Pareto Curves for Probabilistic Model Checking
|
|
|
- Charlotte Stone
- 6 years ago
- Views:
Transcription
1 Pareto Curves for Probabilistic odel Checking Vojtěch Forejt, arta Kwiatkowska, and David Parker 2 Department of Computer Science, University of Oxford, UK 2 School of Computer Science, University of Birmingham, UK Abstract. ulti-objective probabilistic model checking provides a way to verify several, possibly conflicting, quantitative properties of a stochastic system. It has useful applications in controller synthesis and compositional probabilistic verification. However, existing methods are based on linear programming, which limits the scale of systems that can be analysed and makes verification of time-bounded properties very difficult. We present a novel approach that addresses both of these shortcomings, based on the generation of successive approximations of the Pareto curve for a multi-objective model checking problem. We illustrate dramatic improvements in efficiency on a large set of benchmarks and show how the ability to visualise Pareto curves significantly enhances the quality of results obtained from current probabilistic verification tools. Introduction Probabilistic model checking is an automated technique for verifying systems that exhibit stochastic behaviour. This arises due to, for example, failures in physical components, unreliable communication media or randomisation. Systems are typically modelled as arkov chains or arkov decision processes (DPs), and probabilistic temporal logics are used to specify quantitative properties to be verified such as the probability of a message packet being lost is less than 0.05 or the expected energy consumption is at most 00 mj. It is often necessary to incorporate nondeterminism into system models, to represent, for example, the actions of an external controller or the order in which a scheduler chooses to interleave system components running in parallel. In these cases, systems are usually modelled as DPs. Each possible way of resolving the nondeterminism in an DP is represented by an adversary (also known as a strategy or policy). Properties to be verified against the DP quantify over its adversaries, e.g., the probability of a message packet being lost is less than 0.05 for all possible adversaries. It is also common to use numerical queries, e.g., what is the maximum expected energy consumption?. odel checking reduces to an optimisation problem, namely determining the maximum (or minimum) probability (or expected cost/reward) achievable by any adversary. For the most common classes of property (the probability of reaching a set of target states or the expected cumulated reward), model checking can be reduced to solving a linear programming (LP) problem. In practice, however, most probabilistic verification tools use (approximate) iterative numerical methods, such as value iteration [9], since they scale to much larger systems and are
2 2 Vojtěch Forejt, arta Kwiatkowska, and David Parker amenable to symbolic (BDD-based) implementations. Value iteration can also be used for time-bounded (finite-horizon) properties, which is impractical with LP. Another alternative is policy iteration, but this is also impractical for timebounded properties, and preliminary investigations in [0] showed no particular improvement over value iteration in the context of probabilistic verification. There has recently been increased interest in multi-objective probabilistic model checking for DPs [5,9,,4], which can be used to analyse trade-offs between several, possibly conflicting, quantitative properties. Consider, for example, two events of interest, A and B, and let p σ A and pσ B be the probability that each occurs under an adversary σ of an DP. In this paper, we study several kinds of multi-objective properties. Achievability queries ask, e.g., is there an adversary σ satisfying the predicate ψ = p σ A x pσ B y? and numerical queries ask, e.g., what is maximum value of x such that ψ is achievable?. We also consider the Pareto curve of undominated solution points: for this example, the set of pairs (x, y) such that ψ is achievable but any increase in either x or y would necessitate a decrease in the other. ulti-objective techniques have natural applications to controller synthesis for DPs (e.g., how can we maximise the probability of successful message transmission, whilst keeping the expected energy usage below 00 mj? ). They also form the basis of recent compositional verification techniques [5], which decompose model checking into separate tasks for each system component using assume-guarantee reasoning (e.g., what is the maximum probability of a global system error, under the assumption that component fails with probability at most 0.02? ). This approach has been successfully used to verify probabilistic systems too large to analyse without compositional techniques. Existing multi-objective model checking methods [5,9,,4] rely on a reduction to LP. The linear program solved, although of a rather different form to the standard (single objective) case, is still linear in the size of the DP, yielding polynomial time complexity. As discussed above, though, LP-based probabilistic verification has several important weaknesses. In this paper, we present a novel approach to multi-objective model checking of probabilistic reachability and expected total reward properties. Our method is based on the generation of successive, increasingly precise approximations to the Pareto curve by optimising weighted sums of objectives using value iteration. On a large selection of benchmarks, we demonstrate the following benefits: (i) dramatic improvements in run-time efficiency, by factors of up to 50; (ii) significant scalability improvements: over an order of magnitude model size; (iii) the usefulness of visualising Pareto curves for verification problems; (iv) solution of time-bounded probabilistic reachability and cumulative reward. The last of these also paves the way for the development of multi-objective techniques for richer, timed classes of models such as continuous-time DPs. An extended version of this paper, including proofs, is also available [2]. Related work. ulti-objective optimisation has been extensively studied in areas such as operations research, economics and stochastic control [6], including
3 Pareto Curves for Probabilistic odel Checking 3 its application to DPs []. any general approaches exist, based on, for example, normalising multiple objectives into a single weighted objective; constrained approaches optimising one objective while bounding the others; heuristic search using, e.g., evolutionary algorithms [7]; application of satisfiability/constraint solvers [7]; and stochastic search with restarts [6]. Several methods, including e.g. [6], iterate over weighted sums of objectives, as we do; the main difference is that our approach is tailored to the convex, linear problems derived from DPs. ulti-objective optimisation is routinely used in areas such as embedded systems design and a variety of general-purpose optimisation tools exist, e.g., PISA [2], odefrontier and libraries for ATLAB. Such tools tend to be targeted at much more complex (e.g., non-convex and non-linear) design spaces than the ones that we focus on in this paper. They are also typically used for static design problems, rather than our dynamic models of system behaviour. A rigorous complexity analysis of multi-objective optimisation, in particular for approximating Pareto curves, was undertaken in the influential work of [8]. ore recently [8], some of these results were improved for the simpler case of convex multi-objective problems but no practical investigations are undertaken. ost relevant to the current work is the application of multi-objective optimisation to probabilistic verification [5,9,,4]. In [5,9,4], discounted total reward, probabilistic ω-regular and long-run average properties are studied, respectively. In each case, algorithms are given using a reduction to LP, also showing the existence of methods to approximate Pareto curves using the results of [8], but implementations are not considered. The work of [] adds expected total reward properties and provides an implementation, based on LP. As discussed above, the performance and scalability of our approach is significantly better, as we show in Section 5. None of the above consider time-bounded properties. In principle, for discrete-time models like DPs, these can be reduced to unbounded properties using a finite counter but this is generally impractical in terms of scalability. 2 Background Geometry. For a vector x R n, we use x i to denote its i-th component and say x is a weight vector if x i 0 for all i and n i= x i =. The Euclidean inner product of x, y R n is defined as x y = n i= x i y i. For a set of vectors X = {x,... x k } R n, a convex combination is k j= w j x j for some weight vector w R k. We use down(x) to denote the downward closure of the convex hull of X, i.e. the set of vectors z R n that satisfy z y for some convex combination y of X. Given a convex set Y, we say that a point y Y is on the boundary of Y if, for any ε > 0, there is a point z Y such that the Euclidean distance between y and z is at most ε. From the separating hyperplane and supporting hyperplane theorems, we have the following. Proposition ([3]). Let Y R n be a downward closed set of points. For any p R n not in Y, there is a weight vector w R n such that w p > w y for all y Y. Also, for any q on the boundary of Y, there is a weight vector w R n such that w q w y for all y Y. We say that w separates q from down(y ).
4 4 Vojtěch Forejt, arta Kwiatkowska, and David Parker arkov decision processes (DPs). DPs are commonly used to model systems with probabilistic and nondeterministic behaviour. Denoting by Dist(X) the set of probability distributions over a set X, an DP takes the form = (S, s, α, δ), where S is a set of states, s S is an initial state, α is a set of actions and δ : S α Dist(S) is a (partial) probabilistic transition function. Each state s of an DP has an associated set A(s) of enabled actions, given by A(s) def = {a α δ(s, a) is defined}. If action a A(s) is taken in state s, then the next state is determined randomly according to the distribution δ(s, a), i.e., a transition to state s occurs with probability δ(s, a)(s ). A path through is a (finite or infinite) sequence π = s 0 a 0 s a... where s 0 = s, and a i A(s i ) and δ(s i, a i )(s i+ ) > 0 for all i. We denote by IPaths (FPaths) the set of all infinite (finite) paths and, for finite path π, last(π) is its last state. An adversary σ : FPaths Dist(α) (also called a strategy or policy) of is a resolution of the choices of action in each state, based on its execution so far. In standard fashion [3], an adversary σ induces a probability measure Pr σ over IPaths. An adversary σ is deterministic if σ(π) is a Dirac distribution for all π (and randomised if not); it is memoryless if σ(π) depends only on last(π). The set of all adversaries for is Adv. A reward structure for is a function ρ : S α R mapping actions to (positive or negative) reals. For an infinite path π = s 0 a 0 s a... and a number k N { } the total reward in k steps for π over ρ is ρ[k](π) def = k i=0 ρ(s i, a i ). odel checking DPs. In this paper, we focus on two key classes of properties for DPs: the probability of reaching a target and the expected total reward. In each case, we consider both time-bounded and unbounded variants. We will later discuss generalisation to more expressive properties. In this and the following sections, we assume a fixed DP = (S, s, α, δ). Definition (Reachability predicate). A reachability predicate ] k p comprises a set of target states T S, a relational operator {, }, a rational probability bound p and a time-bound k N { }. It states that the probability of reaching T within k steps satisfies p. Formally, satisfaction of ] k p by DP, under adversary σ, denoted, σ = ] k p, is defined as follows:, σ = ] k p Pr σ ({s 0 a 0 s a IPaths i k : s i T }) p. Definition 2 (Reward predicate). A reward predicate [ρ] k r comprises a reward structure ρ : S α R, a relational operator {, }, a rational reward bound r and a time bound k N { }. It states that the expected total reward cumulated within k steps satisfies r. Formally, satisfaction of [ρ] k r by, under adversary σ, denoted, σ = [ρ] k r, is defined as follows:, σ = [ρ] k r ExpTot σ,k σ,k (ρ) r where ExpTot (ρ) def = π ρ[k](π) dpr σ. For the unbounded forms of the notation above (k = ), we will often omit k, writing e.g. [ρ] r instead of [ρ] r or ExpTot σ (ρ) instead of ExpTot σ, (ρ). For this paper, we also need to consider weighted sums of rewards.
