Digital Modulation 2
|
|
|
- Chloe Burns
- 6 years ago
- Views:
Transcription
1 Digital Modulation 2 Lecture Notes Ingmar Land and Bernard H. Fleury Department of Electronic Systems Aalborg University Version: November 15, 2006
2 i Contents 1 Continuous-Phase Modulation General Description Minimum-Shift Keying Gaussian Minimum-Shift Keying State and Trellis of CPM Coherent Demodulation of CPM Modern Representation of CPM Initialization The Reference Phase Trajectory The Reference Frequency The Tilted Phase and the New Symbols Block Diagram of the CPM Transmitter Laurent Representation of CPM Minimum Shift Keying Precoded MSK Precoded Gaussian MSK Modulation in EDGE Trellis-Coded Modulation Motivation Convolutional Codes Goodness of a TCM Scheme Set Partitioning Trellis Coded Modulation Examples for TCM
3 ii A ECB Representation of a Band-Pass Signal 102 A.1 The Block diagram A.2 The Signal A.3 Effect of QA Mod/Demod on Signal A.4 Effect of QA Demodulation on Noise A.5 Noise After LP Filtering and Sampling
4 iii References [1] J. G. Proakis and M. Salehi, Communication Systems Engineering, 2nd ed. Prentice-Hall, [2] J. G. Proakis, Digital Communications. McGraw-Hill, [3] P. Laurent, Exact and approximate construction of digital phase modulations by superposition of amplitude modulated pulses (AMP), IEEE Trans. Commun., vol. 34, no. 2, pp , Feb [4] B. Rimoldi, A decomposition approach to CPM, IEEE Trans. Inform. Theory, vol. 34, no. 2, pp , Mar [5] C. E. Shannon, A mathematical theory of communication, Bell System Technical Journal, vol. 27, pp , , July and Oct
5 1 1 Continuous-Phase Modulation The Classical Representation Continuous-phase modulation allows for a bandwith-efficient transmission. In this section, it is represented in the classical way. The modern representation is discussed in the following section. 1.1 General Description The general description of a CPM signal reads X(t; α) = 2P cos ( 2πf 0 t + ϕ(t; α) ) (1) with the following notation: The (semi-infinite) sequence of information-bearing symbols is α = (α 0, α 1,...) with the symbols α n A = {±1, ±3,..., ±M 1} α n A = {0, ±2,..., ±M 1} if M is even if M is odd The mostly used case is that where M is even. (Or even a power of 2. Why?) Example: Binary CPM M = 2: α n { 1, +1}.
6 2 The time-variant information-bearing phase ϕ(t; α) = ϕ 0 + 2πh α n q(t nt ) Remark: In some cases (see later), L 1 known symbols are transmitted at the beginning. Then the summation starts with (L 1). The modulation index is h = p 1 p 2, where p 1, p 2 are natural numbers that are relatively prime. n=0 The function q(t) is the phase reponse. It satisfies q(t) = 0 for t 0, q(t) = 1 2 for t > LT. q(t) 1 2 T... LT t The value L is the memory of the CPM system: L = 1 L > 1 : full response CPM : partial response CPM The phase ϕ 0 is arbitrary. Without loss of generality, we can assume that ϕ 0 is set such that ϕ(0; α) = 0. The carrier frequency is f 0. The power of the transmitted signal is P. The symbol rate is 1 T.
7 3 Instantaneous Frequency of a CPM signal The derivative f(t; α) = 1 d [ ] 2πf 0 t + ϕ(t; α) 2π dt = f d [ ] ϕ(t; α) 2π dt = f 0 + h d [ ] α n q(t nt ) dt f(t; α) = f 0 + h n=0 α n q (t nt ) n=0 }{{} f(t;α) (frequency deviation) q (t) = d dt q(t) of q(t) is called the frequency response of the CPM signal. We can rewrite the CPM signal from (1) as a function of the instantaneous frequency according to x(t; α) = ( t 2P cos 2π f( t; α) d t ) = ( 2P cos 2πf 0 t + 2πh 0 [ t 0 α n q ( t nt ) d t n=0 ])
8 4 Properties of the Frequency Response q(t) = 0, t < 0 q (t) = 0, t < 0 q(t) = 1 2, t > LT q (t) = 0, t > LT q(lt ) = 1 2 LT 0 q ( t)d t = 1 2 Example: Sketch a valid frequency response for L = 4.
9 5 Block diagram of a CPM transmitter (a) Using a phase modulator α(t) = α m δ(t nt ) n=0 1 2 q(t)... LT t ψ(t; α) Phase Modulator x(t; α) (L = 2) 2πk α(t) ψ(t; α) f πk +2πhq(t T ) 0 T t T t πk 2πhq(t T ) (b) Using a frequency modulator α(t) = α m δ(t nt ) n=0 q (t) 1 2 f(t; α) V C D x(t; α) LT t (L = 2) h α(t) f(t; α) f T t T t 1 1 1
10 6 1.2 Minimum-Shift Keying MSK has the following parameters: Binary modulation symbols, i.e., M = 2 Modulation index h = 1 2 Phase response q MSK (t) = 0 t < t T 0 t < T 1 2 t T q MSK (t) 1 2 T t Example: MSK Assume the transmitted symbol sequence α = [ ]. Sketch the phase and the signal.
11 7 Example: MSK, continued Transmitted symbols α n : ϕ(t; α) π 2 T t π 2 1 d 2π dt 1 d 2π dt ϕ(t; α) = 1 4T 1 π/2 ϕ(t; α) = 2π T = 1 4T f = 1 2T x(t; α) t f 1 = 1 T f 2 = 3 2 T f = 1 1 2T. = min. freq- sep for orthogonality
12 8 Phase tree of MSK Phase 6π/2 5π/2 2π 3π/2 π π/2 π/2 π 3π/2 2π 5π/2 6π/2 T 2T 3T 4T 5T 6T t
13 9 Instantaneous frequency of MSK q MSK(t) = 0 for t < 0 1 2T for 0 t < T 0 for t T q MSK (t) 1 T T t Then f(t; α) = f α n q 2 MSK(t nt ) n=0 }{{} f(t;α) Example: f(t; α) 1 1 4T T 2T t 1 4T
14 10 In symbol interval [nt, (n + 1)T ), we have with α n { 1, +1}. f(t; α) = f α n Therefore the frequency offset is = f 0 + α n 4T 1 2T f = ( f ) ( f0 1 ) 4T 4T = 1 2T
15 Gaussian Minimum-Shift Keying Problem How to reduce the side lobes in the power spectrum of MSK while keeping the essential features of this modulation scheme that coherent demodulation is possible? Solution 1. Insert in the MSK VCO-based (non-causal) transmitter a smoothing filter with impulse response g B (t) in front of the MSK frequency response. q MSK (t) Reduction of the side lobes! α(t) = α n δ(t nt ) n=0 g B (t) q (t) q MSK (t) 1 2T VCO x(t; α) T T t T t h f 0 Smoothing filter MSK-transmitter 2. Design g B (t) such that the overall frequency response q (t) = g B (t) q MSK(t) integrates to 1 2 as does q MSK (t). Coherent demodulation is possible!
16 12 The indexing parameter B is the 3 db bandwidth of the impulse response of the smoothing filter. F{ g B (t)} 2 3dB B f Smoothing filter for GMSK GMSK results by selecting the impulse response of the smoothing filter to be a Gaussian pulse g B (t) = 1 exp 2πσT t2 2σ 2 T 2 (2) with σ = ln 2 2πBT Hence, q GMSK(t) = g B (t) q MSK(t) (3)
17 13 We show now that q GMSK (t) has the required property: + q GMSK(t) dt = 1 2 (4) Proof We can view 2 q MSK (t) and g B(t) as the probability density functions (pdfs) of two independent random variables, say U and V : U 2 q MSK(t) V g B (t) Then from (3), 2 q GMSK (t) is the pdf of the sum W = U + V Equ. (4) follows then because the integral of pdfs equals unity. Selected values of B GSM : BT = 0.3 T = DECT : BT = = 3.69ms
18 14 Example Gaussian Pulse gb(t) BT=0.2 BT=0.3 BT= t/t Frequency response g GMSK (t) BT=0.2 BT=0.3 BT= t/t
19 15 Phase response q GMSK (t) = t q GMSK( t ) d t qgmsk(t) BT=0.2 BT=0.3 BT= t/t
20 16 Casual implementation of a GMSK transmitter A casual implementation of a GMSK transmitter is obtained by truncating the non-casual frequency response q GMSK (t) outside a centered interval [ LT 2, ] +LT 2 normalizing to 1/2, and time delaying by LT 2 : q GMSK(t) = { A q GMSK (t LT 2 ) for t [0, LT ) 0 elsewhere with A = + LT 2 q GMSK( t) d t LT 2 A practical value is L = g GMSK (t) BT=0.2 BT=0.3 BT= t/t
21 17 Casual phase response q GMSK (t) = t q GMSK( t ) d t qgmsk(t) BT=0.2 BT=0.3 BT= t/t
22 18 Phase tree of GMSK Power spectrum of GMSK
23 State and Trellis of CPM Let us consider the phase of a GMSK signal within some arbitrary signaling interval say [nt, (n + 1)T ). 1 2 q GMSK (t (n 3)T ) q GMSK (t nt ) q GMSK (t (n 1)T ) q GMSK (t (n 2)T ) (n 3)T (n 2)T (n 1)T nt (n + 1)T time We consider first the special case L = 3 as depicted above. For t [nt, (n + 1)T ), we can write: ϕ(t; α) = ϕ 0 + π α i q GMSK (t it ) i=0 n 3 = ϕ 0 + π i=0 α i n In the general case where L is arbitrary n L α i ϕ(t; α) = ϕ 0 + π 2 i=0 }{{} θ n + n 1 i=n (L 1) i=n 2 = ϕ ( t; α n, θ n, α n 1,..., α n (L 1) }{{} = ϕ(t; α n, S n ) for t [nt, (n + 1)T ) S n α i q GMSK (t it ) α i q(t it ) + α n q(t nt ) )
24 20 Thus, the behaviour of ϕ(t; α) in the signaling interval [nt, (n + 1)T ) is entirely determined by the (L + 1)-dimensional vector ( ) αn, θ n, α n 1,..., α }{{ n (L 1) } S n S with α n : current transmitted symbol S n : state of ϕ(t; α) in n-th signaling interval S : state space
25 21 State transitions (trellis) for GMSK with L = 3 Notice that θ n+1 = θ n + π 2 α n (L 1) α n = 1 S S n S n+1 α n = 1 (0, 1, 1) (0, 1, 1) (0, 1, 1) (0, 1, 1) (0, 1, 1) ( π 2, 1, 1) ( π 2, 1, 1) ( π 2, 1, 1) ( π 2, 1, 1) ( 2π 2 ( 2π 2 ( 2π 2 ( 2π 2 ( 3π 2 ( 3π 2 ( 3π 2 ( 3π 2, 1, 1), 1, 1), 1, 1), 1, 1), 1, 1), 1, 1), 1, 1), 1, 1) (0, 1, 1) (0, 1, 1) (0, 1, 1) ( π 2, 1, 1) ( π 2, 1, 1) ( π 2, 1, 1) ( π 2, 1, 1) ( 2π 2 ( 2π 2 ( 2π 2 ( 2π 2 ( 3π 2 ( 3π 2 ( 3π 2 ( 3π 2, 1, 1), 1, 1), 1, 1), 1, 1), 1, 1), 1, 1), 1, 1), 1, 1)
26 22 Phase behavior within one signaling interval as a function of the state transitions for GMSK S n ϕ(t; α n ; S n ) ( π 2, 1, 1) 2π ( 3π 2, 1, 1) (0, 1, 1) (0, 1, 1) 3 π 2 ( 2π 2 ( 3π 2, 1, 1), 1, 1) α m = +1 ( 3π 2, 1, 1) ( π 2, 1, 1) 2 π 2 α m = 1 ( 2π 2, 1, 1) ( 2π 2, 1, 1) (0, 1, 1) π 2 ( π 2, 1, 1) ( 3π 2, 1, 1) τ 0 nt (n + 1)T t Initialization ϕ 0 = θ 0 = 0 1 i= (L 1) α i q(t it ) where α 1,..., α (L 1) are known symbols
27 23 Implementation of a CPM transmitter with look-up tables A. Using a phase modulator α n Compute the phase state α n Look-up table S n (α n, s n ) ϕ(τ; α n, S n ) ϕ(τ; α n, S n ) Phase modulator f 0 x(t; α) B. Using an inphase/quadrature modulator Consider the inphase/quadrature representation of x(t; α), where we assume ϕ 0 = 0: x(t; α) = 2Es T s cos(2πf 0 t + ϕ(t; α)) = 2Es cos ϕ(t; α) cos(2πf 0 t) } T s {{} In-phase component 2Es T s sin ϕ(t; α) } {{ } Quadrature component sin(2πf 0 t)
28 α n Compute the phase state αn S n Look-up table (α n, S n ) cosϕ(τ; α n, S n ) Look-up table (α n, S n ) sinϕ(τ; α n, S n ) cosϕ(t; α n, S n ) cos(2πf 0 t) sinϕ(t; α n, S n ) sin(2πf 0 t) 2E s T x(t; α) 24
29 25 Phase state computation α n Compute the phase state S n α n 1 α n 2 α n T T.... T T α L 1 α L 1 ( n L ) α i i=0 mod4 for GMSK (L = 3): α n 1 α n 2 ( n 3 ) α n T T T α i α n 1 α n 2 i=0 mod4
30 Coherent Demodulation of CPM The initial state and the final state of the CPM transmitter are set to known states using the following procedure: Before transmitting the data, L known symbols are transmitted to drive the CPM transmitter into a known initial state. After transmitting the data, L known symbols are transmitted to to drive the CPM transmitter into a known final state. Block of transmitted symbols.... α 0 α N L 1 known symbols t = 0 N data symbols α L + 1 known symbols ML decoding for the AWGN channel Received signal: Y (t) = x(t; α) + W (t) X(t; α) Y (t) W (t) White Gaussian noise with spectral height N 0 2
31 27 ML estimation ˆα = argmax α A N { (N+L+1)T 0 y(t) x(t; α) dt } = argmax α A N { N+L n=0 (n+1)t nt y(t) x(t; α) dt } = argmax α A N { N+L [ (n+1)t n=0 nt y(t) cos ϕ(t; α n, S n ) cos(2πf 0 t) dt (n+1)t nt y(t) sin ϕ(t; α n, S n ) sin(2πf 0 t) dt ]}
32 28 ML receiver Bank of correlators y(t) cos(2πf 0 t) sin(2πf 0 t) (n+1)t nt (n+1)t nt ( )dt cosϕ(t; α n, S n ) α n Q S n S Bank of correlators ( )dt sinϕ(t; α n, S n ) α n Q S n S Viterbi algorithm with states S ˆα
33 29 Performance of MSK and GMSK Performace degradation of GMSK with respect to MSK
34 2 Modern Representation of CPM In the modern representation of CPM [4], the CPM transmitter is decomposed into a vector encoder with memory and a memoryless modulator. 30 u j { { x j } Vector } Memoryless x(t) = Encoder Modulator x j (t jt ) j=0 This modern representation of CPM has already been used in the description of minimum-shift keying (MSK) in the lecture notes for Digital Modulation I. (See therein.)
