heavy Hitters in Insertion Streams and Related Problems
 An Optimal Algorithm for l 1 -Heavy Hitters in Insertion Streams and Related Problems Arnab Bhattacharyya, Palash Dey, and David P. Woodruff Indian Institute of Science, Bangalore {arnabb,palash}@csa.iisc.ernet.in
An Optimal Algorithm for l 1 -Heavy Hitters in Insertion Streams and Related Problems Arnab Bhattacharyya, Palash Dey, and David P. Woodruff Indian Institute of Science, Bangalore {arnabb,palash}@csa.iisc.ernet.in
Lecture Notes to Accompany. Scientific Computing An Introductory Survey. by Michael T. Heath. Chapter 5. Nonlinear Equations
 Lecture Notes to Accompany Scientific Computing An Introductory Survey Second Edition by Michael T Heath Chapter 5 Nonlinear Equations Copyright c 2001 Reproduction permitted only for noncommercial, educational
Lecture Notes to Accompany Scientific Computing An Introductory Survey Second Edition by Michael T Heath Chapter 5 Nonlinear Equations Copyright c 2001 Reproduction permitted only for noncommercial, educational
Queens College, CUNY, Department of Computer Science Numerical Methods CSCI 361 / 761 Spring 2018 Instructor: Dr. Sateesh Mane.
 Queens College, CUNY, Department of Computer Science Numerical Methods CSCI 361 / 761 Spring 2018 Instructor: Dr. Sateesh Mane c Sateesh R. Mane 2018 3 Lecture 3 3.1 General remarks March 4, 2018 This
Queens College, CUNY, Department of Computer Science Numerical Methods CSCI 361 / 761 Spring 2018 Instructor: Dr. Sateesh Mane c Sateesh R. Mane 2018 3 Lecture 3 3.1 General remarks March 4, 2018 This
ROOT FINDING REVIEW MICHELLE FENG
 ROOT FINDING REVIEW MICHELLE FENG 1.1. Bisection Method. 1. Root Finding Methods (1) Very naive approach based on the Intermediate Value Theorem (2) You need to be looking in an interval with only one
ROOT FINDING REVIEW MICHELLE FENG 1.1. Bisection Method. 1. Root Finding Methods (1) Very naive approach based on the Intermediate Value Theorem (2) You need to be looking in an interval with only one
Jim Lambers MAT 610 Summer Session Lecture 2 Notes
 Jim Lambers MAT 610 Summer Session 2009-10 Lecture 2 Notes These notes correspond to Sections 2.2-2.4 in the text. Vector Norms Given vectors x and y of length one, which are simply scalars x and y, the
Jim Lambers MAT 610 Summer Session 2009-10 Lecture 2 Notes These notes correspond to Sections 2.2-2.4 in the text. Vector Norms Given vectors x and y of length one, which are simply scalars x and y, the
New Attacks on the Concatenation and XOR Hash Combiners
 New Attacks on the Concatenation and XOR Hash Combiners Itai Dinur Department of Computer Science, Ben-Gurion University, Israel Abstract. We study the security of the concatenation combiner H 1(M) H 2(M)
New Attacks on the Concatenation and XOR Hash Combiners Itai Dinur Department of Computer Science, Ben-Gurion University, Israel Abstract. We study the security of the concatenation combiner H 1(M) H 2(M)
Analysis of Algorithms [Reading: CLRS 2.2, 3] Laura Toma, csci2200, Bowdoin College
![Analysis of Algorithms [Reading: CLRS 2.2, 3] Laura Toma, csci2200, Bowdoin College Analysis of Algorithms [Reading: CLRS 2.2, 3] Laura Toma, csci2200, Bowdoin College](/thumbs/79/78926994.jpg) Analysis of Algorithms [Reading: CLRS 2.2, 3] Laura Toma, csci2200, Bowdoin College Why analysis? We want to predict how the algorithm will behave (e.g. running time) on arbitrary inputs, and how it will
Analysis of Algorithms [Reading: CLRS 2.2, 3] Laura Toma, csci2200, Bowdoin College Why analysis? We want to predict how the algorithm will behave (e.g. running time) on arbitrary inputs, and how it will
3.1 Introduction. Solve non-linear real equation f(x) = 0 for real root or zero x. E.g. x x 1.5 =0, tan x x =0.
 3.1 Introduction Solve non-linear real equation f(x) = 0 for real root or zero x. E.g. x 3 +1.5x 1.5 =0, tan x x =0. Practical existence test for roots: by intermediate value theorem, f C[a, b] & f(a)f(b)
3.1 Introduction Solve non-linear real equation f(x) = 0 for real root or zero x. E.g. x 3 +1.5x 1.5 =0, tan x x =0. Practical existence test for roots: by intermediate value theorem, f C[a, b] & f(a)f(b)
This chapter covers asymptotic analysis of function growth and big-o notation.