5 Pareto Curves for Probabilistic odel Checking 5 Definition 3 (Weighted reward sum). Given a weight vector w R n and vectors of time bounds k = (k,..., k n ) (N { }) n and reward structures ρ = (ρ,..., ρ n ) for DP, the weighted reward sum w ρ[k] over a path π is defined as w ρ[k](π) def = n i= w iρ i [k](π). The expected total weighted sum is then: ExpTot σ,k def (w ρ) = π w ρ[k](π) dpr σ. For any adversary σ, we have: ExpTot σ,k (w ρ) = n i= w iexptot σ,ki (ρ i). Notice that satisfaction of reachability and reward predicates is defined above with respect to a specific adversary σ of an DP. When performing model checking on the DP, the most common approach is to verify that such a predicate is satisfied for all adversaries σ Adv. An alternative, often described as controller synthesis, is to ask the dual question: whether there exists an adversary σ satisfying the predicate. In either case, model checking reduces to computing the maximum or minimum reachability probability or expected reward. For the unbounded cases, this can be done by solving an LP problem, using policy iteration, or with value iteration, an approximate iterative numerical method [9]. For time-bounded properties, only value iteration is applicable. 3 ulti-objective Queries We now describe how to formalise multi-objective queries for DPs. In the following section, we will present novel, efficient algorithms for their verification. We formulate our queries in a similar style to the one taken in [], but with two key additions. Firstly, we include the ability to specify time-bounded reachability and reward properties. Secondly, we consider Pareto curves. The essence of multi-objective properties for DPs is that they require multiple predicates to be satisfied concurrently for the same adversary. Definition 4 (ulti-objective predicate). A multi-objective predicate is a vector ψ=(ψ,..., ψ n ) of reachability or reward predicates. We say that ψ is satisfied by DP under adversary σ, denoted, σ = ψ, if, σ = ψ i for all i n. We call ψ a basic multi-objective predicate if it is of the form ([ρ ] k r,..., [ρ n ] kn r n ), i.e. it comprises only lower-bounded reward predicates. We define three ways to formulate multi-objective queries for an DP: achievability queries, which check for the existence of an adversary satisfying a multiobjective predicate ψ; numerical queries, which maximise or minimise a reachability/reward objective over the set of adversaries satisfying ψ; and Pareto queries, which determine the Pareto curve for a set of objectives. Definition 5 (Achievability query). For DP and multi-objective predicate ψ, an achievability query asks if ψ is satisfiable (or achievable), i.e. whether there exists an adversary σ Adv such that, σ = ψ. Definition 6 (Numerical query). For DP, a numerical query is of the form num([o ] k, (ψ 2..., ψ n )), comprising an n -sized multi-objective predicate (ψ 2..., ψ n ) and an objective [o ] k, where o is a reward structure ρ or
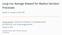
6 6 Vojtěch Forejt, arta Kwiatkowska, and David Parker a, s a, s s 2 s 3 b, 0.9 c, a, 0 (a) (b) Fig.. Example DP (a), graphs for ([{s }] x, [{s 3}] y ) (b) and ([{s }] 2 x, [ρ] y) (c). target set T, k N { } is a time bound and {min, max}. We define: num([o ] k min, (ψ 2,..., ψ n )) def = inf{x R ([o ] k x, ψ 2,..., ψ n ) is satisfiable}. num([o ] k max, (ψ 2,..., ψ n )) def = sup{x R ([o ] k x, ψ 2,..., ψ n ) is satisfiable}. Definition 7 (Pareto query). For DP, a Pareto query takes the form pareto([o ] k,..., [o n ] kn n ), where each [o i ] ki i is an objective as in Defn. 6. The set of achievable values is A = {x R n ([o ] k x,..., [o n ] kn nx n ) is satisfiable} where i = if i = max and i = if i = min. We say, for points x, y A, that x dominates y if x i i y i for all i and x j y j for some j. Then: pareto([o ] k,..., [o n ] kn n ) def = {x A x is not dominated by any y A}. Convexity. A fundamental property of the multi-objective optimisation problems solved in this paper (and on DPs in general) is their convexity. ore precisely, consider target sets T,..., T n, reward structures ρ,..., ρ m and timebounds k,..., k n, l,..., l m N { }. Let x σ R n+m be the vector defined such that x i = Pr σ ( ki T i ) for i n and x n+j = ExpTot σ,kj (ρ j) for j m, where Pr σ ( ki T i ) denotes the probability of reaching T i in k i steps under σ. Then, the set {x σ σ Adv } forms a convex polytope [9,]. As a direct consequence of this, the set of achievable values for a Pareto query is also convex. Example. Fig. (a) shows an DP with accompanying reward structure ρ indicated by underlined numbers. Consider first the multi-objective predicate ψ = ([{s }] x, [{s 3 }] y ), which imposes lower bounds on the probabilities of reaching states s and s 3. The grey area in Fig. (b) shows the values of x and y for which ψ is satisfiable. The two points on the graph marked as + correspond to the two possible memoryless deterministic adversaries in. The line joining them (their convex closure) represents the points for all possible adversaries. For this example, this line also constitutes the Pareto curve. Achievability queries on ψ for (x, y) = (0.2, 0.7) and (0.4, 0.7) return true and false, respectively. Numerical query num([{s }] max, ([{s 3 }] 0.7 )) returns 0.3. Consider a second predicate ψ = ([{s }] 2 x, [ρ] y), now with a time-bounded reachability and reward predicate. Fig. (c) depicts (by +) points for some of the Strictly speaking, this requires finiteness of rewards, which we discuss below. (c)
7 Pareto Curves for Probabilistic odel Checking 7 deterministic adversaries of, of which there are infinitely many. Their convex combination, the dashed area, marks the points achievable by all (randomised) adversaries, and its downward closure, in grey, shows the values of x and y for which ψ is satisfiable. The Pareto curve is the black line along the top edge. Assumptions. For the purposes of model checking the queries described in this section, we need to impose certain restrictions on the use of rewards. For clarity, we describe these in terms of achievability queries but they apply to all three classes. We first need the following definition. Definition 8 (Reward-finiteness). Let be an DP and consider an achievability query ψ=( ] k p,..., n ] kn np n, [ρ ] l r,..., [ρ m ] lm mr m ) for. We say that ψ is reward-finite if, for each j m such that l j = and j =, we have: sup{exptot σ,lj (ρ j), σ = ( ] k p,..., n ] kn np n )} < and is fully reward-finite if, for each j m such that l j = and j =, we have: sup{exptot σ,lj (ρ j) σ Adv } <. Let and ψ be as in Defn. 8. To model check ψ on, we require that: (i) each reward structure ρ i assigns only non-negative values; (ii) ψ is reward-finite; and (iii) for indices j m such that l j =, either all j s are or all are. Condition (ii) imposes natural restrictions on finiteness of rewards. Notice that we only require finiteness for adversaries which satisfy the probabilistic predicates contained in ψ. We adopt this approach from [] where, in addition, algorithms are given to check that ψ is reward-finite and to construct a modified DP that is equivalent (in terms of satisfiability of ψ) but for which ψ is fully reward-finite. This can be checked by a simpler multi-objective query containing only probabilistic predicates. Thus, in the remainder of this paper, we assume that all queries are fully reward-finite. Condition (iii) ensures that the algorithms we define in the next section do not need to compute unbounded expected total rewards for DPs with both positive and negative rewards, which is unsound. For unbounded reachability predicates, again using methods from [], we can easily invert their bounds (to match those of any reward predicates) by making a simple change to the DP. Extensions. We also remark that the class of multi-objective properties outlined in this section can be extended in several respects. In particular, as shown in [], we can add support for probabilistic ω-regular (e.g. LTL) properties via reduction to probabilistic reachability on a product of the DP and one or more deterministic Rabin automata. That work also allows arbitrary Boolean combinations of predicates, which are reduced to disjunctive normal form and treated separately. Both of these extensions can be adapted to our setting; the former we have implemented and used for our experiments in Section 5. 4 ulti-objective Probabilistic odel Checking We now present efficient algorithms for checking the multi-objective queries defined in the previous section. Proofs of correctness can be found in [2].
8 8 Vojtěch Forejt, arta Kwiatkowska, and David Parker Input: DP, multi-objective predicate ψ = ([ρ ] k r,..., [ρ n] kn r n ) Output: true if ψ is achievable, false if not X := ; ρ = (ρ,... ρ n); k = (k,... k n); r = (r,... r n); 2 do 3 Find w separating r from down(x); 4 Find adversary σ maximising ExpTot σ,k (w ρ); 5 q := (ExpTot σ,k i (ρi)) i n; 6 if w q < w r then return false; 7 X := X {q}; 8 while r down(x); 9 return true; Alg.. Basic algorithm for checking achievability queries Reduction to basic form. The first step when checking any type of query is to reduce the problem to one over a basic predicate on a modified DP. We do so by converting reachability predicates into reward predicates (by adding a one-off reward of upon reaching the target) and then negating objectives for predicates with upper bounds. Formally, we do the following. Proposition 2. Let =(S, s, α, δ) be an DP and ψ=( ] k p,..., n ] kn [ρ ] l r,..., [ρ m ] lm mr m ) be a multi-objective predicate. Let =(S, ( s, ), α, δ ) be the DP defined as follows: S =S 2 {,...,n}, α =α 2 {,...,n} and, for all s, s S, a α and c {,..., n}: δ ((s, c), (a, c ))((s, c c )) = δ(s, a)(s ) where c = {i s T i } \ c; δ ((s, c), a )((s, c )) = 0 for all other c, c and a. np n, Now, let ψ be ([ρ T ] k+ p,..., [ρ Tn ] kn+ p n, [ ρ ] l r,..., [ ρ m ] lm r m ), where: reward ρ Ti ((s, c), (a, c )) is equal to if i c and i =, to if i =, and to 0 otherwise; and ρ i ((s, c), (a, c )) is equal to ρ i (s, a) if i = and to ρ i (s, a) if i =. Then ψ is satisfiable in if and only if ψ is satisfiable in. Notice that the reduction described above results in reward structures with both positive and negative rewards. For time-bounded properties, this is not a concern. For unbounded ones, we must take care that they are all either non-negative or non-positive, as mentioned earlier in our discussion of condition (iii). Achievability queries. We begin with achievability queries. We first give an outline of the overall algorithm; subsequently, we will describe in more detail how it is implemented in practice using value iteration. By applying the reduction described above, we only need to consider the case of a basic multi-objective predicate ψ = ([ρ ] k r,..., [ρ n ] kn r n ). Alg. shows how to check if ψ is satisfiable. It works by generating a sequence of weight vectors w and optimising a w-weighted sum of the n objectives. A resulting optimal adversary σ is then used to generate a point q which is guaranteed to be contained on the Pareto curve for ψ, and a collection X of such points is assembled. Each new weight vector w is identified by finding a separating hyperplane between down(x) and r = (r,..., r n ). Once r is found to be contained in down(x), we