35 Initialization We assume that the CPM transmitter is initialized with admissible symbols. we select α 1 = α 2 =... = α (L 1) = (M 1) Notice that (M 1) is a symbol common to both alphabets corresponding to M odd and even. The phase of CPM is then ϕ(t; α) = ϕ 0 + 2πh j= (L 1) α j q(t jt ) where α = (α 0, α 1,...) is the sequence of information-bearing symbols. The transmitted CPM signal reads: x(t; α) = 2P cos(2πf 0 t + ϕ(t; α))
36 32 Without loss of generality, we assume that ϕ 0 is selected in such a way that ϕ(0; α) = 0. Thus we obtain ϕ 0 = 2πh 0 α j q( jt ) = 2πh = 2πh j= (L 1) L 1 j=0 L 1 j=1 = 2πh(M 1) α j q(jt ) α j q(jt ) L 1 j=0 q(jt )
37 The Reference Phase Trajectory We focus on the phase trajectory corresponding to the sequence α = ( (M 1), (M 1),... ) Inserting yields ϕ(t; α ) = ϕ 0 2πh(M 1) j= (L 1) q(t jt ) We investigate the behaviour of ϕ(t; α ) over each signaling interval [nt, (n + 1)T ). To this end, it is worth introducing the relative time variable τ [0, T ). The absolute time variable t within this signaling interval is related to τ according to t = nt + τ (i) Consider: n = 0, t = τ ϕ 0 (τ) = ϕ(τ, α ) = ϕ 0 2πh(M 1) 0 q(τ jt ) = ϕ 0 2πh(M 1) j= (L 1) L 1 (The index in ϕ 0 (τ) is the value of n.) j=0 q(τ + jt ) Inserting for ϕ 0, we obtain L 1 ϕ 0 (τ) = 2πh(M 1) (q(τ + jt ) q(jt )) j=0
38 34 L 1 ϕ 0 (τ) = 2πh(M 1) (q(τ + jt ) q(jt )) j=0 q(t) 1 2 q(t + τ) q(t ) q(2t + τ) q(2t ) L = 3 τ T T + τ 2T 2T + τ 3T t Notice that ϕ 0 (0) = 0 ϕ 0 (T ) = 2πh(M 1)q(LT ) = πh(m 1) Behavior of ϕ 0 (τ): ψ 0 (τ) T τ πh(m 1)
39 35 (ii) Consider: n = 1, t = T + τ ϕ 1 (τ) = ϕ(t + τ; α ) = ϕ 0 2πh(M 1) = ϕ 0 2πh(M 1) = ϕ 0 2πh(M 1) 1 j= (L 1) L 1 j= 1 q(τ + T jt ) q(τ + (j + 1)T ) L q(τ + jt ) j=0 L 1 = 2πh(M 1) q(τ + jt ) j=0 = πh(m 1) + ϕ 0 (τ) L 1 j=0 q(jt ) πh(m 1) (iii) Consider: n 1, t = nt + τ ϕ n (τ) = ϕ(nt + τ, α ) = ϕ 0 2πh(M 1) = ϕ 0 2πh(M 1) = ϕ 0 2πh(M 1) n j= (L 1) (L 1)+n j=0 L 1 j=0 = nπh(m 1) + ϕ 0 (τ) q(τ + nt jt ) q(τ + jt ) q(τ + jt ) + nπh(m 1)
40 36 ϕ(t; α) T 2T 3T nt (n + 1)T t πh(m 1) 2πh(M 1) πh(m 1) t T 3πh(M 1) ϕ(t; α ) nπh(m 1) ϕ0(τ) nπh(m 1) ϕ0(τ) 2πh(M 1) ϕ0(τ) πh(m 1) ϕ0(τ)
41 The Reference Frequency For the sake of simplifying the presentation we assume that ϕ(t; α ) = πh(m 1) t T or equivalently that ϕ 0 (τ) = πh(m 1) τ T In order for ϕ 0 (τ) to exhibit this behavior, q(t) must satisfy the condition 2πh(M 1) which holds if L 1 j=0 L 1 j=0 (q(τ + jt ) q(jt )) = πh(m 1) τ T (q(τ + jt ) q(jt )) = τ 2T Thus for α = α, the CPM signal transmitted reads x(t; α ) = 2P cos ( 2πf 0 t πh(m 1) t T ) (5) with = 2P cos(2πf 1 t) f 1 = f 0 h(m 1) 2T This frequency f 1 is the retained reference frequency with respect to which the phase of CPM is expressed. x(α) = ( 2P cos 2πf 1 t + ϕ(t; α) + πh(m 1) t ) }{{ T} φ(t; α)
42 The Tilted Phase and the New Symbols The so called tilted phase φ(t; α) reads φ(t; α) = ϕ(t; α) + πh(m 1) t T = ϕ 0 + 2πh α j q(t jt ) + πh(m 1) t T j= (L 1) We investigate the behavior of φ(t; α) within each signaling interval. (i) Consider: n = 0, t = τ [0, T ) φ 0 (τ; α) = φ(0 T + τ; α) = ϕ 0 + 2πh L 1 j=0 α j q(τ + jt ) + πh(m 1) τ T As we have (5) due to the assumption regarding ϕ 0 (τ), we conclude that Inserting yields L 1 τ T = 2 = 2 φ 0 (τ; α) = 2πh j=0 L 1 j=0 L 1 j=0 q(τ + jt ) 2 q(τ + jt ) L 1 j=0 q(jt ) [ πh(m 1)] 1ϕ0 α j q(τ + jt ) + 2πh(M 1) L 1( ) = 2πh α j + (M 1) q(τ + jt ) j=0 L 1 j=0 q(τ + jt )
43 39 We introduce the new information-bearing symbols U j = 2( 1 αj + (M 1) ) { } 0, 1,..., M 1 Notice that the new symbol alphabet is similar regardless of whether M is odd or even. Making use of these new symbols, we can recast φ 0 (τ; α) according to φ 0 (τ; α) = φ(τ; α) = 4πh L 1 j=0 U j q(τ + jt )
44 40 (ii) Consider: n 1, t = nt + τ φ n (τ; α) = φ(nt + τ; α) n = ϕ 0 + 2πh j= (L 1) + πh(m 1) nt + τ T = ϕ 0 + 2πh n+(l 1) j=0 α j q(τ + nt jt ) α n j q(τ + jt ) + πh(m 1)n + πh(m 1) τ T = ϕ 0 + 2πh = 4πh = 4πh = 4πh + 2πh L 1 j=0 L 1 j=0 L 1 j=0 L 1 j=0 n+(l 1) j=l α n j q(τ + jt ) + πh(m 1) τ T α n j 1 2 U n j q(τ + jt ) + πh U n j q(τ + jt ) + 2πh U n j q(τ + jt ) + 2πh + πh(m 1)n ( n L j= (L 1) n L j= (L 1) ( n L [ αj + (M 1) ]) U j j= (L 1) U j ) mod p 2 } {{ } V n Remember the definition of the modulation index: h = p 1 /p 2.
45 41 Let us define V n = ( n L U j ) j= (L 1) mod p 2 Then φ n (τ; α) = 4πh L 1 j=0 U n j q(τ + jt ) + 2πhV n = φ ( τ; U n, U n 1,... U n (L 1), V n ) The vector S n := ( ) U n 1,... U n (L 1), V n defines the state in the new description (modern description). (Cf. definition pf state in the traditional description.)
46 2.5 Block Diagram of the CPM Transmitter The previous discussions lead to the following block diagram. x(τ; un; sn) 2P 42 un cos(2πf1τ) Look-up table un 1 un 2 u n (L 2) un cos(φ(τ; un; Sn)) u n (L 1) vn vn T T... T T pa Look-up table u n (L 1) u n (L 2) un 2 sin(φ(τ; un; Sn)) un 1 sin(2πf1τ) un Encoder Memoryless modulator
47 43 Example: GMSK with L = 3 Tilted phase tree: φ(t; α)/π t/t Trajectories of φ ( τ; U n, S n ) : φ(τ; un, sn)/π τ/t
48 3 Laurent Representation of CPM CPM signals can be equivalently represented by a superposition of PAM signals [3]. In this section we use only the first term of this representation as a (fairly) good approximation of the CPM signal Minimum Shift Keying The MSK Signal The MSK signal is given by 2Eb ( ) x(t; α) = T cos 2πf 0 t + ϕ(t; α) with the information-bearing phase t [0, NT ). ϕ(t; α) = π N 1 n=0 α n q MSK (t nt ), The information symbols are { } α n 1, +1, n = 0,..., N 1. The phase pulse q MSK (t) has the following shape: q MSK (t) 1 2 T t
49 45 In the nth signaling interval, t [nt, nt + T ), t = nt + τ, τ [0, T ), we have n 1 α i ϕ n (τ; α) = π + π 2 2 i=0 }{{} θ n τ T α n. Remember that θ n is the phase at the beginning of the nth signaling interval. Notice that θ n {{ } 0, π for n even { π 2, } 3π 2 for n odd The initialization is θ 0 = 0.
50 46 In-phase and quadrature components of MSK Consider t [0, NT ). The MSK signal can be decomposed into its inphase and its quadrature components: Eb ( ) x(t; α) = T cos ϕ(t; α) 2 cos ( 2πf 0 t ) }{{} x I (t; α) Eb ( ) T sin ϕ(t; α) 2 sin ( 2πf 0 t ) }{{} x Q (t; α) Consider now the pulse p MSK (t) = { 1 T cos( πt 2T ) for t [ T, +T ], 0 elsewhere. It is normalized such that it has energy one, i.e., +T T ( p MSK (t)) 2dt = 1. p MSK (t) 1/ T T 0 T t
51 47 Using this pulse, the inphase component x I (t; α) and the quadrature component x Q (t; α) can be written as follows: x I (t; α) = = Eb ( ) T cos ϕ(t; α) N x 1,n p MSK (t nt ) n=0 n even x 1,n = E b cos (θ n ) { E b, + E b } x Q (t; α) = = Eb ( ) T sin ϕ(t; α) N x 2,n p MSK (t nt ) n=1 n odd x 2,n = E b sin (θ n ) { E b, + E b } The symbol α N is a known suffix symbol. The modulation symbols can thus be considered as twodimensional symbols ( ) X1,n X n = S X 2,n out of the signal constellation {( ) ( ) ( ) ( )} + Eb Eb 0 0 S =,, 0 0 +, E b E b }{{}}{{}}{{}}{{} s 1 s }{{ 2 s } 3 s }{{ 4 } n even n odd
52 48 Illustration of the signal constellation: s 3 n even s 2 s 1 s 4 n odd Example: Phase Trajectories Draw the phase and the trajectories of the inphase and quadrature components for the following example. n α n θ n cos θ n sin θ n 0 +1 θ 0 = 0(init) π π N 1 = 4 +1 π 1 0 Suffix N = 5 (+1) 3π (1)
53 49 Complex Representation The Vector X n = (X 1,n, X 2,n ) T can be conceived as the complex number X n = X 1,n + jx 2,n = E b exp(jθ n ) θ n = π 2 n 1 i=0 α i The (complex-valued) signal constellation is thus j s 3 s 2 1 s 1 1 j s 4 The values of the complex-valued modulation symbol can be recursively computed: X n = ( E b exp j π 2 n 1 i=0 α i ) ( = exp j π ) 2 α n 1 E ( b exp j π 2 = jα n 1 X n 1 n 2 i=0 α i )
54 50 Notice that ( exp j π ) 2 α n 1 = (j) α n 1 = jα n 1 as α n 1 { 1, +1}. Thus the MSK signal can be written as {[ N } 2 X(t; α) = R X n p MSK (t nt )] exp(j2πf0 t) for t [0, NT ). n=0 The initialization is X 0 = j α 1 X 1 = E b. This can be achieved by X 1 = j E b, α 1 = 1. Block Diagram α n T α n 1 jα n 1 x n p MSK (t) Re{ } x(t; α) j x n 1 T N δ(t nt ) 2 exp(j2πf0 t) n=0
55 Precoded MSK Precoding The information symbols are mapped from the {0, 1} representation to the {+1, 1} representation: u n α n u n 0 +1 α n 1 1 {0, 1} { 1, +1} The precoding can be done in both representations: u n u n u n α n α n T u n 1 u n 0 +1 α n α n α n T α n 1 Notice that u n 1 u n (addition in F 2 GF (2)) corresponds to α n 1 α n (multiplication in R). This justifies the particular mapping.
