Quantization-Based Data-Hiding Robust to Linear Time-Invariant Filtering
|
|
|
- Madeleine Higgins
- 5 years ago
- Views:
Transcription
1 Quantization-Based Data-Hiding Robust to Linear Time-Invariant Filtering 1 Fernando Pérez-González and Carlos Mosquera Abstract Quantization-based methods, such as Dither Modulation (DM), have gained wide acceptance due to their host rejection capabilities which afford significant performance gains over spread-spectrum-based methods in additive white Gaussian channels. Unfortunately, existing quantization-based schemes are not robust against simple linear-time-invariant (LTI) filtering, which is a common operation with multimedia signals. We propose a new algorithm, named Discrete Fourier Transform Rational Dither Modulation (DFT-RDM) which is robust against LTI filtering and yet does not assume any prior knowledge of the filter at either the embedder or the detector. DFT-RDM basically combines a DFT operation with a quantization-based scheme robust to amplitude scaling. Two easily implementable improvements over the basic DFT-RDM are proposed: windowing and spreading. In particular, the latter leads to performance gains that are much larger than those achieved with spreading in regular DM. We also provide a thorough analysis of our scheme which leads to both accurate predictions and bounds on the per-dft-channel bit error rate, for the basic DFT-RDM and its combination with spreading and windowing. These tools let the designer choose the main embedding parameters without actually requiring any simulation. The results of several simulations for practical filters validating our analysis are presented as well. The benefits of combining DFT-RDM with windowing, spreading and Reed-Solomon channel coding are illustrated with an example. EDICS Category: WAT-BINM Dept. Teoría de la Señal y Comunicaciones, ETSI Telecom., Universidad de Vigo, Vigo, Spain Corresponding author. fperez@gts.tsc.uvigo.es. Tel: Fax: This work was partially funded by Xunta de Galicia under projects PGIDT04 TIC322013PR and PGIDT04 PXIC32202PM; MEC project DIPSTICK, reference TEC /TCM, and European Comission through the IST Programme under Contract IST ECRYPT. ECRYPT disclaimer: The information in this paper is provided as is, and no guarantee or warranty is given or implied that the information is fit for any particular purpose. The user thereof uses the information at its sole risk and liability.
2 2 I. INTRODUCTION Until very recently, one of the main drawbacks of quantization-based schemes, as opposed to spread-spectrum ones, was thought to be their fragility when subject to gain (also known as valumetric) attacks. Motivated by this problem, several researchers have proposed different ways of estimating this gain at the decoder, either by embedding an auxiliary pilot signal known to the decoder [1], or through blind estimation, [2], [3], that is, exploiting certain statistical properties of the received signal due to the periodic structure of the distribution of the watermarked signal amplitude. A different possibility consists in designing codes whose codewords are placed on a high-dimensional hypersphere as a way to achieve robustness to gain attacks [4], [5]. Another approach was taken in [6] to construct a simple, yet effective gain-invariant method which retains most desirable properties of Dither Modulation (DM), which in turn is the most popular algorithm in the family of side-informed ones. Such method is based on the use of a gain-invariant adaptive quantization step-size which is used by the embedder and which holds the advantageous feature of allowing its robust estimation at the decoder. This adaptive stepsize is constructed as a nonlinear function of past watermarked samples. The memory of such function, i.e., the number of past samples used at a certain instant to compute the step-size is a crucial design parameter: a small memory is useful when the target is to cope with varying gains; on the other hand, the larger this memory, the more robust the step-size estimation at the decoder, therefore improving performance. This new method, named Rational Dither Modulation (RDM), has been proven to asymptotically achieve the performance of DM. Full details on RDM and its performance can be found in [7]. Since its inception, several other works have shown the feasibility of combining RDM with channel coding [8] or source coding [9], applying RDM to image data hiding with Watson-like perceptual distances [10], and extending it to account for nonlinear distortions [11]. Under the premise that the gain attack can be considered somewhat solved, it is interesting to mention that there is a much less studied but almost as simple attack to quantization based schemes: linear time-invariant (LTI) filtering. LTI filtering is a recurrent operation with multimedia signals which in many instances can be considered as an unintentional attack. For instance, for audio signals equalization or certain audio effects, such as echo or phasers, well fit in this category. In image processing LTI filtering is also a common operation with applications including denoising, deblurring, interpolation or image enhancement. Unfortunately, existing side-informed methods have not been designed to survive such attacks, which therefore pose considerable concerns upon their alleged superiority over other alternatives such as spread spectrum. To see how devastating those attacks can be, consider the outcome of the following experiment on binary time-domain DM when the host signal is white with power 25 db above that of the watermark, and the watermarked signal is attacked by a lowpass filter of variable cutoff frequency. When this frequency is as high as 0.99π rad, the bit error rate (BER) is 0.5; when the cutoff frequency is 0.999π rad, the BER is still Note that given the tiny fraction of bandwidth that is thrown away in both cases, the attacked signals are very likely to go perceptually unnoticed. The reason for this failure lies in the distortion error due to filtering that moves the watermarked
3 3 signal away from the correct quantization centroids. This distortion error increases with the host signal power; in other words, for a fixed watermark power the larger the host power, the worse the performance. This is clearly in contrast to the performance of quantization-based schemes subject to additive white Gaussian noise (AWGN) attacks, where the host signal power is virtually irrelevant for most cases of practical interest. To the best of our knowledge the only other work dealing with linear filtering attacks is [12], which considers a two-band filter in which the high frequency band is amplitude-scaled. The approach taken there is to estimate the high-pass gain using the maximum likelihood criterion, which unfortunately demands a large number of samples in order to achieve an accurate enough estimate. Furthermore, the decoder is assumed to know the filter coefficients (save for the gain to be estimated), which may be not realistic in most practical cases. In this paper, we propose an extension of RDM that allows us to construct a high-rate scheme that is robust to LTI filtering attacks. Our solution does not assume any prior knowledge of the filter neither at the embedder nor at the decoder. The idea is to perform RDM over parallel channels in the DFT domain, taking advantage of the orthogonality of this transform and the fact that it converts a filtering operation in the time domain into an approximate multiplication on each channel. For this reason, the new scheme is termed DFT-RDM. As we will see, the inevitable distortions incurred during the filtering process cause the solution not to be truly LTI-filtering-invariant; however, by adequately choosing the different design parameters, it is possible to achieve any desired degree of resilience against this attack, at the expense of increased complexity or reduced payload. The remainder of the paper is organized as follows: the used notation and a review of RDM is given in Section II; Section III is devoted to discussing the consequences of filtering on conventional quantization-based methods. We present our new method in Section IV, and analyze its performance in Section V. Windowing and spreading are two mechanisms that considerably improve the performance of DFT-RDM; these are discussed in Section VI. Finally, Sections VII and VIII are devoted to presenting some experimental results and our final remarks, respectively. II. NOTATION AND REVIEW OF RDM For simplicity, we assume one-dimensional real-valued hosts arranged in a vector x; extension to the 2-D case is possible but it has not been pursued here. For convenience, and without loss of generality, we will regard the one-dimensional host as being given in the time-domain. Let x l denote the lth element of x. We will also use {x l } when referring to the sequence whose samples are x l. In data-hiding applications a message is embedded by modifying x to a vector y which we will call watermarked signal. The difference w y x is termed watermark. The lth elements of y and w are denoted by y l and w l, respectively. For analytical purposes, it will be convenient to model the different sequences involved in the embedding and
4 4 decoding operations as realizations of random processes. We will reserve uppercase letters to denote random variables and lowercase letters to denote specific values. Then, X l is a random variable modeling the lth sample of the host sequence, and {X l } is the random process modeling the whole sequence {x l }. In particular, throughout this paper we will assume that {X l } is a zero-mean white process with variance σ 2 x. The case of colored hosts can be taken into account in our analysis by combining the coloring filter with the attack filter. Boldface letters will be used to denote vectors: uppercase for random vectors, and lowercase for realizations. The vector containing the available samples at the decoder, also called observations throughout this paper, will be denoted by z. Those observations z l are obtained after passing the watermarked signal {y l } through the attack filter. As our proposed embedding and decoding schemes operates in the Discrete Fourier Transform (DFT) domain, we will use the tilde to express variables in such domain; for instance, Xm,k will denote the kth coefficient of the DFT of the mth block of {X l }. The superscript will be used to denote conjugate. We will also need to define the embedding distortion D w as the average power of the watermark, i.e., D w 1 M E [ Y X 2] = 1 M E [ W 2], where E[ ] denotes statistical expectation, stands for Euclidean (i.e., l 2 ) norm, and M is the length of W. The Document to Watermark Ratio (DWR), often expressed in decibels, is given by σ 2 x/d w. We will assume that this DWR is large, as it occurs in the vast majority of practical applications, due to perceptual reasons. Values larger than 20 db are customary. Although the procedures here described can be extended to the case of multilevel and lattice-block quantizers, the underlying principles of both RDM and DFT-RDM are fully illustrated by considering the simpler binary case (i.e., every embedding operation is meant to conceal one bit), to which our discussion will be confined. For further details on RDM the reader is referred to [7]. Let us start by recalling the basic principles of binary DM data-hiding. Define the shifted lattices Λ b 2 Z b /2, b = 1,1 (1) which describe the centroids for the respective quantizers Q 1 ( ) and Q 1 ( ), here assumed to be based on Euclidean distances. Given the kth information symbol b k { 1,1}, embedding in the kth sample is performed using the rule y k = Q bk (x k ). After observing the kth sample z k, the decoded binary symbol ˆb k is decided according to a minimum Euclidean distance rule ˆbk = arg min 1,1 z k Q bk (z k ) (2) which can be also seen to be equivalent to quantizing z k with a quantizer with step-size. On the other hand, RDM is based on the following embedding and decoding equations [7] ( ) xk y k = g(y k 1 )Q bk, (3) g(y k 1 ) ( ) ˆbk = arg min z k 1,1 g(z k 1 ) Q zk b k. (4) g(z k 1 )
5 5 where y k 1 (y k 1,y k 2,,y k L ) T, z k 1 (z k 1,z k 2,,z k L ) T, with L a designer parameter that determines the memory of the system. The function g : R L R is designed in such a way that g(ρy) = ρg(y), for any ρ > 0 and any y R L. One convenient choice for the g function is any of the Hölder or l p vector-norms: ( ) k 1 1/p 1 g(y k 1 ) = y m p, p 1. (5) L m=k L Knowing that best performance is obtained when tuning the p parameter to the shape parameter of the host distribution (when X follows a Generalized Gaussian) [7], we will assume from now on p = 2, which suits a Gaussian host distribution and leads to simplified expressions. To understand why RDM is gain-invariant, let us consider a fixed amplitude scaling attack with no noise; hence, the observed vector z becomes z = ρy, with ρ the channel gain unknown to both embedder and detector. Then, substituting z k = ρy k into (4) and taking into account the fact that g(z k 1 ) = ρg(y k 1 ), it is immediate to see that the ρ in the numerator and the denominator cancel out and the decision ˆb k is identical, irrespective of the value of ρ. III. LTI-FILTERING ATTACKS In the remainder of this paper we will consider attacks of the type z l = y l h l, where denotes convolution and h l is the impulse response of a real-valued LTI filter. We will assume that the cursor of the filter (i.e., the largest magnitude coefficient) is located at the origin to facilitate the analysis. Note that in practice this requires that some synchronization measures are effected to align the watermarked signal and the observations. Also note that in the considered model there is no explicit noise component; this is because the filtered-host interference (FHI) will be the dominant impairment. However, in the event such noise were present, it could be easily incorporated in the subsequent developments. To quantify this FHI, suppose that DM is used to hide one bit per sample applying the rule given above. The observed sequence can be written in a way that makes explicit the influence over the desired informationconveying sample y l zl = yl hl = h 0 yl + i 0 h i y l i h 0 y l + i 0 h i x l i (6) where the given approximation follows from the large DWR assumption. The second term in the right hand side of (6) corresponds to the FHI. For i.i.d. zero-mean Gaussian hosts, this FHI will be also zero-mean Gaussian, independent of x l and with variance σf 2 given by σf 2 = σ2 x h l 2 = σ2 x 2π l 0 π π h 0 H(e jω ) 2 dω, (7) where H(e jω ) denotes the Fourier Transform of h l. Now, assuming that h 0 = 1, it is possible to directly apply the results in [13] to derive the bit error probability for DM under LTI attacks: ( ) { ( ) ( )} (4k + 1) (4k + 3) P e,dm = 2 Q Q σ f 2σ f 2σ f k=0 (8)