9 r q (a) Pareto Curves for Probabilistic odel Checking 9 q r (b) (c) p Fig. 2. Example executions of Algorithms, 3 and 4 (see Examples 2, 3 and 4). know that ψ is achievable. If, on the other hand, w q < w r, then we know that ψ cannot possibly be achievable. Correctness of Alg. is proved in [2]. Termination is guaranteed by the fact that each iteration of the loop identifies a point q on a unique face of the Pareto curve. In the worst case, the number of faces is exponential in, k and n [9]; however, our experimental results (in Section 5) show the number of steps is usually small on practical examples. The individual model checking problems solved in each step (lines 4-5 of Alg. ) require time polynomial in. We describe their practical implementation in the next section. Example 2. We illustrate the execution of Alg. on the DP from Example and the achievability query ([{s }] 0.2, [{s 3 }] 0.7 ). Let us assume that we have already applied Proposition 2 so that we have an equivalent reward predicate ([ρ ] 0.2, [ρ 2 ] 0.7 ) (the full reduction is in [2]). As a first (arbitrary) weight vector, we pick w=(0.5, 0.5) and then maximise w ρ. The resulting optimal adversary σ (which chooses a in s 0 ) gives q = (ExpTot σ (ρ ), ExpTot σ (ρ 2 )) = (0.4, 0.6) and we have X = {q}. Fig. 2(a) shows the point q (as ) and the target point r = (0.2, 0.7) (as ). The dotted line represents the hyperplane with orientation w passing through q (i.e. the points x for which w x = w q = 0.5), the points above which correspond to unachievable value pairs. The grey region is down(x), in which all points are achievable. Since r down(x), we continue. Next, we pick a weight w = (0., 0.8). aximising w ρ results in adversary σ (which chooses b in s 0 ) giving q = (0., 0.9), which we add to X. Fig. 2(b) again shows both points in X, down(x) and r. It also plots points x for which w x = w q = Since r is now in down(x), the algorithm returns true. Value iteration. The most expensive part of Alg. in practice is the combination of lines 4-5, which computes the maximum possible value for a weighted sum of reward objectives, determines a corresponding optimal adversary σ, and then finds the value for the n individual objectives under σ. Alg. 2 shows how to perform all these tasks using a value iteration-style computation. One key difference between this algorithm and standard value iteration is that it needs to optimise a combination of unbounded and bounded properties. This is done in three phases (lines 3-8, 9-3 and 4-20). The first two correspond to the unbounded part; the third to the bounded part. Another important difference is that the algorithm performs the optimisation of the weighted sum w ρ[k] and the computation of the vector of individual objective values q = (ExpTot σ,ki (ρ i)) i n simultaneously: the former in phases (d)
10 0 Vojtěch Forejt, arta Kwiatkowska, and David Parker Input: DP =(S, s, α, δ), weight vect. w, reward structures ρ=(ρ,..., ρ n), vector of time bounds k (N { }) n, convergence threshold ε Output: Adv. σ maximising ExpTot σ,k (w ρ), q = (ExpTot σ,k i (ρi)) i n x := 0; x := 0;... ; x n := 0; y = 0; y := 0;... ; y n := 0; 2 σ (s) = for all s S; 3 do 4 foreach s S do 5 y s := max a A(s) ( {i k i = } wi ρi(s, a) + s S δ(s, a)(s ) x s ); 6 σ (s) := arg max a A(s) ( {i k i = } wi ρi(s, a) + s S δ(s, a)(s ) x s ); 7 δ := max s S (y s x s); x := y; 8 while δ > ε; 9 do 0 foreach s S and i {,..., n} where k i = do ys i := ρ i(s, σ (s)) + s S δ(s, σ (s))(s ) x i s ; 2 δ := max n i= max s S (ys i x i s); x := y ;... ; x n := y n ; 3 while δ > ε; 4 for j = max{k l < l {,..., n}} down to do 5 foreach s S do 6 y s := max a A(s) ( {i k i j} wi ρi(s, a) + s S δ(s, a)(s ) x s ); 7 σ j (s) := arg max a A(s) ( {i k i j} wi ρi(s, a) + s S δ(s, a)(s ) x s ); 8 foreach i {,..., n} where k i j do 9 ys i := ρ i(s, σ j (s)) + s S δ(s, σj (s))(s ) x i s ; 20 x := y; x := y ;... ; x n := y n ; 2 foreach i {,..., n} do q i := y ī s ; 22 σ behaves as σ j in j-th step when j < max i {,...,n} k i, and as σ afterwards; 23 return σ, q Alg. 2. Value iteration-based algorithm for lines 4-5 of Alg.. and 3; the latter in phases 2 and 3. Consider first the optimisation of w ρ[k]. The values, for all states s S, are computed as a sequence of increasingly precise approximations, stored in a pair of vectors, x and y. Each new approximation is stored in y (line 5); then, x and y are compared for convergence and x is set to y (line 7) before proceeding to the next iteration. Computation of the bounded part of w ρ[k] continues in phase 3 in similar fashion (although no convergence check is needed). During optimisation of w ρ[k], a corresponding optimal adversary is also determined, with the unbounded and bounded fragments stored in σ and σ j, respectively. The choices made by this adversary are used to compute the value q i for each of the n individual objectives, the values for which are also stored in pairs of vectors (x i, y i for each q i ). In practice, storing multiple S -sized vectors (x, y, x i, and y i ) is relatively expensive. We discuss later how the algorithm s memory usage can be improved. We include an example of the execution of Alg. 2 in [2]. Numerical queries. We now turn our attention to numerical queries. Alg. 3 shows how Alg. can be adapted to check these. Like Alg., it generates points q on the Pareto curve from a sequence of weight functions w. For the objective ρ that is being optimised, we generate a sequence of lower bounds r that are
11 Pareto Curves for Probabilistic odel Checking Input: DP, objective [ρ ] k max, predicate ([ρ 2] k 2 r 2,..., [ρ n] kn r n ) Output: Value of num([ρ ] k max, ([ρ 2] k 2 r 2,..., [ρ n] kn r n )) X:= ; ρ:=(ρ,... ρ n); k:=(k,... k n); r:=( min ExpTot σ,k (ρ), r2,... rn); σ Adv 2 do 3 Find w separating r from down(x) such that w > 0; 4 Find adversary σ maximising ExpTot σ,k (w ρ); 5 q := (ExpTot σ,k i (ρi)) i n; 6 if w q < w r then return ; 7 X := X {q}; r := max{r, max{r (r, r 2,..., r n) down(x)}}; 8 while r down(x) or w q > w r; 9 return r ; Alg. 3. Algorithm for checking numerical queries used in the same fashion as Alg.. Initially, we take r to be the minimum possible value for ρ, which can be computed with a separate instance of value iteration. New (non-decreasing) values for r are generated at each step based on the set of points X determined so far. The numerical computation for each step (lines 4-5 of Alg. 3) can again be carried out with Alg. 2. Correctness of Alg. 3 is proved in [2]. The bound on the number of steps needed is as for Alg.. Example 3. We demonstrate Alg. 3 on the DP from Example and numerical query ([{s }] max, ([{s 3 }] 0.7 )). Initially, r =0. and, with w=(0., 0.8), we get q=(0., 0.9). The resulting area down(x) is shown as dark grey in Fig. 2(c). Next, r remains as 0. and, with w=(, 0), we get q=(0.4, 0.6). Adding this to X, down(x) is enlarged by the light grey area. Finally, r is set to 0.3, choosing w=(0.5, 0.5) yields q=(0.4, 0.6) again, and the loop ends. Fig. 2(c) also shows the points q and r (as and ). The final value returned is r =0.3. Pareto curves. Next, we discuss Pareto queries. Generating and visualising Pareto curves (or their approximations) provides a much clearer view of the trade-offs between objectives. Our algorithm is implemented as a simple modification of our previous algorithms, and is presented as Alg. 4. For simplicity, we focus on the 2-objective case, which is most practical for visualisation. Our implementation, described later, also supports the 3-objective case and, in theory, this can be extended to an arbitrary number of objectives. Alg. 4, like the earlier ones, builds a set X of points on a Pareto curve P using weights w. Since P is convex, the surface of points X represents a lower approximation of P. Our algorithm also constructs an upper approximation Y using the generated weights w. As illustrated in Example 2, for each point q X, there is a corresponding hyperplane passing through q and with orientation w, above which no values are achievable. Hence these represent upper bounds on P and we store, in Y, any weight w that resulted in each point q X. The sequence of weights w is generated as follows. We construct an initial curve using weights (, 0) and (0, ). Then, we repeatedly: (i) sort the points in X; (ii) for each successive pair x i, x i+ in X, find the lowest point p on the intersection of the hyperplanes stored in Y for x i and x i+ ; (iii) choose w as a separating hyperplane between down(x) and p. The algorithm continues
12 2 Vojtěch Forejt, arta Kwiatkowska, and David Parker Input: DP, reward structures ρ = (ρ, ρ 2), time bounds (k, k 2), ε p R >0 Output: An ε p-approximation of a Pareto curve X := ; Y : R 2 2 R2, initially Y (x) = for all x; w = (, 0); 2 Find adversary σ maximising ExpTot σ,k (w ρ); 3 q := (ExpTot σ,k (ρ), ExpTot σ,k 2 (ρ2)); 4 X := X {q}; Y (q) := Y (q) {w}; w = (0, ); 5 do 6 Find adversary σ maximising ExpTot σ,k (w ρ); 7 q := (ExpTot σ,k (ρ), ExpTot σ,k 2 (ρ2)); 8 X := X {q}; Y (q) := Y (q) {w}; w = ; 9 Order X to a sequence x,..., x m such that i: x i x i+ and x i 2 x i+ 2 ; 0 foreach i {,... m } do Let u be the element of Y (x i ) with maximal u ; 2 Let u be the element of Y (x i+ ) with minimal u.; 3 Find a point p such that u p = u x i and u p = u x i+ ; 4 if distance of p from down(x) is ε p then 5 Find w separating down(x) from p, maximising w p max x down(x) w x; 6 while w ; 7 return X Alg. 4. Algorithm for Pareto curve approximation for 2 objectives until the maximum distance between the two approximations falls below some threshold ε p. In principal, the algorithm can enumerate all faces of P. The reason for constructing an ε p -approximation is two-fold: firstly, the number of faces is potentially large, whereas an approximation may suffice; secondly, computation of individual points (using value iteration), is already approximate. Example 4. We illustrate Alg. 4 on the DP from Example with objectives ([{s }] max, [{s 3 }] max ). The first two weight vectors w are (, 0) and (0, ), yielding points q of (0.4, 0.6) and (0., 0.9), repectively (see Fig. 2(d)). The hyperplanes attached to each point are also shown, by dotted lines, as is their intersection p = (0.4, 0.9). We choose separating hyperplane w = (0.5, 0.5), indicated by the sloped dotted line. The algorithm then finds the intersection (0., 0.9) of this with the horizontal line and, since this point is already in down(x), terminates. Adversary generation. Finally, we describe how to generate optimal adversaries for our multi-objective queries. We explain this for achievability queries, but it can easily be adapted to the other types too. Unlike standard (singleobjective) DP model checking, where deterministic adversaries always suffice to optimise reachability/reward objectives, multi-objective optimisation requires randomised adversaries. Alg., when finding that bounds r are achievable, generates points q,..., q m on the Pareto curve. Each corresponding call to Alg. 2 returns a (deterministic) adversary, say σ q j for the current point q j. The final adversary σ opt is constructed from these and a weight vector u R m satisfying r i m j= u i q j i for all i n: it simply makes an initial one-off random choice of adversary σ q j to mimic (each with probability u j ).