 Chapter 14 Big-O This chapter covers asymptotic analysis of function growth and big-o notation. 14.1 Running times of programs An important aspect of designing a computer programs is figuring out how well
Chapter 14 Big-O This chapter covers asymptotic analysis of function growth and big-o notation. 14.1 Running times of programs An important aspect of designing a computer programs is figuring out how well
Application: Bucket Sort
 5.2.2. Application: Bucket Sort Bucket sort breaks the log) lower bound for standard comparison-based sorting, under certain assumptions on the input We want to sort a set of =2 integers chosen I+U@R from
5.2.2. Application: Bucket Sort Bucket sort breaks the log) lower bound for standard comparison-based sorting, under certain assumptions on the input We want to sort a set of =2 integers chosen I+U@R from
Numerical Methods. King Saud University
 Numerical Methods King Saud University Aims In this lecture, we will... Introduce the topic of numerical methods Consider the Error analysis and sources of errors Introduction A numerical method which
Numerical Methods King Saud University Aims In this lecture, we will... Introduce the topic of numerical methods Consider the Error analysis and sources of errors Introduction A numerical method which
1 + lim. n n+1. f(x) = x + 1, x 1. and we check that f is increasing, instead. Using the quotient rule, we easily find that. 1 (x + 1) 1 x (x + 1) 2 =
 Chapter 5 Sequences and series 5. Sequences Definition 5. (Sequence). A sequence is a function which is defined on the set N of natural numbers. Since such a function is uniquely determined by its values
Chapter 5 Sequences and series 5. Sequences Definition 5. (Sequence). A sequence is a function which is defined on the set N of natural numbers. Since such a function is uniquely determined by its values
PART I Lecture Notes on Numerical Solution of Root Finding Problems MATH 435
 PART I Lecture Notes on Numerical Solution of Root Finding Problems MATH 435 Professor Biswa Nath Datta Department of Mathematical Sciences Northern Illinois University DeKalb, IL. 60115 USA E mail: dattab@math.niu.edu
PART I Lecture Notes on Numerical Solution of Root Finding Problems MATH 435 Professor Biswa Nath Datta Department of Mathematical Sciences Northern Illinois University DeKalb, IL. 60115 USA E mail: dattab@math.niu.edu
CHAPTER 10 Zeros of Functions
 CHAPTER 10 Zeros of Functions An important part of the maths syllabus in secondary school is equation solving. This is important for the simple reason that equations are important a wide range of problems
CHAPTER 10 Zeros of Functions An important part of the maths syllabus in secondary school is equation solving. This is important for the simple reason that equations are important a wide range of problems
Zeros of Functions. Chapter 10
 Chapter 10 Zeros of Functions An important part of the mathematics syllabus in secondary school is equation solving. This is important for the simple reason that equations are important a wide range of
Chapter 10 Zeros of Functions An important part of the mathematics syllabus in secondary school is equation solving. This is important for the simple reason that equations are important a wide range of
On Two Class-Constrained Versions of the Multiple Knapsack Problem
 On Two Class-Constrained Versions of the Multiple Knapsack Problem Hadas Shachnai Tami Tamir Department of Computer Science The Technion, Haifa 32000, Israel Abstract We study two variants of the classic
On Two Class-Constrained Versions of the Multiple Knapsack Problem Hadas Shachnai Tami Tamir Department of Computer Science The Technion, Haifa 32000, Israel Abstract We study two variants of the classic
Lecture 3 Sept. 4, 2014
 CS 395T: Sublinear Algorithms Fall 2014 Prof. Eric Price Lecture 3 Sept. 4, 2014 Scribe: Zhao Song In today s lecture, we will discuss the following problems: 1. Distinct elements 2. Turnstile model 3.
CS 395T: Sublinear Algorithms Fall 2014 Prof. Eric Price Lecture 3 Sept. 4, 2014 Scribe: Zhao Song In today s lecture, we will discuss the following problems: 1. Distinct elements 2. Turnstile model 3.