6 6 with Q(x) 1 2π x e τ2 /2 dτ. (See also [13] for several useful approximations to the above equation.) In any case, it is worth noting that while for large DWRs the performance of DM in an AWGN channel is solely governed by the so-called Watermark to Noise Ratio (WNR), here the role of the noise is played by the FHI, so performance will depend in exactly the same way on the Watermark to Interference Ratio (WIR), defined as WIR D w /σf 2. The problem is that the WIR is inversely proportional to the DWR, so if the DWR is increased in, say, 10 db, so as to make the watermark less perceptible, the WIR will be correspondingly decreased in 10 db. This reveals the strong dependence of the performance of DM upon the operating DWR, which typically imposes hard-to-meet constraints, as illustrated by the following example. Example 1: From (8) it is immediate to calculate that a WIR of 10 db will guarantee a bit error probability of , which may be reasonable for many applications. Suppose that h l is an ideal low-pass filter with cutoff frequency ω = ω c and such that h 0 = 1. Then, from (7) we have π σf 2 = σ2 ( x dω = σx 2 1 ω ) c π ω c π From here, it is possible to calculate, for a given DWR, the cutoff frequency that yields a WIR of 10 db. For instance, when DWR=25 db, we have that ω c = π( ) rad, while for DWR=15 db, ω c = π( ) rad. Observe how narrow the stop-band is for both cases. It is also important to remark that if h 0 1 then, besides the FHI problem, DM would be facing a scaling attack which, as we have noted above, is not able to cope with in an effective manner. Even though this problem can be overcome by using RDM, the existing FHI would still render quite a poor performance. A possible countermeasure, proposed in [12] is to invert (equalize) the filtering operation; this of course requires accurately estimating the filter response which in turn needs either transmitting pilot signals or dealing with a very large number of samples at the decoder. Hence, this approach seems only feasible for relatively simple filters and for a decoder with prior knowledge of the attack subbands, as is the case for the two-band filter addressed in [12]. Another potential solution would be to spectrally shape (predistort) the watermark in such a way that the filtering takes no effect on it, but this clearly presumes too much knowledge about the attack at the embedder, and so it is feasible only for a very limited set of unintentional attacks. In the next section we discuss a third possibility that consists in applying RDM in the Discrete Fourier Transform (DFT) domain. (9) IV. DISCRETE FOURIER TRANSFORM RDM The key idea for constructing a quantization-based data-hiding scheme robust to LTI filtering is the gaininvariance property of standard RDM and the convolution theorem [14] that allows to write the output of the filter as a multiplication in the Fourier domain, i.e., Z(e jω ) = Y (e jω )H(e jω ). Hence, in principle, linear filtering can be addressed by applying RDM in the Fourier domain. The problem with this approach is that
7 7 x l S/P x m,0 y m,0 N-point DFT x exp( j ) m, k, + RDM select embed coeffs x m y, N / 2 mn b m, k y m k, /2 Duplicate coeffs + N-point IDFT P/S yl Fig. 1. Embedding in DFT-RDM, detailing the operation in the kth channel. it requires to work with the full sequences, which makes it impractical due to both computational complexity reasons and the fact that RDM requires a vector of past samples to build up the argument of its g function. This suggests operating in a block-by-block basis and approximating the Fourier transform by means of the DFT. Unfortunately, it is not possible to write the effect of the filter on each DFT coefficient as purely multiplicative, as RDM would require. This is a consequence of the fact that exact multiplications in the DFT domain would only be achieved with circular convolutions, while the filter performs ordinary convolutions. We remark that there exist two techniques that can be used to convert ordinary convolutions into circular ones: zero padding and cyclic prefixing [15]. In the first case, blocks are zero-padded so that after filtering block overlaps are avoided; in the second case, blocks are prefixed with a copy of their tail samples so that the result of the ordinary convolution coincides with that of the periodic convolution for the desired samples. However, none of these techniques can be used for the problem at hand because they would entail a significant distortion of the host. Accepting that exact multiplications cannot be achieved, we will proceed by analyzing the errors due to the DFT implementation. As we will see in Section V, by increasing the DFT size (thus approaching the Fourier transform) the errors can be driven to any desired level. This can be further improved by using windows to smooth block boundaries and by spreading, both to be discussed in Section VI. Some additional notation is required to describe the operation in the DFT domain. We will consider a nonoverlapping block-wise operation, with block-size N. Let x m denote the mth block of N samples of the host signal, then x m,k will denote the kth coefficient of the length-n DFT of such block, i.e., x m,k N 1 l=0 x m,l e j(2π/n)lk = mn+n 1 l=mn x l e j(2π/n)lk (10) Even though in principle it would be possible to independently watermark the real and the imaginary parts of every DFT coefficient, a problem arises when multiplying such coefficient by a complex factor (as it turns out to be the case for most filters) because both parts mix in a way that depends on the phase of that complex
8 8 z m,0 N-point z DFT j y l S/P l H( e ) +, select coeffs z m k z m, N / 2 RDM decod RDM decod RDM decod bˆm,0 bˆm, k bˆm, N /2 Fig. 2. Decoding in DFT-RDM factor. For this reason, it is preferable to watermark only the magnitude of each DFT coefficient. 1 Then, for the DFT-domain implementation of RDM (DFT-RDM in the sequel), the modulus of the kth coefficient of the mth block of the watermarked signal, ỹ m,k, is obtained as ( ) xm,k ỹ m,k = g(ỹ m 1,k )Q bm,k, (11) g(ỹ m 1,k ) where b m,k denotes the mth (m > 0) symbol sent through the kth channel (0 k N/2), see Figure 1, and the function g( ), defined in (5), operates on vector ỹ m 1,k (ỹ m 1,k,ỹ m 2,k,,ỹ m L,k ) T. Thus, the proposed scheme essentially constructs an RDM-like scheme for each DFT channel. The phase of ỹ m,k is simply set to that of x m,k to minimize the embedding distortion. This in turn implies that the watermark w m,k is collinear with x m,k. The remaining watermarked samples ỹ m,k, N/2 + 1 < k < N 1, are chosen to preserve the symmetry in such a way that the resulting sequence in the time domain {y k } is real. This is accomplished by making ỹ m,k = ỹ m,n k. The time-domain watermarked sequence {y l } is obtained as the inverse DFT (IDFT) of the watermarked DFT coefficients in a non-overlapping block-by-block basis: y l = 1 N N 1 k=0 ỹ m,k e j(2π/n)lk, mn l mn + N 1 (12) On the other hand, given the kth coefficient of the mth block of the observed signal z m,k, decoding uses the same rule as RDM in (4) with z m,k being the input to the decoder, see Figure 2. The proposed scheme allows to transmit N/2 + 1 bits per DFT-block of size N, so without further channel coding it achieves an approximate rate of 1/2 bits per host sample, that is, half of that attainable with time-domain binary RDM. This is the price to be paid for watermarking only the magnitude in the DFT domain. It is interesting to point out one important implementation issue due to embedding in just the magnitude of the DFT coefficients. For purposes of discussion only, assume that symbol b m,k is embedded in a DFT 1 An extended version of RDM working with complex samples can also be devised, using both magnitude and phase for information embedding and achieving tolerance to complex channel gains. However, the use of the phase for embedding purposes is not advisable (not even in differential form) because for small magnitude values of the host there is a large concentration of codewords near the origin of the complex plane which would be very sensitive to noise.
9 9 coefficient x m,k such that x m,k = /2, and that g(ỹ m 1,k ) = 1. Then, if the centroids in each DFT channel are given by the shifted lattices in (1), it is easy to verify that no matter which value b m,k takes, ỹ m,k will always become /2, and, of course, a bit error will occur with probability 1/2. This defect can be attributed to the phase-preserving operation, since it does not allow for sign changes, as standard dither modulation requires. One simple solution is to admit changes of π radians on the phase of x m,k ; however, for certain signals, such as audio, these phase changes may produce annoying clicking artifacts. For this reason, we have chosen a different alternative that for large DWRs yields exactly the same performance and which consists in employing the following centroids Λ b 2 Z + (1 b) /2, b = 1,1, that is, a /2 shift of the sets described by (1). It is straightforward to check that with this definition, sign changes never occur. To get some intuition on the robustness of DFT-RDM to LTI filtering attacks, given by their frequency response H(e jω ), note that if N is sufficiently large (so that the the filter response can be considered flat where the DFT window has significant spectral contents), then z m,k h k ỹ m,k, with h k = H(e j2πk/n ). On the other hand, g( z m 1,k ) = g( h k ỹ m 1,k ) = h k g(ỹ m 1,k ), where the last equality follows from the properties of the function g. From here, one can easily conclude the robustness of the proposed method against LTI filtering attacks. Note that this approximation is better for larger values of N and for smoother frequency responses of the LTI filter. In [7] it is shown that if a large DWR is assumed, leading to the host having an almost flat pdf within each quantization bin, for p = 2 in the g function, the DWR of time-domain RDM can be well approximated by 3/ 2 RDM, with RDM the quantization step. Thanks to the orthogonality of the DFT it is easy to conclude that an identical relation holds in the DFT-domain. This means that by using the same quantization step in each DFT channel as for the standard time-domain RDM an identical DWR is achieved. Hence, given a desired DWR, we can find the corresponding quantization step DFT-RDM to be used in every DFT channel as 3 DFT-RDM = (13) DWR DFT-RDM Finally, for the performance analysis of DFT-RDM, we will later need to use the following expression for the variance of the host DFT coefficients which easily follows from (10) Var[ X m,k ] = NVar[X m,l ] = Nσ 2 x. (14) V. PERFORMANCE ANALYSIS The performance of DFT-RDM will be measured by the bit error probability. In general, this probability will be different for each DFT channel, being of prime importance to derive analytical approximations as well as manageable bounds to such probabilities. As one would expect, performance will strongly depend on the filter h l ; our next task is to determine in which way.
10 10 A. Problem Formulation Recalling that when the DFT size is large enough we can approximate the kth DFT channel at the output of the attack filter as a multiplication by the kth DFT coefficient of the filter, h k, we will start by writing the random variable representing the observed signal in the DFT-domain Z m,k as Z m,k = h k ( X m,k + W m,k +Ñm,k), where Ñ m,k is a zero-mean complex Gaussian random variable independent of both X m,k and W m,k. The rationale for this model comes from the proposition proven in Appendix I, which states that when H(z) is an FIR filter with no zeros on the unit circle, independence is achieved for all k {0,1,,N 1} asymptotically as N. The term Ñm,k, which will be referred to as per-channel multiplication error, is due to the unavoidable use of ordinary convolutions with the filter impulse response instead of circular convolutions, and thus it is null for unit sample filters, i.e., h l = Kδ l, with K R, and δ l the Kronecker delta function. Let φ l,k denote the impulse response of the kth DFT basis function, i.e., φ l,k exp( j(2π/n)lk), for l,k = 0, N 1, and is zero otherwise. Recalling the filter-bank interpretation of the DFT [14], it is possible to write Z m,k = Z l φ l,k l=mn+n 1 = (X l + W l ) h l φ l,k l=mn+n 1 (15) On the other hand, we have Z m,k = h k ( X m,k + W m,k + Ñm,k) = h k (X l + W l ) φ l,k l=mn+n 1 + h k Ñ m,k (16) Combining (15) and (16) we find that the interference term can be expressed as where f l,k is given by Ñ m,k = (X l + W l ) f l,k l=mn+n 1 X l f l,k l=mn+n 1 (17) f l,k (h l / h k δ l ) φ l,k, k = 0,,N 1. (18) The approximation on the right hand side of (17) is a direct consequence of our assumption of a large DWR. Now, as the process {X l f l,k } is stationary, 2 it is immediate to conclude that the per-channel multiplication error Ñm,k will approximately have zero-mean and variance σx 2 l f l,k 2. Now it becomes necessary to analyze the effect of Ñm,k at each frequency k, keeping in mind that the phase is not used in the embedding scheme (11). This is addressed next. B. Bit error probability As the decisions at the decoder are based on the magnitude of Z m,k, the performance analysis can be based on real quantities. This is formally proved in Appendix II, where the random variables included in the equivalent 2 Note that, in strict sense, the process {(X l +W l ) f l,k } is not stationary but only asymptotically stationary as l [7]. However, the large DWR assumption implies that such process is almost stationary because its statistics are dominated by those of {X l f l,k }.