13 5 Implementation and Results Pareto Curves for Probabilistic odel Checking 3 We implemented our multi-objective model checking techniques in PRIS [4], also adding the automaton construction of [] to support ω-regular properties. Value iteration is built on top of PRIS s sparse engine. It would also be straightforward to adapt its symbolic (TBDD) engine, which can improve scalability on models exhibiting regularity; but, for the current set of experiments, the sparse engine suffices to illustrate the benefits offered by our approach. Heuristics and optimisations. Our core algorithms are based on generating weight vectors w representing separating hyperplanes (e.g. at line 3 of Alg. ). The choice of each w is not unique and affects the number of steps needed by the algorithm. Based on our results, the following is an effective heuristic. For the first n vectors (assuming n objectives), choose w with w i = for some i. Next, given point r and set of points X, choose w to maximise min x X (w q w x), i.e., pick the hyperplane with maximal Euclidean distance d from q. This is done by solving the LP: maximise d subject to n i= w i = and w i (q i x i ) d for all x X. In practice, these problems are small and fast to solve. We also apply various optimisations to the basic value iteration algorithms of Section 4. For unbounded properties, Gauss-Seidel value iteration [9] can be used to increase performance. Furthermore, we can significantly reduce the number of vectors stored with slight changes to Alg. 2; details are in [2]. Experimental results. We evaluated our techniques on benchmarks from several sources. 2 First, we used multi-objective problems resulting from the assumeguarantee framework of [5]. Second, we verified multi-objective properties on existing PRIS models: (i) a task-graph scheduler problem, minimising expected job completion time and expected energy consumption; (ii) a team-formation protocol, maximising the probability of completing two (separate) tasks and the expected size of the team that does so; (iii) a dynamic power management (dpm) controller, minimising over k steps both expected energy consumption and expected average queue size. Experiments were run on a 2.66GHz PC with 8GB of RA. We used ε = 0 6 for value iteration (this is the default in PRIS; smaller values led to very similar results) and ε p = 0 4 for Pareto curve generation. The results are shown in Table : assume-guarantee problems at the top; the others below. For each model, we give the size (number of states), and details of the objectives in the query used. The middle part of the table compares the performance of our value iteration-based technique with the LP-based implementation of [] on numerical queries. In our experiments, performance for achievability queries was very similar, so we omit them. The right part of the table shows times to compute Pareto curves for the same objectives on each model (which cannot be done with the implementation of []). For value iterationbased algorithms, we show the number of points (steps of the algorithm) needed; for LP-based, we show the size of the linear program solved. Comparing the value-iteration and LP-based approaches, we see huge gains in run-time for our methods (up to approx. 50 times faster). There are also 2 All models/properties used are at
14 4 Vojtěch Forejt, arta Kwiatkowska, and David Parker Case study [parameters] consensus (2 proc.s) [R K] consensus (3 proc.s) [R K] zeroconf [K] zeroconf-tb [K T ] team-form. [N] team-form. [N] scheduler [K] dpm [k] Num. states Objectives Numerical query Pareto query LP ([]) Val. iter. Val. iter. Num. Types LP size Time (s) Pt.s Time (s) Pt.s Time (s) ] max ] max ] max ] max mem-out ] max ] max ] max ] max ] max [ρ ] max mem-out ] max ] max [ρ 2] max mem-out [ρ ] min mem-out [ρ ] min mem-out [ρ ] k n/a n/a min [ρ 2] k n/a n/a min n/a n/a Table. Experimental results for our implementation and a comparison with []. significant improvements in scalability: the biggest models solved with value iteration are about 20 times bigger than those for LP. One factor in the low runtimes for our technique is that the algorithms generally require a fairly small number of steps, even when generating the Pareto curve. Pareto curves. Finally, we show in Fig. 3 the Pareto curves generated for some of our examples. Plot (a) shows, for a task-graph scheduling problem, how different schedulers vary in terms of completion time and energy usage. Plot (b) is from an instance of assume-guarantee verification; the plot shows how it is possible to bound the probability of an error in the overall system (y-axis) for various different reliability levels of one of the components (x-axis). Plot (c) shows a 3-objective Pareto curve evaluating strategies in a team-formation protocol (see Fig. 3 caption for objectives). In each case, the plots give a clear, visual illustration of the trade-off between competing objectives. The curves could also be used to quickly answer any additional achievability or numerical queries for those objectives, without running any further model checking. 6 Conclusions We have presented novel techniques for multi-objective model checking of DPs, using a value iteration-based computation to build successive approximations of the Pareto curve. Compared to existing approaches, this gives significant gains in efficiency and scalability, and enables verification of time-bounded properties. Furthermore, we showed the benefits of visualising the Pareto curve for several probabilistic model checking case studies. Future directions include extending our techniques to timed probabilistic models such as CTDPs and PTAs.
15 K= E E E E K= !&% !'#&% !'#"% !'#$% !'#(% K=5!'% !"#&% !"#"% !"#$% !#$$% !#$)%!#$"%!#$'% !#$&%!#$*%!#)%!#)!% !"#$%&$'($+$,-.(/0-$( !"#$%&$'()*$( K= E-04 Pareto Curves for Probabilistic odel Checking 5!"#$%&'()*&+#&,#-./0"&$2&3(3*)-&!#!!!&$"!#!!!&"!#!!!%$"!#!!!%"!#!!!!$"!"!#'''&"!#'''("!#''')"!#'''*" %"!"#$($)*)+2&,#45#--+&(660457#-&6(76.3& x y Fig. 3. Pareto curves from: (a) task-graph scheduler, K=2; (b) Zeroconf protocol, K=2, T =0; (c) team formation protocol, N=3 (axes x/y/z = Probability of completing task /probability of completing task 2/expected size of successful team) Acknowledgments. The authors are part supported by ERC Advanced Grant VERIWARE and EPSRC grant EP/F00096/. Vojtěch Forejt is also supported by a Royal Society Newton Fellowship. References. Altman, E.: Constrained arkov Decision Processes. Chapman & Hall/CRC (999) 2. Bleuler, S., Laumanns,., Thiele, L., Zitzler, E.: PISA-A Platform and Programming Language Independent Interface for Search Algorithms. In: EO 03 (2003) 3. Boyd, S., Vandenberghe, L.: Convex Optimization. Cambridge Univ. Press (2004) 4. Brázdil, T., Brožek, V., Chatterjee, K., Forejt, V., Kučera, A.: Two views on multiple mean-payoff objectives in arkov decision processes. In: LICS (20) 5. Chatterjee, K., ajumdar, R., Henzinger, T.: arkov decision processes with multiple objectives. In: Proc. STACS 06. pp Springer (2006) 6. Clímaco, J. (ed.): ulticriteria Analysis. Springer (997) 7. Coello, C., Lamont, G., van Veldhuizen, D.: Evolutionary Algorithms for Solving ulti-objective Problems. Springer (2007) 8. Diakonikolas, I., Yannakakis,.: Succinct approximate convex Pareto curves. In: Proc. SODA 08. pp SIA (2008) 9. Etessami, K., Kwiatkowska,., Vardi,., Yannakakis,.: ulti-objective model checking of arkov decision processes. LCS 4(4), 2 (2008) 0. Forejt, V., Kwiatkowska,., Norman, G., Parker, D.: Automated verification techniques for probabilistic systems. In: SF. LNCS, vol Springer (20). Forejt, V., Kwiatkowska,., Norman, G., Parker, D., Qu, H.: Quantitative multiobjective verification for probabilistic systems. In: Proc. TACAS (20) 2. Forejt, V., Kwiatkowska,., Parker, D.: 3. Kemeny, J., Snell, J., Knapp, A.: Denumerable arkov Chains. Springer (976) 4. Kwiatkowska,., Norman, G., Parker, D.: PRIS 4.0: Verification of probabilistic real-time systems. In: Proc. CAV. LNCS, vol. 6806, pp Springer (20) 5. Kwiatkowska,., Norman, G., Parker, D., Qu, H.: Assume-guarantee verification for probabilistic systems. In: Proc. TACAS 0. pp Springer (200) 6. Legriel, J., Cotton, S., aler, O.: On universal search strategies for multi-criteria optimization using weighted sums. In: Proc. CEC. pp (20) 7. Legriel, J., Guernic, C.L., Cotton, S., aler, O.: Approximating the Pareto front of multi-criteria optimization problems. In: Proc. TACAS 0. pp (200) 8. Papadimitriou, C., Yannakakis,.: On the approximability of trade-offs and optimal access of web sources. In: Proc. FOCS 00. pp (2000) 9. Puterman,.: arkov Decision Processes: Discrete Stochastic Dynamic Programming. John Wiley and Sons (994) z
Probabilistic Model Checking and Strategy Synthesis for Robot Navigation
 Probabilistic Model Checking and Strategy Synthesis for Robot Navigation Dave Parker University of Birmingham (joint work with Bruno Lacerda, Nick Hawes) AIMS CDT, Oxford, May 2015 Overview Probabilistic
Probabilistic Model Checking and Strategy Synthesis for Robot Navigation Dave Parker University of Birmingham (joint work with Bruno Lacerda, Nick Hawes) AIMS CDT, Oxford, May 2015 Overview Probabilistic
SFM-11:CONNECT Summer School, Bertinoro, June 2011
 SFM-:CONNECT Summer School, Bertinoro, June 20 EU-FP7: CONNECT LSCITS/PSS VERIWARE Part 3 Markov decision processes Overview Lectures and 2: Introduction 2 Discrete-time Markov chains 3 Markov decision
SFM-:CONNECT Summer School, Bertinoro, June 20 EU-FP7: CONNECT LSCITS/PSS VERIWARE Part 3 Markov decision processes Overview Lectures and 2: Introduction 2 Discrete-time Markov chains 3 Markov decision
Probabilistic Model Checking Michaelmas Term Dr. Dave Parker. Department of Computer Science University of Oxford
 Probabilistic Model Checking Michaelmas Term 20 Dr. Dave Parker Department of Computer Science University of Oxford Overview PCTL for MDPs syntax, semantics, examples PCTL model checking next, bounded
Probabilistic Model Checking Michaelmas Term 20 Dr. Dave Parker Department of Computer Science University of Oxford Overview PCTL for MDPs syntax, semantics, examples PCTL model checking next, bounded
Automated Verification and Strategy Synthesis for Probabilistic Systems
 Automated Verification and Strategy Synthesis for Probabilistic Systems Marta Kwiatkowska 1 and David Parker 2 1 Department of Computer Science, University of Oxford, UK 2 School of Computer Science, University
Automated Verification and Strategy Synthesis for Probabilistic Systems Marta Kwiatkowska 1 and David Parker 2 1 Department of Computer Science, University of Oxford, UK 2 School of Computer Science, University