STAT 7032 Probability Spring Wlodek Bryc
 STAT 7032 Probability Spring 2018 Wlodek Bryc Created: Friday, Jan 2, 2014 Revised for Spring 2018 Printed: January 9, 2018 File: Grad-Prob-2018.TEX Department of Mathematical Sciences, University of Cincinnati,
STAT 7032 Probability Spring 2018 Wlodek Bryc Created: Friday, Jan 2, 2014 Revised for Spring 2018 Printed: January 9, 2018 File: Grad-Prob-2018.TEX Department of Mathematical Sciences, University of Cincinnati,
Ad Placement Strategies
 Case Study 1: Estimating Click Probabilities Tackling an Unknown Number of Features with Sketching Machine Learning for Big Data CSE547/STAT548, University of Washington Emily Fox 2014 Emily Fox January
Case Study 1: Estimating Click Probabilities Tackling an Unknown Number of Features with Sketching Machine Learning for Big Data CSE547/STAT548, University of Washington Emily Fox 2014 Emily Fox January
Cryptographic Hash Functions
 Cryptographic Hash Functions Çetin Kaya Koç koc@ece.orst.edu Electrical & Computer Engineering Oregon State University Corvallis, Oregon 97331 Technical Report December 9, 2002 Version 1.5 1 1 Introduction
Cryptographic Hash Functions Çetin Kaya Koç koc@ece.orst.edu Electrical & Computer Engineering Oregon State University Corvallis, Oregon 97331 Technical Report December 9, 2002 Version 1.5 1 1 Introduction
NUMERICAL AND STATISTICAL COMPUTING (MCA-202-CR)
 NUMERICAL AND STATISTICAL COMPUTING (MCA-202-CR) Autumn Session UNIT 1 Numerical analysis is the study of algorithms that uses, creates and implements algorithms for obtaining numerical solutions to problems
NUMERICAL AND STATISTICAL COMPUTING (MCA-202-CR) Autumn Session UNIT 1 Numerical analysis is the study of algorithms that uses, creates and implements algorithms for obtaining numerical solutions to problems
3. Algorithms. What matters? How fast do we solve the problem? How much computer resource do we need?
 3. Algorithms We will study algorithms to solve many different types of problems such as finding the largest of a sequence of numbers sorting a sequence of numbers finding the shortest path between two
3. Algorithms We will study algorithms to solve many different types of problems such as finding the largest of a sequence of numbers sorting a sequence of numbers finding the shortest path between two
StreamSVM Linear SVMs and Logistic Regression When Data Does Not Fit In Memory
 StreamSVM Linear SVMs and Logistic Regression When Data Does Not Fit In Memory S.V. N. (vishy) Vishwanathan Purdue University and Microsoft vishy@purdue.edu October 9, 2012 S.V. N. Vishwanathan (Purdue,
StreamSVM Linear SVMs and Logistic Regression When Data Does Not Fit In Memory S.V. N. (vishy) Vishwanathan Purdue University and Microsoft vishy@purdue.edu October 9, 2012 S.V. N. Vishwanathan (Purdue,
1. Method 1: bisection. The bisection methods starts from two points a 0 and b 0 such that
 Chapter 4 Nonlinear equations 4.1 Root finding Consider the problem of solving any nonlinear relation g(x) = h(x) in the real variable x. We rephrase this problem as one of finding the zero (root) of a
Chapter 4 Nonlinear equations 4.1 Root finding Consider the problem of solving any nonlinear relation g(x) = h(x) in the real variable x. We rephrase this problem as one of finding the zero (root) of a
Math 471 (Numerical methods) Chapter 3 (second half). System of equations
 Math 47 (Numerical methods) Chapter 3 (second half). System of equations Overlap 3.5 3.8 of Bradie 3.5 LU factorization w/o pivoting. Motivation: ( ) A I Gaussian Elimination (U L ) where U is upper triangular
Math 47 (Numerical methods) Chapter 3 (second half). System of equations Overlap 3.5 3.8 of Bradie 3.5 LU factorization w/o pivoting. Motivation: ( ) A I Gaussian Elimination (U L ) where U is upper triangular