56 52 Complex Representation Transmitted symbols: X n = j(α n 1 α n 2 )X n 1, n = 0,..., N 1 Initialization: α 2 = α 1 = 1 X 1 = j E b The symbols are generated as follows: X n n 0 j j E b = E b = j 0 α 1 Eb 1 j α 0 α 1 j 0 α 1 Eb = j 1 α 0 Eb 2 j α 1 α 0 j 1 α 0 Eb = j 2 α 1 Eb 3 j α 2 α 1 j 2 α 1 Eb = j 3 α 2 Eb.. n j n α n 1 Eb This gives the block diagram of precoded MSK using the complex representation of the symbols: α n T α n 1 x n x(t; α) p MSK (t) Re{ } j n N δ(t nt ) n=0 2 exp(j2πf0 t)
57 53 Vector Representation n even: X n = (j) n E b α n 1 = (j 2 ) n 2 E b α n 1 = ( 1) n 2 Eb α n 1 (real-valued) ( ) X n = ( 1) n T 2 Eb α }{{ n 1, 0 }}{{} X n,1 X n,2 n odd: X n = (j) n E b α n 1 = j(j) n 1 E b α n 1 = j( 1) n 1 2 Eb α n 1 (imaginary-valued) ( n 1 ) T X n = }{{} 0, ( 1) 2 Eb α }{{ n 1 } X n,1 X n,2 This results in the following block diagram: 2 cos(2πf0 t) X n,1 p MSK (t) α n T α n 1 N δ(t nt ) n=0 X(t; α) t [0, 1] n even Eb ( 1) n 2 X n,2 p MSK (t) n odd nt 2 sin(2πf 0 t)
58 α n α n α n 1 T ( 1) n 2 n even n odd α n 1 T ( 1) n 2 Eb Eb nt nt Xn, 1 p MSK (t) N δ(t nt ) n=0 X n,2 p MSK (t) V n,1 x n,1 r n V n,2 x n,2 r n 2 cos(2πf0 t) 2 sin(2πf 0 t) Y n,1 Y n,2 Vector decoder X(t; α) t [0, 1] W (t) ˆα n 1 Y (t) 2 cos(2πf0 t) T p MSK (t) p MSK ( t) = p MSK (t) 0 2 sin(2πf 0 t) T p MSK (t) R pp (τ) = non-causal filter t r n = R pp (nt ) + nt E[V n,i V m,j ] = δ ij N 0 2 r m n Vector decoder p MSK (t)p MSK (t + τ)dt ˆα n 1 Demodulation in the AWGN Channel 54
59 55 The effective discrete-time impulse response is r n = R pp (nt ), R pp (τ) = p MSK (t) p MSK (t + τ) dt. The noise after sampling has the covariance (mean is zero) ] E [V n,i V M,j = δ i,j N 0 2 r m n. The optimum vector decoder for MSK can be simplified. To see this, consider the impulse response: r n = R pp r n = 1 for n = 0, r 1 for n = 1, 0 elsewhere. r n 2T T 0 T 2T n Thus, in the upper (lower) branch, symbols are effectively transmitted at even (odd) time indices.
60 56 Example for the upper branch: x n,1 x 0,1 T 2T 3T 4T 5T n x 2,1 x 4,1 x n,1 r n x 0,1 r 1 x 0,1 r 1 x 2,1 r 1 x 2,1 r 1 x 4,1 r 1 x 4,1 n x 2,1 x 4,1 Sampling time upper branch The optimum vector decoder for the AWGN channel can thus be described as follows. V n,1 X n,1 r n Y n,1 α n T α n 1 V n,2 Sign( ) ˆα n 1 X n,2 ( 1) n 2 Eb r n Y n,2 ( 1) n 2 nt Remark: More information about the discrete-time representation of QAM-like signals is provided in the appendix.
61 Precoded Gaussian MSK The lenght of the phase pulse is set to L = 3, as before. Precoded GMSK Signal The signal reads x(t; α) = 2Eb ( ) T cos 2πf 0 t + ϕ(t; α) with ϕ(t; α) = π N 1 n= 2 (α n α n 1 ) q GMSK (t nt ) + ϕ 0 where α n { 1, +1}; prefix symbols (GSM): α n = 1 for n = 3, 2, 1, sufffix symbols (GSM): α n = 1 for n = N, N + 1, N + 2 GMSK phase pulse q GMSK (t): q GMSK (t) t/t
62 58 ϕ 0 is set so that ϕ(0; α) = 0. Hence, ϕ 0 = π 2 n=1 q GMSK (nt ) Within the n-th signaling interval, i.e., for t [nt, nt + T ), n = 0,..., N 1. ϕ n (τ; α) = ϕ 0 + π n 3 (α i α i 1 ) 2 + i= 2 n i=n 2 (α i α i 1 ) q GMSK (τ) In-phase and Quadrature Components The signal can be decomposed as X(t; α) = Eb cos ϕ(t; α) 2 cos(2πf 0 t) } T {{} X I (t; α) Eb sin ϕ(t; α) 2 sin(2πf 0 t). } T {{} X Q (t; α)
63 59 The inphase component and the quadrature component can be approximated as follows: X I (t; α) N+2 n= 2 n even X 1,n p GMSK (t nt ) X 1,n = ( 1) n 2 E b α n 1 X Q (t; α) N+1 n= 1 n odd X 2,n p GMSK (t nt ) X 2,n = ( 1) n 2 E b α n 1 The pulse p GMSK (t) is often denoted as c 0 (t) pulse, referring to [3], and it is defined as follows. Let LT, L = 3, be the length of the truncated GMSK pulse q GMSK (t). Then c 0 (t) = s 0 (t) s 1 (t) s 2 (t) (for larger L, more pulses have to be multiplied) with ( ) s l (t) = sin φ(t + lt ) { π q GMSK (t) for t < LT φ(t) = π 2 π q GMSK(t) for t LT The resulting pulse c 0 (t) has length (L + 1)T = 4T.
64 60 The resulting pulse is depicted for L = 3: p GMSK (t) T 2T 3T 4T t
65 61 Block diagram of precoded GMSK Using the vector representation: 2 cos(2πf0 t) X n,1 p GMSK (t) α n T α n 1 N+2 n= 2 δ(t nt ) X(t; α) n even ( 1) n 2 Eb X n,2 p GMSK (t) n odd nt 2 sin(2πf 0 t) Using the complex representation: α n T α n 1 X n p GMSK (t) Re{ } x(t; α) j n Eb N+2 n= 2 δ(t nt ) 2exp(j2πf0 t) Initialization (prefix symbols): α 3 = α 2 = α 1 = 1, X 2 = j 2 α 3 Eb = E b. Termination (suffix symbols): α N = α N+1 = α N+2 = +1.
66 α n α n α n 1 T ( 1) n 2 n even n odd α n 1 T ( 1) n 2 Eb Eb nt nt X n,1 N+2 n= 2 X n,2 X n,1 X n,2 r n r n δ(t nt ) p GMSK (t) p GMSK (t) V n,1 V n,2 2 cos(2πf0 t) Vector decoder t [0, 1] W (t) {ˆα n } N 1 n=0 2 cos(2πf0 t) 2 sin(2πf 0 t) 2 sin(2πf 0 t) p GMSK (t) p GMSK (t) r n = R pp (nt ) R pp (τ) = LT 2 LT 2 nt Y n,1 Y n,2 Vector decoder p GMSK (t)p GMSK (t + τ)dt {ˆα n } N 1 n=0 Demodulation of precoded GMSK in the AWGN channel 62
67 63 The effective impulse response has the (deterministic) autocorrelation function: R pp (τ) = p GMSK (t) p GMSK (t + τ) dt R pp (τ) τ/t We have approximately r n = 1 for n = for n = 2 0 for n > 2 Hence, ISI occurs in each branch. For optimum decoding, the Viterbi algorithm (VA) may be applied.
68 64 (Close-to-optimum) Vector Decoder V n,1 0 n N + 2 n even nt X n,1 r n Two-state VA {ˆα n } N 1 n=0,n even α n T α n 1 V n,2 ˆα ( 1) n 2 Eb X n,2 r n Two-state VA {ˆα n } N 1 n=1,n odd nt 2 n N + 2 nt n odd 0 n N + 2 nt Metrics to be used in the upper-branch VA (even n): λ(α e ) = N 1 n=0 n even ( 1) n 2 E b α n 1 [y n r 1 ( 1) n 2 1 ] E b α n 3 Metrics to be used in the lower-branch VA (odd n): λ(α o ) = N 1 n=1 n odd ( 1) n 2 E b α n 1 [y n r 1 ( 1) n 2 1 ] E b α n 3
69 65 GSM Burst Structure Time slot 1 control bit 1 control bit Information bits (57) 3 Tail bits Training sequence (26) Normal burst Information bits (57) 8,25 guard bits 3 Tail bits Information bits (39) Training sequence (64) Information bits (39) 8,25 guard bits Synchronization burst
70 Modulation in EDGE Objective Modify the GSM format in order to increase the bit rate while keeping the spectrum requirement of this modulation scheme. Selected Solution Extend the signal space in the Laurent representation of GMSK 8PSK, i.e., 3 bits / symbol Include an additional rotation of the symbols rotation of 3π/8 in each signaling interval Signal Constellation and Mapping (0, 0, 0) Im (U 1, U 2, U 3 ) (0, 1, 0) (0, 1, 1) (0, 0, 1) (1, 1, 1) Re (1, 0, 1) (1, 0, 0) (1, 1, 0)
71 67 Phase Rotation Rotation by 3π 8 in each signaling interval Im Im 1 0 3π π Re 3 6 Re By comparison, for 8 PSK without such phase rotation: Im Im Re Re
72 68 Pulse Shaping p(t) = p GMSK (t) p GMSK (t) T 2T 3T 4T t EDGE Transmitter [U n,1, U n,2, U n,3 ] X n X(t; u) p GMSK (t) Re{ } exp(jn 3π 8 ) Eb N 1 δ(t nt ) n=0 2 exp(j2πf0 t)
73 69 EDGE Receiver Y (t) p GMSK (t) Y n Vector decoder [Ûn,1, Ûn,2, Ûn,3] 2 exp( j2πf0 t) nt Discrete-time Representation of the EDGE System [U n,1, U n,2, U n,3 ] X n r n Vector decoder V n [Ûn,1, Ûn,2, Ûn,3] exp(jn 3π 8 ) The effective impulse response is r n = R pp (nt ) R pp (τ) = LT p GMSK (t) p GMSK (t + τ) dt 0 The noise has the covariance ] E [V n V n+l = N 0 r l.
74 70 R pp (τ) τ/t Optimum Vector Decoder for EDGE For optimum vector decoding of EDGE in the AWGN channel, the Viterbi algorithm may be applied. The corresponding trellis has J = 8 2 = 64 states and 8 transitions per state. The branch metric is λ(u) = N 1 i=0 { ( R x n exp jn 3π 8 ) [ ( y n r 1 x n 1 exp j(n 1) 3π ( 8 r 2 X n 2 exp j(n 2) 3π )]} 8 )
75 71 Discrete-time Model Using the complex-valued representation, the discrete-time model of EDGE is give by the following block diagram: V n [U n,1, U n,2, U n,3 ] X n r n 64-state VA [Ûn,1, Ûn,2, Ûn,3] exp(jn 3π 8 ) The vector with information bits looks like [ [U0,1 ] [ ] ] U =, U 0,2, U 0,3,..., UN 1,1, U N 1,2, U N 1,3 Burst format of EDGE Time slot Tail Sym (3) Data symbols (57) Control sym (1) Training sequence (26) Control sym (1) Data symbols (57) Tail Sym (3) Guard symbols (8,25) Normal burst
76 72 4 Trellis-Coded Modulation 4.1 Motivation We consider the vector representation of a digital communication system transmitting across the AWGN channel. [U 0,..., U K 1 ] [X 0,..., X N 1 ] [Y 0,..., Y N 1 ] [Û0,..., ÛK 1] {0, 1} K Encoder Decoder {0, 1} K [W 0,..., W N 1 ] We restrict our attention to the case where the dimension of the signal constellation X = {S 0..., S M 1 } is one or two. Example: MPAM: dim X = 1 MPSK (M > 2) and QPAM : dim X = 2. 2-AM 4-PSK 8-PSK 4-AM 8-AM 8-AMPM 16-QASK 16-AM 32-AMPM 64-QASK
77 73 For these two cases, the vector channel is either of the form. dimx = 1 X j Y j W j N (0, N 0 2 ), W 0,..., W N 1 independent dimx = 2 X j1 Y j1 X j W j1 W j2 W j N (( ) ( )) 0 N0 /2 0, 0 0 N 0 /2 Y j X j2 Y j2 In both cases, the noise samples are independent.