Probabilistic model checking with PRISM
 Probabilistic model checking with PRISM Marta Kwiatkowska Department of Computer Science, University of Oxford 4th SSFT, Menlo College, May 204 Part 2 Markov decision processes Overview (Part 2) Introduction
Probabilistic model checking with PRISM Marta Kwiatkowska Department of Computer Science, University of Oxford 4th SSFT, Menlo College, May 204 Part 2 Markov decision processes Overview (Part 2) Introduction
PERMISSIVE CONTROLLER SYNTHESIS FOR PROBABILISTIC SYSTEMS
 Logical Methods in Computer Science Vol. 11(2:16)2015, pp. 1 34 www.lmcs-online.org Submitted Nov. 8, 2014 Published Jun. 30, 2015 PERMISSIVE CONTROLLER SYNTHESIS FOR PROBABILISTIC SYSTEMS KLAUS DRÄGER
Logical Methods in Computer Science Vol. 11(2:16)2015, pp. 1 34 www.lmcs-online.org Submitted Nov. 8, 2014 Published Jun. 30, 2015 PERMISSIVE CONTROLLER SYNTHESIS FOR PROBABILISTIC SYSTEMS KLAUS DRÄGER
Probabilistic Model Checking: Advances and Applications
 Probabilistic Model Checking: Advances and Applications Dave Parker University of Birmingham Highlights 18, Berlin, September 2018 Overview Probabilistic model checking & PRISM Markov decision processes
Probabilistic Model Checking: Advances and Applications Dave Parker University of Birmingham Highlights 18, Berlin, September 2018 Overview Probabilistic model checking & PRISM Markov decision processes
Verification and Control of Partially Observable Probabilistic Systems
 Verification and Control of Partially Observable Probabilistic Systems Gethin Norman 1, David Parker 2, and Xueyi Zou 3 1 School of Computing Science, University of Glasgow, UK 2 School of Computer Science,
Verification and Control of Partially Observable Probabilistic Systems Gethin Norman 1, David Parker 2, and Xueyi Zou 3 1 School of Computing Science, University of Glasgow, UK 2 School of Computer Science,
 Kwiatkowska, M., Norman, G., Parker, D. and Qu, H. (2010) Assume-guarantee verification for probabilistic systems. In: Esparza, J. and Majumdar, R. (eds.) Tools and Algorithms for the Construction and
Kwiatkowska, M., Norman, G., Parker, D. and Qu, H. (2010) Assume-guarantee verification for probabilistic systems. In: Esparza, J. and Majumdar, R. (eds.) Tools and Algorithms for the Construction and
Playing Stochastic Games Precisely
 Playing Stochastic Games Precisely Taolue Chen 1, Vojtěch Forejt 1, Marta Kwiatkowska 1, Aistis Simaitis 1, Ashutosh Trivedi 2, and Michael Ummels 3 1 Department of Computer Science, University of Oxford,
Playing Stochastic Games Precisely Taolue Chen 1, Vojtěch Forejt 1, Marta Kwiatkowska 1, Aistis Simaitis 1, Ashutosh Trivedi 2, and Michael Ummels 3 1 Department of Computer Science, University of Oxford,
Compositional Verification of Probabilistic Systems using Learning
 Compositional Verification of Probabilistic Systems using Learning Lu Feng, Marta Kwiatkowska, David Parker Oxford University Computing Laboratory, Parks Road, Oxford, OX1 3QD Email: {lu.feng, marta.kwiatkowska,
Compositional Verification of Probabilistic Systems using Learning Lu Feng, Marta Kwiatkowska, David Parker Oxford University Computing Laboratory, Parks Road, Oxford, OX1 3QD Email: {lu.feng, marta.kwiatkowska,
PRISM An overview. automatic verification of systems with stochastic behaviour e.g. due to unreliability, uncertainty, randomisation,
 PRISM An overview PRISM is a probabilistic model checker automatic verification of systems with stochastic behaviour e.g. due to unreliability, uncertainty, randomisation, Construction/analysis of probabilistic
PRISM An overview PRISM is a probabilistic model checker automatic verification of systems with stochastic behaviour e.g. due to unreliability, uncertainty, randomisation, Construction/analysis of probabilistic
Probabilistic verification and approximation schemes
 Probabilistic verification and approximation schemes Richard Lassaigne Equipe de Logique mathématique, CNRS-Université Paris 7 Joint work with Sylvain Peyronnet (LRDE/EPITA & Equipe de Logique) Plan 1
Probabilistic verification and approximation schemes Richard Lassaigne Equipe de Logique mathématique, CNRS-Université Paris 7 Joint work with Sylvain Peyronnet (LRDE/EPITA & Equipe de Logique) Plan 1
Polynomial-Time Verification of PCTL Properties of MDPs with Convex Uncertainties and its Application to Cyber-Physical Systems
 Polynomial-Time Verification of PCTL Properties of MDPs with Convex Uncertainties and its Application to Cyber-Physical Systems Alberto Puggelli DREAM Seminar - November 26, 2013 Collaborators and PIs:
Polynomial-Time Verification of PCTL Properties of MDPs with Convex Uncertainties and its Application to Cyber-Physical Systems Alberto Puggelli DREAM Seminar - November 26, 2013 Collaborators and PIs:
PRISM: Probabilistic Model Checking for Performance and Reliability Analysis
 PRISM: Probabilistic Model Checking for Performance and Reliability Analysis Marta Kwiatkowska, Gethin Norman and David Parker Oxford University Computing Laboratory, Wolfson Building, Parks Road, Oxford,
PRISM: Probabilistic Model Checking for Performance and Reliability Analysis Marta Kwiatkowska, Gethin Norman and David Parker Oxford University Computing Laboratory, Wolfson Building, Parks Road, Oxford,
Verifying Randomized Distributed Algorithms with PRISM
 Verifying Randomized Distributed Algorithms with PRISM Marta Kwiatkowska, Gethin Norman, and David Parker University of Birmingham, Birmingham B15 2TT, United Kingdom {M.Z.Kwiatkowska,G.Norman,D.A.Parker}@cs.bham.ac.uk
Verifying Randomized Distributed Algorithms with PRISM Marta Kwiatkowska, Gethin Norman, and David Parker University of Birmingham, Birmingham B15 2TT, United Kingdom {M.Z.Kwiatkowska,G.Norman,D.A.Parker}@cs.bham.ac.uk
Markov Decision Processes with Multiple Long-run Average Objectives
 Markov Decision Processes with Multiple Long-run Average Objectives Krishnendu Chatterjee UC Berkeley c krish@eecs.berkeley.edu Abstract. We consider Markov decision processes (MDPs) with multiple long-run
Markov Decision Processes with Multiple Long-run Average Objectives Krishnendu Chatterjee UC Berkeley c krish@eecs.berkeley.edu Abstract. We consider Markov decision processes (MDPs) with multiple long-run
State Explosion in Almost-Sure Probabilistic Reachability
 State Explosion in Almost-Sure Probabilistic Reachability François Laroussinie Lab. Spécification & Vérification, ENS de Cachan & CNRS UMR 8643, 61, av. Pdt. Wilson, 94235 Cachan Cedex France Jeremy Sproston
State Explosion in Almost-Sure Probabilistic Reachability François Laroussinie Lab. Spécification & Vérification, ENS de Cachan & CNRS UMR 8643, 61, av. Pdt. Wilson, 94235 Cachan Cedex France Jeremy Sproston
Modelling and Analysis (and towards Synthesis)
 Modelling and Analysis (and towards Synthesis) Marta Kwiatkowska Department of Computer Science, University of Oxford Dagstuhl meeting 15041, 19-23 rd Jan 2015 Outline Introduction The context: role of
Modelling and Analysis (and towards Synthesis) Marta Kwiatkowska Department of Computer Science, University of Oxford Dagstuhl meeting 15041, 19-23 rd Jan 2015 Outline Introduction The context: role of
The Complexity of Nash Equilibria in Simple Stochastic Multiplayer Games *
 The Complexity of Nash Equilibria in Simple Stochastic Multiplayer Games * Michael Ummels 1 and Dominik Wojtczak 2,3 1 RWTH Aachen University, Germany E-Mail: ummels@logic.rwth-aachen.de 2 CWI, Amsterdam,
The Complexity of Nash Equilibria in Simple Stochastic Multiplayer Games * Michael Ummels 1 and Dominik Wojtczak 2,3 1 RWTH Aachen University, Germany E-Mail: ummels@logic.rwth-aachen.de 2 CWI, Amsterdam,
Probabilistic Model Checking Michaelmas Term Dr. Dave Parker. Department of Computer Science University of Oxford
 Probabilistic Model Checking Michaelmas Term 2011 Dr. Dave Parker Department of Computer Science University of Oxford Probabilistic model checking System Probabilistic model e.g. Markov chain Result 0.5
Probabilistic Model Checking Michaelmas Term 2011 Dr. Dave Parker Department of Computer Science University of Oxford Probabilistic model checking System Probabilistic model e.g. Markov chain Result 0.5
The State Explosion Problem
 The State Explosion Problem Martin Kot August 16, 2003 1 Introduction One from main approaches to checking correctness of a concurrent system are state space methods. They are suitable for automatic analysis
The State Explosion Problem Martin Kot August 16, 2003 1 Introduction One from main approaches to checking correctness of a concurrent system are state space methods. They are suitable for automatic analysis
Stochastic Games with Time The value Min strategies Max strategies Determinacy Finite-state games Cont.-time Markov chains
 Games with Time Finite-state Masaryk University Brno GASICS 00 /39 Outline Finite-state stochastic processes. Games over event-driven stochastic processes. Strategies,, determinacy. Existing results for
Games with Time Finite-state Masaryk University Brno GASICS 00 /39 Outline Finite-state stochastic processes. Games over event-driven stochastic processes. Strategies,, determinacy. Existing results for
Verification and control of partially observable probabilistic systems
 Real-Time Syst (2017) 53:354 402 DOI 10.1007/s11241-017-9269-4 Verification and control of partially observable probabilistic systems Gethin Norman 1 David Parker 2 Xueyi Zou 3 Published online: 8 March
Real-Time Syst (2017) 53:354 402 DOI 10.1007/s11241-017-9269-4 Verification and control of partially observable probabilistic systems Gethin Norman 1 David Parker 2 Xueyi Zou 3 Published online: 8 March
Limiting Behavior of Markov Chains with Eager Attractors
 Limiting Behavior of Markov Chains with Eager Attractors Parosh Aziz Abdulla Uppsala University, Sweden. parosh@it.uu.se Noomene Ben Henda Uppsala University, Sweden. Noomene.BenHenda@it.uu.se Sven Sandberg
Limiting Behavior of Markov Chains with Eager Attractors Parosh Aziz Abdulla Uppsala University, Sweden. parosh@it.uu.se Noomene Ben Henda Uppsala University, Sweden. Noomene.BenHenda@it.uu.se Sven Sandberg
Automated Learning of Probabilistic Assumptions for Compositional Reasoning
 Automated Learning of Probabilistic Assumptions for Compositional Reasoning Lu Feng, Marta Kwiatkowska, and David Parker Oxford University Computing Laboratory, Parks Road, Oxford, OX1 3QD, UK Abstract.
Automated Learning of Probabilistic Assumptions for Compositional Reasoning Lu Feng, Marta Kwiatkowska, and David Parker Oxford University Computing Laboratory, Parks Road, Oxford, OX1 3QD, UK Abstract.