1 What is numerical analysis and scientific computing?
 Mathematical preliminaries 1 What is numerical analysis and scientific computing? Numerical analysis is the study of algorithms that use numerical approximation (as opposed to general symbolic manipulations)
Mathematical preliminaries 1 What is numerical analysis and scientific computing? Numerical analysis is the study of algorithms that use numerical approximation (as opposed to general symbolic manipulations)
min f(x). (2.1) Objectives consisting of a smooth convex term plus a nonconvex regularization term;
 Chapter 2 Gradient Methods The gradient method forms the foundation of all of the schemes studied in this book. We will provide several complementary perspectives on this algorithm that highlight the many
Chapter 2 Gradient Methods The gradient method forms the foundation of all of the schemes studied in this book. We will provide several complementary perspectives on this algorithm that highlight the many
Remainders. We learned how to multiply and divide in elementary
 Remainders We learned how to multiply and divide in elementary school. As adults we perform division mostly by pressing the key on a calculator. This key supplies the quotient. In numerical analysis and
Remainders We learned how to multiply and divide in elementary school. As adults we perform division mostly by pressing the key on a calculator. This key supplies the quotient. In numerical analysis and
Randomized Algorithms
 Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Sequences and Series
 Sequences and Series What do you think of when you read the title of our next unit? In case your answers are leading us off track, let's review the following IB problems. 1 November 2013 HL 2 3 November
Sequences and Series What do you think of when you read the title of our next unit? In case your answers are leading us off track, let's review the following IB problems. 1 November 2013 HL 2 3 November
Algorithms 2/6/2018. Algorithms. Enough Mathematical Appetizers! Algorithm Examples. Algorithms. Algorithm Examples. Algorithm Examples
 Enough Mathematical Appetizers! Algorithms What is an algorithm? Let us look at something more interesting: Algorithms An algorithm is a finite set of precise instructions for performing a computation
Enough Mathematical Appetizers! Algorithms What is an algorithm? Let us look at something more interesting: Algorithms An algorithm is a finite set of precise instructions for performing a computation
14.1 Finding frequent elements in stream
 Chapter 14 Streaming Data Model 14.1 Finding frequent elements in stream A very useful statistics for many applications is to keep track of elements that occur more frequently. It can come in many flavours
Chapter 14 Streaming Data Model 14.1 Finding frequent elements in stream A very useful statistics for many applications is to keep track of elements that occur more frequently. It can come in many flavours
MATH 320, WEEK 11: Eigenvalues and Eigenvectors
 MATH 30, WEEK : Eigenvalues and Eigenvectors Eigenvalues and Eigenvectors We have learned about several vector spaces which naturally arise from matrix operations In particular, we have learned about the
MATH 30, WEEK : Eigenvalues and Eigenvectors Eigenvalues and Eigenvectors We have learned about several vector spaces which naturally arise from matrix operations In particular, we have learned about the
A Randomized Algorithm for the Approximation of Matrices
 A Randomized Algorithm for the Approximation of Matrices Per-Gunnar Martinsson, Vladimir Rokhlin, and Mark Tygert Technical Report YALEU/DCS/TR-36 June 29, 2006 Abstract Given an m n matrix A and a positive
A Randomized Algorithm for the Approximation of Matrices Per-Gunnar Martinsson, Vladimir Rokhlin, and Mark Tygert Technical Report YALEU/DCS/TR-36 June 29, 2006 Abstract Given an m n matrix A and a positive
Given a sequence a 1, a 2,...of numbers, the finite sum a 1 + a 2 + +a n,wheren is an nonnegative integer, can be written
 A Summations When an algorithm contains an iterative control construct such as a while or for loop, its running time can be expressed as the sum of the times spent on each execution of the body of the
A Summations When an algorithm contains an iterative control construct such as a while or for loop, its running time can be expressed as the sum of the times spent on each execution of the body of the
1 Maintaining a Dictionary
 15-451/651: Design & Analysis of Algorithms February 1, 2016 Lecture #7: Hashing last changed: January 29, 2016 Hashing is a great practical tool, with an interesting and subtle theory too. In addition
15-451/651: Design & Analysis of Algorithms February 1, 2016 Lecture #7: Hashing last changed: January 29, 2016 Hashing is a great practical tool, with an interesting and subtle theory too. In addition