78 74 Rate of the encoder The Encoder maps bit-blocks onto modulation symbols x X = { } s 0,..., s M 1. Its rate is R = K N bits/symbol Two equivalent necessary conditions for the encoder to be one-toone are 2 K M N R = K N log 2(M) In the case of uncoded modulation, we have N = 1, K = log 2 (M) R = log 2 (M) Bit Error Probability The BER is defined as P b = 1 K K 1 j=0 P [ ] U j Ûj
79 75 Capacity of the AWGN Channel With the constraint that the transmitted vectors belong to a finite signal constellation X = {s 1..., s M }: C X = max p(s 1 ),...,p(s M ) M p(s m ) m=1 ( p ( ) ( p ( ) ) y s m p(sm ) ) y s m log2 M m =1 p( ) dy y s m p(sm ) Remark The capacity C X depends on the signal constellation X. Dropping the restriction [ that X is finite while assuming a given average power E s = E X j 2], C := log 2 ( 1 + SNR ), SNR = E s N 0 The dimension of C is bit / transmitted symbol.
80 76 Tight lower bounds for the capacities of the signal constellations given on page 72: Channel Coding Theorem Provided R < C, P b can be made arbitrarily small by selecting appropriate encoders. In other words, reliable communication is possible at rates R < C. Converse of the Channel Coding Theorem If R > C, reliable communication is impossible.
81 77 Example: Some comparisons Uncoded 4 PSK: R = 2 bits/t P b = 10 5 at SNR = 12.9 db Coded 8 PSK: Remark: C = 2 bits/symbols at 5.9 db
82 78 Thus, with coded 8PSK it is theoretically possible to transmit reliably 2 bits/symbol at SNR = 5.9 db. Coding gain of coded 8PSK transmitting 2 bits/symbol versus uncoded 4PSK at BER = = 7 db Coding gain of coded digital transmission across the AWGN channel with no restriction on the signal constellation except the average transmitted power, transmitting (on average) 2 bits/symbol versus coded 4PSK at BER = 10 5 : = 8.2 db Similar figures for the above coding gains hold when other signal constellations are considered. Remark By doubling the number of vectors in a signal constellation X, containing 2 K vectors, almost all is achieved in terms of coding gain for reliable transmission of K bits/t versus uncoded transmission using the signal constellation X. (The transmission rates are the same!)
83 79 A way to realize the above coding gains by doubling the number of vectors in the signal constellation is as follows: U j,1 V j,1 U j,k.. Encoder with rate r = K K+1.. Vector mapping. {0, 1} K+1 X V j,k V j,k+1 X = 2 K+1 X j {0, 1} K {0, 1} K+1 X Open issues: 1. how to select the encoder, and 2. how to design the vector mapping, to obtain a scheme for which P b is small. For the encoder, block coding or convolutional coding may be used. In many schemes, convolutional codes are applied due to their low decoding complexity. (The Viterbi algorithm is applicable.) A schemes that consists of the combination of a convolutional encoder with a vector mapping device is called Trellis-Coded Modulation (TCM).
84 80 Block Diagram of a TCM Scheme U j,1 V j,1 U j,k... Convolutional Encoder r = K K+1 memory length ν V j,k V j,k+1 Vector mapping {0, 1} K+1 X X = 2 K+1 X j {0, 1} K {0, 1} K+1 X The overall rate is given by R = r log 2 (K + 1) = K Objective Find TCM schemes that achieve a good bit-error-rate performance. Example: Coded 8PSK U j,1 T T V j, X j U j,2 V j,2 V j,3 110 (V 3, V 2, V 1 ) The parameters are r = 2/3, ν = 2, R = 2/3 log 2 8 = 2.
85 Convolutional Codes Two examples of convolutional encoders. (See e.g. Proakis or Morelos-Zaragoza for a general description.) Example: 1 V j,1 U j,1 T T V j,2 U j,2 V j,3 Code rate: Memory length: r = number of input bits number of output bits = 2 3 ν = number of shift registers = 2 Trellis: States labels: (v 3, v 2, v 1 )
86 82 Example: 2 U j,1 T U j 1,1 U j,2 T U j 2,2 V j,1 V j,2 V j,3 Code rate: r = 2 3 Memory length: ν = 2 Trellis:
87 Goodness of a TCM Scheme Admissible sequences Let A denote the set of sequences (x 0, x 1,...) generated by a given TCM scheme. These sequences are called admissible for the considered TCM scheme. Example: 1 continued A A / {x j } = ( s 0, s 0, s 0, s 0, s 0,... ) {x j } = ( s 0, s 4, s 0, s 0, s 0,... ) {x j } = ( s 2, s 1, s 2, s 0, s 0,... ) { {x j } = ( s 0, s 5, s 3, s 2, s 0,... ) (2 2)E s 4 Es 3 (2 + 2)Es 2 2E s
88 84 Euclidean Distance Let {x j } and { x j} denote two sequences in A. The Euclidean distance between {x j } and {x j } is ( ) d {x j }, {x j} = ( ) 1/2 xj x 2 j j=0 Example: 1 continued ( ) d {x j }, {x j} ( ) d {x j }, {x j } = 4E s = 2 E s = (2 + (2 2) + 2 ) Es = E s Free Euclidean Distance The minimum Euclidean distance between pairs of admissible sequences of a TCM scheme is called the free Euclidean distance of the TCM scheme: ( ) d f = min d {x j }, {x j} {x j },{x j } A x j x j Example: 1 continued It can be shown that ( ) = d {x j }, {x j} d f = 2 E s
89 85 Probability of a Sequence Error Probability that the Viterbi decoder makes a wrong decision on the path in the trellis: ( df ) N(d f ) Q 2N0 P e where (i) Q(z) is the Gaussian error function Q(z) = z 1 exp { 12 } 2π u2 du (ii) N(d f ) is the average number of sequence pairs in A that have the Euclidean distance d f. Remark The above lower bound for P b is tight for high SNR. The reason is that in this case an erroneously detected path has a sequence likely to have an Euclidean distance to the true transmitted sequence equal to d f, when ML decoding is applied. Remember that given a finite observed sequence, {y j } = ( y0, y 1,..., y L 1 ), the Viterbi algorithm (which realizes the ML decoder) searches for the finite sequence generated by the trellis (with initial state 0) which minimizes L 1 j 0 y j x j 2
90 86 Optimality Criterion Optimality criterion for finding a vector mapping for a given convolutional code: Maximize the free Euclidean distance! TCM schemes maximizing the free Euclidean Distance among all TCM with a specified memory length are called optimal. The method proposed by Ungerboeck to identify good vector mapping given a certain convolutional encoder (or equivalently, given a certain trellis) relies on the technique of set partitioning.
91 Set Partitioning Example: 8PSK Es d 0 = (2 2)E s B B 1 v 1 sqrte s d 1 = 2E s C C 2 C 1 0 C 3 1 v 2 d 2 = 2 E s D D 4 D D 6 D D 5 D D 7 v Goals of set partitioning: 1. The subsets should be similar. 2. The points inside each subset should be maximally separated.
92 Trellis Coded Modulation General form of the encoding process: U j,1.... U j,k1 U j,k Convolutional Encoder r = K 1 N 1 V j, V j,n1 1 V j,n1 V j,n1 +1 Vector Mapping Select subset {1, 2,..., 2 N 1 } Select vector from subset X j V j,n U j,k {1, 2,..., 2 K K 1 } Remarks 1. Number of states in the trellis : 2 ν 2. Number of branches leaving each state : 2 K 1 3. Number of parallel branches in each transition : 2 K K 1
93 89 Example: 1 continued Parameters: K = 2, K 1 = 1, N 1 = 2, N = 3 V j, U j,1 T T U j,2 V j,2 V j, xj C 0 C 2 (0, 4) (2, 6) C 1 (1, 5) C 3 (3, 7) C 2 C 0 (2, 6) (0, 4) C 3 (3, 7) C 1 (1, 5) 5
94 90 Rules for the Assignments Experimentally inferred rules for assigning the signal vectors to the transitions: 1. All vectors in X are used with the same frequency. 2. The vectors assigned to branches originating from or merging to the same state belong to the same subset at level Vectors with maximum Euclidean distances are assigned to parallel branches. Remarks Rule 1 guarantees that the trellis code has a regular structure. Rule 2 and Rule 3 guarantee that the minimum distance between paths in the trellis which diverge from any state and re-emerge later exceeds the free Euclidean distance of the uncoded modulation scheme. Example: 1 continued (d f ) 2 coded 8PSK = 4E s 2E s = (d f ) 2 uncoded 4PSK
95 91 Example: 2 continued Consider the following trellis code: U j,1 T U j 1,1 U j,2 T U j 2,2 V j, V j, V j, X j Despite the fact that this trellis code has no parallel branches, its free Euclidean distance is smaller than that of the trellis code of Example 1. (See Exercise 4.1).
96 Examples for TCM In the following, some examples of specific TCM schemes are given and their error probabililites are discussed.
97 93 TCM with 8PSK and 2 bits/t
98 94 Implementation
99 95 Probability of error-event and of bit-error
100 96
101 97 TCM with 16QAM and 3 bits/t Set Partitioning
102 98
103 99 Error event probability
104 100 CCITT V.32 standard CCITT V.32 standard for 9.6 Kbit/s and 14.4 bit/s modems. Convolutional Coder The code is designed to guarantee invariance to phase rotations of ±π/2 and π. These values are the phase ambiguities which result when a phase-locked loop (PLL) is employed for carrierphase estimation.
105 101 Mapping
106 102 A ECB Representation of a Band- Pass Signal Band-pass signals can equivalently be represented as complexvalued base-band signals. This is often called the equivalent complex base-band (ECB) representation. This concept is discussed in more detail in the following.