Stochastic Model Checking
 Stochastic Model Checking Marta Kwiatkowska, Gethin Norman, and David Parker School of Computer Science, University of Birmingham Edgbaston, Birmingham B15 2TT, United Kingdom Abstract. This tutorial presents
Stochastic Model Checking Marta Kwiatkowska, Gethin Norman, and David Parker School of Computer Science, University of Birmingham Edgbaston, Birmingham B15 2TT, United Kingdom Abstract. This tutorial presents
Quantitative Verification and Synthesis of Attack-Defence Scenarios
 Quantitative Verification and Synthesis of Attack-Defence Scenarios Zaruhi Aslanyan, Flemming Nielson DTU Compute Technical University of Denmark Denmark Email: {zaas,fnie}@dtu.dk David Parker School of
Quantitative Verification and Synthesis of Attack-Defence Scenarios Zaruhi Aslanyan, Flemming Nielson DTU Compute Technical University of Denmark Denmark Email: {zaas,fnie}@dtu.dk David Parker School of
Temporal logics and explicit-state model checking. Pierre Wolper Université de Liège
 Temporal logics and explicit-state model checking Pierre Wolper Université de Liège 1 Topics to be covered Introducing explicit-state model checking Finite automata on infinite words Temporal Logics and
Temporal logics and explicit-state model checking Pierre Wolper Université de Liège 1 Topics to be covered Introducing explicit-state model checking Finite automata on infinite words Temporal Logics and
Distributed Optimization. Song Chong EE, KAIST
 Distributed Optimization Song Chong EE, KAIST songchong@kaist.edu Dynamic Programming for Path Planning A path-planning problem consists of a weighted directed graph with a set of n nodes N, directed links
Distributed Optimization Song Chong EE, KAIST songchong@kaist.edu Dynamic Programming for Path Planning A path-planning problem consists of a weighted directed graph with a set of n nodes N, directed links
Planning Under Uncertainty II
 Planning Under Uncertainty II Intelligent Robotics 2014/15 Bruno Lacerda Announcement No class next Monday - 17/11/2014 2 Previous Lecture Approach to cope with uncertainty on outcome of actions Markov
Planning Under Uncertainty II Intelligent Robotics 2014/15 Bruno Lacerda Announcement No class next Monday - 17/11/2014 2 Previous Lecture Approach to cope with uncertainty on outcome of actions Markov
A note on the attractor-property of infinite-state Markov chains
 A note on the attractor-property of infinite-state Markov chains Christel Baier a, Nathalie Bertrand b, Philippe Schnoebelen b a Universität Bonn, Institut für Informatik I, Germany b Lab. Specification
A note on the attractor-property of infinite-state Markov chains Christel Baier a, Nathalie Bertrand b, Philippe Schnoebelen b a Universität Bonn, Institut für Informatik I, Germany b Lab. Specification
Model checking the basic modalities of CTL with Description Logic
 Model checking the basic modalities of CTL with Description Logic Shoham Ben-David Richard Trefler Grant Weddell David R. Cheriton School of Computer Science University of Waterloo Abstract. Model checking
Model checking the basic modalities of CTL with Description Logic Shoham Ben-David Richard Trefler Grant Weddell David R. Cheriton School of Computer Science University of Waterloo Abstract. Model checking
Algorithms. NP -Complete Problems. Dong Kyue Kim Hanyang University
 Algorithms NP -Complete Problems Dong Kyue Kim Hanyang University dqkim@hanyang.ac.kr The Class P Definition 13.2 Polynomially bounded An algorithm is said to be polynomially bounded if its worst-case
Algorithms NP -Complete Problems Dong Kyue Kim Hanyang University dqkim@hanyang.ac.kr The Class P Definition 13.2 Polynomially bounded An algorithm is said to be polynomially bounded if its worst-case
Quantitative analysis with the probabilistic model checker PRISM 1
 QAPL 2005 Preliminary Version Quantitative analysis with the probabilistic model checker PRISM 1 Marta Kwiatkowska Gethin Norman David Parker 2 School of Computer Science, University of Birmingham Edgbaston,
QAPL 2005 Preliminary Version Quantitative analysis with the probabilistic model checker PRISM 1 Marta Kwiatkowska Gethin Norman David Parker 2 School of Computer Science, University of Birmingham Edgbaston,
A Survey of Partial-Observation Stochastic Parity Games
 Noname manuscript No. (will be inserted by the editor) A Survey of Partial-Observation Stochastic Parity Games Krishnendu Chatterjee Laurent Doyen Thomas A. Henzinger the date of receipt and acceptance
Noname manuscript No. (will be inserted by the editor) A Survey of Partial-Observation Stochastic Parity Games Krishnendu Chatterjee Laurent Doyen Thomas A. Henzinger the date of receipt and acceptance
Two Views on Multiple Mean-Payoff Objectives in Markov Decision Processes
 wo Views on Multiple Mean-Payoff Objectives in Markov Decision Processes omáš Brázdil Faculty of Informatics Masaryk University Brno, Czech Republic brazdil@fi.muni.cz Václav Brožek LFCS, School of Informatics
wo Views on Multiple Mean-Payoff Objectives in Markov Decision Processes omáš Brázdil Faculty of Informatics Masaryk University Brno, Czech Republic brazdil@fi.muni.cz Václav Brožek LFCS, School of Informatics
Strategy Synthesis for Markov Decision Processes and Branching-Time Logics
 Strategy Synthesis for Markov Decision Processes and Branching-Time Logics Tomáš Brázdil and Vojtěch Forejt Faculty of Informatics, Masaryk University, Botanická 68a, 60200 Brno, Czech Republic. {brazdil,forejt}@fi.muni.cz
Strategy Synthesis for Markov Decision Processes and Branching-Time Logics Tomáš Brázdil and Vojtěch Forejt Faculty of Informatics, Masaryk University, Botanická 68a, 60200 Brno, Czech Republic. {brazdil,forejt}@fi.muni.cz
Long-run Average Reward for Markov Decision Processes
 Long-run Average Reward for Markov Decision Processes Based on a paper at CAV 2017 Pranav Ashok 1, Krishnendu Chatterjee 2, Przemysław Daca 2, Jan Křetínský 1 and Tobias Meggendorfer 1 August 9, 2017 1
Long-run Average Reward for Markov Decision Processes Based on a paper at CAV 2017 Pranav Ashok 1, Krishnendu Chatterjee 2, Przemysław Daca 2, Jan Křetínský 1 and Tobias Meggendorfer 1 August 9, 2017 1
Multiobjective Optimisation An Overview
 ITNPD8/CSCU9YO Multiobjective Optimisation An Overview Nadarajen Veerapen (nve@cs.stir.ac.uk) University of Stirling Why? Classic optimisation: 1 objective Example: Minimise cost Reality is often more
ITNPD8/CSCU9YO Multiobjective Optimisation An Overview Nadarajen Veerapen (nve@cs.stir.ac.uk) University of Stirling Why? Classic optimisation: 1 objective Example: Minimise cost Reality is often more
Automata-based Verification - III
 COMP30172: Advanced Algorithms Automata-based Verification - III Howard Barringer Room KB2.20: email: howard.barringer@manchester.ac.uk March 2009 Third Topic Infinite Word Automata Motivation Büchi Automata
COMP30172: Advanced Algorithms Automata-based Verification - III Howard Barringer Room KB2.20: email: howard.barringer@manchester.ac.uk March 2009 Third Topic Infinite Word Automata Motivation Büchi Automata
An On-the-fly Tableau Construction for a Real-Time Temporal Logic
 #! & F $ F ' F " F % An On-the-fly Tableau Construction for a Real-Time Temporal Logic Marc Geilen and Dennis Dams Faculty of Electrical Engineering, Eindhoven University of Technology P.O.Box 513, 5600
#! & F $ F ' F " F % An On-the-fly Tableau Construction for a Real-Time Temporal Logic Marc Geilen and Dennis Dams Faculty of Electrical Engineering, Eindhoven University of Technology P.O.Box 513, 5600
Value Iteration. 1 Introduction. Krishnendu Chatterjee 1 and Thomas A. Henzinger 1,2
 Value Iteration Krishnendu Chatterjee 1 and Thomas A. Henzinger 1,2 1 University of California, Berkeley 2 EPFL, Switzerland Abstract. We survey value iteration algorithms on graphs. Such algorithms can
Value Iteration Krishnendu Chatterjee 1 and Thomas A. Henzinger 1,2 1 University of California, Berkeley 2 EPFL, Switzerland Abstract. We survey value iteration algorithms on graphs. Such algorithms can
Helsinki University of Technology Laboratory for Theoretical Computer Science Research Reports 66
 Helsinki University of Technology Laboratory for Theoretical Computer Science Research Reports 66 Teknillisen korkeakoulun tietojenkäsittelyteorian laboratorion tutkimusraportti 66 Espoo 2000 HUT-TCS-A66
Helsinki University of Technology Laboratory for Theoretical Computer Science Research Reports 66 Teknillisen korkeakoulun tietojenkäsittelyteorian laboratorion tutkimusraportti 66 Espoo 2000 HUT-TCS-A66
Automatic Verification of Competitive Stochastic Systems
 Automatic Verification of Competitive Stochastic Systems Taolue Chen, Vojtěch Forejt, Marta Kwiatkowska, David Parker, and Aistis Simaitis Department of Computer Science, University of Oxford, Oxford,
Automatic Verification of Competitive Stochastic Systems Taolue Chen, Vojtěch Forejt, Marta Kwiatkowska, David Parker, and Aistis Simaitis Department of Computer Science, University of Oxford, Oxford,
A Framework for Automated Competitive Analysis of On-line Scheduling of Firm-Deadline Tasks
 A Framework for Automated Competitive Analysis of On-line Scheduling of Firm-Deadline Tasks Krishnendu Chatterjee 1, Andreas Pavlogiannis 1, Alexander Kößler 2, Ulrich Schmid 2 1 IST Austria, 2 TU Wien
A Framework for Automated Competitive Analysis of On-line Scheduling of Firm-Deadline Tasks Krishnendu Chatterjee 1, Andreas Pavlogiannis 1, Alexander Kößler 2, Ulrich Schmid 2 1 IST Austria, 2 TU Wien
Binary Decision Diagrams and Symbolic Model Checking
 Binary Decision Diagrams and Symbolic Model Checking Randy Bryant Ed Clarke Ken McMillan Allen Emerson CMU CMU Cadence U Texas http://www.cs.cmu.edu/~bryant Binary Decision Diagrams Restricted Form of
Binary Decision Diagrams and Symbolic Model Checking Randy Bryant Ed Clarke Ken McMillan Allen Emerson CMU CMU Cadence U Texas http://www.cs.cmu.edu/~bryant Binary Decision Diagrams Restricted Form of
Permissive Controller Synthesis for Probabilistic Systems
 Permissive Controller Synthesis for Probabilistic Systems Klaus Dräger 3, Vojtěch Forejt 1, Marta Kwiatkowska 1, David Parker 2, and Mateusz Ujma 1 1 Department of Computer Science, University of Oxford,
Permissive Controller Synthesis for Probabilistic Systems Klaus Dräger 3, Vojtěch Forejt 1, Marta Kwiatkowska 1, David Parker 2, and Mateusz Ujma 1 1 Department of Computer Science, University of Oxford,
On Decision Problems for Probabilistic Büchi Automata
 On Decision Problems for Probabilistic Büchi Automata Christel Baier a, Nathalie Bertrand a,b, and Marcus Größer a a Technische Universität Dresden, Germany b IRISA/INRIA Rennes, France Abstract. Probabilistic
On Decision Problems for Probabilistic Büchi Automata Christel Baier a, Nathalie Bertrand a,b, and Marcus Größer a a Technische Universität Dresden, Germany b IRISA/INRIA Rennes, France Abstract. Probabilistic
Concept of Statistical Model Checking. Presented By: Diana EL RABIH
 Concept of Statistical Model Checking Presented By: Diana EL RABIH Introduction Model checking of stochastic systems Continuous-time Markov chains Continuous Stochastic Logic (CSL) Probabilistic time-bounded
Concept of Statistical Model Checking Presented By: Diana EL RABIH Introduction Model checking of stochastic systems Continuous-time Markov chains Continuous Stochastic Logic (CSL) Probabilistic time-bounded
PROBLEM SOLVING AND SEARCH IN ARTIFICIAL INTELLIGENCE
 Artificial Intelligence, Computational Logic PROBLEM SOLVING AND SEARCH IN ARTIFICIAL INTELLIGENCE Lecture 4 Metaheuristic Algorithms Sarah Gaggl Dresden, 5th May 2017 Agenda 1 Introduction 2 Constraint
Artificial Intelligence, Computational Logic PROBLEM SOLVING AND SEARCH IN ARTIFICIAL INTELLIGENCE Lecture 4 Metaheuristic Algorithms Sarah Gaggl Dresden, 5th May 2017 Agenda 1 Introduction 2 Constraint
Markov decision processes and interval Markov chains: exploiting the connection
 Markov decision processes and interval Markov chains: exploiting the connection Mingmei Teo Supervisors: Prof. Nigel Bean, Dr Joshua Ross University of Adelaide July 10, 2013 Intervals and interval arithmetic
Markov decision processes and interval Markov chains: exploiting the connection Mingmei Teo Supervisors: Prof. Nigel Bean, Dr Joshua Ross University of Adelaide July 10, 2013 Intervals and interval arithmetic