5 + 9(10) + 3(100) + 0(1000) + 2(10000) =
 Chapter 5 Analyzing Algorithms So far we have been proving statements about databases, mathematics and arithmetic, or sequences of numbers. Though these types of statements are common in computer science,
Chapter 5 Analyzing Algorithms So far we have been proving statements about databases, mathematics and arithmetic, or sequences of numbers. Though these types of statements are common in computer science,
Lecture 8. Root finding II
 1 Introduction Lecture 8 Root finding II In the previous lecture we considered the bisection root-bracketing algorithm. It requires only that the function be continuous and that we have a root bracketed
1 Introduction Lecture 8 Root finding II In the previous lecture we considered the bisection root-bracketing algorithm. It requires only that the function be continuous and that we have a root bracketed
CS 450 Numerical Analysis. Chapter 5: Nonlinear Equations
 Lecture slides based on the textbook Scientific Computing: An Introductory Survey by Michael T. Heath, copyright c 2018 by the Society for Industrial and Applied Mathematics. http://www.siam.org/books/cl80
Lecture slides based on the textbook Scientific Computing: An Introductory Survey by Michael T. Heath, copyright c 2018 by the Society for Industrial and Applied Mathematics. http://www.siam.org/books/cl80
On the Partitioning of Servers in Queueing Systems during Rush Hour
 On the Partitioning of Servers in Queueing Systems during Rush Hour This paper is motivated by two phenomena observed in many queueing systems in practice. The first is the partitioning of server capacity
On the Partitioning of Servers in Queueing Systems during Rush Hour This paper is motivated by two phenomena observed in many queueing systems in practice. The first is the partitioning of server capacity
Problem 3. Give an example of a sequence of continuous functions on a compact domain converging pointwise but not uniformly to a continuous function
 Problem 3. Give an example of a sequence of continuous functions on a compact domain converging pointwise but not uniformly to a continuous function Solution. If we does not need the pointwise limit of
Problem 3. Give an example of a sequence of continuous functions on a compact domain converging pointwise but not uniformly to a continuous function Solution. If we does not need the pointwise limit of
Midterm Review. Igor Yanovsky (Math 151A TA)
 Midterm Review Igor Yanovsky (Math 5A TA) Root-Finding Methods Rootfinding methods are designed to find a zero of a function f, that is, to find a value of x such that f(x) =0 Bisection Method To apply
Midterm Review Igor Yanovsky (Math 5A TA) Root-Finding Methods Rootfinding methods are designed to find a zero of a function f, that is, to find a value of x such that f(x) =0 Bisection Method To apply
A Brief Introduction to Numerical Methods for Differential Equations
 A Brief Introduction to Numerical Methods for Differential Equations January 10, 2011 This tutorial introduces some basic numerical computation techniques that are useful for the simulation and analysis
A Brief Introduction to Numerical Methods for Differential Equations January 10, 2011 This tutorial introduces some basic numerical computation techniques that are useful for the simulation and analysis
Filters. Alden Walker Advisor: Miller Maley. May 23, 2007
 Filters Alden Walker Advisor: Miller Maley May 23, 2007 Contents 1 Introduction 4 1.1 Motivation..................................... 4 1.2 Mathematical Abstraction............................ 5 1.2.1
Filters Alden Walker Advisor: Miller Maley May 23, 2007 Contents 1 Introduction 4 1.1 Motivation..................................... 4 1.2 Mathematical Abstraction............................ 5 1.2.1
Linear Programming Redux
 Linear Programming Redux Jim Bremer May 12, 2008 The purpose of these notes is to review the basics of linear programming and the simplex method in a clear, concise, and comprehensive way. The book contains
Linear Programming Redux Jim Bremer May 12, 2008 The purpose of these notes is to review the basics of linear programming and the simplex method in a clear, concise, and comprehensive way. The book contains
Bloom Filters, general theory and variants
 Bloom Filters: general theory and variants G. Caravagna caravagn@cli.di.unipi.it Information Retrieval Wherever a list or set is used, and space is a consideration, a Bloom Filter should be considered.
Bloom Filters: general theory and variants G. Caravagna caravagn@cli.di.unipi.it Information Retrieval Wherever a list or set is used, and space is a consideration, a Bloom Filter should be considered.