11 11 Fig. 3. Equivalent model for communication over the kth channel in DFT-RDM. {ÑR m,k} corresponds to real white noise. model depicted in Figure 3 are characterized: X m,k is the rotation of X m,k such that it becomes real-valued; {ÑR m,k } is a white noise real process uncorrelated with X m,k, and Z m,k is a process producing the same decoder output as Z m,k. The pdf of ÑR m,k is shown in Appendix II to be fñ R Θ(ñR m,k θ) = N(0,σ2 (θ)) (19) m,k Ñ,k where σñ,k (θ) σ 2 1,k cos2 θ + σ 2 2,k sin2 θ (20) with the random variable Θ U[0,2π), and where σ 2 1,k and σ2 2,k are given in Appendix II as functions of σ2 x and f l,k in (18). Unfortunately, the marginal pdf fñ R (ñ R m,k ) cannot be obtained in closed-form, so one has to m,k keep the auxiliary random variable Θ. In essence, for each Θ = θ we have a classical RDM problem, in which the gain h k in Figure 3 is compensated for by RDM operation, and the noise for each Θ = θ is zero-mean Gaussian. Then, for each Θ = θ, we can resort to the results in [7] to predict the bit error probability. Here we focus in the case were the memory L of the g function is large, but the methodology can be extended to any other values of L by rescuing the appropriate results from [7]. Thus, if P e,k (θ) denotes the bit error probability in the kth channel of DFT-RDM for Θ = θ, we have ( ( P e,k (θ) = f g(z (s)p DFT-RDM Nσx s k) e,dm )ds P e,rdm L, ) DFT-RDM Nσx σñ,k (θ) σñ,k (θ) where [7] 0 f g(z k) (s) 2s 2πσr exp ( (s2 1) 2 2σ 2 r (21) ), s 0. (22) with σ r 2/L. Interestingly, when L, we have that f g(z (s) δ(s 1), and P k) e,k(θ) ) P e,dm ( DFT-RDM Nσx /σñ,k (θ). In arriving at (21) we have used (14) to substitute the host variance in the DFT domain. Finally, the bit error probability in the kth channel of DFT-RDM can be obtained by averaging P e,k (θ) with respect to θ, i.e., P e,k = 1 π P e,k (θ)dθ. (23) 2π π
12 12 As we will confirm in the experimental section, the procedure just given predicts very accurately the actual probability of error; however, from the designer point of view it is desirable to have simpler expressions available. We derive next upper and lower bounds on such probability, which being easier to compute, are only 3 db apart (as measured by the effective signal to noise ratio) when the memory of the g function is such that L. C. Upper bound on the bit error probability For obtaining an upper bound, we will make use of the following Theorem. Theorem 1: The function ϕ : R + [0,1/2) defined as { ( 4k + 1 ϕ(x) = 2 Q 2 x k=0 increases monotonically. Moreover, it is convex for x 1/12. ) Q ( )} 4k x (24) The proof is given in Appendix III. Note that P e,dm (1/x) = ϕ(x 2 ), so the above theorem is useful in handling expressions involving P e,dm for a wide range of noise variances. As a consequence of Theorem 1, the error probability of DM monotonically increases with the noise variance. 3 Simple and meaningful bounds result when considering the total variance of the per-channel multiplication error. This variance, which we will denote by σk 2, can be obtained as σk 2 = σ2 1,k + σ2 2,k σ2 x f l,k 2 (25) by using the corresponding expressions in Appendix II. The variance of Ñ R m,k straightforwardly bounded as σ 2 Ñ,k (θ) σ2 k 0 l conditioned on Θ = θ can be for all θ [0,2π). Then, from Theorem 1 and Eqs. (21) and (23) we can write the following upper bound ( ( P e,k f g(z (s)p DFT-RDM Nσx s k) e,dm )ds = P e,rdm σ L, ) DFT-RDM Nσx k σ k (26) D. Lower bound on the bit error probability In order to get a lower bound, first note that P e,rdm (x) P e,dm (x), for all x R + [7]. Hence, [ ( P e,k = E Θ P e,rdm L, )] ( )] DFT-RDMσ x N DFT-RDM σ x N E Θ [P e,dm σñ,k (Θ) σñ,k (Θ) (27) where expectation is taken with respect to Θ. Now, if DFT-RDM σ x N/σÑ,k (θ) 12 for all θ [0,2π) we can apply Theorem 1 to show that P e,dm in (27) is a convex function of σ 2 Ñ,k (θ). Recalling that σ Ñ,k (θ) < σ k 3 Note that, even though intuitively plausible, to the best of our knowledge this important result is formally proven here for the first time.
13 13 for all θ [0,2π), a sufficient condition for convexity is that DFT-RDM σ x N/σk 12. Now, using (20) we can write E Θ [σ 2 Ñ,k (Θ)] = 1 π σ 2 2π Ñ,k (θ)dθ = σ2 1,k + σ2 2,k π 2 With this result, and the convexity of P e,dm, we can apply Jensen s inequality, and arrive at P e,k P e,dm ( ) DFT-RDMσ x N 2 DFT-RDM σ x N DFT-RDM σ x N EΘ [σ 2Ñ,k (Θ)] = P e,dm, 12, (29) σ k σ k From the performance plot of DM in [7] we can readily see that for the range of validity of Eq. (29) P e,dm < , so at least for probabilities smaller than , it is guaranteed that the right hand side of Eq. (29) acts as a lower bound on P e,k. As we will later confirm, in practice this range is about one order of magnitude larger. A further comment concerns the performance in the asymptotic scenario where the memory of the function g is such that L. As proven in [7], in this case P e,rdm P e,dm, so the lower bound in (26) and the upper bound in (29) only differ by a factor of 2 in the arguments of P e,dm. Alternatively, one may think that the proposed bounds are 3 db apart as measured by their effective signal to noise ratio in the asymptotic case. In interpreting the bounds in both (26) and (29) it is interesting to point out that, while the variance σ 2 k of the per-channel multiplication error is approximately constant with N (for k such that ω 0 = k/n is constant), the variance of the host in the DFT domain increases with N (see Eq. (14)). This is apparent in the numerator of both (26) and (29), meaning that the effective SNR approximately grows as N with the DFT size. On the other hand, a large value of N not only implies a larger computational load but also makes DFT-RDM more sensitive to time-varying filters. = σ2 k 2 (28) VI. IMPROVEMENTS In this section we propose two improvements to the basic DFT-RDM that allow the designer to tradeoff performance against peak-distortion and payload by means of windowing and spreading, respectively. A. Windowing Here we concentrate on ways to reduce the variance σk 2 of the per-channel multiplication errors. A valuable explanation arises from applying Parseval s relation to the expression of σ 2 k Transform of f l,k in (18), which yields σ 2 k = σ2 x π π Φ0 (e jω ) 2 1 H(ej(ω+2πk/N) ) H(e j2πk/n ) 2 in (25), and taking the Fourier dω (30) where Φ 0 (e jω ) is the Fourier Transform of the rectangular window, so that Φ 0 (e jω ) 2 has a squared-sinc aspect. This squared-sinc function weights the error due to the unevenness of the frequency response of the LTI filter. Observe that for a flat frequency response of H(e jω ), the error variance in (30) is null. This fact points at the
14 14 advantages of equalizing the channel response at the decoder s front end, which requires that the frequency response of the LTI filter be properly estimated. From (30) it is possible to see that if the frequency response of the filter is sufficiently smooth so as to consider it approximately constant within the main lobe of the weighting function, then reducing the energy of the sidelobes will be advantageous. In the following we show how to apply such window and which modifications should be made to the developments presented thus far to take windowing into account. Let v = (v 0,v 1,,v N 1 ) T be the window, where N is the DFT size. For reasons that will become apparent shortly, we will constrain v to the class of windows for which (v l ) 1 exists for all l = 0,,N 1. Note that this rules out some popular windows such as Hanning, Blackman or Bartlett, which are null at the borders. Embedding now operates on the windowed host signal x m,k = N 1 l=0 v l x m,l e j(2π/n)lk = mn+n 1 l=mn v l mn x l e j(2π/n)lk (31) and proceeds in the same way as in Section IV to produce a set of watermarked blocks in the DFT domain. Now, given the mth block of the watermarked signal ỹ m,k, the time domain samples are obtained as y l = v (i) N 1 1 l mn ỹ m,k e j(2π/n)lk, mn l mn + N 1 (32) N k=0 where v (i) = (v (i) 0,v(i) 1,,v(i) N 1 )T, with v (i) l (v l ) 1, for all l = 0,,N 1. The reason for postmultiplying by the inverse window in (32) can be easily understood by considering the case where the DWR is infinite (i.e., = 0) because here, combining (32) and (31), one obtains y l = x l, as desired. At the receiver, the decoding rule in (4) is applied to the mth block of the observed signal in the DFT domain z m,k, which is computed in the same way as x m,k in (31), that is, applying the DFT to the mth windowed block of z l. Throughout this section we will use the subscript WDFT-RDM to refer to windowed DFT-RDM. Let us determine the step-size WDFT-RDM for a desired DWR. It is important to remark that the reasoning leading to (13) cannot be directly applied here because windowing and inverse windowing results in a nonorthogonal transform. Under the assumption of a white Gaussian host signal with variance σx 2, the variance of the DFT coefficients X m,k becomes Var[ X m,k ] = v 2 σ 2 x (33) Note that (14) is a particular case of (33) with v = 1. For assessing the embedding distortion, notice that while the watermark coefficients in the DFT domain will be identically distributed, the post-multiplication by v (i) in the time domain renders the watermark non-stationary, but cyclostationary with period N (provided that steady-state has been reached in RDM operation). Then, the embedding distortion must be calculated by averaging the watermark energy over one period. This results in [ ] v (i) 2 Var Wm,k D w,wdft-rdm = N 2 (34)
15 15 Following the same procedure as in Section IV and employing (33) and (34) we obtain the following relation between the DWR and WDFT-RDM DWR WDFT-RDM = σ 2 x D w,wdft-rdm = 3N 2 2 WDFT-RDM v 2 v (i) 2 (35) Again, note that (13) directly derives from (35) when v = v (i) = 1. Also, as a consequence of the Cauchy- Schwarz inequality, v 2 v (i) 2 N 2, so for the same target DWR, WDFT-RDM DFT-RDM, with equality if and only if v is a rectangular window. The performance analysis in Section V can be easily extended to the case of windowing. The impulse response of the kth DFT analysis filter is now given by φ l,k = v l exp( j(2π/n)lk), for l = 0,,N 1, and, in consequence, the variance σk 2 of the per-channel multiplication error (30) is now rewritten as π σk 2 = σ2 x V (e jω ) 2 1 H(ej(ω+2πk/N) ) 2 H(e j2πk/n dω (36) ) π being V (e jω ) the Fourier Transform of the window v. In addition to the modified variance σk 2, now the corresponding bounds for the probability of error of each channel include also the norm of the window: ( ) ( 2 WDFT-RDM σ x v P e,dm < P e,k < P e,rdm L, ) WDFT-RDMσ x v σ k σ k Noticing the influence of the window in both (35) and (37), it is natural to consider the problem of designing a window such that the bit error probability is minimized. We address this problem next. From the bounds in (37) it follows that the performance is determined by the ratio WDFT-RDM σ x v /σ k : its maximization, for a given distortion (35), is expected to help decreasing the probability of error P e,k. It can be readily seen that this criterion is equivalent to the minimization of the cost function J(v,k) = v (i) 2 σ 2 k = σ 2 x H(e j2πk/n ) 2 v(i) 2 π π V (e jω ) 2 H(e j2πk/n ) H(e j(ω+2πk/n) ) 2 dω It can be anticipated that the optimal window will depend upon the specific filter, in a way determined by the overall cost function, i.e., on how the partial costs J(v,k), k = 0,,N 1 are combined. We could have chosen to minimize the sum of J(v,k) for all k, minimize the maximum value, or minimize any other meaningful function of the cost for the different DFT channels. However, in view of the fact that in most practical cases the embedder does not know the attack filter, we deem it more appropriate to make some approximations directed to pose an optimization problem independent of the filter. It is clear from (38) that, as expected, the window must have a low-pass shape, given that for higher ω, the term H(e j2πk/n ) H(e j(ω+2πk/n) ) 2 will likely take higher values. We will use this fact in the sequel. Let us consider an arbitrary filter frequency response, not necessarily causal, for a time response of 2P + 1 coefficients: H(e jω ) = P l= P (37) (38) h l e jωl (39)