Mathematical Logic Part Three
 Mathematical Logic Part hree riday our Square! oday at 4:15PM, Outside Gates Announcements Problem Set 3 due right now. Problem Set 4 goes out today. Checkpoint due Monday, October 22. Remainder due riday,
Mathematical Logic Part hree riday our Square! oday at 4:15PM, Outside Gates Announcements Problem Set 3 due right now. Problem Set 4 goes out today. Checkpoint due Monday, October 22. Remainder due riday,
14 Random Variables and Simulation
 14 Random Variables and Simulation In this lecture note we consider the relationship between random variables and simulation models. Random variables play two important roles in simulation models. We assume
14 Random Variables and Simulation In this lecture note we consider the relationship between random variables and simulation models. Random variables play two important roles in simulation models. We assume
LTL Control in Uncertain Environments with Probabilistic Satisfaction Guarantees
 LTL Control in Uncertain Environments with Probabilistic Satisfaction Guarantees Xu Chu (Dennis) Ding Stephen L. Smith Calin Belta Daniela Rus Department of Mechanical Engineering, Boston University, Boston,
LTL Control in Uncertain Environments with Probabilistic Satisfaction Guarantees Xu Chu (Dennis) Ding Stephen L. Smith Calin Belta Daniela Rus Department of Mechanical Engineering, Boston University, Boston,
Formal Verification Techniques. Riccardo Sisto, Politecnico di Torino
 Formal Verification Techniques Riccardo Sisto, Politecnico di Torino State exploration State Exploration and Theorem Proving Exhaustive exploration => result is certain (correctness or noncorrectness proof)
Formal Verification Techniques Riccardo Sisto, Politecnico di Torino State exploration State Exploration and Theorem Proving Exhaustive exploration => result is certain (correctness or noncorrectness proof)
Solving Partial-Information Stochastic Parity Games
 Solving Partial-Information Stochastic Parity ames Sumit Nain and Moshe Y. Vardi Department of Computer Science, Rice University, Houston, Texas, 77005 Email: {nain,vardi}@cs.rice.edu Abstract We study
Solving Partial-Information Stochastic Parity ames Sumit Nain and Moshe Y. Vardi Department of Computer Science, Rice University, Houston, Texas, 77005 Email: {nain,vardi}@cs.rice.edu Abstract We study
Combining Shared Coin Algorithms
 Combining Shared Coin Algorithms James Aspnes Hagit Attiya Keren Censor Abstract This paper shows that shared coin algorithms can be combined to optimize several complexity measures, even in the presence
Combining Shared Coin Algorithms James Aspnes Hagit Attiya Keren Censor Abstract This paper shows that shared coin algorithms can be combined to optimize several complexity measures, even in the presence
Lecture Notes on Emptiness Checking, LTL Büchi Automata
 15-414: Bug Catching: Automated Program Verification Lecture Notes on Emptiness Checking, LTL Büchi Automata Matt Fredrikson André Platzer Carnegie Mellon University Lecture 18 1 Introduction We ve seen
15-414: Bug Catching: Automated Program Verification Lecture Notes on Emptiness Checking, LTL Büchi Automata Matt Fredrikson André Platzer Carnegie Mellon University Lecture 18 1 Introduction We ve seen
CONTROLLER DEPENDABILITY ANALYSIS BY PROBABILISTIC MODEL CHECKING. Marta Kwiatkowska, Gethin Norman and David Parker 1
 CONTROLLER DEPENDABILITY ANALYSIS BY PROBABILISTIC MODEL CHECKING Marta Kwiatkowska, Gethin Norman and David Parker 1 School of Computer Science, University of Birmingham, Birmingham, B15 2TT, United Kingdom
CONTROLLER DEPENDABILITY ANALYSIS BY PROBABILISTIC MODEL CHECKING Marta Kwiatkowska, Gethin Norman and David Parker 1 School of Computer Science, University of Birmingham, Birmingham, B15 2TT, United Kingdom
Constraint Solving for Program Verification: Theory and Practice by Example
 Constraint Solving for Program Verification: Theory and Practice by Example Andrey Rybalchenko Technische Universität München Abstract. Program verification relies on the construction of auxiliary assertions
Constraint Solving for Program Verification: Theory and Practice by Example Andrey Rybalchenko Technische Universität München Abstract. Program verification relies on the construction of auxiliary assertions
Computation of Efficient Nash Equilibria for experimental economic games
 International Journal of Mathematics and Soft Computing Vol.5, No.2 (2015), 197-212. ISSN Print : 2249-3328 ISSN Online: 2319-5215 Computation of Efficient Nash Equilibria for experimental economic games
International Journal of Mathematics and Soft Computing Vol.5, No.2 (2015), 197-212. ISSN Print : 2249-3328 ISSN Online: 2319-5215 Computation of Efficient Nash Equilibria for experimental economic games
Automata-based Verification - III
 CS3172: Advanced Algorithms Automata-based Verification - III Howard Barringer Room KB2.20/22: email: howard.barringer@manchester.ac.uk March 2005 Third Topic Infinite Word Automata Motivation Büchi Automata
CS3172: Advanced Algorithms Automata-based Verification - III Howard Barringer Room KB2.20/22: email: howard.barringer@manchester.ac.uk March 2005 Third Topic Infinite Word Automata Motivation Büchi Automata
A Survey of Stochastic ω-regular Games
 A Survey of Stochastic ω-regular Games Krishnendu Chatterjee Thomas A. Henzinger EECS, University of California, Berkeley, USA Computer and Communication Sciences, EPFL, Switzerland {c krish,tah}@eecs.berkeley.edu
A Survey of Stochastic ω-regular Games Krishnendu Chatterjee Thomas A. Henzinger EECS, University of California, Berkeley, USA Computer and Communication Sciences, EPFL, Switzerland {c krish,tah}@eecs.berkeley.edu
ONR MURI AIRFOILS: Animal Inspired Robust Flight with Outer and Inner Loop Strategies. Calin Belta
 ONR MURI AIRFOILS: Animal Inspired Robust Flight with Outer and Inner Loop Strategies Provable safety for animal inspired agile flight Calin Belta Hybrid and Networked Systems (HyNeSs) Lab Department of
ONR MURI AIRFOILS: Animal Inspired Robust Flight with Outer and Inner Loop Strategies Provable safety for animal inspired agile flight Calin Belta Hybrid and Networked Systems (HyNeSs) Lab Department of
Chapter 11. Approximation Algorithms. Slides by Kevin Wayne Pearson-Addison Wesley. All rights reserved.
 Chapter 11 Approximation Algorithms Slides by Kevin Wayne. Copyright @ 2005 Pearson-Addison Wesley. All rights reserved. 1 Approximation Algorithms Q. Suppose I need to solve an NP-hard problem. What should
Chapter 11 Approximation Algorithms Slides by Kevin Wayne. Copyright @ 2005 Pearson-Addison Wesley. All rights reserved. 1 Approximation Algorithms Q. Suppose I need to solve an NP-hard problem. What should
Complexity Theory VU , SS The Polynomial Hierarchy. Reinhard Pichler
 Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Outline. Complexity Theory EXACT TSP. The Class DP. Definition. Problem EXACT TSP. Complexity of EXACT TSP. Proposition VU 181.
 Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Generalized Parity Games
 Generalized Parity Games Krishnendu Chatterjee 1, Thomas A. Henzinger 1,2, and Nir Piterman 2 1 University of California, Berkeley, USA 2 EPFL, Switzerland c krish@eecs.berkeley.edu, {tah,nir.piterman}@epfl.ch
Generalized Parity Games Krishnendu Chatterjee 1, Thomas A. Henzinger 1,2, and Nir Piterman 2 1 University of California, Berkeley, USA 2 EPFL, Switzerland c krish@eecs.berkeley.edu, {tah,nir.piterman}@epfl.ch
Optimal Control of Markov Decision Processes with Temporal Logic Constraints
 Optimal Control of Markov Decision Processes with Temporal Logic Constraints Xuchu (Dennis) Ding Stephen L. Smith Calin Belta Daniela Rus Abstract In this paper, we develop a method to automatically generate
Optimal Control of Markov Decision Processes with Temporal Logic Constraints Xuchu (Dennis) Ding Stephen L. Smith Calin Belta Daniela Rus Abstract In this paper, we develop a method to automatically generate
Polynomial-Time Verification of PCTL Properties of MDPs with Convex Uncertainties
 Polynomial-Time Verification of PCTL Properties of MDPs with Convex Uncertainties Alberto Alessandro Angelo Puggelli Wenchao Li Alberto L. Sangiovanni-Vincentelli Sanjit A. Seshia Electrical Engineering
Polynomial-Time Verification of PCTL Properties of MDPs with Convex Uncertainties Alberto Alessandro Angelo Puggelli Wenchao Li Alberto L. Sangiovanni-Vincentelli Sanjit A. Seshia Electrical Engineering
Probabilistic Model Checking Michaelmas Term Dr. Dave Parker. Department of Computer Science University of Oxford
 Probabilistic Model Checking Michaelmas Term 2011 Dr. Dave Parker Department of Computer Science University of Oxford Overview CSL model checking basic algorithm untimed properties time-bounded until the
Probabilistic Model Checking Michaelmas Term 2011 Dr. Dave Parker Department of Computer Science University of Oxford Overview CSL model checking basic algorithm untimed properties time-bounded until the
Polynomial-Time Verification of PCTL Properties of MDPs with Convex Uncertainties
 Polynomial-Time Verification of PCTL Properties of MDPs with Convex Uncertainties Alberto Puggelli, Wenchao Li, Alberto L. Sangiovanni-Vincentelli, Sanjit A. Seshia Department of Electrical Engineering
Polynomial-Time Verification of PCTL Properties of MDPs with Convex Uncertainties Alberto Puggelli, Wenchao Li, Alberto L. Sangiovanni-Vincentelli, Sanjit A. Seshia Department of Electrical Engineering
Alan Bundy. Automated Reasoning LTL Model Checking
 Automated Reasoning LTL Model Checking Alan Bundy Lecture 9, page 1 Introduction So far we have looked at theorem proving Powerful, especially where good sets of rewrite rules or decision procedures have
Automated Reasoning LTL Model Checking Alan Bundy Lecture 9, page 1 Introduction So far we have looked at theorem proving Powerful, especially where good sets of rewrite rules or decision procedures have
Constraint Solving for Program Verification: Theory and Practice by Example
 Constraint Solving for Program Verification: Theory and Practice by Example Andrey Rybalchenko Technische Universität München Abstract. Program verification relies on the construction of auxiliary assertions
Constraint Solving for Program Verification: Theory and Practice by Example Andrey Rybalchenko Technische Universität München Abstract. Program verification relies on the construction of auxiliary assertions
Department of Computer Science CS-RR-16-03
 Department of Computer Science Compositional Strategy Synthesis for Stochastic ames with Multiple Objectives Nicolas Basset, Marta Kwiatkowska and Clemens Wiltsche CS-RR-6-03 Department of Computer Science,
Department of Computer Science Compositional Strategy Synthesis for Stochastic ames with Multiple Objectives Nicolas Basset, Marta Kwiatkowska and Clemens Wiltsche CS-RR-6-03 Department of Computer Science,
arxiv: v3 [cs.gt] 10 Apr 2009
![arxiv: v3 [cs.gt] 10 Apr 2009 arxiv: v3 [cs.gt] 10 Apr 2009](/thumbs/72/66277407.jpg) The Complexity of Nash Equilibria in Simple Stochastic Multiplayer Games Michael Ummels and Dominik Wojtczak,3 RWTH Aachen University, Germany E-Mail: ummels@logicrwth-aachende CWI, Amsterdam, The Netherlands
The Complexity of Nash Equilibria in Simple Stochastic Multiplayer Games Michael Ummels and Dominik Wojtczak,3 RWTH Aachen University, Germany E-Mail: ummels@logicrwth-aachende CWI, Amsterdam, The Netherlands
On Equilibria of Distributed Message-Passing Games
 On Equilibria of Distributed Message-Passing Games Concetta Pilotto and K. Mani Chandy California Institute of Technology, Computer Science Department 1200 E. California Blvd. MC 256-80 Pasadena, US {pilotto,mani}@cs.caltech.edu
On Equilibria of Distributed Message-Passing Games Concetta Pilotto and K. Mani Chandy California Institute of Technology, Computer Science Department 1200 E. California Blvd. MC 256-80 Pasadena, US {pilotto,mani}@cs.caltech.edu
Lecture 2: Symbolic Model Checking With SAT
 Lecture 2: Symbolic Model Checking With SAT Edmund M. Clarke, Jr. School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 (Joint work over several years with: A. Biere, A. Cimatti, Y.