CPSC 467: Cryptography and Computer Security
 CPSC 467: Cryptography and Computer Security Michael J. Fischer Lecture 9 September 30, 2015 CPSC 467, Lecture 9 1/47 Fast Exponentiation Algorithms Number Theory Needed for RSA Elementary Number Theory
CPSC 467: Cryptography and Computer Security Michael J. Fischer Lecture 9 September 30, 2015 CPSC 467, Lecture 9 1/47 Fast Exponentiation Algorithms Number Theory Needed for RSA Elementary Number Theory
DR.RUPNATHJI( DR.RUPAK NATH )
 Contents 1 Sets 1 2 The Real Numbers 9 3 Sequences 29 4 Series 59 5 Functions 81 6 Power Series 105 7 The elementary functions 111 Chapter 1 Sets It is very convenient to introduce some notation and terminology
Contents 1 Sets 1 2 The Real Numbers 9 3 Sequences 29 4 Series 59 5 Functions 81 6 Power Series 105 7 The elementary functions 111 Chapter 1 Sets It is very convenient to introduce some notation and terminology
Scientific Computing: An Introductory Survey
 Scientific Computing: An Introductory Survey Chapter 12 Prof. Michael T. Heath Department of Computer Science University of Illinois at Urbana-Champaign Copyright c 2002. Reproduction permitted for noncommercial,
Scientific Computing: An Introductory Survey Chapter 12 Prof. Michael T. Heath Department of Computer Science University of Illinois at Urbana-Champaign Copyright c 2002. Reproduction permitted for noncommercial,
Chapter 1 Statistical Inference
 Chapter 1 Statistical Inference causal inference To infer causality, you need a randomized experiment (or a huge observational study and lots of outside information). inference to populations Generalizations
Chapter 1 Statistical Inference causal inference To infer causality, you need a randomized experiment (or a huge observational study and lots of outside information). inference to populations Generalizations
CS246: Mining Massive Datasets Jure Leskovec, Stanford University
 CS246: Mining Massive Datasets Jure Leskovec, Stanford University http://cs246.stanford.edu 2/26/2013 Jure Leskovec, Stanford CS246: Mining Massive Datasets, http://cs246.stanford.edu 2 More algorithms
CS246: Mining Massive Datasets Jure Leskovec, Stanford University http://cs246.stanford.edu 2/26/2013 Jure Leskovec, Stanford CS246: Mining Massive Datasets, http://cs246.stanford.edu 2 More algorithms
A General-Purpose Counting Filter: Making Every Bit Count. Prashant Pandey, Michael A. Bender, Rob Johnson, Rob Patro Stony Brook University, NY
 A General-Purpose Counting Filter: Making Every Bit Count Prashant Pandey, Michael A. Bender, Rob Johnson, Rob Patro Stony Brook University, NY Approximate Membership Query (AMQ) insert(x) ismember(x)
A General-Purpose Counting Filter: Making Every Bit Count Prashant Pandey, Michael A. Bender, Rob Johnson, Rob Patro Stony Brook University, NY Approximate Membership Query (AMQ) insert(x) ismember(x)
What Every Programmer Should Know About Floating-Point Arithmetic DRAFT. Last updated: November 3, Abstract
 What Every Programmer Should Know About Floating-Point Arithmetic Last updated: November 3, 2014 Abstract The article provides simple answers to the common recurring questions of novice programmers about
What Every Programmer Should Know About Floating-Point Arithmetic Last updated: November 3, 2014 Abstract The article provides simple answers to the common recurring questions of novice programmers about
Lecture 1 : Data Compression and Entropy
 CPS290: Algorithmic Foundations of Data Science January 8, 207 Lecture : Data Compression and Entropy Lecturer: Kamesh Munagala Scribe: Kamesh Munagala In this lecture, we will study a simple model for
CPS290: Algorithmic Foundations of Data Science January 8, 207 Lecture : Data Compression and Entropy Lecturer: Kamesh Munagala Scribe: Kamesh Munagala In this lecture, we will study a simple model for
IN this paper, we consider the capacity of sticky channels, a
 72 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 1, JANUARY 2008 Capacity Bounds for Sticky Channels Michael Mitzenmacher, Member, IEEE Abstract The capacity of sticky channels, a subclass of insertion
72 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 1, JANUARY 2008 Capacity Bounds for Sticky Channels Michael Mitzenmacher, Member, IEEE Abstract The capacity of sticky channels, a subclass of insertion
Numerical Methods. King Saud University
 Numerical Methods King Saud University Aims In this lecture, we will... find the approximate solutions of derivative (first- and second-order) and antiderivative (definite integral only). Numerical Differentiation
Numerical Methods King Saud University Aims In this lecture, we will... find the approximate solutions of derivative (first- and second-order) and antiderivative (definite integral only). Numerical Differentiation
0. Introduction 1 0. INTRODUCTION
 0. Introduction 1 0. INTRODUCTION In a very rough sketch we explain what algebraic geometry is about and what it can be used for. We stress the many correlations with other fields of research, such as
0. Introduction 1 0. INTRODUCTION In a very rough sketch we explain what algebraic geometry is about and what it can be used for. We stress the many correlations with other fields of research, such as
An analogy from Calculus: limits
 COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
NUMERICAL METHODS. x n+1 = 2x n x 2 n. In particular: which of them gives faster convergence, and why? [Work to four decimal places.