16 16 The integral term in the cost function (38) can be written, once the filter frequency response is included, as π π V (e jω ) 2 P = π π l= P 2πk j h l e l N V (e jω ) 2 P P l= P l= P P l= P 2πk 2 j h l e l N e jωl dω (40) ( 2 2πk j h l e l N 1 e jωl) dω (41) 2πk 2 π j lh l e l N V (e jω ) 2 ω 2 dω (42) π where the approximation is based on the fact that for small values of ω and l, (1 e jωl ) jωl. This approximation makes sense because first, as explained above, the window frequency contents will be concentrated in low frequencies, i.e., small values of ω, and second, assuming the cursor is located at l = 0, most practical filters h l will have their most significant coefficients near the origin, i.e., for small values of l. In any case, we must stress that despite the coarseness of (42), it has the great advantage of decoupling the design of the window from the filter and still furnishes remarkable improvements, as we will confirm in the experimental section. The cost function J(v,k) can be approximated now as J(v,k) σx 2 H (e j2πk/n ) 2 H(e j2πk/n ) 2 v(i) 2 π π V (e jω ) 2 ω 2 dω (43) where H (e jω ) denotes the derivative of H(e jω ) with respect to the frequency ω. The first order approximation that we have used displays a dependence of the probability of error with the first derivative of the filter frequency response. A more accurate approximation would show more derivatives. Equation (43) gives also a useful qualitative intuition regarding the influence of the attack filter on the performance: a higher P e,k will originate from those DFT channels with low spectral contents or large spectral variation. Thus, the design of the window has been decoupled of the filter, and can be stated as π v = arg min v v(i) 2 V (e jω ) 2 ω 2 dω (44) π This is a multivariable nonlinear optimization problem, which must be solved with numerical methods. 4 (We used the fmincon function from the MATLAB optimization toolbox.) In the results presented in Section VII the designed window will be used to show the performance improvement with respect to the use of conventional windows. The improvement due to windowing comes at the price of an increased peak-to-average distortion which is more apparent at block borders. On the other hand, the peak embedding distortion can be easily incorporated as a constraint into the window design process, as we will duly show in Section VII. 4 The problem can also be rephrased as a quadratic optimization problem with nonlinear constraints, equally needing a numerical optimization algorithm.
17 17 B. Spreading From the performance analysis in Section V it is apparent that increasing the size of the DFT entails a gain in the effective SNR which is proportional to that size. Unfortunately, from an implementation perspective, increasing the DFT size implies a large computational burden, even if Fast Fourier Transforms (FFT) algorithms are employed. There is however a well-known simple technique with a small computational complexity that allows to calculate only N evenly spaced coefficients out of a DFT of size M N. This technique amounts to adding (i.e., aliasing) M length-n signal blocks in the time-domain and then computing the size-n DFT [14]. The obvious drawback of this approach is that we reduce the payload by a factor of M, as we are collapsing M blocks down to a single one. Assuming that no windowing (or better to say, that a rectangular windowing) is applied, the km th coefficient of the pth block of the length-nm DFT of the host signal is now obtained as N 1 pm+m 1 N 1 pm+m 1 x p,km = e j(2π/n)lk = e j(2π/n)lk, k = 0,,N 1 (45) l=0 m=pm x m,l l=0 m=pm x mn+l where the parentheses have been inserted to stress the fact that the aliasing stage should be applied first to reduce the required number of arithmetic operations. In order to perform the embedding a slight modification to the block-diagram of Section IV is necessary to cope with the contingency that the pth watermarked block in the DFT domain only consists of the N samples ỹ p,km, which correspond to M N time-domain samples. Surely, the aliasing operation cannot be losslessly reverted, but we are only interested in a watermark such that the desired result is achieved when aliasing is performed again at the receiver. Then, as w p,km = ỹ p,km x p,km, the time domain watermark is obtained by sharing the total watermark among the M involved blocks: w l = 1 N 1 w p,km e j(2π/n)lk, pmn l pmn + MN 1 (46) MN k=0 Finally, the embedder constructs the watermarked samples as y l = x l + w l, for all l. As we have mentioned, decoding works in an identical way to (4), constructing the pth block of the observation in the DFT domain as in (45). Interestingly, the aliasing operation can be seen as a particular instance of spreading, this being the name coined by Chen and Wornell to refer to a technique that consists in projecting onto a lower dimensional subspace where embedding and decoding takes place. Here, through aliasing we are transforming the original M N-dimensional block into an N-dimensional block, using a length-m projection vector s = 1. Of course, other projection sequences can be used, but those having coefficients in {±1} are the preferred choice for implementation simplicity. For analytical purposes, the easiest way to adapt the developments made in Section V is to think that the DFT length is now MN and that we are interested in those DFT coefficients of the form km, for k = 0,1,,N/2+
18 18 1. This straightforwardly leads to Var[ X p,km ] = MNσ 2 x, so the expressions of the bit error probability in Section V hold for this case if N and DFT-RDM are replaced by MN and SDFT-RDM, respectively, where SDFT-RDM is the quantization step size that is applied for embedding in the DFT-domain after spreading has been done in the time-domain. In order to quantify the gain brought about by spreading, we notice that spreading by M allows to reduce the quantization step size by M to achieve the same DWR. Hence, SDFT-RDM = DFT-RDM / M, and the following bounds on the bit error probability result ( 2 DFT-RDM σ x M ) ( N P e,dm < P e,k < P e,rdm L, DFT-RDMσ x M N σ k σ k Therefore, whereas increasing the DFT size entails a gain of 10log 10 N db, spreading provides a gain of 10log 10 M 2 db in the effective SNR. This somewhat surprising result is due to the combination of two factors, each providing a gain of 10log 10 M db: the use of a narrower DFT window and the projection to a lower dimensional subspace. We must remark that this gain occurs because our main source of impairment is the interference from the filtered host, which can be reduced by increasing the DFT size: if additive white noise were the dominant channel effect, then the gain due to spreading would simply be 10log 10 M, as customary. Once again, this gain is obtained at the expense of a reduction in the data rate by a factor of M. ) (47) VII. EXPERIMENTAL RESULTS Several experiments were conducted to test the validity of our theoretical analysis and bounds and to evaluate the actual performance of the proposed method in practical scenarios. In all cases, the host signal is white, the DWR was set to 25 db and the memory L of the g function is 100. No other impairment than LTI filtering has been introduced. For each reported experiment, except those on Reed-Solomon coding (to be discussed later), 10 Monte Carlo runs with N 10 3 transmitted bits each were averaged, with N the DFT size. In all cases reported, the bit error probability of both DM and time-domain RDM is nearly 0.5, thus rendering the retrieval of the hidden information completely unreliable for both methods. Fortunately, DFT-RDM manages to get a BER small enough to be driven to any desired error probability by means of error correcting codes, as we will later show. Our performance plots will reflect the BER per DFT channel, except when we wish to compare different DFT sizes, in which case the BER is represented versus the frequency ω. Bear in mind that due to the symmetry in the involved signals, only the coefficients in the range [0, N/2] are considered. The labels analytical, upper bound and lower bound DM correspond to the plots obtained using (23), (26) and (29), respectively. Figure 4 illustrates the behavior of DFT-RDM with N = 256 when the attack consists in a low-pass filter with cut-off frequency ω c = 0.8π rad. Notice the excellent match between our analytical results and the experimental ones. Also notice that the presented lower bound is valid for bit error probabilities smaller than 10 1 (recall that in Section V-D we established the validity of the lower bound at least for probabilities smaller than );
19 19 the plot labeled as RDM-lower bound is based on using the error probability of RDM instead of that of DM in (29), and in practice acts as a tighter lower bound, even though it cannot be formally proven to hold. It is interesting also to justify why the BER for the DC channel (i.e., that corresponding to k = 0) is larger than for its neighboring coefficients: at DC all the involved quantities are real; this means that all the multiplication error falls in the watermark direction, while for complex coefficients the error has a significant component in the orthogonal direction to the watermark. A similar argument can be made with respect to the coefficient for k = N/2, even though in this example the BER increase is not apparent because for the high-frequency coefficients the BER is already LPF. ω c =0.8 π. DWR=25 db. N= Pb experimental analytical lower bound RDM upper bound lower bound DM DFT channel Fig. 4. BER vs. DFT channel for a low-pass filter with ω c = 0.8π. Figure 5 summarizes the experiment conducted by feeding the watermarked signal through a 10-band graphic audio equalizer. This corresponds to an adaptation of the EQU equalizer for the XMMS multimedia player for Unix platforms, which is modeled after the popular Winamp player for the Windows operating system. Experiments have been performed when the equalizer default presets are chosen, yielding the frequency response depicted in Figure 6. A Hamming window has been used following the procedure outlined in Section VI-A. Note that the lower bounds in Figure 5 are remarkably tight. This is due to the fact that now the error Ñm,k in our model is almost circularly symmetric, which is not the case for the low-pass filtering attack. The best way to illustrate the gain due to spreading (Section VI-B) is to fix an arbitrary DFT channel (in our example k = N/4) and then plot the BER vs DWR for different spreading factors, as is done in Figure 7, where values of M = 1,2 and 3 are considered. A DFT size of N = 256 and a rectangular window were used. The attack channel is the Winamp equalizer of the previous example. Diamonds correspond to experimental results, whereas lines plot the analytical results obtained by adapting (23) to account for spreading in the way
Rational Dither Modulation: A High-Rate Data-Hiding Method Invariant to Gain Attacks
 1 Rational Dither Modulation: A High-Rate Data-Hiding Method Invariant to Gain Attacks Fernando Pérez-González Ý *, Carlos Mosquera Ý, Mauro Barni Þ and Andrea Abrardo Þ. Abstract A novel quantization-based
1 Rational Dither Modulation: A High-Rate Data-Hiding Method Invariant to Gain Attacks Fernando Pérez-González Ý *, Carlos Mosquera Ý, Mauro Barni Þ and Andrea Abrardo Þ. Abstract A novel quantization-based
Witsenhausen s counterexample and its links with multimedia security problems
 Witsenhausen s counterexample and its links with multimedia security problems Pedro Comesaña-Alfaro Fernando Pérez-González Chaouki T. Abdallah IWDW 2011 Atlantic City, New Jersey Outline Introduction
Witsenhausen s counterexample and its links with multimedia security problems Pedro Comesaña-Alfaro Fernando Pérez-González Chaouki T. Abdallah IWDW 2011 Atlantic City, New Jersey Outline Introduction
Chirp Transform for FFT
 Chirp Transform for FFT Since the FFT is an implementation of the DFT, it provides a frequency resolution of 2π/N, where N is the length of the input sequence. If this resolution is not sufficient in a
Chirp Transform for FFT Since the FFT is an implementation of the DFT, it provides a frequency resolution of 2π/N, where N is the length of the input sequence. If this resolution is not sufficient in a
Lecture 12. Block Diagram
 Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Chapter [4] "Operations on a Single Random Variable"
![Chapter [4] Operations on a Single Random Variable Chapter [4] Operations on a Single Random Variable](/thumbs/93/112549011.jpg) Chapter [4] "Operations on a Single Random Variable" 4.1 Introduction In our study of random variables we use the probability density function or the cumulative distribution function to provide a complete
Chapter [4] "Operations on a Single Random Variable" 4.1 Introduction In our study of random variables we use the probability density function or the cumulative distribution function to provide a complete
2. SPECTRAL ANALYSIS APPLIED TO STOCHASTIC PROCESSES
 2. SPECTRAL ANALYSIS APPLIED TO STOCHASTIC PROCESSES 2.0 THEOREM OF WIENER- KHINTCHINE An important technique in the study of deterministic signals consists in using harmonic functions to gain the spectral
2. SPECTRAL ANALYSIS APPLIED TO STOCHASTIC PROCESSES 2.0 THEOREM OF WIENER- KHINTCHINE An important technique in the study of deterministic signals consists in using harmonic functions to gain the spectral
Machine Learning. A Bayesian and Optimization Perspective. Academic Press, Sergios Theodoridis 1. of Athens, Athens, Greece.