Lecture 2: Symbolic Model Checking With SAT Edmund M. Clarke, Jr. School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 (Joint work over several years with: A. Biere, A. Cimatti, Y.
Multi-Objective Planning with Multiple High Level Task Specifications
 Multi-Objective Planning with Multiple High Level Task Specifications Seyedshams Feyzabadi Stefano Carpin Abstract We present an algorithm to solve a sequential stochastic decision making problem whereby
Multi-Objective Planning with Multiple High Level Task Specifications Seyedshams Feyzabadi Stefano Carpin Abstract We present an algorithm to solve a sequential stochastic decision making problem whereby
Probabilistic Model Checking of Randomised Distributed Protocols using PRISM
 Probabilistic Model Checking of Randomised Distributed Protocols using PRISM Marta Kwiatkowska University of Birmingham VPSM PhD School, Copenhagen, October 2006 Tutorial overview Part I - Probabilistic
Probabilistic Model Checking of Randomised Distributed Protocols using PRISM Marta Kwiatkowska University of Birmingham VPSM PhD School, Copenhagen, October 2006 Tutorial overview Part I - Probabilistic
Randomness for Free. 1 Introduction. Krishnendu Chatterjee 1, Laurent Doyen 2, Hugo Gimbert 3, and Thomas A. Henzinger 1
 Randomness for Free Krishnendu Chatterjee 1, Laurent Doyen 2, Hugo Gimbert 3, and Thomas A. Henzinger 1 1 IST Austria (Institute of Science and Technology Austria) 2 LSV, ENS Cachan & CNRS, France 3 LaBri
Randomness for Free Krishnendu Chatterjee 1, Laurent Doyen 2, Hugo Gimbert 3, and Thomas A. Henzinger 1 1 IST Austria (Institute of Science and Technology Austria) 2 LSV, ENS Cachan & CNRS, France 3 LaBri
Notes. Corneliu Popeea. May 3, 2013
 Notes Corneliu Popeea May 3, 2013 1 Propositional logic Syntax We rely on a set of atomic propositions, AP, containing atoms like p, q. A propositional logic formula φ Formula is then defined by the following
Notes Corneliu Popeea May 3, 2013 1 Propositional logic Syntax We rely on a set of atomic propositions, AP, containing atoms like p, q. A propositional logic formula φ Formula is then defined by the following
Running time analysis of a multi-objective evolutionary algorithm on a simple discrete optimization problem
 Research Collection Working Paper Running time analysis of a multi-objective evolutionary algorithm on a simple discrete optimization problem Author(s): Laumanns, Marco; Thiele, Lothar; Zitzler, Eckart;
Research Collection Working Paper Running time analysis of a multi-objective evolutionary algorithm on a simple discrete optimization problem Author(s): Laumanns, Marco; Thiele, Lothar; Zitzler, Eckart;
What You Must Remember When Processing Data Words
 What You Must Remember When Processing Data Words Michael Benedikt, Clemens Ley, and Gabriele Puppis Oxford University Computing Laboratory, Park Rd, Oxford OX13QD UK Abstract. We provide a Myhill-Nerode-like
What You Must Remember When Processing Data Words Michael Benedikt, Clemens Ley, and Gabriele Puppis Oxford University Computing Laboratory, Park Rd, Oxford OX13QD UK Abstract. We provide a Myhill-Nerode-like
Finite-State Transducers
 Finite-State Transducers - Seminar on Natural Language Processing - Michael Pradel July 6, 2007 Finite-state transducers play an important role in natural language processing. They provide a model for
Finite-State Transducers - Seminar on Natural Language Processing - Michael Pradel July 6, 2007 Finite-state transducers play an important role in natural language processing. They provide a model for
Unbounded, Fully Symbolic Model Checking of Timed Automata using Boolean Methods
 Unbounded, Fully Symbolic Model Checking of Timed Automata using Boolean Methods Sanjit A. Seshia and Randal E. Bryant Computer Science Department Carnegie Mellon University Verifying Timed Embedded Systems
Unbounded, Fully Symbolic Model Checking of Timed Automata using Boolean Methods Sanjit A. Seshia and Randal E. Bryant Computer Science Department Carnegie Mellon University Verifying Timed Embedded Systems
Evaluation and Validation
 Evaluation and Validation Jian-Jia Chen (Slides are based on Peter Marwedel) TU Dortmund, Informatik 12 Germany Springer, 2010 2016 年 01 月 05 日 These slides use Microsoft clip arts. Microsoft copyright
Evaluation and Validation Jian-Jia Chen (Slides are based on Peter Marwedel) TU Dortmund, Informatik 12 Germany Springer, 2010 2016 年 01 月 05 日 These slides use Microsoft clip arts. Microsoft copyright
Logic Model Checking
 Logic Model Checking Lecture Notes 10:18 Caltech 101b.2 January-March 2004 Course Text: The Spin Model Checker: Primer and Reference Manual Addison-Wesley 2003, ISBN 0-321-22862-6, 608 pgs. the assignment
Logic Model Checking Lecture Notes 10:18 Caltech 101b.2 January-March 2004 Course Text: The Spin Model Checker: Primer and Reference Manual Addison-Wesley 2003, ISBN 0-321-22862-6, 608 pgs. the assignment
On Model Checking Techniques for Randomized Distributed Systems. Christel Baier Technische Universität Dresden
 On Model Checking Techniques for Randomized Distributed Systems Christel Baier Technische Universität Dresden joint work with Nathalie Bertrand Frank Ciesinski Marcus Größer / 6 biological systems, resilient
On Model Checking Techniques for Randomized Distributed Systems Christel Baier Technische Universität Dresden joint work with Nathalie Bertrand Frank Ciesinski Marcus Größer / 6 biological systems, resilient
A Symbolic Decision Procedure for Symbolic Alternating Finite Automata
 MFPS 2010 A Symbolic Decision Procedure for Symbolic Alternating Finite Automata Loris D Antoni 1 Zachary Kincaid 2 Fang Wang 1 1 University of Wisconsin-Madison 2 Princeton University Abstract We introduce
MFPS 2010 A Symbolic Decision Procedure for Symbolic Alternating Finite Automata Loris D Antoni 1 Zachary Kincaid 2 Fang Wang 1 1 University of Wisconsin-Madison 2 Princeton University Abstract We introduce
Solving Zero-Sum Security Games in Discretized Spatio-Temporal Domains
 Solving Zero-Sum Security Games in Discretized Spatio-Temporal Domains APPENDIX LP Formulation for Constant Number of Resources (Fang et al. 3) For the sae of completeness, we describe the LP formulation
Solving Zero-Sum Security Games in Discretized Spatio-Temporal Domains APPENDIX LP Formulation for Constant Number of Resources (Fang et al. 3) For the sae of completeness, we describe the LP formulation
Computing Laboratory STOCHASTIC GAMES FOR VERIFICATION OF PROBABILISTIC TIMED AUTOMATA. Marta Kwiatkowska Gethin Norman David Parker CL-RR-09-05
 Computing Laboratory STOCHASTIC AMES FOR VERIFICATION OF PROBABILISTIC TIMED AUTOMATA Marta Kwiatkowska ethin Norman David Parker CL-RR-09-05 Oxford University Computing Laboratory Wolfson Building, Parks
Computing Laboratory STOCHASTIC AMES FOR VERIFICATION OF PROBABILISTIC TIMED AUTOMATA Marta Kwiatkowska ethin Norman David Parker CL-RR-09-05 Oxford University Computing Laboratory Wolfson Building, Parks
The Stevens-Stirling-Algorithm For Solving Parity Games Locally Requires Exponential Time
 The Stevens-Stirling-Algorithm For Solving Parity Games Locally Requires Exponential Time Oliver Friedmann Institut für Informatik, LMU München Oliver.Friedmann@googlemail.com Abstract. This paper presents
The Stevens-Stirling-Algorithm For Solving Parity Games Locally Requires Exponential Time Oliver Friedmann Institut für Informatik, LMU München Oliver.Friedmann@googlemail.com Abstract. This paper presents
Decentralized Control of Stochastic Systems
 Decentralized Control of Stochastic Systems Sanjay Lall Stanford University CDC-ECC Workshop, December 11, 2005 2 S. Lall, Stanford 2005.12.11.02 Decentralized Control G 1 G 2 G 3 G 4 G 5 y 1 u 1 y 2 u
Decentralized Control of Stochastic Systems Sanjay Lall Stanford University CDC-ECC Workshop, December 11, 2005 2 S. Lall, Stanford 2005.12.11.02 Decentralized Control G 1 G 2 G 3 G 4 G 5 y 1 u 1 y 2 u
The priority promotion approach to parity games
 The priority promotion approach to parity games Massimo Benerecetti 1, Daniele Dell Erba 1, and Fabio Mogavero 2 1 Università degli Studi di Napoli Federico II 2 Università degli Studi di Verona Abstract.
The priority promotion approach to parity games Massimo Benerecetti 1, Daniele Dell Erba 1, and Fabio Mogavero 2 1 Università degli Studi di Napoli Federico II 2 Università degli Studi di Verona Abstract.
Lecture 26. Daniel Apon
 Lecture 26 Daniel Apon 1 From IPPSPACE to NPPCP(log, 1): NEXP has multi-prover interactive protocols If you ve read the notes on the history of the PCP theorem referenced in Lecture 19 [3], you will already
Lecture 26 Daniel Apon 1 From IPPSPACE to NPPCP(log, 1): NEXP has multi-prover interactive protocols If you ve read the notes on the history of the PCP theorem referenced in Lecture 19 [3], you will already
Strategy Synthesis for Stochastic Games with Multiple Long-Run Objectives
 Strategy Synthesis for Stochastic Games with Multiple Long-Run Objectives Nicolas Basset, Marta Kwiatkowska, Ufuk Topcu, and Clemens Wiltsche Department of Computer Science, University of Oxford, United
Strategy Synthesis for Stochastic Games with Multiple Long-Run Objectives Nicolas Basset, Marta Kwiatkowska, Ufuk Topcu, and Clemens Wiltsche Department of Computer Science, University of Oxford, United
MDP Preliminaries. Nan Jiang. February 10, 2019
 MDP Preliminaries Nan Jiang February 10, 2019 1 Markov Decision Processes In reinforcement learning, the interactions between the agent and the environment are often described by a Markov Decision Process
MDP Preliminaries Nan Jiang February 10, 2019 1 Markov Decision Processes In reinforcement learning, the interactions between the agent and the environment are often described by a Markov Decision Process

 }w!"#$%&'()+,-./02345
}w!"#$%&'()+,-./02345