 NUMERICAL METHODS 1. Rearranging the equation x 3 =.5 gives the iterative formula x n+1 = g(x n ), where g(x) = (2x 2 ) 1. (a) Starting with x = 1, compute the x n up to n = 6, and describe what is happening.
NUMERICAL METHODS 1. Rearranging the equation x 3 =.5 gives the iterative formula x n+1 = g(x n ), where g(x) = (2x 2 ) 1. (a) Starting with x = 1, compute the x n up to n = 6, and describe what is happening.
4 Nonlinear Equations
 4 Nonlinear Equations lecture 27: Introduction to Nonlinear Equations lecture 28: Bracketing Algorithms The solution of nonlinear equations has been a motivating challenge throughout the history of numerical
4 Nonlinear Equations lecture 27: Introduction to Nonlinear Equations lecture 28: Bracketing Algorithms The solution of nonlinear equations has been a motivating challenge throughout the history of numerical
Introduction to statistics
 Introduction to statistics Literature Raj Jain: The Art of Computer Systems Performance Analysis, John Wiley Schickinger, Steger: Diskrete Strukturen Band 2, Springer David Lilja: Measuring Computer Performance:
Introduction to statistics Literature Raj Jain: The Art of Computer Systems Performance Analysis, John Wiley Schickinger, Steger: Diskrete Strukturen Band 2, Springer David Lilja: Measuring Computer Performance:
Advanced topic: Space complexity
 Advanced topic: Space complexity CSCI 3130 Formal Languages and Automata Theory Siu On CHAN Chinese University of Hong Kong Fall 2016 1/28 Review: time complexity We have looked at how long it takes to
Advanced topic: Space complexity CSCI 3130 Formal Languages and Automata Theory Siu On CHAN Chinese University of Hong Kong Fall 2016 1/28 Review: time complexity We have looked at how long it takes to
Lecture 2. Frequency problems
 1 / 43 Lecture 2. Frequency problems Ricard Gavaldà MIRI Seminar on Data Streams, Spring 2015 Contents 2 / 43 1 Frequency problems in data streams 2 Approximating inner product 3 Computing frequency moments
1 / 43 Lecture 2. Frequency problems Ricard Gavaldà MIRI Seminar on Data Streams, Spring 2015 Contents 2 / 43 1 Frequency problems in data streams 2 Approximating inner product 3 Computing frequency moments
Gaussian and Linear Discriminant Analysis; Multiclass Classification
 Gaussian and Linear Discriminant Analysis; Multiclass Classification Professor Ameet Talwalkar Slide Credit: Professor Fei Sha Professor Ameet Talwalkar CS260 Machine Learning Algorithms October 13, 2015
Gaussian and Linear Discriminant Analysis; Multiclass Classification Professor Ameet Talwalkar Slide Credit: Professor Fei Sha Professor Ameet Talwalkar CS260 Machine Learning Algorithms October 13, 2015
DRAFT. Algebraic computation models. Chapter 14
 Chapter 14 Algebraic computation models Somewhat rough We think of numerical algorithms root-finding, gaussian elimination etc. as operating over R or C, even though the underlying representation of the
Chapter 14 Algebraic computation models Somewhat rough We think of numerical algorithms root-finding, gaussian elimination etc. as operating over R or C, even though the underlying representation of the
Elements of Floating-point Arithmetic
 Elements of Floating-point Arithmetic Sanzheng Qiao Department of Computing and Software McMaster University July, 2012 Outline 1 Floating-point Numbers Representations IEEE Floating-point Standards Underflow
Elements of Floating-point Arithmetic Sanzheng Qiao Department of Computing and Software McMaster University July, 2012 Outline 1 Floating-point Numbers Representations IEEE Floating-point Standards Underflow
Numerical Analysis Exam with Solutions
 Numerical Analysis Exam with Solutions Richard T. Bumby Fall 000 June 13, 001 You are expected to have books, notes and calculators available, but computers of telephones are not to be used during the
Numerical Analysis Exam with Solutions Richard T. Bumby Fall 000 June 13, 001 You are expected to have books, notes and calculators available, but computers of telephones are not to be used during the
Lecture 4: Training a Classifier