 Machine Learning A Bayesian and Optimization Perspective Academic Press, 2015 Sergios Theodoridis 1 1 Dept. of Informatics and Telecommunications, National and Kapodistrian University of Athens, Athens,
Machine Learning A Bayesian and Optimization Perspective Academic Press, 2015 Sergios Theodoridis 1 1 Dept. of Informatics and Telecommunications, National and Kapodistrian University of Athens, Athens,
University of Siena. Multimedia Security. Watermark extraction. Mauro Barni University of Siena. M. Barni, University of Siena
 Multimedia Security Mauro Barni University of Siena : summary Optimum decoding/detection Additive SS watermarks Decoding/detection of QIM watermarks The dilemma of de-synchronization attacks Geometric
Multimedia Security Mauro Barni University of Siena : summary Optimum decoding/detection Additive SS watermarks Decoding/detection of QIM watermarks The dilemma of de-synchronization attacks Geometric
INTRODUCTION TO DELTA-SIGMA ADCS
 ECE37 Advanced Analog Circuits INTRODUCTION TO DELTA-SIGMA ADCS Richard Schreier richard.schreier@analog.com NLCOTD: Level Translator VDD > VDD2, e.g. 3-V logic? -V logic VDD < VDD2, e.g. -V logic? 3-V
ECE37 Advanced Analog Circuits INTRODUCTION TO DELTA-SIGMA ADCS Richard Schreier richard.schreier@analog.com NLCOTD: Level Translator VDD > VDD2, e.g. 3-V logic? -V logic VDD < VDD2, e.g. -V logic? 3-V
Discrete Fourier Transform
 Discrete Fourier Transform Virtually all practical signals have finite length (e.g., sensor data, audio records, digital images, stock values, etc). Rather than considering such signals to be zero-padded
Discrete Fourier Transform Virtually all practical signals have finite length (e.g., sensor data, audio records, digital images, stock values, etc). Rather than considering such signals to be zero-padded
Chapter 7. Error Control Coding. 7.1 Historical background. Mikael Olofsson 2005
 Chapter 7 Error Control Coding Mikael Olofsson 2005 We have seen in Chapters 4 through 6 how digital modulation can be used to control error probabilities. This gives us a digital channel that in each
Chapter 7 Error Control Coding Mikael Olofsson 2005 We have seen in Chapters 4 through 6 how digital modulation can be used to control error probabilities. This gives us a digital channel that in each
Chapter 9 Fundamental Limits in Information Theory
 Chapter 9 Fundamental Limits in Information Theory Information Theory is the fundamental theory behind information manipulation, including data compression and data transmission. 9.1 Introduction o For
Chapter 9 Fundamental Limits in Information Theory Information Theory is the fundamental theory behind information manipulation, including data compression and data transmission. 9.1 Introduction o For
DETECTION theory deals primarily with techniques for
 ADVANCED SIGNAL PROCESSING SE Optimum Detection of Deterministic and Random Signals Stefan Tertinek Graz University of Technology turtle@sbox.tugraz.at Abstract This paper introduces various methods for
ADVANCED SIGNAL PROCESSING SE Optimum Detection of Deterministic and Random Signals Stefan Tertinek Graz University of Technology turtle@sbox.tugraz.at Abstract This paper introduces various methods for
Filter Analysis and Design
 Filter Analysis and Design Butterworth Filters Butterworth filters have a transfer function whose squared magnitude has the form H a ( jω ) 2 = 1 ( ) 2n. 1+ ω / ω c * M. J. Roberts - All Rights Reserved
Filter Analysis and Design Butterworth Filters Butterworth filters have a transfer function whose squared magnitude has the form H a ( jω ) 2 = 1 ( ) 2n. 1+ ω / ω c * M. J. Roberts - All Rights Reserved
BASICS OF DETECTION AND ESTIMATION THEORY
 BASICS OF DETECTION AND ESTIMATION THEORY 83050E/158 In this chapter we discuss how the transmitted symbols are detected optimally from a noisy received signal (observation). Based on these results, optimal
BASICS OF DETECTION AND ESTIMATION THEORY 83050E/158 In this chapter we discuss how the transmitted symbols are detected optimally from a noisy received signal (observation). Based on these results, optimal
Sensors. Chapter Signal Conditioning
 Chapter 2 Sensors his chapter, yet to be written, gives an overview of sensor technology with emphasis on how to model sensors. 2. Signal Conditioning Sensors convert physical measurements into data. Invariably,
Chapter 2 Sensors his chapter, yet to be written, gives an overview of sensor technology with emphasis on how to model sensors. 2. Signal Conditioning Sensors convert physical measurements into data. Invariably,
EE4304 C-term 2007: Lecture 17 Supplemental Slides
 EE434 C-term 27: Lecture 17 Supplemental Slides D. Richard Brown III Worcester Polytechnic Institute, Department of Electrical and Computer Engineering February 5, 27 Geometric Representation: Optimal
EE434 C-term 27: Lecture 17 Supplemental Slides D. Richard Brown III Worcester Polytechnic Institute, Department of Electrical and Computer Engineering February 5, 27 Geometric Representation: Optimal
3. ESTIMATION OF SIGNALS USING A LEAST SQUARES TECHNIQUE
 3. ESTIMATION OF SIGNALS USING A LEAST SQUARES TECHNIQUE 3.0 INTRODUCTION The purpose of this chapter is to introduce estimators shortly. More elaborated courses on System Identification, which are given
3. ESTIMATION OF SIGNALS USING A LEAST SQUARES TECHNIQUE 3.0 INTRODUCTION The purpose of this chapter is to introduce estimators shortly. More elaborated courses on System Identification, which are given
Elec4621 Advanced Digital Signal Processing Chapter 11: Time-Frequency Analysis
 Elec461 Advanced Digital Signal Processing Chapter 11: Time-Frequency Analysis Dr. D. S. Taubman May 3, 011 In this last chapter of your notes, we are interested in the problem of nding the instantaneous
Elec461 Advanced Digital Signal Processing Chapter 11: Time-Frequency Analysis Dr. D. S. Taubman May 3, 011 In this last chapter of your notes, we are interested in the problem of nding the instantaneous
Signal Modeling Techniques in Speech Recognition. Hassan A. Kingravi
 Signal Modeling Techniques in Speech Recognition Hassan A. Kingravi Outline Introduction Spectral Shaping Spectral Analysis Parameter Transforms Statistical Modeling Discussion Conclusions 1: Introduction
Signal Modeling Techniques in Speech Recognition Hassan A. Kingravi Outline Introduction Spectral Shaping Spectral Analysis Parameter Transforms Statistical Modeling Discussion Conclusions 1: Introduction
Wavelet Footprints: Theory, Algorithms, and Applications
 1306 IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL. 51, NO. 5, MAY 2003 Wavelet Footprints: Theory, Algorithms, and Applications Pier Luigi Dragotti, Member, IEEE, and Martin Vetterli, Fellow, IEEE Abstract
1306 IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL. 51, NO. 5, MAY 2003 Wavelet Footprints: Theory, Algorithms, and Applications Pier Luigi Dragotti, Member, IEEE, and Martin Vetterli, Fellow, IEEE Abstract
Direct-Sequence Spread-Spectrum
 Chapter 3 Direct-Sequence Spread-Spectrum In this chapter we consider direct-sequence spread-spectrum systems. Unlike frequency-hopping, a direct-sequence signal occupies the entire bandwidth continuously.
Chapter 3 Direct-Sequence Spread-Spectrum In this chapter we consider direct-sequence spread-spectrum systems. Unlike frequency-hopping, a direct-sequence signal occupies the entire bandwidth continuously.