107 103
108 X n,1 X n,2 1 2T N δ(t nt ) n=0 Assumption: p(f) B 1 T 1/T 1 2T p(t) p(t) f 0 1 2T 1 T s i t T 1 T s i t T X 1 (t) 2 cos(2πf0 t) 2 sin(2πf 0 t) X 2 (t) X n,1 r n r n X(t) W (t) Y (t) V n,1 V n,2 Y n,1 X n,2 Y n,2 2 cos(2πf0 t) 1 T s i t T 2 sin(2πf 0 t) 1 T s i t T p( t) p( t) nt Y n,1 = r n X n,1 + V n,1 Y n,2 = r n X n,2 + V n,2 Y n,1 Y n,2 A.1 The Block diagram 104
109 105 Complex discrete-time representation: X n = X n,1 + jx n,2 V n Y n = Y n,1 + jy n,2 X n r n Yn Y n = r n X n + V n V n = V n,1 + jv n,2
110 106 A.2 The Signal Consider a real-valued BP signal: x(t) = x 1 (t) 2 cos(2πf 0 t) x 2 (t) 2 sin(2πf 0 t) [x1 ][ = R{ (t) + jx 2 (t) 2 cos(2πf0 t) + j ] } 2 sin(2πf }{{} 0 t) = x(t) { = R x(t) 2 exp(j2πf 0 t) } {{} 2 exp(j2πf0 t) } The signal x(t) is a complex-valued LP signal, and it is called the ECB representation of x(t). The spectra X(f) = F { } x(t) { } X(f) = F x(t) are related by X(f) = 2 [ S(f f0 ) + S( f f 0 )] 2 The energies of the signals are E s = E s
111 107 A.3 Effect of QA Mod/Demod on Signal x(t) = x 1 (t) 2 cos(2πf 0 t) x 2 (t) 2 sin(2πf 0 t) x 1 (t) = i x i,1 δ(t it ) p(t) x 2 (t) = i x i,2 δ(t it ) p(t) Assumption: p(t) is a LP signal, i.e., its Fourier transform P (f) = F{p(t)} has the property Tricks: In-phase component: P (f) = 0 for f > f 0 2 cos 2 x = 1 + cos 2x 2 sin 2 x = 1 cos 2x 2 sin x cos x = sin 2x z 1 (t) = x(t) 2 cos(2πf 0 t) p( t) [ ] = x 1 (t) 2 cos 2 (2πf 0 t) x }{{} 2 (t) 2 sin(2πf 0 t) cos(2πf 0 t) p( t) }{{} 1 + cos(4πf 0 t) sin(4πf 0 t) [ ] = x 1 (t) p( t) + x 1 (t) cos(4πf 0 t) x 2 (t) sin(4πf 0 t) p( t) }{{}}{{} BP LP }{{} = 0
112 108 z 1 (t) = x 1 (t) p( t) = i = i x i,1 δ(t it ) p(t) p( t) }{{} = R p (t) x i,1 R p (t it ) After sampling: z 1,n = z 1 (nt ) = i x i,1 R p (nt it ) }{{} R p ( (n i)t ) = rn i = i x i,1 r n i = x 1,n r n r n = R p (nt ) Quadrature component: (...similar calculations...) z n,2 = z 2 (nt ) = X n,2 r n
113 x 1 (t) A A x 2 (t) x 1 (t) 2cos(2πf 0 t)...cos(2πf 0 t) A A/2 A A/2 x 2 (t)( 2)sin(2πf 0 t) A 2 2 x 1 (t) 2cos(2πf 0 t) + x 2 (t)( 2)sin(2πf 0 t) A A/2 2f 0 f 0 f 0 2f 0 ja 2 2 A A A/2 A/2...( 2)sin(2πf 0 t) p LP (t) A A...p LP (t) 109
114 110 A.4 Effect of QA Demodulation on Noise Block Diagram 2cos(2πf0 t) Z 1 (t) p( t) Y 1 (t) Y 1 (nt ) = Y n,1 W (t) Z 2 (t) p( t) Y 2 (t) Y 2 (nt ) = Y n,2 2sin(2πf0 t) w(t): WGN with S w (f) = N 0 2 Noise before LP filtering Z 1 (t) = W (t) 2 cos(2πf 0 t) E [ Z 1 (t) Z 1 (t + τ) ] = = E [ W (t)w (t + τ) ] ( 2) 2 cos ( 2πf }{{} 0 t ) cos ( 2πf 0 (t + τ) ) = N 0 2 δ(τ) = N 0 2 δ(τ) 2 cos2 (2πf 0 t) }{{} 1 + cos(4πf 0 t) = N 0 2 δ(τ) + N 0 2 δ(τ) cos(4πf 0t) = R Z1 (τ; t) }{{} time-variant past Time-variant (periodic) auto-correlation function
115 111 Noise after LP filtering Assumption: p(t) is a LP signal, i.e., its Fourier transform P (f) = F{p(t)} has the property P (f) = 0 for f > f 0 Autocorrelation function of Y 1 (t): [ ] E Y 1 (t)y 1 (t + τ) Y 1 (t) = W (t) 2 cos(2πf 0 t) p(t) = = E[ W (t s) 2 cos ( 2πf 0 (t s) ) p(s)ds W (t + τ s ) 2 cos ( 2πf 0 (t + τ s ) ) ] p(s )ds [ ] = E } w(t s) w(t + τ s ) {{} N 0 2 δ(τ s + s) 2 cos ( 2πf 0 (t s) ) cos ( 2πf 0 (t + τ s ) ) p(s) p(s ) ds ds Integrate w.r.t. s 0 for τ s = s s = τ + s = N 0 2 cos 2( 2πf 0 (t s) ) p(s) p(τ + s) ds 2 }{{} 1 + cos ( 4πf 0 (t s) ) = N 0 2 R p(τ) + N 0 2 cos ( 4πf 0 (t s) ) p(s) p(τ + s) ds }{{} = cos ( 4πf 0 (t τ) ) p(τ) p( τ)
116 112 [ ] E Y 1 (t) Y 1 (t + τ) = N 0 2 R p(τ) + N 0 2 cos ( 4πf 0 (t s) ) p(s) p(τ + s) ds } {{ } (1) R p (τ) = p(τ) p( τ) (1) = [ cos ( 4πf 0 (t τ) ) ] p(τ) p( τ) (6) The Fourier transform w.r.t. τ of cos ( 4πf 0 (t τ) ) = cos ( 4πf 0 (τ t) ) = cos ( 4πf 0 τ ) δ(τ t) is 1 [ ] δ(f 2f 0 ) + δ(f + 2f 0 ) exp( j2πf t) = 2 = 1 [ ] δ(f 2f 0 ) exp( j4πf 0 t) + δ(f + 2f 0 ) exp(j4πf 0 t) 2 = (3) Consider the Fourier transform w.r.t. τ of (6): [ ] (2) = (3) P (f) P ( f) = 1 [ P (f 2f 0 ) exp( j4πf 0 t) 2 ] + P (f + 2f 0 ) exp(j4πf 0 t) P ( f) = 0 because P (f) = 0 for f > f 0 according to the assumption.
117 113 [ ] E Y 1 (t) Y 1 (t + τ) }{{} R Y1 (τ) = N 0 2 R p(τ) R Y1 (τ) = N 0 2 R p(τ) A.5 Noise After LP Filtering and Sampling R Y1 (kt ) = N 0 2 R p(kt ) }{{} = r k = N 0 2 r k
Digital Modulation 1
 Digital Modulation 1 Lecture Notes Ingmar Land and Bernard H. Fleury Navigation and Communications () Department of Electronic Systems Aalborg University, DK Version: February 5, 27 i Contents I Basic
Digital Modulation 1 Lecture Notes Ingmar Land and Bernard H. Fleury Navigation and Communications () Department of Electronic Systems Aalborg University, DK Version: February 5, 27 i Contents I Basic
Digital Band-pass Modulation PROF. MICHAEL TSAI 2011/11/10
 Digital Band-pass Modulation PROF. MICHAEL TSAI 211/11/1 Band-pass Signal Representation a t g t General form: 2πf c t + φ t g t = a t cos 2πf c t + φ t Envelope Phase Envelope is always non-negative,
Digital Band-pass Modulation PROF. MICHAEL TSAI 211/11/1 Band-pass Signal Representation a t g t General form: 2πf c t + φ t g t = a t cos 2πf c t + φ t Envelope Phase Envelope is always non-negative,
Signal Design for Band-Limited Channels
 Wireless Information Transmission System Lab. Signal Design for Band-Limited Channels Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal
Wireless Information Transmission System Lab. Signal Design for Band-Limited Channels Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal
This examination consists of 11 pages. Please check that you have a complete copy. Time: 2.5 hrs INSTRUCTIONS
 THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 6 December 2006 This examination consists of
THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 6 December 2006 This examination consists of
that efficiently utilizes the total available channel bandwidth W.
 Signal Design for Band-Limited Channels Wireless Information Transmission System Lab. Institute of Communications Engineering g National Sun Yat-sen University Introduction We consider the problem of signal
Signal Design for Band-Limited Channels Wireless Information Transmission System Lab. Institute of Communications Engineering g National Sun Yat-sen University Introduction We consider the problem of signal
A Family of Nyquist Filters Based on Generalized Raised-Cosine Spectra
 Proc. Biennial Symp. Commun. (Kingston, Ont.), pp. 3-35, June 99 A Family of Nyquist Filters Based on Generalized Raised-Cosine Spectra Nader Sheikholeslami Peter Kabal Department of Electrical Engineering
Proc. Biennial Symp. Commun. (Kingston, Ont.), pp. 3-35, June 99 A Family of Nyquist Filters Based on Generalized Raised-Cosine Spectra Nader Sheikholeslami Peter Kabal Department of Electrical Engineering
BASICS OF DETECTION AND ESTIMATION THEORY
 BASICS OF DETECTION AND ESTIMATION THEORY 83050E/158 In this chapter we discuss how the transmitted symbols are detected optimally from a noisy received signal (observation). Based on these results, optimal
BASICS OF DETECTION AND ESTIMATION THEORY 83050E/158 In this chapter we discuss how the transmitted symbols are detected optimally from a noisy received signal (observation). Based on these results, optimal
A First Course in Digital Communications
 A First Course in Digital Communications Ha H. Nguyen and E. Shwedyk February 9 A First Course in Digital Communications 1/46 Introduction There are benefits to be gained when M-ary (M = 4 signaling methods
A First Course in Digital Communications Ha H. Nguyen and E. Shwedyk February 9 A First Course in Digital Communications 1/46 Introduction There are benefits to be gained when M-ary (M = 4 signaling methods
Direct-Sequence Spread-Spectrum
 Chapter 3 Direct-Sequence Spread-Spectrum In this chapter we consider direct-sequence spread-spectrum systems. Unlike frequency-hopping, a direct-sequence signal occupies the entire bandwidth continuously.
Chapter 3 Direct-Sequence Spread-Spectrum In this chapter we consider direct-sequence spread-spectrum systems. Unlike frequency-hopping, a direct-sequence signal occupies the entire bandwidth continuously.
Data Detection for Controlled ISI. h(nt) = 1 for n=0,1 and zero otherwise.
 Data Detection for Controlled ISI *Symbol by symbol suboptimum detection For the duobinary signal pulse h(nt) = 1 for n=0,1 and zero otherwise. The samples at the output of the receiving filter(demodulator)
Data Detection for Controlled ISI *Symbol by symbol suboptimum detection For the duobinary signal pulse h(nt) = 1 for n=0,1 and zero otherwise. The samples at the output of the receiving filter(demodulator)
1 1 0, g Exercise 1. Generator polynomials of a convolutional code, given in binary form, are g
 Exercise Generator polynomials of a convolutional code, given in binary form, are g 0, g 2 0 ja g 3. a) Sketch the encoding circuit. b) Sketch the state diagram. c) Find the transfer function TD. d) What
Exercise Generator polynomials of a convolutional code, given in binary form, are g 0, g 2 0 ja g 3. a) Sketch the encoding circuit. b) Sketch the state diagram. c) Find the transfer function TD. d) What
SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land
 SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land Ingmar Land, SIPCom8-1: Information Theory and Coding (2005 Spring) p.1 Overview Basic Concepts of Channel Coding Block Codes I:
SIPCom8-1: Information Theory and Coding Linear Binary Codes Ingmar Land Ingmar Land, SIPCom8-1: Information Theory and Coding (2005 Spring) p.1 Overview Basic Concepts of Channel Coding Block Codes I:
Square Root Raised Cosine Filter
 Wireless Information Transmission System Lab. Square Root Raised Cosine Filter Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal design
Wireless Information Transmission System Lab. Square Root Raised Cosine Filter Institute of Communications Engineering National Sun Yat-sen University Introduction We consider the problem of signal design
Power Spectral Density of Digital Modulation Schemes
 Digital Communication, Continuation Course Power Spectral Density of Digital Modulation Schemes Mikael Olofsson Emil Björnson Department of Electrical Engineering ISY) Linköping University, SE-581 83 Linköping,
Digital Communication, Continuation Course Power Spectral Density of Digital Modulation Schemes Mikael Olofsson Emil Björnson Department of Electrical Engineering ISY) Linköping University, SE-581 83 Linköping,
5. Pilot Aided Modulations. In flat fading, if we have a good channel estimate of the complex gain gt, ( ) then we can perform coherent detection.
 5. Pilot Aided Modulations In flat fading, if we have a good channel estimate of the complex gain gt, ( ) then we can perform coherent detection. Obtaining a good estimate is difficult. As we have seen,
5. Pilot Aided Modulations In flat fading, if we have a good channel estimate of the complex gain gt, ( ) then we can perform coherent detection. Obtaining a good estimate is difficult. As we have seen,
Digital Communications
 Digital Communications Chapter 5 Carrier and Symbol Synchronization Po-Ning Chen, Professor Institute of Communications Engineering National Chiao-Tung University, Taiwan Digital Communications Ver 218.7.26
Digital Communications Chapter 5 Carrier and Symbol Synchronization Po-Ning Chen, Professor Institute of Communications Engineering National Chiao-Tung University, Taiwan Digital Communications Ver 218.7.26
a) Find the compact (i.e. smallest) basis set required to ensure sufficient statistics.