 Lecture 4: Training a Classifier Roger Grosse 1 Introduction Now that we ve defined what binary classification is, let s actually train a classifier. We ll approach this problem in much the same way as
Lecture 4: Training a Classifier Roger Grosse 1 Introduction Now that we ve defined what binary classification is, let s actually train a classifier. We ll approach this problem in much the same way as
arxiv: v1 [physics.comp-ph] 22 Jul 2010
![arxiv: v1 [physics.comp-ph] 22 Jul 2010 arxiv: v1 [physics.comp-ph] 22 Jul 2010](/thumbs/71/65800290.jpg) Gaussian integration with rescaling of abscissas and weights arxiv:007.38v [physics.comp-ph] 22 Jul 200 A. Odrzywolek M. Smoluchowski Institute of Physics, Jagiellonian University, Cracov, Poland Abstract
Gaussian integration with rescaling of abscissas and weights arxiv:007.38v [physics.comp-ph] 22 Jul 200 A. Odrzywolek M. Smoluchowski Institute of Physics, Jagiellonian University, Cracov, Poland Abstract
CS229 Supplemental Lecture notes
 CS229 Supplemental Lecture notes John Duchi 1 Boosting We have seen so far how to solve classification (and other) problems when we have a data representation already chosen. We now talk about a procedure,
CS229 Supplemental Lecture notes John Duchi 1 Boosting We have seen so far how to solve classification (and other) problems when we have a data representation already chosen. We now talk about a procedure,
Algebra Exam. Solutions and Grading Guide
 Algebra Exam Solutions and Grading Guide You should use this grading guide to carefully grade your own exam, trying to be as objective as possible about what score the TAs would give your responses. Full
Algebra Exam Solutions and Grading Guide You should use this grading guide to carefully grade your own exam, trying to be as objective as possible about what score the TAs would give your responses. Full
Average Case Complexity: Levin s Theory
 Chapter 15 Average Case Complexity: Levin s Theory 1 needs more work Our study of complexity - NP-completeness, #P-completeness etc. thus far only concerned worst-case complexity. However, algorithms designers
Chapter 15 Average Case Complexity: Levin s Theory 1 needs more work Our study of complexity - NP-completeness, #P-completeness etc. thus far only concerned worst-case complexity. However, algorithms designers
Numerical Methods - Preliminaries
 Numerical Methods - Preliminaries Y. K. Goh Universiti Tunku Abdul Rahman 2013 Y. K. Goh (UTAR) Numerical Methods - Preliminaries 2013 1 / 58 Table of Contents 1 Introduction to Numerical Methods Numerical
Numerical Methods - Preliminaries Y. K. Goh Universiti Tunku Abdul Rahman 2013 Y. K. Goh (UTAR) Numerical Methods - Preliminaries 2013 1 / 58 Table of Contents 1 Introduction to Numerical Methods Numerical
Notes on arithmetic. 1. Representation in base B
 Notes on arithmetic The Babylonians that is to say, the people that inhabited what is now southern Iraq for reasons not entirely clear to us, ued base 60 in scientific calculation. This offers us an excuse
Notes on arithmetic The Babylonians that is to say, the people that inhabited what is now southern Iraq for reasons not entirely clear to us, ued base 60 in scientific calculation. This offers us an excuse
Announcements. CompSci 102 Discrete Math for Computer Science. Chap. 3.1 Algorithms. Specifying Algorithms
 CompSci 102 Discrete Math for Computer Science Announcements Read for next time Chap. 3.1-3.3 Homework 3 due Tuesday We ll finish Chapter 2 first today February 7, 2012 Prof. Rodger Chap. 3.1 Algorithms
CompSci 102 Discrete Math for Computer Science Announcements Read for next time Chap. 3.1-3.3 Homework 3 due Tuesday We ll finish Chapter 2 first today February 7, 2012 Prof. Rodger Chap. 3.1 Algorithms
Analysis of Algorithm Efficiency. Dr. Yingwu Zhu
 Analysis of Algorithm Efficiency Dr. Yingwu Zhu Measure Algorithm Efficiency Time efficiency How fast the algorithm runs; amount of time required to accomplish the task Our focus! Space efficiency Amount
Analysis of Algorithm Efficiency Dr. Yingwu Zhu Measure Algorithm Efficiency Time efficiency How fast the algorithm runs; amount of time required to accomplish the task Our focus! Space efficiency Amount