Dirty Paper Writing and Watermarking Applications
 Dirty Paper Writing and Watermarking Applications G.RaviKiran February 10, 2003 1 Introduction Following an underlying theme in Communication is the duo of Dirty Paper Writing and Watermarking. In 1983
Dirty Paper Writing and Watermarking Applications G.RaviKiran February 10, 2003 1 Introduction Following an underlying theme in Communication is the duo of Dirty Paper Writing and Watermarking. In 1983
Stochastic Realization of Binary Exchangeable Processes
 Stochastic Realization of Binary Exchangeable Processes Lorenzo Finesso and Cecilia Prosdocimi Abstract A discrete time stochastic process is called exchangeable if its n-dimensional distributions are,
Stochastic Realization of Binary Exchangeable Processes Lorenzo Finesso and Cecilia Prosdocimi Abstract A discrete time stochastic process is called exchangeable if its n-dimensional distributions are,
Discrete Simulation of Power Law Noise
 Discrete Simulation of Power Law Noise Neil Ashby 1,2 1 University of Colorado, Boulder, CO 80309-0390 USA 2 National Institute of Standards and Technology, Boulder, CO 80305 USA ashby@boulder.nist.gov
Discrete Simulation of Power Law Noise Neil Ashby 1,2 1 University of Colorado, Boulder, CO 80309-0390 USA 2 National Institute of Standards and Technology, Boulder, CO 80305 USA ashby@boulder.nist.gov
Quantization Based Watermarking Methods Against Valumetric Distortions
 International Journal of Automation and Computing 14(6), December 2017, 672-685 DOI: 10.1007/s11633-016-1010-6 Quantization Based Watermarking Methods Against Valumetric Distortions Zai-Ran Wang 1,2 Jing
International Journal of Automation and Computing 14(6), December 2017, 672-685 DOI: 10.1007/s11633-016-1010-6 Quantization Based Watermarking Methods Against Valumetric Distortions Zai-Ran Wang 1,2 Jing
Time Series Analysis: 4. Linear filters. P. F. Góra
 Time Series Analysis: 4. Linear filters P. F. Góra http://th-www.if.uj.edu.pl/zfs/gora/ 2012 Linear filters in the Fourier domain Filtering: Multiplying the transform by a transfer function. g n DFT G
Time Series Analysis: 4. Linear filters P. F. Góra http://th-www.if.uj.edu.pl/zfs/gora/ 2012 Linear filters in the Fourier domain Filtering: Multiplying the transform by a transfer function. g n DFT G
Research Article A New QIM-Based Watermarking Method Robust to Gain Attack
 International Journal of Digital Multimedia Broadcasting, Article ID 9188, 14 pages http://dx.doi.org/1.1155/214/9188 Research Article A New QIM-Based Watermarking Method Robust to Gain Attack Yevhen Zolotavkin
International Journal of Digital Multimedia Broadcasting, Article ID 9188, 14 pages http://dx.doi.org/1.1155/214/9188 Research Article A New QIM-Based Watermarking Method Robust to Gain Attack Yevhen Zolotavkin
Capacity of a Two-way Function Multicast Channel
 Capacity of a Two-way Function Multicast Channel 1 Seiyun Shin, Student Member, IEEE and Changho Suh, Member, IEEE Abstract We explore the role of interaction for the problem of reliable computation over
Capacity of a Two-way Function Multicast Channel 1 Seiyun Shin, Student Member, IEEE and Changho Suh, Member, IEEE Abstract We explore the role of interaction for the problem of reliable computation over
Design of IIR filters
 Design of IIR filters Standard methods of design of digital infinite impulse response (IIR) filters usually consist of three steps, namely: 1 design of a continuous-time (CT) prototype low-pass filter;
Design of IIR filters Standard methods of design of digital infinite impulse response (IIR) filters usually consist of three steps, namely: 1 design of a continuous-time (CT) prototype low-pass filter;
IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL. 47, NO. 2, FEBRUARY
 IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL. 47, NO. 2, FEBRUARY 1999 389 Oversampling PCM Techniques and Optimum Noise Shapers for Quantizing a Class of Nonbandlimited Signals Jamal Tuqan, Member, IEEE
IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL. 47, NO. 2, FEBRUARY 1999 389 Oversampling PCM Techniques and Optimum Noise Shapers for Quantizing a Class of Nonbandlimited Signals Jamal Tuqan, Member, IEEE
Versatile, Accurate and Analytically Tractable Approximation for the Gaussian Q-function. Miguel López-Benítez and Fernando Casadevall
 Versatile, Accurate and Analytically Tractable Approximation for the Gaussian Q-function Miguel López-Benítez and Fernando Casadevall Department of Signal Theory and Communications Universitat Politècnica
Versatile, Accurate and Analytically Tractable Approximation for the Gaussian Q-function Miguel López-Benítez and Fernando Casadevall Department of Signal Theory and Communications Universitat Politècnica
Design Criteria for the Quadratically Interpolated FFT Method (I): Bias due to Interpolation
 CENTER FOR COMPUTER RESEARCH IN MUSIC AND ACOUSTICS DEPARTMENT OF MUSIC, STANFORD UNIVERSITY REPORT NO. STAN-M-4 Design Criteria for the Quadratically Interpolated FFT Method (I): Bias due to Interpolation
CENTER FOR COMPUTER RESEARCH IN MUSIC AND ACOUSTICS DEPARTMENT OF MUSIC, STANFORD UNIVERSITY REPORT NO. STAN-M-4 Design Criteria for the Quadratically Interpolated FFT Method (I): Bias due to Interpolation
Multimedia Signals and Systems - Audio and Video. Signal, Image, Video Processing Review-Introduction, MP3 and MPEG2
 Multimedia Signals and Systems - Audio and Video Signal, Image, Video Processing Review-Introduction, MP3 and MPEG2 Kunio Takaya Electrical and Computer Engineering University of Saskatchewan December
Multimedia Signals and Systems - Audio and Video Signal, Image, Video Processing Review-Introduction, MP3 and MPEG2 Kunio Takaya Electrical and Computer Engineering University of Saskatchewan December
V(t) = Total Power = Calculating the Power Spectral Density (PSD) in IDL. Thomas Ferree, Ph.D. August 23, 1999
 Calculating the Power Spectral Density (PSD) in IDL Thomas Ferree, Ph.D. August 23, 1999 This note outlines the calculation of power spectra via the fast Fourier transform (FFT) algorithm. There are several
Calculating the Power Spectral Density (PSD) in IDL Thomas Ferree, Ph.D. August 23, 1999 This note outlines the calculation of power spectra via the fast Fourier transform (FFT) algorithm. There are several
Square Root Raised Cosine Filter
 Wireless Information Transmission System Lab. Square Root Raised Cosine Filter Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal design
Wireless Information Transmission System Lab. Square Root Raised Cosine Filter Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal design
Digital Speech Processing Lecture 10. Short-Time Fourier Analysis Methods - Filter Bank Design
 Digital Speech Processing Lecture Short-Time Fourier Analysis Methods - Filter Bank Design Review of STFT j j ˆ m ˆ. X e x[ mw ] [ nˆ m] e nˆ function of nˆ looks like a time sequence function of ˆ looks
Digital Speech Processing Lecture Short-Time Fourier Analysis Methods - Filter Bank Design Review of STFT j j ˆ m ˆ. X e x[ mw ] [ nˆ m] e nˆ function of nˆ looks like a time sequence function of ˆ looks
Multirate Digital Signal Processing
 Multirate Digital Signal Processing Basic Sampling Rate Alteration Devices Up-sampler - Used to increase the sampling rate by an integer factor Down-sampler - Used to decrease the sampling rate by an integer
Multirate Digital Signal Processing Basic Sampling Rate Alteration Devices Up-sampler - Used to increase the sampling rate by an integer factor Down-sampler - Used to decrease the sampling rate by an integer
Lecture Notes 1: Vector spaces
 Optimization-based data analysis Fall 2017 Lecture Notes 1: Vector spaces In this chapter we review certain basic concepts of linear algebra, highlighting their application to signal processing. 1 Vector
Optimization-based data analysis Fall 2017 Lecture Notes 1: Vector spaces In this chapter we review certain basic concepts of linear algebra, highlighting their application to signal processing. 1 Vector
ECE 410 DIGITAL SIGNAL PROCESSING D. Munson University of Illinois Chapter 12
 . ECE 40 DIGITAL SIGNAL PROCESSING D. Munson University of Illinois Chapter IIR Filter Design ) Based on Analog Prototype a) Impulse invariant design b) Bilinear transformation ( ) ~ widely used ) Computer-Aided
. ECE 40 DIGITAL SIGNAL PROCESSING D. Munson University of Illinois Chapter IIR Filter Design ) Based on Analog Prototype a) Impulse invariant design b) Bilinear transformation ( ) ~ widely used ) Computer-Aided
6196 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 9, SEPTEMBER 2011
 6196 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 9, SEPTEMBER 2011 On the Structure of Real-Time Encoding and Decoding Functions in a Multiterminal Communication System Ashutosh Nayyar, Student
6196 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 9, SEPTEMBER 2011 On the Structure of Real-Time Encoding and Decoding Functions in a Multiterminal Communication System Ashutosh Nayyar, Student
Expectation propagation for signal detection in flat-fading channels
 Expectation propagation for signal detection in flat-fading channels Yuan Qi MIT Media Lab Cambridge, MA, 02139 USA yuanqi@media.mit.edu Thomas Minka CMU Statistics Department Pittsburgh, PA 15213 USA
Expectation propagation for signal detection in flat-fading channels Yuan Qi MIT Media Lab Cambridge, MA, 02139 USA yuanqi@media.mit.edu Thomas Minka CMU Statistics Department Pittsburgh, PA 15213 USA
Generalized Writing on Dirty Paper
 Generalized Writing on Dirty Paper Aaron S. Cohen acohen@mit.edu MIT, 36-689 77 Massachusetts Ave. Cambridge, MA 02139-4307 Amos Lapidoth lapidoth@isi.ee.ethz.ch ETF E107 ETH-Zentrum CH-8092 Zürich, Switzerland
Generalized Writing on Dirty Paper Aaron S. Cohen acohen@mit.edu MIT, 36-689 77 Massachusetts Ave. Cambridge, MA 02139-4307 Amos Lapidoth lapidoth@isi.ee.ethz.ch ETF E107 ETH-Zentrum CH-8092 Zürich, Switzerland
Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics. 1 Executive summary
 ECE 830 Spring 207 Instructor: R. Willett Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we saw that the likelihood
ECE 830 Spring 207 Instructor: R. Willett Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we saw that the likelihood
Quantization Index Modulation: A Class of Provably Good Methods for Digital Watermarking and Information Embedding
 To appear in IEEE Trans. Inform. Theory. Quantization Index Modulation: A Class of Provably Good Methods for Digital Watermarking and Information Embedding Brian Chen and Gregory W. Wornell Submitted June
To appear in IEEE Trans. Inform. Theory. Quantization Index Modulation: A Class of Provably Good Methods for Digital Watermarking and Information Embedding Brian Chen and Gregory W. Wornell Submitted June
SNR Calculation and Spectral Estimation [S&T Appendix A]
![SNR Calculation and Spectral Estimation [S&T Appendix A] SNR Calculation and Spectral Estimation [S&T Appendix A]](/thumbs/75/71929358.jpg) SR Calculation and Spectral Estimation [S&T Appendix A] or, How not to make a mess of an FFT Make sure the input is located in an FFT bin 1 Window the data! A Hann window works well. Compute the FFT 3
SR Calculation and Spectral Estimation [S&T Appendix A] or, How not to make a mess of an FFT Make sure the input is located in an FFT bin 1 Window the data! A Hann window works well. Compute the FFT 3
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi
 Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
LAB 6: FIR Filter Design Summer 2011
 University of Illinois at Urbana-Champaign Department of Electrical and Computer Engineering ECE 311: Digital Signal Processing Lab Chandra Radhakrishnan Peter Kairouz LAB 6: FIR Filter Design Summer 011
University of Illinois at Urbana-Champaign Department of Electrical and Computer Engineering ECE 311: Digital Signal Processing Lab Chandra Radhakrishnan Peter Kairouz LAB 6: FIR Filter Design Summer 011
-Digital Signal Processing- FIR Filter Design. Lecture May-16
 -Digital Signal Processing- FIR Filter Design Lecture-17 24-May-16 FIR Filter Design! FIR filters can also be designed from a frequency response specification.! The equivalent sampled impulse response
-Digital Signal Processing- FIR Filter Design Lecture-17 24-May-16 FIR Filter Design! FIR filters can also be designed from a frequency response specification.! The equivalent sampled impulse response
Question Bank. UNIT 1 Part-A
 FATIMA MICHAEL COLLEGE OF ENGINEERING & TECHNOLOGY Senkottai Village, Madurai Sivagangai Main Road, Madurai -625 020 An ISO 9001:2008 Certified Institution Question Bank DEPARTMENT OF ELECTRONICS AND COMMUNICATION
FATIMA MICHAEL COLLEGE OF ENGINEERING & TECHNOLOGY Senkottai Village, Madurai Sivagangai Main Road, Madurai -625 020 An ISO 9001:2008 Certified Institution Question Bank DEPARTMENT OF ELECTRONICS AND COMMUNICATION
This examination consists of 10 pages. Please check that you have a complete copy. Time: 2.5 hrs INSTRUCTIONS
 THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 08 December 2009 This examination consists of
THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 08 December 2009 This examination consists of
Copyright license. Exchanging Information with the Stars. The goal. Some challenges
 Copyright license Exchanging Information with the Stars David G Messerschmitt Department of Electrical Engineering and Computer Sciences University of California at Berkeley messer@eecs.berkeley.edu Talk
Copyright license Exchanging Information with the Stars David G Messerschmitt Department of Electrical Engineering and Computer Sciences University of California at Berkeley messer@eecs.berkeley.edu Talk
UNIVERSITY OF OSLO. Faculty of mathematics and natural sciences. Forslag til fasit, versjon-01: Problem 1 Signals and systems.