 Digital Modulation and Coding Tutorial-1 1. Consider the signal set shown below in Fig.1 a) Find the compact (i.e. smallest) basis set required to ensure sufficient statistics. b) What is the minimum Euclidean
Digital Modulation and Coding Tutorial-1 1. Consider the signal set shown below in Fig.1 a) Find the compact (i.e. smallest) basis set required to ensure sufficient statistics. b) What is the minimum Euclidean
Chapter 7: Channel coding:convolutional codes
 Chapter 7: : Convolutional codes University of Limoges meghdadi@ensil.unilim.fr Reference : Digital communications by John Proakis; Wireless communication by Andreas Goldsmith Encoder representation Communication
Chapter 7: : Convolutional codes University of Limoges meghdadi@ensil.unilim.fr Reference : Digital communications by John Proakis; Wireless communication by Andreas Goldsmith Encoder representation Communication
LECTURE 16 AND 17. Digital signaling on frequency selective fading channels. Notes Prepared by: Abhishek Sood
 ECE559:WIRELESS COMMUNICATION TECHNOLOGIES LECTURE 16 AND 17 Digital signaling on frequency selective fading channels 1 OUTLINE Notes Prepared by: Abhishek Sood In section 2 we discuss the receiver design
ECE559:WIRELESS COMMUNICATION TECHNOLOGIES LECTURE 16 AND 17 Digital signaling on frequency selective fading channels 1 OUTLINE Notes Prepared by: Abhishek Sood In section 2 we discuss the receiver design
This examination consists of 10 pages. Please check that you have a complete copy. Time: 2.5 hrs INSTRUCTIONS
 THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 08 December 2009 This examination consists of
THE UNIVERSITY OF BRITISH COLUMBIA Department of Electrical and Computer Engineering EECE 564 Detection and Estimation of Signals in Noise Final Examination 08 December 2009 This examination consists of
Digital Communications
 Digital Communications Chapter 9 Digital Communications Through Band-Limited Channels Po-Ning Chen, Professor Institute of Communications Engineering National Chiao-Tung University, Taiwan Digital Communications:
Digital Communications Chapter 9 Digital Communications Through Band-Limited Channels Po-Ning Chen, Professor Institute of Communications Engineering National Chiao-Tung University, Taiwan Digital Communications:
Generalize from CPFSK to continuous phase modulation (CPM) by allowing: non-rectangular frequency pulses frequency pulses with durations LT, L > 1
 8.3 Generalize to CPM [P4.3.3] 8.3-8.3. CPM Signals Generalize from CPFSK to continuous phase modulation (CPM) by allowing: non-rectangular frequency pulses frequency pulses with durations LT, L > o Example:
8.3 Generalize to CPM [P4.3.3] 8.3-8.3. CPM Signals Generalize from CPFSK to continuous phase modulation (CPM) by allowing: non-rectangular frequency pulses frequency pulses with durations LT, L > o Example:
ECE6604 PERSONAL & MOBILE COMMUNICATIONS. Week 3. Flat Fading Channels Envelope Distribution Autocorrelation of a Random Process
 1 ECE6604 PERSONAL & MOBILE COMMUNICATIONS Week 3 Flat Fading Channels Envelope Distribution Autocorrelation of a Random Process 2 Multipath-Fading Mechanism local scatterers mobile subscriber base station
1 ECE6604 PERSONAL & MOBILE COMMUNICATIONS Week 3 Flat Fading Channels Envelope Distribution Autocorrelation of a Random Process 2 Multipath-Fading Mechanism local scatterers mobile subscriber base station
Modulation & Coding for the Gaussian Channel
 Modulation & Coding for the Gaussian Channel Trivandrum School on Communication, Coding & Networking January 27 30, 2017 Lakshmi Prasad Natarajan Dept. of Electrical Engineering Indian Institute of Technology
Modulation & Coding for the Gaussian Channel Trivandrum School on Communication, Coding & Networking January 27 30, 2017 Lakshmi Prasad Natarajan Dept. of Electrical Engineering Indian Institute of Technology
3. ESTIMATION OF SIGNALS USING A LEAST SQUARES TECHNIQUE
 3. ESTIMATION OF SIGNALS USING A LEAST SQUARES TECHNIQUE 3.0 INTRODUCTION The purpose of this chapter is to introduce estimators shortly. More elaborated courses on System Identification, which are given
3. ESTIMATION OF SIGNALS USING A LEAST SQUARES TECHNIQUE 3.0 INTRODUCTION The purpose of this chapter is to introduce estimators shortly. More elaborated courses on System Identification, which are given
EE6604 Personal & Mobile Communications. Week 15. OFDM on AWGN and ISI Channels
 EE6604 Personal & Mobile Communications Week 15 OFDM on AWGN and ISI Channels 1 { x k } x 0 x 1 x x x N- 2 N- 1 IDFT X X X X 0 1 N- 2 N- 1 { X n } insert guard { g X n } g X I n { } D/A ~ si ( t) X g X
EE6604 Personal & Mobile Communications Week 15 OFDM on AWGN and ISI Channels 1 { x k } x 0 x 1 x x x N- 2 N- 1 IDFT X X X X 0 1 N- 2 N- 1 { X n } insert guard { g X n } g X I n { } D/A ~ si ( t) X g X
EE401: Advanced Communication Theory
 EE401: Advanced Communication Theory Professor A. Manikas Chair of Communications and Array Processing Imperial College London Introductory Concepts Prof. A. Manikas (Imperial College) EE.401: Introductory
EE401: Advanced Communication Theory Professor A. Manikas Chair of Communications and Array Processing Imperial College London Introductory Concepts Prof. A. Manikas (Imperial College) EE.401: Introductory
EE303: Communication Systems
 EE303: Communication Systems Professor A. Manikas Chair of Communications and Array Processing Imperial College London Introductory Concepts Prof. A. Manikas (Imperial College) EE303: Introductory Concepts
EE303: Communication Systems Professor A. Manikas Chair of Communications and Array Processing Imperial College London Introductory Concepts Prof. A. Manikas (Imperial College) EE303: Introductory Concepts
Consider a 2-D constellation, suppose that basis signals =cosine and sine. Each constellation symbol corresponds to a vector with two real components
 TUTORIAL ON DIGITAL MODULATIONS Part 3: 4-PSK [2--26] Roberto Garello, Politecnico di Torino Free download (for personal use only) at: www.tlc.polito.it/garello Quadrature modulation Consider a 2-D constellation,
TUTORIAL ON DIGITAL MODULATIONS Part 3: 4-PSK [2--26] Roberto Garello, Politecnico di Torino Free download (for personal use only) at: www.tlc.polito.it/garello Quadrature modulation Consider a 2-D constellation,
EE4061 Communication Systems
 EE4061 Communication Systems Week 11 Intersymbol Interference Nyquist Pulse Shaping 0 c 2015, Georgia Institute of Technology (lect10 1) Intersymbol Interference (ISI) Tx filter channel Rx filter a δ(t-nt)
EE4061 Communication Systems Week 11 Intersymbol Interference Nyquist Pulse Shaping 0 c 2015, Georgia Institute of Technology (lect10 1) Intersymbol Interference (ISI) Tx filter channel Rx filter a δ(t-nt)
Carrier frequency estimation. ELEC-E5410 Signal processing for communications
 Carrier frequency estimation ELEC-E54 Signal processing for communications Contents. Basic system assumptions. Data-aided DA: Maximum-lielihood ML estimation of carrier frequency 3. Data-aided: Practical
Carrier frequency estimation ELEC-E54 Signal processing for communications Contents. Basic system assumptions. Data-aided DA: Maximum-lielihood ML estimation of carrier frequency 3. Data-aided: Practical
8 PAM BER/SER Monte Carlo Simulation
 xercise.1 8 PAM BR/SR Monte Carlo Simulation - Simulate a 8 level PAM communication system and calculate bit and symbol error ratios (BR/SR). - Plot the calculated and simulated SR and BR curves. - Plot
xercise.1 8 PAM BR/SR Monte Carlo Simulation - Simulate a 8 level PAM communication system and calculate bit and symbol error ratios (BR/SR). - Plot the calculated and simulated SR and BR curves. - Plot
Es e j4φ +4N n. 16 KE s /N 0. σ 2ˆφ4 1 γ s. p(φ e )= exp 1 ( 2πσ φ b cos N 2 φ e 0
 Problem 6.15 : he received signal-plus-noise vector at the output of the matched filter may be represented as (see (5-2-63) for example) : r n = E s e j(θn φ) + N n where θ n =0,π/2,π,3π/2 for QPSK, and
Problem 6.15 : he received signal-plus-noise vector at the output of the matched filter may be represented as (see (5-2-63) for example) : r n = E s e j(θn φ) + N n where θ n =0,π/2,π,3π/2 for QPSK, and
Trellis Coded Modulation
 Trellis Coded Modulation Trellis coded modulation (TCM) is a marriage between codes that live on trellises and signal designs We have already seen that trellises are the preferred way to view convolutional
Trellis Coded Modulation Trellis coded modulation (TCM) is a marriage between codes that live on trellises and signal designs We have already seen that trellises are the preferred way to view convolutional
EE4304 C-term 2007: Lecture 17 Supplemental Slides
 EE434 C-term 27: Lecture 17 Supplemental Slides D. Richard Brown III Worcester Polytechnic Institute, Department of Electrical and Computer Engineering February 5, 27 Geometric Representation: Optimal
EE434 C-term 27: Lecture 17 Supplemental Slides D. Richard Brown III Worcester Polytechnic Institute, Department of Electrical and Computer Engineering February 5, 27 Geometric Representation: Optimal
Lecture 7: Wireless Channels and Diversity Advanced Digital Communications (EQ2410) 1
 Wireless : Wireless Advanced Digital Communications (EQ2410) 1 Thursday, Feb. 11, 2016 10:00-12:00, B24 1 Textbook: U. Madhow, Fundamentals of Digital Communications, 2008 1 / 15 Wireless Lecture 1-6 Equalization
Wireless : Wireless Advanced Digital Communications (EQ2410) 1 Thursday, Feb. 11, 2016 10:00-12:00, B24 1 Textbook: U. Madhow, Fundamentals of Digital Communications, 2008 1 / 15 Wireless Lecture 1-6 Equalization
EE4512 Analog and Digital Communications Chapter 4. Chapter 4 Receiver Design
 Chapter 4 Receiver Design Chapter 4 Receiver Design Probability of Bit Error Pages 124-149 149 Probability of Bit Error The low pass filtered and sampled PAM signal results in an expression for the probability
Chapter 4 Receiver Design Chapter 4 Receiver Design Probability of Bit Error Pages 124-149 149 Probability of Bit Error The low pass filtered and sampled PAM signal results in an expression for the probability
Introduction to Convolutional Codes, Part 1
 Introduction to Convolutional Codes, Part 1 Frans M.J. Willems, Eindhoven University of Technology September 29, 2009 Elias, Father of Coding Theory Textbook Encoder Encoder Properties Systematic Codes
Introduction to Convolutional Codes, Part 1 Frans M.J. Willems, Eindhoven University of Technology September 29, 2009 Elias, Father of Coding Theory Textbook Encoder Encoder Properties Systematic Codes
Digital Transmission Methods S
 Digital ransmission ethods S-7.5 Second Exercise Session Hypothesis esting Decision aking Gram-Schmidt method Detection.K.K. Communication Laboratory 5//6 Konstantinos.koufos@tkk.fi Exercise We assume
Digital ransmission ethods S-7.5 Second Exercise Session Hypothesis esting Decision aking Gram-Schmidt method Detection.K.K. Communication Laboratory 5//6 Konstantinos.koufos@tkk.fi Exercise We assume
Summary II: Modulation and Demodulation
 Summary II: Modulation and Demodulation Instructor : Jun Chen Department of Electrical and Computer Engineering, McMaster University Room: ITB A1, ext. 0163 Email: junchen@mail.ece.mcmaster.ca Website:
Summary II: Modulation and Demodulation Instructor : Jun Chen Department of Electrical and Computer Engineering, McMaster University Room: ITB A1, ext. 0163 Email: junchen@mail.ece.mcmaster.ca Website:
CHANNEL CAPACITY CALCULATIONS FOR M ARY N DIMENSIONAL SIGNAL SETS
 THE UNIVERSITY OF SOUTH AUSTRALIA SCHOOL OF ELECTRONIC ENGINEERING CHANNEL CAPACITY CALCULATIONS FOR M ARY N DIMENSIONAL SIGNAL SETS Philip Edward McIllree, B.Eng. A thesis submitted in fulfilment of the
THE UNIVERSITY OF SOUTH AUSTRALIA SCHOOL OF ELECTRONIC ENGINEERING CHANNEL CAPACITY CALCULATIONS FOR M ARY N DIMENSIONAL SIGNAL SETS Philip Edward McIllree, B.Eng. A thesis submitted in fulfilment of the
Summary: ISI. No ISI condition in time. II Nyquist theorem. Ideal low pass filter. Raised cosine filters. TX filters
 UORIAL ON DIGIAL MODULAIONS Part 7: Intersymbol interference [last modified: 200--23] Roberto Garello, Politecnico di orino Free download at: www.tlc.polito.it/garello (personal use only) Part 7: Intersymbol
UORIAL ON DIGIAL MODULAIONS Part 7: Intersymbol interference [last modified: 200--23] Roberto Garello, Politecnico di orino Free download at: www.tlc.polito.it/garello (personal use only) Part 7: Intersymbol
EE5713 : Advanced Digital Communications
 EE5713 : Advanced Digital Communications Week 12, 13: Inter Symbol Interference (ISI) Nyquist Criteria for ISI Pulse Shaping and Raised-Cosine Filter Eye Pattern Equalization (On Board) 20-May-15 Muhammad
EE5713 : Advanced Digital Communications Week 12, 13: Inter Symbol Interference (ISI) Nyquist Criteria for ISI Pulse Shaping and Raised-Cosine Filter Eye Pattern Equalization (On Board) 20-May-15 Muhammad
NORWEGIAN UNIVERSITY OF SCIENCE AND TECHNOLOGY DEPARTMENT OF ELECTRONICS AND TELECOMMUNICATIONS
 page 1 of 5 (+ appendix) NORWEGIAN UNIVERSITY OF SCIENCE AND TECHNOLOGY DEPARTMENT OF ELECTRONICS AND TELECOMMUNICATIONS Contact during examination: Name: Magne H. Johnsen Tel.: 73 59 26 78/930 25 534
page 1 of 5 (+ appendix) NORWEGIAN UNIVERSITY OF SCIENCE AND TECHNOLOGY DEPARTMENT OF ELECTRONICS AND TELECOMMUNICATIONS Contact during examination: Name: Magne H. Johnsen Tel.: 73 59 26 78/930 25 534
5 Analog carrier modulation with noise
 5 Analog carrier modulation with noise 5. Noisy receiver model Assume that the modulated signal x(t) is passed through an additive White Gaussian noise channel. A noisy receiver model is illustrated in
5 Analog carrier modulation with noise 5. Noisy receiver model Assume that the modulated signal x(t) is passed through an additive White Gaussian noise channel. A noisy receiver model is illustrated in
ECE 564/645 - Digital Communications, Spring 2018 Midterm Exam #1 March 22nd, 7:00-9:00pm Marston 220
 ECE 564/645 - Digital Communications, Spring 08 Midterm Exam # March nd, 7:00-9:00pm Marston 0 Overview The exam consists of four problems for 0 points (ECE 564) or 5 points (ECE 645). The points for each
ECE 564/645 - Digital Communications, Spring 08 Midterm Exam # March nd, 7:00-9:00pm Marston 0 Overview The exam consists of four problems for 0 points (ECE 564) or 5 points (ECE 645). The points for each
ρ = sin(2π ft) 2π ft To find the minimum value of the correlation, we set the derivative of ρ with respect to f equal to zero.