 UNIVERSITY OF OSLO Faculty of mathematics and natural sciences Examination in INF3470/4470 Digital signal processing Day of examination: December 1th, 016 Examination hours: 14:30 18.30 This problem set
UNIVERSITY OF OSLO Faculty of mathematics and natural sciences Examination in INF3470/4470 Digital signal processing Day of examination: December 1th, 016 Examination hours: 14:30 18.30 This problem set
Diversity Performance of a Practical Non-Coherent Detect-and-Forward Receiver
 Diversity Performance of a Practical Non-Coherent Detect-and-Forward Receiver Michael R. Souryal and Huiqing You National Institute of Standards and Technology Advanced Network Technologies Division Gaithersburg,
Diversity Performance of a Practical Non-Coherent Detect-and-Forward Receiver Michael R. Souryal and Huiqing You National Institute of Standards and Technology Advanced Network Technologies Division Gaithersburg,
Khinchin s approach to statistical mechanics
 Chapter 7 Khinchin s approach to statistical mechanics 7.1 Introduction In his Mathematical Foundations of Statistical Mechanics Khinchin presents an ergodic theorem which is valid also for systems that
Chapter 7 Khinchin s approach to statistical mechanics 7.1 Introduction In his Mathematical Foundations of Statistical Mechanics Khinchin presents an ergodic theorem which is valid also for systems that
VALLIAMMAI ENGINEERING COLLEGE. SRM Nagar, Kattankulathur DEPARTMENT OF INFORMATION TECHNOLOGY. Academic Year
 VALLIAMMAI ENGINEERING COLLEGE SRM Nagar, Kattankulathur- 603 203 DEPARTMENT OF INFORMATION TECHNOLOGY Academic Year 2016-2017 QUESTION BANK-ODD SEMESTER NAME OF THE SUBJECT SUBJECT CODE SEMESTER YEAR
VALLIAMMAI ENGINEERING COLLEGE SRM Nagar, Kattankulathur- 603 203 DEPARTMENT OF INFORMATION TECHNOLOGY Academic Year 2016-2017 QUESTION BANK-ODD SEMESTER NAME OF THE SUBJECT SUBJECT CODE SEMESTER YEAR
Experimental Fourier Transforms
 Chapter 5 Experimental Fourier Transforms 5.1 Sampling and Aliasing Given x(t), we observe only sampled data x s (t) = x(t)s(t; T s ) (Fig. 5.1), where s is called sampling or comb function and can be
Chapter 5 Experimental Fourier Transforms 5.1 Sampling and Aliasing Given x(t), we observe only sampled data x s (t) = x(t)s(t; T s ) (Fig. 5.1), where s is called sampling or comb function and can be
Summary: SER formulation. Binary antipodal constellation. Generic binary constellation. Constellation gain. 2D constellations
 TUTORIAL ON DIGITAL MODULATIONS Part 8a: Error probability A [2011-01-07] 07] Roberto Garello, Politecnico di Torino Free download (for personal use only) at: www.tlc.polito.it/garello 1 Part 8a: Error
TUTORIAL ON DIGITAL MODULATIONS Part 8a: Error probability A [2011-01-07] 07] Roberto Garello, Politecnico di Torino Free download (for personal use only) at: www.tlc.polito.it/garello 1 Part 8a: Error
Parametric Techniques
 Parametric Techniques Jason J. Corso SUNY at Buffalo J. Corso (SUNY at Buffalo) Parametric Techniques 1 / 39 Introduction When covering Bayesian Decision Theory, we assumed the full probabilistic structure
Parametric Techniques Jason J. Corso SUNY at Buffalo J. Corso (SUNY at Buffalo) Parametric Techniques 1 / 39 Introduction When covering Bayesian Decision Theory, we assumed the full probabilistic structure
Signal Design for Band-Limited Channels
 Wireless Information Transmission System Lab. Signal Design for Band-Limited Channels Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal
Wireless Information Transmission System Lab. Signal Design for Band-Limited Channels Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal
Performance of small signal sets
 42 Chapter 5 Performance of small signal sets In this chapter, we show how to estimate the performance of small-to-moderate-sized signal constellations on the discrete-time AWGN channel. With equiprobable
42 Chapter 5 Performance of small signal sets In this chapter, we show how to estimate the performance of small-to-moderate-sized signal constellations on the discrete-time AWGN channel. With equiprobable
DIGITAL SIGNAL PROCESSING UNIT III INFINITE IMPULSE RESPONSE DIGITAL FILTERS. 3.6 Design of Digital Filter using Digital to Digital
 DIGITAL SIGNAL PROCESSING UNIT III INFINITE IMPULSE RESPONSE DIGITAL FILTERS Contents: 3.1 Introduction IIR Filters 3.2 Transformation Function Derivation 3.3 Review of Analog IIR Filters 3.3.1 Butterworth
DIGITAL SIGNAL PROCESSING UNIT III INFINITE IMPULSE RESPONSE DIGITAL FILTERS Contents: 3.1 Introduction IIR Filters 3.2 Transformation Function Derivation 3.3 Review of Analog IIR Filters 3.3.1 Butterworth
Basic Multi-rate Operations: Decimation and Interpolation
 1 Basic Multirate Operations 2 Interconnection of Building Blocks 1.1 Decimation and Interpolation 1.2 Digital Filter Banks Basic Multi-rate Operations: Decimation and Interpolation Building blocks for
1 Basic Multirate Operations 2 Interconnection of Building Blocks 1.1 Decimation and Interpolation 1.2 Digital Filter Banks Basic Multi-rate Operations: Decimation and Interpolation Building blocks for
DHANALAKSHMI COLLEGE OF ENGINEERING DEPARTMENT OF ELECTRICAL AND ELECTRONICS ENGINEERING EC2314- DIGITAL SIGNAL PROCESSING UNIT I INTRODUCTION PART A
 DHANALAKSHMI COLLEGE OF ENGINEERING DEPARTMENT OF ELECTRICAL AND ELECTRONICS ENGINEERING EC2314- DIGITAL SIGNAL PROCESSING UNIT I INTRODUCTION PART A Classification of systems : Continuous and Discrete
DHANALAKSHMI COLLEGE OF ENGINEERING DEPARTMENT OF ELECTRICAL AND ELECTRONICS ENGINEERING EC2314- DIGITAL SIGNAL PROCESSING UNIT I INTRODUCTION PART A Classification of systems : Continuous and Discrete
Filter Design Problem
 Filter Design Problem Design of frequency-selective filters usually starts with a specification of their frequency response function. Practical filters have passband and stopband ripples, while exhibiting
Filter Design Problem Design of frequency-selective filters usually starts with a specification of their frequency response function. Practical filters have passband and stopband ripples, while exhibiting
Inference and estimation in probabilistic time series models
 1 Inference and estimation in probabilistic time series models David Barber, A Taylan Cemgil and Silvia Chiappa 11 Time series The term time series refers to data that can be represented as a sequence
1 Inference and estimation in probabilistic time series models David Barber, A Taylan Cemgil and Silvia Chiappa 11 Time series The term time series refers to data that can be represented as a sequence
Oversampling Converters
 Oversampling Converters David Johns and Ken Martin (johns@eecg.toronto.edu) (martin@eecg.toronto.edu) slide 1 of 56 Motivation Popular approach for medium-to-low speed A/D and D/A applications requiring
Oversampling Converters David Johns and Ken Martin (johns@eecg.toronto.edu) (martin@eecg.toronto.edu) slide 1 of 56 Motivation Popular approach for medium-to-low speed A/D and D/A applications requiring
PREDICTIVE quantization is one of the most widely-used
 618 IEEE JOURNAL OF SELECTED TOPICS IN SIGNAL PROCESSING, VOL. 1, NO. 4, DECEMBER 2007 Robust Predictive Quantization: Analysis and Design Via Convex Optimization Alyson K. Fletcher, Member, IEEE, Sundeep
618 IEEE JOURNAL OF SELECTED TOPICS IN SIGNAL PROCESSING, VOL. 1, NO. 4, DECEMBER 2007 Robust Predictive Quantization: Analysis and Design Via Convex Optimization Alyson K. Fletcher, Member, IEEE, Sundeep
An Information-Theoretic Analysis of Dirty Paper Coding for Informed Audio Watermarking
 1 An Information-Theoretic Analysis of Dirty Paper Coding for Informed Audio Watermarking Andrea Abrardo, Mauro Barni, Andrea Gorrieri, Gianluigi Ferrari Department of Information Engineering and Mathematical
1 An Information-Theoretic Analysis of Dirty Paper Coding for Informed Audio Watermarking Andrea Abrardo, Mauro Barni, Andrea Gorrieri, Gianluigi Ferrari Department of Information Engineering and Mathematical
Parametric Techniques Lecture 3
 Parametric Techniques Lecture 3 Jason Corso SUNY at Buffalo 22 January 2009 J. Corso (SUNY at Buffalo) Parametric Techniques Lecture 3 22 January 2009 1 / 39 Introduction In Lecture 2, we learned how to
Parametric Techniques Lecture 3 Jason Corso SUNY at Buffalo 22 January 2009 J. Corso (SUNY at Buffalo) Parametric Techniques Lecture 3 22 January 2009 1 / 39 Introduction In Lecture 2, we learned how to
1 1.27z z 2. 1 z H 2
 E481 Digital Signal Processing Exam Date: Thursday -1-1 16:15 18:45 Final Exam - Solutions Dan Ellis 1. (a) In this direct-form II second-order-section filter, the first stage has
E481 Digital Signal Processing Exam Date: Thursday -1-1 16:15 18:45 Final Exam - Solutions Dan Ellis 1. (a) In this direct-form II second-order-section filter, the first stage has
Time Series Analysis: 4. Digital Linear Filters. P. F. Góra
 Time Series Analysis: 4. Digital Linear Filters P. F. Góra http://th-www.if.uj.edu.pl/zfs/gora/ 2018 Linear filters Filtering in Fourier domain is very easy: multiply the DFT of the input by a transfer
Time Series Analysis: 4. Digital Linear Filters P. F. Góra http://th-www.if.uj.edu.pl/zfs/gora/ 2018 Linear filters Filtering in Fourier domain is very easy: multiply the DFT of the input by a transfer
ON DECREASING THE COMPLEXITY OF LATTICE-REDUCTION-AIDED K-BEST MIMO DETECTORS.