 Problem 5.1 : The correlation of the two signals in binary FSK is: ρ = sin(π ft) π ft To find the minimum value of the correlation, we set the derivative of ρ with respect to f equal to zero. Thus: ϑρ
Problem 5.1 : The correlation of the two signals in binary FSK is: ρ = sin(π ft) π ft To find the minimum value of the correlation, we set the derivative of ρ with respect to f equal to zero. Thus: ϑρ
Lecture 12. Block Diagram
 Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
Lecture 12 Goals Be able to encode using a linear block code Be able to decode a linear block code received over a binary symmetric channel or an additive white Gaussian channel XII-1 Block Diagram Data
RADIO SYSTEMS ETIN15. Lecture no: Equalization. Ove Edfors, Department of Electrical and Information Technology
 RADIO SYSTEMS ETIN15 Lecture no: 8 Equalization Ove Edfors, Department of Electrical and Information Technology Ove.Edfors@eit.lth.se Contents Inter-symbol interference Linear equalizers Decision-feedback
RADIO SYSTEMS ETIN15 Lecture no: 8 Equalization Ove Edfors, Department of Electrical and Information Technology Ove.Edfors@eit.lth.se Contents Inter-symbol interference Linear equalizers Decision-feedback
Performance of small signal sets
 42 Chapter 5 Performance of small signal sets In this chapter, we show how to estimate the performance of small-to-moderate-sized signal constellations on the discrete-time AWGN channel. With equiprobable
42 Chapter 5 Performance of small signal sets In this chapter, we show how to estimate the performance of small-to-moderate-sized signal constellations on the discrete-time AWGN channel. With equiprobable
Kevin Buckley a i. communication. information source. modulator. encoder. channel. encoder. information. demodulator decoder. C k.
 Kevin Buckley - -4 ECE877 Information Theory & Coding for Digital Communications Villanova University ECE Department Prof. Kevin M. Buckley Lecture Set Review of Digital Communications, Introduction to
Kevin Buckley - -4 ECE877 Information Theory & Coding for Digital Communications Villanova University ECE Department Prof. Kevin M. Buckley Lecture Set Review of Digital Communications, Introduction to
CONTINUOUS phase modulation (CPM) [1] is a
![CONTINUOUS phase modulation (CPM) [1] is a CONTINUOUS phase modulation (CPM) [1] is a](/thumbs/71/66218915.jpg) 1 Timing, Carrier, and Frame Synchronization of Burst-Mode CPM Ehsan Hosseini, Student Member, IEEE, and Erik Perrins, Senior Member, IEEE arxiv:131.757v3 [cs.it] 3 Jan 1 Abstract In this paper, we propose
1 Timing, Carrier, and Frame Synchronization of Burst-Mode CPM Ehsan Hosseini, Student Member, IEEE, and Erik Perrins, Senior Member, IEEE arxiv:131.757v3 [cs.it] 3 Jan 1 Abstract In this paper, we propose
Digital Baseband Systems. Reference: Digital Communications John G. Proakis
 Digital Baseband Systems Reference: Digital Communications John G. Proais Baseband Pulse Transmission Baseband digital signals - signals whose spectrum extend down to or near zero frequency. Model of the
Digital Baseband Systems Reference: Digital Communications John G. Proais Baseband Pulse Transmission Baseband digital signals - signals whose spectrum extend down to or near zero frequency. Model of the
EE456 Digital Communications
 EE456 Digital Communications Professor Ha Nguyen September 5 EE456 Digital Communications Block Diagram of Binary Communication Systems m ( t { b k } b k = s( t b = s ( t k m ˆ ( t { bˆ } k r( t Bits in
EE456 Digital Communications Professor Ha Nguyen September 5 EE456 Digital Communications Block Diagram of Binary Communication Systems m ( t { b k } b k = s( t b = s ( t k m ˆ ( t { bˆ } k r( t Bits in
ENSC327 Communications Systems 2: Fourier Representations. Jie Liang School of Engineering Science Simon Fraser University
 ENSC327 Communications Systems 2: Fourier Representations Jie Liang School of Engineering Science Simon Fraser University 1 Outline Chap 2.1 2.5: Signal Classifications Fourier Transform Dirac Delta Function
ENSC327 Communications Systems 2: Fourier Representations Jie Liang School of Engineering Science Simon Fraser University 1 Outline Chap 2.1 2.5: Signal Classifications Fourier Transform Dirac Delta Function
Figure 1.1 (a) Model of a communication system, and (b) signal processing functions.
 . Introduction to Signals and Operations Model of a Communication System [] Figure. (a) Model of a communication system, and (b) signal processing functions. Classification of Signals. Continuous-time
. Introduction to Signals and Operations Model of a Communication System [] Figure. (a) Model of a communication system, and (b) signal processing functions. Classification of Signals. Continuous-time
Decision-Point Signal to Noise Ratio (SNR)
 Decision-Point Signal to Noise Ratio (SNR) Receiver Decision ^ SNR E E e y z Matched Filter Bound error signal at input to decision device Performance upper-bound on ISI channels Achieved on memoryless
Decision-Point Signal to Noise Ratio (SNR) Receiver Decision ^ SNR E E e y z Matched Filter Bound error signal at input to decision device Performance upper-bound on ISI channels Achieved on memoryless
Impact of channel-state information on coded transmission over fading channels with diversity reception
 Impact of channel-state information on coded transmission over fading channels with diversity reception Giorgio Taricco Ezio Biglieri Giuseppe Caire September 4, 1998 Abstract We study the synergy between
Impact of channel-state information on coded transmission over fading channels with diversity reception Giorgio Taricco Ezio Biglieri Giuseppe Caire September 4, 1998 Abstract We study the synergy between
Weiyao Lin. Shanghai Jiao Tong University. Chapter 5: Digital Transmission through Baseband slchannels Textbook: Ch
 Principles of Communications Weiyao Lin Shanghai Jiao Tong University Chapter 5: Digital Transmission through Baseband slchannels Textbook: Ch 10.1-10.5 2009/2010 Meixia Tao @ SJTU 1 Topics to be Covered
Principles of Communications Weiyao Lin Shanghai Jiao Tong University Chapter 5: Digital Transmission through Baseband slchannels Textbook: Ch 10.1-10.5 2009/2010 Meixia Tao @ SJTU 1 Topics to be Covered
EE 661: Modulation Theory Solutions to Homework 6
 EE 66: Modulation Theory Solutions to Homework 6. Solution to problem. a) Binary PAM: Since 2W = 4 KHz and β = 0.5, the minimum T is the solution to (+β)/(2t ) = W = 2 0 3 Hz. Thus, we have the maximum
EE 66: Modulation Theory Solutions to Homework 6. Solution to problem. a) Binary PAM: Since 2W = 4 KHz and β = 0.5, the minimum T is the solution to (+β)/(2t ) = W = 2 0 3 Hz. Thus, we have the maximum
Solutions to Selected Problems
 Solutions to Selected Problems from Madhow: Fundamentals of Digital Communication and from Johannesson & Zigangirov: Fundamentals of Convolutional Coding Saif K. Mohammed Department of Electrical Engineering
Solutions to Selected Problems from Madhow: Fundamentals of Digital Communication and from Johannesson & Zigangirov: Fundamentals of Convolutional Coding Saif K. Mohammed Department of Electrical Engineering
Summary: SER formulation. Binary antipodal constellation. Generic binary constellation. Constellation gain. 2D constellations
 TUTORIAL ON DIGITAL MODULATIONS Part 8a: Error probability A [2011-01-07] 07] Roberto Garello, Politecnico di Torino Free download (for personal use only) at: www.tlc.polito.it/garello 1 Part 8a: Error
TUTORIAL ON DIGITAL MODULATIONS Part 8a: Error probability A [2011-01-07] 07] Roberto Garello, Politecnico di Torino Free download (for personal use only) at: www.tlc.polito.it/garello 1 Part 8a: Error
Convolutional Codes ddd, Houshou Chen. May 28, 2012
 Representation I, II Representation III, IV trellis of Viterbi decoding Turbo codes Convolutional Codes ddd, Houshou Chen Department of Electrical Engineering National Chung Hsing University Taichung,
Representation I, II Representation III, IV trellis of Viterbi decoding Turbo codes Convolutional Codes ddd, Houshou Chen Department of Electrical Engineering National Chung Hsing University Taichung,
Constellation Shaping for Communication Channels with Quantized Outputs
 Constellation Shaping for Communication Channels with Quantized Outputs Chandana Nannapaneni, Matthew C. Valenti, and Xingyu Xiang Lane Department of Computer Science and Electrical Engineering West Virginia
Constellation Shaping for Communication Channels with Quantized Outputs Chandana Nannapaneni, Matthew C. Valenti, and Xingyu Xiang Lane Department of Computer Science and Electrical Engineering West Virginia
Introduction to Probability and Stochastic Processes I
 Introduction to Probability and Stochastic Processes I Lecture 3 Henrik Vie Christensen vie@control.auc.dk Department of Control Engineering Institute of Electronic Systems Aalborg University Denmark Slides
Introduction to Probability and Stochastic Processes I Lecture 3 Henrik Vie Christensen vie@control.auc.dk Department of Control Engineering Institute of Electronic Systems Aalborg University Denmark Slides
Principles of Communications Lecture 8: Baseband Communication Systems. Chih-Wei Liu 劉志尉 National Chiao Tung University
 Principles of Communications Lecture 8: Baseband Communication Systems Chih-Wei Liu 劉志尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.tw Outlines Introduction Line codes Effects of filtering Pulse
Principles of Communications Lecture 8: Baseband Communication Systems Chih-Wei Liu 劉志尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.tw Outlines Introduction Line codes Effects of filtering Pulse
Revision of Lecture 4
 Revision of Lecture 4 We have discussed all basic components of MODEM Pulse shaping Tx/Rx filter pair Modulator/demodulator Bits map symbols Discussions assume ideal channel, and for dispersive channel
Revision of Lecture 4 We have discussed all basic components of MODEM Pulse shaping Tx/Rx filter pair Modulator/demodulator Bits map symbols Discussions assume ideal channel, and for dispersive channel
ω 0 = 2π/T 0 is called the fundamental angular frequency and ω 2 = 2ω 0 is called the
 he ime-frequency Concept []. Review of Fourier Series Consider the following set of time functions {3A sin t, A sin t}. We can represent these functions in different ways by plotting the amplitude versus
he ime-frequency Concept []. Review of Fourier Series Consider the following set of time functions {3A sin t, A sin t}. We can represent these functions in different ways by plotting the amplitude versus
Communications and Signal Processing Spring 2017 MSE Exam
 Communications and Signal Processing Spring 2017 MSE Exam Please obtain your Test ID from the following table. You must write your Test ID and name on each of the pages of this exam. A page with missing
Communications and Signal Processing Spring 2017 MSE Exam Please obtain your Test ID from the following table. You must write your Test ID and name on each of the pages of this exam. A page with missing
Introduction to Binary Convolutional Codes [1]
![Introduction to Binary Convolutional Codes [1] Introduction to Binary Convolutional Codes [1]](/thumbs/81/82925569.jpg) Introduction to Binary Convolutional Codes [1] Yunghsiang S. Han Graduate Institute of Communication Engineering, National Taipei University Taiwan E-mail: yshan@mail.ntpu.edu.tw Y. S. Han Introduction
Introduction to Binary Convolutional Codes [1] Yunghsiang S. Han Graduate Institute of Communication Engineering, National Taipei University Taiwan E-mail: yshan@mail.ntpu.edu.tw Y. S. Han Introduction
Physical Layer and Coding
 Physical Layer and Coding Muriel Médard Professor EECS Overview A variety of physical media: copper, free space, optical fiber Unified way of addressing signals at the input and the output of these media:
Physical Layer and Coding Muriel Médard Professor EECS Overview A variety of physical media: copper, free space, optical fiber Unified way of addressing signals at the input and the output of these media:
Analog Electronics 2 ICS905
 Analog Electronics 2 ICS905 G. Rodriguez-Guisantes Dépt. COMELEC http://perso.telecom-paristech.fr/ rodrigez/ens/cycle_master/ November 2016 2/ 67 Schedule Radio channel characteristics ; Analysis and
Analog Electronics 2 ICS905 G. Rodriguez-Guisantes Dépt. COMELEC http://perso.telecom-paristech.fr/ rodrigez/ens/cycle_master/ November 2016 2/ 67 Schedule Radio channel characteristics ; Analysis and
Chapter 10. Timing Recovery. March 12, 2008
 Chapter 10 Timing Recovery March 12, 2008 b[n] coder bit/ symbol transmit filter, pt(t) Modulator Channel, c(t) noise interference form other users LNA/ AGC Demodulator receive/matched filter, p R(t) sampler
Chapter 10 Timing Recovery March 12, 2008 b[n] coder bit/ symbol transmit filter, pt(t) Modulator Channel, c(t) noise interference form other users LNA/ AGC Demodulator receive/matched filter, p R(t) sampler
Timing Recovery at Low SNR Cramer-Rao bound, and outperforming the PLL
 T F T I G E O R G A I N S T I T U T E O H E O F E A L P R O G R ESS S A N D 1 8 8 5 S E R V L O G Y I C E E C H N O Timing Recovery at Low SNR Cramer-Rao bound, and outperforming the PLL Aravind R. Nayak
T F T I G E O R G A I N S T I T U T E O H E O F E A L P R O G R ESS S A N D 1 8 8 5 S E R V L O G Y I C E E C H N O Timing Recovery at Low SNR Cramer-Rao bound, and outperforming the PLL Aravind R. Nayak
Rapport technique #INRS-EMT Exact Expression for the BER of Rectangular QAM with Arbitrary Constellation Mapping
 Rapport technique #INRS-EMT-010-0604 Exact Expression for the BER of Rectangular QAM with Arbitrary Constellation Mapping Leszek Szczeciński, Cristian González, Sonia Aïssa Institut National de la Recherche
Rapport technique #INRS-EMT-010-0604 Exact Expression for the BER of Rectangular QAM with Arbitrary Constellation Mapping Leszek Szczeciński, Cristian González, Sonia Aïssa Institut National de la Recherche
Detecting Parametric Signals in Noise Having Exactly Known Pdf/Pmf
 Detecting Parametric Signals in Noise Having Exactly Known Pdf/Pmf Reading: Ch. 5 in Kay-II. (Part of) Ch. III.B in Poor. EE 527, Detection and Estimation Theory, # 5c Detecting Parametric Signals in Noise
Detecting Parametric Signals in Noise Having Exactly Known Pdf/Pmf Reading: Ch. 5 in Kay-II. (Part of) Ch. III.B in Poor. EE 527, Detection and Estimation Theory, # 5c Detecting Parametric Signals in Noise
Digital Communications: A Discrete-Time Approach M. Rice. Errata. Page xiii, first paragraph, bare witness should be bear witness
 Digital Communications: A Discrete-Time Approach M. Rice Errata Foreword Page xiii, first paragraph, bare witness should be bear witness Page xxi, last paragraph, You know who you. should be You know who
Digital Communications: A Discrete-Time Approach M. Rice Errata Foreword Page xiii, first paragraph, bare witness should be bear witness Page xxi, last paragraph, You know who you. should be You know who
E2.5 Signals & Linear Systems. Tutorial Sheet 1 Introduction to Signals & Systems (Lectures 1 & 2)
 E.5 Signals & Linear Systems Tutorial Sheet 1 Introduction to Signals & Systems (Lectures 1 & ) 1. Sketch each of the following continuous-time signals, specify if the signal is periodic/non-periodic,
E.5 Signals & Linear Systems Tutorial Sheet 1 Introduction to Signals & Systems (Lectures 1 & ) 1. Sketch each of the following continuous-time signals, specify if the signal is periodic/non-periodic,
TSKS01 Digital Communication Lecture 1
 TSKS01 Digital Communication Lecture 1 Introduction, Repetition, and Noise Modeling Emil Björnson Department of Electrical Engineering (ISY) Division of Communication Systems Emil Björnson Course Director
TSKS01 Digital Communication Lecture 1 Introduction, Repetition, and Noise Modeling Emil Björnson Department of Electrical Engineering (ISY) Division of Communication Systems Emil Björnson Course Director
2. SPECTRAL ANALYSIS APPLIED TO STOCHASTIC PROCESSES
 2. SPECTRAL ANALYSIS APPLIED TO STOCHASTIC PROCESSES 2.0 THEOREM OF WIENER- KHINTCHINE An important technique in the study of deterministic signals consists in using harmonic functions to gain the spectral
2. SPECTRAL ANALYSIS APPLIED TO STOCHASTIC PROCESSES 2.0 THEOREM OF WIENER- KHINTCHINE An important technique in the study of deterministic signals consists in using harmonic functions to gain the spectral
Residual Versus Suppressed-Carrier Coherent Communications
 TDA Progress Report -7 November 5, 996 Residual Versus Suppressed-Carrier Coherent Communications M. K. Simon and S. Million Communications and Systems Research Section This article addresses the issue
TDA Progress Report -7 November 5, 996 Residual Versus Suppressed-Carrier Coherent Communications M. K. Simon and S. Million Communications and Systems Research Section This article addresses the issue
EE538 Final Exam Fall :20 pm -5:20 pm PHYS 223 Dec. 17, Cover Sheet
 EE538 Final Exam Fall 005 3:0 pm -5:0 pm PHYS 3 Dec. 17, 005 Cover Sheet Test Duration: 10 minutes. Open Book but Closed Notes. Calculators ARE allowed!! This test contains five problems. Each of the five
EE538 Final Exam Fall 005 3:0 pm -5:0 pm PHYS 3 Dec. 17, 005 Cover Sheet Test Duration: 10 minutes. Open Book but Closed Notes. Calculators ARE allowed!! This test contains five problems. Each of the five
Error Correction Methods
 Technologies and Services on igital Broadcasting (7) Error Correction Methods "Technologies and Services of igital Broadcasting" (in Japanese, ISBN4-339-06-) is published by CORONA publishing co., Ltd.
Technologies and Services on igital Broadcasting (7) Error Correction Methods "Technologies and Services of igital Broadcasting" (in Japanese, ISBN4-339-06-) is published by CORONA publishing co., Ltd.
Iterative Timing Recovery
 Iterative Timing Recovery John R. Barry School of Electrical and Computer Engineering, Georgia Tech Atlanta, Georgia U.S.A. barry@ece.gatech.edu 0 Outline Timing Recovery Tutorial Problem statement TED:
Iterative Timing Recovery John R. Barry School of Electrical and Computer Engineering, Georgia Tech Atlanta, Georgia U.S.A. barry@ece.gatech.edu 0 Outline Timing Recovery Tutorial Problem statement TED:
Principles of Communications
 Principles of Communications Chapter V: Representation and Transmission of Baseband Digital Signal Yongchao Wang Email: ychwang@mail.xidian.edu.cn Xidian University State Key Lab. on ISN November 18, 2012
Principles of Communications Chapter V: Representation and Transmission of Baseband Digital Signal Yongchao Wang Email: ychwang@mail.xidian.edu.cn Xidian University State Key Lab. on ISN November 18, 2012
Decoding the Tail-Biting Convolutional Codes with Pre-Decoding Circular Shift
 Decoding the Tail-Biting Convolutional Codes with Pre-Decoding Circular Shift Ching-Yao Su Directed by: Prof. Po-Ning Chen Department of Communications Engineering, National Chiao-Tung University July
Decoding the Tail-Biting Convolutional Codes with Pre-Decoding Circular Shift Ching-Yao Su Directed by: Prof. Po-Ning Chen Department of Communications Engineering, National Chiao-Tung University July
ELEC546 Review of Information Theory
 ELEC546 Review of Information Theory Vincent Lau 1/1/004 1 Review of Information Theory Entropy: Measure of uncertainty of a random variable X. The entropy of X, H(X), is given by: If X is a discrete random
ELEC546 Review of Information Theory Vincent Lau 1/1/004 1 Review of Information Theory Entropy: Measure of uncertainty of a random variable X. The entropy of X, H(X), is given by: If X is a discrete random
Convolutional Codes. Telecommunications Laboratory. Alex Balatsoukas-Stimming. Technical University of Crete. November 6th, 2008
 Convolutional Codes Telecommunications Laboratory Alex Balatsoukas-Stimming Technical University of Crete November 6th, 2008 Telecommunications Laboratory (TUC) Convolutional Codes November 6th, 2008 1
Convolutional Codes Telecommunications Laboratory Alex Balatsoukas-Stimming Technical University of Crete November 6th, 2008 Telecommunications Laboratory (TUC) Convolutional Codes November 6th, 2008 1
Communication Theory Summary of Important Definitions and Results
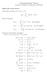 Signal and system theory Convolution of signals x(t) h(t) = y(t): Fourier Transform: Communication Theory Summary of Important Definitions and Results X(ω) = X(ω) = y(t) = X(ω) = j x(t) e jωt dt, 0 Properties
Signal and system theory Convolution of signals x(t) h(t) = y(t): Fourier Transform: Communication Theory Summary of Important Definitions and Results X(ω) = X(ω) = y(t) = X(ω) = j x(t) e jωt dt, 0 Properties
PUNCTURED 8-PSK TURBO-TCM TRANSMISSIONS USING RECURSIVE SYSTEMATIC CONVOLUTIONAL GF ( 2 N ) ENCODERS
 19th European Signal Processing Conference (EUSIPCO 2011) Barcelona, Spain, August 29 - September 2, 2011 PUCTURED 8-PSK TURBO-TCM TRASMISSIOS USIG RECURSIVE SYSTEMATIC COVOLUTIOAL GF ( 2 ) ECODERS Calin
19th European Signal Processing Conference (EUSIPCO 2011) Barcelona, Spain, August 29 - September 2, 2011 PUCTURED 8-PSK TURBO-TCM TRASMISSIOS USIG RECURSIVE SYSTEMATIC COVOLUTIOAL GF ( 2 ) ECODERS Calin
Maximum Likelihood Sequence Detection
 1 The Channel... 1.1 Delay Spread... 1. Channel Model... 1.3 Matched Filter as Receiver Front End... 4 Detection... 5.1 Terms... 5. Maximum Lielihood Detection of a Single Symbol... 6.3 Maximum Lielihood
1 The Channel... 1.1 Delay Spread... 1. Channel Model... 1.3 Matched Filter as Receiver Front End... 4 Detection... 5.1 Terms... 5. Maximum Lielihood Detection of a Single Symbol... 6.3 Maximum Lielihood
Continuous Wave Data Analysis: Fully Coherent Methods
 Continuous Wave Data Analysis: Fully Coherent Methods John T. Whelan School of Gravitational Waves, Warsaw, 3 July 5 Contents Signal Model. GWs from rotating neutron star............ Exercise: JKS decomposition............
Continuous Wave Data Analysis: Fully Coherent Methods John T. Whelan School of Gravitational Waves, Warsaw, 3 July 5 Contents Signal Model. GWs from rotating neutron star............ Exercise: JKS decomposition............
Correlator I. Basics. Chapter Introduction. 8.2 Digitization Sampling. D. Anish Roshi
 Chapter 8 Correlator I. Basics D. Anish Roshi 8.1 Introduction A radio interferometer measures the mutual coherence function of the electric field due to a given source brightness distribution in the sky.
Chapter 8 Correlator I. Basics D. Anish Roshi 8.1 Introduction A radio interferometer measures the mutual coherence function of the electric field due to a given source brightness distribution in the sky.
3.2 Complex Sinusoids and Frequency Response of LTI Systems
 3. Introduction. A signal can be represented as a weighted superposition of complex sinusoids. x(t) or x[n]. LTI system: LTI System Output = A weighted superposition of the system response to each complex
3. Introduction. A signal can be represented as a weighted superposition of complex sinusoids. x(t) or x[n]. LTI system: LTI System Output = A weighted superposition of the system response to each complex
Chapter 4: Continuous channel and its capacity
 meghdadi@ensil.unilim.fr Reference : Elements of Information Theory by Cover and Thomas Continuous random variable Gaussian multivariate random variable AWGN Band limited channel Parallel channels Flat
meghdadi@ensil.unilim.fr Reference : Elements of Information Theory by Cover and Thomas Continuous random variable Gaussian multivariate random variable AWGN Band limited channel Parallel channels Flat
Example: Bipolar NRZ (non-return-to-zero) signaling
 Baseand Data Transmission Data are sent without using a carrier signal Example: Bipolar NRZ (non-return-to-zero signaling is represented y is represented y T A -A T : it duration is represented y BT. Passand
Baseand Data Transmission Data are sent without using a carrier signal Example: Bipolar NRZ (non-return-to-zero signaling is represented y is represented y T A -A T : it duration is represented y BT. Passand
1.4 Unit Step & Unit Impulse Functions
 1.4 Unit Step & Unit Impulse Functions 1.4.1 The Discrete-Time Unit Impulse and Unit-Step Sequences Unit Impulse Function: δ n = ቊ 0, 1, n 0 n = 0 Figure 1.28: Discrete-time Unit Impulse (sample) 1 [n]
1.4 Unit Step & Unit Impulse Functions 1.4.1 The Discrete-Time Unit Impulse and Unit-Step Sequences Unit Impulse Function: δ n = ቊ 0, 1, n 0 n = 0 Figure 1.28: Discrete-time Unit Impulse (sample) 1 [n]
Lecture 15: Thu Feb 28, 2019
 Lecture 15: Thu Feb 28, 2019 Announce: HW5 posted Lecture: The AWGN waveform channel Projecting temporally AWGN leads to spatially AWGN sufficiency of projection: irrelevancy theorem in waveform AWGN:
Lecture 15: Thu Feb 28, 2019 Announce: HW5 posted Lecture: The AWGN waveform channel Projecting temporally AWGN leads to spatially AWGN sufficiency of projection: irrelevancy theorem in waveform AWGN:
Coding on a Trellis: Convolutional Codes
 .... Coding on a Trellis: Convolutional Codes Telecommunications Laboratory Alex Balatsoukas-Stimming Technical University of Crete November 6th, 2008 Telecommunications Laboratory (TUC) Coding on a Trellis:
.... Coding on a Trellis: Convolutional Codes Telecommunications Laboratory Alex Balatsoukas-Stimming Technical University of Crete November 6th, 2008 Telecommunications Laboratory (TUC) Coding on a Trellis:
Coding theory: Applications
 INF 244 a) Textbook: Lin and Costello b) Lectures (Tu+Th 12.15-14) covering roughly Chapters 1,9-12, and 14-18 c) Weekly exercises: For your convenience d) Mandatory problem: Programming project (counts
INF 244 a) Textbook: Lin and Costello b) Lectures (Tu+Th 12.15-14) covering roughly Chapters 1,9-12, and 14-18 c) Weekly exercises: For your convenience d) Mandatory problem: Programming project (counts