 17th European Signal Processing Conference (EUSIPCO 009) Glasgow, Scotland, August 4-8, 009 ON DECREASING THE COMPLEXITY OF LATTICE-REDUCTION-AIDED K-BEST MIMO DETECTORS. Sandra Roger, Alberto Gonzalez,
17th European Signal Processing Conference (EUSIPCO 009) Glasgow, Scotland, August 4-8, 009 ON DECREASING THE COMPLEXITY OF LATTICE-REDUCTION-AIDED K-BEST MIMO DETECTORS. Sandra Roger, Alberto Gonzalez,
Lecture 7 Introduction to Statistical Decision Theory
 Lecture 7 Introduction to Statistical Decision Theory I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 20, 2016 1 / 55 I-Hsiang Wang IT Lecture 7
Lecture 7 Introduction to Statistical Decision Theory I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 20, 2016 1 / 55 I-Hsiang Wang IT Lecture 7
CoherentDetectionof OFDM
 Telematics Lab IITK p. 1/50 CoherentDetectionof OFDM Indo-UK Advanced Technology Centre Supported by DST-EPSRC K Vasudevan Associate Professor vasu@iitk.ac.in Telematics Lab Department of EE Indian Institute
Telematics Lab IITK p. 1/50 CoherentDetectionof OFDM Indo-UK Advanced Technology Centre Supported by DST-EPSRC K Vasudevan Associate Professor vasu@iitk.ac.in Telematics Lab Department of EE Indian Institute
COS513 LECTURE 8 STATISTICAL CONCEPTS
 COS513 LECTURE 8 STATISTICAL CONCEPTS NIKOLAI SLAVOV AND ANKUR PARIKH 1. MAKING MEANINGFUL STATEMENTS FROM JOINT PROBABILITY DISTRIBUTIONS. A graphical model (GM) represents a family of probability distributions
COS513 LECTURE 8 STATISTICAL CONCEPTS NIKOLAI SLAVOV AND ANKUR PARIKH 1. MAKING MEANINGFUL STATEMENTS FROM JOINT PROBABILITY DISTRIBUTIONS. A graphical model (GM) represents a family of probability distributions
Transform Representation of Signals
 C H A P T E R 3 Transform Representation of Signals and LTI Systems As you have seen in your prior studies of signals and systems, and as emphasized in the review in Chapter 2, transforms play a central
C H A P T E R 3 Transform Representation of Signals and LTI Systems As you have seen in your prior studies of signals and systems, and as emphasized in the review in Chapter 2, transforms play a central
Advanced 3 G and 4 G Wireless Communication Prof. Aditya K Jagannathan Department of Electrical Engineering Indian Institute of Technology, Kanpur
 Advanced 3 G and 4 G Wireless Communication Prof. Aditya K Jagannathan Department of Electrical Engineering Indian Institute of Technology, Kanpur Lecture - 19 Multi-User CDMA Uplink and Asynchronous CDMA
Advanced 3 G and 4 G Wireless Communication Prof. Aditya K Jagannathan Department of Electrical Engineering Indian Institute of Technology, Kanpur Lecture - 19 Multi-User CDMA Uplink and Asynchronous CDMA
Oversampled A/D Conversion using Alternate Projections
 Oversampled A/D Conversion using Alternate Projections Nguyen T.Thao and Martin Vetterli Department of Electrical Engineering and Center for Telecommunications Research Columbia University, New York, NY
Oversampled A/D Conversion using Alternate Projections Nguyen T.Thao and Martin Vetterli Department of Electrical Engineering and Center for Telecommunications Research Columbia University, New York, NY
Basics on 2-D 2 D Random Signal
 Basics on -D D Random Signal Spring 06 Instructor: K. J. Ray Liu ECE Department, Univ. of Maryland, College Park Overview Last Time: Fourier Analysis for -D signals Image enhancement via spatial filtering
Basics on -D D Random Signal Spring 06 Instructor: K. J. Ray Liu ECE Department, Univ. of Maryland, College Park Overview Last Time: Fourier Analysis for -D signals Image enhancement via spatial filtering
Noise Reduction in Oversampled Filter Banks Using Predictive Quantization
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 47, NO 1, JANUARY 2001 155 Noise Reduction in Oversampled Filter Banks Using Predictive Quantization Helmut Bölcskei, Member, IEEE, Franz Hlawatsch, Member,
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 47, NO 1, JANUARY 2001 155 Noise Reduction in Oversampled Filter Banks Using Predictive Quantization Helmut Bölcskei, Member, IEEE, Franz Hlawatsch, Member,
arxiv:cs/ v1 [cs.it] 11 Sep 2006
![arxiv:cs/ v1 [cs.it] 11 Sep 2006 arxiv:cs/ v1 [cs.it] 11 Sep 2006](/thumbs/92/109672536.jpg) 0 High Date-Rate Single-Symbol ML Decodable Distributed STBCs for Cooperative Networks arxiv:cs/0609054v1 [cs.it] 11 Sep 2006 Zhihang Yi and Il-Min Kim Department of Electrical and Computer Engineering
0 High Date-Rate Single-Symbol ML Decodable Distributed STBCs for Cooperative Networks arxiv:cs/0609054v1 [cs.it] 11 Sep 2006 Zhihang Yi and Il-Min Kim Department of Electrical and Computer Engineering
ELEG 305: Digital Signal Processing
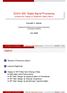 ELEG 305: Digital Signal Processing Lecture : Design of Digital IIR Filters (Part I) Kenneth E. Barner Department of Electrical and Computer Engineering University of Delaware Fall 008 K. E. Barner (Univ.
ELEG 305: Digital Signal Processing Lecture : Design of Digital IIR Filters (Part I) Kenneth E. Barner Department of Electrical and Computer Engineering University of Delaware Fall 008 K. E. Barner (Univ.
Analysis of Finite Wordlength Effects
 Analysis of Finite Wordlength Effects Ideally, the system parameters along with the signal variables have infinite precision taing any value between and In practice, they can tae only discrete values within
Analysis of Finite Wordlength Effects Ideally, the system parameters along with the signal variables have infinite precision taing any value between and In practice, they can tae only discrete values within
EE 367 / CS 448I Computational Imaging and Display Notes: Image Deconvolution (lecture 6)
 EE 367 / CS 448I Computational Imaging and Display Notes: Image Deconvolution (lecture 6) Gordon Wetzstein gordon.wetzstein@stanford.edu This document serves as a supplement to the material discussed in
EE 367 / CS 448I Computational Imaging and Display Notes: Image Deconvolution (lecture 6) Gordon Wetzstein gordon.wetzstein@stanford.edu This document serves as a supplement to the material discussed in
Approximately achieving the feedback interference channel capacity with point-to-point codes
 Approximately achieving the feedback interference channel capacity with point-to-point codes Joyson Sebastian*, Can Karakus*, Suhas Diggavi* Abstract Superposition codes with rate-splitting have been used
Approximately achieving the feedback interference channel capacity with point-to-point codes Joyson Sebastian*, Can Karakus*, Suhas Diggavi* Abstract Superposition codes with rate-splitting have been used
MULTICARRIER code-division multiple access (MC-
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 51, NO. 2, FEBRUARY 2005 479 Spectral Efficiency of Multicarrier CDMA Antonia M. Tulino, Member, IEEE, Linbo Li, and Sergio Verdú, Fellow, IEEE Abstract We
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 51, NO. 2, FEBRUARY 2005 479 Spectral Efficiency of Multicarrier CDMA Antonia M. Tulino, Member, IEEE, Linbo Li, and Sergio Verdú, Fellow, IEEE Abstract We
Fourier Analysis of Signals Using the DFT
 Fourier Analysis of Signals Using the DFT ECE 535 Lecture April 29, 23 Overview: Motivation Many applications require analyzing the frequency content of signals Speech processing study resonances of vocal
Fourier Analysis of Signals Using the DFT ECE 535 Lecture April 29, 23 Overview: Motivation Many applications require analyzing the frequency content of signals Speech processing study resonances of vocal
5682 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 55, NO. 12, DECEMBER /$ IEEE
 5682 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 55, NO. 12, DECEMBER 2009 Hyperplane-Based Vector Quantization for Distributed Estimation in Wireless Sensor Networks Jun Fang, Member, IEEE, and Hongbin
5682 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 55, NO. 12, DECEMBER 2009 Hyperplane-Based Vector Quantization for Distributed Estimation in Wireless Sensor Networks Jun Fang, Member, IEEE, and Hongbin
Quadrature-Mirror Filter Bank
 Quadrature-Mirror Filter Bank In many applications, a discrete-time signal x[n] is split into a number of subband signals { v k [ n]} by means of an analysis filter bank The subband signals are then processed
Quadrature-Mirror Filter Bank In many applications, a discrete-time signal x[n] is split into a number of subband signals { v k [ n]} by means of an analysis filter bank The subband signals are then processed
Sound & Vibration Magazine March, Fundamentals of the Discrete Fourier Transform
 Fundamentals of the Discrete Fourier Transform Mark H. Richardson Hewlett Packard Corporation Santa Clara, California The Fourier transform is a mathematical procedure that was discovered by a French mathematician
Fundamentals of the Discrete Fourier Transform Mark H. Richardson Hewlett Packard Corporation Santa Clara, California The Fourier transform is a mathematical procedure that was discovered by a French mathematician
Digital Band-pass Modulation PROF. MICHAEL TSAI 2011/11/10
 Digital Band-pass Modulation PROF. MICHAEL TSAI 211/11/1 Band-pass Signal Representation a t g t General form: 2πf c t + φ t g t = a t cos 2πf c t + φ t Envelope Phase Envelope is always non-negative,
Digital Band-pass Modulation PROF. MICHAEL TSAI 211/11/1 Band-pass Signal Representation a t g t General form: 2πf c t + φ t g t = a t cos 2πf c t + φ t Envelope Phase Envelope is always non-negative,
ECG782: Multidimensional Digital Signal Processing
 Professor Brendan Morris, SEB 3216, brendan.morris@unlv.edu ECG782: Multidimensional Digital Signal Processing Filtering in the Frequency Domain http://www.ee.unlv.edu/~b1morris/ecg782/ 2 Outline Background
Professor Brendan Morris, SEB 3216, brendan.morris@unlv.edu ECG782: Multidimensional Digital Signal Processing Filtering in the Frequency Domain http://www.ee.unlv.edu/~b1morris/ecg782/ 2 Outline Background
EE6604 Personal & Mobile Communications. Week 15. OFDM on AWGN and ISI Channels
 EE6604 Personal & Mobile Communications Week 15 OFDM on AWGN and ISI Channels 1 { x k } x 0 x 1 x x x N- 2 N- 1 IDFT X X X X 0 1 N- 2 N- 1 { X n } insert guard { g X n } g X I n { } D/A ~ si ( t) X g X
EE6604 Personal & Mobile Communications Week 15 OFDM on AWGN and ISI Channels 1 { x k } x 0 x 1 x x x N- 2 N- 1 IDFT X X X X 0 1 N- 2 N- 1 { X n } insert guard { g X n } g X I n { } D/A ~ si ( t) X g X
Sequential Monte Carlo methods for filtering of unobservable components of multidimensional diffusion Markov processes
 Sequential Monte Carlo methods for filtering of unobservable components of multidimensional diffusion Markov processes Ellida M. Khazen * 13395 Coppermine Rd. Apartment 410 Herndon VA 20171 USA Abstract
Sequential Monte Carlo methods for filtering of unobservable components of multidimensional diffusion Markov processes Ellida M. Khazen * 13395 Coppermine Rd. Apartment 410 Herndon VA 20171 USA Abstract
DFT & Fast Fourier Transform PART-A. 7. Calculate the number of multiplications needed in the calculation of DFT and FFT with 64 point sequence.
 SHRI ANGALAMMAN COLLEGE OF ENGINEERING & TECHNOLOGY (An ISO 9001:2008 Certified Institution) SIRUGANOOR,TRICHY-621105. DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING UNIT I DFT & Fast Fourier
SHRI ANGALAMMAN COLLEGE OF ENGINEERING & TECHNOLOGY (An ISO 9001:2008 Certified Institution) SIRUGANOOR,TRICHY-621105. DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING UNIT I DFT & Fast Fourier
Es e j4φ +4N n. 16 KE s /N 0. σ 2ˆφ4 1 γ s. p(φ e )= exp 1 ( 2πσ φ b cos N 2 φ e 0
 Problem 6.15 : he received signal-plus-noise vector at the output of the matched filter may be represented as (see (5-2-63) for example) : r n = E s e j(θn φ) + N n where θ n =0,π/2,π,3π/2 for QPSK, and
Problem 6.15 : he received signal-plus-noise vector at the output of the matched filter may be represented as (see (5-2-63) for example) : r n = E s e j(θn φ) + N n where θ n =0,π/2,π,3π/2 for QPSK, and
2. What are the tradeoffs among different measures of error (e.g. probability of false alarm, probability of miss, etc.)?
 ECE 830 / CS 76 Spring 06 Instructors: R. Willett & R. Nowak Lecture 3: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we
ECE 830 / CS 76 Spring 06 Instructors: R. Willett & R. Nowak Lecture 3: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we
Multirate signal processing
 Multirate signal processing Discrete-time systems with different sampling rates at various parts of the system are called multirate systems. The need for such systems arises in many applications, including
Multirate signal processing Discrete-time systems with different sampling rates at various parts of the system are called multirate systems. The need for such systems arises in many applications, including
LTI Systems, Additive Noise, and Order Estimation
 LTI Systems, Additive oise, and Order Estimation Soosan Beheshti, Munther A. Dahleh Laboratory for Information and Decision Systems Department of Electrical Engineering and Computer Science Massachusetts
LTI Systems, Additive oise, and Order Estimation Soosan Beheshti, Munther A. Dahleh Laboratory for Information and Decision Systems Department of Electrical Engineering and Computer Science Massachusetts
